Application-level simulation for network security
|
|
|
- Justin Cobb
- 8 years ago
- Views:
Transcription
1 Application-level simulation for network security Stephan Schmidt, Rainer Bye, Joël Chinnow Karsten Bsufka, Ahmet Camtepe and Sahin Albayrak DAI-Labor, Berlin Institute of Technology, Ernst-Reuter-Platz 7, Berlin 1 ABSTRACT NeSSi (Network Security Simulator) is a novel network simulation tool which incorporates a variety of features relevant to network security distinguishing it from general-purpose network simulators. Its capabilities such as profile-based automated attack generation, traffic analysis and support for detection algorithm plugins allow it to be used for security research and evaluation purposes. NeSSi has been successfully used for testing intrusion detection algorithms, conducting network security analysis, and developing overlay security frameworks. NeSSi is built upon the agent framework JIAC [1], resulting in a distributed and extensible architecture. In this paper, we provide an overview of the NeSSi architecture as well as its distinguishing features and briefly demonstrate its application in current security research projects. Keywords Keywords: Network simulation, Network security, Discrete-event simulation, Packet-level simulation, Application-level simulation 1. INTRODUCTION In contemporary communication infrastructures, IP-based computer networks play a prominent role. The deployment of these networks is progressing at an exponential rate as different kinds of participants such as corporations, public authorities and individuals rely on sophisticated and complex services and communication systems. With regard to information security, this leads to new challenges as large amounts of data, which may hold malicious content such as worms, viruses, or Trojans, are transferred over open networks. Network security measures dealing with these threats can be implemented in the network itself as well as at hosts connected to access routers of the network. The host-based approach has its merits, especially with respect to the scalability of a resulting security framework; for example, placing security capabilities such as firewalls or virus scanners on individual hosts does not inhibit the traffic traveling through the network. However, as 1 Research supported and funded by Deutsche Telekom AG. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee. SIMUTools (Revised and extended version) March 03-07, 2008, Marseille, France Copyright 2008 ACM ISBN $5.00. the hosts are generally not under the control of network operators, there is no way of ensuring a certain network-wide security policy. A consequence for network service providers (NSPs) striving to offer improved security features to their customers as a valueadding feature is to devise a security framework in which detection devices are placed within the network. Before doing so, the NSP must take into account that it is not desirable to make frequent changes or experiment with various security feature deployments in the network infrastructure of a production system. For this reason, network operators can greatly profit from a network simulation tool in which various features of the security architectures can be tested in order to ensure maximum attack detection efficiency before the actual physical deployment. The advantage over conventional testbeds is the low cost and ease at which tests can be carried out. The presented Network Security Simulator NeSSi (see Figure 1) allows NSPs to experiment with different network-centric security framework setups and algorithms in order to evaluate and compare intrusion detection efficiency and operational costs. In this fashion, a devised security framework can be tested in a simulation environment before the actual detection units are physically deployed in the network. In the following section, we provide an overview of existing network simulation tools, focusing on security evaluation capabilities. We then describe the general software architecture of NeSSi in Section 3. Subsequently, we focus on the traffic and protocol support in Section 4 and security features in Section 5 and finally demonstrate how it can be used for the setup and execution of realistic attack scenarios. In conclusion, an outlook on future extensions of NeSSi is given in Section RELATED WORK In recent years, the research community has used various network simulation tools for the verification of new algorithms, the investigation of design and interaction behavior of newly developed protocols as well as the examination of performance issues encountered in large-scale network architectures. The most popular general-purpose software tool in the research community is the open-source network simulator ns2 [2]. ns2 performs network simulation using a discrete event model. This approach has several advantages regarding application performance and scalability. These important issues are discussed for example in [3] and [4]. Discrete simulation allows very cost-efficient exploration and experimentation with real-life network topologies and architectures. In many areas involving network analysis, ns2 is a powerful tool; however, it also poses certain limitations to the user. Concerning the aspect of simulation efficiency for large networks, ns2 does not support out-of-the-box a parallel execution model. It does not support generic sockets, but protocols have to be rewritten for the usage
2 in ns2. Moreover, the script language interface is not intuitive to use for novice users. Alternatives to ns2 are for example the QualNET simulator [5] or the Georgia Tech Network Simulator GTNetS [6], which, in contrast to ns2, also offers parallel execution support for large-scale simulation. Most important of all, these simulators have limitations in standard support of real-world network security evaluation. A lot of work has been done in the limited area of worm simulation, as described extensively by Wei et al. [7]. In this work, the authors note that existing simulators are mostly single-machine tools and hence do not scale to model realistic attack mechanisms in largescale real-world networks. They propose a distributed approach termed PAWS, which is nevertheless not a comprehensive tool but limited to worm simulation only. Another security evaluation tool is RINSE, which is described by Liljenstam et al. in [8]. It focuses on supporting real-time large-scale simulations and allows for realistic emulation of CPU and memory effects within the simulation. However, there is no mention of application-level simulation capabilities in RINSE. The same drawback exists in the solution presented in [9], although it allows model-driven attack tree-based simulation in a reusable object-oriented software architecture. 2.1 Our Contribution NeSSi aims to fill this gap by offering simulation and evaluation features specifically tailored to meet the needs of security experts and network administrators. This target group will be able to test and evaluate the performance of commonly available security solutions as well as new research approaches. As a distinguishing feature to the previous tools described above, NeSSi provides extensive support of complex application-level scenarios on top of a faithful simulation of the TCP/IP protocol stack. Simulated networks are modeled to reflect real-world network topologies by supporting subnet-layer modeling and different node types with varying capabilities (Core and Access subnets, wireless networks etc.). In particular, NeSSi adheres to a modular design pattern and fosters the integration of third-party applications via a standardized plugin interface. Furthermore, it provides a comprehensive Detection API for the integration and evaluation of simulated as well as external detection units. In particular, special common attack scenarios are supported and can be simulated, worm-spread scenarios and botnet-based DDoS attacks are only two of the example scenarios supported by NeSSi. In addition, customized profiles expressing the node behavior can be applied within the simulation. The application layer simulation capabilities in NeSSi are provided by distributed software agents, introducing another layer of abstraction. In order to maintain scalability, a parallel execution model is used in conjunction with a discrete event model. In this context, the agent platforms are running on multiple parallel machines and connect independently to a database server from which simulation results can be retrieved in an asynchronous and concurrent fashion. The graphical user interface allows for real-time inspection and configuration of scenarios. 3. NESSI ARCHITECTURE The design of a packet-level discrete-event simulator is a challenging task. In order to handle the inherent complexity, NeSSi has been structured into three distinct components, the Graphical User Interface, the simulation backend and the result database. Each of these modules may be run on separate machines depending on the computational requirements; furthermore, this modular design facilitates network security researchers using NeSSi to easily exchange network topologies, scenario definitions and simulation results via remote repositories. In the following sections, we will describe each of these modules in turn and delineate the workflow in NeSSi, beginning with the creation of a network from scratch up to the analysis of the simulation results. 3.1 Graphical User Interface The graphical user interface is a Rich Client Platform (RCP) application based on the Eclipse framework [10]. It uses the Standard Widget Toolkit (SWT, [11]), a cross-platform open-source widget toolkit which allows NeSSi to be run on almost all operating systems. As an RCP application, NeSSi is structured into views, editors and perspectives. A view is a composite widget for displaying data of a certain type to the user; the different views implemented in NeSSi will be described later in this section. Editor windows contain the main data of interest (in the case of NeSSi graphical representations of networks respectively subnets), while the surrounding views display context-related information based on the selection in the editor window. Perspectives on the other hand are used to bundle thematically related views and editors to present the user with an interface to execute the desired task while hiding functionality that is not essential to the current task. The graphical frontend of NeSSi allows the user to create and edit network topologies, attach runtime information, and schedule them for execution at the simulation backend. On the other hand, finished (or even currently executing, long-running) simulations can be retrieved from the database server and the corresponding simulation results are visualized in the GUI. This constitutes two distinct use cases: pre- and post-simulation visualization. For this reason, the GUI has been divided in two perspectives, a Network Editor perspective and a Network Simulation perspective Network Editor Perspective The Network Editor perspective comprises a main network editor window grouped with a variety of different views which provide additional information pertaining to the element currently selected in the network editor. Some of these views appear in both perspectives since they are valuable in the editing as well as the evaluation phase. These are: Console Here, network status information and logged events are displayed. The desired level of verbosity can be configured. Routing Table When a network node, i.e. a client, server or router, is selected, the respective routing table is displayed. For each reachable target machine, it contains the IP addresses of the gateway, the subnet mask and the hop count. Properties Displays and allows editing a number of properties for the selected element. Among other information, device name and device type are displayed for nodes; for links, bandwidth, latency and maximum transfer unit (MTU) is available. Statistics Graphical representation of simulation results. The content of this view adapts to the element selected in the editor or the outline. Apart from these, by reusing existing plugins available for Eclipse, we offer valuable standard functionality in NeSSi such as: Team Support Users of NeSSi can share networks, scenarios and sessions as well as database resources via remote repositories based on CVS or SVN. Update Functionality New versions can be downloaded via an update site. The updates are deployed as separate features, allowing the user to decide which components of his NeSSi
3 Figure 1: Graphical user interface of NeSSi - Main Network Editor window distribution he wants to update. NeSSi is open source since late 2008; the update site location will be published at http: //nessi2.de. Integrated Help NeSSi offers an inline help system. This comprises different types of manuals (user, developer etc.), Javadoc documentation and context-based help for the current UI selection. Other views such as Bookmarks, Tasks and Progress are also supported and used by NeSSi. They will not be described here for the sake of brevity. Before starting to create his first simulation, the user needs to familiarize himself with the network/scenario/session concept which NeSSi is built upon. This paradigm serves to distinguish static topology information from dynamic behavioral information with the goal of enhancing the reusability of previously created elements. Oftentimes, simulations need to be carried out for large networks which differ only in a few parameters while most of the information stays the same; sometimes the user wants to apply different traffic generation functionality in the same network without having to create and subsequently manage unnecessary copies of the same static topology information. Network topology The network topology describes the static information contained in the network, i.e. the nodes of the network, their (initial) properties and how they are interconnected. Thus, a topology can be reused in combination with several different scenarios. Scenario A scenario contains runtime information attached to a particular network topology. For instance, a scenario may contain the traffic generation properties for different nodes in the network. A scenario can be reused in combination with different sessions. For detailed information on the type of scenarios that can be created with the standard NeSSi version, refer to Section 4. Session Finally, the session information contains additional information specific for the selected scenario. For example, the user may be interested only in a certain type of traffic, or the scenario should be carried out repeatedly, but with different tick runtimes (Tick is the term for the atomic discrete time unit). This kind of information is encapsulated in the Session object for a particular scenario. Network topologies can be created by choosing network elements such as routers and different kinds of end devices such as web
