Who s Endian?
|
|
|
- Madeleine Jennings
- 10 years ago
- Views:
Transcription
1 Who s Endian? Endian was founded in 2003 at Appiano, Italy, by a team of experienced network specialists and Linux enthusiasts. Endian s goal and path of development are immediately clear: creating sophisticated UTM solutions, totally based on open source technology. Just one year later the community version is available: to date we count more than downloads from the kick off. Dating back to the first release of the Enterprise version, more than 4000 companies, based on 50 countries, have chosen Endian UTM. Endian US - Houston Endian Germany - Munich Endian - Bolzano e Milano Endian - Turkey Endian Japan - Tokyo 1
2 Endian - Securing everything 2
3 Endian Solutions We meet all your needs Network Security Hotspot Management Secure Remote Connectivity Industrial IoT Security 3
4 Protection for any environment Which is your platform? Hardware Appliances Software Appliances Virtual Appliances 4
5 Endian UTM Software Appliances Run Endian on your own Hardware Run on your own X86 Hardware Offered in bundles of users Upgrade hardware resources as necessary Lower initial investment 5
6 Endian UTM Virtual Appliance Secure and Protect Cloud & Virtual Infrastructure Run in VMware, Xen, KVM hypervisors Allocate resources as necessary No user or VPN license restrictions 6
7 Endian UTM Hardware Appliances Appliances for Any Size Network Mini 25 Mercury 50 Mercury 100 Macro 250/500 Macro 1000/2500 7
8 Endian UTM Mini 25 The new generation of UTM hardware appliances 4 Ethernet ports 2 GB RAM 8 GB CFast Flash Memory Desktop Appliance WIFI Upgrade Available Performance Mini 25 Firewall Throughput 1.2 Gbit/s VPN Throughput (IPsec & SSL) 120 Mbit/s IPS Throughput 100 Mbit/s Antivirus Throughput (Proxy) Web Security Throughput 120 Mbit/s 180 Mbit/s Concurrent Sessions 300,000 8
9 Endian UTM Mercury 50 The new generation of UTM hardware appliances 5 Ethernet ports 2 GB RAM 320 GB Hard disk Desktop Appliance Performance Mercury 50 Firewall Throughput 1.55 Gbit/s VPN Throughput (IPsec & SSL) 155 Mbit/s IPS Throughput 120 Mbit/s Antivirus Throughput (Proxy) Web Security Throughput 150 Mbit/s 250 Mbit/s Concurrent Sessions 300,000 9
10 Endian UTM Mercury 100 The new generation of UTM hardware appliances 6 Ethernet ports 4 GB RAM 2x320 GB Hard disk LAN-Bypass Rack 1U Performance Mercury 100 Firewall Throughput 2.5 Gbit/s VPN Throughput (IPsec & SSL) 220 Mbit/s IPS Throughput 160 Mbit/s Antivirus Throughput (Proxy) Web Security Throughput 250 Mbit/s 400 Mbit/s Concurrent Sessions 500,000 10
11 Endian UTM Macro 250 and 500 The new generation of UTM hardware appliances 8 Ethernet ports 4 / 8 GB RAM 2x320 / 2x500 GB Hard disk LAN-Bypass Rack 1U Performance Macro 250 Macro 500 Firewall Throughput 5.1 Gbit/s 10 Gbit/s VPN Throughput 880 Mbit/s 1.4 Gbit/s (IPsec & SSL) IPS Throughput 590 Mbit/s 900 Mbit/s Antivirus Throughput 1.4 Gbit/s 2.5 Gbit/s (Proxy) Web Security 2.7 Gbit/s 4.8 Gbit/s Throughput Concurrent Sessions 1,500,000 2,500,000 11
12 Endian UTM Macro 1000 and 2500 The new generation of UTM hardware appliances 10/18 Ethernet ports 16/32 GB RAM 2x500/2x1000 GB Hard disk LAN-Bypass Rack 2U 2x 10Gigabit SFP+ (optional) Performance Macro 1000 Macro 2500 Firewall Throughput 20 Gbit/s 30 Gbit/s VPN Throughput (IPsec & SSL) 2.5 Gbit/s 4 Gbit/s IPS Throughput 1.8 Gbit/s 2.5 Gbit/s Antivirus Throughput (Proxy) Web Security Throughput 3.5 Gbit/s 5 Gbit/s 10 Gbit/s 15 Gbit/s Concurrent Sessions 2,500,000 5,000,000 12
13 Endian 4i Industrial IoT Security We meet all your needs 13
14 Endian 4i Edge 112 Powerful desktop industrial solution Highlights: 0 to +60 C operating temperature Simple, secure VPN access Power input 24V DC Recommended for: Infrastructure Healthcare Communications Performance 4i Edge 112 Firewall Throughput VPN Throughput IPS Throughput 120 Mbps 30 Mbps 20 Mbps 14
15 Endian 4i Edge 313 The DIN rail industrial solution Highlights: 0 to +60 C operating temperature Simple, secure VPN access 3G Module (optional) Power input 24V DC Recommended for: Machine building Manufacturing Infrastructure Performance 4i Edge 313 Firewall Throughput VPN Throughput IPS Throughput 120 Mbps 30 Mbps 20 Mbps 15
16 Endian 4i Edge 515 The most robust industrial solution Highlights: -20 to +70 C operating temperature Simple, secure VPN access 3G Module (optional) Dual power input 24V DC Recommended for: Machine building Manufacturing Infrastructure Healthcare Communications Performance 4i Edge 515 Firewall Throughput VPN Throughput IPS Throughput 120 Mbps 30 Mbps 20 Mbps 16
17 Endian UTM Key Features 17
18 Firewall Overview 18
19 Firewall Overview Diagram 19
20 Network Architecture 20
21 Multiple WAN & Policy Routing 21
22 IP Static Routing 22
23 DNS Proxy Diagram 23
24 IPS - Firewall Integration 24
25 IPS Firewall - Example 25
26 Application Control 26
27 Intelligent Application Firewall 27
28 VPN Firewall 28
29 IPsec & SSL VPN Architecture 29
30 Web Proxy Architecture 30
31 Proxy Architecture 31
32 Hotspot Network Architecture 32
33 QoS Diagram 33
34 Added Support for: ios (iphone, ipad, and ipod Touch ) and Android No Requirement to Install 3rd Party VPN Application -- Works Natively (OpenVPN, IPsec) with ios, Android, Windows 7 and Mac OS X Available on All Endian Appliances 34
35 Endian Hotspot - Hotspot Management WiFi and Bring Your Own Device 35
36 Endian Hotspot for tourist accomodations and public places Provide your customers and visitors with a simple and secure internet access Provide your visitors with secure wireless connection Ideal solution for hotels, airports, train stations, public squares, libraries Free or charged tickets: you can choose. By using SmartConnect you can directly send ID and password to the user Public Venues & Government Naval & Maritime Industry Hospitality Retail Education 36
37 Live Monitoring 37
38 Connection status 38
39 Backup / Restore 39
