After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application.
|
|
|
- Juniper Burke
- 8 years ago
- Views:
Transcription
1 Rohos Disk Encryption - creates hidden and password protected partitions on the computer or USB flash drive. With megabytes of sensitive files and private data on your computer or USB drive you can not imagine life without the hidden partition that is created using this wonderful tool. It has a separate portable tool that allows accessing encrypted partition on USB flash drive from any PC where you work as a guest or user with no admin rights. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 Click on Encrypt USB drive The program automatically determines the best Rohos disk options for your system. It will create a partition namely I: with 900 Mb space. You can customize the partition size, disk letter and file system by clicking [Change ]. screen shot 2 Tesline-Service S.R.L. All rights reserved
2 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive s available free space. Also file system may be changed. By default, Rohos Disk Encryption creates disk in NTFS but it may be changed to FAT/FAT32. After all disk settings are adjusted you may insert a password to Rohos disk, confirm it and click on Create disk. screen shot 4 Tesline-Service S.R.L. All rights reserved
3 screen shot 5 It should take a few seconds to create an encrypted volume on your USB device. screen shot 6 Portable Application allows working with a password protected partition on any PC, you just click on Rohos Mini.exe icon on the USB flash drive root folder Tesline-Service S.R.L. All rights reserved
4 screen shot 7 and enter disk password. screen shot 8 Now your Rohos disk is accessible from Windows Explorer. And double-clicking on it you have access to your encrypted files to edit and save files, listen to music and look through your pictures. screen shot 9 After you finished working with your encrypted files you may disconnect Rohos disk using Rohos icon in the system tray. screen shot 10 Tesline-Service S.R.L. All rights reserved
5 Hide Folder With this feature your protected items can be quickly and easily rendered inaccessible to other users but are instantly accessible when you turn on your Rohos disk. Security benefits with Hide Folder feature: Allows encrypting any regular folder on the computer. Password protect any Application folder, for example C:\Program Files\Firefox Encrypt and hide your Skype chat, received files, contacts, Skype password; Google Chome history, favorites, form data (credit card number), saved passwords. How it works: Turn on your Rohos disk -> click on Hide folder link in the program s main window screen shot 11 In the Hide folder dialogue window there are given predefined folders, e.g. My Documents, Google Chrome data, Skype, etc. You ll need to choose a folder that will be linked with your Rohos disk. screen shot 12 In our case we have chosen to encrypt/ password protect Skype profile. Then all you have to do is to click on OK button. Tesline-Service S.R.L. All rights reserved
6 From now on you folder will be encrypted and hidden, and accessible only after your Rohos disk is turned on. Encrypt HDD Using Rohos Disk Encryption you may encrypt your HDD. At right bottom of Rohos Disk main window click on Create another one link screen shot 13 You may change Rohos disk image path clicking on [Change ]. Rohos Disk displays the available free disk space on disk drives. You may change the disk drive by clicking on the button next to the field with Rohos Disk proposed disk drive. Other parameters may also be changed. Specify your Rohos disk password, confirm it and click on Create disk button Tesline-Service S.R.L. All rights reserved
7 Have USB Key for access control You can use any USB flash drive or security tokens like Aladdin etoken to access your secured disk automatically without need to remember and enter password manually. In Rohos Disk main window click on Setup USB Key Screen shot 14 Insert password for Rohos disk access and Click on Setup USB Key button By clicking on drop-down window you may choose the type of device to use for Rohos disk access Please, note that in case you have got several Rohos encrypted disks you may specify the one you would like to be accessed by USB Key (only one). Click on [Specify ] next to Disk. Favorite disk In Windows Explorer choose the appropriate Rohos disk image-file (rdisk.rdi) and click OK Tesline-Service S.R.L. All rights reserved
8 Rohos disk options You can set up Hotkeys to quickly disconnect encrypted disk and create a password to access Rohos main window. Screen shot 15 Steganography Hide your sensitive files into a single AVI movie or media file such as MP3, OGG, WMA etc. In Rohos Disk main window click on Create Rohos Disk within media file link Screen shot 16 Click on the link Choose media file link Specify Rohos disk password and click Create disk button Other Rohos Disk features By clicking on Tools in Rohos Disk main window you may: 1. Enlarge your Rohos disk (one at a time) 2. Check Rohos disk for errors in case your Rohos disk doesn t get connected. 3. Delete disk easy as 1, 2, 3 4. Change password of your Rohos disk Tesline-Service S.R.L. All rights reserved
9 5. Create Password Reset file but remember to keep a secret where you have saved this file 6. Make a shortcut to the disk on your desktop - creating disk shortcut just with one mouse click. screen shot 17 Integrated File-Shredder Any file or folder can be easily moved into Encrypted Rohos disk with shredding afterwards. This tool helps you to delete file reliably and be sure that nobody can recover it. screen shot 18 Tesline-Service S.R.L. All rights reserved
10 Access your Rohos portable partition on a PC without Admin rights On a computer without administrative rights Rohos Mini Drive Portable will automatically be launched and you will be able to work with your encrypted partition, which is seen as Windows Explorer. screen shot 19 You can run any application and work with your hidden volume as usual - open, copy, edit files, view images, ect. screen shot 20 Rohos Mini Drive Portable utility uses on the fly encryption principle, thus the program doesn t save files in temporary folder and doesn t leave unencrypted data on a PC or unprotected part of USB flash drive. When you open a file such as MS Word document, MS Word application will read and write changes to the file using Rohos Mini Drive Portable. When you run the program, the *. exe will be decrypted and run in the program memory. Tesline-Service S.R.L. All rights reserved
11 Virtual Keyboard will help you to protect your encrypted disk password from a key-logger. Screen shot 21 Rohos Disk Encryption download page - Rohos Disk Encryption home page - Rohos Mini Drive Portable page - Type: Shareware (30-day trial version) Tesline-Service S.R.L. All rights reserved
Guide how to protect your private data with Rohos Disk Encryption
 Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options
Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options
Here is a guide on how to encrypt a part of your USB flash drive and access it on any computer:
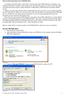 How to password protect your USB flash drive. According to the XXX agency reports 80% of all lost and stolen USB flash drives contained a very important information: business or government data. The following
How to password protect your USB flash drive. According to the XXX agency reports 80% of all lost and stolen USB flash drives contained a very important information: business or government data. The following
Step by step guide how to password protect your USB flash drive
 Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
www.rohos.com Two-factor authentication Free portable encryption for USB drive Hardware disk encryption Face recognition logon
 Two-factor authentication Free portable encryption for USB drive Hardware disk encryption Face recognition logon Secure Windows and Mac login by USB key www.rohos.com Rohos Logon Key Secure two-factor
Two-factor authentication Free portable encryption for USB drive Hardware disk encryption Face recognition logon Secure Windows and Mac login by USB key www.rohos.com Rohos Logon Key Secure two-factor
MAC/OSX - How to Encrypt Data using TrueCrypt. v.05201011
 MAC/OSX - How to Encrypt Data using TrueCrypt v.05201011 This chapter contains step-by-step instructions on how to create, mount, and use a TrueCrypt volume. We strongly recommend that you read the entire
MAC/OSX - How to Encrypt Data using TrueCrypt v.05201011 This chapter contains step-by-step instructions on how to create, mount, and use a TrueCrypt volume. We strongly recommend that you read the entire
Verbatim Secure Data USB Drive. User Guide. User Guide Version 2.0 All rights reserved
 Verbatim Secure Data USB Drive User Guide User Guide Version 2.0 All rights reserved Table of Contents Table of Contents... 2 1. Introduction to Verbatim Secure Data USB Drive... 3 2. System Requirements...
