A RESTful Web Service for Whois. Andy Newton Chief Engineer, ARIN
|
|
|
- Anabel Thompson
- 10 years ago
- Views:
Transcription
1 A RESTful Web Service for Whois Andy Newton Chief Engineer, ARIN
2 My Background on Whois Prototyped an LDAP alternative to Whois (RFC 3663) Principal author of CRISP (IRIS) documents RFC 3707, RFC 3981, RFC 3983, RFC 4698, RFC 4991, RFC 4992, RFC 4993, RFC 5144 Worked with principal authors of Rwhois and Whois++ at VeriSign Most recently driver behind ARIN s Whois RESTful Web Service Slide 2
3 Basics of All Protocols Control Framing, Security, etc Data What Users See Slide 3
4 LDAP The Control part heavily dictates the Data part. Slide 4
5 IRIS The Control part is specific to the Data part. Slide 5
6 WHOIS/NICNAME The Control part specifies nothing about the Data part. Slide 6
7 RESTful Web Services The Control part enables richness in the Data part. Slide 7
8 Why a RESTful Web Service? I18N support referrals security see (RFC 3707) Leads to the following conclusion Slide 8
9 We Need to go beyond Port 43 The Control part specifies nothing about the Data part. Slide 9
10 Non-Port 43 Solutions Rwhois Problem specific technology Only used by a subset of the ARIN community Whois++ Focuses on distributed indexes LDAP Widely used in Intranets, not the Internet IRIS Requirements by lawyers, design by committee RESTful Web Services (RWS) Simple reuse of web technologies Slide 10
11 What is REST? Representation State Transfer As applied to web services defines a pattern of usage with HTTP to create, read, update, and delete (CRUD) data Resources are addressable in URLs Very popular protocol model Amazon S3, Yahoo & Google services, Slide 11
12 How is this Useful to WHOIS? POC, ORG, NET, ASN resources have URLs that you can cut & paste Gives a very simple programmatic API into WHOIS data Compared to NICNAME TCP/43: Better inputs and queries More meaningful array of outputs Uses HTTP infrastructure (e.g. caches) Slide 12
13 Where can more information on REST be found? RESTful Web Services O Reilly Media Leonard Richardson Sam Ruby
14 Applicability to ICANN Whois This is a framework useful to ICANN/ Registries/Registrars Not an out-of-the-box solution Somebody has to decide how it is used But Well within the mainstream of modern Internet communications (i.e. not hard to find programmers who understand it) As the RIRs are showing, it is easy to apply to the Internet Infrastructure space Slide 14
15 Status of Services ARIN Full Production as of July 2010 Our RESTful provisioning service goes operational in a few days RIPE NCC Announced their RESTful proxy to Whois March 2010 Now in production APNIC Has been using RESTful services internally for years Slide 15
16 The BIG Advantage of REST Easily understood Any modern programmer can incorporate it Can look like web pages Re-uses HTTP in a simple manner Many, many clients Other HTTP advantages This is why it is very, very popular with Google, Amazon, Yahoo, Twitter, Facebook, YouTube, Flickr, Slide 16
17 What does it look like? Where the data is. What type of data it is. The ID of the data. It is a standard URL. Go ahead, put it into your browser. Slide 17
18 Addressable URLs Mark Kosters ARIN (the organization) ARIN s autonomous systems numbers ARIN s POCs ARIN-HOSTMASTER s networks Slide 18
19 Searches Same capabilities as port 43, but they can be refined Organizations by name Organizations starting with ARIN Mark Kosters by first and last name Slide 19
20 Outputs XML Computers can easily digest XML With stylesheets, you can transform XML to pretty, user-friendly web pages JSON (your choice here) Slide 20
21 Machine Readable & Pretty Slide 21
22 Clients are Ubiquitous One of the problems with a non-port 43 solution is Who will write the client software? With RWS, your web browser is a client. Command line clients: Curl, wget, xmllint, etc Embedded clients: Libcurl, libraries for Perl, PHP, Java, etc Slide 22
23 Slide 23
