Traffic Analysis Attacks and Countermeasures in Wireless Body Area Sensor Networks
|
|
|
- Ethelbert Whitehead
- 8 years ago
- Views:
Transcription
1 Traffic Analysis Attacks and Countermeasures in Wireless Body Area Sensor Networks Levente Buttyan and Tamas Holczer Laboratory of Cryptography and Systems Security (CrySyS) Budapest University of Technology and Economics {buttyan, Abstract In this paper, we study the problem of traffic analysis attacks in wireless body area sensor networks. When these networks are used in health-care for remote patient monitoring, traffic analysis can reveal the type of medical sensors mounted on the patient, and this information may be used to infer the patient s health problems. We show that simple signal processing methods can be used effectively for performing traffic analysis attacks and identifying the sensor types in a rather weak adversary model. We then investigate possible traffic obfuscation mechanisms aiming at hiding the regular patterns in the observable wireless traffic. Among the investigated countermeasures, traffic shaping, a mechanism that introduces carefully chosen delays for message transmissions, appears to be the best choice, as it achieves close to optimal protection and incurs no overhead. I. INTRODUCTION Wireless Body Area Sensor Networks (BASNs) consist of wearable sensors with wireless communication capabilities. Their typical application area is the health-care domain, where they can be used for remote patient monitoring. In this context, the BASN nodes are equipped with different types of medical sensors capable for collecting, for instance, ECG signals, temperature readings, pulse counts, and blood pressure measurements. The BASN nodes may perform some preprocessing of the collected data, however, due to their resource constraints, they cannot accomplish complex processing tasks, neither they can store large amount of data. Therefore, the BASN nodes off-load, using their wireless communication capabilities, their collected data to some gateway node, which is assumed to be a more powerful device such as a smart phone or PDA. The gateway can host various medical applications that use the sensor data collected from the BASN nodes. These applications may interact with the patient himself via welldesigned graphical user interfaces, and in addition, they may also provide controlled access to the collected sensor data for remote parties such as a physician. Wireless communication in case of BASNs typically means radio communication, which is known to be vulnerable to eavesdropping attacks. While message contents can be effectively protected against disclosure by encryption, traffic analysis attacks are still possible even on encrypted traffic. Moreover, in case of remote patient monitoring applications, traffic analysis is a serious threat, because traffic patterns may reveal the type of sensors mounted on the patient s body, which in turn may allow for inferring information about /12/$31.00 c 2012 IEEE the possible health problems of the patient. Identification of sensor types is made possible by the fact that medical sensors typically perform measurements in a periodic manner. As the BASN nodes have limited storage capabilities, these periodic measurements are typically transferred to the gateway device immediately, resulting in a periodic communication pattern between the BASN nodes and the gateway. A key observation is that different types of sensors perform measurements with different frequencies; for instance, ECG sampling rate can be in the range of 100 to 1000 Hz [1], while temperature sampling usually has a much lower rate of 1 measurement in every 5 minutes. Consequently, the types of sensors on the patient s body can be identified by identifying the different frequency components in the observable traffic. This can potentially work even if the messages are fully encrypted, including their addressing information. In this paper, our goal is to investigate the feasibility of traffic analysis attacks on BASN traffic, and to propose countermeasures that alleviate the traffic analysis problem. For this, we first introduce a system model and an attacker model in Section II that determine the conditions and the framework of our study. Then, in Section III, we show that simple signal processing techniques provide effective traffic analysis tools that allow identification of different sensors even by a very weak adversary and even if there are perturbations in the regularity of the transmissions of the nodes. In Section IV, we propose countermeasures against traffic analysis and evaluate their effectiveness by means of simulations. Finally, we conclude the paper in Section VI. II. SYSTEM AND ATTACKER MODELS The system that we study consists of some BASN nodes and a gateway that use single-hop wireless communication to send messages to each other. The majority of the messages are generated by the BASN nodes that transmit sensor readings to the gateway for storage and further processing. The traffic generated by a BASN node is largely periodic, however, we allow some perturbations in regularity in the form of slight shifts in exact message transmission times (which can represent delays and irregularities due to processing and networking issues) and in the form of a certain level of burstiness (which models the transmission of the result of a measurement campaign where multiple readings of the same sensor are collected and transmitted in multiple messages in a short period of time).
2 More specifically, we assume that time is slotted, there are multiple sources, and each source generates traffic independently with the following parameters: Frequency: This parameter is a constant that determines the frequency of the activity of the given source. Note that activity does not necessarily mean a single message transmission, but it can also mean the transmission of multiple messages in a burst. In the latter case, the frequency parameter determines the frequency of the bursty periods. Deviation: This parameter is a random variable and it determines a random shift of the exact transmission time (or beginning of the burst) with respect to the regular time determined by the frequency parameter. Burstiness: This parameter determines the level of burstiness of the traffic generated by the source. We allow for three types of burstiness in our model: no burst, fix burst, and Markov burst. No burst means that the source always transmits a single message when it is active. Fix burst means that a constant number of messages are transmitted when the source is active. Finally, in case of the Markov burst model, the amount of messages in the bursty period is a random value determined by a geometric distribution with some parameter p. In other words, after sending a message, the source continues transmission in the next time slot with some probability p, and stops sending more messages (and terminates the burst) with probability 1 p. We assume that the messages are encrypted, including their addressing information 1, and they have a uniform size (message padding can be used to achieve this). In addition, sources of transmissions cannot be distinguished by the attacker based on location information (all BASN nodes are mounted on the body of the patient, and the gateway is carried on the patient too, such that all devices appear to be too close to each other for the attacker), and radio fingerprinting is beyond the capabilities of the attacker (it is not yet mature and reliable enough as a technology). Thus, the attacker cannot distinguish different sources easily by their unique addresses, by their physical characteristics, or by any special properties of the messages themselves (i.e., all messages look a random string of bits with uniform length). These assumptions are needed, since otherwise the attacker could trivially identify different sources and distinguish their transmissions. Thus, in our model, the attacker can only observe the fact of a wireless transmission, and his knowledge, therefore, can be represented by a time series X 1, X 2,..., where X i is a random variable representing the time of the i-th transmission. Note that this is 1 Note that BASN nodes only communicate with the gateway, so each BASN node has a single key that it can use to decrypt messages and determine after decryption if the message was destined to it or not. Furthermore, by appropriate design, this decision can be made without requiring to decrypt the entire message (e.g., the message header can be encrypted separately). The gateway needs to try multiple keys for decrypting incoming messages, but it is a more powerful device. In any case, a careful design of the header encryption scheme is required to prevent Denial-of-Service type attacks where an attacker floods the network with randomly generated messages and forces the nodes to spend precious energy resources to decrypt and verify them. a very weak attacker model in the sense that the capabilities of the attacker are kept at the minimum. Finally, we assume that the attacker observes the wireless channel for some extended period of time, and his goal is to identify different sources and the characteristics of their traffic, most