Check Point taps the power of virtualization to simplify security for private clouds
|
|
|
- Junior Rodgers
- 8 years ago
- Views:
Transcription
1 Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private cloud? Need customized and finely tuned solutions to better protect your growing network needs? You are not alone. In fact, you are among the majority of today s IT professionals who are faced with the challenging task of managing complex securities in an ever growing and more demanding network environment. The increasing complexity of network security and new threats combined with a slowing growth of IT budget drive the need for a solution that improves operational efficiency, optimizes security and lowers costs. Network security consolidation has become a strategic trend for IT professionals to deliver more effective security at lower costs. By consolidating multiple security gateways in a single solution, both enterprises and service providers have the opportunity to optimize productivity and minimize the total cost of ownership (TCO). Organizations can achieve an overall reduction in capital equipment costs (CapEx) as well as in operating costs (OpEx) by reducing the hardware investment and streamlining the management of securing large segmented networks and data centers. Service Providers have the opportunity to increase revenue by delivering new security services easily and efficiency to customers through their managed services. OVERVIEW Check Point Virtual Systems enable organizations to consolidate infrastructure by creating multiple virtualized security gateways on a single hardware device, delivering deep cost savings, seamless security and infrastructure consolidation. Based on proven virtualized security design and the extensible Software Blade Architecture, Virtual Systems provide best-in-class customized security protections to multiple networks and simplify enterprise-wide policy by creating tailored policies for each network. Administrators can replicate conventional physical security gateways with Virtual Systems to deliver advanced protection to multiple networks and network segments. Up to 250 fully independent Virtual Systems can be supported on Check Point gateways or Open Servers, delivering scalability, availability and performance while dramatically reduce hardware investment, space requirements and maintenance costs. KEY FEATURES n Consolidate up to 250 gateways in a single device n Software Blade Architecture n GAiA 64-bit operating system n Separation of management duties n Customized security policies per Virtual System n Per Virtual System Monitoring of resource usage n Linear scalability of up to 13 clustered gateways with technology n Simple one-click conversion from physical to virtual n Supported as software-only on Check Point Appliances or Open Servers and as pre-configured appliances KEY BENEFITS n Easily add virtual systems to any security gateway n Out of the box complete solution with virtualized system appliances n Reduce hardware cost and simplified network policy by consolidating multiple gateways into a single device n Stronger performance and manageability enable enterprises to better leverage their investment n More granularity and greater manageability with customizable policies per Virtual System n Better usage-based resource planning with per Virtual System monitoring n Boost performance with Multi-core CoreXL technology SUPPORTED SOFTWARE BLADES Firewall 3 VPN 3 Identity Awareness 3 IPS 3 Application Control 3 URL Filtering 3 Antivirus 3 Anti-bot 3 Mobile Access* 3 * SSL VPN available in a future releases 1
2 The latest Check Point technologies ensure best performance for virtualized security; CoreXL technology utilizes multi-core processors to increase throughput, 64-bit GAiA OS provides over eight times more concurrent connections, and patented technology delivers unmatched performance scalability with up to 8 members per cluster. PROVEN VIRTUAL SYSTEM TECHNOLOGY For years, Check Point s Virtual Systems technology has been providing value and protection for enterprises and service providers. This proven technology enables organizations to segment their network while simplifying policy settings, consolidating multiple gateways into a hardware platform and providing savings on both capital equipment investments and going support and maintenance. The streamlined management of the virtualized gateways further improves the operational efficiency of a resource-challenged IT department. SOFTWARE BLADE ARCHITECTURE SUPPORT Supporting the latest Check Point Software Blade Architecture on every Virtual System, this solution delivers comprehensive protection to multiple networks. Administrators have the flexibility to configure any Software Blades with any security policy to any Virtual System. CUSTOMIZABLE SECURITY POLICIES Simplify complex network security policy with more granular and manageable one by creating tailored policies for each Virtual System. Customizing security policy base on requirements and minimizing the complexity create better security practice to meet the business needs. STREAMLIZED CENTRAL MANAGEMENT Check Point Security Management and Multi-Domain Security Management solutions provide an effective tool for the administration of the Virtual Systems. Dedicated Virtual Systems for Web Security, Threat Prevention, Firewall, and Remote access enable separation of IT duties. Separate management per Virtual Systems and data segregation support cloud based security-as-a-service needs. INTEGRATED VIRTUAL ROUTERS AND SWITCHES Complete virtualization of network infrastructure allows easy deployment and configuration of network topology with simpler inter-vs communication. Save the costs of external network routers and switches. The integrated virtual routers, switches and links direct traffics to their intended destinations with higher efficiency. HIGH PERFORMANCE Along with the latest technology and the 64-bit GAiA OS, performance boosts for virtualized security deployments. Up to eight times more concurrent connection capacity, multi-gigabit-per-second performance for firewall and IPS throughputs are just a few examples of the outstanding performance enhancements these Virtual Systems will have. Check Point CoreXL technology utilizes today s gateways multi-core processors to accelerate traffic and increase throughput. LINEAR SCALABILITY Today s networks require flexibility and expandability to support the fast-evolving business needs. To meet this demanding business environment, Virtual Systems can be deployed on multiple gateways ensuring secure, resilient, multi-gigabit throughput. Virtual System Load Sharing () distributes traffic load within a cluster, providing the ability to distribute virtual systems across multiple cluster members, without requiring any change to existing topology. Every addition of a cluster member effectively spreads the virtual system traffic load within the cluster, providing the benefits of throughput, concurrent connections, redundancy, cost efficiency, configuration simplicity, priority designation, and system scalability. PER-VS RESOURCE MONITORING Need to understand how your