Smart Card Setup Guide
|
|
|
- Aleesha Nicholson
- 10 years ago
- Views:
Transcription
1 Smart Card Setup Guide
2 K Apple Computer, Inc Apple Computer, Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole or in part, without the written consent of Apple. The Apple logo is a trademark of Apple Computer, Inc., registered in the U.S. and other countries. Use of the keyboard Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Every effort has been made to ensure that the information in this manual is accurate. Apple is not responsible for printing or clerical errors. Apple 1 Infinite Loop Cupertino, CA Apple, the Apple logo, Keychain, Mac, Macintosh, and Mac OS are trademarks of Apple Computer, Inc., registered in the U.S. and other countries. Safari and Tiger are trademarks of Apple Computer, Inc. Other company and product names mentioned herein are trademarks of their respective companies. Mention of third-party products is for informational purposes only and constitutes neither an endorsement nor a recommendation. Apple assumes no responsibility with regard to the performance or use of these products. The product described in this manual incorporates copyright protection technology that is protected by method claims of certain U.S. patents and other intellectual property rights owned by Macrovision Corporation and other rights owners. Use of this copyright protection technology must be authorized by Macrovision Corporation and is intended for home and other limited viewing uses only unless otherwise authorized by Macrovision Corporation. Reverse engineering or disassembly is prohibited. Apparatus Claims of U.S. Patent Nos. 4,631,603, 4,577,216, 4,819,098 and 4,907,093 licensed for limited viewing uses only. Simultaneously published in the United States and Canada /
3 1 Contents Chapter 1 4 About Using Smart Cards with Mac OS X 4 Setting Up Your Computer 5 Updating Your Computer s System Software 5 Compatible Smart Card Readers 5 Compatible Smart Cards Chapter 2 6 Setting Up Your Smart Card 6 Enabling Smart Card Login 8 Setting Up an Account for Smart Card Access 8 Setting Account Preferences 8 Securing Your Idle Computer 9 Using Keychain Access 10 Setting Up Directory Services for Smart Cards 10 Using the Public Key Hash Method 11 Using the Attribute Lookup Method 12 Modifying the Configuration File for Attribute Lookup Chapter 3 14 Using Smart Cards 14 Using a Smart Card to Log In 14 Using Keychain Access to Manage Access 15 Viewing Smart Card Information in Keychain Access 15 Changing the PIN in Keychain Access 15 Getting More Information About Smart Cards 3
4 1 About Using Smart Cards with Mac OS X 1 The security architecture in Mac OS X v10.4 Tiger and later includes improvements in smart card services and integration. Follow the instructions in this guide to configure your system to use smart cards. A smart card is a plastic card, similar in size to a credit card, that has memory and a microprocessor embedded in it. Smart cards can store passwords, certificates, and keys. A smart card normally requires an additional security measure such as a personal identification number (PIN), or sometimes a biometric measurement (such as a fingerprint). A computer can retrieve information from a smart card through a smart card reader. Smart card services have been expanded for Mac OS X Tiger. Smart card support is now integrated into the credential management of the security architecture. Smart card services are preinstalled with Mac OS X Tiger and later, and no longer require installation of smart card software. The setup process for smart cards is now simplified, and many of the steps required in previous versions are no longer needed. Warning: The smart card software that is preinstalled with Mac OS X Tiger is not compatible with software or configuration settings created for previous versions of the Mac OS. Do not install smart card software or use files or configuration settings designed for earlier versions of Mac OS X. Doing so may corrupt the system software, and require that you reinstall Mac OS X. Setting Up Your Computer To use a smart card with your Macintosh, make sure you have:  Mac OS X v10.4 Tiger or later  A compatible smart card reader  A compatible smart card 4
5 Updating Your Computer s System Software Make sure you are using Mac OS X Tiger or later to take advantage of the latest smart card features. m To identify which version you are using, choose Apple (apple) menu > About This Mac. You should update your system software regularly to be sure you have the most reliable and up-to-date software. To update your system software: 1 Choose Apple (apple) menu > Software Update. 2 If an update for Mac OS X appears in the list, select its checkbox. 3 Click Install, and then follow the onscreen instructions. Compatible Smart Card Readers Mac OS X Tiger includes built-in support for many types of smart card readers. Compatible smart card readers include:  Any certified Chip Card Interface Device (CCID) USB class reader  USB readers such as Athena, CryptoCard, GemPlus, and SCM  PC Card readers such as CryptoCard, SCM, and OmniKey  USB dongle readers such as OmniKey and GemPlus Other smart card readers can also be used if you install their software drivers, which are available from the manufacturer. For more information about compatible smart card readers, visit the Apple Support website at Compatible Smart Cards Mac OS X Tiger includes support for many types of smart cards. Compatible smart cards include:  U.S. Federal Government smart cards such as Common Access Card (CAC), Government Smart Card Interoperability Specification (GSCIS), and Personal ID Verification (PIV)  Belgian Personal ID Card (BELPIC)  Japanese PKI Card (JPKI) Any supported smart card with signing capabilities can be used for both directory services based authentication and cryptographic login. For more information about supported smart cards, visit the Apple Support website at Chapter 1 About Using Smart Cards with Mac OS X 5
6 2 Setting Up Your Smart Card 2 Follow the instructions in this chapter to learn how to enable smart card services and configure your computer to use smart cards. Smart card services are preinstalled with Mac OS X v10.4 Tiger or later, but smart card login and system administration are not enabled. You can enable smart card login on any system with or without a smart card reader attached. When the smart card services are enabled, your computer checks whether a smart card reader is attached. Enabling smart card login does not affect performance even if a card reader is not attached. If a card reader is not attached, you can continue to use your user name and password to log in. Enabling Smart Card Login To enable smart card login, you must edit the /etc/authorization file. To modify this file, you need an administrator password and you must be authorized to use the sudo command in Terminal to modify the system s configuration files. You must also be familiar with editing text files using a terminal text editor such as pico; a text editing application; or a property editor such as Property List Editor, which is included in the Apple Developer Kit. Follow these steps to enable smart card login: 1 Open the Terminal application, located in the Utilities folder in the Applications folder. 2 To access the authorization files, enter the following command in Terminal: sudo -s 3 To navigate to the correct directory, enter: cd /etc 4 To delete the outdated authorization.cac file installed on your computer, enter: rm authorization.cac 6
7 5 To back up the original authorization file and create a separate file to modify, enter: cp authorization authorization.orig cp authorization /tmp/authorization.mod 6 Open the authorization.mod file you just created in a text editor or property list editor. The file is located in the tmp folder on your startup drive: /tmp/authorization.mod 7 The authorization.mod file is made up of a list of properties arranged in a hierarchy of dictionaries. At the root level of the property list is the rights dictionary, which contains a long list of other dictionaries. Find the system.login.console dictionary in the rights dictionary. It contains an array called mechanisms that must be modified. 8 Make the following changes to the mechanisms array within the system.login.console dictionary: a Add <string>builtin:smartcard-sniffer,privileged</string> after the item <string>builtin:auto-login,privileged</string>. b Delete <string>authinternal</string>. c Add <string>builtin:authenticate,privileged</string> after the item <string>builtin:reset-password,privileged</string>. 9 At the root level of the property list is the rules dictionary. Find the authenticate dictionary. It contains an array called mechanisms that must be modified. 10 Make the following changes to the mechanisms array within the authenticate dictionary. a Add <string>builtin:smartcard-sniffer,privileged</string> to the beginning of the mechanisms array. b Delete <string>authinternal</string>. c Add <string>builtin:authenticate,privileged</string> after the item <string>builtin:authenticate</string>. 11 Save your changes. 12 Your original session should still be running in Terminal. To replace the actual authorization file with the edited version, enter: cp /tmp/authorization.mod /etc/authorization The changes take place immediately; you don t need to restart the system. After smart card login is enabled, the system starts checking whether a card reader is attached to the computer. Unlike with previous versions of smart card software, you do not need to enter additional commands for your computer to recognize the reader. Chapter 2 Setting Up Your Smart Card 7