Verbatim Secure Data USB Drive User Guide User Guide Version 2.0 All rights reserved Table of Contents Table of Contents... 2 1. Introduction to Verbatim Secure Data USB Drive... 3 2. System Requirements...
USB Flash Security Free Edition Quick Start
 Quick Start [For USB Flash Security Free Edition] 1 / 18 USB Flash Security Free Edition Quick Start Before use USB Flash Security 1. Free edition can only be installed on the USB Flash Drive up to 4GB
Quick Start [For USB Flash Security Free Edition] 1 / 18 USB Flash Security Free Edition Quick Start Before use USB Flash Security 1. Free edition can only be installed on the USB Flash Drive up to 4GB
Encrypting a USB Drive Using TrueCrypt
 Encrypting a USB Drive Using TrueCrypt This document details the steps to encrypt a USB Pen drive using TrueCrypt. TrueCrypt is free and open-source security software allowing encryption of documents and
Encrypting a USB Drive Using TrueCrypt This document details the steps to encrypt a USB Pen drive using TrueCrypt. TrueCrypt is free and open-source security software allowing encryption of documents and
SecureLock. User Manual
 SecureLock User Manual Encryption Application for portable Storage Devices User Manual Version 1.0.0.3 2004-2011 Integral Memory plc Table of Contents Table of Contents... 2 1. Introduction... 3 2. System
SecureLock User Manual Encryption Application for portable Storage Devices User Manual Version 1.0.0.3 2004-2011 Integral Memory plc Table of Contents Table of Contents... 2 1. Introduction... 3 2. System
How to create a portable encrypted USB Key using TrueCrypt
 How to create a portable encrypted USB Key using TrueCrypt INTRODUCTION TrueCrypt Traveler Mode provides secure encryption for programs/files on portable devices such as USB Memory keys. It uses strong
How to create a portable encrypted USB Key using TrueCrypt INTRODUCTION TrueCrypt Traveler Mode provides secure encryption for programs/files on portable devices such as USB Memory keys. It uses strong
Contents. Getting Started...1. Managing Your Drives...14. Backing Up & Restoring Folders...28. Synchronizing Folders...48. Managing Security...
 Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
User Manual - Secure Lock Ware
 User Manual - Secure Lock Ware Drive Encryption System Ultra High Security - 256-bit Capable AES Encryption for Buffalo USB Hard Drives www.buffalotech.com v1.8 Table of Contents Introduction.................................
User Manual - Secure Lock Ware Drive Encryption System Ultra High Security - 256-bit Capable AES Encryption for Buffalo USB Hard Drives www.buffalotech.com v1.8 Table of Contents Introduction.................................
SSH Secure Client (Telnet & SFTP) Installing & Using SSH Secure Shell for Windows Operation Systems
 SSH Secure Client (Telnet & SFTP) Installing & Using SSH Secure Shell for Windows Operation Systems What is SSH?: SSH is an application that protects the TCP/IP connections between two computers. The software
SSH Secure Client (Telnet & SFTP) Installing & Using SSH Secure Shell for Windows Operation Systems What is SSH?: SSH is an application that protects the TCP/IP connections between two computers. The software
Windows Data Recovery Home 6.0
 Installation Guide Stellar Phoenix Windows Data Recovery Home 6.0 Overview Stellar Phoenix Windows Data Recovery - Home edition is a complete solution to recover lost data from your hard disks and removable
Installation Guide Stellar Phoenix Windows Data Recovery Home 6.0 Overview Stellar Phoenix Windows Data Recovery - Home edition is a complete solution to recover lost data from your hard disks and removable
Only smart people read the manual.
 Only smart people read the manual. Contents Getting Started... 1 Installing the FreeAgent Tools... 1 Using the FreeAgent Tools Icons... 9 Using the System Tray Icon... 10 Disconnecting the FreeAgent Drive...
Only smart people read the manual. Contents Getting Started... 1 Installing the FreeAgent Tools... 1 Using the FreeAgent Tools Icons... 9 Using the System Tray Icon... 10 Disconnecting the FreeAgent Drive...
2. To encrypt the drive for future use, click Yes (Fig 1, 2). This will start the encryption process.
 Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Comodo Disk Encryption
 Comodo Disk Encryption Version 2.0 User Guide Version 2.0.122010 Versi Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1.Comodo Disk Encryption Introduction... 3
Comodo Disk Encryption Version 2.0 User Guide Version 2.0.122010 Versi Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1.Comodo Disk Encryption Introduction... 3
HDDtoGO. User Guide. User Manual Version 3.4 2004-2010 CoSoSys SRL 2010 A-DATA Technology Co., Ltd. HDDtoGO User Manual
 HDDtoGO User Guide User Manual Version 3.4 2004-2010 CoSoSys SRL 2010 A-DATA Technology Co., Ltd. HDDtoGO User Manual Table of Contents Table of Contents...1 1. Introduction...2 2. System Requirements...3
HDDtoGO User Guide User Manual Version 3.4 2004-2010 CoSoSys SRL 2010 A-DATA Technology Co., Ltd. HDDtoGO User Manual Table of Contents Table of Contents...1 1. Introduction...2 2. System Requirements...3
Kaspersky Password Manager USER GUIDE
 Kaspersky Password Manager USER GUIDE Dear User! Thank you for choosing our product. We hope that this documentation helps you in your work and provides answers you may need. Any type of reproduction or
Kaspersky Password Manager USER GUIDE Dear User! Thank you for choosing our product. We hope that this documentation helps you in your work and provides answers you may need. Any type of reproduction or
Carry it Easy. User Guide
 Carry it Easy User Guide User Manual Version 3.2 2004-2010 CoSoSys Ltd. Carry it Easy User Manual Table of Contents Table of Contents... I 1. Introduction... 1 2. System Requirements... 1 3. Installation...