Virtual Systems are used to better plan your security resources or to create billable customer services? Granular resource monitoring of CPU and Memory for each Virtual System gives you the necessary insights to effectively plan for your network security resources, or to provide usage-based services to your customers. Resource Control allows administrators to manage the processing load by guaranteeing that each virtual system will receive only the memory and CPU allocation it needs to deliver its functions. Resources not needed by one virtual system are automatically made available to other virtual systems. Administrators can also limit the CPU resource available to a lower-priority virtual system and assign more resources to mission-critical virtual systems. IPV6 READY Control and manage IPv4 and IPv6 networks with Software Blades security using the same rule base and objects for both IPv4 and IPv6. Ease the transition to IPv6 with dual stack IPv4 and IPv6 architecture, IPv6 in IPv4 (RFC4213) tunneling and NAT66 network address translation. FLEXIBLE PACKAGING OPTIONS Check Point Virtual Systems are offered either as a software-only option or in pre-configured bundles with Check Point Security Appliances and Software Blades, providing the flexibility and convenience for different deployment situations. The software only option allows customers to enable Virtual Systems from a physical system with an easy one-click conversion. 2
3 SPECIFICATIONS Software Release Operating System Minimum Memory Supported Technologies R75.40VS or later GAiA 2GB CoreXL, ClusterXL, SSL Inspection VIRTUAL SYSTEMS UPGRADE PACKAGES SKU Description Supported Appliance CPSB-VS-3, CPSB-VS-3 CPSB-VS-3, CPSB-VS-3- CPSB-VS-3, CPSB-VS-10 CPSB-VS-3, CPSB-VS-10- CPSB-VS-3, CPSB-VS-25 CPSB-VS-3, CPSB-VS-25- CPSB-VS-3, CPSB-VS-50 CPSB-VS-3, CPSB-VS-50-3 Virtual Systems Package 10 Virtual Systems Package 25 Virtual Systems Package 50 Virtual Systems Package 2200, 4200, 4400, 4600, UTM , Open Server (1 or 2 cores) 4400, 4600, 4800, 12200, 12400, 12600, 13500, 21400, 21600, 21700, 61000, Power , Power , IAS, Open Server (4+ cores) 4800, 12200, 12400, 12600, 13500, 21400, 21600, 21700, 61000, Power , Power , IAS, Open Server (4+ cores) 12200, 12400,12600, 13500, 21400, 21600, 21700, 61000, Power , Power , IP1280, IP2450, IAS, Open Server (4+ cores) MAXIMUM VIRTUAL SYSTEMS Supported Appliances Appliance Memory (default/max) GB Maximum VS Supported (with default appliance memory) Maximum VS Supported (with max appliance memory) / / / / / / / / / / / / / UTM / Power / Power / Power / IP / IP /
4 VIRTUAL SYSTEMS APPLIANCES Pre-configured Virtual Systems bundled with Check Point Security Appliance, Virtual Systems and Software Blades. The Virtual System Appliances are available in single system and dual-system high-availability () configurations. Performance Firewall Throughput (Gbps) VPN Throughput (Gbps) Concurrent Sessions (M) Network Base-T Ports Base-S SFP Ports Base-F SFP+ Ports /12 16/24 8/12 16/24 8/16 16/32 8/16 16/32 10/26 20/52 0/4 0/8 0/4 0/8 0/4 0/8 0/4 0/8 0/12 0/24 N/A N/A N/A N/A 0/2 0/4 0/4 0/8 0/12 0/24 Expansion Slots Additional Features Virtual Systems (Included/Maximum) Physical 5/10 5/10 5/10 5/10 10/25 10/25 10/50 10/50 10/75 10/75 Enclosure 1U 2U 1U 2U 1U 2U 1U 2U 2U 4U Weight (lb.) Power Dual, Hot-Swap PSU No No No No Optional Optional Yes Yes Yes Yes Power Input VAC, 47-63Hz Max power Consumption (W) DC Power Option 2 No No Yes Yes Yes Yes Yes Yes Yes Yes Software Blades Included Software Blades 1 With memory upgrade and GAiA OS 2 Via a Solution Center Request Firewall, VPN, Identity Awareness, Advanced Networking & Clustering, Mobile Access, IPS and Application Control 4
5 VIRTUAL SYSTEMS APPLIANCES (Continued) Performance Firewall Throughput (Gbps) VPN Throughput (Gbps) Concurrent Sessions (M) Network Base-T Ports Base-S SFP Ports Base-F SFP+ Ports /26 28/52 14/26 28/52 13/37 26/74 13/37 26/74 13/37 26/74 0/12 0/24 0/12 0/24 0/36 0/72 0/36 0/72 0/36 0/72 0/12 0/24 0/12 0/24 0/12 0/24 0/13 0/26 0/13 0/26 Expansion Slots Additional Features Virtual Systems (Included/Maximum) Physical 20/150 20/150 20/250 20/250 20/250 20/250 20/250 20/250 20/250 20/250 Enclosure 2U 4U 2U 4U 2U 4U 2U 4U 2U 4U Weight (lb.) Power Dual, Hot-Swap PSU Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Power Input VAC, 47-63Hz Max power Consumption (W) W 978W DC Power Option 2 Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Software Blades Included Software Blades 1 With memory upgrade and GAiA OS 2 Via a Solution Center Request Firewall, VPN, Identity Awareness, Advanced Networking & Clustering, Mobile Access, IPS and Application Control CONTACT CHECK POINT Worldwide Headquarters 5 Ha Solelim Street, Tel Aviv 67897, Israel Tel: Fax: info@checkpoint.com U.S. Headquarters 959 Skyway Road, Suite 300, San Carlos, CA Tel: ; Fax: July 26, 2013
Securing Virtualization with Check Point and Consolidation with Virtualized Security
 Securing Virtualization with Check Point and Consolidation with Virtualized Security consolidate security gateways with full power of Software Blades with Check Point Virtual Systems (VSX) secure virtualized
Securing Virtualization with Check Point and Consolidation with Virtualized Security consolidate security gateways with full power of Software Blades with Check Point Virtual Systems (VSX) secure virtualized
Check Point 4800 Appliance
 Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance (623 SPU/Gbps) great multi-blade performance and 0Gb Fiber connectivity options Check Point 4800 Appliance Today the enterprise
Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance (623 SPU/Gbps) great multi-blade performance and 0Gb Fiber connectivity options Check Point 4800 Appliance Today the enterprise
Appliance Comparison Chart
 202 Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark) Security 4 4 223 374 623 Firewall (Gbps).4.4 2.2 3.4 5.8 Firewall and IPS (Mbps) 50 50
202 Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark) Security 4 4 223 374 623 Firewall (Gbps).4.4 2.2 3.4 5.8 Firewall and IPS (Mbps) 50 50
Check Point 13500 Appliance
 Datasheet: Check Point 3500 Appliance 3500 Blazing fast data center cyber-security Check Point 3500 Appliance YOUR CHALLENGE Large data centers have uncompromising needs for performance, uptime and scalability.
Datasheet: Check Point 3500 Appliance 3500 Blazing fast data center cyber-security Check Point 3500 Appliance YOUR CHALLENGE Large data centers have uncompromising needs for performance, uptime and scalability.
Scalable. Reliable. Flexible. High Performance Architecture. Fault Tolerant System Design. Expansion Options for Unique Business Needs
 Protecting the Data That Drives Business SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding network environments.
Protecting the Data That Drives Business SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding network environments.
Scalable. Reliable. Flexible. High Performance Architecture. Fault Tolerant System Design. Expansion Options for Unique Business Needs
 Protecting the Data That Drives Business SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding network environments.