8 Setting Up an Account for Smart Card Access You must have a user account to bind to the smart card, and then configure that account to work properly with the smart card. Follow these instructions to set up a user account for a smart card. Setting Account Preferences Use the Accounts preferences pane in System Preferences to create or configure the user account that will be bound to the smart card. To create or configure a user account for a smart card: 1 Choose Apple (apple) menu > System Preferences, and then click Accounts. 2 If some settings are dimmed, click the lock icon and then enter an administrator name and password. 3 Select the user account you want to change, or if you want to create a new user, click Add (+) and then enter the user's name and password in the Name, Password, and Verify fields. If you don't want to use the automatically generated short name, enter a new short name. (After the account is created, you won't be able to change the short name). 4 If you want the user to have administrator privileges, click Password and select the option Allow user to administer this computer. 5 Click Login Options. 6 Deselect the option Automatically log in as. 7 Deselect the option Show the Restart, Sleep, and Shut Down buttons. 8 Deselect the option Enable fast user switching. 9 Close System Preferences. Securing Your Idle Computer If you want to be sure that the computer is secured when it is idle, you can require users to authenticate using the smart card and PIN when they wake the computer from sleep or return to the desktop from a screen saver. To require user authentication: 1 Open System Preferences, and then click Security. 2 If some settings are dimmed, click the lock icon and then enter an administrator name and password. 3 Select the option Require password to wake this computer from sleep or screen saver. 4 Close System Preferences. 8 Chapter 2 Setting Up Your Smart Card
9 Using Keychain Access You must set up Keychain Access to work with your organization s policy. There are two common methods for verifying the validity of a certificate: Online Certificate Status Protocol (OCSP) and Certificate Revocation List (CRL). Information about the status of certificates is stored on a revocation server. The Mac OS X security system can check with the revocation server to validate the certificate. Here is an explanation of the settings available: Â Off: No revocation checking will be performed. Â Best Attempt: The certificate passes unless an indication of a bad certificate is returned from the server. Â Require if Cert Indicates: If the URL to the revocation server is provided in the certificate, this setting requires a successful connection to a revocation server and no indication of a bad certificate. Â Require for All Certs: This setting requires successful validation of all certificates. It is most useful in a tightly controlled environment that guarantees the presence of a CRL server or OCSP responder. Â Priority: Determines which method (OCSP or CRL) is attempted first. If the first method chosen returns a successful validation, the second method is not attempted. Check with your network administrator for the settings required by your organization. To set certificate validation in Keychain Access preferences: 1 Open Keychain Access, located in the Utilities folder in the Applications folder. 2 Choose Keychain Access menu > Preferences. 3 Click Certificates. 4 Choose settings from the Online Certificate Status Protocol (OCSP) and the Certificate Revocation List (CRL) pop-up menus to match the requirements of your organization s policy. If there is no policy in place, it often works well to choose Best Attempt from the OCSP and CRL pop-up menus. If you are a U.S. Federal Government Department of Defense user, you need to enable the X.509 Certificates in Keychain Access. To install the X.509 Certificates in Keychain Access: 1 Open Keychain Access, located in the Utilities folder in the Applications folder. 2 Choose Edit menu > Keychain List. 3 Click Add (+), and then select X509Certificates located in /System/Library/Keychains/. 4 Click Open. Chapter 2 Setting Up Your Smart Card 9
10 Setting Up Directory Services for Smart Cards Smart card login does a lookup for the expected user in a directory service to authenticate the user s identification. It uses one of two methods: Â The public key hash method Adds the public key hash (pubkeyhash) to the user's directory record. This method uses Open Directory and the default directory schema is NetInfo. Â The attribute lookup method Performs a search for a value based on a key from the signing certificate on the smart card. This method uses user accounts in an existing directory service. All U.S. Federal Government smart card users use the attribute lookup method. Using the Public Key Hash Method This is the most convenient and secure way of identifying a smart card user. It uses Open Directory. The default for the user record is a local NetInfo network. You will retrieve a key from the smart card, and then bind that key to the account. After setting up the user account, you are ready to attach the smart card reader and read the card identity information. To read the smart card identity information: 1 Attach the smart card reader to the computer. 2 Insert the smart card into the card reader. 3 Open the Terminal application, located in the Utilities folder in the Applications folder. 4 To read the identity keys, or hash, from the smart card, use the sc_auth command. You can enter the command in Terminal without any parameter to see a description of the command s usage displayed, for example: $ sc_auth Usage: sc_auth accept[-v][-u user][-k keyname] #by key on inserted card(s) sc_auth accept[-v][-u user] -h hash #by known pubkey hash sc_auth remove[-v][-u user] #remove all public keys for this user sc_auth hash[-k keyname] #print hashes for keys on inserted card(s) Enter the following command in Terminal: sc_auth hash Here is an example of the results: $ sc_auth hash 01C2E294XP77B57B63B0A15B8F204C1 Identity Private Key 443F30C356E676F447CD4DCCED Signing Private Key C1F8C6B372CE422933CF1FD1 Encryption Private Key Not all cards have three private keys. In this example, any of the hash entries listed could be used for binding the card to the account. The following example uses the identity private key to bind the smart card to the user account. 10 Chapter 2 Setting Up Your Smart Card
11 5 You bind the card to the user s local directory domain by using the sc_auth accept command. Using the identity private key from the previous example, the command looks like this: sudo sc_auth accept -u myuser -h 01C2E294XP77B57B63B0A15B8F204C1 In Terminal, enter the following command, using the account s short user name for <username> and the smart card s identity private key for <# Identity Private Key>: sudo sc_auth accept -u <username> -h <# Identity Private Key> The sc_auth command adds a field to the user's authentication called the authentication_authority property. You can see the authentication_authority property by using the nidump command. The following example shows the new identity private key written into the user public key hash. nidump -r /users/myuser... "authentication_authority" = ( ";ShadowHash;", ";pubkeyhash 01C2E294XP77B57B63B0A15B8F204C1" );... In the previous example with three hash keys, any of the key entries could have been used for binding the card to the account. More than one smart card can be bound to a single user account by running the script again with the hash for each additional card. Note: Multiple cards can be bound to a single account, but a single card cannot be bound to multiple accounts accessible from a single system. Using the Attribute Lookup Method If your network doesn t use NetInfo with Open Directory, the attribute lookup method should be used to bind the user account to the smart card. This method looks up the user based on values drawn from the signing certificate. Attribute lookup works with user accounts from an existing directory service such as LDAP, NetInfo, NIS, or Active Directory. You configure the smart card authorization plug-in to map an attribute from a certificate on the smart card to a field in the directory. Attribute lookup is mainly used by Common Access Card (CAC) smart cards although it does work with other similarly designed smart cards. Attribute lookup is required for all U.S. Federal Government smart cards. The examples show commonly used attribute lookups. However, you need to be familiar with the attributes and directory fields required by your particular directory service. Check with your network administrator for configuration information specific to your directory service. Chapter 2 Setting Up Your Smart Card 11
