Wireshark Certified Network Analyst Program
|
|
|
- Virgil McCormick
- 10 years ago
- Views:
Transcription
1 Wireshark Certified Network Analyst Program Laura Chappell, Wireshark University
2 Wireshark Certified Network Analyst Designed to confirm individual competencies in using Wireshark to locate the cause of network problems (poor performance or security related) and confirm your knowledge of TCP/IP network communications in general. Wireshark Certified Network Analyst Exam was DoD 8570 approved by the US Army Download Wireshark for free from
3 Contents Maintenance Wireshark Certified Network Analyst Online Portal Registering for the Exam Sample Exam Questions Q & A
4 The
5 The Pre (Study/Prepare) Maintenance Recertification
6 The Pre (Study/Prepare) Maintenance Recertification Wireshark University Authorized Training Partner Courses Study Guide Exam Prep Guide On the Job Study Practice Exam
7 The Pre (Study/Prepare) Maintenance Recertification Wireshark University Authorized Training Partner Courses Study Guide Exam Prep Guide On the Job Study Practice Exam ISBN10: ISBN13: Paperback: 800 pages Book URL: I have recommended all my junior analysts read WNA. They will learn a ton about Wireshark, and will also Be able to follow Laura's explanations of many common network protocols. We may even pursue the certification tied to the book. Great work Laura! Richard Bejtlich, TaoSecurity.com
8 The Pre (Study/Prepare) Maintenance Recertification Wireshark University Authorized Training Partner Courses Study Guide Exam Prep Guide 10 digit ISBN: digit ISBN: Paperback: 202 pages (includes CD) Book URL: Released: August 2010 Sold through Amazon.com On the Job Study Practice Exam
9 The Pre (Study/Prepare) Maintenance Recertification Wireshark University Authorized Training Partner Courses Study Guide Exam Prep Guide On the Job Study Practice Exam
10 The Pre (Study/Prepare) Maintenance Recertification Wireshark University Authorized Training Partner Courses Study Guide Exam Prep Guide On the Job Study Practice Exam
11 The Pre (Study/Prepare) Maintenance Recertification Register and take the Exam at 80 countries and almost 500 testing centers worldwide No testing center? Learn about the Online Proctored option at
12 Your Welcome Kit Your signed Certificate Your ID Number Your Portal login information Logo access and usage details CPE requirement details
13 The Pre (Study/Prepare) Maintenance Recertification 20 Continuing Professional Education (CPE) Credits yearly for 3 years Free training through your Online Portal Wireshark Functionality Network Communications Network Troubleshooting Network Security
14 The Pre (Study/Prepare) Maintenance Recertification Register and take the current Exam Latest version of Wireshark Latest Exam objectives Updated technologies Updated methods
15 This is NOT Your Typical Program Our goal is to build a global team of Wireshark Certified Network Analysts capable of tackling the biggest network challenges. We want you to succeed and benefit from achieving the Wireshark Certified Network Analyst designation. The Online Portal provides you with free updated/advanced training after your certification to enhance your network analysis skills
16 Maintenance
17 Maintenance Pre (Study/Prepare) Maintenance Recertification 20 Continuing Professional Education (CPE) Credits yearly for 3 years Free training through your Online Portal Wireshark Functionality Network Communications Network Troubleshooting Network Security
18 60 Minutes of Activity = 1 CPE Read/Write Technical Books, RFCs, Articles, etc. Listen/Watch Podcasts, webinars, online training events Attend Conferences, seminars, member meetings Work Submit reports based on your on the job experience
19 Manual CPE Submission /cpe Only required for CPEs gained outside your Wireshark Analyst Online Portal
20 Your Online Portal
21 Maintenance Pre (Study/Prepare) Maintenance Recertification 20 Continuing Professional Education (CPE) Credits yearly for 3 years Free training through your Online Portal Wireshark Functionality Network Communications Network Troubleshooting Network Security
22 The Wireshark Certified Network Analyst Pre (Study/Prepare) Maintenance Recertification WCNA Online Portal Activities worth +20 CPE credits per year (online courses/study) Up to date techniques and dissections of network traffic You can contribute using work related experience for credit No need to submit CPEs for this CPE training automatically credited to your Wireshark Certified Network Analyst Account
23 The Online Portal WCNA Online Portal Take Wireshark Certified Network Analyst CPE training and print your transcript to meet other CPE requirements* * Provided training meets requirements by third party certification programs.
24 Wireshark Certified Network Analyst CPE Training and Other Cert Programs CISSP CPE Requirements
25 Register for the Exam
26 Register for a Free Test Taker Account at
27 Choose your desired Exam and click Buy Now. You will not be asked for payment until you have completed scheduling your Exam. You must complete payment information before accessing Practice Exams.
28 The Exam
29 What s On the Exam? Four Focus Areas Wireshark Functionality Network Communications Network Troubleshooting Network Forensics/Security Pass/Fail indication upon completion of Exam
30 Thirty Three Specific Sections Section Detail is located in the Info Pack at /certification.
31 Sample Multiple Choice Question What type of TCP scan would this filter display? (tcp.flags.urg==1) && (tcp.flags.push==1) && (tcp.flags.fin==1) A. IP scan B. Xmas scan C. stealth scan D. half connect scan
32 Sample Multiple Choice Question (with image) Which statement about the Preferences setting shown above is correct? A. Wireshark may generate DNS PTR queries to resolve host names. B. Wireshark may generate port queries to ietf.org to resolve transport names. C. Wireshark may generate OUI queries to ieee.org to resolve MAC addresses. D. Wireshark may generate mdns queries to resolve 500 host names simultaneously.
33 Sample Multiple Choice Question (with image) Which statement about the DNS packet shown is correct? A. This is an inverse DNS query. B. This is a DNS response packet. C. This DNS packet indicates that a domain name could not be resolved. D. This is a request to resolve the IP address
34 Sample True/False Question A Window Update packet contains no data, but indicates that the sender's TCP window size field value has decreased. True False
35 What if I Have Questions? Visit us online /certification Contact us [email protected] Phone: Fax:
36 Q&A Time Thank you for joining me today Laura Chappell, Wireshark University
Get Certified on the World s Foremost Network Protocol Analyzer
 Wireshark is downloaded over 500,000 per month on average Wireshark University Get Certified on the World s Foremost Network Protocol Analyzer Exam Version 102.1 (updated 07/02/2012) Welcome to Wireshark
Wireshark is downloaded over 500,000 per month on average Wireshark University Get Certified on the World s Foremost Network Protocol Analyzer Exam Version 102.1 (updated 07/02/2012) Welcome to Wireshark
Wireshark Certified Network Analyst Official Exam Prep Guide Second Edition
 Wireshark Certified Network Analyst Official Exam Prep Guide Second Edition Exam WCNA-102.x 2 nd Edition (Version 2.0b) Laura Chappell Founder, Chappell University Founder, Wireshark University This book
Wireshark Certified Network Analyst Official Exam Prep Guide Second Edition Exam WCNA-102.x 2 nd Edition (Version 2.0b) Laura Chappell Founder, Chappell University Founder, Wireshark University This book
6. INTRODUCTION TO THE LABORATORY: SOFTWARE TOOLS
 6. INTRODUCTION TO THE LABORATORY: SOFTWARE TOOLS 6.1. Wireshark network sniffer Wireshark (originally called Ethereal) is a freeware network sniffer. A sniffer investigates and analyzes network traffic.
6. INTRODUCTION TO THE LABORATORY: SOFTWARE TOOLS 6.1. Wireshark network sniffer Wireshark (originally called Ethereal) is a freeware network sniffer. A sniffer investigates and analyzes network traffic.
Tcpdump Lab: Wired Network Traffic Sniffing
 Cyber Forensics Laboratory 1 Tcpdump Lab: Wired Network Traffic Sniffing Copyright c 2012 Hui Li and Xinwen Fu, University of Massachusetts Lowell Permission is granted to copy, distribute and/or modify
Cyber Forensics Laboratory 1 Tcpdump Lab: Wired Network Traffic Sniffing Copyright c 2012 Hui Li and Xinwen Fu, University of Massachusetts Lowell Permission is granted to copy, distribute and/or modify
Are Second Generation Firewalls Good for Industrial Control Systems?
 Are Second Generation Firewalls Good for Industrial Control Systems? Bernie Pella, CISSP Schneider Electric Cyber Security Services [email protected] Firewall Overview Firewalls provide
Are Second Generation Firewalls Good for Industrial Control Systems? Bernie Pella, CISSP Schneider Electric Cyber Security Services [email protected] Firewall Overview Firewalls provide
1 You will need the following items to get started:
 QUICKSTART GUIDE 1 Getting Started You will need the following items to get started: A desktop or laptop computer Two ethernet cables (one ethernet cable is shipped with the _ Blocker, and you must provide
QUICKSTART GUIDE 1 Getting Started You will need the following items to get started: A desktop or laptop computer Two ethernet cables (one ethernet cable is shipped with the _ Blocker, and you must provide
Websense Web Security Gateway: What to do when a Web site does not load as expected
 Websense Web Security Gateway: What to do when a Web site does not load as expected Websense Support Webinar November 2011 web security data security email security Support Webinars 2009 Websense, Inc.
Websense Web Security Gateway: What to do when a Web site does not load as expected Websense Support Webinar November 2011 web security data security email security Support Webinars 2009 Websense, Inc.
EINTE LAB EXERCISES LAB EXERCISE #5 - SIP PROTOCOL
 EINTE LAB EXERCISES LAB EXERCISE #5 - SIP PROTOCOL PREPARATIONS STUDYING SIP PROTOCOL The aim of this exercise is to study the basic aspects of the SIP protocol. Before executing the exercise you should
EINTE LAB EXERCISES LAB EXERCISE #5 - SIP PROTOCOL PREPARATIONS STUDYING SIP PROTOCOL The aim of this exercise is to study the basic aspects of the SIP protocol. Before executing the exercise you should
How To - Configure Virtual Host using FQDN How To Configure Virtual Host using FQDN
 How To - Configure Virtual Host using FQDN How To Configure Virtual Host using FQDN Applicable Version: 10.6.2 onwards Overview Virtual host implementation is based on the Destination NAT concept. Virtual
How To - Configure Virtual Host using FQDN How To Configure Virtual Host using FQDN Applicable Version: 10.6.2 onwards Overview Virtual host implementation is based on the Destination NAT concept. Virtual
Course Title: Penetration Testing: Security Analysis
 Course Title: Penetration Testing: Security Analysis Page 1 of 9 Course Description: The Security Analyst Series from EC-Council Press is comprised of five books covering a broad base of topics in advanced
Course Title: Penetration Testing: Security Analysis Page 1 of 9 Course Description: The Security Analyst Series from EC-Council Press is comprised of five books covering a broad base of topics in advanced
What communication protocols are used to discover Tesira servers on a network?
 Understanding device discovery methods in Tesira OBJECTIVES In this application note, basic networking concepts will be summarized to better understand how Tesira servers are discovered over networks.
Understanding device discovery methods in Tesira OBJECTIVES In this application note, basic networking concepts will be summarized to better understand how Tesira servers are discovered over networks.