Protecting the Data That Drives Business SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding network environments.
Check Point 4800 Appliance
 Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance Check Point 4800 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance Check Point 4800 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Check Point 21400 Appliance
 Datasheet: Check Point 2400 Appliance 2400 Datacenter-grade security appliance Check Point 2400 Appliance Today s firewall is a security device presented with an ever-increasing number of sophisticated
Datasheet: Check Point 2400 Appliance 2400 Datacenter-grade security appliance Check Point 2400 Appliance Today s firewall is a security device presented with an ever-increasing number of sophisticated
Check Point 12200 Appliance
 Datasheet: Check Point 2200 Appliance 2200 Datacenter-grade security appliance Check Point 2200 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Datasheet: Check Point 2200 Appliance 2200 Datacenter-grade security appliance Check Point 2200 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Check Point 12400 Appliance
 Datasheet: Check Point 400 Appliance 400 Datacenter-grade security appliance Check Point 400 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an ever-increasing
Datasheet: Check Point 400 Appliance 400 Datacenter-grade security appliance Check Point 400 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an ever-increasing
Check Point 12600 Appliance
 Datasheet: Check Point 2600 Appliance 2600 Datacenter-grade security appliance Check Point 2600 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Datasheet: Check Point 2600 Appliance 2600 Datacenter-grade security appliance Check Point 2600 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Check Point 2200 Appliance
 Datasheet: Check Point 2200 Appliance 2200 Branch & Small Office Solution Enterprise security in a desktop package Check Point 2200 Appliance Today the Internet gateway is more than a firewall. It is a
Datasheet: Check Point 2200 Appliance 2200 Branch & Small Office Solution Enterprise security in a desktop package Check Point 2200 Appliance Today the Internet gateway is more than a firewall. It is a
CHECK POINT. Software Blade Architecture. Secure. Flexible. Simple.
 CHECK POINT Software Blade Architecture Secure. Flexible. Simple. softwareblades from Check Point Today s Security Challenge Protecting networks against today s constantly evolving threat environment has
CHECK POINT Software Blade Architecture Secure. Flexible. Simple. softwareblades from Check Point Today s Security Challenge Protecting networks against today s constantly evolving threat environment has
Appliance Comparison Chart
 Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Appliance Comparison Chart
 Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Check Point Appliances
 Check Point Appliances Table of Contents Introduction 3 Check Point GAiA - a Unified Secure Operating System 4 About SecurityPower 5 Next Generation Security Solutions 6 600 Appliances 7 1100 Appliances
Check Point Appliances Table of Contents Introduction 3 Check Point GAiA - a Unified Secure Operating System 4 About SecurityPower 5 Next Generation Security Solutions 6 600 Appliances 7 1100 Appliances
Cisco ACE 4710 Application Control Engine
 Data Sheet Cisco ACE 4710 Application Control Engine Product Overview The Cisco ACE 4710 Application Control Engine (Figure 1) belongs to the Cisco ACE family of application switches, used to increase
Data Sheet Cisco ACE 4710 Application Control Engine Product Overview The Cisco ACE 4710 Application Control Engine (Figure 1) belongs to the Cisco ACE family of application switches, used to increase
The Attacker s Target: The Small Business
 Check Point Whitepaper The Attacker s Target: The Small Business Even Small Businesses Need Enterprise-class Security to protect their Network July 2013 Contents Introduction 3 Enterprise-grade Protection
Check Point Whitepaper The Attacker s Target: The Small Business Even Small Businesses Need Enterprise-class Security to protect their Network July 2013 Contents Introduction 3 Enterprise-grade Protection
Extreme Security Threat Protection G2 - Intrusion Prevention Integrated security, visibility, and control for next- generation network protection
 DATA SHEET Extreme Security Threat Protection G2 - Intrusion Prevention Integrated security, visibility, and control for next- generation network protection HIGHLIGHTS Delivers superior zero-day threat
DATA SHEET Extreme Security Threat Protection G2 - Intrusion Prevention Integrated security, visibility, and control for next- generation network protection HIGHLIGHTS Delivers superior zero-day threat
CHECK POINT TOTAL SECURITY APPLIANCES. Flexible Deployment. Centralized Management.
 CHECK POINT TOTAL SECURITY APPLIANCES Flexible Deployment. Centralized Management. Check Point appliances deliver a powerful turnkey solution for deploying Check Point awardwinning software solutions to
CHECK POINT TOTAL SECURITY APPLIANCES Flexible Deployment. Centralized Management. Check Point appliances deliver a powerful turnkey solution for deploying Check Point awardwinning software solutions to
Imperva SecureSphere Appliances
 Imperva SecureSphere Appliances DA T A SH E E T Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior and resiliency for demanding data center environments. With fail open interfaces,
Imperva SecureSphere Appliances DA T A SH E E T Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior and resiliency for demanding data center environments. With fail open interfaces,
Introduction to VMware EVO: RAIL. White Paper
 Introduction to VMware EVO: RAIL White Paper Table of Contents Introducing VMware EVO: RAIL.... 3 Hardware.................................................................... 4 Appliance...............................................................
Introduction to VMware EVO: RAIL White Paper Table of Contents Introducing VMware EVO: RAIL.... 3 Hardware.................................................................... 4 Appliance...............................................................
VIRTUALIZED SECURITY: THE NEXT GENERATION OF CONSOLIDATION
 WHITEPAPER A consolidated security infrastructure is more than just an idea; in today s world of increasingly diversified threats and associated rising costs, it s imperative that organizations adopt a
WHITEPAPER A consolidated security infrastructure is more than just an idea; in today s world of increasingly diversified threats and associated rising costs, it s imperative that organizations adopt a
Radware ADC-VX Solution. The Agility of Virtual; The Predictability of Physical
 Radware ADC-VX Solution The Agility of Virtual; The Predictability of Physical Table of Contents General... 3 Virtualization and consolidation trends in the data centers... 3 How virtualization and consolidation
Radware ADC-VX Solution The Agility of Virtual; The Predictability of Physical Table of Contents General... 3 Virtualization and consolidation trends in the data centers... 3 How virtualization and consolidation
Increase Simplicity and Improve Reliability with VPLS on the MX Series Routers
 SOLUTION BRIEF Enterprise Data Center Interconnectivity Increase Simplicity and Improve Reliability with VPLS on the Routers Challenge As enterprises improve business continuity by enabling resource allocation
SOLUTION BRIEF Enterprise Data Center Interconnectivity Increase Simplicity and Improve Reliability with VPLS on the Routers Challenge As enterprises improve business continuity by enabling resource allocation
Virtualized Security: The Next Generation of Consolidation
 Virtualization. Consolidation. Simplification. Choice. WHITE PAPER Virtualized Security: The Next Generation of Consolidation Virtualized Security: The Next Generation of Consolidation As we approach the
Virtualization. Consolidation. Simplification. Choice. WHITE PAPER Virtualized Security: The Next Generation of Consolidation Virtualized Security: The Next Generation of Consolidation As we approach the
Benefits. Product Overview. There is nothing more important than our customers. DATASHEET
 DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
Business Case for Data Center Network Consolidation
 Business Case for Data Center Network Consolidation Executive Summary Innovations in cloud, big data, and mobility as well as users expectations for anywhere, anytime, and any device access are defining
Business Case for Data Center Network Consolidation Executive Summary Innovations in cloud, big data, and mobility as well as users expectations for anywhere, anytime, and any device access are defining
SecureSphere Appliances
 DATASHEET SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding datacenter environments. With fail open interfaces,
DATASHEET SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding datacenter environments. With fail open interfaces,
Support of Windows Server 2012 The NCP Secure Enterprise VPN Server supports the Windows Server 2012 (64 bit) operating system.
