Learning Evolving and Emerging Topics in Social Media: A Dynamic NMF approach with Temporal Regularization
|
|
|
- Felicia Price
- 7 years ago
- Views:
Transcription
1 Learning Evolving and Emerging Topics in Social Media: A Dynamic NMF approach with Temporal Regularization Ankan Saha Department of Computer Science University of Chicago, Chicago IL ankans@cs.uchicago.edu Vikas Sindhwani IBM T.J. Watson Research Center Yorktown Heights, NY vsindhw@us.ibm.com ABSTRACT As massive repositories of real-time human commentary, social media platforms have arguably evolved far beyond passive facilitation of online social interactions. Rapid analysis of information content in online social media streams (news articles, blogs,tweets etc.) is the need of the hour as it allows business and government bodies to understand public opinion about products and policies. In most of these settings, data points appear as a stream of high dimensional feature vectors. Guided by real-world industrial deployment scenarios, we revisit the problem of online learning of topics from streaming social media content. On one hand, the topics need to be dynamically adapted to the statistics of incoming datapoints, and on the other hand, early detection of rising new trends is important in many applications. We propose an online nonnegative matrix factorization framework to capture the evolution and emergence of themes in unstructured text under a novel temporal regularization framework. We develop scalable optimization algorithms for our framework, propose a new set of evaluation metrics, and report promising empirical results on traditional TDT tasks as well as streaming Twitter data. Our system is able to rapidly capture emerging themes, track existing topics over time while maintaining temporal consistency and continuity in user views, and can be explicitly configured to bound the amount of information being presented to the user. Categories and Subject Descriptors H.3.3 [Information Storage and Retrieval]: Information Search and RetrievalRetrieval Models General Terms Algorithms, Experimentation Keywords Dictionary Learning, NMF, Topic Models, Time Series Analysis Work done as a summer intern at IBM Research Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee. WSDM 12, February 8 12, 2012, Seattle, Washington, USA. Copyright 2012 ACM /12/02...$ INTRODUCTION Over the last few years, the growth and ease of internet access accompanied by the advent of various facets of online social media viz. blogs, social networks and lately, twitter, has provided a vast continuous supply of dynamic diverse information content. When analyzed with appropriate statistical and computational tools, social media content can be turned into invaluable scientific and business insights. A recent large-scale study [9] of 500 million tweets generated in 2009, for example, concluded that the appearance of flu-related topics in Twitter was highly predictive of future influenza rates in the general population. While the early years of social media platforms were focussed on developing software infrastructure for connecting people, the emphasis has only very recently begun to shift towards understanding collective public opinion by using deep, data-driven social media analytics [21]. One of the most basic and necessary tasks that arises in this setting is to organize streaming social media into coherent threads of discussion that can be easily analyzed and utilized to improve various services that are affected by social media. In this paper, we argue that traditional topic detection and tracking methodologies historically rooted in Information Retrieval literature need to be revisited in the context of the demands of these emerging applications. Over regular intervals of time (which might be per day or even every few hours), any user who is continuously mining social media content, has the following natural expectations from the system: (1) to be alerted to any new emerging themes of discussion that is fast gathering steam in social media, (2) to be able to follow the evolution of existing topics that have already been identified as being of particular interest and (3) not to be overloaded with excessive bits of information that is time consuming to sift through. Several tradeoffs become naturally evident in the design of a satisfactory system. By definition, an emerging theme is one that has not been observed before and is somewhat of an anomaly in the data stream, not necessarily distinguishable from noise when first encountered. Yet, not every anomaly can be presented to the user as an early warning as this would lead to excessive information overload in a large-scale setting. At the same time, information presented in the past sets up expectations for what the user expects in the future, e.g., the ability to clearly see how a topic has evolved possibly in response to marketing or PR interventions. What is needed, is an ability to distinguish valid emerging topics (with steep information content) from noise and some method to continuously summarize essential data character-
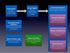
2 istics in terms of a small number of human interpretable components. Several social media monitoring tools rely on communicating individual keywords whose usage has rapidly increased in recent time, as proxies for emerging topics. Such a methodology has obvious limitations in characterizing the separate strands of conversations that may have simulatenously Joemerged in the data stream. In this paper, we describe a system for online analysis of streaming text using more rigorous machine learning and optimization methodologies in the form of powerful topic modeling and non negative matrix factorization techniques. Unlike previously proposed IR techniques, our approach incorporates special algorithmic constructs to attempt to detect emerging topics early, maintains temporal continuity while evolving existing topics in response to the statistics of incoming data, and allows the amount of information being presented to the user to be explictly configured. While we demonstrate these ideas in the context of online topic modeling, our methods apply much more broadly to early detection problems in more general signal separation and decomposition settings. A preliminary version of this work appeared in the NIPS 2010 workshop on Social Computing. 2. RELATED WORK AND OVERVIEW Over the last decade, different methods have been used for topic modeling and detection from a corpus of documents available as a batch or an online stream. Early impetus in this research was provided by DARPA sponsorship of Topic Detection and Tracking evaluations which led to the design of several TDT engines [26, 1]. One of the best performing engines, GAC-INCR [26], uses a clustering algorithm (GAC) to cluster incoming new data in the first phase, and then, based on a similarity/novelty threshold, either merges each of these clusters with those discovered in the past or treat them as a new cluster/topic to be tracked going forward. Probabilistic latent semantic indexing (plsi) [16] and Latent Dirichlet Allocation (LDA) [5] are probabilistic methods that have found remarkable success in building topic models of text. Both of them characterize topics as a multinomial distribution over a vocabulary of words rather than clusters of documents. The topics are treated as latent variables and the joint probability of the terms and documents is represented as the mixture of conditional probabilities over the latent topics which are typically inferred by maximum likelihood or Bayesian procedures that involve either variational inference or Gibbs sampling techniques. The notion of a topic is then communicated to a user via keywords that have highest mass in these learnt distributions.the two models are essentially equivalent [12], the key difference being that while the PLSI approach may be viewed as maximum likelihood estimation of model parameters, LDA applies a Dirichlet prior on them. Variants of plsi and LDA have been proposed for online and dynamic topic modeling (see [6, 13, 15, 4, 2] and references therein). Another line of seemingly unrelated work which finds use in topic modeling is that of dictionary learning and nonprobabilistic matrix factorizations[20]. Dictionary Learning is the problem of estimating a collection of basis vectors over which a given data collection can be accurately reconstructed, often with sparse encodings. It may be formulated in terms of uncovering low-rank structure in the data using matrix factorizations possibly with sparsity-inducing priors [20]. These are closely related to probabilistic topic models (plsi, LDA) for textual datasets. In this paper, we propose a framework for online topic detection to handle streaming non-negative data matrices with possibly growing number of components. Our methods are rooted in non-negative matrix factorizations (NMF) [18, 25] whose unregularized variants for (generalized) KL-divergence minimization can be shown to be equivalent to plsi [10]. For squared loss, NMF finds a low-rank approximation to a data matrix X by minimizing the Frobenius norm of X WH 2 fro under non-negativity and scaling constraints on the factors W and H. Finding the minimum rank NMF of X is a non-convex problem and the general algorithm used is due to the multiplicative weight methods of [18]. It is common to add some form of l 1/l 2 regularization, generally to encourage sparse factors and prevent overfitting. If X is an N D document-term matrix, then W is a N K matrix of topic encodings of documents where each column corresponds to a topic and represents the contribution of the documents to the particular topic. H is a K D matrix of topic-word associations, whose rows are the dictionary elements learnt by the NMF approach. Figure 1: A snapshot of the online NMF system for tracking and capturing topics t 3 t 2 sliding window ω t 1 X(t 1) t W(t) X(t) INPUT OUTPUT H(t) time } evolving emerging We give a preview of our online learning framework in Figure 1. At any given timepoint, our system consumes the incoming data together with recently seen documents over a short time window. The output is an NMF that yields a new set of topics together with encodings for the most recently seen documents. These topics can be divided into two sets, which we call evolving and emerging sets. The evolving set is a smooth evolution of previously discovered topics. This evolution is constrained to prevent excessive drift or change that can negatively affect user interpretability. The emerging set comprises of a small number of topics injected into the model for the purpose of detecting emerging themes. This is done by finding the optimal word distributions that show rising temporal trends after correcting for spurious discontinuities. We show that constrained topic evolution and trend estimation can be posed naturally as extended matrix factorization problems that infact also have a link to margin-based
3 learning methods such as SVMs. We then develop scalable alternating optimization algorithms using efficient schemes to solve rank-one subproblems. Once the online model is learnt, the emerging set (whose size can be configured) is presented to the user who may choose to explicitly discard a subset from current consideration. Going forward in time, the emerging set becomes part of the evolving set, and new emerging bandwidth is introduced for the next timepoint. The use of explicit temporal regularizers for emerging topic detection in a matrix factorization framework in this manner is novel to the best of our knowledge. Prior work on online matrix factorization has not dealt with low-rank approximations with gradually increasing rank. In the next section, we describe the details of our online models. Notation: In the sequel we abuse notation to denote h i as the i th row of H and h ij = H ij. D denotes the D dimensional simplex. [K] refers to the set {1, 2... K} and 0 d, 1 d refers to the vector of all 0 s and 1 s of dimension d. 3. DYNAMIC NMF FRAMEWORK Let {X(t) R N(t) D(t), t = 1, 2...t,..