TCP Packet Tracing Part 1
 TCP Packet Tracing Part 1 Robert L Boretti Jr ([email protected]) Marvin Knight ([email protected]) Advisory Software Engineers 24 May 2011 Agenda Main Focus - TCP Packet Tracing What is TCP - general description
TCP Packet Tracing Part 1 Robert L Boretti Jr ([email protected]) Marvin Knight ([email protected]) Advisory Software Engineers 24 May 2011 Agenda Main Focus - TCP Packet Tracing What is TCP - general description
Network Security. Network Packet Analysis
 Network Security Network Packet Analysis Module 3 Keith A. Watson, CISSP, CISA IA Research Engineer, CERIAS [email protected] 1 Network Packet Analysis Definition: Examining network packets to determine
Network Security Network Packet Analysis Module 3 Keith A. Watson, CISSP, CISA IA Research Engineer, CERIAS [email protected] 1 Network Packet Analysis Definition: Examining network packets to determine
Tenable for CyberArk
 HOW-TO GUIDE Tenable for CyberArk Introduction This document describes how to deploy Tenable SecurityCenter and Nessus for integration with CyberArk Enterprise Password Vault. Please email any comments
HOW-TO GUIDE Tenable for CyberArk Introduction This document describes how to deploy Tenable SecurityCenter and Nessus for integration with CyberArk Enterprise Password Vault. Please email any comments
Lab Exercise SSL/TLS. Objective. Requirements. Step 1: Capture a Trace
 Lab Exercise SSL/TLS Objective To observe SSL/TLS (Secure Sockets Layer / Transport Layer Security) in action. SSL/TLS is used to secure TCP connections, and it is widely used as part of the secure web:
Lab Exercise SSL/TLS Objective To observe SSL/TLS (Secure Sockets Layer / Transport Layer Security) in action. SSL/TLS is used to secure TCP connections, and it is widely used as part of the secure web:
F-SECURE MESSAGING SECURITY GATEWAY
 F-SECURE MESSAGING SECURITY GATEWAY DEFAULT SETUP GUIDE This guide describes how to set up and configure the F-Secure Messaging Security Gateway appliance in a basic e-mail server environment. AN EXAMPLE
F-SECURE MESSAGING SECURITY GATEWAY DEFAULT SETUP GUIDE This guide describes how to set up and configure the F-Secure Messaging Security Gateway appliance in a basic e-mail server environment. AN EXAMPLE
ecopy ShareScan v4.3 Pre-Installation Checklist
 ecopy ShareScan v4.3 Pre-Installation Checklist This document is used to gather data about your environment in order to ensure a smooth product implementation. The Network Communication section describes
ecopy ShareScan v4.3 Pre-Installation Checklist This document is used to gather data about your environment in order to ensure a smooth product implementation. The Network Communication section describes
Application-Centric Analysis Helps Maximize the Value of Wireshark
 Application-Centric Analysis Helps Maximize the Value of Wireshark The cost of freeware Protocol analysis has long been viewed as the last line of defense when it comes to resolving nagging network and
Application-Centric Analysis Helps Maximize the Value of Wireshark The cost of freeware Protocol analysis has long been viewed as the last line of defense when it comes to resolving nagging network and
USER GUIDE. Ethernet Configuration Guide (Lantronix) P/N: 2900-300321 Rev 6
 KRAMER ELECTRONICS LTD. USER GUIDE Ethernet Configuration Guide (Lantronix) P/N: 2900-300321 Rev 6 Contents 1 Connecting to the Kramer Device via the Ethernet Port 1 1.1 Connecting the Ethernet Port Directly
KRAMER ELECTRONICS LTD. USER GUIDE Ethernet Configuration Guide (Lantronix) P/N: 2900-300321 Rev 6 Contents 1 Connecting to the Kramer Device via the Ethernet Port 1 1.1 Connecting the Ethernet Port Directly
Lab 8.3.2 Conducting a Network Capture with Wireshark
 Lab 8.3.2 Conducting a Network Capture with Wireshark Objectives Perform a network traffic capture with Wireshark to become familiar with the Wireshark interface and environment. Analyze traffic to a web
Lab 8.3.2 Conducting a Network Capture with Wireshark Objectives Perform a network traffic capture with Wireshark to become familiar with the Wireshark interface and environment. Analyze traffic to a web
Customer Tips. Basic E-mail Configuration and Troubleshooting. for the user. Overview. Basic Configuration. Xerox Multifunction Devices.
 Xerox Multifunction Devices Customer Tips November 24, 2003 This document applies to these Xerox products: x WC Pro 32/40 Color x WC Pro 65/75/90 x WC Pro 35/45/55 WC M35/M45/M55 x DC 555/545/535 x DC
Xerox Multifunction Devices Customer Tips November 24, 2003 This document applies to these Xerox products: x WC Pro 32/40 Color x WC Pro 65/75/90 x WC Pro 35/45/55 WC M35/M45/M55 x DC 555/545/535 x DC
H0/H2/H4 -ECOM100 DHCP & HTML Configuration. H0/H2/H4--ECOM100 DHCP Disabling DHCP and Assigning a Static IP Address Using HTML Configuration
 H0/H2/H4 -ECOM100 DHCP & HTML 6 H0/H2/H4--ECOM100 DHCP Disabling DHCP and Assigning a Static IP Address Using HTML 6-2 H0/H2/H4 -ECOM100 DHCP DHCP Issues The H0/H2/H4--ECOM100 is configured at the factory
H0/H2/H4 -ECOM100 DHCP & HTML 6 H0/H2/H4--ECOM100 DHCP Disabling DHCP and Assigning a Static IP Address Using HTML 6-2 H0/H2/H4 -ECOM100 DHCP DHCP Issues The H0/H2/H4--ECOM100 is configured at the factory
How To Configure A Kiwi Ip Address On A Gbk (Networking) To Be A Static Ip Address (Network) On A Ip Address From A Ipad (Netware) On An Ipad Or Ipad 2 (
 UAG715 Support Note Revision 1.00 August, 2012 Written by CSO Scenario 1 - Trunk Interface (Dual WAN) Application Scenario The Internet has become an integral part of our lives; therefore, a smooth Internet
UAG715 Support Note Revision 1.00 August, 2012 Written by CSO Scenario 1 - Trunk Interface (Dual WAN) Application Scenario The Internet has become an integral part of our lives; therefore, a smooth Internet
Lab 9.1.1 Organizing CCENT Objectives by OSI Layer
 Lab 9.1.1 Organizing CCENT Objectives by OSI Layer Objectives Organize the CCENT objectives by which layer or layers they address. Background / Preparation In this lab, you associate the objectives of
Lab 9.1.1 Organizing CCENT Objectives by OSI Layer Objectives Organize the CCENT objectives by which layer or layers they address. Background / Preparation In this lab, you associate the objectives of
How To Install A New Database On A 2008 R2 System With A New Version Of Aql Server 2008 R 2 On A Windows Xp Server 2008 (Windows) R2 (Windows Xp) (Windows 8) (Powerpoint) (Mysql
 Microsoft SQL Server Express 2008 R2 Install on Windows Server 2008 r2 for HoleBASE SI The following guide covers setting up a SQL server Express 2008 R2 system and adding a new database and user for HoleBASE
Microsoft SQL Server Express 2008 R2 Install on Windows Server 2008 r2 for HoleBASE SI The following guide covers setting up a SQL server Express 2008 R2 system and adding a new database and user for HoleBASE
Introduction to Wireshark Network Analysis
 Introduction to Wireshark Network Analysis Page 2 of 24 Table of Contents INTRODUCTION 4 Overview 4 CAPTURING LIVE DATA 5 Preface 6 Capture Interfaces 6 Capture Options 6 Performing the Capture 8 ANALYZING
Introduction to Wireshark Network Analysis Page 2 of 24 Table of Contents INTRODUCTION 4 Overview 4 CAPTURING LIVE DATA 5 Preface 6 Capture Interfaces 6 Capture Options 6 Performing the Capture 8 ANALYZING
Scan Report Executive Summary. Part 2. Component Compliance Summary IP Address : 69.43.165.11
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: rsync.net ASV Company: Comodo CA Limited 06-02-2015 Scan expiration date: 08-31-2015 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: rsync.net ASV Company: Comodo CA Limited 06-02-2015 Scan expiration date: 08-31-2015 Part 2. Component
WhatsUp Gold v16.3 Installation and Configuration Guide
 WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
How To Protect A Dns Authority Server From A Flood Attack
 the Availability Digest @availabilitydig Surviving DNS DDoS Attacks November 2013 DDoS attacks are on the rise. A DDoS attack launches a massive amount of traffic to a website to overwhelm it to the point
the Availability Digest @availabilitydig Surviving DNS DDoS Attacks November 2013 DDoS attacks are on the rise. A DDoS attack launches a massive amount of traffic to a website to overwhelm it to the point
DNS (Domain Name System) is the system & protocol that translates domain names to IP addresses.