12 Modifying the Configuration File for Attribute Lookup In most directory services you will use a configuration file that contains a search key for an Open Directory search. A configuration file is an array of dictionaries. Each dictionary in this array contains one search key in an Open Directory search. The default configuration file is: /etc/caclogingconfig.plist The following example shows a common configuration: <dict> <key>dsattributestring</key> <string>dsattrtypenative:userprincipalname</string> <key>fields</key> <array> <string>nt Principal Name</string> </array> <key>formatstring</key> <string>$1</string> </dict> The dsattrtypenative: string is followed by the ntprincipalname token, which represents the name of the attribute to use in your directory schema. When an Open Directory search is performed on the ntprincipalname token, it returns is the ID. For example: @mil Another example shows multiple strings formatted to return the ID: <dict> <key>values</key> <array> <string>rfc 822 Name</string> <string>nt Principal Name</string> <string>country</string> </array> <key>format</key> <string>$1#$2/$3</string> <key>directorysearchkey</key> <string>dsattrtypenative:uniqueid</string> </dict> The directorysearchkey is the user s lookup key. It specifies the directory key to search for. This example returns a combined search string: [email protected]# @mil/us 12 Chapter 2 Setting Up Your Smart Card
13 Here is an example of CAC keys that can appear as fields in the configuration file: Key String Country Organization Organizational Unit:1 Organizational Unit:2 Organizational Unit:3 Common Name RFC 822 Name NT Principal Name Example U.S. U.S. Government DoD PKI USN SURNAME.GIVEN.MI Chapter 2 Setting Up Your Smart Card 13
14 3 Using Smart Cards 3 Follow the instructions in this chapter to learn how to use smart cards in Mac OS X v10.4 Tiger or later and how to manage authorization. You can use smart cards to provide authentication for a number of applications and services in Mac OS X, including:  Login  Mail  Safari  Waking from sleep or screen saver  VPN  System administration  Other applications that use CDSA or CDSA based APIs Using a Smart Card to Log In After the smart card login is enabled, the standard login screen appears. To log in using your smart card: 1 Insert your smart card into the reader. The standard login screen is replaced by a smart card login screen asking for a PIN. 2 Enter your PIN number. You are now able to access and use your computer normally. Using Keychain Access to Manage Access When a smart card is used to log in to a computer in Mac OS X Tiger, the smart card becomes a keychain in Keychain Access. Use Keychain Access to manage all of your keychains and passwords. 14
15 Viewing Smart Card Information in Keychain Access Smart cards are displayed in Keychain Access as keychains in the Keychain list. With Keychain Access you can view and manage authorization information related to your smart card. To view smart card information: 1 Open Keychain Access located in the Utilities folder in the Applications folder. 2 Select the smart card keychain in the Keychains list (click Show Keychains if the list is not open). Changing the PIN in Keychain Access You can use Keychain Access to change your smart card s PIN. Warning: Check with your smart card administrator to be sure that you are allowed to change the PIN, and to confirm the required format of the PIN. The card or the card management system may require certain formats or types of characters, for example, only numeric or alpha-numeric characters. To change the PIN used with your smart card: 1 Open Keychain Access located in the Utilities folder in the Applications folder, and then select the keychain in the Keychains list (click Show Keychains if the list is not open). 2 Choose Edit menu > Change Password for Keychain 'smartcard# '. (The name of the keychain in the menu matches the name of the selected keychain). 3 If the keychain is locked, enter the password to unlock it. 4 Type the current password for the keychain. 5 Type a new password, and then type it again to verify it. 6 Click OK. Getting More Information About Smart Cards For more information about smart cards, visit these websites:  Apple Support website at  Apple Customer Training website at train.apple.com  Apple Discussions website at discussions.info.apple.com  Apple Product Security website at  Apple Government website at  Apple Enterprise website at Chapter 3 Using Smart Cards 15
16 For more information about security configurations, visit these websites:  NSA security configuration guides at  NIST Security Configuration Checklists Repository at checklists.nist.gov/repository/ category.htm 16 Chapter 3 Using Smart Cards
Standardizing PKI in Higher Education Apple PKI and Universal Hi-Ed Spec proposal
 Standardizing PKI in Higher Education Apple PKI and Universal Hi-Ed Spec proposal Shawn Geddis Security Consulting Engineer, Apple Enterprise [email protected] 703-264-5103 1 Agenda A View of Apples PKI
Standardizing PKI in Higher Education Apple PKI and Universal Hi-Ed Spec proposal Shawn Geddis Security Consulting Engineer, Apple Enterprise [email protected] 703-264-5103 1 Agenda A View of Apples PKI
Apple Server Diagnostics User Guide. For Version 3X106
 Apple Server Diagnostics User Guide For Version 3X106 KKApple Inc. 2009 Apple Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole or in part, without the written
Apple Server Diagnostics User Guide For Version 3X106 KKApple Inc. 2009 Apple Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole or in part, without the written
Mac OS X Server Migration Guide
 Mac OS X Server Migration Guide Includes detailed instructions for upgrading to Mac OS X Server from AppleShare IP, Macintosh Manager, and Mac OS X Server 1.2 K Apple Computer, Inc. 2001 Apple Computer,
Mac OS X Server Migration Guide Includes detailed instructions for upgrading to Mac OS X Server from AppleShare IP, Macintosh Manager, and Mac OS X Server 1.2 K Apple Computer, Inc. 2001 Apple Computer,
Xserve Apple Xserve Diagnostics User Guide. For Version 3X104
 Xserve Apple Xserve Diagnostics User Guide For Version 3X104 KKApple Inc. 2009 Apple Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole or in part, without the
Xserve Apple Xserve Diagnostics User Guide For Version 3X104 KKApple Inc. 2009 Apple Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole or in part, without the
Apple Remote Desktop Focus on Task Server
 Apple Remote Desktop Focus on Task Server K Apple Computer, Inc. 2006 Apple Computer, Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole or in part, without the
Apple Remote Desktop Focus on Task Server K Apple Computer, Inc. 2006 Apple Computer, Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole or in part, without the
Using RAID Admin and Disk Utility
 Using RAID Admin and Disk Utility Xserve RAID Includes instructions for creating RAID arrays and monitoring Xserve RAID systems K Apple Computer, Inc. 2003 Apple Computer, Inc. All rights reserved. Under
Using RAID Admin and Disk Utility Xserve RAID Includes instructions for creating RAID arrays and monitoring Xserve RAID systems K Apple Computer, Inc. 2003 Apple Computer, Inc. All rights reserved. Under
Implementing Federal Personal Identity Verification for VMware View. By Bryan Salek, Federal Desktop Systems Engineer, VMware
 Implementing Federal Personal Identity Verification for VMware View By Bryan Salek, Federal Desktop Systems Engineer, VMware Technical WHITE PAPER Introduction This guide explains how to implement authentication
Implementing Federal Personal Identity Verification for VMware View By Bryan Salek, Federal Desktop Systems Engineer, VMware Technical WHITE PAPER Introduction This guide explains how to implement authentication
