Web cluster alternatives
|
|
|
- Cuthbert Sharp
- 9 years ago
- Views:
Transcription
1 Web cluster alternatives Web cluster Web switch Layer 4 (TCP) Web switch Layer 7 (HTTP) Two-way One-way Two-way One-way TCP gateway TCP splicing TCP handoff TCP conn. hop Packet rewriting Packet tunneling Packet forwarding 1.83 Layer 4 Web switch Layer 4 Web switch works at TCP/IP level Mapping on a per-connection basis Packets pertaining to the same TCP connection must be assigned to the same machine Binding table maintained by the Web switch to associate each active connection with the assigned The Web switch examines the header of each incoming packet new connection (SYN bit) new assignment existing connection lookup in the binding table Each connection requires about 32 bytes of information in the binding table 1.84
2 Two-way architecture Packet rewriting technique HTTP 1 HTTP 2 HTTP 3 Client browser INTERNET (VIP) Web switch LAN Application Servers DB s 1.85 Layer 4 Two way Packet rewriting Packet rewriting is based on the IP Network Address Translation (NAT) technique [K. Egevang, P. Francis, The IP Network Address Translator (NAT), RFC 1631, May 1994] Each internal has its own private IP address Outbound packets must pass back through the Web switch The Web switch dynamically modifies both inbound and outbound IP packets IP destination address in inbound packet (VIP IP address) IP source address in outbound packet (IP VIP) IP and TCP checksum recalculation 1.86
3 One-way architecture Packet rewriting Packet tunneling Packet forwarding Web 1 Web 2 Web 3 Client browser INTERNET (VIP) Web switch LAN Application Servers DB s 1.87 Layer 4 One way Packet rewriting Outbound packets do not need to pass back through the Web switch A separate high-bandwidth connection can be used for outbound packets Each internal has its own unique IP address The Web switch modifies only inbound IP packets IP destination address in inbound packet (VIP IP ) IP and TCP checksum recalculation The HTTP modifies outbound IP packets IP source address in outbound packet (IP VIP) IP and TCP checksum recalculation Modifications of the kernel (TCP/IP stack) 1.88
4 Layer 4 One way Packet tunneling IP tunneling (or IP encapsulation) is a technique to encapsulate IP datagrams within IP datagrams. The effect is to transform the old headers and data into the payload of the new packet The Web switch tunnels the inbound packet destined to the VIP address to the HTTP by encapsulating it within an IP datagram When the target receives the encapsulated packet it strips the IP header off and finds that the inside packet is destined to the VIP address it processes the request and returns the response directly to the client by using VIP as the source address 1.89 Layer 4 One way Packet forwarding Clever idea! PRO: Little overhead per packet CON: Web switch and HTTP s must be on the same physical network segment There is no modification of inbound/outbound packets at TCP/IP layers Packets are forwarded from the Web switch to an HTTP and vice versa at the MAC level (through a redirection of the MAC frames) 1.90
5 Layer 4 One way Packet forwarding The same VIP address is shared by the Web switch and the s through the use of primary ( switch) and secondary IP addresses ( HTTP s) Even if all nodes share the VIP address, the inbound packets reach the Web switch because, to avoid collisions, the nodes disable ARP The private addresses are now at the MAC layer (packet forwarding = MAC address translation) The Web switch forwards an inbound packet to a by writing the MAC address in the layer 2 destination address and re-transmitting the frame on the shared LAN segment Since all nodes share the same VIP address, the with the right MAC address can recognize itself as a destination and can respond directly to the client 1.91 Prototypes/Products (layer 4 clusters) Two-way One-way Packet rewriting Packet rewriting Packet tunneling Packet forwarding Cisco s LocalDirector Magicrouter Foundry Networks ServerIron Alteon WebSystems LSNAT Linux Virtual Server F5 Networks BIG/ip HydraWebTechs Coyote Point Systems Equalizer Radware s WSD IBM TCP router Linux Virtual (LVS) IBM Network Dispatcher ONE-IP LSMAC Dispatcher BIG-IP F5 Networks LSMAC NetStructure Intel Traffic Director Alteon 180 Nortel Networks 2002 Radware Foundry Networks Server Iron 1.92
6 Web cluster alternatives Web cluster Web switch Layer 4 (TCP) Web switch Layer 7 (HTTP) Two-way One-way Two-way One-way TCP gateway TCP splicing TCP handoff TCP conn. hop Packet rewriting Packet tunneling Packet forwarding 1.93 Layer 7 Web switch Level 7 Web switch works at application level The Web switch must establish a connection with the client, and inspects the HTTP request content to decide about dispatching The switch parses HTTP header (URL, cookie) The switch manages inbound packets (ACK packets) 1.94
7 Layer 7 Two way TCP gateway On the Web switch is executed an application level proxy that mediates all communications between a client and a The Web switch: maintains a permanent TCP connection with each HTTP (for efficiency reasons) issues the same request to the selected HTTP Packets are forwarded by the Web switch at application level TCP gateway technique is affected by serious overhead Two TCP connections per HTTP request Way up and down through the protocol stack from/to the application layer 1.95 Communication through layer-7 switch data application transport network link physical Client network link physical router HTTP application transport network link physical application transport network link physical DISPATCHING application transport network link physical Web switch data application transport network link physical 1.96
8 Layer 7 Two way TCP splicing It is quite similar to the TCP gateway technique, but data are forwarded by the switch at network level Once the TCP connection between the client and the Web switch has been established and the persistent TCP connection between the switch and the target has been chosen, the two connections are spliced together ( joined ) IP packets are forwarded from one endpoint to the others without traversing the transport layer up to the application layer on the Web switch The Web switch kernel handles the subsequent packets by changing the IP and TCP packet headers so that both the client and HTTP can recognize these packets as destined to them It requires modifications at the kernel level 1.97 Layer 7 One way TCP handoff Permanent TCP connection between the Web switch and each HTTP The Web switch passes (handoff) the TCP connection established by the client with the Web switch to the HTTP, which can communicate directly with the client The TCP hand-off mechanism remains transparent to the client, as packets sent by the s appear to be coming from the Web switch Incoming traffic on already established connections (i.e., any ack packet sent by the client to the switch) is forwarded to the target by an efficient module of the Web switch The TCP hand-off mechanism requires consistent modifications to the switch and kernels 1.98
9 Layer 7 One way TCP connection hop This a software-based proprietary solution implemented by Resonate as a TCP-based encapsulation protocol It is executed at the network layer between the network interface card (NIC) driver and the s native TCP/IP stack Proprietary protocol Not enough information 1.99 Prototypes/Products (layer 7 clusters) Two-way One-way TCP gateway TCP splicing TCP handoff TCP conn. hop IBM Network Dispatcher HACC Nortel s Alteon Web Systems F5 BIG-IP Foundry Nets ServerIron ScalaServer ClubWeb* [by Weblab] Resonate s Central Dispatcher IBM Network Dispatcher Cisco CSS Radware WSD Zeus Load Balancer 1.100
10 DISPATCHING ALGORITHMS Decisions at the Web switch Client TCP/HTTP interactions Web switch (VIP) LAN HTTP s httpd 1. Access control 2. Request dispatching Both of them important for: - QoWS implementation - open space for reasearch Web application s Back-end s WEB CLUSTER servlet EJB 1.102
11 Web switch dispatching Mapping from VIP to actual address Hit/Page request distribution Fine grain control on request assignment Centralized control Layer 4 vs. Layer 7 operations Client SYN Layer 4 Web switch HTTP Client SYN Layer 7 Web switch HTTP SYN, ACK ACK HTTP request SYN, ACK ACK HTTP request (parsing) 1.104
12 Consequences on dispatching Layer 4 TCP connection Content blind dispatching Stateless and state-aware algorithms Layer 7 HTTP connection Content aware dispatching Stateless and state-aware algorithms Layer 7 Web switch properties Main features of content-aware dispatching (or content-based routing) allows content/type segregation on specialized s supports persistent connections facilitates caching mechanisms allows HTTP/1.1 requests to be assigned to different HTTP s 1.106
13 Layer 4 Web switch algorithms Layer 4 algorithms Information less Client info aware Server state aware Random Round Robin IP address TCP port Active conn. CPU/disk utiliz. Response time Client partition Weighted Round Robin Least loaded Static algorithms Random no information regarding the cluster state no history about previous assignments Round Robin (RR) no information regarding the cluster state history regarding only the previous assignment 1.108
14 Client info aware algorithms Client partition Request assignment based on client information in inbound packets Client IP address Client port Rough method to implement QoWS disciplines for individuals or group of clients (not users!) Server state aware algorithms Request assignment based on load info Least loaded ( AVOID!) Weighted Round-Robin (WRR) it allows configuration of weights as a function of load 1.110
