KT-1 Key Chain Token. QUICK Reference. Copyright 2005 CRYPTOCard Corporation All Rights Reserved
|
|
|
- Percival Francis
- 9 years ago
- Views:
Transcription
1 KT-1 Key Chain Token QUICK Reference Copyright 2005 CRYPTOCard Corporation All Rights Reserved
2 Table of Contents OVERVIEW... 1 Token control... 1 OPERATING MODES & OPTIONS... 2 USING THE KT-1, PIN STORED ON SERVER... 8 Generating a Passcode... 8 Changing PIN... 8 USING THE KT-1, TOKEN ACTIVATED BY PIN... 9 Generating a Passcode... 9 User-changeable PIN... 9 PASSWORD RESYNCHRONIZATION...11 ADJUSTING THE LCD CONTRAST...12 LCD DISPLAY TEST...12 TOKEN INITIALIZATION...13 BATTERY REPLACEMENT...14 Copyright 2005 CRYPTOCard Corporation All Rights Reserved i
3 Overview The KT-1 Key Chain token generates a new, pseudorandom passcode each time the token is activated. The token is activated by pressing the button located to the right and below the LCD display. A KT-1 PIN consists of a string of 3 to 8 characters that is used to guard against unauthorized use. If PIN protection is enabled, the user must provide a PIN with the one-time passcode to authenticate. Token control Depending upon the options enabled in the token, the user may be permitted to enter a PIN, adjust the LCD contrast, change his PIN, or resynchronize the token. These actions require the use of the button to accept options presented to the user through the LCD display. The token will provide prompts and allow the user to input the digits 0 through 9, the letter E, and the symbol <. Where input is required, the token will cycle through the input options. When the correct digit, letter, or symbol is displayed, the user pushes the button to accept the input. For example, to input the PIN 123, the user will press the button 3 times, once after each of the numbers 1, 2, and 3 is displayed. Pressing the button when the letter E is displayed indicates to the token that the user will provide no additional input. Pressing the button when the < symbol is displayed erases the input immediately to the left of the symbol. This is used to correct input errors. Copyright 2005 CRYPTOCard Corporation All Rights Reserved 1
4 Operating Modes & Options The KT-1 supports a wide range of operating modes that can be modified using the CRYPTO-Console GUI and a serial or USB token initializer, according to organizational and security policy requirements. The PIN length, complexity, and maximum number of incorrect consecutive PIN attempts must be configured during token initialization. If the PIN attempts threshold is exceeded, the token will not generate a passcode and will, depending on the configuration, either require reinitialization or a PIN reset before it can be used again. A brief list of the more common operating modes follows. Refer to the CRYPTO- Server Administrator Guide for a complete list of modes and options. Display Type: Hexadecimal: token generates passcodes comprised of digits and letters from 0 9 and A-F. Decimal: token generates passcodes comprised of digits from 0-9. Base32: token generates passcodes comprised of digits and letters from 0-9 and A-Z. Base64: token generates passcodes comprised of digits and letters from 0-9 and Aa-Zz, as well as other printable characters available via Shift Telephone mode: Yes: replaces the fourth character of a passcode with a dash (-). This is generally used in combination with Response length: 8 characters and Display type: Decimal to resemble the North American telephone number format. No: passcode is displayed as set by Response length and Display type. Response Length: Determines the passcode length. Options are 5, 6, 7, or 8 characters. Automatic shut-off: Determines the length of time a passcode is displayed on the token, after which the token display is cleared and the token turned off. Options are 30, 60, and 90 seconds. Also used to prevent the token from being reactivated before expiration of the shut-off period. Copyright 2005 CRYPTOCard Corporation All Rights Reserved 2
5 Display Name: The value entered (typically the UserID) is displayed by the token before the passcode is displayed. Maximum length is 8 characters. PIN Style: PIN styles are separated into two general groups: Stored on Server or Token Activated by PIN. The KT-1 also supports a No PIN option, although this is not recommended. Stored on Server requires the user to prepend the PIN to the passcode displayed on the token. The combination of the PIN and passcode form the password that is used to authenticate the user (the passcode cannot be used to authenticate unless the PIN is prepended). The PIN is not input into the token (i.e. it is not required to activate the token and generate a passcode). When operating in this mode, the PIN can consist of alphanumeric characters. Stored on server, Fixed PIN: this PIN must be prepended to the passcode. An Operator can change the PIN. This mode emulates SecurID PIN mode. Stored on server, User-changeable PIN: periodic PIN change is forced by the Server according to the PIN Change Period option. The user will determine the new PIN value within the limits set under the Min PIN Length, Characters allowed, Try Attempts, and Allow Trivial PINs options. This PIN must be prepended to the passcode. This mode emulates the SecurID PIN mode. If a token in this mode becomes locked by exceeding the Try Attempts value and is re-enabled, the user must authenticate at least once before the token Try Attempts is reset to its default value. Stored on server, Server-changeable PIN: periodic PIN change is forced by the Server according to the PIN Change Period option. The Server will determine the new PIN value within the limits set under the Min PIN Length, Characters allowed, Try Attempts, and Allow Trivial PINs options. This PIN must be prepended to the passcode. This mode emulates the SecurID PIN mode. This mode is currently not supported when performing MSCHAPv2 authentication requests. If a token in this mode becomes locked by exceeding the Try Attempts value and is reenabled, the user must authenticate at least once before the token Try Attempts is reset to its default value. Initial PIN modifications for a Stored on Server PIN only become active when Reset Server-side PIN is selected. Token Activated by PIN requires the user to key the PIN into the token before a passcode is generated. In this mode, only the passcode displayed by the token is sent to the Copyright 2005 CRYPTOCard Corporation All Rights Reserved 3
6 authentication server; the PIN is not transmitted across the network. When operating in this mode the PIN can only consist of numeric characters. Fixed PIN: the PIN created for the token at the time of initialization is permanent and cannot be modified by the user or operator. Fixed PIN can only be changed by re-initializing the token after selecting a new PIN value through this tab. This PIN must be entered into the token before a passcode is displayed. User-changeable PIN: the user may change the PIN at any time. The initial PIN set during initialization must be changed by the user on first use of the token. This PIN must be entered into the token before a passcode is displayed. The PIN value selected by the user must be within the limits set under the Min PIN Length, Characters allowed, Try Attempts, and Allow Trivial PINs options. Initial PIN: The initial PIN value required for the token. The value is permanent if Fixed PIN is selected as the PIN Style. This value must be changed on first use of the token for User-changeable PIN. Use the Randomize button to change the initial value to a random number within the limits set under the Random PIN Length, Min PIN Length, and Characters allowed options. Use this feature as a Deployment PIN with CRYPTO-Deploy to ensure that only valid users are registering their token. Note that the minimum initial PIN length can be longer than the minimum PIN length required by the user. Random PIN Length: The minimum PIN length generated when clicking the Randomize button. The valid range is 3 8 characters. Minimum PIN Length: The minimum PIN length required to authenticate. The valid range is 1-8 characters. Characters allowed: Digits only: permits the digits 0 9 in the PIN. Alpha-numeric: permits the digits 0 9 and the characters Aa Zz in the PIN. Strong Alpha-numeric: requires at least one uppercase character, one lowercase character, and one digit in the PIN. This setting is affected by the Allow Trivial PINs option. It is also affected by the PIN Style - if operating in a Token Activated by PIN mode, only digits are Copyright 2005 CRYPTOCard Corporation All Rights Reserved 4
