ManageEngine Password Manager Pro BEST PRACTICES GUIDE. ZOHO Corp
|
|
|
- Milo Shields
- 10 years ago
- Views:
Transcription
1 BEST PRACTICES GUIDE ZOHO Corp
2 2 Password Manager Pro - Best Practices Guide 1.0 Overview This document describes the best practices in setting up and using Password Manager Pro in an enterprise network environment. It is intended to offer guidance to IT administrators when they set up the software for use in their production environment. Best practices during all stages - product installation, configuration, setup and deployment have been explained with special focus on data security. 2.0 Installation 2.1 System Configuration Before installing PMP, you need to decide on the configuration of the system where you would install PMP. The following table provides information on the minimum hardware and software configuration required by PMP. Minimum Requirements Hardware Operating systems Web-Client& Database Processor Windows HTML client requires one of the following browsers** to be installed in the system: RAM 1.8 GHz Pentium processor 1 GB Hard Disk 200 MB for product 10 GB for database Windows 2000 Server / Professional Windows Server 2003 Windows Server 2008 Windows Server 2008 R2 Windows Server 2012 Windows Server 2012 R2 Windows XP Professional Windows Vista Windows 7 Windows 8 Linux Ubuntu 9.x and above CentOS 4.4 Red Hat Linux 9.0 Red Hat Enterprise Linux 5.3, 5.4, 5.5 PMP normally works well with any flavor of Linux IE 7 and above (on Windows) Chrome, Firefox and Safari (on Windows, Linux and Mac) ** PMP is optimized for 1280 x 800 resolution and above. Database PostgreSQL 9.2.4, bundled with the product. Supports MySQL and MS SQL Server 2005 and above also. SQL server should be installed in Windows 2003 Server and above.
3 3 Note: Password Manager Pro can be run on VMs of the above operating systems 2.2 Recommended Configuration for Better Performance, Scalability & Security For better performance and security, it is recommended to install PMP in a dedicated, hardened, high-end server.also, the performance of PMP depends a lot on the following factors: Number of Users & User Groups Number of Resources & Resource Groups Number of Resources/Passwords Shared Number of Scheduled Tasks Though PMP will very well run in the systems having the minimum configuration, you may have to choose a higher configuration if the above factors weigh high at your end. We can roughly say that if the above factors are very high of the order of hundreds of users and user groups with a few thousands of resources and resource groups and shares, you may choose a high-end configuration as below: Single / Dual processor 4 GB RAM 40 GB hard disk space 2.3 Installing PMP in Windows Vs Linux PMP can be installed in Windows and Linux. Though PMP will run equally fine in both the platforms, installation in Windows has some inherent advantages. Active Directory Synchronization (for resource & user import) can be leveraged only in Windows installation Single Sign-on (users who have logged into the Windows system using their domain account need not separately sign in to PMP) is possible only in Windows installation If you have installed PMP in Linux, agentless mode of password reset cannot be leveraged for Windows resources. You will have to use agent mode for resetting the passwords of Windows resources. Same is the case with Windows domain account password reset, Service Account and Scheduled Task password reset and Password reset for Services & Scheduled Tasks which are using local accounts
4 4 2.4 Using MS SQL Server as Backend Database SQL Server encrypts data with a hierarchical encryption and key management infrastructure. Each layer encrypts the layer below it by using a combination of certificates and symmetric keys. One among them is the Database Master Key, which in turn is created by Service Master Key and a password. This password is stored in PMP under <Password Manager Pro Installation Folder>/conf directory in a file named master_key.key. It is not secure to leave this file here, unless the server is sufficiently hardened to protect any illegal access of this file. It is highly recommended to move this file out of its default location. Take care to keep this key safe. You will require it while performing High Availability and Disaster Recovery. If you lose this key, you will have to configure MS SQL server setup all over again.for more details, refer to the following section of our help documentation. Since PMP connects to MSSQL only in SSL mode, it is recommended that you create a dedicated database instance running in a specific port for PMP. Rename sa account:renaming the sa account is a good security measure to be adopted on SQL Servers running in mixed authentication mode Remove all sample databases Use Windows Authentication logins instead of SQL Server logins If you are not using High Availability o Create a service account and map it to dbcreator role If you are using High Availability o Create a service account and map it to sysadmin role To ensure high level of security, PMP has been configured to connect to SQL server only through SSL. So, SSL encryption should be enabled in SQL server. PMP will start only ifssl connection is enabled ForceEncryption option should be enabled for the clients to connect to this SQL instance. When this is done, all client/server communication will be encrypted and clients that cannot support encryption will be denied access Disable all protocols other than TCP/IP in SQL server Hide this SQL instance to prevent it from being enumerated by other tools If the SQL Server resides in a different server than PMP installation, enable firewall rule in such a way that the IP <SQL-Instance>:Port is accessible only from the PMP Server If you have chosen to use a different database for PMP other than the default database created by PMP, make sure the service account used is the dbowner of the database Ensure that the users other than those with the role sa and sysadmin are not able to access the PMP database though they could have physical access to the database It is quite possible for the sa accounts and sysadmin privileged users to access the PMP database and access the passwords present there. So, take necessary precautions By default, symmetric key is created using AES 256 algorithm during PMP Installation. You can also create your own symmetric key, which PMPcan use for encryption Certain user defined functions and stored procedures are installed in the PMP database during installation.those user defined functions and stored procedures are in encryption format, which can be run by thedbownerandsa/sysadmin privileged accounts.
5 5 3.0 Key Settings after Installation 3.1 Secure the Installation Master Key (MySQL/MS SQL/PostgreSQL) PMP uses AES-256 encryption to secure the passwords and other sensitive information in the password database. The key used for encryption is auto-generated and is unique for every installation. By default, this encryption key is stored in a file named pmp_key.key under <PMP_HOME>/conf folder. For production instances, PMP does not allow the encryption key to be stored within its installation folder. This is done to ensure that the encryption key and the encrypted data, in both live and backed-up database, do not reside together. We strongly recommend that you move and store this encryption key outside of the machine in which PMP is installed - in another machine or an external drive. You can supply the full path of the folder where you want to move the pmp_key.key file and manually move the file to that location and delete any reference within PMP server installation folder. The path can be a mapped network drive or external USB (hard drive / thumb drive) device. PMP will store the location of the pmp_key.key in a configuration file named manage_key.conf present under <PMP_HOME>/conf folder. You can also edit that file directly to change the key file location. After configuring the folder location, move the pmp_key.key file to that location and ensure the file or the key value is not stored anywhere within the PMP installation folder.pmp requires the pmp_key.key folder accessible with necessary permissions to read the pmp_key.key file when it starts up every time. After a successful start-up, it does not need access to the file anymore and so the device with the file can be taken offline. Important Note: You need to take care of sufficiently protecting the key with layers of encryption (like using Windows File Encryption for example) and access control. Only the PMP application needs access to this key, so make sure no other software, script or person has access to this key under any circumstance. You also need to take care of securely backing up the pmp_key.key file yourself. You can recover from PMP backups only if you supply this key. If you misplace the key or lose it, PMP will not start. 3.2 Take Control of Database Key (MySQL/PostgreSQL) Apart from the AES encryption, the PMP database is secured through a separate key, which is auto - generated and unique for every installation. The key for the database can be stored securely in the PMP itself. There is also option to store it at some other secure location accessible to the PMP server. It is better to store the database key outside PMP. By default, the database password is present in the file <PMP Installation Folder>/conf/database_params.conf file If you choose to manage the database key by yourself, you need to store this configuration file somewhere securely and instruct the location of the file to PMP
6 6 If you are starting PMP as service, go to <<PMP InstallationFolder>/conf/wrapper.conf (in Windows) / <PMP Installation Folder>/conf/wrapper_lin.conf (in Linux) and edit the following entry under "Java Additional Parameters" wrapper.java.additional.9=-ddatabaseparams.file=<full path of the database_params.conf file location> If you are starting PMP from command line or through Start >> Programs, you need to edit the file system_properties.conf present in <PMP Installation Folder>/conf directory. In this file, edit the following entry under "Splash Screen default Properties" databaseparams.file=<full path of database_params.conf file> Note: If you misplace the conf file or lose it, PMP will not start. So, take care to save it in a secure location. 3.3 Database Key for MS SQL as Backend SQL server encrypts data with a hierarchical encryption and key management infrastructure. Each layer encrypts the layer below it by using a combination of certificates, asymmetric keys, and symmetric keys. One among them is the Database Master Key, which in turn is created by Service Master Key and a password. This password is stored in PMP under <Password Manager Pro Installation Folder>/conf directory in a file named masterkey.key. It is highly recommended that you move the masterkey.key file to a secure location. This is to ensure data security. Take care to keep this key safe. You will require it while performing High Availability and Disaster Recovery. If you lose this key, you will have to configure MS SQL server setup all over again. 4.0 Integration 4.1 Integration with Directory Services/Identity Stores Password Manager Pro can be integrated with third party identity stores such as Active Directory / LDAP. If you have AD or LDAP in place, it is recommended to integrate them with PMP. You can import users from AD / LDAP and also leverage their authentication mechanism. Users get the advantage of logging into PMP using the AD / Credentials. Additionally, PMP user database can be synchronized with AD / LDAP database at specified, periodic intervals. 5.0 User Management 5.1 Use Local PMP Accounts for Fire-Call Purposes Only By default, PMP allows local authentication along with AD or LDAP authentication. The best practice approach is to use local PMP account only for 'fire call' purposes and all other user accounts should be from a directory service to leverage good user management practices.