4 Figure 2: Wizard-assisted network creation clients, mail servers etc. and adding them from a palette to the network editor main window via drag-and-drop (cf. Figure 1). In the simulation, agents realize the behavior of the nodes (cf. Section 3.2.2). The node modeling occurs in two layers; the first layer reflects their role in the network (client, server, switch or router). This is further refined according to their application-level role (such as web clients, mail clients, IRC server etc.) and inherent functionality. The network is hierarchically structured by dividing it into subnets. For example, a large-scale network usually consists of a core area, a number of distribution networks (for example university or metropolitan area networks) and access networks, i.e. company networks. In the central network editor window of Figure 1, such a network with a hierarchical structure is displayed. It is also possible to automatically generate networks by specifying various parameters such as the number of individual subnets and their types, node degree, topology (star, ring etc.), average link bandwidth in the core, distribution and access subnets and many more (see Figure 2). This is especially useful for generating large-scale topologies, where the network generation is a two-step process: the user generates a topology automatically and adjusts the resulting network by fine-tuning individual devices or device properties. These subnets and their individual network elements such as routers and links and their properties, i.e. routing tables, network interfaces etc., are modeled using the Eclipse Modeling Framework (EMF [12]) which also allows automated source code generation. Consequently, the model can easily be extended to include new features or adapted to match new requirements. Supported standard device properties are processing speed, packet queuing mechanisms and supported routing protocols; link properties include delay and bandwidth. Individual subnets are connected at edge routers, which are logically assigned to both subnets. The user can jump to the corresponding other subnet by double-clicking on an edge router, which allows for easy navigation through the entire network, although individual subnets are displayed in separate tabs. The user interacts with the application via context-sensitive actions. For more complex operations, the user is supported by wizards. For example, when an IRC server is drag-and-dropped on the network editor, a context-menu action is dynamically created for this node which allows executing a pre-defined IRC exploit scenario. When the user selects it, a wizard appears, describing the scenario and guiding the user through the process. After the static network topology configuration is complete, the dynamic scenario components need to be created. A scenario is comprised of elementary building blocks for each device in the network, the concept of node profiles. Node profiles allow the customization of network node behavior in order to automatically generate traffic adhering to well-defined characteristics, simulate network outages by means of router or link failures as well as evaluating network-based defense measures. The basic elements used to describe these profiles are actions and plans:
5 Figure 3: Subnet Editor with user-defined devices like XML firewalls and packet sniffers Actions Actions are clustered into three different types: traffic, failure and detection units. Traffic actions describe the behavior of a single service (HTTP, SMTP, etc.) with various parameters depending on their type. Failure actions are used to simulate network failures like link outage or router malfunction. Detection unit actions configure security-related applications which utilize the Detection Unit API 5.2. Plans The time characteristics are described with plans for the corresponding action. They contain, at least one, time spans in which the action is executed according to various distribution functions (standard, binomial etc.). Profiles Profiles, the top level elements, describe the actual node behavior by utilizing different plans. An execution plan can be included in a profile multiple times for repeated execution. After defining a profile, it can easily be attached to several clients by enabling it in the respective clients context menu. Additionally, the profiles can be distributed in a percentage based fashion on end devices, routers or (in case of failures) links. Security-related applications such as NIDS sensor components can also be deployed on a selection of machines based on a user-defined measure of optimality in order to maximize the efficiency of the NIDS. To this end, the set of machines selected for running the profile may for example be obtained by a betweenness centrality or gametheory approach (cf. Section 6.2). The sum of all profiles for a given network topology constitutes the scenario. In order to execute a scenario, the last set of parameters to specify are the session parameters. These include for example the number of times a given scenario is to be executed and the types of events to log in the database. The security expert may desire to run a single scenario multiple times if the employed node profiles are not statically configured but make use of distribution functions for generating network traffic. In this case, multiple runs allow the generation of statistically significant mean values and the comparison of individual runs to examine standard deviations. The ability to specify the types of events to log allows for a higher degree of scalability for large-scale simulations, where the user is only interested in a particular subset of the simulation results. For example, it can be configured that only application-level traffic for a certain protocol type is to be logged, which may greatly increase the simulation speed when a lot of other background traffic is generated which does not need to be logged. Supplementary NeSSi includes automated attack generation for the purpose of examining security-related network features. Several adversary models are supported, among others worm spread and DDoS attack models. This feature has proven highly useful in the research of the cooperative detection approach for generating simulation data (cf. Section 5). In the resulting paper [13], traffic statistics of captured real traffic data were mapped to node profiles. Once a session has been created for a particular scenario and
6 backend runs on a Sun XFire 4600 blade server (8 blades, 8 cores per blade). Once a session is submitted for execution, the simulation backend parses the desired session parameters (which event types to log, how many runs to execute etc.), creates a corresponding simulation environment, sets up the database connection and schedules the simulation to run as soon as the necessary processing resources are available. Figure 4: Preference pages allow the user to control all aspects of NeSSi - from local preferences to remote repository locations topology, it can be transmitted to the simulation backend for execution. For details on how the simulation is carried out refer to Section 3.2; in the following section we first describe how the results are presented to the user of NeSSi Network Simulation Perspective The Network Simulation Perspective contains a set of related views which allow the visualization of simulation results. Upon connecting to the database server, the available simulation results are depicted in a tree structure annotated with the date of the execution and the user who has submitted them. The desired session can be selected, and the corresponding simulation results are downloaded for display. The user has several options for displaying the simulation results. The main editor window contains the network topology associated with the selected session; naturally however, no network elements may be edited or deleted (in contrast to the Network Editor perspective). In the menu bar, the user can step forward and backward through the simulation to inspect the state of the network at the desired tick. For demonstration purposes, a playback functionality is also provided where the simulation is visualized at the desired speed. In the main network window, the status of the network elements is visualized by different means. For example, link widths and colors change depending on the type and amount of traffic on the link, while devices which have failed (for example due to a successful attack) appear grayed out, or devices which are infected but operational are flagged with a corresponding symbol. Since not all relevant information can be displayed in the editor window however, two additional views contain context-based information relevant to the network element selected in the editor. The Properties view displays detail information for the current tick (for example, routing tables may change over time), while the Statistics view contains graphical information of logged events for the selected network element. For example, this may be a graphical representation of the packets on a given link, sorted by protocol type. As an added feature, this view is highly configurable and may be adapted to show cumulative values, restrict the results to certain subsets of interesting data sources and so on. 3.2 Simulation Backend The actual simulation is performed on a machine with hardware dedicated solely to this purpose, the simulation backend. At the Berlin Institute of Technology for example, the NeSSi simulation JIAC Agent Framework NeSSi is built upon the JIAC framework [1]. JIAC is a servicecentric java-based middleware architecture based on the agent paradigm. Within NeSSi, agents are used for modeling and implementing the network entities such as routers, clients, and servers. The underlying JIAC agent framework provides a rich and flexible basis for implementing and testing of various security deployments and algorithms in NeSSi. Moreover, building upon an agent framework allows combining the partial knowledge of the agents residing in the network in a cooperative approach for identifying and eventually eliminating IP-based threats. For example, this may be achieved by monitoring the structure of the encountered IP traffic and the behavior of potentially compromised target systems. For an illustrative example where we successfully utilized the agents cooperative features, refer to Section 5. Although the software agents provide powerful application-level capabilities, their complexity unfortunately also affects the scalability of the simulation. NeSSi mitigates this problem by building upon a parallel-execution model Parallel-Execution Model Simulations in large-scale networks are very costly in terms of processing time and memory consumption. Therefore, NeSSi has been designed as a distributed simulation, allowing the subdivision of tasks to different computers and processes in a parallel-execution model. NeSSi introduces an additional layer of abstraction at the level of network design by explicitly modeling subnets (which constitute the nodes of the abstract network view in Figure 1). This abstract view on the network is shown in the main editor area, which contains core, distribution and access subnets. In this instance, the network depicted in Figure 1) contains 3 core, 3 distribution and 9 access subnets. In the property sheet below the editor area, the properties of the selected element is visible; in this case it displays that for the Access1 network, the network address is and the subnet mask is Each of these subnets can in turn be opened (via double-clicking or the outline view on the right) to show the devices of the subnet. An example of a subnet open in the main editor window can be seen in Figure 3, where a section of an access subnet containing web clients and servers, firewalls and access routers is visible. This view also contains more detailed information such as network interfaces or link bandwidths. Additionally, actual traffic in the runtime phase will be visualized on the links by color and thickness, which allows the selection of "interesting" links in order to obtain even more detailed statistical and graphical information (cf. Figure 5). In NeSSi, the handling of subnets and the contained devices is distributed to several processes on different individual machines, allowing the simulation to scale better with increasing network size. Figure 6 shows the main components of NeSSi, backend, GUI and Simulation Data Base, as well as their interaction. In the GUI, the network with appropriate scenario and session information is created (cf. Section 3.1.1) and transmitted to the backend, where the simulation is executed. In this regard, log data is stored in the Simulation Data Base and can be accessed again by the GUI to show the results of a simulation run (cf. Section 3.1.2).
7 Figure 5: Graphical depiction of traffic in the network simulation perspective In the backend, different agent roles carry out the task of the parallel simulation execution. On Master as well as Slave Simulation Node, Subnet Agents (SA) and a Platform Coordination Agent (PCA) are running. In addition, the Master Simulation Node executes the Network Coordination Agent (NCA). Subnet Agent (SA) A subnet agent is responsible for managing an individual subnet. During execution, the SA receives events from the PCA (see below) indicating that a new tick has started. It performs all relevant operations such as packet forwarding and application handling that need to be executed for the current tick (an atomic time frame in the discrete event model). Once all events have been handled, the SA reports back to the PCA that the tick has been successfully executed. Platform Coordination Agent (PCA) On a single platform, different subnet agents are created, configured and controlled by a platform coordination agent (PCA). A platform is meant as a software environment for agents running on one computer. The number of subnet agents handled by the PCA is dependent on the available computing resources. The PCA receives events from the NCA and relays them to all the SAs residing on its platform. As soon as all SAs have reported back that a tick has been executed successfully, the PCA is responsible for forwarding the packets traveling from one subnet to another subnet on a different platform to the respective target PCA. Subsequently, it informs the NCA that the platform has finished the requested task. The platform also sustains a connection to the database, where simulation results and history can be stored (see Section 3.3). Network Coordination Agent (NCA) The entire network simulation is controlled by the network coordination agent (NCA). The NCA coordinates the distribution of the subnets at the beginning of a simulation as well as the synchronization of the platforms. The NCA receives its network model data from the GUI agent. The GUI can also trigger the beginning and determine the end of the simulation, but the NCA does not depend on a GUI agent to be present once it has been started. This architecture allows the distributed network simulation. In addition, the graphical user interface can be disconnected from the simulation environment and later reconnected to it even from another computer. Figure 6 is a graphical representation of the distributed agent architecture. 3.3 Persistent Session Management In NeSSi, we refer to a scenario where we generate traffic via pre-defined profiles (cf. Section 3.1.1) on a single network over a certain amount of time as a session. The accurate reproduction of a session enables users to use different detection methods or various deployments of detection units for the same traffic data set. This allows the comparison of performance and detection efficiency of different security framework setups.
8 Figure 6: Architecture for distributed simulations with NeSSi For these purposes, we use a distributed database in which the traffic generated during a session is stored. For each session, the agents log the traffic and detection data and send it to the database that occurs in a simulated scenario between a start and end time. The data types to be logged are specified by the user in the session parameters. The network model is saved in an XML file. This network file is stored and annotated with a version number based on its hash code in order to link a network uniquely to a session. Additionally, attack related events can be stored in the database for evaluation purposes. Those events are explained in greater detail in Section 5.3. Due to the modular design of the database component, the actual implementation of the database is up to the user. This can be comfortably managed via the graphical user interface, where the location of the database, database user name, password and the database driver can be specified. NeSSi has been tested extensively with a MySQL database server, but depending on the user s preferences, this can easily be substituted by another module (see Figure 4). The event types to log are specified independent of the underlying implementation via XML-based log4j logger repository settings where multiple appenders can be configured. For example, for simple scenarios the user can simply write the results to a text file if he so desires. 4. THE FEATURES OF NESSI NeSSi is designed to extend conventional network simulation tool features by supporting detailed examination and testing opportunities of security-related network algorithms, detection units and frameworks. The main focus of NeSSi is to provide a realistic packet-level simulation environment as a testbed for the development of new detection units as well as existing ones. We use detection unit as an abstract term for any algorithm or tool employed for the purpose of detecting malicious activity such as intrusion or service degradation attempts. NeSSi has been designed as a modular application with the focus on extensibility. In particular, NeSSi provides out-of-the-box support for various protocols of the TCP/IP stack; a selection of these is described in Section 4.2. These features provide the basis for designing, incorporating and simulating detection units. The framework provided by NeSSi for simulating is subsequently described in Section 5.2. The general plugin API for integrating new user-designed protocols, device types and detection units is beyond the scope of this paper. 4.1 Traffic Generation Network traffic in the form of IP packets, complete with header and body, can be generated by different means. Implementing the TCP/IP protocol stack, NeSSi features an application layer module which is based on standard Java socket implementations. NeSSi incorporates several application level protocols (HTTP, SMTP, etc.) and supports static and dynamic routing protocols which can be selected by the user. At the moment, static and dynamic protocols are implemented. A static routing protocol centrally computes the shortest paths as the network is loaded and each time the topology changes. The resulting routing tables are subsequently loaded onto the individual network nodes. On the other hand, IS- IS (Intermediate-System-to-Intermediate-System) has been implemented as a link-state protocol, which relies on a decentralized algorithm during which routers exchange information about their link states and gather topology information locally. In an iterative fashion, the routing tables at the individual nodes are updated through control message exchange. NeSSi can also easily be extended to
9 support a variety of other applications (see Section 4.2). For this purpose, it is necessary to implement, besides the application, the previously described action with the required parameter. In case of a DDoS application, this would be source and destination port, the attacked IP address as well as the packet frequency. Through this, own enhancements can be easily configured, deployed in a network and simulated with NeSSi. 4.2 Protocol Stack and Socket-based API The TCP/IP reference model is the de-facto standard for Internet communication. Due to its importance, NeSSi also offers an implementation for it. The routers as well as the end devices in the simulation contain a Network Layer; end devices also exclusively have a Transport and an Application Layer. At the Network Layer, IPv4 is realized with the key features global addressing, routing and fragmentation support. Moreover, TCP/IP model implementation allows containing several protocols in each layer; hence, we also provide IPv6 support in NeSSi. For the fault management, TTL (Time to live) and header checksums supported and the ICMP protocol has been implemented for failure notification. Network Layer communication is realized directly on the drop-tail queues that are located at the network interfaces. On the next level, the Transport Layer is comprised of UDP and TCP. TCP in NeSSi offers a reliable and in-order delivery of data. Sockets represent the interface to the Application Layer, i.e., applications can set up several stream sockets as well as the corresponding server sockets. In this fashion, third-party Java libraries can easily be integrated in the simulation by substituting Java sockets with NeSSi sockets. As a proof-of-concept, the JavaMail API 1 has been successfully adapted in NeSSi. All applications that are run in NeSSi follow a common interface that abstracts from their specific behavior but allows a standardized way of executing them. Currently, the HTTP, SMTP and IRC protocols are integrated in NeSSi. Generated traffic in NeSSi can also be exported to files in the pcap 2 format in order to inspect the data with standard traffic inspection tools such as wireshark 3. Several tests have been conducted with the traffic exported from NeSSi, verifying that the generated traffic is well-formed. Wireshark is able to reconstruct the application data stream without errors if all corresponding IP packets are in the exported file. The generated traffic can be analyzed either offline, for example with the aforementioned tools, or online within the application itself, for example by displaying a graphical summary (cf. Figure 1). 5. SECURITY SIMULATION FEATURES In the previous sections, we described the basic network model and traffic generation features of NeSSi as well as other aspects regarding general network simulation. The distinguishing feature of NeSSi is the focus on network security framework and algorithm evaluation. Figure 8 provides a conceptual view on NeSSi the Network Security Simulator. The bottom layer shows some of the important technologies that NeSSi uses. This includes the JIAC agent framework used for representation of the different entities in the simulation, EMF for the network data model and Eclipse RCP as the platform-independent, plugin-based execution environment. On top of the bottom layer, several concepts realized in NeSSi can be found. These are the aforementioned general network simulation components like traffic modeling via node profiles, a parallel Figure 8: NeSSi is comprised of several components presented in the middle layer. The bottom layer depicts the main technologies NeSSi relies upon. execution model, discrete event simulation and the visualization. In this section, we presume that a network topology and background traffic has been created, as described in the previous sections. We will now highlight the security simulation capabilities of NeSSi that can be added to this basic setup in a four-step process. First, we will describe how attacks are modeled and generated in Section 5.1. Subsequently, detection capabilities are added to the network in order to evaluate their efficiency in detecting the configured attack scenarios (Section 5.2). Finally, Section 5.3 demonstrates how the results of the simulation are presented to the user in order to draw conclusions whether the selected detection approach is performing well in protecting against the configured attack. In a final step, we show how the abovementioned concepts are put into practice by means of an example scenario. Using the example of detecting and containing worm spread in a network of multiple Autonomous Systems, Section 5.4 applies the concepts from the sections 5.1, 5.2 and 5.3 in a step-by-step process. 5.1 Generating Attacks The simulation setup in NeSSi is not only comprised of network creation and attachment of traffic profiles (c.f. Section 3.1.1), but additionally security related settings can be configured. When a security framework composed of several detection units is to be tested, profiles can also be used in NeSSi to simulate attacker behavior and attack patterns. Accordingly, NeSSi provides out-of-the box support for various attack scenarios such as bot networks initiating DDoS attacks. Here, infected end device nodes, zombies, are controlled by the bot net commander via the Internet Relay Chat application. The commander is capable of initiating different kinds of DDoS attacks like the SYN Flooding or UDP Storm. To this end, the attacker connects to an IRC communication server and sends attack commands to a chat channel all the bots are listening to. As a result, the bots execute the desired attack. Besides, worm propagation schemes are supported. Here, the behavior of the SQL Slammer worm and the Blaster worm have been realized exemplarily in NeSSi. In general, a worm propagation scheme as well as the SIR model (Susceptible Infected Recovered) as an epidemiological model is included in NeSSi. The worm propagations scheme can be configured in different ways: on the one hand there exist configuration files defining the number of initial propagators and where in the network the outbreak should take place. Additionally, the spreading scheme, i.e. which IP addresses
10 Figure 7: Setting up a security simulation: Worm spread inside a topology of multiple Autonomous Systems to attack and delays in between, can be set. On the other hand, the worm application model itself can either be extended or a new one can seamlessly be integrated via the application interface provided in NeSSi (cf. 4.2). In the second step, newly developed or pre-configured detection units can be deployed on a set of links in the simulation. Therefore, analogous to the traffic profiles, detection profiles can be created. Those detection profiles consist of one or more detection units and can be deployed on end devices, links or routers. Details of how these deployments are evaluated with regard to their efficiency can be found in Section 6.2. The tools used for these evaluation tasks are described in the next section. 5.2 Detection Unit API Foremost, NeSSi provides a Detection Unit API for the development of new detection algorithms as well as the integration of existing ones. The architecture for this purpose is shown in figure 9. It consists of four main components whose activation depends on the configuration of the detection approach; the Packet Capturing component is mandatory and processes incoming traffic from a data source. This is usually a link in the NeSSi simulation but can also be file system streams or a database connection. Here, packets are selected according to filter rules and a sampling policy (like every tenth packet ) to narrow down the processing overhead. Accordingly, the packets are associated with time stamps. Several detection algorithms, e.g. behavior-based approaches, do not only process packets but also related statistical information. As an example, the well-known SYN Flood attack is characterized by a massive amount of open TCP connections. In this case, the Packet Processing component offers the construction of IPFIX 4 data flows based on the packet data. The flow specifica- 4 tion is open to the developer by configuration files. To this end, a tree structure of the flow is defined by providing key attributes and optional data fields. A data flow representing distinct TCP sessions must have at least a source IP address, destination IP address, source port, destination port and a protocol flag as key attributes. Moreover, the Packet Post Processing component generates the actual input to the detection units. This input can also be specified by a detection unit which ranges from raw packets for signaturebased schemes like virus scanners, to complex ratios of traffic statistics based on the flow data; for example in the case of a SYN Flood attack, the ratio of half-open TCP connections to all TCP connections can be specified. Finally, the detection units may be well-known security solutions as contemporary commercial virus scanner software or new tools developed in scientific research projects. In NeSSi, both can be incorporated as long as they adhere to a specified interface. The configuration of a detection unit and the required components are stored in a template. Furthermore, additional properties like Inlining, i.e. synchronous packet processing, can be set. This allows the application of counter measures. A processing interval for a detection algorithm is another option that can be set here. 5.3 Reporting and Evaluation NeSSi allows the simulation of various security scenarios. Additionally, there is a huge diversity in network security evaluation metrics. Here, the developer of a detection algorithm respectively of a special security infrastructure set-up may not only be interested in detection rates, but also in the economical assessment of a scenario. Hence, the gathering of simulation results and the evaluation needs to be very flexible. Here, we apply an event-based approach, the so-called Meta Attack Events. Already included events incorporate dropped packets, infected flows, compromised machines, un-
11 Figure 11: Evaluating worm spread prevention efficiency: Spread in protected (lower, blue) and unprotected (upper, yellow) AS available services etc. Those events are stored in the database at runtime. Events belonging to the same attack refer to a global ID to differentiate between the impacts of different attacks. The database associates those events with a time stamp in the simulation as well as a device and/or transmitted packets related to that specific event. Furthermore, we apply BIRT [14] (Business Intelligence and Reporting Tools) for visualization and analysis of results. BIRT is comprised on the one hand of a graphical report designer capable of creating report templates. In those templates, different input sources like databases, simple Java objects or XML files can be declared. Additionally, BIRT allows standard statistical operations on the data and enables the choice of several chart types to display the resulting data series. More complex preprocessing can easily be carried out by adding Java or JavaScript code. On the other hand, BIRT offers an environment for the generation of the reports at runtime. In this case, a report template is loaded and the actual selected data source, in the example of NeSSi usually a simulation session is bound to the report. Subsequently, an HTML document containing the desired report is generated and can be shown in any Internet Browser. Figure 10 shows an example report created in the NeSSi environment. It compares detection rates of different algorithms; the detection rate is measured as detected number of infections in comparison to the total number of infections (sensitivity). 5.4 Example scenario: Signature-based worm spread detection and prevention Computer worms represent a serious threat to communication networks, even motivating the development of several special-purpose simulation tools to examine their properties (cf. Section 2. Therefore, we analyzed how the impact of an epidemic that spreads too fast to be contained using human supervision processes can be minimized with signature-based countermeasures. To be able to model realistic scenarios, we extended NeSSi to support multi AS topologies. In the following, we show how this simulation study is conducted; selected steps are shown in Figure 7. In the beginning, the AS topology is created using the wizard for parameter-based automated network creation. An extract is shown in the main editor window in the background of Figure 7 (step 1). Next, this scenario requires a worm and a detection unit application. As shown in Figure 7 (step 2), applications can be customized specifying various parameters. In this manner, it is possible to emulate the behavior of existing malware such as CodeRed or SQL Slammer. We used a CodeRed-like scanning behavior with small adaptions due to the smaller IP space. The worm application has two states: susceptible and infected. Initially, only a few worm applications are in the infected state, but they will be switched if they receive a worm packet on the vulnerable port. The detection application utilizes network error messages (ICMP). If hosts cause too much ICMP traffic, they are marked as suspicious and the detection application starts generating signatures for their traffic. After a predefined amount of a certain signature has been created for different hosts, it will be deployed and prevents infections. For multi AS topologies, the applications are deployed automatically. Alternatively, manual configuration as shown in step 3 is also possible. Now that both the attack and the detection profiles have been set up, the user has to create a session, configure and execute it. Finally, the simulation can be evaluated in the corresponding perspective. The results of this example run are pictured in Figure 11. Here, we differ between the spread in- and outside the protected AS. For the latter, the events are split in two graphs, the infections inside the protected AS and the averted attacks after the signatures where deployed. Here the mitigation was successful as less then a quarter of the vulnerable hosts has been infected. In the following section, we discuss further security research conducted in NeSSi to demonstrate that it is not merely a worm simulation tool but has been successfully used to conduct a wide variety of simulation studies in various fields.