7 permitted; if operating in a Stored on Server PIN mode, alpha-numeric characters are permitted. Try Attempts: Number of consecutive incorrect PIN attempts permitted. The valid range is 1 7 attempts. If this value is exceeded for Stored on Server PINs, authentication will not be permitted until the operator has reset the PIN value. If this value is exceeded for Token Activated by PIN options, the token will be locked and will not generate passcodes until it is re-initialized. Allow Trivial PINs: No: prevents the use of sequences or consecutive digits/characters longer than 2. For example, 124 or ABD are permitted; 123 or ABC are not permitted. Yes: no sequence checking. For example, 123 is permitted. PIN Change Period: Mode: The period in days between forced PIN changes. The value 0 means unlimited. This option is valid only with Stored on Server PINs.\ QUICKLog: password is displayed immediately by token (or after Display Name, if this option is enabled on the Display tab). Challenge-response: requires the user to key a numeric challenge into the token before a response is generated. QUICKLog is the recommended mode for all CRYPTOCard token types. Algorithm: Mk 1 Algorithm: supports older token types using DES only. Mk 2 Algorithm: supported on most token types and supports DES, 3DES, AES (128/192/256). This mode is automatically selected if supported by the token. KT-1 tokens with serial numbers beginning with 3121xxxxx support this algorithm. The encryption algorithm used in all other series is permanently factory preset. Copyright 2005 CRYPTOCard Corporation All Rights Reserved 5
8 Challenge in QUICKLog mode: No: a challenge is not displayed to the user. This is the recommended setting. Yes: a challenge is displayed if supported by network equipment. User will not need to key challenge into token unless token is out of synchronization. Passwords per power cycle: Single: only one passcode is provided after the token is activated. The token must be powered off and re-activated to generate another passcode. Multiple: the token will generate passcodes as required until it is powered off. The Single password (passcode) per power cycle option is recommended. For applications requiring dual authentication or where multiple consecutive logons are required, select Multiple mode. Note that the Automatic shut-off option will power the token off automatically after the specified time interval elapses. User can turn token off: Yes: user can force token off at any time. No: user cannot force token off. The token will automatically turn off (based on Automatic shut-off configuration). The No setting is recommended when using the KT-1 token. Start date: The first date, in yyyymmdd format, that the token may be used to authenticate. Expiry date: The last date, in yyyymmdd format, that the token may be used to authenticate. When an operator changes the Expiry date, the change immediately becomes active on the server and valid for the affected token. This is often used for periodic access typical of contractors. It permits the token to be issued once, while ensuring that the user can only authenticate with an active token during the set periods. Copyright 2005 CRYPTOCard Corporation All Rights Reserved 6
9 Operational Flags: Force PIN change on next use: If checked, the user must change his PIN on the next authentication attempt and the box is cleared on PIN change. Property Flags: Delete token at expiry: On expiry, this token is automatically removed from inventory, if checked. Don t change key at initialization: the encryption key used for this token is reused during re-initialization, if checked. It is recommended that this box remain clear to ensure that keys are changed with every initialization. Usage Flags: Authentication enabled: token can be used to authenticate, if checked. Copyright 2005 CRYPTOCard Corporation All Rights Reserved 7
10 Using the KT-1, PIN Stored on Server In this mode (assuming QUICKLog TM mode is being used), the token requires no input data to generate a new, one-time passcode, but the user must prepend his PIN to the passcode displayed by the token in order to generate an acceptable password. The Stored on server, Server-changeable PIN mode is currently not supported when performing MSCHAPv2 authentication requests. Generating a Passcode Press the button to activate the token. A one-time passcode is automatically generated. Enter the PIN (e.g. ABCD) and passcode (e.g ) at the password prompt (ABCD ). Changing PIN If enabled, this feature permits the PIN to be changed according to the established security policy. The CRYPTO-Server will enforce a PIN change at regular intervals. Depending on the options selected, the user will be prompted to enter a new PIN or will be provided with a new PIN generated by the CRYPTO-Server. In both cases, the PIN will meet the minimum PIN policy requirements (complexity, length, non-trivial, etc.) as configured on the Server. A CRYPTO- Server Operator may also force a PIN change for individual users, as required. When a PIN change is required, the user will be prompted through the process. Once complete, the user must re-authenticate to gain access to protected resources. Copyright 2005 CRYPTOCard Corporation All Rights Reserved 8
11 Using the KT-1, Token activated by PIN In this mode, the user must key a PIN into the token before a passcode is generated. The displayed passcode is then used during logon. The KT-1 supports numeric PINs only in this mode. Note that the PIN is not prepended to the passcode and is never sent across the network. Generating a Passcode Press button to enable token. The token will display the prompt: PIN? # where # corresponds to: the digits 0 through 9 that are used for the PIN. Press the button when the correct digit of the PIN is displayed. E, which is used to indicate that all digits of the PIN have been entered. This applies only where the PIN length is 7 or less. Press the button when E is displayed and all digits of the PIN have been entered. <, which is used to erase an incorrectly entered digit. Press the button to erase the digit to the left of the < symbol. For example, if the PIN is 123: Token Displays Action PIN? 1 Press Button *2 Press Button **3 Press Button ***E Press Button The token will display the one-time passcode. User-changeable PIN If configured, the KT-1 permits the user to change the PIN required to activate the token. The user can change the PIN when the Chg PIN prompt is displayed. When the user keys in the initial PIN (sometimes referred to as the deployment PIN), he will be prompted with Chg PIN to immediately change the PIN to a new value, within the parameters of the security policy established during initialization. Thereafter, the user can change their PIN as often as desired: Copyright 2005 CRYPTOCard Corporation All Rights Reserved 9
12 1. Press and hold the button (approximately 3-4 seconds) on the token until the Init prompt appears. Then release the button. 2. The token will cycle through a series of prompts: Init, LCD Test, Contrast, Chg PIN, and ReSync. The prompts and sequence will vary depending on the options enabled for the token. Press the button while the Chg PIN prompt is displayed. 3. Press the button as each digit of the current PIN is displayed. To accept the entered PIN, press the button when E is displayed. 4. At the New PIN? prompt, use the button to select the new PIN, one digit at a time as the correct digits are displayed. To accept the entered PIN, press the button when E is displayed. 5. At the Verify? Prompt, use the button to re-input the new PIN by repeating step The token displays a Token OK message to indicate that the new PIN has been accepted. For example, if the old PIN is 123, and the new PIN is 7835: Token Displays Action PIN? 1 Press Button *2 Press Button **3 Press Button ***E Press Button NewPIN? 7 Press Button 78 Press Button 783 Press Button 7835 Press Button 7835E Press Button Verify? 7 Press Button 78 Press Button 783 Press Button 7835 Press Button 7835E Press Button Copyright 2005 CRYPTOCard Corporation All Rights Reserved 10