40 Switchboard Key Features The deployment of the solution Simply and securely connect your various users or groups (of users) to individual devices or device groups without any client side configuration. The client just installs the software and connects to the Switchboard and all their device access is available. Group your users and/or devices by job roles or device access levels to only allow the access required (and nothing more) 40
41 Switchboard Key Features Subnet Mapping IPs overlapping is no longer a problem: Endian Switchboard automatically remaps all your customers networks. 41
42 Switchboard Key Features USB Provisioning The provisioning is implemented through a simple USB key that spreads the chosen configuration settings to the Endian 4i appliances. 42
43 Switchboard Key Features Development Access (API) Thanks to API interface it is possible to integrate all the Switchboard functionalities on existent platforms (such as partners support portal). 43
44 Switchboard Key Features Applications With Endian 4i series it is possible to set up actions and group of actions for any device: via pre-configured hyperlinks one can launch applications to access the endpoints (PLCs, HMIs, Web Servers, etc.) behind the firewall. 44
45 Switchboard Key Features Interoperable In the event where existing endpoint devices are in place, you can use the Switchboard to manage any device that utilizes Open VPN (SSL) technology. This helps to reduce the cost of replacing edge devices and minimizes the impact of potential down-time of the network. 45
46 Endian Switchboard: Control your traffic with 2 tunnels send request establish manage 46
47 Endian Network Secure remote and mobile access Remote SSH Remote Web Endian Network Centralized package push Internet Local Web Local SSH Local package pull en-liveclient en-liveclient en-liveclient 47
48 Endian Maintenance Packages What s Included with Endian Maintenance Endian Network Endian Updates Endian Upgrades Endian Support (Central Management) (Protection Packages) (Newest Features) (Product Assistance) 48
49 Endian - Securing everything Endian UTM Online Demo Endian Hotspot Online Demo Endian Connect Switchboard Online Demo Endian 4i Online Demo Thank you! 49
Security with Passion www.endian.com
 Security with Passion www.endian.com Endian 4i Switchboard Securely Connect Users to SCADA Devices 2 Security with Passion www.endian.com Table of contents A 360 Solution to Secure Industrial Connectivity
Security with Passion www.endian.com Endian 4i Switchboard Securely Connect Users to SCADA Devices 2 Security with Passion www.endian.com Table of contents A 360 Solution to Secure Industrial Connectivity
SVN5800 Secure Access Gateway
 The development of networks allows enterprises to provide remote access to branch offices, partners, customers, mobile employees, and home offices so that they can access application and data resources,
The development of networks allows enterprises to provide remote access to branch offices, partners, customers, mobile employees, and home offices so that they can access application and data resources,
Remote Access Clients for Windows
 Remote Access Clients for Windows E80.60 Release Notes 3 December 2014 Classification: [Protected] 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation
Remote Access Clients for Windows E80.60 Release Notes 3 December 2014 Classification: [Protected] 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation
Proof of Concept Guide
 Proof of Concept Guide Version 4.0 Published: OCT-2013 Updated: 2005-2013 Propalms Ltd. All rights reserved. The information contained in this document represents the current view of Propalms Ltd. on the
Proof of Concept Guide Version 4.0 Published: OCT-2013 Updated: 2005-2013 Propalms Ltd. All rights reserved. The information contained in this document represents the current view of Propalms Ltd. on the
Microsoft Azure Configuration
 Microsoft Azure Configuration Azure Setup for VNS3 2015 copyright 2015 1 Table of Contents Introduction 3 Create Azure Private VLAN 10 Launch VNS3 Image from Azure Marketplace 15 VNS3 Configuration Document
Microsoft Azure Configuration Azure Setup for VNS3 2015 copyright 2015 1 Table of Contents Introduction 3 Create Azure Private VLAN 10 Launch VNS3 Image from Azure Marketplace 15 VNS3 Configuration Document
NetScaler VPX FAQ. Table of Contents
 NetScaler VPX FAQ Table of Contents Feature and Functionality Frequently Asked Questions... 2 Pricing and Packaging Frequently Asked Questions... 4 NetScaler VPX Express Frequently Asked Questions... 5
NetScaler VPX FAQ Table of Contents Feature and Functionality Frequently Asked Questions... 2 Pricing and Packaging Frequently Asked Questions... 4 NetScaler VPX Express Frequently Asked Questions... 5
OnApp Cloud. The complete platform for cloud service providers. 114 Cores. 286 Cores / 400 Cores
 OnApp Cloud The complete platform for cloud service providers 286 Cores / 400 Cores 114 Cores 218 10 86 20 The complete platform for cloud service providers OnApp software turns your datacenter into an
OnApp Cloud The complete platform for cloud service providers 286 Cores / 400 Cores 114 Cores 218 10 86 20 The complete platform for cloud service providers OnApp software turns your datacenter into an
Secure Communication Made Easy
 Secure Communication Made Easy Remote Access to Industrial Equipment Easy Setup Central Administration Firewall Friendly State-of-Art Security Fast Return On Investment PROGRAMMING CONTROL LOGGING INFRASTRUCTURE
Secure Communication Made Easy Remote Access to Industrial Equipment Easy Setup Central Administration Firewall Friendly State-of-Art Security Fast Return On Investment PROGRAMMING CONTROL LOGGING INFRASTRUCTURE
Industrial Firewalls Endpoint Security
 Industrial Firewalls Endpoint Security Is there a need for a new type of industrial firewall? Industries have a huge park of different management and control systems to monitor their production. These
Industrial Firewalls Endpoint Security Is there a need for a new type of industrial firewall? Industries have a huge park of different management and control systems to monitor their production. These
