The RFID agenda of the European Commission. Florent Frederix European Commission Directorate General Information Society and Media
|
|
|
- Benedict Rogers
- 8 years ago
- Views:
Transcription
1 The RFID agenda of the European Commission RFID i Danmark 2011 May 3, 2011, IT-University in Copenhagen Florent Frederix European Commission Directorate General Information Society and Media This document does not necessarily reflect any official position of the Commission
2 Recommendation on RFID to member countries International cooperation on RFID and IoT The Privacy Impact Assessment Security of RFID applications RFID signage and emblem EU norm
3 The international dimension Share best practices/conferences OECD (2005, 2009) RFID/USN South Korea (October 2007) Exchanges with China (MOST2006, CESI 2009) FTC / DoC / DoD conferences ( ) Exchanges with Japan (METI ) Enhanced co-operation EU-US RFID lighthouse project (2008) Co-operation agreement with METI Japan Partnership of standards organisations under GRIFS project (EU / US / Japan / China / South Korea / )
4 Recommendation on RFID Small chips with big potential Recommendation on the implementation of privacy and data protection principles in applications supported by radiofrequency identification 12 th May 2009 (2009) 585
5 RFID Policy Mix Charter of Fundamentals Right E-Privacy Directive Data Protection Directive Recommendation Self-regulation Codes of Conduct R&TTE Directive Standardization
6 OBJECTIVE Promote: a wider take-up of RFID under lawful, ethical, socially and politically acceptable conditions the Internal Market
7 History (references) WG 29 Working document on data protection issues related to RFID technology Communication: Radio Frequency Identification (RFID) in Europe:steps towards a policy framework The Commission Decision setting up the RFID Expert Group Opinion of the European Economic and Social Committee on Radio Frequency Identification Results of the public online consultation on future RFID Technology Policy European Data Protection Supervisor adopted an opinion Recommendation on the privacy and data protection principles in applications supported by RFID
8 Operators RFID Recommendation: operator Similarity Data Protection Directive controller Difference
9 Application RFID Recommendation: application
10 PIA PIA from the UK Information Commissioner s Privacy Impact Assessment is usefully defined as a process whereby a project's potential privacy issues and risks are identified and examined from the perspectives of all stakeholders, and a search is undertaken for ways to avoid or minimise privacy concerns. Src.: The Information Commissioner's Office (UK)
11 who what what who why Information Security RFID applications with implications for the general public, are especially critical with regard to information security and privacy and therefore require specific attention. Member States Identify the applications that might raise information security threats with implications for the general public. Operators Develop new schemes i.e. certification. ENISA study on Airport applications (2010)
12 who what why Information and Transparency on RFID if the processing of data is to be fair, the data subject must be in a position to learn of the existence of a processing operation and, where data are collected from him, must be given accurate and full information Operators Src.: Data Protection Directive Develop and publish information policy for each of their application Use European sign: identity and a point of contact
13 Information and Transparency on RFID (emblem and signage standard) RFID Information Policy the identity and address of the operators the purpose of the application what data will be processed by the identity of the the application? operator(s) will personal data be processed? will the location of tags be + monitored? a summary of the PIA a point of contact for the likely privacy risks (if any) more information the measures that individuals can take to mitigate these risks
14 how who what why RFID in retail (I) Use of a European Sign if the processing of data is to be fair, the data subject must be in a position to learn of the existence of a processing operation and, where data are collected from him, must be given accurate and full information Src.: Data Protection Directive Retailers Inform individuals of the presence of tags in the products Not specified!
15 Examples in retail
16 how who what why RFID in retail (II) Tag deactivation RFID tags contain unique IDs attached to consumer products: if each tag has a unique ID, such identification can be used for surveillance purposes... Src.: EDPS opinion Retailers Deactivate or remove at the point of sale the tag unless consumer give their consent. Free of charge Immediately Consumer can verify
17 what RFID in retail (III) Tag deactivation Deactivation of the tags should be understood as any process that stops those interactions of a tag with its environment which do not require the active involvement of the consumer
18 how who what why RFID in retail (IV) Tag deactivation Some PIA will conclude that the application doesn t represent a likely threat to privacy or the protection of personal data Retailers Don t deactivate but make available an easy means to deactivate or remove the tags Free of charge Immediately & later
19 retailers are not operators what if what what RFID in retail (V) Tag deactivation Retailers Default No threat to privacy Opt-in Opt-out Retailer has no obligation Operator should determine whether tagged products sold to consumers through retailers who are not operators represent a likely threat to privacy or the protection of personal data, etc
20 what who why Awareness raising action and R&D Awareness RFID technology among the public and SME and spread the trust in this technology All stakeholders Inform and raise awareness among: Citizens SMEs Support security and privacy by design
21 Summary of follow up actions Privacy Impact Assessment Security applications Information policy, including signs/logos Retail specific provisions Awareness Raising Research and Development
22 RFID recommendation Follow-up what Develop PIA Framework who leads? Industry Security applications Development of signs Awareness Raising Members States Standardisation Organisations Member States Research and Development Member States Inform on actions taken Member States
23 RFID Follow-up Commission s role what Develop PIA Framework Security applications Development of signs report Follow-up Standards Support Closely Continue Member monitor with mandate Member funding States the is implementation States, research already to development innovation carry including the adopted activities work. of of through such and this the Recommendation, the development includes framework as i2010 the the RACE Committee development thematic through efforts and its effectiveness the through of regular network such Article signs meetings FP7 and (and 29 upcoming and Working FP8) inviting its impact Party all pilot interested projects on operators parties and to consumers report progress made Awareness Raising Research and Development Inform on actions taken Report on Recommendation
24 Standards (the standardisation mandate) - ensure compliance to recommendation - Interoperability - Economies of scale - Lowering entry barriers - Operational costs RFID standardisation mandate
25 For more information on IOT and RFID visit the policy pages of the European Commission: Access to an extensive library, events, links and news section
RECOMMENDATIONS COMMISSION
 16.5.2009 Official Journal of the European Union L 122/47 RECOMMENDATIONS COMMISSION COMMISSION RECOMMENDATION of 12 May 2009 on the implementation of privacy and data protection principles in applications
16.5.2009 Official Journal of the European Union L 122/47 RECOMMENDATIONS COMMISSION COMMISSION RECOMMENDATION of 12 May 2009 on the implementation of privacy and data protection principles in applications
COMMISSION OF THE EUROPEAN COMMUNITIES COMMISSION RECOMMENDATION. of 12.5.2009
 COMMISSION OF THE EUROPEAN COMMUNITIES Brussels, 12.5.2009 C(2009) 3200 final COMMISSION RECOMMENDATION of 12.5.2009 on the implementation of privacy and data protection principles in applications supported
COMMISSION OF THE EUROPEAN COMMUNITIES Brussels, 12.5.2009 C(2009) 3200 final COMMISSION RECOMMENDATION of 12.5.2009 on the implementation of privacy and data protection principles in applications supported
The definitions of Article 2 might be misleading, especially for the definition of public spaces.
 APRIL 2008 Position on European Commission consultation on "Draft Recommendation on the implementation of privacy, data protection and information security principles in applications supported by Radio
APRIL 2008 Position on European Commission consultation on "Draft Recommendation on the implementation of privacy, data protection and information security principles in applications supported by Radio
European Policy in support of the emerging Internet of Things
 European Policy in support of the emerging Internet of Things Dr. Florent Frederix, Head of Sector Information Society and Media European Commission This document does not necessarily reflect any official
European Policy in support of the emerging Internet of Things Dr. Florent Frederix, Head of Sector Information Society and Media European Commission This document does not necessarily reflect any official
2012 ISO TC46/SC4/WG11 N246
 RFID PRIVACY IN EUROPE Implications for Libraries Paul Chartier Convergent Software Ltd CILIP Conference, Nov 2012 ISO TC46/SC4/WG11 N246 Today s Presentation Broad Overview of the EU position A bit of
RFID PRIVACY IN EUROPE Implications for Libraries Paul Chartier Convergent Software Ltd CILIP Conference, Nov 2012 ISO TC46/SC4/WG11 N246 Today s Presentation Broad Overview of the EU position A bit of
Comments and Responses by FoeBuD for the EU Consultation on RFID, April 2008
 Comments and Responses by FoeBuD for the EU Consultation on RFID, April 2008 Article 1 - Scope 1. This Recommendation provides guidance to Member States and stakeholders on the design and operation of
Comments and Responses by FoeBuD for the EU Consultation on RFID, April 2008 Article 1 - Scope 1. This Recommendation provides guidance to Member States and stakeholders on the design and operation of
EU Policy on RFID & Privacy
 EU Policy on RFID & Privacy Developments 2007, Outlook 2008 Andreas Krisch http://www.edri.org/ http://www.unwatched.org/ 24C3, 30.12.2007 European Digital Rights (EDRi) Umbrella
EU Policy on RFID & Privacy Developments 2007, Outlook 2008 Andreas Krisch http://www.edri.org/ http://www.unwatched.org/ 24C3, 30.12.2007 European Digital Rights (EDRi) Umbrella
RFIDs and European Policies
 ICTSB Seminar on RFID Standardisation CEN/CENELEC Meeting Centre Brussels, Belgium RFIDs and European Policies Gérald SANTUCCI, Head of Unit gerald.santucci@ec.europa.eu European Commission Directorate
ICTSB Seminar on RFID Standardisation CEN/CENELEC Meeting Centre Brussels, Belgium RFIDs and European Policies Gérald SANTUCCI, Head of Unit gerald.santucci@ec.europa.eu European Commission Directorate
Privacy(and(Data( Protection( (Part(II(
 Privacy(Recap( Privacy(and(Data( Protection( (Part(II( KTH, Media Law Pam Storr O Legal requirements on data controller. Must consider: O why store personal data? O what personal data? O is the data correct
Privacy(Recap( Privacy(and(Data( Protection( (Part(II( KTH, Media Law Pam Storr O Legal requirements on data controller. Must consider: O why store personal data? O what personal data? O is the data correct
European Commission initiatives on e- and mhealth
 European Commission initiatives on e- and mhealth Fundamental Rights Forum, 22 June 2016 WG 24: E-health: improving rights fulfilment through innovation Claudia Prettner, Unit for Health and Well-Being,
European Commission initiatives on e- and mhealth Fundamental Rights Forum, 22 June 2016 WG 24: E-health: improving rights fulfilment through innovation Claudia Prettner, Unit for Health and Well-Being,
Approaches to Impact Assessment
 Approaches to Impact Assessment Roger Clarke Xamax Consultancy, Canberra Visiting Professor in Cyberspace Law & Policy, UNSW, Sydney Visiting Professor in Computer Science, ANU, Canberra http://www.rogerclarke.com/sos/ia-1401
Approaches to Impact Assessment Roger Clarke Xamax Consultancy, Canberra Visiting Professor in Cyberspace Law & Policy, UNSW, Sydney Visiting Professor in Computer Science, ANU, Canberra http://www.rogerclarke.com/sos/ia-1401
Guidelines on the Use of the Common European RFID Sign
 Guidelines on the Use of the Common European RFID Sign Final Version 15 January 2012 Disclaimer: This document has been prepared by Unit "Networked Enterprise and RFID" of the European Commission's Directorate
Guidelines on the Use of the Common European RFID Sign Final Version 15 January 2012 Disclaimer: This document has been prepared by Unit "Networked Enterprise and RFID" of the European Commission's Directorate
The RFID Revolution: Your voice on the Challenges, Opportunities and Threats. Online Public Consultation Preliminary Overview of the Results
 The RFID Revolution: Your voice on the Challenges, Opportunities and Threats Online Public Consultation Preliminary Overview of the Results 16 October 2006 Disclaimer: This document is a working document
The RFID Revolution: Your voice on the Challenges, Opportunities and Threats Online Public Consultation Preliminary Overview of the Results 16 October 2006 Disclaimer: This document is a working document
RESOLUTION ON RADIO-FREQUENCY IDENTIFICATION (RFID)
 DOC NO. INTERNET-31-05 DATE ISSUED: APRIL, 2005 RESOLUTION ON RADIO-FREQUENCY IDENTIFICATION (RFID) Introduction The Trans Atlantic Consumer Dialogue (TACD) believes action is urgently needed to address
DOC NO. INTERNET-31-05 DATE ISSUED: APRIL, 2005 RESOLUTION ON RADIO-FREQUENCY IDENTIFICATION (RFID) Introduction The Trans Atlantic Consumer Dialogue (TACD) believes action is urgently needed to address
Privacy and Data Protection Impact Assessment Framework for RFID Applications. 12 January 2011
 Privacy and Data Protection Impact Assessment Framework for RFID Applications 12 January 2011 1 INDEX 1. Introduction...3 1.1. Key Concepts...4 1.2. Internal Procedures...5 2. The PIA Process...6 2.1.
Privacy and Data Protection Impact Assessment Framework for RFID Applications 12 January 2011 1 INDEX 1. Introduction...3 1.1. Key Concepts...4 1.2. Internal Procedures...5 2. The PIA Process...6 2.1.
Prof. Udo Helmbrecht
 Prof. Udo Helmbrecht Guiding EU Cybersecurity from Policy to Implementation Udo Helmbrecht Executive Director Information Security for the Public Sector 2015 Stockholm 02/09/15 European Union Agency for
Prof. Udo Helmbrecht Guiding EU Cybersecurity from Policy to Implementation Udo Helmbrecht Executive Director Information Security for the Public Sector 2015 Stockholm 02/09/15 European Union Agency for
Summary of feedback on Big data and data protection and ICO response
 Summary of feedback on Big data and data protection and ICO response Contents Introduction... 2 Question 1... 3 Impacts and benefits; privacy impact assessments (PIAs)... 3 New approaches to data protection...
Summary of feedback on Big data and data protection and ICO response Contents Introduction... 2 Question 1... 3 Impacts and benefits; privacy impact assessments (PIAs)... 3 New approaches to data protection...
EUROPEAN COMMISSION ENTERPRISE AND INDUSTRY DIRECTORATE-GENERAL. Space, Security and GMES Security Research and Development
 Ref. Ares(2011)193990-22/02/2011 EUROPEAN COMMISSION ENTERPRISE AND INDUSTRY DIRECTORATE-GENERAL Space, Security and GMES Security Research and Development Brussels, 17 th February 2011 M/487 EN PROGRAMMING
Ref. Ares(2011)193990-22/02/2011 EUROPEAN COMMISSION ENTERPRISE AND INDUSTRY DIRECTORATE-GENERAL Space, Security and GMES Security Research and Development Brussels, 17 th February 2011 M/487 EN PROGRAMMING
A. Background. In this Communication we can read:
 On RFID The Next Step to THE INTERNET OF THINGS Information of the Presidency 2832nd Council meeting, Competitiveness (Internal Market, Industry and Research), Brussels, 22-23 November 2007 A. Background
On RFID The Next Step to THE INTERNET OF THINGS Information of the Presidency 2832nd Council meeting, Competitiveness (Internal Market, Industry and Research), Brussels, 22-23 November 2007 A. Background
Privacy Guidelines for RFID Information Systems (RFID Privacy Guidelines)
 Privacy Guidelines for RFID Information Systems (RFID Privacy Guidelines) Information and Privacy Ann Cavoukian, Ph.D. Commissioner June 2006 Commissioner Ann Cavoukian gratefully acknowledges the work
Privacy Guidelines for RFID Information Systems (RFID Privacy Guidelines) Information and Privacy Ann Cavoukian, Ph.D. Commissioner June 2006 Commissioner Ann Cavoukian gratefully acknowledges the work
Internet of Things Value Proposition for Europe
 Internet of Things Value Proposition for Europe European Commission - DG CONNECT Dr Florent Frederix, (Online) Trust and Cybersecurity unit 7 th European Conference on ICT for Transport Logistics 5 th
Internet of Things Value Proposition for Europe European Commission - DG CONNECT Dr Florent Frederix, (Online) Trust and Cybersecurity unit 7 th European Conference on ICT for Transport Logistics 5 th
Speakers. Navigating Through The Legal Complexities And Cloudy Conditions To Implement A Successful Global OBA Program
 Speakers Navigating Through The Legal Complexities And Cloudy Conditions To Implement A Successful Global OBA Program Speakers: Ashlen Cherry, Americas Privacy Officer, Dell, ashlen_cherry@dell.com Ruth
Speakers Navigating Through The Legal Complexities And Cloudy Conditions To Implement A Successful Global OBA Program Speakers: Ashlen Cherry, Americas Privacy Officer, Dell, ashlen_cherry@dell.com Ruth
Internet Governance and Cybersecurity Patrick Curry MACCSA patrick.curry@maccsa.net
 Internet Governance and Cybersecurity Patrick Curry MACCSA patrick.curry@maccsa.net This project has received funding from the European Union s Seventh Framework Programme for research, technological development
Internet Governance and Cybersecurity Patrick Curry MACCSA patrick.curry@maccsa.net This project has received funding from the European Union s Seventh Framework Programme for research, technological development
RFID and Privacy Impact Assessment (PIA)
 URSI-France Journées scientifiques 25/26 mars 2014 Claude Tételin RFID and Privacy Impact Assessment (PIA) Centre National de Référence RFID, ctetelin@centrenational-rfid.com Mots clés : RFID, privacy,
URSI-France Journées scientifiques 25/26 mars 2014 Claude Tételin RFID and Privacy Impact Assessment (PIA) Centre National de Référence RFID, ctetelin@centrenational-rfid.com Mots clés : RFID, privacy,
Best Practices at Research Level
 PReparing Industry to Privacy-by-design by supporting its Application in REsearch Best Practices at Research Level Hisain Elshaafi Telecommunications Software and Systems Group (TSSG) Waterford Institute
PReparing Industry to Privacy-by-design by supporting its Application in REsearch Best Practices at Research Level Hisain Elshaafi Telecommunications Software and Systems Group (TSSG) Waterford Institute
EU Cybersecurity: Ensuring Trust in the European Digital Economy
 EU Cybersecurity: Ensuring Trust in the European Digital Economy Synthesis of the FIC Breakfast-Debate 15 October 2013, Brussels With the participation of Tunne Kelam Member of the European Parliament'
EU Cybersecurity: Ensuring Trust in the European Digital Economy Synthesis of the FIC Breakfast-Debate 15 October 2013, Brussels With the participation of Tunne Kelam Member of the European Parliament'
How To Write An Article On The European Cyberspace Policy And Security Strategy
 EU Cybersecurity Policy & Legislation ENISA s Contribution Steve Purser Head of Core Operations Oslo 26 May 2015 European Union Agency for Network and Information Security Agenda 01 Introduction to ENISA
EU Cybersecurity Policy & Legislation ENISA s Contribution Steve Purser Head of Core Operations Oslo 26 May 2015 European Union Agency for Network and Information Security Agenda 01 Introduction to ENISA
In which new or innovative ways do you think RPAS will be used in the future?
 Written evidence Submitted by Trilateral Research & Consulting On the House of Lords Select Committee on the European Union call for evidence on Civil use of remotely piloted aircraft systems (RPAS) in
Written evidence Submitted by Trilateral Research & Consulting On the House of Lords Select Committee on the European Union call for evidence on Civil use of remotely piloted aircraft systems (RPAS) in
ROADMAP. A Pan-European framework for electronic identification, authentication and signature
 TITLE OF THE INITIATIVE ROADMAP A Pan-European framework for electronic identification, authentication and signature TYPE OF INITIATIVE CWP Non-CWP Implementing act/delegated act LEAD DG RESPONSIBLE UNIT
TITLE OF THE INITIATIVE ROADMAP A Pan-European framework for electronic identification, authentication and signature TYPE OF INITIATIVE CWP Non-CWP Implementing act/delegated act LEAD DG RESPONSIBLE UNIT
ENISA workshop on Security Certification of ICT products in Europe
 ENISA workshop on Security Certification of ICT products in Europe Introduction On 16th of March 2016 ENISA organised a workshop aiming at bringing together stakeholders from the ICT security certification
ENISA workshop on Security Certification of ICT products in Europe Introduction On 16th of March 2016 ENISA organised a workshop aiming at bringing together stakeholders from the ICT security certification
Questions & Answers clarifying key aspects of the SEPA Cards Framework
 Doc. EPC075-08 (Version 10.0) 11 June 2008 Questions & Answers clarifying key aspects of the SEPA Cards Framework Circulation: Publicly available Restricted: No SEPA a Guide to the Single Euro Payments
Doc. EPC075-08 (Version 10.0) 11 June 2008 Questions & Answers clarifying key aspects of the SEPA Cards Framework Circulation: Publicly available Restricted: No SEPA a Guide to the Single Euro Payments
Tesco: use of IT and information systems
 Student Self-administered case study Tesco: use of IT and information systems Introduction to MIS Case duration (Min): 45-60 Management Information Systems (MIS) Introduction to MIS Business functions
Student Self-administered case study Tesco: use of IT and information systems Introduction to MIS Case duration (Min): 45-60 Management Information Systems (MIS) Introduction to MIS Business functions
Demystifying cloud computing for SMEs
 Demystifying cloud computing for SMEs Tools & Guides for SMEs moving to the Cloud Silvana Muscella, Founder and CEO Trust-IT Services Ltd s.muscella@trust-itservices.com @silvanamuscella www.cloudwatchhub.eu
Demystifying cloud computing for SMEs Tools & Guides for SMEs moving to the Cloud Silvana Muscella, Founder and CEO Trust-IT Services Ltd s.muscella@trust-itservices.com @silvanamuscella www.cloudwatchhub.eu
Unleashing the Potential of Cloud Computing in Europe - What is it and what does it mean for me?
 EUROPEAN COMMISSION MEMO Brussels, 27 September 2012 Unleashing the Potential of Cloud Computing in Europe - What is it and what does it mean for me? See also IP/12/1025 What is Cloud Computing? Cloud
EUROPEAN COMMISSION MEMO Brussels, 27 September 2012 Unleashing the Potential of Cloud Computing in Europe - What is it and what does it mean for me? See also IP/12/1025 What is Cloud Computing? Cloud
ICT WP 09-10 Obj. 1.3 Internet of Things and Enterprise Environments
 Call 5 NCP briefing 12th May 2009 ICT WP 09-10 Obj. 1.3 Internet of Things and Enterprise Environments Peter Friess, Project officer, Head of Cluster Alain Jaume, Deputy Head of Unit D4 Cristina Martinez,
Call 5 NCP briefing 12th May 2009 ICT WP 09-10 Obj. 1.3 Internet of Things and Enterprise Environments Peter Friess, Project officer, Head of Cluster Alain Jaume, Deputy Head of Unit D4 Cristina Martinez,
Bringing European values to the Internet of Things
 SPEECH/10/279 Neelie Kroes European Commissioner for Digital agenda Bringing European values to the Internet of Things 2 nd Annual Internet of Things Conference Brussels, 1 st June 2010 Ladies and gentlemen,
SPEECH/10/279 Neelie Kroes European Commissioner for Digital agenda Bringing European values to the Internet of Things 2 nd Annual Internet of Things Conference Brussels, 1 st June 2010 Ladies and gentlemen,
Value of the EU Data Protection Reform against the Big Data challenges. Keynote address 5th European Data Protection Days Berlin, 4.5.
 Value of the EU Data Protection Reform against the Big Data challenges Keynote address 5th European Data Protection Days Berlin, 4.5.2015 Giovanni Buttarelli European Data Protection Supervisor (Check
Value of the EU Data Protection Reform against the Big Data challenges Keynote address 5th European Data Protection Days Berlin, 4.5.2015 Giovanni Buttarelli European Data Protection Supervisor (Check
EU Priorities in Cybersecurity. Steve Purser Head of Core Operations Department June 2013
 EU Priorities in Cybersecurity Steve Purser Head of Core Operations Department June 2013 Agenda About ENISA The EU Cyber Security Strategy Protecting Critical Information Infrastructure National & EU Cyber
EU Priorities in Cybersecurity Steve Purser Head of Core Operations Department June 2013 Agenda About ENISA The EU Cyber Security Strategy Protecting Critical Information Infrastructure National & EU Cyber
Information Security Seminar 2013
 Information Security Seminar 2013 Mr. Victor Lam, JP Deputy Government Chief Information Officer Office of the Government Chief Information Officer The Government of the Hong Kong Special Administrative
Information Security Seminar 2013 Mr. Victor Lam, JP Deputy Government Chief Information Officer Office of the Government Chief Information Officer The Government of the Hong Kong Special Administrative
BCS, The Chartered Institute for IT Consultation Response to:
 BCS, The Chartered Institute for IT Consultation Response to: A Comprehensive Approach to Personal Data Protection in the European Union Dated: 15 January 2011 BCS The Chartered Institute for IT First
BCS, The Chartered Institute for IT Consultation Response to: A Comprehensive Approach to Personal Data Protection in the European Union Dated: 15 January 2011 BCS The Chartered Institute for IT First
Privacy by Design. Ian Brown, Prof. of Information Security and Privacy Oxford Internet Institute, University of Oxford @IanBrownOII
 Privacy by Design Ian Brown, Prof. of Information Security and Privacy Oxford Internet Institute, University of Oxford @IanBrownOII Privacy by Design principles 1. Proactive not Reactive; Preventative
Privacy by Design Ian Brown, Prof. of Information Security and Privacy Oxford Internet Institute, University of Oxford @IanBrownOII Privacy by Design principles 1. Proactive not Reactive; Preventative
The Information Commissioner s Office response to HM Treasury s Call for Evidence on Data Sharing and Open Data in Banking
 The Information Commissioner s Office response to HM Treasury s Call for Evidence on Data Sharing and Open Data in Banking The Information Commissioner has responsibility for promoting and enforcing the
The Information Commissioner s Office response to HM Treasury s Call for Evidence on Data Sharing and Open Data in Banking The Information Commissioner has responsibility for promoting and enforcing the
8970/15 FMA/AFG/cb 1 DG G 3 C
 Council of the European Union Brussels, 19 May 2015 (OR. en) 8970/15 NOTE RECH 141 TELECOM 119 COMPET 228 IND 80 From: Permanent Representatives Committee (Part 1) To: Council No. prev. doc.: 8583/15 RECH
Council of the European Union Brussels, 19 May 2015 (OR. en) 8970/15 NOTE RECH 141 TELECOM 119 COMPET 228 IND 80 From: Permanent Representatives Committee (Part 1) To: Council No. prev. doc.: 8583/15 RECH
Technical Guidelines RFID as Templates for the PIA- Framework
 Technical Guidelines RFID as Templates for the PIA- Framework Federal Office for Information Security (BSI) Postbox 20 03 63 53133 Bonn, Germany Tel.: +49 22899 9582-0 E-Mail: rfid@bsi.bund.de Internet:
Technical Guidelines RFID as Templates for the PIA- Framework Federal Office for Information Security (BSI) Postbox 20 03 63 53133 Bonn, Germany Tel.: +49 22899 9582-0 E-Mail: rfid@bsi.bund.de Internet:
Digitizing European Industry: Digital Industrial Platform Building
 Digitizing European Industry: Digital Industrial Platform Building EFFRA General Assembly Dr Max Lemke Head of Unit DG CONNECT A3 European Commission 1 The political context Speech of Commissioner Oettinger
Digitizing European Industry: Digital Industrial Platform Building EFFRA General Assembly Dr Max Lemke Head of Unit DG CONNECT A3 European Commission 1 The political context Speech of Commissioner Oettinger
Cooperation in Securing National Critical Infrastructure
 Cooperation in Securing National Critical Infrastructure Dr. Steve Purser Head of Core Operations Department European Network and Information Security Agency Agenda About ENISA Protecting Critical Information
Cooperation in Securing National Critical Infrastructure Dr. Steve Purser Head of Core Operations Department European Network and Information Security Agency Agenda About ENISA Protecting Critical Information
Horizon 2020 Secure Societies
 Horizon 2020 Secure Societies Khoen Liem Policy and Research in security DG Enterprise and Industry Vienna, 18 Nov. 2013i 2013 1 Security research & the 7 th Framework Programme (FP7) FP7-Security (2007-2013):
Horizon 2020 Secure Societies Khoen Liem Policy and Research in security DG Enterprise and Industry Vienna, 18 Nov. 2013i 2013 1 Security research & the 7 th Framework Programme (FP7) FP7-Security (2007-2013):
9360/15 FMA/AFG/cb 1 DG G 3 C
 Council of the European Union Brussels, 29 May 2015 (OR. en) 9360/15 OUTCOME OF PROCEEDINGS From: To: Council Delegations RECH 183 TELECOM 134 COMPET 288 IND 92 No. prev. doc.: 8970/15 RECH 141 TELECOM
Council of the European Union Brussels, 29 May 2015 (OR. en) 9360/15 OUTCOME OF PROCEEDINGS From: To: Council Delegations RECH 183 TELECOM 134 COMPET 288 IND 92 No. prev. doc.: 8970/15 RECH 141 TELECOM
Template for Automatic Number Plate Recognition (ANPR) Infrastructure Development Privacy Impact Assessment
 Template for Automatic Number Plate Recognition (ANPR) Infrastructure Development Privacy Impact Assessment This template is provided to support the police service and other law enforcement agencies (LEA)
Template for Automatic Number Plate Recognition (ANPR) Infrastructure Development Privacy Impact Assessment This template is provided to support the police service and other law enforcement agencies (LEA)
Reflection Paper of the Federal Government of Germany. From Berlin 2007 to Nice 2008 and Beyond: RFID Internet of Things Internet of the Future
 Reflection Paper of the Federal Government of Germany From Berlin 2007 to Nice 2008 and Beyond: RFID Internet of Things Internet of the Future Applications based on Radio Frequency Identification (RFID)
Reflection Paper of the Federal Government of Germany From Berlin 2007 to Nice 2008 and Beyond: RFID Internet of Things Internet of the Future Applications based on Radio Frequency Identification (RFID)
ICT Research in Norway The road ahead. Till Christopher Lech The Research Council of Norway
 ICT Research in Norway The road ahead Till Christopher Lech The Research Council of Norway, The remainder of this presentation: The view back The view on the present The view forward Public investments
ICT Research in Norway The road ahead Till Christopher Lech The Research Council of Norway, The remainder of this presentation: The view back The view on the present The view forward Public investments
Towards an RFID policy for Europe
 Towards an RFID policy for Europe Workshop report MAARTEN VAN DE VOORT ANDREAS LIGTVOET DRR-4046-EC 31 August 2006 Prepared for the EUROPEAN COMMISSION, Directorate General Information Society and Media
Towards an RFID policy for Europe Workshop report MAARTEN VAN DE VOORT ANDREAS LIGTVOET DRR-4046-EC 31 August 2006 Prepared for the EUROPEAN COMMISSION, Directorate General Information Society and Media
Resolution on Privacy Protection in Social Network Services
 30 th International Conference of Data Protection and Privacy Commissioners Strasbourg, 17 October 2008 Resolution on Privacy Protection in Social Network Services Proposer: Data Protection and Freedom
30 th International Conference of Data Protection and Privacy Commissioners Strasbourg, 17 October 2008 Resolution on Privacy Protection in Social Network Services Proposer: Data Protection and Freedom
FRAMEWORK FOR ADVANCING TRANSATLANTIC ECONOMIC INTEGRATION BETWEEN THE EUROPEAN UNION AND THE UNITED STATES OF AMERICA
 FRAMEWORK FOR ADVANCING TRANSATLANTIC ECONOMIC INTEGRATION BETWEEN THE EUROPEAN UNION AND THE UNITED STATES OF AMERICA We, leaders of the European Union and the United States of America: Believing that
FRAMEWORK FOR ADVANCING TRANSATLANTIC ECONOMIC INTEGRATION BETWEEN THE EUROPEAN UNION AND THE UNITED STATES OF AMERICA We, leaders of the European Union and the United States of America: Believing that
COMMISSION OF THE EUROPEAN COMMUNITIES
 EN EN EN COMMISSION OF THE EUROPEAN COMMUNITIES Brussels, [ ] COM(2006) 251 COMMUNICATION FROM THE COMMISSION TO THE COUNCIL, THE EUROPEAN PARLIAMENT, THE EUROPEAN ECONOMIC AND SOCIAL COMMITTEE AND THE
EN EN EN COMMISSION OF THE EUROPEAN COMMUNITIES Brussels, [ ] COM(2006) 251 COMMUNICATION FROM THE COMMISSION TO THE COUNCIL, THE EUROPEAN PARLIAMENT, THE EUROPEAN ECONOMIC AND SOCIAL COMMITTEE AND THE
Cloud Computing. by Civic Consulting (research conducted October 2011 January 2012)
 Cloud Computing by (research conducted October 2011 January 2012) for the European Parliament, DG Internal Policies of the Union, Directorate A (Economic and Scientific Policy); presentation for the EP
Cloud Computing by (research conducted October 2011 January 2012) for the European Parliament, DG Internal Policies of the Union, Directorate A (Economic and Scientific Policy); presentation for the EP
EUROPEAN DATA PROTECTION SUPERVISOR
 C 47/6 Official Journal of the European Union 25.2.2010 EUROPEAN DATA PROTECTION SUPERVISOR Opinion of the European Data Protection Supervisor on the Communication from the Commission on an Action Plan
C 47/6 Official Journal of the European Union 25.2.2010 EUROPEAN DATA PROTECTION SUPERVISOR Opinion of the European Data Protection Supervisor on the Communication from the Commission on an Action Plan
Position Paper e-regulation
 Position Paper e-regulation Ecommerce Europe s Proposal for Sustainable Growth of E-commerce in Europe www.ecommerce-europe.eu POSITION PAPER 3 Table of contents 1 Introduction 4 5.1.4 Harmonisation and
Position Paper e-regulation Ecommerce Europe s Proposal for Sustainable Growth of E-commerce in Europe www.ecommerce-europe.eu POSITION PAPER 3 Table of contents 1 Introduction 4 5.1.4 Harmonisation and
Horizon 2020 - ICT Call 2016 Topic Preview 5 th May 2015
 Horizon 2020 - ICT Call 206 Topic Preview 5 th May 205 Call Identifier: H2020-ICT-206 Call Publication: late Q3 205 Call Deadline: Q-2 206 (except for the instrument) Estimated budget for this call: 970
Horizon 2020 - ICT Call 206 Topic Preview 5 th May 205 Call Identifier: H2020-ICT-206 Call Publication: late Q3 205 Call Deadline: Q-2 206 (except for the instrument) Estimated budget for this call: 970
What is Quantified Self (QS)?
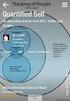 Subtitle Title Content Quantified Self (QS) (Sensitive) Personal data Security risks QS Privacy risks QS Art. 29 Working Party (WP29) on QS WP29 on ehealth WP29 on Internet of Things (IoT) QS data at risk
Subtitle Title Content Quantified Self (QS) (Sensitive) Personal data Security risks QS Privacy risks QS Art. 29 Working Party (WP29) on QS WP29 on ehealth WP29 on Internet of Things (IoT) QS data at risk
Privacy and Data Protection Impact Assessment Framework for RFID Applications. 12 January 2011
 Privacy and Data Protection Impact Assessment Framework for RFID Applications 12 January 2011 1 INDEX 1. Introduction...3 1.1. Key Concepts...4 1.2. Internal Procedures...5 2. The PIA Process...6 2.1.
Privacy and Data Protection Impact Assessment Framework for RFID Applications 12 January 2011 1 INDEX 1. Introduction...3 1.1. Key Concepts...4 1.2. Internal Procedures...5 2. The PIA Process...6 2.1.
Towards a data-driven economy in Europe
 Towards a data-driven economy in Europe Trusting Big Data Trust in the Digital World Conference 26 February 2015 Dr. Márta NAGY-ROTHENGASS Head of Unit CNECT.G3 (Data Value Chain) Why is data-driven economy
Towards a data-driven economy in Europe Trusting Big Data Trust in the Digital World Conference 26 February 2015 Dr. Márta NAGY-ROTHENGASS Head of Unit CNECT.G3 (Data Value Chain) Why is data-driven economy
How RFID can deliver benefits to the operating theatre A presentation to King's Fund Leadership Summit May 2013 Date Thursday 23rd May 2012 By Mark
 How RFID can deliver benefits to the operating theatre A presentation to King's Fund Leadership Summit May 2013 Date Thursday 23rd May 2012 By Mark Capel Synergy Health's, Group IT Director Overview What
How RFID can deliver benefits to the operating theatre A presentation to King's Fund Leadership Summit May 2013 Date Thursday 23rd May 2012 By Mark Capel Synergy Health's, Group IT Director Overview What
Automotive Oil & Fuel Filter Market
 http://www.gosreports.com Smart Label Market by Type (EAS, RFID, Sensing, & ESL), Tracking Application, Industry (Aerospace, Data Centre & Library, Food & Beverage, Healthcare & Pharmaceutical, Logistics,
http://www.gosreports.com Smart Label Market by Type (EAS, RFID, Sensing, & ESL), Tracking Application, Industry (Aerospace, Data Centre & Library, Food & Beverage, Healthcare & Pharmaceutical, Logistics,
Health Data Governance: Privacy, Monitoring and Research - Policy Brief
 Health Data Governance: Privacy, Monitoring and Research - Policy Brief October 2015 www.oecd.org/health Highlights All countries can improve their health information systems and make better use of data
Health Data Governance: Privacy, Monitoring and Research - Policy Brief October 2015 www.oecd.org/health Highlights All countries can improve their health information systems and make better use of data
Data Protection & Cyber Security Law Update 1 st October 2015
 Data Protection & Cyber Security Law Update 1 st October 2015 Robert Bond, Partner Janine Regan, Associate Viktoria Protokova, Data Protection Executive charlesrussellspeechlys.com Brief introduction to
Data Protection & Cyber Security Law Update 1 st October 2015 Robert Bond, Partner Janine Regan, Associate Viktoria Protokova, Data Protection Executive charlesrussellspeechlys.com Brief introduction to
Dr. Jehad Al Amri and Dr. Salha Al Zahrani 02/12/2013. Computing Ethics. Lecture 7 Privacy. Dr. Jehad Al Amri and Dr. Salha Al Zahrani 1
 Computing Ethics Lecture 7 Privacy Dr. Jehad Al Amri and Dr. Salha Al Zahrani 1 1 2 Outline Learning Outcomes Computer Revolution and Ethics TheConcept of Privacy Privacy concepts in different cultures
Computing Ethics Lecture 7 Privacy Dr. Jehad Al Amri and Dr. Salha Al Zahrani 1 1 2 Outline Learning Outcomes Computer Revolution and Ethics TheConcept of Privacy Privacy concepts in different cultures
Consent Receipts. Addressing the biggest lies which are: consent & notice
 Consent Receipts Addressing the biggest lies which are: consent & notice 1 What is a consent receipt? A consent receipt does what it says on the tin. It tracks consent by making a record of it. (Similar
Consent Receipts Addressing the biggest lies which are: consent & notice 1 What is a consent receipt? A consent receipt does what it says on the tin. It tracks consent by making a record of it. (Similar
HORIZON 2020. ENERGY context and Calls 2014/15. Ljubljana, 23 January 2014 THE EU FRAMEWORK PROGRAMME FOR RESEARCH AND INNOVATION
 THE EU FRAMEWORK PROGRAMME FOR RESEARCH AND INNOVATION HORIZON 2020 ENERGY context and Calls 2014/15 Ljubljana, 23 January 2014 Jeroen SCHUPPERS European Commission, DG Research and Innovation Europe's
THE EU FRAMEWORK PROGRAMME FOR RESEARCH AND INNOVATION HORIZON 2020 ENERGY context and Calls 2014/15 Ljubljana, 23 January 2014 Jeroen SCHUPPERS European Commission, DG Research and Innovation Europe's
Procurement Innovation for Cloud Services in Europe - PICSE
 Procurement Innovation for Cloud Services in Europe - PICSE Sara Garavelli, Trust-IT Services s.garavelli@trust-itservices.com ICT Proposer s Day, 9 October 2014, Florence, Italy 1 The road to PICSE Cloud
Procurement Innovation for Cloud Services in Europe - PICSE Sara Garavelli, Trust-IT Services s.garavelli@trust-itservices.com ICT Proposer s Day, 9 October 2014, Florence, Italy 1 The road to PICSE Cloud
TOWARDS A STRATEGIC NANOTECHNOLOGY ACTION PLAN (SNAP) 2010-2015
 TOWARDS A STRATEGIC NANOTECHNOLOGY ACTION PLAN (SNAP) 2010-2015 1. Respondent profile For individuals: - Name, age, gender, country, e-mail. - From which perspective are you interested in nanotechnologies:
TOWARDS A STRATEGIC NANOTECHNOLOGY ACTION PLAN (SNAP) 2010-2015 1. Respondent profile For individuals: - Name, age, gender, country, e-mail. - From which perspective are you interested in nanotechnologies:
DELIVERING OUR STRATEGY
 www.lawsociety.org.uk DELIVERING OUR STRATEGY Our three year plan 2015 2018 >2 > Delivering our strategy Catherine Dixon Chief executive Foreword Welcome to our three year business plan which sets out
www.lawsociety.org.uk DELIVERING OUR STRATEGY Our three year plan 2015 2018 >2 > Delivering our strategy Catherine Dixon Chief executive Foreword Welcome to our three year business plan which sets out
Data protection. Wi-Fi location analytics
 Data protection Wi-Fi location analytics ICO lo Wi-Fi location analytics Data Protection Act Contents Introduction... 2 Overview... 2 What the DPA says... 2 What is Wi-Fi analytics?... 3 Conduct a privacy
Data protection Wi-Fi location analytics ICO lo Wi-Fi location analytics Data Protection Act Contents Introduction... 2 Overview... 2 What the DPA says... 2 What is Wi-Fi analytics?... 3 Conduct a privacy
Opportunities for the Automotive Sector in Horizon 2020. Cliff Funnell UK FP7/H2020 Surface Transport NCP FP7UK
 Opportunities for the Automotive Sector in Horizon 2020 Cliff Funnell UK FP7/H2020 Surface Transport NCP Opportunity: The performance of the UK automotive sector and the success of the Low Carbon Vehicles
Opportunities for the Automotive Sector in Horizon 2020 Cliff Funnell UK FP7/H2020 Surface Transport NCP Opportunity: The performance of the UK automotive sector and the success of the Low Carbon Vehicles
Call topics (funding action), expected EU funding per project
 Horizon 2020 Energy Calls The EU Energy Focus service is a free, Government-funded service that aims to ensure that UK companies, research institutions and other organisations are well informed and have
Horizon 2020 Energy Calls The EU Energy Focus service is a free, Government-funded service that aims to ensure that UK companies, research institutions and other organisations are well informed and have
How To Help The Internet Of Things (Iot) Work With The Government
 Promoting investment and innovation in the Internet of Things Call for input Publication date: 23 July 2014 Closing Date for Responses: 1 October 2014 About this document This document seeks stakeholders
Promoting investment and innovation in the Internet of Things Call for input Publication date: 23 July 2014 Closing Date for Responses: 1 October 2014 About this document This document seeks stakeholders
E-PRIVACY DIRECTIVE: Personal Data Breach Notification
 E-PRIVACY DIRECTIVE: Personal Data Breach Notification PUBLIC CONSULTATION BEUC Response Contact: Kostas Rossoglou digital@beuc.eu Ref.: X/2011/092-13/09/11 EC register for interest representatives: identification
E-PRIVACY DIRECTIVE: Personal Data Breach Notification PUBLIC CONSULTATION BEUC Response Contact: Kostas Rossoglou digital@beuc.eu Ref.: X/2011/092-13/09/11 EC register for interest representatives: identification
ICT 6: Cloud computing
 computing Jorge GASÓS Software and Services, Cloud Unit DG Connect Jorge.Gasos@ec.europa.eu Cloud computing in previous WPs FP7 ICT Work Programmes (Calls 1, 5, 8, 10) Total investment in the software,
computing Jorge GASÓS Software and Services, Cloud Unit DG Connect Jorge.Gasos@ec.europa.eu Cloud computing in previous WPs FP7 ICT Work Programmes (Calls 1, 5, 8, 10) Total investment in the software,
QUESTIONS FOR COMMENT ON PROPOSED FRAMEWORK
 QUESTIONS FOR COMMENT ON PROPOSED FRAMEWORK Scope Are there practical considerations that support excluding certain types of companies or businesses from the framework for example, businesses that collect,
QUESTIONS FOR COMMENT ON PROPOSED FRAMEWORK Scope Are there practical considerations that support excluding certain types of companies or businesses from the framework for example, businesses that collect,
Funding Privacy Commissioner of Canada: Secondary use of data from the EHR current governance challenges & potential approaches
 Don Willison, Sc.D. Senior Scientist, Ontario Agency for Health Protection and Promotion Associate Professor, Part time, Clinical Epidemiology & Biostatistics, McMaster University don.willision@oahpp.ca
Don Willison, Sc.D. Senior Scientist, Ontario Agency for Health Protection and Promotion Associate Professor, Part time, Clinical Epidemiology & Biostatistics, McMaster University don.willision@oahpp.ca
H2020-LEIT-ICT WP2016-17. Big Data PPP
 H2020-LEIT-ICT WP2016-17 Big Data PPP H2020-LEIT-ICT-2016 ICT 14 Big Data PPP: cross-sectorial and cross-lingual data integration and experimentation (IA) - Budget 27 M ICT 15 Big Data PPP: large scale
H2020-LEIT-ICT WP2016-17 Big Data PPP H2020-LEIT-ICT-2016 ICT 14 Big Data PPP: cross-sectorial and cross-lingual data integration and experimentation (IA) - Budget 27 M ICT 15 Big Data PPP: large scale
Ofcom guidance on security requirements in sections 105A to D of the Communications Act 2003
 Ofcom guidance on security requirements in sections 105A to D of the Communications Act 2003 Guidance Publication date: 08 August 2014 About this document The legislation that applies to telecoms providers
Ofcom guidance on security requirements in sections 105A to D of the Communications Act 2003 Guidance Publication date: 08 August 2014 About this document The legislation that applies to telecoms providers
The Role of Networking & CSR. Beatriz Berruga Garcia CSR Europe
 The Role of Beatriz Berruga Garcia CSR Europe CSR Europe Corporate Members CSR Europe National Partner Network CSR Europe A Platform For... Connecting companies to share and further develop best practice
The Role of Beatriz Berruga Garcia CSR Europe CSR Europe Corporate Members CSR Europe National Partner Network CSR Europe A Platform For... Connecting companies to share and further develop best practice
EUROPEAN DATA PROTECTION SUPERVISOR. Inventory 2014. A strategic approach to legislative consultation
 Brussels, 18 December 2013 EUROPEAN DATA PROTECTION SUPERVISOR Inventory 2014 A strategic approach to legislative consultation 1 1. ISSUES OF STRATEGIC IMPORTANCE FOR 2014 This document presents the public
Brussels, 18 December 2013 EUROPEAN DATA PROTECTION SUPERVISOR Inventory 2014 A strategic approach to legislative consultation 1 1. ISSUES OF STRATEGIC IMPORTANCE FOR 2014 This document presents the public
Working Group on Cloud Security and Privacy. Brief Update on EGCCSS and WGPIUCS 24 June 2015
 Working Group on Cloud Security and Privacy Brief Update on EGCCSS and WGPIUCS 24 June 2015 1 Expert Group on Cloud Computing Services and Standards 8th EGCCSS Meeting held on 6 May 2015 Sharing of Experience
Working Group on Cloud Security and Privacy Brief Update on EGCCSS and WGPIUCS 24 June 2015 1 Expert Group on Cloud Computing Services and Standards 8th EGCCSS Meeting held on 6 May 2015 Sharing of Experience
OECD PROJECT ON CYBER RISK INSURANCE
 OECD PROJECT ON CYBER RISK INSURANCE Introduction 1. Cyber risks pose a real threat to society and the economy, the recognition of which has been given increasingly wide media coverage in recent years.
OECD PROJECT ON CYBER RISK INSURANCE Introduction 1. Cyber risks pose a real threat to society and the economy, the recognition of which has been given increasingly wide media coverage in recent years.
The European Platform in Network and Information Security (NIS) Fabio Martinelli
 The European Platform in Network and Information Security (NIS) Fabio Martinelli Istituto di Informatica e Telematica Consiglio Nazionale delle Ricerche IIT-CNR, Pisa, Italy Cyber security directive -
The European Platform in Network and Information Security (NIS) Fabio Martinelli Istituto di Informatica e Telematica Consiglio Nazionale delle Ricerche IIT-CNR, Pisa, Italy Cyber security directive -
EU Threat Landscape Threat Analysis in Research ENISA Workshop Brussels 24th February 2015
 EU Threat Landscape Threat Analysis in Research ENISA Workshop Brussels 24th February 2015 Aristotelis Tzafalias Trust and Security Unit H.4 DG Connect European Commission Trust and Security: One Mission
EU Threat Landscape Threat Analysis in Research ENISA Workshop Brussels 24th February 2015 Aristotelis Tzafalias Trust and Security Unit H.4 DG Connect European Commission Trust and Security: One Mission
European Innovation Partnership Smart Cities and Communities Henriette VAN EIJL, European Commission, DG MOVE-C2
 European Innovation Partnership Smart Cities and Communities Henriette VAN EIJL, European Commission, DG MOVE-C2 ERRIN-EURADA-EUROCITIES-Dutch Provinces Information/ de-brief meeting 14-5-2013 Overview
European Innovation Partnership Smart Cities and Communities Henriette VAN EIJL, European Commission, DG MOVE-C2 ERRIN-EURADA-EUROCITIES-Dutch Provinces Information/ de-brief meeting 14-5-2013 Overview
Procurement Strategy 2013-2017 Delivering Social Value for our Community
 Procurement Strategy 2013-2017 Delivering Social Value for our Community Making Bath & North East Somerset an even better place to live, work and visit 1 Picture courtesy of Bath & News Media Group Our
Procurement Strategy 2013-2017 Delivering Social Value for our Community Making Bath & North East Somerset an even better place to live, work and visit 1 Picture courtesy of Bath & News Media Group Our
The Netherlands response to the public consultation on the revision of the European Commission s Impact Assessment guidelines
 The Netherlands response to the public consultation on the revision of the European Commission s Impact Assessment guidelines Introduction Robust impact assessment is a vital element of both the Dutch
The Netherlands response to the public consultation on the revision of the European Commission s Impact Assessment guidelines Introduction Robust impact assessment is a vital element of both the Dutch
I am grateful to Rod Freeman and Valerie Kenyon at Hogan Lovells for their invaluable contribution to these speaking points
 Speaking points made by Robert MacDougall, Vodafone, during the IoT liability workshop as part of the Digital Revolution event at the University of Münster, 2 October 2015 1 Good afternoon everyone and
Speaking points made by Robert MacDougall, Vodafone, during the IoT liability workshop as part of the Digital Revolution event at the University of Münster, 2 October 2015 1 Good afternoon everyone and
Table of Contents. This document brings together the following three OECD reports on Radio-Frequency Identification (RFID)
 Table of Contents This document brings together the following three OECD reports on Radio-Frequency Identification (RFID) OECD Policy Guidance on Radio Frequency Identification... 2 Radio-Frequency Identification:
Table of Contents This document brings together the following three OECD reports on Radio-Frequency Identification (RFID) OECD Policy Guidance on Radio Frequency Identification... 2 Radio-Frequency Identification:
EPCglobal RFID standards & regulations. Henri Barthel OECD Paris, 5 October 2005
 EPCglobal RFID standards & regulations Henri Barthel OECD Paris, 5 October 2005 Roots of EPCglobal Auto ID Center (launched in 1999) Six world-class academia Labs: MIT (US), Cambridge (UK), Adelaide (Australia),
EPCglobal RFID standards & regulations Henri Barthel OECD Paris, 5 October 2005 Roots of EPCglobal Auto ID Center (launched in 1999) Six world-class academia Labs: MIT (US), Cambridge (UK), Adelaide (Australia),
DCA Certifications Scheme
 DCA Certifications Scheme www.datacentrealliance.org Background Data Centres are the critical facilities that all citizens and businesses depend on for the digital services that support our economic and
DCA Certifications Scheme www.datacentrealliance.org Background Data Centres are the critical facilities that all citizens and businesses depend on for the digital services that support our economic and
Legal Aspects of the MonIKA-Project - Privacy meets Cybersecurity
 Legal Aspects of the MonIKA-Project - Privacy meets Cybersecurity Sebastian Meissner Security Incident Information Sharing Workshop Berlin, 26.07.2013 Introduction Opening question Privacy & cybersecurity:
Legal Aspects of the MonIKA-Project - Privacy meets Cybersecurity Sebastian Meissner Security Incident Information Sharing Workshop Berlin, 26.07.2013 Introduction Opening question Privacy & cybersecurity:
Guidance notes and templates for Project Technical Review involving Independent Expert(s)
 Guidance notes and templates for Project Technical Review involving Independent Expert(s) FP7 Collaborative Projects (CP), Networks of Excellence, Coordination and Support Actions (CSA), CP-CSA, ERA-NET,
Guidance notes and templates for Project Technical Review involving Independent Expert(s) FP7 Collaborative Projects (CP), Networks of Excellence, Coordination and Support Actions (CSA), CP-CSA, ERA-NET,
Privacy Challenges in the Internet of Things (IoT) a European Perspective
 Privacy Challenges in the Internet of Things (IoT) a European Perspective Alicja Gniewek, PhD Student Interdisciplinary Centre for Security, Reliability and Trust Weicker Building, Université du Luxembourg
Privacy Challenges in the Internet of Things (IoT) a European Perspective Alicja Gniewek, PhD Student Interdisciplinary Centre for Security, Reliability and Trust Weicker Building, Université du Luxembourg
Report of the Nuisance Calls and Texts Task Force on Consent and Lead Generation
 Report of the Nuisance Calls and Texts Task Force on Consent and Lead Generation Contents Summary of actions recommended by the Task Force 1 Introduction 4 Consumer consent and lead generation in the context
Report of the Nuisance Calls and Texts Task Force on Consent and Lead Generation Contents Summary of actions recommended by the Task Force 1 Introduction 4 Consumer consent and lead generation in the context
Draft Code of Conduct on privacy for mobile health applications
 Draft Code of Conduct on privacy for mobile health applications I. About this Code 1) Introduction To be drafted as a last step, when the rest of the Code is more or less stable Ed. 2) Purpose The purpose
Draft Code of Conduct on privacy for mobile health applications I. About this Code 1) Introduction To be drafted as a last step, when the rest of the Code is more or less stable Ed. 2) Purpose The purpose