13 Password Resynchronization Token resynchronization requires the user to enter a challenge into the token. The challenge must be provided by the Help Desk or via a Web-based resynchronization page. In the unlikely event that the token requires resynchronization with the authentication server: 1. Press and hold the button (approximately 3-4 seconds) on the token until the Init prompt appears. Then release the button. 2. The token will cycle through a series of prompts: Init, LCD Test, Contrast, Chg PIN, and ReSync. The prompts and sequence will vary depending on the options enabled for the token. Press the button while the Resync prompt is displayed. 3. The digits 0 through 9 will be displayed sequentially to the right of the Resync prompt. For every digit of the resynchronization challenge, press the button to accept the displayed digit. For example, if the resynchronization challenge is : Token Displays Action Resync 1 Press Button 16 Press Button 162 Press Button 1627 Press Button Press Button Press Button Press Button Press Button Press Button Copyright 2005 CRYPTOCard Corporation All Rights Reserved 11
14 Adjusting the LCD Contrast The LCD display contrast can be adjusted to lighten or darken the displayed passcodes and prompts. To adjust the contrast: 1. Press and hold the button (approximately 3-4 seconds) on the token until the Init prompt appears. Then release the button. 2. The token will cycle through a series of prompts: Init, LCD Test, Contrast, Chg PIN, and ReSync. The prompts and sequence will vary depending on the options enabled for the token. Press the button while the Contrast prompt is displayed. 3. The token will prompt the user for his PIN. 4. The token will cycle through a series of prompts in the form of XX##XX- where ## are digits from 00 to 15 that represent the lowest to highest contrast. The contrast will change as the digits change providing a visual indication of the selection. When the desired contrast is displayed, press the button two times to set. LCD Display Test The KT-1 provides a test routine that checks all pixels of the LCD for proper operation. To enable the test: 1. Press and hold the button (approximately 3-4 seconds) on the token until the Init prompt appears. Then release the button. 2. The token will cycle through a series of prompts: Init, LCD Test, Contrast, Chg PIN, and ReSync. The prompts and sequence will vary depending on the options enabled for the token. Press the button while the LCD Test prompt is displayed. 3. The token will cycle through a series of displays that provide a visual indication of any malfunctioning pixels. The token will shut off automatically on completion of the test. Copyright 2005 CRYPTOCard Corporation All Rights Reserved 12
15 Token Initialization The KT-1 can be reprogrammed as often as required to enable new options, encryption modes, and keys. CRYPTO-Console, and a serial or USB token initializer are required. To initialize a token: 1. To prepare a KT token for initialization, start with the KT-1 token off, press and hold the KT-1 token button until the display shows Init (approximately 3-4 seconds). 2. Release and quickly press the button again. The display will show the prompt RDY 4 IR. The KT-1 token will remain in the RDY 4 IR state for approximately 1 minute. The token cannot be initialized while in any other state. 3. Insert the token into the initializer with the LCD display facing the front of the initializer. 4. Follow the instructions on the CRYPTO-Console. The token will display the Token OK message on successful initialization. The token will shut off automatically seconds after initialization. Copyright 2005 CRYPTOCard Corporation All Rights Reserved 13
16 Battery Replacement CRYPTOCard tokens operate for approximately 5-6 years before battery replacement is required. Depending on the model, the token display will indicate a low battery condition about two months before failing (by displaying BATTERY!) or will grow noticeably dim. Each KT-1 token holds two coin-cell batteries. Replacement of one battery at a time permits the token to continue functioning. As long as only one battery at a time is removed and replaced, the token will not need to be returned to the Administrator for reprogramming. 1. Remove the battery compartment cover. 2. Remove one battery and replace it with a new battery (CR2016). 3. Remove the other battery and replace it. Copyright 2005 CRYPTOCard Corporation All Rights Reserved 14
BlackShield ID MP Token Guide. for Java Enabled Phones
 BlackShield ID MP Token Guide for Java Enabled Phones Copyright 2010 CRYPTOCard Inc. http:// www.cryptocard.com Trademarks CRYPTOCard and the CRYPTOCard logo are registered trademarks of CRYPTOCard Corp.
BlackShield ID MP Token Guide for Java Enabled Phones Copyright 2010 CRYPTOCard Inc. http:// www.cryptocard.com Trademarks CRYPTOCard and the CRYPTOCard logo are registered trademarks of CRYPTOCard Corp.
Cisco VPN Concentrator Implementation Guide
 Cisco VPN Concentrator Implementation Guide Copyright Copyright 2006, CRYPTOCard Corp. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Cisco VPN Concentrator Implementation Guide Copyright Copyright 2006, CRYPTOCard Corp. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Flexible Identity. OTP software tokens guide. Multi-Factor Authentication. version 1.0
 Flexible Identity Multi-Factor Authentication OTP software tokens guide version 1.0 Publication History Date Description Revision 2014.02.07 initial release 1.0 Copyright Orange Business Services 2 of
Flexible Identity Multi-Factor Authentication OTP software tokens guide version 1.0 Publication History Date Description Revision 2014.02.07 initial release 1.0 Copyright Orange Business Services 2 of
Juniper Networks SSL VPN Implementation Guide
 Juniper Networks SSL VPN Implementation Guide Copyright Copyright 2006, CRYPTOCard Corp. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Juniper Networks SSL VPN Implementation Guide Copyright Copyright 2006, CRYPTOCard Corp. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Hang Seng Business e-banking. New Security Device. Frequently Asked Questions
 Hang Seng Business e-banking New Security Device Frequently Asked Questions We are delighted to introduce a new Security Device with enhanced security and service on 27 May 2013. Existing Security Device
Hang Seng Business e-banking New Security Device Frequently Asked Questions We are delighted to introduce a new Security Device with enhanced security and service on 27 May 2013. Existing Security Device
User Guide. SafeNet MobilePASS for Windows Phone
 SafeNet MobilePASS for Windows Phone User Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information Product
SafeNet MobilePASS for Windows Phone User Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information Product
Check Point FW-1/VPN-1 NG/FP3
 Check Point FW-1/VPN-1 NG/FP3 Implementation Guide Copyright Copyright 2006, CRYPTOCard Corp. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Check Point FW-1/VPN-1 NG/FP3 Implementation Guide Copyright Copyright 2006, CRYPTOCard Corp. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
PaymentNet Federal Card Solutions Cardholder FAQs
 PaymentNet Federal Card Solutions It s easy to find the answers to your questions about PaymentNet! June 2014 Frequently Asked Questions First Time Login How do I obtain my login information?... 2 How
PaymentNet Federal Card Solutions It s easy to find the answers to your questions about PaymentNet! June 2014 Frequently Asked Questions First Time Login How do I obtain my login information?... 2 How
Department of Supply & Services (CIMS) RSA Web Express User Guide v1.2
 Department of Supply & Services (CIMS) RSA Web Express User Guide v1.2 Created: May 22, 2008 Updated: April 23, 2009 The RSA Web Express web express web site automates functions required to deploy hardware
Department of Supply & Services (CIMS) RSA Web Express User Guide v1.2 Created: May 22, 2008 Updated: April 23, 2009 The RSA Web Express web express web site automates functions required to deploy hardware
CRYPTOLogon Agent. for Windows Domain Logon Authentication. Deployment Guide. Copyright 2002-2003, CRYPTOCard Corporation, All Rights Reserved.