SILVER PEAK ACCELERATION WITH EMC VSPEX PRIVATE CLOUD WITH RECOVERPOINT FOR VMWARE VSPHERE
 VSPEX IMPLEMENTATION GUIDE SILVER PEAK ACCELERATION WITH EMC VSPEX PRIVATE CLOUD WITH RECOVERPOINT FOR VMWARE VSPHERE Silver Peak Abstract This Implementation Guide describes the deployment of Silver Peak
VSPEX IMPLEMENTATION GUIDE SILVER PEAK ACCELERATION WITH EMC VSPEX PRIVATE CLOUD WITH RECOVERPOINT FOR VMWARE VSPHERE Silver Peak Abstract This Implementation Guide describes the deployment of Silver Peak
Endian Unified Threat Management
 Endian Unified Threat Management Introduction/Demo to Endian UTM lmarzke Lee Marzke (4AERO.com) Infrastructure Consultant: Software Development organizations Specialize in SCM, Process, PM, Tools Just
Endian Unified Threat Management Introduction/Demo to Endian UTM lmarzke Lee Marzke (4AERO.com) Infrastructure Consultant: Software Development organizations Specialize in SCM, Process, PM, Tools Just
Endpoint Security VPN for Mac
 Security VPN for Mac E75 Release Notes 8 April 2012 Classification: [Protected] 2012 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by
Security VPN for Mac E75 Release Notes 8 April 2012 Classification: [Protected] 2012 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by
Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding
 Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding This chapter describes the configuration for the SSL VPN Tunnel Client and for Port Forwarding. When a remote user accesses the SSL VPN
Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding This chapter describes the configuration for the SSL VPN Tunnel Client and for Port Forwarding. When a remote user accesses the SSL VPN
Security with Passion www.endian.com. Complete Network Security - For Small Businesses & Branch Offices
 Security with Passion www.endian.com Endian UTM Mini series Complete Network Security - For Small Businesses & Branch s Quick & Easy Setup: Get your network protected in a matter of minutes. Rock Solid
Security with Passion www.endian.com Endian UTM Mini series Complete Network Security - For Small Businesses & Branch s Quick & Easy Setup: Get your network protected in a matter of minutes. Rock Solid
BLOOMBERG ANYWHERE FOR MOBILE CUSTOMERS
 BLOOMBERG ANYWHERE FOR MOBILE CUSTOMERS Software & Connectivity Requirements 11 March 2014 Version: 1.03 BLOOMBERG ANYWHERE users have access to their information on a variety of mobile platforms including
BLOOMBERG ANYWHERE FOR MOBILE CUSTOMERS Software & Connectivity Requirements 11 March 2014 Version: 1.03 BLOOMBERG ANYWHERE users have access to their information on a variety of mobile platforms including
Connecting an Android to a FortiGate with SSL VPN
 Connecting an Android to a FortiGate with SSL VPN This recipe describes how to provide a group of remote Android users with secure, encrypted access to the network using FortiClient and SSL VPN. You must
Connecting an Android to a FortiGate with SSL VPN This recipe describes how to provide a group of remote Android users with secure, encrypted access to the network using FortiClient and SSL VPN. You must
Interact Intranet Version 7. Technical Requirements. August 2014. 2014 Interact
 Interact Intranet Version 7 Technical Requirements August 2014 2014 Interact Definitions... 3 Licenses... 3 On-Premise... 3 Cloud... 3 Pulic Cloud... 3 Private Cloud... 3 Perpetual... 3 Self-Hosted...
Interact Intranet Version 7 Technical Requirements August 2014 2014 Interact Definitions... 3 Licenses... 3 On-Premise... 3 Cloud... 3 Pulic Cloud... 3 Private Cloud... 3 Perpetual... 3 Self-Hosted...
USING GENIE REMOTELY
 USING GENIE REMOTELY This document outlines the available options for using Genie in offsite logging mode (Genie single user) or remotely in real-time via a remote desktop (terminal services) connection.
USING GENIE REMOTELY This document outlines the available options for using Genie in offsite logging mode (Genie single user) or remotely in real-time via a remote desktop (terminal services) connection.
Deployment Guide. How to prepare your environment for an OnApp Cloud deployment.
 Deployment Guide How to prepare your environment for an OnApp Cloud deployment. Document version 1.07 Document release date 28 th November 2011 document revisions 1 Contents 1. Overview... 3 2. Network
Deployment Guide How to prepare your environment for an OnApp Cloud deployment. Document version 1.07 Document release date 28 th November 2011 document revisions 1 Contents 1. Overview... 3 2. Network
Mobile Configuration Profiles for ios Devices Technical Note
 Mobile Configuration Profiles for ios Devices Technical Note Mobile Configuration Profiles for ios Devices Technical Note December 10, 2013 04-502-197517-20131210 Copyright 2013 Fortinet, Inc. All rights
Mobile Configuration Profiles for ios Devices Technical Note Mobile Configuration Profiles for ios Devices Technical Note December 10, 2013 04-502-197517-20131210 Copyright 2013 Fortinet, Inc. All rights
Cisco Small Business ISA500 Series Integrated Security Appliances
 Q & A Cisco Small Business ISA500 Series Integrated Security Appliances Q. What is the Cisco Small Business ISA500 Series Integrated Security Appliance? A. The Cisco Small Business ISA500 Series Integrated
Q & A Cisco Small Business ISA500 Series Integrated Security Appliances Q. What is the Cisco Small Business ISA500 Series Integrated Security Appliance? A. The Cisco Small Business ISA500 Series Integrated
Sophos SG Series Appliances
 Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Aqua Connect Load Balancer User Manual (Mac)
 Aqua Connect Load Balancer User Manual (Mac) Table of Contents About Aqua Connect Load Balancer... 3 System Requirements... 4 Hardware... 4 Software... 4 Installing the Load Balancer... 5 Configuration...
Aqua Connect Load Balancer User Manual (Mac) Table of Contents About Aqua Connect Load Balancer... 3 System Requirements... 4 Hardware... 4 Software... 4 Installing the Load Balancer... 5 Configuration...
Acronis and Acronis Secure Zone are registered trademarks of Acronis International GmbH.