} denote a sequence of streaming matrices where each row of X(t) represents an observation whose time stamp is t. For simplicity in notation and exposition, we will assume that D(t) = D for all t. In topic modeling applications over streaming documents, X(t) will represent the highly sparse document-term matrix observed at time t 1. We will use the conventional vector space model [23] used in the information retrieval literature. Terms in a document are statistically weighted using standard measures Term Frequency(T F ) and Inverse-Document Frequency(IDF ). The (d, r)-th entry of X(t) corresponding to document d and term r is given by X(t)(d, r) = (1 + log 2 T F (d, r)) log 2 IDF (r) C where C normalizes the representation to unit norm l 2 norm vectors. We use X(t 1, t 2) to denote the document-term matrix formed by vertically concatenating {X(t), t 1 t t 2}. Since we operate in an online framework, we introduce a short sliding time window ω over which trends are estimated at every time point. At the current time point t, our model consumes the incoming data X(t) and appends to documents seen in a recent ω-window, X(t ω + 1, t). It generates a factorization (W, H(t)) comprising of K(t) topics (see equation (1)). Each column of W and each row of H(t) corresponds to a topic. Note that W has the same number of rows as all the documents accumulated over the ω-window ending at time point t. The last N(t) rows of W (corresponding to X(t)) represent the weight matrix W(t) at time t. Furthermore, since H(t) is the matrix of topic-term dependence at time t, we normalize each row of H(t) so that it resembles a probability distribution of words over the corresponding topic. This online factorization mechanism is designed to satisfy two considerations: The first K(t 1) topics in H(t) must be smooth evolutions of the K(t 1) topics found upto the previous 1 As new documents come in and new terms are identified, we expand the vocabulary and zero-pad the previous matrices so that at the current time t, all previous and the current documents have a representation over the same vocabulary space. time point in H(t 1). These topics are assumed to be gradually changing over time (with steady temporal profile). We call this the evolving set and introduce an evolution parameter, δ, which constrains the evolving set so that each entry of these K(t 1) topics in H(t) resides within a box of size δ on the probability simplex around their previous values in H(t 1) (see equation (4)). With minor modifications, δ can also be made topic or word-specific e.g., to take topic volatility or word dominance into account. The second consideration is the fast detection of emerging topics. At each time point, we inject additional topic bandwidth for this purpose which constitute the K(t) K(t 1) remaining rows of H(t). This represents the emerging set. Thus the topic variable H(t) can be partitioned into an evolving set of K(t 1) topics, H ev, and an emerging set of K em topics H em where K(t) = K(t 1) + K em. It should be noted that the set H ev is an increasing set over time. Older topics that are no longer active may be removed for efficiency, but for simplicity, we do not discuss such a removal process in this paper. As new discussions take place over social forums, new topics emerge and are added to the system. Furthermore, we assume that emerging topics can be distinguished from noise based on their temporal profile. In other words, the number of documents that a true emerging topic associates with rapidly increases. This may occur due to a sudden large increase in discussions about the topic in documents over time. The discussion above motivates the following objective function that is optimized at every time point t. (W, H(t)) = argmin X(t ω + 1, t) WH 2 fro + µω(w) W,H (1) where Ω plays the role of a temporal emergence regularizer (described in section 4) which penalizes static temporal profiles and encourages the discovery of topics whose temporal profiles exhibit steep increase. These intuitively correspond to the emerging topics. This objective function is minimized under the following non-negativity, normalization and evolution constraints as discussed above. W, H 0 (2) D H ij = 1 i [K(t 1) + K em ] j=1 min(h ij(t 1) δ, 0) H ij max(h ij(t 1) + δ, 1), i [K(t 1)], j [D] The last equation (4) enforces the smoothness condition for the evolving topics H ev by forcing the individual topic components at time t to stay within δ of their value at the previous time step. We then extract W(t) from the bottom rows of W that correspond to X(t) which came in at time t. Since W(t) stores the weights assigned to each topic by the documents, the i th document (row) in X(t) is tagged in the following way: π system(i) = argmax W(t)(i, j) (5) j (3) (4)
4 Figure 2: Hodrick Prescott Trend Filtering original λ=100 λ=1.0 λ=0.1 λ= Time. Thus each document at time t is assigned to the corresponding most dominating topic by the system. Note that this gives a clustering of the documents per topic. In the next section, we define the emergence regularization operator Ω(W) that forms an essential component of our optimization algorithm. 4. EMERGENCE REGULARIZATION In this section, we formulate the temporal regularization operator Ω(W) by chaining together trend extraction with a margin-based loss function to penalize static or decaying topics. We begin with a brief introduction to trend filtering. 4.1 Hodrick-Prescott (HP) Trend Filtering Let {y t} T t=1 be a univariate time-series which is composed of an unknown, slowly varying trend component {x t} T t=1 perturbed by random noise {α t} T t=1. Trend Filtering is the task of recovering the trend component {x t} given the observations {y t}. The Hodrick-Prescott filter is an approach to estimate the trend assuming that it is smooth and that the random residual is small. It is based on solving the following optimization problem: argmin {x t } 1 2 T T 1 (y i x i) 2 + λ ((x t+1 x t) (x t x t 1)) 2 i=1 t=2 (6) The first term tries to minimize the reconstruction error while the second term penalizes the change in the underlying time series over successive time points thus enforcing the concept that the underlying trend component is smooth. Let us introduce the second order difference matrix D R (T 2) T such that D ii = 1, D i,i+1 = 2 and D i,i+2 = 1 for all i [T 2]. It is easy to see that the solution to the optimization problem of Equation 6 is given by: x = [I + 2λD D] 1 y where we use the notation y = (y 1... y T ), x = (x 1... x T ). In the sequel, we use F to denote [I +2λD D] 1, the linear smoothing operator associated with the Hodrick-Prescott Filter. Given the time series y, the Hodrick-Prescott (HP) trend estimate simply is x = F y. Figure 2 captures the notion of Hodrick-Prescott trend filtering where a smooth reconstruction of the observed signal is demonstrated for different values of the parameter λ. In our experiments, we use λ = Loss Function for Emerging Trends Let x = F y be the HP trend of the time series y. Let D be the forward difference operator, i.e., the only non-zero entries of D are: D i,i = 1 and D i,i+1 = 1. If z = Dx, then z i = x i+1 x i reflects the discrete numerical gradient in the trend x. Given z i, we define a margin based loss function (the l 2 hinge loss), L(z i) = c i max(0, ν z i) 2. If the growth in the trend at time i is sufficient, i.e., greater than ν, the loss evaluates to 0. If the growth is insufficient, the loss evaluates to c i(ν z i) 2 where c i is the weight of timepoint i. We observed experimentally that the best results are given by weights c i s which typically increase with i. For a vector z, the loss is added over the time components. In terms of the original time series y, this loss function is, T 1 L(y) = c i max(0, ν (DF y) i) 2 (7) i=1 Optimization Problem: As documents arrive over t {1, 2,... T }, we use S to denote a T N time-document matrix, where S(i, j) = 1 if the document j has time stamp i. Noting that each column w of W, denotes the document associations for a given topic, Sw captures the time series of total contribution of the topic corresponding to w, which is analogous to the temporal profile of the topic and is expected to rapidly grow for emerging topics. Finally, we concretize (1) as the following optimization problem argmin W,H 0 X WH 2 fro + µ w i W em L(Sw i) (8) subject to constraints in equations 3 and 4. Note that the sum in the penalization term only runs over the emerging topic variables. 5. OPTIMIZATION ALGORITHMS We approximate X as the sum of rank-one matrices w ih i and optimize cyclically over individual w i and h i variables while keeping all other variables fixed. This results in three specific sub-problems, each of which requires an efficient projection of a vector onto an appropriate space. Optimization of rank-one subproblems has been previously shown to be very effective for standard NMFs [14, 7] and is also reminiscent of the K-SVD approach for dictionary learning [11]. Optimization over h i: Firstly note that since the regularization term is independent of h i, it does not contribute to this optimization problem. Holding all variables except h i fixed and omitting additive constants independent of h i, (8) can be reduced to argmin hi C R wih 2 i where fro R = X j i w jh j (9) is the residual matrix independent of h i. Note that R is the difference of a sparse matrix and rank one matrices. While it can possibly be a dense matrix, we never need to evaluate it explicitly. In particular, our algorithm only needs to compute matrix vector products against R, namely Rh i = Xh i j i w j(h j h i) and R w i = X w i j i h j(w j w i) We use sparse matrix computations to evaluate Xh i and X w i thus allowing us to efficiently compute the updates without evaluating R explicitly.
5 Algorithm 1: Online Learning Algorithm for Topic Evolution and Emergence. Input: New data X(t) R N(t) D, Old data X(t ω + 1, t 1), Previous topic matrix H(t 1) of size K(t 1) D, Emerging Topic Bandwidth B, Hyperparameters: Evolution δ, Emergence µ, Hinge ν. Output: W(t) R N(t) K(t), H(t) R K(t) D ɛ = 10 6 Set K(t) = K(t 1) + B Define X = X(t ω + 1, t) R N D Initialize W = W init, H = H init where W init R N K(t), H init R K(t) D (details in Section 5). while not(converge) do for i = 1,... K(t) do if i K(t 1) then Rh i = Xh i j i wj(h j h i) Evolving w i: w ij = max ( 0, 1 h i 2 (Rh i) j ). else Emerging w i (use Projected Gradient): w i = argmin w 0 w Rhi/ h i µ T 1 h i 2 j=1 cj max(0, νj q j w i) 2 (see Section 5). end if end for for i = 1,... K(t) do R w i = X w i j i hj(w j w i) if i K(t 1) then l ij = max (0, h ij(t 1) δ), u ij = min (h ij(t 1) + δ, 1). Evolving h i (Simplex projection with box constraints): h i = argmin h C1 h R w i/ w i 2 2 where C 1 = {h : h D, l ij h j u ij}. else Emerging h i (use Simplex Projection): h i = argmin h D h R w i/ w i 2 2 end if end for Convergence Check: Relative change in Objective value < ɛ end while H(t) = H and W(t) is last N(t) rows of W. minimizer in O(D) time i.e. linear in the number of coordinates. Emerging h i: For an emerging topic, we do not have the smoothness constraints and the domain C = {h i : h i D} is just the D dimensional simplex. The optimization (10) becomes equivalent to a projection onto the simplex D. The same algorithm [22] again gives us the minimizer in linear time O(D). Evolving w i: When w i W ev, the regularization term in (8) does not contribute and the corresponding optimization problem boils down to wi = argmin wi 0 R wih 2 i. Similar to (10), simple algebraic operations yield that the above minimization is equal to the following simple projection problem, argmin w i 0 wi Rh i/ h i 2 2. The projection set now is just the non-negative orthant, for which there( is a closed form minimizer: 1 w ij = max 0, (Rh h i i) 2 j ). Emerging w i: When w i W em, the second term in (8) is active and the corresponding optimization problem looks like argmin R w ih i 2 + µl(sw i) w i 0 Omitting the terms independent of w i, simple algebra yields that the above is equivalent to argmin w i Rh i/ h i µl(sw i)/ h i 2 (11) w i 0 Noting that we choose L to be the l 2 hinge loss, (11) can be rewritten as argmin wi Rh i/ h i µ T 1 w i 0 h i 2 c j max(0, ν j q j w i) 2 j=1 where q j = (DF S) j,:, the j th row of DF S where the operators are defined in (7) and (8) respectively. Assimilating the µ/ h i 2 into the constant c i, the above optimization problem can be written in the following generic form min w 0 J(w) where J(w) = i max (0, c i(ν i w, x i )) 2 + λ 2 w w0 2 (12) Simple linear algebraic operations yield that the above is equivalent to argmin h i C h i R w i/ w i 2 2 (10) Note that the domain of dependence C changes according to different constraints on h i depending on whether it is an emerging or evolving topic. Evolving h i: For an evolving topic, the optimization needs to be performed under the smoothness and the normalization constraints ((4) and (3) respectively). Thus the optimum h i is obtained by optimizing the above objective over the set C = {h i : h i D, l j h ij u j} for appropriate lower and upper bounds l j and u j determined by (4). This is equivalent to a projection onto a simplex with box constraints. Adapting a method due to [22], we can find the where w 0 refers to the term Rh i/ h i 2. Note that this is the same as the L2-SVM optimization problem with additional non-negativity constraints on w i and the regularizer measuring distance from the vector w 0 instead of the origin. This objective is minimized using a projected gradient algorithm (due to the non-negativity constraint) [19] on the primal objective directly, as it is smooth and therefore the gradient is well defined. The update is given by w (k+1) = (w (k) η k J(w (k) )) where is the projection operator (s) = max(s, 0) and J(w (k) ) = 2 ( ) ] max [c i ν i w (k), x i, 0 x i i +λ(w (k) w 0)
