JAVA 2 Network Security
|
|
|
- Verity Perkins
- 9 years ago
- Views:
Transcription
1 JAVA 2 Network Security M A R C O PISTOIA DUANE F. RELLER DEEPAK GUPTA MILIND NAGNUR ASHOK K. RAMANI PTR, UPPER PRENTICE HALL SADDLE RIVER, NEW JERSEY 07458
2 Contents Foreword Preface The Team That Wrote This Redbook Comments Welcome v xix xix xxi Part 1. Introduction to Java and Security 1 Chapter 1. An Overview of Java and Security Java Is Not Just a Language What Java Does Java Is Not an Island: Java as a Part of Security Safety and Security Java as an Aid to Security Java as a Threat to Security Writing Secure Java Staying One Jump Ahead The Vigilant Web Site Understanding Java 2 Security An Example of Applet Security in Java An Example of Application Security in Java Summary 33 Chapter 2. Attack and Defense Components of Java The Development Environment The Execution Environment Interfaces and Architectures Java 2 and Cryptography Cryptographic Tools in Brief Java Cryptography Architecture United States Export Rules for Encryption Signed Code The Other Side of the Coin - Access Control Attacking the World of Java Perils in the Life of Remote Code Vulnerabilities in Java Applications Summary 68 Chapter 3. The New Java Security Model The Need for Java Security 69 ix
3 3.2 Evolution of the Java Security Model The JDK 1.0 Sandbox Security Model The Concept of Trusted Code in JDK The Fine-Grained Access Control of Java A Comparison of the Three Java Security Models Java 2 Protection Domain and Permissions Model New Class Search Path Boot Class Path Extensions Framework Application Class Path Class Search Paths in Summary Java 2 Class Loading Mechanism Run-Time Access Controls The Policy File The Default System-Wide Policy File Security Manager vs Access Controller Security Management with Java Applying a Security Manager to Applets and Applications Applying a User-Defined Security Policy Java Security Debugging Summary 106 Part 2. Under the Hood 107 Chapter 4. The Java Virtual Machine The Java Virtual Machine, Close Up The Class Loader The Class File Verifier The Heap The Class Area The Native Method Loader The Security Manager The Execution Engine Just-in-Time Compilers Summary 115 Chapter 5. Class Files in Java The Traditional Development Life Cycle The Java Development Life Cycle The Java 2 Class File Format Decompilation Attacks The Constant Pool Beating the Decompilation Threat 134 X Java 2 Network Security
4 5.5 Java Bytecode A Bytecode Example 136 Chapter 6. The Class Loader and Class File Verifier Class Loaders Loading Classes from Trusted Sources Loading Classes from Untrusted Sources Beyond What the JVM Provides The Class Loading Process Should You Build Your Own Class Loader The Class File Verifier An Example of Class File Verification The Duties of the Class File Verifier The Four Passes of the Class File Verifier The Bytecode Verifier in Detail The Data Flow Analyzer An Incompleteness Theorem for Bytecode Verifiers Summary 184 Chapter 7. The Java 2 SecurityManager What SecurityManager Does Operation of the Security Manager Interdependence of the Three JVM Security Elements Attacking the Defenses of Java Types of Attack Malicious Applets Avoiding Security Hazards How to Test Examples of Security Manager Extensions First Example - Overriding checkwrite() Second Example - Overriding checkpermission() Third Example - Overriding checkread() and checkwrite() Summary 224 Chapter 8. Security Configuration Files in the Java 2 SDK A Note on Java.home and the JRE Installation Directory Keystores The Certificates KeyStore File cacerts The Security Properties File, Java.security Security Policy Files keystore Entry grant Entries An Example of Security Settings in the Java 2 Platform The Count Application Source Code 248 xi
5 8.5.2 A Sample Text File Compiling the Application Running the Application without a Security Manager Running the Application with the Default Security Manager Policy File Modification File Read Access to Files in the Code Base URL Directory Security Properties and Policy File Protection How to Implement a Policy Server 252 Chapter 9. Java 2 SDK Security Tools Key and Certificate Management Tool keytool Syntax Store and Private Key Password Commands and Options Associated with keytool An Example of keytool Usage Java Archive Tool Options of the jar Command Running a JAR File JAR Signing and Verification Tool jarsigner Scenario Observations on the jarsigner Verification Process Tampering with a Signed JAR File Policy File Creation and Management Tool Observations on the Use of the Policy Tool 295 Chapter 10. Security APIs in Java The Package Java.security Principals Guard Interface and GuardedObject Class Providers The Security Class Access Control APIs Key Management Message Digests and Digital Signatures Secure Random Number Generation The SignedObject Class Permission APIs Code Source Protection Domain Policy Secure Class Loader Algorithm Parameters The Package Java.security.spec 322 Java 2 Network Security
6 10.3 The Package Java.security.cert Package Java.security.interfaces The Package Java.security.acl Examples Using the Java 2 Security APIs Signature and Signature Verification Using Keystores The Permission Classes How to Create New Permissions Working with Signed Permissions How to Write Privileged Code First Case - No Return Value, No Exception Thrown Second Case - Return Value, No Exception Thrown Third Case - Return Value, Exception Thrown Accessing Local Variables An Example of Privileged Blocks Usage General Recommendations on Using the Privileged Blocks Chapter 11. The Java Plug-In Main Features of Java Plug-In What Does the Java Plug-In Do? Java Plug-In HTML Changes Changes Supported by Navigator Changes Supported by Internet Explorer Changes Supported by Both Navigator and Internet Explorer All the Web Browsers Java Plug-in Software HTML Converter Java Plug-In Control Panel The Basic Panel The Advanced Panel The Proxies Panel Java Plug-In Security Scenario First Step - Without Using the Java Plug-in Second Step - Using the Java Plug-in 377 Chapter 12. Java Gets Out of Its Box JAR Files and Applet Signing Manifest File Signature File Signature Block File Signed Code Scenario in JDK 1.1 and Sun HotJava Creating the CA Key Database Creating the Server Key Database Creating and Signing a JAR File 397
7 Running the Applet Creating the Client Key Database Signed Code Scenario in Java 2 SDK, Standard Edition, V Creating a Keystore for Certification Authorities Creating the Server Certificate Creating and Signing a JAR file Granting the Permissions and Running the Applet Signed Code Scenario in Netscape Communicator Using the netscape.security Package Installing Keys and Certificates in Netscape Communicator Signing JAR Files with Netscape Signing Tool Signed Code Scenario in Microsoft Internet Explorer First Example with Signed CAB Files A More Complex Signed CAB File Example The JAR Bug - Fixed In Java 2 SDK, Standard Edition, V The Solution in Java 2 SDK, Standard Edition, V Future Developments 470 Part 3. Beyond the Island of Java - Surfing into the Unknown 473 Chapter 13. Cryptography in Java Security Questions, Cryptographic Answers Public Key Certificates The Java Cryptography Architecture Framework JCE and United States Export Considerations Relationship between Java 2 SDK, JCA and JCE APIs JCA Terms and Definitions The Provider Concept in the JCA Engine Classes Algorithms Java Cryptography Extension JCE - Packages and Their Contents The Cipher Class The Cipher Stream Classes Secret Key Interfaces and Classes The KeyGenerator Class The Key Agreement Class The SealedObject Class Java Cryptography in Practice First Scenario Second Scenario Asymmetric Encryption with the Java 2 SDK and JCE Using Asymmetric Encryption 516 xiv Java 2 Network Security