Carry it Easy User Guide User Manual Version 3.2 2004-2010 CoSoSys Ltd. Carry it Easy User Manual Table of Contents Table of Contents... I 1. Introduction... 1 2. System Requirements... 1 3. Installation...
Stellar Phoenix Windows Data Recovery. Stellar Phoenix Windows Data Recovery 5.0 User Guide
 Stellar Phoenix Windows Data Recovery Stellar Phoenix Windows Data Recovery 5.0 User Guide Overview Stellar Phoenix Windows Data Recovery - Professional edition is a complete solution to recover lost data
Stellar Phoenix Windows Data Recovery Stellar Phoenix Windows Data Recovery 5.0 User Guide Overview Stellar Phoenix Windows Data Recovery - Professional edition is a complete solution to recover lost data
EMAILING USING HOTMAIL
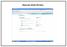 EMAILING USING HOTMAIL Signing into Your Email Account Open up explorer and type in www.hotmail.com in the address bar. Enter your email address. Hit the tab key on the keyboard and enter your password.
EMAILING USING HOTMAIL Signing into Your Email Account Open up explorer and type in www.hotmail.com in the address bar. Enter your email address. Hit the tab key on the keyboard and enter your password.
EasyLock. User Manual. Intuitive Encryption Application for portable Storage Devices
 1 EasyLock User Manual Intuitive Encryption Application for portable Storage Devices User Manual Version 1.0.0.8 2004-2010 CoSoSys Ltd. 2 Table of Contents Table of Contents... 2 1. Introduction... 3 2.
1 EasyLock User Manual Intuitive Encryption Application for portable Storage Devices User Manual Version 1.0.0.8 2004-2010 CoSoSys Ltd. 2 Table of Contents Table of Contents... 2 1. Introduction... 3 2.
Cloud Catcher TM Software
 Cloud Catcher TM Software User Manual Version 2.0 Technical Support SanDisk Knowledgebase Contact SanDisk Table of Contents Overview... 2 Minimum System Requirements... 2 Languages Supported... 2 Installing
Cloud Catcher TM Software User Manual Version 2.0 Technical Support SanDisk Knowledgebase Contact SanDisk Table of Contents Overview... 2 Minimum System Requirements... 2 Languages Supported... 2 Installing
Practical Application How to Use a Flash Drive
 Practical Application How to Use a Flash Drive Practical application How to Use a Flash Drive Page 1 of 6 About this Practical Application Prerequisite Skills To use this Application you will need be comfortable
Practical Application How to Use a Flash Drive Practical application How to Use a Flash Drive Page 1 of 6 About this Practical Application Prerequisite Skills To use this Application you will need be comfortable
Surf it Easy. User Guide
 Surf it Easy User Guide User Manual Version 1.1 2004 CoSoSys SRL Surf it Easy User Manual Table of Contents Table of Contents... I 1. Introduction... 1 2. System Requirements... 2 3. Installation... 2
Surf it Easy User Guide User Manual Version 1.1 2004 CoSoSys SRL Surf it Easy User Manual Table of Contents Table of Contents... I 1. Introduction... 1 2. System Requirements... 2 3. Installation... 2
Clickfree Software User Guide
 Clickfree Software User Guide Last Revised: Nov 2, 2011 Clickfree_backup_software_user_guide_v1.0 Clickfree and the Clickfree logo are trademarks or registered trademarks of Storage Appliance Corporation.
Clickfree Software User Guide Last Revised: Nov 2, 2011 Clickfree_backup_software_user_guide_v1.0 Clickfree and the Clickfree logo are trademarks or registered trademarks of Storage Appliance Corporation.
How to Encrypt your Windows 7 SDS Machine with Bitlocker
 How to Encrypt your Windows 7 SDS Machine with Bitlocker ************************************ IMPORTANT ******************************************* Before encrypting your SDS Windows 7 Machine it is highly
How to Encrypt your Windows 7 SDS Machine with Bitlocker ************************************ IMPORTANT ******************************************* Before encrypting your SDS Windows 7 Machine it is highly
Chapter 4. Backup / Restore
 Recovery Guide 9 Restoring with the OS CD (Only for models that ship with the operating system CD) 98 Samsung Recovery Solution (Optional) 00 Recovery Guide 9 This section describes how to restore your
Recovery Guide 9 Restoring with the OS CD (Only for models that ship with the operating system CD) 98 Samsung Recovery Solution (Optional) 00 Recovery Guide 9 This section describes how to restore your
USER MANUAL. v. 1.0.0.95 Windows Client ------------------------ January 2014 ------------------------
 USER MANUAL v. 1.0.0.95 Windows Client ------------------------ January 2014 ------------------------ 1 Contents At a Glance Troubleshoot 3 About SkyCrypt 23 FAQ 4 About this manual 23 Contact support
USER MANUAL v. 1.0.0.95 Windows Client ------------------------ January 2014 ------------------------ 1 Contents At a Glance Troubleshoot 3 About SkyCrypt 23 FAQ 4 About this manual 23 Contact support
Acer erecovery Management
 Acer erecovery Management The Acer erecovery Management provides fast, reliable and safe method of restoring your computer to its factory default settings or user-defined system configuration from an image
Acer erecovery Management The Acer erecovery Management provides fast, reliable and safe method of restoring your computer to its factory default settings or user-defined system configuration from an image
1. Scope of Service. 1.1 About Boxcryptor Classic
 Manual for Mac OS X Content 1. Scope of Service... 3 1.1 About Boxcryptor Classic... 3 1.2 About this manual... 4 2. Installation... 5 2.1 Installing Boxcryptor Classic... 5 2.2 Licensing Boxcryptor Classic
Manual for Mac OS X Content 1. Scope of Service... 3 1.1 About Boxcryptor Classic... 3 1.2 About this manual... 4 2. Installation... 5 2.1 Installing Boxcryptor Classic... 5 2.2 Licensing Boxcryptor Classic
Samsung Drive Manager User Manual
 Samsung Drive Manager User Manual The contents of this manual are subject to change without notice. Companies, names and data used in examples are not actual companies, names or data unless otherwise noted.
Samsung Drive Manager User Manual The contents of this manual are subject to change without notice. Companies, names and data used in examples are not actual companies, names or data unless otherwise noted.