 Lab Exercise DNS Objective DNS (Domain Name System) is the system & protocol that translates domain names to IP addresses. Step 1: Analyse the supplied DNS Trace Here we examine the supplied trace of a
Lab Exercise DNS Objective DNS (Domain Name System) is the system & protocol that translates domain names to IP addresses. Step 1: Analyse the supplied DNS Trace Here we examine the supplied trace of a
EKT 332/4 COMPUTER NETWORK
 UNIVERSITI MALAYSIA PERLIS SCHOOL OF COMPUTER & COMMUNICATIONS ENGINEERING EKT 332/4 COMPUTER NETWORK LABORATORY MODULE LAB 2 NETWORK PROTOCOL ANALYZER (SNIFFING AND IDENTIFY PROTOCOL USED IN LIVE NETWORK)
UNIVERSITI MALAYSIA PERLIS SCHOOL OF COMPUTER & COMMUNICATIONS ENGINEERING EKT 332/4 COMPUTER NETWORK LABORATORY MODULE LAB 2 NETWORK PROTOCOL ANALYZER (SNIFFING AND IDENTIFY PROTOCOL USED IN LIVE NETWORK)
Troubleshooting Tips and Tricks
 Troubleshooting Tips and Tricks for TCP/IP Networks June 16, 2011 Laura Chappell Founder Chappell University/Wireshark University [email protected] SHARKFEST 11 Stanford University June 13 16, 2011 The
Troubleshooting Tips and Tricks for TCP/IP Networks June 16, 2011 Laura Chappell Founder Chappell University/Wireshark University [email protected] SHARKFEST 11 Stanford University June 13 16, 2011 The
State Health Repository Tool (SHRT) Testing Instructions
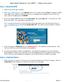 Step 1 - Access the SHRT State Health Repository Tool (SHRT) Testing Instructions 1. Close out any other open browsers. 2. Enter https://shrt.adp.com in the Address field of your browser and press Enter
Step 1 - Access the SHRT State Health Repository Tool (SHRT) Testing Instructions 1. Close out any other open browsers. 2. Enter https://shrt.adp.com in the Address field of your browser and press Enter
TheGreenBow IPsec VPN Client. Configuration Guide Cisco RV325 v1. Website: www.thegreenbow.com Contact: [email protected]
 TheGreenBow IPsec VPN Client Configuration Guide Cisco RV325 v1 Website: www.thegreenbow.com Contact: [email protected] Table of Contents 1 Introduction... 3 1.1 Goal of this document... 3 1.2 VPN
TheGreenBow IPsec VPN Client Configuration Guide Cisco RV325 v1 Website: www.thegreenbow.com Contact: [email protected] Table of Contents 1 Introduction... 3 1.1 Goal of this document... 3 1.2 VPN
SSL... 2 2.1. 3 2.2. 2.2.1. 2.2.2. SSL VPN
 1. Introduction... 2 2. Remote Access via SSL... 2 2.1. Configuration of the Astaro Security Gateway... 3 2.2. Configuration of the Remote Client...10 2.2.1. Astaro User Portal: Getting Software and Certificates...10
1. Introduction... 2 2. Remote Access via SSL... 2 2.1. Configuration of the Astaro Security Gateway... 3 2.2. Configuration of the Remote Client...10 2.2.1. Astaro User Portal: Getting Software and Certificates...10
Using WhatsUp IP Address Manager 1.0
 Using WhatsUp IP Address Manager 1.0 Contents Table of Contents Welcome to WhatsUp IP Address Manager Finding more information and updates... 1 Sending feedback... 2 Installing and Licensing IP Address
Using WhatsUp IP Address Manager 1.0 Contents Table of Contents Welcome to WhatsUp IP Address Manager Finding more information and updates... 1 Sending feedback... 2 Installing and Licensing IP Address
Network Forensics Network Traffic Analysis
 Copyright: The development of this document is funded by Higher Education of Academy. Permission is granted to copy, distribute and /or modify this document under a license compliant with the Creative
Copyright: The development of this document is funded by Higher Education of Academy. Permission is granted to copy, distribute and /or modify this document under a license compliant with the Creative
HRG Performance Series DVR DDNS Support Application Note (hrgddns)
 HRG Performance Series DVR DDNS Support Application Note (hrgddns) This document describes how to enable and configure Dynamic DNS (DDNS) functionality on the HRG Performance Series digital video recorder
HRG Performance Series DVR DDNS Support Application Note (hrgddns) This document describes how to enable and configure Dynamic DNS (DDNS) functionality on the HRG Performance Series digital video recorder
Lab Exercise SSL/TLS. Objective. Step 1: Open a Trace. Step 2: Inspect the Trace
 Lab Exercise SSL/TLS Objective To observe SSL/TLS (Secure Sockets Layer / Transport Layer Security) in action. SSL/TLS is used to secure TCP connections, and it is widely used as part of the secure web:
Lab Exercise SSL/TLS Objective To observe SSL/TLS (Secure Sockets Layer / Transport Layer Security) in action. SSL/TLS is used to secure TCP connections, and it is widely used as part of the secure web:
Print Audit Facilities Manager Technical Overview
 Print Audit Facilities Manager Technical Overview Print Audit Facilities Manager is a powerful, easy to use tool designed to remotely collect meter reads, automate supplies fulfilment and report service
Print Audit Facilities Manager Technical Overview Print Audit Facilities Manager is a powerful, easy to use tool designed to remotely collect meter reads, automate supplies fulfilment and report service
BT Business Broadband
 Small Office Network Guide BT Business Broadband with the BT Business Hub www.btbroadbandoffice.com Notice to users Updates and additions to software may require an additional charge. Subscriptions to
Small Office Network Guide BT Business Broadband with the BT Business Hub www.btbroadbandoffice.com Notice to users Updates and additions to software may require an additional charge. Subscriptions to
Network Security: Workshop. Dr. Anat Bremler-Barr. Assignment #2 Analyze dump files Solution Taken from www.chrissanders.org
 1.pcap - File download Network Security: Workshop Dr. Anat Bremler-Barr Assignment #2 Analyze dump files Solution Taken from www.chrissanders.org Downloading a file is a pretty basic function when described