8 13.7 How to Implement Your Own Provider Write the Service Implementation Code Give the Provider a Name Write a Master Class Compile the Code Install and Configure the Provider Test if the Provider Is Ready Algorithm Aliases Dependencies on Other Algorithms Default Initializations A Sample Master Class 526 Chapter 14. Enterprise Java Browser Add-On Applets Networked Architectures Applying the Java 2 Access Control Mechanisms Two-Tier Architecture Three-Tier Architecture Network Security Secure Clients and Network Computers Server-Side Java The Cost of Server-Side Java Servlets Advantages of Servlets Servlets and CGI-BINs Java Servlet APIs Servlet Life Cycle IBM WebSphere Application Server A Sample Servlet The Current Servlet Security Model Distributed Object Architectures - RMI Stubs and Skeletons RMI Registry A Sample RMI Program The Security of RMI Enterprise JavaBeans 580 Chapter 15. Java and Firewalls - In and Out of the Net What Is a Firewall? What Does a Firewall Do? Inside a TCP/IP Packet How Can Programs Communicate through a Firewall? Detailed Example of TCP/IP Protocol 588 xv
9 DNS Flow (UDP Example) HTTP Flow (TCP Example) Proxy Servers and SOCKS Gateways Proxy Servers What Is SOCKS? Using Proxy Servers or SOCKS Gateways The Effect of Firewalls on Java Downloading an Applet Using HTTP Stopping Java Downloads with a Firewall Java Network Connections through the Firewall Java and Firewall Scenarios URL Connection Socket Connection Conclusions Remote Method Invocation Summary 628 Chapter 16. Java and SSL What Is SSL? Using SSL from an Applet Using SSL URLs with Java Java and SSL with Sun Microsystems The javax.net Package The javax.net.ssl Package The javax.security.cert Package How to Use Java and SSL Skeleton Program without SSL Using SSL with the Sun Microsystems API Java and SSL with IBM SSLite Extensions to the SSL Protocol SSLite Key Ring Management Tools SSL Server Authentication with IBM SSLite for Java Conclusions Summary 668 Chapter 17. Epilogue Future Directions of Java Java 2 SDK-The Path Ahead Resource Consumption Management Java Authentication and Authorization Service Java RMI Security Extension Arbitrary Grouping of Permissions Object-Level Protection 671 XVI Java 2 Network Security
10 Subdividing Protection Domains Running Applets with Signed Content Java 2 Platform, Enterprise Edition Conclusion 673 Appendix A. Getting Internal System Properties 675 A.1 Program GetAIIProperties 675 A.2 Program GetProperty 678 Appendix B. Signature Formats 681 Appendix C. X.509 Certificates 683 C.1 X.509 Certificate Versions 684 Appendix D. Sources of Information about Java Security 685 D.1 Companies 685 D.1.1 JavaSoft 685 D.1.2 Sun 686 D.1.3 IBM 686 D.1.4 Microsoft 687 D.1.5 Reliable Software Technologies 688 D.1.6 JavaWorld 688 D.1.7 JCE Providers outside the United States 688 D.2 Universities 689 D.2.1 Princeton 689 D.2.2 Yale 689 D.2.3 Others 690 Appendix E. What's on the Diskette? 691 E.1 How to Access the Diskette 691 E.2 How to Get the Same Software Material from the Web 691 Appendix F. Special Notices 693 Appendix G. Related Publications 697 G.1 International Technical Support Organization Publications 697 G.2 Redbooks on CD-ROMs 697 G.3 Other Publications 697 How to Get ITSO Redbooks 699 IBM Redbook Fax Order Form 700 xvii
11 Glossary 701 Index 703 ITSO Redbook Evaluation 713 XVIII Java 2 Network Security
Java Thin-Client Programming for a Network Computing Environment
 Java Thin-Client Programming for a Network Computing Environment JÜRGEN FRIEDRICHS HENRI J I B I N AND THE JALAPENO TEAM / - : / :.. : :. ISBN 0-13-011117-1 PRENTICE HALL PTR, UPPER SADDLE RIVER, NEW JERSEY
Java Thin-Client Programming for a Network Computing Environment JÜRGEN FRIEDRICHS HENRI J I B I N AND THE JALAPENO TEAM / - : / :.. : :. ISBN 0-13-011117-1 PRENTICE HALL PTR, UPPER SADDLE RIVER, NEW JERSEY
Enabling SSL and Client Certificates on the SAP J2EE Engine
 Enabling SSL and Client Certificates on the SAP J2EE Engine Angel Dichev RIG, SAP Labs SAP AG 1 Learning Objectives As a result of this session, you will be able to: Understand the different SAP J2EE Engine
Enabling SSL and Client Certificates on the SAP J2EE Engine Angel Dichev RIG, SAP Labs SAP AG 1 Learning Objectives As a result of this session, you will be able to: Understand the different SAP J2EE Engine
Angel Dichev RIG, SAP Labs
 Enabling SSL and Client Certificates on the SAP J2EE Engine Angel Dichev RIG, SAP Labs Learning Objectives As a result of this session, you will be able to: Understand the different SAP J2EE Engine SSL
Enabling SSL and Client Certificates on the SAP J2EE Engine Angel Dichev RIG, SAP Labs Learning Objectives As a result of this session, you will be able to: Understand the different SAP J2EE Engine SSL
Enterprise Java. Where, How, When (and When Not) to Apply Java in Client/Server Business Environments. Jeffrey Savit Sean Wilcox Bhuvana Jayaraman
 Enterprise Java Where, How, When (and When Not) to Apply Java in Client/Server Business Environments Jeffrey Savit Sean Wilcox Bhuvana Jayaraman McGraw-Hill j New York San Francisco Washington, D.C. Auckland
Enterprise Java Where, How, When (and When Not) to Apply Java in Client/Server Business Environments Jeffrey Savit Sean Wilcox Bhuvana Jayaraman McGraw-Hill j New York San Francisco Washington, D.C. Auckland
Entrust Certificate Services. Java Code Signing. User Guide. Date of Issue: December 2014. Document issue: 2.0
 Entrust Certificate Services Java Code Signing User Guide Date of Issue: December 2014 Document issue: 2.0 Copyright 2009-2014 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Entrust Certificate Services Java Code Signing User Guide Date of Issue: December 2014 Document issue: 2.0 Copyright 2009-2014 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Using etoken for SSL Web Authentication. SSL V3.0 Overview
 Using etoken for SSL Web Authentication Lesson 12 April 2004 etoken Certification Course SSL V3.0 Overview Secure Sockets Layer protocol, version 3.0 Provides communication privacy over the internet. Prevents
Using etoken for SSL Web Authentication Lesson 12 April 2004 etoken Certification Course SSL V3.0 Overview Secure Sockets Layer protocol, version 3.0 Provides communication privacy over the internet. Prevents
PowerChute TM Network Shutdown Security Features & Deployment
 PowerChute TM Network Shutdown Security Features & Deployment By David Grehan, Sarah Jane Hannon ABSTRACT PowerChute TM Network Shutdown (PowerChute) software works in conjunction with the UPS Network
PowerChute TM Network Shutdown Security Features & Deployment By David Grehan, Sarah Jane Hannon ABSTRACT PowerChute TM Network Shutdown (PowerChute) software works in conjunction with the UPS Network
SafeNet KMIP and Google Cloud Storage Integration Guide
 SafeNet KMIP and Google Cloud Storage Integration Guide Documentation Version: 20130719 Table of Contents CHAPTER 1 GOOGLE CLOUD STORAGE................................. 2 Introduction...............................................................
