TECHNICAL NOTE INSTALLING AND CONFIGURING ALE USING A CLI. Installing the Adaptive Log Exporter
|
|
|
- Shana Peters
- 9 years ago
- Views:
Transcription
1 TECHNICAL NOTE INSTALLING AND CONFIGURING ALE USING A CLI NOVEMBER 2010 If you want to install the Adaptive Log Exporter without the installation wizard, this document provides information about installing the Adaptive Log Exporter using a command line interface (CLI) utility. This CLI utility allows you to deploy your Adaptive Log Exporter to multiple remote systems in your deployment using any third-party product that allows remote or batch installs, for example, MSI Packaging Tools or Message-Oriented Middleware (MOM). Note: The procedures in this document assume an advanced knowledge of network administration. This document includes: Installing the Adaptive Log Exporter Updating Your Windows Event Log Device Updating Your TCP Syslog Plug-in Adaptive Log Exporter CLI Utility Examples Windows Event Log Device CLI Utility Examples TCP Syslog Plug-in CLI Utility Examples Installing the Adaptive Log Exporter Step 1 Step 2 Step 3 To install the Adaptive Log Exporter using a CLI: Obtain the Adaptive Log Exporter CLI utility from the Juniper customer support web site: Note: Once you download the Adaptive Log Exporter CLI utility, you must select a distribution method to deploy the Adaptive Log Exporter to remote systems in your deployment. Close all other active applications before installing the Adaptive Log Exporter. In a Windows CLI, enter the following command: Release TN D
2 2 TECHNICAL NOTE Step 4 s Note: The SP-, VERYSILENT, and SUPPRESSMSGBOXES parameters are required parameters for each command entry. Enter parameters, as necessary. For more information, see s. When entering the CLI utility options, the following parameters are available: Required s Optional s Windows Event Log Monitoring s Note: All parameters are case sensitive. Required s The following parameters are required for the CLI utility: /SP- /VERYSILENT /SUPPRESSMSGBOXES Optional s The following table provides the optional parameters for use with the CLI utility: Table<n=1> Optional s /DIR /COMPONENTS /NOICONS /GROUP Specify the fully qualified path name to the destination directory for the Adaptive Log Exporter installation files. By default, the Adaptive Log Exporter is installed in the Program Files/Adaptive Log Exporter directory. Specify the list of Adaptive Log Exporter components you want to install. The options are: main - Mandatory. You must specify this parameter to install the base components of the Adaptive Log Exporter service. ui - Specify this parameter to install the user interface. If you do not specify any parameters in the /COMPONENTS option, the main and ui components are installed by default. Specify if you do not want to include the Adaptive Log Exporter icon to appear in your Start menu options. By default, the Start menu displays the application as Adaptive Log Exporter. This parameter allows you to define a new group name. Release TN D
3 Updating Your Windows Event Log Device 3 Windows Event Log Monitoring s The Windows event log monitoring parameters allow you to automatically create a Windows event log device and a corresponding syslog destination. All of the below parameters must be included in the command. The following table provides the Windows event log monitoring parameters: Table 1-1 Windows Event Log Monitoring s /MONITOR /MONITORDEST /MONITORPROTO /DEVICEADDRESS Specify using a comma separated list of event logs you want to monitor. For example: /MONITOR=Application,Security,System Specify the syslog destination that you want to receive the logs. You can specify this value in an <IP address or hostname>:<port> format. The port number defaults to 514 if not specified. Specify the protocol to use when sending syslog log files. The protocol can be specified as TCP or UDP. The protocol defaults to UDP if not specified. Specify the hostname or IP address you want to use in the syslog header when events are created. To the syslog receiver, this will appear as though this device address generated the message. Updating Your Windows Event Log Device Once you have installed the Adaptive Log Exporter using the CLI utility (see Installing the Adaptive Log Exporter), you can use the CLI utility to update your Windows Event Log Device configuration. Your Windows Event Log Device must be configured in your deployment before you update your Windows Event Log Device using the CLI. Also, ensure your Windows Event Log Device configuration includes the default configuration values before you apply the update. Step 1 Step 2 Step 3 To update your Windows Event Log Device configuration: Download the Windows Event Log Device plug-in from the Juniper customer support web site: Close all other active applications before installing the Windows Event Log Device plug-in. In a Windows CLI, enter the following command: /SUPPRESSMSGBOXES /PATCHONLY Note: The SP-, VERYSILENT, and SUPPRESSMSGBOXES parameters are required parameters for each command entry. TN D Release
4 4 TECHNICAL NOTE Step 4 Enter parameters, as necessary. Table 1-2 Windows Event Log Monitoring s /MONITOR /MONITORDEST /DEVICEADDRESS /PATCHONLY Specify using a comma separated list of event logs you want to monitor. For example: /MONITOR=Application,Security,System Specify the syslog destination that you want to receive the logs. You can specify this value in an <IP address or hostname>:<port> format. The port number defaults to 514 if not specified. Specify the hostname or IP address you want to use in the syslog header when events are created. To the syslog receiver, this appears as though this device address generated the message. Specify this parameter if you update your configuration to a later version of the Windows Event Log plug-in without modifying the existing configuration. Updating Your TCP Syslog Plug-in Step 1 Step 2 Step 3 Step 4 Once you have installed the Adaptive Log Exporter using the CLI utility (see Installing the Adaptive Log Exporter), you can use the CLI utility to update your TCP Syslog plug-in. To update the TCP Syslog plug-in using the CLI: Download the TCP Syslog plug-in from the Juniper customer support web site: Close all other active applications before installing an update to the TCP Syslog plug-in. In a Windows CLI, update the plug-in using the following command: /SUPPRESSMSGBOXES /PATCHONLY Note: The SP-, VERYSILENT, and SUPPRESSMSGBOXES parameters are required parameters for each command entry. Enter parameters, as necessary. Table 1-3 Windows Event Log Monitoring s /MONITOR /MONITORDEST Specify using a comma separated list of event logs you want to monitor. For example: /MONITOR=Application,Security,System Specify the syslog destination that you want to receive the logs. You can specify this value in an <IP address or hostname>:<port> format. The port number defaults to 514 if not specified. Release TN D