12 Figure 10: Reporting in NeSSi: This example report shows an evaluation of the detection ratio (sensitivity) of different detection algorithms Figure 9: The components of the Detection API and the packet/data flow between them. The Packet Processing component is not necessary for all detection algorithms. 6. RECENT AND PUBLISHED RESEARCH ACTIVITIES NeSSi has already demonstrated its value in recent research and was employed as a test framework for various network-centric security approaches. 6.1 Artificial Immune System For example, a distributed and collaborative Artificial Immune System (AIS) was implemented in NeSSi for testing an anomalybased detection algorithm [13]. In this scenario, anomaly detection units on different hosts compute the probability of an anomaly by an AIS component. The idea of AIS is to compute the possibility of an anomaly by comparing the actual status of the system to a set of detectors created by negative selection [15]. This algorithm is a metaphor of the biological negative selection taking place during the maturation of the immune cells. The detectors are produced nearly randomly and compared to the normal data; if a detector is similar to a normal feature vector, it is deleted and a new one is created, this is done until no detector is similar to the normal feature vector set (training set). The data processed by the AIS is statistical in nature and obtained by a monitoring component on the host agent. Here, the probability of an anomaly constitutes the status of a client. The cooperation between the clients takes place by sharing these status levels and computing new status level information based on the incoming status of others and its own status. The tests results, verified in NeSSi, indicated a very good performance of the AIS in general while the false positive rate (the main problem of anomaly detection systems) was lowered significantly. The communication between the AIS clients described in [13] has been implemented in NeSSi via a customized peer-to-peer protocol to avoid the single point-of-failure of a central server. This peer-to-peer protocol allows the combination of AI Systems into detection groups. As an extension, a scheme for the decentralized detector set generation was presented by Bye et al. [16]. Here, the overall feature space is partitioned in several sub spaces administrated by AISenabled nodes. As a result, the individual computational load for each node is decreased. Nevertheless, by the application of combinatorial design techniques like Symmetric Balanced Incomplete Block Design or Generalized Quadrangles a controlled level of overlap between the detector sets is realized and sets are exchanged deterministically between peers. Finally, this results in a trade-off between the aforementioned computational task on the one hand and a guaranteed level of redundancy on the other hand. 6.2 Detection Device Placement As a second use-case scenario, we studied various detection device placement approaches. To this end, we used a number of identical detection units in order to ensure comparability. The type of detection unit to use can be selected prior to starting the device placement scenario in NeSSi. Furthermore, the configuration dialog allows selecting how many total detection devices may be placed, representing a total sampling budget. The objective is then to maximize the detection efficiency subject to the budget constraints. Several algorithms are supported for computing sensible deployment strategies, for example Betweenness Centrality [17], Traffic Betweenness Centrality [18] or a selection of gametheoretic approaches [19, 20]. In NeSSi, we have already successfully evaluated two of these approaches, namely node selection algorithms using the Betweenness Centrality paradigm as well as a monitor placement game described in [20]. The Betweenness Centrality algorithm originates from social network theory and indicates the importance of a node in the overall network communication. It is run asynchronously in NeSSi after a change to the network topology occurs and returns a
13 numerical value for every node indicating its centrality index. Subsequently, detection devices are placed on the devices corresponding to the nodes with the largest values as an optimal deployment. We then ran a test with default traffic generation profiles on all clients for a fixed number of execution cycles. For comparison, we subsequently fed the same traffic in the same network but deployed the detection units randomly. The results indicate the superiority of deploying on nodes with high Betweenness Centrality index. We assume that in case traffic is not uniformly distributed in the network, i.e. there are clients who generate considerably more traffic than others, the Traffic Betweenness Centrality [18] approach would be even more suitable. Puzis et al. [21] mention the possibility of adapting the Betweenness Centrality to find a most prominent group in a network, which they define as a set of nodes which covers the most distinct source-destination (clientserver) paths. In a more recent paper, Brandes also considers various variants of Shortest-Path Betweenness Centrality [22]. Some of these are particularly suited for applying them to real-world scenarios, such as the proxies and endpoints subproblems. In NeSSi, we have applied the algorithms for these variants in order to generate more realistic Betweenness Centrality values. These applications result in being able to generate subnet-weighted BC values, where it is assumed that traffic in subnets will be proportionally larger than intra-subnet traffic. A second variant takes into account that only end devices will initiate connections and generate traffic while the intermediate routers merely forward it. This enables us to disregard all shortest paths (s, t) where s or t is a router, leading to more meaningful centrality values. In the second study, a game-theoretic approached was employed where the attackers and the IDS are modeled as adversaries in a two-person game. We were able to demonstrate the existence of a mixed-strategy saddle-point equilibrium and computed its value for two example networks. The adversaries are modeled as Runnables in NeSSi. Upon starting the simulation, the respective threads are started concurrently, and elementary player actions from the strategy matrix are selected using a random number generator. It was possible to verify the game-theoretic optimality and measure the performance of the obtained strategies to the devised network security game. Finally, hierarchical intrusion detection approaches are emerging as important tools in managing the increasing complexity of network-based intrusion detection systems. This is particularly true for ad-hoc networks, where the lack of central audit points mandates a distributed and adaptive intrusion detection approach [23]. The hierarchy needs to be constantly able to adapt to nodes leaving and entering the network. In this respect, we have implemented Basagni s algorithm [24] for performing a distributed clustering and determining the clusterheads of the intrusion detection hierarchy. This is a first step towards building a multi-level intrusion detection hierarchy as described in [23]. We expect to obtain relevant results as soon as adhoc network protocol support in NeSSi through plugins reaches a mature level. 6.3 Collaborative Intrusion and Malware Detection Another case study realized in NeSSi took place in the scope of CIMD, Collaborative Intrusion and Malware Detection. The CIMD framework enables cooperative intrusion detection approaches via an overlay network. For this purpose detection groups, i.e. groups with a common objective for intrusion detection are built. Each participant of CIMD is characterized by attributes, e.g. hardware, software or network configuration. Based on this data model, the Figure 12: Backbone of simulated network used for heterogeneous detection group scenario interests, i.e. characteristics of desired group members can be expressed. Subsequently, the overlay network performs the look-up of potential group members and conducts the grouping. Bye et al. introduced the main aspects of CIMD which are the data model, grouping algorithm and matching function(s) in [25]. In this work, also vulnerability analysis and realization strategies of the system are given as well as simulation and analysis was conducted pinpointing the benefit of the overall approach. In this regard, the case study of heterogeneous detection groups for signature exchange was applied. These groups of disparate network-based IDS (NIDS) follow the common objective signature exchange while originating from distinct manufacturers. Customer networks are connected to a NSP and provided a portfolio of disparate NIDS products as a commercial service. Each customer network is protected by a randomly selected NIDS type installed at the gateway to the NSP. The attack vector bases on drive-by downloads, i.e. malicious web servers exploit browser vulnerabilities of a user when accessing web sites. In this regard, clients in the customer networks continuously access the web servers and become infected in the case the server is malicious. But, in the case a signature for the attack is already available on the NIDS, the attack is prevented. In the beginning, attacks are unknown and devices are exposed to the vulnerability window, i.e. time between an exploit becomes available and appropriate signature is generated. But signatures for the threats become available with different update times depending on the manufacturer. In the non-collaborative scenario, the NIDS are working on their own, whereas in the collaborative scenario the heterogeneous detection groups are built in advance with the purpose to mediate upcoming signatures between the distinct participants. The benefit of the detection groups has been evaluated in NeSSi. Here, a topology of 58 access networks connected to the backbone of the NSP was realized (c.f. Figure 12). The NIDS portfolio was comprised of three different products, that were equally dis-
14 tributed over the customer networks. Signatures for the attack become available in the interval between a minimum and a maximum update time. We simulated the collaborative and non-collaborative in NeSSi with varying malicious web server probabilities. The results of the simulation showed a reduction of the number of infections compared to the non-collaborative approach. Probabilistic analysis was also conducted to support the simulation results showing also that collaboration becomes the more feasible the more heterogeneous the detection groups are. 6.4 Detection Algorithm Evaluation In a university graduate class, NeSSi was used to produce data for evaluating detection algorithms implemented by students without any knowledge of the simulator. When it is not required to analyze simulation data at runtime, NeSSi allows to store simulation data, e.g. the IP packets, in the database. In the anomaly detection class, NeSSi was used to simulate non-infected traffic, a DDoS attack and a worm attack. The students were tasked with implementing an anomaly detection algorithm and comparing detection results between different algorithms, attack types and detector placements within in NeSSi. All these different experiments were based on the simulation data stored in the NeSSi database. The evaluated detection approaches included a distributed Artificial Immune System [26], a Self-Organizing Map [27] and Naive Bayes Classifiers [28]. 7. CONCLUSION AND OUTLOOK We have presented and described the Network Security Simulator NeSSi. Based on agent technology and discrete event simulation, it is a highly-scalable, platform-independent network simulation tool with special features for evaluating security solutions. In particular, the plug-in-based API allows security experts to write their own detection unit plug-ins and test them in NeSSi. Network simulation is a very wide and complex area in software engineering. There is an abundance of features existing in reallife networks; moreover, standards are changing and new standards are introduced continuously at a rapid rate. Hence, keeping NeSSi up-to-date with the latest trends in network technology is a great challenge. The following is a list of features we plan to focus on in the further development of NeSSi. For comparison, a list of features for the next generation of ns-2 (some of them are already supported in NeSSi ) can be found in [29]. Usability In order to appeal to a greater audience, the usability of the simulator can be improved. This includes role-based user interface perspectives dependent on experience level (novice or expert). Scenarios More default attack scenarios will be supported. We will extend the already realized Bot Net infrastructure capable of executing DDoS-attacks (cf. Figure 7) by peer-to-peer principles. Peer-to-peer bot nets are regarded as an emerging important threat in Network Security. Critical Infrastructures In future versions, we aim to extend the strictly IP-based topology models by adding features for examining higher-level security risks, for example in critical infrastructures. In particular, we focus on providing more generic network models which interoperate with standard graph libraries, for example JUNG [30]. This will allow the user to examine interdependencies between different types of commodities (i.e. power and communication infrastructures) and assess the related security risks. Since the end of 2008, NeSSi is available under an open-source license. Please visit for the newest developments. Acknowledgements: The authors would especially like to thank their scientific advisors Tansu Alpcan and Katja Luther for their invaluable support and their fellow colleagues Thorsten Rimkus, Sebastian Linkiewicz, Marcus Lagemann, Thomas Hauschild, Jakob Strafer and Dennis Grunewald for their dedicated work on this project. 8. REFERENCES [1] Stefan Fricke, Karsten Bsufka, Jan Keiser, Torge Schmidt, Ralf Sesseler, and Sahin Albayrak. Agent-based telematic services and telecom applications. Communications of the ACM, 44(4):43 48, April [2] USC Information Sciences Institute. NS-2 network simulator http: // last accessed on 07/15/2008. [3] David M. Nicol, Michael Liljenstam, and Jason Liu. Advanced concepts in large-scale network simulation. In Michael E. Kuhl, Natalie M. Steiger, Frank Armstrong, and Jeffrey A. Joines, editors, 37th Winter Simulation Conference, pages ACM, [4] B. Liu, D.R. Figueiredo, Y. Guo, J. Kurose, and D. Towsley. A study of networks simulation efficiency: Fluid simulation vs. packet-level simulation. In INFOCOM Twentieth Annual Joint Conference of the IEEE Computer and Communications Societies. Proceedings. IEEE, volume 3, pages , [5] Scalable Network Technologies Inc. Qualnet. [6] George F. Riley. The Georgia Tech Network Simulator. In Proceedings of the ACM SIGCOMM workshop on Models, methods and tools for reproducible network research, pages ACM Press, [7] Songjie Wei, J. Mirkovic, and M. Swany. Distributed worm simulation with a realistic internet model. Principles of Advanced and Distributed Simulation, PADS Workshop on, pages 71 79, June [8] Michael Liljenstam, Jason Liu, David M. Nicol, Yougu Yuan, Guanhua Yan, and Chris Grier. RINSE: The Real-Time Immersive Network Simulation Environment for Network Security Exercises (Extended Version). SIMULATION, 82(1):43 59, [9] Joo Beom Yun, Eung Ki Park, Eul Gyu Im, and Hoh Peter In. A scalable, ordered scenario-based network security simulator. In Systems Modeling and Simulation: Theory and Applications, volume 3389 of Lecture Notes in Computer Science (LNCS), pages Springer-Verlag, [10] Eclipse Foundation. Eclipsepedia - RCP. last accessed on 10/11/2008. [11] Eclipse Foundation. Eclipsepedia - SWT. last accessed on 10/11/2008. [12] Eclipse Foundation. Eclipse modeling framework project. last accessed on 10/11/2008. [13] Katja Luther, Rainer Bye, Tansu Alpcan, Sahin Albayrak, and Achim Müller. A Cooperative AIS Framework for
15 Intrusion Detection. In Proceedings of the IEEE International Conference on Communications (ICC 2007), [14] Eclipse Foundation. Business intelligence and reporting tools. last accessed on 10/11/2008. [15] Stephanie Forrest, Alan S. Perelson, Lawrence Allen, and Rajesh Cherukuri. Self-nonself Discrimination in a Computer. In Proceedings of the IEEE Symposium on Research in Security and Privacy, pages IEEE Computer Society Press, [16] Rainer Bye, Katja Luther, Seyit Ahmet Camtepe, Tansu Alpcan, Sahin Albayrak, and Bülent Yener. Decentralized Detector Generation in Cooperative Intrusion Detection Systems. In Sebastien Masuzawa, Toshimitsu; Tixeuil, editor, Stabilization, Safety, and Security of Distributed Systems 9th International Symposium, SSS 2007 Paris, France, November 14-16, 2007 Proceedings, Lecture Notes in Computer Science, Vol Springer, [17] Ulrik Brandes. A faster algorithm for betweenness centrality. Journal of Mathematical Sociology, 25(2): , [18] M. Bloem, T. Alpean, S. Schmidt, and T. Basar. Malware Filtering for Network Security Using Weighted Optimality Measures. In IEEE International Conference on Control Applications, CCA 2007, pages , [19] M. Kodialam and T. Lakshman. Detecting network intrusions via sampling: A game theoretic approach. In Proceedings IEEE INFOCOM Twenty-Second Annual Joint Conference of the IEEE Computer and Communications Societies, volume 3, pages , April [20] Stephan Schmidt, Tansu Alpcan, Sahin Albayrak, and Achim Müller. A Monitor Placement Game for Intrusion Detection. In Proc. of CRITIS, 2nd International Workshop on Critical Information Infrastructures Security, volume 5141 of Lecture Notes in Computer Science. Springer, [21] Rami Puzis, Yuval Elovici, and Shlomi Dolev. Fast algorithm for successive computation of group betweenness centrality. Physical Review E (Statistical, Nonlinear, and Soft Matter Physics), 76(5):056709, [22] Ulrik Brandes. On variants of shortest-path betweenness centrality and their generic computation. Social Networks, 30(2): , May [23] D. Sterne, P. Balasubramanyam, D. Carman, B. Wilson, R. Talpade, C. Ko, R. Balupari, C.-Y. Tseng, and T. Bowen. A general cooperative intrusion detection architecture for manets. In Proceedings of the Third IEEE International Workshop on Information Assurance, pages 57 70, March [24] Stefano Basagni. Distributed clustering for ad hoc networks. Parallel Architectures, Algorithms, and Networks, (I-SPAN 99) Proceedings. Fourth InternationalSymposium on, pages , [25] Rainer Bye and Sahin Albayrak. CIMD- Collaborative Intrusion and Malware Detection. Technical Report TUB-DAI 08/08-01, Technische Universität Berlin - DAI-Labor, August [26] Stephen Hofmeyr and Stephanie Forrest. Architecture for an Artificial Immune System. Evolutionary Computation Journal, 8(4): , [27] Albert J. Höglund, Kimmo Hätönen, and Antti S. Sorvari. A Computer Host-Based User Anomaly Detection System Using the Self-Organizing Map. In IJCNN 00: Proceedings of the IEEE-INNS-ENNS International Joint Conference on Neural Networks (IJCNN 00)-Volume 5, page 5411, Washington, DC, USA, IEEE Computer Society. [28] Nahla Ben Amor, Salem Benferhat, and Zied Elouedi. Naive bayes vs decision trees in intrusion detection systems. In SAC 04: Proceedings of the 2004 ACM symposium on Applied computing, pages , New York, NY, USA, ACM Press. [29] ns-3 project. NS-3 network simulator. http: // last accessed on 07/15/2008. [30] JUNG. Java universal network/graph framework software library Open Source, accessed on
How To Create A Network Security Simulator
 Application-level simulation for network security Rainer Bye, Stephan Schmidt Katja Luther and Sahin Albayrak 1 DAI-Labor, Technische Universität Berlin {rainer.bye, stephan.schmidt, katja.luther, sahin.albayrak}@dai-labor.de
Application-level simulation for network security Rainer Bye, Stephan Schmidt Katja Luther and Sahin Albayrak 1 DAI-Labor, Technische Universität Berlin {rainer.bye, stephan.schmidt, katja.luther, sahin.albayrak}@dai-labor.de
packet retransmitting based on dynamic route table technology, as shown in fig. 2 and 3.