 CRYPTOLogon Agent for Windows Domain Logon Authentication Deployment Guide Table of Contents 1. OVERVIEW... 1 1.1 SINGLE AUTHENTICATION MODE (MS-GINA REPLACEMENT)... 1 1.2 DUAL AUTHENTICATION MODE (MS-GINA
CRYPTOLogon Agent for Windows Domain Logon Authentication Deployment Guide Table of Contents 1. OVERVIEW... 1 1.1 SINGLE AUTHENTICATION MODE (MS-GINA REPLACEMENT)... 1 1.2 DUAL AUTHENTICATION MODE (MS-GINA
Implementation Guide for protecting
 Implementation Guide for protecting Remote Web Workplace (RWW) Outlook Web Access (OWA) 2003 SharePoint 2003 IIS Web Sites with BlackShield ID Copyright 2010 CRYPTOCard Inc. http:// www.cryptocard.com
Implementation Guide for protecting Remote Web Workplace (RWW) Outlook Web Access (OWA) 2003 SharePoint 2003 IIS Web Sites with BlackShield ID Copyright 2010 CRYPTOCard Inc. http:// www.cryptocard.com
Apache Server Implementation Guide
 Apache Server Implementation Guide 340 March Road Suite 600 Kanata, Ontario, Canada K2K 2E4 Tel: +1-613-599-2441 Fax: +1-613-599-2442 International Voice: +1-613-599-2441 North America Toll Free: 1-800-307-7042
Apache Server Implementation Guide 340 March Road Suite 600 Kanata, Ontario, Canada K2K 2E4 Tel: +1-613-599-2441 Fax: +1-613-599-2442 International Voice: +1-613-599-2441 North America Toll Free: 1-800-307-7042
SAS. Administration Guide. Version 1.6 09/aug/12
 Administration Guide 09/aug/12 Table of contents 1 References... 4 2 Introduction... 5 3 overview... 6 4 management portal... 9 4.1 Access... 9 4.2 Account Manager view...10 4.3 Operator view...11 5 Customizing
Administration Guide 09/aug/12 Table of contents 1 References... 4 2 Introduction... 5 3 overview... 6 4 management portal... 9 4.1 Access... 9 4.2 Account Manager view...10 4.3 Operator view...11 5 Customizing
IMS Health Secure Outlook Web Access Portal. Quick Setup
 IMS Health Secure Outlook Web Access Portal Purpose: This service has been developed to allow access to the IMS Health email system for staff that can not access the email system through VPN which is preferred
IMS Health Secure Outlook Web Access Portal Purpose: This service has been developed to allow access to the IMS Health email system for staff that can not access the email system through VPN which is preferred
Borderware MXtreme. Secure Email Gateway QuickStart Guide. Copyright 2005 CRYPTOCard Corporation All Rights Reserved
 Borderware MXtreme Secure Email Gateway QuickStart Guide Copyright 2005 CRYPTOCard Corporation All Rights Reserved http://www.cryptocard.com Overview MXtreme is a hardened appliance with a highly robust
Borderware MXtreme Secure Email Gateway QuickStart Guide Copyright 2005 CRYPTOCard Corporation All Rights Reserved http://www.cryptocard.com Overview MXtreme is a hardened appliance with a highly robust
RSA Authentication Manager 8.1 Help Desk Administrator s Guide
 RSA Authentication Manager 8.1 Help Desk Administrator s Guide Contact Information Go to the RSA corporate website for regional Customer Support telephone and fax numbers: www.emc.com/domains/rsa/index.htm
RSA Authentication Manager 8.1 Help Desk Administrator s Guide Contact Information Go to the RSA corporate website for regional Customer Support telephone and fax numbers: www.emc.com/domains/rsa/index.htm
Desktop Programmer (DTP)
 INSTALLATION Desktop Programmer (DTP) Keypads & Readers Contents Set up the System...1 RCI DTP Contents...1 Install the System...2 Initialize the Program...2 Initialize the Door Locks...3 Add a User...4
INSTALLATION Desktop Programmer (DTP) Keypads & Readers Contents Set up the System...1 RCI DTP Contents...1 Install the System...2 Initialize the Program...2 Initialize the Door Locks...3 Add a User...4
Implementation Guide for. Juniper SSL VPN SSO with OWA. with. BlackShield ID
 Implementation Guide for Juniper SSL VPN SSO with OWA with BlackShield ID Copyright 2009 CRYPTOCard Inc. http:// www.cryptocard.com Copyright Copyright 2009, CRYPTOCard All Rights Reserved. No part of
Implementation Guide for Juniper SSL VPN SSO with OWA with BlackShield ID Copyright 2009 CRYPTOCard Inc. http:// www.cryptocard.com Copyright Copyright 2009, CRYPTOCard All Rights Reserved. No part of
RSA Authentication Manager 8.1 Help Desk Administrator s Guide. Revision 1
 RSA Authentication Manager 8.1 Help Desk Administrator s Guide Revision 1 Contact Information Go to the RSA corporate website for regional Customer Support telephone and fax numbers: www.emc.com/domains/rsa/index.htm
RSA Authentication Manager 8.1 Help Desk Administrator s Guide Revision 1 Contact Information Go to the RSA corporate website for regional Customer Support telephone and fax numbers: www.emc.com/domains/rsa/index.htm
LCD MONITOR / 8 CHANNEL DVR COMBO
 LCD MONITOR / 8 CHANNEL DVR COMBO Overview - New System Setup SERIES: SG17LD800 & SG19LD800 www.lorexcctv.com Copyright 2007 LOREX Technology Inc. New System Setup - Overview New System Setup - Overview
LCD MONITOR / 8 CHANNEL DVR COMBO Overview - New System Setup SERIES: SG17LD800 & SG19LD800 www.lorexcctv.com Copyright 2007 LOREX Technology Inc. New System Setup - Overview New System Setup - Overview
Integration Guide. SafeNet Authentication Service. VMWare View 5.1
 SafeNet Authentication Service Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information
SafeNet Authentication Service Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7.
 Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
BlackShield ID PRO. Steel Belted RADIUS 6.x. Implementation Guide. Copyright 2008 to present CRYPTOCard Corporation. All Rights Reserved
 BlackShield ID PRO Steel Belted RADIUS 6.x Implementation Guide Copyright 2008 to present CRYPTOCard Corporation. All Rights Reserved License and Warranty Information CRYPTOCard and its affiliates retain
BlackShield ID PRO Steel Belted RADIUS 6.x Implementation Guide Copyright 2008 to present CRYPTOCard Corporation. All Rights Reserved License and Warranty Information CRYPTOCard and its affiliates retain
SafeGuard Enterprise Web Helpdesk. Product version: 6 Document date: February 2012
 SafeGuard Enterprise Web Helpdesk Product version: 6 Document date: February 2012 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Helpdesk
SafeGuard Enterprise Web Helpdesk Product version: 6 Document date: February 2012 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Helpdesk
9243054 Issue 1. Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation
 9243054 Issue 1 Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation VPN Client User s Guide 9243054 Issue 1 Reproduction, transfer, distribution or storage of part or all of
9243054 Issue 1 Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation VPN Client User s Guide 9243054 Issue 1 Reproduction, transfer, distribution or storage of part or all of
Welcome Guide for MP-1 Token for Microsoft Windows
 Welcome Guide for MP-1 Token for Microsoft Windows Protecting Your On-line Identity Authentication Service Delivery Made EASY Copyright 2012 SafeNet, Inc. All rights reserved. All attempts have been made
Welcome Guide for MP-1 Token for Microsoft Windows Protecting Your On-line Identity Authentication Service Delivery Made EASY Copyright 2012 SafeNet, Inc. All rights reserved. All attempts have been made
BlackShield Authentication Service
 BlackShield Authentication Service Guide for Users of CRYPTOCard MP-1 Software Tokens on Smart Phones Protecting Your On-line Identity Authentication Service Delivery Made EASY Copyright Copyright 2011.
BlackShield Authentication Service Guide for Users of CRYPTOCard MP-1 Software Tokens on Smart Phones Protecting Your On-line Identity Authentication Service Delivery Made EASY Copyright Copyright 2011.