 NCP Secure Enterprise HA Server Service Release 3.03 Build 007 (Windows 32/64) Date: March 2013 1. New Features and Enhancements The following new feature has been introduced in this release: Support of
NCP Secure Enterprise HA Server Service Release 3.03 Build 007 (Windows 32/64) Date: March 2013 1. New Features and Enhancements The following new feature has been introduced in this release: Support of
Product Factsheet MANAGED SECURITY SERVICES - FIREWALLS - FACT SHEET
 Product Factsheet MANAGED SECURITY SERVICES - FIREWALLS - FACT SHEET ELITE S NEXT GENERATION MANAGED SECURITY SERVICES Security risks to business information systems are expanding at a rapid rate; often,
Product Factsheet MANAGED SECURITY SERVICES - FIREWALLS - FACT SHEET ELITE S NEXT GENERATION MANAGED SECURITY SERVICES Security risks to business information systems are expanding at a rapid rate; often,
APV9650. Application Delivery Controller
 APV9650 D a t a S h e e t Application Delivery Controller Array Networks APV Series of Application Delivery Controllers optimizes the availability, user experience, performance, security and scalability
APV9650 D a t a S h e e t Application Delivery Controller Array Networks APV Series of Application Delivery Controllers optimizes the availability, user experience, performance, security and scalability
CHECK POINT. Software Blade Architecture
 CHECK POINT Software Blade Architecture 2 softwareblades from Check Point Today s Security Challenge Protecting enterprises against today s constantly evolving threat environment has never been more challenging.
CHECK POINT Software Blade Architecture 2 softwareblades from Check Point Today s Security Challenge Protecting enterprises against today s constantly evolving threat environment has never been more challenging.
Deliver More Applications for More Users
 HARDWARE DATASHEET Deliver More Applications for More Users F5 BIG-IP Application Delivery Controller (ADC) platforms can manage even the heaviest traffic loads at both layer 4 and layer 7. By merging
HARDWARE DATASHEET Deliver More Applications for More Users F5 BIG-IP Application Delivery Controller (ADC) platforms can manage even the heaviest traffic loads at both layer 4 and layer 7. By merging
Astaro Gateway Software Applications
 Astaro Overview Astaro Products - Astaro Security Gateway - Astaro Web Gateway - Astaro Mail Gateway - Astaro Command Center - Astaro Report Manager Astaro Gateway Software Applications - Network Security
Astaro Overview Astaro Products - Astaro Security Gateway - Astaro Web Gateway - Astaro Mail Gateway - Astaro Command Center - Astaro Report Manager Astaro Gateway Software Applications - Network Security
IREBOX X. Firebox X Family of Security Products. Comprehensive Unified Threat Management Solutions That Scale With Your Business
 IREBOX X IREBOX X Firebox X Family of Security Products Comprehensive Unified Threat Management Solutions That Scale With Your Business Family of Security Products Comprehensive unified threat management
IREBOX X IREBOX X Firebox X Family of Security Products Comprehensive Unified Threat Management Solutions That Scale With Your Business Family of Security Products Comprehensive unified threat management
Sophos SG Series Appliances
 Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Customer Service Description Next Generation Network Firewall
 Customer Service Description Next Generation Network Firewall Interoute, Walbrook Building, 195 Marsh Wall, London, E14 9SG, UK Tel: +800 4683 7681 Email: info@interoute.com Interoute Communications Limited
Customer Service Description Next Generation Network Firewall Interoute, Walbrook Building, 195 Marsh Wall, London, E14 9SG, UK Tel: +800 4683 7681 Email: info@interoute.com Interoute Communications Limited
Next Generation Network Firewall
 Next Generation Network Firewall Overview Next Generation Network Firewalls are an important part of protecting any organisation from Internet traffic. Next Generation Firewalls provide a central point
Next Generation Network Firewall Overview Next Generation Network Firewalls are an important part of protecting any organisation from Internet traffic. Next Generation Firewalls provide a central point
Cisco Small Business ISA500 Series Integrated Security Appliances
 Q & A Cisco Small Business ISA500 Series Integrated Security Appliances Q. What is the Cisco Small Business ISA500 Series Integrated Security Appliance? A. The Cisco Small Business ISA500 Series Integrated
Q & A Cisco Small Business ISA500 Series Integrated Security Appliances Q. What is the Cisco Small Business ISA500 Series Integrated Security Appliance? A. The Cisco Small Business ISA500 Series Integrated
Business Case for a DDoS Consolidated Solution
 Business Case for a DDoS Consolidated Solution Executive Summary Distributed denial-of-service (DDoS) attacks are becoming more serious and sophisticated. Attack motivations are increasingly financial
Business Case for a DDoS Consolidated Solution Executive Summary Distributed denial-of-service (DDoS) attacks are becoming more serious and sophisticated. Attack motivations are increasingly financial
Centralized Orchestration and Performance Monitoring
 DATASHEET NetScaler Command Center Centralized Orchestration and Performance Monitoring Key Benefits Performance Management High Availability (HA) Support Seamless VPX management Enables Extensible architecture
DATASHEET NetScaler Command Center Centralized Orchestration and Performance Monitoring Key Benefits Performance Management High Availability (HA) Support Seamless VPX management Enables Extensible architecture
Benefits. Product Overview. There is nothing more important than our customers. DATASHEET
 DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
WATCHGUARD FIREBOX SOHO 6TC AND SOHO 6
 WATCHGUARD FIREBOX SOHO 6TC AND SOHO 6 FIREWALL AND VPN APPLIANCES FOR SMALL BUSINESSES AND BRANCH OFFICES Today, complete Internet security goes beyond a firewall. Firebox SOHO 6tc and SOHO 6 are dedicated
