Java Client Side Application Basics: Decompiling, Recompiling and Signing
|
|
|
- Leona McCarthy
- 8 years ago
- Views:
Transcription
1 Java Client Side Application Basics: Decompiling, Recompiling and Signing Written By: Brad Antoniewicz
2 Introduction... 3 Java Web Start and JNLP... 3 Java Archives and META-INF... 4 Getting Started... 4 JDK Quick Install... 5 Downloading and Extracting... 5 Dealing with Signed JARs... 6 Decompiling... 7 Recompiling and Re-JARing... 7 Signing the JAR... 8 Making it work... 9 Enabling Verbose logging within Java... 9 Conclusion More Information... 11
3 Introduction One of the major rules of security is Never trust client side security. Somehow this rule is often forgotten, especially when companies deploy client side Java applications. They can try their best to obfuscate every part of code, but in the end, its all run on the client side, which means the user has the ability to control everything. This brief document will teach you the first steps of picking apart the contents of a client side Java application, and hopefully lead you on your way to some great findings. Java Web Start and JNLP Java Web Start is a mechanism for program delivery through a web server. These programs are initiated by the client s web browser, deployed, and ultimately executed independently on the system. Since they run outside of the browser, security may appear to be an initial concern, however the application runs within a restricted container (called a sandbox), which sits atop of the Java 2 platform s security architecture. This provides a couple nice layers of security between the application and the local machine. The Java Network Launch Protocol (JNLP) is an XML-based technology for launching Java executables. The.JNLP file is basically the Table of Contents for the Java application; most importantly, for our use, it defines the location of application resources. This file is what we re usually directed to when accessing a Java Web Start application. Example JNLP: java_app.jnlp <?xml version="1.0" encoding="utf-8"?> <jnlp codebase=" href="java_app.jnlp"> <information> <title>super ClientSide APP v1.0</title> <vendor>not Real INC</vendor> <icon kind="splash" href="logo.jpg" width="200" height="60"/> </information> <security> <all-permissions/> </security> <resources> <!-- Requires J2SE or higher --> <j2se version="1.4.2*" href=" <j2se version="1.5+"/> <jar href="inc/app-core.jar"/> <jar href="inc/app-gui.jar"/> <!-- Properties --> <property name="banner.colour" value="black"/> <property name="module.1.name" value="model"/> <property name="module.1.class" value="com.fakecompany.model"/>
4 <!-- Disable DNS caching to allow Wide IP failover/load balancing --> <property name="networkaddress.cache.ttl" value="0"/> </resources> <application-desc main-class="com.fakecompany"/> </jnlp> Java Archives and META-INF A Java Archive (JAR) is a file format based on the popular ZIP file format. In its most basic form, it is a compressed archive containing all of the Java class files (which we will decompile) of the application. It also contains one very important directory: META-INF. At a minimum, this directory contains the MANIFEST.MF. The JAR s manifest contains package and extension related data. An important thing to remember is that when the JAR is signed, MANIFEST.MF will also contains SHA1 hashes of every file within itself. This means if we ever want to modify a class within the archive and maintain valid signatures, we ll have to completely recompile the JAR and resign it rather than just updating it. Also inside the META-INF folder of signed archives is a signature file (.SF) and its corresponding block file (.DSA). When we recompile our JAR, we ll remove the META-INF folder entirely so that there is little to no trace of the initial company who signed it. Getting Started Since the JNLP is simply a XML file, we can download this file to get a list of all the JARs which comprise the application. Using the above java_app.jnlp example, we can see that this application is comprised of two JARs: app-core.jar and app-gui.jar. These two files will be extracted, and their contents decompiled so that we can further understand the way they work. Two important things we ll need to install to accomplish our mission will be the Java Development Kit (JDK), and the Java Decompiler (JAD). They can be found using the below links: JDK JAD Installation for both is relatively simple. Follow their instructions and it should be a snap. These can both be set up on Windows, but it is highly recommended to do this on a Linux box somewhere. Depending on the way application was written, it is possible to have multiple classes within the JAR whose filenames are case sensitive. For example, take a look at these two filenames: aa.class and Aa.class. Since Windows does not consider case in the filenames, it will overwrite aa.class with Aa.class, which can completely destroy our application. Linux, however does take the case of filenames into consideration, so that is why it is heavily recommended. All commands given below will be specifically for use under Linux; however it is possible they may work on Windows as well.
5 JDK Quick Install Once you have downloaded the JDK, installation is relatively painless. Follow the below installation procedure. We ve snipped the majority of the output, but most of it is not really important anyway. Nonetheless this should give you enough information. Installing the Java Development Kit Sun Microsystems, Inc. Binary Code License Agreement for the JAVA 2 PLATFORM STANDARD EDITION DEVELOPMENT KIT 5.0 SUN MICROSYSTEMS, INC. ("SUN") IS WILLING TO LICENSE THE SOFTWARE IDENTIFIED BELOW TO YOU ONLY UPON THE CONDITION SNIPED --. Creating jdk1.5.0_10/jre/lib/charsets.jar Creating jdk1.5.0_10/jre/lib/ext/localedata.jar Creating jdk1.5.0_10/jre/lib/plugin.jar Creating jdk1.5.0_10/jre/lib/javaws.jar Creating jdk1.5.0_10/jre/lib/deploy.jar Done. root@jdkdemo:/home/user# mv jdk1.5.0_10/ /usr/local root@jdkdemo:/usr/local# cd /usr/local root@jdkdemo:/usr/local# ln -s jdk1.5.0_10/ jdk root@jdkdemo:/usr/local# export PATH=$PATH:/usr/local/jdk/bin Downloading and Extracting We ve identified which JARs make up the application using the JNLP file, and now we ll need to download and extract them. Following our example, we ll execute the following commands to download our JARs: Downloading the JARs root@jdkdemo:/home/user# wget root@jdkdemo:/home/user# wget
6 Now you ll have the two JARs in your current directory, and they ll need to be extracted. Extracting the JARs mkdir app-gui cp app-gui.jar app-gui cd app-gui jar xf app-gui.jar rm app-gui.jar cd.. mkdir app-core cp app-core.jar app-core cd app-core jar xf app-core.jar rm app-core.jar cd.. Obviously, the only command that needs to be executed is the jar xf jarfile.jar, but I added all the extra commands so we can have a nice neat directory structure. Dealing with Signed JARs Now we ll need to determine if our JARs are signed or not. We can do that in one of two ways. The easiest way at this point is to just check within the decompiled JAR and see if there is a.sf in the META-INF directory. If there is, then the JAR is signed, and we ll need to resign. Alternately you can do the following: Identify if the JAR was signed root@jdkdemo:/home/user/app-gui# jarsigner verbose certs verify app-gui.jar root@jdkdemo:/home/user/app-core# jarsigner verbose certs verify app-core.jar This will give you a good amount of information if the JAR is actually signed. If it does not, then most likely the JAR is not signed and it will state that clearly near the bottom of the command output. As mentioned above, it is important to determine if the JAR was signed because with a signed JAR, the MANIFEST.MF will contain a SHA1 digest of each file within itself. If we update a particular file, the digest will not match the one in the MANIFEST.MF, and the application may fail to run (again, this is only if the JAR was signed). Also if we recompile and re-sign any one particular JAR, we are required to recompile and resign every other JAR that is specified within the same JNLP. Finally, it is not uncommon for the Java application to require complete access to the local system through the <all-permissions> security directive. If this directive is set, the JAR must be signed.