 Implementation of an Emulation Environment for Large Scale Network Security Experiments Cui Yimin, Liu Li, Jin Qi, Kuang Xiaohui National Key Laboratory of Science and Technology on Information System
Implementation of an Emulation Environment for Large Scale Network Security Experiments Cui Yimin, Liu Li, Jin Qi, Kuang Xiaohui National Key Laboratory of Science and Technology on Information System
INCREASE NETWORK VISIBILITY AND REDUCE SECURITY THREATS WITH IMC FLOW ANALYSIS TOOLS
 WHITE PAPER INCREASE NETWORK VISIBILITY AND REDUCE SECURITY THREATS WITH IMC FLOW ANALYSIS TOOLS Network administrators and security teams can gain valuable insight into network health in real-time by
WHITE PAPER INCREASE NETWORK VISIBILITY AND REDUCE SECURITY THREATS WITH IMC FLOW ANALYSIS TOOLS Network administrators and security teams can gain valuable insight into network health in real-time by
Avaya P330 Load Balancing Manager User Guide
 Avaya P330 Load Balancing Manager User Guide March 2002 Avaya P330 Load Balancing Manager User Guide Copyright 2002 Avaya Inc. ALL RIGHTS RESERVED The products, specifications, and other technical information
Avaya P330 Load Balancing Manager User Guide March 2002 Avaya P330 Load Balancing Manager User Guide Copyright 2002 Avaya Inc. ALL RIGHTS RESERVED The products, specifications, and other technical information
Software Development Kit
 Open EMS Suite by Nokia Software Development Kit Functional Overview Version 1.3 Nokia Siemens Networks 1 (21) Software Development Kit The information in this document is subject to change without notice
Open EMS Suite by Nokia Software Development Kit Functional Overview Version 1.3 Nokia Siemens Networks 1 (21) Software Development Kit The information in this document is subject to change without notice
Radware s Smart IDS Management. FireProof and Intrusion Detection Systems. Deployment and ROI. North America. International. www.radware.
 Radware s Smart IDS Management FireProof and Intrusion Detection Systems Deployment and ROI North America Radware Inc. 575 Corporate Dr. Suite 205 Mahwah, NJ 07430 Tel 888 234 5763 International Radware
Radware s Smart IDS Management FireProof and Intrusion Detection Systems Deployment and ROI North America Radware Inc. 575 Corporate Dr. Suite 205 Mahwah, NJ 07430 Tel 888 234 5763 International Radware
Distack. Towards Understanding the Global Behavior of DDoS Attacks A Framework for Distributed Attack Detection and Beyond
 Distack Towards Understanding the Global Behavior of DDoS Attacks A Framework for and Beyond Thomas Gamer, Christoph P. Mayer, Martina Zitterbart 29. Aug 2008, EURECOM, France, (TH) Karlsruhe Institute
Distack Towards Understanding the Global Behavior of DDoS Attacks A Framework for and Beyond Thomas Gamer, Christoph P. Mayer, Martina Zitterbart 29. Aug 2008, EURECOM, France, (TH) Karlsruhe Institute
Deploying the BIG-IP LTM system and Microsoft Windows Server 2003 Terminal Services
 Deployment Guide Deploying the BIG-IP System with Microsoft Windows Server 2003 Terminal Services Deploying the BIG-IP LTM system and Microsoft Windows Server 2003 Terminal Services Welcome to the BIG-IP
Deployment Guide Deploying the BIG-IP System with Microsoft Windows Server 2003 Terminal Services Deploying the BIG-IP LTM system and Microsoft Windows Server 2003 Terminal Services Welcome to the BIG-IP
Internet Firewall CSIS 4222. Packet Filtering. Internet Firewall. Examples. Spring 2011 CSIS 4222. net15 1. Routers can implement packet filtering
 Internet Firewall CSIS 4222 A combination of hardware and software that isolates an organization s internal network from the Internet at large Ch 27: Internet Routing Ch 30: Packet filtering & firewalls
Internet Firewall CSIS 4222 A combination of hardware and software that isolates an organization s internal network from the Internet at large Ch 27: Internet Routing Ch 30: Packet filtering & firewalls
SOUTHERN POLYTECHNIC STATE UNIVERSITY. Snort and Wireshark. IT-6873 Lab Manual Exercises. Lucas Varner and Trevor Lewis Fall 2013
 SOUTHERN POLYTECHNIC STATE UNIVERSITY Snort and Wireshark IT-6873 Lab Manual Exercises Lucas Varner and Trevor Lewis Fall 2013 This document contains instruction manuals for using the tools Wireshark and
SOUTHERN POLYTECHNIC STATE UNIVERSITY Snort and Wireshark IT-6873 Lab Manual Exercises Lucas Varner and Trevor Lewis Fall 2013 This document contains instruction manuals for using the tools Wireshark and
SysPatrol - Server Security Monitor
 SysPatrol Server Security Monitor User Manual Version 2.2 Sep 2013 www.flexense.com www.syspatrol.com 1 Product Overview SysPatrol is a server security monitoring solution allowing one to monitor one or
SysPatrol Server Security Monitor User Manual Version 2.2 Sep 2013 www.flexense.com www.syspatrol.com 1 Product Overview SysPatrol is a server security monitoring solution allowing one to monitor one or
Advancement in Virtualization Based Intrusion Detection System in Cloud Environment
 Advancement in Virtualization Based Intrusion Detection System in Cloud Environment Jaimin K. Khatri IT Systems and Network Security GTU PG School, Ahmedabad, Gujarat, India Mr. Girish Khilari Senior Consultant,
Advancement in Virtualization Based Intrusion Detection System in Cloud Environment Jaimin K. Khatri IT Systems and Network Security GTU PG School, Ahmedabad, Gujarat, India Mr. Girish Khilari Senior Consultant,
Transformation of honeypot raw data into structured data
 Transformation of honeypot raw data into structured data 1 Majed SANAN, Mahmoud RAMMAL 2,Wassim RAMMAL 3 1 Lebanese University, Faculty of Sciences. 2 Lebanese University, Director of center of Research
Transformation of honeypot raw data into structured data 1 Majed SANAN, Mahmoud RAMMAL 2,Wassim RAMMAL 3 1 Lebanese University, Faculty of Sciences. 2 Lebanese University, Director of center of Research
CHAPETR 3. DISTRIBUTED DEPLOYMENT OF DDoS DEFENSE SYSTEM
 59 CHAPETR 3 DISTRIBUTED DEPLOYMENT OF DDoS DEFENSE SYSTEM 3.1. INTRODUCTION The last decade has seen many prominent DDoS attack on high profile webservers. In order to provide an effective defense against
59 CHAPETR 3 DISTRIBUTED DEPLOYMENT OF DDoS DEFENSE SYSTEM 3.1. INTRODUCTION The last decade has seen many prominent DDoS attack on high profile webservers. In order to provide an effective defense against
Complete Protection against Evolving DDoS Threats
 Complete Protection against Evolving DDoS Threats AhnLab, Inc. Table of Contents Introduction... 2 The Evolution of DDoS Attacks... 2 Typical Protection against DDoS Attacks... 3 Firewalls... 3 Intrusion
Complete Protection against Evolving DDoS Threats AhnLab, Inc. Table of Contents Introduction... 2 The Evolution of DDoS Attacks... 2 Typical Protection against DDoS Attacks... 3 Firewalls... 3 Intrusion
Radware s Behavioral Server Cracking Protection
 Radware s Behavioral Server Cracking Protection A DefensePro Whitepaper By Renaud Bidou Senior Security Specialist,Radware October 2007 www.radware.com Page - 2 - Table of Contents Abstract...3 Information
Radware s Behavioral Server Cracking Protection A DefensePro Whitepaper By Renaud Bidou Senior Security Specialist,Radware October 2007 www.radware.com Page - 2 - Table of Contents Abstract...3 Information
AlienVault. Unified Security Management (USM) 5.x Policy Management Fundamentals
 AlienVault Unified Security Management (USM) 5.x Policy Management Fundamentals USM 5.x Policy Management Fundamentals Copyright 2015 AlienVault, Inc. All rights reserved. The AlienVault Logo, AlienVault,
AlienVault Unified Security Management (USM) 5.x Policy Management Fundamentals USM 5.x Policy Management Fundamentals Copyright 2015 AlienVault, Inc. All rights reserved. The AlienVault Logo, AlienVault,
Application Security Backgrounder
 Essential Intrusion Prevention System (IPS) & DoS Protection Knowledge for IT Managers October 2006 North America Radware Inc. 575 Corporate Dr., Lobby 1 Mahwah, NJ 07430 Tel: (888) 234-5763 International
Essential Intrusion Prevention System (IPS) & DoS Protection Knowledge for IT Managers October 2006 North America Radware Inc. 575 Corporate Dr., Lobby 1 Mahwah, NJ 07430 Tel: (888) 234-5763 International
Wedge Networks: Transparent Service Insertion in SDNs Using OpenFlow
 Wedge Networks: EXECUTIVE SUMMARY In this paper, we will describe a novel way to insert Wedge Network s multiple content security services (such as Anti-Virus, Anti-Spam, Web Filtering, Data Loss Prevention,
Wedge Networks: EXECUTIVE SUMMARY In this paper, we will describe a novel way to insert Wedge Network s multiple content security services (such as Anti-Virus, Anti-Spam, Web Filtering, Data Loss Prevention,
Intrusion Detection in AlienVault
 Complete. Simple. Affordable Copyright 2014 AlienVault. All rights reserved. AlienVault, AlienVault Unified Security Management, AlienVault USM, AlienVault Open Threat Exchange, AlienVault OTX, Open Threat
Complete. Simple. Affordable Copyright 2014 AlienVault. All rights reserved. AlienVault, AlienVault Unified Security Management, AlienVault USM, AlienVault Open Threat Exchange, AlienVault OTX, Open Threat
Considerations In Developing Firewall Selection Criteria. Adeptech Systems, Inc.