Last modified on 03-01-2010 for application version 4.4.4
 Last modified on 03-01-2010 for application version 4.4.4 RemotePC User Manual Table of Contents Introduction... 3 Features... 3 Install the Remote Access Host application... 4 Install the Remote Access
Last modified on 03-01-2010 for application version 4.4.4 RemotePC User Manual Table of Contents Introduction... 3 Features... 3 Install the Remote Access Host application... 4 Install the Remote Access
1. System Requirements
 BounceBack Ultimate 14.2 User Guide This guide presents you with information on how to use BounceBack Ultimate 14.2. Contents 1. System Requirements 2. BounceBack Pre-Installation 3. How To Install The
BounceBack Ultimate 14.2 User Guide This guide presents you with information on how to use BounceBack Ultimate 14.2. Contents 1. System Requirements 2. BounceBack Pre-Installation 3. How To Install The
SP Widget. Users Manual
 SP Widget Users Manual 1 Contents 1. Disclaimer notice... 4 2. Product intro...5 3. System requirements... 5 4. Introduction... 6 4.1 Activating SP Widget... 6 Illustration 4.1... 6 4.2 Browser interface...
SP Widget Users Manual 1 Contents 1. Disclaimer notice... 4 2. Product intro...5 3. System requirements... 5 4. Introduction... 6 4.1 Activating SP Widget... 6 Illustration 4.1... 6 4.2 Browser interface...
Installing FileMaker Pro 11 in Windows
 Installing FileMaker Pro 11 in Windows Before you begin the installation process, please exit other open programs and save your work. Installation notes Before you install FileMaker Pro, review the following
Installing FileMaker Pro 11 in Windows Before you begin the installation process, please exit other open programs and save your work. Installation notes Before you install FileMaker Pro, review the following
WINDOWS 7 MANAGE FILES AND FOLDER WITH WINDOWS EXPLORER
 WINDOWS 7 MANAGE FILES AND FOLDER WITH WINDOWS EXPLORER Last Edited: 2012-07-10 1 Introduce Windows Explorer... 3 Navigate folders and their contents... 5 Organize files and folders... 8 Move or copy files
WINDOWS 7 MANAGE FILES AND FOLDER WITH WINDOWS EXPLORER Last Edited: 2012-07-10 1 Introduce Windows Explorer... 3 Navigate folders and their contents... 5 Organize files and folders... 8 Move or copy files
MyPBX Client User Manual
 MyPBX Client User Manual Version 1.0.0.4 Yeastar Information Technology Co. Ltd Table of Contents PART 1 HOW TO ACTIVATE MYPBX CLIENT ADDON... 4 1 ACTIVATE MYPBX CLIENT ADDON... 4 2 MYPBX CLIENT ADDON
MyPBX Client User Manual Version 1.0.0.4 Yeastar Information Technology Co. Ltd Table of Contents PART 1 HOW TO ACTIVATE MYPBX CLIENT ADDON... 4 1 ACTIVATE MYPBX CLIENT ADDON... 4 2 MYPBX CLIENT ADDON
Seagate Manager. User Guide. For Use With Your FreeAgent TM Drive. Seagate Manager User Guide for Use With Your FreeAgent Drive 1
 Seagate Manager User Guide For Use With Your FreeAgent TM Drive Seagate Manager User Guide for Use With Your FreeAgent Drive 1 Seagate Manager User Guide for Use With Your FreeAgent Drive Revision 1 2008
Seagate Manager User Guide For Use With Your FreeAgent TM Drive Seagate Manager User Guide for Use With Your FreeAgent Drive 1 Seagate Manager User Guide for Use With Your FreeAgent Drive Revision 1 2008
Online Backup - Installation and Setup
 The following guide will assist you in installing the Attix5 Backup Professional Server Edition on your Admin Server. You will have received your Group Name and Group Create Key from the Schools Broadband
The following guide will assist you in installing the Attix5 Backup Professional Server Edition on your Admin Server. You will have received your Group Name and Group Create Key from the Schools Broadband
TPM. (Trusted Platform Module) Installation Guide V3.3.0. for Windows Vista
 TPM (Trusted Platform Module) Installation Guide V3.3.0 for Windows Vista Table of contents 1 Introduction 1.1 Convention... 4 1.2 TPM - An Overview... 5 2 Using TPM for the first time 2.1 Enabling TPM...
TPM (Trusted Platform Module) Installation Guide V3.3.0 for Windows Vista Table of contents 1 Introduction 1.1 Convention... 4 1.2 TPM - An Overview... 5 2 Using TPM for the first time 2.1 Enabling TPM...
Yeastar Technology Co., Ltd.
 Client Manual 1.0.0.4 (English Version) Yeastar Technology Co., Ltd. Table of Contents MyPBX Client Manual Part 1 How To Activate MyPBX Client Addon 4 1 Activate MyPBX Client Addon 4 2 MyPBX Client Addon
Client Manual 1.0.0.4 (English Version) Yeastar Technology Co., Ltd. Table of Contents MyPBX Client Manual Part 1 How To Activate MyPBX Client Addon 4 1 Activate MyPBX Client Addon 4 2 MyPBX Client Addon
Table of Contents. TPM Configuration Procedure... 2. 1. Configuring the System BIOS... 2
 Table of Contents TPM Configuration Procedure... 2 1. Configuring the System BIOS... 2 2. Installing the Infineon TPM Driver and the GIGABYTE Ultra TPM Utility... 3 3. Initializing the TPM Chip... 4 3.1.
Table of Contents TPM Configuration Procedure... 2 1. Configuring the System BIOS... 2 2. Installing the Infineon TPM Driver and the GIGABYTE Ultra TPM Utility... 3 3. Initializing the TPM Chip... 4 3.1.