SafeGuard Enterprise Web Helpdesk
 SafeGuard Enterprise Web Helpdesk Product version: 5.60 Document date: April 2011 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Help Desk
SafeGuard Enterprise Web Helpdesk Product version: 5.60 Document date: April 2011 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Help Desk
RSA SecurID Token User Guide February 12, 2015
 RSA SecurID Token User Guide Page i Table of Contents Section I How to request an RSA SecurID token... 1 Section II Setting your RSA SecurID PIN... 6 Section III Setting up PuTTY on your Windows workstation
RSA SecurID Token User Guide Page i Table of Contents Section I How to request an RSA SecurID token... 1 Section II Setting your RSA SecurID PIN... 6 Section III Setting up PuTTY on your Windows workstation
Flexible Identity. Tokenless authenticators guide. Multi-Factor Authentication. version 1.0
 Flexible Identity Multi-Factor Authentication Tokenless authenticators guide version 1.0 Publication History Date Description Revision 2014.02.07 initial release 1.0 Copyright Orange Business Services
Flexible Identity Multi-Factor Authentication Tokenless authenticators guide version 1.0 Publication History Date Description Revision 2014.02.07 initial release 1.0 Copyright Orange Business Services
SafeNet MobilePASS Version 8.2.0, Revision B
 SafeNet MobilePASS Version 8.2.0, Revision B User Guide Software Version 8.2.0 Documentation Version: 20101118 2012 SafeNet, Inc. All rights reserved Preface All intellectual property is protected by copyright.
SafeNet MobilePASS Version 8.2.0, Revision B User Guide Software Version 8.2.0 Documentation Version: 20101118 2012 SafeNet, Inc. All rights reserved Preface All intellectual property is protected by copyright.
Android support for Microsoft Exchange in pure Google devices
 Android support for Microsoft Exchange in pure Google devices Note: The information presented here is intended for Microsoft Exchange administrators who are planning and implementing support for any of
Android support for Microsoft Exchange in pure Google devices Note: The information presented here is intended for Microsoft Exchange administrators who are planning and implementing support for any of
RSA SecurID Software Token 1.0 for Android Administrator s Guide
 RSA SecurID Software Token 1.0 for Android Administrator s Guide Contact Information See the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA,
RSA SecurID Software Token 1.0 for Android Administrator s Guide Contact Information See the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA,
RSA SecurID Software Token Security Best Practices Guide
 RSA SecurID Software Token Security Best Practices Guide Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA, the RSA
RSA SecurID Software Token Security Best Practices Guide Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA, the RSA
Business ebanking - User Sign On & Set Up
 About Sign On Business ebanking has two authentication methods that reduce the risk of online identity theft: secure token authentication and out-of-band authentication. The authentication method companies
About Sign On Business ebanking has two authentication methods that reduce the risk of online identity theft: secure token authentication and out-of-band authentication. The authentication method companies
GENEVA COLLEGE INFORMATION TECHNOLOGY SERVICES. Password POLICY
 GENEVA COLLEGE INFORMATION TECHNOLOGY SERVICES Password POLICY Table of Contents OVERVIEW... 2 PURPOSE... 2 SCOPE... 2 DEFINITIONS... 2 POLICY... 3 RELATED STANDARDS, POLICIES AND PROCESSES... 4 EXCEPTIONS...
GENEVA COLLEGE INFORMATION TECHNOLOGY SERVICES Password POLICY Table of Contents OVERVIEW... 2 PURPOSE... 2 SCOPE... 2 DEFINITIONS... 2 POLICY... 3 RELATED STANDARDS, POLICIES AND PROCESSES... 4 EXCEPTIONS...
Two-Factor Authentication
 Two-Factor Authentication This document describes SonicWALL s implementation of two-factor authentication for SonicWALL SSL-VPN appliances. This document contains the following sections: Feature Overview
Two-Factor Authentication This document describes SonicWALL s implementation of two-factor authentication for SonicWALL SSL-VPN appliances. This document contains the following sections: Feature Overview
SafeNet Authentication Client (Windows)
 SafeNet Authentication Client (Windows) Version 8.1 SP1 Revision A User s Guide Copyright 2011 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete
SafeNet Authentication Client (Windows) Version 8.1 SP1 Revision A User s Guide Copyright 2011 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete
Information Systems. Connecting Smartphones to NTU s Email System
 Information Systems Connecting Smartphones to NTU s Email System Connecting Smartphones to NTU s Email System Contents Things to be aware of before you start 3 Connecting a Windows Mobile 6 (6.0-6.5) Phone
Information Systems Connecting Smartphones to NTU s Email System Connecting Smartphones to NTU s Email System Contents Things to be aware of before you start 3 Connecting a Windows Mobile 6 (6.0-6.5) Phone
Android 4.0.4 Support on Galaxy Nexus, Nexus S, and Motorola Xoom for Microsoft Exchange Policies
 Android 4.0.4 Support on Galaxy Nexus, Nexus S, and Motorola Xoom for Microsoft Exchange Policies Overview Requirements Supported Information Services Supported Security Policies Require password Require
Android 4.0.4 Support on Galaxy Nexus, Nexus S, and Motorola Xoom for Microsoft Exchange Policies Overview Requirements Supported Information Services Supported Security Policies Require password Require
RSA Authentication Manager 7.1 Security Best Practices Guide. Version 5
 RSA Authentication Manager 7.1 Security Best Practices Guide Version 5 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks
RSA Authentication Manager 7.1 Security Best Practices Guide Version 5 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks
Windows Live Mail Setup Guide
 Versions Addressed: Windows Live Mail 2011 Document Updated: 11/24/2010 Copyright 2010 Purpose: This document will assist the end user in configuring Windows Live Mail to access a POP3 email account hosted
Versions Addressed: Windows Live Mail 2011 Document Updated: 11/24/2010 Copyright 2010 Purpose: This document will assist the end user in configuring Windows Live Mail to access a POP3 email account hosted
RSA Authentication Manager 7.1 Security Best Practices Guide. Version 2
 RSA Authentication Manager 7.1 Security Best Practices Guide Version 2 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks
RSA Authentication Manager 7.1 Security Best Practices Guide Version 2 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks
NODE4 SERVICE DESK SYSTEM
 NODE4 SERVICE DESK SYSTEM KNOWLEDGE BASE ARTICLE INTERNAL USE ONLY NODE4 LIMITED 24/04/2015 ADD A POP, IMAP OR OFFICE 365 ACCOUNT TO OUTLOOK USING CUSTOM SETTINGS If you re setting up Outlook for the first
NODE4 SERVICE DESK SYSTEM KNOWLEDGE BASE ARTICLE INTERNAL USE ONLY NODE4 LIMITED 24/04/2015 ADD A POP, IMAP OR OFFICE 365 ACCOUNT TO OUTLOOK USING CUSTOM SETTINGS If you re setting up Outlook for the first
Quick Reference Guide. Online Courier: FTP. Signing On. Using FTP Pickup. To Access Online Courier. https://onlinecourier.suntrust.
 Quick Reference Guide Online Courier: FTP https://onlinecourier.suntrust.com With SunTrust Online Courier, you can have reports and files delivered to you using an FTP connection. There are two delivery
Quick Reference Guide Online Courier: FTP https://onlinecourier.suntrust.com With SunTrust Online Courier, you can have reports and files delivered to you using an FTP connection. There are two delivery
progecad NLM User Guide
 progecad NLM User Guide Rel. 14.1 Table of Contents Table of Contents... 2 Introduction... 3 How to start... 3 progecad NLM Server Installation... 3 progecad NLM Server Registration... 3 Licenses Addition
progecad NLM User Guide Rel. 14.1 Table of Contents Table of Contents... 2 Introduction... 3 How to start... 3 progecad NLM Server Installation... 3 progecad NLM Server Registration... 3 Licenses Addition
McAfee Endpoint Encryption 7.0 Users Guide and FAQ
 McAfee Endpoint Encryption 7.0 Users Guide and FAQ Table of Contents Introduction... 1 Installation... 1 Boot-Up/Login... 1 Encryption Status... 3 Notes for Encryption... 4 Changing Your Password... 4
McAfee Endpoint Encryption 7.0 Users Guide and FAQ Table of Contents Introduction... 1 Installation... 1 Boot-Up/Login... 1 Encryption Status... 3 Notes for Encryption... 4 Changing Your Password... 4
Digital Signatures on iqmis User Access Request Form
 Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
BlackShield ID. Professional Edition Version 2.7 Administrator Guide. 2010 CRYPTOCard Corp. All rights reserved. http://www.cryptocard.
 BlackShield ID Professional Edition Version 2.7 2010 CRYPTOCard Corp. All rights reserved. http://www.cryptocard.com Trademarks CRYPTOCard and the CRYPTOCard logo are registered trademarks of CRYPTOCard
BlackShield ID Professional Edition Version 2.7 2010 CRYPTOCard Corp. All rights reserved. http://www.cryptocard.com Trademarks CRYPTOCard and the CRYPTOCard logo are registered trademarks of CRYPTOCard
RSA SecurID Software Token 1.3 for iphone and ipad Administrator s Guide
 RSA SecurID Software Token 1.3 for iphone and ipad Administrator s Guide Contact Information See the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks
RSA SecurID Software Token 1.3 for iphone and ipad Administrator s Guide Contact Information See the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks
IBM Security Access Manager for Enterprise Single Sign-On Version 8.2.1. User Guide IBM SC23-9950-05
 IBM Security Access Manager for Enterprise Single Sign-On Version 8.2.1 User Guide IBM SC23-9950-05 IBM Security Access Manager for Enterprise Single Sign-On Version 8.2.1 User Guide IBM SC23-9950-05
IBM Security Access Manager for Enterprise Single Sign-On Version 8.2.1 User Guide IBM SC23-9950-05 IBM Security Access Manager for Enterprise Single Sign-On Version 8.2.1 User Guide IBM SC23-9950-05
ONE Mail Direct for Mobile Devices
 ONE Mail Direct for Mobile Devices User Guide Version: 2.0 Document ID: 3292 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2014, ehealth Ontario All rights reserved No part of this document
ONE Mail Direct for Mobile Devices User Guide Version: 2.0 Document ID: 3292 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2014, ehealth Ontario All rights reserved No part of this document
Operating Manual QUESTOR
 QUESTOR AS 273 Management Software Document: KSW3s527.0004 / en 2010.08 Edition: August 2010 QUESTOR TABLE OF CONTENT 1 Product description EN-4 1.1 Purpose... EN-4 1.2 System components... EN-4 1.2.1
QUESTOR AS 273 Management Software Document: KSW3s527.0004 / en 2010.08 Edition: August 2010 QUESTOR TABLE OF CONTENT 1 Product description EN-4 1.1 Purpose... EN-4 1.2 System components... EN-4 1.2.1
EMMA Application v. 4.9 User Manual
 EMMA Application v. 4.9 User Manual Prepared by: HP/DMDC 1600 N. Beauregard Street Alexandria, VA 22311 Abstract This guide describes how to use the EMMA system, which allows users to provision for required
EMMA Application v. 4.9 User Manual Prepared by: HP/DMDC 1600 N. Beauregard Street Alexandria, VA 22311 Abstract This guide describes how to use the EMMA system, which allows users to provision for required
ipad in Business Security
 ipad in Business Security Device protection Strong passcodes Passcode expiration Passcode reuse history Maximum failed attempts Over-the-air passcode enforcement Progressive passcode timeout Data security
ipad in Business Security Device protection Strong passcodes Passcode expiration Passcode reuse history Maximum failed attempts Over-the-air passcode enforcement Progressive passcode timeout Data security
iphone in Business How-To Setup Guide for Users
 iphone in Business How-To Setup Guide for Users iphone is ready for business. It supports Microsoft Exchange ActiveSync, as well as standards-based services, delivering email, calendars, and contacts over
iphone in Business How-To Setup Guide for Users iphone is ready for business. It supports Microsoft Exchange ActiveSync, as well as standards-based services, delivering email, calendars, and contacts over
Question How do I access the router s web-based setup page? Answer
 http://linksys.custhelp.com/cgi-bin/linksys.cfg/php/enduser/std_adp.php?p_faqid=3676 Question How do I access the router s web-based setup page? Answer All Linksys routers have a built-in web-based setup
http://linksys.custhelp.com/cgi-bin/linksys.cfg/php/enduser/std_adp.php?p_faqid=3676 Question How do I access the router s web-based setup page? Answer All Linksys routers have a built-in web-based setup
Setting up CU@Round On line Account
 Setting up CU@Round On line Account Created Date: October 6, 2009 Purpose: This document is a step by step process on how to set up a member s CU@Round online account. Note: The member will need the following
Setting up CU@Round On line Account Created Date: October 6, 2009 Purpose: This document is a step by step process on how to set up a member s CU@Round online account. Note: The member will need the following
Thank you for choosing Huwei E589 4G Mobile WiFi
 Thank you for choosing Huwei E589 4G Mobile WiFi This guide briefly describes the functions of your Huawei E589 4G Mobile WiFi. For more details, see help on the web management page. See Accessing the
Thank you for choosing Huwei E589 4G Mobile WiFi This guide briefly describes the functions of your Huawei E589 4G Mobile WiFi. For more details, see help on the web management page. See Accessing the
RSA Authentication Manager 7.1 Basic Exercises
 RSA Authentication Manager 7.1 Basic Exercises Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA and the RSA logo
RSA Authentication Manager 7.1 Basic Exercises Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA and the RSA logo
BlackShield ID Agent for Terminal Services Web and Remote Desktop Web
 Agent for Terminal Services Web and Remote Desktop Web 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication
Agent for Terminal Services Web and Remote Desktop Web 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication
Virtual Code Authentication User s Guide. June 25, 2015
 Virtual Code Authentication User s Guide June 25, 2015 Virtual Code Authentication User s Guide Overview of New Security Modern technologies call for higher security standards as practiced among many other
Virtual Code Authentication User s Guide June 25, 2015 Virtual Code Authentication User s Guide Overview of New Security Modern technologies call for higher security standards as practiced among many other
1 of 10 1/31/2014 4:08 PM
 1 of 10 1/31/2014 4:08 PM copyright 2014 How to backup Microsoft SQL Server with Nordic Backup Pro Before creating a SQL backup set within Nordic Backup Pro it is first necessary to verify that the settings
1 of 10 1/31/2014 4:08 PM copyright 2014 How to backup Microsoft SQL Server with Nordic Backup Pro Before creating a SQL backup set within Nordic Backup Pro it is first necessary to verify that the settings
Identikey Server Getting Started Guide 3.1
 Identikey Server Getting Started Guide 3.1 Disclaimer of Warranties and Limitations of Liabilities Disclaimer of Warranties and Limitations of Liabilities The Product is provided on an 'as is' basis, without
