Reconfigurable Networking Hardware: A Classroom Tool
|
|
|
- Elijah Paul
- 8 years ago
- Views:
Transcription
1 1 Reconfigurable Networking Hardware: A Classroom Tool Martin Casado Department of Computer Science Stanford University Stanford, CA casado@cs.stanford.edu Nick McKeown Department of Electrical Engineering Stanford University Stanford, CA nickm@stanford.edu Greg Watson Department of Electrical Engineering Stanford University Stanford, CA gwatson@stanford.edu Abstract We present an educational platform for teaching the design, debugging and deployment of real networking equipment in the operational Internet. The emphasis of our work is on teaching and, therefore, on providing an environment that is flexible, robust, low cost and easy to use. The platform is built around NetFPGAs custom boards containing eight ethernet ports and two FPGAs. NetFPGA boards, when used with VNS (Virtual Network System - another tool we have developed), can be integrated into dynamically configurable network topologies reachable from the Internet. VNS enables a user-space process running on any remote computer to function as a system controller for the NetFPGA boards. NetFPGA and VNS are used at Stanford in a graduate level networking course to teach router implementation in hardware and software. I. INTRODUCTION Most college-level digital design classes still use the microprocessor as a canonical design, yet few students go on to design microprocessors after they graduate. Instead, an increasing number of our graduates go on to design networking equipment: complex hardware-software systems that must interoperate with existing systems and infrastructure. In general, graduating students are ill-prepared for this task, and have little experience with this scale and complexity of project work. And so the goal of our work is to give students hands-on experience designing, debugging and deploying fully-functional networking equipment and deploying it into the Internet. In this paper we describe a low-cost and configurable platform which enables students, using industry standard design tools, to develop networking hardware. The platform we have created is comprised of two core technologies, NetFPGA and VNS [7] which, when used cooperatively, provide the infrastructure to implement network hardware on rich and varied networks. NetFPGAs are custom boards with eight Ethernet ports and two on-board programmable FPGAs (Field Programmable Gate Arrays). A This work was funded by the NSF, under grant and grant EIA canonical design exercise would be for a student to design an Ethernet switch, or Internet router, by writing Verilog and downloading their design to the NetFPGA board. NetFPGA boards can be programmed and debugged over the network and therefore allow students to build sophisticated hardware, deploy and test it from the other side of the country, without ever having to see the physical board. VNS (the virtual network system) virtualizes network topologies at the link layer by mapping between VLANs. With VNS a small network of commodity PCs running Linux can emulate thousands of different isolated virtual networks that are reachable from the internet and connect to real operating systems running real services. Any networking device can be included in a virtual topology emulated by VNS, including NetFPGA nodes. This allows us to provide an environment using VNS and NetFPGA where students program their NetFPGAs, and then insert them into a variety of different topologies. Their NetFPGA board processes traffic that comes from anywhere in the Internet, and their design must interoperate correctly with other nodes in the same topology. VNS supports multiple network topologies at the same time; so while one student is testing their NetFPGA design in their own private toplogy, another set of students might be testing how their designs interoperate on a different topology. Typically, a student implements the main datapath of the system in hardware. For example, in an Ethernet switch, they write Verilog to implement the header processing, address lookup and switching in hardware. But the control software, such as a spanning tree algorithm, or command line interface, needs to run on a microprocessor, yet NetFPGA doesn t have an embedded CPU. VNS enables the control software to run as a user-space program running anywhere on the Internet (i.e. the NetFPGA has a remote virtual cpu). This allows the implementation of sophisticated, integrated hardware and software devices. For example students could build IP routers with hardware forwarding paths and complex protocol processing done in software, using a familiar development and debugging environment.
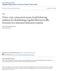
2 2 NetFPGA and VNS are used in CS344: Build an Internet Router - a graduate level class at Stanford. In this class, students work in teams of two (one proficient in hardware the other in software) to develop fully-functional, integrated hardware/software IP routers that process live Internet traffic. The routers support integrated TCP/IP stacks, an OSPF-like routing protocol and must interoperate with the routers developed by the other student teams. Both NetFPGA and VNS are designed for use by other schools. Our goal is to make both tools available at little or no cost - and is funded to do so by the National Science Foundation. Initially, both tools are available for remote use. Several hundred students at different schools have already used VNS remotely. NetFPGA is being prepared for remote use starting in Fall of We provide pre-packaged assignments (and solutions), remote access to tools, tool support, classroom support, and will even grade assignments. In short, we plan to remove any barriers to the adoption of these tools widely in the networking curriculum. This paper is organized as follows. The first two sections describe NetFPGA and VNS. Section 4 discusses how virtual topologies are created and managed. Section 5 discusses system transparency and debug support. We then present our experiences with NetFPGA and VNS in the classroom in section 6. Finally we end with an overview of our efforts to redesign NetFPGA and our conclusions. II. THE NETFPGA PLATFORM NetFPGA is a complete system for teaching the design of Ethernet-based network hardware such as routers or firewalls. The emphasis is on teaching and therefore on providing an environment that is flexible, robust, low cost and easy to use. The NetFPGA system comprises some custom hardware, offthe-shelf design tools, and some additional scripts and libraries. The current NetFPGA board measures six inches by nine inches and contains three Altera EP20K400 APEX devices, an eight-port Ethernet controller, three 1MByte SRAMs and ancillary logic. There is no on-board CPU. The architecture of the board is shown in figure 1. The Control-FPGA (CFPGA) is preprogrammed and does two things: it manages the 8-port Ethernet controller, and it provides a simple packet protocol for the two User-FPGAs. Each User-FPGA (UFPGA) has one Mbyte of private SRAM, as well as some on-chip SRAM. Each UF- PGA is connected to the CFPGA via a common bus, and to each other via a private bus. The bandwidths of the buses are such that they are not the bottleneck in the system - the throughput limitation will be either the user designs or the Ethernets themselves. The only external connections are the eight 10Mb/s Ethernet ports and a small connector that provides power and a single reset line. Consequently, all communication with the board is via the Ethernets. The operation of the board is as follows. The CFPGA buffers incoming packets in a local SRAM, and asserts a signal to the UFPGAs indicating that a packet is available from the relevant Ethernet port. Some time later one of the UFPGAs requests the packet which is then transferred to the UFPGA. The UF- PGA(s) contain the student s design, be it a switch, router, firewall, XML analyzer, whatever. So the UFPGAs process the Fig. 1. NetFPGA Board Architecture packet and may need to then send one or more packets. The UFPGAs pass their packets to the CFPGA, specifying the desired egress Ethernet port. The CFPGA accepts the packet and then forwards it to the Ethernet controller. The design resources available to the student are the two UF- PGAs, each with 1Mbyte of SRAM. Stanford students have implemented several obvious designs include Ethernet switches and Internet Routers. Less obvious extensions to these have included IPSec packet encryption, flow-based rate control, and switches employing flow-based weighted fair queueing. Most commercial networking products also include one or more CPUs to handle the more complex aspects of the device such as route update messages in an IP router. However the NetFPGA board has no CPU. Instead it has a mechanism that allows the CPU to exist elsewhere. The NetFPGA board recognizes specially encoded packets called control packets that enable a process running on an external computer to perform low level register reads and writes on the student s design. So for example a student can run a routing protocol process on their laptop, and have that process control the actual hardware that is in their NetFPGA board. We do not specifically advocate the CPU-less approach; indeed our latest version of NetFPGA has a CPU so that we can explore other architectures. On reflection, the use of these encoded packets to perform register accesses has been positive in that it uses the same basic transport mechanism (packets). On the negative side, the performance is poor (hundreds of accesses per second), and the student s software must deal with the fact that packets may be lost in transit. In practice, given that we have a rack of NetFPGA boards, we need a way to be able to manage the flow of packets between the NetFPGA boards and the campus internet. This flow is handled by the VNS system described in the next section, using VLAN tags [9] to provide isolation between NetFPGA boards. The next part of the NetFPGA system is the design flow. For this we use commercially available tools (which are usually very cheap or free to academic institutions). We use Synopsys VCS and FPGA Compiler for logic simulation and synthesis respectively. Place and route of the design is performed by Altera s Quartus tool. Since the external behavior of a NetFPGA system is completely defined by the sequence of ingress and egress packets, then verification tests consist of lists of packets. Each test specifies the sequence of ingress packets at each port, as well as
3 3 Fig. 3. A VNS virtual topology consisting of a hub between three commodity PCs. Each PC interface is a virtual interface with a unique VLAN identifier. The VNS server provides the mapping between the VLAN ids so that each packet that is sent by an interface on the topology is received by the other two. Fig. 2. A Typical setup of VNS. The application servers and firewalls are configured with multiple virtual interfaces each configured on a unique VLAN. the sequence of expected egress packets from each port. The students use a Perl program to specify these packets. The reason for this is that the Perl program generates a test environment that works in simulation (with VCS) and also on the real hardware, thus obviating the need for separate hardware tests. A second script is used to verify that the observed sequence of egress packets matches the expected sequence. This script works for both simulation and the actual hardware tests. Once the students have debugged and synthesized their design, they need to download it to the hardware. This is accomplished using the third part of the system: a Java-based web interface. This interface enables students to: acquire a board from the rack of boards, download their design to the board, send packets to the board, capture all egress packets from their board. The NetFPGA tools use the pcap library format [1] for packets, and so the students can use widely available network packet analysis tools such as Ethereal[3] for debugging their systems. III. THE VIRTUAL NETWORK SYSTEM NetFPGA provides the foundation on which students implement networking devices in hardware. In order to provide the students with a realistic, dynamic environment for development and testing on the operational Internet, we ve developed a complementary technology, the Virtual Network System (VNS) [7]. In short, VNS virtualizes the network allowing the simulation of many complex and configurable network topologies on which NetFPGA boards can participate. Each of the simulated topologies is reachable from the Internet and thus carries live Internet traffic. In this section we present VNS and discuss how it interoperates with NetFPGA to integrate student projects into the Internet. A typical setup of VNS is shown in Figure 2. The firewall and the application servers are standard PCs running Linux. Each PC is configured with one or more virtual interface each of which is on a unique VLAN (and therefore tagged with a unique VLAN id). The core of the system is the VNS server which accesses all of the traffic on the network by placing its interface in promiscuous mode. The server can determine the Fig. 4. VNS system with connected NetFPGA boards. The application servers and firewalls are configured with multiple virtual interfaces each configured on a unique VLAN. Packets from all NetFPGA ports are also tagged by the switch with unique VLAN IDs. source of any packet by its VLAN ID and the destination by inspecting the destination address of the Ethernet header. Because it can access all traffic on the network, the VNS server is able to to emulate arbitrary network topologies by mapping between VLANs. Figure 3 shows an example of a virtual topology emulated by the VNS server using the setup shown in figure 2. In this case, the virtual topology consists of the firewall connected to a hub with two connected application servers. For each packet the VNS server intercepts from one of the interfaces on the virtual topology (identified by their VLAN IDs) it will generate two more packets with VLAN IDs of the two other interfaces, thus emulating a network hub. Note that the original packet is never intercepted (taken off the wire) by the VNS server which can only passively listen, however because it is on a VLAN unique to the sending interface, the other listening interfaces are unable to process it. A virtual topology is therefore simply a mapping, performed by the VNS server between separate VLANs. Each of the connected PCs can be configured with many (hundreds) of virtual interfaces and each of these interfaces my participate on a different topology in complete isolation. A. Integrating with NetFPGA VNS allows us the ability to integrate one or more NetF- PGA boards into multiple complex topologies. Doing so does