6 The main trick lies in choosing the best rate η k at the k th step. Following [19], we start with η 0 = 1 and at every step hot start η k = η k 1. If η k satisfies J(w (k+1) ) J(w (k) ) σ J(w (k) ), w (k+1) w (k) (13) we continuously increase η k η k /β as long it satisfies (13). If η k initially does not satisfy (13), we continuously decrease η k η k β until the condition is satisfied. For our experiments, we choose β = 0.05 and σ = Our online learning algorithm can now be composed as in the table labeled Algorithm 1. ( Initializations: ) Note that in the algorithm above, H init = H ev H em where H ev, the evolving set is initialized from H(t 1) and H em is initialized to random ( distributions. ) W11 W The corresponding parts of W init = 12 are W 21 W 22 initialized in the following way: W 11 is extracted from previous runs (previous association of old documents with existing topics), W 12 = 0 (old documents have weak association with emerging topics), W 21 optimizes argmin X(t) ŴHev 2 fro Ŵ 0 In other words, existing topics are allowed to first reconstruct new documents. Finally, W 22 is chosen to be the columns of W corresponding to emerging topics where W is chosen randomly and scaled appropriately with α = argmin X(t) βwh init 2 fro β>0 (see [14] for simple expressions for α). Convergence: Using a general result on convergence of Block Coordinate Descent, from [3], we can show that the limit point (W, H(t)) generated by algorithm 1 is a stationary point of the objective function (1). This follows from the uniqueness of the projection onto a closed convex set (simplex, or simplex with box constraints) and the strict convexity of Eq PERFORMANCE EVALUATION We conducted a comprehensive empirical evaluation of our system on both traditional topic detection and tracking datasets comprising of streaming news stories, as well as a twitter stream filtered for tweets relevant to IBM that was collected over a span of 6 weeks. It should be noted that the goal of our experiments is to empirically understand the effectiveness of the temporal regularizers. As a result, most of our experiments try to demonstrate the role of these temporal regularizers on traditional news datasets as well as twitter streams as opposed to exhaustive comparison with existing TDT algorithms. However we still perform comparisons with a simple baseline TDT model to put our models into perspective. We begin with a discussion on appropriate evaluation metrics, some of which are new to the best of our knowledge. 6.1 Metrics and Methodology For performance evaluation, we assume that documents in the corpus have been manually identified with a set of E events. For simplicity, we assume that each document i is tagged with a single, most dominant event that it associates with π true(i) {1... E}. In the description below, we call these human labeled topics as events or true topics and assume them to be the ground truth. Microaveraged F1: This measure has been commonly reported in topic detection and tracking (TDT) literature (see, e.g., [6]). Let us assume that the system generates S topics where in general S E i.e., the system is allowed to generate any number of topics. We first construct the E S confusion matrix CM between events and system topics, i.e., CM e,s is the number of documents that were tagged e by the human and tagged s by the system. From this matrix, for each event e, we identify top k (e) the set of top-k most frequently co-occuring system topics. We can then compute the microaveraged F1 measure as follows: E e=1 Dtrue(e) Dsystem(e) P recision k = E e=1 Dsystem(e) (14) Recall k = F 1 k = E e=1 Dtrue(e) Dsystem(e) E e=1 Dtrue(e) (15) P recision Recall P recision + Recall (16) where D true(e) is the set of documents human-tagged e and D system(e) is the set of documents system-tagged with a topic in top k (e), denotes the cardinality and denotes intersection operators on sets. Note that while k in top k is typically chosen to be 1, higher values may also be meaningful to study particularly when multiple system topics attempt to capture the same semantic event. Also note that the F1 score also implicitly measures topic continuity which is important in providing a stable, consistent association across time between events and system topics. Miss First Detection: This measure attempts to intuitively capture the following notion: how much of an event has been missed before the system is able to communicate its existence to the user via the word-distribution of a topic. It is a direct measure of the quality of an online topic detection model to serve as an early warning system for emerging themes. To compute this measure, we find the first detection timepoint: the earliest timepoint when the word-distribution of a system generated topic gets sufficiently near the word distribution of the event e (which is itself evolving temporally). We then compute the percentage of documents tagged with e that have streamed away prior to first detection. This fraction is called the miss first detection. To operationalize this measure, we define the following: (a) Word distribution of an event e at time t: the normalized centroid of all documents on event e upto time t. Note that this distribution is also obtained from the solution to the optimization problem H true(t) = argmin H 0,H1 D =1 E X(1 : t) W trueh 2 fro where W true is simply the matrix encoding for π true, i.e., W true(i, e) = 1 if π true(i) = e and 0 otherwise. H true(t) serves as a proxy for the word distributions of the true topics. (b) Similarity measure for Topic nearness: Given two discrete distributions p and q, we use the Jensen-Shannon Divergence (JSD) as a measure of topic proximity, JSD(p, q) = 1 (KL(p m) + KL(q m)) 2
7 Figure 3: Metrics for TDT2 (note that F1 score for independent models (not plotted) is 0.21). where m = 1 (p+q). Other measures (KL-divergence, Symmetric KL-divergence, Overlap in top words etc) are also 2 possible. However, we chose JSD because it is always numerically well defined and bounded between 0 and 1. (c) First detection Time for an event e is defined as: t detect (e) = argmin t [ t : min s ] JSD (h true(e; t), h sys(s; t)) < θ where θ is a detection threshold and h true(e; t) is the word distribution for event e at time t i.e. the row corresponding to event e in H true(t), and h sys(s; t) is a row of H(t), i.e., a system topic s at time t. Hence, t detect simply measures the first timepoint at which a system topic comes θ-close to an event as measured by JSD. In our experiments, we either set θ to a small value (0.2) or study variation with respect to its choice. The miss rate for event e can now be defined as: d : d D true(e), timestamp(d) < t detect (e) 100 D true(e) (17) We study miss rates for individual events or report an average across all events. Topic Continuity: We adapt a direct measure of topic continuity suggested in [6]. This measure essentially reports the JSD between word-distributions in consecutive timepoints both for events (true topics) as well as for systemtopics. It therefore measures temporal smoothness in topic distributions. Emerging Bandwidth: The topics in the emerging set can a) either all become part of the evolving set going forward in time, b) can be manually selected with some of them being discarded as noise by the user or c) can be selected using criteria such as net current strength (sum of the document weights of a topic from the corresponding column of W). In our experiments, we choose (a) and retain all topics in the emerging set. 6.2 Threshold Based TDT model We adopt a simple baseline model (Threshold Based TDT) based on a body of work in topic detection [1, 8] which corresponds to one of the classic topic detection frameworks. We adapt these body of algorithms for comparison to our experimental setup by using analogous concepts like adhoc period and emerging topics. In particular, we learn an initial set of topics by k-means clustering of the documents over an adhoc period. New documents then stream in one time unit at a time and if their similarity to the existing topics exceed a certain threshold (Yes/No threshold), they are allocated to those topics. We also incorporate adaptation [8] so that if the similarity of an incoming document to a topic exceeds a certain adaptation threshold τ, we modify the corresponding cluster (topic) center to incorporate the effect of the new document. The threshold values are treated as tunable parameters. The remaining documents which are not similar to the existing topics are then considered as belonging to emerging topics. We perform another k-means clustering to cluster these documents into a set of emerging topics. The documents which are very far from these cluster centers are assigned to singleton topics. Similar to our temporal model, the emerging topics are absorbed into the evolving set going forward in time. 6.3 TDT2 Dataset Our first dataset is drawn from the NIST Topic Detection and Tracking (TDT2) corpus 2 which consists of news stories in the first half of In our evaluation, we used a set of 9394 documents represented over terms and distributed into the top 30 TDT2 human-labeled topics over a period of 27 weeks. We choose the hinge parameter to be ν = 20 and emerging bandwidth of 2 per week for this dataset. In our experiments, we use a sliding window of ω = 4 weeks. The left panel of Figure 3 shows tracking performance (F 1) as a function of the evolution parameter δ for various values of µ. When δ = 0, the system freezes a topic as soon as it is detected not allowing the word distributions to change as the underlying topic drifts over time. When δ = 1, the system has complete freedom in retraining topic distributions causing no single channel to remain consistently associated with an underlying topic. It can be seen that both these extremes are suboptimal. Tracking is much more effective when topic distributions are allowed to evolve under sufficient constraints in response to the statistics of incoming data. Moreover, the presence of emergence regularizer µ > 0 tends to lead to higher F1-score also. In the middle panel of Figure 3 we turn to the miss rate at first detection. Higher values of µ typically reduces miss rates helping emerging topics to be detected early. As δ is increased, topics become less constrained and therefore provide additional bandwidth to drift towards emerging topics, therefore lowering the miss rate curves. However, this comes at the price of reduced tracking performance. Thus, for a fixed amount of available topic bandwidth (which also corresponds to user information overload), there is a tradeoff between tracking and early detection that can be navigated 2
8 with the choice of µ and δ. The rightmost panel of Figure 3 shows topic continuity. Choosing δ = 0 leads to no evolution of word distributions while δ = 1 can lead to abrupt changes than can cause user confusion. For other values of δ we see that the system allows drift that is of the same scale as the drift in the true word distributions. Figure 3 also plots the metrics for a simple online methodology where a fresh NMF is learnt at every timepoint over all the data seen so far, independent of previous runs. This model is labeled independent in the Figure. As can be seen, independent runs lead to high miss rate (see middle panel) since small emerging topics can be swamped by the goal of reconstructing the ever expanding set of historical documents. Due to complete temporal independence, no system topic can maintain a stable association with an event leading to low F1 score (0.20, not plotted in the left panel) and high temporal discontinuity (see right panel). In Figure 4, we see that, as expected, training online models across short sliding windows takes much lesser time overall than training fresh batch models at every timepoint. Figure 4: Training time on TDT2 We perform baseline experiments with the Threshold Based TDT model over the TDT2 dataset. Due to space constraints, we just report the tracking performance using F1 score (left panel on Figure 5) as a function of the Yes/No threshold for various values of the Adaptation threshold, τ. The F1 scores obtained by our temporal model are clearly much better than the simple baseline. Figure 5: Metrics for TDT-Adapt: F1 score on TDT2 and Twitter The first 7 days are used to build an initial adhoc model after which the data is streamed into our models for online analysis. In order to facilitate quantitative benchmarking, we labeled approximately 23% of this data in a semi-automatic fashion. First, we learnt a batch NMF model over the entire dataset with 100 topics. From this model, we identified 10 salient events in this time period concerning IBM, listed in the table below together with an estimate of date of peak strength from the model. Table 1: 10 events comprising roughly 23% of tweets between Dec 21, 2010 and Feb 2, ID Event Size Peak Date 1 Lotusphere 2011 Conference 5020 Jan 31, Watson Jeopardy Contest Jan 14, Graphene Transistors 874 Jan 24, IBM Patents 2459 Jan 10, IBM Virtual Desktop Offering 1889 Jan 24, IBM Cloud Computing Data Center 2823 Jan 26, IBM Centennial 2558 Jan 22, IBM Quarterly Earnings 6944 Jan 18, IBM Analytics Study 3413 Jan 14, IBM ARM Partnership 3168 Jan 20, 2011 Several topics in the batch model were found to cover these events and induced a partial clustering of tweets which was treated as ground truth. Note, the online model needs to make a real-time judgement of emerging topics and online tracking of evolving ones, and does not have the benefit of retrospective hindsight that the batch model does. It is important to note that our online models are trained on the entire dataset, and only the evaluation is restricted to these labeled events. In other words, these events need to each be teased apart from the entire data collection as they emerge. These 10 events are quite diverse and cover the victory of the IBM Watson supercomputer in a practice Jeopardy! round in January, IBM s quarterly earnings statement, announcements such as creation of the largest cloud computing data center in Asia and a new virtual desktop offering, new partnerships, market studies, patent leadership, centennial celebrations and super fast Graphene transistors. In our empirical study, we fixed the hinge parameter ν = 20, evolution parameter δ = 0.001, sliding window of one week (ω = 7) and emerging topic bandwidth to be 4. regularization. Figure 6 shows that the miss rate at first detection Figure 6: Miss Rate at First Detection as a function of Detection Threshold on IBM Twitter data 6.4 IBM Twitter Archive We used the Twitter Search API to collect all tweets mentioning IBM in the time period Dec 21, 2010 to Feb 2, Our dataset comprises of tweets spread over 43 days. curve as a function of detection threshold (θ in Equation 17) is significantly lower when the emergence regularizer is used.