Digital Signatures on iqmis User Access Request Form
 Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Getting Started With. Mac OS X Server. Includes installation and setup information for Mac OS X Server version 10.2
 Getting Started With Mac OS X Server Includes installation and setup information for Mac OS X Server version 10.2 K Apple Computer, Inc. 2002 Apple Computer, Inc. All rights reserved. Under the copyright
Getting Started With Mac OS X Server Includes installation and setup information for Mac OS X Server version 10.2 K Apple Computer, Inc. 2002 Apple Computer, Inc. All rights reserved. Under the copyright
NAVAL POSTGRADUATE SCHOOL
 NPS-CS-06-009 NAVAL POSTGRADUATE SCHOOL MONTEREY, CALIFORNIA CAC on a MAC: Setting up a DOD Common Access Card Reader on the Macintosh OS X Operating System by Phil Hopfner March 2006 Approved for public
NPS-CS-06-009 NAVAL POSTGRADUATE SCHOOL MONTEREY, CALIFORNIA CAC on a MAC: Setting up a DOD Common Access Card Reader on the Macintosh OS X Operating System by Phil Hopfner March 2006 Approved for public
Outlook Web Access 2003 Remote User Guide
 UNITED STATES COAST GUARD Outlook Web Access 2003 Remote User Guide Using Common Access Card Access TISCOM TIS-42 07/29/2008 Version 1.0 CAC Enabled Outlook Web Access CAC Enabled OWA is a way to view
UNITED STATES COAST GUARD Outlook Web Access 2003 Remote User Guide Using Common Access Card Access TISCOM TIS-42 07/29/2008 Version 1.0 CAC Enabled Outlook Web Access CAC Enabled OWA is a way to view
Creating Home Directories for Windows and Macintosh Computers
 ExtremeZ-IP Active Directory Integrated Home Directories Configuration! 1 Active Directory Integrated Home Directories Overview This document explains how to configure home directories in Active Directory
ExtremeZ-IP Active Directory Integrated Home Directories Configuration! 1 Active Directory Integrated Home Directories Overview This document explains how to configure home directories in Active Directory
Administering FileVault 2 on OS X Lion with the Casper Suite. Technical Paper July 2012
 Administering FileVault 2 on OS X Lion with the Casper Suite Technical Paper July 2012 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that
Administering FileVault 2 on OS X Lion with the Casper Suite Technical Paper July 2012 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that
Virtual CD v10. Network Management Server Manual. H+H Software GmbH
 Virtual CD v10 Network Management Server Manual H+H Software GmbH Table of Contents Table of Contents Introduction 1 Legal Notices... 2 What Virtual CD NMS can do for you... 3 New Features in Virtual
Virtual CD v10 Network Management Server Manual H+H Software GmbH Table of Contents Table of Contents Introduction 1 Legal Notices... 2 What Virtual CD NMS can do for you... 3 New Features in Virtual
USER GUIDE WWPass Security for Windows Logon
 USER GUIDE WWPass Security for Windows Logon December 2015 TABLE OF CONTENTS Chapter 1 Welcome... 3 Introducing WWPass Security for Windows Logon... 4 Related Documentation... 4 Presenting Your PassKey
USER GUIDE WWPass Security for Windows Logon December 2015 TABLE OF CONTENTS Chapter 1 Welcome... 3 Introducing WWPass Security for Windows Logon... 4 Related Documentation... 4 Presenting Your PassKey
Two Factor Authentication in SonicOS
 Two Factor Authentication in SonicOS 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential damage
Two Factor Authentication in SonicOS 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential damage
Newton Backup Utility User s Guide. for the Windows Operating System
 Newton Backup Utility User s Guide for the Windows Operating System K Apple Computer, Inc. 1995 Apple Computer, Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole
Newton Backup Utility User s Guide for the Windows Operating System K Apple Computer, Inc. 1995 Apple Computer, Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole
QuickStart Guide for Mobile Device Management
 QuickStart Guide for Mobile Device Management Version 8.5 Inventory Configuration Security Management Distribution JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made
QuickStart Guide for Mobile Device Management Version 8.5 Inventory Configuration Security Management Distribution JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made
FileMaker Server 7. Administrator s Guide. For Windows and Mac OS
 FileMaker Server 7 Administrator s Guide For Windows and Mac OS 1994-2004, FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark
FileMaker Server 7 Administrator s Guide For Windows and Mac OS 1994-2004, FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark
VMware Horizon FLEX User Guide
 Horizon FLEX 1.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Horizon FLEX 1.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
You're reading an excerpt. Click here to read official APPLE REMOTE DESKTOP 1.2 user guide http://yourpdfguides.com/dref/1168427
 You can read the recommendations in the user guide, the technical guide or the installation guide for APPLE REMOTE DESKTOP 1.2. You'll find the answers to all your questions on the APPLE REMOTE DESKTOP
You can read the recommendations in the user guide, the technical guide or the installation guide for APPLE REMOTE DESKTOP 1.2. You'll find the answers to all your questions on the APPLE REMOTE DESKTOP
SafeNet Authentication Client (Mac)
 SafeNet Authentication Client (Mac) Version 8.2 SP2 Revision A Administrator s Guide 1 Copyright 2014 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document
SafeNet Authentication Client (Mac) Version 8.2 SP2 Revision A Administrator s Guide 1 Copyright 2014 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document
QuickStart Guide for Mobile Device Management. Version 8.6
 QuickStart Guide for Mobile Device Management Version 8.6 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF
QuickStart Guide for Mobile Device Management Version 8.6 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF
IBM Client Security Solutions. Client Security User's Guide
 IBM Client Security Solutions Client Security User's Guide December 1999 1 Before using this information and the product it supports, be sure to read Appendix B - Notices and Trademarks, on page 22. First
IBM Client Security Solutions Client Security User's Guide December 1999 1 Before using this information and the product it supports, be sure to read Appendix B - Notices and Trademarks, on page 22. First
Mac OS X 10.6 Snow Leopard Installation and Setup Guide
 Mac OS X 10.6 Snow Leopard Installation and Setup Guide Read this document before you install Mac OS X. It includes important information about installing Mac OS X. For more information about Mac OS X,
Mac OS X 10.6 Snow Leopard Installation and Setup Guide Read this document before you install Mac OS X. It includes important information about installing Mac OS X. For more information about Mac OS X,
Binding an OS X computer to Active Directory at NEIU (Existing User)
 Binding an OS X computer to Active Directory at NEIU (Existing User) The instructions in this guide assume that a local Administrator account is available on the Macintosh computer. These instructions
Binding an OS X computer to Active Directory at NEIU (Existing User) The instructions in this guide assume that a local Administrator account is available on the Macintosh computer. These instructions
FileMaker Server 8. Administrator s Guide
 FileMaker Server 8 Administrator s Guide 1994-2005 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark of FileMaker, Inc.,
FileMaker Server 8 Administrator s Guide 1994-2005 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark of FileMaker, Inc.,
Endpoint Security Client for Mac
 Endpoint Security Client for Mac E80.60 User Guide 23 December 2014 Classification: [Protected] 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are
Endpoint Security Client for Mac E80.60 User Guide 23 December 2014 Classification: [Protected] 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are
Imaging License Server User Guide
 IMAGING LICENSE SERVER USER GUIDE Imaging License Server User Guide PerkinElmer Viscount Centre II, University of Warwick Science Park, Millburn Hill Road, Coventry, CV4 7HS T +44 (0) 24 7669 2229 F +44
IMAGING LICENSE SERVER USER GUIDE Imaging License Server User Guide PerkinElmer Viscount Centre II, University of Warwick Science Park, Millburn Hill Road, Coventry, CV4 7HS T +44 (0) 24 7669 2229 F +44
OUTLOOK WEB ACCESS (OWA) AND SSL VPN HOME USERS MANUAL
 United States Army Special Operations Command (USASOC) Special Operations Forces Information Technology Enterprise Contracts (SITEC) OUTLOOK WEB ACCESS (OWA) AND SSL VPN HOME USERS MANUAL Prepared by:
United States Army Special Operations Command (USASOC) Special Operations Forces Information Technology Enterprise Contracts (SITEC) OUTLOOK WEB ACCESS (OWA) AND SSL VPN HOME USERS MANUAL Prepared by:
Copyright 2012 Trend Micro Incorporated. All rights reserved.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
DeployStudio Server Quick Install
 DeployStudio Server Quick Install v1.7.0 The DeployStudio Team [email protected] Requirements OS X 10.7.5 to 10.11.1 DeployStudioServer_v1.7.x.pkg and later NetBoot based deployment 100 Mb/s switched
DeployStudio Server Quick Install v1.7.0 The DeployStudio Team [email protected] Requirements OS X 10.7.5 to 10.11.1 DeployStudioServer_v1.7.x.pkg and later NetBoot based deployment 100 Mb/s switched
Apache Server Implementation Guide
 Apache Server Implementation Guide 340 March Road Suite 600 Kanata, Ontario, Canada K2K 2E4 Tel: +1-613-599-2441 Fax: +1-613-599-2442 International Voice: +1-613-599-2441 North America Toll Free: 1-800-307-7042
Apache Server Implementation Guide 340 March Road Suite 600 Kanata, Ontario, Canada K2K 2E4 Tel: +1-613-599-2441 Fax: +1-613-599-2442 International Voice: +1-613-599-2441 North America Toll Free: 1-800-307-7042
FileMaker Server 14. FileMaker Server Help
 FileMaker Server 14 FileMaker Server Help 2007 2015 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker and FileMaker Go are trademarks
FileMaker Server 14 FileMaker Server Help 2007 2015 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker and FileMaker Go are trademarks
VMware Horizon FLEX User Guide
 Horizon FLEX 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Horizon FLEX 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
HOTPin Integration Guide: DirectAccess
 1 HOTPin Integration Guide: DirectAccess Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as is'; Celestix assumes no responsibility
1 HOTPin Integration Guide: DirectAccess Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as is'; Celestix assumes no responsibility
OUTLOOK WEB ACCESS (OWA) AND SSL VPN HOME USERS MANUAL
 United States Army Special Operations Command (USASOC) Special Operations Forces Information Technology Enterprise Contracts (SITEC) OUTLOOK WEB ACCESS (OWA) AND SSL VPN HOME USERS MANUAL Prepared by:
United States Army Special Operations Command (USASOC) Special Operations Forces Information Technology Enterprise Contracts (SITEC) OUTLOOK WEB ACCESS (OWA) AND SSL VPN HOME USERS MANUAL Prepared by:
FileMaker Server 13. FileMaker Server Help
 FileMaker Server 13 FileMaker Server Help 2010-2013 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker and Bento are trademarks of FileMaker,
FileMaker Server 13 FileMaker Server Help 2010-2013 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker and Bento are trademarks of FileMaker,
SECO Whitepaper. SuisseID Smart Card Logon Configuration Guide. Prepared for SECO. Publish Date 19.05.2010 Version V1.0
 SECO Whitepaper SuisseID Smart Card Logon Configuration Guide Prepared for SECO Publish Date 19.05.2010 Version V1.0 Prepared by Martin Sieber (Microsoft) Contributors Kunal Kodkani (Microsoft) Template
SECO Whitepaper SuisseID Smart Card Logon Configuration Guide Prepared for SECO Publish Date 19.05.2010 Version V1.0 Prepared by Martin Sieber (Microsoft) Contributors Kunal Kodkani (Microsoft) Template
Integration with Active Directory
 VMWARE TECHNICAL NOTE VMware ACE Integration with Active Directory This document explains how to set up Active Directory to use with VMware ACE. This document contains the following topics: About Active
VMWARE TECHNICAL NOTE VMware ACE Integration with Active Directory This document explains how to set up Active Directory to use with VMware ACE. This document contains the following topics: About Active
Managed Services PKI 60-day Trial Quick Start Guide
 Entrust Managed Services PKI Managed Services PKI 60-day Trial Quick Start Guide Document issue: 3.0 Date of issue: Nov 2011 Copyright 2011 Entrust. All rights reserved. Entrust is a trademark or a registered
Entrust Managed Services PKI Managed Services PKI 60-day Trial Quick Start Guide Document issue: 3.0 Date of issue: Nov 2011 Copyright 2011 Entrust. All rights reserved. Entrust is a trademark or a registered
DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication
 DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication Certificate Based 2010 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 31 Disclaimer Disclaimer of
DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication Certificate Based 2010 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 31 Disclaimer Disclaimer of
Setting Up Mac OS X Server for Xserve. Includes software installation and setup information for Mac OS X Server and Xserve
 Setting Up Mac OS X Server for Xserve Includes software installation and setup information for Mac OS X Server and Xserve K Apple Computer, Inc. 2002 Apple Computer, Inc. All rights reserved. Under the
Setting Up Mac OS X Server for Xserve Includes software installation and setup information for Mac OS X Server and Xserve K Apple Computer, Inc. 2002 Apple Computer, Inc. All rights reserved. Under the
VMware Virtual Desktop Manager User Authentication Guide
 Technical Note VMware Virtual Desktop Manager User Authentication Guide VMware Virtual Desktop Manager The purpose of this guide is to provide details of user authentication in VMware Virtual Desktop Manager
Technical Note VMware Virtual Desktop Manager User Authentication Guide VMware Virtual Desktop Manager The purpose of this guide is to provide details of user authentication in VMware Virtual Desktop Manager
DECS DER APPLE WIRELESS HELPER DOCUMENT
 DECS DER APPLE WIRELESS HELPER DOCUMENT A GUIDE TO THE DEPLOYMENT OF APPLE MAC NOTEBOOK COMPUTERS IN DECS WIRELESS NETWORKS apple Chris Downing, Senior Systems Engineer apple Viano Jaksa, Area Manager
DECS DER APPLE WIRELESS HELPER DOCUMENT A GUIDE TO THE DEPLOYMENT OF APPLE MAC NOTEBOOK COMPUTERS IN DECS WIRELESS NETWORKS apple Chris Downing, Senior Systems Engineer apple Viano Jaksa, Area Manager
HP ProtectTools User Guide
 HP ProtectTools User Guide Copyright 2007 Hewlett-Packard Development Company, L.P. Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation. Intel is a trademark or registered trademark
HP ProtectTools User Guide Copyright 2007 Hewlett-Packard Development Company, L.P. Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation. Intel is a trademark or registered trademark
8x8 Click2Pop User Guide
 USER GUIDE 8x8 User Guide Getting Started with April 2014 Contents Introduction... 3 What s new.... 3 8x8.... 3 Here is how works...4 8x8 Click2Connect.... 4 Requirements.... 4 Installation on Microsoft
USER GUIDE 8x8 User Guide Getting Started with April 2014 Contents Introduction... 3 What s new.... 3 8x8.... 3 Here is how works...4 8x8 Click2Connect.... 4 Requirements.... 4 Installation on Microsoft
Open Directory. Contents. Before You Start 2. Configuring Rumpus 3. Testing Accessible Directory Service Access 4. Specifying Home Folders 4
 Contents Before You Start 2 Configuring Rumpus 3 Testing Accessible Directory Service Access 4 Specifying Home Folders 4 Open Directory Groups 6 Maxum Development Corp. Before You Start Open Directory
Contents Before You Start 2 Configuring Rumpus 3 Testing Accessible Directory Service Access 4 Specifying Home Folders 4 Open Directory Groups 6 Maxum Development Corp. Before You Start Open Directory
Connection Broker Managing User Connections to Workstations and Blades, OpenStack Clouds, VDI, and More
 Connection Broker Managing User Connections to Workstations and Blades, OpenStack Clouds, VDI, and More Leostream Connect Administrator s Guide and End User s Manual Version 3.5 / 3.1 January 14, 2016
Connection Broker Managing User Connections to Workstations and Blades, OpenStack Clouds, VDI, and More Leostream Connect Administrator s Guide and End User s Manual Version 3.5 / 3.1 January 14, 2016
iphone in Business How-To Setup Guide for Users
 iphone in Business How-To Setup Guide for Users iphone is ready for business. It supports Microsoft Exchange ActiveSync, as well as standards-based services, delivering email, calendars, and contacts over
iphone in Business How-To Setup Guide for Users iphone is ready for business. It supports Microsoft Exchange ActiveSync, as well as standards-based services, delivering email, calendars, and contacts over
Entrust Managed Services PKI
 Entrust Managed Services PKI Entrust Managed Services PKI Windows Smart Card Logon Configuration Guide Using Web-based applications Document issue: 1.0 Date of Issue: June 2009 Copyright 2009 Entrust.