notably, the frequency of their activities, as this information can reveal the type of the source. III. TRAFFIC ANALYSIS ATTACKS As the attacker essentially wants to identify the different periodic components of the observed aggregate traffic, it is natural to interpret the time series representing the transmission events as a discrete signal, and use standard signal processing techniques to transform and analyze it in the spectral domain in order to identify the strongest frequency components. In this section, we introduce the standard Discrete Fourier Transform (DST) and the Welch Averaged Periodogram (WAP) [2] for this purpose, and we show that WAP can be used effectively for traffic analysis. Our selection of these tools has been inspired by [3] where these methods have already been used successfully for traffic analysis in a WiFi based multi-hop ad hoc network. Discrete Fourier Transform (DFT): Many spectral processing techniques use the standard Discrete Fourier Transform (DFT) to compute the spectrum of a signal in the time domain. The DFT of a uniformly sampled signal x(n) with M samples provides an M-point discrete spectrum X M (k), where X M (k) = M 1 n=0 2πkn j x(n)e M = DFT [x(n)] (1) The resulting spectrum X M (k) is a vector of complex numbers. This spectrum can be efficiently computed by the Fast Fourier Transform (FFT). The peak values in the spectrum correspond to frequencies of message transmission events. Thus, examination of the DFT spectrum can provide a visualization of flows in the form of characteristic peaks. However, it is often the case that the spectral content contains many harmonically related peaks. In addition, when the signal is noisy, conventional DFT processing does not provide a good unbiased estimate of the signal power spectrum. A better result in this case can be obtained with the signal periodogram which utilizes averaging in order to reduce the influence of noise. Welch Averaged Periodogram (WAP): The Welch Averaged Periodogram (WAP) uses windowing to account for the aperiodic nature of the signal. The periodogram P x (k) of a signal x(n) is generated by averaging the power of K separate spectra X (r) L (k) computed over K different segments of the data, each of length L: P x (k) = 1 K 1 X (r) L KU (k) 2 (2) r=0
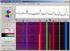
3 Figure 1 Sources Frequencies Deviations Burstiness (a) 2 1/23 2 no burst 1/29 3 no burst (b) 2 1/23 0 Markov p = 0.4 1/29 0 Markov p = 0.4 (c) 2 1/23 2 fix 3 1/29 3 Markov p = 0.4 (d) 3 1/23 2 Markov p = 0.4 1/29 3 Markov p = 0.4 1/37 3 Markov p = 0.3 TABLE I: Summary of parameter settings for the performance evaluation of DFT and WAP based traffic analysis where X (r) L (k) = DFT [ω(n)x r(n)] (3) U = 1 L 1 ω 2 (n) (4) L n=0 where x r (n) is the r-th windowed segment of x(n), ω(n) is a windowing function used to reduce artifacts caused by the abrupt changes at the endpoints of the window, and U is the normalized window power. We investigated the performance of DFT and WAP by means of simulations. The simulation environment was OM- NeT++ (version 4.2.1) with the MiXiM framework (version 2.2.1, , ZigBee protocol stack). We generated the time series of transmission events according to the model described in Section II with different number of sources and different combinations for the parameters of frequency, deviation, and burstiness. Then, we computed the spectrum of the signal obtained from the time series of transmission events by DFT and by WAP. The results are shown in Figure 1. The parameter settings of the figures are summarized in Table I. As one can see from the figures, both DFT and WAP identify the transmission frequency of the sources despite of the noise caused by the deviation and burstiness parameters, as well as by the characteristics of the wireless channel and the ZigBee protocol used in the simulations. However, WAP better eliminates the harmonic components in most of the cases. Hence, we can conclude that traffic analysis based on WAP works in a robust way, and allows the attacker to identify the sources and the characteristics of their traffic patterns with high confidence. IV. COUNTERMEASURES In order to make traffic analysis harder for the attacker, the traffic patterns must be obfuscated. This can be achieved by adding some dummy traffic to the original traffic or by altering the timing of transmissions such that they do not follow a regular pattern. An obvious disadvantage of using dummy traffic to obfuscate the original traffic patterns is that this approach introduces some communication (and computing) overhead, which ultimately results in an increased energy consumption by the BASN nodes. This means that using dummy traffic reduces the lifetime of the BASN nodes, which is undesirable for practical reasons. Note, however, that the energy consumption overhead of the BASN nodes can be reduced, if we let the gateway generate all the dummy messages. This is possible, because in our model, the attacker cannot distinguish between messages generated by the BASN nodes and messages generated by the gateway (they all appear to be random bit strings of some uniform length). In addition, the gateway has more resources and its battery can be recharged easier. But even in this case, the BASN nodes still need to receive and decrypt at least the header of each message, including dummy messages, in order to determine who is the intended destination of the message. Reception and computation also consume energy, therefore, even if the dummy messages are generated by the gateway, the energy consumption of the BASN nodes will be increased. The advantage of altering the timing of transmissions as a traffic pattern obfuscation mechanism for BASNs is that this approach has no overhead. On the other hand, it introduces some delivery delay for every message and requires some memory on the BASN nodes to store sensor readings until they are transmitted to the gateway. Thus, this approach requires some trade-off between the maximum delay introduced for messages and the level of protection achieved against traffic analysis attacks. In the following, we introduce and investigate three traffic pattern obfuscation mechanisms: Dummy noise: This is a dummy traffic generation mechanism, where the gateway injects dummy messages in a completely random manner, hence, creating noise that covers the real traffic. Dummy source: This is also a dummy traffic generation mechanism, where the gateway simulates the transmissions of a fake sensor, hence, making the attacker believe that the given type of sensor is mounted on the patient, while in reality, it is not. More specifically, if the attacker knows that this mechanism is used for dummy traffic generation, then he cannot be sure that any identified sensor type is actually on the patient or its presence is just simulated by the gateway. Traffic shaping: This mechanism assumes that the delivery of sensor readings can be delayed up to a maximum delay D, and there are some limited memory on the BASN nodes to store sensor data until they are transmitted to the gateway. When a new sensor reading is obtained, the BASN node schedules its transmission such that the sensor data does not suffer a longer delay than D and the observable inter-transmission times have a close to uniform distribution. This is achieved by continuously tracking (and updating in the memory) the empirical distribution, i.e., the histogram of some granularity, of the inter-transmission times on the wireless interface of the BASN node, and scheduling a new transmission such that the resulting new inter-transmission time falls in the smallest size bin of the histogram. We evaluated the performance of these countermeasures by means of simulations using OMNeT++ (version 4.2.1) with the
4 (a) (b) (c) Fig. 1: Traffic analysis with DFT and WAP. Parameter settings are summarized in Table I. (d) MiXiM framework (version 2.2.1, , ZigBee protocol stack) as the simulation environment. For the purpose of the evaluation, we gave advantage to the attacker, and we used a single real source that generated completely regular traffic with frequency equal to 1/23. We applied the traffic pattern obfuscation mechanisms described above, and computed the DFT and WAP spectra of the signal representing the time series of transmission events observed by the attacker. The results are shown in Figure 2. Figure 2(a) shows the spectra of the traffic of the real source without using any countermeasures. The peaks at frequency 1/23 and its multiples in both the DFT and WAP spectra are well identifiable. Figure 2(b) shows the spectra when the gateway generates dummy transmissions randomly. We can observe the noise in the spectra, although the DFT spectrum preserves the peak at frequency 1/23, and hence, this method does not properly covers the original traffic pattern. Figure 2(c) shows the spectra when the gateway simulates a fake sensor that generates transmissions with frequency equal to 1/29. Clearly, for the attacker both frequencies (1/23, 1/29) appear in the spectra just as if there were two sensors transmitting. Finally, Figure 2(d) shows the situation when the BASN node obfuscates its traffic pattern by traffic shaping, using D = 100 and 100 bins in the histogram. It can be clearly seen that neither the DFT nor the WAP spectrum preserves any useful information for the attacker. For the purpose of some quantitative comparison of the different approaches, we define the entropy of the WAP spectrum, denoted by H, as a metric to measure the information content in the spectrum of the traffic signal. For this, we compute the WAP spectrum of a given length (in our experiments we used length L = 100, which resulted in an L/2 + 1 = 51 point periodogram), we omit the component at frequency equal to 0, we normalize the remaining values and interpret them as elements of a discrete probability distribution, and finally, we compute the entropy of this distribution. The entropy values that we obtained for the original traffic signal and the obfuscated signals are shown in Table II, together with the theoretical maximum of the entropy (which was log 50 = 5.64 in our case). Clearly, the closer the entropy of a WAP spectrum is to the theoretical maximum, the larger is its information content, and larger information content of the WAP spectrum means higher uncertainty for the attacker. As we can see from the table, adding dummy noise and