SafeNet KMIP and Google Cloud Storage Integration Guide Documentation Version: 20130719 Table of Contents CHAPTER 1 GOOGLE CLOUD STORAGE................................. 2 Introduction...............................................................
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
SSL Configuration on Weblogic Oracle FLEXCUBE Universal Banking Release 12.0.87.01.0 [August] [2014]
![SSL Configuration on Weblogic Oracle FLEXCUBE Universal Banking Release 12.0.87.01.0 [August] [2014] SSL Configuration on Weblogic Oracle FLEXCUBE Universal Banking Release 12.0.87.01.0 [August] [2014]](/thumbs/34/16904074.jpg) SSL Configuration on Weblogic Oracle FLEXCUBE Universal Banking Release 12.0.87.01.0 [August] [2014] Table of Contents 1. CONFIGURING SSL ON ORACLE WEBLOGIC... 1-1 1.1 INTRODUCTION... 1-1 1.2 SETTING UP
SSL Configuration on Weblogic Oracle FLEXCUBE Universal Banking Release 12.0.87.01.0 [August] [2014] Table of Contents 1. CONFIGURING SSL ON ORACLE WEBLOGIC... 1-1 1.1 INTRODUCTION... 1-1 1.2 SETTING UP
Installing Digital Certificates for Server Authentication SSL on. BEA WebLogic 8.1
 Installing Digital Certificates for Server Authentication SSL on BEA WebLogic 8.1 Installing Digital Certificates for Server Authentication SSL You use utilities provided with the BEA WebLogic server software
Installing Digital Certificates for Server Authentication SSL on BEA WebLogic 8.1 Installing Digital Certificates for Server Authentication SSL You use utilities provided with the BEA WebLogic server software
SSL CONFIGURATION GUIDE
 HYPERION RELEASE 9.3.1 SSL CONFIGURATION GUIDE CONTENTS IN BRIEF About This Document... 2 Assumptions... 2 Information Sources... 2 Identifying SSL Points for Hyperion Products... 4 Common Activities...
HYPERION RELEASE 9.3.1 SSL CONFIGURATION GUIDE CONTENTS IN BRIEF About This Document... 2 Assumptions... 2 Information Sources... 2 Identifying SSL Points for Hyperion Products... 4 Common Activities...
E-Commerce Security. The Client-Side Vulnerabilities. Securing the Data Transaction LECTURE 7 (SECURITY)
 E-Commerce Security An e-commerce security system has four fronts: LECTURE 7 (SECURITY) Web Client Security Data Transport Security Web Server Security Operating System Security A safe e-commerce system
E-Commerce Security An e-commerce security system has four fronts: LECTURE 7 (SECURITY) Web Client Security Data Transport Security Web Server Security Operating System Security A safe e-commerce system
Configuring IBM WebSphere Application Server 7 for Secure Sockets Layer and Client-Certificate Authentication on SAS 9.3 Enterprise BI Server Web
 Configuring IBM WebSphere Application Server 7 for Secure Sockets Layer and Client-Certificate Authentication on SAS 9.3 Enterprise BI Server Web Applications Configuring IBM WebSphere 7 for SSL and Client-Certificate
Configuring IBM WebSphere Application Server 7 for Secure Sockets Layer and Client-Certificate Authentication on SAS 9.3 Enterprise BI Server Web Applications Configuring IBM WebSphere 7 for SSL and Client-Certificate
Table of Contents Preface...1 Chapter 1. Java Application Security...7 Chapter 2. The Default Sandbox...21 Chapter 3. Java Language Security...
 Table of Contents Preface...1 Who Should Read This Book?...1 Versions Used in This Book...2 Conventions Used in This Book...2 Organization of This Book...3 What's New in This Edition...5 How to Contact
Table of Contents Preface...1 Who Should Read This Book?...1 Versions Used in This Book...2 Conventions Used in This Book...2 Organization of This Book...3 What's New in This Edition...5 How to Contact
Workday Mobile Security FAQ
 Workday Mobile Security FAQ Workday Mobile Security FAQ Contents The Workday Approach 2 Authentication 3 Session 3 Mobile Device Management (MDM) 3 Workday Applications 4 Web 4 Transport Security 5 Privacy
Workday Mobile Security FAQ Workday Mobile Security FAQ Contents The Workday Approach 2 Authentication 3 Session 3 Mobile Device Management (MDM) 3 Workday Applications 4 Web 4 Transport Security 5 Privacy
HOW TO CONFIGURE PASS-THRU PROXY FOR ORACLE APPLICATIONS
 HOW TO CONFIGURE PASS-THRU PROXY FOR ORACLE APPLICATIONS Overview of Oracle JInitiator Oracle JInitiator enables users to run Oracle Forms applications using Netscape Navigator or Internet Explorer. It
HOW TO CONFIGURE PASS-THRU PROXY FOR ORACLE APPLICATIONS Overview of Oracle JInitiator Oracle JInitiator enables users to run Oracle Forms applications using Netscape Navigator or Internet Explorer. It
Security Digital Certificate Manager
 System i Security Digital Certificate Manager Version 5 Release 4 System i Security Digital Certificate Manager Version 5 Release 4 Note Before using this information and the product it supports, be sure
System i Security Digital Certificate Manager Version 5 Release 4 System i Security Digital Certificate Manager Version 5 Release 4 Note Before using this information and the product it supports, be sure
GoToMyPC Corporate Advanced Firewall Support Features
 F A C T S H E E T GoToMyPC Corporate Advanced Firewall Support Features Citrix GoToMyPC Corporate features Citrix Online s advanced connectivity technology. We support all of the common firewall and proxy
F A C T S H E E T GoToMyPC Corporate Advanced Firewall Support Features Citrix GoToMyPC Corporate features Citrix Online s advanced connectivity technology. We support all of the common firewall and proxy
Secure Communication Requirements
 Secure Communication Requirements 1993-2016 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording or otherwise)
Secure Communication Requirements 1993-2016 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording or otherwise)
IUCLID 5 Guidance and Support
 IUCLID 5 Guidance and Support Web Service Installation Guide July 2012 v 2.4 July 2012 1/11 Table of Contents 1. Introduction 3 1.1. Important notes 3 1.2. Prerequisites 3 1.3. Installation files 4 2.
IUCLID 5 Guidance and Support Web Service Installation Guide July 2012 v 2.4 July 2012 1/11 Table of Contents 1. Introduction 3 1.1. Important notes 3 1.2. Prerequisites 3 1.3. Installation files 4 2.