 Considerations In Developing Firewall Selection Criteria Adeptech Systems, Inc. Table of Contents Introduction... 1 Firewall s Function...1 Firewall Selection Considerations... 1 Firewall Types... 2 Packet
Considerations In Developing Firewall Selection Criteria Adeptech Systems, Inc. Table of Contents Introduction... 1 Firewall s Function...1 Firewall Selection Considerations... 1 Firewall Types... 2 Packet
Architecture Overview
 Architecture Overview Design Fundamentals The networks discussed in this paper have some common design fundamentals, including segmentation into modules, which enables network traffic to be isolated and
Architecture Overview Design Fundamentals The networks discussed in this paper have some common design fundamentals, including segmentation into modules, which enables network traffic to be isolated and
ESET Endpoint Security 6 ESET Endpoint Antivirus 6 for Windows
 ESET Endpoint Security 6 ESET Endpoint Antivirus 6 for Windows Products Details ESET Endpoint Security 6 protects company devices against most current threats. It proactively looks for suspicious activity
ESET Endpoint Security 6 ESET Endpoint Antivirus 6 for Windows Products Details ESET Endpoint Security 6 protects company devices against most current threats. It proactively looks for suspicious activity
Introduction of Intrusion Detection Systems
 Introduction of Intrusion Detection Systems Why IDS? Inspects all inbound and outbound network activity and identifies a network or system attack from someone attempting to compromise a system. Detection:
Introduction of Intrusion Detection Systems Why IDS? Inspects all inbound and outbound network activity and identifies a network or system attack from someone attempting to compromise a system. Detection:
Understanding TCP/IP. Introduction. What is an Architectural Model? APPENDIX
 APPENDIX A Introduction Understanding TCP/IP To fully understand the architecture of Cisco Centri Firewall, you need to understand the TCP/IP architecture on which the Internet is based. This appendix
APPENDIX A Introduction Understanding TCP/IP To fully understand the architecture of Cisco Centri Firewall, you need to understand the TCP/IP architecture on which the Internet is based. This appendix
Network- vs. Host-based Intrusion Detection
 Network- vs. Host-based Intrusion Detection A Guide to Intrusion Detection Technology 6600 Peachtree-Dunwoody Road 300 Embassy Row Atlanta, GA 30348 Tel: 678.443.6000 Toll-free: 800.776.2362 Fax: 678.443.6477
Network- vs. Host-based Intrusion Detection A Guide to Intrusion Detection Technology 6600 Peachtree-Dunwoody Road 300 Embassy Row Atlanta, GA 30348 Tel: 678.443.6000 Toll-free: 800.776.2362 Fax: 678.443.6477
Chapter 9 Firewalls and Intrusion Prevention Systems
 Chapter 9 Firewalls and Intrusion Prevention Systems connectivity is essential However it creates a threat Effective means of protecting LANs Inserted between the premises network and the to establish
Chapter 9 Firewalls and Intrusion Prevention Systems connectivity is essential However it creates a threat Effective means of protecting LANs Inserted between the premises network and the to establish
PROFESSIONAL SECURITY SYSTEMS
 PROFESSIONAL SECURITY SYSTEMS Security policy, active protection against network attacks and management of IDP Introduction Intrusion Detection and Prevention (IDP ) is a new generation of network security
PROFESSIONAL SECURITY SYSTEMS Security policy, active protection against network attacks and management of IDP Introduction Intrusion Detection and Prevention (IDP ) is a new generation of network security
Middleware- Driven Mobile Applications
 Middleware- Driven Mobile Applications A motwin White Paper When Launching New Mobile Services, Middleware Offers the Fastest, Most Flexible Development Path for Sophisticated Apps 1 Executive Summary
Middleware- Driven Mobile Applications A motwin White Paper When Launching New Mobile Services, Middleware Offers the Fastest, Most Flexible Development Path for Sophisticated Apps 1 Executive Summary
KASPERSKY LAB. Kaspersky Administration Kit version 6.0. Administrator s manual
 KASPERSKY LAB Kaspersky Administration Kit version 6.0 Administrator s manual KASPERSKY ADMINISTRATION KIT VERSION 6.0 Administrator s manual Kaspersky Lab Visit our website: http://www.kaspersky.com/
KASPERSKY LAB Kaspersky Administration Kit version 6.0 Administrator s manual KASPERSKY ADMINISTRATION KIT VERSION 6.0 Administrator s manual Kaspersky Lab Visit our website: http://www.kaspersky.com/
Network Based Intrusion Detection Using Honey pot Deception
 Network Based Intrusion Detection Using Honey pot Deception Dr.K.V.Kulhalli, S.R.Khot Department of Electronics and Communication Engineering D.Y.Patil College of Engg.& technology, Kolhapur,Maharashtra,India.
Network Based Intrusion Detection Using Honey pot Deception Dr.K.V.Kulhalli, S.R.Khot Department of Electronics and Communication Engineering D.Y.Patil College of Engg.& technology, Kolhapur,Maharashtra,India.
Technical Specification. Solutions created by knowledge and needs
 Technical Specification Solutions created by knowledge and needs The industrial control and alarm management system that integrates video, voice and data Technical overview Process Architechture OPC-OCI
Technical Specification Solutions created by knowledge and needs The industrial control and alarm management system that integrates video, voice and data Technical overview Process Architechture OPC-OCI
Net Inspector 2015 GETTING STARTED GUIDE. MG-SOFT Corporation. Document published on October 16, 2015. (Document Version: 10.6)
 MG-SOFT Corporation Net Inspector 2015 GETTING STARTED GUIDE (Document Version: 10.6) Document published on October 16, 2015 Copyright 1995-2015 MG-SOFT Corporation Introduction In order to improve the
MG-SOFT Corporation Net Inspector 2015 GETTING STARTED GUIDE (Document Version: 10.6) Document published on October 16, 2015 Copyright 1995-2015 MG-SOFT Corporation Introduction In order to improve the
The flow back tracing and DDoS defense mechanism of the TWAREN defender cloud
 Proceedings of the APAN Network Research Workshop 2013 The flow back tracing and DDoS defense mechanism of the TWAREN defender cloud Ming-Chang Liang 1, *, Meng-Jang Lin 2, Li-Chi Ku 3, Tsung-Han Lu 4,
Proceedings of the APAN Network Research Workshop 2013 The flow back tracing and DDoS defense mechanism of the TWAREN defender cloud Ming-Chang Liang 1, *, Meng-Jang Lin 2, Li-Chi Ku 3, Tsung-Han Lu 4,
Comparison of Firewall, Intrusion Prevention and Antivirus Technologies
 White Paper Comparison of Firewall, Intrusion Prevention and Antivirus Technologies How each protects the network Juan Pablo Pereira Technical Marketing Manager Juniper Networks, Inc. 1194 North Mathilda
White Paper Comparison of Firewall, Intrusion Prevention and Antivirus Technologies How each protects the network Juan Pablo Pereira Technical Marketing Manager Juniper Networks, Inc. 1194 North Mathilda
Chapter 2 TOPOLOGY SELECTION. SYS-ED/ Computer Education Techniques, Inc.
 Chapter 2 TOPOLOGY SELECTION SYS-ED/ Computer Education Techniques, Inc. Objectives You will learn: Topology selection criteria. Perform a comparison of topology selection criteria. WebSphere component
Chapter 2 TOPOLOGY SELECTION SYS-ED/ Computer Education Techniques, Inc. Objectives You will learn: Topology selection criteria. Perform a comparison of topology selection criteria. WebSphere component
International Journal of Enterprise Computing and Business Systems ISSN (Online) : 2230-8849
 WINDOWS-BASED APPLICATION AWARE NETWORK INTERCEPTOR Ms. Shalvi Dave [1], Mr. Jimit Mahadevia [2], Prof. Bhushan Trivedi [3] [1] Asst.Prof., MCA Department, IITE, Ahmedabad, INDIA [2] Chief Architect, Elitecore
WINDOWS-BASED APPLICATION AWARE NETWORK INTERCEPTOR Ms. Shalvi Dave [1], Mr. Jimit Mahadevia [2], Prof. Bhushan Trivedi [3] [1] Asst.Prof., MCA Department, IITE, Ahmedabad, INDIA [2] Chief Architect, Elitecore
Intrusion Detection and Prevention System (IDPS) Technology- Network Behavior Analysis System (NBAS)
 ISCA Journal of Engineering Sciences ISCA J. Engineering Sci. Intrusion Detection and Prevention System (IDPS) Technology- Network Behavior Analysis System (NBAS) Abstract Tiwari Nitin, Solanki Rajdeep
ISCA Journal of Engineering Sciences ISCA J. Engineering Sci. Intrusion Detection and Prevention System (IDPS) Technology- Network Behavior Analysis System (NBAS) Abstract Tiwari Nitin, Solanki Rajdeep
White paper. TrusGuard DPX: Complete Protection against Evolving DDoS Threats. AhnLab, Inc.
 TrusGuard DPX: Complete Protection against Evolving DDoS Threats AhnLab, Inc. Table of Contents Introduction... 2 The Evolution of DDoS Attacks... 2 Typical Protection against DDoS Attacks... 3 Firewalls...
TrusGuard DPX: Complete Protection against Evolving DDoS Threats AhnLab, Inc. Table of Contents Introduction... 2 The Evolution of DDoS Attacks... 2 Typical Protection against DDoS Attacks... 3 Firewalls...
Avaya ExpertNet Lite Assessment Tool
 IP Telephony Contact Centers Mobility Services WHITE PAPER Avaya ExpertNet Lite Assessment Tool April 2005 avaya.com Table of Contents Overview... 1 Network Impact... 2 Network Paths... 2 Path Generation...
IP Telephony Contact Centers Mobility Services WHITE PAPER Avaya ExpertNet Lite Assessment Tool April 2005 avaya.com Table of Contents Overview... 1 Network Impact... 2 Network Paths... 2 Path Generation...
Network Security Demonstration - Snort based IDS Integration -
 Network Security Demonstration - Snort based IDS Integration - Hyuk Lim (hlim@gist.ac.kr) with TJ Ha, CW Jeong, J Narantuya, JW Kim Wireless Communications and Networking Lab School of Information and
Network Security Demonstration - Snort based IDS Integration - Hyuk Lim (hlim@gist.ac.kr) with TJ Ha, CW Jeong, J Narantuya, JW Kim Wireless Communications and Networking Lab School of Information and
Managing Latency in IPS Networks
 Application Note Revision B McAfee Network Security Platform Managing Latency in IPS Networks Managing Latency in IPS Networks McAfee Network Security Platform provides you with a set of pre-defined recommended
Application Note Revision B McAfee Network Security Platform Managing Latency in IPS Networks Managing Latency in IPS Networks McAfee Network Security Platform provides you with a set of pre-defined recommended
NMS300 Network Management System
 NMS300 Network Management System User Manual June 2013 202-11289-01 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing your device, locate
NMS300 Network Management System User Manual June 2013 202-11289-01 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing your device, locate
Applications of Passive Message Logging and TCP Stream Reconstruction to Provide Application-Level Fault Tolerance. Sunny Gleason COM S 717
 Applications of Passive Message Logging and TCP Stream Reconstruction to Provide Application-Level Fault Tolerance Sunny Gleason COM S 717 December 17, 2001 0.1 Introduction The proliferation of large-scale
Applications of Passive Message Logging and TCP Stream Reconstruction to Provide Application-Level Fault Tolerance Sunny Gleason COM S 717 December 17, 2001 0.1 Introduction The proliferation of large-scale
Pharos Control User Guide
 Outdoor Wireless Solution Pharos Control User Guide REV1.0.0 1910011083 Contents Contents... I Chapter 1 Quick Start Guide... 1 1.1 Introduction... 1 1.2 Installation... 1 1.3 Before Login... 8 Chapter
Outdoor Wireless Solution Pharos Control User Guide REV1.0.0 1910011083 Contents Contents... I Chapter 1 Quick Start Guide... 1 1.1 Introduction... 1 1.2 Installation... 1 1.3 Before Login... 8 Chapter
IDS / IPS. James E. Thiel S.W.A.T.