9 Table 2: Tracking Performance on Twitter top 1 top 5 Measure µ = 0 µ = 1000 µ = 0 µ = 1000 Precision Recall F Figure 7: Emerging Topics in IBM Tweets In Figures 7, 8 we see the effect of emergence regularization: on several events, the online model with µ = 1000 shows a much sharper dip (see bottom panel for each event) as compared to µ = 0 in terms of JSD with respect to the true word distribution, around the time the event emerges (see top panel for each event). These results clearly show the effectiveness and potential value of emergence regularization. The training time is 3.8 minutes per day for µ = 0 and 4.5 minutes per day for µ = 1000 on a commodity desktop running MATLAB. In the Table 2, we report F 1 scores at k = 1 and k = 5 respectively. We see that the models tend to have high precision and in particular, the presence of the emergence regularizer also significantly improves precision when upto 5 best matched system topics are associated with each event. Finally, in Figure 9, we show a visualization of topic temporal rivers [24] populated by keyword clouds (the words with highest mass) associated with system topics generated by our model. We show two different time points each spanning 1 week that has some coverage for most of the events. We see that the system is able to communicate the semantic essence (in terms of words) as well as the temporal profile of each event very effectively. We perform baseline experiments with Threshold Based TDT as described in section 6.2 for both k = 1 and k = 5 just like our model. For k = 1, the maximum F1 score for the thresholds considered is obtained for precision and recall values of and respectively. The corresponding numbers for k = 5 is F1 of with precision and recall respectively. We plot the F1 score in the same way as for the TDT2 dataset for the k = 1 case(figure 5 right panel). 7. CONCLUSION AND FUTURE WORK We have developed a new framework for modeling the evolution of topics and aiding the fast discovery of emerging themes in streaming social media content. We have shown the effectiveness and value of novel temporal regularizers in analyzing twitter streams. There are several avenues for future work including a detailed large-scale empirical study of the interplay between the model parameters as well as the tradeoff between evolution and emergence, coming up with convex formulations to avoid local minima problems possibly using nuclear norm regularization[17], and effective means to do model selection in the online setting. Other fascinating directions include incorporating topic volatility into the evolution constraints, and building sparser models using l 0/l 1-regularizers. 8. REFERENCES [1] J. Allan, editor. Topic Detection and Tracking: Event-based Information Organization. Kluwer Academic Publ, [2] L. AlSumait, D. Barbara, and C. Domeniconi. On-line lda: Adaptive topic models for mining text streams. In ICDM, [3] D. Bertsekas. Non-linear Programming. Athena Scientific, [4] D. Blei and J. Lafferty. Dynamic topic models. In ICML, [5] D. Blei and M.Jordan. Latent dirichlet allocation. JMLR, 3: , [6] Tzu-Chuan Chou and Meng Chang Chen. Using Incremental PLSI for Treshhold-Resilient Online Event Analysis. IEEE transactions on Knowledge and Data Engineering, [7] A. Cichocki, R. Zdunek, A. H. Phan, and S. Amari. Non-negative and Tensor Factorizations: Applications to Exploratory Multiway Data Analysis and Blind Source Separation. Wiley, 2009.
10 Figure 8: Emerging Topics in IBM Tweets Figure 9: TIARA visualizations [24]: Topics are organized as stacked rivers with width proportional to strength. Top keywords for each topic are also show. [8] Margaret Connell, Ao Feng, Giridhar Kumaran, Hema Raghavan, Chirag Shah, and James Allan. UMass at TDT [9] Aron Culotta. Towards detecting influenza epidemics by analyzing twitter messages, [10] C. Ding, T. Li, and W. Peng. On the equivalence between non-negative matrix factorizations and probabilistic latent semantic analysis. Computational Statistics and Data Analysis, [11] M. Elad. Sparse and Redundant Representations: From Theory to Applications in Signal and Image Processing. Springer, [12] Mark Girolami and A. Kaban. On an equivalence between plsi and lda. SIGIR. [13] A. Gohr, A. Hinneburg, R. Schult, and M. Spiliopoulou. Topic evolution in a stream of documents. In SDM, [14] Ngoc-Diep Ho, Paul Van Dooren, and Vincent D. Blondel. Descent methods for nonnegative matrix factorization. Numerical Linear Algebra in Signals, abs/ , [15] Matthew D. Hoffman, David M. Blei, and Frances Bach. Online learning for latent dirichlet allocation. In NIPS, [16] T. Hoffman. Probabilistic latent semantic analysis. In UAI, [17] M. Jaggi and M. Sulovský. A simple algorithm for nuclear norm regularized problems. In ICML, [18] D. Lee and H.S. Seung. Learning the parts of objects using non-negative matrix factorizations. Nature, [19] C.J. Lin. Projected gradient methods for non-negative matrix factorization. In Neural Computation, [20] J. Mairal, F. Bach, J. Ponce, and G. Sapiro. Online learning for matrix factorization and sparse coding. JMLR, [21] P. Melville, V. Sindhwani, and R. Lawrence. Social media analytics: Channeling the power of the blogosphere for marketing insight. Workshop on Information in Networks, [22] P. M. Pardalos and N. Kovoor. An algorithm for singly constrained class of quadratic programs subject to upper and lower bounds. Mathematical Programming, 46: , [23] G. Salton. Automatic Text Processing: The Transformation, Analysis, and Retrieval of Information by Computer. Addison-Wesley, [24] Furu Wei Shimie Pan Michelle X. Zhou Weihong Qian Lei Shi Li Tan Qiang Zhang Shixia Liu, Yangqiu Song. Tiara: Visually analyzing topic evolution in large text collections. In KDD, [25] Wei Xu, Xin Liu, and Yihong Gong. Document clustering based on non-negative matrix factorization. In SIGIR, [26] Yiming Yang, Tom Pierce, and James Carbonell. A Study on Retrospective and Online Event Detection. In SIGIR, 1998.
Dynamic NMFs with Temporal Regularization for Online Analysis of Streaming Text
 JMLR: Workshop and Conference Proceedings 14 (2011) Workshop on Machine Learning for Social Computing Dynamic NMFs with Temporal Regularization for Online Analysis of Streaming Text Ankan Saha Department
JMLR: Workshop and Conference Proceedings 14 (2011) Workshop on Machine Learning for Social Computing Dynamic NMFs with Temporal Regularization for Online Analysis of Streaming Text Ankan Saha Department
Data Mining Yelp Data - Predicting rating stars from review text
 Data Mining Yelp Data - Predicting rating stars from review text Rakesh Chada Stony Brook University rchada@cs.stonybrook.edu Chetan Naik Stony Brook University cnaik@cs.stonybrook.edu ABSTRACT The majority
Data Mining Yelp Data - Predicting rating stars from review text Rakesh Chada Stony Brook University rchada@cs.stonybrook.edu Chetan Naik Stony Brook University cnaik@cs.stonybrook.edu ABSTRACT The majority
Predict the Popularity of YouTube Videos Using Early View Data
 000 001 002 003 004 005 006 007 008 009 010 011 012 013 014 015 016 017 018 019 020 021 022 023 024 025 026 027 028 029 030 031 032 033 034 035 036 037 038 039 040 041 042 043 044 045 046 047 048 049 050
000 001 002 003 004 005 006 007 008 009 010 011 012 013 014 015 016 017 018 019 020 021 022 023 024 025 026 027 028 029 030 031 032 033 034 035 036 037 038 039 040 041 042 043 044 045 046 047 048 049 050
Efficient online learning of a non-negative sparse autoencoder
 and Machine Learning. Bruges (Belgium), 28-30 April 2010, d-side publi., ISBN 2-93030-10-2. Efficient online learning of a non-negative sparse autoencoder Andre Lemme, R. Felix Reinhart and Jochen J. Steil
and Machine Learning. Bruges (Belgium), 28-30 April 2010, d-side publi., ISBN 2-93030-10-2. Efficient online learning of a non-negative sparse autoencoder Andre Lemme, R. Felix Reinhart and Jochen J. Steil
Least-Squares Intersection of Lines
 Least-Squares Intersection of Lines Johannes Traa - UIUC 2013 This write-up derives the least-squares solution for the intersection of lines. In the general case, a set of lines will not intersect at a
Least-Squares Intersection of Lines Johannes Traa - UIUC 2013 This write-up derives the least-squares solution for the intersection of lines. In the general case, a set of lines will not intersect at a
Clustering. Danilo Croce Web Mining & Retrieval a.a. 2015/201 16/03/2016
 Clustering Danilo Croce Web Mining & Retrieval a.a. 2015/201 16/03/2016 1 Supervised learning vs. unsupervised learning Supervised learning: discover patterns in the data that relate data attributes with
Clustering Danilo Croce Web Mining & Retrieval a.a. 2015/201 16/03/2016 1 Supervised learning vs. unsupervised learning Supervised learning: discover patterns in the data that relate data attributes with
1 Teaching notes on GMM 1.
 Bent E. Sørensen January 23, 2007 1 Teaching notes on GMM 1. Generalized Method of Moment (GMM) estimation is one of two developments in econometrics in the 80ies that revolutionized empirical work in
Bent E. Sørensen January 23, 2007 1 Teaching notes on GMM 1. Generalized Method of Moment (GMM) estimation is one of two developments in econometrics in the 80ies that revolutionized empirical work in
1 Solving LPs: The Simplex Algorithm of George Dantzig
 Solving LPs: The Simplex Algorithm of George Dantzig. Simplex Pivoting: Dictionary Format We illustrate a general solution procedure, called the simplex algorithm, by implementing it on a very simple example.