Oracle Fusion Middleware
 Oracle Fusion Middleware Administrator s Guide for Oracle Directory Integration Platform 11g Release 1 (11.1.1) E10031-03 April 2010 Oracle Fusion Middleware Administrator's Guide for Oracle Directory
Oracle Fusion Middleware Administrator s Guide for Oracle Directory Integration Platform 11g Release 1 (11.1.1) E10031-03 April 2010 Oracle Fusion Middleware Administrator's Guide for Oracle Directory
Introduction to Mobile Access Gateway Installation
 Introduction to Mobile Access Gateway Installation This document describes the installation process for the Mobile Access Gateway (MAG), which is an enterprise integration component that provides a secure
Introduction to Mobile Access Gateway Installation This document describes the installation process for the Mobile Access Gateway (MAG), which is an enterprise integration component that provides a secure
VMware vrealize Operations for Horizon Security
 VMware vrealize Operations for Horizon Security vrealize Operations for Horizon 6.1 This document supports the version of each product listed and supports all subsequent versions until the document is
VMware vrealize Operations for Horizon Security vrealize Operations for Horizon 6.1 This document supports the version of each product listed and supports all subsequent versions until the document is
Application Servers - BEA WebLogic. Installing the Application Server
 Proven Practice Application Servers - BEA WebLogic. Installing the Application Server Product(s): IBM Cognos 8.4, BEA WebLogic Server Area of Interest: Infrastructure DOC ID: AS01 Version 8.4.0.0 Application
Proven Practice Application Servers - BEA WebLogic. Installing the Application Server Product(s): IBM Cognos 8.4, BEA WebLogic Server Area of Interest: Infrastructure DOC ID: AS01 Version 8.4.0.0 Application
JVA-122. Secure Java Web Development
 JVA-122. Secure Java Web Development Version 7.0 This comprehensive course shows experienced developers of Java EE applications how to secure those applications and to apply best practices with regard
JVA-122. Secure Java Web Development Version 7.0 This comprehensive course shows experienced developers of Java EE applications how to secure those applications and to apply best practices with regard
Chapter 17. Transport-Level Security
 Chapter 17 Transport-Level Security Web Security Considerations The World Wide Web is fundamentally a client/server application running over the Internet and TCP/IP intranets The following characteristics
Chapter 17 Transport-Level Security Web Security Considerations The World Wide Web is fundamentally a client/server application running over the Internet and TCP/IP intranets The following characteristics
VMware vrealize Operations for Horizon Security
 VMware vrealize Operations for Horizon Security vrealize Operations for Horizon 6.2 This document supports the version of each product listed and supports all subsequent versions until the document is
VMware vrealize Operations for Horizon Security vrealize Operations for Horizon 6.2 This document supports the version of each product listed and supports all subsequent versions until the document is
CMSC 421, Operating Systems. Fall 2008. Security. URL: http://www.csee.umbc.edu/~kalpakis/courses/421. Dr. Kalpakis
 CMSC 421, Operating Systems. Fall 2008 Security Dr. Kalpakis URL: http://www.csee.umbc.edu/~kalpakis/courses/421 Outline The Security Problem Authentication Program Threats System Threats Securing Systems
CMSC 421, Operating Systems. Fall 2008 Security Dr. Kalpakis URL: http://www.csee.umbc.edu/~kalpakis/courses/421 Outline The Security Problem Authentication Program Threats System Threats Securing Systems
Universal Content Management Version 10gR3. Security Providers Component Administration Guide
 Universal Content Management Version 10gR3 Security Providers Component Administration Guide Copyright 2008 Oracle. All rights reserved. The Programs (which include both the software and documentation)
Universal Content Management Version 10gR3 Security Providers Component Administration Guide Copyright 2008 Oracle. All rights reserved. The Programs (which include both the software and documentation)
Detailed Table of Contents
 Detailed Table of Contents Foreword Preface 1. Networking Protocols and OSI Model 1 1.1 Protocols in Computer Communications 3 1.2 The OSI Model 7 1.3 OSI Layer Functions 11 Summary 19 Key Terms and Concepts
Detailed Table of Contents Foreword Preface 1. Networking Protocols and OSI Model 1 1.1 Protocols in Computer Communications 3 1.2 The OSI Model 7 1.3 OSI Layer Functions 11 Summary 19 Key Terms and Concepts
Release 6.2.1 System Administrator s Guide
 IBM Maximo Release 6.2.1 System Administrator s Guide Note Before using this information and the product it supports, read the information in Notices on page Notices-1. First Edition (January 2007) This
IBM Maximo Release 6.2.1 System Administrator s Guide Note Before using this information and the product it supports, read the information in Notices on page Notices-1. First Edition (January 2007) This
No.1 IT Online training institute from Hyderabad Email: [email protected] URL: sriramtechnologies.com
 I. Basics 1. What is Application Server 2. The need for an Application Server 3. Java Application Solution Architecture 4. 3-tier architecture 5. Various commercial products in 3-tiers 6. The logic behind
I. Basics 1. What is Application Server 2. The need for an Application Server 3. Java Application Solution Architecture 4. 3-tier architecture 5. Various commercial products in 3-tiers 6. The logic behind
SECURITY COMPARISON BETWEEN IBM WEBSPHERE MQ 7.5 AND APACHE ACTIVEMQ 5.9
 SECURITY COMPARISON BETWEEN IBM WEBSPHERE MQ 7.5 AND APACHE ACTIVEMQ 5.9 Author: Timothy N. Scaggs, IBM, March 2014 Edited: Rodney Thomas, IBM, June, 2015 Table of Contents Executive Summary... 2 IBM WebSphere
SECURITY COMPARISON BETWEEN IBM WEBSPHERE MQ 7.5 AND APACHE ACTIVEMQ 5.9 Author: Timothy N. Scaggs, IBM, March 2014 Edited: Rodney Thomas, IBM, June, 2015 Table of Contents Executive Summary... 2 IBM WebSphere
How To Use A Sas Server On A Java Computer Or A Java.Net Computer (Sas) On A Microsoft Microsoft Server (Sasa) On An Ipo (Sauge) Or A Microsas (Sask
