BACKUP STRATEGY AND DISASTER RECOVERY POLICY STATEMENT
|
|
|
- Adrian Charles
- 10 years ago
- Views:
Transcription
1 TADCASTER GRAMMAR SCHOOL Toulston, Tadcaster, North Yorkshire. LS24 9NB BACKUP STRATEGY AND DISASTER RECOVERY POLICY STATEMENT Written by Steve South November 2003 Discussed with ICT Strategy Group January 2004 Discussed with Leadership Group February 2004 Revised by ICT Strategy Group February 2004 Confirmed by Leadership Group April 2004 Confirmed by Governors June 2004 Reviewed November 2013 Next Review As Required
2 Backup Strategy and Disaster Recovery Policy Policy Statement The purpose of this policy is to set in place strategies to ensure the secure backup and recovery of important data that is stored on the school administration and curriculum networks. The data to backup includes school management data files, administration network user documents, teaching staff documents and student documents. The strategies in place will be robust enough to ensure the recovery of data in any circumstance, including fire, catastrophic hardware or software failure, file deletion or virus or hacker attack. Data can be destroyed by system malfunction or accidental or intentional means. Adequate backups will allow data to be readily recovered as necessary. The ongoing availability of important data is critical to the operation of the school. In order to minimise any potential loss or corruption of this data, people responsible for providing and operating administrative applications need to ensure that data is adequately backed up by establishing and following an appropriate system backup procedure. Statement of Authority and Scope This policy is intended to detail the accepted good practice policies in the backing up and restoring of data on networked computer systems. The Network Manager provides the framework, design and implementation of backup strategies employed at Tadcaster Grammar School. The Network Manager and authorised persons within the ICT \ Network Department are then responsible for the operation of these strategies. The Network Manager administers this policy with the full support of the Leadership Group and the Governing body. Disk Based Backups The following data will be backed up every weeknight onto the School s Backup SAN (Storage Area Network) MIS data files Finance data files Administration network user documents Curriculum network user documents Student documents School reports Shared documents on both the administration and curriculum networks 1
3 Snapshot Backups Snapshot backups (A full copy of the data at a particular point in time) are to be kept for a period of six months and stored on an external RAID device and external USB Device. This is to provide a means of restoring data from a backup at any time period, up to a maximum of six months previously. Due to the amount of data to be backed up and the storage space required to provide backups, only selective critical data will be stored in this way. This will include MIS data files Finance data files Shadow Copy Backups This is a means of restoring previous versions of documents that have inadvertently become corrupted over time, where the normal backup process is insufficient as it would be the corrupted file that is backed up. This is particularly prevalent with Microsoft Office and Corel documents where the end user doesn t close the document correctly or inserts objects (video, audio or graphic files that corrupt the document). Shadow Copy Backups allow any of the last fourteen saved instances of a document to be restored. Shadow Copy runs twice a day across the servers holding staff and student documents. Backup Hardware It is the responsibility of the Network Manager to determine the appropriate hardware necessary to provide reliable backup and archiving of data. As the amount of data to backup increases over time so the hardware requirements will need to be reviewed annually. This review will be submitted to the Leadership Group. Backup Software It is the responsibility of the Network Manager to determine the appropriate software necessary to provide reliable backup and archiving of data. As the amount of data to backup increases over time so the software requirements will need to be reviewed annually. This review will be submitted to the Leadership Group. 2
4 Frequency of Backups Disk backups are performed every weeknight on the backup server. Each backup, which is unattended runs through the night Snapshot backups are performed manually, once a week at the end of the day. Shadow copy backups are performed automatically twice a day. Off Site Storage It is established good practice to keep a copy of all important data stored offsite. In the event of normal backup and restore devices being unavailable due to fire for example, it is imperative that alternative backups are available in a separate location. Any sensitive data stored off-site is first encrypted. Backup Logs The Network Manager will monitor backup logs to ensure that network data has been fully backed up. Backup of data stored on Laptops \ Departmental computers All data should be stored centrally on the network servers, personal data should be stored in a user's home directory. There are instances though where users may want to store their data locally on the computers and \ or laptops hard drive. In this instance it is the responsibility of the user to ensure that their data is backed up. The means of doing this will be dependent on the capabilities of their machine, but could include floppy disk, USB data storage or CD-R. In the event of a user losing work that is stored locally on a Laptop or Desktop PC, the Network department using various undelete and disaster recovery software shall attempt recovery of these lost files. The success of this will be very dependent on a mixture of circumstances beyond the control of the Network Department. Disaster Recovery In the event of a complete network failure, power cut, server breakdown, fire or any other eventuality where the network is unavailable a disaster plan needs to be in place to ensure the continued smooth running of the school. This would include periods when the time taken to restore the network would take more than a day. The following emergency procedures would need to be in place To ensure that school timetabling, staff cover, financial transactions and any other critical school management systems can still run the member of 3