Password Memory 6 User s Guide
 C O D E : A E R O T E C H N O L O G I E S Password Memory 6 User s Guide 2007-2015 by code:aero technologies Phone: +1 (321) 285.7447 E-mail: info@codeaero.com Table of Contents Password Memory 6... 1
C O D E : A E R O T E C H N O L O G I E S Password Memory 6 User s Guide 2007-2015 by code:aero technologies Phone: +1 (321) 285.7447 E-mail: info@codeaero.com Table of Contents Password Memory 6... 1
I. Configuring Digital signature certificate in Microsoft Outlook 2003:
 I. Configuring Digital signature certificate in Microsoft Outlook 2003: In order to configure Outlook 2003 to use the new message security settings please follow these steps: 1. Open Outlook. 2. Go to
I. Configuring Digital signature certificate in Microsoft Outlook 2003: In order to configure Outlook 2003 to use the new message security settings please follow these steps: 1. Open Outlook. 2. Go to
PhoneCrypt Desktop. Phone Encryption Software. PhoneCrypt Manual Mobile phone encryption for Windows Platforms
 PhoneCrypt Desktop Phone Encryption Software PhoneCrypt Manual Mobile phone encryption for Windows Platforms Introduction Contents http:// www. securstar.com info@securstar.com 2009 by SecurStar GmbH,
PhoneCrypt Desktop Phone Encryption Software PhoneCrypt Manual Mobile phone encryption for Windows Platforms Introduction Contents http:// www. securstar.com info@securstar.com 2009 by SecurStar GmbH,
Image Backup and Recovery Procedures
 Image Backup and Recovery Procedures Thank you for purchasing a Fujitsu computer. Fujitsu is committed to bringing you the best computing experience with your new system. It is very important that you
Image Backup and Recovery Procedures Thank you for purchasing a Fujitsu computer. Fujitsu is committed to bringing you the best computing experience with your new system. It is very important that you
Vess A2000 Series. NVR Storage Appliance. Windows Recovery Instructions. Version 1.0. 2014 PROMISE Technology, Inc. All Rights Reserved.
 Vess A2000 Series NVR Storage Appliance Windows Recovery Instructions Version 1.0 2014 PROMISE Technology, Inc. All Rights Reserved. Contents Introduction 1 Different ways to backup the system disk 2 Before
Vess A2000 Series NVR Storage Appliance Windows Recovery Instructions Version 1.0 2014 PROMISE Technology, Inc. All Rights Reserved. Contents Introduction 1 Different ways to backup the system disk 2 Before
How To Install Ru-Vpn On A Pc Or Macbook Or Ipad (For Macbook) With A Microsoft Macbook (For Pc) With An Ipad Or Ipa (For A Macbook). Pc (For An
 RU-VPN Installation Instructions (Windows Vista and Windows 7) An RU-VPN id allows authorized users to access Ryerson s Administrative Systems via the internet. RU-VPN utilizes a digital certificate that
RU-VPN Installation Instructions (Windows Vista and Windows 7) An RU-VPN id allows authorized users to access Ryerson s Administrative Systems via the internet. RU-VPN utilizes a digital certificate that
NAS 249 Virtual Machine Configuration with VirtualBox
 NAS 249 Virtual Machine Configuration with VirtualBox Configure and run Virtual Machines on ASUSTOR Portal with VirtualBox A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you
NAS 249 Virtual Machine Configuration with VirtualBox Configure and run Virtual Machines on ASUSTOR Portal with VirtualBox A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you
Password Protection Application for Verbatim USB Flash Drives
 Introduction User Manual Verbatim EasyLock Password Protection Application for Verbatim USB Flash Drives Version 1.00 Copyright 2010 Verbatim Americas, LLC. All rights reserved. All other brands and product
Introduction User Manual Verbatim EasyLock Password Protection Application for Verbatim USB Flash Drives Version 1.00 Copyright 2010 Verbatim Americas, LLC. All rights reserved. All other brands and product
NTI CORPORATION. NTI Backup Now EZ v3. User's Guide
 NTI CORPORATION NTI Backup Now EZ v3 NTI Backup Now EZ v3 User's Guide Backup Now EZ v3 User's Guide 2013 NTI Corporation i Table of Contents INTRODUCTION... 3 WELCOME TO NTI BACKUP NOW EZ... 5 OVERVIEW
NTI CORPORATION NTI Backup Now EZ v3 NTI Backup Now EZ v3 User's Guide Backup Now EZ v3 User's Guide 2013 NTI Corporation i Table of Contents INTRODUCTION... 3 WELCOME TO NTI BACKUP NOW EZ... 5 OVERVIEW
VMWare Workstation 11 Installation MICROSOFT WINDOWS SERVER 2008 R2 STANDARD ENTERPRISE ED.
 VMWare Workstation 11 Installation MICROSOFT WINDOWS SERVER 2008 R2 STANDARD ENTERPRISE ED. Starting Vmware Workstation Go to the start menu and start the VMware Workstation program. *If you are using
VMWare Workstation 11 Installation MICROSOFT WINDOWS SERVER 2008 R2 STANDARD ENTERPRISE ED. Starting Vmware Workstation Go to the start menu and start the VMware Workstation program. *If you are using
Yale Software Library
 Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, helpdesk@yale.edu Two-factor authentication: Installation and configuration instructions for
Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, helpdesk@yale.edu Two-factor authentication: Installation and configuration instructions for
NTI Backup Now EZ v2 User s Guide
 NTI Backup Now EZ v2 User s Guide GMAA00423010 11/12 2 Copyright statement This guide is copyrighted by Toshiba Corporation with all rights reserved. Under the copyright laws, this guide cannot be reproduced
NTI Backup Now EZ v2 User s Guide GMAA00423010 11/12 2 Copyright statement This guide is copyrighted by Toshiba Corporation with all rights reserved. Under the copyright laws, this guide cannot be reproduced
Technical Publications. Author: Zultys Technical Support Department
 September 09 MXMeeting User Guide Author: Zultys Technical Support Department MXMeeting is a multi-function web collaboration system. The client-server architecture requires Internet connectivity for its
September 09 MXMeeting User Guide Author: Zultys Technical Support Department MXMeeting is a multi-function web collaboration system. The client-server architecture requires Internet connectivity for its
Hi-Speed USB Flash Disk User s Manual Guide
 Hi-Speed USB Flash Disk User s Manual Guide System Requirements Windows 98, ME, 2000, XP, Mac OS 10.1, Linux 2.4 or above AMD or Intel Pentium 133MHz or better based computer USB 1.1, USB 2.0 or higher
Hi-Speed USB Flash Disk User s Manual Guide System Requirements Windows 98, ME, 2000, XP, Mac OS 10.1, Linux 2.4 or above AMD or Intel Pentium 133MHz or better based computer USB 1.1, USB 2.0 or higher
Keystone 600N5 SERVER and STAND-ALONE INSTALLATION INSTRUCTIONS
 The following instructions are required for installation of Best Access System s Keystone 600N5 (KS600N) network key control software for the server side. Please see the system requirements on the Keystone
The following instructions are required for installation of Best Access System s Keystone 600N5 (KS600N) network key control software for the server side. Please see the system requirements on the Keystone
Vodafone PC Backup User Guide Version 1.16
 Vodafone PC Backup User Guide Version 1.16 Contents Preface: Preface...v Chapter 1: Overview...7 Chapter 2: Installing Vodafone PC Backup...9 Downloading the Vodafone PC Backup Client...9 Installing the
Vodafone PC Backup User Guide Version 1.16 Contents Preface: Preface...v Chapter 1: Overview...7 Chapter 2: Installing Vodafone PC Backup...9 Downloading the Vodafone PC Backup Client...9 Installing the
FAQ No. 01695. Q: What should we know before we start Windows 10 upgrade?