5 (a) (b) (c) (d) Fig. 2: Traffic analysis of the obfuscated traffic with DFT and WAP. Obfuscation Entropy None Dummy noise Dummy source Traffic shaping Theoretical maximum TABLE II: Entropy values obtained for the original traffic signal and the obfuscated signals. The table also shows the maximum achievable entropy for the spectrum length we used in our experiment. using traffic shaping both result in an entropy value close to the theoretical optimum. However, as we said before, the dummy noise mechanisms incurs a considerable message overhead, while traffic shaping has no overhead at all. Therefore, among the three traffic pattern obfuscation techniques, traffic shaping seems to be the most promising in our application. We investigated the performance of traffic shaping a bit further. More specifically, we measured the entropy of the WAP spectrum of a traffic signal obfuscated with traffic shaping using different values for the maximum delay that we allow for the message transmissions and for different granularities (number of bins) of the histogram used to track the empirical distribution of the inter-transmission times. The results of these measurements are shown in Figure 3, where part (a) shows the measured entropy as a function of the maximum delay, and part (b) shows the entropy as the function of the number of the bins. Recall that the frequency of the original traffic signal was 1/23, meaning that a message was sent in every 23th time slots. From Figure 3(a), we can see that the entropy of the WAP spectrum increases as the maximum delay increases, and the minimum value of the maximum delay where a sufficiently high level of protection is provided is around twice the period length, in our case, around 50. From Figure 3(b), we can see that when the maximum delay as above this threshold, then the number of bins used in the histogram, does not really influence the performance. V. RELATED WORK The paper with the strongest relation to our work is [3], in which the authors study traffic analysis attacks in wireless networks and show that signal processing techniques such as DFT and WAP can be very effective in practice. Indeed, the work in [3] inspired us to use DFT and WAP in the special
6 (a) Fig. 3: Entropy of WAP as a function of (a) the maximum delay and (b) the number of the bins. (b) case of traffic analysis in BASNs. Besides the difference in the application domains, and hence, in the related wireless technologies, a major difference between [3] and our work is that the former does not propose and investigate possible countermeasures at all. Another related paper is [4], where the authors use statistical and structural content models for separating different traffic types that use different applicationlayer protocols. However, their approach is based on the flow content, whereas in our model, the attacker cannot access the content of the messages. Countermeasures against traffic analysis attacks are proposed in [5], [6], [7], [8]. However, [5], [6] are limited to traffic padding with dummy messages. In addition, in [7], [8], the authors consider a problem somewhat different from ours, namely, the identification of the sink in a multi-hop wireless sensor network using the spatial patterns of the traffic. In our work, we focus on traffic shaping that does not require dummy messages, and we are not concerned with the spatial properties of the traffic. VI. CONCLUSION In this paper, we studied traffic analysis attacks in BASNs and we proposed some countermeasures. One of our main conclusions is that simple signal processing methods can be used effectively for performing traffic analysis attacks and identifying the sensor types mounted on the patients. The attacks work in a weak attacker model. Clearly, in a stronger model (e.g., if header encryption is not supported), the traffic analysis attacks become easier; or even trivial. The other main conclusion is that among the possible countermeasures that we investigated, traffic shaping by introducing carefully chosen inter-transmission delays appears to be the best solution, because it has no overhead and it obfuscates traffic patterns effectively. Furthermore, in order to achieve close to optimal protection, the maximum delay used by traffic shaping should be at least twice of the period length of the traffic signal. We believe that in practice, this amount of delay for sensor readings is acceptable as it does not really affect the applications that use the collected sensor data. Acknowledgment: The work described in this paper is based on results of the CHIRON project 2, which receives research funding from the EU ARTEMIS Joint Undertaking. Apart from this, ARTEMIS has no responsibility for the content of this paper. The information in this document is provided as is and no guarantee or warranty is given that the information is fit for any particular purpose. The user thereof uses the information at its sole risk and liability. REFERENCES [1] R. Fensli, E. Gunnarson, and T. Gundersen, A wearable ECG-recording system for continuous arrhythmia monitoring in a wireless tele-home-care situation, in Proceedings of the 18th IEEE Symposium on Computer- Based Medical Systems, June [2] P. D. Welch, The use of fast fourier transform for estimation of power spectra: A method based on time averaging over short, modified periodograms, IEEE Transactions on Audio Electroacoustics, vol. AU- 15, pp , [3] C. Partridge, D. Cousins, A. W. Jackson, R. Krishnan, T. Saxena, and W. Strayer, Using signal processing to analyze wireless data traffic, in Proceedings of the 1st ACM workshop on Wireless security. ACM, 2002, pp [4] J. Ma, K. Levchenko, C. Kreibich, S. Savage, and G. M. Voelker, Unexpected means of protocol inference, in Proceedings of the 6th ACM SIGCOMM conference on Internet measurement, ser. IMC 06, [5] X. Fu, B. Graham, R. Bettati, and W. Zhao, On effectiveness of link padding for statistical traffic analysis attacks, in Proceedings of the 23rd International Conference on Distributed Computing Systems, ser. ICDCS 03, [6] R. E. Newman, I. S. Moskowitz, P. Syverson, and A. Serjantov, Metrics for traffic analysis prevention, in Proceedings of Privacy Enhancing Technologies workshop, ser. PET 03, [7] J. Deng, R. Han, and S. Mishra, Countermeasures against traffic analysis attacks in wireless sensor networks, in Proceedings of the First International Conference on Security and Privacy for Emerging Areas in Communications Networks, ser. SECURECOMM 05, [8] Y. Fan, Y. Jiang, H. Zhu, J. Chen, and X. Shen, Network coding based privacy preservation against traffic analysis in multi-hop wireless networks, IEEE Transactions on Wireless Communications, vol. 10, no. 3, March
Preventing Resource Exhaustion Attacks in Ad Hoc Networks
 Preventing Resource Exhaustion Attacks in Ad Hoc Networks Masao Tanabe and Masaki Aida NTT Information Sharing Platform Laboratories, NTT Corporation, 3-9-11, Midori-cho, Musashino-shi, Tokyo 180-8585
Preventing Resource Exhaustion Attacks in Ad Hoc Networks Masao Tanabe and Masaki Aida NTT Information Sharing Platform Laboratories, NTT Corporation, 3-9-11, Midori-cho, Musashino-shi, Tokyo 180-8585
Special Properties of Ad-hoc Wireless Network and Security Models
 Special Properties of Ad-hoc Wireless Network and Security Models Han Zhong Department of Computer Science, University of Auckland E-mail: hzho023@aucklanduni.ac.nz Abstract:There are certain amounts of
Special Properties of Ad-hoc Wireless Network and Security Models Han Zhong Department of Computer Science, University of Auckland E-mail: hzho023@aucklanduni.ac.nz Abstract:There are certain amounts of
Prediction of DDoS Attack Scheme
 Chapter 5 Prediction of DDoS Attack Scheme Distributed denial of service attack can be launched by malicious nodes participating in the attack, exploit the lack of entry point in a wireless network, and
Chapter 5 Prediction of DDoS Attack Scheme Distributed denial of service attack can be launched by malicious nodes participating in the attack, exploit the lack of entry point in a wireless network, and