5 staff responsible for these areas should ensure that they have their own disaster recovery plan. This will then enable them to at least continue working in these areas. The person responsible for their particular area should follow the following guidelines in formulating their own disaster recovery plan Identify essential school management functions. Essential school functions are those functions that must take place in order to support an acceptable level of continuity for the school. Document procedures to implement this disaster recovery plan. Make sure the plan can work effectively in the event of a disaster. Make sure staff who work within these critical school management areas are aware of the plan and are able to carry it out effectively. Plan for the alternate processing of data to use during a disaster. This would include keeping hard copies of certain data and documents and documentation of any disaster plan. Make the Leadership Group aware of what strategies would be employed in the event of a disaster. When the server and network have been restored any new information can then be transferred or entered back into the network system. If a user on the administration network needs to load up an important document this should be possible due to the fact that extra backups are made independent of the network servers. A user could then work locally (not attached to the network) on their desktop PC or laptop with that document. When the server and network have been restored any new information can then be transferred or re-entered into the network system. On the curriculum network, as the amount of data files and documents is so much greater it may not always be possible to have an up to date backup stored on media separate from the network server backups. To provide the maximum protection against the possibility of server failure it is the schools policy that all network servers that are purchased have built in fault tolerance and redundancy. Server Backup and Restore Each Virtualised Server is backed up every weeknight, this backup includes the server operating system, configuration files and in the case of the Primary Domain Controller this would include network data such as usernames, policy and profile data and security information. In the event of complete server operating system failure the server operating system would initially need to be re-installed then the server backup restored. In the event of server hardware failure, the server would first need to be repaired, then the server backup restored. 4
6 Data Restoration Only the Network Manager and ICT Technicians will have access to the means to restore network data. The Network Manager will determine if a successful restoration is possible. Any requests for restoration of user data will be made to the Network Manager. In the event of complete server failure where a full restoration of school management software and data files is necessary, a member of the Leadership Group after discussion with the Network Manager will need to give approval. 5
NETWORK AND INTERNET SECURITY POLICY STATEMENT
 TADCASTER GRAMMAR SCHOOL Toulston, Tadcaster, North Yorkshire. LS24 9NB NETWORK AND INTERNET SECURITY POLICY STATEMENT Written by Steve South November 2003 Discussed with ICT Strategy Group January 2004
TADCASTER GRAMMAR SCHOOL Toulston, Tadcaster, North Yorkshire. LS24 9NB NETWORK AND INTERNET SECURITY POLICY STATEMENT Written by Steve South November 2003 Discussed with ICT Strategy Group January 2004
Education and Workforce Development Cabinet POLICY/PROCEDURE. Policy Number: EDU-06 Effective Date: April 15, 2006 Revision Date: December 20, 2012
 Education and Workforce Development Cabinet POLICY/PROCEDURE Policy Number: EDU-06 Effective Date: April 15, 2006 Revision Date: December 20, 2012 Subject: Backup Procedures Tower and Server Farms Policy:
Education and Workforce Development Cabinet POLICY/PROCEDURE Policy Number: EDU-06 Effective Date: April 15, 2006 Revision Date: December 20, 2012 Subject: Backup Procedures Tower and Server Farms Policy:
StorageCraft Technology Corporation Leading the Way to Safer Computing 2009 StorageCraft Technology Corporation. All Rights Reserved.
 PRODUCT WHITEPAPER This brochure is for informational purposes only. STORAGECRAFT MAKES NO WARRANTIES, EXPRESSED OR IMPLIED, IN THIS SUMMARY. StorageCraft, ShadowProtect and ExactState and the StorageCraft
PRODUCT WHITEPAPER This brochure is for informational purposes only. STORAGECRAFT MAKES NO WARRANTIES, EXPRESSED OR IMPLIED, IN THIS SUMMARY. StorageCraft, ShadowProtect and ExactState and the StorageCraft
ScoMIS Encryption Service
 Introduction This guide explains how to implement the ScoMIS Encryption Service for a secondary school. We recommend that the software should be installed onto the laptop by ICT staff; they will then spend
Introduction This guide explains how to implement the ScoMIS Encryption Service for a secondary school. We recommend that the software should be installed onto the laptop by ICT staff; they will then spend
Tk20 Backup Procedure
 Tk20 Backup Procedure 1 TK20 BACKUP PROCEDURE OVERVIEW 3 FEATURES AND ADVANTAGES: 3 TK20 BACKUP PROCEDURE 4 DAILY BACKUP CREATION 4 TRANSFER OF BACKUPS 5 AUDITING PROCESS 5 BACKUP REPOSITORY 5 WRITE TO
Tk20 Backup Procedure 1 TK20 BACKUP PROCEDURE OVERVIEW 3 FEATURES AND ADVANTAGES: 3 TK20 BACKUP PROCEDURE 4 DAILY BACKUP CREATION 4 TRANSFER OF BACKUPS 5 AUDITING PROCESS 5 BACKUP REPOSITORY 5 WRITE TO
TECHNICAL SECURITY AND DATA BACKUP POLICY
 TECHNICAL SECURITY AND DATA BACKUP POLICY PURPOSE Effective technical security depends not only on technical measures, but also on appropriate policies and procedures and on good user education and training.
TECHNICAL SECURITY AND DATA BACKUP POLICY PURPOSE Effective technical security depends not only on technical measures, but also on appropriate policies and procedures and on good user education and training.