WATCHGUARD FIREBOX SOHO 6TC AND SOHO 6 FIREWALL AND VPN APPLIANCES FOR SMALL BUSINESSES AND BRANCH OFFICES Today, complete Internet security goes beyond a firewall. Firebox SOHO 6tc and SOHO 6 are dedicated
Proactively Secure Your Cloud Computing Platform
 Proactively Secure Your Cloud Computing Platform Dr. Krutartha Patel Security Engineer 2010 Check Point Software Technologies Ltd. [Restricted] ONLY for designated groups and individuals Agenda 1 Cloud
Proactively Secure Your Cloud Computing Platform Dr. Krutartha Patel Security Engineer 2010 Check Point Software Technologies Ltd. [Restricted] ONLY for designated groups and individuals Agenda 1 Cloud
MANAGED SHAREPOINT SOLUTIONS
 Page 0 2015 SOLUTION BRIEF MANAGED SHAREPOINT SOLUTIONS Private SharePoint 2013 SharePoint 2013 with Office apps NET ACCESS LLC 9 Wing Drive Cedar Knolls, NJ 07927 www.nac.net Page 1 Table of Contents
Page 0 2015 SOLUTION BRIEF MANAGED SHAREPOINT SOLUTIONS Private SharePoint 2013 SharePoint 2013 with Office apps NET ACCESS LLC 9 Wing Drive Cedar Knolls, NJ 07927 www.nac.net Page 1 Table of Contents
Radware ADC-VX Solution. The Agility of Virtual; The Predictability of Physical
 Radware ADC-VX Solution The Agility of Virtual; The Predictability of Physical Table of Contents General... 3 Virtualization and consolidation trends in the data centers... 3 How virtualization and consolidation
Radware ADC-VX Solution The Agility of Virtual; The Predictability of Physical Table of Contents General... 3 Virtualization and consolidation trends in the data centers... 3 How virtualization and consolidation
Appliance Comparison Chart
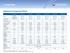 Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Check Point Software Blade Architecture. Achieving the right balance between security protection and investment
 Check Point Software Blade Architecture Achieving the right balance between security protection and investment Contents Introduction 3 Check Point Software Blade architecture overview 3 What is a Software
Check Point Software Blade Architecture Achieving the right balance between security protection and investment Contents Introduction 3 Check Point Software Blade architecture overview 3 What is a Software
Sophos SG Series Appliances
 Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
MANAGED EXCHANGE SOLUTIONS Secure, Scalable and Compliant Hosted Environments
 Page 0 2015 SOLUTION BRIEF MANAGED EXCHANGE SOLUTIONS Secure, Scalable and Compliant Hosted Environments NET ACCESS LLC 9 Wing Drive Cedar Knolls NJ 07927 www.nac.net Page 1 Table of Contents 1. Introduction...
Page 0 2015 SOLUTION BRIEF MANAGED EXCHANGE SOLUTIONS Secure, Scalable and Compliant Hosted Environments NET ACCESS LLC 9 Wing Drive Cedar Knolls NJ 07927 www.nac.net Page 1 Table of Contents 1. Introduction...
The On-Demand Application Delivery Controller
 What s Inside: 2 Increase Intelligence, Not Operating Costs 2 Simplify Your Network 2 Maximize Large-Scale Application Performance 2 Achieve Ultimate Reliability 2 The Advantages of Technology 6 Platforms
What s Inside: 2 Increase Intelligence, Not Operating Costs 2 Simplify Your Network 2 Maximize Large-Scale Application Performance 2 Achieve Ultimate Reliability 2 The Advantages of Technology 6 Platforms
Array Secure Mail Solution
 Array Secure Mail Solution Array Networks SSL VPN Solution Brief for Service Providers What is Array Secure Mail Solution? The Array Secure Mail Solution (SMS) is based on Array SSL VPN technology and
Array Secure Mail Solution Array Networks SSL VPN Solution Brief for Service Providers What is Array Secure Mail Solution? The Array Secure Mail Solution (SMS) is based on Array SSL VPN technology and
PRODUCTS & TECHNOLOGY
 PRODUCTS & TECHNOLOGY DATA CENTER CLASS WAN OPTIMIZATION Today s major IT initiatives all have one thing in common: they require a well performing Wide Area Network (WAN). However, many enterprise WANs
PRODUCTS & TECHNOLOGY DATA CENTER CLASS WAN OPTIMIZATION Today s major IT initiatives all have one thing in common: they require a well performing Wide Area Network (WAN). However, many enterprise WANs
How Solace Message Routers Reduce the Cost of IT Infrastructure
 How Message Routers Reduce the Cost of IT Infrastructure This paper explains how s innovative solution can significantly reduce the total cost of ownership of your messaging middleware platform and IT
How Message Routers Reduce the Cost of IT Infrastructure This paper explains how s innovative solution can significantly reduce the total cost of ownership of your messaging middleware platform and IT
Why Choose Integrated VPN/Firewall Solutions over Stand-alone VPNs
 Why Choose Integrated VPN/Firewall Solutions over Stand-alone VPNs P/N 500205 July 2000 Check Point Software Technologies Ltd. In this Document: Introduction Page 1 Integrated VPN/firewall Page 2 placed
Why Choose Integrated VPN/Firewall Solutions over Stand-alone VPNs P/N 500205 July 2000 Check Point Software Technologies Ltd. In this Document: Introduction Page 1 Integrated VPN/firewall Page 2 placed
安 瑞 科 技 物 聯 網 對 應 用 交 付 器 (ADC) 的 需 求 及 應 用 實 例 徐 乃 丁 博 士 研 發 副 總 裁 / 技 術 長
 安 瑞 科 技 物 聯 網 對 應 用 交 付 器 (ADC) 的 需 求 及 應 用 實 例 徐 乃 丁 博 士 研 發 副 總 裁 / 技 術 長 Internet of Things needs Application Delivery Controller (ADC) But Internet of Things demands a new class of networking equipment,
安 瑞 科 技 物 聯 網 對 應 用 交 付 器 (ADC) 的 需 求 及 應 用 實 例 徐 乃 丁 博 士 研 發 副 總 裁 / 技 術 長 Internet of Things needs Application Delivery Controller (ADC) But Internet of Things demands a new class of networking equipment,
Business Case for S/Gi Network Simplification
 Business Case for S/Gi Network Simplification Executive Summary Mobile broadband traffic growth is driving large cost increases but revenue is failing to keep pace. Service providers, consequently, are