1.pcap - File download Network Security: Workshop Dr. Anat Bremler-Barr Assignment #2 Analyze dump files Solution Taken from www.chrissanders.org Downloading a file is a pretty basic function when described
User Manual. Onsight Management Suite Version 5.1. Another Innovation by Librestream
 User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER
 NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.1.0.XXX Requirements and Implementation Guide (Rev 4-10209) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis Training Series
NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.1.0.XXX Requirements and Implementation Guide (Rev 4-10209) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis Training Series
SIMPLE NETWORK MANAGEMENT PROTOCOL (SNMP)
 1 SIMPLE NETWORK MANAGEMENT PROTOCOL (SNMP) Mohammad S. Hasan Agenda 2 Looking at Today What is a management protocol and why is it needed Addressing a variable within SNMP Differing versions Ad-hoc Network
1 SIMPLE NETWORK MANAGEMENT PROTOCOL (SNMP) Mohammad S. Hasan Agenda 2 Looking at Today What is a management protocol and why is it needed Addressing a variable within SNMP Differing versions Ad-hoc Network
Cisco SA 500 Series Security Appliance
 TheGreenBow IPSec VPN Client Configuration Guide Cisco SA 500 Series Security Appliance This guide applies to the following models: Cisco SA 520 Cisco SA 520W Cisco SA 540 WebSite: Contact: http://www.thegreenbow.de
TheGreenBow IPSec VPN Client Configuration Guide Cisco SA 500 Series Security Appliance This guide applies to the following models: Cisco SA 520 Cisco SA 520W Cisco SA 540 WebSite: Contact: http://www.thegreenbow.de
How To Set Up A Xerox Econcierge Powered By Xerx Account
 Xerox econcierge Account Setup Guide Xerox econcierge Account Setup Guide The free Xerox econcierge service provides the quickest, easiest way for your customers to order printer supplies for all their
Xerox econcierge Account Setup Guide Xerox econcierge Account Setup Guide The free Xerox econcierge service provides the quickest, easiest way for your customers to order printer supplies for all their
Installing and Setting up Microsoft DNS Server
 Training Installing and Setting up Microsoft DNS Server Introduction Versions Used Windows Server 2003 Setup Used i. Server Name = martini ii. Credentials: User = Administrator, Password = password iii.
Training Installing and Setting up Microsoft DNS Server Introduction Versions Used Windows Server 2003 Setup Used i. Server Name = martini ii. Credentials: User = Administrator, Password = password iii.
Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0
 Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0 Course length: 5 Days Course No. 688 - Five days - Instructor-led Introduction This course provides students with the knowledge and skills required
Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0 Course length: 5 Days Course No. 688 - Five days - Instructor-led Introduction This course provides students with the knowledge and skills required
Troubleshooting Procedures for Cisco TelePresence Video Communication Server
 Troubleshooting Procedures for Cisco TelePresence Video Communication Server Reference Guide Cisco VCS X7.2 D14889.01 September 2011 Contents Contents Introduction... 3 Alarms... 3 VCS logs... 4 Event
Troubleshooting Procedures for Cisco TelePresence Video Communication Server Reference Guide Cisco VCS X7.2 D14889.01 September 2011 Contents Contents Introduction... 3 Alarms... 3 VCS logs... 4 Event
Configuring SSL VPN on the Cisco ISA500 Security Appliance
 Application Note Configuring SSL VPN on the Cisco ISA500 Security Appliance This application note describes how to configure SSL VPN on the Cisco ISA500 security appliance. This document includes these
Application Note Configuring SSL VPN on the Cisco ISA500 Security Appliance This application note describes how to configure SSL VPN on the Cisco ISA500 security appliance. This document includes these
Configuring Network Address Translation (NAT)
 8 Configuring Network Address Translation (NAT) Contents Overview...................................................... 8-3 Translating Between an Inside and an Outside Network........... 8-3 Local and
8 Configuring Network Address Translation (NAT) Contents Overview...................................................... 8-3 Translating Between an Inside and an Outside Network........... 8-3 Local and
Wharf T&T Limited DDoS Mitigation Service Customer Portal User Guide
 Table of Content I. Note... 1 II. Login... 1 III. Real-time, Daily and Monthly Report... 3 Part A: Real-time Report... 3 Part 1: Traffic Details... 4 Part 2: Protocol Details... 5 Part B: Daily Report...
Table of Content I. Note... 1 II. Login... 1 III. Real-time, Daily and Monthly Report... 3 Part A: Real-time Report... 3 Part 1: Traffic Details... 4 Part 2: Protocol Details... 5 Part B: Daily Report...
F-Secure Messaging Security Gateway. Deployment Guide
 F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
Savvius Insight Initial Configuration
 The configuration utility on Savvius Insight lets you configure device, network, and time settings. Additionally, if you are forwarding your data from Savvius Insight to a Splunk server, You can configure
The configuration utility on Savvius Insight lets you configure device, network, and time settings. Additionally, if you are forwarding your data from Savvius Insight to a Splunk server, You can configure
Richard Bejtlich [email protected] www.taosecurity.com / taosecurity.blogspot.com BSDCan 14 May 04
 Network Security Monitoring with Sguil Richard Bejtlich [email protected] www.taosecurity.com / taosecurity.blogspot.com BSDCan 14 May 04 Overview Introduction to NSM The competition (ACID, etc.)
Network Security Monitoring with Sguil Richard Bejtlich [email protected] www.taosecurity.com / taosecurity.blogspot.com BSDCan 14 May 04 Overview Introduction to NSM The competition (ACID, etc.)
Configuring Vertafore WebFSC for Google Analytics
 Configuring Vertafore WebFSC This guide is produced only as a convenience for our customers. Vertafore does not sell, re-sell, market, or support Google products. Vertafore does not certify that Google
Configuring Vertafore WebFSC This guide is produced only as a convenience for our customers. Vertafore does not sell, re-sell, market, or support Google products. Vertafore does not certify that Google
Chapter 1 Configuring Basic Connectivity
 Chapter 1 Configuring Basic Connectivity This chapter describes the settings for your Internet connection and your wireless local area network (LAN) connection. When you perform the initial configuration
Chapter 1 Configuring Basic Connectivity This chapter describes the settings for your Internet connection and your wireless local area network (LAN) connection. When you perform the initial configuration
Astaro Security Gateway V8. Remote Access via SSL Configuring ASG and Client
 Astaro Security Gateway V8 Remote Access via SSL Configuring ASG and Client 1. Introduction This guide contains complementary information on the Administration Guide and the Online Help. If you are not
Astaro Security Gateway V8 Remote Access via SSL Configuring ASG and Client 1. Introduction This guide contains complementary information on the Administration Guide and the Online Help. If you are not
ENABLING RPC OVER HTTPS CONNECTIONS TO M-FILES SERVER
 M-FILES CORPORATION ENABLING RPC OVER HTTPS CONNECTIONS TO M-FILES SERVER VERSION 2.3 DECEMBER 18, 2015 Page 1 of 15 CONTENTS 1. Version history... 3 2. Overview... 3 2.1. System Requirements... 3 3. Network
M-FILES CORPORATION ENABLING RPC OVER HTTPS CONNECTIONS TO M-FILES SERVER VERSION 2.3 DECEMBER 18, 2015 Page 1 of 15 CONTENTS 1. Version history... 3 2. Overview... 3 2.1. System Requirements... 3 3. Network
Configuring Windows Server Clusters
 Configuring Windows Server Clusters In Enterprise network, group of servers are often used to provide a common set of services. For example, Different physical computers can be used to answer request directed
Configuring Windows Server Clusters In Enterprise network, group of servers are often used to provide a common set of services. For example, Different physical computers can be used to answer request directed
IP Filtering for Patton RAS Products
 RAS Filtering: Applications and Functionality Security PLUS Service Differentiation Did you know you can use IP filtering to boost your revenues? Patton s Remote Access Server (RAS) provides IP Filtering
RAS Filtering: Applications and Functionality Security PLUS Service Differentiation Did you know you can use IP filtering to boost your revenues? Patton s Remote Access Server (RAS) provides IP Filtering
Qualys PC/SCAP Auditor
 Qualys PC/SCAP Auditor Getting Started Guide August 3, 2015 COPYRIGHT 2011-2015 BY QUALYS, INC. ALL RIGHTS RESERVED. QUALYS AND THE QUALYS LOGO ARE REGISTERED TRADEMARKS OF QUALYS, INC. ALL OTHER TRADEMARKS
Qualys PC/SCAP Auditor Getting Started Guide August 3, 2015 COPYRIGHT 2011-2015 BY QUALYS, INC. ALL RIGHTS RESERVED. QUALYS AND THE QUALYS LOGO ARE REGISTERED TRADEMARKS OF QUALYS, INC. ALL OTHER TRADEMARKS
Implementing, Managing, and Maintaining a Microsoft Windows Server 2003 Network Infrastructure: Network Services (5 days)
 Implementing, Managing, and Maintaining a Microsoft Windows Server 2003 Network Infrastructure: Network Services (5 days) Course 2277: Five days; Instructor-led Introduction This five-day, instructor-led
Implementing, Managing, and Maintaining a Microsoft Windows Server 2003 Network Infrastructure: Network Services (5 days) Course 2277: Five days; Instructor-led Introduction This five-day, instructor-led
QUICK START GUIDE. Cisco S170 Web Security Appliance. Web Security Appliance
 1 0 0 0 1 1 QUICK START GUIDE Web Security Appliance Web Security Appliance Cisco S170 303417 Cisco S170 Web Security Appliance 1 Welcome 2 Before You Begin 3 Document Network Settings 4 Plan the Installation
1 0 0 0 1 1 QUICK START GUIDE Web Security Appliance Web Security Appliance Cisco S170 303417 Cisco S170 Web Security Appliance 1 Welcome 2 Before You Begin 3 Document Network Settings 4 Plan the Installation
Transport and Network Layer
 Transport and Network Layer 1 Introduction Responsible for moving messages from end-to-end in a network Closely tied together TCP/IP: most commonly used protocol o Used in Internet o Compatible with a
Transport and Network Layer 1 Introduction Responsible for moving messages from end-to-end in a network Closely tied together TCP/IP: most commonly used protocol o Used in Internet o Compatible with a
Controlling Risk, Conserving Bandwidth, and Monitoring Productivity with Websense Web Security and Websense Content Gateway
 Controlling Risk, Conserving Bandwidth, and Monitoring Productivity with Websense Web Security and Websense Content Gateway Websense Support Webinar January 2010 web security data security email security
Controlling Risk, Conserving Bandwidth, and Monitoring Productivity with Websense Web Security and Websense Content Gateway Websense Support Webinar January 2010 web security data security email security
Port Scanning and Vulnerability Assessment. ECE4893 Internetwork Security Georgia Institute of Technology
 Port Scanning and Vulnerability Assessment ECE4893 Internetwork Security Georgia Institute of Technology Agenda Reconnaissance Scanning Network Mapping OS detection Vulnerability assessment Reconnaissance
Port Scanning and Vulnerability Assessment ECE4893 Internetwork Security Georgia Institute of Technology Agenda Reconnaissance Scanning Network Mapping OS detection Vulnerability assessment Reconnaissance
Firewall Defaults, Public Server Rule, and Secondary WAN IP Address
 Firewall Defaults, Public Server Rule, and Secondary WAN IP Address This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSafe Wireless-N
Firewall Defaults, Public Server Rule, and Secondary WAN IP Address This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSafe Wireless-N
M2M Series Routers. Port Forwarding / DMZ Setup
 Introduction Port forwarding enables programs or devices running on your LAN to communicate with the internet as if they were directly connected. Many internet services and applications use designated
Introduction Port forwarding enables programs or devices running on your LAN to communicate with the internet as if they were directly connected. Many internet services and applications use designated