 1 Copyright Acronis International GmbH, 2002-2016 Copyright Statement Copyright Acronis International GmbH, 2002-2016. All rights reserved. Acronis and Acronis Secure Zone are registered trademarks of
1 Copyright Acronis International GmbH, 2002-2016 Copyright Statement Copyright Acronis International GmbH, 2002-2016. All rights reserved. Acronis and Acronis Secure Zone are registered trademarks of
Vyatta Network OS for Network Virtualization
 Complete Security and Compliance for Virtual Environments Vyatta takes the concept of virtualization beyond just applications and operating systems and allows enterprise IT to also virtualize network components
Complete Security and Compliance for Virtual Environments Vyatta takes the concept of virtualization beyond just applications and operating systems and allows enterprise IT to also virtualize network components
IN DETAIL. Smart & Dedicated Servers
 IN DETAIL Smart & Dedicated Servers Automate everything - including dedicated servers OnApp brings cloud hosting, dedicated hosting and hybrid hosting together in one platform. Through one control panel
IN DETAIL Smart & Dedicated Servers Automate everything - including dedicated servers OnApp brings cloud hosting, dedicated hosting and hybrid hosting together in one platform. Through one control panel
Price-to-Performance Comparison of Load Balancers
 Price-to-Performance Comparison of Load Balancers New York: 631-345-5292 Limerick: +353-61-260-101 Hannover: +49-511-367393-0 Singapore: +65-62222429 About KEMP KEMP Technologies provides a robust and
Price-to-Performance Comparison of Load Balancers New York: 631-345-5292 Limerick: +353-61-260-101 Hannover: +49-511-367393-0 Singapore: +65-62222429 About KEMP KEMP Technologies provides a robust and
Application-Centric WLAN. Rob Mellencamp
 Application-Centric WLAN Rob Mellencamp Agenda NX Integrated Services Platform Integrated Services Architecture Application Installation Example Application Monitoring Enterprise Mobility Architecture
Application-Centric WLAN Rob Mellencamp Agenda NX Integrated Services Platform Integrated Services Architecture Application Installation Example Application Monitoring Enterprise Mobility Architecture
TECHNICAL WHITEPAPER. Author: Tom Kistner, Chief Software Architect. Table of Contents
 TECHNICAL WHITEPAPER Author: Tom Kistner, Chief Software Architect Last update: 18. Dez 2014 Table of Contents Introduction... 2 Terminology... 2 Basic Concepts... 2 Appliances... 3 Hardware...3 Software...3
TECHNICAL WHITEPAPER Author: Tom Kistner, Chief Software Architect Last update: 18. Dez 2014 Table of Contents Introduction... 2 Terminology... 2 Basic Concepts... 2 Appliances... 3 Hardware...3 Software...3
msuite5 & mdesign Installation Prerequisites
 CommonTime Limited msuite5 & mdesign Installation Prerequisites Administration considerations prior to installing msuite5 and mdesign. 7/7/2011 Version 2.4 Overview... 1 msuite version... 1 SQL credentials...
CommonTime Limited msuite5 & mdesign Installation Prerequisites Administration considerations prior to installing msuite5 and mdesign. 7/7/2011 Version 2.4 Overview... 1 msuite version... 1 SQL credentials...
CenturyLink Cloud Configuration
 CenturyLink Cloud Configuration CenturyLink Setup for VNS3:vpn, VNS3:net and VNS3:turret 2015 copyright 2015 1 Table of Contents Introduction 3 CenturyLink Cloud Deployment Setup 9 VNS3 Configuration Document
CenturyLink Cloud Configuration CenturyLink Setup for VNS3:vpn, VNS3:net and VNS3:turret 2015 copyright 2015 1 Table of Contents Introduction 3 CenturyLink Cloud Deployment Setup 9 VNS3 Configuration Document
AC1200 Multi-Function Concurrent Dual-Band Gigabit Wi-Fi Router
 The extraordinary growth in the number of wireless devices found in modern homes has seen a huge increase in demand for wireless speed, range and bandwidth. This continuing trend away from wired connections
The extraordinary growth in the number of wireless devices found in modern homes has seen a huge increase in demand for wireless speed, range and bandwidth. This continuing trend away from wired connections
Sophos Roadshow. Complete Security Vision
 Sophos Roadshow Complete Security Vision Reconized leader Over 25 years of experience Data protection experts Global company with local presence 100 million users trust Sophos Reputation for highest quality
Sophos Roadshow Complete Security Vision Reconized leader Over 25 years of experience Data protection experts Global company with local presence 100 million users trust Sophos Reputation for highest quality
OVERVIEW. The complete IaaS platform for service providers
 OVERVIEW The complete IaaS platform for service providers The complete IaaS platform for service providers With OnApp you can sell more services, automate more of your infrastructure and extend your reach
OVERVIEW The complete IaaS platform for service providers The complete IaaS platform for service providers With OnApp you can sell more services, automate more of your infrastructure and extend your reach
Overview and Deployment Guide. Sophos UTM on AWS
 Overview and Deployment Guide Sophos UTM on AWS Overview and Deployment Guide Document date: November 2014 1 Sophos UTM and AWS Contents 1 Amazon Web Services... 4 1.1 AMI (Amazon Machine Image)... 4 1.2
Overview and Deployment Guide Sophos UTM on AWS Overview and Deployment Guide Document date: November 2014 1 Sophos UTM and AWS Contents 1 Amazon Web Services... 4 1.1 AMI (Amazon Machine Image)... 4 1.2
Game changing Technology für Ihre Kunden. Thomas Bürgis System Engineering Manager CEE
 Game changing Technology für Ihre Kunden Thomas Bürgis System Engineering Manager CEE Threats have evolved traditional firewalls & IPS have not Protection centered around ports & protocols Expensive to
Game changing Technology für Ihre Kunden Thomas Bürgis System Engineering Manager CEE Threats have evolved traditional firewalls & IPS have not Protection centered around ports & protocols Expensive to
How To Set Up A Vns3 Controller On An Ipad Or Ipad (For Ahem) On A Network With A Vlan (For An Ipa) On An Uniden Vns 3 Instance On A Vn3 Instance On
 ElasticHosts Configuration ElasticHosts Setup for VNS3 2015 copyright 2015 1 Table of Contents Introduction 3 ElasticHosts Deployment Setup 9 VNS3 Configuration Document Links 20 copyright 2015 2 Requirements
ElasticHosts Configuration ElasticHosts Setup for VNS3 2015 copyright 2015 1 Table of Contents Introduction 3 ElasticHosts Deployment Setup 9 VNS3 Configuration Document Links 20 copyright 2015 2 Requirements
Introduction to Mobile Access Gateway Installation
 Introduction to Mobile Access Gateway Installation This document describes the installation process for the Mobile Access Gateway (MAG), which is an enterprise integration component that provides a secure
Introduction to Mobile Access Gateway Installation This document describes the installation process for the Mobile Access Gateway (MAG), which is an enterprise integration component that provides a secure
Custom Integration Solutions
 Welcome to this introduction into a true business class network solution for you and your clients This solution has been designed, by integrators, for integrators. We look forward to producing an ever
Welcome to this introduction into a true business class network solution for you and your clients This solution has been designed, by integrators, for integrators. We look forward to producing an ever
Overview. The OnApp Cloud Platform. Dashboard APPLIANCES. Used Total Used Total. Virtual Servers. Blueprint Servers. Load Balancers.
