How UTM-1, DLP and Application Control Protect your IT environment
|
|
|
- Marybeth Sharp
- 9 years ago
- Views:
Transcription
1 How UTM-1, DLP and Application Control Protect your IT environment Louis Cheung Security Consultant CISSP, CISA Dec Check Point Software Technologies Ltd. [Restricted] ONLY for designated groups and individuals
2 Agenda Security Evolution What s new on UTM-1 Appliance New Software blades DLP Application Control Q & A 2
3 Security Evolution In the past there were few security challenges and few solutions The Internet grew and so did security. and it became pretty complex. 3
4 The Security Maze 15 different point products 4
5 The Security Maze Try to find your way 5
6 The Security Maze or take the Check Point route. 6
7 The Security Maze or take the Check Point route. 7
8 Today Challenge Performance needs Investment Cost Operation Cost Product lifecycle Security needs Number of users Applications Internet bandwidth NETWORK SECURITY Firewall VPN IPS Web Filtering Anti-malware Protection SSL VPN DLP & more 8
9 What s New in UTM-1 R Check Point Software Technologies Ltd. [Restricted] ONLY for designated groups and individuals
10 R71 AV and URLF Performance boost Anti Virus & Anti Malware Introduce new industry-leading AV engine by Kaspersky New Stream mode uses kernel stream Performance is significantly higher Improve stability and memory consumption URL Filtering Introduce enhanced URL Filtering engine Move to a new kernel architecture Performance is significantly higher eliminates the limitation of concurrent connections Improve stability and memory consumption. Support wild characters ( * ) in Allow/Block lists 10
11 Patented Acceleration Technology: SecureXL Accelerated path, optimized securityprocessing tier. Accelerates packet and session Hardware: IP ADP (former Nokia) Performance Pack (SecurePlatform, Crossbeam) IPSO SecureXL software implementation Throughput Performance Acceleration CPS 11
12 R71 UTM-1 Boost Maximum Performance and Capacity FW (1518 bytes), Mbps IPS Throughput - Default Protections, Mbps Anti-Virus, Mbps Connection rate (cps) Max concurrent HTTP AV & URLF UTM UTM R70 R71 Boost R70 R71 Boost 600 1,500 X2.5 2,000 3,000 x ,000 X ,200 X X X4 3,400 10,000 X2.9 8,800 25,000 X2.8 2,500 50,000 X20 4, ,000 X27 All UTM-1 platforms include SecureXL (R71) 12
13 Firewall throughput (Gbps) Raising the Bar on UTM-1 Performance 5 Small office or branch SMB to medium branch UTM UTM UTM UTM UTM Up to 4x Firewall throughput improvement with SW update only!!! 13
14 Security Enhancement: DLP Application Control 2010 Check Point Software Technologies Ltd. [Restricted] ONLY for designated groups and individuals
15 Data Loss Prevention What is DLP? Corporate Strategy Green World Strategy Plan sent to the wrong recipient, intentionally or by mistake. Company document uploaded to an external website. Data breaches have happened to all of us 15
16 How Does Check Point DLP Work? MultiSpect Detection Engine Simple Rule-based Policy Management Full Network Enforcement 16
17 New MultiSpect Technology MultiSpect Detection Engine Correlates data from multiple sources using open language Item No. Name Social Security Number Job Title Gross Pay 1 John Smith CEO $200,000 2 Kevin Brian VP R&D $150,000 3 Margret White 250+ Data Types 600+ File Formats VP Marketing $153,000 4 Bob Johns CFO $140,000 5 Mike Riddle COO $180,000 Detects more than 600 file formats Over 250 pre-defined content data types Detect and recognize proprietary forms and templates 17
18 DLP Has Not Yet Been Solved! Technology IT Staff Challenge Computers can not reliably understand human content and context Challenge Burden of incident handling Exposure to sensitive data 18
19 Check Point Makes DLP Work Data Loss Prevention Alert John, An that you have just sent has been quarantined. John Corporate Reason: Strategy attached document contains confidential internal data Green World Strategy Plan 2010 The message is being held until further action. Confidential data sent to the wrong recipient! User prompted to take action Let s review the corporate strategy in our morning meeting. Send, Discard, or Review Issue User remediates 19
20 Introducing Check Point Data Loss Prevention Check Point Combines Technology and Processes to Make DLP Work NEW! John, Corporate Strategy Green World Strategy Plan 2010 Data Loss Prevention Alert An that you have just sent has been quarantined. Let s review the corporate strategy in our morning meeting. Reason: attached document contains confidential internal data Prevent Move from detection to prevention Educate Users on corporate data policies The message is being held until further action. Send, Discard, or Review Issue Enforce Data loss business processes 20
21 Check Point Solves the DLP Challenge New UserCheck Technology Technology Challenge Empowers users to remediate incidents in real time IT Staff Challenge Educates users on DLP policies without involving IT staff 21
22 Ease-of-Deployment Software Blade Dedicated Appliance Network-based Inline Solution On Existing Gateways or Open Servers DLP-1 Be Up and Running Day-1! 22
23 Check Point DLP At-A-Glance Move from Detection to Prevention Proactively block intentional and unintentional data loss Inline network-based Software Blade running on any existing Check Point gateway Supporting HTTP, SMTP and FTP protocols UserCheck notification using either thin agent or a returning to the user Scaling from hundred to thousands of users 23
24 The Problem with Internet Applications Malware Threats Bandwidth Hogging Productivity Loss 24