 Exploiting SAS Software Using Java Technology Barbara Walters, SAS Institute Inc., Cary, NC Abstract This paper describes how to use Java technology with SAS software. SAS Institute currently offers several
Exploiting SAS Software Using Java Technology Barbara Walters, SAS Institute Inc., Cary, NC Abstract This paper describes how to use Java technology with SAS software. SAS Institute currently offers several
Exploiting the Web with Tivoli Storage Manager
 Exploiting the Web with Tivoli Storage Manager Oxford University ADSM Symposium 29th Sept. - 1st Oct. 1999 Roland Leins, IBM ITSO Center - San Jose [email protected] Agenda The Web Client Concept Tivoli
Exploiting the Web with Tivoli Storage Manager Oxford University ADSM Symposium 29th Sept. - 1st Oct. 1999 Roland Leins, IBM ITSO Center - San Jose [email protected] Agenda The Web Client Concept Tivoli
Deploying EMC Documentum WDK Applications with IBM WebSEAL as a Reverse Proxy
 Deploying EMC Documentum WDK Applications with IBM WebSEAL as a Reverse Proxy Applied Technology Abstract This white paper serves as a detailed solutions guide for installing and configuring IBM WebSEAL
Deploying EMC Documentum WDK Applications with IBM WebSEAL as a Reverse Proxy Applied Technology Abstract This white paper serves as a detailed solutions guide for installing and configuring IBM WebSEAL
What is Web Security? Motivation
 [email protected] http://www.brucker.ch/ Information Security ETH Zürich Zürich, Switzerland Information Security Fundamentals March 23, 2004 The End Users View The Server Providers View What is Web
[email protected] http://www.brucker.ch/ Information Security ETH Zürich Zürich, Switzerland Information Security Fundamentals March 23, 2004 The End Users View The Server Providers View What is Web
Elements of Advanced Java Programming
 Appendix A Elements of Advanced Java Programming Objectives At the end of this appendix, you should be able to: Understand two-tier and three-tier architectures for distributed computing Understand the
Appendix A Elements of Advanced Java Programming Objectives At the end of this appendix, you should be able to: Understand two-tier and three-tier architectures for distributed computing Understand the
RHEV 2.2: REST API INSTALLATION
 RHEV 2.2: REST API INSTALLATION BY JAMES RANKIN REVISED 02/14/11 RHEV 2.2: REST API INSTALLATION 1 TABLE OF CONTENTS OVERVIEW PAGE 3 JAVA AND ENVIRONMENT VARIABLES PAGE 3 JBOSS INSTALLATION PAGE 5 REST
RHEV 2.2: REST API INSTALLATION BY JAMES RANKIN REVISED 02/14/11 RHEV 2.2: REST API INSTALLATION 1 TABLE OF CONTENTS OVERVIEW PAGE 3 JAVA AND ENVIRONMENT VARIABLES PAGE 3 JBOSS INSTALLATION PAGE 5 REST
Oracle WebLogic Server 11g Administration
 Oracle WebLogic Server 11g Administration This course is designed to provide instruction and hands-on practice in installing and configuring Oracle WebLogic Server 11g. These tasks include starting and
Oracle WebLogic Server 11g Administration This course is designed to provide instruction and hands-on practice in installing and configuring Oracle WebLogic Server 11g. These tasks include starting and
Feature and Technical
 BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 4 Feature and Technical Overview Published: 2013-11-07 SWD-20131107160132924 Contents 1 Document revision history...6 2 What's
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 4 Feature and Technical Overview Published: 2013-11-07 SWD-20131107160132924 Contents 1 Document revision history...6 2 What's
New Features... 1 Installation... 3 Upgrade Changes... 3 Fixed Limitations... 4 Known Limitations... 5 Informatica Global Customer Support...
 Informatica Corporation B2B Data Exchange Version 9.5.0 Release Notes June 2012 Copyright (c) 2006-2012 Informatica Corporation. All rights reserved. Contents New Features... 1 Installation... 3 Upgrade
Informatica Corporation B2B Data Exchange Version 9.5.0 Release Notes June 2012 Copyright (c) 2006-2012 Informatica Corporation. All rights reserved. Contents New Features... 1 Installation... 3 Upgrade
McAfee Web Gateway Administration Intel Security Education Services Administration Course Training
 McAfee Web Gateway Administration Intel Security Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction
McAfee Web Gateway Administration Intel Security Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction
Certificates for computers, Web servers, and Web browser users
 Entrust Managed Services PKI Certificates for computers, Web servers, and Web browser users Document issue: 3.0 Date of issue: June 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark
Entrust Managed Services PKI Certificates for computers, Web servers, and Web browser users Document issue: 3.0 Date of issue: June 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark
CHAPTER 1 - JAVA EE OVERVIEW FOR ADMINISTRATORS
 CHAPTER 1 - JAVA EE OVERVIEW FOR ADMINISTRATORS Java EE Components Java EE Vendor Specifications Containers Java EE Blueprint Services JDBC Data Sources Java Naming and Directory Interface Java Message
CHAPTER 1 - JAVA EE OVERVIEW FOR ADMINISTRATORS Java EE Components Java EE Vendor Specifications Containers Java EE Blueprint Services JDBC Data Sources Java Naming and Directory Interface Java Message
DEVELOPING CERTIFICATE-BASED PROJECTS FOR WEB SECURITY CLASSES *
 DEVELOPING CERTIFICATE-BASED PROJECTS FOR WEB SECURITY CLASSES * Shamima Rahman Tuan Anh Nguyen T. Andrew Yang Univ. of Houston Clear Lake 2700 Bay Area Blvd., Houston, TX 77058 [email protected] [email protected]
DEVELOPING CERTIFICATE-BASED PROJECTS FOR WEB SECURITY CLASSES * Shamima Rahman Tuan Anh Nguyen T. Andrew Yang Univ. of Houston Clear Lake 2700 Bay Area Blvd., Houston, TX 77058 [email protected] [email protected]
Enterprise Content Management System Monitor. How to deploy the JMX monitor application in WebSphere ND clustered environments. Revision 1.
 Enterprise Content Management System Monitor How to deploy the JMX monitor application in WebSphere ND clustered environments Revision 1.3 CENIT AG Author: Juergen Poiger 25. August 2015 2 Content Disclaimer...
Enterprise Content Management System Monitor How to deploy the JMX monitor application in WebSphere ND clustered environments Revision 1.3 CENIT AG Author: Juergen Poiger 25. August 2015 2 Content Disclaimer...