 IDS / IPS An introduction to intrusion detection and intrusion prevention systems James E. Thiel January 14, 2005 S.W.A.T. Drexel University Overview Intrusion Detection Purpose Types Detection Methods
IDS / IPS An introduction to intrusion detection and intrusion prevention systems James E. Thiel January 14, 2005 S.W.A.T. Drexel University Overview Intrusion Detection Purpose Types Detection Methods
Intrusion Detection System Based Network Using SNORT Signatures And WINPCAP
 Intrusion Detection System Based Network Using SNORT Signatures And WINPCAP Aakanksha Vijay M.tech, Department of Computer Science Suresh Gyan Vihar University Jaipur, India Mrs Savita Shiwani Head Of
Intrusion Detection System Based Network Using SNORT Signatures And WINPCAP Aakanksha Vijay M.tech, Department of Computer Science Suresh Gyan Vihar University Jaipur, India Mrs Savita Shiwani Head Of
Application Discovery Manager User s Guide vcenter Application Discovery Manager 6.2.1
 Application Discovery Manager User s Guide vcenter Application Discovery Manager 6.2.1 This document supports the version of each product listed and supports all subsequent versions until the document
Application Discovery Manager User s Guide vcenter Application Discovery Manager 6.2.1 This document supports the version of each product listed and supports all subsequent versions until the document
Cisco Application Networking for Citrix Presentation Server
 Cisco Application Networking for Citrix Presentation Server Faster Site Navigation, Less Bandwidth and Server Processing, and Greater Availability for Global Deployments What You Will Learn To address
Cisco Application Networking for Citrix Presentation Server Faster Site Navigation, Less Bandwidth and Server Processing, and Greater Availability for Global Deployments What You Will Learn To address
Configuration Information
 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
How To Test Your Web Site On Wapt On A Pc Or Mac Or Mac (Or Mac) On A Mac Or Ipad Or Ipa (Or Ipa) On Pc Or Ipam (Or Pc Or Pc) On An Ip
 Load testing with WAPT: Quick Start Guide This document describes step by step how to create a simple typical test for a web application, execute it and interpret the results. A brief insight is provided
Load testing with WAPT: Quick Start Guide This document describes step by step how to create a simple typical test for a web application, execute it and interpret the results. A brief insight is provided
HONEYD (OPEN SOURCE HONEYPOT SOFTWARE)
 HONEYD (OPEN SOURCE HONEYPOT SOFTWARE) Author: Avinash Singh Avinash Singh is a Technical Evangelist currently worksing at Appin Technology Lab, Noida. Educational Qualification: B.Tech from Punjab Technical
HONEYD (OPEN SOURCE HONEYPOT SOFTWARE) Author: Avinash Singh Avinash Singh is a Technical Evangelist currently worksing at Appin Technology Lab, Noida. Educational Qualification: B.Tech from Punjab Technical
Security+ Guide to Network Security Fundamentals, Fourth Edition. Chapter 6 Network Security
 Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 6 Network Security Objectives List the different types of network security devices and explain how they can be used Define network
Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 6 Network Security Objectives List the different types of network security devices and explain how they can be used Define network
NETWORK SECURITY (W/LAB) Course Syllabus
 6111 E. Skelly Drive P. O. Box 477200 Tulsa, OK 74147-7200 NETWORK SECURITY (W/LAB) Course Syllabus Course Number: NTWK-0008 OHLAP Credit: Yes OCAS Code: 8131 Course Length: 130 Hours Career Cluster: Information
6111 E. Skelly Drive P. O. Box 477200 Tulsa, OK 74147-7200 NETWORK SECURITY (W/LAB) Course Syllabus Course Number: NTWK-0008 OHLAP Credit: Yes OCAS Code: 8131 Course Length: 130 Hours Career Cluster: Information
Lab VI Capturing and monitoring the network traffic
 Lab VI Capturing and monitoring the network traffic 1. Goals To gain general knowledge about the network analyzers and to understand their utility To learn how to use network traffic analyzer tools (Wireshark)
Lab VI Capturing and monitoring the network traffic 1. Goals To gain general knowledge about the network analyzers and to understand their utility To learn how to use network traffic analyzer tools (Wireshark)
Configuring the BIG-IP and Check Point VPN-1 /FireWall-1
 Configuring the BIG-IP and Check Point VPN-1 /FireWall-1 Introducing the BIG-IP and Check Point VPN-1/FireWall-1 LB, HALB, VPN, and ELA configurations Configuring the BIG-IP and Check Point FireWall-1
Configuring the BIG-IP and Check Point VPN-1 /FireWall-1 Introducing the BIG-IP and Check Point VPN-1/FireWall-1 LB, HALB, VPN, and ELA configurations Configuring the BIG-IP and Check Point FireWall-1
Intruders and viruses. 8: Network Security 8-1
 Intruders and viruses 8: Network Security 8-1 Intrusion Detection Systems Firewalls allow traffic only to legitimate hosts and services Traffic to the legitimate hosts/services can have attacks CodeReds
Intruders and viruses 8: Network Security 8-1 Intrusion Detection Systems Firewalls allow traffic only to legitimate hosts and services Traffic to the legitimate hosts/services can have attacks CodeReds
VisuSniff: A Tool For The Visualization Of Network Traffic
 VisuSniff: A Tool For The Visualization Of Network Traffic Rainer Oechsle University of Applied Sciences, Trier Postbox 1826 D-54208 Trier +49/651/8103-508 oechsle@informatik.fh-trier.de Oliver Gronz University
VisuSniff: A Tool For The Visualization Of Network Traffic Rainer Oechsle University of Applied Sciences, Trier Postbox 1826 D-54208 Trier +49/651/8103-508 oechsle@informatik.fh-trier.de Oliver Gronz University
How To Manage Sourcefire From A Command Console
 Sourcefire TM Sourcefire Capabilities Store up to 100,000,000 security & host events, including packet data Centralized policy & sensor management Centralized audit logging of configuration & security
Sourcefire TM Sourcefire Capabilities Store up to 100,000,000 security & host events, including packet data Centralized policy & sensor management Centralized audit logging of configuration & security
Scalable Linux Clusters with LVS
 Scalable Linux Clusters with LVS Considerations and Implementation, Part I Eric Searcy Tag1 Consulting, Inc. emsearcy@tag1consulting.com April 2008 Abstract Whether you are perusing mailing lists or reading
Scalable Linux Clusters with LVS Considerations and Implementation, Part I Eric Searcy Tag1 Consulting, Inc. emsearcy@tag1consulting.com April 2008 Abstract Whether you are perusing mailing lists or reading
Fuzzy Network Profiling for Intrusion Detection
 Fuzzy Network Profiling for Intrusion Detection John E. Dickerson (jedicker@iastate.edu) and Julie A. Dickerson (julied@iastate.edu) Electrical and Computer Engineering Department Iowa State University
Fuzzy Network Profiling for Intrusion Detection John E. Dickerson (jedicker@iastate.edu) and Julie A. Dickerson (julied@iastate.edu) Electrical and Computer Engineering Department Iowa State University
Intrusion Detection Systems and Supporting Tools. Ian Welch NWEN 405 Week 12
 Intrusion Detection Systems and Supporting Tools Ian Welch NWEN 405 Week 12 IDS CONCEPTS Firewalls. Intrusion detection systems. Anderson publishes paper outlining security problems 1972 DNS created 1984
Intrusion Detection Systems and Supporting Tools Ian Welch NWEN 405 Week 12 IDS CONCEPTS Firewalls. Intrusion detection systems. Anderson publishes paper outlining security problems 1972 DNS created 1984
10 Configuring Packet Filtering and Routing Rules
 Blind Folio 10:1 10 Configuring Packet Filtering and Routing Rules CERTIFICATION OBJECTIVES 10.01 Understanding Packet Filtering and Routing 10.02 Creating and Managing Packet Filtering 10.03 Configuring
Blind Folio 10:1 10 Configuring Packet Filtering and Routing Rules CERTIFICATION OBJECTIVES 10.01 Understanding Packet Filtering and Routing 10.02 Creating and Managing Packet Filtering 10.03 Configuring
A Brief. Introduction. of MG-SOFT s SNMP Network Management Products. Document Version 1.3, published in June, 2008
 A Brief Introduction of MG-SOFT s SNMP Network Management Products Document Version 1.3, published in June, 2008 MG-SOFT s SNMP Products Overview SNMP Management Products MIB Browser Pro. for Windows and
A Brief Introduction of MG-SOFT s SNMP Network Management Products Document Version 1.3, published in June, 2008 MG-SOFT s SNMP Products Overview SNMP Management Products MIB Browser Pro. for Windows and
Seminar Computer Security
 Seminar Computer Security DoS/DDoS attacks and botnets Hannes Korte Overview Introduction What is a Denial of Service attack? The distributed version The attacker's motivation Basics Bots and botnets Example
Seminar Computer Security DoS/DDoS attacks and botnets Hannes Korte Overview Introduction What is a Denial of Service attack? The distributed version The attacker's motivation Basics Bots and botnets Example
Per-Flow Queuing Allot's Approach to Bandwidth Management
 White Paper Per-Flow Queuing Allot's Approach to Bandwidth Management Allot Communications, July 2006. All Rights Reserved. Table of Contents Executive Overview... 3 Understanding TCP/IP... 4 What is Bandwidth
White Paper Per-Flow Queuing Allot's Approach to Bandwidth Management Allot Communications, July 2006. All Rights Reserved. Table of Contents Executive Overview... 3 Understanding TCP/IP... 4 What is Bandwidth
Computer Networks/DV2 Lab
 Computer Networks/DV2 Lab Room: BB 219 Additional Information: http://www.fb9dv.uni-duisburg.de/ti/en/education/teaching/ss08/netlab Equipment for each group: - 1 Server computer (OS: Windows 2000 Advanced
Computer Networks/DV2 Lab Room: BB 219 Additional Information: http://www.fb9dv.uni-duisburg.de/ti/en/education/teaching/ss08/netlab Equipment for each group: - 1 Server computer (OS: Windows 2000 Advanced
Firewalls and Intrusion Detection
 Firewalls and Intrusion Detection What is a Firewall? A computer system between the internal network and the rest of the Internet A single computer or a set of computers that cooperate to perform the firewall
Firewalls and Intrusion Detection What is a Firewall? A computer system between the internal network and the rest of the Internet A single computer or a set of computers that cooperate to perform the firewall
Performance Management Platform
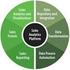 Open EMS Suite by Nokia Performance Management Platform Functional Overview Version 1.4 Nokia Siemens Networks 1 (16) Performance Management Platform The information in this document is subject to change
Open EMS Suite by Nokia Performance Management Platform Functional Overview Version 1.4 Nokia Siemens Networks 1 (16) Performance Management Platform The information in this document is subject to change
CS 356 Lecture 17 and 18 Intrusion Detection. Spring 2013
 CS 356 Lecture 17 and 18 Intrusion Detection Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists
CS 356 Lecture 17 and 18 Intrusion Detection Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists
HoneyBOT User Guide A Windows based honeypot solution
 HoneyBOT User Guide A Windows based honeypot solution Visit our website at http://www.atomicsoftwaresolutions.com/ Table of Contents What is a Honeypot?...2 How HoneyBOT Works...2 Secure the HoneyBOT Computer...3
HoneyBOT User Guide A Windows based honeypot solution Visit our website at http://www.atomicsoftwaresolutions.com/ Table of Contents What is a Honeypot?...2 How HoneyBOT Works...2 Secure the HoneyBOT Computer...3
Agenda. Taxonomy of Botnet Threats. Background. Summary. Background. Taxonomy. Trend Micro Inc. Presented by Tushar Ranka
 Taxonomy of Botnet Threats Trend Micro Inc. Presented by Tushar Ranka Agenda Summary Background Taxonomy Attacking Behavior Command & Control Rallying Mechanisms Communication Protocols Evasion Techniques
Taxonomy of Botnet Threats Trend Micro Inc. Presented by Tushar Ranka Agenda Summary Background Taxonomy Attacking Behavior Command & Control Rallying Mechanisms Communication Protocols Evasion Techniques
GFI Product Manual. Administration and Configuration Manual
 GFI Product Manual Administration and Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and is provided "as is"
GFI Product Manual Administration and Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and is provided "as is"
Intelligent Worms: Searching for Preys
 Intelligent Worms: Searching for Preys By Zesheng Chen and Chuanyi Ji ABOUT THE AUTHORS. Zesheng Chen is currently a Ph.D. Candidate in the Communication Networks and Machine Learning Group at the School
Intelligent Worms: Searching for Preys By Zesheng Chen and Chuanyi Ji ABOUT THE AUTHORS. Zesheng Chen is currently a Ph.D. Candidate in the Communication Networks and Machine Learning Group at the School
LASTLINE WHITEPAPER. Large-Scale Detection of Malicious Web Pages
 LASTLINE WHITEPAPER Large-Scale Detection of Malicious Web Pages Abstract Malicious web pages that host drive-by-download exploits have become a popular means for compromising hosts on the Internet and,
LASTLINE WHITEPAPER Large-Scale Detection of Malicious Web Pages Abstract Malicious web pages that host drive-by-download exploits have become a popular means for compromising hosts on the Internet and,
IT Architecture Review. ISACA Conference Fall 2003
 IT Architecture Review ISACA Conference Fall 2003 Table of Contents Introduction Business Drivers Overview of Tiered Architecture IT Architecture Review Why review IT architecture How to conduct IT architecture
IT Architecture Review ISACA Conference Fall 2003 Table of Contents Introduction Business Drivers Overview of Tiered Architecture IT Architecture Review Why review IT architecture How to conduct IT architecture
Configuration Information
 Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
Basic & Advanced Administration for Citrix NetScaler 9.2
 Basic & Advanced Administration for Citrix NetScaler 9.2 Day One Introducing and deploying Citrix NetScaler Key - Brief Introduction to the NetScaler system Planning a NetScaler deployment Deployment scenarios
Basic & Advanced Administration for Citrix NetScaler 9.2 Day One Introducing and deploying Citrix NetScaler Key - Brief Introduction to the NetScaler system Planning a NetScaler deployment Deployment scenarios
Quick Start for Network Agent. 5-Step Quick Start. What is Network Agent?