Identikey Server Getting Started Guide 3.1 Disclaimer of Warranties and Limitations of Liabilities Disclaimer of Warranties and Limitations of Liabilities The Product is provided on an 'as is' basis, without
SafeGuard Enterprise Web Helpdesk. Product version: 6.1
 SafeGuard Enterprise Web Helpdesk Product version: 6.1 Document date: February 2014 Contents 1 SafeGuard web-based Challenge/Response...3 2 Scope of Web Helpdesk...4 3 Installation...5 4 Allow Web Helpdesk
SafeGuard Enterprise Web Helpdesk Product version: 6.1 Document date: February 2014 Contents 1 SafeGuard web-based Challenge/Response...3 2 Scope of Web Helpdesk...4 3 Installation...5 4 Allow Web Helpdesk
Help for DTVP-M Users
 help.pdf Help for DTVP-M Users Introduction Recommendations Initialization DTVP-M Login Password Criteria Device Lockout Forgot Password Change Password Reset Option About DTVP-M Drive Letter Conflict
help.pdf Help for DTVP-M Users Introduction Recommendations Initialization DTVP-M Login Password Criteria Device Lockout Forgot Password Change Password Reset Option About DTVP-M Drive Letter Conflict
New Brunswick Internal Services Agency. RSA Self-Service Console User Guide
 New Brunswick Internal Services Agency RSA Self-Service Console User Guide Version: 1.0 Created: November 27, 2013 Modified: November 27, 2013 Table of Contents Introduction...1 Logging on to the RSA Self-Service
New Brunswick Internal Services Agency RSA Self-Service Console User Guide Version: 1.0 Created: November 27, 2013 Modified: November 27, 2013 Table of Contents Introduction...1 Logging on to the RSA Self-Service
Changing Passwords in Cisco Unity 8.x
 CHAPTER 9 Changing Passwords in Cisco Unity 8.x This chapter contains the following sections: Changing Passwords for the Cisco Unity 8.x Service Accounts (Without Failover), page 9-1 Changing Passwords
CHAPTER 9 Changing Passwords in Cisco Unity 8.x This chapter contains the following sections: Changing Passwords for the Cisco Unity 8.x Service Accounts (Without Failover), page 9-1 Changing Passwords
Avalanche Enabler 5.3 User Guide
 Avalanche Enabler 5.3 User Guide 30/05/2012 ii Copyright 2012 by Wavelink Corporation. All rights reserved. Wavelink Corporation 10808 South River Front Parkway, Suite 200 South Jordan, Utah 84095 Telephone:
Avalanche Enabler 5.3 User Guide 30/05/2012 ii Copyright 2012 by Wavelink Corporation. All rights reserved. Wavelink Corporation 10808 South River Front Parkway, Suite 200 South Jordan, Utah 84095 Telephone:
Managing Software Feature Licenses
 Managing Software Feature Licenses This chapter includes the following information: Understanding Alcatel software feature licenses Installing software feature licenses Maintenance of software feature
Managing Software Feature Licenses This chapter includes the following information: Understanding Alcatel software feature licenses Installing software feature licenses Maintenance of software feature
Operating instructions TSE Wireless Software Home
 Operating instructions TSE Wireless Software Home Table of contents 1. GENERAL 2 2. INSTALL SOFTWARE 2 2.1. Installation in Windows XP 2 2.2. Installation in Windows Vista 3 3. THE PROGRAM 0 3.1. Setup
Operating instructions TSE Wireless Software Home Table of contents 1. GENERAL 2 2. INSTALL SOFTWARE 2 2.1. Installation in Windows XP 2 2.2. Installation in Windows Vista 3 3. THE PROGRAM 0 3.1. Setup
NetIQ Advanced Authentication Framework - Client. User's Guide. Version 5.1.0
 NetIQ Advanced Authentication Framework - Client User's Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 4 About This Document 4 NetIQ Advanced Authentication Framework Overview
NetIQ Advanced Authentication Framework - Client User's Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 4 About This Document 4 NetIQ Advanced Authentication Framework Overview
Merchant On The Move Android Professional Edition User Guide and Tutorial
 Merchant On The Move Android Professional Edition User Guide and Tutorial Copyright (c) 2010 Primary Merchant Solutions Inc All rights reserved Merchant On The Move for Android p. 1 Requirements Merchant
Merchant On The Move Android Professional Edition User Guide and Tutorial Copyright (c) 2010 Primary Merchant Solutions Inc All rights reserved Merchant On The Move for Android p. 1 Requirements Merchant
RSA SecurID Certified Administrator (RSA Authentication Manager 8.0) Certification Examination Study Guide
 RSA SecurID Certified Administrator (RSA Authentication Manager 8.0) Certification Examination Study Guide Introduction The RSA SecurID Certified Administrator (CA) examination is based on the critical
RSA SecurID Certified Administrator (RSA Authentication Manager 8.0) Certification Examination Study Guide Introduction The RSA SecurID Certified Administrator (CA) examination is based on the critical
Borderware Firewall Server Version 7.1. VPN Authentication Configuration Guide. Copyright 2005 CRYPTOCard Corporation All Rights Reserved
 Borderware Firewall Server Version 7.1 VPN Authentication Configuration Guide Copyright 2005 CRYPTOCard Corporation All Rights Reserved http://www.cryptocard.com Overview The BorderWare Firewall Server
Borderware Firewall Server Version 7.1 VPN Authentication Configuration Guide Copyright 2005 CRYPTOCard Corporation All Rights Reserved http://www.cryptocard.com Overview The BorderWare Firewall Server
User Guide. Version R91. English
 AuthAnvil User Guide Version R91 English August 25, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
AuthAnvil User Guide Version R91 English August 25, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
Quest Soft Token for Windows Phone User Guide
 Quest Soft Token for Windows Phone User Guide What is the Quest Soft Token for Windows Phone? The Quest Soft Token for Windows Phone is a two-factor authentication token that can be used with any OATH-compliant
Quest Soft Token for Windows Phone User Guide What is the Quest Soft Token for Windows Phone? The Quest Soft Token for Windows Phone is a two-factor authentication token that can be used with any OATH-compliant
Full disk encryption with Sophos Safeguard Enterprise With Two-Factor authentication of Users Using SecurAccess by SecurEnvoy
 Full disk encryption with Sophos Safeguard Enterprise With Two-Factor authentication of Users Using SecurAccess by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview
Full disk encryption with Sophos Safeguard Enterprise With Two-Factor authentication of Users Using SecurAccess by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview
ZENworks 11 Support Pack 4 Full Disk Encryption Agent Reference. May 2016
 ZENworks 11 Support Pack 4 Full Disk Encryption Agent Reference May 2016 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government
ZENworks 11 Support Pack 4 Full Disk Encryption Agent Reference May 2016 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government
DIS VPN Service Client Documentation
 DIS VPN Service Client Documentation Background ------------------------------------------------------------------------------------------------ 1 Downloading the Client ---------------------------------------------------------------------------------
DIS VPN Service Client Documentation Background ------------------------------------------------------------------------------------------------ 1 Downloading the Client ---------------------------------------------------------------------------------
Symantec Endpoint Encryption Full Disk
 Symantec Endpoint Encryption Full Disk User Guide Version 6.0 Information in this document is subject to change without notice. No part of this document may be reproduced or transmitted in any form or
Symantec Endpoint Encryption Full Disk User Guide Version 6.0 Information in this document is subject to change without notice. No part of this document may be reproduced or transmitted in any form or
BlackBerry Business Cloud Services. Policy Reference Guide
 BlackBerry Business Cloud Services Policy Reference Guide Published: 2012-01-30 SWD-1710801-0125055002-001 Contents 1 IT policy rules... 5 Preconfigured IT policies... 5 Default for preconfigured IT policies...