JAVA r VOLUME II-ADVANCED FEATURES. e^i v it;
 ..ui. : ' :>' JAVA r VOLUME II-ADVANCED FEATURES EIGHTH EDITION 'r.", -*U'.- I' -J L."'.!'.;._ ii-.ni CAY S. HORSTMANN GARY CORNELL It.. 1 rlli!>*-
..ui. : ' :>' JAVA r VOLUME II-ADVANCED FEATURES EIGHTH EDITION 'r.", -*U'.- I' -J L."'.!'.;._ ii-.ni CAY S. HORSTMANN GARY CORNELL It.. 1 rlli!>*-
WebSphere Training Outline
 WEBSPHERE TRAINING WebSphere Training Outline WebSphere Platform Overview o WebSphere Product Categories o WebSphere Development, Presentation, Integration and Deployment Tools o WebSphere Application
WEBSPHERE TRAINING WebSphere Training Outline WebSphere Platform Overview o WebSphere Product Categories o WebSphere Development, Presentation, Integration and Deployment Tools o WebSphere Application
Microsoft 10972 - Administering the Web Server (IIS) Role of Windows Server
 1800 ULEARN (853 276) www.ddls.com.au Microsoft 10972 - Administering the Web Server (IIS) Role of Windows Server Length 5 days Price $4169.00 (inc GST) Version B Overview This course provides students
1800 ULEARN (853 276) www.ddls.com.au Microsoft 10972 - Administering the Web Server (IIS) Role of Windows Server Length 5 days Price $4169.00 (inc GST) Version B Overview This course provides students
Certify your Software Integrity with thawte Code Signing Certificates
 Certify your Software Integrity with thawte Code Signing Certificates Sign your code and active content for secure online distribution... 1. Overview 2. Why a thawte Code Signing Certificate? 3. Who needs
Certify your Software Integrity with thawte Code Signing Certificates Sign your code and active content for secure online distribution... 1. Overview 2. Why a thawte Code Signing Certificate? 3. Who needs
Security Digital Certificate Manager
 IBM i Security Digital Certificate Manager 7.1 IBM i Security Digital Certificate Manager 7.1 Note Before using this information and the product it supports, be sure to read the information in Notices,
IBM i Security Digital Certificate Manager 7.1 IBM i Security Digital Certificate Manager 7.1 Note Before using this information and the product it supports, be sure to read the information in Notices,
SafeNet KMIP and Amazon S3 Integration Guide
 SafeNet KMIP and Amazon S3 Integration Guide Documentation Version: 20130524 2013 SafeNet, Inc. All rights reserved Preface All intellectual property is protected by copyright. All trademarks and product
SafeNet KMIP and Amazon S3 Integration Guide Documentation Version: 20130524 2013 SafeNet, Inc. All rights reserved Preface All intellectual property is protected by copyright. All trademarks and product
Java History. Java History (cont'd)
 Java History Created by James Gosling et. al. at Sun Microsystems in 1991 "The Green Team" Were to investigate "convergence" technologies Gosling created a processor-independent language for '*7', a 2-way
Java History Created by James Gosling et. al. at Sun Microsystems in 1991 "The Green Team" Were to investigate "convergence" technologies Gosling created a processor-independent language for '*7', a 2-way
Security Guide. BlackBerry Enterprise Service 12. for ios, Android, and Windows Phone. Version 12.0
 Security Guide BlackBerry Enterprise Service 12 for ios, Android, and Windows Phone Version 12.0 Published: 2015-02-06 SWD-20150206130210406 Contents About this guide... 6 What is BES12?... 7 Key features
Security Guide BlackBerry Enterprise Service 12 for ios, Android, and Windows Phone Version 12.0 Published: 2015-02-06 SWD-20150206130210406 Contents About this guide... 6 What is BES12?... 7 Key features
Secure web transactions system
 Secure web transactions system TRUSTED WEB SECURITY MODEL Recently, as the generally accepted model in Internet application development, three-tier or multi-tier applications are used. Moreover, new trends
Secure web transactions system TRUSTED WEB SECURITY MODEL Recently, as the generally accepted model in Internet application development, three-tier or multi-tier applications are used. Moreover, new trends
Risks with web programming technologies. Steve Branigan Lucent Technologies
 Risks with web programming technologies Steve Branigan Lucent Technologies Risks with web programming technologies Abstract Java applets and their kind are bringing new life to the World Wide Web. Through
Risks with web programming technologies Steve Branigan Lucent Technologies Risks with web programming technologies Abstract Java applets and their kind are bringing new life to the World Wide Web. Through
SSL Configuration Best Practices for SAS Visual Analytics 7.1 Web Applications and SAS LASR Authorization Service
 Paper SAS1541-2015 SSL Configuration Best Practices for SAS Visual Analytics 7.1 Web Applications and SAS LASR Authorization Service Heesun Park and Jerome Hughes, SAS Institute Inc., Cary, NC ABSTRACT
Paper SAS1541-2015 SSL Configuration Best Practices for SAS Visual Analytics 7.1 Web Applications and SAS LASR Authorization Service Heesun Park and Jerome Hughes, SAS Institute Inc., Cary, NC ABSTRACT
ERserver. iseries. Secure Sockets Layer (SSL)
 ERserver iseries Secure Sockets Layer (SSL) ERserver iseries Secure Sockets Layer (SSL) Copyright International Business Machines Corporation 2000, 2002. All rights reserved. US Government Users Restricted
ERserver iseries Secure Sockets Layer (SSL) ERserver iseries Secure Sockets Layer (SSL) Copyright International Business Machines Corporation 2000, 2002. All rights reserved. US Government Users Restricted
1 Reflection ZFE 5. 2 Security Considerations 13. 3 Troubleshooting the Installation 19. Contents 1
 1 Reflection ZFE 5 Introducing Reflection ZFE......................................................... 5 Reflection ZFE components.................................................. 5 System requirements..............................................................
1 Reflection ZFE 5 Introducing Reflection ZFE......................................................... 5 Reflection ZFE components.................................................. 5 System requirements..............................................................
BlackBerry Enterprise Service 10. Version: 10.2. Configuration Guide
 BlackBerry Enterprise Service 10 Version: 10.2 Configuration Guide Published: 2015-02-27 SWD-20150227164548686 Contents 1 Introduction...7 About this guide...8 What is BlackBerry Enterprise Service 10?...9
BlackBerry Enterprise Service 10 Version: 10.2 Configuration Guide Published: 2015-02-27 SWD-20150227164548686 Contents 1 Introduction...7 About this guide...8 What is BlackBerry Enterprise Service 10?...9
TIBCO iprocess Web Services Server Plug-in Installation. Software Release 11.3.0 October 2011
 TIBCO iprocess Web Services Server Plug-in Installation Software Release 11.3.0 October 2011 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED
TIBCO iprocess Web Services Server Plug-in Installation Software Release 11.3.0 October 2011 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED
IBM Application Hosting EDI Services Expedite software adds Secure Sockets Layer TCP/IP support
 Software Announcement June 1, 2004 Services Expedite software adds Secure Sockets Layer TCP/IP support Overview Services Expedite software for Microsoft Windows, AIX, and OS/400 is being enhanced to support
Software Announcement June 1, 2004 Services Expedite software adds Secure Sockets Layer TCP/IP support Overview Services Expedite software for Microsoft Windows, AIX, and OS/400 is being enhanced to support
Course Description. Course Audience. Course Outline. Course Page - Page 1 of 5
 Course Page - Page 1 of 5 WebSphere Application Server 7.0 Administration on Windows BSP-1700 Length: 5 days Price: $ 2,895.00 Course Description This course teaches the basics of the administration and
Course Page - Page 1 of 5 WebSphere Application Server 7.0 Administration on Windows BSP-1700 Length: 5 days Price: $ 2,895.00 Course Description This course teaches the basics of the administration and
Forward proxy server vs reverse proxy server
 Using a reverse proxy server for TAD4D/LMT Intended audience The intended recipient of this document is a TAD4D/LMT administrator and the staff responsible for the configuration of TAD4D/LMT agents. Purpose
Using a reverse proxy server for TAD4D/LMT Intended audience The intended recipient of this document is a TAD4D/LMT administrator and the staff responsible for the configuration of TAD4D/LMT agents. Purpose
Active Directory Adapter with 64-bit Support Installation and Configuration Guide
 IBM Security Identity Manager Version 6.0 Active Directory Adapter with 64-bit Support Installation and Configuration Guide SC27-4384-02 IBM Security Identity Manager Version 6.0 Active Directory Adapter
IBM Security Identity Manager Version 6.0 Active Directory Adapter with 64-bit Support Installation and Configuration Guide SC27-4384-02 IBM Security Identity Manager Version 6.0 Active Directory Adapter
Securing SAS Web Applications with SiteMinder
 Configuration Guide Securing SAS Web Applications with SiteMinder Audience Two application servers that SAS Web applications can run on are IBM WebSphere Application Server and Oracle WebLogic Server.
Configuration Guide Securing SAS Web Applications with SiteMinder Audience Two application servers that SAS Web applications can run on are IBM WebSphere Application Server and Oracle WebLogic Server.