 What is Network Agent? The Websense Network Agent software component uses sniffer technology to monitor all of the internet traffic on the network machines that you assign to it. Network Agent filters
What is Network Agent? The Websense Network Agent software component uses sniffer technology to monitor all of the internet traffic on the network machines that you assign to it. Network Agent filters
Detection of Distributed Denial of Service Attack with Hadoop on Live Network
 Detection of Distributed Denial of Service Attack with Hadoop on Live Network Suchita Korad 1, Shubhada Kadam 2, Prajakta Deore 3, Madhuri Jadhav 4, Prof.Rahul Patil 5 Students, Dept. of Computer, PCCOE,
Detection of Distributed Denial of Service Attack with Hadoop on Live Network Suchita Korad 1, Shubhada Kadam 2, Prajakta Deore 3, Madhuri Jadhav 4, Prof.Rahul Patil 5 Students, Dept. of Computer, PCCOE,
A Critical Investigation of Botnet
 Global Journal of Computer Science and Technology Network, Web & Security Volume 13 Issue 9 Version 1.0 Year 2013 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals
Global Journal of Computer Science and Technology Network, Web & Security Volume 13 Issue 9 Version 1.0 Year 2013 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals
Firewall Introduction Several Types of Firewall. Cisco PIX Firewall
 Firewall Introduction Several Types of Firewall. Cisco PIX Firewall What is a Firewall? Non-computer industries: a wall that controls the spreading of a fire. Networks: a designed device that controls
Firewall Introduction Several Types of Firewall. Cisco PIX Firewall What is a Firewall? Non-computer industries: a wall that controls the spreading of a fire. Networks: a designed device that controls
A Tool for Evaluation and Optimization of Web Application Performance
 A Tool for Evaluation and Optimization of Web Application Performance Tomáš Černý 1 cernyto3@fel.cvut.cz Michael J. Donahoo 2 jeff_donahoo@baylor.edu Abstract: One of the main goals of web application
A Tool for Evaluation and Optimization of Web Application Performance Tomáš Černý 1 cernyto3@fel.cvut.cz Michael J. Donahoo 2 jeff_donahoo@baylor.edu Abstract: One of the main goals of web application
ExtraHop and AppDynamics Deployment Guide
 ExtraHop and AppDynamics Deployment Guide This guide describes how to use ExtraHop and AppDynamics to provide real-time, per-user transaction tracing across the entire application delivery chain. ExtraHop
ExtraHop and AppDynamics Deployment Guide This guide describes how to use ExtraHop and AppDynamics to provide real-time, per-user transaction tracing across the entire application delivery chain. ExtraHop
FioranoMQ 9. High Availability Guide
 FioranoMQ 9 High Availability Guide Copyright (c) 1999-2008, Fiorano Software Technologies Pvt. Ltd., Copyright (c) 2008-2009, Fiorano Software Pty. Ltd. All rights reserved. This software is the confidential
FioranoMQ 9 High Availability Guide Copyright (c) 1999-2008, Fiorano Software Technologies Pvt. Ltd., Copyright (c) 2008-2009, Fiorano Software Pty. Ltd. All rights reserved. This software is the confidential
SILVER PEAK ACCELERATION WITH EMC VSPEX PRIVATE CLOUD WITH RECOVERPOINT FOR VMWARE VSPHERE
 VSPEX IMPLEMENTATION GUIDE SILVER PEAK ACCELERATION WITH EMC VSPEX PRIVATE CLOUD WITH RECOVERPOINT FOR VMWARE VSPHERE Silver Peak Abstract This Implementation Guide describes the deployment of Silver Peak
VSPEX IMPLEMENTATION GUIDE SILVER PEAK ACCELERATION WITH EMC VSPEX PRIVATE CLOUD WITH RECOVERPOINT FOR VMWARE VSPHERE Silver Peak Abstract This Implementation Guide describes the deployment of Silver Peak
VXLAN: Scaling Data Center Capacity. White Paper
 VXLAN: Scaling Data Center Capacity White Paper Virtual Extensible LAN (VXLAN) Overview This document provides an overview of how VXLAN works. It also provides criteria to help determine when and where
VXLAN: Scaling Data Center Capacity White Paper Virtual Extensible LAN (VXLAN) Overview This document provides an overview of how VXLAN works. It also provides criteria to help determine when and where
PATROL Internet Server Manager Technical Brief
 PATROL Internet Server Manager Technical Brief Contents Why Manage Web Applications?...1 What Is PATROL?...1 The PATROL Agent...2 PATROL Knowledge Modules...2 The PATROL Console...2 PATROL Internet Server
PATROL Internet Server Manager Technical Brief Contents Why Manage Web Applications?...1 What Is PATROL?...1 The PATROL Agent...2 PATROL Knowledge Modules...2 The PATROL Console...2 PATROL Internet Server
Monitoring Infrastructure (MIS) Software Architecture Document. Version 1.1
 Monitoring Infrastructure (MIS) Software Architecture Document Version 1.1 Revision History Date Version Description Author 28-9-2004 1.0 Created Peter Fennema 8-10-2004 1.1 Processed review comments Peter
Monitoring Infrastructure (MIS) Software Architecture Document Version 1.1 Revision History Date Version Description Author 28-9-2004 1.0 Created Peter Fennema 8-10-2004 1.1 Processed review comments Peter
DEPLOYMENT GUIDE Version 1.1. Deploying the BIG-IP LTM v10 with Citrix Presentation Server 4.5
 DEPLOYMENT GUIDE Version 1.1 Deploying the BIG-IP LTM v10 with Citrix Presentation Server 4.5 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Citrix Presentation Server Prerequisites
DEPLOYMENT GUIDE Version 1.1 Deploying the BIG-IP LTM v10 with Citrix Presentation Server 4.5 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Citrix Presentation Server Prerequisites
Comprehensive IP Traffic Monitoring with FTAS System
 Comprehensive IP Traffic Monitoring with FTAS System Tomáš Košňar kosnar@cesnet.cz CESNET, association of legal entities Prague, Czech Republic Abstract System FTAS is designed for large-scale continuous
Comprehensive IP Traffic Monitoring with FTAS System Tomáš Košňar kosnar@cesnet.cz CESNET, association of legal entities Prague, Czech Republic Abstract System FTAS is designed for large-scale continuous
Introducing the BIG-IP and SharePoint Portal Server 2003 configuration
 Deployment Guide Deploying Microsoft SharePoint Portal Server 2003 and the F5 BIG-IP System Introducing the BIG-IP and SharePoint Portal Server 2003 configuration F5 and Microsoft have collaborated on
Deployment Guide Deploying Microsoft SharePoint Portal Server 2003 and the F5 BIG-IP System Introducing the BIG-IP and SharePoint Portal Server 2003 configuration F5 and Microsoft have collaborated on
JK0 015 CompTIA E2C Security+ (2008 Edition) Exam
 JK0 015 CompTIA E2C Security+ (2008 Edition) Exam Version 4.1 QUESTION NO: 1 Which of the following devices would be used to gain access to a secure network without affecting network connectivity? A. Router
JK0 015 CompTIA E2C Security+ (2008 Edition) Exam Version 4.1 QUESTION NO: 1 Which of the following devices would be used to gain access to a secure network without affecting network connectivity? A. Router
Endpoint Based Policy Management: The Road Ahead
 Endpoint Based Policy Management: The Road Ahead Introduction In a rapidly growing and crowded security solutions market, organizations need to deploy the most effective technologies taking into consideration
Endpoint Based Policy Management: The Road Ahead Introduction In a rapidly growing and crowded security solutions market, organizations need to deploy the most effective technologies taking into consideration
Performance of Cisco IPS 4500 and 4300 Series Sensors
 White Paper Performance of Cisco IPS 4500 and 4300 Series Sensors White Paper September 2012 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of
White Paper Performance of Cisco IPS 4500 and 4300 Series Sensors White Paper September 2012 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of
Denial of Service Attacks, What They are and How to Combat Them
 Denial of Service Attacks, What They are and How to Combat Them John P. Pironti, CISSP Genuity, Inc. Principal Enterprise Solutions Architect Principal Security Consultant Version 1.0 November 12, 2001
Denial of Service Attacks, What They are and How to Combat Them John P. Pironti, CISSP Genuity, Inc. Principal Enterprise Solutions Architect Principal Security Consultant Version 1.0 November 12, 2001
Cisco Application Networking for IBM WebSphere
 Cisco Application Networking for IBM WebSphere Faster Downloads and Site Navigation, Less Bandwidth and Server Processing, and Greater Availability for Global Deployments What You Will Learn To address
Cisco Application Networking for IBM WebSphere Faster Downloads and Site Navigation, Less Bandwidth and Server Processing, and Greater Availability for Global Deployments What You Will Learn To address
Detecting Computer Worms in the Cloud
 Detecting Computer Worms in the Cloud Sebastian Biedermann and Stefan Katzenbeisser Security Engineering Group Department of Computer Science Technische Universität Darmstadt {biedermann,katzenbeisser}@seceng.informatik.tu-darmstadt.de
Detecting Computer Worms in the Cloud Sebastian Biedermann and Stefan Katzenbeisser Security Engineering Group Department of Computer Science Technische Universität Darmstadt {biedermann,katzenbeisser}@seceng.informatik.tu-darmstadt.de
WhatsUp Gold v11 Features Overview
 WhatsUp Gold v11 Features Overview This guide provides an overview of the core functionality of WhatsUp Gold v11, and introduces interesting features and processes that help users maximize productivity
WhatsUp Gold v11 Features Overview This guide provides an overview of the core functionality of WhatsUp Gold v11, and introduces interesting features and processes that help users maximize productivity
Detecting peer-to-peer botnets
 Detecting peer-to-peer botnets Reinier Schoof & Ralph Koning System and Network Engineering University of Amsterdam mail: reinier.schoof@os3.nl, ralph.koning@os3.nl February 4, 2007 1 Introduction Spam,
Detecting peer-to-peer botnets Reinier Schoof & Ralph Koning System and Network Engineering University of Amsterdam mail: reinier.schoof@os3.nl, ralph.koning@os3.nl February 4, 2007 1 Introduction Spam,