25 Introducing Check Point Application Control Software Blade Detect and control application usage AppWiki Industry s largest library with over 50,000 applications Educate users on corporate policies Available Soon Available on EVERY gateway 25
26 Introducing Check Point AppWiki Unparalleled Application Control Over 4,500 applications Over 50,000 social-network widgets Grouped in over 150 categories (including Web 2.0, IM, P2P, Voice & Video, File Share) World s largest Application Classification Library 26
27 Granular Application Categorization Application Type IM Web conferencing Gaming. Advanced Properties Share files High bandwidth Use stealth techniques Security Risk Measures the potential risk 27
28 User and Machine Awareness Includes User Identification Corporate Active Directory Security Gateway User- and group-aware Machine-aware User identification with both agent-based and seamless, agentless Active Directory integration 28
29 Application Detection and Usage Controls Application Detection and Usage Controls Enable access for support team Identify, allow, block or limit usage of applications at user or group level 29
30 Practical Implementation Involve end-users using multiple policy actions Accept / Drop Traditional security policies are suitable for clear-cut cases Inform Allow but inform the user about the risks Ask Learn usage patterns to create better policies Limit Use to preserve resources (bandwidth) or control acceptable use 30
31 Certifications ICSA CC EAL4 VPNC FIPS
32 Awards Leader in the 2010 Magic Quadrant for UTM 32
33 The vision, More, Better and Simpler Application control UTM services Future technology KEEPING SSL YOUR INVESTMENT VPN DLP VPN Future technology IPS Future technology 33
34 Thank You 2010 Check Point Software Technologies Ltd. [Restricted] ONLY for designated groups and individuals
Check Point 3D Security
 Check Point 3D Security Combining Policies, People and Enforcement for Unbeatable Protection John Vecchi Head of WW Product Marketing 2011 Check Point Software Technologies Ltd. [Unrestricted] For everyone
Check Point 3D Security Combining Policies, People and Enforcement for Unbeatable Protection John Vecchi Head of WW Product Marketing 2011 Check Point Software Technologies Ltd. [Unrestricted] For everyone
Unified Threat Management, Managed Security, and the Cloud Services Model
 Unified Threat Management, Managed Security, and the Cloud Services Model Kurtis E. Minder CISSP Global Account Manager - Service Provider Group Fortinet, Inc. Introduction Kurtis E. Minder, Technical
Unified Threat Management, Managed Security, and the Cloud Services Model Kurtis E. Minder CISSP Global Account Manager - Service Provider Group Fortinet, Inc. Introduction Kurtis E. Minder, Technical
Firewall Testing Methodology W H I T E P A P E R
 Firewall ing W H I T E P A P E R Introduction With the deployment of application-aware firewalls, UTMs, and DPI engines, the network is becoming more intelligent at the application level With this awareness
Firewall ing W H I T E P A P E R Introduction With the deployment of application-aware firewalls, UTMs, and DPI engines, the network is becoming more intelligent at the application level With this awareness
Securing Virtualization with Check Point and Consolidation with Virtualized Security
 Securing Virtualization with Check Point and Consolidation with Virtualized Security consolidate security gateways with full power of Software Blades with Check Point Virtual Systems (VSX) secure virtualized
Securing Virtualization with Check Point and Consolidation with Virtualized Security consolidate security gateways with full power of Software Blades with Check Point Virtual Systems (VSX) secure virtualized
10 Strategies to Optimize IT Spending in an Economic Downturn. Wong Kang Yeong, CISA, CISM, CISSP Regional Security Architect, ASEAN
 10 Strategies to Optimize IT Spending in an Economic Downturn Wong Kang Yeong, CISA, CISM, CISSP Regional Security Architect, ASEAN Current Economic Landscape 2 Basically you Basically you ve had to throw
10 Strategies to Optimize IT Spending in an Economic Downturn Wong Kang Yeong, CISA, CISM, CISSP Regional Security Architect, ASEAN Current Economic Landscape 2 Basically you Basically you ve had to throw
ANNEXURE TO TENDER NO. MRPU/IGCAR/COMP/5239
 ANNEXURE TO TENDER NO. MRPU/IGCAR/COMP/5239 Check Point Firewall Software and Management Software I. Description of the Item Up gradation, installation and commissioning of Checkpoint security gateway
ANNEXURE TO TENDER NO. MRPU/IGCAR/COMP/5239 Check Point Firewall Software and Management Software I. Description of the Item Up gradation, installation and commissioning of Checkpoint security gateway
McAfee Endpoint Protection Products
 McAfee Total Protection Security Overview for MEEC Sumeet Gohri, CISSP Sr. Sales Engineer GovED + Healthcare McAfee, Inc. Agenda Protection Challenges McAfee Protection Products McAfee epo walkthrough
McAfee Total Protection Security Overview for MEEC Sumeet Gohri, CISSP Sr. Sales Engineer GovED + Healthcare McAfee, Inc. Agenda Protection Challenges McAfee Protection Products McAfee epo walkthrough
Check Point Security Administrator R70
 Page 1 of 6 Check Point Security Administrator R70 Check Point Security Administration R70 Length Prerequisites 5 days* (recommended) Basic networking knowledge, knowledge of Windows Server and/or UNIX,
Page 1 of 6 Check Point Security Administrator R70 Check Point Security Administration R70 Length Prerequisites 5 days* (recommended) Basic networking knowledge, knowledge of Windows Server and/or UNIX,
Application Control and URL Filtering