Entrust Managed Services PKI Entrust Managed Services PKI Windows Smart Card Logon Configuration Guide Using Web-based applications Document issue: 1.0 Date of Issue: June 2009 Copyright 2009 Entrust.
VeriSign PKI Client Government Edition v 1.5. VeriSign PKI Client Government. VeriSign PKI Client VeriSign, Inc. Government.
 END USER S GUIDE VeriSign PKI Client Government Edition v 1.5 End User s Guide VeriSign PKI Client Government Version 1.5 Administrator s Guide VeriSign PKI Client VeriSign, Inc. Government Copyright 2010
END USER S GUIDE VeriSign PKI Client Government Edition v 1.5 End User s Guide VeriSign PKI Client Government Version 1.5 Administrator s Guide VeriSign PKI Client VeriSign, Inc. Government Copyright 2010
I. Configuring Digital signature certificate in Microsoft Outlook 2003:
 I. Configuring Digital signature certificate in Microsoft Outlook 2003: In order to configure Outlook 2003 to use the new message security settings please follow these steps: 1. Open Outlook. 2. Go to
I. Configuring Digital signature certificate in Microsoft Outlook 2003: In order to configure Outlook 2003 to use the new message security settings please follow these steps: 1. Open Outlook. 2. Go to
User Guide Remote Access to VDI/Workplace Using PIV
 User Guide Remote Access to VDI/Workplace Using PIV Innovation & Engineering Office (IM-64) May 2015 Table of Contents 1 Overview... 3 1.1 Web Browsers... 3 1.2 Operating Systems... 3 2 Types of Smart
User Guide Remote Access to VDI/Workplace Using PIV Innovation & Engineering Office (IM-64) May 2015 Table of Contents 1 Overview... 3 1.1 Web Browsers... 3 1.2 Operating Systems... 3 2 Types of Smart
Check Point FDE integration with Digipass Key devices
 INTEGRATION GUIDE Check Point FDE integration with Digipass Key devices 1 VASCO Data Security Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document
INTEGRATION GUIDE Check Point FDE integration with Digipass Key devices 1 VASCO Data Security Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document
Sage 200 Web Time & Expenses Guide
 Sage 200 Web Time & Expenses Guide Sage (UK) Limited Copyright Statement Sage (UK) Limited, 2006. All rights reserved If this documentation includes advice or information relating to any matter other than
Sage 200 Web Time & Expenses Guide Sage (UK) Limited Copyright Statement Sage (UK) Limited, 2006. All rights reserved If this documentation includes advice or information relating to any matter other than
The cloud server setup program installs the cloud server application, Apache Tomcat, Java Runtime Environment, and PostgreSQL.
 GO-Global Cloud 4.1 QUICK START SETTING UP A WINDOWS CLOUD SERVER AND HOST This guide provides instructions for setting up a cloud server and configuring a host so it can be accessed from the cloud server.
GO-Global Cloud 4.1 QUICK START SETTING UP A WINDOWS CLOUD SERVER AND HOST This guide provides instructions for setting up a cloud server and configuring a host so it can be accessed from the cloud server.
User Manual. Onsight Management Suite Version 5.1. Another Innovation by Librestream
 User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
Oracle Virtual Desktop Infrastructure. VDI Demo (Microsoft Remote Desktop Services) for Version 3.2
 Oracle Virtual Desktop Infrastructure VDI Demo (Microsoft Remote Desktop Services) for Version 2 April 2011 Copyright 2011, Oracle and/or its affiliates. All rights reserved. This software and related
Oracle Virtual Desktop Infrastructure VDI Demo (Microsoft Remote Desktop Services) for Version 2 April 2011 Copyright 2011, Oracle and/or its affiliates. All rights reserved. This software and related
USER GUIDE WWPass Security for Email (Outlook) For WWPass Security Pack 2.4
 USER GUIDE WWPass Security for Email (Outlook) For WWPass Security Pack 2.4 March 2014 TABLE OF CONTENTS Chapter 1 Welcome... 4 Introducing WWPass Security for Email (Outlook)... 5 Supported Outlook Products...
USER GUIDE WWPass Security for Email (Outlook) For WWPass Security Pack 2.4 March 2014 TABLE OF CONTENTS Chapter 1 Welcome... 4 Introducing WWPass Security for Email (Outlook)... 5 Supported Outlook Products...
Print Management. User's Guide
 Print Management User's Guide November 2014 www.lexmark.com Contents 2 Contents Overview...3 Performing user authentication...4 Using standard authentication...4 Using Single Sign On authentication...4
Print Management User's Guide November 2014 www.lexmark.com Contents 2 Contents Overview...3 Performing user authentication...4 Using standard authentication...4 Using Single Sign On authentication...4
Embedded Document Accounting Solution (edas) for Cost Recovery. Administrator's Guide
 Embedded Document Accounting Solution (edas) for Cost Recovery Administrator's Guide September 2013 www.lexmark.com Contents 2 Contents Overview...4 Getting started...5 Understanding installation requirements...5
Embedded Document Accounting Solution (edas) for Cost Recovery Administrator's Guide September 2013 www.lexmark.com Contents 2 Contents Overview...4 Getting started...5 Understanding installation requirements...5
NetIQ Advanced Authentication Framework - MacOS Client
 NetIQ Advanced Authentication Framework - MacOS Client Installation Guide Version 5.2.0 1 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 About MacOS Client 4 System Requirements
NetIQ Advanced Authentication Framework - MacOS Client Installation Guide Version 5.2.0 1 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 About MacOS Client 4 System Requirements
DigiDelivery Client Quick Start
 DigiDelivery Client Quick Start Installing the DigiDelivery Client To download and install the DigiDelivery client software: 1 Launch your Web browser and navigate to www.digidesign.com/digidelivery/clients.
DigiDelivery Client Quick Start Installing the DigiDelivery Client To download and install the DigiDelivery client software: 1 Launch your Web browser and navigate to www.digidesign.com/digidelivery/clients.