7 Decompiling Now that we have extracted the JAR and identified if it has been signed, our next step is to decompile whichever classe(s) we d like to investigate. This is where JAD comes in. JAD s usage is very simple and straightforward. You can decompile everything within a certain directory, source tree, or an individual file. JAD does not decompile JAR files directly so you need to extract the JAR first as detailed above. We would recommend dissecting everything for your investigation. Later on, if you plan on modifying something specifically, re-extract the JAR and only decompile that particular class as it makes things less complicated with the recompile. You can also avoid these complications by decompiling to completely different directory. Decompiling Individual files root@jdkdemo:/home/user/app-gui/classes# jad classfile.class Decompiling All files within Directory root@jdkdemo:/home/user/app-gui/classes# jad *.class Decompile all class files within a source tree to a different directory, renaming them to.java files root@jdkdemo:/home/user/app-gui/classes# jad r sjava d/home/user/app-gui/src /home/user/appgui/classes/*.class By default JAD will output a.jad file for the source code that can be read or modified. JAD can also decompile directly to.java files by using the s option. The destination for source files can be set with d, and the package directory structure is restored with r. Other JAD options can be displayed by calling jad with no arguments. The application s source is now available for you to dissect and investigate. If there is a particular function that is getting in your way by making some obscure check, why not take it out! The power is yours! It may be a good idea to make a minor change in the logging portion of the application, and you can verify that it s working through the Java logging console. One quick note, if you re making any changes, remove the original.class and leave the.java in the same directory. If you decompiled to a different directory, after you modify it, copy the.java over to the compile directory when ready to recompile. It will make the recompile process smoother. Recompiling and Re-JARing The task of recompiling is nearly as simple as that of decompiling; however we ll need to make an important change: removing the META-INF. As mentioned above, the META-INF directory contains a couple
8 goodies that are particular to the JAR. Since we re recompiling the entire archive, we can take it out, as it will be added automatically when we recompile. Here are our steps for recompiling and rejaring. We took a hypothetical file, classfile.java (was decompiled with JAD) within the gui/ and core/ directories, respectively. Recompiling and rejaring root@jdkdemo:/home/user# cd app-gui/ root@jdkdemo:/home/user/app-gui# rm classes/classfile.class root@jdkdemo:/home/user/app-gui# javac cp. classes/classfile.java root@jdkdemo:/home/user/app-gui# rm rf META-INF root@jdkdemo:/home/user/app-gui# jar cvf app-gui.jar. root@jdkdemo:/home/user/app-gui# cd../app-core/ root@jdkdemo:/home/user/app-core# rm classes/classfile.class root@jdkdemo:/home/user/app-core# javac cp. clasees/classfile.java root@jdkdemo:/home/user/app-core# rm rf META-INF root@jdkdemo:/home/user/app-core# jar cvf app-gui.jar We removed the preexisting class files as a matter of organization, and so we can verify they were created after the recompiling process. Great! So now we modified our class, recompiled it, and re-jared it. Depending on how the application was initially set up, you could be done! Just give it a run and see if it worked out! However, it s more likely that it was signed, so let s get to the annoying part. Signing the JAR IF YOUR JAD WAS NOT SIGNED TO BEGIN WITH THIS STEP MAY BE SKIPPED! This is the most annoying part of the whole process. Since we obviously cannot resign the JAR using with the originally owners key, we ll have to make our own and then sign it ourselves. The first thing we ll have to do is make a keystore using keytool: Creating a Keystore And Public/Private Key Pair keytool -genkey -keystore mykeystore -alias myalias Enter keystore password: <password> What is your first and last name? What is the name of your organizational unit? What is the name of your organization? What is the name of your City or Locality? What is the name of your State or Province?
9 What is the two-letter country code for this unit? Is CN=Unknown, OU=Unknown, O=Unknown, L=Unknown, ST=Unknown, C=Unknown correct? [no]: yes Enter key password for <myalias> (RETURN if same as keystore password):[press Enter button] Your keystore has now been created. Look for the file mykeystore in your current directory. Now we can sign the JAR (assuming mykeystore is in the same directory you started in)! Sign the JAR cd app-core/ jarsigner -keystore../mykeystore -storepass <password> app-core.jar myalias cd../app-gui jarsigner -keystore../mykeystore -storepass <password> app-gui.jar myalias Just verify using the jarsigner tool mentioned above and you re ready to put it all into action. Making it work You can go back to your Windows box and do some basic tests to figure out where the application is saving itself once it downloads to your machine. You can use Filemon ( or just simply search for the.jar on your machine (usually in c:\documents and settings\<user>\application data\ ). Once you figure this out, simply replace those with your repacked and resigned JARs. Double click the JNLP to launch the application, and hopefully your modification will work! You may see a Java warning message complaining that the application is signed by an unknown authority, but you can safely ignore that, as you re that unknown authority! Enabling Verbose logging within Java If you made the recommended logging change in the application or you re just curious to investigate the logs of the application, you can make Java display more verbose logging within the Java Control Panel. Enabling Java Logging Within the Windows Control Panel, click the Java icon to display the
10 following window. Navigate to the Advanced Tab Expand the Trees under Debugging and Java Console. Under Debugging, mark the Enable Tracing, Enable Logging, and Show applet lifecycle exceptions checkboxes. Under Java console mark the Show console radio button. Hit OK
11 Conclusion Excellent job! You have successfully decompiled your JAR, figured out how to recompile it, and learned how to resign it if necessary. Now it s up to you to closely analyze the application and figure out what you can to with the decompiled JAR to identify vulnerabilities in the application. The important thing to remember here is that because this is client side, all the power is now in your hands. For example, if the application waits for a server response to validate authentication, try to change that check to automatically return true. This way you can see the application functionality without actually logging in. That s just one very simple idea - go ahead, play around, and most importantly, HAVE FUN! More Information If you re new to Java or would like to get more oriented with Java development, check out the following links: The Java Tutorials OWASP Guide - General Web Application Testing Java Programming Resources Learn More For additional information about Foundstone consulting, please contact your local sales representative: Phone: FOUND Consulting@foundstone.com
Entrust Certificate Services. Java Code Signing. User Guide. Date of Issue: December 2014. Document issue: 2.0
 Entrust Certificate Services Java Code Signing User Guide Date of Issue: December 2014 Document issue: 2.0 Copyright 2009-2014 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Entrust Certificate Services Java Code Signing User Guide Date of Issue: December 2014 Document issue: 2.0 Copyright 2009-2014 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Quick and Easy Solutions With Free Java Libraries Part II
 A Quick and Easy Solutions With Free Java Libraries Part II By Shaun Haney s mentioned in Part I of "Quick and Easy Solutions With Free Java Libraries," BBj allows developers to integrate Java objects
A Quick and Easy Solutions With Free Java Libraries Part II By Shaun Haney s mentioned in Part I of "Quick and Easy Solutions With Free Java Libraries," BBj allows developers to integrate Java objects
Configuring the BBj Jetty Web Server (rev10.02) for OSAS
 Introduction: Through the relative short history of Open Systems use with the BBJ interpreter there have been many ways to configure client connections. The most common has been the typical Thin Client
Introduction: Through the relative short history of Open Systems use with the BBJ interpreter there have been many ways to configure client connections. The most common has been the typical Thin Client
Java Language Tools COPYRIGHTED MATERIAL. Part 1. In this part...