BlackBerry Business Cloud Services Policy Reference Guide Published: 2012-01-30 SWD-1710801-0125055002-001 Contents 1 IT policy rules... 5 Preconfigured IT policies... 5 Default for preconfigured IT policies...
Sophos Mobile Control User guide for Apple ios. Product version: 4
 Sophos Mobile Control User guide for Apple ios Product version: 4 Document date: May 2014 Contents 1 About Sophos Mobile Control...3 2 About this guide...4 3 Login to the Self Service Portal...5 4 Set
Sophos Mobile Control User guide for Apple ios Product version: 4 Document date: May 2014 Contents 1 About Sophos Mobile Control...3 2 About this guide...4 3 Login to the Self Service Portal...5 4 Set
F-Series Desktop User Manual F20. English - Europe/New Zealand
 F-Series Desktop User Manual F20 en English - Europe/New Zealand Contents Key to icons and text...3 What is F-Series Desktop?...4 How do I install F-Series Desktop onto my computer?...4 How do I subscribe
F-Series Desktop User Manual F20 en English - Europe/New Zealand Contents Key to icons and text...3 What is F-Series Desktop?...4 How do I install F-Series Desktop onto my computer?...4 How do I subscribe
September 25, 2015. Programming YubiKeys for Okta Adaptive Multi-Factor Authentication
 Programming YubiKeys for Okta Adaptive Multi-Factor Authentication September 25, 2015 Programming YubiKeys for Okta Adaptive Multi-Factor Authentication Page 1 of 14 Copyright 2015 Yubico Inc. All rights
Programming YubiKeys for Okta Adaptive Multi-Factor Authentication September 25, 2015 Programming YubiKeys for Okta Adaptive Multi-Factor Authentication Page 1 of 14 Copyright 2015 Yubico Inc. All rights
Moving Forward Together
 Moving Forward Together AMITA HEALTH INFORMATION SERVICES EMAIL MIGRATION INFORMATION The purpose of IT integration is to bridge the technology and infrastructure between Adventist Midwest Health sites
Moving Forward Together AMITA HEALTH INFORMATION SERVICES EMAIL MIGRATION INFORMATION The purpose of IT integration is to bridge the technology and infrastructure between Adventist Midwest Health sites
Yubico PIV Management Tools
 Yubico PIV Management Tools Active Directory Smart Card Logon using the YubiKey NEO or NEO-n Document Version 1.0 April 15, 2015 Yubico PIV Management Tools 2015 Yubico. All rights reserved. Page 1 of
Yubico PIV Management Tools Active Directory Smart Card Logon using the YubiKey NEO or NEO-n Document Version 1.0 April 15, 2015 Yubico PIV Management Tools 2015 Yubico. All rights reserved. Page 1 of
Active Directory User Management System (ADUMS)
 Active Directory User Management System (ADUMS) Release 2.9.3 User Guide Revision History Version Author Date Comments (MM/DD/YYYY) i RMA 08/05/2009 Initial Draft Ii RMA 08/20/09 Addl functionality and
Active Directory User Management System (ADUMS) Release 2.9.3 User Guide Revision History Version Author Date Comments (MM/DD/YYYY) i RMA 08/05/2009 Initial Draft Ii RMA 08/20/09 Addl functionality and
Connec ng to Northwest s WIFI with Windows 7
 Connecting to Northwest s Secure wireless network with your personal computer should be fast and easy if you follow these instructions. To connect your personally-owned computer (with Windows 7 OS) to
Connecting to Northwest s Secure wireless network with your personal computer should be fast and easy if you follow these instructions. To connect your personally-owned computer (with Windows 7 OS) to
Smart Card Authentication Client. Administrator's Guide
 Smart Card Authentication Client Administrator's Guide April 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Smart Card Authentication Client...4 Configuring printer settings for use
Smart Card Authentication Client Administrator's Guide April 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Smart Card Authentication Client...4 Configuring printer settings for use
Objectives. At the end of this chapter students should be able to:
 NTFS PERMISSIONS AND SECURITY SETTING.1 Introduction to NTFS Permissions.1.1 File Permissions and Folder Permission.2 Assigning NTFS Permissions and Special Permission.2.1 Planning NTFS Permissions.2.2
NTFS PERMISSIONS AND SECURITY SETTING.1 Introduction to NTFS Permissions.1.1 File Permissions and Folder Permission.2 Assigning NTFS Permissions and Special Permission.2.1 Planning NTFS Permissions.2.2
McAfee Endpoint Encryption (SafeBoot) User Documentation
 TABLE OF CONTENTS Press the CTRL key while clicking on topic to go straight to the topic in this document. I. Introduction... 1 II. Installation Process Overview... 1 III. Checking for a Valid Current
TABLE OF CONTENTS Press the CTRL key while clicking on topic to go straight to the topic in this document. I. Introduction... 1 II. Installation Process Overview... 1 III. Checking for a Valid Current
Password Reset Server User Guide
 Table of Contents Getting Started... 3 Product Overview... 3 Installation... 3 Accessing Password Reset Server... 3 Terminology... 4 Password Sources... 5 Creating a new Password Source... 5 Security Policies...
Table of Contents Getting Started... 3 Product Overview... 3 Installation... 3 Accessing Password Reset Server... 3 Terminology... 4 Password Sources... 5 Creating a new Password Source... 5 Security Policies...
Corporate and Payment Card Industry (PCI) compliance
 Citrix GoToMyPC Corporate and Payment Card Industry (PCI) compliance GoToMyPC Corporate provides industryleading configurable security controls and centralized endpoint management that can be implemented
Citrix GoToMyPC Corporate and Payment Card Industry (PCI) compliance GoToMyPC Corporate provides industryleading configurable security controls and centralized endpoint management that can be implemented
Virtual Code Authentication User Guide for Administrators
 Virtual Code Authentication User Guide for Administrators Virtual Code Authentication - User Guide for Administrators Document No.: 05-001 2001-2015 All rights reserved. Under copyright laws, this document
Virtual Code Authentication User Guide for Administrators Virtual Code Authentication - User Guide for Administrators Document No.: 05-001 2001-2015 All rights reserved. Under copyright laws, this document
Configuring Settings on the Cisco Unified Wireless IP Phone 7925G
 CHAPTER 5 Configuring Settings on the Cisco Unified Wireless IP Phone 7925G This chapter describes the available configuration settings on the Cisco Unified Wireless IP Phone 7925G. It contains the following
CHAPTER 5 Configuring Settings on the Cisco Unified Wireless IP Phone 7925G This chapter describes the available configuration settings on the Cisco Unified Wireless IP Phone 7925G. It contains the following
Customer Tips. Configuring Color Access on the WorkCentre 7328/7335/7345 using Windows Active Directory. for the user. Overview
 Xerox Multifunction Devices Customer Tips February 13, 2008 This document applies to the stated Xerox products. It is assumed that your device is equipped with the appropriate option(s) to support the
Xerox Multifunction Devices Customer Tips February 13, 2008 This document applies to the stated Xerox products. It is assumed that your device is equipped with the appropriate option(s) to support the
Employee Self Service Guide
 Introduction The PDS Employee Self Service Portal (ESS) is an interactive web based tool allowing you to view and mange critical information about you, your benefits, and your compensation. The Portal
Introduction The PDS Employee Self Service Portal (ESS) is an interactive web based tool allowing you to view and mange critical information about you, your benefits, and your compensation. The Portal
Outlook Express IMAP Instructions - Bloomsburg University Students
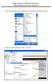 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