24 The Future Enabled: Caching Addressable URLs make HTTP caching work with WHOIS data Useful for automated security analysis For ARIN, 99% of WHOIS queries are IP address lookups Slide 24
25 The Future Enabled: Referrals NetName: ARIN-2610 NetHandle: NET NetType: Allocated to Big Network Provider RegDate: Updated: CIDR: 2620::/23 Ref: HolderRef: Not just for Orgs Nets POCs Etc NetHandle: NET NetType: Allocated to Customer CIDR: 2620::/23 Comment: Problems? Commnet: Contact our NOC Slide 25
26 The Future Enabled: Auth* Authentication allows tiered Authorization Policies no longer need to assume all or nothing Slide 26
27 The Future Enabled: Versioning With standard HTTP headers, we can version our output Changes the data model with as little disruption as possible GET /rest/poc/dude1-arin HTTP/1.0 Accept: application/arin.whoisrws-v1+xml You always get the latest if you don t specify Slide 27
28 What Would It Take? Just saying do RWS is not enough. A standard is needed Define the proper URL patterns Define extensible output DREG could be used as a starting point Make it more flexible Switch to RelaxNG or other schema language Define pattern for referrals HTTP referrals and/or embedded links Slide 28
29 REST is Easy Re-use the web technologies Define patterns Use definitions you already have Done! Slide 29
30 What We Set Out To Do ARIN s problem wasn t with Whois. We needed a fundamental change in our data model to accommodate better zone delegation management and DNSSEC in the reverse DNS. Our legacy Whois would need to be completely rewritten. So we felt if it had to be completely rewritten, then we should do more than a simple rewrite. Slide 30
31 Technical Approach We wanted to reuse our new web infrastructure Original RWS technology demonstrator took me a couple of weeks to implement as a side project Our Port 43 server would be a proxy into the RWS Port 43 Proxy Server RESTful Web Server Database Slide 31
32 Level of Effort Once greenlighted Single senior developer for a couple of months Then a small team for a couple of months But we had non-protocol problems to solve as well Added in a new near-realtime replication system Developed geometric search system to add CIDR search capabilities Non-trivial amount of time was spent trying to make Port 43 service as backward compatible as possible Slide 32
33 Adoption Before we even got to production Several people started using the public pilot to reconcile their records with ours programmatically Somebody wrote a Flash application against our service After release Hard to tell what real adoption of RWS is because right after release our query rates skyrocketed We added a psuedo-resource called PFT to help web browser users Our previous stats indicated little use of port 80 Whois Demand now for a RESTful provisioning interface to be released real soon now Slide 33
34 Conclusion ARIN s Whois-RWS: Technical questions for all our services can be directed to [email protected]. Q&A Slide 34
Distributed Systems. 09. Naming. Paul Krzyzanowski. Rutgers University. Fall 2015
 Distributed Systems 09. Naming Paul Krzyzanowski Rutgers University Fall 2015 October 7, 2015 2014-2015 Paul Krzyzanowski 1 Naming things Naming: map names to objects Helps with using, sharing, and communicating
Distributed Systems 09. Naming Paul Krzyzanowski Rutgers University Fall 2015 October 7, 2015 2014-2015 Paul Krzyzanowski 1 Naming things Naming: map names to objects Helps with using, sharing, and communicating
Internet Operations and the RIRs
 Internet Operations and the RIRs Overview ARIN and the Regional Internet Registry (RIR) System IP Number Resources, DNS and Routing IP Address Management Whois ARIN and the RIR System About ARIN One of
Internet Operations and the RIRs Overview ARIN and the Regional Internet Registry (RIR) System IP Number Resources, DNS and Routing IP Address Management Whois ARIN and the RIR System About ARIN One of
Beyond The Web Drupal Meets The Desktop (And Mobile) Justin Miller Code Sorcery Workshop, LLC http://codesorcery.net/dcdc