 Part 1 Java Language Tools This beginning, ground-level part presents reference information for setting up the Java development environment and for compiling and running Java programs. This includes downloading
Part 1 Java Language Tools This beginning, ground-level part presents reference information for setting up the Java development environment and for compiling and running Java programs. This includes downloading
Click Start > Control Panel > System icon to open System Properties dialog box. Click Advanced > Environment Variables.
 Configure Java environment on Windows After installing Java Development Kit on Windows, you may still need to do some configuration to get Java ready for compiling and executing Java programs. The following
Configure Java environment on Windows After installing Java Development Kit on Windows, you may still need to do some configuration to get Java ready for compiling and executing Java programs. The following
Cisco Prime Central Managing Certificates
 Cisco Prime Central Managing Certificates Version 1.0.5 September, 2015 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000
Cisco Prime Central Managing Certificates Version 1.0.5 September, 2015 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000
JAVA WEB START OVERVIEW
 JAVA WEB START OVERVIEW White Paper May 2005 Sun Microsystems, Inc. Table of Contents Table of Contents 1 Introduction................................................................. 1 2 A Java Web Start
JAVA WEB START OVERVIEW White Paper May 2005 Sun Microsystems, Inc. Table of Contents Table of Contents 1 Introduction................................................................. 1 2 A Java Web Start
Deploying a Logi Info Application on WAS
 Deploying a Logi Info Application on WAS Updated 30 April 2015 These instructions apply to WAS 7.x and WAS 8.x, for use with Logi Info and JDK 1.6 or 7.x. WAS versions earlier than 7.0 cannot be used with
Deploying a Logi Info Application on WAS Updated 30 April 2015 These instructions apply to WAS 7.x and WAS 8.x, for use with Logi Info and JDK 1.6 or 7.x. WAS versions earlier than 7.0 cannot be used with
RHEV 2.2: REST API INSTALLATION
 RHEV 2.2: REST API INSTALLATION BY JAMES RANKIN REVISED 02/14/11 RHEV 2.2: REST API INSTALLATION 1 TABLE OF CONTENTS OVERVIEW PAGE 3 JAVA AND ENVIRONMENT VARIABLES PAGE 3 JBOSS INSTALLATION PAGE 5 REST
RHEV 2.2: REST API INSTALLATION BY JAMES RANKIN REVISED 02/14/11 RHEV 2.2: REST API INSTALLATION 1 TABLE OF CONTENTS OVERVIEW PAGE 3 JAVA AND ENVIRONMENT VARIABLES PAGE 3 JBOSS INSTALLATION PAGE 5 REST
Hadoop Tutorial. General Instructions
 CS246: Mining Massive Datasets Winter 2016 Hadoop Tutorial Due 11:59pm January 12, 2016 General Instructions The purpose of this tutorial is (1) to get you started with Hadoop and (2) to get you acquainted
CS246: Mining Massive Datasets Winter 2016 Hadoop Tutorial Due 11:59pm January 12, 2016 General Instructions The purpose of this tutorial is (1) to get you started with Hadoop and (2) to get you acquainted
How to FTP (How to upload files on a web-server)
 How to FTP (How to upload files on a web-server) In order for a website to be visible to the world, it s files (text files,.html files, image files, etc.) have to be uploaded to a web server. A web server
How to FTP (How to upload files on a web-server) In order for a website to be visible to the world, it s files (text files,.html files, image files, etc.) have to be uploaded to a web server. A web server
Windows Intune Walkthrough: Windows Phone 8 Management
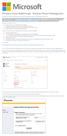 Windows Intune Walkthrough: Windows Phone 8 Management This document will review all the necessary steps to setup and manage Windows Phone 8 using the Windows Intune service. Note: If you want to test
Windows Intune Walkthrough: Windows Phone 8 Management This document will review all the necessary steps to setup and manage Windows Phone 8 using the Windows Intune service. Note: If you want to test
FlexSim LAN License Server
 FlexSim LAN License Server Installation Instructions Rev. 20150318 Table of Contents Introduction... 2 Using lmtools... 2 1. Download the installation files... 3 2. Install the license server... 4 3. Connecting
FlexSim LAN License Server Installation Instructions Rev. 20150318 Table of Contents Introduction... 2 Using lmtools... 2 1. Download the installation files... 3 2. Install the license server... 4 3. Connecting
Online Backup Client User Manual
 Online Backup Client User Manual Software version 3.21 For Linux distributions January 2011 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have
Online Backup Client User Manual Software version 3.21 For Linux distributions January 2011 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have
Packaging and Deploying Java Projects in Forte
 CHAPTER 8 Packaging and Deploying Java Projects in Forte This chapter introduces to use Forte s Archive wizard to package project files for deployment. You will also learn how to create shortcut for applications
CHAPTER 8 Packaging and Deploying Java Projects in Forte This chapter introduces to use Forte s Archive wizard to package project files for deployment. You will also learn how to create shortcut for applications
Reflection DBR USER GUIDE. Reflection DBR User Guide. 995 Old Eagle School Road Suite 315 Wayne, PA 19087 USA 610.964.8000 www.evolveip.
 Reflection DBR USER GUIDE 995 Old Eagle School Road Suite 315 Wayne, PA 19087 USA 610.964.8000 www.evolveip.net Page 1 of 1 Table of Contents Overview 3 Reflection DBR Client and Console Installation 4
Reflection DBR USER GUIDE 995 Old Eagle School Road Suite 315 Wayne, PA 19087 USA 610.964.8000 www.evolveip.net Page 1 of 1 Table of Contents Overview 3 Reflection DBR Client and Console Installation 4
A Practical Guide to creating, compiling and signing an Android Application using Processing for Android.