Solving LPs: The Simplex Algorithm of George Dantzig. Simplex Pivoting: Dictionary Format We illustrate a general solution procedure, called the simplex algorithm, by implementing it on a very simple example.
Support Vector Machines with Clustering for Training with Very Large Datasets
 Support Vector Machines with Clustering for Training with Very Large Datasets Theodoros Evgeniou Technology Management INSEAD Bd de Constance, Fontainebleau 77300, France theodoros.evgeniou@insead.fr Massimiliano
Support Vector Machines with Clustering for Training with Very Large Datasets Theodoros Evgeniou Technology Management INSEAD Bd de Constance, Fontainebleau 77300, France theodoros.evgeniou@insead.fr Massimiliano
Facebook Friend Suggestion Eytan Daniyalzade and Tim Lipus
 Facebook Friend Suggestion Eytan Daniyalzade and Tim Lipus 1. Introduction Facebook is a social networking website with an open platform that enables developers to extract and utilize user information
Facebook Friend Suggestion Eytan Daniyalzade and Tim Lipus 1. Introduction Facebook is a social networking website with an open platform that enables developers to extract and utilize user information
Linear Threshold Units
 Linear Threshold Units w x hx (... w n x n w We assume that each feature x j and each weight w j is a real number (we will relax this later) We will study three different algorithms for learning linear
Linear Threshold Units w x hx (... w n x n w We assume that each feature x j and each weight w j is a real number (we will relax this later) We will study three different algorithms for learning linear
Methodology for Emulating Self Organizing Maps for Visualization of Large Datasets
 Methodology for Emulating Self Organizing Maps for Visualization of Large Datasets Macario O. Cordel II and Arnulfo P. Azcarraga College of Computer Studies *Corresponding Author: macario.cordel@dlsu.edu.ph
Methodology for Emulating Self Organizing Maps for Visualization of Large Datasets Macario O. Cordel II and Arnulfo P. Azcarraga College of Computer Studies *Corresponding Author: macario.cordel@dlsu.edu.ph
Machine Learning and Pattern Recognition Logistic Regression
 Machine Learning and Pattern Recognition Logistic Regression Course Lecturer:Amos J Storkey Institute for Adaptive and Neural Computation School of Informatics University of Edinburgh Crichton Street,
Machine Learning and Pattern Recognition Logistic Regression Course Lecturer:Amos J Storkey Institute for Adaptive and Neural Computation School of Informatics University of Edinburgh Crichton Street,
Adaptive Online Gradient Descent
 Adaptive Online Gradient Descent Peter L Bartlett Division of Computer Science Department of Statistics UC Berkeley Berkeley, CA 94709 bartlett@csberkeleyedu Elad Hazan IBM Almaden Research Center 650
Adaptive Online Gradient Descent Peter L Bartlett Division of Computer Science Department of Statistics UC Berkeley Berkeley, CA 94709 bartlett@csberkeleyedu Elad Hazan IBM Almaden Research Center 650
Practical Guide to the Simplex Method of Linear Programming
 Practical Guide to the Simplex Method of Linear Programming Marcel Oliver Revised: April, 0 The basic steps of the simplex algorithm Step : Write the linear programming problem in standard form Linear
Practical Guide to the Simplex Method of Linear Programming Marcel Oliver Revised: April, 0 The basic steps of the simplex algorithm Step : Write the linear programming problem in standard form Linear
MSCA 31000 Introduction to Statistical Concepts
 MSCA 31000 Introduction to Statistical Concepts This course provides general exposure to basic statistical concepts that are necessary for students to understand the content presented in more advanced
MSCA 31000 Introduction to Statistical Concepts This course provides general exposure to basic statistical concepts that are necessary for students to understand the content presented in more advanced
Probabilistic Models for Big Data. Alex Davies and Roger Frigola University of Cambridge 13th February 2014
 Probabilistic Models for Big Data Alex Davies and Roger Frigola University of Cambridge 13th February 2014 The State of Big Data Why probabilistic models for Big Data? 1. If you don t have to worry about
Probabilistic Models for Big Data Alex Davies and Roger Frigola University of Cambridge 13th February 2014 The State of Big Data Why probabilistic models for Big Data? 1. If you don t have to worry about
1 Prior Probability and Posterior Probability
 Math 541: Statistical Theory II Bayesian Approach to Parameter Estimation Lecturer: Songfeng Zheng 1 Prior Probability and Posterior Probability Consider now a problem of statistical inference in which
Math 541: Statistical Theory II Bayesian Approach to Parameter Estimation Lecturer: Songfeng Zheng 1 Prior Probability and Posterior Probability Consider now a problem of statistical inference in which
Inner Product Spaces
 Math 571 Inner Product Spaces 1. Preliminaries An inner product space is a vector space V along with a function, called an inner product which associates each pair of vectors u, v with a scalar u, v, and
Math 571 Inner Product Spaces 1. Preliminaries An inner product space is a vector space V along with a function, called an inner product which associates each pair of vectors u, v with a scalar u, v, and
Follow links Class Use and other Permissions. For more information, send email to: permissions@pupress.princeton.edu
 COPYRIGHT NOTICE: David A. Kendrick, P. Ruben Mercado, and Hans M. Amman: Computational Economics is published by Princeton University Press and copyrighted, 2006, by Princeton University Press. All rights
COPYRIGHT NOTICE: David A. Kendrick, P. Ruben Mercado, and Hans M. Amman: Computational Economics is published by Princeton University Press and copyrighted, 2006, by Princeton University Press. All rights
CSCI567 Machine Learning (Fall 2014)
 CSCI567 Machine Learning (Fall 2014) Drs. Sha & Liu {feisha,yanliu.cs}@usc.edu September 22, 2014 Drs. Sha & Liu ({feisha,yanliu.cs}@usc.edu) CSCI567 Machine Learning (Fall 2014) September 22, 2014 1 /
CSCI567 Machine Learning (Fall 2014) Drs. Sha & Liu {feisha,yanliu.cs}@usc.edu September 22, 2014 Drs. Sha & Liu ({feisha,yanliu.cs}@usc.edu) CSCI567 Machine Learning (Fall 2014) September 22, 2014 1 /
Modern Optimization Methods for Big Data Problems MATH11146 The University of Edinburgh
 Modern Optimization Methods for Big Data Problems MATH11146 The University of Edinburgh Peter Richtárik Week 3 Randomized Coordinate Descent With Arbitrary Sampling January 27, 2016 1 / 30 The Problem
Modern Optimization Methods for Big Data Problems MATH11146 The University of Edinburgh Peter Richtárik Week 3 Randomized Coordinate Descent With Arbitrary Sampling January 27, 2016 1 / 30 The Problem
Sensitivity Analysis 3.1 AN EXAMPLE FOR ANALYSIS
 Sensitivity Analysis 3 We have already been introduced to sensitivity analysis in Chapter via the geometry of a simple example. We saw that the values of the decision variables and those of the slack and
Sensitivity Analysis 3 We have already been introduced to sensitivity analysis in Chapter via the geometry of a simple example. We saw that the values of the decision variables and those of the slack and
Several Views of Support Vector Machines
 Several Views of Support Vector Machines Ryan M. Rifkin Honda Research Institute USA, Inc. Human Intention Understanding Group 2007 Tikhonov Regularization We are considering algorithms of the form min
Several Views of Support Vector Machines Ryan M. Rifkin Honda Research Institute USA, Inc. Human Intention Understanding Group 2007 Tikhonov Regularization We are considering algorithms of the form min
SMTP: Stedelijk Museum Text Mining Project
 SMTP: Stedelijk Museum Text Mining Project Jeroen Smeets Maastricht University smeetsjeroen@hotmail.com Prof. Dr. Ir. Johannes C. Scholtes Maastricht University j.scholtes@maastrichtuniversity.nl Dr. Claartje
SMTP: Stedelijk Museum Text Mining Project Jeroen Smeets Maastricht University smeetsjeroen@hotmail.com Prof. Dr. Ir. Johannes C. Scholtes Maastricht University j.scholtes@maastrichtuniversity.nl Dr. Claartje
FUZZY CLUSTERING ANALYSIS OF DATA MINING: APPLICATION TO AN ACCIDENT MINING SYSTEM
 International Journal of Innovative Computing, Information and Control ICIC International c 0 ISSN 34-48 Volume 8, Number 8, August 0 pp. 4 FUZZY CLUSTERING ANALYSIS OF DATA MINING: APPLICATION TO AN ACCIDENT
International Journal of Innovative Computing, Information and Control ICIC International c 0 ISSN 34-48 Volume 8, Number 8, August 0 pp. 4 FUZZY CLUSTERING ANALYSIS OF DATA MINING: APPLICATION TO AN ACCIDENT
CHAPTER 2 Estimating Probabilities
 CHAPTER 2 Estimating Probabilities Machine Learning Copyright c 2016. Tom M. Mitchell. All rights reserved. *DRAFT OF January 24, 2016* *PLEASE DO NOT DISTRIBUTE WITHOUT AUTHOR S PERMISSION* This is a
CHAPTER 2 Estimating Probabilities Machine Learning Copyright c 2016. Tom M. Mitchell. All rights reserved. *DRAFT OF January 24, 2016* *PLEASE DO NOT DISTRIBUTE WITHOUT AUTHOR S PERMISSION* This is a
Probabilistic Latent Semantic Analysis (plsa)
 Probabilistic Latent Semantic Analysis (plsa) SS 2008 Bayesian Networks Multimedia Computing, Universität Augsburg Rainer.Lienhart@informatik.uni-augsburg.de www.multimedia-computing.{de,org} References
Probabilistic Latent Semantic Analysis (plsa) SS 2008 Bayesian Networks Multimedia Computing, Universität Augsburg Rainer.Lienhart@informatik.uni-augsburg.de www.multimedia-computing.{de,org} References
Network Big Data: Facing and Tackling the Complexities Xiaolong Jin
 Network Big Data: Facing and Tackling the Complexities Xiaolong Jin CAS Key Laboratory of Network Data Science & Technology Institute of Computing Technology Chinese Academy of Sciences (CAS) 2015-08-10
Network Big Data: Facing and Tackling the Complexities Xiaolong Jin CAS Key Laboratory of Network Data Science & Technology Institute of Computing Technology Chinese Academy of Sciences (CAS) 2015-08-10
Statistical Machine Learning
 Statistical Machine Learning UoC Stats 37700, Winter quarter Lecture 4: classical linear and quadratic discriminants. 1 / 25 Linear separation For two classes in R d : simple idea: separate the classes
Statistical Machine Learning UoC Stats 37700, Winter quarter Lecture 4: classical linear and quadratic discriminants. 1 / 25 Linear separation For two classes in R d : simple idea: separate the classes
Introduction to Support Vector Machines. Colin Campbell, Bristol University
 Introduction to Support Vector Machines Colin Campbell, Bristol University 1 Outline of talk. Part 1. An Introduction to SVMs 1.1. SVMs for binary classification. 1.2. Soft margins and multi-class classification.