SIP Trunking Quick Reference Document
 SIP Trunking Quick Reference Document Publication Information SAMSUNG TELECOMMUNICATIONS AMERICA reserves the right without prior notice to revise information in this publication for any reason. SAMSUNG
SIP Trunking Quick Reference Document Publication Information SAMSUNG TELECOMMUNICATIONS AMERICA reserves the right without prior notice to revise information in this publication for any reason. SAMSUNG
WatchGuard XCS Exam Study Guide
 WatchGuard XCS Exam Study Guide The WatchGuard XCS Exam tests your knowledge of how to configure and manage a WatchGuard XCS device. This exam is appropriate for network administrators who have experience
WatchGuard XCS Exam Study Guide The WatchGuard XCS Exam tests your knowledge of how to configure and manage a WatchGuard XCS device. This exam is appropriate for network administrators who have experience
Macintosh Clients and Windows Print Queues
 Macintosh Clients and Windows Print Queues OS X Maverick, Lion Mountain, Leopard, Tiger, and Panther Pre-Configuration Requirements Ensure Macintosh machines have a valid Host A and PTR records in your
Macintosh Clients and Windows Print Queues OS X Maverick, Lion Mountain, Leopard, Tiger, and Panther Pre-Configuration Requirements Ensure Macintosh machines have a valid Host A and PTR records in your
Traditional Telephony IP Telephony Voice, Data, Video Integration. Media Convergence. IP Router Server IP Router. Video Distribution Fax
 Introduction IP telephony allows organizations and individuals to lower the costs of existing services such as data and broadcast video, while broadening their means of communication to include modern
Introduction IP telephony allows organizations and individuals to lower the costs of existing services such as data and broadcast video, while broadening their means of communication to include modern
Security Threat Kill Chain What log data would you need to identify an APT and perform forensic analysis?
 Security Threat Kill Chain What log data would you need to identify an APT and perform forensic analysis? This paper presents a scenario in which an attacker attempts to hack into the internal network
Security Threat Kill Chain What log data would you need to identify an APT and perform forensic analysis? This paper presents a scenario in which an attacker attempts to hack into the internal network
idatafax Troubleshooting
 idatafax Troubleshooting About idatafax idatafax is a client application that connects back to a server at the PHRI based in Hamilton, Ontario, Canada. It is not known to interfere with any software and
idatafax Troubleshooting About idatafax idatafax is a client application that connects back to a server at the PHRI based in Hamilton, Ontario, Canada. It is not known to interfere with any software and
Linksys RV042. TheGreenBow IPSec VPN Client. Configuration Guide. http://www.thegreenbow.com [email protected]
 TheGreenBow IPSec VPN Client Configuration Guide Linksys RV042 WebSite: Contact: http://www.thegreenbow.com [email protected] Configuration Guide written by: Writer: TheGreenBow Support Team Company:
TheGreenBow IPSec VPN Client Configuration Guide Linksys RV042 WebSite: Contact: http://www.thegreenbow.com [email protected] Configuration Guide written by: Writer: TheGreenBow Support Team Company:
Websense Certified Engineer Web Security Professional Examination Specification
 Websense Certified Engineer Web Security Professional Examination Specification Introduction This is an exam specification for the Websense Certified Engineer - Web Security Professional examination. The
Websense Certified Engineer Web Security Professional Examination Specification Introduction This is an exam specification for the Websense Certified Engineer - Web Security Professional examination. The
Network Configuration Settings
 Network Configuration Settings Many small businesses already have an existing firewall device for their local network when they purchase Microsoft Windows Small Business Server 2003. Often, these devices
Network Configuration Settings Many small businesses already have an existing firewall device for their local network when they purchase Microsoft Windows Small Business Server 2003. Often, these devices
WildFire. Preparing for Modern Network Attacks
 WildFire WildFire automatically protects your networks from new and customized malware across a wide range of applications, including malware hidden within SSL-encrypted traffic. WildFire easily extends
WildFire WildFire automatically protects your networks from new and customized malware across a wide range of applications, including malware hidden within SSL-encrypted traffic. WildFire easily extends
Juniper NetScreen 5GT
 TheGreenBow IPSec VPN Client Configuration Guide Juniper NetScreen 5GT WebSite: Contact: http://www.thegreenbow.com [email protected] Configuration Guide written by: Writer: Connected Team Company:
TheGreenBow IPSec VPN Client Configuration Guide Juniper NetScreen 5GT WebSite: Contact: http://www.thegreenbow.com [email protected] Configuration Guide written by: Writer: Connected Team Company:
This Lecture. The Internet and Sockets. The Start 1969. If everyone just sends a small packet of data, they can all use the line at the same.
 This Lecture The Internet and Sockets Computer Security Tom Chothia How the Internet works. Some History TCP/IP Some useful network tools: Nmap, WireShark Some common attacks: The attacker controls the
This Lecture The Internet and Sockets Computer Security Tom Chothia How the Internet works. Some History TCP/IP Some useful network tools: Nmap, WireShark Some common attacks: The attacker controls the
Preliminary Course Syllabus
 Preliminary Course Syllabus Implementing, Managing, and Maintaining a Microsoft Windows Server 2003 Network Infrastructure: Network Services Elements of this syllabus are subject to change. Key Data Course
Preliminary Course Syllabus Implementing, Managing, and Maintaining a Microsoft Windows Server 2003 Network Infrastructure: Network Services Elements of this syllabus are subject to change. Key Data Course
NetSpective Global Proxy Configuration Guide
 NetSpective Global Proxy Configuration Guide Table of Contents NetSpective Global Proxy Deployment... 3 Configuring NetSpective for Global Proxy... 5 Restrict Admin Access... 5 Networking... 6 Apply a
NetSpective Global Proxy Configuration Guide Table of Contents NetSpective Global Proxy Deployment... 3 Configuring NetSpective for Global Proxy... 5 Restrict Admin Access... 5 Networking... 6 Apply a
Setting Up Scan to SMB on TaskALFA series MFP s.