Understanding Backup and Recovery Methods
 Lesson 8 Understanding Backup and Recovery Methods Learning Objectives Students will learn to: Understand Local, Online, and Automated Backup Methods Understand Backup Options Understand System Restore
Lesson 8 Understanding Backup and Recovery Methods Learning Objectives Students will learn to: Understand Local, Online, and Automated Backup Methods Understand Backup Options Understand System Restore
Online Backup Plus Frequently Asked Questions
 Online Backup Plus Frequently Asked Questions 1 INSTALLATION 1.1 Who installs the Redstor Online Backup Plus service? 1.2 How does the installed client connect to Redstor s Cloud Platform? 1.3 On which
Online Backup Plus Frequently Asked Questions 1 INSTALLATION 1.1 Who installs the Redstor Online Backup Plus service? 1.2 How does the installed client connect to Redstor s Cloud Platform? 1.3 On which
Computer Backup Strategies
 Computer Backup Strategies Think how much time it would take to recreate everything on your computer...if you could. Given all the threats to your data (viruses, natural disasters, computer crashes, and
Computer Backup Strategies Think how much time it would take to recreate everything on your computer...if you could. Given all the threats to your data (viruses, natural disasters, computer crashes, and
Planning a Backup Strategy
 Planning a Backup Strategy White Paper Backups, restores, and data recovery operations are some of the most important tasks that an IT organization performs. Businesses cannot risk losing access to data
Planning a Backup Strategy White Paper Backups, restores, and data recovery operations are some of the most important tasks that an IT organization performs. Businesses cannot risk losing access to data
Backup Policy (ITP004) Information Technology Services Department
 Introduction This policy defines the backup guidelines for systems within the Central Dauphin School District. These systems are typically servers, Storage Area Network devices (SAN), or Network-Attached
Introduction This policy defines the backup guidelines for systems within the Central Dauphin School District. These systems are typically servers, Storage Area Network devices (SAN), or Network-Attached
Data Security Policy
 Policy Number: Revision Number: 0 QP1.44 Date of issue: March 2009 Status: Approved Date of approval: April 2009 Responsibility for policy: Responsibility for implementation: Responsibility for review:
Policy Number: Revision Number: 0 QP1.44 Date of issue: March 2009 Status: Approved Date of approval: April 2009 Responsibility for policy: Responsibility for implementation: Responsibility for review:
Little-Known Facts and Insider Secrets Every Business Owner Should Know About Backing Up Their Data and Choosing a Remote Backup Service
 Little-Known Facts and Insider Secrets Every Business Owner Should Know About Backing Up Their Data and Choosing a Remote Backup Service If your data is important to your business and you cannot afford
Little-Known Facts and Insider Secrets Every Business Owner Should Know About Backing Up Their Data and Choosing a Remote Backup Service If your data is important to your business and you cannot afford
Yiwo Tech Development Co., Ltd. EaseUS Todo Backup. Reliable Backup & Recovery Solution. EaseUS Todo Backup Solution Guide. All Rights Reserved Page 1
 EaseUS Todo Backup Reliable Backup & Recovery Solution EaseUS Todo Backup Solution Guide. All Rights Reserved Page 1 Part 1 Overview EaseUS Todo Backup Solution Guide. All Rights Reserved Page 2 Introduction
EaseUS Todo Backup Reliable Backup & Recovery Solution EaseUS Todo Backup Solution Guide. All Rights Reserved Page 1 Part 1 Overview EaseUS Todo Backup Solution Guide. All Rights Reserved Page 2 Introduction
Version: 1.5 2014 Page 1 of 5
 Version: 1.5 2014 Page 1 of 5 1.0 Overview A backup policy is similar to an insurance policy it provides the last line of defense against data loss and is sometimes the only way to recover from a hardware
Version: 1.5 2014 Page 1 of 5 1.0 Overview A backup policy is similar to an insurance policy it provides the last line of defense against data loss and is sometimes the only way to recover from a hardware
About Backing Up a Cisco Unity System
 CHAPTER 4 Introduction This chapter describes in general terms backing up a Cisco Unity system. When you back up a Cisco Unity server (and one or more Exchange servers) you need to consider the same issues
CHAPTER 4 Introduction This chapter describes in general terms backing up a Cisco Unity system. When you back up a Cisco Unity server (and one or more Exchange servers) you need to consider the same issues
Read this guide and you ll discover:
 BUSINESS ADVISOR REPORT Provided as an educational service by: Rick Reynolds, General Manager Read this guide and you ll discover: What remote, offsite, or managed backups are, and why EVERY business should
BUSINESS ADVISOR REPORT Provided as an educational service by: Rick Reynolds, General Manager Read this guide and you ll discover: What remote, offsite, or managed backups are, and why EVERY business should
MFR IT Technical Guides
 MFR IT Technical Guides Windows 7 Backup and Recovery Page 1 of 33 Table of Contents 1 Glossary... 3 2 Backup Strategy... 4 3 Windows Backup Options... 5 3.1 Windows Backup... 5 3.2 Windows System Image
MFR IT Technical Guides Windows 7 Backup and Recovery Page 1 of 33 Table of Contents 1 Glossary... 3 2 Backup Strategy... 4 3 Windows Backup Options... 5 3.1 Windows Backup... 5 3.2 Windows System Image
WDL RemoteBunker Online Backup For Client Name
 WDL RemoteBunker Online Backup For Client Name November, 2011 Contact Phone: +234 802 698 7025 Email: [email protected] [email protected] http://remotebunker.webdatalinks.com INTRODUCTION
WDL RemoteBunker Online Backup For Client Name November, 2011 Contact Phone: +234 802 698 7025 Email: [email protected] [email protected] http://remotebunker.webdatalinks.com INTRODUCTION
Disaster Recovery for Small Businesses
 Technical White Paper Disaster Recovery for Small Businesses A disaster recovery plan helps you understand what data is critical to your business operations and how to best protect it from unexpected failures.
Technical White Paper Disaster Recovery for Small Businesses A disaster recovery plan helps you understand what data is critical to your business operations and how to best protect it from unexpected failures.
ADMINISTRATION COMPUTER NETWORK
 ADMINISTRATION COMPUTER NETWORK School Administrative Computer Network The Cumberland School operates a network of computers specifically for administrative purposes in the school. This network is electronically
ADMINISTRATION COMPUTER NETWORK School Administrative Computer Network The Cumberland School operates a network of computers specifically for administrative purposes in the school. This network is electronically
Tameside Metropolitan Borough Council ICT Security Policy for Schools. Adopted by:
 Tameside Metropolitan Borough Council ICT Security Policy for Schools Adopted by: 1. Introduction 1.1. The purpose of the Policy is to protect the institution s information assets from all threats, whether
Tameside Metropolitan Borough Council ICT Security Policy for Schools Adopted by: 1. Introduction 1.1. The purpose of the Policy is to protect the institution s information assets from all threats, whether
VIPERVAULT STORAGECRAFT SHADOWPROTECT SETUP GUIDE
 VIPERVAULT STORAGECRAFT SHADOWPROTECT SETUP GUIDE Solution Overview Thank you for choosing the ViperVault cloud replication, backup and disaster recovery service. Using this service you can replicate your
VIPERVAULT STORAGECRAFT SHADOWPROTECT SETUP GUIDE Solution Overview Thank you for choosing the ViperVault cloud replication, backup and disaster recovery service. Using this service you can replicate your
Frequently Asked Questions About WebDrv Online (Remote) Backup
 Frequently Asked Questions About WebDrv Online (Remote) Backup GENERAL INFORMATION Why backup? What is online backup? What if we already have a tape backup system? How secure are online backups? What tasks
Frequently Asked Questions About WebDrv Online (Remote) Backup GENERAL INFORMATION Why backup? What is online backup? What if we already have a tape backup system? How secure are online backups? What tasks
Modification after decommission of AX100 SAN (RVN00-FILEDR) 1.2 26/3/2009 Deputy IT Operations Manager
 Information Management & Technology Document No: AWP/ IT/LP/ITOPS-009 Title: AWP IT Backup Strategy and Procedure Version: 2.0 Date: 06/04/2009 Author: IT Operations Manager Distribution List: IMT Operations
Information Management & Technology Document No: AWP/ IT/LP/ITOPS-009 Title: AWP IT Backup Strategy and Procedure Version: 2.0 Date: 06/04/2009 Author: IT Operations Manager Distribution List: IMT Operations
Secondary School 1/04/2015. ICT Service Specification by: Andrea Warburton ONE IT SERVICES AND SOLUTIONS
 1/04/2015 Secondary School ICT Service Specification by: 1 Andrea Warburton ONE IT SERVICES AND SOLUTIONS SERVICE SPECIFICATION One IT Services and Solutions offer a one stop shop ICT support service,
1/04/2015 Secondary School ICT Service Specification by: 1 Andrea Warburton ONE IT SERVICES AND SOLUTIONS SERVICE SPECIFICATION One IT Services and Solutions offer a one stop shop ICT support service,
ICT Policy. Executive Summary. Date of ratification Executive Team Committee 22nd October 2013. Document Author(s) Collette McQueen
 ICT Policy THCCGIT20 Version: 01 Executive Summary This document defines the Network Infrastructure and File Server Security Policy for Tower Hamlets Clinical Commissioning Group (CCG). The Network Infrastructure
ICT Policy THCCGIT20 Version: 01 Executive Summary This document defines the Network Infrastructure and File Server Security Policy for Tower Hamlets Clinical Commissioning Group (CCG). The Network Infrastructure
Backup & Disaster Recovery Options
 Backup & Disaster Recovery Options Since businesses have become more dependent on their internal computing capability, they are increasingly concerned about recovering from equipment failure, human error,
Backup & Disaster Recovery Options Since businesses have become more dependent on their internal computing capability, they are increasingly concerned about recovering from equipment failure, human error,
Disk-to-Disk-to-Offsite Backups for SMBs with Retrospect
 Disk-to-Disk-to-Offsite Backups for SMBs with Retrospect Abstract Retrospect backup and recovery software provides a quick, reliable, easy-to-manage disk-to-disk-to-offsite backup solution for SMBs. Use
Disk-to-Disk-to-Offsite Backups for SMBs with Retrospect Abstract Retrospect backup and recovery software provides a quick, reliable, easy-to-manage disk-to-disk-to-offsite backup solution for SMBs. Use
BACKUP SOLUTIONS FOR SCHOOLS. Advice and Guidance. ICT Services 42 New Union Street Coventry CV1 2HN
 BACKUP SOLUTIONS FOR SCHOOLS Advice and Guidance ICT Services 42 New Union Street Coventry CV1 2HN Revision History and Approval Date Author Version Comments Approval 26/02/2014 Alison York 1.00 Initial
BACKUP SOLUTIONS FOR SCHOOLS Advice and Guidance ICT Services 42 New Union Street Coventry CV1 2HN Revision History and Approval Date Author Version Comments Approval 26/02/2014 Alison York 1.00 Initial
HOW SAFE IS YOUR DATA??
 HOW SAFE IS YOUR DATA?? MANAGER AAffordable Protection for Electronic Business Data MANAGER YOUR KEY TO... Peace of mind Data Security Off-Site Data Protection State of the art Virus Protection Professional
HOW SAFE IS YOUR DATA?? MANAGER AAffordable Protection for Electronic Business Data MANAGER YOUR KEY TO... Peace of mind Data Security Off-Site Data Protection State of the art Virus Protection Professional
VDI can reduce costs, simplify systems and provide a less frustrating experience for users.
 1 INFORMATION TECHNOLOGY GROUP VDI can reduce costs, simplify systems and provide a less frustrating experience for users. infor ation technology group 2 INFORMATION TECHNOLOGY GROUP CONTENTS Introduction...3
1 INFORMATION TECHNOLOGY GROUP VDI can reduce costs, simplify systems and provide a less frustrating experience for users. infor ation technology group 2 INFORMATION TECHNOLOGY GROUP CONTENTS Introduction...3
MAXIMUM PROTECTION, MINIMUM DOWNTIME
 MANAGED SERVICES MAXIMUM PROTECTION, MINIMUM DOWNTIME Get peace of mind with proactive IT support Designed to protect your business, save you money and give you peace of mind, Talon Managed Services is
MANAGED SERVICES MAXIMUM PROTECTION, MINIMUM DOWNTIME Get peace of mind with proactive IT support Designed to protect your business, save you money and give you peace of mind, Talon Managed Services is
NETWORK SERVICES WITH SOME CREDIT UNIONS PROCESSING 800,000 TRANSACTIONS ANNUALLY AND MOVING OVER 500 MILLION, SYSTEM UPTIME IS CRITICAL.
 NETWORK SERVICES WITH SOME CREDIT UNIONS PROCESSING 800,000 TRANSACTIONS ANNUALLY AND MOVING OVER 500 MILLION, SYSTEM UPTIME IS CRITICAL. Your Credit Union information is irreplaceable. Data loss can result
NETWORK SERVICES WITH SOME CREDIT UNIONS PROCESSING 800,000 TRANSACTIONS ANNUALLY AND MOVING OVER 500 MILLION, SYSTEM UPTIME IS CRITICAL. Your Credit Union information is irreplaceable. Data loss can result
Managing and Maintaining a Windows Server 2003 Network Environment
 Managing and maintaining a Windows Server 2003 Network Environment. AIM This course provides students with knowledge and skills needed to Manage and Maintain a Windows Server 2003 Network Environment.
Managing and maintaining a Windows Server 2003 Network Environment. AIM This course provides students with knowledge and skills needed to Manage and Maintain a Windows Server 2003 Network Environment.
One Solution for Real-Time Data protection, Disaster Recovery & Migration
 One Solution for Real-Time Data protection, Disaster Recovery & Migration Built-in standby virtualisation server Backs up every 15 minutes up to 12 servers On and Off-site Backup User initialed file, folder
One Solution for Real-Time Data protection, Disaster Recovery & Migration Built-in standby virtualisation server Backs up every 15 minutes up to 12 servers On and Off-site Backup User initialed file, folder
Creating a Complete Backup of Shelby v5 Data
 Creating a Complete Backup of Shelby v5 Data Backup the Shelby folder and all its contents Since the Shelby v5 software now stores information in the \Shelby\ssv5.dat folder as well as in the SQL database;
Creating a Complete Backup of Shelby v5 Data Backup the Shelby folder and all its contents Since the Shelby v5 software now stores information in the \Shelby\ssv5.dat folder as well as in the SQL database;
16 Common Backup Problems & Mistakes
 16 Common Backup Problems & Mistakes 1. Tape errors, Tape Drive failures. Probably the number one backup problem is simply caused by the unreliability of tape. Tape drives have a higher failure rate than
16 Common Backup Problems & Mistakes 1. Tape errors, Tape Drive failures. Probably the number one backup problem is simply caused by the unreliability of tape. Tape drives have a higher failure rate than
Information Security Policy September 2009 Newman University IT Services. Information Security Policy
 Contents 1. Statement 1.1 Introduction 1.2 Objectives 1.3 Scope and Policy Structure 1.4 Risk Assessment and Management 1.5 Responsibilities for Information Security 2. Compliance 3. HR Security 3.1 Terms
Contents 1. Statement 1.1 Introduction 1.2 Objectives 1.3 Scope and Policy Structure 1.4 Risk Assessment and Management 1.5 Responsibilities for Information Security 2. Compliance 3. HR Security 3.1 Terms
Designing, Optimizing and Maintaining a Database Administrative Solution for Microsoft SQL Server 2008
 Course 50400A: Designing, Optimizing and Maintaining a Database Administrative Solution for Microsoft SQL Server 2008 Length: 5 Days Language(s): English Audience(s): IT Professionals Level: 300 Technology:
Course 50400A: Designing, Optimizing and Maintaining a Database Administrative Solution for Microsoft SQL Server 2008 Length: 5 Days Language(s): English Audience(s): IT Professionals Level: 300 Technology:
Birkenhead Sixth Form College IT Disaster Recovery Plan
 Author: Role: Mal Blackburne College Learning Manager Page 1 of 14 Introduction...3 Objectives/Constraints...3 Assumptions...4 Incidents Requiring Action...4 Physical Safeguards...5 Types of Computer Service
Author: Role: Mal Blackburne College Learning Manager Page 1 of 14 Introduction...3 Objectives/Constraints...3 Assumptions...4 Incidents Requiring Action...4 Physical Safeguards...5 Types of Computer Service
DISASTER RECOVERY. Omniture Disaster Plan. June 2, 2008 Version 2.0
 DISASTER RECOVERY Omniture Disaster Plan June 2, 2008 Version 2.0 CHAPTER 1 1 Disaster Recovery Plan Overview In the event that one of our data collection environments are unavailable due to an event,
DISASTER RECOVERY Omniture Disaster Plan June 2, 2008 Version 2.0 CHAPTER 1 1 Disaster Recovery Plan Overview In the event that one of our data collection environments are unavailable due to an event,
Welcome to My E-Book
 Welcome to My E-Book I decided to write this e-book as a response to the many questions that I get from business owners about data backup solutions. I have seen first-hand that business owners are very
Welcome to My E-Book I decided to write this e-book as a response to the many questions that I get from business owners about data backup solutions. I have seen first-hand that business owners are very
M4 Systems. M4 Online Backup. M4 Systems Ltd Tel: 0845 5000 777 International: +44 (0)1443 863910 www.m4systems.com www.dynamicsplus.
 M4 Systems M4 Online Backup M4 Systems Ltd Tel: 0845 5000 777 International: +44 (0)1443 863910 www.m4systems.com www.dynamicsplus.net Table of Contents Introduction... 3 Benefits... 3 Features... 4 Data
M4 Systems M4 Online Backup M4 Systems Ltd Tel: 0845 5000 777 International: +44 (0)1443 863910 www.m4systems.com www.dynamicsplus.net Table of Contents Introduction... 3 Benefits... 3 Features... 4 Data
Managing and Maintaining a Microsoft Windows Server 2003 Environment
 Managing and Maintaining a Microsoft Windows Server 2003 Environment Course 2273: Five days; Blended (classroom/e-learning) Introduction Elements of this syllabus are subject to change. This course combines
Managing and Maintaining a Microsoft Windows Server 2003 Environment Course 2273: Five days; Blended (classroom/e-learning) Introduction Elements of this syllabus are subject to change. This course combines
ICT Disaster Recovery Plan
 7 Appendix A ICT Disaster Recovery Plan Definition of a Disaster A computer disaster is the occurrence of any computer system or associated event which causes the interruption of business, leading in the
7 Appendix A ICT Disaster Recovery Plan Definition of a Disaster A computer disaster is the occurrence of any computer system or associated event which causes the interruption of business, leading in the
Chapter 8: Security Measures Test your knowledge
 Security Equipment Chapter 8: Security Measures Test your knowledge 1. How does biometric security differ from using password security? Biometric security is the use of human physical characteristics (such
Security Equipment Chapter 8: Security Measures Test your knowledge 1. How does biometric security differ from using password security? Biometric security is the use of human physical characteristics (such
Creating a Domain Tree
 156 Chapter 4 Installing and Managing Trees and Forests Using the Active Directory Installation Wizard, you can quickly and easily create new domains by promoting a Windows Server 2008 stand-alone server
156 Chapter 4 Installing and Managing Trees and Forests Using the Active Directory Installation Wizard, you can quickly and easily create new domains by promoting a Windows Server 2008 stand-alone server
10 Things Your Data Center Backup Solution Should Do. Reliable, fast and easy backup is only the beginning
 10 Things Your Data Center Backup Solution Should Do Reliable, fast and easy backup is only the beginning Table of Contents Ten Things Your Data Center Backup Should Do 1 #1: Reduce Hours Spent on Backup
10 Things Your Data Center Backup Solution Should Do Reliable, fast and easy backup is only the beginning Table of Contents Ten Things Your Data Center Backup Should Do 1 #1: Reduce Hours Spent on Backup
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e. Chapter 3 Installing Windows
 : Managing, Maintaining, and Troubleshooting, 5e Chapter 3 Installing Windows Objectives How to plan a Windows installation How to install Windows Vista How to install Windows XP How to install Windows
: Managing, Maintaining, and Troubleshooting, 5e Chapter 3 Installing Windows Objectives How to plan a Windows installation How to install Windows Vista How to install Windows XP How to install Windows
COVER SHEET OF POLICY DOCUMENT Code Number Policy Document Name
 COVER SHEET OF POLICY DOCUMENT Code Number Policy Document Name Introduction Removable Media and Mobile Device Policy Removable media and mobile devices are increasingly used to enable information access
COVER SHEET OF POLICY DOCUMENT Code Number Policy Document Name Introduction Removable Media and Mobile Device Policy Removable media and mobile devices are increasingly used to enable information access
BACKUP SECURITY GUIDELINE
 Section: Information Security Revised: December 2004 Guideline: Description: Backup Security Guidelines: are recommended processes, models, or actions to assist with implementing procedures with respect
Section: Information Security Revised: December 2004 Guideline: Description: Backup Security Guidelines: are recommended processes, models, or actions to assist with implementing procedures with respect
MS-50400 - Design, Optimize and Maintain Database for Microsoft SQL Server 2008
 MS-50400 - Design, Optimize and Maintain Database for Microsoft SQL Server 2008 Table of Contents Introduction Audience At Completion Prerequisites Microsoft Certified Professional Exams Student Materials
MS-50400 - Design, Optimize and Maintain Database for Microsoft SQL Server 2008 Table of Contents Introduction Audience At Completion Prerequisites Microsoft Certified Professional Exams Student Materials
NetIQ Advanced Authentication Framework. Maintenance Guide. Version 5.1.0
 NetIQ Advanced Authentication Framework Maintenance Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Purposes of Maintenance 3 Difficulties of Maintenance
NetIQ Advanced Authentication Framework Maintenance Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Purposes of Maintenance 3 Difficulties of Maintenance
BounceBack Server Solution Reference Guide
 BounceBack Server Solution Reference Guide Contents Introduction... 2 System Requirements... 3 Initial Setup... 4 BounceBack Server Appliance Front View... 5 BounceBack Server Appliance Rear View... 6
BounceBack Server Solution Reference Guide Contents Introduction... 2 System Requirements... 3 Initial Setup... 4 BounceBack Server Appliance Front View... 5 BounceBack Server Appliance Rear View... 6
ICT NETWORK AND INFRASTRUCTURE FILE SERVER POLICY
 ICT NETWORK AND INFRASTRUCTURE FILE SERVER POLICY Version 1.0 Ratified By Date Ratified Author(s) Responsible Committee / Officers Issue Date Review Date Intended Audience Impact Assessed CCG Committee
ICT NETWORK AND INFRASTRUCTURE FILE SERVER POLICY Version 1.0 Ratified By Date Ratified Author(s) Responsible Committee / Officers Issue Date Review Date Intended Audience Impact Assessed CCG Committee
www.cadline.co.uk www.midastechnology.co.uk Page 1 of 5
 Page 1 of 5 Support Are you confident that you have all eventualities covered and that your current IT support provider can handle all of your issues? Are you frustrated with your application supplier
Page 1 of 5 Support Are you confident that you have all eventualities covered and that your current IT support provider can handle all of your issues? Are you frustrated with your application supplier
CHAPTER 9 System Backup and Restoration, Disk Cloning
 CHAPTER 9 System Backup and Restoration, Disk Cloning Learning Objectives After completing this lesson, you should be able to: i. Explain the method of doing data backup and restoration. ii. Describe the
CHAPTER 9 System Backup and Restoration, Disk Cloning Learning Objectives After completing this lesson, you should be able to: i. Explain the method of doing data backup and restoration. ii. Describe the
Countering and reducing ICT security risks 1. Physical and environmental risks
 Countering and reducing ICT security risks 1. Physical and environmental risks 1. Physical and environmental risks Theft of equipment from staff areas and Theft of equipment from public areas Theft of
Countering and reducing ICT security risks 1. Physical and environmental risks 1. Physical and environmental risks Theft of equipment from staff areas and Theft of equipment from public areas Theft of
Disaster Recovery Planning Save Your Business
 Disaster Recovery Planning Save Your Business Your business at risk! Your company is at risk for failure in the event of disaster Your data is at risk for costly loss Your revenue is at risk with lack
Disaster Recovery Planning Save Your Business Your business at risk! Your company is at risk for failure in the event of disaster Your data is at risk for costly loss Your revenue is at risk with lack
Windows 7 Hard Disk Recovery
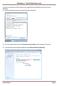 In order to restore your hard drive back to the original factory settings you will need to do the following: 1) Press the start button and in the search area type Recovery 2) From the search results, launch
In order to restore your hard drive back to the original factory settings you will need to do the following: 1) Press the start button and in the search area type Recovery 2) From the search results, launch
ICT SECURITY POLICY. Strategic Aim To continue to develop and ensure effective leadership, governance and management throughout the organisation
 ICT SECURITY POLICY Strategic Aim To continue to develop and ensure effective leadership, governance and management throughout the organisation Responsibility Assistant Principal, Learner Services Jannette
ICT SECURITY POLICY Strategic Aim To continue to develop and ensure effective leadership, governance and management throughout the organisation Responsibility Assistant Principal, Learner Services Jannette
The Benefits of Continuous Data Protection (CDP) for IBM i and AIX Environments
 The Benefits of Continuous Data Protection (CDP) for IBM i and AIX Environments New flexible technologies enable quick and easy recovery of data to any point in time. Introduction Downtime and data loss
The Benefits of Continuous Data Protection (CDP) for IBM i and AIX Environments New flexible technologies enable quick and easy recovery of data to any point in time. Introduction Downtime and data loss
Which Backup Option is Best?
 Which Backup Option is Best? Which Backup Option is Best? Why Protect Your Data? Data loss disasters happen more frequently than you would think, for many different reasons: Human error and accidental
Which Backup Option is Best? Which Backup Option is Best? Why Protect Your Data? Data loss disasters happen more frequently than you would think, for many different reasons: Human error and accidental
This policy is not designed to use systems backup for the following purposes:
 Number: AC IT POL 003 Subject: Backup and Restore Policy 1. PURPOSE The backup and restore policy establishes the need and rules for performing periodic system backup to permit timely restoration of Africa
Number: AC IT POL 003 Subject: Backup and Restore Policy 1. PURPOSE The backup and restore policy establishes the need and rules for performing periodic system backup to permit timely restoration of Africa
NCTE Advice Sheet Storage and Backup Advice Sheet 7
 Storage and Backup No matter how well you treat your system, no matter how much care you take, you cannot guarantee that your data will be safe if it exists in only one place. The risks are much greater
Storage and Backup No matter how well you treat your system, no matter how much care you take, you cannot guarantee that your data will be safe if it exists in only one place. The risks are much greater
Technology Solutions That Make Business Sense. The 10 Disaster Planning Essentials For A Small Business Network
 Technology Solutions That Make Business Sense. The 10 Disaster Planning Essentials For A Small Business Network If your data is important to your business and you cannot afford to have your operations
Technology Solutions That Make Business Sense. The 10 Disaster Planning Essentials For A Small Business Network If your data is important to your business and you cannot afford to have your operations
SOLUTION GUIDE AND BEST PRACTICES
 SOLUTION GUIDE AND BEST PRACTICES Last Updated December 2012 Solution Overview Combine the best in bare-metal backup with the best in remote backup to offer your customers a complete disaster recovery
SOLUTION GUIDE AND BEST PRACTICES Last Updated December 2012 Solution Overview Combine the best in bare-metal backup with the best in remote backup to offer your customers a complete disaster recovery
Database Operations (Backup/Restore/Move/Manage) Technical Support Engineering Rosslare Security NA For more information please see www.axtraxng.
 Database Operations (Backup/Restore/Move/Manage) Technical Support Engineering Rosslare Security NA For more information please see www.axtraxng.com Database management operations may be performed to insure
Database Operations (Backup/Restore/Move/Manage) Technical Support Engineering Rosslare Security NA For more information please see www.axtraxng.com Database management operations may be performed to insure
Backup and Recovery in Laserfiche 8. White Paper
 Backup and Recovery in Laserfiche 8 White Paper July 2008 The information contained in this document represents the current view of Compulink Management Center, Inc on the issues discussed as of the date
Backup and Recovery in Laserfiche 8 White Paper July 2008 The information contained in this document represents the current view of Compulink Management Center, Inc on the issues discussed as of the date
Data Protection Simple. Compliant. Secure. CONTACT US Call: 020 3397 9026 Email: [email protected] Visit: www.jms-securedata.co.