 Overview The OnApp Cloud Platform Dashboard APPLIANCES Virtual Servers Blueprint Servers Load Balancers Bare Metal Smart Servers Hypervisors Assets Integrated Storage COMPONENTS DNS Templates Blueprints
Overview The OnApp Cloud Platform Dashboard APPLIANCES Virtual Servers Blueprint Servers Load Balancers Bare Metal Smart Servers Hypervisors Assets Integrated Storage COMPONENTS DNS Templates Blueprints
Edgewater Routers User Guide
 Edgewater Routers User Guide For use with 8x8 Service Version 1.0, March 2011 Table of Contents EdgeMarc 200AE1-10 Router Overview...3 EdgeMarc 4550-15 Router Overview...4 Basic Setup of the 200AE1 and
Edgewater Routers User Guide For use with 8x8 Service Version 1.0, March 2011 Table of Contents EdgeMarc 200AE1-10 Router Overview...3 EdgeMarc 4550-15 Router Overview...4 Basic Setup of the 200AE1 and
Licenses are not interchangeable between the ISRs and NGX Series ISRs.
 Q&A Cisco IOS SSL VPN Q. What is Cisco IOS SSL VPN or SSL VPN? A. Secure Sockets Layer (SSL)-based VPN is an emerging technology that provides remote-access connectivity from almost any Internet-enabled
Q&A Cisco IOS SSL VPN Q. What is Cisco IOS SSL VPN or SSL VPN? A. Secure Sockets Layer (SSL)-based VPN is an emerging technology that provides remote-access connectivity from almost any Internet-enabled
Application Notes. How to Configure UTM with Apple OSX and ios Devices for IPsec VPN
 How to Configure UTM with Apple OSX and ios Devices for IPsec VPN T a b l e o f C o n t e n t s Concepts...3 Components...3 Configuration Steps...3 UTM VPN Configuration...3 Mode Config Record...3 IKE
How to Configure UTM with Apple OSX and ios Devices for IPsec VPN T a b l e o f C o n t e n t s Concepts...3 Components...3 Configuration Steps...3 UTM VPN Configuration...3 Mode Config Record...3 IKE
A Guide to New Features in Propalms OneGate 4.0
 A Guide to New Features in Propalms OneGate 4.0 Propalms Ltd. Published April 2013 Overview This document covers the new features, enhancements and changes introduced in Propalms OneGate 4.0 Server (previously
A Guide to New Features in Propalms OneGate 4.0 Propalms Ltd. Published April 2013 Overview This document covers the new features, enhancements and changes introduced in Propalms OneGate 4.0 Server (previously
Evaluating the Cisco ASA Adaptive Security Appliance VPN Subsystem Architecture
 Deploying Cisco ASA VPN Solutions Volume 1 Course Introduction Learner Skills and Knowledge Course Goal and Course Flow Additional Cisco Glossary of Terms Your Training Curriculum Evaluation of the Cisco
Deploying Cisco ASA VPN Solutions Volume 1 Course Introduction Learner Skills and Knowledge Course Goal and Course Flow Additional Cisco Glossary of Terms Your Training Curriculum Evaluation of the Cisco
Remote Desktop Gateway. Accessing a Campus Managed Device (Windows Only) from home.
 Remote Desktop Gateway Accessing a Campus Managed Device (Windows Only) from home. Contents Introduction... 2 Quick Reference... 2 Gateway Setup - Windows Desktop... 3 Gateway Setup Windows App... 4 Gateway
Remote Desktop Gateway Accessing a Campus Managed Device (Windows Only) from home. Contents Introduction... 2 Quick Reference... 2 Gateway Setup - Windows Desktop... 3 Gateway Setup Windows App... 4 Gateway
WATCHGUARD FIREBOX SOHO 6TC AND SOHO 6
 WATCHGUARD FIREBOX SOHO 6TC AND SOHO 6 FIREWALL AND VPN APPLIANCES FOR SMALL BUSINESSES AND BRANCH OFFICES Today, complete Internet security goes beyond a firewall. Firebox SOHO 6tc and SOHO 6 are dedicated
WATCHGUARD FIREBOX SOHO 6TC AND SOHO 6 FIREWALL AND VPN APPLIANCES FOR SMALL BUSINESSES AND BRANCH OFFICES Today, complete Internet security goes beyond a firewall. Firebox SOHO 6tc and SOHO 6 are dedicated
Level 1 Technical Firewall Traversal & Security. Level 1 Technical. Firewall Traversal & Security. V3 Page 1 of 15
 Level 1 Technical Firewall Traversal & Security V3 Page 1 of 15 Contents 1 - Glossary... 3 2 - Features... 4 RealPresence Access Director... 4 SIP Management... 5 H.323 Management... 5 Media Relay... 5
Level 1 Technical Firewall Traversal & Security V3 Page 1 of 15 Contents 1 - Glossary... 3 2 - Features... 4 RealPresence Access Director... 4 SIP Management... 5 H.323 Management... 5 Media Relay... 5
Avaya IP Office 9.1. Set Up Guide for The IP Office Anywhere Demo Platform
 Avaya IP Office 9.1 Set Up Guide for The IP Office Anywhere Demo Platform Date: February 2015 Version: 2.0 Subject: Avaya IP Office 9.1 Anywhere Demonstration Set Up Guide Regional Availability: Global
Avaya IP Office 9.1 Set Up Guide for The IP Office Anywhere Demo Platform Date: February 2015 Version: 2.0 Subject: Avaya IP Office 9.1 Anywhere Demonstration Set Up Guide Regional Availability: Global
Systems Manager Cloud Based Mobile Device Management
 Datasheet Systems Manager Systems Manager Cloud Based Mobile Device Management Overview Meraki Systems Manager provides cloud-based over-the-air centralized management, diagnostics, and monitoring of the
Datasheet Systems Manager Systems Manager Cloud Based Mobile Device Management Overview Meraki Systems Manager provides cloud-based over-the-air centralized management, diagnostics, and monitoring of the
Rally Installation Guide
 Rally Installation Guide Rally On-Premises release 2015.1 [email protected] www.rallydev.com Version 2015.1 Table of Contents Overview... 3 Server requirements... 3 Browser requirements... 3 Access
Rally Installation Guide Rally On-Premises release 2015.1 [email protected] www.rallydev.com Version 2015.1 Table of Contents Overview... 3 Server requirements... 3 Browser requirements... 3 Access
Professional Integrated SSL-VPN Appliance for Small and Medium-sized businesses
 Professional Integrated Appliance for Small and Medium-sized businesses Benefits Clientless Secure Remote Access Seamless Integration behind the Existing Firewall Infrastructure UTM Security Integration
Professional Integrated Appliance for Small and Medium-sized businesses Benefits Clientless Secure Remote Access Seamless Integration behind the Existing Firewall Infrastructure UTM Security Integration
Aerohive Networks Inc. Free Bonjour Gateway FAQ
 Aerohive Networks Inc. Free Bonjour Gateway FAQ 1. About the Product... 1 2. Installation... 2 3. Management... 3 4. Troubleshooting... 4 1. About the Product What is the Aerohive s Free Bonjour Gateway?