Business Case for S/Gi Network Simplification Executive Summary Mobile broadband traffic growth is driving large cost increases but revenue is failing to keep pace. Service providers, consequently, are
Game changing Technology für Ihre Kunden. Thomas Bürgis System Engineering Manager CEE
 Game changing Technology für Ihre Kunden Thomas Bürgis System Engineering Manager CEE Threats have evolved traditional firewalls & IPS have not Protection centered around ports & protocols Expensive to
Game changing Technology für Ihre Kunden Thomas Bürgis System Engineering Manager CEE Threats have evolved traditional firewalls & IPS have not Protection centered around ports & protocols Expensive to
ZEN LOAD BALANCER EE v3.04 DATASHEET The Load Balancing made easy
 ZEN LOAD BALANCER EE v3.04 DATASHEET The Load Balancing made easy OVERVIEW The global communication and the continuous growth of services provided through the Internet or local infrastructure require to
ZEN LOAD BALANCER EE v3.04 DATASHEET The Load Balancing made easy OVERVIEW The global communication and the continuous growth of services provided through the Internet or local infrastructure require to
Content Scanning for secure transactions using Radware s SecureFlow and AppXcel together with Aladdin s esafe Gateway
 TESTING & INTEGRATION GROUP SOLUTION GUIDE Content Scanning for secure transactions using Radware s SecureFlow and AppXcel together with Aladdin s esafe Gateway INTRODUCTION...2 RADWARE SECUREFLOW... 3
TESTING & INTEGRATION GROUP SOLUTION GUIDE Content Scanning for secure transactions using Radware s SecureFlow and AppXcel together with Aladdin s esafe Gateway INTRODUCTION...2 RADWARE SECUREFLOW... 3
NET ACCESS HIPAA COMPLIANT FLEXCloud
 Page 0 2015 SOLUTION BRIEF NET ACCESS HIPAA COMPLIANT FLEXCloud A Managed Infrastructure Solution that Meets the Regulatory Demands of the Health Care Industry NET ACCESS LLC 9 Wing Drive Cedar Knolls,
Page 0 2015 SOLUTION BRIEF NET ACCESS HIPAA COMPLIANT FLEXCloud A Managed Infrastructure Solution that Meets the Regulatory Demands of the Health Care Industry NET ACCESS LLC 9 Wing Drive Cedar Knolls,
Cisco WAAS Express. Product Overview. Cisco WAAS Express Benefits. The Cisco WAAS Express Advantage
 Data Sheet Cisco WAAS Express Product Overview Organizations today face several unique WAN challenges: the need to provide employees with constant access to centrally located information at the corporate
Data Sheet Cisco WAAS Express Product Overview Organizations today face several unique WAN challenges: the need to provide employees with constant access to centrally located information at the corporate
Clavister SSP Security Service Platform firewall VPN termination intrusion prevention anti-virus content filtering traffic shaping authentication
 Feature Brief Policy-Based Server Load Balancing March 2007 Clavister SSP Security Service Platform firewall VPN termination intrusion prevention anti-virus content filtering traffic shaping authentication
Feature Brief Policy-Based Server Load Balancing March 2007 Clavister SSP Security Service Platform firewall VPN termination intrusion prevention anti-virus content filtering traffic shaping authentication
QRadar Security Intelligence Platform Appliances
 DATASHEET Total Security Intelligence An IBM Company QRadar Security Intelligence Platform Appliances QRadar Security Intelligence Platform appliances combine typically disparate network and security management
DATASHEET Total Security Intelligence An IBM Company QRadar Security Intelligence Platform Appliances QRadar Security Intelligence Platform appliances combine typically disparate network and security management
SonicWALL Advantages Over WatchGuard
 Competitive Analysis August 2001 WatchGuard SOHO - Product Overview WatchGuard Technologies extended its product offerings to the fast-growing broadband market through the acquisition of BeadleNet, LLC,
Competitive Analysis August 2001 WatchGuard SOHO - Product Overview WatchGuard Technologies extended its product offerings to the fast-growing broadband market through the acquisition of BeadleNet, LLC,
access convergence management performance security
 access convergence management performance security 2010 2009 2008 2007 WINNER 2007 WINNER 2008 WINNER 2009 WINNER 2010 AX Series Advantage A10 Networks was created to solve business problems through the
access convergence management performance security 2010 2009 2008 2007 WINNER 2007 WINNER 2008 WINNER 2009 WINNER 2010 AX Series Advantage A10 Networks was created to solve business problems through the
SonicWALL Corporate Design System. The SonicWALL Brand Identity
 SonicWALL Corporate Design System The SonicWALL Brand Identity 1 SonicWALL Corporate Vision Vision Dynamic Security for the Global Network Our vision is simple: we believe security solutions should be
SonicWALL Corporate Design System The SonicWALL Brand Identity 1 SonicWALL Corporate Vision Vision Dynamic Security for the Global Network Our vision is simple: we believe security solutions should be
WatchGuard: Your Security Partner of Choice. Carlos Vieira
 WatchGuard: Your Security Partner of Choice Carlos Vieira About WatchGuard Over a decade of security expertise Security is our sole focus Firewall appliance pioneer Headquartered in Seattle, WA Offices
WatchGuard: Your Security Partner of Choice Carlos Vieira About WatchGuard Over a decade of security expertise Security is our sole focus Firewall appliance pioneer Headquartered in Seattle, WA Offices
Radware s AppDirector and AppXcel An Application Delivery solution for applications developed over BEA s Weblogic
 TESTING & INTEGRATION GROUP SOLUTION GUIDE Radware s AppDirector and AppXcel An Application Delivery solution for applications developed over BEA s Weblogic Contents INTRODUCTION... 2 RADWARE APPDIRECTOR...
TESTING & INTEGRATION GROUP SOLUTION GUIDE Radware s AppDirector and AppXcel An Application Delivery solution for applications developed over BEA s Weblogic Contents INTRODUCTION... 2 RADWARE APPDIRECTOR...