 A Practical Guide to creating, compiling and signing an Android Application using Processing for Android. By Joseph Alexander Boston http://www.jaboston.com IMPORTANT NOTE: EVERYTHING YOU INSTALL SHOULD
A Practical Guide to creating, compiling and signing an Android Application using Processing for Android. By Joseph Alexander Boston http://www.jaboston.com IMPORTANT NOTE: EVERYTHING YOU INSTALL SHOULD
IDS 561 Big data analytics Assignment 1
 IDS 561 Big data analytics Assignment 1 Due Midnight, October 4th, 2015 General Instructions The purpose of this tutorial is (1) to get you started with Hadoop and (2) to get you acquainted with the code
IDS 561 Big data analytics Assignment 1 Due Midnight, October 4th, 2015 General Instructions The purpose of this tutorial is (1) to get you started with Hadoop and (2) to get you acquainted with the code
Configuring HTTPS support. Overview. Certificates
 Configuring HTTPS support Overview Destiny provides the option to configure secure access when password information is transmitted between the client browser and the server. Destiny can switch from HTTP
Configuring HTTPS support Overview Destiny provides the option to configure secure access when password information is transmitted between the client browser and the server. Destiny can switch from HTTP
SafeNet KMIP and Amazon S3 Integration Guide
 SafeNet KMIP and Amazon S3 Integration Guide Documentation Version: 20130524 2013 SafeNet, Inc. All rights reserved Preface All intellectual property is protected by copyright. All trademarks and product
SafeNet KMIP and Amazon S3 Integration Guide Documentation Version: 20130524 2013 SafeNet, Inc. All rights reserved Preface All intellectual property is protected by copyright. All trademarks and product
RecoveryVault Express Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
WA2262 Applied Data Science and Big Data Analytics Boot Camp for Business Analysts. Classroom Setup Guide. Web Age Solutions Inc.
 WA2262 Applied Data Science and Big Data Analytics Boot Camp for Business Analysts Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Software
WA2262 Applied Data Science and Big Data Analytics Boot Camp for Business Analysts Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Software
Configuring Secure Socket Layer (SSL) for use with BPM 7.5.x
 Configuring Secure Socket Layer (SSL) for use with BPM 7.5.x Configuring Secure Socket Layer (SSL) communication for a standalone environment... 2 Import the Process Server WAS root SSL certificate into
Configuring Secure Socket Layer (SSL) for use with BPM 7.5.x Configuring Secure Socket Layer (SSL) communication for a standalone environment... 2 Import the Process Server WAS root SSL certificate into
1. Product Information
 ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
Team Foundation Server 2013 Installation Guide
 Team Foundation Server 2013 Installation Guide Page 1 of 164 Team Foundation Server 2013 Installation Guide Benjamin Day benday@benday.com v1.1.0 May 28, 2014 Team Foundation Server 2013 Installation Guide
Team Foundation Server 2013 Installation Guide Page 1 of 164 Team Foundation Server 2013 Installation Guide Benjamin Day benday@benday.com v1.1.0 May 28, 2014 Team Foundation Server 2013 Installation Guide
Online Backup Client User Manual Linux
 Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Online Backup Linux Client User Manual
 Online Backup Linux Client User Manual Software version 4.0.x For Linux distributions August 2011 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might
Online Backup Linux Client User Manual Software version 4.0.x For Linux distributions August 2011 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might
How To Restore Your Data On A Backup By Mozy (Windows) On A Pc Or Macbook Or Macintosh (Windows 2) On Your Computer Or Mac) On An Pc Or Ipad (Windows 3) On Pc Or Pc Or Micro
 Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Online Backup Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
Accessing PostgreSQL through JDBC via a Java SSL tunnel
 LinuxFocus article number 285 http://linuxfocus.org Accessing PostgreSQL through JDBC via a Java SSL tunnel by Chianglin Ng About the author: I live in Singapore, a modern multiracial
LinuxFocus article number 285 http://linuxfocus.org Accessing PostgreSQL through JDBC via a Java SSL tunnel by Chianglin Ng About the author: I live in Singapore, a modern multiracial
educ Office 365 email: Remove & create new Outlook profile
 Published: 29/01/2015 If you have previously used Outlook the with the SCC/SWO service then once you have been moved into Office 365 your Outlook will need to contact the SCC/SWO servers one last time
Published: 29/01/2015 If you have previously used Outlook the with the SCC/SWO service then once you have been moved into Office 365 your Outlook will need to contact the SCC/SWO servers one last time
USING STUFFIT DELUXE THE STUFFIT START PAGE CREATING ARCHIVES (COMPRESSED FILES)
 USING STUFFIT DELUXE StuffIt Deluxe provides many ways for you to create zipped file or archives. The benefit of using the New Archive Wizard is that it provides a way to access some of the more powerful
USING STUFFIT DELUXE StuffIt Deluxe provides many ways for you to create zipped file or archives. The benefit of using the New Archive Wizard is that it provides a way to access some of the more powerful
AlienVault Unified Security Management (USM) 4.x-5.x. Deploying HIDS Agents to Linux Hosts
 AlienVault Unified Security Management (USM) 4.x-5.x Deploying HIDS Agents to Linux Hosts USM 4.x-5.x Deploying HIDS Agents to Linux Hosts, rev. 2 Copyright 2015 AlienVault, Inc. All rights reserved. AlienVault,
AlienVault Unified Security Management (USM) 4.x-5.x Deploying HIDS Agents to Linux Hosts USM 4.x-5.x Deploying HIDS Agents to Linux Hosts, rev. 2 Copyright 2015 AlienVault, Inc. All rights reserved. AlienVault,
AES Crypt User Guide
 AES Crypt User Guide Publication Date: 2013-12-26 Original Author: Gary C. Kessler (gck@garykessler.net) Revision History Date Contributor Changes 2012-01-17 Gary C. Kessler First version 2013-03-03 Doug
AES Crypt User Guide Publication Date: 2013-12-26 Original Author: Gary C. Kessler (gck@garykessler.net) Revision History Date Contributor Changes 2012-01-17 Gary C. Kessler First version 2013-03-03 Doug
EVALUATION ONLY. WA2088 WebSphere Application Server 8.5 Administration on Windows. Student Labs. Web Age Solutions Inc.
 WA2088 WebSphere Application Server 8.5 Administration on Windows Student Labs Web Age Solutions Inc. Copyright 2013 Web Age Solutions Inc. 1 Table of Contents Directory Paths Used in Labs...3 Lab Notes...4
WA2088 WebSphere Application Server 8.5 Administration on Windows Student Labs Web Age Solutions Inc. Copyright 2013 Web Age Solutions Inc. 1 Table of Contents Directory Paths Used in Labs...3 Lab Notes...4
Recommended File System Ownership and Privileges
 FOR MAGENTO COMMUNITY EDITION Whenever a patch is released to fix an issue in the code, a notice is sent directly to your Admin Inbox. If the update is security related, the incoming message is colorcoded
FOR MAGENTO COMMUNITY EDITION Whenever a patch is released to fix an issue in the code, a notice is sent directly to your Admin Inbox. If the update is security related, the incoming message is colorcoded
CHAPTER 7 SSL CONFIGURATION AND TESTING
 CHAPTER 7 SSL CONFIGURATION AND TESTING 7.1 Configuration and Testing of SSL Nowadays, it s very big challenge to handle the enterprise applications as they are much complex and it is a very sensitive
CHAPTER 7 SSL CONFIGURATION AND TESTING 7.1 Configuration and Testing of SSL Nowadays, it s very big challenge to handle the enterprise applications as they are much complex and it is a very sensitive
Exchange Reporter Plus SSL Configuration Guide
 Exchange Reporter Plus SSL Configuration Guide Table of contents Necessity of a SSL guide 3 Exchange Reporter Plus Overview 3 Why is SSL certification needed? 3 Steps for enabling SSL 4 Certificate Request
Exchange Reporter Plus SSL Configuration Guide Table of contents Necessity of a SSL guide 3 Exchange Reporter Plus Overview 3 Why is SSL certification needed? 3 Steps for enabling SSL 4 Certificate Request
Installing Java. Table of contents
 Table of contents 1 Jargon...3 2 Introduction...4 3 How to install the JDK...4 3.1 Microsoft Windows 95... 4 3.1.1 Installing the JDK... 4 3.1.2 Setting the Path Variable...5 3.2 Microsoft Windows 98...