 Application Control and URL Filtering R77 Versions Administration Guide 17 May 2015 Classification: [Protected] 2015 Check Point Software Technologies Ltd. All rights reserved. This product and related
Application Control and URL Filtering R77 Versions Administration Guide 17 May 2015 Classification: [Protected] 2015 Check Point Software Technologies Ltd. All rights reserved. This product and related
Next Generation Enterprise Network Security Platform
 Next Generation Enterprise Network Security Platform November 2014 Lyndon Clough - Territory Sales Manager Derran Guinan Systems Engineer Agenda The Palo Alto Networks story Today s Threat Landscape The
Next Generation Enterprise Network Security Platform November 2014 Lyndon Clough - Territory Sales Manager Derran Guinan Systems Engineer Agenda The Palo Alto Networks story Today s Threat Landscape The
Unified Threat Management Throughput Performance
 Unified Threat Management Throughput Performance Desktop Device Comparison DR150818C October 2015 Miercom www.miercom.com Contents Executive Summary... 3 Introduction... 4 Products Tested... 6 How We Did
Unified Threat Management Throughput Performance Desktop Device Comparison DR150818C October 2015 Miercom www.miercom.com Contents Executive Summary... 3 Introduction... 4 Products Tested... 6 How We Did
Appliance Comparison Chart
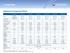 Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Nokia IP Security Platforms Technical Specifications Guide Nokia Enterprise Solutions
 Nokia IP Security Platforms Technical Specifications Guide Nokia Enterprise Solutions Positioning Enterprise ROBO 8, 16, 32 and Unlimited Work extender, telecommuter, small office FW or VPN Medium businesses
Nokia IP Security Platforms Technical Specifications Guide Nokia Enterprise Solutions Positioning Enterprise ROBO 8, 16, 32 and Unlimited Work extender, telecommuter, small office FW or VPN Medium businesses
IBM Security Network Protection
 IBM Software Data sheet IBM Security Network Protection Highlights Delivers superior zero-day threat protection and security intelligence powered by IBM X- Force Provides critical insight and visibility
IBM Software Data sheet IBM Security Network Protection Highlights Delivers superior zero-day threat protection and security intelligence powered by IBM X- Force Provides critical insight and visibility
How To Protect Your Network From Attack From A Virus And Attack From Your Network (D-Link)
 NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls (DFL-260/860) integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content Filtering
NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls (DFL-260/860) integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content Filtering
How Traditional Firewalls Fail Today s Networks And Why Next-Generation Firewalls Will Prevail
 How Fail Today s Networks And Why Will Prevail Why your current firewall may be jeopardizing your security, and how you can counter today s threats, manage web 2.0 apps and enforce acceptable-use policies.
How Fail Today s Networks And Why Will Prevail Why your current firewall may be jeopardizing your security, and how you can counter today s threats, manage web 2.0 apps and enforce acceptable-use policies.
FROM PRODUCT TO PLATFORM
 FROM PRODUCT TO PLATFORM DATA EQUIPMENT 2016 Mikkel Bossen Agenda Today s Challenges Data Growth, SSL encryption, Application Growth & SaaS What s hiding in under the surface? Legacy Security is that really
FROM PRODUCT TO PLATFORM DATA EQUIPMENT 2016 Mikkel Bossen Agenda Today s Challenges Data Growth, SSL encryption, Application Growth & SaaS What s hiding in under the surface? Legacy Security is that really
Check Point 2200 Appliance
 Datasheet: Check Point 2200 Appliance 2200 Branch & Small Office Solution Enterprise security in a desktop package Check Point 2200 Appliance Today the Internet gateway is more than a firewall. It is a
Datasheet: Check Point 2200 Appliance 2200 Branch & Small Office Solution Enterprise security in a desktop package Check Point 2200 Appliance Today the Internet gateway is more than a firewall. It is a
SonicWALL Clean VPN. Protect applications with granular access control based on user identity and device identity/integrity
 SSL-VPN Combined With Network Security Introducing A popular feature of the SonicWALL Aventail SSL VPN appliances is called End Point Control (EPC). This allows the administrator to define specific criteria
SSL-VPN Combined With Network Security Introducing A popular feature of the SonicWALL Aventail SSL VPN appliances is called End Point Control (EPC). This allows the administrator to define specific criteria
Cyberoam Perspective BFSI Security Guidelines. Overview
 Overview The term BFSI stands for Banking, Financial Services and Insurance (BFSI). This term is widely used to address those companies which provide an array of financial products or services. Financial
Overview The term BFSI stands for Banking, Financial Services and Insurance (BFSI). This term is widely used to address those companies which provide an array of financial products or services. Financial
QUOTATION FOR UTM 4/26(1)/2009/EDP-HO 06/08/2015
 MARINE PRODUCTS EXPORT DEVELOPMENT AUTHORITY (Ministry of Commerce and Industry, Govt. of India) Panampilly Avenue, Cochin 682 036 (Ph: 0484-2311979, e-mail: [email protected]) QUOTATION FOR UTM 4/26(1)/2009/EDP-HO
MARINE PRODUCTS EXPORT DEVELOPMENT AUTHORITY (Ministry of Commerce and Industry, Govt. of India) Panampilly Avenue, Cochin 682 036 (Ph: 0484-2311979, e-mail: [email protected]) QUOTATION FOR UTM 4/26(1)/2009/EDP-HO
Applications erode the secure network How can malware be stopped?