Next Gen Data Center. KwaiSeng Consulting Systems Engineer kslai@cisco.com
 Next Gen Data Center KwaiSeng Consulting Systems Engineer kslai@cisco.com Taiwan Update Feb 08, kslai 2006 Cisco 2006 Systems, Cisco Inc. Systems, All rights Inc. reserved. All rights reserved. 1 Agenda
Next Gen Data Center KwaiSeng Consulting Systems Engineer kslai@cisco.com Taiwan Update Feb 08, kslai 2006 Cisco 2006 Systems, Cisco Inc. Systems, All rights Inc. reserved. All rights reserved. 1 Agenda
APV x600 Series. Application Delivery Controller APV1600, APV2600, APV4600, APV5600, APV6600, APV8600, APV9600
 APV x600 Series D a t a S h e e t Application Delivery Controller APV1600, APV2600, APV4600, APV5600, APV6600, APV8600, APV9600 Array Networks APV Series of Application Delivery Controllers optimizes the
APV x600 Series D a t a S h e e t Application Delivery Controller APV1600, APV2600, APV4600, APV5600, APV6600, APV8600, APV9600 Array Networks APV Series of Application Delivery Controllers optimizes the
AppDirector Load balancing IBM Websphere and AppXcel
 TESTING & INTEGRATION GROUP SOLUTION GUIDE AppDirector Load balancing IBM Websphere and AppXcel INTRODUCTION...2 RADWARE APPDIRECTOR...3 RADWARE APPXCEL...3 IBM WEBSPHERE...4 SOLUTION DETAILS...4 HOW IT
TESTING & INTEGRATION GROUP SOLUTION GUIDE AppDirector Load balancing IBM Websphere and AppXcel INTRODUCTION...2 RADWARE APPDIRECTOR...3 RADWARE APPXCEL...3 IBM WEBSPHERE...4 SOLUTION DETAILS...4 HOW IT
VMware vcloud Networking and Security Overview
 VMware vcloud Networking and Security Overview Networks and Security for Virtualized Compute Environments WHITE PAPER Overview Organizations worldwide have gained significant efficiency and flexibility
VMware vcloud Networking and Security Overview Networks and Security for Virtualized Compute Environments WHITE PAPER Overview Organizations worldwide have gained significant efficiency and flexibility
Bivio 7000 Series Network Appliance Platforms
 W H I T E P A P E R Bivio 7000 Series Network Appliance Platforms Uncompromising performance. Unmatched flexibility. Uncompromising performance. Unmatched flexibility. The Bivio 7000 Series Programmable
W H I T E P A P E R Bivio 7000 Series Network Appliance Platforms Uncompromising performance. Unmatched flexibility. Uncompromising performance. Unmatched flexibility. The Bivio 7000 Series Programmable
Virtual Compute Appliance Frequently Asked Questions
 General Overview What is Oracle s Virtual Compute Appliance? Oracle s Virtual Compute Appliance is an integrated, wire once, software-defined infrastructure system designed for rapid deployment of both
General Overview What is Oracle s Virtual Compute Appliance? Oracle s Virtual Compute Appliance is an integrated, wire once, software-defined infrastructure system designed for rapid deployment of both
Secure Access Complete Visibility
 PACKET CAPTURE APPLIANCE PACKET CAPTURE APPLIANCE PACKET CAPTURE APPLIANCE PACKET CAPTURE APPLIANCE Intrusion Detection Switch TAP Data Recorder VoIP Analyzer Switch Secure Access Complete Visibility Web
PACKET CAPTURE APPLIANCE PACKET CAPTURE APPLIANCE PACKET CAPTURE APPLIANCE PACKET CAPTURE APPLIANCE Intrusion Detection Switch TAP Data Recorder VoIP Analyzer Switch Secure Access Complete Visibility Web
The Cisco ASA 5500 as a Superior Firewall Solution
 The Cisco ASA 5500 as a Superior Firewall Solution The Cisco ASA 5500 Series Adaptive Security Appliance provides leading-edge firewall capabilities and expands to support other security services. Firewalls
The Cisco ASA 5500 as a Superior Firewall Solution The Cisco ASA 5500 Series Adaptive Security Appliance provides leading-edge firewall capabilities and expands to support other security services. Firewalls
Mit Soft- & Hardware zum Erfolg. Giuseppe Paletta
 Mit Soft- & Hardware zum Erfolg IT-Transformation VCE Converged and Hyperconverged Infrastructure VCE VxRack EMC VSPEX Blue IT-Transformation IT has changed dramatically in last past years The requirements
Mit Soft- & Hardware zum Erfolg IT-Transformation VCE Converged and Hyperconverged Infrastructure VCE VxRack EMC VSPEX Blue IT-Transformation IT has changed dramatically in last past years The requirements
AVX SERIES VIRTUALIZED APPLIANCES
 MULTI-TENANT EQUALS MULTI-BENEFIT. AVX DATASHEET AVX SERIES VIRTUALIZED APPLIANCES AVX Series multi-tenant virtualized appliances support multiple independent ADC or SSL VPN instances to deliver the performance
MULTI-TENANT EQUALS MULTI-BENEFIT. AVX DATASHEET AVX SERIES VIRTUALIZED APPLIANCES AVX Series multi-tenant virtualized appliances support multiple independent ADC or SSL VPN instances to deliver the performance
Purpose-Built Load Balancing The Advantages of Coyote Point Equalizer over Software-based Solutions
 Purpose-Built Load Balancing The Advantages of Coyote Point Equalizer over Software-based Solutions Abstract Coyote Point Equalizer appliances deliver traffic management solutions that provide high availability,
Purpose-Built Load Balancing The Advantages of Coyote Point Equalizer over Software-based Solutions Abstract Coyote Point Equalizer appliances deliver traffic management solutions that provide high availability,
Who s Endian? www.cloudrouter.dk
 Who s Endian? Endian was founded in 2003 at Appiano, Italy, by a team of experienced network specialists and Linux enthusiasts. Endian s goal and path of development are immediately clear: creating sophisticated
Who s Endian? Endian was founded in 2003 at Appiano, Italy, by a team of experienced network specialists and Linux enthusiasts. Endian s goal and path of development are immediately clear: creating sophisticated
Check Point Software Blade Architecture. Achieving the right balance between security protection and investment
 Check Point Software Blade Architecture Achieving the right balance between security protection and investment Check Point Software Blade Architecture Contents Introduction 3 Check Point Software Blade
Check Point Software Blade Architecture Achieving the right balance between security protection and investment Check Point Software Blade Architecture Contents Introduction 3 Check Point Software Blade
VM-Series for VMware. PALO ALTO NETWORKS: VM-Series for VMware
 VM-Series for VMware The VM-Series for VMware supports VMware NSX, ESXI stand-alone and vcloud Air, allowing you to deploy next-generation firewall security and advanced threat prevention within your VMware-based
VM-Series for VMware The VM-Series for VMware supports VMware NSX, ESXI stand-alone and vcloud Air, allowing you to deploy next-generation firewall security and advanced threat prevention within your VMware-based
Dell Desktop Virtualization Solutions Simplified. All-in-one VDI appliance creates a new level of simplicity for desktop virtualization
 Dell Desktop Virtualization Solutions Simplified All-in-one VDI appliance creates a new level of simplicity for desktop virtualization Executive summary Desktop virtualization is a proven method for delivering