4 4 Fig. 5. A VNS virtual topology with a virtual host interposed between the firewall and two application servers. The VNS server tunnels all packets to the virtual host over a TCP connection to a client program executing in user space on a PC. The client program is therefore able to function as an entity on the network. not require any modifications to either NetFPGA nor VNS. As shown in figure 4, we connect NetFPGA boards to the network through a switch which marks each port with a unique VLAN identifier. Using the VLAN identifier, the VNS server can determine which port a packet originates from and thus can be configured to allow one or more NetFPGA boards to participate on the topology like any other networking device. Our experimental setup uses a single, 96 port switch, to connect 8 NetFPGA boards, the VNS server, a firewall and three unix servers running various services including http and ftp. Using this setup, VNS can be dynamically configured to include the NetFPGA boards in arbitrary topologies connected to commodity machines. Figure 6 shows a logical topology with a NetF- PGA board interposed between the firewall and three application servers. The NetFPGA board can then be programmed to operate as an intermediary networking device such as an Ethernet hub, a learning switch or an IP router. B. Providing a User Space CPU In addition to mapping between VLANs, the VNS server is able to interpose one or more virtual hosts in the network as shown in figure 5. Each virtual host is emulated at the link layer by the VNS server. The goal of supporting virtual hosts in the VNS server is to provide a mechanism in which user-level client programs running on standard operating systems can participate on the virtual topology. When the VNS server intercepts a packet destined to an interface on a virtual host, instead of mapping that packet to another VLAN ID and placing it back on the wire, the server strips of the VLAN header and sends the packet over a TCP connection to the associated client program. The client therefore will receive all packets seen by any of the virtual host s interfaces on the topology and can send packets to the server to be injected back into the network specifying, which of its interfaces to send the packet out on. The server will then ensure that the sent packet is tagged with the correct VLANs for all connecting interfaces. The user level program is in essence, functioning as an entity on the network. The ability of the VNS server to support integration of user space processes into the virtual network topology can be used to add a virtual cpu to the NetFPGA cards. The NetFPGA can be controlled via control packets sent to port zero which read Fig. 6. VNS allows NetFGPA boards to participate in virtual topologies. A virtual host connected to port 0 of the NetFPGA board can function as an offboard control unit. The client program can control the NetFPGA by sending special packets which can read and write to registers. and write to all accessible registers. It is possible then, to create a topology in which a virtual host is connected directly to port zero of the NetFPGA board, as shown in figure 6. The VNS server will handle moving packets between the user process associated with the virtual host and port zero of the NetFPGA board. In this configuration the virtual host can effectively act as a cpu for the NetFPGA. For example, assuming the configuration in figure 6, the NetFPGA board can be programmed to function as a 3 port Internet router. However, the more complex functions such as OSPF support can be implemented within the virtual host. The model of allowing a user-space program to function as an offboard cpu has a number of advantages. Standard PC operating systems typically provide much richer debugging and development environments than those for embedded processors. There is no need to cross compile nor download code to the board and standard debuggers, such as gdb, can be used to monitor and debug the program during runtime. Furthermore, because the main focus of our work is to provide an educational platform we believe supporting a familiar development and runtime environment, such as a Unix, greatly eases introduction to an otherwise complex system. C. Creating Topologies Creating a virtual topology in VNS requires writing a topology description file in XML and copying it to a directory monitored by the VNS server. Topology description files contain the connectivity of the hosts in the topology, the IP addresses each interface and the VLAN identifiers assigned to the NetF- PGA ports that will be participating on the topology. Given a description file an installation script will create a topology by performing the following actions: Create a virtual interface on each participating PC and assign the interface the given IP addresses and VLAN ids Set up routes on each of the PCs to forward packets Copy the topology file to the directory monitored by the server Once the server determines that a topology file has been added or has changed it will perform the VLAN mappings specified by the new file. Because the topology files can be updated at runtime, the system supports dynamic topologies which may
5 5 include link failures, changes in connectivity or changes in link properties. IV. SYSTEM TRANSPARENCY Typical use of NetFPGA does not require the developer to have hands-on access to the hardware. The developer may in fact develop from anywhere on the Internet. A significant challenge to supporting remote development is to provide the same level of debugging transparency into the system as would be available if the developer had physical access to the board and the connected network. To provide transparency in the system via two mechanisms, we provide a remote logic probe and generation of pcap compatible trace files. A traditional hardware development system would provide the capability to capture signals in real time via a logic analyzer. Indeed Altera provides such a capability with their embedded logic analyzer. However this capability requires a computer to be connected to each board which is prohibitively expensive for NetFPGA. Instead we provide a logic analyzer that runs on one of the UFPGAs. In practice this is not much of a restriction because we found that most student designs only use a single FPGA. This logic analyzer, while not as sophisticated as commercial Logic Analyzers, has proven reasonably flexible. The user can specify a sophisticated four-stage trigger and the local SRAM can capture up to 256K samples of 32 signals. Of course the students use the logic analyzer via the web: they can launch the analyzer and then start a simulation, and see when the analyzer triggers. The analyzer then automatically provides the student with the trace file in Value Change Dump format, and so the student can use commercial or free waveform viewers to examine the trace dump. In addition to the logic probe the system provides debug support by logging all packets processed by the user space program operating as a NetFPGA cpu. VNS client programs communicate with the server using a simple libarary. This library logs all packets that are exchanged between it and the server in pcap[1] trace format. The packet traces are saved client side and can be used with tcpdump[2] or Ethereal[3] to inspect all traffic processed by the client. V. TEACHING NETWORKING HARDWARE NetFPGA and VNS are integral to an upper level projects course here at Stanford in which students learn to design and develop Internet routers. During the course, two-student teams design fully functional, integrated hardware/software routers that process live Internet traffic. Each team consists of a student proficient in hardware and a student proficient in software. At the end of the course, all student routers are tested on a large shared topology in which they must interoperate to build their forwarding tables and route traffic correctly despite multiple, periodic link failures. The students design their own interoperability tests, and use VNS to implement on arbitrary private topologies of their choosing that connect to the Internet. The students are presented with the verilog code for a two port, unintelligent layer two switch. Their first job is to extend this design into a three port learning switch their switch must automatically learn where nodes are located based on the source address of incoming packets. The next step is to provide control packet support so that an external software process can perform register accesses on their design. The third step is to implement ARP functionality - the students router must identify ARP packets and be able to pass them to their CPU process. Then the main stage is the implementation of the actual IP routing protocol - the students must add longest-prefix matching capability, as well as the necessary route tables to their design. In parallel with the hardware portion of the project, the student responsible for the software develops complex functionality in C which operates as the router CPU through VNS as discussed previously. The software must support the following functionality. an integrated TCP stack which exports a bsd/style socket interface a command line interface for managing the router (this runs on top of the student s socket interface and TCP stack) malformed packet processing, such as handling fragments or packets with bad headers ICMP support including generation of time exceeded messages, port and host unreachable messages and echo replies a simplified link state routing protocol (based on OSPFv2) which must interoperate with the other student routers setting up and managing the hardware forwarding table and ARP cache Designing an integrated software and hardware router requires students to face complex design issues such as the performance flexibility tradeoff of moving functionality between hardware and software. These issues become particularly important in the final portion of the project in which the students must implement advanced functionality of their own design into their routers. Including an open-ended design component to the project allows students to explore areas of interest to them while tackling an integrated hardware/software design problem without the guidance of detailed specifications. The only requirement to this portion of the project is that the implemented features have both a hardware and software component that operate cooperatively. We have been delighted by the sophistication and inventiveness of the students in coming up with advanced functionality. During the pilot offering of the course during the Spring quarter of 2004, student projects included MAC level encryption, flow rate limiting, VPN support, NAT and a web programmable hardware firewall. In our latest class (spring 05) one team used their router to implement a man-in-the-middle security attack on SSH connections, and used it to demonstrate how to capture passwords. A more detailed description of the course is presented in [8]. Ultimately, it is our goal to host remote courses at other institutions and Universities. The full router project can be done remotely without requiring the students to have direct access with the test network or the NetFPGA boards. All course materials are publicly available online at the course website which is included in the conclusion of this paper. We provide all tools support and grading. Funding is provided by NSF and comes at no cost to the participating institution.
6 6 VI. REDESIGNING NETFPGA After using NetFPGA for three years we have feedback from our users, and we are now in the process of developing new versions of hardware (and software). The issues we are addressing next are: The biggest problem with the current system is that the hardware is awkward to distribute to others. The NetF- PGA boards use a proprietary backplane that distributes power and reset. The new board will use standard 3.3V PCI and will fit into a personal computer. Indeed we are designing the system to have up to five boards per computer, with one board as the control board and the remaining four for use by the students. Thus the entire NetFPGA system can be delivered shrink-wrapped for installation on a standard x86-based personal computer. The networks are too slow. NetFPGA uses eight 10Mbit/s ports. While suitable for teaching they are too slow for interesting research projects. Consequently our new board will provide four Ethernet ports each operating at 10, 100 or 1000 Mbps. This will require us to upgrade the VNS server and infrastructure to use 1.0Gbps links also; fortunately they are now very affordable. Already two researchers have expressed interest in using the board to explore new transport protocols - their protocols require custom network interfaces which, of course, is the main attribute of NetFPGA. The new board also has two 3.0Gbps duplex serial links which can be used to interconnect multiple boards to form a larger system. The mechanism used to provide low-level register access to the hardware is awkward for students and slow, as mentioned earlier. Currently, the students control unit running within VNS must send ethernet frames conforming to a particular format over an unreliable network to issue register reads and writes. The new board will address this by using the PCI bus to map the board s registers directly into memory thus providing a much faster access mechanism. The cost of this is added complexity to the system as we will need a way to provide students with restricted access to their board. While the basic functionality of the boards is still provided by a CFPGA (as in the first iteration) the new board will have an on-chip CPU (PowerPC). It is our hope that the students can use these in future projects. Note that the presence of a CPU does not mean that we are moving away from the remote CPU approach that we have used so effectively. Rather the presence of an onboard CPU provides new avenues to explore. For example it might provide the opportunity for some simple per-packet computations required by emerging variants of TCP. The cost of using the onboard CPU is a significantly more complicated tool flow and thus might be limited to more advanced projects. The current tool flow is outdated, slow and only runs on non-mswindows operating systems. The new board will use a single tool for synthesis and place-and-route and is supported on MSWindows as well as Linux and other versions of UNIX. We also intend to support several commercial Verilog simulators, including VCS and ModelSim. The FPGA technology is now dated. We will be using newer FPGA devices (Virtex II Pro 30) and SRAMs with greater speed and capacity. This will provide the resources for more interesting student projects. Logic Analyzer support will be continued. The new board has two independent SRAMs, with one that can be dedicated for use by the Analyzer. However we have observed that students rarely use the Analyzer. We believe there are two reasons for this: first, the simulation environment is sufficient to identify almost all bugs. Second, it requires some work: deciding which signals to capture, hooking those signals to the analyzer block, and then setting up trigger definitions. VII. RELATED WORK The FPX project [4] [5] at Washington University provides FPGA hardware that can be attached to a single OC-48 ATM port. As such it is not aimed at providing a complete networking system, but rather on providing programmable hardware assist for functions that are too complex to be done in software (such as on-the-fly JPEG encoding at Gbit/s rates). Also at WU is the Open Network Laboratory project [6] This is a collection of open-source, extensible routers built using their FPX technology. They plan to have four of these configurable routers interconnected a programmable switch. This is primarily a research project, providing a high-speed flexible environment for use in router research. VIII. CONCLUSIONS University networking classes often contain projects, but these projects generally operate at the socket-layer and above. To operate below a socket might involve dabbling with operating system structures, dedicated hardware, kernel hacking, and security nightmares as students generate corrupt packets and inject them into the network. As a result, few networking classes are able to give hands-on experience at a lower level - where, arguably, the real networking infrastructure exists. Our goal is to give students hands-on experience with the Internet infrastructure. We don t expect our approach to replace traditional system design classes anytime soon, but we do hope to make it possible to include meaningful, low-level networking projects in a standard curriculum. To this end, we produced two tools: NetFPGA and VNS, each of which aids in the development of networking hardware on configurable network topologies. Our approach allows users to build network devices out of custom boards that can be programmed and tested over the Internet. We provide a remotely accessible logic probe to aid in development and testing. In addition, the environment supports the emulation of multiple, complex network topologies that can integrate with commodity operating systems and arbitrary networking hardware. These topologies are reachable from the Internet and therefore allow testing of network devices on real traffic in real time. In addition, the system provides a method for adding a cpu to the network device as a user space process thus simplifying prototyping, developing and testing complex functionality.
7 7 The focus of our work has been to provide a robust, lowcost environment for teaching the implementation of networking hardware in relation to Internet infrastructure. We are using both NetFPGA and VNS in a graduate level projects course in computer networks in which students develop sophisticated routers in hardware and software. All use of NetFPGA and VNS can be done remotely. We are thus able to support remote courses in network hardware design and it is our goal to support such courses at other universities. If you are interested in learning more about NetFPGA, VNS or the course we offer, please visit the following websites or contact us directly by . NetFPGA Website: NetFPGA 2 Website: VNS Website: Course Website: public/ IX. ACKNOWLEDGEMENTS This work was funded by the NSF, under grant and grant EIA Special thanks to Alan Swithenbank and Jim Weaver for their time spent on board design. We also acknowledge the tremendous support provided by Altera, Xilinx and Synopsys. REFERENCES [1] libpcap packet capture library. [2] tcpdump network sniffer. [3] The ethereal network analyzer. [4] John W. Lockwood, An Open Platform for Development of Network Processing Modules in Reprogrammable Hardware, IEC DesignCon 2001, Santa Clara, CA, Jan. 2001, Paper WB-19. [5] the FPX project page. [6] Open Network Laboratory project [7] Martin Casado, Nick McKeown. The Virtual Network System ACM SIGCSE Bulletin, Volume 37, Pages 76-80, 2005 [8] Martin Casado, Gregory Watson, Nick McKeown. Teaching Networking Hardware To appear in ACM ITiCSE, 2005 [9] IEEE 802.1Q VLAN Specification
Open Flow Controller and Switch Datasheet
 Open Flow Controller and Switch Datasheet California State University Chico Alan Braithwaite Spring 2013 Block Diagram Figure 1. High Level Block Diagram The project will consist of a network development
Open Flow Controller and Switch Datasheet California State University Chico Alan Braithwaite Spring 2013 Block Diagram Figure 1. High Level Block Diagram The project will consist of a network development
OpenFlow: Enabling Innovation in Campus Networks
 OpenFlow: Enabling Innovation in Campus Networks Nick McKeown Stanford University Presenter: Munhwan Choi Table of contents What is OpenFlow? The OpenFlow switch Using OpenFlow OpenFlow Switch Specification
OpenFlow: Enabling Innovation in Campus Networks Nick McKeown Stanford University Presenter: Munhwan Choi Table of contents What is OpenFlow? The OpenFlow switch Using OpenFlow OpenFlow Switch Specification
Building an Accelerated and Energy-Efficient Traffic Monitor onto the NetFPGA platform
 Building an Accelerated and Energy-Efficient Traffic Monitor onto the NetFPGA platform Alfio Lombardo Department of Computer Science and Telecommunication Engineering V.le A. Doria, 6 95125, Catania, Italy
Building an Accelerated and Energy-Efficient Traffic Monitor onto the NetFPGA platform Alfio Lombardo Department of Computer Science and Telecommunication Engineering V.le A. Doria, 6 95125, Catania, Italy
Lab VI Capturing and monitoring the network traffic
 Lab VI Capturing and monitoring the network traffic 1. Goals To gain general knowledge about the network analyzers and to understand their utility To learn how to use network traffic analyzer tools (Wireshark)
Lab VI Capturing and monitoring the network traffic 1. Goals To gain general knowledge about the network analyzers and to understand their utility To learn how to use network traffic analyzer tools (Wireshark)
A Research Study on Packet Sniffing Tool TCPDUMP
 A Research Study on Packet Sniffing Tool TCPDUMP ANSHUL GUPTA SURESH GYAN VIHAR UNIVERSITY, INDIA ABSTRACT Packet sniffer is a technique of monitoring every packet that crosses the network. By using this
A Research Study on Packet Sniffing Tool TCPDUMP ANSHUL GUPTA SURESH GYAN VIHAR UNIVERSITY, INDIA ABSTRACT Packet sniffer is a technique of monitoring every packet that crosses the network. By using this
Linux Network Security
 Linux Network Security Course ID SEC220 Course Description This extremely popular class focuses on network security, and makes an excellent companion class to the GL550: Host Security course. Protocols
Linux Network Security Course ID SEC220 Course Description This extremely popular class focuses on network security, and makes an excellent companion class to the GL550: Host Security course. Protocols
High-Performance IP Service Node with Layer 4 to 7 Packet Processing Features
 UDC 621.395.31:681.3 High-Performance IP Service Node with Layer 4 to 7 Packet Processing Features VTsuneo Katsuyama VAkira Hakata VMasafumi Katoh VAkira Takeyama (Manuscript received February 27, 2001)
UDC 621.395.31:681.3 High-Performance IP Service Node with Layer 4 to 7 Packet Processing Features VTsuneo Katsuyama VAkira Hakata VMasafumi Katoh VAkira Takeyama (Manuscript received February 27, 2001)
Router Architectures
 Router Architectures An overview of router architectures. Introduction What is a Packet Switch? Basic Architectural Components Some Example Packet Switches The Evolution of IP Routers 2 1 Router Components
Router Architectures An overview of router architectures. Introduction What is a Packet Switch? Basic Architectural Components Some Example Packet Switches The Evolution of IP Routers 2 1 Router Components
基 於 SDN 與 可 程 式 化 硬 體 架 構 之 雲 端 網 路 系 統 交 換 器
 基 於 SDN 與 可 程 式 化 硬 體 架 構 之 雲 端 網 路 系 統 交 換 器 楊 竹 星 教 授 國 立 成 功 大 學 電 機 工 程 學 系 Outline Introduction OpenFlow NetFPGA OpenFlow Switch on NetFPGA Development Cases Conclusion 2 Introduction With the proposal
基 於 SDN 與 可 程 式 化 硬 體 架 構 之 雲 端 網 路 系 統 交 換 器 楊 竹 星 教 授 國 立 成 功 大 學 電 機 工 程 學 系 Outline Introduction OpenFlow NetFPGA OpenFlow Switch on NetFPGA Development Cases Conclusion 2 Introduction With the proposal
Stress-Testing a Gbps Intrusion Prevention Device on DETER
 Stress-Testing a Gbps Intrusion Prevention Device on DETER Nicholas Weaver Vern Paxson ICSI Acknowledgements Joint work with Jose Chema Gonzalez Sponsored by NSF/DHS ANI-0335290 (EMIST) DOE DE-F602-04ER25638
Stress-Testing a Gbps Intrusion Prevention Device on DETER Nicholas Weaver Vern Paxson ICSI Acknowledgements Joint work with Jose Chema Gonzalez Sponsored by NSF/DHS ANI-0335290 (EMIST) DOE DE-F602-04ER25638
How To Monitor And Test An Ethernet Network On A Computer Or Network Card
 3. MONITORING AND TESTING THE ETHERNET NETWORK 3.1 Introduction The following parameters are covered by the Ethernet performance metrics: Latency (delay) the amount of time required for a frame to travel
3. MONITORING AND TESTING THE ETHERNET NETWORK 3.1 Introduction The following parameters are covered by the Ethernet performance metrics: Latency (delay) the amount of time required for a frame to travel
FWSM introduction Intro 5/1
 Intro 5/0 Content: FWSM introduction Requirements for FWSM 3.2 How the Firewall Services Module Works with the Switch Using the MSFC Firewall Mode Overview Stateful Inspection Overview Security Context
Intro 5/0 Content: FWSM introduction Requirements for FWSM 3.2 How the Firewall Services Module Works with the Switch Using the MSFC Firewall Mode Overview Stateful Inspection Overview Security Context
Guideline for setting up a functional VPN
 Guideline for setting up a functional VPN Why do I want a VPN? VPN by definition creates a private, trusted network across an untrusted medium. It allows you to connect offices and people from around the
Guideline for setting up a functional VPN Why do I want a VPN? VPN by definition creates a private, trusted network across an untrusted medium. It allows you to connect offices and people from around the
Linux. Reverse Debugging. Target Communication Framework. Nexus. Intel Trace Hub GDB. PIL Simulation CONTENTS
 Android NEWS 2016 AUTOSAR Linux Windows 10 Reverse ging Target Communication Framework ARM CoreSight Requirements Analysis Nexus Timing Tools Intel Trace Hub GDB Unit Testing PIL Simulation Infineon MCDS
Android NEWS 2016 AUTOSAR Linux Windows 10 Reverse ging Target Communication Framework ARM CoreSight Requirements Analysis Nexus Timing Tools Intel Trace Hub GDB Unit Testing PIL Simulation Infineon MCDS
Analysis of Open Source Drivers for IEEE 802.11 WLANs
 Preprint of an article that appeared in IEEE conference proceeding of ICWCSC 2010 Analysis of Open Source Drivers for IEEE 802.11 WLANs Vipin M AU-KBC Research Centre MIT campus of Anna University Chennai,
Preprint of an article that appeared in IEEE conference proceeding of ICWCSC 2010 Analysis of Open Source Drivers for IEEE 802.11 WLANs Vipin M AU-KBC Research Centre MIT campus of Anna University Chennai,
Protecting and controlling Virtual LANs by Linux router-firewall
 Protecting and controlling Virtual LANs by Linux router-firewall Tihomir Katić Mile Šikić Krešimir Šikić Faculty of Electrical Engineering and Computing University of Zagreb Unska 3, HR 10000 Zagreb, Croatia
Protecting and controlling Virtual LANs by Linux router-firewall Tihomir Katić Mile Šikić Krešimir Šikić Faculty of Electrical Engineering and Computing University of Zagreb Unska 3, HR 10000 Zagreb, Croatia
Building Secure Network Infrastructure For LANs
 Building Secure Network Infrastructure For LANs Yeung, K., Hau; and Leung, T., Chuen Abstract This paper discusses the building of secure network infrastructure for local area networks. It first gives
Building Secure Network Infrastructure For LANs Yeung, K., Hau; and Leung, T., Chuen Abstract This paper discusses the building of secure network infrastructure for local area networks. It first gives
Network Security. Network Packet Analysis
 Network Security Network Packet Analysis Module 3 Keith A. Watson, CISSP, CISA IA Research Engineer, CERIAS kaw@cerias.purdue.edu 1 Network Packet Analysis Definition: Examining network packets to determine
Network Security Network Packet Analysis Module 3 Keith A. Watson, CISSP, CISA IA Research Engineer, CERIAS kaw@cerias.purdue.edu 1 Network Packet Analysis Definition: Examining network packets to determine
Information- Centric Networks. Section # 13.2: Alternatives Instructor: George Xylomenos Department: Informatics
 Information- Centric Networks Section # 13.2: Alternatives Instructor: George Xylomenos Department: Informatics Funding These educational materials have been developed as part of the instructors educational
Information- Centric Networks Section # 13.2: Alternatives Instructor: George Xylomenos Department: Informatics Funding These educational materials have been developed as part of the instructors educational
7a. System-on-chip design and prototyping platforms
 7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
Network Defense Tools
 Network Defense Tools Prepared by Vanjara Ravikant Thakkarbhai Engineering College, Godhra-Tuwa +91-94291-77234 www.cebirds.in, www.facebook.com/cebirds ravikantvanjara@gmail.com What is Firewall? A firewall
Network Defense Tools Prepared by Vanjara Ravikant Thakkarbhai Engineering College, Godhra-Tuwa +91-94291-77234 www.cebirds.in, www.facebook.com/cebirds ravikantvanjara@gmail.com What is Firewall? A firewall
BASIC ANALYSIS OF TCP/IP NETWORKS
 BASIC ANALYSIS OF TCP/IP NETWORKS INTRODUCTION Communication analysis provides powerful tool for maintenance, performance monitoring, attack detection, and problems fixing in computer networks. Today networks
BASIC ANALYSIS OF TCP/IP NETWORKS INTRODUCTION Communication analysis provides powerful tool for maintenance, performance monitoring, attack detection, and problems fixing in computer networks. Today networks
Logical & Physical Security
 Building a Secure Ethernet Environment By Frank Prendergast Manager, Network Certification Services Schneider Electric s Automation Business North Andover, MA The trend toward using Ethernet as the sole
Building a Secure Ethernet Environment By Frank Prendergast Manager, Network Certification Services Schneider Electric s Automation Business North Andover, MA The trend toward using Ethernet as the sole
Open Source in Network Administration: the ntop Project
 Open Source in Network Administration: the ntop Project Luca Deri 1 Project History Started in 1997 as monitoring application for the Univ. of Pisa 1998: First public release v 0.4 (GPL2) 1999-2002:
Open Source in Network Administration: the ntop Project Luca Deri 1 Project History Started in 1997 as monitoring application for the Univ. of Pisa 1998: First public release v 0.4 (GPL2) 1999-2002:
Axon: A Flexible Substrate for Source- routed Ethernet. Jeffrey Shafer Brent Stephens Michael Foss Sco6 Rixner Alan L. Cox
 Axon: A Flexible Substrate for Source- routed Ethernet Jeffrey Shafer Brent Stephens Michael Foss Sco6 Rixner Alan L. Cox 2 Ethernet Tradeoffs Strengths Weaknesses Cheap Simple High data rate Ubiquitous
Axon: A Flexible Substrate for Source- routed Ethernet Jeffrey Shafer Brent Stephens Michael Foss Sco6 Rixner Alan L. Cox 2 Ethernet Tradeoffs Strengths Weaknesses Cheap Simple High data rate Ubiquitous
Packet Sniffers Submitted in partial fulfillment of the requirement for the award of degree Of MCA
 A Seminar report On Packet Sniffers Submitted in partial fulfillment of the requirement for the award of degree Of MCA SUBMITTED TO: www.studymafia.org SUBMITTED BY: www.studymafia.org Preface I have made
A Seminar report On Packet Sniffers Submitted in partial fulfillment of the requirement for the award of degree Of MCA SUBMITTED TO: www.studymafia.org SUBMITTED BY: www.studymafia.org Preface I have made
"Charting the Course...
 Description "Charting the Course... Course Summary Interconnecting Cisco Networking Devices: Accelerated (CCNAX), is a course consisting of ICND1 and ICND2 content in its entirety, but with the content
Description "Charting the Course... Course Summary Interconnecting Cisco Networking Devices: Accelerated (CCNAX), is a course consisting of ICND1 and ICND2 content in its entirety, but with the content
OpenFlow: Load Balancing in enterprise networks using Floodlight Controller
 OpenFlow: Load Balancing in enterprise networks using Floodlight Controller Srinivas Govindraj, Arunkumar Jayaraman, Nitin Khanna, Kaushik Ravi Prakash srinivas.govindraj@colorado.edu, arunkumar.jayaraman@colorado.edu,
OpenFlow: Load Balancing in enterprise networks using Floodlight Controller Srinivas Govindraj, Arunkumar Jayaraman, Nitin Khanna, Kaushik Ravi Prakash srinivas.govindraj@colorado.edu, arunkumar.jayaraman@colorado.edu,
Intrusion Detection Systems (IDS)
 Intrusion Detection Systems (IDS) What are They and How do They Work? By Wayne T Work Security Gauntlet Consulting 56 Applewood Lane Naugatuck, CT 06770 203.217.5004 Page 1 6/12/2003 1. Introduction Intrusion
Intrusion Detection Systems (IDS) What are They and How do They Work? By Wayne T Work Security Gauntlet Consulting 56 Applewood Lane Naugatuck, CT 06770 203.217.5004 Page 1 6/12/2003 1. Introduction Intrusion
Virtual private network. Network security protocols VPN VPN. Instead of a dedicated data link Packets securely sent over a shared network Internet VPN
 Virtual private network Network security protocols COMP347 2006 Len Hamey Instead of a dedicated data link Packets securely sent over a shared network Internet VPN Public internet Security protocol encrypts
Virtual private network Network security protocols COMP347 2006 Len Hamey Instead of a dedicated data link Packets securely sent over a shared network Internet VPN Public internet Security protocol encrypts
Infrastructure for active and passive measurements at 10Gbps and beyond
 Infrastructure for active and passive measurements at 10Gbps and beyond Best Practice Document Produced by UNINETT led working group on network monitoring (UFS 142) Author: Arne Øslebø August 2014 1 TERENA
Infrastructure for active and passive measurements at 10Gbps and beyond Best Practice Document Produced by UNINETT led working group on network monitoring (UFS 142) Author: Arne Øslebø August 2014 1 TERENA
Overview of Routing between Virtual LANs
 Overview of Routing between Virtual LANs This chapter provides an overview of virtual LANs (VLANs). It describes the encapsulation protocols used for routing between VLANs and provides some basic information
Overview of Routing between Virtual LANs This chapter provides an overview of virtual LANs (VLANs). It describes the encapsulation protocols used for routing between VLANs and provides some basic information
Digitale Signalverarbeitung mit FPGA (DSF) Soft Core Prozessor NIOS II Stand Mai 2007. Jens Onno Krah
 (DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de jens_onno.krah@fh-koeln.de NIOS II 1 1 What is Nios II? Altera s Second Generation
(DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de jens_onno.krah@fh-koeln.de NIOS II 1 1 What is Nios II? Altera s Second Generation
Procedure: You can find the problem sheet on Drive D: of the lab PCs. Part 1: Router & Switch
 University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Networks Laboratory 907528 Lab. 2 Network Devices & Packet Tracer Objectives 1. To become familiar with
University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Networks Laboratory 907528 Lab. 2 Network Devices & Packet Tracer Objectives 1. To become familiar with
WHITE PAPER. Extending Network Monitoring Tool Performance
 WHITE PAPER Extending Network Monitoring Tool Performance www.ixiacom.com 915-6915-01 Rev. A, July 2014 2 Table of Contents Benefits... 4 Abstract... 4 Introduction... 4 Understanding Monitoring Tools...
WHITE PAPER Extending Network Monitoring Tool Performance www.ixiacom.com 915-6915-01 Rev. A, July 2014 2 Table of Contents Benefits... 4 Abstract... 4 Introduction... 4 Understanding Monitoring Tools...
packet retransmitting based on dynamic route table technology, as shown in fig. 2 and 3.
 Implementation of an Emulation Environment for Large Scale Network Security Experiments Cui Yimin, Liu Li, Jin Qi, Kuang Xiaohui National Key Laboratory of Science and Technology on Information System
Implementation of an Emulation Environment for Large Scale Network Security Experiments Cui Yimin, Liu Li, Jin Qi, Kuang Xiaohui National Key Laboratory of Science and Technology on Information System
Troubleshooting the Firewall Services Module
 CHAPTER 25 This chapter describes how to troubleshoot the FWSM, and includes the following sections: Testing Your Configuration, page 25-1 Reloading the FWSM, page 25-6 Performing Password Recovery, page
CHAPTER 25 This chapter describes how to troubleshoot the FWSM, and includes the following sections: Testing Your Configuration, page 25-1 Reloading the FWSM, page 25-6 Performing Password Recovery, page
Chapter 1 Reading Organizer
 Chapter 1 Reading Organizer After completion of this chapter, you should be able to: Describe convergence of data, voice and video in the context of switched networks Describe a switched network in a small
Chapter 1 Reading Organizer After completion of this chapter, you should be able to: Describe convergence of data, voice and video in the context of switched networks Describe a switched network in a small
TABLE OF CONTENTS NETWORK SECURITY 2...1
 Network Security 2 This document is the exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
Network Security 2 This document is the exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
10/100/1000Mbps Ethernet MAC with Protocol Acceleration MAC-NET Core with Avalon Interface
 1 Introduction Ethernet is available in different speeds (10/100/1000 and 10000Mbps) and provides connectivity to meet a wide range of needs from desktop to switches. MorethanIP IP solutions provide a
1 Introduction Ethernet is available in different speeds (10/100/1000 and 10000Mbps) and provides connectivity to meet a wide range of needs from desktop to switches. MorethanIP IP solutions provide a
OpenFlow Based Load Balancing
 OpenFlow Based Load Balancing Hardeep Uppal and Dane Brandon University of Washington CSE561: Networking Project Report Abstract: In today s high-traffic internet, it is often desirable to have multiple
OpenFlow Based Load Balancing Hardeep Uppal and Dane Brandon University of Washington CSE561: Networking Project Report Abstract: In today s high-traffic internet, it is often desirable to have multiple
Lecture 17 - Network Security
 Lecture 17 - Network Security CMPSC 443 - Spring 2012 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse443-s12/ Idea Why donʼt we just integrate some of these neat
Lecture 17 - Network Security CMPSC 443 - Spring 2012 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse443-s12/ Idea Why donʼt we just integrate some of these neat
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY
 INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK PACKET SNIFFING MS. SONALI A. KARALE 1, MS. PUNAM P. HARKUT 2 HVPM COET Amravati.