Table of contents 1 Jargon...3 2 Introduction...4 3 How to install the JDK...4 3.1 Microsoft Windows 95... 4 3.1.1 Installing the JDK... 4 3.1.2 Setting the Path Variable...5 3.2 Microsoft Windows 98...
Security in Android apps
 Security in Android apps Falco Peijnenburg (3749002) August 16, 2013 Abstract Apps can be released on the Google Play store through the Google Developer Console. The Google Play store only allows apps
Security in Android apps Falco Peijnenburg (3749002) August 16, 2013 Abstract Apps can be released on the Google Play store through the Google Developer Console. The Google Play store only allows apps
National Fire Incident Reporting System (NFIRS 5.0) Configuration Tool User's Guide
 National Fire Incident Reporting System (NFIRS 5.0) Configuration Tool User's Guide NFIRS 5.0 Software Version 5.6 1/7/2009 Department of Homeland Security Federal Emergency Management Agency United States
National Fire Incident Reporting System (NFIRS 5.0) Configuration Tool User's Guide NFIRS 5.0 Software Version 5.6 1/7/2009 Department of Homeland Security Federal Emergency Management Agency United States
SQL Server Setup for Assistant/Pro applications Compliance Information Systems
 SQL Server Setup for Assistant/Pro applications Compliance Information Systems The following document covers the process of setting up the SQL Server databases for the Assistant/PRO software products form
SQL Server Setup for Assistant/Pro applications Compliance Information Systems The following document covers the process of setting up the SQL Server databases for the Assistant/PRO software products form
Enabling SSL and Client Certificates on the SAP J2EE Engine
 Enabling SSL and Client Certificates on the SAP J2EE Engine Angel Dichev RIG, SAP Labs SAP AG 1 Learning Objectives As a result of this session, you will be able to: Understand the different SAP J2EE Engine
Enabling SSL and Client Certificates on the SAP J2EE Engine Angel Dichev RIG, SAP Labs SAP AG 1 Learning Objectives As a result of this session, you will be able to: Understand the different SAP J2EE Engine
Tutorial 5: Developing Java applications
 Tutorial 5: Developing Java applications p. 1 Tutorial 5: Developing Java applications Georgios Gousios gousiosg@aueb.gr Department of Management Science and Technology Athens University of Economics and
Tutorial 5: Developing Java applications p. 1 Tutorial 5: Developing Java applications Georgios Gousios gousiosg@aueb.gr Department of Management Science and Technology Athens University of Economics and
1. If there is a temporary SSL certificate in your /ServerRoot/ssl/certs/ directory, move or delete it. 2. Run the following command:
 C2Net Stronghold Cisco Adaptive Security Appliance (ASA) 5500 Cobalt RaQ4/XTR F5 BIG IP (version 9) F5 BIG IP (pre-version 9) F5 FirePass VPS HSphere Web Server IBM HTTP Server Java-based web server (generic)
C2Net Stronghold Cisco Adaptive Security Appliance (ASA) 5500 Cobalt RaQ4/XTR F5 BIG IP (version 9) F5 BIG IP (pre-version 9) F5 FirePass VPS HSphere Web Server IBM HTTP Server Java-based web server (generic)
SafeNet KMIP and Google Cloud Storage Integration Guide
 SafeNet KMIP and Google Cloud Storage Integration Guide Documentation Version: 20130719 Table of Contents CHAPTER 1 GOOGLE CLOUD STORAGE................................. 2 Introduction...............................................................
SafeNet KMIP and Google Cloud Storage Integration Guide Documentation Version: 20130719 Table of Contents CHAPTER 1 GOOGLE CLOUD STORAGE................................. 2 Introduction...............................................................
Oracle Universal Content Management 10.1.3
 Date: 2007/04/16-10.1.3 Oracle Universal Content Management 10.1.3 Document Management Quick Start Tutorial Oracle Universal Content Management 10.1.3 Document Management Quick Start Guide Page 1 Contents
Date: 2007/04/16-10.1.3 Oracle Universal Content Management 10.1.3 Document Management Quick Start Tutorial Oracle Universal Content Management 10.1.3 Document Management Quick Start Guide Page 1 Contents
http://www.apple.com/downloads/macosx/internet_utilities/mozillafirefox.html
 Using Citrix SPSS on a Mac Accessing and using the SPSS software on a Mac computer is a fairly straightforward process, but there are few little glitches that seem to come up again and again. The following
Using Citrix SPSS on a Mac Accessing and using the SPSS software on a Mac computer is a fairly straightforward process, but there are few little glitches that seem to come up again and again. The following
Developers Integration Lab (DIL) Certificate Installation Instructions. Version 1.4
 Developers Integration Lab (DIL) Certificate Installation Instructions Version 1.4 July 22, 2013 REVISION HISTORY REVISION DATE DESCRIPTION 0.1 17 September 2011 First Draft Release DIL Certificate Installation
Developers Integration Lab (DIL) Certificate Installation Instructions Version 1.4 July 22, 2013 REVISION HISTORY REVISION DATE DESCRIPTION 0.1 17 September 2011 First Draft Release DIL Certificate Installation
Deploying Intellicus Portal on IBM WebSphere
 Deploying Intellicus Portal on IBM WebSphere Intellicus Web-based Reporting Suite Version 4.5 Enterprise Professional Smart Developer Smart Viewer Intellicus Technologies info@intellicus.com www.intellicus.com
Deploying Intellicus Portal on IBM WebSphere Intellicus Web-based Reporting Suite Version 4.5 Enterprise Professional Smart Developer Smart Viewer Intellicus Technologies info@intellicus.com www.intellicus.com
EVault Software. Course 361 Protecting Linux and UNIX with EVault
 EVault Software Course 361 Protecting Linux and UNIX with EVault Table of Contents Objectives... 3 Scenario... 3 Estimated Time to Complete This Lab... 3 Requirements for This Lab... 3 Computers Used in
EVault Software Course 361 Protecting Linux and UNIX with EVault Table of Contents Objectives... 3 Scenario... 3 Estimated Time to Complete This Lab... 3 Requirements for This Lab... 3 Computers Used in
Installing Digital Certificates for Server Authentication SSL on. BEA WebLogic 8.1
 Installing Digital Certificates for Server Authentication SSL on BEA WebLogic 8.1 Installing Digital Certificates for Server Authentication SSL You use utilities provided with the BEA WebLogic server software
Installing Digital Certificates for Server Authentication SSL on BEA WebLogic 8.1 Installing Digital Certificates for Server Authentication SSL You use utilities provided with the BEA WebLogic server software
JAMF Software Server Installation Guide for Linux. Version 8.6
 JAMF Software Server Installation Guide for Linux Version 8.6 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate.