7 7 5.2 Decide about notification on user creation By default, whenever a new user account is added in PMP, an is triggered to the respective user with information about the login password in the case of new user addition. When you integrate AD/LDAP, decide beforehand if you wish PMP to send notification. Particularly, when you are evaluating the product, it is recommended that you disable notification. It can be done from General Settings option. 5.3 Create User Groups Organize the PMP users into groups - for example, Windows Administrators, Linux Administrators and so on. The grouping of users will immensely help in sharing resources. In case, you have integrated AD/LDAP, you can automatically have the same hierarchical structure in PMP just as in AD/LDAP, including the user groups. 5.4 Assign User Roles Properly After adding users, assign proper roles to them - Administrator, Password Administrator, Password Auditor or Password User. Also, decide if your organization requires any administrator or password administrator to act as a 'Super Administrator', who will have the privilege to view all the passwords in the system. 5.5 Use Two Factor Authentication To access the PMP web-interface, there is provision to enforce users to authenticate through two successive stages. While the first authentication is through the usual native authentication or AD / LDAP, the second level of authentication could be either through a one-time, randomly generated unique password sent by PMP to the user by , PhoneFactor Authentication, Google Authenticator, RADIUS Compliant or by leveraging RSA SecurID authentication as the second level of authentication. From security standpoint, it is recommended to make use of the Two Factor Authentication. 5.6 Remove the Default 'admin' Account For security reasons, it is highly recommended that the default 'admin' account of PMP be removed once you add another user with 'administrator' role. 6.0 Data Population & Organization 6.1 Prepare Inventory of Administrative Accounts The first step prior to actual Password Management using Password Manager Pro is identifying all the administrative accounts in your organization. This can be done by first preparing the inventory of all servers, databases, network devices and other sensitive applications. If you are
8 8 using other ManageEngine products such as Asset Explorer, OpManager, DeviceExpertetc, you can easily build an inventory of your resources. You can export the inventory as a CSV and then import them in PMP. In addition, each resource might contain more than one administrative account. You need to identify all such accounts. These are the accounts that are to be managed by PMP. 6.2 Leverage the Power of Resource Groups After adding resources, organize your resources into resource groups. Resource Groups are quite powerful in PMP.Most of the enterprise-class password management operations in PMP can be performed only at resource group level. Among the two types of resource group creation, "Criteria-based" resource groups are highly recommended. Criteria-based groups act as dynamic groups providing the flexibility to automatically make a resource, which satisfies certain criteria to become part of specific groups, without any manual intervention. For example, if you create a criteria-based resource group based on the condition "Resource Type Contains Windows", all Windows resources could be made part of the Windows group automatically after resource addition. Apart from the dynamic nature, the criteria-based resource groups allow you to create resource groups matching any required criteria - like department, location, type, name and even based on custom criteria. You can make use of a combination of criteria too. For example, you can create a group of resources belonging to type 'Linux' and location 'Second Floor' of the building. Moreover, if you have thousands of resources in your environment, picking resources individually to make them a resource group, would be a laborious task. So, making use of the criteria-based resource group is the best practice approach. 6.3 Resource Group - User Group Sharing: The Best Approach Though PMP has provision for sharing a single password or a single resource, the best practice approach here is sharing a resource group with a user group. This will come in handy when performing several bulk operations. For instance, assume there is a user group named "Windows Administrators" and there is a resource group named "Windows Servers" and all Windows Administrators should have access to all the Windows Resources. In this case, the best practice approach is: creating a criteria-based resource group (matching all resources of type "Windows") so that if you add a new "Windows Server", it will automatically become a part of the group sharing this criteria group to the "Windows Administrators" user group
9 9 if a new Windows Administrator joins the organization and gets an account in the AD/LDAP, the user will be automatically added to PMP; that too directly to the corresponding user group (if you have integrated AD/LDAP) the user will automatically inherit the permissions of the group to view the passwords of Windows servers Another example to bring out the benefit of Resource Group User Group Sharing: Consider that you have integrated Active Directory and you want to manage the passwords of the Windows resources belonging to a certain OU. Also, assume that you have an IT administrator group, which is also part of that OU. In this case, you can import the resources from the domain and create a criteria-based resource group. Similarly, you may import the users from the domain belonging to the OU and create that as a user group. In both the cases above, you can specify certain synchronization interval to keep the resources / users in PMP in sync with the ones in the Active Directory. You can then share the resource group with the user group. Once you do this, if any new resource/user is added to the OU, they will be automatically imported to PMP with the same share permissions. 6.4 Additional Fields for Easy Reference & Search Make use of the "Additional Field" creation feature to create customized columns at resource and accounts view. The additional fields will come in handy in creating criteria-based groups, searching specific resources or passwords and in sharing the resources etc. Assume the scenario that you have three levels of IT administrators in your organization. While creating resources, if you have an additional field specifying the level to which that particular resource belongs, it will be very convenient to share those resources to the respective level of users. That is, you will have an additional field titled "Access Level" for resources. Each resource will then have a level associated - Level I / Level II / Level III. You can then create a criteria-based resource group based on the level. Similarly, you can create three levels of user groups - all users belonging to Level I as a group and so on. You can then assign 'Level I' resources to 'Level I' users. 6.5 Make Use of Access Control Workflow If you have stored certain sensitive passwords, it is strongly recommended to enable 'Access Control Workflow' for that particular resource. When access control is enabled, users will have to go through a request-release flow for password access. It also helps in granting time-limited, exclusive privilege to passwords to select users.
10 Force Users to Provide Reason while Retrieving the Passwords By default, when a user tries to retrieve the password of a resource, on clicking the asterisks, the passwords appear in plain text. It is better to force the users to provide a reason why access to the password is needed. You can achieve this through an option in General Settings. 6.7 Agentless Mode for Password Reset One of the basic doubts that arise in the minds of PMP users is whether to use agentless mode or agent mode for password reset. Before recommending an option, let us first look at the requisites for both the modes: The agent mode requires the agent to be installed as a service and run with administrative privileges to perform password changes. The agent could be used in target machines, which will communicate with the PMP server and effect password changes. All password related communication is over HTTPS and is secure.the communication is always one way - that is, the agent alone will contact the server. The PMP server will not communicate with the agent. So, there is no need to keep any port open in the host where the agent has been installed. For the agentless mode, you must supply administrative credentials to perform the password changes. For Linux you must specify two accounts, one with root privileges and one with normal user privileges that can be used to login from remote. Telnet or SSH service must be running on the resources. For Windows domain, you must supply the domain administrator credentials. For Windows and Windows domain, PMP uses remote calls and relevant ports must be open on the resource. Based on this you can choose which mode you want for your environment, indicated by the following tips: Choose agent mode when, you do not have administrative credentials stored for a particular resource in PMP you do not have the required services running on the resource (Telnet / SSH for Linux,RPC for Windows) you run PMP in Linux and want to make password changes to a Windows resource Choose agentless mode in all other cases as it is a more convenient and reliable way of doing password changes. 6.8 Do Not Perform Password Resets Across Untrusted Domains By design, PMP is capable of resetting even foreign domain passwords without a trust. It is strictly NOT recommended to perform password resets across untrusted domains, as the setup could be exploited for malpractices.