 Setting Up Scan to SMB on TaskALFA series MFP s. There are three steps necessary to set up a new Scan to SMB function button on the TaskALFA series color MFP. 1. A folder must be created on the PC and
Setting Up Scan to SMB on TaskALFA series MFP s. There are three steps necessary to set up a new Scan to SMB function button on the TaskALFA series color MFP. 1. A folder must be created on the PC and
Lab 2. CS-335a. Fall 2012 Computer Science Department. Manolis Surligas [email protected]
 Lab 2 CS-335a Fall 2012 Computer Science Department Manolis Surligas [email protected] 1 Summary At this lab we will cover: Basics of Transport Layer (TCP, UDP) Broadcast ARP DNS More Wireshark filters
Lab 2 CS-335a Fall 2012 Computer Science Department Manolis Surligas [email protected] 1 Summary At this lab we will cover: Basics of Transport Layer (TCP, UDP) Broadcast ARP DNS More Wireshark filters
CompTIA Continuing Education Program and Certification Renewal Policy
 CompTIA Continuing Education Program and Certification Renewal Policy CompTIA A+, CompTIA Network+, CompTIA Storage+, CompTIA Security+ and CompTIA Advanced Security Practitioner (CASP) certifications
CompTIA Continuing Education Program and Certification Renewal Policy CompTIA A+, CompTIA Network+, CompTIA Storage+, CompTIA Security+ and CompTIA Advanced Security Practitioner (CASP) certifications
Intel Security Certified Product Specialist Security Information Event Management (SIEM)
 Intel Security Certified Product Specialist Security Information Event Management (SIEM) Why Get Intel Security Certified? As technology and security threats continue to evolve, organizations are looking
Intel Security Certified Product Specialist Security Information Event Management (SIEM) Why Get Intel Security Certified? As technology and security threats continue to evolve, organizations are looking
Fireware Essentials Exam Study Guide
 Fireware Essentials Exam Study Guide The Fireware Essentials exam tests your knowledge of how to configure, manage, and monitor a WatchGuard Firebox that runs Fireware OS. This exam is appropriate for
Fireware Essentials Exam Study Guide The Fireware Essentials exam tests your knowledge of how to configure, manage, and monitor a WatchGuard Firebox that runs Fireware OS. This exam is appropriate for
https://elearn.zdresearch.com https://training.zdresearch.com/course/pentesting
 https://elearn.zdresearch.com https://training.zdresearch.com/course/pentesting Chapter 1 1. Introducing Penetration Testing 1.1 What is penetration testing 1.2 Different types of test 1.2.1 External Tests
https://elearn.zdresearch.com https://training.zdresearch.com/course/pentesting Chapter 1 1. Introducing Penetration Testing 1.1 What is penetration testing 1.2 Different types of test 1.2.1 External Tests
LAN TCP/IP and DHCP Setup
 CHAPTER 2 LAN TCP/IP and DHCP Setup 2.1 Introduction In this chapter, we will explain in more detail the LAN TCP/IP and DHCP Setup. 2.2 LAN IP Network Configuration In the Vigor 2900 router, there are
CHAPTER 2 LAN TCP/IP and DHCP Setup 2.1 Introduction In this chapter, we will explain in more detail the LAN TCP/IP and DHCP Setup. 2.2 LAN IP Network Configuration In the Vigor 2900 router, there are
Snare for Firefox Snare Agent for the Firefox Browser
 Snare Agent for the Firefox Browser InterSect Alliance International Pty Ltd Page 1 of 11 Intersect Alliance International Pty Ltd. All rights reserved worldwide. Intersect Alliance Pty Ltd shall not be
Snare Agent for the Firefox Browser InterSect Alliance International Pty Ltd Page 1 of 11 Intersect Alliance International Pty Ltd. All rights reserved worldwide. Intersect Alliance Pty Ltd shall not be
Version 0.1 June 2010. Xerox WorkCentre 7120 Fax over Internet Protocol (FoIP)
 Version 0.1 June 2010 Xerox WorkCentre 7120 Fax over Internet Protocol (FoIP) Thank you for choosing the Xerox WorkCentre 7120. Table of Contents Introduction.........................................
Version 0.1 June 2010 Xerox WorkCentre 7120 Fax over Internet Protocol (FoIP) Thank you for choosing the Xerox WorkCentre 7120. Table of Contents Introduction.........................................
Looking for Trouble: ICMP and IP Statistics to Watch
 Looking for Trouble: ICMP and IP Statistics to Watch Laura Chappell, Senior Protocol Analyst Protocol Analysis Institute [[email protected]] www.packet-level.com www.podbooks.com HTCIA Member,
Looking for Trouble: ICMP and IP Statistics to Watch Laura Chappell, Senior Protocol Analyst Protocol Analysis Institute [[email protected]] www.packet-level.com www.podbooks.com HTCIA Member,
Kaseya Server Instal ation User Guide June 6, 2008
 Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
150-420. Brocade Certified Layer 4-7 Professional 2010. Version: Demo. Page <<1/8>>
 150-420 Brocade Certified Layer 4-7 Professional 2010 Version: Demo Page QUESTION NO: 1 Given the command shown below, which statement is true? aaa authentication enable default radius local A.
150-420 Brocade Certified Layer 4-7 Professional 2010 Version: Demo Page QUESTION NO: 1 Given the command shown below, which statement is true? aaa authentication enable default radius local A.
Connecting to and Setting Up a Network
 Chapter 9 Connecting to and Setting Up a Network Reviewing the Basics 1. How many bits are in a MAC address? 48 bits 2. How many bits are in an IPv4 IP address? In an IPv6 IP address? 32 bits, 128 bits
Chapter 9 Connecting to and Setting Up a Network Reviewing the Basics 1. How many bits are in a MAC address? 48 bits 2. How many bits are in an IPv4 IP address? In an IPv6 IP address? 32 bits, 128 bits
Dynamic DNS How-To Guide
 Configuration Guide Dynamic DNS How-To Guide Overview This guide will show you how to set up a Dynamic DNS host name under the D-Link DDNS service with your D-Link ShareCenter TM. Dynamic DNS is a protocol
Configuration Guide Dynamic DNS How-To Guide Overview This guide will show you how to set up a Dynamic DNS host name under the D-Link DDNS service with your D-Link ShareCenter TM. Dynamic DNS is a protocol