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK PACKET SNIFFING MS. SONALI A. KARALE 1, MS. PUNAM P. HARKUT 2 HVPM COET Amravati.
Putting it on the NIC: A Case Study on application offloading to a Network Interface Card (NIC)
 This full text paper was peer reviewed at the direction of IEEE Communications Society subject matter experts for publication in the IEEE CCNC 2006 proceedings. Putting it on the NIC: A Case Study on application
This full text paper was peer reviewed at the direction of IEEE Communications Society subject matter experts for publication in the IEEE CCNC 2006 proceedings. Putting it on the NIC: A Case Study on application
LANs and VLANs A Simplified Tutorial
 Application Note LANs and VLANs A Simplified Tutorial Version 3.0 May 2002 COMPAS ID 90947 Avaya Labs 1 Companion document IP Addressing: A Simplified Tutorial COMPAS ID 92962 2 Introduction As the name
Application Note LANs and VLANs A Simplified Tutorial Version 3.0 May 2002 COMPAS ID 90947 Avaya Labs 1 Companion document IP Addressing: A Simplified Tutorial COMPAS ID 92962 2 Introduction As the name
Firewalls. Chapter 3
 Firewalls Chapter 3 1 Border Firewall Passed Packet (Ingress) Passed Packet (Egress) Attack Packet Hardened Client PC Internet (Not Trusted) Hardened Server Dropped Packet (Ingress) Log File Internet Border
Firewalls Chapter 3 1 Border Firewall Passed Packet (Ingress) Passed Packet (Egress) Attack Packet Hardened Client PC Internet (Not Trusted) Hardened Server Dropped Packet (Ingress) Log File Internet Border
Chapter 15: Advanced Networks
 Chapter 15: Advanced Networks IT Essentials: PC Hardware and Software v4.0 1 Determine a Network Topology A site survey is a physical inspection of the building that will help determine a basic logical
Chapter 15: Advanced Networks IT Essentials: PC Hardware and Software v4.0 1 Determine a Network Topology A site survey is a physical inspection of the building that will help determine a basic logical
Interconnecting Cisco Networking Devices, Part 2 **Part of CCNA Route/Switch**
 Course: Interconnecting Cisco Networking Devices, Part 2 Duration: 5 Day Hands-On Lab & Lecture Course Price: $ 3,295.00 Learning Credits: 33 Certification: CCNA Route/Switch Description: The Interconnecting
Course: Interconnecting Cisco Networking Devices, Part 2 Duration: 5 Day Hands-On Lab & Lecture Course Price: $ 3,295.00 Learning Credits: 33 Certification: CCNA Route/Switch Description: The Interconnecting
EE984 Laboratory Experiment 2: Protocol Analysis
 EE984 Laboratory Experiment 2: Protocol Analysis Abstract This experiment provides an introduction to protocols used in computer communications. The equipment used comprises of four PCs connected via a
EE984 Laboratory Experiment 2: Protocol Analysis Abstract This experiment provides an introduction to protocols used in computer communications. The equipment used comprises of four PCs connected via a
WANPIPE TM. Multi-protocol WANPIPE Driver CONFIGURATION M A N U A L. Author: Nenad Corbic/Alex Feldman
 WANPIPE TM Multi-protocol WANPIPE Driver CONFIGURATION M A N U A L Author: Nenad Corbic/Alex Feldman Copyright (c) 1995-2002 Sangoma Technologies Inc. Introduction WANPIPE from Sangoma Technologies Inc.
WANPIPE TM Multi-protocol WANPIPE Driver CONFIGURATION M A N U A L Author: Nenad Corbic/Alex Feldman Copyright (c) 1995-2002 Sangoma Technologies Inc. Introduction WANPIPE from Sangoma Technologies Inc.
SonicOS Enhanced 5.7.0.2 Release Notes
 SonicOS Contents Platform Compatibility... 1 Key Features... 2 Known Issues... 3 Resolved Issues... 4 Upgrading SonicOS Enhanced Image Procedures... 6 Related Technical Documentation... 11 Platform Compatibility
SonicOS Contents Platform Compatibility... 1 Key Features... 2 Known Issues... 3 Resolved Issues... 4 Upgrading SonicOS Enhanced Image Procedures... 6 Related Technical Documentation... 11 Platform Compatibility
CTS2134 Introduction to Networking. Module 8.4 8.7 Network Security
 CTS2134 Introduction to Networking Module 8.4 8.7 Network Security Switch Security: VLANs A virtual LAN (VLAN) is a logical grouping of computers based on a switch port. VLAN membership is configured by
CTS2134 Introduction to Networking Module 8.4 8.7 Network Security Switch Security: VLANs A virtual LAN (VLAN) is a logical grouping of computers based on a switch port. VLAN membership is configured by
GregSowell.com. Mikrotik Basics
 Mikrotik Basics Terms Used Layer X When I refer to something being at layer X I m referring to the OSI model. VLAN 802.1Q Layer 2 marking on traffic used to segment sets of traffic. VLAN tags are applied
Mikrotik Basics Terms Used Layer X When I refer to something being at layer X I m referring to the OSI model. VLAN 802.1Q Layer 2 marking on traffic used to segment sets of traffic. VLAN tags are applied
Architecture of distributed network processors: specifics of application in information security systems
 Architecture of distributed network processors: specifics of application in information security systems V.Zaborovsky, Politechnical University, Sait-Petersburg, Russia vlad@neva.ru 1. Introduction Modern
Architecture of distributed network processors: specifics of application in information security systems V.Zaborovsky, Politechnical University, Sait-Petersburg, Russia vlad@neva.ru 1. Introduction Modern
UPPER LAYER SWITCHING
 52-20-40 DATA COMMUNICATIONS MANAGEMENT UPPER LAYER SWITCHING Gilbert Held INSIDE Upper Layer Operations; Address Translation; Layer 3 Switching; Layer 4 Switching OVERVIEW The first series of LAN switches
52-20-40 DATA COMMUNICATIONS MANAGEMENT UPPER LAYER SWITCHING Gilbert Held INSIDE Upper Layer Operations; Address Translation; Layer 3 Switching; Layer 4 Switching OVERVIEW The first series of LAN switches
Networking Virtualization Using FPGAs
 Networking Virtualization Using FPGAs Russell Tessier, Deepak Unnikrishnan, Dong Yin, and Lixin Gao Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Massachusetts,
Networking Virtualization Using FPGAs Russell Tessier, Deepak Unnikrishnan, Dong Yin, and Lixin Gao Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Massachusetts,
IP Link Best Practices for Network Integration and Security. Introduction...2. Passwords...4 ACL...5 VLAN...6. Protocols...6. Conclusion...