Introduction to Support Vector Machines Colin Campbell, Bristol University 1 Outline of talk. Part 1. An Introduction to SVMs 1.1. SVMs for binary classification. 1.2. Soft margins and multi-class classification.
Tensor Methods for Machine Learning, Computer Vision, and Computer Graphics
 Tensor Methods for Machine Learning, Computer Vision, and Computer Graphics Part I: Factorizations and Statistical Modeling/Inference Amnon Shashua School of Computer Science & Eng. The Hebrew University
Tensor Methods for Machine Learning, Computer Vision, and Computer Graphics Part I: Factorizations and Statistical Modeling/Inference Amnon Shashua School of Computer Science & Eng. The Hebrew University
Statistical machine learning, high dimension and big data
 Statistical machine learning, high dimension and big data S. Gaïffas 1 14 mars 2014 1 CMAP - Ecole Polytechnique Agenda for today Divide and Conquer principle for collaborative filtering Graphical modelling,
Statistical machine learning, high dimension and big data S. Gaïffas 1 14 mars 2014 1 CMAP - Ecole Polytechnique Agenda for today Divide and Conquer principle for collaborative filtering Graphical modelling,
System Identification for Acoustic Comms.:
 System Identification for Acoustic Comms.: New Insights and Approaches for Tracking Sparse and Rapidly Fluctuating Channels Weichang Li and James Preisig Woods Hole Oceanographic Institution The demodulation
System Identification for Acoustic Comms.: New Insights and Approaches for Tracking Sparse and Rapidly Fluctuating Channels Weichang Li and James Preisig Woods Hole Oceanographic Institution The demodulation
Topic models for Sentiment analysis: A Literature Survey
 Topic models for Sentiment analysis: A Literature Survey Nikhilkumar Jadhav 123050033 June 26, 2014 In this report, we present the work done so far in the field of sentiment analysis using topic models.
Topic models for Sentiment analysis: A Literature Survey Nikhilkumar Jadhav 123050033 June 26, 2014 In this report, we present the work done so far in the field of sentiment analysis using topic models.
Clarify Some Issues on the Sparse Bayesian Learning for Sparse Signal Recovery
 Clarify Some Issues on the Sparse Bayesian Learning for Sparse Signal Recovery Zhilin Zhang and Bhaskar D. Rao Technical Report University of California at San Diego September, Abstract Sparse Bayesian
Clarify Some Issues on the Sparse Bayesian Learning for Sparse Signal Recovery Zhilin Zhang and Bhaskar D. Rao Technical Report University of California at San Diego September, Abstract Sparse Bayesian
Towards an Evaluation Framework for Topic Extraction Systems for Online Reputation Management
 Towards an Evaluation Framework for Topic Extraction Systems for Online Reputation Management Enrique Amigó 1, Damiano Spina 1, Bernardino Beotas 2, and Julio Gonzalo 1 1 Departamento de Lenguajes y Sistemas
Towards an Evaluation Framework for Topic Extraction Systems for Online Reputation Management Enrique Amigó 1, Damiano Spina 1, Bernardino Beotas 2, and Julio Gonzalo 1 1 Departamento de Lenguajes y Sistemas
Collaborative Filtering. Radek Pelánek
 Collaborative Filtering Radek Pelánek 2015 Collaborative Filtering assumption: users with similar taste in past will have similar taste in future requires only matrix of ratings applicable in many domains
Collaborative Filtering Radek Pelánek 2015 Collaborative Filtering assumption: users with similar taste in past will have similar taste in future requires only matrix of ratings applicable in many domains
Lecture 2: The SVM classifier
 Lecture 2: The SVM classifier C19 Machine Learning Hilary 2015 A. Zisserman Review of linear classifiers Linear separability Perceptron Support Vector Machine (SVM) classifier Wide margin Cost function
Lecture 2: The SVM classifier C19 Machine Learning Hilary 2015 A. Zisserman Review of linear classifiers Linear separability Perceptron Support Vector Machine (SVM) classifier Wide margin Cost function
EM Clustering Approach for Multi-Dimensional Analysis of Big Data Set
 EM Clustering Approach for Multi-Dimensional Analysis of Big Data Set Amhmed A. Bhih School of Electrical and Electronic Engineering Princy Johnson School of Electrical and Electronic Engineering Martin
EM Clustering Approach for Multi-Dimensional Analysis of Big Data Set Amhmed A. Bhih School of Electrical and Electronic Engineering Princy Johnson School of Electrical and Electronic Engineering Martin
Distinguishing Humans from Robots in Web Search Logs: Preliminary Results Using Query Rates and Intervals
 Distinguishing Humans from Robots in Web Search Logs: Preliminary Results Using Query Rates and Intervals Omer Duskin Dror G. Feitelson School of Computer Science and Engineering The Hebrew University
Distinguishing Humans from Robots in Web Search Logs: Preliminary Results Using Query Rates and Intervals Omer Duskin Dror G. Feitelson School of Computer Science and Engineering The Hebrew University
Database Marketing, Business Intelligence and Knowledge Discovery
 Database Marketing, Business Intelligence and Knowledge Discovery Note: Using material from Tan / Steinbach / Kumar (2005) Introduction to Data Mining,, Addison Wesley; and Cios / Pedrycz / Swiniarski
Database Marketing, Business Intelligence and Knowledge Discovery Note: Using material from Tan / Steinbach / Kumar (2005) Introduction to Data Mining,, Addison Wesley; and Cios / Pedrycz / Swiniarski
Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay
 Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay Lecture - 17 Shannon-Fano-Elias Coding and Introduction to Arithmetic Coding
Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay Lecture - 17 Shannon-Fano-Elias Coding and Introduction to Arithmetic Coding
15.062 Data Mining: Algorithms and Applications Matrix Math Review
 .6 Data Mining: Algorithms and Applications Matrix Math Review The purpose of this document is to give a brief review of selected linear algebra concepts that will be useful for the course and to develop
.6 Data Mining: Algorithms and Applications Matrix Math Review The purpose of this document is to give a brief review of selected linear algebra concepts that will be useful for the course and to develop
CHAPTER 1 INTRODUCTION
 1 CHAPTER 1 INTRODUCTION Exploration is a process of discovery. In the database exploration process, an analyst executes a sequence of transformations over a collection of data structures to discover useful
1 CHAPTER 1 INTRODUCTION Exploration is a process of discovery. In the database exploration process, an analyst executes a sequence of transformations over a collection of data structures to discover useful
Lecture Topic: Low-Rank Approximations
 Lecture Topic: Low-Rank Approximations Low-Rank Approximations We have seen principal component analysis. The extraction of the first principle eigenvalue could be seen as an approximation of the original
Lecture Topic: Low-Rank Approximations Low-Rank Approximations We have seen principal component analysis. The extraction of the first principle eigenvalue could be seen as an approximation of the original
Group Sparse Coding. Fernando Pereira Google Mountain View, CA pereira@google.com. Dennis Strelow Google Mountain View, CA strelow@google.
 Group Sparse Coding Samy Bengio Google Mountain View, CA bengio@google.com Fernando Pereira Google Mountain View, CA pereira@google.com Yoram Singer Google Mountain View, CA singer@google.com Dennis Strelow
Group Sparse Coding Samy Bengio Google Mountain View, CA bengio@google.com Fernando Pereira Google Mountain View, CA pereira@google.com Yoram Singer Google Mountain View, CA singer@google.com Dennis Strelow
Knowledge Discovery from patents using KMX Text Analytics
 Knowledge Discovery from patents using KMX Text Analytics Dr. Anton Heijs anton.heijs@treparel.com Treparel Abstract In this white paper we discuss how the KMX technology of Treparel can help searchers
Knowledge Discovery from patents using KMX Text Analytics Dr. Anton Heijs anton.heijs@treparel.com Treparel Abstract In this white paper we discuss how the KMX technology of Treparel can help searchers
Epipolar Geometry. Readings: See Sections 10.1 and 15.6 of Forsyth and Ponce. Right Image. Left Image. e(p ) Epipolar Lines. e(q ) q R.
 Epipolar Geometry We consider two perspective images of a scene as taken from a stereo pair of cameras (or equivalently, assume the scene is rigid and imaged with a single camera from two different locations).
Epipolar Geometry We consider two perspective images of a scene as taken from a stereo pair of cameras (or equivalently, assume the scene is rigid and imaged with a single camera from two different locations).