Contents Introduction xxvi Chapter 1: Understanding the Threats: E-mail Viruses, Trojans, Mail Bombers, Worms, and Illicit Servers
 Contents Introduction xxvi Chapter 1: Understanding the Threats: E-mail Viruses, Trojans, Mail Bombers, Worms, and Illicit Servers 1 Introduction 2 Essential Concepts 3 Servers, Services, and Clients 3
Contents Introduction xxvi Chapter 1: Understanding the Threats: E-mail Viruses, Trojans, Mail Bombers, Worms, and Illicit Servers 1 Introduction 2 Essential Concepts 3 Servers, Services, and Clients 3
TIBCO ActiveMatrix Adapter for LDAP Configuration and Deployment. Software Release 6.0 August 2010
 TIBCO ActiveMatrix Adapter for LDAP Configuration and Deployment Software Release 6.0 August 2010 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED
TIBCO ActiveMatrix Adapter for LDAP Configuration and Deployment Software Release 6.0 August 2010 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED
Transport Layer Security Protocols
 SSL/TLS 1 Transport Layer Security Protocols Secure Socket Layer (SSL) Originally designed to by Netscape to secure HTTP Version 2 is being replaced by version 3 Subsequently became Internet Standard known
SSL/TLS 1 Transport Layer Security Protocols Secure Socket Layer (SSL) Originally designed to by Netscape to secure HTTP Version 2 is being replaced by version 3 Subsequently became Internet Standard known
Java Web Start. Brad Shuler Software Engineer Object Computing, Inc. St. Louis, MO
 Java Web Start Brad Shuler Software Engineer Object Computing, Inc. St. Louis, MO OCI Java Lunch, 30 Nov 2001 Overview Java Web Start (JWS) What is it? Demo How it works Deployment on Server Security Application
Java Web Start Brad Shuler Software Engineer Object Computing, Inc. St. Louis, MO OCI Java Lunch, 30 Nov 2001 Overview Java Web Start (JWS) What is it? Demo How it works Deployment on Server Security Application
Programming Flaws and How to Fix Them
 19 ö Programming Flaws and How to Fix Them MICHAEL HOWARD DAVID LEBLANC JOHN VIEGA McGraw-Hill /Osborne New York Chicago San Francisco Lisbon London Madrid Mexico City- Milan New Delhi San Juan Seoul Singapore
19 ö Programming Flaws and How to Fix Them MICHAEL HOWARD DAVID LEBLANC JOHN VIEGA McGraw-Hill /Osborne New York Chicago San Francisco Lisbon London Madrid Mexico City- Milan New Delhi San Juan Seoul Singapore
Single Sign-on (SSO) technologies for the Domino Web Server
 Single Sign-on (SSO) technologies for the Domino Web Server Jane Marcus December 7, 2011 2011 IBM Corporation Welcome Participant Passcode: 4297643 2011 IBM Corporation 2 Agenda USA Toll Free (866) 803-2145
Single Sign-on (SSO) technologies for the Domino Web Server Jane Marcus December 7, 2011 2011 IBM Corporation Welcome Participant Passcode: 4297643 2011 IBM Corporation 2 Agenda USA Toll Free (866) 803-2145
An Overview of Oracle Forms Server Architecture. An Oracle Technical White Paper April 2000
 An Oracle Technical White Paper INTRODUCTION This paper is designed to provide you with an overview of some of the key points of the Oracle Forms Server architecture and the processes involved when forms
An Oracle Technical White Paper INTRODUCTION This paper is designed to provide you with an overview of some of the key points of the Oracle Forms Server architecture and the processes involved when forms
PrivyLink Internet Application Security Environment *
 WHITE PAPER PrivyLink Internet Application Security Environment * The End-to-end Security Solution for Internet Applications September 2003 The potential business advantages of the Internet are immense.
WHITE PAPER PrivyLink Internet Application Security Environment * The End-to-end Security Solution for Internet Applications September 2003 The potential business advantages of the Internet are immense.
IBM Security Identity Manager Version 6.0. Security Guide SC14-7699-02
 IBM Security Identity Manager Version 6.0 Security Guide SC14-7699-02 IBM Security Identity Manager Version 6.0 Security Guide SC14-7699-02 Note Before using this information and the product it supports,
IBM Security Identity Manager Version 6.0 Security Guide SC14-7699-02 IBM Security Identity Manager Version 6.0 Security Guide SC14-7699-02 Note Before using this information and the product it supports,
Java Client Side Application Basics: Decompiling, Recompiling and Signing
 Java Client Side Application Basics: Decompiling, Recompiling and Signing Written By: Brad Antoniewicz [email protected] Introduction... 3 Java Web Start and JNLP... 3 Java Archives and META-INF...
Java Client Side Application Basics: Decompiling, Recompiling and Signing Written By: Brad Antoniewicz [email protected] Introduction... 3 Java Web Start and JNLP... 3 Java Archives and META-INF...
Java and Java Virtual Machine Security
 Java and Java Virtual Machine Security Vulnerabilities and their Exploitation Techniques by Last Stage of Delirium Research Group http://lsd-pl.net Version: 1.0.0 Updated: October 2nd, 2002 Copyright c
Java and Java Virtual Machine Security Vulnerabilities and their Exploitation Techniques by Last Stage of Delirium Research Group http://lsd-pl.net Version: 1.0.0 Updated: October 2nd, 2002 Copyright c
EUCIP - IT Administrator. Module 5 IT Security. Version 2.0
 EUCIP - IT Administrator Module 5 IT Security Version 2.0 Module 5 Goals Module 5 Module 5, IT Security, requires the candidate to be familiar with the various ways of protecting data both in a single
EUCIP - IT Administrator Module 5 IT Security Version 2.0 Module 5 Goals Module 5 Module 5, IT Security, requires the candidate to be familiar with the various ways of protecting data both in a single
WebSphere Server Administration Course
 WebSphere Server Administration Course Chapter 1. Java EE and WebSphere Overview Goals of Enterprise Applications What is Java? What is Java EE? The Java EE Specifications Role of Application Server What
WebSphere Server Administration Course Chapter 1. Java EE and WebSphere Overview Goals of Enterprise Applications What is Java? What is Java EE? The Java EE Specifications Role of Application Server What
IBM Unica emessage Version 8 Release 6 February 13, 2015. Startup and Administrator's Guide
 IBM Unica emessage Version 8 Release 6 February 13, 2015 Startup and Administrator's Guide Note Before using this information and the product it supports, read the information in Notices on page 83. This
IBM Unica emessage Version 8 Release 6 February 13, 2015 Startup and Administrator's Guide Note Before using this information and the product it supports, read the information in Notices on page 83. This
Using the Adobe Access Server for Protected Streaming
 Adobe Access April 2014 Version 4.0 Using the Adobe Access Server for Protected Streaming Copyright 2012-2014 Adobe Systems Incorporated. All rights reserved. This guide is protected under copyright law,
Adobe Access April 2014 Version 4.0 Using the Adobe Access Server for Protected Streaming Copyright 2012-2014 Adobe Systems Incorporated. All rights reserved. This guide is protected under copyright law,