11 Keep Tab on Activities Using Password Action Notification PMP offers provision to send notifications upon certain password events like a password access or modification or changing the share permission or when the password expires or when password policy is violated. Enabling 'Password Action Notification' helps achieve this Randomize Passwords Periodically Foremost among the 'Password Management Best Practices' is to periodically reset the administrative passwords. PMP provides option to automatically reset the passwords at predetermined intervals. Making use of the 'Scheduled Password Reset' feature you can achieve this. 7.0 Performance & Maintenance 7.1 MySQL Tuning PMP comes with an inbuilt MYSQL database, in which passwords and other sensitive information are stored in encrypted form. You can carry out the following MySQL tuning procedure to enhance the performance of PMP. Stop PMP server, if running Go to PMP_HOME\bin folder and open startdb.bat (in Windows) or startdb.sh (in Linux) in an editor Search for the line starting MySQL /B(Windows) and $DB_HOME/bin/mysqld(Linux)as shown below Windows "MySQL" /B "%DB_HOME%\bin\mysqld-nt" --no-defaults --standalone -- default-character-set=utf8 --basedir="%db_home%" --port=%db_port% -- datadir="%db_home%\data" --tmpdir="%db_home%\tmp" --user=root --serverid=%tstamp1% --log-bin=mysql-bin --log-slave-updates --master-connectretry=30 --slave-net-timeout=30 --expire_logs_days=7 --log-slave-updates -- log-slave-updates --max_allowed_packet= max_binlog_cache_size= binlog-do-db=passtrix -- binlog_cache_size= max_binlog_size= max_relay_log_size=0 -- relay_log_purge=1 --ssl-ca=..\conf\cacert.pem --sslcert=..\conf\servercer.cer --ssl-key=..\conf\serverkey.key Linux (startdb.sh) $DB_HOME/bin/mysqld --no-defaults --default-character-set=utf8 -- basedir=$db_home --tmpdir=$tmp_home --port=$db_port -- socket=$tmp_home/mysql.sock --user=root --server-id=$id --log-bin=mysql-bin - -log-slave-updates --master-connect-retry=30 --slave-net-timeout=30 -- expire_logs_days=7 --log-slave-updates --log-slave-updates -- max_allowed_packet= max_binlog_cache_size= binlog-
12 12 do-db=passtrix --binlog_cache_size= max_binlog_size= max_relay_log_size=0 --relay_log_purge=1 --ssl-ca=$pwd/../conf/cacert.pem -- ssl-cert=$pwd/../conf/servercer.cer --ssl-key=$pwd/../conf/serverkey.key -- log=mysql.log 2>>$TMP_HOME/mysql.out 1>>$TMP_HOME/mysql.out Two parameters - key buffer size and innodb buffer pool sizeare to be tuned to make sure it makes the most of the dedicated RAM. If the parameters are already present in the above line, just change the values as shown below. If they are not present, just add the parameters after the entry max_binlog_cache_size entry For 1 GB RAM, you can try values -- innodb_buffer_pool_size= (or) -- innodb_buffer_pool_size= For 3 GB RAM, you can try values -- key_buffer_size= innodb_buffer_pool_size= Stop and start the PMP server and see if there is any difference in performance Important Note: (1) In the above lines, any of the existing parameters should not be removed (2) Similarly, other than the suggested changes, no other new parameter be introduced 7.2 Purge Audit Records All operations performed in PMP are comprehensively audited and the trails are stored in the database. Naturally, the audit records grow at a faster rate. If you do not need the audit records that are older than a specified number of days, you can purge them. However, if regulatory compliance requirements demand retention of the audit records for longer period of time, you may have to retain the trails. 7.3 Configure Templates Password Manager Pro facilitates sending notifications on the occurrence of various password actions. By default, PMP has a specific content for the notification. It is recommended that you configure the template to suit your needs and have your own content.
13 Setup Disaster Recovery Data stored in PMP database are of critical importance. In the unlikely event of something going wrong with the production setup, all passwords would be lost. Disaster recovery provision is highly essential. PMP provides two options - live backup and scheduled backup. Choose any convenient method and backup your data. You can always rely on the backup data. 7.5 Moving PMP Installation from one Machine to Another If you want to move the PMP installed in one machine to another, follow the procedure detailed below: Caution Do not remove existing installation of PMP until the new installation works fine. This is to ensure having a valid backup setup to overcome disasters/data corruption during the movement. Procedure Stop PMP server / service, if running Simply copy the entire PMP installation folder from one machine to another Then, install it to run as service. In this option, you will not be able to uninstall the program through windows Add/Remove programs console. If you want to uninstall anytime, just delete the entire installation folder. 8.0 Security 8.1 Always Choose SSL in all Communication PMP offers both SSL mode and non-ssl mode for sensitive operations like password reset, resource addition/import etc. For obvious security advantages, it is recommended that you use SSL communication is used always. 8.2 Restrict plain-text password access for password users and auditors when auto logon is configured Through the auto logon feature, PMP provides the option to establish direct connection to the resource eliminating the need for copy-paste of passwords. By default, password users and auditors will be able to retrieve the passwords that are shared with them. If auto logon is configured, they might not need access to the passwords. In such cases, it is recommended to restrict access to passwords through an option in General Settings.
14 Configure Inactivity Timeout As PMP users are dealing with sensitive passwords, from the information security point of view, it would be hazardous to allow the web-interface session to remain alive if users leave their workstation unattended. Inactivity timeout could be configured by specifying the time limit in minutes through an option in General Settings. 8.4 Mask Passwords when Exporting Resources to CSV When you export PMP resources to a CSV file, by default, password of the accounts are included in plain text. From security standpoint, it is better to mask the password in the report. You can achieve this through an option in General Settings. 8.5 Make Use of Auto-Reset Provisions PMP provides options to carry out automatic password resets upon the completion of various activities such as changing password shares, password expiry, policy violation and when the password stored in PMP is not in sync with the one in the actual resource. From security standpoint, it is recommended that you make use of all the auto password reset options. 8.6 Audit Filters for Fine-Grained Tracking PMP has provision for granular recording of audit events and also to send notifications on the occurrence of each event. From security standpoint, it is highly recommended that you register for specific events or to the daily notification digest to achieve granular tracking of events. 8.7 Carry Out User Deprovisioning Promptly When an administrator leaves the organization, it is important that the passwords owned by the administrator are transferred to some other administrator. Otherwise, system lockout issues will occur. Also, it is quite possible that the administrator might have copied some / all the passwords. To rule out security breaches, it is recommended to reset all the passwords owned by the outgoing administrator before transferring the ownership. Website: Online Demo: Support: [email protected]
ManageEngine Password Manager Pro BEST PRACTICES GUIDE. ZOHO Corp
 BEST PRACTICES GUIDE ZOHO Corp 2 Password Manager Pro - Best Practices Guide 1.0 Overview This document describes the best practices in setting up and using Password Manager Pro in an enterprise network
BEST PRACTICES GUIDE ZOHO Corp 2 Password Manager Pro - Best Practices Guide 1.0 Overview This document describes the best practices in setting up and using Password Manager Pro in an enterprise network
GETTING STARTED. 2 USER MANAGEMENT. 36 TWO FACTOR AUTHENTICATION. 74 RESOURCE MANAGEMENT. 100 HIGH AVAILABLILITY. 219 SESSION MANAGEMENT. 250 MISC.