 Vulnerabilities will continue to persist Vulnerabilities in the software everyone uses everyday Private Cloud Security It s Human Nature Programmers make mistakes Malware exploits mistakes Joe Gast Recent
Vulnerabilities will continue to persist Vulnerabilities in the software everyone uses everyday Private Cloud Security It s Human Nature Programmers make mistakes Malware exploits mistakes Joe Gast Recent
Websense Data Security Solutions
 Data Security Suite Data Discover Data Monitor Data Protect Data Endpoint Data Security Solutions What is your confidential data and where is it stored? Who is using your confidential data and how? Protecting
Data Security Suite Data Discover Data Monitor Data Protect Data Endpoint Data Security Solutions What is your confidential data and where is it stored? Who is using your confidential data and how? Protecting
Sonicwall Reporting Server
 Sonicwall Reporting Server How to access the reporting server: Navigate to https://swreports.hitechsupport.com.au, and enter your username and password provided. After you have logged in, click on the
Sonicwall Reporting Server How to access the reporting server: Navigate to https://swreports.hitechsupport.com.au, and enter your username and password provided. After you have logged in, click on the
Astaro Gateway Software Applications
 Astaro Overview Astaro Products - Astaro Security Gateway - Astaro Web Gateway - Astaro Mail Gateway - Astaro Command Center - Astaro Report Manager Astaro Gateway Software Applications - Network Security
Astaro Overview Astaro Products - Astaro Security Gateway - Astaro Web Gateway - Astaro Mail Gateway - Astaro Command Center - Astaro Report Manager Astaro Gateway Software Applications - Network Security
Cisco Cloud Web Security
 Data Sheet Today s highly connected and fast-moving world is filled with complex and sophisticated web security threats. Cisco delivers the strong protection, complete control, and investment value that
Data Sheet Today s highly connected and fast-moving world is filled with complex and sophisticated web security threats. Cisco delivers the strong protection, complete control, and investment value that
SourceFireNext-Generation IPS
 D Ů V Ě Ř U J T E S I L N Ý M SourceFireNext-Generation IPS Petr Salač CCNP Security, CCNP, CICSP, CCSI #33835 [email protected] Our Customers Biggest Security Challenges Maintaining security posture
D Ů V Ě Ř U J T E S I L N Ý M SourceFireNext-Generation IPS Petr Salač CCNP Security, CCNP, CICSP, CCSI #33835 [email protected] Our Customers Biggest Security Challenges Maintaining security posture
How to choose the right NGFW for your organization: Independent 3 rd Party Testing
 How to choose the right NGFW for your organization: Independent 3 rd Party Testing Daniel Ayoub, CISSP, CISM, CISA, CEH Manager, Product Marketing Dell Marketing 2 Confidential Marketing vs. Reality 3
How to choose the right NGFW for your organization: Independent 3 rd Party Testing Daniel Ayoub, CISSP, CISM, CISA, CEH Manager, Product Marketing Dell Marketing 2 Confidential Marketing vs. Reality 3
What s Next for Network Security - Visibility is king! Gøran Tømte March 2013
 What s Next for Network Security - Visibility is king! Gøran Tømte March 2013 Technology Sprawl and Creep Aren t the Answer More stuff doesn t solve the problem Firewall helpers have limited view of traffic
What s Next for Network Security - Visibility is king! Gøran Tømte March 2013 Technology Sprawl and Creep Aren t the Answer More stuff doesn t solve the problem Firewall helpers have limited view of traffic
SonicWALL Unified Threat Management. Alvin Mann April 2009
 SonicWALL Unified Threat Management Alvin Mann April 2009 Agenda Who is SonicWALL? Networking Drivers & Trends SonicWALL Unified Threat Management (UTM) Next Generation Protection SonicWALL CONFIDENTIAL
SonicWALL Unified Threat Management Alvin Mann April 2009 Agenda Who is SonicWALL? Networking Drivers & Trends SonicWALL Unified Threat Management (UTM) Next Generation Protection SonicWALL CONFIDENTIAL
Check Point Positions
 Check Point Positions - Gartner Magic Quadrants - IDC Market Share Research 2012 Dean J. Whitehair Analyst Relations October 2012 Version 9.0 Updated 10/17/2012 2012 Check Point Software Technologies Ltd.
Check Point Positions - Gartner Magic Quadrants - IDC Market Share Research 2012 Dean J. Whitehair Analyst Relations October 2012 Version 9.0 Updated 10/17/2012 2012 Check Point Software Technologies Ltd.
CHECK POINT. Software Blade Architecture
 CHECK POINT Software Blade Architecture 2 softwareblades from Check Point Today s Security Challenge Protecting enterprises against today s constantly evolving threat environment has never been more challenging.
CHECK POINT Software Blade Architecture 2 softwareblades from Check Point Today s Security Challenge Protecting enterprises against today s constantly evolving threat environment has never been more challenging.