 IP Link Best Practices for Network Integration and Security Table of Contents Introduction...2 Passwords...4 ACL...5 VLAN...6 Protocols...6 Conclusion...9 Abstract Extron IP Link technology enables A/V
IP Link Best Practices for Network Integration and Security Table of Contents Introduction...2 Passwords...4 ACL...5 VLAN...6 Protocols...6 Conclusion...9 Abstract Extron IP Link technology enables A/V
Exploiting Stateful Inspection of Network Security in Reconfigurable Hardware
 Exploiting Stateful Inspection of Network Security in Reconfigurable Hardware Shaomeng Li, Jim Tørresen, Oddvar Søråsen Department of Informatics University of Oslo N-0316 Oslo, Norway {shaomenl, jimtoer,
Exploiting Stateful Inspection of Network Security in Reconfigurable Hardware Shaomeng Li, Jim Tørresen, Oddvar Søråsen Department of Informatics University of Oslo N-0316 Oslo, Norway {shaomenl, jimtoer,
A low-cost, connection aware, load-balancing solution for distributing Gigabit Ethernet traffic between two intrusion detection systems
 Iowa State University Digital Repository @ Iowa State University Graduate Theses and Dissertations Graduate College 2010 A low-cost, connection aware, load-balancing solution for distributing Gigabit Ethernet
Iowa State University Digital Repository @ Iowa State University Graduate Theses and Dissertations Graduate College 2010 A low-cost, connection aware, load-balancing solution for distributing Gigabit Ethernet
Networking. Systems Design and. Development. CRC Press. Taylor & Francis Croup. Boca Raton London New York. CRC Press is an imprint of the
 Networking Systems Design and Development Lee Chao CRC Press Taylor & Francis Croup Boca Raton London New York CRC Press is an imprint of the Taylor & Francis Croup, an Informa business AN AUERBACH BOOK
Networking Systems Design and Development Lee Chao CRC Press Taylor & Francis Croup Boca Raton London New York CRC Press is an imprint of the Taylor & Francis Croup, an Informa business AN AUERBACH BOOK
Network Virtualization and Data Center Networks 263-3825-00 Data Center Virtualization - Basics. Qin Yin Fall Semester 2013
 Network Virtualization and Data Center Networks 263-3825-00 Data Center Virtualization - Basics Qin Yin Fall Semester 2013 1 Walmart s Data Center 2 Amadeus Data Center 3 Google s Data Center 4 Data Center
Network Virtualization and Data Center Networks 263-3825-00 Data Center Virtualization - Basics Qin Yin Fall Semester 2013 1 Walmart s Data Center 2 Amadeus Data Center 3 Google s Data Center 4 Data Center
Facility Usage Scenarios
 Facility Usage Scenarios GDD-06-41 GENI: Global Environment for Network Innovations December 22, 2006 Status: Draft (Version 0.1) Note to the reader: this document is a work in progress and continues to
Facility Usage Scenarios GDD-06-41 GENI: Global Environment for Network Innovations December 22, 2006 Status: Draft (Version 0.1) Note to the reader: this document is a work in progress and continues to
Software Defined Networking and the design of OpenFlow switches
 Software Defined Networking and the design of OpenFlow switches Paolo Giaccone Notes for the class on Packet Switch Architectures Politecnico di Torino December 2015 Outline 1 Introduction to SDN 2 OpenFlow
Software Defined Networking and the design of OpenFlow switches Paolo Giaccone Notes for the class on Packet Switch Architectures Politecnico di Torino December 2015 Outline 1 Introduction to SDN 2 OpenFlow
The new frontier of the DATA acquisition using 1 and 10 Gb/s Ethernet links. Filippo Costa on behalf of the ALICE DAQ group
 The new frontier of the DATA acquisition using 1 and 10 Gb/s Ethernet links Filippo Costa on behalf of the ALICE DAQ group DATE software 2 DATE (ALICE Data Acquisition and Test Environment) ALICE is a
The new frontier of the DATA acquisition using 1 and 10 Gb/s Ethernet links Filippo Costa on behalf of the ALICE DAQ group DATE software 2 DATE (ALICE Data Acquisition and Test Environment) ALICE is a
Network Simulation Traffic, Paths and Impairment
 Network Simulation Traffic, Paths and Impairment Summary Network simulation software and hardware appliances can emulate networks and network hardware. Wide Area Network (WAN) emulation, by simulating
Network Simulation Traffic, Paths and Impairment Summary Network simulation software and hardware appliances can emulate networks and network hardware. Wide Area Network (WAN) emulation, by simulating
OpenFlow: History and Overview. Demo of OpenFlow@home routers
 Affan A. Syed affan.syed@nu.edu.pk Syed Ali Khayam ali.khayam@seecs.nust.edu.pk OpenFlow: History and Overview Dr. Affan A. Syed OpenFlow and Software Defined Networking Dr. Syed Ali Khayam Demo of OpenFlow@home
Affan A. Syed affan.syed@nu.edu.pk Syed Ali Khayam ali.khayam@seecs.nust.edu.pk OpenFlow: History and Overview Dr. Affan A. Syed OpenFlow and Software Defined Networking Dr. Syed Ali Khayam Demo of OpenFlow@home
Introduction To Computer Networking
 Introduction To Computer Networking Alex S. 1 Introduction 1.1 Serial Lines Serial lines are generally the most basic and most common communication medium you can have between computers and/or equipment.
Introduction To Computer Networking Alex S. 1 Introduction 1.1 Serial Lines Serial lines are generally the most basic and most common communication medium you can have between computers and/or equipment.
Executive Summary and Purpose
 ver,1.0 Hardening and Securing Opengear Devices Copyright Opengear Inc. 2013. All Rights Reserved. Information in this document is subject to change without notice and does not represent a commitment on
ver,1.0 Hardening and Securing Opengear Devices Copyright Opengear Inc. 2013. All Rights Reserved. Information in this document is subject to change without notice and does not represent a commitment on
TCP Offload Engines. As network interconnect speeds advance to Gigabit. Introduction to
 Introduction to TCP Offload Engines By implementing a TCP Offload Engine (TOE) in high-speed computing environments, administrators can help relieve network bottlenecks and improve application performance.
Introduction to TCP Offload Engines By implementing a TCP Offload Engine (TOE) in high-speed computing environments, administrators can help relieve network bottlenecks and improve application performance.
Multiple Service Load-Balancing with OpenFlow
 2012 IEEE 13th International Conference on High Performance Switching and Routing Multiple Service Load-Balancing with OpenFlow Marc Koerner Technische Universitaet Berlin Department of Telecommunication
2012 IEEE 13th International Conference on High Performance Switching and Routing Multiple Service Load-Balancing with OpenFlow Marc Koerner Technische Universitaet Berlin Department of Telecommunication
How To Learn Cisco Cisco Ios And Cisco Vlan
 Interconnecting Cisco Networking Devices: Accelerated Course CCNAX v2.0; 5 Days, Instructor-led Course Description Interconnecting Cisco Networking Devices: Accelerated (CCNAX) v2.0 is a 60-hour instructor-led
Interconnecting Cisco Networking Devices: Accelerated Course CCNAX v2.0; 5 Days, Instructor-led Course Description Interconnecting Cisco Networking Devices: Accelerated (CCNAX) v2.0 is a 60-hour instructor-led
Security+ Guide to Network Security Fundamentals, Fourth Edition. Chapter 6 Network Security
 Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 6 Network Security Objectives List the different types of network security devices and explain how they can be used Define network
Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 6 Network Security Objectives List the different types of network security devices and explain how they can be used Define network
NLoad Balancing Stackable Switch
 NLoad Balancing Stackable Switch Now you can implement load balancing when and where you need it to support all your information applications. The, the most recent addition to the Avaya P330 stackable
NLoad Balancing Stackable Switch Now you can implement load balancing when and where you need it to support all your information applications. The, the most recent addition to the Avaya P330 stackable
Set Up a VM-Series Firewall on the Citrix SDX Server
 Set Up a VM-Series Firewall on the Citrix SDX Server Palo Alto Networks VM-Series Deployment Guide PAN-OS 6.1 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa
Set Up a VM-Series Firewall on the Citrix SDX Server Palo Alto Networks VM-Series Deployment Guide PAN-OS 6.1 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa
Stateful Inspection Technology
 Stateful Inspection Technology Security Requirements TECH NOTE In order to provide robust security, a firewall must track and control the flow of communication passing through it. To reach control decisions
Stateful Inspection Technology Security Requirements TECH NOTE In order to provide robust security, a firewall must track and control the flow of communication passing through it. To reach control decisions
The Lagopus SDN Software Switch. 3.1 SDN and OpenFlow. 3. Cloud Computing Technology
 3. The Lagopus SDN Software Switch Here we explain the capabilities of the new Lagopus software switch in detail, starting with the basics of SDN and OpenFlow. 3.1 SDN and OpenFlow Those engaged in network-related
3. The Lagopus SDN Software Switch Here we explain the capabilities of the new Lagopus software switch in detail, starting with the basics of SDN and OpenFlow. 3.1 SDN and OpenFlow Those engaged in network-related
Pre-lab and In-class Laboratory Exercise 10 (L10)
 ECE/CS 4984: Wireless Networks and Mobile Systems Pre-lab and In-class Laboratory Exercise 10 (L10) Part I Objectives and Lab Materials Objective The objectives of this lab are to: Familiarize students
ECE/CS 4984: Wireless Networks and Mobile Systems Pre-lab and In-class Laboratory Exercise 10 (L10) Part I Objectives and Lab Materials Objective The objectives of this lab are to: Familiarize students
What is LOG Storm and what is it useful for?