 Data Protection Simple. Compliant. Secure CONTACT US Call: 020 3397 9026 Email: [email protected] Visit: www.jms-securedata.co.uk COMPLEX CHALLENGES SIMPLE SOLUTIONS Backups Tricky but necessary
Data Protection Simple. Compliant. Secure CONTACT US Call: 020 3397 9026 Email: [email protected] Visit: www.jms-securedata.co.uk COMPLEX CHALLENGES SIMPLE SOLUTIONS Backups Tricky but necessary
IT NETWORK AND INFRASTRUCTURE FILE SERVER POLICY
 IT NETWORK AND INFRASTRUCTURE FILE SERVER POLICY Version 3.0 Ratified By Date Ratified April 2013 Author(s) Responsible Committee / Officers Issue Date January 2014 Review Date Intended Audience Impact
IT NETWORK AND INFRASTRUCTURE FILE SERVER POLICY Version 3.0 Ratified By Date Ratified April 2013 Author(s) Responsible Committee / Officers Issue Date January 2014 Review Date Intended Audience Impact
IT NETWORK AND INFRASTRUCTURE FILE SERVER POLICY (for Cheshire CCGs)
 IT NETWORK AND INFRASTRUCTURE FILE SERVER POLICY (for Cheshire CCGs) Version 3.2 Ratified By Date Ratified November 2014 Author(s) Responsible Committee / Officers Issue Date November 2014 Review Date
IT NETWORK AND INFRASTRUCTURE FILE SERVER POLICY (for Cheshire CCGs) Version 3.2 Ratified By Date Ratified November 2014 Author(s) Responsible Committee / Officers Issue Date November 2014 Review Date
Disaster Prevention and Recovery Plan
 Disaster Prevention and Recovery Plan for Windows Based Networks by Jeff Kendrick, 1. Prevention A. Daily tape backups B. Monthly Automated System Restore (ASR) or Windows 2008 backups and updates C. Alternate
Disaster Prevention and Recovery Plan for Windows Based Networks by Jeff Kendrick, 1. Prevention A. Daily tape backups B. Monthly Automated System Restore (ASR) or Windows 2008 backups and updates C. Alternate
Storage Backup and Disaster Recovery: Using New Technology to Develop Best Practices
 Storage Backup and Disaster Recovery: Using New Technology to Develop Best Practices September 2008 Recent advances in data storage and data protection technology are nothing short of phenomenal. Today,
Storage Backup and Disaster Recovery: Using New Technology to Develop Best Practices September 2008 Recent advances in data storage and data protection technology are nothing short of phenomenal. Today,
Suite. How to Use GrandMaster Suite. Backup and Restore
 Suite How to Use GrandMaster Suite Backup and Restore This page intentionally left blank Backup and Restore 3 Table of Contents: HOW TO USE GRANDMASTER SUITE - PAYROLL BACKUP AND RESTORE...4 OVERVIEW...4
Suite How to Use GrandMaster Suite Backup and Restore This page intentionally left blank Backup and Restore 3 Table of Contents: HOW TO USE GRANDMASTER SUITE - PAYROLL BACKUP AND RESTORE...4 OVERVIEW...4
Overview. Remote access and file transfer. SSH clients by platform. Logging in remotely
 Remote access and file transfer Overview Remote logins to Bio-Linux with ssh Running software from another machine Logging in from another machine Getting files on and off Bio-Linux Transferring files
Remote access and file transfer Overview Remote logins to Bio-Linux with ssh Running software from another machine Logging in from another machine Getting files on and off Bio-Linux Transferring files
Our Cloud Offers You a Brighter Future
 Our Cloud Offers You a Brighter Future Qube Global Software Cloud Services are used by many diverse organisations including financial institutions, international service providers, property companies,
Our Cloud Offers You a Brighter Future Qube Global Software Cloud Services are used by many diverse organisations including financial institutions, international service providers, property companies,
Traditionally, a typical SAN topology uses fibre channel switch wiring while a typical NAS topology uses TCP/IP protocol over common networking
 Network Storage for Business Continuity and Disaster Recovery and Home Media White Paper Abstract Network storage is a complex IT discipline that includes a multitude of concepts and technologies, like
Network Storage for Business Continuity and Disaster Recovery and Home Media White Paper Abstract Network storage is a complex IT discipline that includes a multitude of concepts and technologies, like
Backup Strategies for Small Business
 Backup Strategies for Small Business StarTech Group, Inc. Jim Scalise 11.15.2014 1 StarTech Group, Inc. 2771-29 Monument Rd. PMB 232 Jacksonville, FL 32225 CONTENTS BACKUP STRATEGIES.. 1 CLOUD BACKUP 2
Backup Strategies for Small Business StarTech Group, Inc. Jim Scalise 11.15.2014 1 StarTech Group, Inc. 2771-29 Monument Rd. PMB 232 Jacksonville, FL 32225 CONTENTS BACKUP STRATEGIES.. 1 CLOUD BACKUP 2
How to Plan for Disaster Recovery
 ImproMed LLC How to Plan for Disaster Recovery Revised January 27, 2015 2015 ImproMed, LLC. All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
ImproMed LLC How to Plan for Disaster Recovery Revised January 27, 2015 2015 ImproMed, LLC. All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Availability and Disaster Recovery: Basic Principles
 Availability and Disaster Recovery: Basic Principles by Chuck Petch, WVS Senior Technical Writer At first glance availability and recovery may seem like opposites. Availability involves designing computer
Availability and Disaster Recovery: Basic Principles by Chuck Petch, WVS Senior Technical Writer At first glance availability and recovery may seem like opposites. Availability involves designing computer
The Microsoft Large Mailbox Vision
 WHITE PAPER The Microsoft Large Mailbox Vision Giving users large mailboxes without breaking your budget Introduction Giving your users the ability to store more e mail has many advantages. Large mailboxes
WHITE PAPER The Microsoft Large Mailbox Vision Giving users large mailboxes without breaking your budget Introduction Giving your users the ability to store more e mail has many advantages. Large mailboxes
Westek Technology Snapshot and HA iscsi Replication Suite
 Westek Technology Snapshot and HA iscsi Replication Suite Westek s Power iscsi models have feature options to provide both time stamped snapshots of your data; and real time block level data replication
Westek Technology Snapshot and HA iscsi Replication Suite Westek s Power iscsi models have feature options to provide both time stamped snapshots of your data; and real time block level data replication
StorageCraft Technology Corporation Leading the Way to Safer Computing 2004-2009 StorageCraft Technology Corporation. All Rights Reserved.
 PRODUCT SCENARIOS Introduction Fast and reliable online backup and bare metal recovery for Windows servers ShadowProtect Server Edition creates an exact point-in-time backup of your entire server or specific
PRODUCT SCENARIOS Introduction Fast and reliable online backup and bare metal recovery for Windows servers ShadowProtect Server Edition creates an exact point-in-time backup of your entire server or specific