VPN Configuration Guide SonicWALL with SonicWALL Simple Client Provisioning
 VPN Configuration Guide SonicWALL with SonicWALL Simple Client Provisioning SonicOS Enhanced 2010 equinux AG and equinux USA, Inc. All rights reserved. Under copyright law, this manual may not be copied,
VPN Configuration Guide SonicWALL with SonicWALL Simple Client Provisioning SonicOS Enhanced 2010 equinux AG and equinux USA, Inc. All rights reserved. Under copyright law, this manual may not be copied,
Setting up a Mac on the CU network
 School of Medicine IT Office Setting up a Mac on the CU network v1.3 JAM 23/12/13 This document explains how to setup a Mac on the Cardiff University network, access useful resources and configure native
School of Medicine IT Office Setting up a Mac on the CU network v1.3 JAM 23/12/13 This document explains how to setup a Mac on the Cardiff University network, access useful resources and configure native
RSA Authentication Manager 7.1 Basic Exercises
 RSA Authentication Manager 7.1 Basic Exercises Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA and the RSA logo
RSA Authentication Manager 7.1 Basic Exercises Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA and the RSA logo
Parallels Panel. Parallels Small Business Panel 10.2: User's Guide. Revision 1.0
 Parallels Panel Parallels Small Business Panel 10.2: User's Guide Revision 1.0 Copyright Notice ISBN: N/A Parallels 660 SW 39 th Street Suite 205 Renton, Washington 98057 USA Phone: +1 (425) 282 6400 Fax:
Parallels Panel Parallels Small Business Panel 10.2: User's Guide Revision 1.0 Copyright Notice ISBN: N/A Parallels 660 SW 39 th Street Suite 205 Renton, Washington 98057 USA Phone: +1 (425) 282 6400 Fax:
Building a BYOD Program Using the Casper Suite. Technical Paper Casper Suite v9.4 or Later 17 September 2014
 Building a BYOD Program Using the Casper Suite Technical Paper Casper Suite v9.4 or Later 17 September 2014 JAMF Software, LLC 2014 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts
Building a BYOD Program Using the Casper Suite Technical Paper Casper Suite v9.4 or Later 17 September 2014 JAMF Software, LLC 2014 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts
How To Package In Composer 2.5.2.2 (Amd64)
 Composer User Guide Version 9.1 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave S Suite
Composer User Guide Version 9.1 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave S Suite
Configuring Active Directory Binding for OS X (10.4.x) within Miami Dade Schools
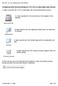 Configuring Active Directory Binding for OS X (10.4.x) within Miami Dade Schools 1) Login to the Mac OS X (10.4.x) workstation with a local administrative account. 2) Open (double-click) the hard drive
Configuring Active Directory Binding for OS X (10.4.x) within Miami Dade Schools 1) Login to the Mac OS X (10.4.x) workstation with a local administrative account. 2) Open (double-click) the hard drive
PageScope Router. Version 1.5. Configuration Guide
 PageScope Router Version 1.5 Configuration Guide Table of Contents TABLE OF CONTENTS... 2 1. Introduction...3 1.1 IP Address and Domain Name...3 2. Sending Files to PageScope Router...4 2.1 MFP Device
PageScope Router Version 1.5 Configuration Guide Table of Contents TABLE OF CONTENTS... 2 1. Introduction...3 1.1 IP Address and Domain Name...3 2. Sending Files to PageScope Router...4 2.1 MFP Device
Token User Guide. Version 1.0/ July 2013
 Token User Guide Version 1.0/ July 2013 Index Overview... 3 Usage requirements... 4 KIT contents... 5 Smart Card installation... 6 Reader driver installation... 7 In the case of Windows XP... 7 In the
Token User Guide Version 1.0/ July 2013 Index Overview... 3 Usage requirements... 4 KIT contents... 5 Smart Card installation... 6 Reader driver installation... 7 In the case of Windows XP... 7 In the
Smart Card Authentication Client. Administrator's Guide
 Smart Card Authentication Client Administrator's Guide April 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Smart Card Authentication Client...4 Configuring printer settings for use
Smart Card Authentication Client Administrator's Guide April 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Smart Card Authentication Client...4 Configuring printer settings for use
Cloud Server powered by Mac OS X. Getting Started Guide. Cloud Server. powered by Mac OS X. AKJZNAzsqknsxxkjnsjx Getting Started Guide Page 1
 Getting Started Guide Cloud Server powered by Mac OS X Getting Started Guide Page 1 Getting Started Guide: Cloud Server powered by Mac OS X Version 1.0 (02.16.10) Copyright 2010 GoDaddy.com Software, Inc.
Getting Started Guide Cloud Server powered by Mac OS X Getting Started Guide Page 1 Getting Started Guide: Cloud Server powered by Mac OS X Version 1.0 (02.16.10) Copyright 2010 GoDaddy.com Software, Inc.
Connection Broker Managing User Connections to Workstations, Blades, VDI, and More. Quick Start with Microsoft Hyper-V
 Connection Broker Managing User Connections to Workstations, Blades, VDI, and More Quick Start with Microsoft Hyper-V Version 8.1 October 21, 2015 Contacting Leostream Leostream Corporation http://www.leostream.com
Connection Broker Managing User Connections to Workstations, Blades, VDI, and More Quick Start with Microsoft Hyper-V Version 8.1 October 21, 2015 Contacting Leostream Leostream Corporation http://www.leostream.com
Guest PC. for Mac OS X. User Guide. Version 1.6. Copyright 1996-2005 Lismore Software Systems, Ltd. All rights reserved.
 Guest PC for Mac OS X Version 1.6 User Guide Copyright 1996-2005 Lismore Software Systems, Ltd. All rights reserved. Table of Contents About Guest PC... 1 About your Virtual Computer... 1 Creating a Virtual
Guest PC for Mac OS X Version 1.6 User Guide Copyright 1996-2005 Lismore Software Systems, Ltd. All rights reserved. Table of Contents About Guest PC... 1 About your Virtual Computer... 1 Creating a Virtual
6) Click the lock in the lower left corner of the Directory Utility Window and authenticate with the local administrator account s credentials.