5 Adaptive Log Exporter CLI Utility Examples 5 Table 1-3 Windows Event Log Monitoring s (continued) /DEVICEADDRESS /PATCHONLY Specify the hostname or IP address you want to use in the syslog header when events are created. To the syslog receiver, this appears as though this device address generated the message. Specify this parameter if you update your configuration to a later version of the Windows Event Log plug-in without modifying the existing configuration. Adaptive Log Exporter CLI Utility Examples Install Service Only Service Only Monitoring Windows Security Log Full Install Full Install Monitoring Windows Security Logs This section provides several examples of using the CLI utility including: Install Service Only Service Only Monitoring Windows Security Log Full Install Full Install Monitoring Windows Security Logs If you want to install the Adaptive Log Exporter functionality without the user interface, enter the following command: /COMPONENTS=main If you want to install the Adaptive Log Exporter functionality without the user interface, and you also want to monitor Windows security logs and send events using the default syslog port (UDP port 514), enter the following command: /COMPONENTS=main /MONITOR=Security /MONITORDEST= /DEVICEADDRESS=Device hostname or IP address If you want to the fully install the Adaptive Log Exporter, including the user interface and requiring no further configuration, enter the following command: /COMPONENTS=main,ui If you want to fully install the Adaptive Log Exporter, including the user interface and the ability to monitor Windows Security Logs, enter the following command: /COMPONENTS=main,ui /MONITOR=Security /MONITORDEST=Syslog Destination hostname or IP address /DEVICEADDRESS=Device hostname or IP address TN D Release
6 6 TECHNICAL NOTE Windows Event Log Device CLI Utility Examples Update IP Address for Windows Event Log Device Update Logs Monitored for Windows Event Log Device Copy Files for Windows Event Log Configuration Add a New Windows Event Log Device This section provides several examples of using the CLI utility to update your Windows Event Log Device including: Update IP Address for Windows Event Log Device Update Logs Monitored for Windows Event Log Device Copy Files for Windows Event Log Configuration Add a New Windows Event Log Device If you install the Windows Event Log Device plug-in and want to modify the IP address of the Window Event Log Device, enter the following command: /SUPPRESSMSGBOXES /DEVICEADDRESS=Device hostname or IP address If you install the Windows Event Log Device plug-in and want to change the type of logs you are monitoring, enter the following command: /SUPPRESSMSGBOXES /MONITOR=Security,System If you install the Windows Event Log Device plug-in and want to preserve your existing configuration while copying the necessary updated files from a patch, enter the following command: /SUPPRESSMSGBOXES /PATCHONLY To install a new Windows Event Log Device plug-in, enter the following command: /SUPPRESSMSGBOXES /COMPONENTS=main /DEVICEADDRESS=Device hostname or IP address /MONITOR=Security,Application,System /MONITORDEST=Syslog Destination hostname or IP address:514 TCP Syslog Plug-in CLI Utility Examples Update IP Address for TCP Syslog Plug-in This section provides several examples of using the CLI utility to update your TCP Syslog plug-in including: Update IP Address for TCP Syslog Plug-in Update Logs Monitored for a TCP Syslog Plug-in Copy Files for TCP Syslog Plug-in Add a New TCP Syslog Plug-in If you install the TCP Syslog plug-in and want to modify the device address, enter the following command: ALE_TCPSyslogPlugin_setup.exe /SP- /VERYSILENT /SUPPRESSMSGBOXES /DEVICEADDRESS=Device hostname or IP address Release TN D
7 TCP Syslog Plug-in CLI Utility Examples 7 Update Logs Monitored for a TCP Syslog Plug-in Copy Files for TCP Syslog Plug-in Add a New TCP Syslog Plug-in If you install the TCP Syslog plug-in and want to change the type of logs you are monitoring, enter the following command: ALE_TCPSyslogPlugin_setup.exe /SP- /VERYSILENT /SUPPRESSMSGBOXES /MONITOR=Security,System If you install the TCP Syslog plug-in and want to preserve your existing configuration while copying the necessary updated files from a patch, enter the following command: ALE_TCPSyslogPlugin_setup.exe /SP- /VERYSILENT /SUPPRESSMSGBOXES /PATCHONLY To install the TCP Syslog plug-in on a new device, enter the following command: ALE_TCPSyslogPlugin_setup.exe /SP- /VERYSILENT /SUPPRESSMSGBOXES /COMPONENTS=main /DEVICEADDRESS=Device hostname or IP address /MONITOR=Security,Application,System /MONITORDEST=Syslog Destination hostname or IP address:514 TN D Release
8 Juniper Networks, Inc North Mathilda Avenue Sunnyvale, CA USA Copyright Notice Copyright 2010 Juniper Networks, Inc. All rights reserved. Juniper Networks and the Juniper Networks logo are registered trademarks of Juniper Networks Inc. in the United States and other countries. All other trademarks, service marks, registered trademarks, or registered service marks in this document are the property of Juniper Networks or their respective owners. All specifications are subject to change without notice. Juniper Networks assumes no responsibility for any inaccuracies in this document or for any obligation to update information in this document. Juniper Networks reserves the right to change, modify, transfer, or otherwise revise this publication without notice.
Adaptive Log Exporter Users Guide
 Security Threat Response Manager Release 2012.0 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2012-05-30 Copyright Notice Copyright 2012
Security Threat Response Manager Release 2012.0 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2012-05-30 Copyright Notice Copyright 2012
Adaptive Log Exporter Users Guide
 IBM Security QRadar Version 7.1.0 (MR1) Note: Before using this information and the product that it supports, read the information in Notices and Trademarks on page page 119. Copyright IBM Corp. 2012,
IBM Security QRadar Version 7.1.0 (MR1) Note: Before using this information and the product that it supports, read the information in Notices and Trademarks on page page 119. Copyright IBM Corp. 2012,
Unless otherwise noted, all references to STRM refer to STRM, STRM Log Manager, and STRM Network Anomaly Detection.
 TECHNICAL NOTE FORWARDING LOGS USING TAIL2SYSLOG MARCH 2013 The Tail2Syslog support script provides a method for monitoring and forwarding events to STRM using syslog for real-time correlation. Tail2Syslog
TECHNICAL NOTE FORWARDING LOGS USING TAIL2SYSLOG MARCH 2013 The Tail2Syslog support script provides a method for monitoring and forwarding events to STRM using syslog for real-time correlation. Tail2Syslog
After you have created your text file, see Adding a Log Source.