Aerohive Networks Inc. Free Bonjour Gateway FAQ 1. About the Product... 1 2. Installation... 2 3. Management... 3 4. Troubleshooting... 4 1. About the Product What is the Aerohive s Free Bonjour Gateway?
Endpoint Security VPN for Mac
 Security VPN for Mac E80.41 Release Notes 16 January 2013 Classification: [Protected] 2013 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
Security VPN for Mac E80.41 Release Notes 16 January 2013 Classification: [Protected] 2013 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
Product Factsheet MANAGED SECURITY SERVICES - FIREWALLS - FACT SHEET
 Product Factsheet MANAGED SECURITY SERVICES - FIREWALLS - FACT SHEET ELITE S NEXT GENERATION MANAGED SECURITY SERVICES Security risks to business information systems are expanding at a rapid rate; often,
Product Factsheet MANAGED SECURITY SERVICES - FIREWALLS - FACT SHEET ELITE S NEXT GENERATION MANAGED SECURITY SERVICES Security risks to business information systems are expanding at a rapid rate; often,
Request for Proposal MDM0031012338. Offeror s Questions for RFP for Virtual Private Network Solution (VPN)
 Request for Proposal MDM0031012338 Offeror s Questions for RFP for Virtual Private Network Solution (VPN) 1. How much throughput must the VPN support long-term? Answer: 10 GB firewall, 4 GB 3DES/AES VPN
Request for Proposal MDM0031012338 Offeror s Questions for RFP for Virtual Private Network Solution (VPN) 1. How much throughput must the VPN support long-term? Answer: 10 GB firewall, 4 GB 3DES/AES VPN
Edgewater Routers User Guide
 Edgewater Routers User Guide For use with 8x8 Service May 2012 Table of Contents EdgeMarc 250w Router Overview.... 3 EdgeMarc 4550-15 Router Overview... 4 Basic Setup of the 250w, 200AE1 and 4550... 5
Edgewater Routers User Guide For use with 8x8 Service May 2012 Table of Contents EdgeMarc 250w Router Overview.... 3 EdgeMarc 4550-15 Router Overview... 4 Basic Setup of the 250w, 200AE1 and 4550... 5
A Nemaris Company. Formal Privacy & Security Assessment For Surgimap version 2.2.6 and higher
 A Nemaris Company Formal Privacy & Security Assessment For Surgimap version 2.2.6 and higher 306 East 15 th Street Suite 1R, New York, New York 10003 Application Name Surgimap Vendor Nemaris Inc. Version
A Nemaris Company Formal Privacy & Security Assessment For Surgimap version 2.2.6 and higher 306 East 15 th Street Suite 1R, New York, New York 10003 Application Name Surgimap Vendor Nemaris Inc. Version
How To Understand The Architecture Of An Ulteo Virtual Desktop Server Farm
 ULTEO OPEN VIRTUAL DESKTOP V4.0.2 ARCHITECTURE OVERVIEW Contents 1 Introduction 2 2 Servers Roles 3 2.1 Session Manager................................. 3 2.2 Application Server................................
ULTEO OPEN VIRTUAL DESKTOP V4.0.2 ARCHITECTURE OVERVIEW Contents 1 Introduction 2 2 Servers Roles 3 2.1 Session Manager................................. 3 2.2 Application Server................................
About the VM-Series Firewall
 About the VM-Series Firewall Palo Alto Networks VM-Series Deployment Guide PAN-OS 6.1 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 http://www.paloaltonetworks.com/contact/contact/
About the VM-Series Firewall Palo Alto Networks VM-Series Deployment Guide PAN-OS 6.1 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 http://www.paloaltonetworks.com/contact/contact/
BENEFITS. Capex reduction with bundling of all required features in a single appliance. Promote your brand with customized Guest Login pages.
 www.prontonetworks.com Powered By Pronto s Unifi OneBox Its a complete end-to-end platform that enables the monetization of a Wi-Fi Access Point network, while minimizing ongoing management and operation
www.prontonetworks.com Powered By Pronto s Unifi OneBox Its a complete end-to-end platform that enables the monetization of a Wi-Fi Access Point network, while minimizing ongoing management and operation
Deploying iphone and ipad Virtual Private Networks
 Deploying iphone and ipad Virtual Private Networks Secure access to private corporate networks is available on iphone and ipad using established industry-standard virtual private network (VPN) protocols.
Deploying iphone and ipad Virtual Private Networks Secure access to private corporate networks is available on iphone and ipad using established industry-standard virtual private network (VPN) protocols.
Check Point taps the power of virtualization to simplify security for private clouds
 Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private
Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private
Customer Service Description Next Generation Network Firewall
 Customer Service Description Next Generation Network Firewall Interoute, Walbrook Building, 195 Marsh Wall, London, E14 9SG, UK Tel: +800 4683 7681 Email: [email protected] Interoute Communications Limited
Customer Service Description Next Generation Network Firewall Interoute, Walbrook Building, 195 Marsh Wall, London, E14 9SG, UK Tel: +800 4683 7681 Email: [email protected] Interoute Communications Limited
NERC CIP Whitepaper How Endian Solutions Can Help With Compliance
 NERC CIP Whitepaper How Endian Solutions Can Help With Compliance Introduction Critical infrastructure is the backbone of any nations fundamental economic and societal well being. Like any business, in
NERC CIP Whitepaper How Endian Solutions Can Help With Compliance Introduction Critical infrastructure is the backbone of any nations fundamental economic and societal well being. Like any business, in
Appliance Comparison Chart
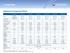 Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Preparation Guide. How to prepare your environment for an OnApp Cloud v3.0 (beta) deployment.
 Preparation Guide v3.0 BETA How to prepare your environment for an OnApp Cloud v3.0 (beta) deployment. Document version 1.0 Document release date 25 th September 2012 document revisions 1 Contents 1. Overview...
Preparation Guide v3.0 BETA How to prepare your environment for an OnApp Cloud v3.0 (beta) deployment. Document version 1.0 Document release date 25 th September 2012 document revisions 1 Contents 1. Overview...