 Table of Contents GETTING STARTED... 2 USER MANAGEMENT... 36 TWO FACTOR AUTHENTICATION... 74 RESOURCE MANAGEMENT... 100 HIGH AVAILABLILITY... 219 SESSION MANAGEMENT... 250 MISC... 275 Getting Started Introduction
Table of Contents GETTING STARTED... 2 USER MANAGEMENT... 36 TWO FACTOR AUTHENTICATION... 74 RESOURCE MANAGEMENT... 100 HIGH AVAILABLILITY... 219 SESSION MANAGEMENT... 250 MISC... 275 Getting Started Introduction
ManageEngine Password Manager Pro Vs Thycotic Secret Server
 ManageEngine Password Manager Pro Vs Thycotic Secret Server Features Comparison Sheet (As per the information available in Thycotic Secret Server s website on August 19, 2015) Feature ManageEngine Password
ManageEngine Password Manager Pro Vs Thycotic Secret Server Features Comparison Sheet (As per the information available in Thycotic Secret Server s website on August 19, 2015) Feature ManageEngine Password
DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014
 DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014 Contents Overview... 2 System requirements:... 2 Before installing... 3 Download and installation... 3 Configure DESLock+ Enterprise Server...
DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014 Contents Overview... 2 System requirements:... 2 Before installing... 3 Download and installation... 3 Configure DESLock+ Enterprise Server...
Privileged. Account Management. Accounts Discovery, Password Protection & Management. Overview. Privileged. Accounts Discovery
 Overview Password Manager Pro offers a complete solution to control, manage, monitor and audit the entire life-cycle of privileged access. In a single package it offers three solutions - privileged account
Overview Password Manager Pro offers a complete solution to control, manage, monitor and audit the entire life-cycle of privileged access. In a single package it offers three solutions - privileged account
Stellar Active Directory Manager
 Stellar Active Directory Manager What is the need of Active Directory Manager? Every organization uses Active Directory Services (ADMS) to manage the users working in the organization. This task is mostly
Stellar Active Directory Manager What is the need of Active Directory Manager? Every organization uses Active Directory Services (ADMS) to manage the users working in the organization. This task is mostly
FileCloud Security FAQ
 is currently used by many large organizations including banks, health care organizations, educational institutions and government agencies. Thousands of organizations rely on File- Cloud for their file
is currently used by many large organizations including banks, health care organizations, educational institutions and government agencies. Thousands of organizations rely on File- Cloud for their file
Synchronizer Installation
 Synchronizer Installation Synchronizer Installation Synchronizer Installation This document provides instructions for installing Synchronizer. Synchronizer performs all the administrative tasks for XenClient
Synchronizer Installation Synchronizer Installation Synchronizer Installation This document provides instructions for installing Synchronizer. Synchronizer performs all the administrative tasks for XenClient
User's Guide. Product Version: 2.5.0 Publication Date: 7/25/2011
 User's Guide Product Version: 2.5.0 Publication Date: 7/25/2011 Copyright 2009-2011, LINOMA SOFTWARE LINOMA SOFTWARE is a division of LINOMA GROUP, Inc. Contents GoAnywhere Services Welcome 6 Getting Started
User's Guide Product Version: 2.5.0 Publication Date: 7/25/2011 Copyright 2009-2011, LINOMA SOFTWARE LINOMA SOFTWARE is a division of LINOMA GROUP, Inc. Contents GoAnywhere Services Welcome 6 Getting Started
ManageEngine Exchange Reporter Plus :: Help Documentation WELCOME TO EXCHANGE REPORTER PLUS... 4 GETTING STARTED... 7 DASHBOARD VIEW...
 TABLE OF CONTENTS WELCOME TO EXCHANGE REPORTER PLUS... 4 CONTACT ZOHO CORP.... 5 GETTING STARTED... 7 SYSTEM REQUIREMENTS... 8 INSTALLATION OF EXCHANGE REPORTER PLUS... 9 HOW EXCHANGE REPORTER PLUS WORKS...
TABLE OF CONTENTS WELCOME TO EXCHANGE REPORTER PLUS... 4 CONTACT ZOHO CORP.... 5 GETTING STARTED... 7 SYSTEM REQUIREMENTS... 8 INSTALLATION OF EXCHANGE REPORTER PLUS... 9 HOW EXCHANGE REPORTER PLUS WORKS...
ManageEngine EventLog Analyzer. Best Practices Document
 ManageEngine EventLog Analyzer Best Practices Document Table of Contents System Requirements... 3 Up to 50 hosts... 3 Up to 100 hosts... 3 Up to 200 hosts... 3 Up to 500 hosts... 3 Above 500 hosts... 4
ManageEngine EventLog Analyzer Best Practices Document Table of Contents System Requirements... 3 Up to 50 hosts... 3 Up to 100 hosts... 3 Up to 200 hosts... 3 Up to 500 hosts... 3 Above 500 hosts... 4
Table of Contents. Introduction...9. Installation...17. Program Tour...31. The Program Components...10 Main Program Features...11
 2011 AdRem Software, Inc. This document is written by AdRem Software and represents the views and opinions of AdRem Software regarding its content, as of the date the document was issued. The information
2011 AdRem Software, Inc. This document is written by AdRem Software and represents the views and opinions of AdRem Software regarding its content, as of the date the document was issued. The information
Lepide Active Directory Self Service. Configuration Guide. Follow the simple steps given in this document to start working with
 Lepide Active Directory Self Service Configuration Guide 2014 Follow the simple steps given in this document to start working with Lepide Active Directory Self Service Table of Contents 1. Introduction...3
Lepide Active Directory Self Service Configuration Guide 2014 Follow the simple steps given in this document to start working with Lepide Active Directory Self Service Table of Contents 1. Introduction...3
Sophos Mobile Control Installation guide. Product version: 3.6
 Sophos Mobile Control Installation guide Product version: 3.6 Document date: November 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...5 3 Set up Sophos Mobile Control...11 4 External
Sophos Mobile Control Installation guide Product version: 3.6 Document date: November 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...5 3 Set up Sophos Mobile Control...11 4 External
White Paper. Anywhere, Any Device File Access with IT in Control. Enterprise File Serving 2.0
 White Paper Enterprise File Serving 2.0 Anywhere, Any Device File Access with IT in Control Like it or not, cloud- based file sharing services have opened up a new world of mobile file access and collaborative
White Paper Enterprise File Serving 2.0 Anywhere, Any Device File Access with IT in Control Like it or not, cloud- based file sharing services have opened up a new world of mobile file access and collaborative
How To Set Up Safetica Insight 9 (Safetica) For A Safetrica Management Service (Sms) For An Ipad Or Ipad (Smb) (Sbc) (For A Safetaica) (
 SAFETICA INSIGHT INSTALLATION MANUAL SAFETICA INSIGHT INSTALLATION MANUAL for Safetica Insight version 6.1.2 Author: Safetica Technologies s.r.o. Safetica Insight was developed by Safetica Technologies
SAFETICA INSIGHT INSTALLATION MANUAL SAFETICA INSIGHT INSTALLATION MANUAL for Safetica Insight version 6.1.2 Author: Safetica Technologies s.r.o. Safetica Insight was developed by Safetica Technologies
ADSelfService Plus Client Software Installation Guide
 ADSelfService Plus Client Software Installation Guide ( I n s t a l l a t io n t h r o u g h A DS e l f S e r v ic e P l u s w e b p o r t a l a n d M a n u a l I n s t a l l a t io n ) 1 Table of Contents
ADSelfService Plus Client Software Installation Guide ( I n s t a l l a t io n t h r o u g h A DS e l f S e r v ic e P l u s w e b p o r t a l a n d M a n u a l I n s t a l l a t io n ) 1 Table of Contents
Sophos Mobile Control Installation guide. Product version: 3.5
 Sophos Mobile Control Installation guide Product version: 3.5 Document date: July 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...4 3 Set up Sophos Mobile Control...10 4 External
Sophos Mobile Control Installation guide Product version: 3.5 Document date: July 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...4 3 Set up Sophos Mobile Control...10 4 External
Ekran System Help File
 Ekran System Help File Table of Contents About... 9 What s New... 10 System Requirements... 11 Updating Ekran to version 4.1... 13 Program Structure... 14 Getting Started... 15 Deployment Process... 15
Ekran System Help File Table of Contents About... 9 What s New... 10 System Requirements... 11 Updating Ekran to version 4.1... 13 Program Structure... 14 Getting Started... 15 Deployment Process... 15
Installation & Configuration Guide
 Installation & Configuration Guide Bluebeam Studio Enterprise ( Software ) 2014 Bluebeam Software, Inc. All Rights Reserved. Patents Pending in the U.S. and/or other countries. Bluebeam and Revu are trademarks
Installation & Configuration Guide Bluebeam Studio Enterprise ( Software ) 2014 Bluebeam Software, Inc. All Rights Reserved. Patents Pending in the U.S. and/or other countries. Bluebeam and Revu are trademarks
Desktop Surveillance Help
 Desktop Surveillance Help Table of Contents About... 9 What s New... 10 System Requirements... 11 Updating from Desktop Surveillance 2.6 to Desktop Surveillance 3.2... 13 Program Structure... 14 Getting
Desktop Surveillance Help Table of Contents About... 9 What s New... 10 System Requirements... 11 Updating from Desktop Surveillance 2.6 to Desktop Surveillance 3.2... 13 Program Structure... 14 Getting
Table of Contents WELCOME TO AD360... 2. Welcome to AD360... 2. Contact Us... 4 GETTING STARTED... 6. Getting Started... 6. Sysem Requirements...