 TECHNICAL UPLOADING TEXT FILES INTO A REFERENCE SET MAY 2012 This technical note provides information on how to upload a text file into a STRM reference set. You need to be comfortable with writing regular
TECHNICAL UPLOADING TEXT FILES INTO A REFERENCE SET MAY 2012 This technical note provides information on how to upload a text file into a STRM reference set. You need to be comfortable with writing regular
Setting up an icap Server for ISG- 1000/2000 AV Support
 Application Note Setting up an icap Server for ISG- 1000/2000 AV Support Version 1.1 Ronald Ng AJTAC Engineer AV/DI/UF Specialist Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA
Application Note Setting up an icap Server for ISG- 1000/2000 AV Support Version 1.1 Ronald Ng AJTAC Engineer AV/DI/UF Specialist Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA
TECHNICAL NOTE SETTING UP A STRM UPDATE SERVER. Configuring your Update Server
 TECHNICAL NOTE SETTING UP A STRM UPDATE SERVER AUGUST 2012 STRM uses system configuration files to provide useful characterizations of network data flows. Updates to the system configuration files, available
TECHNICAL NOTE SETTING UP A STRM UPDATE SERVER AUGUST 2012 STRM uses system configuration files to provide useful characterizations of network data flows. Updates to the system configuration files, available
IBM Security QRadar Version 7.1.0 (MR1) WinCollect User Guide
 IBM Security QRadar Version 7.1.0 (MR1) WinCollect User Guide Note: Before using this information and the product that it supports, read the information in Notices and Trademarks on page 59. Copyright
IBM Security QRadar Version 7.1.0 (MR1) WinCollect User Guide Note: Before using this information and the product that it supports, read the information in Notices and Trademarks on page 59. Copyright
By default, STRM provides an untrusted SSL certificate. You can replace the untrusted SSL certificate with a self-signed or trusted certificate.
 TECHNICAL NOTE REPLACING THE SSL CERTIFICATE AUGUST 2012 By default, STRM provides an untrusted SSL certificate. You can replace the untrusted SSL certificate with a self-signed or trusted certificate.
TECHNICAL NOTE REPLACING THE SSL CERTIFICATE AUGUST 2012 By default, STRM provides an untrusted SSL certificate. You can replace the untrusted SSL certificate with a self-signed or trusted certificate.
Identity-Based Traffic Logging and Reporting
 Application Note Identity-Based Traffic Logging and Reporting Using UAC in Conjunction with NSM and Infranet Enforcers to Give Additional, User-Identified Visibility into Network Traffic Juniper Networks,
Application Note Identity-Based Traffic Logging and Reporting Using UAC in Conjunction with NSM and Infranet Enforcers to Give Additional, User-Identified Visibility into Network Traffic Juniper Networks,
Juniper Secure Analytics
 Juniper Secure Analytics Big Data Management Guide Release 2014.2 Published: 2014-08-12 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All
Juniper Secure Analytics Big Data Management Guide Release 2014.2 Published: 2014-08-12 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All
Juniper Secure Analytics
 Juniper Secure Analytics Big Data Management Guide Release 2014.1 Published: 2014-03-17 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All
Juniper Secure Analytics Big Data Management Guide Release 2014.1 Published: 2014-03-17 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All
Migrating Log Manager to JSA
 Juniper Log Manager Release 2014.4 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2015-03-02 Copyright Notice Copyright 2015 Juniper Networks,
Juniper Log Manager Release 2014.4 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2015-03-02 Copyright Notice Copyright 2015 Juniper Networks,
Unless otherwise noted, all references to STRM refer to STRM, STRM Log Manager, and STRM Network Anomaly Detection.
 TECHNICAL NOTE INSTALLING STRM USING A BOOTABLE USB FLASH-DRIVE JULY 2013 This technical note provides information on how to re-install STRM software on the STRM appliances using a bootable USB flash-drive.
TECHNICAL NOTE INSTALLING STRM USING A BOOTABLE USB FLASH-DRIVE JULY 2013 This technical note provides information on how to re-install STRM software on the STRM appliances using a bootable USB flash-drive.
This technical note provides information on how to customize your email notifications. This section includes the following topics:
 TECHNICAL NOTE CONFIGURING CUSTOM EMAIL NOTIFICATIONS AUGUST 2012 When configuring rules in STRM, you can specify that each time the rule generates a response, an email notification is sent to recipients
TECHNICAL NOTE CONFIGURING CUSTOM EMAIL NOTIFICATIONS AUGUST 2012 When configuring rules in STRM, you can specify that each time the rule generates a response, an email notification is sent to recipients
RSA Security Analytics
 RSA Security Analytics Event Source Log Configuration Guide RSA Authentication Manager and User Credential Manager Last Modified: Friday, March 13, 2015 Event Source Product Information: Vendor: RSA, The
RSA Security Analytics Event Source Log Configuration Guide RSA Authentication Manager and User Credential Manager Last Modified: Friday, March 13, 2015 Event Source Product Information: Vendor: RSA, The
WinCollect User Guide
 Juniper Secure Analytics Release 2014.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2014-03-14 Copyright Notice Copyright 2014 Juniper
Juniper Secure Analytics Release 2014.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2014-03-14 Copyright Notice Copyright 2014 Juniper
Unless otherwise noted, all references to STRM refer to STRM, STRM Log Manager, and STRM Network Anomaly Detection.
 TECHNICAL USING NFS FOR STRM BACKUPS SEPTEMBER 2013 This technical note provides guidelines and procedures for using a Network File System (NFS) storage solution in your STRM deployment. Unless otherwise
TECHNICAL USING NFS FOR STRM BACKUPS SEPTEMBER 2013 This technical note provides guidelines and procedures for using a Network File System (NFS) storage solution in your STRM deployment. Unless otherwise
NSM Plug-In Users Guide
 Juniper Secure Analytics Release 2014.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2014-03-14 Copyright Notice Copyright 2014 Juniper
Juniper Secure Analytics Release 2014.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2014-03-14 Copyright Notice Copyright 2014 Juniper
IF-MAP FEDERATION WITH JUNIPER NETWORKS UNIFIED ACCESS CONTROL
 IF-MAP FEDERATION WITH JUNIPER NETWORKS UNIFIED ACCESS CONTROL An illustrated Guide to Configuring a Simple IF-MAP Federated Network Juniper Networks, Inc. 1 Table of Contents Introduction...3 Scope...3
IF-MAP FEDERATION WITH JUNIPER NETWORKS UNIFIED ACCESS CONTROL An illustrated Guide to Configuring a Simple IF-MAP Federated Network Juniper Networks, Inc. 1 Table of Contents Introduction...3 Scope...3
REPLACING THE SSL CERTIFICATE
 Juniper Secure Analytics REPLACING THE SSL CERTIFICATE Release 2014.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2014-03-14 Copyright
Juniper Secure Analytics REPLACING THE SSL CERTIFICATE Release 2014.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2014-03-14 Copyright
Monitoring Network Traffic Using sflow Technology on EX Series Ethernet Switches
 APPLICATION NOTE Monitoring Network Traffic Using sflow Technology on EX Series Ethernet Switches Exporting sflow to Collectors Through a Separate Virtual Routing Instance Copyright 2009, Juniper Networks,
APPLICATION NOTE Monitoring Network Traffic Using sflow Technology on EX Series Ethernet Switches Exporting sflow to Collectors Through a Separate Virtual Routing Instance Copyright 2009, Juniper Networks,
MONITORING NETWORK TRAFFIC USING sflow TECHNOLOGY ON EX SERIES ETHERNET SWITCHES
 APPLICATION NOTE MONITORING NETWORK TRAFFIC USING sflow TECHNOLOGY ON EX SERIES ETHERNET SWITCHES Exporting sflow to Collectors Through a Separate Virtual Routing Instance Copyright 2010, Juniper Networks,
APPLICATION NOTE MONITORING NETWORK TRAFFIC USING sflow TECHNOLOGY ON EX SERIES ETHERNET SWITCHES Exporting sflow to Collectors Through a Separate Virtual Routing Instance Copyright 2010, Juniper Networks,
JUNOS PULSE APPCONNECT
 White Paper JUNOS PULSE APPCONNECT A Micro VPN That Allows Specific Applications on Mobile Devices to Independently Leverage the Connect Secure Gateway Copyright 2014, Juniper Networks, Inc. 1 Table of
White Paper JUNOS PULSE APPCONNECT A Micro VPN That Allows Specific Applications on Mobile Devices to Independently Leverage the Connect Secure Gateway Copyright 2014, Juniper Networks, Inc. 1 Table of
Remote Logging Agent Configuration Guide
 Remote Logging Agent Configuration Guide Powerful Authentication Management for Service Providers and Enterprises Authentication Service Delivery Made EASY Synchronization Agent Configuration Guide Copyright
Remote Logging Agent Configuration Guide Powerful Authentication Management for Service Providers and Enterprises Authentication Service Delivery Made EASY Synchronization Agent Configuration Guide Copyright
Limitation of Riverbed s Quality of Service (QoS)
 Application Note Limitation of Riverbed s Quality of Service (QoS) Riverbed s Quality of Service (QoS) configuration and limitations Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California
Application Note Limitation of Riverbed s Quality of Service (QoS) Riverbed s Quality of Service (QoS) configuration and limitations Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California
Managing Vulnerability Assessment
 Security Threat Response Manager Release 2012.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2013-03-12 Copyright Notice Copyright 2013
Security Threat Response Manager Release 2012.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2013-03-12 Copyright Notice Copyright 2013
SMART Classroom Suite 2011
 SMART Classroom Suite 2011 Windows operating systems System administrator s guide Trademark notice SMART Board, SMART Classroom Suite, SMART Notebook, SMART Response, SMART Sync, SMART Document Camera,
SMART Classroom Suite 2011 Windows operating systems System administrator s guide Trademark notice SMART Board, SMART Classroom Suite, SMART Notebook, SMART Response, SMART Sync, SMART Document Camera,
Dell One Identity Cloud Access Manager 8.0.1- How to Configure for High Availability
 Dell One Identity Cloud Access Manager 8.0.1- How to Configure for High Availability May 2015 Cloning the database Cloning the STS host Cloning the proxy host This guide describes how to extend a typical
Dell One Identity Cloud Access Manager 8.0.1- How to Configure for High Availability May 2015 Cloning the database Cloning the STS host Cloning the proxy host This guide describes how to extend a typical
Syslog Server Configuration on Wireless LAN Controllers (WLCs)
 Syslog Server Configuration on Wireless LAN Controllers (WLCs) Document ID: 107252 Contents Introduction Prerequisites Requirements Components Used Conventions Syslog Server Support on Wireless LAN Controllers
Syslog Server Configuration on Wireless LAN Controllers (WLCs) Document ID: 107252 Contents Introduction Prerequisites Requirements Components Used Conventions Syslog Server Support on Wireless LAN Controllers
Integrate Websense Web Security Gateway (WSG)
 Integrate Websense Web Security Gateway (WSG) EventTracker v7.x Publication Date: June 2, 2014 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide provides instructions
Integrate Websense Web Security Gateway (WSG) EventTracker v7.x Publication Date: June 2, 2014 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide provides instructions
For Active Directory Installation Guide
 For Active Directory Installation Guide Version 2.5.2 April 2010 Copyright 2010 Legal Notices makes no representations or warranties with respect to the contents or use of this documentation, and specifically
For Active Directory Installation Guide Version 2.5.2 April 2010 Copyright 2010 Legal Notices makes no representations or warranties with respect to the contents or use of this documentation, and specifically
JUNOScope IP Service Manager
 Datasheet JUNOScope IP Service Manager Product Description As service providers and enterprises evolve to meet the demands of their customer base, one key to success is the enhancement of operational efficiencies
Datasheet JUNOScope IP Service Manager Product Description As service providers and enterprises evolve to meet the demands of their customer base, one key to success is the enhancement of operational efficiencies
PrintFleet Local Beacon
 PrintFleet Local Beacon User Guide Version 2.5.15 as of March 3, 2008. 2008 PrintFleet Inc. All rights reserved. Copyright 2008 PrintFleet Inc. All rights reserved. PrintFleet Local Beacon User Guide.
PrintFleet Local Beacon User Guide Version 2.5.15 as of March 3, 2008. 2008 PrintFleet Inc. All rights reserved. Copyright 2008 PrintFleet Inc. All rights reserved. PrintFleet Local Beacon User Guide.
Setting Up a Unisphere Management Station for the VNX Series P/N 300-011-796 Revision A01 January 5, 2010
 Setting Up a Unisphere Management Station for the VNX Series P/N 300-011-796 Revision A01 January 5, 2010 This document describes the different types of Unisphere management stations and tells how to install
Setting Up a Unisphere Management Station for the VNX Series P/N 300-011-796 Revision A01 January 5, 2010 This document describes the different types of Unisphere management stations and tells how to install
J-Flow on J Series Services Routers and Branch SRX Series Services Gateways
 APPLICATION NOTE Juniper Flow Monitoring J-Flow on J Series Services Routers and Branch SRX Series Services Gateways Copyright 2011, Juniper Networks, Inc. 1 APPLICATION NOTE - Juniper Flow Monitoring
APPLICATION NOTE Juniper Flow Monitoring J-Flow on J Series Services Routers and Branch SRX Series Services Gateways Copyright 2011, Juniper Networks, Inc. 1 APPLICATION NOTE - Juniper Flow Monitoring
Education Software Installer 2011
 Education Software Installer 2011 Windows operating systems System administrator s guide Trademark notice SMART Notebook, SMART Document Camera, SMART Response, SMART Sync, SMART Classroom Suite, Senteo,
Education Software Installer 2011 Windows operating systems System administrator s guide Trademark notice SMART Notebook, SMART Document Camera, SMART Response, SMART Sync, SMART Classroom Suite, Senteo,
NetIQ Sentinel 7.0.1 Quick Start Guide
 NetIQ Sentinel 7.0.1 Quick Start Guide April 2012 Getting Started Use the following information to get Sentinel installed and running quickly. Meeting System Requirements on page 1 Installing Sentinel
NetIQ Sentinel 7.0.1 Quick Start Guide April 2012 Getting Started Use the following information to get Sentinel installed and running quickly. Meeting System Requirements on page 1 Installing Sentinel
RSA Security Analytics
 RSA Security Analytics Event Source Log Configuration Guide VMware NSX Last Modified: Friday, March 13, 2015 Event Source Product Information: Vendor: VMware Event Source: VMware NSX Version: 6.1.2 RSA
RSA Security Analytics Event Source Log Configuration Guide VMware NSX Last Modified: Friday, March 13, 2015 Event Source Product Information: Vendor: VMware Event Source: VMware NSX Version: 6.1.2 RSA
How to add your Weebly website to a TotalCloud hosted Server
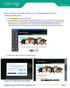 How to add your Weebly website to a TotalCloud hosted Server Creating your Weebly website: 1.) Go to weebly.com and create a free account. 2.) Build and design your personal website using the Weebly features.
How to add your Weebly website to a TotalCloud hosted Server Creating your Weebly website: 1.) Go to weebly.com and create a free account. 2.) Build and design your personal website using the Weebly features.
MIGRATING IPS SECURITY POLICY TO JUNIPER NETWORKS SRX SERIES SERVICES GATEWAYS
 APPLICATION NOTE MIGRATING IPS SECURITY POLICY TO JUNIPER NETWORKS SRX SERIES SERVICES GATEWAYS Migrating Advanced Security Policies to SRX Series Services Gateways Copyright 2009, Juniper Networks, Inc.
APPLICATION NOTE MIGRATING IPS SECURITY POLICY TO JUNIPER NETWORKS SRX SERIES SERVICES GATEWAYS Migrating Advanced Security Policies to SRX Series Services Gateways Copyright 2009, Juniper Networks, Inc.
Installing JSA Using a Bootable USB Flash Drive
 Juniper Secure Analytics Installing JSA Using a Bootable USB Flash Drive Release 2014.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published:
Juniper Secure Analytics Installing JSA Using a Bootable USB Flash Drive Release 2014.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published:
Tuning Guide. Release 2014.1. Juniper Secure Analytics. Juniper Networks, Inc. www.juniper.net
 Juniper Secure Analytics Release 2014.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2014-12-05 Copyright Notice Copyright 2014 Juniper
Juniper Secure Analytics Release 2014.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2014-12-05 Copyright Notice Copyright 2014 Juniper
Web Application Firewall
 Web Application Firewall Getting Started Guide August 3, 2015 Copyright 2014-2015 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks
Web Application Firewall Getting Started Guide August 3, 2015 Copyright 2014-2015 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks
VMware vcenter Log Insight Getting Started Guide
 VMware vcenter Log Insight Getting Started Guide vcenter Log Insight 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
VMware vcenter Log Insight Getting Started Guide vcenter Log Insight 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
How to - Install EventTracker and Change Audit Agent
 How to - Install EventTracker and Change Audit Agent Agent Deployment User Manual Publication Date: Oct.17, 2015 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract EventTracker
How to - Install EventTracker and Change Audit Agent Agent Deployment User Manual Publication Date: Oct.17, 2015 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract EventTracker
Secure, Mobile Access to Corporate Email, Applications, and Intranet Resources
 APPLICATION NOTE Juniper NETWORKS SSL VPN and Windows Mobile Secure, Mobile Access to Corporate Email, Applications, and Intranet Resources Table of Contents Introduction.........................................................................................
APPLICATION NOTE Juniper NETWORKS SSL VPN and Windows Mobile Secure, Mobile Access to Corporate Email, Applications, and Intranet Resources Table of Contents Introduction.........................................................................................
IBM Security QRadar SIEM Version 7.1.0 MR1. Vulnerability Assessment Configuration Guide
 IBM Security QRadar SIEM Version 7.1.0 MR1 Vulnerability Assessment Configuration Guide Note: Before using this information and the product that it supports, read the information in Notices and Trademarks
IBM Security QRadar SIEM Version 7.1.0 MR1 Vulnerability Assessment Configuration Guide Note: Before using this information and the product that it supports, read the information in Notices and Trademarks
RSA Security Analytics
 RSA Security Analytics Event Source Log Configuration Guide Microsoft Windows using Eventing Collection Last Modified: Thursday, July 30, 2015 Event Source Product Information: Vendor: Microsoft Event
RSA Security Analytics Event Source Log Configuration Guide Microsoft Windows using Eventing Collection Last Modified: Thursday, July 30, 2015 Event Source Product Information: Vendor: Microsoft Event
Log Sources Users Guide
 Security Threat Response Manager Release 2013.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2013-03-15 Copyright Notice Copyright 2013
Security Threat Response Manager Release 2013.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2013-03-15 Copyright Notice Copyright 2013
Using the Content Management Tool
 Security Threat Response Manager Release 2013.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2013-03-15 Copyright Notice Copyright 2013
Security Threat Response Manager Release 2013.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2013-03-15 Copyright Notice Copyright 2013
Upgrade Guide. CA Application Delivery Analysis 10.1
 Upgrade Guide CA Application Delivery Analysis 10.1 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation ) is
Upgrade Guide CA Application Delivery Analysis 10.1 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation ) is
VMWARE VIEW WITH JUNIPER NETWORKS SA SERIES SSL VPN APPLIANCES
 APPLICATION NOTE VMWARE VIEW WITH JUNIPER NETWORKS SA SERIES SSL VPN APPLIANCES Configuring Secure SSL VPN Access in a VMware Virtual Desktop Environment Copyright 2010, Juniper Networks, Inc. 1 Table
APPLICATION NOTE VMWARE VIEW WITH JUNIPER NETWORKS SA SERIES SSL VPN APPLIANCES Configuring Secure SSL VPN Access in a VMware Virtual Desktop Environment Copyright 2010, Juniper Networks, Inc. 1 Table
Quick Start Guide for Symantec Event Collector for ForeScout CounterACT
 Quick Start Guide for Symantec Event Collector for ForeScout CounterACT Quick Start Guide for Symantec Event Collector for ForeScout CounterACT The software described in this book is furnished under a
Quick Start Guide for Symantec Event Collector for ForeScout CounterACT Quick Start Guide for Symantec Event Collector for ForeScout CounterACT The software described in this book is furnished under a
Windows Firewall Configuration with Group Policy for SyAM System Client Installation
 with Group Policy for SyAM System Client Installation SyAM System Client can be deployed to systems on your network using SyAM Management Utilities. If Windows Firewall is enabled on target systems, it
with Group Policy for SyAM System Client Installation SyAM System Client can be deployed to systems on your network using SyAM Management Utilities. If Windows Firewall is enabled on target systems, it
Entrust Managed Services PKI. Configuring secure LDAP with Domain Controller digital certificates
 Entrust Managed Services Entrust Managed Services PKI Configuring secure LDAP with Domain Controller digital certificates Document issue: 1.0 Date of issue: October 2009 Copyright 2009 Entrust. All rights
Entrust Managed Services Entrust Managed Services PKI Configuring secure LDAP with Domain Controller digital certificates Document issue: 1.0 Date of issue: October 2009 Copyright 2009 Entrust. All rights
Adobe Acrobat 9 Deployment on Microsoft Windows Group Policy and the Active Directory service
 Adobe Acrobat 9 Deployment on Microsoft Windows Group Policy and the Active Directory service white paper TABLE OF CONTENTS 1. Document overview......... 1 2. References............. 1 3. Product overview..........
Adobe Acrobat 9 Deployment on Microsoft Windows Group Policy and the Active Directory service white paper TABLE OF CONTENTS 1. Document overview......... 1 2. References............. 1 3. Product overview..........
User Manual. Onsight Management Suite Version 5.1. Another Innovation by Librestream
 User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
Acronis Backup & Recovery 11.5 Quick Start Guide
 Acronis Backup & Recovery 11.5 Quick Start Guide Applies to the following editions: Advanced Server for Windows Virtual Edition Advanced Server SBS Edition Advanced Workstation Server for Linux Server
Acronis Backup & Recovery 11.5 Quick Start Guide Applies to the following editions: Advanced Server for Windows Virtual Edition Advanced Server SBS Edition Advanced Workstation Server for Linux Server
A-AUTO 50 for Windows Setup Guide
 A-AUTO 50 for Windows Setup Guide 1st Edition 1 A-AUTO is a registered trade mark of UNIRITA Inc. "This product includes software developed by the Apache Software Foundation (http://www.apache.org/)."
A-AUTO 50 for Windows Setup Guide 1st Edition 1 A-AUTO is a registered trade mark of UNIRITA Inc. "This product includes software developed by the Apache Software Foundation (http://www.apache.org/)."
Identity-Based Application and Network Profiling
 Application Note Identity-Based Application and Network Profiling Using UAC in Conjunction with NSM, IDP and Infranet Enforcers Permits User-Identified Application and Network Profiling Juniper Networks,
Application Note Identity-Based Application and Network Profiling Using UAC in Conjunction with NSM, IDP and Infranet Enforcers Permits User-Identified Application and Network Profiling Juniper Networks,
Installation and Deployment
 Installation and Deployment Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Installation and Deployment SmarterStats
Installation and Deployment Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Installation and Deployment SmarterStats
Network Configuration Example
 Network Configuration Example Configuring Multiple Port Mirroring Sessions on EX4200 Switches Published: 2014-04-09 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000
Network Configuration Example Configuring Multiple Port Mirroring Sessions on EX4200 Switches Published: 2014-04-09 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000
IBM Security QRadar Version 7.2.2. WinCollect User Guide V7.2.2
 IBM Security QRadar Version 7.2.2 WinCollect User Guide V7.2.2 Note Before using this information and the product that it supports, read the information in Notices on page 47. Product information This
IBM Security QRadar Version 7.2.2 WinCollect User Guide V7.2.2 Note Before using this information and the product that it supports, read the information in Notices on page 47. Product information This
SMART Sync 2011. Windows operating systems. System administrator s guide
 SMART Sync 2011 Windows operating systems System administrator s guide Trademark notice SMART Sync, smarttech and the SMART logo are trademarks or registered trademarks of SMART Technologies ULC in the
SMART Sync 2011 Windows operating systems System administrator s guide Trademark notice SMART Sync, smarttech and the SMART logo are trademarks or registered trademarks of SMART Technologies ULC in the
Juniper Secure Analytics
 Juniper Secure Analytics Log Sources Users Guide Release 2014.1 Modified: 2015-11-30 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights reserved.
Juniper Secure Analytics Log Sources Users Guide Release 2014.1 Modified: 2015-11-30 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All rights reserved.
Web Security Firewall Setup. Administrator Guide
 Web Security Firewall Setup Administrator Guide Web Security Firewall Setup Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec,
Web Security Firewall Setup Administrator Guide Web Security Firewall Setup Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec,
Adaptive Log Exporter Service Update
 Juniper Secure Analytics Release 2014.6 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2016-04-21 Copyright Notice Copyright 2016 Juniper
Juniper Secure Analytics Release 2014.6 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2016-04-21 Copyright Notice Copyright 2016 Juniper
Version 5.0. SurfControl Web Filter for Citrix Installation Guide for Service Pack 2
 Version 5.0 SurfControl Web Filter for Citrix Installation Guide for Service Pack 2 NOTICES Updates to the SurfControl documentation and software, as well as Support information are available at www.surfcontrol.com/support.
Version 5.0 SurfControl Web Filter for Citrix Installation Guide for Service Pack 2 NOTICES Updates to the SurfControl documentation and software, as well as Support information are available at www.surfcontrol.com/support.
Migrating Mobile Security for Enterprise (TMMS) 8.0 to version 9.0
 Before Migration Migrating Mobile Security for Enterprise (TMMS) 8.0 to version 9.0 You must have TMMS 8.0/8.0 SP1 installed before upgrading to TMMS 9.0. Pay attention to the following when migrating
Before Migration Migrating Mobile Security for Enterprise (TMMS) 8.0 to version 9.0 You must have TMMS 8.0/8.0 SP1 installed before upgrading to TMMS 9.0. Pay attention to the following when migrating
Comparison of Firewall, Intrusion Prevention and Antivirus Technologies
 White Paper Comparison of Firewall, Intrusion Prevention and Antivirus Technologies How each protects the network Juan Pablo Pereira Technical Marketing Manager Juniper Networks, Inc. 1194 North Mathilda
White Paper Comparison of Firewall, Intrusion Prevention and Antivirus Technologies How each protects the network Juan Pablo Pereira Technical Marketing Manager Juniper Networks, Inc. 1194 North Mathilda
HP IMC User Behavior Auditor
 HP IMC User Behavior Auditor Administrator Guide Abstract This guide describes the User Behavior Auditor (UBA), an add-on service module of the HP Intelligent Management Center. UBA is designed for IMC
HP IMC User Behavior Auditor Administrator Guide Abstract This guide describes the User Behavior Auditor (UBA), an add-on service module of the HP Intelligent Management Center. UBA is designed for IMC
Sophos for Microsoft SharePoint startup guide
 Sophos for Microsoft SharePoint startup guide Product version: 2.0 Document date: March 2011 Contents 1 About this guide...3 2 About Sophos for Microsoft SharePoint...3 3 System requirements...3 4 Planning
Sophos for Microsoft SharePoint startup guide Product version: 2.0 Document date: March 2011 Contents 1 About this guide...3 2 About Sophos for Microsoft SharePoint...3 3 System requirements...3 4 Planning
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Deploying Business Objects Crystal Reports Server on IBM InfoSphere Balanced Warehouse C-Class Solution for Windows
 Deploying Business Objects Crystal Reports Server on IBM InfoSphere Balanced Warehouse C-Class Solution for Windows I Installation & Configuration Guide Author: Thinh Hong Business Partner Technical Enablement
Deploying Business Objects Crystal Reports Server on IBM InfoSphere Balanced Warehouse C-Class Solution for Windows I Installation & Configuration Guide Author: Thinh Hong Business Partner Technical Enablement
Oracle Enterprise Manager. Description. Platforms Supported. Versions Supported
 Oracle Enterprise Manager System Monitoring Plug-in Installation Guide for Check Point Firewall 10g Release 2 (10.2) B28038-02 May 2007 This document provides a brief description about the Oracle System
Oracle Enterprise Manager System Monitoring Plug-in Installation Guide for Check Point Firewall 10g Release 2 (10.2) B28038-02 May 2007 This document provides a brief description about the Oracle System
Configuring and Implementing A10
 IMPLEMENTATION GUIDE Configuring and Implementing A10 Networks Load Balancing Solution with Juniper s SSL VPN Appliances Although Juniper Networks has attempted to provide accurate information in this
IMPLEMENTATION GUIDE Configuring and Implementing A10 Networks Load Balancing Solution with Juniper s SSL VPN Appliances Although Juniper Networks has attempted to provide accurate information in this
Junos Pulse. Windows In-Box Junos Pulse Client Quick Start Guide. Published: 2013-10-18. Copyright 2013, Juniper Networks, Inc.
 Junos Pulse Windows In-Box Junos Pulse Client Quick Start Guide Published: 2013-10-18 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All
Junos Pulse Windows In-Box Junos Pulse Client Quick Start Guide Published: 2013-10-18 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net All
How Do I Upgrade Firmware and Save Configurations on PowerConnect Switches?