Web Drive Limited TERMS AND CONDITIONS FOR THE SUPPLY OF SERVER HOSTING
 Web Drive Limited TERMS AND CONDITIONS FOR THE SUPPLY OF SERVER HOSTING Application of Terms Agreement to these terms requires agreement to Web Drive s Standard Terms & Conditions located online at the
Web Drive Limited TERMS AND CONDITIONS FOR THE SUPPLY OF SERVER HOSTING Application of Terms Agreement to these terms requires agreement to Web Drive s Standard Terms & Conditions located online at the
MANAGE SECURE ACCESS TO APPLICATIONS BASED ON USER IDENTITY. EMEA Webinar July 2013
 MANAGE SECURE ACCESS TO APPLICATIONS BASED ON USER IDENTITY EMEA Webinar July 2013 Protecting the Enterprise Full Footprint Mobile user Application access management & Application security Enterprise headquarters
MANAGE SECURE ACCESS TO APPLICATIONS BASED ON USER IDENTITY EMEA Webinar July 2013 Protecting the Enterprise Full Footprint Mobile user Application access management & Application security Enterprise headquarters
NetLeverage UK ThinPoint Solution Overview Version 2 Copyright 2012 NetLeverage UK
 NetLeverage UK ThinPoint Solution Overview Version 2 Copyright 2012 NetLeverage UK 1. ThinPoint solution to Access your Own PC You require your business users to access their own PC in the office remotely
NetLeverage UK ThinPoint Solution Overview Version 2 Copyright 2012 NetLeverage UK 1. ThinPoint solution to Access your Own PC You require your business users to access their own PC in the office remotely
How to set up the HotSpot module with SmartConnect. Panda GateDefender 5.0
 How to set up the HotSpot module with SmartConnect Panda GateDefender 5.0 Content Introduction... 3 Minimum requirements to enable the hotspot module... 4 Hotspot settings... 6 General settings....6 Configuring
How to set up the HotSpot module with SmartConnect Panda GateDefender 5.0 Content Introduction... 3 Minimum requirements to enable the hotspot module... 4 Hotspot settings... 6 General settings....6 Configuring
NAS 242 Using AiMaster on Your Mobile Devices
 NAS 242 Using AiMaster on Your Mobile Devices Learn to use AiMaster on your mobile devices A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you should be able to: 1. Use AiMaster
NAS 242 Using AiMaster on Your Mobile Devices Learn to use AiMaster on your mobile devices A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you should be able to: 1. Use AiMaster
Sophos SG Series Appliances
 Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
ACME Enterprises IT Infrastructure Assessment
 Prepared for ACME Enterprises March 25, 2014 Table of Contents Executive Summary...2 Introduction...2 Background...2 Scope of IT Assessment...2 Findings...2 Detailed Findings for Key Areas Reviewed...3
Prepared for ACME Enterprises March 25, 2014 Table of Contents Executive Summary...2 Introduction...2 Background...2 Scope of IT Assessment...2 Findings...2 Detailed Findings for Key Areas Reviewed...3
Dell Wyse Cloud Connect discussion card
 Dell Wyse Cloud Connect discussion card What is Cloud Connect? Cloud Connect is a portable enterprise IT-controlled HDMI/MHL (mobile high-definition link) cloud device that allows people to convert a capable
Dell Wyse Cloud Connect discussion card What is Cloud Connect? Cloud Connect is a portable enterprise IT-controlled HDMI/MHL (mobile high-definition link) cloud device that allows people to convert a capable
SonicWALL Mobile Connect. Mobile Connect for OS X 3.0. User Guide
 SonicWALL Mobile Connect Mobile Connect for OS X 3.0 User Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION
SonicWALL Mobile Connect Mobile Connect for OS X 3.0 User Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION
Fundamentals of Windows Server 2008 Network and Applications Infrastructure
 Fundamentals of Windows Server 2008 Network and Applications Infrastructure MOC6420 About this Course This five-day instructor-led course introduces students to network and applications infrastructure
Fundamentals of Windows Server 2008 Network and Applications Infrastructure MOC6420 About this Course This five-day instructor-led course introduces students to network and applications infrastructure
VIA COLLAGE Deployment Guide
 VIA COLLAGE Deployment Guide www.true-collaboration.com Infinite Ways to Collaborate CONTENTS Introduction... 3 User Experience... 3 Pre-Deployment Planning... 3 Connectivity... 3 Network Addressing...
VIA COLLAGE Deployment Guide www.true-collaboration.com Infinite Ways to Collaborate CONTENTS Introduction... 3 User Experience... 3 Pre-Deployment Planning... 3 Connectivity... 3 Network Addressing...
Boas Betzler. Planet. Globally Distributed IaaS Platform Examples AWS and SoftLayer. November 9, 2015. 20014 IBM Corporation
 Boas Betzler Cloud IBM Distinguished Computing Engineer for a Smarter Planet Globally Distributed IaaS Platform Examples AWS and SoftLayer November 9, 2015 20014 IBM Corporation Building Data Centers The
Boas Betzler Cloud IBM Distinguished Computing Engineer for a Smarter Planet Globally Distributed IaaS Platform Examples AWS and SoftLayer November 9, 2015 20014 IBM Corporation Building Data Centers The
EdgeRouter Lite 3-Port Router. Datasheet. Model: ERLite-3. Sophisticated Routing Features. Advanced Security, Monitoring, and Management
 EdgeRouter Lite 3-Port Router Model: ERLite-3 Sophisticated Routing Features Advanced Security, Monitoring, and Management High-Performance Gigabit Ports Advanced 3-Port Router Introducing the EdgeRouter
EdgeRouter Lite 3-Port Router Model: ERLite-3 Sophisticated Routing Features Advanced Security, Monitoring, and Management High-Performance Gigabit Ports Advanced 3-Port Router Introducing the EdgeRouter
Next Generation Network Firewall
 Next Generation Network Firewall Overview Next Generation Network Firewalls are an important part of protecting any organisation from Internet traffic. Next Generation Firewalls provide a central point
Next Generation Network Firewall Overview Next Generation Network Firewalls are an important part of protecting any organisation from Internet traffic. Next Generation Firewalls provide a central point
Cloud Security Best Practices
 Cloud Security Best Practices Cohesive Networks - your applications secured VNS3 security and connectivity solutions protect cloud-based applications from exploitation by hackers, criminal gangs, and foreign
Cloud Security Best Practices Cohesive Networks - your applications secured VNS3 security and connectivity solutions protect cloud-based applications from exploitation by hackers, criminal gangs, and foreign
Chapter 11 Cloud Application Development
 Chapter 11 Cloud Application Development Contents Motivation. Connecting clients to instances through firewalls. Chapter 10 2 Motivation Some of the questions of interest to application developers: How
Chapter 11 Cloud Application Development Contents Motivation. Connecting clients to instances through firewalls. Chapter 10 2 Motivation Some of the questions of interest to application developers: How
Uniport appliances For corporate networks and operators
 Uniport appliances For corporate networks and operators Uniport EN series Datasheet... 2 Products and services... 3 Uniport AN series Datasheet... 4 Products and services... 5 Uniport ON series Datasheet...