JAMF Software Server Installation Guide for Linux Version 8.6 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate.
Oracle Managed File Getting Started - Transfer FTP Server to File Table of Contents
 Oracle Managed File Getting Started - Transfer FTP Server to File Table of Contents Goals... 3 High- Level Steps... 4 Basic FTP to File with Compression... 4 Steps in Detail... 4 MFT Console: Login and
Oracle Managed File Getting Started - Transfer FTP Server to File Table of Contents Goals... 3 High- Level Steps... 4 Basic FTP to File with Compression... 4 Steps in Detail... 4 MFT Console: Login and
An Oracle White Paper March 2011. Integrating the SharePoint 2007 Adapter with WebCenter Spaces (11.1.1.3.0 & 11.1.1.4.0)
 An Oracle White Paper March 2011 Integrating the SharePoint 2007 Adapter with WebCenter Spaces (11.1.1.3.0 & 11.1.1.4.0) Table of Contents Introduction... 2 Overview... 2 Adding WebCenter Adapter for
An Oracle White Paper March 2011 Integrating the SharePoint 2007 Adapter with WebCenter Spaces (11.1.1.3.0 & 11.1.1.4.0) Table of Contents Introduction... 2 Overview... 2 Adding WebCenter Adapter for
EMC Documentum Composer
 EMC Documentum Composer Version 6.5 User Guide P/N 300 007 217 A02 EMC Corporation Corporate Headquarters: Hopkinton, MA 01748 9103 1 508 435 1000 www.emc.com Copyright 2008 EMC Corporation. All rights
EMC Documentum Composer Version 6.5 User Guide P/N 300 007 217 A02 EMC Corporation Corporate Headquarters: Hopkinton, MA 01748 9103 1 508 435 1000 www.emc.com Copyright 2008 EMC Corporation. All rights
How to connect to the University of Exeter VPN service
 How to connect to the University of Exeter VPN service *****Important Part of the process of using the VPN service involves the automatic download and installation of Juniper Network Connect software,
How to connect to the University of Exeter VPN service *****Important Part of the process of using the VPN service involves the automatic download and installation of Juniper Network Connect software,
Pre-configured AS2 Host Quick-Start Guide
 Pre-configured AS2 Host Quick-Start Guide Document Version 2.2, October 19, 2004 Copyright 2004 Cleo Communications Refer to the Cleo website at http://www.cleo.com/products/lexihubs.asp for the current
Pre-configured AS2 Host Quick-Start Guide Document Version 2.2, October 19, 2004 Copyright 2004 Cleo Communications Refer to the Cleo website at http://www.cleo.com/products/lexihubs.asp for the current
Outlook Data File navigate to the PST file that you want to open, select it and choose OK. The file will now appear as a folder in Outlook.
 Migrate Archived Outlook Items Outlook includes archiving functionality that is used to free up space on the mail server by moving older items from the mail server to PST files stored on your computer
Migrate Archived Outlook Items Outlook includes archiving functionality that is used to free up space on the mail server by moving older items from the mail server to PST files stored on your computer
Cloud Backup Express
 Cloud Backup Express Table of Contents Installation and Configuration Workflow for RFCBx... 3 Cloud Management Console Installation Guide for Windows... 4 1: Run the Installer... 4 2: Choose Your Language...
Cloud Backup Express Table of Contents Installation and Configuration Workflow for RFCBx... 3 Cloud Management Console Installation Guide for Windows... 4 1: Run the Installer... 4 2: Choose Your Language...
SSO Plugin. Case study: Integrating with Ping Federate. J System Solutions. http://www.javasystemsolutions.com. Version 4.0
 SSO Plugin Case study: Integrating with Ping Federate J System Solutions Version 4.0 JSS SSO Plugin v4.0 Release notes Introduction... 3 Ping Federate Service Provider configuration... 4 Assertion Consumer
SSO Plugin Case study: Integrating with Ping Federate J System Solutions Version 4.0 JSS SSO Plugin v4.0 Release notes Introduction... 3 Ping Federate Service Provider configuration... 4 Assertion Consumer
IBM WebSphere Application Server Version 7.0
 IBM WebSphere Application Server Version 7.0 Centralized Installation Manager for IBM WebSphere Application Server Network Deployment Version 7.0 Note: Before using this information, be sure to read the
IBM WebSphere Application Server Version 7.0 Centralized Installation Manager for IBM WebSphere Application Server Network Deployment Version 7.0 Note: Before using this information, be sure to read the
Application. 1.1 About This Tutorial. 1.1.1 Tutorial Requirements. 1.1.2 Provided Files
 About This Tutorial 1Creating an End-to-End HL7 Over MLLP Application 1.1 About This Tutorial 1.1.1 Tutorial Requirements 1.1.2 Provided Files This tutorial takes you through the steps of creating an end-to-end
About This Tutorial 1Creating an End-to-End HL7 Over MLLP Application 1.1 About This Tutorial 1.1.1 Tutorial Requirements 1.1.2 Provided Files This tutorial takes you through the steps of creating an end-to-end
Com-Trader. Installation Guide
 Com-Trader Installation Guide Table of Contents 1 Introduction 1 1.1. Java Web Start 1 1.2. Download Time 1 1.3. Definitions and Abbreviations 2 2 Installation of Components 3 2.1 Connectivity Setup 3
Com-Trader Installation Guide Table of Contents 1 Introduction 1 1.1. Java Web Start 1 1.2. Download Time 1 1.3. Definitions and Abbreviations 2 2 Installation of Components 3 2.1 Connectivity Setup 3
SDK Code Examples Version 2.4.2
 Version 2.4.2 This edition of SDK Code Examples refers to version 2.4.2 of. This document created or updated on February 27, 2014. Please send your comments and suggestions to: Black Duck Software, Incorporated
Version 2.4.2 This edition of SDK Code Examples refers to version 2.4.2 of. This document created or updated on February 27, 2014. Please send your comments and suggestions to: Black Duck Software, Incorporated
BF2CC Daemon Linux Installation Guide
 BF2CC Daemon Linux Installation Guide Battlefield 2 + BF2CC Installation Guide (Linux) 1 Table of contents 1. Introduction... 3 2. Opening ports in your firewall... 4 3. Creating a new user account...
BF2CC Daemon Linux Installation Guide Battlefield 2 + BF2CC Installation Guide (Linux) 1 Table of contents 1. Introduction... 3 2. Opening ports in your firewall... 4 3. Creating a new user account...