 PowerConnect Application Note #12 February 2004 How Do I Upgrade Firmware and Save Configurations on PowerConnect Switches? This Application Notes relates to the following Dell PowerConnect products: PowerConnect
PowerConnect Application Note #12 February 2004 How Do I Upgrade Firmware and Save Configurations on PowerConnect Switches? This Application Notes relates to the following Dell PowerConnect products: PowerConnect
QRadar SIEM 7.2 Windows Event Collection Overview
 QRadar Open Mic Webcast #3 August 26, 2014 QRadar SIEM 7.2 Windows Event Collection Overview Panelists Aaron Breen QRadar World-wide Support Leader Adam Frank Principal Solutions Architect Jonathan Pechta
QRadar Open Mic Webcast #3 August 26, 2014 QRadar SIEM 7.2 Windows Event Collection Overview Panelists Aaron Breen QRadar World-wide Support Leader Adam Frank Principal Solutions Architect Jonathan Pechta
4cast Client Specification and Installation
 4cast Client Specification and Installation Version 2015.00 10 November 2014 Innovative Solutions for Education Management www.drakelane.co.uk System requirements The client requires Administrative rights
4cast Client Specification and Installation Version 2015.00 10 November 2014 Innovative Solutions for Education Management www.drakelane.co.uk System requirements The client requires Administrative rights
SOA Software API Gateway Appliance 7.1.x Administration Guide
 SOA Software API Gateway Appliance 7.1.x Administration Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software, Inc. Other product names,
SOA Software API Gateway Appliance 7.1.x Administration Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software, Inc. Other product names,
File Transfer Examples. Running commands on other computers and transferring files between computers
 Running commands on other computers and transferring files between computers 1 1 Remote Login Login to remote computer and run programs on that computer Once logged in to remote computer, everything you
Running commands on other computers and transferring files between computers 1 1 Remote Login Login to remote computer and run programs on that computer Once logged in to remote computer, everything you
RSA Security Analytics
 RSA Security Analytics Event Source Log Configuration Guide Cisco IOS Last Modified: Thursday, February 19, 2015 Event Source Product Information: Vendor: Cisco Event Source: IOS Versions: IOS 12.4, 15.x
RSA Security Analytics Event Source Log Configuration Guide Cisco IOS Last Modified: Thursday, February 19, 2015 Event Source Product Information: Vendor: Cisco Event Source: IOS Versions: IOS 12.4, 15.x
Print Audit 6 Network Installation Guide
 Print Audit 6 Network Installation Guide IMPORTANT: READ THIS BEFORE PERFORMING A PRINT AUDIT 6 INSTALLATION Print Audit 6 is a desktop application that you must install on every computer where you want
Print Audit 6 Network Installation Guide IMPORTANT: READ THIS BEFORE PERFORMING A PRINT AUDIT 6 INSTALLATION Print Audit 6 is a desktop application that you must install on every computer where you want
VMware vcenter Log Insight Security Guide
 VMware vcenter Log Insight Security Guide vcenter Log Insight 2.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
VMware vcenter Log Insight Security Guide vcenter Log Insight 2.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Using LifeSize systems with Microsoft Office Communications Server 2007. Server Setup
 Using LifeSize systems with Microsoft Office Communications Server 2007 This technical note describes the steps to integrate a LifeSize video communications device with Microsoft Office Communication Server
Using LifeSize systems with Microsoft Office Communications Server 2007 This technical note describes the steps to integrate a LifeSize video communications device with Microsoft Office Communication Server
CA NetQoS Performance Center
 CA NetQoS Performance Center Install and Configure SSL for Windows Server 2008 Release 6.1 (and service packs) This Documentation, which includes embedded help systems and electronically distributed materials,
CA NetQoS Performance Center Install and Configure SSL for Windows Server 2008 Release 6.1 (and service packs) This Documentation, which includes embedded help systems and electronically distributed materials,
Installing and Configuring vcenter Multi-Hypervisor Manager
 Installing and Configuring vcenter Multi-Hypervisor Manager vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.1 This document supports the version of each product listed and supports all subsequent
Installing and Configuring vcenter Multi-Hypervisor Manager vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.1 This document supports the version of each product listed and supports all subsequent
Migrating Trend Micro Mobile Security for Enterprise (TMMS) 8.0 to TMMS 9.0
 Migrating Trend Micro Mobile Security for Enterprise (TMMS) 8.0 to TMMS 9.0 Migrating TMMS 8.0 to version 9.0 involves the following steps: 1. Installing TMMS 8.0 Service Pack (SP) 1, installing the SQLcmd
Migrating Trend Micro Mobile Security for Enterprise (TMMS) 8.0 to TMMS 9.0 Migrating TMMS 8.0 to version 9.0 involves the following steps: 1. Installing TMMS 8.0 Service Pack (SP) 1, installing the SQLcmd
VMware vcenter Log Insight Administration Guide
 VMware vcenter Log Insight Administration Guide vcenter Log Insight 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
VMware vcenter Log Insight Administration Guide vcenter Log Insight 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
Symantec AntiVirus Corporate Edition Patch Update
 Symantec AntiVirus Corporate Edition Patch Update Symantec AntiVirus Corporate Edition Update Documentation version 10.0.1.1007 Copyright 2005 Symantec Corporation. All rights reserved. Symantec, the Symantec
Symantec AntiVirus Corporate Edition Patch Update Symantec AntiVirus Corporate Edition Update Documentation version 10.0.1.1007 Copyright 2005 Symantec Corporation. All rights reserved. Symantec, the Symantec
vsphere Upgrade Update 1 ESXi 6.0 vcenter Server 6.0 EN-001804-02
 Update 1 ESXi 6.0 vcenter Server 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent
Update 1 ESXi 6.0 vcenter Server 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent
vsphere Upgrade vsphere 6.0 EN-001721-03
 vsphere 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document,
vsphere 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document,
STRM Log Manager Administration Guide
 Security Threat Response Manager Release 2013.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2013-03-15 Copyright Notice Copyright 2013
Security Threat Response Manager Release 2013.1 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Published: 2013-03-15 Copyright Notice Copyright 2013
EMC ViPR Controller Add-in for Microsoft System Center Virtual Machine Manager
 EMC ViPR Controller Add-in for Microsoft System Center Virtual Machine Manager Version 2.3 Installation and Configuration Guide 302-002-080 01 Copyright 2013-2015 EMC Corporation. All rights reserved.
EMC ViPR Controller Add-in for Microsoft System Center Virtual Machine Manager Version 2.3 Installation and Configuration Guide 302-002-080 01 Copyright 2013-2015 EMC Corporation. All rights reserved.
IBM WebSphere Application Server Communications Enabled Applications
 IBM WebSphere Application Server Communications Enabled Applications Configuring a CEA environment 2011 IBM Corporation This presentation describes how to configure a WebSphere Application Server environment
IBM WebSphere Application Server Communications Enabled Applications Configuring a CEA environment 2011 IBM Corporation This presentation describes how to configure a WebSphere Application Server environment
Dell One Identity Cloud Access Manager 8.0.1 - How to Configure Microsoft Office 365
 Dell One Identity Cloud Access Manager 8.0.1 - How to Configure Microsoft Office 365 May 2015 This guide describes how to configure Microsoft Office 365 for use with Dell One Identity Cloud Access Manager
Dell One Identity Cloud Access Manager 8.0.1 - How to Configure Microsoft Office 365 May 2015 This guide describes how to configure Microsoft Office 365 for use with Dell One Identity Cloud Access Manager
Clearswift SECURE Email Gateway V3.*
 Clearswift SECURE Email Gateway V3.* Ports and Protocols Issue 3.12 July 2015 Copyright Version 1.1, July, 2015 Published by Clearswift Ltd. 1995 2015 Clearswift Ltd. All rights reserved. The materials
Clearswift SECURE Email Gateway V3.* Ports and Protocols Issue 3.12 July 2015 Copyright Version 1.1, July, 2015 Published by Clearswift Ltd. 1995 2015 Clearswift Ltd. All rights reserved. The materials