Uniport appliances For corporate networks and operators Uniport EN series Datasheet... 2 Products and services... 3 Uniport AN series Datasheet... 4 Products and services... 5 Uniport ON series Datasheet...
SECURE ACCESS TO THE VIRTUAL DATA CENTER
 SOLUTION BRIEF SECURE ACCESS TO THE VIRTUAL DATA CENTER Ensure that Remote Users Can Securely Access the Virtual Data Center s Virtual Desktops and Other Resources Challenge VDI is driving a unique need
SOLUTION BRIEF SECURE ACCESS TO THE VIRTUAL DATA CENTER Ensure that Remote Users Can Securely Access the Virtual Data Center s Virtual Desktops and Other Resources Challenge VDI is driving a unique need
ReadyNAS Replicate. Software Reference Manual. 350 East Plumeria Drive San Jose, CA 95134 USA. November 2010 202-10727-01 v1.0
 ReadyNAS Replicate Software Reference Manual 350 East Plumeria Drive San Jose, CA 95134 USA November 2010 202-10727-01 v1.0 2010 NETGEAR, Inc. All rights reserved. No part of this publication may be reproduced,
ReadyNAS Replicate Software Reference Manual 350 East Plumeria Drive San Jose, CA 95134 USA November 2010 202-10727-01 v1.0 2010 NETGEAR, Inc. All rights reserved. No part of this publication may be reproduced,
The Hybrid Enterprise. Enhance network performance and build your hybrid WAN
 The Hybrid Enterprise Enhance network performance and build your hybrid WAN ABOUT ELFIQ NETWORKS With today s growing Internet demands, Elfiq Networks enhances network performance and business continuity
The Hybrid Enterprise Enhance network performance and build your hybrid WAN ABOUT ELFIQ NETWORKS With today s growing Internet demands, Elfiq Networks enhances network performance and business continuity
Remote Unix Lab Environment (RULE)
 Remote Unix Lab Environment (RULE) Kris Mitchell [email protected] Introducing RULE RULE provides an alternative way to teach Unix! Increase student exposure to Unix! Do it cost effectively http://caia.swin.edu.au
Remote Unix Lab Environment (RULE) Kris Mitchell [email protected] Introducing RULE RULE provides an alternative way to teach Unix! Increase student exposure to Unix! Do it cost effectively http://caia.swin.edu.au
Gigabit Multi-Homing VPN Security Router
 As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is a ideal to help the SMBs increase the broadband
As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is a ideal to help the SMBs increase the broadband
Wowza Media Systems provides all the pieces in the streaming puzzle, from capture to delivery, taking the complexity out of streaming live events.
 Deciding what event you want to stream live that s the easy part. Figuring out how to stream it? That s a different question, one with as many answers as there are options. Cameras? Encoders? Origin and
Deciding what event you want to stream live that s the easy part. Figuring out how to stream it? That s a different question, one with as many answers as there are options. Cameras? Encoders? Origin and
ipad Classroom Installation & Deployment Important information
 ipad Classroom Installation & Deployment Important information Our aim is to carry out your installation as quickly and efficiently as possible whilst utilising Apple s recommended procedures for the deployment
ipad Classroom Installation & Deployment Important information Our aim is to carry out your installation as quickly and efficiently as possible whilst utilising Apple s recommended procedures for the deployment
It is recommended that you use a clean installation of Lion client before upgrading to Lion Server.
 Wazza s Lion Server QuickStart 1. Installing Lion Server About this Document This document is the first in a series of documents describing the process of installing and configuring a Mac OS X 10.7 Server
Wazza s Lion Server QuickStart 1. Installing Lion Server About this Document This document is the first in a series of documents describing the process of installing and configuring a Mac OS X 10.7 Server
VM-Series Firewall Deployment Tech Note PAN-OS 5.0
 VM-Series Firewall Deployment Tech Note PAN-OS 5.0 Revision A 2012, Palo Alto Networks, Inc. www.paloaltonetworks.com Contents Overview... 3 Supported Topologies... 3 Prerequisites... 4 Licensing... 5
VM-Series Firewall Deployment Tech Note PAN-OS 5.0 Revision A 2012, Palo Alto Networks, Inc. www.paloaltonetworks.com Contents Overview... 3 Supported Topologies... 3 Prerequisites... 4 Licensing... 5
PROMAPP TECHNICAL INFORMATION
 Promapp Software Architecture Promapp is designed in accordance with Microsoft best practices, developed with the Microsoft.net framework and uses a Microsoft SQL database. The software architecture is
Promapp Software Architecture Promapp is designed in accordance with Microsoft best practices, developed with the Microsoft.net framework and uses a Microsoft SQL database. The software architecture is
YubiRADIUS Deployment Guide for corporate remote access. How to Guide
 YubiRADIUS Deployment Guide for corporate remote access How to Guide May 15, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company s flagship
YubiRADIUS Deployment Guide for corporate remote access How to Guide May 15, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company s flagship
Corente Cloud Services Exchange
 Corente Cloud Services Exchange Oracle s Corente Cloud Services Exchange (Corente CSX) is a cloud-based software-defined networking (SDN) solution that enables distributed enterprises to deliver trusted
Corente Cloud Services Exchange Oracle s Corente Cloud Services Exchange (Corente CSX) is a cloud-based software-defined networking (SDN) solution that enables distributed enterprises to deliver trusted
Appliance Comparison Chart
 202 Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark) Security 4 4 223 374 623 Firewall (Gbps).4.4 2.2 3.4 5.8 Firewall and IPS (Mbps) 50 50
202 Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark) Security 4 4 223 374 623 Firewall (Gbps).4.4 2.2 3.4 5.8 Firewall and IPS (Mbps) 50 50
AC 1200. Wireless Dual Band ADSL2+ Modem Router. Highlights
 AC 1200 Wireless Dual Band ADSL2+ Modem Router Highlights 1200Mbps Wireless Speed 300Mbps on 2.4GHz + 867Mbps on 5GHz Broad Coverage Two external antennas provide maximum omni-directional wireless coverage
AC 1200 Wireless Dual Band ADSL2+ Modem Router Highlights 1200Mbps Wireless Speed 300Mbps on 2.4GHz + 867Mbps on 5GHz Broad Coverage Two external antennas provide maximum omni-directional wireless coverage