Dell Desktop Virtualization Solutions Simplified All-in-one VDI appliance creates a new level of simplicity for desktop virtualization Executive summary Desktop virtualization is a proven method for delivering
Application Delivery Testing at 100Gbps and Beyond
 Application Delivery Testing at 100Gbps and Beyond The Need for Speed 10 Gigabit Ethernet (GE) rapidly became the technology of choice for high speed connections to servers and network devices. Advancements
Application Delivery Testing at 100Gbps and Beyond The Need for Speed 10 Gigabit Ethernet (GE) rapidly became the technology of choice for high speed connections to servers and network devices. Advancements
Your Security Partner of Choice
 Your Security Partner of Choice 6/16/14 2 About WatchGuard 100% CHANNEL 5,000 partners in 120 countries Ø Firewall appliance pioneer Ø Nearing 1,000,000 appliances shipped to business customers worldwide
Your Security Partner of Choice 6/16/14 2 About WatchGuard 100% CHANNEL 5,000 partners in 120 countries Ø Firewall appliance pioneer Ø Nearing 1,000,000 appliances shipped to business customers worldwide
Business Case for Virtual Managed Services
 Business Case for Virtual Managed Services Executive Summary Managed services allow businesses to offload day-to-day network management tasks to service providers and thus free up internal talent to focus
Business Case for Virtual Managed Services Executive Summary Managed services allow businesses to offload day-to-day network management tasks to service providers and thus free up internal talent to focus
Total Cost of Ownership: Benefits of Comprehensive, Real-Time Gateway Security
 Total Cost of Ownership: Benefits of Comprehensive, Real-Time Gateway Security White Paper September 2003 Abstract The network security landscape has changed dramatically over the past several years. Until
Total Cost of Ownership: Benefits of Comprehensive, Real-Time Gateway Security White Paper September 2003 Abstract The network security landscape has changed dramatically over the past several years. Until
How To Use The Cisco Wide Area Application Services (Waas) Network Module
 Cisco Wide Area Application Services (WAAS) Network Module The Cisco Wide Area Application Services (WAAS) Network Module for the Cisco Integrated Services Routers (ISR) is a powerful WAN optimization
Cisco Wide Area Application Services (WAAS) Network Module The Cisco Wide Area Application Services (WAAS) Network Module for the Cisco Integrated Services Routers (ISR) is a powerful WAN optimization
Leveraging Radware s ADC-VX to Reduce Data Center TCO An ROI Paper on Radware s Industry-First ADC Hypervisor
 Leveraging Radware s ADC-VX to Reduce Data Center TCO An ROI Paper on Radware s Industry-First ADC Hypervisor Table of Contents Executive Summary... 3 Virtual Data Center Trends... 3 Reducing Data Center
Leveraging Radware s ADC-VX to Reduce Data Center TCO An ROI Paper on Radware s Industry-First ADC Hypervisor Table of Contents Executive Summary... 3 Virtual Data Center Trends... 3 Reducing Data Center
White Paper Solarflare High-Performance Computing (HPC) Applications
 Solarflare High-Performance Computing (HPC) Applications 10G Ethernet: Now Ready for Low-Latency HPC Applications Solarflare extends the benefits of its low-latency, high-bandwidth 10GbE server adapters
Solarflare High-Performance Computing (HPC) Applications 10G Ethernet: Now Ready for Low-Latency HPC Applications Solarflare extends the benefits of its low-latency, high-bandwidth 10GbE server adapters
Official distributor for The Netherlands Exertis GO Connect T. +31 (0) 78 88 00 700 F. +31 (0) 78 88 00 777 E. kemp@exertisgoconnect.
 Official distributor for The Netherlands Exertis GO Connect T. +31 (0) 78 88 00 700 F. +31 (0) 78 88 00 777 E. kemp@exertisgoconnect.nl For the latest information, specifications pricing and tailored service
Official distributor for The Netherlands Exertis GO Connect T. +31 (0) 78 88 00 700 F. +31 (0) 78 88 00 777 E. kemp@exertisgoconnect.nl For the latest information, specifications pricing and tailored service
VMware vshield App Design Guide TECHNICAL WHITE PAPER
 ware vshield App Design Guide TECHNICAL WHITE PAPER ware vshield App Design Guide Overview ware vshield App is one of the security products in the ware vshield family that provides protection to applications
ware vshield App Design Guide TECHNICAL WHITE PAPER ware vshield App Design Guide Overview ware vshield App is one of the security products in the ware vshield family that provides protection to applications
Market Application Delivery Networking. Products ADC, WAN Optimization, Secure Access
 Company snapshot Founded 2000 Headquarters Milpitas, CA, USA Employees 400+ Market Application Delivery Networking Products ADC, WAN Optimization, Secure Access Segments Enterprise, Service Provider, Public
Company snapshot Founded 2000 Headquarters Milpitas, CA, USA Employees 400+ Market Application Delivery Networking Products ADC, WAN Optimization, Secure Access Segments Enterprise, Service Provider, Public
Business Case for NFV/SDN Programmable Networks
 Business Case for NFV/SDN Programmable Networks Executive Summary Traditional network designs are failing to meet service providers business requirements. The designs lead to complex hardware stacks, over-provisioning
Business Case for NFV/SDN Programmable Networks Executive Summary Traditional network designs are failing to meet service providers business requirements. The designs lead to complex hardware stacks, over-provisioning
NetLeverage UK ThinPoint Solution Overview Version 2 Copyright 2012 NetLeverage UK
 NetLeverage UK ThinPoint Solution Overview Version 2 Copyright 2012 NetLeverage UK 1. ThinPoint solution to Access your Own PC You require your business users to access their own PC in the office remotely
NetLeverage UK ThinPoint Solution Overview Version 2 Copyright 2012 NetLeverage UK 1. ThinPoint solution to Access your Own PC You require your business users to access their own PC in the office remotely
SummitStack in the Data Center
 SummitStack in the Data Center Abstract: This white paper describes the challenges in the virtualized server environment and the solution Extreme Networks offers a highly virtualized, centrally manageable
SummitStack in the Data Center Abstract: This white paper describes the challenges in the virtualized server environment and the solution Extreme Networks offers a highly virtualized, centrally manageable
COMLINK Cloud Technical Specification Guide DEDICATED SERVER
 COMLINK Cloud Technical Specification Guide DEDICATED SERVER Updated June 13, 2014 *Subject to Change* Table of Contents 1 Overview of Cloud Dedicated Server 2 Why Choose Dedicated Servers? 2-4 Features
COMLINK Cloud Technical Specification Guide DEDICATED SERVER Updated June 13, 2014 *Subject to Change* Table of Contents 1 Overview of Cloud Dedicated Server 2 Why Choose Dedicated Servers? 2-4 Features