Lab Testing Summary Report
 Lab Testing Summary Report February 14 Report 132B Product Category: Web Security Gateway Vendor Tested: Key findings and conclusions: security appliance exhibits best rate to date, 91.3%, for classifying
Lab Testing Summary Report February 14 Report 132B Product Category: Web Security Gateway Vendor Tested: Key findings and conclusions: security appliance exhibits best rate to date, 91.3%, for classifying
Workflow Guide. Configuring Web Protection. For Customers with Sophos Firewall Document Date: November 2015. November 2015 Page 1 of 44
 Workflow Guide Configuring Web Protection For Customers with Sophos Firewall Document Date: November 2015 November 2015 Page 1 of 44 Contents Overview... 3 Implementing Web Anti Virus (Web AV)... 3 Use
Workflow Guide Configuring Web Protection For Customers with Sophos Firewall Document Date: November 2015 November 2015 Page 1 of 44 Contents Overview... 3 Implementing Web Anti Virus (Web AV)... 3 Use
Reporting and Incident Management for Firewalls
 Reporting and Incident Management for Firewalls The keys to unlocking your firewall s secrets Contents White Paper November 8, 2001 The Role Of The Firewall In Network Security... 2 Firewall Activity Reporting
Reporting and Incident Management for Firewalls The keys to unlocking your firewall s secrets Contents White Paper November 8, 2001 The Role Of The Firewall In Network Security... 2 Firewall Activity Reporting
Integrated Approach to Network Security. Lee Klarich Senior Vice President, Product Management March 2013
 Integrated Approach to Network Security Lee Klarich Senior Vice President, Product Management March 2013 Real data from actual networks 2 2012, Palo Alto Networks. Confidential and Proprietary. 2008: HTTP,
Integrated Approach to Network Security Lee Klarich Senior Vice President, Product Management March 2013 Real data from actual networks 2 2012, Palo Alto Networks. Confidential and Proprietary. 2008: HTTP,
Sizing Guideline. Sophos UTM 9.1
 Sizing Guideline Sophos UTM 9.1 Three steps to specifying the right appliance model This document provides a guideline for choosing the right Sophos UTM appliance for your customer. Specifying the right
Sizing Guideline Sophos UTM 9.1 Three steps to specifying the right appliance model This document provides a guideline for choosing the right Sophos UTM appliance for your customer. Specifying the right
PCI Compliance for Branch Offices: Using Router-Based Security to Protect Cardholder Data
 White Paper PCI Compliance for Branch Offices: Using Router-Based Security to Protect Cardholder Data Using credit cards to pay for goods and services is a common practice. Credit cards enable easy and
White Paper PCI Compliance for Branch Offices: Using Router-Based Security to Protect Cardholder Data Using credit cards to pay for goods and services is a common practice. Credit cards enable easy and
Fortigate Features & Demo
 & Demo Prepared and Presented by: Georges Nassif Technical Manager Triple C Firewall Antivirus IPS Web Filtering AntiSpam Application Control DLP Client Reputation (cont d) Traffic Shaping IPSEC VPN SSL
& Demo Prepared and Presented by: Georges Nassif Technical Manager Triple C Firewall Antivirus IPS Web Filtering AntiSpam Application Control DLP Client Reputation (cont d) Traffic Shaping IPSEC VPN SSL
Evolutionism of Intrusion Detection
 Evolutionism of Intrusion Detection Jackie Lai The network technology changes with each passing day; and the attack technique of hacker also weeds through the old to bring forth the new. Worms such as
Evolutionism of Intrusion Detection Jackie Lai The network technology changes with each passing day; and the attack technique of hacker also weeds through the old to bring forth the new. Worms such as
The Cisco ASA 5500 as a Superior Firewall Solution
 The Cisco ASA 5500 as a Superior Firewall Solution The Cisco ASA 5500 Series Adaptive Security Appliance provides leading-edge firewall capabilities and expands to support other security services. Firewalls
The Cisco ASA 5500 as a Superior Firewall Solution The Cisco ASA 5500 Series Adaptive Security Appliance provides leading-edge firewall capabilities and expands to support other security services. Firewalls
Check Point submitted the SWG-12600 Secure Web Gateway for
 Key findings and conclusions: Lab Testing Summary Report September 213 Report 1382 Product Category: Web Security Gateway Vendors/Products Tested: Secure Web Gateway BlueCoat Proxy SG3-5 Appliance Websense
Key findings and conclusions: Lab Testing Summary Report September 213 Report 1382 Product Category: Web Security Gateway Vendors/Products Tested: Secure Web Gateway BlueCoat Proxy SG3-5 Appliance Websense
Internal Network Firewall (INFW) Protecting your network from the inside out
 Internal Network Firewall (INFW) Protecting your network from the inside out Ted Maniatis, SE Central Canada Fortinet Technologies Data Connectors 2015 Copyright Fortinet Inc. All rights reserved. Agenda
Internal Network Firewall (INFW) Protecting your network from the inside out Ted Maniatis, SE Central Canada Fortinet Technologies Data Connectors 2015 Copyright Fortinet Inc. All rights reserved. Agenda
Check Point Software Blade Architecture. Achieving the right balance between security protection and investment
 Check Point Software Blade Architecture Achieving the right balance between security protection and investment Contents Introduction 3 Check Point Software Blade architecture overview 3 What is a Software
Check Point Software Blade Architecture Achieving the right balance between security protection and investment Contents Introduction 3 Check Point Software Blade architecture overview 3 What is a Software
IPS AIM for Cisco Integrated Services Routers
 IPS AIM for Cisco Integrated Services Routers Technical Overview James Weathersby, TME, ARTG Tina Lam, Product Manager, ARTG 1 Cisco Integrated Threat Control Industry-Certified Security Embedded Within
IPS AIM for Cisco Integrated Services Routers Technical Overview James Weathersby, TME, ARTG Tina Lam, Product Manager, ARTG 1 Cisco Integrated Threat Control Industry-Certified Security Embedded Within
1110 Cool Things Your Firewall Should Do. Extending beyond blocking network threats to protect, manage and control application traffic
 1110 Cool Things Your Firewall Should Do Extending beyond blocking network threats to protect, manage and control application traffic Table of Contents The Firewall Grows Up 1 What does SonicWALL Application
1110 Cool Things Your Firewall Should Do Extending beyond blocking network threats to protect, manage and control application traffic Table of Contents The Firewall Grows Up 1 What does SonicWALL Application
Check Point 2013-2014 Partner Marketing Campaign Plan
 Check Point 2013-2014 Partner Marketing Campaign Plan 1 Welcome To keep pace with the changes and complexities of today s security challenges, you need a partner that is uniquely equipped to provide security
Check Point 2013-2014 Partner Marketing Campaign Plan 1 Welcome To keep pace with the changes and complexities of today s security challenges, you need a partner that is uniquely equipped to provide security
SonicWALL Email Security Quick Start Guide. Version 4.6
 SonicWALL Email Security Quick Start Guide Version 4.6 Quick Start Guide - Introduction This document guides you through the most basic steps to set up and administer SonicWALL Email Security. For more
SonicWALL Email Security Quick Start Guide Version 4.6 Quick Start Guide - Introduction This document guides you through the most basic steps to set up and administer SonicWALL Email Security. For more
Kelvin Wee CISA, CISM, CISSP Principal Consultant (DLP Specialist) Asia Pacific and Japan
 The Truth about Data Loss Kelvin Wee CISA, CISM, CISSP Principal Consultant (DLP Specialist) Asia Pacific and Japan RSA Data Loss Prevention Data Breaches Overview RSA DLP Solution Five Critical Factors
The Truth about Data Loss Kelvin Wee CISA, CISM, CISSP Principal Consultant (DLP Specialist) Asia Pacific and Japan RSA Data Loss Prevention Data Breaches Overview RSA DLP Solution Five Critical Factors
Sourcefire Solutions Overview Security for the Real World. SEE everything in your environment. LEARN by applying security intelligence to data
 SEE everything in your environment LEARN by applying security intelligence to data ADAPT defenses automatically ACT in real-time Sourcefire Solutions Overview Security for the Real World Change is constant.
SEE everything in your environment LEARN by applying security intelligence to data ADAPT defenses automatically ACT in real-time Sourcefire Solutions Overview Security for the Real World Change is constant.
Protecting the Infrastructure: Symantec Web Gateway
 Protecting the Infrastructure: Symantec Web Gateway 1 Why Symantec for Web Security? Flexibility and Choice Best in class hosted service, appliance, and virtual appliance (upcoming) deployment options
Protecting the Infrastructure: Symantec Web Gateway 1 Why Symantec for Web Security? Flexibility and Choice Best in class hosted service, appliance, and virtual appliance (upcoming) deployment options
NetDefend Firewall UTM Services
 NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content Filtering (WCF) for superior
NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content Filtering (WCF) for superior
Securing and Optimizing the Next Generation Branch Office
 Securing and Optimizing the Next Generation Branch Office 1 Global Organizations Current state of affairs 3 Globally distributed enterprises rely on the WAN for day to day operations to stay competitive
Securing and Optimizing the Next Generation Branch Office 1 Global Organizations Current state of affairs 3 Globally distributed enterprises rely on the WAN for day to day operations to stay competitive
The Dirty Secret Behind the UTM: What Security Vendors Don t Want You to Know
 The Dirty Secret Behind the UTM: What Security Vendors Don t Want You to Know I n t r o d u c t i o n Until the late 1990s, network security threats were predominantly written by programmers seeking notoriety,
The Dirty Secret Behind the UTM: What Security Vendors Don t Want You to Know I n t r o d u c t i o n Until the late 1990s, network security threats were predominantly written by programmers seeking notoriety,
http://docs.trendmicro.com/en-us/enterprise/safesync-for-enterprise.aspx
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Did you know your security solution can help with PCI compliance too?
 Did you know your security solution can help with PCI compliance too? High-profile data losses have led to increasingly complex and evolving regulations. Any organization or retailer that accepts payment
Did you know your security solution can help with PCI compliance too? High-profile data losses have led to increasingly complex and evolving regulations. Any organization or retailer that accepts payment
European developer & provider ensuring data protection User console: Simile Fingerprint Filter Policies and content filtering rules
 Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
CONTINUOUS MONITORING THE MISSING PIECE TO SECURITY OPERATION (SOC) TODAY
 CONTINUOUS MONITORING THE MISSING PIECE TO SECURITY OPERATION (SOC) TODAY MATTHIAS YEO Chief Technology Officer - APAC CISSP, CISA, CISM, PMP 1 OVER REACTING VS UNDER REACTING Reason for the world today
CONTINUOUS MONITORING THE MISSING PIECE TO SECURITY OPERATION (SOC) TODAY MATTHIAS YEO Chief Technology Officer - APAC CISSP, CISA, CISM, PMP 1 OVER REACTING VS UNDER REACTING Reason for the world today
Content Security Gateway Series Real-time Gateway Web Security Against Spyware and Viruses
 Content Security Gateway Series Real-time Gateway Web Security Against Spyware and Viruses 1. Why do I need a Web security or gateway anti-spyware solution? Malware attack vector is rapidly shifting from
Content Security Gateway Series Real-time Gateway Web Security Against Spyware and Viruses 1. Why do I need a Web security or gateway anti-spyware solution? Malware attack vector is rapidly shifting from
McAfee Web Gateway Administration Intel Security Education Services Administration Course Training
 McAfee Web Gateway Administration Intel Security Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction
McAfee Web Gateway Administration Intel Security Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction
Check Point taps the power of virtualization to simplify security for private clouds
 Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private
Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private
CALNET 3 Category 7 Network Based Management Security. Table of Contents
 State of California IFB STPD 12-001-B CALNET 3 Category 7 Network Based Security Table of Contents 7.2.1.4.a DDoS Detection and Mitigation Features... 1 7.2.2.3 Email Monitoring Service Features... 2 7.2.3.2
State of California IFB STPD 12-001-B CALNET 3 Category 7 Network Based Security Table of Contents 7.2.1.4.a DDoS Detection and Mitigation Features... 1 7.2.2.3 Email Monitoring Service Features... 2 7.2.3.2
Virtualized Security: The Next Generation of Consolidation
 Virtualization. Consolidation. Simplification. Choice. WHITE PAPER Virtualized Security: The Next Generation of Consolidation Virtualized Security: The Next Generation of Consolidation As we approach the
Virtualization. Consolidation. Simplification. Choice. WHITE PAPER Virtualized Security: The Next Generation of Consolidation Virtualized Security: The Next Generation of Consolidation As we approach the
Dell SonicWALL Next Generation Firewall(Gen6) and Integrated Solution. Colin Wu / 吳 炳 東 [email protected]
 Dell Next Generation Firewall(Gen6) and Integrated Solution Colin Wu / 吳 炳 東 [email protected] Agenda Company Overview Dell Product Line-Up Architecture Firewall security services Add-on products Wireless
Dell Next Generation Firewall(Gen6) and Integrated Solution Colin Wu / 吳 炳 東 [email protected] Agenda Company Overview Dell Product Line-Up Architecture Firewall security services Add-on products Wireless
Sophos Roadshow. Complete Security Vision
 Sophos Roadshow Complete Security Vision Reconized leader Over 25 years of experience Data protection experts Global company with local presence 100 million users trust Sophos Reputation for highest quality
Sophos Roadshow Complete Security Vision Reconized leader Over 25 years of experience Data protection experts Global company with local presence 100 million users trust Sophos Reputation for highest quality
Networking for Caribbean Development
 Networking for Caribbean Development BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n o g. o r g N E T W O R K I N G F O R C A R I B B E A N D E V E L O P M E N T BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n
Networking for Caribbean Development BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n o g. o r g N E T W O R K I N G F O R C A R I B B E A N D E V E L O P M E N T BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n
74% 96 Action Items. Compliance
 Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
NGFWs will be most effective when working in conjunction with other layers of security controls.
 Research Publication Date: 12 October 2009 ID Number: G00171540 Defining the Next-Generation Firewall John Pescatore, Greg Young Firewalls need to evolve to be more proactive in blocking new threats, such
Research Publication Date: 12 October 2009 ID Number: G00171540 Defining the Next-Generation Firewall John Pescatore, Greg Young Firewalls need to evolve to be more proactive in blocking new threats, such
Network Security Solution. Arktos Lam
 Network Security Solution Arktos Lam Dell Software Group(DSG) 2 Confidential Trend Dell Software addresses key trends Cloud Big data Mobility Security Management Security 3 Software We deliver security
Network Security Solution Arktos Lam Dell Software Group(DSG) 2 Confidential Trend Dell Software addresses key trends Cloud Big data Mobility Security Management Security 3 Software We deliver security
WildFire. Preparing for Modern Network Attacks
 WildFire WildFire automatically protects your networks from new and customized malware across a wide range of applications, including malware hidden within SSL-encrypted traffic. WildFire easily extends
WildFire WildFire automatically protects your networks from new and customized malware across a wide range of applications, including malware hidden within SSL-encrypted traffic. WildFire easily extends
DDoS Protection on the Security Gateway
 DDoS Protection on the Security Gateway Best Practices 24 August 2014 Protected 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by
DDoS Protection on the Security Gateway Best Practices 24 August 2014 Protected 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by
Symantec Enterprise Firewalls. From the Internet Thomas Jerry Scott
 Symantec Enterprise Firewalls From the Internet Thomas Symantec Firewalls Symantec offers a whole line of firewalls The Symantec Enterprise Firewall, which emerged from the older RAPTOR product We are
Symantec Enterprise Firewalls From the Internet Thomas Symantec Firewalls Symantec offers a whole line of firewalls The Symantec Enterprise Firewall, which emerged from the older RAPTOR product We are
How To Choose A Network Firewall
 Critical Considerations in Choosing a Network Firewall Version 5.4.3 July 2014 Why today s Firewalls are broken Visibility No visibility into user behavior No control over applications Manageability No
Critical Considerations in Choosing a Network Firewall Version 5.4.3 July 2014 Why today s Firewalls are broken Visibility No visibility into user behavior No control over applications Manageability No
Sophos XG Firewall v 15.01.0 Release Notes. Sophos XG Firewall Reports Guide v15.01.0
 Sophos XG Firewall v 15.01.0 Release Notes Sophos XG Firewall Reports Guide v15.01.0 For Sophos and Cyberoam Customers Document Date: November 2015 Contents 2 Contents Reports... 4 Basics...4 Reports Navigation...
Sophos XG Firewall v 15.01.0 Release Notes Sophos XG Firewall Reports Guide v15.01.0 For Sophos and Cyberoam Customers Document Date: November 2015 Contents 2 Contents Reports... 4 Basics...4 Reports Navigation...
Hillstone Intelligent Next Generation Firewall
 Hillstone Intelligent Next Generation Firewall Kris Nawani Solution Manager (Thailand) 12 th March 2015 1 About Hillstone Networks Founded 2006 by Netscreen visionaries World class team with security,
Hillstone Intelligent Next Generation Firewall Kris Nawani Solution Manager (Thailand) 12 th March 2015 1 About Hillstone Networks Founded 2006 by Netscreen visionaries World class team with security,
Advantages of Consolidating Network Security with Wireless for Small & Mid-Size Businesses
 Advantages of Consolidating Network Security with Wireless for Small & Mid-Size Businesses Patrick Bedwell VP, Product Marketing 1 Copyright 2014 Fortinet Inc. All rights reserved. Today s Agenda Security
Advantages of Consolidating Network Security with Wireless for Small & Mid-Size Businesses Patrick Bedwell VP, Product Marketing 1 Copyright 2014 Fortinet Inc. All rights reserved. Today s Agenda Security
Assuring Your Business Continuity
 Assuring Your Business Continuity Q-Balancer Range Offering Business Continuity, Productivity, and Security Q-Balancer is designed to offer assured network connectivity to small and medium business (SME)
Assuring Your Business Continuity Q-Balancer Range Offering Business Continuity, Productivity, and Security Q-Balancer is designed to offer assured network connectivity to small and medium business (SME)
NetDefend Firewall UTM Services
 Product Highlights Intrusion Prevention System Dectects and prevents known and unknown attacks/ exploits/vulnerabilities, preventing outbreaks and keeping your network safe. Gateway Anti Virus Protection
Product Highlights Intrusion Prevention System Dectects and prevents known and unknown attacks/ exploits/vulnerabilities, preventing outbreaks and keeping your network safe. Gateway Anti Virus Protection
REVOLUTIONIZING ADVANCED THREAT PROTECTION
 REVOLUTIONIZING ADVANCED THREAT PROTECTION A NEW, MODERN APPROACH Blue Coat Advanced Threat Protection Group GRANT ASPLUND Senior Technology Evangelist 1 WHY DO I STAND ON MY DESK? "...I stand upon my
REVOLUTIONIZING ADVANCED THREAT PROTECTION A NEW, MODERN APPROACH Blue Coat Advanced Threat Protection Group GRANT ASPLUND Senior Technology Evangelist 1 WHY DO I STAND ON MY DESK? "...I stand upon my
INTRODUCING KERIO WINROUTE FIREWALL
 KERIO TECHNOLOGIES, INC. KERIO WINROUTE FIREWALL 6.1 REVIEWER S GUIDE JUNE 2005 WHAT IS KERIO? Kerio Technologies, Inc. provides Internet messaging and firewall software solutions for small to medium sized
KERIO TECHNOLOGIES, INC. KERIO WINROUTE FIREWALL 6.1 REVIEWER S GUIDE JUNE 2005 WHAT IS KERIO? Kerio Technologies, Inc. provides Internet messaging and firewall software solutions for small to medium sized
Fortinet Advanced Threat Protection- Part 3
 Fortinet Advanced Threat Protection- Part 3 Upgrading Your Endpoint Security to Meet Advanced Threats Copyright Fortinet Inc. All rights reserved. Agenda Brief Recap on Breaches and the Need for Advanced
Fortinet Advanced Threat Protection- Part 3 Upgrading Your Endpoint Security to Meet Advanced Threats Copyright Fortinet Inc. All rights reserved. Agenda Brief Recap on Breaches and the Need for Advanced
Delphi 9.5.3 System Requirements
 Market Intelligence Enterprise Business Management Sales & Catering Distribution & Content Delphi 9.5.3 System Requirements Revision 1.3 November 1, 2011 Delphi 9.5.3 System Requirements Users Server Hardware
Market Intelligence Enterprise Business Management Sales & Catering Distribution & Content Delphi 9.5.3 System Requirements Revision 1.3 November 1, 2011 Delphi 9.5.3 System Requirements Users Server Hardware
Huawei Eudemon200E-N Next-Generation Firewall
 Huawei 200E-N Next-Generation Firewall With the popularity of mobile working using smartphones and tablets, mobile apps, Web2.0, and social networking become integral parts of works. This change in IT
Huawei 200E-N Next-Generation Firewall With the popularity of mobile working using smartphones and tablets, mobile apps, Web2.0, and social networking become integral parts of works. This change in IT
Data Sheet: Messaging Security Symantec Brightmail Gateway Award-winning messaging security for inbound protection and outbound control
 Award-winning messaging security for inbound protection and outbound control Overview The delivers inbound and outbound messaging security for email and IM, with effective and accurate antispam and antivirus
Award-winning messaging security for inbound protection and outbound control Overview The delivers inbound and outbound messaging security for email and IM, with effective and accurate antispam and antivirus
CHECK POINT. Software Blade Architecture. Secure. Flexible. Simple.
 CHECK POINT Software Blade Architecture Secure. Flexible. Simple. softwareblades from Check Point Today s Security Challenge Protecting networks against today s constantly evolving threat environment has
CHECK POINT Software Blade Architecture Secure. Flexible. Simple. softwareblades from Check Point Today s Security Challenge Protecting networks against today s constantly evolving threat environment has
ΕΠΛ 674: Εργαστήριο 5 Firewalls
 ΕΠΛ 674: Εργαστήριο 5 Firewalls Παύλος Αντωνίου Εαρινό Εξάμηνο 2011 Department of Computer Science Firewalls A firewall is hardware, software, or a combination of both that is used to prevent unauthorized
ΕΠΛ 674: Εργαστήριο 5 Firewalls Παύλος Αντωνίου Εαρινό Εξάμηνο 2011 Department of Computer Science Firewalls A firewall is hardware, software, or a combination of both that is used to prevent unauthorized
Appliance Comparison Chart
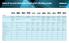
 Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
E-Guide. Sponsored By:
 Security and WAN optimization: Getting the best of both worlds E-Guide As the number of people working outside primary office locations increases, the challenges surrounding security and optimization are
Security and WAN optimization: Getting the best of both worlds E-Guide As the number of people working outside primary office locations increases, the challenges surrounding security and optimization are