Recurrent Neural Networks
 Recurrent Neural Networks Neural Computation : Lecture 12 John A. Bullinaria, 2015 1. Recurrent Neural Network Architectures 2. State Space Models and Dynamical Systems 3. Backpropagation Through Time
Recurrent Neural Networks Neural Computation : Lecture 12 John A. Bullinaria, 2015 1. Recurrent Neural Network Architectures 2. State Space Models and Dynamical Systems 3. Backpropagation Through Time
Incorporating Window-Based Passage-Level Evidence in Document Retrieval
 Incorporating -Based Passage-Level Evidence in Document Retrieval Wensi Xi, Richard Xu-Rong, Christopher S.G. Khoo Center for Advanced Information Systems School of Applied Science Nanyang Technological
Incorporating -Based Passage-Level Evidence in Document Retrieval Wensi Xi, Richard Xu-Rong, Christopher S.G. Khoo Center for Advanced Information Systems School of Applied Science Nanyang Technological
Extend Table Lens for High-Dimensional Data Visualization and Classification Mining
 Extend Table Lens for High-Dimensional Data Visualization and Classification Mining CPSC 533c, Information Visualization Course Project, Term 2 2003 Fengdong Du fdu@cs.ubc.ca University of British Columbia
Extend Table Lens for High-Dimensional Data Visualization and Classification Mining CPSC 533c, Information Visualization Course Project, Term 2 2003 Fengdong Du fdu@cs.ubc.ca University of British Columbia
Science Navigation Map: An Interactive Data Mining Tool for Literature Analysis
 Science Navigation Map: An Interactive Data Mining Tool for Literature Analysis Yu Liu School of Software yuliu@dlut.edu.cn Zhen Huang School of Software kobe_hz@163.com Yufeng Chen School of Computer
Science Navigation Map: An Interactive Data Mining Tool for Literature Analysis Yu Liu School of Software yuliu@dlut.edu.cn Zhen Huang School of Software kobe_hz@163.com Yufeng Chen School of Computer
Standardization and Its Effects on K-Means Clustering Algorithm
 Research Journal of Applied Sciences, Engineering and Technology 6(7): 399-3303, 03 ISSN: 040-7459; e-issn: 040-7467 Maxwell Scientific Organization, 03 Submitted: January 3, 03 Accepted: February 5, 03
Research Journal of Applied Sciences, Engineering and Technology 6(7): 399-3303, 03 ISSN: 040-7459; e-issn: 040-7467 Maxwell Scientific Organization, 03 Submitted: January 3, 03 Accepted: February 5, 03
Large Scale Learning to Rank
 Large Scale Learning to Rank D. Sculley Google, Inc. dsculley@google.com Abstract Pairwise learning to rank methods such as RankSVM give good performance, but suffer from the computational burden of optimizing
Large Scale Learning to Rank D. Sculley Google, Inc. dsculley@google.com Abstract Pairwise learning to rank methods such as RankSVM give good performance, but suffer from the computational burden of optimizing
CHAPTER VII CONCLUSIONS
 CHAPTER VII CONCLUSIONS To do successful research, you don t need to know everything, you just need to know of one thing that isn t known. -Arthur Schawlow In this chapter, we provide the summery of the
CHAPTER VII CONCLUSIONS To do successful research, you don t need to know everything, you just need to know of one thing that isn t known. -Arthur Schawlow In this chapter, we provide the summery of the
Learning in Abstract Memory Schemes for Dynamic Optimization
 Fourth International Conference on Natural Computation Learning in Abstract Memory Schemes for Dynamic Optimization Hendrik Richter HTWK Leipzig, Fachbereich Elektrotechnik und Informationstechnik, Institut
Fourth International Conference on Natural Computation Learning in Abstract Memory Schemes for Dynamic Optimization Hendrik Richter HTWK Leipzig, Fachbereich Elektrotechnik und Informationstechnik, Institut
A Learning Based Method for Super-Resolution of Low Resolution Images
 A Learning Based Method for Super-Resolution of Low Resolution Images Emre Ugur June 1, 2004 emre.ugur@ceng.metu.edu.tr Abstract The main objective of this project is the study of a learning based method
A Learning Based Method for Super-Resolution of Low Resolution Images Emre Ugur June 1, 2004 emre.ugur@ceng.metu.edu.tr Abstract The main objective of this project is the study of a learning based method
Bayesian Predictive Profiles with Applications to Retail Transaction Data
 Bayesian Predictive Profiles with Applications to Retail Transaction Data Igor V. Cadez Information and Computer Science University of California Irvine, CA 92697-3425, U.S.A. icadez@ics.uci.edu Padhraic
Bayesian Predictive Profiles with Applications to Retail Transaction Data Igor V. Cadez Information and Computer Science University of California Irvine, CA 92697-3425, U.S.A. icadez@ics.uci.edu Padhraic
Data a systematic approach
 Pattern Discovery on Australian Medical Claims Data a systematic approach Ah Chung Tsoi Senior Member, IEEE, Shu Zhang, Markus Hagenbuchner Member, IEEE Abstract The national health insurance system in
Pattern Discovery on Australian Medical Claims Data a systematic approach Ah Chung Tsoi Senior Member, IEEE, Shu Zhang, Markus Hagenbuchner Member, IEEE Abstract The national health insurance system in
Big Data Analytics: Optimization and Randomization
 Big Data Analytics: Optimization and Randomization Tianbao Yang, Qihang Lin, Rong Jin Tutorial@SIGKDD 2015 Sydney, Australia Department of Computer Science, The University of Iowa, IA, USA Department of
Big Data Analytics: Optimization and Randomization Tianbao Yang, Qihang Lin, Rong Jin Tutorial@SIGKDD 2015 Sydney, Australia Department of Computer Science, The University of Iowa, IA, USA Department of
INDISTINGUISHABILITY OF ABSOLUTELY CONTINUOUS AND SINGULAR DISTRIBUTIONS
 INDISTINGUISHABILITY OF ABSOLUTELY CONTINUOUS AND SINGULAR DISTRIBUTIONS STEVEN P. LALLEY AND ANDREW NOBEL Abstract. It is shown that there are no consistent decision rules for the hypothesis testing problem
INDISTINGUISHABILITY OF ABSOLUTELY CONTINUOUS AND SINGULAR DISTRIBUTIONS STEVEN P. LALLEY AND ANDREW NOBEL Abstract. It is shown that there are no consistent decision rules for the hypothesis testing problem
Course: Model, Learning, and Inference: Lecture 5
 Course: Model, Learning, and Inference: Lecture 5 Alan Yuille Department of Statistics, UCLA Los Angeles, CA 90095 yuille@stat.ucla.edu Abstract Probability distributions on structured representation.
Course: Model, Learning, and Inference: Lecture 5 Alan Yuille Department of Statistics, UCLA Los Angeles, CA 90095 yuille@stat.ucla.edu Abstract Probability distributions on structured representation.
1 Review of Least Squares Solutions to Overdetermined Systems
 cs4: introduction to numerical analysis /9/0 Lecture 7: Rectangular Systems and Numerical Integration Instructor: Professor Amos Ron Scribes: Mark Cowlishaw, Nathanael Fillmore Review of Least Squares
cs4: introduction to numerical analysis /9/0 Lecture 7: Rectangular Systems and Numerical Integration Instructor: Professor Amos Ron Scribes: Mark Cowlishaw, Nathanael Fillmore Review of Least Squares
Efficient Cluster Detection and Network Marketing in a Nautural Environment
 A Probabilistic Model for Online Document Clustering with Application to Novelty Detection Jian Zhang School of Computer Science Cargenie Mellon University Pittsburgh, PA 15213 jian.zhang@cs.cmu.edu Zoubin
A Probabilistic Model for Online Document Clustering with Application to Novelty Detection Jian Zhang School of Computer Science Cargenie Mellon University Pittsburgh, PA 15213 jian.zhang@cs.cmu.edu Zoubin
Moving Least Squares Approximation
 Chapter 7 Moving Least Squares Approimation An alternative to radial basis function interpolation and approimation is the so-called moving least squares method. As we will see below, in this method the
Chapter 7 Moving Least Squares Approimation An alternative to radial basis function interpolation and approimation is the so-called moving least squares method. As we will see below, in this method the
Spazi vettoriali e misure di similaritá
 Spazi vettoriali e misure di similaritá R. Basili Corso di Web Mining e Retrieval a.a. 2008-9 April 10, 2009 Outline Outline Spazi vettoriali a valori reali Operazioni tra vettori Indipendenza Lineare
Spazi vettoriali e misure di similaritá R. Basili Corso di Web Mining e Retrieval a.a. 2008-9 April 10, 2009 Outline Outline Spazi vettoriali a valori reali Operazioni tra vettori Indipendenza Lineare
Numerical methods for American options
 Lecture 9 Numerical methods for American options Lecture Notes by Andrzej Palczewski Computational Finance p. 1 American options The holder of an American option has the right to exercise it at any moment
Lecture 9 Numerical methods for American options Lecture Notes by Andrzej Palczewski Computational Finance p. 1 American options The holder of an American option has the right to exercise it at any moment
STA 4273H: Statistical Machine Learning
 STA 4273H: Statistical Machine Learning Russ Salakhutdinov Department of Statistics! rsalakhu@utstat.toronto.edu! http://www.cs.toronto.edu/~rsalakhu/ Lecture 6 Three Approaches to Classification Construct
STA 4273H: Statistical Machine Learning Russ Salakhutdinov Department of Statistics! rsalakhu@utstat.toronto.edu! http://www.cs.toronto.edu/~rsalakhu/ Lecture 6 Three Approaches to Classification Construct
Statistical Machine Learning from Data
 Samy Bengio Statistical Machine Learning from Data 1 Statistical Machine Learning from Data Gaussian Mixture Models Samy Bengio IDIAP Research Institute, Martigny, Switzerland, and Ecole Polytechnique
Samy Bengio Statistical Machine Learning from Data 1 Statistical Machine Learning from Data Gaussian Mixture Models Samy Bengio IDIAP Research Institute, Martigny, Switzerland, and Ecole Polytechnique
An Introduction to Data Mining
 An Introduction to Intel Beijing wei.heng@intel.com January 17, 2014 Outline 1 DW Overview What is Notable Application of Conference, Software and Applications Major Process in 2 Major Tasks in Detail
An Introduction to Intel Beijing wei.heng@intel.com January 17, 2014 Outline 1 DW Overview What is Notable Application of Conference, Software and Applications Major Process in 2 Major Tasks in Detail
A Simple Introduction to Support Vector Machines
 A Simple Introduction to Support Vector Machines Martin Law Lecture for CSE 802 Department of Computer Science and Engineering Michigan State University Outline A brief history of SVM Large-margin linear
A Simple Introduction to Support Vector Machines Martin Law Lecture for CSE 802 Department of Computer Science and Engineering Michigan State University Outline A brief history of SVM Large-margin linear
Automatic 3D Reconstruction via Object Detection and 3D Transformable Model Matching CS 269 Class Project Report
 Automatic 3D Reconstruction via Object Detection and 3D Transformable Model Matching CS 69 Class Project Report Junhua Mao and Lunbo Xu University of California, Los Angeles mjhustc@ucla.edu and lunbo
Automatic 3D Reconstruction via Object Detection and 3D Transformable Model Matching CS 69 Class Project Report Junhua Mao and Lunbo Xu University of California, Los Angeles mjhustc@ucla.edu and lunbo
Large-Scale Similarity and Distance Metric Learning
 Large-Scale Similarity and Distance Metric Learning Aurélien Bellet Télécom ParisTech Joint work with K. Liu, Y. Shi and F. Sha (USC), S. Clémençon and I. Colin (Télécom ParisTech) Séminaire Criteo March
Large-Scale Similarity and Distance Metric Learning Aurélien Bellet Télécom ParisTech Joint work with K. Liu, Y. Shi and F. Sha (USC), S. Clémençon and I. Colin (Télécom ParisTech) Séminaire Criteo March
CURVE FITTING LEAST SQUARES APPROXIMATION
 CURVE FITTING LEAST SQUARES APPROXIMATION Data analysis and curve fitting: Imagine that we are studying a physical system involving two quantities: x and y Also suppose that we expect a linear relationship