Source Anonymity in Sensor Networks
 Source Anonymity in Sensor Networks Bertinoro PhD. Summer School, July 2009 Radha Poovendran Network Security Lab Electrical Engineering Department University of Washington, Seattle, WA http://www.ee.washington.edu/research/nsl
Source Anonymity in Sensor Networks Bertinoro PhD. Summer School, July 2009 Radha Poovendran Network Security Lab Electrical Engineering Department University of Washington, Seattle, WA http://www.ee.washington.edu/research/nsl
Mobile Security Wireless Mesh Network Security. Sascha Alexander Jopen
 Mobile Security Wireless Mesh Network Security Sascha Alexander Jopen Overview Introduction Wireless Ad-hoc Networks Wireless Mesh Networks Security in Wireless Networks Attacks on Wireless Mesh Networks
Mobile Security Wireless Mesh Network Security Sascha Alexander Jopen Overview Introduction Wireless Ad-hoc Networks Wireless Mesh Networks Security in Wireless Networks Attacks on Wireless Mesh Networks
A NOVEL OVERLAY IDS FOR WIRELESS SENSOR NETWORKS
 A NOVEL OVERLAY IDS FOR WIRELESS SENSOR NETWORKS Sumanta Saha, Md. Safiqul Islam, Md. Sakhawat Hossen School of Information and Communication Technology The Royal Institute of Technology (KTH) Stockholm,
A NOVEL OVERLAY IDS FOR WIRELESS SENSOR NETWORKS Sumanta Saha, Md. Safiqul Islam, Md. Sakhawat Hossen School of Information and Communication Technology The Royal Institute of Technology (KTH) Stockholm,
Defending Against Traffic Analysis Attacks with Link Padding for Bursty Traffics
 Proceedings of the 4 IEEE United States Military Academy, West Point, NY - June Defending Against Traffic Analysis Attacks with Link Padding for Bursty Traffics Wei Yan, Student Member, IEEE, and Edwin
Proceedings of the 4 IEEE United States Military Academy, West Point, NY - June Defending Against Traffic Analysis Attacks with Link Padding for Bursty Traffics Wei Yan, Student Member, IEEE, and Edwin
Wireless Sensor Networks Chapter 14: Security in WSNs
 Wireless Sensor Networks Chapter 14: Security in WSNs António Grilo Courtesy: see reading list Goals of this chapter To give an understanding of the security vulnerabilities of Wireless Sensor Networks
Wireless Sensor Networks Chapter 14: Security in WSNs António Grilo Courtesy: see reading list Goals of this chapter To give an understanding of the security vulnerabilities of Wireless Sensor Networks
Protecting Receiver-Location Privacy in Wireless Sensor Networks
 Protecting Receiver-Location Privacy in Wireless Sensor Networks Ying Jian Shigang Chen Zhan Zhang Liang Zhang Department of Computer & Information Science & Engineering University of Florida {yjian, sgchen,
Protecting Receiver-Location Privacy in Wireless Sensor Networks Ying Jian Shigang Chen Zhan Zhang Liang Zhang Department of Computer & Information Science & Engineering University of Florida {yjian, sgchen,
Demystifying Wireless for Real-World Measurement Applications
 Proceedings of the IMAC-XXVIII February 1 4, 2010, Jacksonville, Florida USA 2010 Society for Experimental Mechanics Inc. Demystifying Wireless for Real-World Measurement Applications Kurt Veggeberg, Business,
Proceedings of the IMAC-XXVIII February 1 4, 2010, Jacksonville, Florida USA 2010 Society for Experimental Mechanics Inc. Demystifying Wireless for Real-World Measurement Applications Kurt Veggeberg, Business,
Statistical Framework for Source Anonymity in Sensor Networks
 Statistical Framework for Source Anonymity in Sensor Networks Basel Alomair, Andrew Clark, Jorge Cuellar, and Radha Poovendran Network Security Lab (NSL),University of Washington, Seattle, Washington Siemens
Statistical Framework for Source Anonymity in Sensor Networks Basel Alomair, Andrew Clark, Jorge Cuellar, and Radha Poovendran Network Security Lab (NSL),University of Washington, Seattle, Washington Siemens
Thwarting Selective Insider Jamming Attacks in Wireless Network by Delaying Real Time Packet Classification
 Thwarting Selective Insider Jamming Attacks in Wireless Network by Delaying Real Time Packet Classification LEKSHMI.M.R Department of Computer Science and Engineering, KCG College of Technology Chennai,
Thwarting Selective Insider Jamming Attacks in Wireless Network by Delaying Real Time Packet Classification LEKSHMI.M.R Department of Computer Science and Engineering, KCG College of Technology Chennai,
Log-Likelihood Ratio-based Relay Selection Algorithm in Wireless Network
 Recent Advances in Electrical Engineering and Electronic Devices Log-Likelihood Ratio-based Relay Selection Algorithm in Wireless Network Ahmed El-Mahdy and Ahmed Walid Faculty of Information Engineering
Recent Advances in Electrical Engineering and Electronic Devices Log-Likelihood Ratio-based Relay Selection Algorithm in Wireless Network Ahmed El-Mahdy and Ahmed Walid Faculty of Information Engineering
Securing MANET Using Diffie Hellman Digital Signature Scheme
 Securing MANET Using Diffie Hellman Digital Signature Scheme Karamvir Singh 1, Harmanjot Singh 2 1 Research Scholar, ECE Department, Punjabi University, Patiala, Punjab, India 1 Karanvirk09@gmail.com 2
Securing MANET Using Diffie Hellman Digital Signature Scheme Karamvir Singh 1, Harmanjot Singh 2 1 Research Scholar, ECE Department, Punjabi University, Patiala, Punjab, India 1 Karanvirk09@gmail.com 2
End-to-End Security in Wireless Sensor Networks (WSNs) Talk by Claudio Anliker Supervised by Dr. Corinna Schmitt CSG@IFI, University of Zurich
 End-to-End Security in Wireless Sensor (WSNs) Talk by Supervised by Dr. Corinna Schmitt CSG@IFI, University of Zurich Content 1. Motivation 2. Security Issues and Principles 3. Internet-of-Things and Wireless
End-to-End Security in Wireless Sensor (WSNs) Talk by Supervised by Dr. Corinna Schmitt CSG@IFI, University of Zurich Content 1. Motivation 2. Security Issues and Principles 3. Internet-of-Things and Wireless
Depiction of Body Area Network in Cloud Environment
 I JMEIT Vol. 2 Issue 1 Jan 2014 Page No: 55-63 ISSN:2348-196x Depiction of Body Area Network in Cloud Environment P.Sankardayal 1, S.Grahalakshmi 2, P.Gopikannan 3, R.Vidhya Lakshmi 4, G.Sankareswari 5
I JMEIT Vol. 2 Issue 1 Jan 2014 Page No: 55-63 ISSN:2348-196x Depiction of Body Area Network in Cloud Environment P.Sankardayal 1, S.Grahalakshmi 2, P.Gopikannan 3, R.Vidhya Lakshmi 4, G.Sankareswari 5
Review of Prevention techniques for Denial of Service Attacks in Wireless Sensor Network
 Review of Prevention techniques for Denial of Service s in Wireless Sensor Network Manojkumar L Mahajan MTech. student, Acropolis Technical Campus, Indore (MP), India Dushyant Verma Assistant Professor,
Review of Prevention techniques for Denial of Service s in Wireless Sensor Network Manojkumar L Mahajan MTech. student, Acropolis Technical Campus, Indore (MP), India Dushyant Verma Assistant Professor,
Performance Monitoring and Control in Contention- Based Wireless Sensor Networks
 Performance Monitoring and Control in Contention- Based Wireless Sensor Networks Thomas Lindh #1, Ibrahim Orhan #2 # School of Technology and Health, KTH Royal Institute of Technology Marinens vag 30,
Performance Monitoring and Control in Contention- Based Wireless Sensor Networks Thomas Lindh #1, Ibrahim Orhan #2 # School of Technology and Health, KTH Royal Institute of Technology Marinens vag 30,
QUALITY OF SERVICE METRICS FOR DATA TRANSMISSION IN MESH TOPOLOGIES
 QUALITY OF SERVICE METRICS FOR DATA TRANSMISSION IN MESH TOPOLOGIES SWATHI NANDURI * ZAHOOR-UL-HUQ * Master of Technology, Associate Professor, G. Pulla Reddy Engineering College, G. Pulla Reddy Engineering
QUALITY OF SERVICE METRICS FOR DATA TRANSMISSION IN MESH TOPOLOGIES SWATHI NANDURI * ZAHOOR-UL-HUQ * Master of Technology, Associate Professor, G. Pulla Reddy Engineering College, G. Pulla Reddy Engineering
SPY AGENT BASED SECURE DATA AGGREGATION IN WSN
 ISSN: 2229-6948(ONLINE) ICTACT JOURNAL ON COMMUNICATION TECHNOLOGY, DECEMBER 214, VOLUME: 5, ISSUE: 4 SPY AGENT BASED SECURE DATA AGGREGATION IN WSN T. Lathies Bhasker 1 and G. Arul Jagan 2 1 Department
ISSN: 2229-6948(ONLINE) ICTACT JOURNAL ON COMMUNICATION TECHNOLOGY, DECEMBER 214, VOLUME: 5, ISSUE: 4 SPY AGENT BASED SECURE DATA AGGREGATION IN WSN T. Lathies Bhasker 1 and G. Arul Jagan 2 1 Department
Attacks on neighbor discovery
 Cryptographic Protocols (EIT ICT MSc) Dr. Levente Buttyán associate professor BME Hálózati Rendszerek és Szolgáltatások Tanszék Lab of Cryptography and System Security (CrySyS) buttyan@hit.bme.hu, buttyan@crysys.hu
Cryptographic Protocols (EIT ICT MSc) Dr. Levente Buttyán associate professor BME Hálózati Rendszerek és Szolgáltatások Tanszék Lab of Cryptography and System Security (CrySyS) buttyan@hit.bme.hu, buttyan@crysys.hu
Transmission Security (TRANSEC) in an IP-based VSAT Architecture. February 2011
 Transmission Security (TRANSEC) in an IP-based VSAT Architecture February 2011 As the ability to monitor satellite transmissions grows more sophisticated, the need to implement increased levels of security
Transmission Security (TRANSEC) in an IP-based VSAT Architecture February 2011 As the ability to monitor satellite transmissions grows more sophisticated, the need to implement increased levels of security
Security in Ad Hoc Network