15 Server state aware algorithms Possible metrics to evaluate load Input metrics: information get by the Web switch without cooperation, e.g., Active connections Server metrics: information get by the Web s and transmitted to the Web switch, e.g., CPU/Disk utilization, response time Forward metrics: information get directly by the Web switch, e.g., emulation of requests to Web s HTTP s Web application s Back-end s WEB CLUSTER Web switch (VIP) LAN httpd servlet EJB Layer 7 Web switch algorithms Layer 7 algorithms Client info aware Client info and state aware Cookie SSL id URL URL Active connections Session Id. Content partition CAP LARD 1.112
16 Client info aware algorithms Session identifiers HTTP requests with same SSL id or same cookie assigned to the same Goal: avoid multiple client identifications for the same session Content partition Content partitioned among s according to file type (HTML, image, dynamic content, audio, video, ) Goal: use specialized s for different contents Content partitioned among s according to file size (Thresholds may be chosen dynamically.) Goal: augment load balancing File space partitioned among the s through a hash function Goal: improve cache hit rate in Web s Client info aware algorithms Content Aware Partition (CAP Proc. WWW 2000) Resource classification according to the impact of HTTP requests on main Web components, e.g., Low impact (small-medium static files) Network bound (large file download) Disk bound (database queries) CPU bound ( secure requests) Cyclic assignment of each class of requests to Web s Goal: augment load sharing of component bound requests among Web s 1.114
17 Client and state aware algorithm Locality-Aware Request Distribution (LARD) First request for a given target assigned to the least loaded (metrics: number of active connections) Subsequent requests for the same target assigned to the previously selected Goal: improve locality (cache hit rate) in cache A A A A A Web A A A A C B C A A C B Level 7 Web switch C B C C B Web B C Final considerations (Web clusters) Alternative architettures Layer-4 Web switch (Content information blind) Layer-7 Web switch (Content information aware) Main pros Fine grain control on dispatching of client requests High internal availability High security High performance ( infinite performance?) 1.116
18 Web cluster power Client browser INTERNET HTTP (s) LAN (Presentation logic) 1. Is there any theoretical limit for adding new s? 2. Is there any practical limit for adding new s? Web application (s) Back-end (s) (Business logic) (Transaction / Data ) Limits? HTTP s Web application s Web switch (VIP) LAN No limit at the Presentation level No limit at the Business level Some limits at the Data level Back-end s WEB CLUSTER NO LIMIT?? INFINITE POWER?? 1.118
19 Single points of failure Internet connection Web switch Web cluster cons Maximum scalability bounded by Web switch capacity Internet access bandwidth System possibilities and network limits Web cluster throughput: 5 Mbps 85 Mbps W Network throughputs: T1 - T2: Large company to ISP 3.1/6.3 Mbps T3 - OC1: ISP to Internet infrastructure Mpbs OC3: Large company backbone Mbps OC12 - OC256: Internet backbones Gbps 1.120
20 Network bottlenecks Last mile Internet Core Peering point First mile Managing a popular Web site If your Web site is really popular Youcan afford larger investments You cannot take any kind of risks about availability Network Electrical power Road works Bad weather Unfaithful employee 1.122
21 SYSTEM (GEOGRAPHICAL DISTRIBUTION) Pressure on Web-based architectures Scale-up HW/SW improvements LAN Scale-out Sistemswith multiple s (Web/cache) WAN 1.124
22 Taxonomy Scalable Web systems Local distribution Global distribution Web cluster Mirror site Distributed s Distributed Web clusters Mirror site Information that is geographically replicated on multiple Web sites Web site addresses Multiple hostnames (e.g., ) One IP address for each site Dispatching left to users 1.126
23 Mirror sites Mars Polar Lander Mission Public Sector Mirror Sites Mirror site Site Address Load Capacity SDSC - USA Bandwidth Internet2 - USA Bandwidth NCSA - USA Bandwidth Mars Society - USA Bandwidth KSC - USA Bandwidth HIGP - USA Bandwidth Simple architecture, but Visibly replicated architecture It is very hard to maintain information consistency among mirror sites No way of controlling load distribution Hard to trace users Geographically distributed s If your Web site is really popular Do you think is a good choice to spread single saround the world? 1.128
24 Taxonomy Scalable Web systems Local distribution Global distribution Web cluster Mirror site Distributed s Distributed Web clusters Taxonomy Scalable Web systems Local distribution Global distribution Web cluster Mirror site Distributed s Distributed Web clusters Two-levels dispatching (DNS+ Web switch) Three-levels dispatching (DNS+ Web switch+ HTTP s) 1.130
25 Distributed Web clusters Web site realized on an architecture of geographically distributed Web clusters Web site addresses One hostname (e.g., ) One IP address for each Web cluster First level dispatching Authoritative DNS or other entity during the lookup phase Second level dispatching Web switchof the Web cluster selects one Third level dispatching Each Web may redirect the received request to another Distributed Web cluster Web switch Web switch Web switch Local DNS Web switch Authoritative DNS for
26 Dispatching mechanisms 1. DNS dispatching -- global 2. Web switch dispatching -- local 3. HTTP dispatching (HTTP redirection) -- local Distributed Web cluster (2-level dispatching) Web switch HTTP request Web switch Web object Web switch Local DNS ( ,TTL) Web switch Authoritative DNS for
27 Distributed Web cluster (3-level dispatching) Web switch Web switch First HTTP request Web object OR goto Web object Web switch Second HTTP request Local DNS ( ,TTL) Web switch Authoritative DNS for DNS dispatching The distributed Web cluster architectures implement global dispatching by intervening in the lookup phase of the address request: A client asks for the IP address of a Web corresponding to the hostname in the URL If the hostname is valid, it receives the couple (IP address, TimeToLive) The enhanced authoritative DNS of the Web site (or another entity that replaces or integrates the authoritative DNS) can use various dispatching policies to select the best Web cluster 1.136
28 Issues of DNS dispatching Typical issues Load spikes in some hours/days Additional issues Traffic depending on time zones Client distribution among Internet zones Proximity between client and Web Caching of [hostname-ip] at intermediate DNS s for TTL interval Issues of DNS dispatching Because of hostname - IP address caching, the DNS of highly popular Web sites controls only 5-7% of traffic reaching the s of the site [IBM source data] Unlike Web switch (controlling 100% traffic), the DNS should use sophisticated algorithms Nevertheless, all CDN architectures use some sort of DNS dispatching 1.138
29 Actions on TTL values Constant TTL Set TTL=0 to augment DNS control Drawbacks Not cooperative DNSes (name s may ignore very small TTL values <300 seconds) Browser caches Risk of overloading authoritative DNS Adaptive TTL Tailor TTL value adaptively for each address request by taking into account the popularity of client Internet domain and Web loads DNS dispatching algorithms DNS dispatching Information less Client info aware Server state aware Client and state aware Random RR Internet domain Least loaded Internet domain Server load Proximity Multi-tier RR Least residual load Adaptive TTL 1.140
30 Internet proximity Internet proximity is an interesting open issue Client- geographic proximity does not mean Internet proximity (round trip latency) Static information client IP address to determine Internet zone (geographical distance) hop count ( stable more than static information) network hops (e.g., traceroute) Autonomous System hops (routing table queries) It does not guarantee selection of the best connected Web, e.g., links are not created equal Internet proximity Dynamic evaluation of proximity round trip time (e.g., ping, tcping) available link bandwidth (e.g., cprobe) latency time of HTTP requests (request emulation) Additional time and traffic costs for evaluation A related open issue: Correlation between hop count and round trip time? Old measures: close to zero [Crovella 95] Recent measures: strong, reasonably strong 1.142
31 Addressing DNS dispatching issues Utilizing multiple level DNS dispatching CDN choice [-->] Integrating DNS dispatching with HTTP or Web switch global dispatching: HTTP redirection IP tunneling HTTP redirection The redirection mechanism is part of the HTTP protocol and is supported by current browser and software DNS and Web switch use centralized scheduling disciplines Redirection is a distributed scheduling policy, in which all Web nodes can participate in (re-)assigning requests Redirection is completely transparent to the user (not to the client!) 1.144
32 HTTP redirection message header HTTP OK status code Moved temporarily to a new location New location Redirection to an IP address (better performance) Redirection to an hostname Redirection policies - alternatives Trigger mechanism Centralized: DNS or other entity Distributed: any Web (typically when highly loaded) Selection policy (page requests to be redirected) all page requests (All) all page requests larger than a threshold (Size) all page requests with many embedded objects (Num) Location policy (choice of the new target Web cluster) Round Robin (RR) Hash function Least loaded (Load) Client-to- proximity (Prox) 1.146
33 Performance comparison Two-levels vs. Three-levels dispatching Which selection policy? Redirect-All vs. Redirect-Heavy Which location policy? Dispatching algorithms Level 1 (DNS): proximity Level 2 (Web switch): Weighted Round Robin Level 3 (Web s) Selection policy ( which page requests have to be redirected? ): Redirect all requests (All) Redirect heavy requests: Size, number of embedded objects (Num) Location policy ( towards which cluster? ): RoundRobin (RR) Least loaded cluster (Load) Cluster proximity (Prox) Performance results 2 level dispatching Size-based redirection Redirect-all policy 1.148