 FAQ No. 01695 Important Cautions of Windows 10 Upgrade Affected Model: All Q: What should we know before we start Windows 10 upgrade? A: MSI recommends that user should create system recovery before Windows
FAQ No. 01695 Important Cautions of Windows 10 Upgrade Affected Model: All Q: What should we know before we start Windows 10 upgrade? A: MSI recommends that user should create system recovery before Windows
USB DATA Link Cable USER MANUAL. (Model: DA-70010-1) GO! Suite Quick Start Guide
 USB DATA Link Cable USER MANUAL (Model: DA-70010-1) GO! Suite Quick Start Guide - GO! Suite Introduction - GO! Bridge Introduction - Remote Share Introduction - Folder Sync - Outlook Sync GO! Suite Quick
USB DATA Link Cable USER MANUAL (Model: DA-70010-1) GO! Suite Quick Start Guide - GO! Suite Introduction - GO! Bridge Introduction - Remote Share Introduction - Folder Sync - Outlook Sync GO! Suite Quick
BackupAssist v6 quickstart guide
 Using the new features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 2 Backing up VSS applications... 2 Restoring VSS applications... 3 System State backup and restore...
Using the new features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 2 Backing up VSS applications... 2 Restoring VSS applications... 3 System State backup and restore...
Time Stamp. Instruction Booklet
 Time Stamp Instruction Booklet Time Stamp Introductions Time stamp is a useful solution for backing up and restoring system, it backs up the entire computer system to the Backup Zone. Time Stamp is used
Time Stamp Instruction Booklet Time Stamp Introductions Time stamp is a useful solution for backing up and restoring system, it backs up the entire computer system to the Backup Zone. Time Stamp is used
Enterprise Remote Control 5.6 Manual
 Enterprise Remote Control 5.6 Manual Solutions for Network Administrators Copyright 2015, IntelliAdmin, LLC Revision 3/26/2015 http://www.intelliadmin.com Page 1 Table of Contents What is Enterprise Remote
Enterprise Remote Control 5.6 Manual Solutions for Network Administrators Copyright 2015, IntelliAdmin, LLC Revision 3/26/2015 http://www.intelliadmin.com Page 1 Table of Contents What is Enterprise Remote
Smart TPM. User's Manual. Rev. 1001 12MD-STPM-1001R
 Smart TPM User's Manual Rev. 1001 12MD-STPM-1001R We recommend that you download the latest version of the Smart TPM utility from GIGABYTE's website. If you have installed Ultra TPM earlier, you can install
Smart TPM User's Manual Rev. 1001 12MD-STPM-1001R We recommend that you download the latest version of the Smart TPM utility from GIGABYTE's website. If you have installed Ultra TPM earlier, you can install
NEWTECH INFOSYSTEMS, INC. NTI Backup Now EZ. NTI Backup Now EZ User's Guide
 NEWTECH INFOSYSTEMS, INC. NTI Backup Now EZ NTI Backup Now EZ User's Guide Backup Now EZ User's Guide 2009 NewTech Infosystems, Inc. i Table of Contents INTRODUCTION... 3 WELCOME TO NTI BACKUP NOW EZ...
NEWTECH INFOSYSTEMS, INC. NTI Backup Now EZ NTI Backup Now EZ User's Guide Backup Now EZ User's Guide 2009 NewTech Infosystems, Inc. i Table of Contents INTRODUCTION... 3 WELCOME TO NTI BACKUP NOW EZ...
Identity Finder Setup
 Identity Finder Information Sheet for MAC This document will walk you through how to install, scan, and secure any SI found on your computer, or storage devices using the Identity Finder Software. This
Identity Finder Information Sheet for MAC This document will walk you through how to install, scan, and secure any SI found on your computer, or storage devices using the Identity Finder Software. This
Royal Mail Group. getting started. with Symantec Endpoint Encryption. A user guide from Royal Mail Technology
 getting started with Symantec Endpoint Encryption A user guide from Royal Mail Technology For further help, contact the IT Helpdesk on 5415 2555 (01246 282555) March 2010 Contents 1 Introduction to Symantec
getting started with Symantec Endpoint Encryption A user guide from Royal Mail Technology For further help, contact the IT Helpdesk on 5415 2555 (01246 282555) March 2010 Contents 1 Introduction to Symantec
Lenovo Online Data Backup User Guide Version 1.8.14
 Lenovo Online Data Backup User Guide Version 1.8.14 Contents Chapter 1: Installing Lenovo Online Data Backup...5 Downloading the Lenovo Online Data Backup Client...5 Installing the Lenovo Online Data
Lenovo Online Data Backup User Guide Version 1.8.14 Contents Chapter 1: Installing Lenovo Online Data Backup...5 Downloading the Lenovo Online Data Backup Client...5 Installing the Lenovo Online Data
BackupAssist v6 quickstart guide
 New features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 3 System State backup... 3 Restore files, applications, System State and mailboxes... 4 Fully cloud ready Internet
New features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 3 System State backup... 3 Restore files, applications, System State and mailboxes... 4 Fully cloud ready Internet
USB 3.0 DUAL SATA HDD DOCKING STATION
 USB 3.0 DUAL SATA HDD DOCKING STATION User Manual (DA-70547) Introduction DA-70547 is a USB3.0 enabled dual-sata hard drive enclosure. It supports simultaneously use of two 2.5 or 3.5 SATA hard disk for
USB 3.0 DUAL SATA HDD DOCKING STATION User Manual (DA-70547) Introduction DA-70547 is a USB3.0 enabled dual-sata hard drive enclosure. It supports simultaneously use of two 2.5 or 3.5 SATA hard disk for
Telecom DaySave. User Guide. Client Version 2.2.0.3
 Telecom DaySave User Guide Client Version 2.2.0.3 Table of Contents Chapter 1: DaySave Overview... 4 Chapter 2: Installing DaySave... 5 Downloading the DaySave Client... 5 Installing the DaySave Client...
Telecom DaySave User Guide Client Version 2.2.0.3 Table of Contents Chapter 1: DaySave Overview... 4 Chapter 2: Installing DaySave... 5 Downloading the DaySave Client... 5 Installing the DaySave Client...