 Configuring Active Directory Binding for OS X (10.5.x) within Miami Dade Schools Directory Utility determines which directory services a Mac OS X computer uses and how it connects to specific directory
Configuring Active Directory Binding for OS X (10.5.x) within Miami Dade Schools Directory Utility determines which directory services a Mac OS X computer uses and how it connects to specific directory
FileMaker Server 11. FileMaker Server Help
 FileMaker Server 11 FileMaker Server Help 2010 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark of FileMaker, Inc. registered
FileMaker Server 11 FileMaker Server Help 2010 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark of FileMaker, Inc. registered
www.rohos.com Two-factor authentication Free portable encryption for USB drive Hardware disk encryption Face recognition logon
 Two-factor authentication Free portable encryption for USB drive Hardware disk encryption Face recognition logon Secure Windows and Mac login by USB key www.rohos.com Rohos Logon Key Secure two-factor
Two-factor authentication Free portable encryption for USB drive Hardware disk encryption Face recognition logon Secure Windows and Mac login by USB key www.rohos.com Rohos Logon Key Secure two-factor
Apple Mac VPN Service Setting up Remote Desktop
 Apple Mac VPN Service Setting up Remote Desktop After you have successfully connected via the VPN client to the University network you will then need to make the connection to your machine. To do this
Apple Mac VPN Service Setting up Remote Desktop After you have successfully connected via the VPN client to the University network you will then need to make the connection to your machine. To do this
Yubico PIV Management Tools
 Yubico PIV Management Tools Active Directory Smart Card Logon using the YubiKey NEO or NEO-n Document Version 1.0 April 15, 2015 Yubico PIV Management Tools 2015 Yubico. All rights reserved. Page 1 of
Yubico PIV Management Tools Active Directory Smart Card Logon using the YubiKey NEO or NEO-n Document Version 1.0 April 15, 2015 Yubico PIV Management Tools 2015 Yubico. All rights reserved. Page 1 of
Smart Card Certificate Authentication with VMware View 4.5 and Above WHITE PAPER
 Smart Card Certificate Authentication with VMware View 4.5 and Above WHITE PAPER Table of Contents.... About This Paper.... 3 Introduction... 3 Smart Card Overview.... 3 Getting Started... 4 Authenticating
Smart Card Certificate Authentication with VMware View 4.5 and Above WHITE PAPER Table of Contents.... About This Paper.... 3 Introduction... 3 Smart Card Overview.... 3 Getting Started... 4 Authenticating
Citrix Web Client Installation and CAC Registration Guide
 Citrix Web Client Installation and CAC Registration Guide Prepared By: Department of Defense Education Activity 1 Revision 1.1 To ensure a reasonably smooth process of establishing connectivity with the
Citrix Web Client Installation and CAC Registration Guide Prepared By: Department of Defense Education Activity 1 Revision 1.1 To ensure a reasonably smooth process of establishing connectivity with the
MassTransit 6.0 Enterprise Web Configuration for Macintosh OS 10.5 Server
 MassTransit 6.0 Enterprise Web Configuration for Macintosh OS 10.5 Server November 6, 2008 Group Logic, Inc. 1100 North Glebe Road, Suite 800 Arlington, VA 22201 Phone: 703-528-1555 Fax: 703-528-3296 E-mail:
MassTransit 6.0 Enterprise Web Configuration for Macintosh OS 10.5 Server November 6, 2008 Group Logic, Inc. 1100 North Glebe Road, Suite 800 Arlington, VA 22201 Phone: 703-528-1555 Fax: 703-528-3296 E-mail:
VPN Web Portal Usage Guide
 VPN Web Portal Usage Guide Table of Contents WHAT IS VPN WEB CLIENT 4 SUPPORTED WEB BROWSERS 4 LOGGING INTO VPN WEB CLIENT 5 ESTABLISHING A VPN CONNECTION 6 KNOWN ISSUES WITH MAC COMPUTERS 6 ACCESS INTRANET
VPN Web Portal Usage Guide Table of Contents WHAT IS VPN WEB CLIENT 4 SUPPORTED WEB BROWSERS 4 LOGGING INTO VPN WEB CLIENT 5 ESTABLISHING A VPN CONNECTION 6 KNOWN ISSUES WITH MAC COMPUTERS 6 ACCESS INTRANET
CA Nimsoft Service Desk
 CA Nimsoft Service Desk Single Sign-On Configuration Guide 6.2.6 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation
CA Nimsoft Service Desk Single Sign-On Configuration Guide 6.2.6 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation
Getting Started with VMware Fusion
 Getting Started with VMware Fusion VMware Fusion for Mac OS X 2008 2012 EN-000933-00 2 Getting Started with VMware Fusion You can find the most up-to-date technical documentation on the VMware Web site
Getting Started with VMware Fusion VMware Fusion for Mac OS X 2008 2012 EN-000933-00 2 Getting Started with VMware Fusion You can find the most up-to-date technical documentation on the VMware Web site
Information in this document, including URL and other Internet Web site references, is subject to change without notice. Unless otherwise noted, the
 Information in this document, including URL and other Internet Web site references, is subject to change without notice. Unless otherwise noted, the example companies, organizations, products, domain names,
Information in this document, including URL and other Internet Web site references, is subject to change without notice. Unless otherwise noted, the example companies, organizations, products, domain names,
VMware Horizon FLEX User Guide
 Horizon FLEX 1.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Horizon FLEX 1.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
FileMaker 11. ODBC and JDBC Guide
 FileMaker 11 ODBC and JDBC Guide 2004 2010 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark of FileMaker, Inc. registered
FileMaker 11 ODBC and JDBC Guide 2004 2010 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark of FileMaker, Inc. registered
Remote Desktop Services User's Guide
 Contents Remote Desktop Services Document Revision Control Revision Description Author DATE 1.0 Initial Release Karen M. Hess 3/24/2015 1.1 Added section for viewing mapped drives Karen M. Hess 4/15/2015
Contents Remote Desktop Services Document Revision Control Revision Description Author DATE 1.0 Initial Release Karen M. Hess 3/24/2015 1.1 Added section for viewing mapped drives Karen M. Hess 4/15/2015
Administering FileVault 2 on OS X Mavericks with the Casper Suite v9.2 or Later. Technical Paper October 2013
 Administering FileVault 2 on OS X Mavericks with the Casper Suite v9.2 or Later Technical Paper October 2013 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all
Administering FileVault 2 on OS X Mavericks with the Casper Suite v9.2 or Later Technical Paper October 2013 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all
Mac OS X Secure Wireless Setup Guide
 Mac OS X Secure Wireless Setup Guide Requirements: Apple computer with built-in AirPort card capable of WPA2-Enterprise encryption Mac OS X Snow Leopard version 10.6.0 or greater or Mac OS X Lion version
Mac OS X Secure Wireless Setup Guide Requirements: Apple computer with built-in AirPort card capable of WPA2-Enterprise encryption Mac OS X Snow Leopard version 10.6.0 or greater or Mac OS X Lion version
ES3452 MFP, ES5462 MFP,
 Configuration Guide This guide supports the following models: MC332dn, MC342dn, MC342dw, MC352dn, MC362dn, MC362dw, MC562dn, MC562dw, ES3452 MFP, ES5462 MFP, MPS2731mc PREFACE Every effort has been made
Configuration Guide This guide supports the following models: MC332dn, MC342dn, MC342dw, MC352dn, MC362dn, MC362dw, MC562dn, MC562dw, ES3452 MFP, ES5462 MFP, MPS2731mc PREFACE Every effort has been made
License Patrol TM Mac Client Installation Guide 7.0 for Mac OS X. September 2015 VERALAB TM
 License Patrol TM Mac Client Installation Guide 7.0 for Mac OS X September 2015 VERALAB TM License Patrol Client Installation Guide, 7.0 for Mac OS X. Copyright 2015 VeraLab Inc. All rights reserved. The
License Patrol TM Mac Client Installation Guide 7.0 for Mac OS X September 2015 VERALAB TM License Patrol Client Installation Guide, 7.0 for Mac OS X. Copyright 2015 VeraLab Inc. All rights reserved. The
Smart Card Installation and Configuration Guide
 Version 3.0 October 2014 Smart Card Installation and Configuration Guide (CAC/PIV/.Net/Access Client & Rijkspas) Xerox WorkCentre 3655 Multifunction Printer Xerox WorkCentre 5845/5855/5865/5875/5890 Multifunction
Version 3.0 October 2014 Smart Card Installation and Configuration Guide (CAC/PIV/.Net/Access Client & Rijkspas) Xerox WorkCentre 3655 Multifunction Printer Xerox WorkCentre 5845/5855/5865/5875/5890 Multifunction
Core Protection for Virtual Machines 1
 Core Protection for Virtual Machines 1 Comprehensive Threat Protection for Virtual Environments. Installation Guide e Endpoint Security Trend Micro Incorporated reserves the right to make changes to this
Core Protection for Virtual Machines 1 Comprehensive Threat Protection for Virtual Environments. Installation Guide e Endpoint Security Trend Micro Incorporated reserves the right to make changes to this