 What is LOG Storm and what is it useful for? LOG Storm is a high-speed digital data logger used for recording and analyzing the activity from embedded electronic systems digital bus and data lines. It
What is LOG Storm and what is it useful for? LOG Storm is a high-speed digital data logger used for recording and analyzing the activity from embedded electronic systems digital bus and data lines. It
Cisco Integrated Services Routers Performance Overview
 Integrated Services Routers Performance Overview What You Will Learn The Integrated Services Routers Generation 2 (ISR G2) provide a robust platform for delivering WAN services, unified communications,
Integrated Services Routers Performance Overview What You Will Learn The Integrated Services Routers Generation 2 (ISR G2) provide a robust platform for delivering WAN services, unified communications,
Implementing the Application Control Engine Service Module
 Course: Implementing the Application Control Engine Service Module Duration: 4 Day Hands-On Lab & Lecture Course Price: $ 2,995.00 Learning Credits: 30 Hitachi HiPass: 4 Description: Implementing the Application
Course: Implementing the Application Control Engine Service Module Duration: 4 Day Hands-On Lab & Lecture Course Price: $ 2,995.00 Learning Credits: 30 Hitachi HiPass: 4 Description: Implementing the Application
Packet Sniffer Detection with AntiSniff
 Ryan Spangler University of Wisconsin - Whitewater Department of Computer and Network Administration May 2003 Abstract Packet sniffing is a technique of monitoring every packet that crosses the network.
Ryan Spangler University of Wisconsin - Whitewater Department of Computer and Network Administration May 2003 Abstract Packet sniffing is a technique of monitoring every packet that crosses the network.
Universal Flash Storage: Mobilize Your Data
 White Paper Universal Flash Storage: Mobilize Your Data Executive Summary The explosive growth in portable devices over the past decade continues to challenge manufacturers wishing to add memory to their
White Paper Universal Flash Storage: Mobilize Your Data Executive Summary The explosive growth in portable devices over the past decade continues to challenge manufacturers wishing to add memory to their
Troubleshooting and Maintaining Cisco IP Networks Volume 1
 Troubleshooting and Maintaining Cisco IP Networks Volume 1 Course Introduction Learner Skills and Knowledge Course Goal and E Learning Goal and Course Flow Additional Cisco Glossary of Terms Your Training
Troubleshooting and Maintaining Cisco IP Networks Volume 1 Course Introduction Learner Skills and Knowledge Course Goal and E Learning Goal and Course Flow Additional Cisco Glossary of Terms Your Training
What s New in VMware vsphere 5.5 Networking
 VMware vsphere 5.5 TECHNICAL MARKETING DOCUMENTATION Table of Contents Introduction.................................................................. 3 VMware vsphere Distributed Switch Enhancements..............................
VMware vsphere 5.5 TECHNICAL MARKETING DOCUMENTATION Table of Contents Introduction.................................................................. 3 VMware vsphere Distributed Switch Enhancements..............................
Ethernet. Ethernet. Network Devices
 Ethernet Babak Kia Adjunct Professor Boston University College of Engineering ENG SC757 - Advanced Microprocessor Design Ethernet Ethernet is a term used to refer to a diverse set of frame based networking
Ethernet Babak Kia Adjunct Professor Boston University College of Engineering ENG SC757 - Advanced Microprocessor Design Ethernet Ethernet is a term used to refer to a diverse set of frame based networking
Networking Technology Online Course Outline
 Networking Technology Online Course Outline Introduction Networking Technology Introduction Welcome to InfoComm University About InfoComm International About Networking Technology Network Technology Course
Networking Technology Online Course Outline Introduction Networking Technology Introduction Welcome to InfoComm University About InfoComm International About Networking Technology Network Technology Course
LAN extensions for Instrumentation
 LAN extensions for Instrumentation LXI: It s About Your Time It took years for Ethernet and the Web to transform the way we work. Now it s time for both to transform test systems. That s why leading test
LAN extensions for Instrumentation LXI: It s About Your Time It took years for Ethernet and the Web to transform the way we work. Now it s time for both to transform test systems. That s why leading test
Case Study for Layer 3 Authentication and Encryption
 CHAPTER 2 Case Study for Layer 3 Authentication and Encryption This chapter explains the basic tasks for configuring a multi-service, extranet Virtual Private Network (VPN) between a Cisco Secure VPN Client
CHAPTER 2 Case Study for Layer 3 Authentication and Encryption This chapter explains the basic tasks for configuring a multi-service, extranet Virtual Private Network (VPN) between a Cisco Secure VPN Client
Make a folder named Lab3. We will be using Unix redirection commands to create several output files in that folder.
 CMSC 355 Lab 3 : Penetration Testing Tools Due: September 31, 2010 In the previous lab, we used some basic system administration tools to figure out which programs where running on a system and which files
CMSC 355 Lab 3 : Penetration Testing Tools Due: September 31, 2010 In the previous lab, we used some basic system administration tools to figure out which programs where running on a system and which files
Course Overview: Learn the essential skills needed to set up, configure, support, and troubleshoot your TCP/IP-based network.
 Course Name: TCP/IP Networking Course Overview: Learn the essential skills needed to set up, configure, support, and troubleshoot your TCP/IP-based network. TCP/IP is the globally accepted group of protocols
Course Name: TCP/IP Networking Course Overview: Learn the essential skills needed to set up, configure, support, and troubleshoot your TCP/IP-based network. TCP/IP is the globally accepted group of protocols
IP Networking. Overview. Networks Impact Daily Life. IP Networking - Part 1. How Networks Impact Daily Life. How Networks Impact Daily Life
 Overview Dipl.-Ing. Peter Schrotter Institute of Communication Networks and Satellite Communications Graz University of Technology, Austria Fundamentals of Communicating over the Network Application Layer
Overview Dipl.-Ing. Peter Schrotter Institute of Communication Networks and Satellite Communications Graz University of Technology, Austria Fundamentals of Communicating over the Network Application Layer
PCI Express Overview. And, by the way, they need to do it in less time.
 PCI Express Overview Introduction This paper is intended to introduce design engineers, system architects and business managers to the PCI Express protocol and how this interconnect technology fits into
PCI Express Overview Introduction This paper is intended to introduce design engineers, system architects and business managers to the PCI Express protocol and how this interconnect technology fits into
Internetworking II: VPNs, MPLS, and Traffic Engineering
 Internetworking II: VPNs, MPLS, and Traffic Engineering 3035/GZ01 Networked Systems Kyle Jamieson Lecture 10 Department of Computer Science University College London Taxonomy of communica@on networks Virtual
Internetworking II: VPNs, MPLS, and Traffic Engineering 3035/GZ01 Networked Systems Kyle Jamieson Lecture 10 Department of Computer Science University College London Taxonomy of communica@on networks Virtual
Software Defined Networks
 Software Defined Networks Damiano Carra Università degli Studi di Verona Dipartimento di Informatica Acknowledgements! Credits Part of the course material is based on slides provided by the following authors
Software Defined Networks Damiano Carra Università degli Studi di Verona Dipartimento di Informatica Acknowledgements! Credits Part of the course material is based on slides provided by the following authors
CHAPTER 3 STATIC ROUTING
 CHAPTER 3 STATIC ROUTING This chapter addresses the end-to-end delivery service of IP and explains how IP routers and hosts handle IP datagrams. The first section discusses how datagrams are forwarded
CHAPTER 3 STATIC ROUTING This chapter addresses the end-to-end delivery service of IP and explains how IP routers and hosts handle IP datagrams. The first section discusses how datagrams are forwarded
Performance of Software Switching
 Performance of Software Switching Based on papers in IEEE HPSR 2011 and IFIP/ACM Performance 2011 Nuutti Varis, Jukka Manner Department of Communications and Networking (COMNET) Agenda Motivation Performance
Performance of Software Switching Based on papers in IEEE HPSR 2011 and IFIP/ACM Performance 2011 Nuutti Varis, Jukka Manner Department of Communications and Networking (COMNET) Agenda Motivation Performance
Packet Capture. Document Scope. SonicOS Enhanced Packet Capture
 Packet Capture Document Scope This solutions document describes how to configure and use the packet capture feature in SonicOS Enhanced. This document contains the following sections: Feature Overview
Packet Capture Document Scope This solutions document describes how to configure and use the packet capture feature in SonicOS Enhanced. This document contains the following sections: Feature Overview
TCP/IP Security Problems. History that still teaches
 TCP/IP Security Problems History that still teaches 1 remote login without a password rsh and rcp were programs that allowed you to login from a remote site without a password The.rhosts file in your home
TCP/IP Security Problems History that still teaches 1 remote login without a password rsh and rcp were programs that allowed you to login from a remote site without a password The.rhosts file in your home
Network Access Security. Lesson 10
 Network Access Security Lesson 10 Objectives Exam Objective Matrix Technology Skill Covered Exam Objective Exam Objective Number Firewalls Given a scenario, install and configure routers and switches.
Network Access Security Lesson 10 Objectives Exam Objective Matrix Technology Skill Covered Exam Objective Exam Objective Number Firewalls Given a scenario, install and configure routers and switches.
How To Understand and Configure Your Network for IntraVUE
 How To Understand and Configure Your Network for IntraVUE Summary This document attempts to standardize the methods used to configure Intrauve in situations where there is little or no understanding of
How To Understand and Configure Your Network for IntraVUE Summary This document attempts to standardize the methods used to configure Intrauve in situations where there is little or no understanding of