Print Server Application Guide. This guide applies to the following models.
 Print Server Application Guide This guide applies to the following models. TL-WR842ND TL-WR1042ND TL-WR1043ND TL-WR2543ND TL-WDR4300 CONTENTS Chapter 1. Overview... 1 Chapter 2. Before Installation...
Print Server Application Guide This guide applies to the following models. TL-WR842ND TL-WR1042ND TL-WR1043ND TL-WR2543ND TL-WDR4300 CONTENTS Chapter 1. Overview... 1 Chapter 2. Before Installation...
KeePass Getting Started on Windows
 KeePass Getting Started on Windows This guide includes the initial installation of KeePass 2.x on a Windows PC, creating your first password database, testing the software and entering your first accounts.
KeePass Getting Started on Windows This guide includes the initial installation of KeePass 2.x on a Windows PC, creating your first password database, testing the software and entering your first accounts.
CONNECT-TO-CHOP USER GUIDE
 CONNECT-TO-CHOP USER GUIDE VERSION V8 Table of Contents 1 Overview... 3 2 Requirements... 3 2.1 Security... 3 2.2 Computer... 3 2.3 Application... 3 2.3.1 Web Browser... 3 2.3.2 Prerequisites... 3 3 Logon...
CONNECT-TO-CHOP USER GUIDE VERSION V8 Table of Contents 1 Overview... 3 2 Requirements... 3 2.1 Security... 3 2.2 Computer... 3 2.3 Application... 3 2.3.1 Web Browser... 3 2.3.2 Prerequisites... 3 3 Logon...
TPM. (Trusted Platform Module) Installation Guide V2.1
 TPM (Trusted Platform Module) Installation Guide V2.1 Table of contents 1 Introduction 1.1 Convention... 4 1.2 TPM - An Overview... 5 2 Using TPM for the first time 2.1 Enabling TPM... 6 2.2 Installing
TPM (Trusted Platform Module) Installation Guide V2.1 Table of contents 1 Introduction 1.1 Convention... 4 1.2 TPM - An Overview... 5 2 Using TPM for the first time 2.1 Enabling TPM... 6 2.2 Installing
A computer running Windows Vista or Mac OS X
 lab File Management Objectives: Upon successful completion of Lab 2, you will be able to Define the terms file and folder Understand file and memory storage capacity concepts including byte, kilobyte,
lab File Management Objectives: Upon successful completion of Lab 2, you will be able to Define the terms file and folder Understand file and memory storage capacity concepts including byte, kilobyte,
MyUSBOnly User Guide Menu
 MyUSBOnly User Guide Menu Welcome - Lock the Bad Guys out of your USB ports!... 2 System Requirement... 4 Important Notes... 4 FAQ How to install a trial version MyUSBOnly?... 5 FAQ How to buy and install
MyUSBOnly User Guide Menu Welcome - Lock the Bad Guys out of your USB ports!... 2 System Requirement... 4 Important Notes... 4 FAQ How to install a trial version MyUSBOnly?... 5 FAQ How to buy and install
Introduction to Computers: Session 3 Files, Folders and Windows
 Introduction to Computers: Session 3 Files, Folders and Windows Files and folders Files are documents you create using a computer program. For example, this document is a file, made with a program called
Introduction to Computers: Session 3 Files, Folders and Windows Files and folders Files are documents you create using a computer program. For example, this document is a file, made with a program called
Virtual Office Remote Installation Guide
 Virtual Office Remote Installation Guide Table of Contents VIRTUAL OFFICE REMOTE INSTALLATION GUIDE... 3 UNIVERSAL PRINTER CONFIGURATION INSTRUCTIONS... 12 CHANGING DEFAULT PRINTERS ON LOCAL SYSTEM...
Virtual Office Remote Installation Guide Table of Contents VIRTUAL OFFICE REMOTE INSTALLATION GUIDE... 3 UNIVERSAL PRINTER CONFIGURATION INSTRUCTIONS... 12 CHANGING DEFAULT PRINTERS ON LOCAL SYSTEM...
Wireless Network Adapter Installation
 Belkin 54 Mbps Wireless Network Adapter Installation Version 1.0 Copyright Copyright 2013 Watthour Engineering Co., Inc.. All rights reserved. Information in this document is subject to change without
Belkin 54 Mbps Wireless Network Adapter Installation Version 1.0 Copyright Copyright 2013 Watthour Engineering Co., Inc.. All rights reserved. Information in this document is subject to change without
Hosting Users Guide 2011
 Hosting Users Guide 2011 eofficemgr technology support for small business Celebrating a decade of providing innovative cloud computing services to small business. Table of Contents Overview... 3 Configure
Hosting Users Guide 2011 eofficemgr technology support for small business Celebrating a decade of providing innovative cloud computing services to small business. Table of Contents Overview... 3 Configure
itunes Basics Website: http://etc.usf.edu/te/
 Website: http://etc.usf.edu/te/ itunes is the digital media management program included in ilife. With itunes you can easily import songs from your favorite CDs or purchase them from the itunes Store.
Website: http://etc.usf.edu/te/ itunes is the digital media management program included in ilife. With itunes you can easily import songs from your favorite CDs or purchase them from the itunes Store.
MiraCosta College now offers two ways to access your student virtual desktop.
 MiraCosta College now offers two ways to access your student virtual desktop. We now feature the new VMware Horizon View HTML access option available from https://view.miracosta.edu. MiraCosta recommends
MiraCosta College now offers two ways to access your student virtual desktop. We now feature the new VMware Horizon View HTML access option available from https://view.miracosta.edu. MiraCosta recommends
E-CERT C ONTROL M ANAGER
 E-CERT C ONTROL M ANAGER for e-cert on Smart ID Card I NSTALLATION G UIDE Version v1.7 Copyright 2003 Hongkong Post CONTENTS Introduction About e-cert Control Manager... 3 Features... 3 System requirements...
E-CERT C ONTROL M ANAGER for e-cert on Smart ID Card I NSTALLATION G UIDE Version v1.7 Copyright 2003 Hongkong Post CONTENTS Introduction About e-cert Control Manager... 3 Features... 3 System requirements...