 Beyond The Web Drupal Meets The Desktop (And Mobile) Justin Miller Code Sorcery Workshop, LLC http://codesorcery.net/dcdc Introduction Personal introduction Format & conventions for this talk Assume familiarity
Beyond The Web Drupal Meets The Desktop (And Mobile) Justin Miller Code Sorcery Workshop, LLC http://codesorcery.net/dcdc Introduction Personal introduction Format & conventions for this talk Assume familiarity
XML Processing and Web Services. Chapter 17
 XML Processing and Web Services Chapter 17 Textbook to be published by Pearson Ed 2015 in early Pearson 2014 Fundamentals of http://www.funwebdev.com Web Development Objectives 1 XML Overview 2 XML Processing
XML Processing and Web Services Chapter 17 Textbook to be published by Pearson Ed 2015 in early Pearson 2014 Fundamentals of http://www.funwebdev.com Web Development Objectives 1 XML Overview 2 XML Processing
The IANA Functions. An Introduction to the Internet Assigned Numbers Authority (IANA) Functions
 The IANA Functions An Introduction to the Internet Assigned Numbers Authority (IANA) Functions Contents SECTION 1: INTRODUCTION 4 SECTION 2: POLICY, STAKEHOLDERS AND STEWARDSHIP IMPLEMENTATION 6 SECTION
The IANA Functions An Introduction to the Internet Assigned Numbers Authority (IANA) Functions Contents SECTION 1: INTRODUCTION 4 SECTION 2: POLICY, STAKEHOLDERS AND STEWARDSHIP IMPLEMENTATION 6 SECTION
Computer Networks. Lecture 7: Application layer: FTP and HTTP. Marcin Bieńkowski. Institute of Computer Science University of Wrocław
 Computer Networks Lecture 7: Application layer: FTP and Marcin Bieńkowski Institute of Computer Science University of Wrocław Computer networks (II UWr) Lecture 7 1 / 23 Reminder: Internet reference model
Computer Networks Lecture 7: Application layer: FTP and Marcin Bieńkowski Institute of Computer Science University of Wrocław Computer networks (II UWr) Lecture 7 1 / 23 Reminder: Internet reference model
ITP 140 Mobile Technologies. Mobile Topics
 ITP 140 Mobile Technologies Mobile Topics Topics Analytics APIs RESTful Facebook Twitter Google Cloud Web Hosting 2 Reach We need users! The number of users who try our apps Retention The number of users
ITP 140 Mobile Technologies Mobile Topics Topics Analytics APIs RESTful Facebook Twitter Google Cloud Web Hosting 2 Reach We need users! The number of users who try our apps Retention The number of users
How Comcast Built An Open Source Content Delivery Network National Engineering & Technical Operations
 How Comcast Built An Open Source Content Delivery Network National Engineering & Technical Operations Jan van Doorn Distinguished Engineer VSS CDN Engineering 1 What is a CDN? 2 Content Router get customer
How Comcast Built An Open Source Content Delivery Network National Engineering & Technical Operations Jan van Doorn Distinguished Engineer VSS CDN Engineering 1 What is a CDN? 2 Content Router get customer
We Recommend: Click here to increase PC Speed! URL Decode Lookup. Express. DNS Records (Advanced Tool) URL Encode Trace.
 Manage Microsoft Windows - Streamline Wind and Management. Free 30-day Trial www.systemtools. 212.21.112.177 has not accessed this page recently We Recommend: Click here to increase PC Speed! Ping Express
Manage Microsoft Windows - Streamline Wind and Management. Free 30-day Trial www.systemtools. 212.21.112.177 has not accessed this page recently We Recommend: Click here to increase PC Speed! Ping Express
Junos Space for Android: Manage Your Network on the Go
 Junos Space for Android: Manage Your Network on the Go Combining the power of Junos Space and Android SDKs to build powerful and smart applications for network administrators Challenge It is important
Junos Space for Android: Manage Your Network on the Go Combining the power of Junos Space and Android SDKs to build powerful and smart applications for network administrators Challenge It is important
ICE Futures Europe. AFTS Technical Guide for Large Position Reporting V1.0
 ICE Futures Europe AFTS Technical Guide for Large Position Reporting V1.0 ICE FUTURES EUROPE Page 1 of 7 Contents 1. