Identity Management Planning: Best Practices, Insights and Recommendations
|
|
|
- Britney George
- 8 years ago
- Views:
Transcription
1 Technical White Paper IDENTITY MANAGEMENT AND SECURITY Identity Management Planning: Best Practices, Insights and Recommendations
2 Identity Management Planning: Best Practices, Insights and Recommendations Table of Contents: Why Identity Management Best Practice Planning? Stages of Identity Management (IDM) Maturity Categories of Identity Management Best Practice 4... Best Practice 1: Identity Strategy and Organizational Positioning 5... Best Practice 2: Future-state Identity Services Architecture Definition 7... Best Practice 3: Best-in-class Identity Services Technologies and Functionality 10.. Best Practice 4: Business Benefit Definition and Quantification 11.. Best Practice 5: Identity Services Initiative Roadmapping 12.. Best Practice 6: Planning for Implementation Competence 12.. Best Practice 7: Identity Services Governance Conclusion p. 1
3 Why Identity Management Best Practice Planning? Best Practice IDM Planning The organizations that are most successful with identity management are those that follow best practice methods and approaches in their planning of identity technology initiatives. Authored by: John H. Dobbs Principal Strategist Novell Worldwide Services Given its complexity, breadth, implications and importance, the phrase don t attempt this at home might well apply to identity management deployment. But the truth is most organizations today don t have much choice other than to proceed. The privacy, security, compliance and business governance challenges that many organizations face today make identity programs essential. Add to this the potential to create business value by improving efficiencies and automating business processes, and there is more than ample justification for investing in identity management (IDM). As the famous philosopher, Yogi Berra, once said, When you come to a fork in the road, take it. There are many forks in the road along the path to an identity management solution, represented by a host of decisions that must be made in order to deploy successfully as well as to gain the available business benefits. The limited length of this paper does not permit discussion of the many possible areas of identity management best practice. Instead we will attempt to create awareness of the IDM best practice planning areas that we consider essential. In the process, we will describe how these planning factors can account for differences between leading and below average identity programs. Where practical, we will illustrate some of these factors with examples, criteria and suggested approaches. Our goal is simply to inform decision-makers and sponsors of enterprise-grade identity management (or for short, IDM) programs about the benefits of best practice identity management planning and increase awareness of the associated (and unfortunately not-so-obvious) pitfalls of failing to do so. Our experience (formed while working with literally hundreds of IDM clients) reveals that the organizations that are most successful with identity management are those that follow best practice methods and approaches in their planning of identity technology initiatives. Best practice is easily aspired to, but is fairly difficult to accomplish for a variety of reasons. Two key reasons are: first, identity management touches so many parts of the organization, within IT and beyond; and, second, IDM must integrate with diverse areas and components of the technical infrastructure. These two realities can make it difficult to create the support and degree of consensus required for a successful identity management program. These two issues aside, there are many other challenges that necessitate best practice planning. A working definition of identity management best practice may be helpful at this point: Methods, approaches and capabilities that are leading edge and/or that maximize the probability of successful identity and security management program implementation and business benefit capture. p. 2
4 Identity Management Planning: Best Practices, Insights and Recommendations Stages of Identity Management (IDM) Maturity Although best practice identity management is a desirable goal, it is a status that can realistically be achieved only in stages. That is, the level of IDM maturity at which the organization finds itself in essence determines the degree of best practice that can be expected and experienced at that stage of program maturity. For example, an organization just beginning to deploy an IDM infrastructure will not and cannot have the IDM capabilities of an organization that has achieved a more advanced degree of IDM maturity. That being said, using best practice approaches and technology early on greatly affects an organization s ability to achieve best practice capabilities in subsequent stages of maturity. The Identity Services Maturity Continuum shown below illustrates typical enterprise capabilities by stage. It is primarily during the enhanced and advanced maturity stages of IDM deployment that organizations will realize the significant ROI that can come from identity technologies. Stages of Identity Management Maturity At the beginning of 2008 we estimate that most organizations (50 percent or so) are still in the basic-foundational stages of IDM deployment, while only 30 percent are in the enhanced or advanced stages. Some have yet to begin in any serious way with a real program. This is a meaningful observation because it is primarily during the enhanced and advanced maturity stages of IDM deployment that organizations will realize the significant ROI that can come from identity technologies. So the challenge is to move adroitly from basic to enhanced, and then to advanced maturity stages. While that may seem logical, in practice moving from one stage to the next can be daunting. Our experience has shown that a reliable predictor of such progress is the observability of multiple best practice techniques and approaches during both planning and deployment of IDM capabilities. p. 3
5 An Identity Services strategy considers many ways the business will leverage and benefit from its IDM infrastructure, including physical security, logical security, asset accountability, compliance, risk mitigation, partner enablement and so on. Categories of Identity Management Best Practice Our experience with IDM initiatives has revealed seven basic categories of best practice planning to be aware of throughout all stages of program maturity: 1. Identity strategy and organizational positioning 2. Future-state identity services architecture definition 3. Best-in-class identity services technologies and functionality 4. Business benefit definition and quantification 5. Identity services initiative roadmapping 6. Planning for implementation competence 7. Identity services governance Each of these categories can by itself make a difference in the quality and success of an IDM deployment. But taken together, achieving best practice in all of these seven areas has tremendous potential to impact the outcome of any IDM program. Best Practice 1: Identity Strategy and Organizational Positioning Identity management initiatives frequently suffer from a lack of broad organizational understanding and support. The reasons for this typically include one or more of the following: Lack of education about identity-related technologies and capabilities Poor understanding of program benefits Point solutions being pursued (rather than enterprise enablement) IT sponsorship vs. business sponsorship Lack of realistic business case to justify investments; lack of budget Reluctance of some system/data owners Slow deployment; failure to show rapid value or benefit capture Technical complexity and IDM software product issues Divided opinions about technology/ vendor selection A key issue is often that an enterprise-wide executive level understanding of how identity management will add value to the business does not exist. Frequently, IT or IT security functions begin deploying limited IDM capabilities that benefit their functions, such as user directory integration or automated account creation, but that do not necessarily benefit the business as a whole. Another example is when the finance/audit department wants the capability to monitor access, but few if any other areas of the business will benefit. These are hard problems that most organizations we ve worked with have had to address. What works is a well-defined identity strategy that takes these problems into account ahead of time. It s also useful to always keep the big picture of benefits and capabilities in view; that way the inevitable challenges that arise are kept in context. Rather than focusing on just one or two favored point solutions, it s best to define a more comprehensive, enterprise-level identity services program and strategy. An identity services strategy recognizes and plans for a full range of identity capabilities that will drive benefits across multiple areas of the business, thus creating support for an initiative that can be positioned in a more strategic, value-producing way. p. 4
6 Identity Management Planning: Best Practices, Insights and Recommendations Identity Services A Best Practice Enterprise-level Value Proposition for IDM An identity services strategy considers many ways the business will leverage and benefit from its IDM infrastructure, including physical security, logical security, asset accountability, compliance, risk mitigation, partner enablement and so on. Because of this broader range of potential capabilities and benefits, a certain amount of internal education is usually necessary to help key stakeholders understand how foundational an identity management infrastructure can be to the business. In fact, an identity management foundation is fundamental to support and enable security, and to risk management, compliance and governance programs of all types. As an understanding of these critical capabilities develops, broader support for identity management also occurs. And, even if budgets are small, or the organization wants to proceed cautiously with identity management, defining enterpriselevel value and strategies up front is highly beneficial to avoid stalling out as the IDM initiative progresses. Best Practice 2: Future-state Identity Services Architecture Definition Many organizations have embarked on identity management initiatives and projects without understanding the implications for their larger enterprise infrastructure and architecture. This is especially common in organizations where limited function or point solutions are deployed. Repercussions of deploying without architecting include the potential for implementing technologies that are not standards based (and therefore do not integrate properly with future infrastructure elements), or selecting technologies that will not interoperate with all required existing systems successfully. Best practice, on the other hand, means defining and documenting both a shortterm and a longer-term, future-state identity p. 5
7 A best practice, futurestate identity services architecture generally conforms to multiple desired architectural characteristics: Service oriented Standards based Flexible and interoperable Loosely coupled Secure Appropriately redundant Scalable Efficient architecture for the enterprise. This proactively created future architecture should be identity services comprehensive, incorporating but not necessarily limited to the following: HR systems Service directories Metadirectory, or identity vault Access management system Identity management provisioning system system File and print services Network; intranet Remote access Telephone system Mainframes Badge system for physical facilities access Databases Helpdesk system ERP systems Document management system Roles management system Portals, and so on The future-state architecture should define how the identity services infrastructure will integrate with each of these systems as well as any other systems that will be authoritative for identity attributes. The architecture will define how the various systems will synchronize, protect and audit identity data. A best practice, future-state identity services architecture generally conforms to multiple desired architectural characteristics, including: Service oriented Standards based Flexible and interoperable Loosely coupled Secure Appropriately redundant Scalable Efficient A best practice identity services architecture is designed in such a way as to accommodate immediate needs and enable short-term identity and security functionality requirements. But its design must also anticipate and provide for future capabilities (both known and unknown) as well as acknowledge the need for growth and scalability over time. Among the identity-related capabilities to be enabled by the architecture are: Centralized identity store or metadirectory Identity data synchronization Reduced or single sign-on Distributed ownership of identity data and permissions Automated provisioning Roles-based provisioning Workflow-based provisioning Integrated physical and logical access control Policy-based roles management Identity federation Compliance monitoring and reporting Zero-day start; zero-day stop Among architectural best practices, key (and frequently overlooked) is the design and deployment of a centralized identity vault that functions as the hub of a wellplanned hub and spoke directory architecture. The identity vault is the central nervous system or metadirectory that synchronizes and manages identity attributes from other authoritative, trusted sources and shares them with other consuming directories and applications. This is the foundational element of an identity services infrastructure. In its absence, deploying advanced identityrelated capabilities becomes problematic. A best practice identity architecture is service-oriented, meaning that identity capabilities such as those mentioned p. 6
8 Identity Management Planning: Best Practices, Insights and Recommendations previously are available to the enterprise as a service that is accessible to a variety of applications, systems and user constituencies. It is this service orientation that accounts for many of the business efficiencies that can be accomplished by a well-designed identity services infrastructure. For some organizations, deploying a serviceoriented identity services architecture is a logical step toward SOA (service oriented architectures) in general, because the identity architecture can be a good example of how SOA should work. Best Practice 3: Best-in-class Identity Services Technologies and Functionality Best-in-class technologies are in and of themselves best practice when it comes to designing identity management solutions. IT departments often start down the path of IDM deployment using the technologies they are most familiar with only to realize later that the products selected are not capable of the functionality that is needed in subsequent phases. Or they find that the products selected initially do not integrate well with other systems or won t scale as required. These organizations then hit the wall and stall in their effort to move from the basic to more advanced stages of IDM maturity where more visible benefits and ROI occur. This problem can be averted by choosing best-in-class technologies. When scanning for best-in-class IDM technology components, Gartner s Leaders Quadrant evaluations are a good place to begin identification of potentially useful identity and security-related technologies. But the Gartner criteria of ability to execute and completeness of vision are a bit too high level to compare against specific business needs. In our experience, best-in-class technologies or products will exhibit several or preferably all of these characteristics: 1. Unique or superior functionality when compared with other products 2. Ease or simplicity of integration; less need for customization 3. High levels of interoperability with other solution components and/or connected systems 4. Ability to scale to meet future needs or requirements, known or unknown 5. Low cost of ongoing use These criteria should be considered when choosing between commercially available software or when having custom or internally developed technologies designed. In a best practice identity services infrastructure, the full range of needed identity infrastructure components should be evaluated by applying the best-in-class technology characteristics cited previously. Components to consider include: Metadirectory Log-in management Access management Identity management and provisioning Roles management Logging, auditing, reporting (compliance) To provide an illustration of a technology comparison analysis, the metadirectory component is used as an example for comparing multiple directory products. In our example, specific product/technology characteristics and capabilities are judged to be either: 1. Best in Class (or advanced) 2. At Parity with capabilities exhibited by products in this category 3. Lagging compared with capabilities exhibited by products in this category p. 7
9 Metadirectories: Key Functionality/Capability Analysis This type of analysis can be done for the characteristics of each component of the practice infrastructure. Of course, IDM functionality requirements vary from one organization to another. For example, federation of partner or other external identities from a trusted source may be critical to some organizations, but not others. Likewise, if future plans and needs do not include managing and storing identities of large numbers of customers or physical assets, scalability may not be as important. Another factor to consider when selecting technology is that some vendors have assembled their IDM technology components from acquisitions rather than developing them internally. This means that although the various components may perform well separately, when integrated together they either do not perform well, are costly to integrate or both. When analyzing technologies, role-based access control as well as audit/compliance technologies merit special mention because so few organizations have achieved mature capability in these areas. Role-Based Access Control Capability In organizations that are more advanced with identity programs, there is rapidly increasing interest in role-based access control (RBAC). RBAC is an approach to policy-driven user provisioning and access control. It is important because it improves p. 8
10 Identity Management Planning: Best Practices, Insights and Recommendations security and compliance, while at the same time reducing IT administration costs. RBAC capability is becoming more common within application suites. Major application vendors such as SAP and Oracle are already using RBAC to manage user access rights within the scope of their applications. However, the real enterprise transforming potential of RBAC is its ability to manage access rights, or permissions, across many applications. The same RBAC process that controls access to the corporate network can also manage the provisioning of cell phones or building access cards. RBAC offers greater business benefit as an enterprise-wide identity service than as an application-specific one. Best practice RBAC initiatives include the analysis and definition of roles from both a top-down (enterprise level) and a bottom-up (user group) perspective. Why? Because existing organization roles may be at too high a level or be too poorly defined to function properly in an RBAC environment. The goal is to define the minimal, simplest set of roles that will correctly provision users with all the access rights they require and are authorized to have, but no more. Best practice methodology will create neither too few nor too many roles. Some organizations have ended up with more roles than they have jobs! Best practice RBAC also requires meaningful coordination between stakeholders IT, security, compliance, application owners and business managers. A recent study by Ponemon Institute shows that these groups rarely coordinate. In fact, 86 percent of organizations surveyed still audit user access and permissions manually at only the departmental or application level. Integrated IDM and Security Information and Event Management Systems In today s enterprise there is an inordinate emphasis on compliance with government regulations (such as PCI, HIPAA, SOX, GLBA, FISMA and so on), not to mention the numerous governance requirements imposed internally. In most organizations the technologies that enable compliancerelated tasks and activities such as monitoring, logging and reporting of security events operate completely separately from the identity management infrastructure. In a best practice identity environment, the identity and security systems are integrated to enable a more robust set of compliance capabilities. These capabilities are able to reliably detect and take action on issues such as: Separation of duties violations Unauthorized system administrator activity User provisioning violations Critical file access violations Exploit detection Real-time attack detection Unauthorized access Business policy violations, and so on In best practice environments, organizations can leverage their RBAC and integrated security monitoring capabilities (based on policy) to detect, report and remediate separation of duties issues as well as a wide range of other security risks and violations. p. 9
11 Best Practice 4: Business Benefit Definition and Quantification A frequent barrier to adoption of identity management within organizations is the absence of a clear business case that defines and quantifies the financial benefits of identity initiatives in a format that is meaningful and persuasive to key executives. In the absence of clear financial data, executives tend to view IDM initiatives strictly as a cost issue, rather than as an ROI-producing activity. For this reason, best practice IDM planning includes development of an organization-specific business case that considers all relevant costs and benefits associated with the initiative. A thorough business benefit analysis for IDM focuses not just on benefits that accrue to the IT and security functions, but also identifies benefits that are achievable within business operating units. This means that business initiatives that could potentially benefit from identity services enablement should be investigated to determine the financial value of such enablement. For example, in a large benefits management company, the identity services solution is being used to dramatically shorten the time required to reassign and reprovision client data access for customer service personnel. At the same time it is also validating the security clearance of these representatives so as not to violate client confidentiality commitments. This secure, automated access provisioning capability has delivered considerable financial benefit to the business unit. Of course, not all business benefits are quantifiable, so it is also reasonable and appropriate to include such benefits as user satisfaction or time savings in the analysis, even if they are not quantifiable. Security and risk mitigation benefits can also be difficult to quantify. The analysis can be segmented into quantifiable and nonquantifiable benefits, but it is the quantifiable side that most interests business sponsors. These quantifiable benefits typically include reduced manual administrative burdens, increased speed to productivity for employees being provisioned with access rights, decreased licensing costs as unnecessary users are deprovisioned, reduced application development costs due to reusable security and access controls, and cost avoidance from better management of assets such as computers, cell phones and so on. A well-implemented identity services initiative is capable of delivering meaningful benefits in a combination of ways, such as: Cost avoidance (reducing planned future expenditures) Cost reduction (reducing existing costs) Time, productivity and process improvements User convenience and satisfaction and complaint reduction Sales and revenue improvement (customer facing initiatives) Security and compliance enhancement The key is to understand which benefits in each of these categories apply to specific user groups, functions or business units across the enterprise. Then you can calculate the magnitude of the financial benefit over time. An analysis of the business value generated across multiple organizations implementing identity services showed a three-year net present value (NPV) of US$1,349 per employee. IDC estimates an average annual savings of US$60,210 per 100 users from deploying identity and security management solutions. It should be acknowledged that the financial benefit of identity services initiatives can vary widely, depending on an organization s size, existing technical environment, program p. 10
12 Identity Management Planning: Best Practices, Insights and Recommendations objectives and so on. This is another reason for validating your organization s specific business case for identity management. Best Practice 5: Identity Services Initiative Roadmapping There are typically multiple identity initiatives or projects that need to be implemented once an overall identity strategy has been defined and the business benefits have been established. Experience has shown that there is normally uncertainty (or even internal competition) about the priorities of these initiatives. For example, should technical considerations or business needs drive implementation sequencing? Best practice for these decisions is represented by an identity services deployment roadmap. Considering business need, business value, technical dependencies and prerequisites, resource availability, budgets and other factors, an implementation roadmap should be developed that defines the preferred, optimal and agreed upon path forward for identity program implementation. The identity services roadmap becomes the agreed plan for implementing the future-state identity architecture over time as outlined previously in this white paper. The roadmap is typically laid out for an month period. Once finalized, it serves as the guidepost against which more detailed planning can be done and implementation progress can be monitored. Because identity programs touch so many of the organization s systems, the roadmap becomes a valuable planning and communications tool for all those involved, as well as a coordination mechanism for avoiding duplication of effort and overlapping technologies. While deployment roadmaps look quite different from one organization to another, this example is typical for an early stage implementation. Identity Services Roadmap Example p. 11
13 The roadmap illustrates the need for a phased implementation that is orchestrated in order to optimize both resources and results. Best practice means that the roadmap is revisited and updated every six to 12 months in order to keep the deployment plan up-todate and aligned with actual events and program progress. Best Practice 6: Planning for Implementation Competence Although thoughtful planning and roadmapping are key predictors of success, they don t guarantee successful implementation. The breadth and depth of coordination required to successfully implement IDM capabilities demands strong program management skills and tools. Typically, IDM implementations are characterized by multiple tracks or projects being underway simultaneously, with numerous interdependencies. This requires implementation oversight and coordination beyond management of discrete projects. Organizations need to view IDM implementations as a program with the necessary levels of visibility and authority to span multiple projects. Competent implementation means that the individuals responsible for deploying IDM capabilities are appropriately skilled in their new roles and technologies. This may require that skills assessments and corresponding training plans be in place early, well before any advanced identity services capabilities are scheduled to go live. Implementation competence also means addressing business process change and technology change in parallel, not as separate issues. Best Practice 7: Identity Services Governance The very same issues that make identity initiatives difficult to advance in organizations (for example, many organizational areas being affected and involved; a large number of systems to integrate) make it necessary to provide governance to guide the overall program, ensuring that it is properly sponsored and managed. At its most basic, governance means creating the structure, processes and policies required to keep the initiative in line with the organization s expectations and plans. Governance provides appropriate oversight, ensuring steady, coordinated progress. It will also provide a mechanism for cross-functional involvement and decision making. What takes governance beyond the realm of traditional program management is its ongoing nature and its focus on continuous improvement. At a practical level, there are varied constituencies (as well as risks) that need to be considered as part of an identity services governance plan. Best practice identity governance is a priority from the beginning and is ongoing. Governance must focus on both the business and technology domains of the identity equation. Representative issues and topics are illustrated in the following illustration: p. 12
14 Identity Management Planning: Best Practices, Insights and Recommendations Identity Services Governance A best practice starting point for good IDM governance involves articulation and communication of guiding principles for enterprise identity programs. Among other things, these principles convey the necessity for consistency and standards they suggest important do s and don ts. Examples of a few selected guiding principles from actual companies are illustrated here: Guiding Principles for Enterprise Identity Services In our business, the identity management system manages the identities of multiple entities including humans, computers, mobile devices, network elements, applications, and other physical and intellectual assets. Every entity shall have a unique identifier that does not change over time. A well defined, single, logical identity repository shall contain the gold copy of all identity information that is in turn updated solely by trusted, authoritative sources. The business processes that create or change the status of an entity result in the automatic updating and synchronization of identity information. All internally developed and externally sourced applications will be LDAPcompliant and leverage the shared enterprise identity infrastructure, rather than relying on application-specific authentication methods. The identity infrastructure provides meaningful reports on auditable identity events as required for compliance purposes. The identity management infrastructure is sufficiently flexible and interoperable to support a heterogeneous environment. The identity solution is loosely coupled, ensuring no single point of failure. The identity infrastructure is based on service oriented architecture principles. p. 13
15 The best, most effective identity management programs will be those that benefit from best practice planning approaches. Conclusion Identity services deployment is a challenging journey for any organization, but it is a journey made considerably less risky and with eminently more impact when undertaken in a well-orchestrated manner. Our experience convinces us that shortcutting the IDM planning disciplines described here frequently results in less than desired rates of progress toward the more advanced stages of program maturity and resulting ROI. We assert with considerable confidence that the best, most effective identity management programs will be those that benefit from best practice planning approaches. Contact your local Novell Solutions Provider, or call Novell at: U.S./Canada Worldwide Facsimile Novell, Inc. 404 Wyman Street Waltham, MA USA / Novell, Inc. All rights reserved. Novell, the Novell logo and the N logo are registered trademarks of Novell, Inc. in the United States and other countries. *All third-party trademarks are the property of their respective owners.
IDENTITY MANAGEMENT AND WEB SECURITY. A Customer s Pragmatic Approach
 IDENTITY MANAGEMENT AND WEB SECURITY A Customer s Pragmatic Approach AGENDA What is Identity Management (IDM) or Identity and Access Management (IAM)? Benefits of IDM IDM Best Practices Challenges to Implement
IDENTITY MANAGEMENT AND WEB SECURITY A Customer s Pragmatic Approach AGENDA What is Identity Management (IDM) or Identity and Access Management (IAM)? Benefits of IDM IDM Best Practices Challenges to Implement
The Unique Alternative to the Big Four. Identity and Access Management
 The Unique Alternative to the Big Four Identity and Access Management Agenda Introductions Identity and Access Management (I&AM) Overview Benefits of I&AM I&AM Best Practices I&AM Market Place Closing
The Unique Alternative to the Big Four Identity and Access Management Agenda Introductions Identity and Access Management (I&AM) Overview Benefits of I&AM I&AM Best Practices I&AM Market Place Closing
5 Steps to Choosing the Right BPM Suite
 5 Steps to Choosing the Right BPM Suite BPM Suites can deliver significant business benefits and a fast ROI but only if you choose the right one By Laura Mooney, Metastorm Copyright 2009, Metastorm Inc.
5 Steps to Choosing the Right BPM Suite BPM Suites can deliver significant business benefits and a fast ROI but only if you choose the right one By Laura Mooney, Metastorm Copyright 2009, Metastorm Inc.
Achieving Regulatory Compliance through Security Information Management
 www.netforensics.com NETFORENSICS WHITE PAPER Achieving Regulatory Compliance through Security Information Management Contents Executive Summary The Compliance Challenge Common Requirements of Regulations
www.netforensics.com NETFORENSICS WHITE PAPER Achieving Regulatory Compliance through Security Information Management Contents Executive Summary The Compliance Challenge Common Requirements of Regulations
OPTIMUS SBR. Optimizing Results with Business Intelligence Governance CHOICE TOOLS. PRECISION AIM. BOLD ATTITUDE.
 OPTIMUS SBR CHOICE TOOLS. PRECISION AIM. BOLD ATTITUDE. Optimizing Results with Business Intelligence Governance This paper investigates the importance of establishing a robust Business Intelligence (BI)
OPTIMUS SBR CHOICE TOOLS. PRECISION AIM. BOLD ATTITUDE. Optimizing Results with Business Intelligence Governance This paper investigates the importance of establishing a robust Business Intelligence (BI)
The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into
 The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material,
The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material,
THE NEXT GENERATION OF HR SHARED SERVICES SUBHEADLINE RUNS HERE AND HERE AND HERE AND HERE
 THE NEXT GENERATION OF HR SHARED SERVICES SUBHEADLINE RUNS HERE AND HERE AND HERE AND HERE SAP Executive Insight It s no secret that implementing HR shared services can help organizations generate significant
THE NEXT GENERATION OF HR SHARED SERVICES SUBHEADLINE RUNS HERE AND HERE AND HERE AND HERE SAP Executive Insight It s no secret that implementing HR shared services can help organizations generate significant
How To Buy Nitro Security
 McAfee Acquires NitroSecurity McAfee announced that it has closed the acquisition of privately owned NitroSecurity. 1. Who is NitroSecurity? What do they do? NitroSecurity develops high-performance security
McAfee Acquires NitroSecurity McAfee announced that it has closed the acquisition of privately owned NitroSecurity. 1. Who is NitroSecurity? What do they do? NitroSecurity develops high-performance security
Agile Master Data Management A Better Approach than Trial and Error
 Agile Master Data Management A Better Approach than Trial and Error A whitepaper by First San Francisco Partners First San Francisco Partners Whitepaper Executive Summary Market leading corporations are
Agile Master Data Management A Better Approach than Trial and Error A whitepaper by First San Francisco Partners First San Francisco Partners Whitepaper Executive Summary Market leading corporations are
Vermont Enterprise Architecture Framework (VEAF) Master Data Management (MDM) Abridged Strategy Level 0
 Vermont Enterprise Architecture Framework (VEAF) Master Data Management (MDM) Abridged Strategy Level 0 EA APPROVALS EA Approving Authority: Revision
Vermont Enterprise Architecture Framework (VEAF) Master Data Management (MDM) Abridged Strategy Level 0 EA APPROVALS EA Approving Authority: Revision
Provide access control with innovative solutions from IBM.
 Security solutions To support your IT objectives Provide access control with innovative solutions from IBM. Highlights Help protect assets and information from unauthorized access and improve business
Security solutions To support your IT objectives Provide access control with innovative solutions from IBM. Highlights Help protect assets and information from unauthorized access and improve business
Oracle s Primavera P6 Enterprise Project Portfolio Management
 Oracle s Primavera P6 Enterprise Project Portfolio Management Oracle s Primavera P6 Enterprise Project Portfolio Management is the most powerful, robust and easy-to-use solution for prioritizing, planning,
Oracle s Primavera P6 Enterprise Project Portfolio Management Oracle s Primavera P6 Enterprise Project Portfolio Management is the most powerful, robust and easy-to-use solution for prioritizing, planning,
The following is intended to outline our general product direction. It is intended for informational purposes only, and may not be incorporated into
 The following is intended to outline our general product direction. It is intended for informational purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any
The following is intended to outline our general product direction. It is intended for informational purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any
Maximizing enterprise resource planning ROI: A guide for midsize companies
 IBM Global Business Services Thought Leadership White Paper April 2010 Maximizing enterprise resource planning ROI: A guide for midsize companies 2 Maximizing enterprise resource planning ROI: A guide
IBM Global Business Services Thought Leadership White Paper April 2010 Maximizing enterprise resource planning ROI: A guide for midsize companies 2 Maximizing enterprise resource planning ROI: A guide
How To Improve Your Business
 IT Risk Management Life Cycle and enabling it with GRC Technology 21 March 2013 Overview IT Risk management lifecycle What does technology enablement mean? Industry perspective Business drivers Trends
IT Risk Management Life Cycle and enabling it with GRC Technology 21 March 2013 Overview IT Risk management lifecycle What does technology enablement mean? Industry perspective Business drivers Trends
www.em-i.com Dr. Donn Di Nunno
 GOVERNANCE AND TECHNOLOGY CONSULTING W H I T E P A P E R www.em-i.com Business Solutions That Raise Performance Outcomes Written By: Dr. Donn Di Nunno Engineering, Management & Integration, Inc. 455 Spring
GOVERNANCE AND TECHNOLOGY CONSULTING W H I T E P A P E R www.em-i.com Business Solutions That Raise Performance Outcomes Written By: Dr. Donn Di Nunno Engineering, Management & Integration, Inc. 455 Spring
Identity and Access Management Point of View
 Identity and Access Management Point of View Agenda What is Identity and Access Management (IAM)? Business Drivers and Challenges Compliance and Business Benefits IAM Solution Framework IAM Implementation
Identity and Access Management Point of View Agenda What is Identity and Access Management (IAM)? Business Drivers and Challenges Compliance and Business Benefits IAM Solution Framework IAM Implementation
Pragmatic Business Service Management
 Pragmatic Business Service Management Written by Quest Software, Inc. White Paper Copyright Quest Software, Inc. 2007. All rights reserved. This guide contains proprietary information, which is protected
Pragmatic Business Service Management Written by Quest Software, Inc. White Paper Copyright Quest Software, Inc. 2007. All rights reserved. This guide contains proprietary information, which is protected
Adopting Service Oriented Architecture increases the flexibility of your enterprise
 Adopting Service Oriented Architecture increases the flexibility of your enterprise Shireesh Jayashetty, Pradeep Kumar M Introduction Information Technology (IT) systems lasted longer earlier. Organization
Adopting Service Oriented Architecture increases the flexibility of your enterprise Shireesh Jayashetty, Pradeep Kumar M Introduction Information Technology (IT) systems lasted longer earlier. Organization
Vermont Enterprise Architecture Framework (VEAF) Identity & Access Management (IAM) Abridged Strategy Level 0
 Vermont Enterprise Architecture Framework (VEAF) Identity & Access Management (IAM) Abridged Strategy Level 0 EA APPROVALS EA Approving Authority: Revision
Vermont Enterprise Architecture Framework (VEAF) Identity & Access Management (IAM) Abridged Strategy Level 0 EA APPROVALS EA Approving Authority: Revision
White Paper Achieving GLBA Compliance through Security Information Management. White Paper / GLBA
 White Paper Achieving GLBA Compliance through Security Information Management White Paper / GLBA Contents Executive Summary... 1 Introduction: Brief Overview of GLBA... 1 The GLBA Challenge: Securing Financial
White Paper Achieving GLBA Compliance through Security Information Management White Paper / GLBA Contents Executive Summary... 1 Introduction: Brief Overview of GLBA... 1 The GLBA Challenge: Securing Financial
Enterprise Data Governance
 DATA GOVERNANCE Enterprise Data Governance Strategies and Approaches for Implementing a Multi-Domain Data Governance Model Mark Allen Sr. Consultant, Enterprise Data Governance WellPoint, Inc. 1 Introduction:
DATA GOVERNANCE Enterprise Data Governance Strategies and Approaches for Implementing a Multi-Domain Data Governance Model Mark Allen Sr. Consultant, Enterprise Data Governance WellPoint, Inc. 1 Introduction:
ROUTES TO VALUE. Business Service Management: How fast can you get there?
 ROUTES TO VALUE Business Service : How fast can you get there? BMC Software helps you achieve business value quickly Each Route to Value offers a straightforward entry point to BSM; a way to quickly synchronize
ROUTES TO VALUE Business Service : How fast can you get there? BMC Software helps you achieve business value quickly Each Route to Value offers a straightforward entry point to BSM; a way to quickly synchronize
Drive Growth and Value with proven BPM solutions from IBM
 IBM Software Thought Leadership White Paper June 2011 Drive Growth and Value with proven BPM solutions from IBM 2 Drive Growth and Value with proven BPM solutions from IBM Contents 2 Executive summary
IBM Software Thought Leadership White Paper June 2011 Drive Growth and Value with proven BPM solutions from IBM 2 Drive Growth and Value with proven BPM solutions from IBM Contents 2 Executive summary
Enterprise IT Portfolio Governance and Management Model
 STATE OF MICHIGAN Department of Information Technology Enterprise IT Portfolio Governance and Management Model NASCIO 2007 RECOGNITION AWARDS CATEGORY: IT PROJECT AND PORTFOLIO MANAGEMENT Enterprise IT
STATE OF MICHIGAN Department of Information Technology Enterprise IT Portfolio Governance and Management Model NASCIO 2007 RECOGNITION AWARDS CATEGORY: IT PROJECT AND PORTFOLIO MANAGEMENT Enterprise IT
7 Best Practices for Business Process Management in Customer Service
 7 Best Practices for Business Process Management in Customer Service 7 Best Practices for Business Process Management in Customer Service Table of Contents Introduction 3 Defining Your Process 3 Empowering
7 Best Practices for Business Process Management in Customer Service 7 Best Practices for Business Process Management in Customer Service Table of Contents Introduction 3 Defining Your Process 3 Empowering
Infor CloudSuite. Defense-in-depth. Table of Contents. Technical Paper Plain talk about Infor CloudSuite security
 Technical Paper Plain talk about security When it comes to Cloud deployment, security is top of mind for all concerned. The Infor CloudSuite team uses best-practice protocols and a thorough, continuous
Technical Paper Plain talk about security When it comes to Cloud deployment, security is top of mind for all concerned. The Infor CloudSuite team uses best-practice protocols and a thorough, continuous
EMA Service Catalog Assessment Service
 MORE INFORMATION: To learn more about the EMA Service Catalog, please contact the EMA Business Development team at +1.303.543.9500 or enterpriseit@enterprisemanagement.com The IT Service Catalog Aligning
MORE INFORMATION: To learn more about the EMA Service Catalog, please contact the EMA Business Development team at +1.303.543.9500 or enterpriseit@enterprisemanagement.com The IT Service Catalog Aligning
Sage ERP X3 I White Paper
 I White Paper Optimize Your ERP System: How to Avoid the Implementation Sins By Jeff Law, CPIM, Senior Manager, Consulting Services The Premier Provider of Effective Business Software Solutions National
I White Paper Optimize Your ERP System: How to Avoid the Implementation Sins By Jeff Law, CPIM, Senior Manager, Consulting Services The Premier Provider of Effective Business Software Solutions National
White paper. Business-Driven Identity and Access Management: Why This New Approach Matters
 White paper Business-Driven Identity and Access Management: Why This New Approach Matters Executive Summary For years, security and business managers have known that identity and access management (IAM)
White paper Business-Driven Identity and Access Management: Why This New Approach Matters Executive Summary For years, security and business managers have known that identity and access management (IAM)
Fortune 500 Medical Devices Company Addresses Unique Device Identification
 Fortune 500 Medical Devices Company Addresses Unique Device Identification New FDA regulation was driver for new data governance and technology strategies that could be leveraged for enterprise-wide benefit
Fortune 500 Medical Devices Company Addresses Unique Device Identification New FDA regulation was driver for new data governance and technology strategies that could be leveraged for enterprise-wide benefit
Whitepaper: 7 Steps to Developing a Cloud Security Plan
 Whitepaper: 7 Steps to Developing a Cloud Security Plan Executive Summary: 7 Steps to Developing a Cloud Security Plan Designing and implementing an enterprise security plan can be a daunting task for
Whitepaper: 7 Steps to Developing a Cloud Security Plan Executive Summary: 7 Steps to Developing a Cloud Security Plan Designing and implementing an enterprise security plan can be a daunting task for
Enterprise Identity Management Reference Architecture
 Enterprise Identity Management Reference Architecture Umut Ceyhan Principal Sales Consultant, IDM SEE Agenda Introduction Virtualization Access Management Provisioning Demo Architecture
Enterprise Identity Management Reference Architecture Umut Ceyhan Principal Sales Consultant, IDM SEE Agenda Introduction Virtualization Access Management Provisioning Demo Architecture
Masterminding Data Governance
 Why Data Governance Matters The Five Critical Steps for Data Governance Data Governance and BackOffice Associates Masterminding Data Governance 1 of 11 A 5-step strategic roadmap to sustainable data quality
Why Data Governance Matters The Five Critical Steps for Data Governance Data Governance and BackOffice Associates Masterminding Data Governance 1 of 11 A 5-step strategic roadmap to sustainable data quality
Critical Success Factors for Product Information Management (PIM) System Implementation
 Critical Success Factors for Product Information Management (PIM) System Implementation Improving product data and streamlining product-related processes directly translate into quality products, higher
Critical Success Factors for Product Information Management (PIM) System Implementation Improving product data and streamlining product-related processes directly translate into quality products, higher
Leveraging a Maturity Model to Achieve Proactive Compliance
 Leveraging a Maturity Model to Achieve Proactive Compliance White Paper: Proactive Compliance Leveraging a Maturity Model to Achieve Proactive Compliance Contents Introduction............................................................................................
Leveraging a Maturity Model to Achieve Proactive Compliance White Paper: Proactive Compliance Leveraging a Maturity Model to Achieve Proactive Compliance Contents Introduction............................................................................................
View Point. Lifting the Fog on Cloud
 View Point Lifting the Fog on Cloud There s a massive Cloud build-up on the horizon and the forecast promises a rain of benefits for the enterprise. Cloud is no more a buzzword. The enabling power of the
View Point Lifting the Fog on Cloud There s a massive Cloud build-up on the horizon and the forecast promises a rain of benefits for the enterprise. Cloud is no more a buzzword. The enabling power of the
Realizing business flexibility through integrated SOA policy management.
 SOA policy management White paper April 2009 Realizing business flexibility through integrated How integrated management supports business flexibility, consistency and accountability John Falkl, distinguished
SOA policy management White paper April 2009 Realizing business flexibility through integrated How integrated management supports business flexibility, consistency and accountability John Falkl, distinguished
Introduction to SOA governance and service lifecycle management.
 -oriented architecture White paper March 2009 Introduction to SOA governance and Best practices for development and deployment Bill Brown, executive IT architect, worldwide SOA governance SGMM lead, SOA
-oriented architecture White paper March 2009 Introduction to SOA governance and Best practices for development and deployment Bill Brown, executive IT architect, worldwide SOA governance SGMM lead, SOA
How can Identity and Access Management help me to improve compliance and drive business performance?
 SOLUTION BRIEF: IDENTITY AND ACCESS MANAGEMENT (IAM) How can Identity and Access Management help me to improve compliance and drive business performance? CA Identity and Access Management automates the
SOLUTION BRIEF: IDENTITY AND ACCESS MANAGEMENT (IAM) How can Identity and Access Management help me to improve compliance and drive business performance? CA Identity and Access Management automates the
Security management solutions White paper. Extend business reach with a robust security infrastructure.
 Security management solutions White paper Extend business reach with a robust security infrastructure. July 2007 2 Contents 2 Overview 3 Adapt to today s security landscape 4 Drive value from end-to-end
Security management solutions White paper Extend business reach with a robust security infrastructure. July 2007 2 Contents 2 Overview 3 Adapt to today s security landscape 4 Drive value from end-to-end
IBM Customer Experience Suite and Electronic Forms
 Introduction It s more important than ever to have a set of capabilities that allow you to create dynamic, self service options for your customers that leverage existing processes and infrastructure. Your
Introduction It s more important than ever to have a set of capabilities that allow you to create dynamic, self service options for your customers that leverage existing processes and infrastructure. Your
IBM Information Management
 IBM Information Management January 2008 IBM Information Management software Enterprise Information Management, Enterprise Content Management, Master Data Management How Do They Fit Together An IBM Whitepaper
IBM Information Management January 2008 IBM Information Management software Enterprise Information Management, Enterprise Content Management, Master Data Management How Do They Fit Together An IBM Whitepaper
EMC PERSPECTIVE. The Private Cloud for Healthcare Enables Coordinated Patient Care
 EMC PERSPECTIVE The Private Cloud for Healthcare Enables Coordinated Patient Care Table of Contents A paradigm shift for Healthcare IT...................................................... 3 Cloud computing
EMC PERSPECTIVE The Private Cloud for Healthcare Enables Coordinated Patient Care Table of Contents A paradigm shift for Healthcare IT...................................................... 3 Cloud computing
ORACLE ENTERPRISE GOVERNANCE, RISK, AND COMPLIANCE MANAGER FUSION EDITION
 ORACLE ENTERPRISE GOVERNANCE, RISK, AND COMPLIANCE MANAGER FUSION EDITION KEY FEATURES AND BENEFITS Manage multiple GRC initiatives on a single consolidated platform Support unique areas of operation with
ORACLE ENTERPRISE GOVERNANCE, RISK, AND COMPLIANCE MANAGER FUSION EDITION KEY FEATURES AND BENEFITS Manage multiple GRC initiatives on a single consolidated platform Support unique areas of operation with
Top 10 Trends In Business Intelligence for 2007
 W H I T E P A P E R Top 10 Trends In Business Intelligence for 2007 HP s New Information Management Practice Table of contents Trend #1: BI Governance: Ensuring the Effectiveness of Programs and Investments
W H I T E P A P E R Top 10 Trends In Business Intelligence for 2007 HP s New Information Management Practice Table of contents Trend #1: BI Governance: Ensuring the Effectiveness of Programs and Investments
Explore the Possibilities
 Explore the Possibilities 2013 HR Service Delivery Forum Best Practices in Data Management: Creating a Sustainable and Robust Repository for Reporting and Insights 2013 Towers Watson. All rights reserved.
Explore the Possibilities 2013 HR Service Delivery Forum Best Practices in Data Management: Creating a Sustainable and Robust Repository for Reporting and Insights 2013 Towers Watson. All rights reserved.
Oracle Role Manager. An Oracle White Paper Updated June 2009
 Oracle Role Manager An Oracle White Paper Updated June 2009 Oracle Role Manager Introduction... 3 Key Benefits... 3 Features... 5 Enterprise Role Lifecycle Management... 5 Organization and Relationship
Oracle Role Manager An Oracle White Paper Updated June 2009 Oracle Role Manager Introduction... 3 Key Benefits... 3 Features... 5 Enterprise Role Lifecycle Management... 5 Organization and Relationship
POINT OF VIEW. The Critical Role of Networking in Enterprise Resource Planning. Introduction
 The Critical Role of Networking in Enterprise Resource Planning Introduction Achieving and maintaining competitive advantage is the raison d etre for every business around the world. Doing so requires
The Critical Role of Networking in Enterprise Resource Planning Introduction Achieving and maintaining competitive advantage is the raison d etre for every business around the world. Doing so requires
Cloud computing insights from 110 implementation projects
 IBM Academy of Technology Thought Leadership White Paper October 2010 Cloud computing insights from 110 implementation projects IBM Academy of Technology Survey 2 Cloud computing insights from 110 implementation
IBM Academy of Technology Thought Leadership White Paper October 2010 Cloud computing insights from 110 implementation projects IBM Academy of Technology Survey 2 Cloud computing insights from 110 implementation
Business Intelligence
 Transforming Information into Business Intelligence Solutions Business Intelligence Client Challenges The ability to make fast, reliable decisions based on accurate and usable information is essential
Transforming Information into Business Intelligence Solutions Business Intelligence Client Challenges The ability to make fast, reliable decisions based on accurate and usable information is essential
accelerating time to value in Microsoft Hyper-V environments
 SOLUTION BRIEF accelerating time to value in Microsoft Hyper-V environments 01 CA Technologies 30-year partnership with Microsoft uniquely positions us to help you exceed your Microsoft virtual and cloud
SOLUTION BRIEF accelerating time to value in Microsoft Hyper-V environments 01 CA Technologies 30-year partnership with Microsoft uniquely positions us to help you exceed your Microsoft virtual and cloud
Configuration Management System:
 True Knowledge of IT infrastructure Part of the SunView Software White Paper Series: Service Catalog Service Desk Change Management Configuration Management 1 Contents Executive Summary... 1 Challenges
True Knowledge of IT infrastructure Part of the SunView Software White Paper Series: Service Catalog Service Desk Change Management Configuration Management 1 Contents Executive Summary... 1 Challenges
Sage ERP I White Paper. Optimize Your System: How to Avoid Implementation Sins
 I White Paper Optimize Your System: How to Avoid Implementation Sins Introduction Enterprise resource planning (ERP) systems improve the way of doing business. By providing accurate, real-time information
I White Paper Optimize Your System: How to Avoid Implementation Sins Introduction Enterprise resource planning (ERP) systems improve the way of doing business. By providing accurate, real-time information
SOACertifiedProfessional.Braindumps.S90-03A.v2014-06-03.by.JANET.100q. Exam Code: S90-03A. Exam Name: SOA Design & Architecture
 SOACertifiedProfessional.Braindumps.S90-03A.v2014-06-03.by.JANET.100q Number: S90-03A Passing Score: 800 Time Limit: 120 min File Version: 14.5 http://www.gratisexam.com/ Exam Code: S90-03A Exam Name:
SOACertifiedProfessional.Braindumps.S90-03A.v2014-06-03.by.JANET.100q Number: S90-03A Passing Score: 800 Time Limit: 120 min File Version: 14.5 http://www.gratisexam.com/ Exam Code: S90-03A Exam Name:
Successful Enterprise Architecture. Aligning Business and IT
 Successful Enterprise Architecture Aligning Business and IT 1 Business process SOLUTIONS WHITE PAPER Executive Summary...3 An Integrated Business & IT Infrastructure...3 Benefits to Business and IT Go
Successful Enterprise Architecture Aligning Business and IT 1 Business process SOLUTIONS WHITE PAPER Executive Summary...3 An Integrated Business & IT Infrastructure...3 Benefits to Business and IT Go
SAP Thought Leadership Business Intelligence IMPLEMENTING BUSINESS INTELLIGENCE STANDARDS SAVE MONEY AND IMPROVE BUSINESS INSIGHT
 SAP Thought Leadership Business Intelligence IMPLEMENTING BUSINESS INTELLIGENCE STANDARDS SAVE MONEY AND IMPROVE BUSINESS INSIGHT Your business intelligence strategy should take into account all sources
SAP Thought Leadership Business Intelligence IMPLEMENTING BUSINESS INTELLIGENCE STANDARDS SAVE MONEY AND IMPROVE BUSINESS INSIGHT Your business intelligence strategy should take into account all sources
Customer effectiveness
 www.pwc.com/sap Customer effectiveness PwC SAP Consulting Services Advance your ability to win, keep and deepen relationships with your customers. Are your customers satisfied? How do you know? Five leading
www.pwc.com/sap Customer effectiveness PwC SAP Consulting Services Advance your ability to win, keep and deepen relationships with your customers. Are your customers satisfied? How do you know? Five leading
IBM Security & Privacy Services
 Enter Click Here The challenge of identity management Today organizations are facing paradoxical demands for greater information access and more stringent information security. You must deliver more data
Enter Click Here The challenge of identity management Today organizations are facing paradoxical demands for greater information access and more stringent information security. You must deliver more data
Security management White paper. Develop effective user management to demonstrate compliance efforts and achieve business value.
 Security management White paper Develop effective user management to demonstrate compliance efforts and achieve business value. September 2008 2 Contents 2 Overview 3 Understand the challenges of user
Security management White paper Develop effective user management to demonstrate compliance efforts and achieve business value. September 2008 2 Contents 2 Overview 3 Understand the challenges of user
IRMAC SAS INFORMATION MANAGEMENT, TRANSFORMING AN ANALYTICS CULTURE. Copyright 2012, SAS Institute Inc. All rights reserved.
 IRMAC SAS INFORMATION MANAGEMENT, TRANSFORMING AN ANALYTICS CULTURE ABOUT THE PRESENTER Marc has been with SAS for 10 years and leads the information management practice for canada. Marc s area of specialty
IRMAC SAS INFORMATION MANAGEMENT, TRANSFORMING AN ANALYTICS CULTURE ABOUT THE PRESENTER Marc has been with SAS for 10 years and leads the information management practice for canada. Marc s area of specialty
Customer requirements. Asset management planning Inspection and assessment Route asset planning Annual work plans Contracting strategy
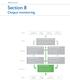 Section 8 Output monitoring Inputs Customer requirements Safety standards Outputs and funding SRA and Government Policy Network stewardship strategy Asset and operational policies Maintenance & renewal
Section 8 Output monitoring Inputs Customer requirements Safety standards Outputs and funding SRA and Government Policy Network stewardship strategy Asset and operational policies Maintenance & renewal
Analytics Strategy Information Architecture Data Management Analytics Value and Governance Realization
 1/22 As a part of Qlik Consulting, works with Customers to assist in shaping strategic elements related to analytics to ensure adoption and success throughout their analytics journey. Qlik Advisory 2/22
1/22 As a part of Qlik Consulting, works with Customers to assist in shaping strategic elements related to analytics to ensure adoption and success throughout their analytics journey. Qlik Advisory 2/22
Building a Roadmap to Robust Identity and Access Management
 Building a Roadmap to Robust Identity and Access Management Elevating IAM from Responsive to Proactive From cases involving private retailers to government agencies, instances of organizations failing
Building a Roadmap to Robust Identity and Access Management Elevating IAM from Responsive to Proactive From cases involving private retailers to government agencies, instances of organizations failing
Driving Business Value. A closer look at ERP consolidations and upgrades
 IT advisory SERVICES Driving Business Value A closer look at ERP consolidations and upgrades KPMG LLP Meaningful business decisions that help accomplish business goals and growth objectives may call for
IT advisory SERVICES Driving Business Value A closer look at ERP consolidations and upgrades KPMG LLP Meaningful business decisions that help accomplish business goals and growth objectives may call for
Delivering IT Security and Compliance as a Service
 Delivering IT Security and Compliance as a Service Jason Falciola GCIH, GAWN Technical Account Manager, Northeast Qualys, Inc. www.qualys.com Agenda Technology Overview h The Problem: Delivering IT Security
Delivering IT Security and Compliance as a Service Jason Falciola GCIH, GAWN Technical Account Manager, Northeast Qualys, Inc. www.qualys.com Agenda Technology Overview h The Problem: Delivering IT Security
Blending Corporate Governance with. Information Security
 Blending Corporate Governance with Information Security WHAT IS CORPORATE GOVERNANCE? Governance has proved an issue since people began to organise themselves for a common purpose. How to ensure the power
Blending Corporate Governance with Information Security WHAT IS CORPORATE GOVERNANCE? Governance has proved an issue since people began to organise themselves for a common purpose. How to ensure the power
Demonstrating the ROI for SIEM: Tales from the Trenches
 Whitepaper Demonstrating the ROI for SIEM: Tales from the Trenches Research 018-101409-01 ArcSight, Inc. 5 Results Way, Cupertino, CA 95014, USA www.arcsight.com info@arcsight.com Corporate Headquarters:
Whitepaper Demonstrating the ROI for SIEM: Tales from the Trenches Research 018-101409-01 ArcSight, Inc. 5 Results Way, Cupertino, CA 95014, USA www.arcsight.com info@arcsight.com Corporate Headquarters:
What You Need to Know About Transitioning to SOA
 What You Need to Know About Transitioning to SOA written by: David A. Kelly, ebizq Analyst What You Need to Know About Transitioning to SOA Organizations are increasingly turning to service-oriented architectures
What You Need to Know About Transitioning to SOA written by: David A. Kelly, ebizq Analyst What You Need to Know About Transitioning to SOA Organizations are increasingly turning to service-oriented architectures
FIVE PRACTICAL STEPS
 WHITEPAPER FIVE PRACTICAL STEPS To Protecting Your Organization Against Breach How Security Intelligence & Reducing Information Risk Play Strategic Roles in Driving Your Business CEOs, CIOs, CTOs, AND
WHITEPAPER FIVE PRACTICAL STEPS To Protecting Your Organization Against Breach How Security Intelligence & Reducing Information Risk Play Strategic Roles in Driving Your Business CEOs, CIOs, CTOs, AND
B2C, B2B and B2E:! Leveraging IAM to Achieve Real Business Value
 B2C, B2B and B2E:! Leveraging IAM to Achieve Real Business Value IDM, 12 th November 2014 Colin Miles Chief Technology Officer, Pirean Copyright 2014 Pirean Limited. All rights reserved. Safe Harbor All
B2C, B2B and B2E:! Leveraging IAM to Achieve Real Business Value IDM, 12 th November 2014 Colin Miles Chief Technology Officer, Pirean Copyright 2014 Pirean Limited. All rights reserved. Safe Harbor All
Preemptive security solutions for healthcare
 Helping to secure critical healthcare infrastructure from internal and external IT threats, ensuring business continuity and supporting compliance requirements. Preemptive security solutions for healthcare
Helping to secure critical healthcare infrastructure from internal and external IT threats, ensuring business continuity and supporting compliance requirements. Preemptive security solutions for healthcare
The Ten How Factors That Can Affect ERP TCO
 The Ten How Factors That Can Affect ERP TCO Gartner RAS Core Research Note G00172356, Denise Ganly, 1 February 2010, V1RA9 04082011 Organizations tend to focus on the what that is, the vendor or the product
The Ten How Factors That Can Affect ERP TCO Gartner RAS Core Research Note G00172356, Denise Ganly, 1 February 2010, V1RA9 04082011 Organizations tend to focus on the what that is, the vendor or the product
INSIGHTS LIFE SCIENCES
 LIFE SCIENCES INSIGHTS Authors: Theresa Greco and Tom Beatty Master Data Management and Life Sciences: Industry Complexity Requires Investment, Governance, an Enterprise View and Mission- Specific MDM
LIFE SCIENCES INSIGHTS Authors: Theresa Greco and Tom Beatty Master Data Management and Life Sciences: Industry Complexity Requires Investment, Governance, an Enterprise View and Mission- Specific MDM
Making Compliance Work for You
 white paper Making Compliance Work for You with application lifecycle management Rocket bluezone.rocketsoftware.com Making Compliance Work for You with Application Lifecycle Management A White Paper by
white paper Making Compliance Work for You with application lifecycle management Rocket bluezone.rocketsoftware.com Making Compliance Work for You with Application Lifecycle Management A White Paper by
Title here. Successful Business Model Transformation. in the Financial Services Industry. KPMG s Evolving World of Risk Management SECTORS AND THEMES
 SECTORS AND THEMES Successful Business Model Transformation Title here in the Financial Services Industry Additional information in Univers 45 Light 12pt on 16pt leading KPMG s Evolving World of Risk Management
SECTORS AND THEMES Successful Business Model Transformation Title here in the Financial Services Industry Additional information in Univers 45 Light 12pt on 16pt leading KPMG s Evolving World of Risk Management
Office of Information Technology. County of Dallas FY2014 FY2018 Information Technology Strategic Plan
 Office of Information Technology County of Dallas Letter from the Office of Information Technology This Information Technology Strategic Plan is the culmination of hard work and collaboration by County
Office of Information Technology County of Dallas Letter from the Office of Information Technology This Information Technology Strategic Plan is the culmination of hard work and collaboration by County
Extend the value of your core business systems.
 Legacy systems renovation to SOA September 2006 Extend the value of your core business systems. Transforming legacy applications into an SOA framework Page 2 Contents 2 Unshackling your core business systems
Legacy systems renovation to SOA September 2006 Extend the value of your core business systems. Transforming legacy applications into an SOA framework Page 2 Contents 2 Unshackling your core business systems
Beyond risk identification Evolving provider ERM programs
 Beyond risk identification Evolving provider ERM programs March 2016 At a glance PwC conducted research to assess the state of enterprise risk management (ERM) within healthcare providers and found many
Beyond risk identification Evolving provider ERM programs March 2016 At a glance PwC conducted research to assess the state of enterprise risk management (ERM) within healthcare providers and found many
CITY OF BOULDER IT GOVERNANCE AND DECISION-MAKING STRUCTURE. (Approved May 2011)
 CITY OF BOULDER IT GOVERNANCE AND DECISION-MAKING STRUCTURE (Approved May 2011) I. Citywide IT Mission, Goals and Guiding Principles The following mission, goal and principle statements are applied throughout
CITY OF BOULDER IT GOVERNANCE AND DECISION-MAKING STRUCTURE (Approved May 2011) I. Citywide IT Mission, Goals and Guiding Principles The following mission, goal and principle statements are applied throughout
Service Oriented Architecture (SOA) Architecture, Governance, Standards and Technologies
 Service Oriented Architecture (SOA) Architecture, Governance, Standards and Technologies 3-day seminar Give Your Business the Competitive Edge SOA has rapidly seized the momentum and center stage because
Service Oriented Architecture (SOA) Architecture, Governance, Standards and Technologies 3-day seminar Give Your Business the Competitive Edge SOA has rapidly seized the momentum and center stage because
Leveraging the Synergy between Identity Management and ITIL Processes
 BEST PRACTICES WHITE PAPER Leveraging the Synergy between Identity Management and ITIL Processes Ken Turbitt, best practices director, BMC Software Rami Elron, senior system architect, Identity Management,
BEST PRACTICES WHITE PAPER Leveraging the Synergy between Identity Management and ITIL Processes Ken Turbitt, best practices director, BMC Software Rami Elron, senior system architect, Identity Management,
Cross-Domain Service Management vs. Traditional IT Service Management for Service Providers
 Position Paper Cross-Domain vs. Traditional IT for Providers Joseph Bondi Copyright-2013 All rights reserved. Ni², Ni² logo, other vendors or their logos are trademarks of Network Infrastructure Inventory
Position Paper Cross-Domain vs. Traditional IT for Providers Joseph Bondi Copyright-2013 All rights reserved. Ni², Ni² logo, other vendors or their logos are trademarks of Network Infrastructure Inventory
CT30A8901 Chapter 10 SOA Delivery Strategies
 CT30A8901 Chapter 10 SOA Delivery Strategies Prof. Jari Porras Communications Software Laboratory Contents 10.1 SOA Delivery lifecycle phases 10.2 The top-down strategy 10.3 The bottom-up strategy 10.4
CT30A8901 Chapter 10 SOA Delivery Strategies Prof. Jari Porras Communications Software Laboratory Contents 10.1 SOA Delivery lifecycle phases 10.2 The top-down strategy 10.3 The bottom-up strategy 10.4
How to leverage SAP NetWeaver Identity Management and SAP Access Control combined solutions
 How to leverage SAP NetWeaver Identity Management and SAP Access Control combined solutions Introduction This paper provides an overview of the integrated solution and a summary of implementation options
How to leverage SAP NetWeaver Identity Management and SAP Access Control combined solutions Introduction This paper provides an overview of the integrated solution and a summary of implementation options
Cloud Computing. Key Initiative Overview
 David W. Cearley Research Vice President and Gartner Fellow This overview provides a high-level description of the Cloud Computing Key Initiative. IT leaders can use this guide to understand what they
David W. Cearley Research Vice President and Gartner Fellow This overview provides a high-level description of the Cloud Computing Key Initiative. IT leaders can use this guide to understand what they
Choosing the Right Master Data Management Solution for Your Organization
 Choosing the Right Master Data Management Solution for Your Organization Buyer s Guide for IT Professionals BUYER S GUIDE This document contains Confidential, Proprietary and Trade Secret Information (
Choosing the Right Master Data Management Solution for Your Organization Buyer s Guide for IT Professionals BUYER S GUIDE This document contains Confidential, Proprietary and Trade Secret Information (
WHITE PAPER: STRATEGIC IMPACT PILLARS FOR OPTIMIZING BUSINESS PROCESS MANAGEMENT IN GOVERNMENT
 WHITE PAPER: STRATEGIC IMPACT PILLARS FOR OPTIMIZING BUSINESS PROCESS MANAGEMENT IN GOVERNMENT IntelliDyne, LLC MARCH 2012 Strategic Impact Pillars for Optimizing Business Process Management in Government
WHITE PAPER: STRATEGIC IMPACT PILLARS FOR OPTIMIZING BUSINESS PROCESS MANAGEMENT IN GOVERNMENT IntelliDyne, LLC MARCH 2012 Strategic Impact Pillars for Optimizing Business Process Management in Government
How To Achieve Pca Compliance With Redhat Enterprise Linux
 Achieving PCI Compliance with Red Hat Enterprise Linux June 2009 CONTENTS EXECUTIVE SUMMARY...2 OVERVIEW OF PCI...3 1.1. What is PCI DSS?... 3 1.2. Who is impacted by PCI?... 3 1.3. Requirements for achieving
Achieving PCI Compliance with Red Hat Enterprise Linux June 2009 CONTENTS EXECUTIVE SUMMARY...2 OVERVIEW OF PCI...3 1.1. What is PCI DSS?... 3 1.2. Who is impacted by PCI?... 3 1.3. Requirements for achieving
ECM as a Shared Service: The New Frontier
 Doculabs White Paper: ECM as a Shared Service: The New Frontier Organizations are struggling with the increasing growth of unstructured content: all the word processing files, e-mail, spreadsheets, web
Doculabs White Paper: ECM as a Shared Service: The New Frontier Organizations are struggling with the increasing growth of unstructured content: all the word processing files, e-mail, spreadsheets, web
Service Oriented Architecture (SOA) Architecture, Governance, Standards and Technologies
 Service Oriented Architecture (SOA) Architecture, Governance, Standards and Technologies 3-day seminar Give Your Business the Competitive Edge SOA has rapidly seized the momentum and center stage because
Service Oriented Architecture (SOA) Architecture, Governance, Standards and Technologies 3-day seminar Give Your Business the Competitive Edge SOA has rapidly seized the momentum and center stage because
Avoiding the Accidental SOA Cloud Architecture
 A UBM WHITE PAPER NOVEMBER 2011 Avoiding the Accidental SOA Cloud Architecture Prior to the hybrid cloud, IT determined how an enterprise infrastructure grew. With the introduction of Software-as-a- Service
A UBM WHITE PAPER NOVEMBER 2011 Avoiding the Accidental SOA Cloud Architecture Prior to the hybrid cloud, IT determined how an enterprise infrastructure grew. With the introduction of Software-as-a- Service
Surviving an Identity Audit
 What small and midsize organizations need to know about the identity portion of an IT compliance audit Whitepaper Contents Executive Overview.......................................... 2 Introduction..............................................
What small and midsize organizations need to know about the identity portion of an IT compliance audit Whitepaper Contents Executive Overview.......................................... 2 Introduction..............................................
Thriving in the New Normal for Tax Administration
 Experience the commitment ISSUE PAPER Thriving in the New Normal for Tax Administration This paper discusses how tax agencies can identify specific revenue collection initiatives and begin to build the
Experience the commitment ISSUE PAPER Thriving in the New Normal for Tax Administration This paper discusses how tax agencies can identify specific revenue collection initiatives and begin to build the
Customizing Identity Management to fit complex ecosystems
 Customizing Identity Management to fit complex ecosystems Advisory Services PwC Security - Identity Management 12 July 2011 Client s challenge One of the world s largest aerospace and defense corporations
Customizing Identity Management to fit complex ecosystems Advisory Services PwC Security - Identity Management 12 July 2011 Client s challenge One of the world s largest aerospace and defense corporations
Top Five Reasons Not to Master Your Data in SAP ERP. White Paper
 Top Five Reasons Not to Master Your Data in SAP ERP White Paper This document contains Confidential, Proprietary and Trade Secret Information ( Confidential Information ) of Informatica Corporation and
Top Five Reasons Not to Master Your Data in SAP ERP White Paper This document contains Confidential, Proprietary and Trade Secret Information ( Confidential Information ) of Informatica Corporation and
Strengthen security with intelligent identity and access management
 Strengthen security with intelligent identity and access management IBM Security solutions help safeguard user access, boost compliance and mitigate insider threats Highlights Enable business managers
Strengthen security with intelligent identity and access management IBM Security solutions help safeguard user access, boost compliance and mitigate insider threats Highlights Enable business managers
SOA : To Do or Not to Do
 Abstract SOA : To Do or Not to Do Gopala Krishna Behara and K.T.R.B Sarma As business moves from Web services to SOA, adoption and successful implementations of SOA become more evident. The goal of SOA
Abstract SOA : To Do or Not to Do Gopala Krishna Behara and K.T.R.B Sarma As business moves from Web services to SOA, adoption and successful implementations of SOA become more evident. The goal of SOA
Brochure. Update your Windows. HP Technology Services for Microsoft Windows 2003 End of Support (EOS) and Microsoft Migrations
 Brochure Update your Windows HP Technology Services for Microsoft End of Support (EOS) and Microsoft Migrations Stabilize and secure your infrastructure Microsoft will end support for Windows Server 2003/R2
Brochure Update your Windows HP Technology Services for Microsoft End of Support (EOS) and Microsoft Migrations Stabilize and secure your infrastructure Microsoft will end support for Windows Server 2003/R2
DEMONSTRATING THE ROI FOR SIEM
 DEMONSTRATING THE ROI FOR SIEM Tales from the Trenches HP Enterprise Security Business Whitepaper Introduction Security professionals sometimes struggle to demonstrate the return on investment for new
DEMONSTRATING THE ROI FOR SIEM Tales from the Trenches HP Enterprise Security Business Whitepaper Introduction Security professionals sometimes struggle to demonstrate the return on investment for new