BounceBack User Guide
 Table Of Contents 1. Table of Contents... 2 2. 1-0 Introduction... 3 2.1 1-0: Introduction... 4 2.2 1-1: BounceBack Software Overview... 6 3. 2-0 Navigating the BounceBack Control Center... 9 3.1 2-0:
Table Of Contents 1. Table of Contents... 2 2. 1-0 Introduction... 3 2.1 1-0: Introduction... 4 2.2 1-1: BounceBack Software Overview... 6 3. 2-0 Navigating the BounceBack Control Center... 9 3.1 2-0:
Introduction to MS WINDOWS XP
 Introduction to MS WINDOWS XP Mouse Desktop Windows Applications File handling Introduction to MS Windows XP 2 Table of Contents What is Windows XP?... 3 Windows within Windows... 3 The Desktop... 3 The
Introduction to MS WINDOWS XP Mouse Desktop Windows Applications File handling Introduction to MS Windows XP 2 Table of Contents What is Windows XP?... 3 Windows within Windows... 3 The Desktop... 3 The
Windows 7 Hard Disk Recovery
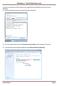 In order to restore your hard drive back to the original factory settings you will need to do the following: 1) Press the start button and in the search area type Recovery 2) From the search results, launch
In order to restore your hard drive back to the original factory settings you will need to do the following: 1) Press the start button and in the search area type Recovery 2) From the search results, launch
Guide to Installing BBL Crystal MIND on Windows 7
 Guide to Installing BBL Crystal MIND on Windows 7 Introduction The BBL Crystal MIND software can not be directly installed on the Microsoft Windows 7 platform, however it can be installed and run via XP
Guide to Installing BBL Crystal MIND on Windows 7 Introduction The BBL Crystal MIND software can not be directly installed on the Microsoft Windows 7 platform, however it can be installed and run via XP
HEALTH INFORMATION SYSTEM (HIS) HOW TO COMMUNICATE WITH THE HIS PROJECT TEAM. How To Communicate with the HIS Project Team
 How To Communicate with the HIS Project Team This guide is intended to provide you with support for communicating with the HIS Project Team. There may be instances where the HIS Project Team will require
How To Communicate with the HIS Project Team This guide is intended to provide you with support for communicating with the HIS Project Team. There may be instances where the HIS Project Team will require
Using a USB Flash Drive to Back Up Your Data Files on a Mac Computer
 Using a USB Flash Drive to Back Up Your Data Files on a Mac Computer Your GWU-provided flash drive has a storage capacity of 1 GB and is provided as a means for you to back up data files, including email
Using a USB Flash Drive to Back Up Your Data Files on a Mac Computer Your GWU-provided flash drive has a storage capacity of 1 GB and is provided as a means for you to back up data files, including email
USD WEB SERVICES UPLOADING DOCUMENTS TO PASSWORD-PROTECTED SECTIONS OF YOUR WEBSITE
 USD WEB SERVICES UPLOADING DOCUMENTS TO PASSWORD-PROTECTED SECTIONS OF YOUR WEBSITE INFORMATION TECHNOLOGY SERVICES UNIVERSITY OF SAN DIEGO DEVELOPED BY MORGAN ANDERSEN WEBSUPPORT@SANDIEGO.EDU JUNE 2011
USD WEB SERVICES UPLOADING DOCUMENTS TO PASSWORD-PROTECTED SECTIONS OF YOUR WEBSITE INFORMATION TECHNOLOGY SERVICES UNIVERSITY OF SAN DIEGO DEVELOPED BY MORGAN ANDERSEN WEBSUPPORT@SANDIEGO.EDU JUNE 2011
Accessing Windows 7 in the Student Labs
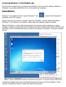 Accessing Windows 7 in the Student Labs This document explains how to access and use Windows 7 and some of the software installed on Windows 7, such as Microsoft Office 2010, on the student lab computers.
Accessing Windows 7 in the Student Labs This document explains how to access and use Windows 7 and some of the software installed on Windows 7, such as Microsoft Office 2010, on the student lab computers.
Interactive Whiteboard Functionality Overview... 4. Choosing Pen Style... 5. Erasing / Modifying Writing... 6. Undo / Redo... 6. Email...
 Quick Start Guide 1 Stand-alone Usage Interactive Whiteboard Functionality Overview... 4 Choosing Pen Style... 5 Erasing / Modifying Writing... 6 Undo / Redo... 6 Email... 7 Import / Open file... 7 Saving
Quick Start Guide 1 Stand-alone Usage Interactive Whiteboard Functionality Overview... 4 Choosing Pen Style... 5 Erasing / Modifying Writing... 6 Undo / Redo... 6 Email... 7 Import / Open file... 7 Saving
Simple Computer Backup
 Title: Simple Computer Backup (Win 7 and 8) Author: Nancy DeMarte Date Created: 11/10/13 Date(s) Revised: 1/20/15 Simple Computer Backup This tutorial includes these methods of backing up your PC files:
Title: Simple Computer Backup (Win 7 and 8) Author: Nancy DeMarte Date Created: 11/10/13 Date(s) Revised: 1/20/15 Simple Computer Backup This tutorial includes these methods of backing up your PC files:
Wireless Remote Control of the TT24
 of the TT24 Updated: 7/20/04 by Benjamin Olswang The TT24 includes a powerful piece of software called TT Control. With this software, you can monitor and control the TT24 console from a PC attached via
of the TT24 Updated: 7/20/04 by Benjamin Olswang The TT24 includes a powerful piece of software called TT Control. With this software, you can monitor and control the TT24 console from a PC attached via
Welcome to EMP Monitor (Employee monitoring system):
 Welcome to EMP Monitor (Employee monitoring system): Overview: Admin End. User End. 1.0 Admin End: Introduction to Admin panel. Admin panel log in. Introduction to UI. Adding an Employee. Getting and editing
Welcome to EMP Monitor (Employee monitoring system): Overview: Admin End. User End. 1.0 Admin End: Introduction to Admin panel. Admin panel log in. Introduction to UI. Adding an Employee. Getting and editing
Free GMATPrep Test-Preparation Software Download and Installation Instructions
 Welcome! Welcome to the GMATPrep application. The GMATPrep test-preparation software was designed by the people who created the GMAT exam, to help you get ready to take the test. It includes practice questions
Welcome! Welcome to the GMATPrep application. The GMATPrep test-preparation software was designed by the people who created the GMAT exam, to help you get ready to take the test. It includes practice questions
How to use the VMware Workstation / Player to create an ISaGRAF (Ver. 3.55) development environment?
 Author Janice Hong Version 1.0.0 Date Mar. 2014 Page 1/56 How to use the VMware Workstation / Player to create an ISaGRAF (Ver. 3.55) development environment? Application Note The 32-bit operating system
Author Janice Hong Version 1.0.0 Date Mar. 2014 Page 1/56 How to use the VMware Workstation / Player to create an ISaGRAF (Ver. 3.55) development environment? Application Note The 32-bit operating system