Configuring SSL in OBIEE 11g
 By Krishna Marur Configuring SSL in OBIEE 11g This white paper covers configuring SSL for OBIEE 11g in a scenario where the SSL certificate is not in a format that Web Logic Server (WLS) readily accepts
By Krishna Marur Configuring SSL in OBIEE 11g This white paper covers configuring SSL for OBIEE 11g in a scenario where the SSL certificate is not in a format that Web Logic Server (WLS) readily accepts
NetBeans IDE Field Guide
 NetBeans IDE Field Guide Copyright 2005 Sun Microsystems, Inc. All rights reserved. Table of Contents Introduction to J2EE Development in NetBeans IDE...1 Configuring the IDE for J2EE Development...2 Getting
NetBeans IDE Field Guide Copyright 2005 Sun Microsystems, Inc. All rights reserved. Table of Contents Introduction to J2EE Development in NetBeans IDE...1 Configuring the IDE for J2EE Development...2 Getting
Java Web Start. Brad Shuler Software Engineer Object Computing, Inc. St. Louis, MO
 Java Web Start Brad Shuler Software Engineer Object Computing, Inc. St. Louis, MO OCI Java Lunch, 30 Nov 2001 Overview Java Web Start (JWS) What is it? Demo How it works Deployment on Server Security Application
Java Web Start Brad Shuler Software Engineer Object Computing, Inc. St. Louis, MO OCI Java Lunch, 30 Nov 2001 Overview Java Web Start (JWS) What is it? Demo How it works Deployment on Server Security Application
SSL Certificate Generation
 SSL Certificate Generation Last updated: 2/09/2014 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion of an existing certificate chain available in a
SSL Certificate Generation Last updated: 2/09/2014 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion of an existing certificate chain available in a
Hadoop Installation MapReduce Examples Jake Karnes
 Big Data Management Hadoop Installation MapReduce Examples Jake Karnes These slides are based on materials / slides from Cloudera.com Amazon.com Prof. P. Zadrozny's Slides Prerequistes You must have an
Big Data Management Hadoop Installation MapReduce Examples Jake Karnes These slides are based on materials / slides from Cloudera.com Amazon.com Prof. P. Zadrozny's Slides Prerequistes You must have an
Setting up Citrix XenServer for 2X VirtualDesktopServer Manual
 Setting up Citrix XenServer for 2X VirtualDesktopServer Manual URL: www.2x.com E-mail: info@2x.com Information in this document is subject to change without notice. Companies, names, and data used in examples
Setting up Citrix XenServer for 2X VirtualDesktopServer Manual URL: www.2x.com E-mail: info@2x.com Information in this document is subject to change without notice. Companies, names, and data used in examples
Installing Windows Server Update Services (WSUS) on Windows Server 2012 R2 Essentials
 Installing Windows Server Update Services (WSUS) on Windows Server 2012 R2 Essentials With Windows Server 2012 R2 Essentials in your business, it is important to centrally manage your workstations to ensure
Installing Windows Server Update Services (WSUS) on Windows Server 2012 R2 Essentials With Windows Server 2012 R2 Essentials in your business, it is important to centrally manage your workstations to ensure
JBoss Portal 2.4. Quickstart User Guide
 Portal 2.4 Quickstart User Guide Table of Contents Portal - Overview... iii 1. Tutorial Forward...1 2. Installation...2 2.1. Downloading and Installing...2 2.2. Starting Portal...3 3. Portal Terminology...5
Portal 2.4 Quickstart User Guide Table of Contents Portal - Overview... iii 1. Tutorial Forward...1 2. Installation...2 2.1. Downloading and Installing...2 2.2. Starting Portal...3 3. Portal Terminology...5
JAVA 2 Network Security
 JAVA 2 Network Security M A R C O PISTOIA DUANE F. RELLER DEEPAK GUPTA MILIND NAGNUR ASHOK K. RAMANI PTR, UPPER http://www.phptr.com PRENTICE HALL SADDLE RIVER, NEW JERSEY 07458 Contents Foreword Preface
JAVA 2 Network Security M A R C O PISTOIA DUANE F. RELLER DEEPAK GUPTA MILIND NAGNUR ASHOK K. RAMANI PTR, UPPER http://www.phptr.com PRENTICE HALL SADDLE RIVER, NEW JERSEY 07458 Contents Foreword Preface
Moxa Device Manager 2.3 User s Manual
 User s Manual Third Edition, March 2011 www.moxa.com/product 2011 Moxa Inc. All rights reserved. User s Manual The software described in this manual is furnished under a license agreement and may be used
User s Manual Third Edition, March 2011 www.moxa.com/product 2011 Moxa Inc. All rights reserved. User s Manual The software described in this manual is furnished under a license agreement and may be used
IBM Security QRadar Vulnerability Manager Version 7.2.1. User Guide
 IBM Security QRadar Vulnerability Manager Version 7.2.1 User Guide Note Before using this information and the product that it supports, read the information in Notices on page 61. Copyright IBM Corporation
IBM Security QRadar Vulnerability Manager Version 7.2.1 User Guide Note Before using this information and the product that it supports, read the information in Notices on page 61. Copyright IBM Corporation
Installation Notes for Outpost Network Security (ONS) version 3.2
 Outpost Network Security Installation Notes version 3.2 Page 1 Installation Notes for Outpost Network Security (ONS) version 3.2 Contents Installation Notes for Outpost Network Security (ONS) version 3.2...
Outpost Network Security Installation Notes version 3.2 Page 1 Installation Notes for Outpost Network Security (ONS) version 3.2 Contents Installation Notes for Outpost Network Security (ONS) version 3.2...
Setting up FileMaker 10 Server
 Setting up FileMaker 10 Server Note : If your current live Database folder is located in the default database folder ( C:\Program Files\FileMaker\FileMaker Server\Data\Databases ), move\copy this folder
Setting up FileMaker 10 Server Note : If your current live Database folder is located in the default database folder ( C:\Program Files\FileMaker\FileMaker Server\Data\Databases ), move\copy this folder
Online Backup Client User Manual Mac OS
 Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS
 Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
KMIP installation Guide. DataSecure and KeySecure Version 6.1.2. 2012 SafeNet, Inc. 007-012120-001
 KMIP installation Guide DataSecure and KeySecure Version 6.1.2 2012 SafeNet, Inc. 007-012120-001 Introduction This guide provides you with the information necessary to configure the KMIP server on the
KMIP installation Guide DataSecure and KeySecure Version 6.1.2 2012 SafeNet, Inc. 007-012120-001 Introduction This guide provides you with the information necessary to configure the KMIP server on the
Introduction to Android Development
 2013 Introduction to Android Development Keshav Bahadoor An basic guide to setting up and building native Android applications Science Technology Workshop & Exposition University of Nigeria, Nsukka Keshav
2013 Introduction to Android Development Keshav Bahadoor An basic guide to setting up and building native Android applications Science Technology Workshop & Exposition University of Nigeria, Nsukka Keshav
Linux Overview. Local facilities. Linux commands. The vi (gvim) editor
 Linux Overview Local facilities Linux commands The vi (gvim) editor MobiLan This system consists of a number of laptop computers (Windows) connected to a wireless Local Area Network. You need to be careful
Linux Overview Local facilities Linux commands The vi (gvim) editor MobiLan This system consists of a number of laptop computers (Windows) connected to a wireless Local Area Network. You need to be careful
How to Install Applications (APK Files) on Your Android Phone
 How to Install Applications (APK Files) on Your Android Phone Overview An Android application is stored in an APK file (i.e., a file named by {Application Name}.apk). You must install the APK on your Android
How to Install Applications (APK Files) on Your Android Phone Overview An Android application is stored in an APK file (i.e., a file named by {Application Name}.apk). You must install the APK on your Android
NexentaConnect for VMware Virtual SAN
 NexentaConnect for VMware Virtual SAN User Guide 1.0.2 FP3 Date: April, 2016 Subject: NexentaConnect for VMware Virtual SAN User Guide Software: NexentaConnect for VMware Virtual SAN Software Version:
NexentaConnect for VMware Virtual SAN User Guide 1.0.2 FP3 Date: April, 2016 Subject: NexentaConnect for VMware Virtual SAN User Guide Software: NexentaConnect for VMware Virtual SAN Software Version:
SEZ SEZ Online Manual- DSC Signing with Java Applet. V Version 1.0 ersion 1.0
 SEZ SEZ Online Manual- V Version 1.0 ersion 1.0 Table of Contents 1 Introduction...2 2 DSC signing functionality with java applet...2 3 Troubleshooting...5 4 Annexure I: JAVA Console Setting... 13 5 Annexure
SEZ SEZ Online Manual- V Version 1.0 ersion 1.0 Table of Contents 1 Introduction...2 2 DSC signing functionality with java applet...2 3 Troubleshooting...5 4 Annexure I: JAVA Console Setting... 13 5 Annexure
Installing Ruby on Windows XP
 Table of Contents 1 Installation...2 1.1 Installing Ruby... 2 1.1.1 Downloading...2 1.1.2 Installing Ruby...2 1.1.3 Testing Ruby Installation...6 1.2 Installing Ruby DevKit... 7 1.3 Installing Ruby Gems...