 Security in Ad Hoc Network Bingwen He Joakim Hägglund Qing Gu Abstract Security in wireless network is becoming more and more important while the using of mobile equipments such as cellular phones or laptops
Security in Ad Hoc Network Bingwen He Joakim Hägglund Qing Gu Abstract Security in wireless network is becoming more and more important while the using of mobile equipments such as cellular phones or laptops
Image Compression through DCT and Huffman Coding Technique
 International Journal of Current Engineering and Technology E-ISSN 2277 4106, P-ISSN 2347 5161 2015 INPRESSCO, All Rights Reserved Available at http://inpressco.com/category/ijcet Research Article Rahul
International Journal of Current Engineering and Technology E-ISSN 2277 4106, P-ISSN 2347 5161 2015 INPRESSCO, All Rights Reserved Available at http://inpressco.com/category/ijcet Research Article Rahul
Vulnerabilities of Intrusion Detection Systems in Mobile Ad-hoc Networks - The routing problem
 Vulnerabilities of Intrusion Detection Systems in Mobile Ad-hoc Networks - The routing problem Ernesto Jiménez Caballero Helsinki University of Technology erjica@gmail.com Abstract intrusion detection
Vulnerabilities of Intrusion Detection Systems in Mobile Ad-hoc Networks - The routing problem Ernesto Jiménez Caballero Helsinki University of Technology erjica@gmail.com Abstract intrusion detection
An Experimental Study on Wireless Security Protocols over Mobile IP Networks
 An Experimental Study on Wireless Security Protocols over Mobile IP Networks Avesh K. Agarwal Department of Computer Science Email: akagarwa@unity.ncsu.edu Jorinjit S. Gill Department of Electrical and
An Experimental Study on Wireless Security Protocols over Mobile IP Networks Avesh K. Agarwal Department of Computer Science Email: akagarwa@unity.ncsu.edu Jorinjit S. Gill Department of Electrical and
III. Our Proposal ASOP ROUTING ALGORITHM. A.Position Management
 Secured On-Demand Position Based Private Routing Protocol for Ad-Hoc Networks Ramya.R, Shobana.K, Thangam.V.S ramya_88@yahoo.com, k shobsi@yahoo.co.in,thangam_85@yahoo.com Department of Computer Science,
Secured On-Demand Position Based Private Routing Protocol for Ad-Hoc Networks Ramya.R, Shobana.K, Thangam.V.S ramya_88@yahoo.com, k shobsi@yahoo.co.in,thangam_85@yahoo.com Department of Computer Science,
CHAPTER 6 SECURE PACKET TRANSMISSION IN WIRELESS SENSOR NETWORKS USING DYNAMIC ROUTING TECHNIQUES
 CHAPTER 6 SECURE PACKET TRANSMISSION IN WIRELESS SENSOR NETWORKS USING DYNAMIC ROUTING TECHNIQUES 6.1 Introduction The process of dispersive routing provides the required distribution of packets rather
CHAPTER 6 SECURE PACKET TRANSMISSION IN WIRELESS SENSOR NETWORKS USING DYNAMIC ROUTING TECHNIQUES 6.1 Introduction The process of dispersive routing provides the required distribution of packets rather
CHAPTER 1 INTRODUCTION
 CHAPTER 1 INTRODUCTION 1.0 Introduction Voice over Internet Protocol (VoIP) is the most popular in telecommunication technology. Nowadays, three million users use VoIP. It is estimated that the number
CHAPTER 1 INTRODUCTION 1.0 Introduction Voice over Internet Protocol (VoIP) is the most popular in telecommunication technology. Nowadays, three million users use VoIP. It is estimated that the number
AN OVERVIEW OF QUALITY OF SERVICE COMPUTER NETWORK
 Abstract AN OVERVIEW OF QUALITY OF SERVICE COMPUTER NETWORK Mrs. Amandeep Kaur, Assistant Professor, Department of Computer Application, Apeejay Institute of Management, Ramamandi, Jalandhar-144001, Punjab,
Abstract AN OVERVIEW OF QUALITY OF SERVICE COMPUTER NETWORK Mrs. Amandeep Kaur, Assistant Professor, Department of Computer Application, Apeejay Institute of Management, Ramamandi, Jalandhar-144001, Punjab,
A Secure Data Transmission for Cluster based Wireless Sensor Network Using LEACH Protocol
 A Secure Data Transmission for Cluster based Wireless Sensor Network Using LEACH Protocol Vinoda B Dibbad 1, C M Parameshwarappa 2 1 PG Student, Dept of CS&E, STJIT, Ranebennur, Karnataka, India 2 Professor,
A Secure Data Transmission for Cluster based Wireless Sensor Network Using LEACH Protocol Vinoda B Dibbad 1, C M Parameshwarappa 2 1 PG Student, Dept of CS&E, STJIT, Ranebennur, Karnataka, India 2 Professor,
Controlled Cloud-Based SaaS Service Scheme to Denial the Hotspot- Locating Attacks in Wireless Sensor Networks
 Controlled Cloud-Based SaaS Service Scheme to Denial the Hotspot- Locating Attacks in Wireless Sensor Networks K.Jegadeeswaran, S.Ramakrishnan, M.Mailsamy Assistant Professor(Sr.G) Assistant Professor
Controlled Cloud-Based SaaS Service Scheme to Denial the Hotspot- Locating Attacks in Wireless Sensor Networks K.Jegadeeswaran, S.Ramakrishnan, M.Mailsamy Assistant Professor(Sr.G) Assistant Professor
Detecting Multiple Selfish Attack Nodes Using Replica Allocation in Cognitive Radio Ad-Hoc Networks
 Detecting Multiple Selfish Attack Nodes Using Replica Allocation in Cognitive Radio Ad-Hoc Networks Kiruthiga S PG student, Coimbatore Institute of Engineering and Technology Anna University, Chennai,
Detecting Multiple Selfish Attack Nodes Using Replica Allocation in Cognitive Radio Ad-Hoc Networks Kiruthiga S PG student, Coimbatore Institute of Engineering and Technology Anna University, Chennai,
Algorithms for Interference Sensing in Optical CDMA Networks
 Algorithms for Interference Sensing in Optical CDMA Networks Purushotham Kamath, Joseph D. Touch and Joseph A. Bannister {pkamath, touch, joseph}@isi.edu Information Sciences Institute, University of Southern
Algorithms for Interference Sensing in Optical CDMA Networks Purushotham Kamath, Joseph D. Touch and Joseph A. Bannister {pkamath, touch, joseph}@isi.edu Information Sciences Institute, University of Southern
Attenuation (amplitude of the wave loses strength thereby the signal power) Refraction Reflection Shadowing Scattering Diffraction
 Wireless Physical Layer Q1. Is it possible to transmit a digital signal, e.g., coded as square wave as used inside a computer, using radio transmission without any loss? Why? It is not possible to transmit
Wireless Physical Layer Q1. Is it possible to transmit a digital signal, e.g., coded as square wave as used inside a computer, using radio transmission without any loss? Why? It is not possible to transmit
Wireless Home Networks based on a Hierarchical Bluetooth Scatternet Architecture
 Wireless Home Networks based on a Hierarchical Bluetooth Scatternet Architecture W. Lilakiatsakun'. 2, A. Seneviratne' I School of Electrical Engineering and Telecommunication University of New South Wales,
Wireless Home Networks based on a Hierarchical Bluetooth Scatternet Architecture W. Lilakiatsakun'. 2, A. Seneviratne' I School of Electrical Engineering and Telecommunication University of New South Wales,
Mobile network security report: Poland
 Mobile network security report: Poland GSM Map Project gsmmap@srlabs.de Security Research Labs, Berlin February 2015 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Poland GSM Map Project gsmmap@srlabs.de Security Research Labs, Berlin February 2015 Abstract. Mobile networks differ widely in their protection capabilities against common
Medium Access Control with Dynamic Frame Length in Wireless Sensor Networks
 Journal of Information Processing Systems, Vol.6, No.4, December 2010 DOI : 10.3745/JIPS.2010.6.4.501 Medium Access Control with Dynamic Frame Length in Wireless Sensor Networks Dae-Suk Yoo* and Seung
Journal of Information Processing Systems, Vol.6, No.4, December 2010 DOI : 10.3745/JIPS.2010.6.4.501 Medium Access Control with Dynamic Frame Length in Wireless Sensor Networks Dae-Suk Yoo* and Seung
Adaptive MAC Protocol for Emergency Data Transmission in Wireless Body Sensor Networks
 , pp. 205-216 http://dx.doi.org/10.14257/ijseia.2015.9.9.18 Adaptive MAC Protocol for Emergency Data Transmission in Wireless Body Sensor Networks Rae Hyun Kim and Jeong Gon Kim 1 Department of Electronic
, pp. 205-216 http://dx.doi.org/10.14257/ijseia.2015.9.9.18 Adaptive MAC Protocol for Emergency Data Transmission in Wireless Body Sensor Networks Rae Hyun Kim and Jeong Gon Kim 1 Department of Electronic
A Lightweight Secure SIP Model for End-to-End Communication
 A Lightweight Secure SIP Model for End-to-End Communication Weirong Jiang Research Institute of Information Technology, Tsinghua University, Beijing, 100084, P.R.China jwr2000@mails.tsinghua.edu.cn Abstract
A Lightweight Secure SIP Model for End-to-End Communication Weirong Jiang Research Institute of Information Technology, Tsinghua University, Beijing, 100084, P.R.China jwr2000@mails.tsinghua.edu.cn Abstract
Wireless Encryption Protection
 Wireless Encryption Protection We re going to jump around a little here and go to something that I really find interesting, how do you secure yourself when you connect to a router. Now first and foremost
Wireless Encryption Protection We re going to jump around a little here and go to something that I really find interesting, how do you secure yourself when you connect to a router. Now first and foremost
Security Scheme for Distributed DoS in Mobile Ad Hoc Networks
 Security Scheme for Distributed DoS in Mobile Ad Hoc Networks Sugata Sanyal 1, Ajith Abraham 2, Dhaval Gada 3, Rajat Gogri 3, Punit Rathod 3, Zalak Dedhia 3 and Nirali Mody 3 1 School of Technology and
Security Scheme for Distributed DoS in Mobile Ad Hoc Networks Sugata Sanyal 1, Ajith Abraham 2, Dhaval Gada 3, Rajat Gogri 3, Punit Rathod 3, Zalak Dedhia 3 and Nirali Mody 3 1 School of Technology and
Inter-Cell Interference Coordination (ICIC) Technology
 Inter-Cell Interference Coordination (ICIC) Technology Dai Kimura Hiroyuki Seki Long Term Evolution (LTE) is a promising standard for next-generation cellular systems targeted to have a peak downlink bit
Inter-Cell Interference Coordination (ICIC) Technology Dai Kimura Hiroyuki Seki Long Term Evolution (LTE) is a promising standard for next-generation cellular systems targeted to have a peak downlink bit
Single Sign-On Secure Authentication Password Mechanism
 Single Sign-On Secure Authentication Password Mechanism Deepali M. Devkate, N.D.Kale ME Student, Department of CE, PVPIT, Bavdhan, SavitribaiPhule University Pune, Maharashtra,India. Assistant Professor,
Single Sign-On Secure Authentication Password Mechanism Deepali M. Devkate, N.D.Kale ME Student, Department of CE, PVPIT, Bavdhan, SavitribaiPhule University Pune, Maharashtra,India. Assistant Professor,
Performance Evaluation of The Split Transmission in Multihop Wireless Networks
 Performance Evaluation of The Split Transmission in Multihop Wireless Networks Wanqing Tu and Vic Grout Centre for Applied Internet Research, School of Computing and Communications Technology, Glyndwr
Performance Evaluation of The Split Transmission in Multihop Wireless Networks Wanqing Tu and Vic Grout Centre for Applied Internet Research, School of Computing and Communications Technology, Glyndwr
Metrics for Detection of DDoS Attacks
 Chapter 3 Metrics for Detection of DDoS Attacks The DDoS attacks are trying to interfere with the physical transmission and reception of wireless communications. Attacks are caused by jamming, exhaustion,
Chapter 3 Metrics for Detection of DDoS Attacks The DDoS attacks are trying to interfere with the physical transmission and reception of wireless communications. Attacks are caused by jamming, exhaustion,
ssumathy@vit.ac.in upendra_mcs2@yahoo.com
 S. Sumathy 1 and B.Upendra Kumar 2 1 School of Computing Sciences, VIT University, Vellore-632 014, Tamilnadu, India ssumathy@vit.ac.in 2 School of Computing Sciences, VIT University, Vellore-632 014,
S. Sumathy 1 and B.Upendra Kumar 2 1 School of Computing Sciences, VIT University, Vellore-632 014, Tamilnadu, India ssumathy@vit.ac.in 2 School of Computing Sciences, VIT University, Vellore-632 014,
Network Monitoring in Multicast Networks Using Network Coding
 Network Monitoring in Multicast Networks Using Network Coding Tracey Ho Coordinated Science Laboratory University of Illinois Urbana, IL 6181 Email: trace@mit.edu Ben Leong, Yu-Han Chang, Yonggang Wen
Network Monitoring in Multicast Networks Using Network Coding Tracey Ho Coordinated Science Laboratory University of Illinois Urbana, IL 6181 Email: trace@mit.edu Ben Leong, Yu-Han Chang, Yonggang Wen
A Slow-sTart Exponential and Linear Algorithm for Energy Saving in Wireless Networks
 1 A Slow-sTart Exponential and Linear Algorithm for Energy Saving in Wireless Networks Yang Song, Bogdan Ciubotaru, Member, IEEE, and Gabriel-Miro Muntean, Member, IEEE Abstract Limited battery capacity
1 A Slow-sTart Exponential and Linear Algorithm for Energy Saving in Wireless Networks Yang Song, Bogdan Ciubotaru, Member, IEEE, and Gabriel-Miro Muntean, Member, IEEE Abstract Limited battery capacity
Problems of Security in Ad Hoc Sensor Network
 Problems of Security in Ad Hoc Sensor Network Petr Hanáček * hanacek@fit.vutbr.cz Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
Problems of Security in Ad Hoc Sensor Network Petr Hanáček * hanacek@fit.vutbr.cz Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
Further Analysis Of A Framework To Analyze Network Performance Based On Information Quality
 Further Analysis Of A Framework To Analyze Network Performance Based On Information Quality A Kazmierczak Computer Information Systems Northwest Arkansas Community College One College Dr. Bentonville,
Further Analysis Of A Framework To Analyze Network Performance Based On Information Quality A Kazmierczak Computer Information Systems Northwest Arkansas Community College One College Dr. Bentonville,
Capture Resilient ElGamal Signature Protocols
 Capture Resilient ElGamal Signature Protocols Hüseyin Acan 1, Kamer Kaya 2,, and Ali Aydın Selçuk 2 1 Bilkent University, Department of Mathematics acan@fen.bilkent.edu.tr 2 Bilkent University, Department
Capture Resilient ElGamal Signature Protocols Hüseyin Acan 1, Kamer Kaya 2,, and Ali Aydın Selçuk 2 1 Bilkent University, Department of Mathematics acan@fen.bilkent.edu.tr 2 Bilkent University, Department
Wireless Sensor Network: Challenges, Issues and Research
 ISBN 978-93-84468-20-0 Proceedings of 2015 International Conference on Future Computational Technologies (ICFCT'2015) Singapore, March 29-30, 2015, pp. 224-228 Wireless Sensor Network: Challenges, Issues
ISBN 978-93-84468-20-0 Proceedings of 2015 International Conference on Future Computational Technologies (ICFCT'2015) Singapore, March 29-30, 2015, pp. 224-228 Wireless Sensor Network: Challenges, Issues
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY
 INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK AN OVERVIEW OF MOBILE ADHOC NETWORK: INTRUSION DETECTION, TYPES OF ATTACKS AND
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK AN OVERVIEW OF MOBILE ADHOC NETWORK: INTRUSION DETECTION, TYPES OF ATTACKS AND
LOAD BALANCING AND EFFICIENT CLUSTERING FOR IMPROVING NETWORK PERFORMANCE IN AD-HOC NETWORKS
 LOAD BALANCING AND EFFICIENT CLUSTERING FOR IMPROVING NETWORK PERFORMANCE IN AD-HOC NETWORKS Saranya.S 1, Menakambal.S 2 1 M.E., Embedded System Technologies, Nandha Engineering College (Autonomous), (India)
LOAD BALANCING AND EFFICIENT CLUSTERING FOR IMPROVING NETWORK PERFORMANCE IN AD-HOC NETWORKS Saranya.S 1, Menakambal.S 2 1 M.E., Embedded System Technologies, Nandha Engineering College (Autonomous), (India)
SIMULATION STUDY OF BLACKHOLE ATTACK IN THE MOBILE AD HOC NETWORKS
 Journal of Engineering Science and Technology Vol. 4, No. 2 (2009) 243-250 School of Engineering, Taylor s University College SIMULATION STUDY OF BLACKHOLE ATTACK IN THE MOBILE AD HOC NETWORKS SHEENU SHARMA
Journal of Engineering Science and Technology Vol. 4, No. 2 (2009) 243-250 School of Engineering, Taylor s University College SIMULATION STUDY OF BLACKHOLE ATTACK IN THE MOBILE AD HOC NETWORKS SHEENU SHARMA
Performance Evaluation of Mobile Wi-Fi-based M2M Data Traffic Multiplexing
 Performance Evaluation of Mobile Wi-Fi-based M2M Data Traffic Multiplexing Muhammad Tariq Afridi 1, Safdar Nawaz Khan Marwat 1, Yasir Mehmood 2, Jebran Khan 1, Carmelita Görg 2 1 Department of Computer
Performance Evaluation of Mobile Wi-Fi-based M2M Data Traffic Multiplexing Muhammad Tariq Afridi 1, Safdar Nawaz Khan Marwat 1, Yasir Mehmood 2, Jebran Khan 1, Carmelita Görg 2 1 Department of Computer
SOFTWARE FOR GENERATION OF SPECTRUM COMPATIBLE TIME HISTORY
 3 th World Conference on Earthquake Engineering Vancouver, B.C., Canada August -6, 24 Paper No. 296 SOFTWARE FOR GENERATION OF SPECTRUM COMPATIBLE TIME HISTORY ASHOK KUMAR SUMMARY One of the important
3 th World Conference on Earthquake Engineering Vancouver, B.C., Canada August -6, 24 Paper No. 296 SOFTWARE FOR GENERATION OF SPECTRUM COMPATIBLE TIME HISTORY ASHOK KUMAR SUMMARY One of the important
SECURE DATA TRANSMISSION USING INDISCRIMINATE DATA PATHS FOR STAGNANT DESTINATION IN MANET
 SECURE DATA TRANSMISSION USING INDISCRIMINATE DATA PATHS FOR STAGNANT DESTINATION IN MANET MR. ARVIND P. PANDE 1, PROF. UTTAM A. PATIL 2, PROF. B.S PATIL 3 Dept. Of Electronics Textile and Engineering
SECURE DATA TRANSMISSION USING INDISCRIMINATE DATA PATHS FOR STAGNANT DESTINATION IN MANET MR. ARVIND P. PANDE 1, PROF. UTTAM A. PATIL 2, PROF. B.S PATIL 3 Dept. Of Electronics Textile and Engineering
A Power Efficient QoS Provisioning Architecture for Wireless Ad Hoc Networks
 A Power Efficient QoS Provisioning Architecture for Wireless Ad Hoc Networks Didem Gozupek 1,Symeon Papavassiliou 2, Nirwan Ansari 1, and Jie Yang 1 1 Department of Electrical and Computer Engineering
A Power Efficient QoS Provisioning Architecture for Wireless Ad Hoc Networks Didem Gozupek 1,Symeon Papavassiliou 2, Nirwan Ansari 1, and Jie Yang 1 1 Department of Electrical and Computer Engineering
SECURITY RISK ANALYSIS AND EVALUATION OF INTEGRATING CUSTOMER ENERGY MANAGEMENT SYSTEMS INTO SMART DISTRIBUTION GRIDS
 SECURITY RISK ANALYSIS AND EVALUATION OF INTEGRATING CUSTOMER ENERGY MANAGEMENT SYSTEMS INTO SMART DISTRIBUTION GRIDS Christian HÄGERLING Fabian M. KURTZ Christian WIETFELD TU Dortmund University Germany
SECURITY RISK ANALYSIS AND EVALUATION OF INTEGRATING CUSTOMER ENERGY MANAGEMENT SYSTEMS INTO SMART DISTRIBUTION GRIDS Christian HÄGERLING Fabian M. KURTZ Christian WIETFELD TU Dortmund University Germany
An Efficient Hybrid Data Gathering Scheme in Wireless Sensor Networks
 An Efficient Hybrid Data Gathering Scheme in Wireless Sensor Networks Ayon Chakraborty 1, Swarup Kumar Mitra 2, and M.K. Naskar 3 1 Department of CSE, Jadavpur University, Kolkata, India 2 Department of
An Efficient Hybrid Data Gathering Scheme in Wireless Sensor Networks Ayon Chakraborty 1, Swarup Kumar Mitra 2, and M.K. Naskar 3 1 Department of CSE, Jadavpur University, Kolkata, India 2 Department of
SECURE AND RELIABLE DATA TRANSMISSION IN WIRELESS SENSOR NETWORKS
 SECURE AND RELIABLE DATA TRANSMISSION IN WIRELESS SENSOR NETWORKS Kokilavani.V Mother Teresa College Of Engineering And Technology,Pudhukottai Abstract Network security involves the authorization of access
SECURE AND RELIABLE DATA TRANSMISSION IN WIRELESS SENSOR NETWORKS Kokilavani.V Mother Teresa College Of Engineering And Technology,Pudhukottai Abstract Network security involves the authorization of access
Reliability Trade-off Analysis of Deadline-Sensitive Wireless Messaging Systems
 Reliability Trade-off Analysis of Deadline-Sensitive Wireless Messaging Systems Debessay Fesehaye, Shameem Ahmed,Thadpong Pongthawornkamol, Klara Nahrstedt and Guijun Wang Dept. of Computer Science, University
Reliability Trade-off Analysis of Deadline-Sensitive Wireless Messaging Systems Debessay Fesehaye, Shameem Ahmed,Thadpong Pongthawornkamol, Klara Nahrstedt and Guijun Wang Dept. of Computer Science, University
Packet Queueing Delay in Wireless Networks with Multiple Base Stations and Cellular Frequency Reuse
 Packet Queueing Delay in Wireless Networks with Multiple Base Stations and Cellular Frequency Reuse Abstract - Cellular frequency reuse is known to be an efficient method to allow many wireless telephone
Packet Queueing Delay in Wireless Networks with Multiple Base Stations and Cellular Frequency Reuse Abstract - Cellular frequency reuse is known to be an efficient method to allow many wireless telephone
DeuceScan: Deuce-Based Fast Handoff Scheme in IEEE 802.11 Wireless Networks
 : Deuce-Based Fast Handoff Scheme in IEEE 82.11 Wireless Networks Yuh-Shyan Chen, Chung-Kai Chen, and Ming-Chin Chuang Department of Computer Science and Information Engineering National Chung Cheng University,
: Deuce-Based Fast Handoff Scheme in IEEE 82.11 Wireless Networks Yuh-Shyan Chen, Chung-Kai Chen, and Ming-Chin Chuang Department of Computer Science and Information Engineering National Chung Cheng University,
DAG based In-Network Aggregation for Sensor Network Monitoring
 DAG based In-Network Aggregation for Sensor Network Monitoring Shinji Motegi, Kiyohito Yoshihara and Hiroki Horiuchi KDDI R&D Laboratories Inc. {motegi, yosshy, hr-horiuchi}@kddilabs.jp Abstract Wireless
DAG based In-Network Aggregation for Sensor Network Monitoring Shinji Motegi, Kiyohito Yoshihara and Hiroki Horiuchi KDDI R&D Laboratories Inc. {motegi, yosshy, hr-horiuchi}@kddilabs.jp Abstract Wireless
AS MORE WIRELESS and sensor networks are deployed,
 2418 IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 59, NO. 5, JUNE 2010 Detecting and Localizing Identity-Based Attacks in Wireless and Sensor Networks Yingying Chen, Member, IEEE, Jie Yang, Student
2418 IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 59, NO. 5, JUNE 2010 Detecting and Localizing Identity-Based Attacks in Wireless and Sensor Networks Yingying Chen, Member, IEEE, Jie Yang, Student
CHAPTER 1 INTRODUCTION
 21 CHAPTER 1 INTRODUCTION 1.1 PREAMBLE Wireless ad-hoc network is an autonomous system of wireless nodes connected by wireless links. Wireless ad-hoc network provides a communication over the shared wireless
21 CHAPTER 1 INTRODUCTION 1.1 PREAMBLE Wireless ad-hoc network is an autonomous system of wireless nodes connected by wireless links. Wireless ad-hoc network provides a communication over the shared wireless
AN EFFICIENT STRATEGY OF AGGREGATE SECURE DATA TRANSMISSION
 INTERNATIONAL JOURNAL OF REVIEWS ON RECENT ELECTRONICS AND COMPUTER SCIENCE AN EFFICIENT STRATEGY OF AGGREGATE SECURE DATA TRANSMISSION K.Anusha 1, K.Sudha 2 1 M.Tech Student, Dept of CSE, Aurora's Technological
INTERNATIONAL JOURNAL OF REVIEWS ON RECENT ELECTRONICS AND COMPUTER SCIENCE AN EFFICIENT STRATEGY OF AGGREGATE SECURE DATA TRANSMISSION K.Anusha 1, K.Sudha 2 1 M.Tech Student, Dept of CSE, Aurora's Technological
Whitepaper. 802.11n The Next Generation in Wireless Technology
 Whitepaper 802.11n The Next Generation in Wireless Technology Introduction Wireless technology continues to evolve and add value with its inherent characteristics. First came 802.11, then a & b, followed
Whitepaper 802.11n The Next Generation in Wireless Technology Introduction Wireless technology continues to evolve and add value with its inherent characteristics. First came 802.11, then a & b, followed
Analysis and Enhancement of QoS in Cognitive Radio Network for Efficient VoIP Performance
 Analysis and Enhancement of QoS in Cognitive Radio Network for Efficient VoIP Performance Tamal Chakraborty 1, Atri Mukhopadhyay 2 1 Dept. of Electronics and Telecommunication Engineering 2 School of Mobile
Analysis and Enhancement of QoS in Cognitive Radio Network for Efficient VoIP Performance Tamal Chakraborty 1, Atri Mukhopadhyay 2 1 Dept. of Electronics and Telecommunication Engineering 2 School of Mobile
Course Curriculum for Master Degree in Electrical Engineering/Wireless Communications
 Course Curriculum for Master Degree in Electrical Engineering/Wireless Communications The Master Degree in Electrical Engineering/Wireless Communications, is awarded by the Faculty of Graduate Studies
Course Curriculum for Master Degree in Electrical Engineering/Wireless Communications The Master Degree in Electrical Engineering/Wireless Communications, is awarded by the Faculty of Graduate Studies
Energy Optimal Routing Protocol for a Wireless Data Network
 Energy Optimal Routing Protocol for a Wireless Data Network Easwar Vivek Colloborator(s): Venkatesh Ramaiyan, Srikrishna Bhashyam Department of Electrical Engineering, Indian Institute of Technology, Madras.
Energy Optimal Routing Protocol for a Wireless Data Network Easwar Vivek Colloborator(s): Venkatesh Ramaiyan, Srikrishna Bhashyam Department of Electrical Engineering, Indian Institute of Technology, Madras.
QoSIP: A QoS Aware IP Routing Protocol for Multimedia Data
 QoSIP: A QoS Aware IP Routing Protocol for Multimedia Data Md. Golam Shagadul Amin Talukder and Al-Mukaddim Khan Pathan* Department of Computer Science and Engineering, Metropolitan University, Sylhet,
QoSIP: A QoS Aware IP Routing Protocol for Multimedia Data Md. Golam Shagadul Amin Talukder and Al-Mukaddim Khan Pathan* Department of Computer Science and Engineering, Metropolitan University, Sylhet,
IN THIS PAPER, we study the delay and capacity trade-offs
 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 15, NO. 5, OCTOBER 2007 981 Delay and Capacity Trade-Offs in Mobile Ad Hoc Networks: A Global Perspective Gaurav Sharma, Ravi Mazumdar, Fellow, IEEE, and Ness
IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 15, NO. 5, OCTOBER 2007 981 Delay and Capacity Trade-Offs in Mobile Ad Hoc Networks: A Global Perspective Gaurav Sharma, Ravi Mazumdar, Fellow, IEEE, and Ness
Assessing trade-offs between energy consumption and security in sensor networks: simulations or testbeds?
 Assessing trade-offs between energy consumption and security in sensor networks: simulations or testbeds? F. Maraninchi 1, Grenoble INP/Ensimag, VERIMAG mainly summarizing discussions with: Laurent Mounier,
Assessing trade-offs between energy consumption and security in sensor networks: simulations or testbeds? F. Maraninchi 1, Grenoble INP/Ensimag, VERIMAG mainly summarizing discussions with: Laurent Mounier,
Efficient Data Transmission For Wireless Sensor Networks
 Volume: 2, Issue: 4, 221-225 April 2015 www.allsubjectjournal.com e-issn: 2349-4182 p-issn: 2349-5979 Impact Factor: 3.762 Girijalaxmi M.Tech scholar, Department of computer Vasudev S Senior assistant
Volume: 2, Issue: 4, 221-225 April 2015 www.allsubjectjournal.com e-issn: 2349-4182 p-issn: 2349-5979 Impact Factor: 3.762 Girijalaxmi M.Tech scholar, Department of computer Vasudev S Senior assistant
Rapid Prototyping of a Frequency Hopping Ad Hoc Network System
 Rapid Prototyping of a Frequency Hopping Ad Hoc Network System Martin Braun, Nico Otterbach, Jens Elsner, and Friedrich K. Jondral Communications Engineering Lab, Karlsruhe Institute of Technology (KIT),
Rapid Prototyping of a Frequency Hopping Ad Hoc Network System Martin Braun, Nico Otterbach, Jens Elsner, and Friedrich K. Jondral Communications Engineering Lab, Karlsruhe Institute of Technology (KIT),
Internet Sustainability and Network Marketing Safety
 Protecting Neighbor Discovery Against Node Compromises in Sensor Networks Donggang Liu isec Laboratory, CSE Department The University of Texas at Arlington Abstract The neighborhood information has been
Protecting Neighbor Discovery Against Node Compromises in Sensor Networks Donggang Liu isec Laboratory, CSE Department The University of Texas at Arlington Abstract The neighborhood information has been
A Security Architecture for. Wireless Sensor Networks Environmental
 Contemporary Engineering Sciences, Vol. 7, 2014, no. 15, 737-742 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/10.12988/ces.2014.4683 A Security Architecture for Wireless Sensor Networks Environmental
Contemporary Engineering Sciences, Vol. 7, 2014, no. 15, 737-742 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/10.12988/ces.2014.4683 A Security Architecture for Wireless Sensor Networks Environmental
Body Area Network Security: Robust Secret Sharing
 Body Area Network Security: Robust Secret Sharing Sang-Yoon Chang, Yih-Chun Hu, Hans Anderson, Ting Fu, Evelyn Huang University of Illinois Body Area Network Background Body area network (BAN) consists
Body Area Network Security: Robust Secret Sharing Sang-Yoon Chang, Yih-Chun Hu, Hans Anderson, Ting Fu, Evelyn Huang University of Illinois Body Area Network Background Body area network (BAN) consists
Voice Service Support over Cognitive Radio Networks
 Voice Service Support over Cognitive Radio Networks Ping Wang, Dusit Niyato, and Hai Jiang Centre For Multimedia And Network Technology (CeMNeT), School of Computer Engineering, Nanyang Technological University,
Voice Service Support over Cognitive Radio Networks Ping Wang, Dusit Niyato, and Hai Jiang Centre For Multimedia And Network Technology (CeMNeT), School of Computer Engineering, Nanyang Technological University,
A Novel Packet Marketing Method in DDoS Attack Detection
 SCI-PUBLICATIONS Author Manuscript American Journal of Applied Sciences 4 (10): 741-745, 2007 ISSN 1546-9239 2007 Science Publications A Novel Packet Marketing Method in DDoS Attack Detection 1 Changhyun
SCI-PUBLICATIONS Author Manuscript American Journal of Applied Sciences 4 (10): 741-745, 2007 ISSN 1546-9239 2007 Science Publications A Novel Packet Marketing Method in DDoS Attack Detection 1 Changhyun
SINGLE SIGN-ON MECHANISM FOR DISTRIBUTED COMPUTING SECURITY ENVIRONMENT
 SINGLE SIGN-ON MECHANISM FOR DISTRIBUTED COMPUTING SECURITY ENVIRONMENT K.karthika 1, M. Daya kanimozhi Rani 2 1 K.karthika, Assistant professor, Department of IT, Adhiyamaan College of Engineering, Hosur
SINGLE SIGN-ON MECHANISM FOR DISTRIBUTED COMPUTING SECURITY ENVIRONMENT K.karthika 1, M. Daya kanimozhi Rani 2 1 K.karthika, Assistant professor, Department of IT, Adhiyamaan College of Engineering, Hosur
Performance Evaluation of AODV, OLSR Routing Protocol in VOIP Over Ad Hoc
 (International Journal of Computer Science & Management Studies) Vol. 17, Issue 01 Performance Evaluation of AODV, OLSR Routing Protocol in VOIP Over Ad Hoc Dr. Khalid Hamid Bilal Khartoum, Sudan dr.khalidbilal@hotmail.com
(International Journal of Computer Science & Management Studies) Vol. 17, Issue 01 Performance Evaluation of AODV, OLSR Routing Protocol in VOIP Over Ad Hoc Dr. Khalid Hamid Bilal Khartoum, Sudan dr.khalidbilal@hotmail.com
OPTIMIZED SENSOR NODES BY FAULT NODE RECOVERY ALGORITHM
 OPTIMIZED SENSOR NODES BY FAULT NODE RECOVERY ALGORITHM S. Sofia 1, M.Varghese 2 1 Student, Department of CSE, IJCET 2 Professor, Department of CSE, IJCET Abstract This paper proposes fault node recovery
OPTIMIZED SENSOR NODES BY FAULT NODE RECOVERY ALGORITHM S. Sofia 1, M.Varghese 2 1 Student, Department of CSE, IJCET 2 Professor, Department of CSE, IJCET Abstract This paper proposes fault node recovery
Alternative Biometric as Method of Information Security of Healthcare Systems
 Alternative Biometric as Method of Information Security of Healthcare Systems Ekaterina Andreeva Saint-Petersburg State University of Aerospace Instrumentation Saint-Petersburg, Russia eandreeva89@gmail.com
Alternative Biometric as Method of Information Security of Healthcare Systems Ekaterina Andreeva Saint-Petersburg State University of Aerospace Instrumentation Saint-Petersburg, Russia eandreeva89@gmail.com
Performance Evaluation of VANETs with Multiple Car Crashes in Different Traffic Conditions
 Performance Evaluation of VANETs with Multiple Car Crashes in Different Traffic Conditions Georgios Charalampopoulos 1,2 and Tasos Dagiuklas 1 1. Dept. of Computer Science, Hellenic Open University, Greece,
Performance Evaluation of VANETs with Multiple Car Crashes in Different Traffic Conditions Georgios Charalampopoulos 1,2 and Tasos Dagiuklas 1 1. Dept. of Computer Science, Hellenic Open University, Greece,
Vampire Attack Detecting and Preventing in Wireless Sensor Network
 International Journal of Emerging Engineering Research and Technology Volume 2, Issue 4, July 2014, PP 306-310 ISSN 2349-4395 (Print) & ISSN 2349-4409 (Online) Vampire Attack Detecting and Preventing in
International Journal of Emerging Engineering Research and Technology Volume 2, Issue 4, July 2014, PP 306-310 ISSN 2349-4395 (Print) & ISSN 2349-4409 (Online) Vampire Attack Detecting and Preventing in
International Journal of Computer Sciences and Engineering. Research Paper Volume-4, Issue-4 E-ISSN: 2347-2693
 International Journal of Computer Sciences and Engineering Open Access Research Paper Volume-4, Issue-4 E-ISSN: 2347-2693 PAPR Reduction Method for the Localized and Distributed DFTS-OFDM System Using
International Journal of Computer Sciences and Engineering Open Access Research Paper Volume-4, Issue-4 E-ISSN: 2347-2693 PAPR Reduction Method for the Localized and Distributed DFTS-OFDM System Using
EFFICIENT DETECTION IN DDOS ATTACK FOR TOPOLOGY GRAPH DEPENDENT PERFORMANCE IN PPM LARGE SCALE IPTRACEBACK
 EFFICIENT DETECTION IN DDOS ATTACK FOR TOPOLOGY GRAPH DEPENDENT PERFORMANCE IN PPM LARGE SCALE IPTRACEBACK S.Abarna 1, R.Padmapriya 2 1 Mphil Scholar, 2 Assistant Professor, Department of Computer Science,
EFFICIENT DETECTION IN DDOS ATTACK FOR TOPOLOGY GRAPH DEPENDENT PERFORMANCE IN PPM LARGE SCALE IPTRACEBACK S.Abarna 1, R.Padmapriya 2 1 Mphil Scholar, 2 Assistant Professor, Department of Computer Science,
Privacy Vulnerabilities in Encrypted HTTP Streams
 University of Massachusetts - Amherst ScholarWorks@UMass Amherst Computer Science Department Faculty Publication Series Computer Science 2005 Privacy Vulnerabilities in Encrypted HTTP Streams George Dean
University of Massachusetts - Amherst ScholarWorks@UMass Amherst Computer Science Department Faculty Publication Series Computer Science 2005 Privacy Vulnerabilities in Encrypted HTTP Streams George Dean
Network Security. Chapter 9 Integrating Security Services into Communication Architectures
 Network Security Chapter 9 Integrating Security Services into Communication Architectures Network Security (WS 00): 09 Integration of Security Services Motivation: What to do where?! Analogous to the methodology
Network Security Chapter 9 Integrating Security Services into Communication Architectures Network Security (WS 00): 09 Integration of Security Services Motivation: What to do where?! Analogous to the methodology
Secure Anonymous Routing in Clustered Multihop Wireless Ad Hoc Networks
 Secure Anonymous Routing in Clustered Multihop Wireless Ad Hoc Networks Lijun Qian and Ning Song Department of Electrical Engineering Prairie View A&M University Prairie View, Texas 77446 Email: LiQian,
Secure Anonymous Routing in Clustered Multihop Wireless Ad Hoc Networks Lijun Qian and Ning Song Department of Electrical Engineering Prairie View A&M University Prairie View, Texas 77446 Email: LiQian,
Expert Reference Series of White Papers. Wireless Bandwidth Not Necessarily as Advertised 1-800-COURSES. www.globalknowledge.com
 Expert Reference Series of White Papers Wireless Bandwidth Not Necessarily as Advertised 1-800-COURSES www.globalknowledge.com Wireless Bandwidth Not Necessarily as Advertised Ted Rohling, Global Knowledge
Expert Reference Series of White Papers Wireless Bandwidth Not Necessarily as Advertised 1-800-COURSES www.globalknowledge.com Wireless Bandwidth Not Necessarily as Advertised Ted Rohling, Global Knowledge
MONITORING OF TRAFFIC OVER THE VICTIM UNDER TCP SYN FLOOD IN A LAN
 MONITORING OF TRAFFIC OVER THE VICTIM UNDER TCP SYN FLOOD IN A LAN Kanika 1, Renuka Goyal 2, Gurmeet Kaur 3 1 M.Tech Scholar, Computer Science and Technology, Central University of Punjab, Punjab, India
MONITORING OF TRAFFIC OVER THE VICTIM UNDER TCP SYN FLOOD IN A LAN Kanika 1, Renuka Goyal 2, Gurmeet Kaur 3 1 M.Tech Scholar, Computer Science and Technology, Central University of Punjab, Punjab, India
Preventing DDOS attack in Mobile Ad-hoc Network using a Secure Intrusion Detection System
 Preventing DDOS attack in Mobile Ad-hoc Network using a Secure Intrusion Detection System Shams Fathima M.Tech,Department of Computer Science Kakatiya Institute of Technology & Science, Warangal,India
Preventing DDOS attack in Mobile Ad-hoc Network using a Secure Intrusion Detection System Shams Fathima M.Tech,Department of Computer Science Kakatiya Institute of Technology & Science, Warangal,India
A Review on Zero Day Attack Safety Using Different Scenarios
 Available online www.ejaet.com European Journal of Advances in Engineering and Technology, 2015, 2(1): 30-34 Review Article ISSN: 2394-658X A Review on Zero Day Attack Safety Using Different Scenarios
Available online www.ejaet.com European Journal of Advances in Engineering and Technology, 2015, 2(1): 30-34 Review Article ISSN: 2394-658X A Review on Zero Day Attack Safety Using Different Scenarios
Security Solutions for Wireless Sensor Networks
 Dirk WESTHOFF, Joao GIRAO, Amardeo SARMA Abstract This paper describes security solutions for collecting and processing data in Wireless Sensor Networks (WSNs). Adequate security capabilities for medium
Dirk WESTHOFF, Joao GIRAO, Amardeo SARMA Abstract This paper describes security solutions for collecting and processing data in Wireless Sensor Networks (WSNs). Adequate security capabilities for medium