 Table of Contents WELCOME TO AD360... 2 Welcome to AD360... 2 Contact Us... 4 GETTING STARTED... 6 Getting Started... 6 Sysem Requirements... 7 Installing AD360... 8 Deployment Scenarios... 9 Working with
Table of Contents WELCOME TO AD360... 2 Welcome to AD360... 2 Contact Us... 4 GETTING STARTED... 6 Getting Started... 6 Sysem Requirements... 7 Installing AD360... 8 Deployment Scenarios... 9 Working with
XenClient Enterprise Synchronizer Installation Guide
 XenClient Enterprise Synchronizer Installation Guide Version 5.1.0 March 26, 2014 Table of Contents About this Guide...3 Hardware, Software and Browser Requirements...3 BIOS Settings...4 Adding Hyper-V
XenClient Enterprise Synchronizer Installation Guide Version 5.1.0 March 26, 2014 Table of Contents About this Guide...3 Hardware, Software and Browser Requirements...3 BIOS Settings...4 Adding Hyper-V
System Administration Training Guide. S100 Installation and Site Management
 System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
SECURITY DOCUMENT. BetterTranslationTechnology
 SECURITY DOCUMENT BetterTranslationTechnology XTM Security Document Documentation for XTM Version 6.2 Published by XTM International Ltd. Copyright XTM International Ltd. All rights reserved. No part of
SECURITY DOCUMENT BetterTranslationTechnology XTM Security Document Documentation for XTM Version 6.2 Published by XTM International Ltd. Copyright XTM International Ltd. All rights reserved. No part of
1.0 Hardware Requirements:
 01 - ServiceDesk Plus - Best Practices We appreciate you choosing ServiceDesk Plus for your organization to deliver world-class IT services. Before installing the product, take a few minutes to go through
01 - ServiceDesk Plus - Best Practices We appreciate you choosing ServiceDesk Plus for your organization to deliver world-class IT services. Before installing the product, take a few minutes to go through
Administrators Help Manual
 Administrators Help Manual Lepide Active Directory Self Service Lepide Software Private Limited Page 1 Administrators Help Manual for Active Directory Self-Service Lepide Active Directory Self Service
Administrators Help Manual Lepide Active Directory Self Service Lepide Software Private Limited Page 1 Administrators Help Manual for Active Directory Self-Service Lepide Active Directory Self Service
The SSL device also supports the 64-bit Internet Explorer with new ActiveX loaders for Assessment, Abolishment, and the Access Client.
 WatchGuard SSL v3.2 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 355419 Revision Date January 28, 2013 Introduction WatchGuard is pleased to announce the release of WatchGuard
WatchGuard SSL v3.2 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 355419 Revision Date January 28, 2013 Introduction WatchGuard is pleased to announce the release of WatchGuard
Sophos Mobile Control Installation guide. Product version: 3
 Sophos Mobile Control Installation guide Product version: 3 Document date: January 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...4 3 Set up Sophos Mobile Control...16 4 External
Sophos Mobile Control Installation guide Product version: 3 Document date: January 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...4 3 Set up Sophos Mobile Control...16 4 External
ManageEngine EventLog Analyzer. Best Practices Document
 ManageEngine EventLog Analyzer Best Practices Document Table of Contents System Requirements... 3 Up to 50 hosts... 3 Up to 100 hosts... 3 Up to 200 hosts... 3 Up to 500 hosts... 3 Above 500 hosts... 4
ManageEngine EventLog Analyzer Best Practices Document Table of Contents System Requirements... 3 Up to 50 hosts... 3 Up to 100 hosts... 3 Up to 200 hosts... 3 Up to 500 hosts... 3 Above 500 hosts... 4
AD Self-Service Suite for Active Directory
 The Dot Net Factory AD Self-Service Suite for Active Directory Version 3.6 The Dot Net Factory, LLC. 2005-2011. All rights reserved. This guide contains proprietary information, which is protected by copyright.
The Dot Net Factory AD Self-Service Suite for Active Directory Version 3.6 The Dot Net Factory, LLC. 2005-2011. All rights reserved. This guide contains proprietary information, which is protected by copyright.
NETWRIX IDENTITY MANAGEMENT SUITE
 NETWRIX IDENTITY MANAGEMENT SUITE FEATURES AND REQUIREMENTS Product Version: 3.3 February 2013. Legal Notice The information in this publication is furnished for information use only, and does not constitute
NETWRIX IDENTITY MANAGEMENT SUITE FEATURES AND REQUIREMENTS Product Version: 3.3 February 2013. Legal Notice The information in this publication is furnished for information use only, and does not constitute
JAMF Software Server Installation and Configuration Guide for Linux. Version 9.2
 JAMF Software Server Installation and Configuration Guide for Linux Version 9.2 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide
JAMF Software Server Installation and Configuration Guide for Linux Version 9.2 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide
Quick Start Guide for VMware and Windows 7
 PROPALMS VDI Version 2.1 Quick Start Guide for VMware and Windows 7 Rev. 1.1 Published: JULY-2011 1999-2011 Propalms Ltd. All rights reserved. The information contained in this document represents the
PROPALMS VDI Version 2.1 Quick Start Guide for VMware and Windows 7 Rev. 1.1 Published: JULY-2011 1999-2011 Propalms Ltd. All rights reserved. The information contained in this document represents the
(Installation through ADSelfService Plus web portal and Manual Installation)
 ADSelfService Plus Client Software Installation Guide (Installation through ADSelfService Plus web portal and Manual Installation) 1 Table of Contents Introduction:... 3 ADSelfService Plus Client software:...
ADSelfService Plus Client Software Installation Guide (Installation through ADSelfService Plus web portal and Manual Installation) 1 Table of Contents Introduction:... 3 ADSelfService Plus Client software:...
Product Manual. MDM On Premise Installation Version 8.1. Last Updated: 06/07/15
 Product Manual MDM On Premise Installation Version 8.1 Last Updated: 06/07/15 Parallels IP Holdings GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 632 0411 Fax: + 41 52 672 2010 www.parallels.com
Product Manual MDM On Premise Installation Version 8.1 Last Updated: 06/07/15 Parallels IP Holdings GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 632 0411 Fax: + 41 52 672 2010 www.parallels.com
Metalogix SharePoint Backup. Advanced Installation Guide. Publication Date: August 24, 2015
 Metalogix SharePoint Backup Publication Date: August 24, 2015 All Rights Reserved. This software is protected by copyright law and international treaties. Unauthorized reproduction or distribution of this
Metalogix SharePoint Backup Publication Date: August 24, 2015 All Rights Reserved. This software is protected by copyright law and international treaties. Unauthorized reproduction or distribution of this
JIJI AUDIT REPORTER FEATURES
 JIJI AUDIT REPORTER FEATURES JiJi AuditReporter is a web based auditing solution for live monitoring of the enterprise changes and for generating audit reports on each and every event occurring in the
JIJI AUDIT REPORTER FEATURES JiJi AuditReporter is a web based auditing solution for live monitoring of the enterprise changes and for generating audit reports on each and every event occurring in the
ManageEngine IT360. Professional Edition Installation Guide. [[email protected]]
![ManageEngine IT360. Professional Edition Installation Guide. [ims-eval@manageengine.com] ManageEngine IT360. Professional Edition Installation Guide. [ims-eval@manageengine.com]](/thumbs/20/454087.jpg) ManageEngine IT360 (Division of ZOHO Corporation) ) www.manageengine.com/it360 ManageEngine IT360 Professional Edition Installation Guide [[email protected]] [This document is a guideline for installing
ManageEngine IT360 (Division of ZOHO Corporation) ) www.manageengine.com/it360 ManageEngine IT360 Professional Edition Installation Guide [[email protected]] [This document is a guideline for installing
NSi Mobile Installation Guide. Version 6.2
 NSi Mobile Installation Guide Version 6.2 Revision History Version Date 1.0 October 2, 2012 2.0 September 18, 2013 2 CONTENTS TABLE OF CONTENTS PREFACE... 5 Purpose of this Document... 5 Version Compatibility...
NSi Mobile Installation Guide Version 6.2 Revision History Version Date 1.0 October 2, 2012 2.0 September 18, 2013 2 CONTENTS TABLE OF CONTENTS PREFACE... 5 Purpose of this Document... 5 Version Compatibility...
JAMF Software Server Installation and Configuration Guide for OS X. Version 9.0
 JAMF Software Server Installation and Configuration Guide for OS X Version 9.0 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide
JAMF Software Server Installation and Configuration Guide for OS X Version 9.0 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide
Propalms TSE Deployment Guide
 Propalms TSE Deployment Guide Version 7.0 Propalms Ltd. Published October 2013 Overview This guide provides instructions for deploying Propalms TSE in a production environment running Windows Server 2003,
Propalms TSE Deployment Guide Version 7.0 Propalms Ltd. Published October 2013 Overview This guide provides instructions for deploying Propalms TSE in a production environment running Windows Server 2003,
Copyright 2012 Trend Micro Incorporated. All rights reserved.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
JAMF Software Server Installation and Configuration Guide for OS X. Version 9.2
 JAMF Software Server Installation and Configuration Guide for OS X Version 9.2 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide
JAMF Software Server Installation and Configuration Guide for OS X Version 9.2 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide
Installation Guide for Pulse on Windows Server 2012
 MadCap Software Installation Guide for Pulse on Windows Server 2012 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
MadCap Software Installation Guide for Pulse on Windows Server 2012 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
Password Reset PRO INSTALLATION GUIDE
 Password Reset PRO INSTALLATION GUIDE This guide covers the new features and settings available in Password Reset PRO. Please read this guide completely to ensure a trouble-free installation. March 2009
Password Reset PRO INSTALLATION GUIDE This guide covers the new features and settings available in Password Reset PRO. Please read this guide completely to ensure a trouble-free installation. March 2009
Installation Guide for Pulse on Windows Server 2008R2
 MadCap Software Installation Guide for Pulse on Windows Server 2008R2 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
MadCap Software Installation Guide for Pulse on Windows Server 2008R2 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
Agency Pre Migration Tasks
 Agency Pre Migration Tasks This document is to be provided to the agency and will be reviewed during the Migration Technical Kickoff meeting between the ICS Technical Team and the agency. Network: Required
Agency Pre Migration Tasks This document is to be provided to the agency and will be reviewed during the Migration Technical Kickoff meeting between the ICS Technical Team and the agency. Network: Required
FileMaker Server 7. Administrator s Guide. For Windows and Mac OS
 FileMaker Server 7 Administrator s Guide For Windows and Mac OS 1994-2004, FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark
FileMaker Server 7 Administrator s Guide For Windows and Mac OS 1994-2004, FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark
WhatsUp Gold v16.3 Installation and Configuration Guide
 WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
VERSION 9.02 INSTALLATION GUIDE. www.pacifictimesheet.com
 VERSION 9.02 INSTALLATION GUIDE www.pacifictimesheet.com PACIFIC TIMESHEET INSTALLATION GUIDE INTRODUCTION... 4 BUNDLED SOFTWARE... 4 LICENSE KEY... 4 SYSTEM REQUIREMENTS... 5 INSTALLING PACIFIC TIMESHEET
VERSION 9.02 INSTALLATION GUIDE www.pacifictimesheet.com PACIFIC TIMESHEET INSTALLATION GUIDE INTRODUCTION... 4 BUNDLED SOFTWARE... 4 LICENSE KEY... 4 SYSTEM REQUIREMENTS... 5 INSTALLING PACIFIC TIMESHEET
LifeSize Control Installation Guide
 LifeSize Control Installation Guide April 2005 Part Number 132-00001-001, Version 1.0 Copyright Notice Copyright 2005 LifeSize Communications. All rights reserved. LifeSize Communications has made every
LifeSize Control Installation Guide April 2005 Part Number 132-00001-001, Version 1.0 Copyright Notice Copyright 2005 LifeSize Communications. All rights reserved. LifeSize Communications has made every
NetWrix USB Blocker. Version 3.6 Administrator Guide
 NetWrix USB Blocker Version 3.6 Administrator Guide Table of Contents 1. Introduction...3 1.1. What is NetWrix USB Blocker?...3 1.2. Product Architecture...3 2. Licensing...4 3. Operation Guide...5 3.1.
NetWrix USB Blocker Version 3.6 Administrator Guide Table of Contents 1. Introduction...3 1.1. What is NetWrix USB Blocker?...3 1.2. Product Architecture...3 2. Licensing...4 3. Operation Guide...5 3.1.
VMware vcenter Log Insight Getting Started Guide
 VMware vcenter Log Insight Getting Started Guide vcenter Log Insight 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
VMware vcenter Log Insight Getting Started Guide vcenter Log Insight 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
KASPERSKY LAB. Kaspersky Administration Kit version 6.0. Administrator s manual
 KASPERSKY LAB Kaspersky Administration Kit version 6.0 Administrator s manual KASPERSKY ADMINISTRATION KIT VERSION 6.0 Administrator s manual Kaspersky Lab Visit our website: http://www.kaspersky.com/
KASPERSKY LAB Kaspersky Administration Kit version 6.0 Administrator s manual KASPERSKY ADMINISTRATION KIT VERSION 6.0 Administrator s manual Kaspersky Lab Visit our website: http://www.kaspersky.com/
MEGA Web Application Architecture Overview MEGA 2009 SP4
 Revised: September 2, 2010 Created: March 31, 2010 Author: Jérôme Horber CONTENTS Summary This document describes the system requirements and possible deployment architectures for MEGA Web Application.
Revised: September 2, 2010 Created: March 31, 2010 Author: Jérôme Horber CONTENTS Summary This document describes the system requirements and possible deployment architectures for MEGA Web Application.
NETWRIX PASSWORD MANAGER
 NETWRIX PASSWORD MANAGER ADMINISTRATOR S GUIDE Product Version: 6.1 February/2012 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
NETWRIX PASSWORD MANAGER ADMINISTRATOR S GUIDE Product Version: 6.1 February/2012 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
Symantec Endpoint Encryption Full Disk
 Symantec Endpoint Encryption Full Disk Installation Guide Version 7.0 Information in this document is subject to change without notice. No part of this document may be reproduced or transmitted in any
Symantec Endpoint Encryption Full Disk Installation Guide Version 7.0 Information in this document is subject to change without notice. No part of this document may be reproduced or transmitted in any
POLICY PATROL MFT. Manual
 POLICY PATROL MFT Manual MANUAL Policy Patrol MFT This manual, and the software described in this manual, are copyrighted. No part of this manual or the described software may be copied, reproduced, translated
POLICY PATROL MFT Manual MANUAL Policy Patrol MFT This manual, and the software described in this manual, are copyrighted. No part of this manual or the described software may be copied, reproduced, translated
Sysax Multi Server User manual
 Sysax Multi Server User manual Table of Contents 1. Introduction to Sysax Multi Server... 1 1.1. Introduction to Sysax Multi Server... 2 2. Minimum System Requirements... 4 2.1. System Requirements...
Sysax Multi Server User manual Table of Contents 1. Introduction to Sysax Multi Server... 1 1.1. Introduction to Sysax Multi Server... 2 2. Minimum System Requirements... 4 2.1. System Requirements...
NETWRIX FILE SERVER CHANGE REPORTER
 NETWRIX FILE SERVER CHANGE REPORTER ADMINISTRATOR S GUIDE Product Version: 3.3 April/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute
NETWRIX FILE SERVER CHANGE REPORTER ADMINISTRATOR S GUIDE Product Version: 3.3 April/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute
WatchGuard SSL v3.2 Update 1 Release Notes. Introduction. Windows 8 and 64-bit Internet Explorer Support. Supported Devices SSL 100 and 560
 WatchGuard SSL v3.2 Update 1 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 445469 Revision Date 3 April 2014 Introduction WatchGuard is pleased to announce the release of WatchGuard
WatchGuard SSL v3.2 Update 1 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 445469 Revision Date 3 April 2014 Introduction WatchGuard is pleased to announce the release of WatchGuard
enicq 5 System Administrator s Guide
 Vermont Oxford Network enicq 5 Documentation enicq 5 System Administrator s Guide Release 2.0 Published November 2014 2014 Vermont Oxford Network. All Rights Reserved. enicq 5 System Administrator s Guide
Vermont Oxford Network enicq 5 Documentation enicq 5 System Administrator s Guide Release 2.0 Published November 2014 2014 Vermont Oxford Network. All Rights Reserved. enicq 5 System Administrator s Guide
Kaseya 2. User Guide. Version R8. English
 Kaseya 2 Discovery User Guide Version R8 English September 19, 2014 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as
Kaseya 2 Discovery User Guide Version R8 English September 19, 2014 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as
InstaFile. Complete Document management System
 InstaFile Complete Document management System Index : About InstaFile 1.1 What is InstaFile 1.2 How does it work 1.3 Where you can use InstaFile 1.4 Why only InstaFile InstaFile features and benefits Start
InstaFile Complete Document management System Index : About InstaFile 1.1 What is InstaFile 1.2 How does it work 1.3 Where you can use InstaFile 1.4 Why only InstaFile InstaFile features and benefits Start
insync Installation Guide
 insync Installation Guide 5.2 Private Cloud Druva Software June 21, 13 Copyright 2007-2013 Druva Inc. All Rights Reserved. Table of Contents Deploying insync Private Cloud... 4 Installing insync Private
insync Installation Guide 5.2 Private Cloud Druva Software June 21, 13 Copyright 2007-2013 Druva Inc. All Rights Reserved. Table of Contents Deploying insync Private Cloud... 4 Installing insync Private
NETWRIX EVENT LOG MANAGER
 NETWRIX EVENT LOG MANAGER QUICK-START GUIDE FOR THE ENTERPRISE EDITION Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not
NETWRIX EVENT LOG MANAGER QUICK-START GUIDE FOR THE ENTERPRISE EDITION Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not
Setting up High Availability
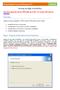 ManageEngine Password Manager Pro Tutorial Setting up High Availability (Procedure applicable only for PMP builds up to 6301. For versions 6302 and later, click here ) Overview Setting up high availability
ManageEngine Password Manager Pro Tutorial Setting up High Availability (Procedure applicable only for PMP builds up to 6301. For versions 6302 and later, click here ) Overview Setting up high availability
Sage Grant Management System Requirements
 Sage Grant Management System Requirements You should meet or exceed the following system requirements: One Server - Database/Web Server The following system requirements are for Sage Grant Management to
Sage Grant Management System Requirements You should meet or exceed the following system requirements: One Server - Database/Web Server The following system requirements are for Sage Grant Management to
WhatsUp Gold v16.1 Installation and Configuration Guide
 WhatsUp Gold v16.1 Installation and Configuration Guide Contents Installing and Configuring Ipswitch WhatsUp Gold v16.1 using WhatsUp Setup Installing WhatsUp Gold using WhatsUp Setup... 1 Security guidelines
WhatsUp Gold v16.1 Installation and Configuration Guide Contents Installing and Configuring Ipswitch WhatsUp Gold v16.1 using WhatsUp Setup Installing WhatsUp Gold using WhatsUp Setup... 1 Security guidelines
DESlock+ Basic Setup Guide ENTERPRISE SERVER ESSENTIAL/STANDARD/PRO
 DESlock+ Basic Setup Guide ENTERPRISE SERVER ESSENTIAL/STANDARD/PRO Contents Overview...1 System requirements...1 Enterprise Server:...1 Client PCs:...1 Section 1: Before installing...1 Section 2: Download
DESlock+ Basic Setup Guide ENTERPRISE SERVER ESSENTIAL/STANDARD/PRO Contents Overview...1 System requirements...1 Enterprise Server:...1 Client PCs:...1 Section 1: Before installing...1 Section 2: Download
Lexia Network Installation Instructions
 Lexia Network Installation Instructions For Lexia Early Reading 3.x, Primary Reading 1.x, Foundation Reading 1.x, Strategies for Older Students 4.x, Cross-Trainer 1.x and Quick Reading Test 2.x (NOT for
Lexia Network Installation Instructions For Lexia Early Reading 3.x, Primary Reading 1.x, Foundation Reading 1.x, Strategies for Older Students 4.x, Cross-Trainer 1.x and Quick Reading Test 2.x (NOT for
Installing CaseMap Server User Guide
 Installing CaseMap Server User Guide CaseMap Server, Version 1.8 System Requirements Installing CaseMap Server Installing the CaseMap Admin Console Installing the CaseMap SQL Import Utility Testing Installation
Installing CaseMap Server User Guide CaseMap Server, Version 1.8 System Requirements Installing CaseMap Server Installing the CaseMap Admin Console Installing the CaseMap SQL Import Utility Testing Installation
JAMF Software Server Installation and Configuration Guide for Windows. Version 9.3
 JAMF Software Server Installation and Configuration Guide for Windows Version 9.3 JAMF Software, LLC 2014 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this
JAMF Software Server Installation and Configuration Guide for Windows Version 9.3 JAMF Software, LLC 2014 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this
Table of Contents INTRODUCTION...7
 Table of Contents INTRODUCTION...7 System Requirements... 9 Installing AssetExplorer... 10 Uninstalling AssetExplorer... 14 Registering AssetExplorer... 15 Contacting ZOHO Corporation... 16 HOME...17 Dashboard...
Table of Contents INTRODUCTION...7 System Requirements... 9 Installing AssetExplorer... 10 Uninstalling AssetExplorer... 14 Registering AssetExplorer... 15 Contacting ZOHO Corporation... 16 HOME...17 Dashboard...
NetWrix USB Blocker Version 3.6 Quick Start Guide
 NetWrix USB Blocker Version 3.6 Quick Start Guide Table of Contents 1. Introduction...3 1.1. What is NetWrix USB Blocker?...3 1.2. Product Architecture...3 2. Licensing...4 3. Getting Started...5 3.1.
NetWrix USB Blocker Version 3.6 Quick Start Guide Table of Contents 1. Introduction...3 1.1. What is NetWrix USB Blocker?...3 1.2. Product Architecture...3 2. Licensing...4 3. Getting Started...5 3.1.
PAYMENTVAULT TM LONG TERM DATA STORAGE
 PAYMENTVAULT TM LONG TERM DATA STORAGE Version 3.0 by Auric Systems International 1 July 2010 Copyright c 2010 Auric Systems International. All rights reserved. Contents 1 Overview 1 1.1 Platforms............................
PAYMENTVAULT TM LONG TERM DATA STORAGE Version 3.0 by Auric Systems International 1 July 2010 Copyright c 2010 Auric Systems International. All rights reserved. Contents 1 Overview 1 1.1 Platforms............................
Storage Sync for Hyper-V. Installation Guide for Microsoft Hyper-V
 Installation Guide for Microsoft Hyper-V Egnyte Inc. 1890 N. Shoreline Blvd. Mountain View, CA 94043, USA Phone: 877-7EGNYTE (877-734-6983) www.egnyte.com 2013 by Egnyte Inc. All rights reserved. Revised
Installation Guide for Microsoft Hyper-V Egnyte Inc. 1890 N. Shoreline Blvd. Mountain View, CA 94043, USA Phone: 877-7EGNYTE (877-734-6983) www.egnyte.com 2013 by Egnyte Inc. All rights reserved. Revised
Password Reset PRO. Quick Setup Guide for Single Server or Two-Tier Installation
 Password Reset PRO Quick Setup Guide for Single Server or Two-Tier Installation This guide covers the features and settings available in Password Reset PRO version 3.x.x. Please read this guide completely
Password Reset PRO Quick Setup Guide for Single Server or Two-Tier Installation This guide covers the features and settings available in Password Reset PRO version 3.x.x. Please read this guide completely
Acronis Backup & Recovery 11.5
 Acronis Backup & Recovery 11.5 Update 2 Installation Guide Applies to the following editions: Advanced Server Server for Windows Virtual Edition Server for Linux Advanced Server SBS Edition Workstation
Acronis Backup & Recovery 11.5 Update 2 Installation Guide Applies to the following editions: Advanced Server Server for Windows Virtual Edition Server for Linux Advanced Server SBS Edition Workstation
STEALTHbits Technologies, Inc. StealthAUDIT v5.1 System Requirements and Installation Notes
 STEALTHbits Technologies, Inc. StealthAUDIT v5.1 System Requirements and Installation Notes June 2011 Table of Contents Overview... 3 Installation Overview... 3 Hosting System Requirements... 4 Recommended
STEALTHbits Technologies, Inc. StealthAUDIT v5.1 System Requirements and Installation Notes June 2011 Table of Contents Overview... 3 Installation Overview... 3 Hosting System Requirements... 4 Recommended
EventTracker Enterprise v7.3 Installation Guide
 EventTracker Enterprise v7.3 Installation Guide Publication Date: Sep 11, 2012 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide will help the users to install
EventTracker Enterprise v7.3 Installation Guide Publication Date: Sep 11, 2012 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide will help the users to install
HP A-IMC Firewall Manager
 HP A-IMC Firewall Manager Configuration Guide Part number: 5998-2267 Document version: 6PW101-20110805 Legal and notice information Copyright 2011 Hewlett-Packard Development Company, L.P. No part of this
HP A-IMC Firewall Manager Configuration Guide Part number: 5998-2267 Document version: 6PW101-20110805 Legal and notice information Copyright 2011 Hewlett-Packard Development Company, L.P. No part of this
VERITAS Backup Exec TM 10.0 for Windows Servers
 VERITAS Backup Exec TM 10.0 for Windows Servers Quick Installation Guide N134418 July 2004 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software
VERITAS Backup Exec TM 10.0 for Windows Servers Quick Installation Guide N134418 July 2004 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software
Netwrix Auditor. Administrator's Guide. Version: 7.1 10/30/2015
 Netwrix Auditor Administrator's Guide Version: 7.1 10/30/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix Corporation
Netwrix Auditor Administrator's Guide Version: 7.1 10/30/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix Corporation
SysPatrol - Server Security Monitor
 SysPatrol Server Security Monitor User Manual Version 2.2 Sep 2013 www.flexense.com www.syspatrol.com 1 Product Overview SysPatrol is a server security monitoring solution allowing one to monitor one or
SysPatrol Server Security Monitor User Manual Version 2.2 Sep 2013 www.flexense.com www.syspatrol.com 1 Product Overview SysPatrol is a server security monitoring solution allowing one to monitor one or
4cast Server Specification and Installation
 4cast Server Specification and Installation Version 2015.00 10 November 2014 Innovative Solutions for Education Management www.drakelane.co.uk System requirements Item Minimum Recommended Operating system
4cast Server Specification and Installation Version 2015.00 10 November 2014 Innovative Solutions for Education Management www.drakelane.co.uk System requirements Item Minimum Recommended Operating system
1. Product Information
 ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
Microsoft SQL Server Security Best Practices
 Microsoft SQL Server Security Best Practices This white paper contains administrative and operational best practices that should be performed from a security perspective when using Microsoft SQL Server.
Microsoft SQL Server Security Best Practices This white paper contains administrative and operational best practices that should be performed from a security perspective when using Microsoft SQL Server.
Netwrix Auditor for Exchange
 Netwrix Auditor for Exchange Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix
Netwrix Auditor for Exchange Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix
WhatsUp Gold v16.2 Installation and Configuration Guide
 WhatsUp Gold v16.2 Installation and Configuration Guide Contents Installing and Configuring Ipswitch WhatsUp Gold v16.2 using WhatsUp Setup Installing WhatsUp Gold using WhatsUp Setup... 1 Security guidelines
WhatsUp Gold v16.2 Installation and Configuration Guide Contents Installing and Configuring Ipswitch WhatsUp Gold v16.2 using WhatsUp Setup Installing WhatsUp Gold using WhatsUp Setup... 1 Security guidelines
Manual POLICY PATROL SECURE FILE TRANSFER
 Manual POLICY PATROL SECURE FILE TRANSFER MANUAL Policy Patrol Secure File Transfer This manual, and the software described in this manual, are copyrighted. No part of this manual or the described software
Manual POLICY PATROL SECURE FILE TRANSFER MANUAL Policy Patrol Secure File Transfer This manual, and the software described in this manual, are copyrighted. No part of this manual or the described software
Online Backup Client User Manual Linux
 Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Implementing HIPAA Compliance with ScriptLogic
 Implementing HIPAA Compliance with ScriptLogic A ScriptLogic Product Positioning Paper By Nick Cavalancia 1.800.424.9411 www.scriptlogic.com Table of Contents INTRODUCTION... 3 HIPAA BACKGROUND... 3 ADMINISTRATIVE
Implementing HIPAA Compliance with ScriptLogic A ScriptLogic Product Positioning Paper By Nick Cavalancia 1.800.424.9411 www.scriptlogic.com Table of Contents INTRODUCTION... 3 HIPAA BACKGROUND... 3 ADMINISTRATIVE
Workflow Templates Library
 Workflow s Library Table of Contents Intro... 2 Active Directory... 3 Application... 5 Cisco... 7 Database... 8 Excel Automation... 9 Files and Folders... 10 FTP Tasks... 13 Incident Management... 14 Security
Workflow s Library Table of Contents Intro... 2 Active Directory... 3 Application... 5 Cisco... 7 Database... 8 Excel Automation... 9 Files and Folders... 10 FTP Tasks... 13 Incident Management... 14 Security
How To Install Powerpoint 6 On A Windows Server With A Powerpoint 2.5 (Powerpoint) And Powerpoint 3.5.5 On A Microsoft Powerpoint 4.5 Powerpoint (Powerpoints) And A Powerpoints 2
 DocAve 6 Service Pack 1 Installation Guide Revision C Issued September 2012 1 Table of Contents About the Installation Guide... 4 Submitting Documentation Feedback to AvePoint... 4 Before You Begin...
DocAve 6 Service Pack 1 Installation Guide Revision C Issued September 2012 1 Table of Contents About the Installation Guide... 4 Submitting Documentation Feedback to AvePoint... 4 Before You Begin...
CTERA Agent for Linux
 User Guide CTERA Agent for Linux September 2013 Version 4.0 Copyright 2009-2013 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
User Guide CTERA Agent for Linux September 2013 Version 4.0 Copyright 2009-2013 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
Novell Open Workgroup Suite
 Novell Open Workgroup Suite Small Business Edition QUICK START GUIDE September 2007 v1.5 Page 1 Introduction This Quick Start explains how to install the Novell Open Workgroup Suite software on a server.
Novell Open Workgroup Suite Small Business Edition QUICK START GUIDE September 2007 v1.5 Page 1 Introduction This Quick Start explains how to install the Novell Open Workgroup Suite software on a server.