Table of Contents 1 Installation...2 1.1 Installing Ruby... 2 1.1.1 Downloading...2 1.1.2 Installing Ruby...2 1.1.3 Testing Ruby Installation...6 1.2 Installing Ruby DevKit... 7 1.3 Installing Ruby Gems...
WA1826 Designing Cloud Computing Solutions. Classroom Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1
 WA1826 Designing Cloud Computing Solutions Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum
WA1826 Designing Cloud Computing Solutions Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum
SSO Plugin. J System Solutions. Upgrading SSO Plugin 3x to 4x - BMC AR System & Mid Tier. http://www.javasystemsolutions.com
 SSO Plugin Upgrading SSO Plugin 3x to 4x - BMC AR System & Mid Tier J System Solutions JSS SSO Plugin Upgrading 3x to 4x Introduction... 3 [Prerequisite] Generate a new license... 4 [Prerequisite] Download
SSO Plugin Upgrading SSO Plugin 3x to 4x - BMC AR System & Mid Tier J System Solutions JSS SSO Plugin Upgrading 3x to 4x Introduction... 3 [Prerequisite] Generate a new license... 4 [Prerequisite] Download
Delegated Administration Quick Start
 Delegated Administration Quick Start Topic 50200 Delegated Administration Quick Start Updated 22-Oct-2013 Applies to: Web Filter, Web Security, Web Security Gateway, and Web Security Gateway Anywhere,
Delegated Administration Quick Start Topic 50200 Delegated Administration Quick Start Updated 22-Oct-2013 Applies to: Web Filter, Web Security, Web Security Gateway, and Web Security Gateway Anywhere,
Director and Certificate Authority Issuance
 VMware vcloud Director and Certificate Authority Issuance Leveraging QuoVadis Certificate Authority with VMware vcloud Director TECHNICAL WHITE PAPER OCTOBER 2012 Table of Contents Introduction.... 3 Process
VMware vcloud Director and Certificate Authority Issuance Leveraging QuoVadis Certificate Authority with VMware vcloud Director TECHNICAL WHITE PAPER OCTOBER 2012 Table of Contents Introduction.... 3 Process
Hypercosm. Studio. www.hypercosm.com
 Hypercosm Studio www.hypercosm.com Hypercosm Studio Guide 3 Revision: November 2005 Copyright 2005 Hypercosm LLC All rights reserved. Hypercosm, OMAR, Hypercosm 3D Player, and Hypercosm Studio are trademarks
Hypercosm Studio www.hypercosm.com Hypercosm Studio Guide 3 Revision: November 2005 Copyright 2005 Hypercosm LLC All rights reserved. Hypercosm, OMAR, Hypercosm 3D Player, and Hypercosm Studio are trademarks
How to Implement Transport Layer Security in PowerCenter Web Services
 How to Implement Transport Layer Security in PowerCenter Web Services 2008 Informatica Corporation Table of Contents Introduction... 2 Security in PowerCenter Web Services... 3 Step 1. Create the Keystore
How to Implement Transport Layer Security in PowerCenter Web Services 2008 Informatica Corporation Table of Contents Introduction... 2 Security in PowerCenter Web Services... 3 Step 1. Create the Keystore
Migrating From Bobcat Mail To Google Apps (Using Microsoft Outlook and Google Apps Sync)
 Migrating From Bobcat Mail To Google Apps (Using Microsoft Outlook and Google Apps Sync) This document is intended for those users moving from WVWC s Bobcat Mail system to the new Google Apps mail system
Migrating From Bobcat Mail To Google Apps (Using Microsoft Outlook and Google Apps Sync) This document is intended for those users moving from WVWC s Bobcat Mail system to the new Google Apps mail system
HP Cloud Service Automation
 Technical white paper HP Cloud Service Automation Integration with HP Service Manager Table of contents Introduction 2 Required software components 2 Configuration requirements 2 Downloading the distribution
Technical white paper HP Cloud Service Automation Integration with HP Service Manager Table of contents Introduction 2 Required software components 2 Configuration requirements 2 Downloading the distribution
Setting Up Your Android Development Environment. For Mac OS X (10.6.8) v1.0. By GoNorthWest. 3 April 2012
 Setting Up Your Android Development Environment For Mac OS X (10.6.8) v1.0 By GoNorthWest 3 April 2012 Setting up the Android development environment can be a bit well challenging if you don t have all
Setting Up Your Android Development Environment For Mac OS X (10.6.8) v1.0 By GoNorthWest 3 April 2012 Setting up the Android development environment can be a bit well challenging if you don t have all
Using FTP to update L300 Firmware
 July 6, 2011 Using FTP to update L300 Firmware NComputing L300s can download and apply firmware updates from FTP servers located virtually anywhere in the world. This document describes how use FTP to
July 6, 2011 Using FTP to update L300 Firmware NComputing L300s can download and apply firmware updates from FTP servers located virtually anywhere in the world. This document describes how use FTP to
Attix5 Pro Server Edition
 Attix5 Pro Server Edition V7.0.3 User Manual for Linux and Unix operating systems Your guide to protecting data with Attix5 Pro Server Edition. Copyright notice and proprietary information All rights reserved.
Attix5 Pro Server Edition V7.0.3 User Manual for Linux and Unix operating systems Your guide to protecting data with Attix5 Pro Server Edition. Copyright notice and proprietary information All rights reserved.