Payment Client 3.2.0.0
 Payment Client 3.2.0.0 Deployment Guide Version 1.0 Disclaimer Copyright 2009 TNS Payment Technologies Pty Ltd ("TNS"). All rights reserved. This document is provided by TNS on the basis that you will
Payment Client 3.2.0.0 Deployment Guide Version 1.0 Disclaimer Copyright 2009 TNS Payment Technologies Pty Ltd ("TNS"). All rights reserved. This document is provided by TNS on the basis that you will
NetBeans IDE Field Guide
 NetBeans IDE Field Guide Copyright 2005 Sun Microsystems, Inc. All rights reserved. Table of Contents Introduction to J2EE Development in NetBeans IDE...1 Configuring the IDE for J2EE Development...2 Getting
NetBeans IDE Field Guide Copyright 2005 Sun Microsystems, Inc. All rights reserved. Table of Contents Introduction to J2EE Development in NetBeans IDE...1 Configuring the IDE for J2EE Development...2 Getting
Web Security (SSL) Tecniche di Sicurezza dei Sistemi 1
 Web Security (SSL) Tecniche di Sicurezza dei Sistemi 1 How the Web Works - HTTP Hypertext transfer protocol (http). Clients request documents (or scripts) through URL. Server response with documents. Documents
Web Security (SSL) Tecniche di Sicurezza dei Sistemi 1 How the Web Works - HTTP Hypertext transfer protocol (http). Clients request documents (or scripts) through URL. Server response with documents. Documents
As you learned about in Chapter 1, WebSphere Application Server V6 supports the
 23 J2EE Packaging, Enhanced EARs, and the Application Server Toolkit As you learned about in Chapter 1, WebSphere Application Server V6 supports the full Java 2 Platform, Enterprise Edition (J2EE) 1.4
23 J2EE Packaging, Enhanced EARs, and the Application Server Toolkit As you learned about in Chapter 1, WebSphere Application Server V6 supports the full Java 2 Platform, Enterprise Edition (J2EE) 1.4
TIBCO Runtime Agent Domain Utility User s Guide Software Release 5.8.0 November 2012
 TIBCO Runtime Agent Domain Utility User s Guide Software Release 5.8.0 November 2012 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED TIBCO
TIBCO Runtime Agent Domain Utility User s Guide Software Release 5.8.0 November 2012 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED TIBCO
JPMorgan Chase Treasury Workstation. Certification Setup Guide Version 2.0
 EMENTS JPMorgan Chase Treasury Workstation Certification Setup Guide Version 2.0 December 2010 TABLE OF CONTENTS Introduction... 1 About this Guide... 1 When to Create the Certificates... 2 Getting Help...
EMENTS JPMorgan Chase Treasury Workstation Certification Setup Guide Version 2.0 December 2010 TABLE OF CONTENTS Introduction... 1 About this Guide... 1 When to Create the Certificates... 2 Getting Help...
Enterprise Security Interests Require SSL with telnet server from outside the LAN
 Create and Use an SSL on Goals Provide secure and encrypted 5250 data stream conversations with the server (including authentication) use a digital certificate we create with Digital Manager Show a client
Create and Use an SSL on Goals Provide secure and encrypted 5250 data stream conversations with the server (including authentication) use a digital certificate we create with Digital Manager Show a client
Security Technical. Overview. BlackBerry Enterprise Service 10. BlackBerry Device Service Solution Version: 10.2
 BlackBerry Enterprise Service 10 BlackBerry Device Service Solution Version: 10.2 Security Technical Overview Published: 2014-09-10 SWD-20140908123239883 Contents 1 About BlackBerry Device Service solution
BlackBerry Enterprise Service 10 BlackBerry Device Service Solution Version: 10.2 Security Technical Overview Published: 2014-09-10 SWD-20140908123239883 Contents 1 About BlackBerry Device Service solution
Click Start > Control Panel > System icon to open System Properties dialog box. Click Advanced > Environment Variables.
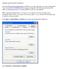 Configure Java environment on Windows After installing Java Development Kit on Windows, you may still need to do some configuration to get Java ready for compiling and executing Java programs. The following
Configure Java environment on Windows After installing Java Development Kit on Windows, you may still need to do some configuration to get Java ready for compiling and executing Java programs. The following
EMC Smarts Service Assurance Manager Dashboard Version 8.0. Configuration Guide P/N 300-007-748 REV A01
 EMC Smarts Service Assurance Manager Dashboard Version 8.0 Configuration Guide P/N 300-007-748 REV A01 EMC Corporation Corporate Headquarters: Hopkinton, MA 01748-9103 1-508-435-1000 www.emc.com Copyright
EMC Smarts Service Assurance Manager Dashboard Version 8.0 Configuration Guide P/N 300-007-748 REV A01 EMC Corporation Corporate Headquarters: Hopkinton, MA 01748-9103 1-508-435-1000 www.emc.com Copyright
Cornerstones of Security
 Internet Security Cornerstones of Security Authenticity the sender (either client or server) of a message is who he, she or it claims to be Privacy the contents of a message are secret and only known to
Internet Security Cornerstones of Security Authenticity the sender (either client or server) of a message is who he, she or it claims to be Privacy the contents of a message are secret and only known to
Implementing Secure Sockets Layer on iseries
 Implementing Secure Sockets Layer on iseries Presented by Barbara Brown Alliance Systems & Programming, Inc. Agenda SSL Concepts Digital Certificate Manager Local Certificate Authority Server Certificates
Implementing Secure Sockets Layer on iseries Presented by Barbara Brown Alliance Systems & Programming, Inc. Agenda SSL Concepts Digital Certificate Manager Local Certificate Authority Server Certificates
APPLETS AND NETWORK SECURITY: A MANAGEMENT OVERVIEW
 84-10-25 DATA SECURITY MANAGEMENT APPLETS AND NETWORK SECURITY: A MANAGEMENT OVERVIEW Al Berg INSIDE Applets and the Web, The Security Issue, Java: Secure Applets, Java: Holes and Bugs, Denial-of-Service
84-10-25 DATA SECURITY MANAGEMENT APPLETS AND NETWORK SECURITY: A MANAGEMENT OVERVIEW Al Berg INSIDE Applets and the Web, The Security Issue, Java: Secure Applets, Java: Holes and Bugs, Denial-of-Service
Scheduler Job Scheduling Console
 Tivoli IBM Tivoli Workload Scheduler Job Scheduling Console Feature Level 1.3 (Revised December 2004) User s Guide SC32-1257-02 Tivoli IBM Tivoli Workload Scheduler Job Scheduling Console Feature Level
Tivoli IBM Tivoli Workload Scheduler Job Scheduling Console Feature Level 1.3 (Revised December 2004) User s Guide SC32-1257-02 Tivoli IBM Tivoli Workload Scheduler Job Scheduling Console Feature Level
TN3270 Security Enhancements
 TN3270 Security Enhancements SecureWay Communication Server for OS/390 Copyright IBM Corporation, 1999 1 Support in OS/390 V2.R6 Copyright IBM Corporation, 1999 2 Secure Sockets Layer - What is it? Application
TN3270 Security Enhancements SecureWay Communication Server for OS/390 Copyright IBM Corporation, 1999 1 Support in OS/390 V2.R6 Copyright IBM Corporation, 1999 2 Secure Sockets Layer - What is it? Application