34 Performance results (2) Percentage of redirected requests Response time (90-percentile) Summary A third-level dispatching mechanism guarantees immediate actions to shift the load away from an overloaded Web cluster augments the Quality of Web-based Services because the percentage of client requests with guaranteed response time is much higher HTTP redirection is easy to implement but works for HTTP services only IP tunneling can be used when it is necessary to provide other services Limiting redirection to the heaviest requests (Redirect- Heavy) reduces the percentage of redirection to a small fraction of requests (about 5%) without deteriorating the response time achieved by Redirect-All policies 1.150
35 Comparison Distributed Web cluster (two-level dispatching) High control on load reaching the Web cluster Slow reaction to an overloaded Web cluster Distributed Web cluster (three-level dispatching) Immediate actions to shift the load away from an overloaded Web cluster Redirection valid only for HTTP services Summing up Scalable Web- systems are based on multiple platforms A dispatching mechanism to direct the client request to the best A dispatching algorithm to define the best An executor to carry out the scheduling algorithm and the relative mechanism 1.152
36 Web dispatching mechanisms Mechanism Executor Item Coarse Hostname resolution - Local dispatching - Global dispatching HTTP redirection - Local dispatching DNS / Other entity Web Session Page request Granularity control - Global dispatching Packet redirection - Local dispatching Web switch Hit / Page request Fine Web dispatching algorithms Static (information-less) Dynamic client info aware state aware client info and state aware Adaptive (not yet investigated) Low Level of information dependency High 1.154
37 SYSTEM (AFTER REPLICATION, CACHING) Pressure on Web-based architectures Scale-up HW/SW improvements LAN Scale-out Sistemswith multiple s (Web/cache) WAN 1.156
38 Proxy origin Intranet gateway After, cache repository Client1 Proxy HTTP Client k FIREWALL CONTENT CONSUMER Proxy Caching mechanisms CONTENT PROVIDER Web cluster + Reverse proxy Web cluster + Reverse proxy THIRD PARTIES ISP (content consumer side) cooperative proxy s Companies (content provider side) Content Delivery Network (CDN) 1.158
39 CONTENT CONSUMER Client1 Proxy (cache) Cache Hit Cache Miss HTTP Client k FIREWALL Virtual / Reverse proxy (CONTENT PROVIDER side) Client Virtual or Reverse proxy Web Web Virtual Web Pushing techniques 1.160
40 Possibility of spreading VS in different network regions (AS) Client Virtual Virtual Web Web Virtual Virtual Web Architecture for 1 million hits per minute Primary site (master) Primary site Reverse proxy or Secondary 1.162
41 Why few primary sites and thousands of secondary s? Manageability Alternative solution # primary s Performance # secondary s Push model ( Content provider manages everything) Content generator Primary sites Secondary s (cache s) Content consumer Master 1.164
42 Modello push (altre ipotesi di gestione) Content generator Primary sites Secondary s (cache s) Content consumer Master Replication and Caching Local distribution Global distribution Web cluster Web switch (livello 4) Web switch (livello 7) Content Provider Web multi-cluster 2 level Dispatching (DNS+ Web switch) 3 level Dispatching (DNS+ Web switch+ ) Cache Proxy (cooperative) Reverse proxy (virtual s) ISP Content Delivery Networks (CDN) Special companies 1.166
43 Web caching ISP Clients Web 1 AS AS Web Server 2 AS ISP proxy Web Server N Cooperativo Web caching (ISP) 1 Client 4 Cache miss proxy 2 proxy proxy proxy 3 Cache proxy hit proxy proxy Many alternative architectures (hierarchical, flat, hybrid) Many lookup algorithms Many cooperation algorithms proxy Web Server 1.168
44 Hierarchical vs. Flat scheme Hierarchical Flat Client Possible advantages of Web caching Latency reduction Less traffic Less overhead on Web sites But, many studies show that generalized Web caching has limited benefits (low cache hit rates) 1.170
45 Business alternative: content delivery Content delivery information delivery data delivery Content = digital material for which someone (user, ISP, content provider, ) can spend money Exemples Web embedded objects video-on-demand pay-per-download music software distribution pay-per-use software Web caching CDN Cooperative cache s Cache s distributed over many Internet regions (AS) Web caching is independent of Web site management Generalized caching: content of any Web site ISP can pay because they save bandwidth (content provider don t) Content provider outsources content distribution problems to CDN company Selective caching: just content of customer Web sites Content providers pay (ISP don t) 1.172
46 CDN Architecture Application level On-demand contents Streaming on-demand Streaming live Middleware level Data placement Content consistency Monitoring & Billing Network level Content/Service lookup Routing mechanisms Servers Web Media static secure streaming cache cache media cache Origin (s) Content s DNS s CDN routing through URL rewriting content Client content content content content content content HTML Page (URL) content Origin HTML page 1.174
47 Akamai example Twofold DNS resolution Origin content 6 content Client HTML file with modified URL 2 Local DNS 4 3 Low level DNS (CDN) Top level DNS (CDN) Does a CDN work? (their measures #1) Internet anomay 1.176
48 Does a CDN work? (their measures #2) Stripe: with CDN Cyan: without CDN Users leave Source: Keynote Systems, Inc Does a CDN work? (our measures #1) Distribuzione cumulativa with CDN without CDN Tr Tr* Tempo di risposta (sec) HTTP GET method is the larger contribution to the response time Bimodal effects for DNS resolution Distribuzione cumulativa Tempo di risposta (sec) Tr TDNS,p TDNS,I Tconn TGET 1.178
49 Does a CDN work? (our measures #2) Tr(media) Tr(mediana) Tr*(media) Tr*(mediana) CDNs work! Tempo di risposta (sec) :00 1:00 2:00 3:00 4:00 5:00 6:00 7:00 8:00 9:00 10:00 11:00 12:00 13:00 14:00 15:00 16:00 17:00 18:00 19:00 20:00 21:00 22:00 23:00 They can have limited effects on clients on narrow bandwidth connections Ora della giornata 1.179
CS514: Intermediate Course in Computer Systems
 : Intermediate Course in Computer Systems Lecture 7: Sept. 19, 2003 Load Balancing Options Sources Lots of graphics and product description courtesy F5 website (www.f5.com) I believe F5 is market leader
: Intermediate Course in Computer Systems Lecture 7: Sept. 19, 2003 Load Balancing Options Sources Lots of graphics and product description courtesy F5 website (www.f5.com) I believe F5 is market leader
GLOBAL SERVER LOAD BALANCING WITH SERVERIRON
 APPLICATION NOTE GLOBAL SERVER LOAD BALANCING WITH SERVERIRON Growing Global Simply by connecting to the Internet, local businesses transform themselves into global ebusiness enterprises that span the
APPLICATION NOTE GLOBAL SERVER LOAD BALANCING WITH SERVERIRON Growing Global Simply by connecting to the Internet, local businesses transform themselves into global ebusiness enterprises that span the
Server Traffic Management. Jeff Chase Duke University, Department of Computer Science CPS 212: Distributed Information Systems
 Server Traffic Management Jeff Chase Duke University, Department of Computer Science CPS 212: Distributed Information Systems The Server Selection Problem server array A server farm B Which server? Which
Server Traffic Management Jeff Chase Duke University, Department of Computer Science CPS 212: Distributed Information Systems The Server Selection Problem server array A server farm B Which server? Which
Load Balancing in Mobile IPv6 s Correspondent Networks with Mobility Agents
 Load Balancing in Mobile IPv6 s Correspondent Networks with Mobility Agents Albert Cabellos-Aparicio, Jordi Domingo Pascual Departament d Arquitectura de Computadors Universitat Politècnica de Catalunya
Load Balancing in Mobile IPv6 s Correspondent Networks with Mobility Agents Albert Cabellos-Aparicio, Jordi Domingo Pascual Departament d Arquitectura de Computadors Universitat Politècnica de Catalunya
Load Balancing in Mobile IPv6 s Correspondent Networks with Mobility Agents
 1 Load Balancing in Mobile IPv6 s Correspondent Networks with Mobility Agents Albert Cabellos-Aparicio, Jordi Domingo-Pascual Abstract A foreseeable scenario is where on the Internet Mobile IPv6 is deployed
1 Load Balancing in Mobile IPv6 s Correspondent Networks with Mobility Agents Albert Cabellos-Aparicio, Jordi Domingo-Pascual Abstract A foreseeable scenario is where on the Internet Mobile IPv6 is deployed
Lecture 3: Scaling by Load Balancing 1. Comments on reviews i. 2. Topic 1: Scalability a. QUESTION: What are problems? i. These papers look at
 Lecture 3: Scaling by Load Balancing 1. Comments on reviews i. 2. Topic 1: Scalability a. QUESTION: What are problems? i. These papers look at distributing load b. QUESTION: What is the context? i. How
Lecture 3: Scaling by Load Balancing 1. Comments on reviews i. 2. Topic 1: Scalability a. QUESTION: What are problems? i. These papers look at distributing load b. QUESTION: What is the context? i. How
Scalability Issues in Cluster Web Servers
 Scalability Issues in Cluster Web Servers Arkaitz Bitorika A dissertation submitted to the University of Dublin, in partial fulfillment of the requirements for the degree of Master of Science in Computer
Scalability Issues in Cluster Web Servers Arkaitz Bitorika A dissertation submitted to the University of Dublin, in partial fulfillment of the requirements for the degree of Master of Science in Computer
Content Delivery Networks
 Content Delivery Networks Terena 2000 ftp://ftpeng.cisco.com/sgai/t2000cdn.pdf Silvano Gai Cisco Systems, USA Politecnico di Torino, IT [email protected] Terena 2000 1 Agenda What are Content Delivery Networks?
Content Delivery Networks Terena 2000 ftp://ftpeng.cisco.com/sgai/t2000cdn.pdf Silvano Gai Cisco Systems, USA Politecnico di Torino, IT [email protected] Terena 2000 1 Agenda What are Content Delivery Networks?
Introduction. Linux Virtual Server for Scalable Network Services. Linux Virtual Server. 3-tier architecture of LVS. Virtual Server via NAT
 Linux Virtual Server for Scalable Network Services Wensong Zhang [email protected] Ottawa Linux Symposium 2000 July 22th, 2000 1 Introduction Explosive growth of the Internet The requirements for servers
Linux Virtual Server for Scalable Network Services Wensong Zhang [email protected] Ottawa Linux Symposium 2000 July 22th, 2000 1 Introduction Explosive growth of the Internet The requirements for servers
Advanced Computer Networks. Layer-7-Switching and Loadbalancing
 Oriana Riva, Department of Computer Science ETH Zürich Advanced Computer Networks 263-3501-00 Layer-7-Switching and Loadbalancing Patrick Stuedi, Qin Yin and Timothy Roscoe Spring Semester 2015 Outline
Oriana Riva, Department of Computer Science ETH Zürich Advanced Computer Networks 263-3501-00 Layer-7-Switching and Loadbalancing Patrick Stuedi, Qin Yin and Timothy Roscoe Spring Semester 2015 Outline
How To Understand The Power Of A Content Delivery Network (Cdn)
 Overview 5-44 5-44 Computer Networking 5-64 Lecture 8: Delivering Content Content Delivery Networks Peter Steenkiste Fall 04 www.cs.cmu.edu/~prs/5-44-f4 Web Consistent hashing Peer-to-peer CDN Motivation
Overview 5-44 5-44 Computer Networking 5-64 Lecture 8: Delivering Content Content Delivery Networks Peter Steenkiste Fall 04 www.cs.cmu.edu/~prs/5-44-f4 Web Consistent hashing Peer-to-peer CDN Motivation
Availability Digest. www.availabilitydigest.com. Redundant Load Balancing for High Availability July 2013
 the Availability Digest Redundant Load Balancing for High Availability July 2013 A large data center can comprise hundreds or thousands of servers. These servers must not only be interconnected, but they
the Availability Digest Redundant Load Balancing for High Availability July 2013 A large data center can comprise hundreds or thousands of servers. These servers must not only be interconnected, but they
Advanced Networking Technologies
 Advanced Networking Technologies Chapter 14 Navigating Content Networks (Acknowledgement: These slides have been prepared by Dr.-Ing. Markus Hofmann) Advanced Networking (SS 15): 14 Navigating Content
Advanced Networking Technologies Chapter 14 Navigating Content Networks (Acknowledgement: These slides have been prepared by Dr.-Ing. Markus Hofmann) Advanced Networking (SS 15): 14 Navigating Content
1. Comments on reviews a. Need to avoid just summarizing web page asks you for:
 1. Comments on reviews a. Need to avoid just summarizing web page asks you for: i. A one or two sentence summary of the paper ii. A description of the problem they were trying to solve iii. A summary of
1. Comments on reviews a. Need to avoid just summarizing web page asks you for: i. A one or two sentence summary of the paper ii. A description of the problem they were trying to solve iii. A summary of
CS 188/219. Scalable Internet Services Andrew Mutz October 8, 2015
 CS 188/219 Scalable Internet Services Andrew Mutz October 8, 2015 For Today About PTEs Empty spots were given out If more spots open up, I will issue more PTEs You must have a group by today. More detail
CS 188/219 Scalable Internet Services Andrew Mutz October 8, 2015 For Today About PTEs Empty spots were given out If more spots open up, I will issue more PTEs You must have a group by today. More detail
Direct Web Switch Routing with State Migration, TCP Masquerade, and Cookie Name Rewriting
 Direct Web Switch Routing with State Migration, TCP Masquerade, and Cookie Name Rewriting Ying-Dar Lin, Ping-Tsai Tsai, Po-Ching Lin, and Ching-Ming Tien Department of Computer and Information Science,
Direct Web Switch Routing with State Migration, TCP Masquerade, and Cookie Name Rewriting Ying-Dar Lin, Ping-Tsai Tsai, Po-Ching Lin, and Ching-Ming Tien Department of Computer and Information Science,
Network Security TCP/IP Refresher
 Network Security TCP/IP Refresher What you (at least) need to know about networking! Dr. David Barrera Network Security HS 2014 Outline Network Reference Models Local Area Networks Internet Protocol (IP)
Network Security TCP/IP Refresher What you (at least) need to know about networking! Dr. David Barrera Network Security HS 2014 Outline Network Reference Models Local Area Networks Internet Protocol (IP)
Understanding Slow Start
 Chapter 1 Load Balancing 57 Understanding Slow Start When you configure a NetScaler to use a metric-based LB method such as Least Connections, Least Response Time, Least Bandwidth, Least Packets, or Custom
Chapter 1 Load Balancing 57 Understanding Slow Start When you configure a NetScaler to use a metric-based LB method such as Least Connections, Least Response Time, Least Bandwidth, Least Packets, or Custom
Scalable Linux Clusters with LVS
 Scalable Linux Clusters with LVS Considerations and Implementation, Part I Eric Searcy Tag1 Consulting, Inc. [email protected] April 2008 Abstract Whether you are perusing mailing lists or reading
Scalable Linux Clusters with LVS Considerations and Implementation, Part I Eric Searcy Tag1 Consulting, Inc. [email protected] April 2008 Abstract Whether you are perusing mailing lists or reading
EECS 489 Winter 2010 Midterm Exam
 EECS 489 Winter 2010 Midterm Exam Name: This is an open-book, open-resources exam. Explain or show your work for each question. Your grade will be severely deducted if you don t show your work, even if
EECS 489 Winter 2010 Midterm Exam Name: This is an open-book, open-resources exam. Explain or show your work for each question. Your grade will be severely deducted if you don t show your work, even if
Load Balancing and Sessions. C. Kopparapu, Load Balancing Servers, Firewalls and Caches. Wiley, 2002.
 Load Balancing and Sessions C. Kopparapu, Load Balancing Servers, Firewalls and Caches. Wiley, 2002. Scalability multiple servers Availability server fails Manageability Goals do not route to it take servers
Load Balancing and Sessions C. Kopparapu, Load Balancing Servers, Firewalls and Caches. Wiley, 2002. Scalability multiple servers Availability server fails Manageability Goals do not route to it take servers
A Task-Based Adaptive-TTL approach for Web Server Load Balancing *
 A Task-Based Adaptive-TTL approach for Web Server Load Balancing * Devarshi Chatterjee Zahir Tari RMIT University School of Computer Science and IT Melbourne, Australia zahirt@cs cs.rmit.edu.au * Supported
A Task-Based Adaptive-TTL approach for Web Server Load Balancing * Devarshi Chatterjee Zahir Tari RMIT University School of Computer Science and IT Melbourne, Australia zahirt@cs cs.rmit.edu.au * Supported
Proxy Server, Network Address Translator, Firewall. Proxy Server
 Proxy Server, Network Address Translator, Firewall 1 Proxy Server 2 1 Introduction What is a proxy server? Acts on behalf of other clients, and presents requests from other clients to a server. Acts as
Proxy Server, Network Address Translator, Firewall 1 Proxy Server 2 1 Introduction What is a proxy server? Acts on behalf of other clients, and presents requests from other clients to a server. Acts as
Measuring the Web: Part I - - Content Delivery Networks. Prof. Anja Feldmann, Ph.D. Dr. Ramin Khalili Georgios Smaragdakis, PhD
 Measuring the Web: Part I - - Content Delivery Networks Prof. Anja Feldmann, Ph.D. Dr. Ramin Khalili Georgios Smaragdakis, PhD Acknowledgement Material presented in these slides is borrowed from presentajons
Measuring the Web: Part I - - Content Delivery Networks Prof. Anja Feldmann, Ph.D. Dr. Ramin Khalili Georgios Smaragdakis, PhD Acknowledgement Material presented in these slides is borrowed from presentajons
Building a Highly Available and Scalable Web Farm
 Page 1 of 10 MSDN Home > MSDN Library > Deployment Rate this page: 10 users 4.9 out of 5 Building a Highly Available and Scalable Web Farm Duwamish Online Paul Johns and Aaron Ching Microsoft Developer
Page 1 of 10 MSDN Home > MSDN Library > Deployment Rate this page: 10 users 4.9 out of 5 Building a Highly Available and Scalable Web Farm Duwamish Online Paul Johns and Aaron Ching Microsoft Developer
Communications and Networking
 Communications and Networking History and Background telephone system local area networks Internet architecture: what the pieces are and how they fit together names and addresses: what's your name and
Communications and Networking History and Background telephone system local area networks Internet architecture: what the pieces are and how they fit together names and addresses: what's your name and
Purpose-Built Load Balancing The Advantages of Coyote Point Equalizer over Software-based Solutions
 Purpose-Built Load Balancing The Advantages of Coyote Point Equalizer over Software-based Solutions Abstract Coyote Point Equalizer appliances deliver traffic management solutions that provide high availability,
Purpose-Built Load Balancing The Advantages of Coyote Point Equalizer over Software-based Solutions Abstract Coyote Point Equalizer appliances deliver traffic management solutions that provide high availability,
Alteon Global Server Load Balancing
 Alteon Global Server Load Balancing Whitepaper GSLB Operation Overview Major Components Distributed Site Monitoring Distributed Site State Protocol Internet Topology Awareness DNS Authoritative Name Server
Alteon Global Server Load Balancing Whitepaper GSLB Operation Overview Major Components Distributed Site Monitoring Distributed Site State Protocol Internet Topology Awareness DNS Authoritative Name Server
Single Pass Load Balancing with Session Persistence in IPv6 Network. C. J. (Charlie) Liu Network Operations Charter Communications
 Single Pass Load Balancing with Session Persistence in IPv6 Network C. J. (Charlie) Liu Network Operations Charter Communications Load Balancer Today o Load balancing is still in use today. It is now considered
Single Pass Load Balancing with Session Persistence in IPv6 Network C. J. (Charlie) Liu Network Operations Charter Communications Load Balancer Today o Load balancing is still in use today. It is now considered
Web Caching and CDNs. Aditya Akella
 Web Caching and CDNs Aditya Akella 1 Where can bottlenecks occur? First mile: client to its ISPs Last mile: server to its ISP Server: compute/memory limitations ISP interconnections/peerings: congestion
Web Caching and CDNs Aditya Akella 1 Where can bottlenecks occur? First mile: client to its ISPs Last mile: server to its ISP Server: compute/memory limitations ISP interconnections/peerings: congestion
Application Delivery Networking
 Application Delivery Networking. Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 [email protected] These slides and audio/video recordings of this class lecture are at: 8-1 Overview
Application Delivery Networking. Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 [email protected] These slides and audio/video recordings of this class lecture are at: 8-1 Overview
How To Run A Web Farm On Linux (Ahem) On A Single Computer (For Free) On Your Computer (With A Freebie) On An Ipv4 (For Cheap) Or Ipv2 (For A Free) (For
 Creating Web Farms with Linux (Linux High Availability and Scalability) Horms (Simon Horman) [email protected] October 2000 http://verge.net.au/linux/has/ http://ultramonkey.sourceforge.net/ Introduction:
Creating Web Farms with Linux (Linux High Availability and Scalability) Horms (Simon Horman) [email protected] October 2000 http://verge.net.au/linux/has/ http://ultramonkey.sourceforge.net/ Introduction:
Content Delivery Networks
 Content Delivery Networks Silvano Gai Cisco Systems, USA Politecnico di Torino, IT [email protected] 1 Agenda What are Content Delivery Networks? DNS based routing Server Load Balancing Content Routers Ethical
Content Delivery Networks Silvano Gai Cisco Systems, USA Politecnico di Torino, IT [email protected] 1 Agenda What are Content Delivery Networks? DNS based routing Server Load Balancing Content Routers Ethical
Scalable Web-Server Systems: Architectures, Models and Load Balancing Algorithms
 Scalable Web-Server Systems: Architectures, Models and Load Balancing Algorithms Michele Colajanni University of Modena, Italy, [email protected] Philip S. Yu T.J. Watson Research Center, NY, [email protected]
Scalable Web-Server Systems: Architectures, Models and Load Balancing Algorithms Michele Colajanni University of Modena, Italy, [email protected] Philip S. Yu T.J. Watson Research Center, NY, [email protected]
Content Distribution Networks (CDN)
 229 Content Distribution Networks (CDNs) A content distribution network can be viewed as a global web replication. main idea: each replica is located in a different geographic area, rather then in the
229 Content Distribution Networks (CDNs) A content distribution network can be viewed as a global web replication. main idea: each replica is located in a different geographic area, rather then in the
Content-Aware Load Balancing using Direct Routing for VOD Streaming Service
 Content-Aware Load Balancing using Direct Routing for VOD Streaming Service Young-Hwan Woo, Jin-Wook Chung, Seok-soo Kim Dept. of Computer & Information System, Geo-chang Provincial College, Korea School
Content-Aware Load Balancing using Direct Routing for VOD Streaming Service Young-Hwan Woo, Jin-Wook Chung, Seok-soo Kim Dept. of Computer & Information System, Geo-chang Provincial College, Korea School
Internet Content Distribution
 Internet Content Distribution Chapter 2: Server-Side Techniques (TUD Student Use Only) Chapter Outline Server-side techniques for content distribution Goals Mirrors Server farms Surrogates DNS load balancing
Internet Content Distribution Chapter 2: Server-Side Techniques (TUD Student Use Only) Chapter Outline Server-side techniques for content distribution Goals Mirrors Server farms Surrogates DNS load balancing
DEPLOYMENT GUIDE Version 1.1. DNS Traffic Management using the BIG-IP Local Traffic Manager
 DEPLOYMENT GUIDE Version 1.1 DNS Traffic Management using the BIG-IP Local Traffic Manager Table of Contents Table of Contents Introducing DNS server traffic management with the BIG-IP LTM Prerequisites
DEPLOYMENT GUIDE Version 1.1 DNS Traffic Management using the BIG-IP Local Traffic Manager Table of Contents Table of Contents Introducing DNS server traffic management with the BIG-IP LTM Prerequisites
Multicast-based Distributed LVS (MD-LVS) for improving. scalability and availability
 Multicast-based Distributed LVS (MD-LVS) for improving scalability and availability Haesun Shin, Sook-Heon Lee, and Myong-Soon Park Internet Computing Lab. Department of Computer Science and Engineering,
Multicast-based Distributed LVS (MD-LVS) for improving scalability and availability Haesun Shin, Sook-Heon Lee, and Myong-Soon Park Internet Computing Lab. Department of Computer Science and Engineering,
Internet Protocol: IP packet headers. vendredi 18 octobre 13
 Internet Protocol: IP packet headers 1 IPv4 header V L TOS Total Length Identification F Frag TTL Proto Checksum Options Source address Destination address Data (payload) Padding V: Version (IPv4 ; IPv6)
Internet Protocol: IP packet headers 1 IPv4 header V L TOS Total Length Identification F Frag TTL Proto Checksum Options Source address Destination address Data (payload) Padding V: Version (IPv4 ; IPv6)
SiteCelerate white paper
 SiteCelerate white paper Arahe Solutions SITECELERATE OVERVIEW As enterprises increases their investment in Web applications, Portal and websites and as usage of these applications increase, performance
SiteCelerate white paper Arahe Solutions SITECELERATE OVERVIEW As enterprises increases their investment in Web applications, Portal and websites and as usage of these applications increase, performance
architecture: what the pieces are and how they fit together names and addresses: what's your name and number?
 Communications and networking history and background telephone system local area networks Internet architecture: what the pieces are and how they fit together names and addresses: what's your name and
Communications and networking history and background telephone system local area networks Internet architecture: what the pieces are and how they fit together names and addresses: what's your name and
Internet Firewall CSIS 4222. Packet Filtering. Internet Firewall. Examples. Spring 2011 CSIS 4222. net15 1. Routers can implement packet filtering
 Internet Firewall CSIS 4222 A combination of hardware and software that isolates an organization s internal network from the Internet at large Ch 27: Internet Routing Ch 30: Packet filtering & firewalls
Internet Firewall CSIS 4222 A combination of hardware and software that isolates an organization s internal network from the Internet at large Ch 27: Internet Routing Ch 30: Packet filtering & firewalls
Lab 5 Explicit Proxy Performance, Load Balancing & Redundancy
 Lab 5 Explicit Proxy Performance, Load Balancing & Redundancy Objectives The purpose of this lab is to demonstrate both high availability and performance using virtual IPs coupled with DNS round robin
Lab 5 Explicit Proxy Performance, Load Balancing & Redundancy Objectives The purpose of this lab is to demonstrate both high availability and performance using virtual IPs coupled with DNS round robin
Content Delivery Networks (CDN) Dr. Yingwu Zhu
 Content Delivery Networks (CDN) Dr. Yingwu Zhu Web Cache Architecure Local ISP cache cdn Reverse Reverse Proxy Reverse Proxy Reverse Proxy Proxy L4 Switch Content Content Content Server Content Server
Content Delivery Networks (CDN) Dr. Yingwu Zhu Web Cache Architecure Local ISP cache cdn Reverse Reverse Proxy Reverse Proxy Reverse Proxy Proxy L4 Switch Content Content Content Server Content Server
DATA COMMUNICATOIN NETWORKING
 DATA COMMUNICATOIN NETWORKING Instructor: Ouldooz Baghban Karimi Course Book: Computer Networking, A Top-Down Approach, Kurose, Ross Slides: - Course book Slides - Slides from Princeton University COS461
DATA COMMUNICATOIN NETWORKING Instructor: Ouldooz Baghban Karimi Course Book: Computer Networking, A Top-Down Approach, Kurose, Ross Slides: - Course book Slides - Slides from Princeton University COS461
High-Performance IP Service Node with Layer 4 to 7 Packet Processing Features
 UDC 621.395.31:681.3 High-Performance IP Service Node with Layer 4 to 7 Packet Processing Features VTsuneo Katsuyama VAkira Hakata VMasafumi Katoh VAkira Takeyama (Manuscript received February 27, 2001)
UDC 621.395.31:681.3 High-Performance IP Service Node with Layer 4 to 7 Packet Processing Features VTsuneo Katsuyama VAkira Hakata VMasafumi Katoh VAkira Takeyama (Manuscript received February 27, 2001)
Request Routing, Load-Balancing and Fault- Tolerance Solution - MediaDNS
 White paper Request Routing, Load-Balancing and Fault- Tolerance Solution - MediaDNS June 2001 Response in Global Environment Simply by connecting to the Internet, local businesses transform themselves
White paper Request Routing, Load-Balancing and Fault- Tolerance Solution - MediaDNS June 2001 Response in Global Environment Simply by connecting to the Internet, local businesses transform themselves
Web Application Hosting Cloud Architecture
 Web Application Hosting Cloud Architecture Executive Overview This paper describes vendor neutral best practices for hosting web applications using cloud computing. The architectural elements described
Web Application Hosting Cloud Architecture Executive Overview This paper describes vendor neutral best practices for hosting web applications using cloud computing. The architectural elements described
VXLAN: Scaling Data Center Capacity. White Paper
 VXLAN: Scaling Data Center Capacity White Paper Virtual Extensible LAN (VXLAN) Overview This document provides an overview of how VXLAN works. It also provides criteria to help determine when and where
VXLAN: Scaling Data Center Capacity White Paper Virtual Extensible LAN (VXLAN) Overview This document provides an overview of how VXLAN works. It also provides criteria to help determine when and where
SSL Inspection Step-by-Step Guide. June 6, 2016
 SSL Inspection Step-by-Step Guide June 6, 2016 Key Drivers for Inspecting Outbound SSL Traffic Eliminate blind spots of SSL encrypted communication to/from the enterprise Maintaining information s communication
SSL Inspection Step-by-Step Guide June 6, 2016 Key Drivers for Inspecting Outbound SSL Traffic Eliminate blind spots of SSL encrypted communication to/from the enterprise Maintaining information s communication
Web Switching (Draft)
 Web Switching (Draft) Giuseppe Attardi, Università di Pisa Angelo Raffaele Meo, Politecnico di Torino January 2003 1. The Problem Web servers are becoming the primary interface to a number of services,
Web Switching (Draft) Giuseppe Attardi, Università di Pisa Angelo Raffaele Meo, Politecnico di Torino January 2003 1. The Problem Web servers are becoming the primary interface to a number of services,
Content Distribu-on Networks (CDNs)
 Content Distribu-on Networks (CDNs) Jennifer Rexford COS 461: Computer Networks Lectures: MW 10-10:0am in Architecture N101 hjp://www.cs.princeton.edu/courses/archive/spr12/cos461/ Second Half of the Course
Content Distribu-on Networks (CDNs) Jennifer Rexford COS 461: Computer Networks Lectures: MW 10-10:0am in Architecture N101 hjp://www.cs.princeton.edu/courses/archive/spr12/cos461/ Second Half of the Course
Load Balancing. Final Network Exam LSNAT. Sommaire. How works a "traditional" NAT? Un article de Le wiki des TPs RSM.
 Load Balancing Un article de Le wiki des TPs RSM. PC Final Network Exam Sommaire 1 LSNAT 1.1 Deployement of LSNAT in a globally unique address space (LS-NAT) 1.2 Operation of LSNAT in conjunction with
Load Balancing Un article de Le wiki des TPs RSM. PC Final Network Exam Sommaire 1 LSNAT 1.1 Deployement of LSNAT in a globally unique address space (LS-NAT) 1.2 Operation of LSNAT in conjunction with
Layer 4-7 Server Load Balancing. Security, High-Availability and Scalability of Web and Application Servers
 Layer 4-7 Server Load Balancing Security, High-Availability and Scalability of Web and Application Servers Foundry Overview Mission: World Headquarters San Jose, California Performance, High Availability,
Layer 4-7 Server Load Balancing Security, High-Availability and Scalability of Web and Application Servers Foundry Overview Mission: World Headquarters San Jose, California Performance, High Availability,
Distributed Systems. 23. Content Delivery Networks (CDN) Paul Krzyzanowski. Rutgers University. Fall 2015
 Distributed Systems 23. Content Delivery Networks (CDN) Paul Krzyzanowski Rutgers University Fall 2015 November 17, 2015 2014-2015 Paul Krzyzanowski 1 Motivation Serving web content from one location presents
Distributed Systems 23. Content Delivery Networks (CDN) Paul Krzyzanowski Rutgers University Fall 2015 November 17, 2015 2014-2015 Paul Krzyzanowski 1 Motivation Serving web content from one location presents
Chapter 12 Supporting Network Address Translation (NAT)
 [Previous] [Next] Chapter 12 Supporting Network Address Translation (NAT) About This Chapter Network address translation (NAT) is a protocol that allows a network with private addresses to access information
[Previous] [Next] Chapter 12 Supporting Network Address Translation (NAT) About This Chapter Network address translation (NAT) is a protocol that allows a network with private addresses to access information
FLEX: Load Balancing and Management Strategy for Scalable Web Hosting Service
 : Load Balancing and Management Strategy for Scalable Hosting Service Ludmila Cherkasova Hewlett-Packard Labs 1501 Page Mill Road,Palo Alto, CA 94303, USA e-mail:[email protected] Abstract is a new
: Load Balancing and Management Strategy for Scalable Hosting Service Ludmila Cherkasova Hewlett-Packard Labs 1501 Page Mill Road,Palo Alto, CA 94303, USA e-mail:[email protected] Abstract is a new
Radware AppDirector and Juniper Networks Secure Access SSL VPN Solution Implementation Guide
 Implementation Guide Radware AppDirector and Juniper Networks Secure Access SSL VPN Solution Implementation Guide Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408.745.2000
Implementation Guide Radware AppDirector and Juniper Networks Secure Access SSL VPN Solution Implementation Guide Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408.745.2000
The Ecosystem of Computer Networks. Ripe 46 Amsterdam, The Netherlands
 The Ecosystem of Computer Networks Ripe 46 Amsterdam, The Netherlands Silvia Veronese NetworkPhysics.com [email protected] September 2003 1 Agenda Today s IT challenges Introduction to Network
The Ecosystem of Computer Networks Ripe 46 Amsterdam, The Netherlands Silvia Veronese NetworkPhysics.com [email protected] September 2003 1 Agenda Today s IT challenges Introduction to Network
Internet Control Protocols Reading: Chapter 3
 Internet Control Protocols Reading: Chapter 3 ARP - RFC 826, STD 37 DHCP - RFC 2131 ICMP - RFC 0792, STD 05 1 Goals of Today s Lecture Bootstrapping an end host Learning its own configuration parameters
Internet Control Protocols Reading: Chapter 3 ARP - RFC 826, STD 37 DHCP - RFC 2131 ICMP - RFC 0792, STD 05 1 Goals of Today s Lecture Bootstrapping an end host Learning its own configuration parameters
Improving DNS performance using Stateless TCP in FreeBSD 9
 Improving DNS performance using Stateless TCP in FreeBSD 9 David Hayes, Mattia Rossi, Grenville Armitage Centre for Advanced Internet Architectures, Technical Report 101022A Swinburne University of Technology
Improving DNS performance using Stateless TCP in FreeBSD 9 David Hayes, Mattia Rossi, Grenville Armitage Centre for Advanced Internet Architectures, Technical Report 101022A Swinburne University of Technology
Category: Informational Juniper Networks, Inc. August 1998. Load Sharing using IP Network Address Translation (LSNAT)
 Network Working Group Request for Comments: 2391 Category: Informational P. Srisuresh Lucent Technologies D. Gan Juniper Networks, Inc. August 1998 Load Sharing using IP Network Address Translation (LSNAT)
Network Working Group Request for Comments: 2391 Category: Informational P. Srisuresh Lucent Technologies D. Gan Juniper Networks, Inc. August 1998 Load Sharing using IP Network Address Translation (LSNAT)
WAN Traffic Management with PowerLink Pro100
 Whitepaper WAN Traffic Management with PowerLink Pro100 Overview In today s Internet marketplace, optimizing online presence is crucial for business success. Wan/ISP link failover and traffic management
Whitepaper WAN Traffic Management with PowerLink Pro100 Overview In today s Internet marketplace, optimizing online presence is crucial for business success. Wan/ISP link failover and traffic management
Implementation, Simulation of Linux Virtual Server in ns-2
 Implementation, Simulation of Linux Virtual Server in ns-2 CMPT 885 Special Topics: High Performance Networks Project Final Report Yuzhuang Hu [email protected] ABSTRACT LVS(Linux Virtual Server) provides
Implementation, Simulation of Linux Virtual Server in ns-2 CMPT 885 Special Topics: High Performance Networks Project Final Report Yuzhuang Hu [email protected] ABSTRACT LVS(Linux Virtual Server) provides
Technical Support Information Belkin internal use only
 The fundamentals of TCP/IP networking TCP/IP (Transmission Control Protocol / Internet Protocols) is a set of networking protocols that is used for communication on the Internet and on many other networks.
The fundamentals of TCP/IP networking TCP/IP (Transmission Control Protocol / Internet Protocols) is a set of networking protocols that is used for communication on the Internet and on many other networks.
HyLARD: A Hybrid Locality-Aware Request Distribution Policy in Cluster-based Web Servers
 TANET2007 臺 灣 網 際 網 路 研 討 會 論 文 集 二 HyLARD: A Hybrid Locality-Aware Request Distribution Policy in Cluster-based Web Servers Shang-Yi Zhuang, Mei-Ling Chiang Department of Information Management National
TANET2007 臺 灣 網 際 網 路 研 討 會 論 文 集 二 HyLARD: A Hybrid Locality-Aware Request Distribution Policy in Cluster-based Web Servers Shang-Yi Zhuang, Mei-Ling Chiang Department of Information Management National
Overview. Securing TCP/IP. Introduction to TCP/IP (cont d) Introduction to TCP/IP
 Overview Securing TCP/IP Chapter 6 TCP/IP Open Systems Interconnection Model Anatomy of a Packet Internet Protocol Security (IPSec) Web Security (HTTP over TLS, Secure-HTTP) Lecturer: Pei-yih Ting 1 2
Overview Securing TCP/IP Chapter 6 TCP/IP Open Systems Interconnection Model Anatomy of a Packet Internet Protocol Security (IPSec) Web Security (HTTP over TLS, Secure-HTTP) Lecturer: Pei-yih Ting 1 2
Load Balancing Web Applications
 Mon Jan 26 2004 18:14:15 America/New_York Published on The O'Reilly Network (http://www.oreillynet.com/) http://www.oreillynet.com/pub/a/onjava/2001/09/26/load.html See this if you're having trouble printing
Mon Jan 26 2004 18:14:15 America/New_York Published on The O'Reilly Network (http://www.oreillynet.com/) http://www.oreillynet.com/pub/a/onjava/2001/09/26/load.html See this if you're having trouble printing
INTRODUCTION TO FIREWALL SECURITY
 INTRODUCTION TO FIREWALL SECURITY SESSION 1 Agenda Introduction to Firewalls Types of Firewalls Modes and Deployments Key Features in a Firewall Emerging Trends 2 Printed in USA. What Is a Firewall DMZ
INTRODUCTION TO FIREWALL SECURITY SESSION 1 Agenda Introduction to Firewalls Types of Firewalls Modes and Deployments Key Features in a Firewall Emerging Trends 2 Printed in USA. What Is a Firewall DMZ
DNS ROUND ROBIN HIGH-AVAILABILITY LOAD SHARING
 PolyServe High-Availability Server Clustering for E-Business 918 Parker Street Berkeley, California 94710 (510) 665-2929 wwwpolyservecom Number 990903 WHITE PAPER DNS ROUND ROBIN HIGH-AVAILABILITY LOAD
PolyServe High-Availability Server Clustering for E-Business 918 Parker Street Berkeley, California 94710 (510) 665-2929 wwwpolyservecom Number 990903 WHITE PAPER DNS ROUND ROBIN HIGH-AVAILABILITY LOAD
Global Server Load Balancing
 White Paper Overview Many enterprises attempt to scale Web and network capacity by deploying additional servers and increased infrastructure at a single location, but centralized architectures are subject
White Paper Overview Many enterprises attempt to scale Web and network capacity by deploying additional servers and increased infrastructure at a single location, but centralized architectures are subject
Chapter 8 Security Pt 2
 Chapter 8 Security Pt 2 IC322 Fall 2014 Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 All material copyright 1996-2012 J.F Kurose and K.W. Ross,
Chapter 8 Security Pt 2 IC322 Fall 2014 Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 All material copyright 1996-2012 J.F Kurose and K.W. Ross,
Computer Networks - CS132/EECS148 - Spring 2013 ------------------------------------------------------------------------------
 Computer Networks - CS132/EECS148 - Spring 2013 Instructor: Karim El Defrawy Assignment 2 Deadline : April 25 th 9:30pm (hard and soft copies required) ------------------------------------------------------------------------------
Computer Networks - CS132/EECS148 - Spring 2013 Instructor: Karim El Defrawy Assignment 2 Deadline : April 25 th 9:30pm (hard and soft copies required) ------------------------------------------------------------------------------
Cisco Integrated Services Routers Performance Overview
 Integrated Services Routers Performance Overview What You Will Learn The Integrated Services Routers Generation 2 (ISR G2) provide a robust platform for delivering WAN services, unified communications,
Integrated Services Routers Performance Overview What You Will Learn The Integrated Services Routers Generation 2 (ISR G2) provide a robust platform for delivering WAN services, unified communications,
DMZ Network Visibility with Wireshark June 15, 2010
 DMZ Network Visibility with Wireshark June 15, 2010 Ashok Desai Senior Network Specialist Intel Information Technology SHARKFEST 10 Stanford University June 14-17, 2010 Outline Presentation Objective DMZ
DMZ Network Visibility with Wireshark June 15, 2010 Ashok Desai Senior Network Specialist Intel Information Technology SHARKFEST 10 Stanford University June 14-17, 2010 Outline Presentation Objective DMZ
Outline. CSc 466/566. Computer Security. 18 : Network Security Introduction. Network Topology. Network Topology. Christian Collberg
 Outline Network Topology CSc 466/566 Computer Security 18 : Network Security Introduction Version: 2012/05/03 13:59:29 Department of Computer Science University of Arizona [email protected] Copyright
Outline Network Topology CSc 466/566 Computer Security 18 : Network Security Introduction Version: 2012/05/03 13:59:29 Department of Computer Science University of Arizona [email protected] Copyright
IP address format: Dotted decimal notation: 10000000 00001011 00000011 00011111 128.11.3.31
 IP address format: 7 24 Class A 0 Network ID Host ID 14 16 Class B 1 0 Network ID Host ID 21 8 Class C 1 1 0 Network ID Host ID 28 Class D 1 1 1 0 Multicast Address Dotted decimal notation: 10000000 00001011
IP address format: 7 24 Class A 0 Network ID Host ID 14 16 Class B 1 0 Network ID Host ID 21 8 Class C 1 1 0 Network ID Host ID 28 Class D 1 1 1 0 Multicast Address Dotted decimal notation: 10000000 00001011
Link Load Balancing 2015-04-28 08:50:44 UTC. 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement
 Link Load Balancing 2015-04-28 08:50:44 UTC 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents Link Load Balancing... 3 Link Load Balancing... 4 Configuring
Link Load Balancing 2015-04-28 08:50:44 UTC 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents Link Load Balancing... 3 Link Load Balancing... 4 Configuring
UNIVERSITY OF OSLO Department of Informatics. Performance Measurement of Web Services Linux Virtual Server. Muhammad Ashfaq Oslo University College
 UNIVERSITY OF OSLO Department of Informatics Performance Measurement of Web Services Linux Virtual Server Muhammad Ashfaq Oslo University College May 19, 2009 Performance Measurement of Web Services Linux
UNIVERSITY OF OSLO Department of Informatics Performance Measurement of Web Services Linux Virtual Server Muhammad Ashfaq Oslo University College May 19, 2009 Performance Measurement of Web Services Linux
ExamPDF. Higher Quality,Better service!
 ExamPDF Higher Quality,Better service! Q&A Exam : 1Y0-A21 Title : Basic Administration for Citrix NetScaler 9.2 Version : Demo 1 / 5 1.Scenario: An administrator is working with a Citrix consultant to
ExamPDF Higher Quality,Better service! Q&A Exam : 1Y0-A21 Title : Basic Administration for Citrix NetScaler 9.2 Version : Demo 1 / 5 1.Scenario: An administrator is working with a Citrix consultant to
Scalable Internet Services and Load Balancing
 Scalable Services and Load Balancing Kai Shen Services brings ubiquitous connection based applications/services accessible to online users through Applications can be designed and launched quickly and
Scalable Services and Load Balancing Kai Shen Services brings ubiquitous connection based applications/services accessible to online users through Applications can be designed and launched quickly and
Internet Content Distribution
 Internet Content Distribution Chapter 4: Content Distribution Networks (TUD Student Use Only) Chapter Outline Basics of content distribution networks (CDN) Why CDN? How do they work? Client redirection
Internet Content Distribution Chapter 4: Content Distribution Networks (TUD Student Use Only) Chapter Outline Basics of content distribution networks (CDN) Why CDN? How do they work? Client redirection
A Link Load Balancing Solution for Multi-Homed Networks
 A Link Load Balancing Solution for Multi-Homed Networks Overview An increasing number of enterprises are using the Internet for delivering mission-critical content and applications. By maintaining only
A Link Load Balancing Solution for Multi-Homed Networks Overview An increasing number of enterprises are using the Internet for delivering mission-critical content and applications. By maintaining only
Network Layers. CSC358 - Introduction to Computer Networks
 Network Layers Goal Understand how application processes set up a connection and exchange messages. Understand how addresses are determined Data Exchange Between Application Processes TCP Connection-Setup
Network Layers Goal Understand how application processes set up a connection and exchange messages. Understand how addresses are determined Data Exchange Between Application Processes TCP Connection-Setup
Network Simulation Traffic, Paths and Impairment
 Network Simulation Traffic, Paths and Impairment Summary Network simulation software and hardware appliances can emulate networks and network hardware. Wide Area Network (WAN) emulation, by simulating
Network Simulation Traffic, Paths and Impairment Summary Network simulation software and hardware appliances can emulate networks and network hardware. Wide Area Network (WAN) emulation, by simulating
High volume Internet data centers. MPLS-based Request Routing. Current dispatcher technology. MPLS-based architecture
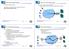 MPLS-based Request Routing High volume Internet data centers MPLS-based Request Routing Arup Acharya, Anees Shaikh, Renu Tewari, Dinesh Verma IBM TJ Watson Research Center Web server cluster + front-end
MPLS-based Request Routing High volume Internet data centers MPLS-based Request Routing Arup Acharya, Anees Shaikh, Renu Tewari, Dinesh Verma IBM TJ Watson Research Center Web server cluster + front-end
FortiBalancer: Global Server Load Balancing WHITE PAPER
 FortiBalancer: Global Server Load Balancing WHITE PAPER FORTINET FortiBalancer: Global Server Load Balancing PAGE 2 Introduction Scalability, high availability and performance are critical to the success
FortiBalancer: Global Server Load Balancing WHITE PAPER FORTINET FortiBalancer: Global Server Load Balancing PAGE 2 Introduction Scalability, high availability and performance are critical to the success
Creating Web Farms with Linux (Linux High Availability and Scalability)
 Creating Web Farms with Linux (Linux High Availability and Scalability) Horms (Simon Horman) [email protected] December 2001 For Presentation in Tokyo, Japan http://verge.net.au/linux/has/ http://ultramonkey.org/
Creating Web Farms with Linux (Linux High Availability and Scalability) Horms (Simon Horman) [email protected] December 2001 For Presentation in Tokyo, Japan http://verge.net.au/linux/has/ http://ultramonkey.org/
Introduction to LAN/WAN. Network Layer (part II)
 Introduction to LAN/WAN Network Layer (part II) Topics The Network Layer Introduction Routing (5.2) The Internet (5.5) IP, IP addresses ARP (5.5.4) OSPF (5.5.5) BGP (5.5.6) Congestion Control (5.3) Internetworking
Introduction to LAN/WAN Network Layer (part II) Topics The Network Layer Introduction Routing (5.2) The Internet (5.5) IP, IP addresses ARP (5.5.4) OSPF (5.5.5) BGP (5.5.6) Congestion Control (5.3) Internetworking
Chapter 2 TOPOLOGY SELECTION. SYS-ED/ Computer Education Techniques, Inc.
 Chapter 2 TOPOLOGY SELECTION SYS-ED/ Computer Education Techniques, Inc. Objectives You will learn: Topology selection criteria. Perform a comparison of topology selection criteria. WebSphere component
Chapter 2 TOPOLOGY SELECTION SYS-ED/ Computer Education Techniques, Inc. Objectives You will learn: Topology selection criteria. Perform a comparison of topology selection criteria. WebSphere component
Outline VLAN. Inter-VLAN communication. Layer-3 Switches. Spanning Tree Protocol Recap
 Outline Network Virtualization and Data Center Networks 263-3825-00 DC Virtualization Basics Part 2 Qin Yin Fall Semester 2013 More words about VLAN Virtual Routing and Forwarding (VRF) The use of load
Outline Network Virtualization and Data Center Networks 263-3825-00 DC Virtualization Basics Part 2 Qin Yin Fall Semester 2013 More words about VLAN Virtual Routing and Forwarding (VRF) The use of load
CLE202 Introduction to ServerIron ADX Application Switching and Load Balancing
 Introduction to ServerIron ADX Application Switching and Load Balancing Student Guide Revision : Introduction to ServerIron ADX Application Switching and Load Balancing Corporate Headquarters - San
Introduction to ServerIron ADX Application Switching and Load Balancing Student Guide Revision : Introduction to ServerIron ADX Application Switching and Load Balancing Corporate Headquarters - San
Application. Transport. Network. Data Link. Physical. Network Layers. Goal
 Layers Goal Understand how application processes set up a connection and exchange messages. Understand how addresses are determined 1 2 Data Exchange Between Processes TCP Connection-Setup Between Processes
Layers Goal Understand how application processes set up a connection and exchange messages. Understand how addresses are determined 1 2 Data Exchange Between Processes TCP Connection-Setup Between Processes
Firewalls. Ahmad Almulhem March 10, 2012
 Firewalls Ahmad Almulhem March 10, 2012 1 Outline Firewalls The Need for Firewalls Firewall Characteristics Types of Firewalls Firewall Basing Firewall Configurations Firewall Policies and Anomalies 2
Firewalls Ahmad Almulhem March 10, 2012 1 Outline Firewalls The Need for Firewalls Firewall Characteristics Types of Firewalls Firewall Basing Firewall Configurations Firewall Policies and Anomalies 2