CURVE FITTING LEAST SQUARES APPROXIMATION Data analysis and curve fitting: Imagine that we are studying a physical system involving two quantities: x and y Also suppose that we expect a linear relationship
Research of Postal Data mining system based on big data
 3rd International Conference on Mechatronics, Robotics and Automation (ICMRA 2015) Research of Postal Data mining system based on big data Xia Hu 1, Yanfeng Jin 1, Fan Wang 1 1 Shi Jiazhuang Post & Telecommunication
3rd International Conference on Mechatronics, Robotics and Automation (ICMRA 2015) Research of Postal Data mining system based on big data Xia Hu 1, Yanfeng Jin 1, Fan Wang 1 1 Shi Jiazhuang Post & Telecommunication
UMass at TREC 2008 Blog Distillation Task
 UMass at TREC 2008 Blog Distillation Task Jangwon Seo and W. Bruce Croft Center for Intelligent Information Retrieval University of Massachusetts, Amherst Abstract This paper presents the work done for
UMass at TREC 2008 Blog Distillation Task Jangwon Seo and W. Bruce Croft Center for Intelligent Information Retrieval University of Massachusetts, Amherst Abstract This paper presents the work done for
HT2015: SC4 Statistical Data Mining and Machine Learning
 HT2015: SC4 Statistical Data Mining and Machine Learning Dino Sejdinovic Department of Statistics Oxford http://www.stats.ox.ac.uk/~sejdinov/sdmml.html Bayesian Nonparametrics Parametric vs Nonparametric
HT2015: SC4 Statistical Data Mining and Machine Learning Dino Sejdinovic Department of Statistics Oxford http://www.stats.ox.ac.uk/~sejdinov/sdmml.html Bayesian Nonparametrics Parametric vs Nonparametric
Expert Finding Using Social Networking
 San Jose State University SJSU ScholarWorks Master's Projects Master's Theses and Graduate Research 1-1-2009 Expert Finding Using Social Networking Parin Shah San Jose State University Follow this and
San Jose State University SJSU ScholarWorks Master's Projects Master's Theses and Graduate Research 1-1-2009 Expert Finding Using Social Networking Parin Shah San Jose State University Follow this and
Multi-variable Calculus and Optimization
 Multi-variable Calculus and Optimization Dudley Cooke Trinity College Dublin Dudley Cooke (Trinity College Dublin) Multi-variable Calculus and Optimization 1 / 51 EC2040 Topic 3 - Multi-variable Calculus
Multi-variable Calculus and Optimization Dudley Cooke Trinity College Dublin Dudley Cooke (Trinity College Dublin) Multi-variable Calculus and Optimization 1 / 51 EC2040 Topic 3 - Multi-variable Calculus
Text Mining in JMP with R Andrew T. Karl, Senior Management Consultant, Adsurgo LLC Heath Rushing, Principal Consultant and Co-Founder, Adsurgo LLC
 Text Mining in JMP with R Andrew T. Karl, Senior Management Consultant, Adsurgo LLC Heath Rushing, Principal Consultant and Co-Founder, Adsurgo LLC 1. Introduction A popular rule of thumb suggests that
Text Mining in JMP with R Andrew T. Karl, Senior Management Consultant, Adsurgo LLC Heath Rushing, Principal Consultant and Co-Founder, Adsurgo LLC 1. Introduction A popular rule of thumb suggests that
Lecture 3: Linear methods for classification
 Lecture 3: Linear methods for classification Rafael A. Irizarry and Hector Corrada Bravo February, 2010 Today we describe four specific algorithms useful for classification problems: linear regression,
Lecture 3: Linear methods for classification Rafael A. Irizarry and Hector Corrada Bravo February, 2010 Today we describe four specific algorithms useful for classification problems: linear regression,
Largest Fixed-Aspect, Axis-Aligned Rectangle
 Largest Fixed-Aspect, Axis-Aligned Rectangle David Eberly Geometric Tools, LLC http://www.geometrictools.com/ Copyright c 1998-2016. All Rights Reserved. Created: February 21, 2004 Last Modified: February
Largest Fixed-Aspect, Axis-Aligned Rectangle David Eberly Geometric Tools, LLC http://www.geometrictools.com/ Copyright c 1998-2016. All Rights Reserved. Created: February 21, 2004 Last Modified: February
Solving Three-objective Optimization Problems Using Evolutionary Dynamic Weighted Aggregation: Results and Analysis
 Solving Three-objective Optimization Problems Using Evolutionary Dynamic Weighted Aggregation: Results and Analysis Abstract. In this paper, evolutionary dynamic weighted aggregation methods are generalized
Solving Three-objective Optimization Problems Using Evolutionary Dynamic Weighted Aggregation: Results and Analysis Abstract. In this paper, evolutionary dynamic weighted aggregation methods are generalized
Tutorial on Markov Chain Monte Carlo
 Tutorial on Markov Chain Monte Carlo Kenneth M. Hanson Los Alamos National Laboratory Presented at the 29 th International Workshop on Bayesian Inference and Maximum Entropy Methods in Science and Technology,
Tutorial on Markov Chain Monte Carlo Kenneth M. Hanson Los Alamos National Laboratory Presented at the 29 th International Workshop on Bayesian Inference and Maximum Entropy Methods in Science and Technology,
Mathematical finance and linear programming (optimization)
 Mathematical finance and linear programming (optimization) Geir Dahl September 15, 2009 1 Introduction The purpose of this short note is to explain how linear programming (LP) (=linear optimization) may
Mathematical finance and linear programming (optimization) Geir Dahl September 15, 2009 1 Introduction The purpose of this short note is to explain how linear programming (LP) (=linear optimization) may
ALMOST COMMON PRIORS 1. INTRODUCTION
 ALMOST COMMON PRIORS ZIV HELLMAN ABSTRACT. What happens when priors are not common? We introduce a measure for how far a type space is from having a common prior, which we term prior distance. If a type
ALMOST COMMON PRIORS ZIV HELLMAN ABSTRACT. What happens when priors are not common? We introduce a measure for how far a type space is from having a common prior, which we term prior distance. If a type
An Overview of Knowledge Discovery Database and Data mining Techniques
 An Overview of Knowledge Discovery Database and Data mining Techniques Priyadharsini.C 1, Dr. Antony Selvadoss Thanamani 2 M.Phil, Department of Computer Science, NGM College, Pollachi, Coimbatore, Tamilnadu,
An Overview of Knowledge Discovery Database and Data mining Techniques Priyadharsini.C 1, Dr. Antony Selvadoss Thanamani 2 M.Phil, Department of Computer Science, NGM College, Pollachi, Coimbatore, Tamilnadu,
Support Vector Machines Explained
 March 1, 2009 Support Vector Machines Explained Tristan Fletcher www.cs.ucl.ac.uk/staff/t.fletcher/ Introduction This document has been written in an attempt to make the Support Vector Machines (SVM),
March 1, 2009 Support Vector Machines Explained Tristan Fletcher www.cs.ucl.ac.uk/staff/t.fletcher/ Introduction This document has been written in an attempt to make the Support Vector Machines (SVM),
Creating, Solving, and Graphing Systems of Linear Equations and Linear Inequalities
 Algebra 1, Quarter 2, Unit 2.1 Creating, Solving, and Graphing Systems of Linear Equations and Linear Inequalities Overview Number of instructional days: 15 (1 day = 45 60 minutes) Content to be learned
Algebra 1, Quarter 2, Unit 2.1 Creating, Solving, and Graphing Systems of Linear Equations and Linear Inequalities Overview Number of instructional days: 15 (1 day = 45 60 minutes) Content to be learned
Music Mood Classification
 Music Mood Classification CS 229 Project Report Jose Padial Ashish Goel Introduction The aim of the project was to develop a music mood classifier. There are many categories of mood into which songs may
Music Mood Classification CS 229 Project Report Jose Padial Ashish Goel Introduction The aim of the project was to develop a music mood classifier. There are many categories of mood into which songs may
Non-negative Matrix Factorization (NMF) in Semi-supervised Learning Reducing Dimension and Maintaining Meaning
 Non-negative Matrix Factorization (NMF) in Semi-supervised Learning Reducing Dimension and Maintaining Meaning SAMSI 10 May 2013 Outline Introduction to NMF Applications Motivations NMF as a middle step
Non-negative Matrix Factorization (NMF) in Semi-supervised Learning Reducing Dimension and Maintaining Meaning SAMSI 10 May 2013 Outline Introduction to NMF Applications Motivations NMF as a middle step
Introduction to Matrix Algebra
 Psychology 7291: Multivariate Statistics (Carey) 8/27/98 Matrix Algebra - 1 Introduction to Matrix Algebra Definitions: A matrix is a collection of numbers ordered by rows and columns. It is customary
Psychology 7291: Multivariate Statistics (Carey) 8/27/98 Matrix Algebra - 1 Introduction to Matrix Algebra Definitions: A matrix is a collection of numbers ordered by rows and columns. It is customary
Lecture 3: Finding integer solutions to systems of linear equations
 Lecture 3: Finding integer solutions to systems of linear equations Algorithmic Number Theory (Fall 2014) Rutgers University Swastik Kopparty Scribe: Abhishek Bhrushundi 1 Overview The goal of this lecture
Lecture 3: Finding integer solutions to systems of linear equations Algorithmic Number Theory (Fall 2014) Rutgers University Swastik Kopparty Scribe: Abhishek Bhrushundi 1 Overview The goal of this lecture
On the Interaction and Competition among Internet Service Providers
 On the Interaction and Competition among Internet Service Providers Sam C.M. Lee John C.S. Lui + Abstract The current Internet architecture comprises of different privately owned Internet service providers
On the Interaction and Competition among Internet Service Providers Sam C.M. Lee John C.S. Lui + Abstract The current Internet architecture comprises of different privately owned Internet service providers
Log-Linear Models. Michael Collins
 Log-Linear Models Michael Collins 1 Introduction This note describes log-linear models, which are very widely used in natural language processing. A key advantage of log-linear models is their flexibility:
Log-Linear Models Michael Collins 1 Introduction This note describes log-linear models, which are very widely used in natural language processing. A key advantage of log-linear models is their flexibility:
Azure Machine Learning, SQL Data Mining and R
 Azure Machine Learning, SQL Data Mining and R Day-by-day Agenda Prerequisites No formal prerequisites. Basic knowledge of SQL Server Data Tools, Excel and any analytical experience helps. Best of all:
Azure Machine Learning, SQL Data Mining and R Day-by-day Agenda Prerequisites No formal prerequisites. Basic knowledge of SQL Server Data Tools, Excel and any analytical experience helps. Best of all:
Background: State Estimation
 State Estimation Cyber Security of the Smart Grid Dr. Deepa Kundur Background: State Estimation University of Toronto Dr. Deepa Kundur (University of Toronto) Cyber Security of the Smart Grid 1 / 81 Dr.
State Estimation Cyber Security of the Smart Grid Dr. Deepa Kundur Background: State Estimation University of Toronto Dr. Deepa Kundur (University of Toronto) Cyber Security of the Smart Grid 1 / 81 Dr.
Descriptive statistics Statistical inference statistical inference, statistical induction and inferential statistics
 Descriptive statistics is the discipline of quantitatively describing the main features of a collection of data. Descriptive statistics are distinguished from inferential statistics (or inductive statistics),
Descriptive statistics is the discipline of quantitatively describing the main features of a collection of data. Descriptive statistics are distinguished from inferential statistics (or inductive statistics),
Machine Learning for Data Science (CS4786) Lecture 1
 Machine Learning for Data Science (CS4786) Lecture 1 Tu-Th 10:10 to 11:25 AM Hollister B14 Instructors : Lillian Lee and Karthik Sridharan ROUGH DETAILS ABOUT THE COURSE Diagnostic assignment 0 is out:
Machine Learning for Data Science (CS4786) Lecture 1 Tu-Th 10:10 to 11:25 AM Hollister B14 Instructors : Lillian Lee and Karthik Sridharan ROUGH DETAILS ABOUT THE COURSE Diagnostic assignment 0 is out:
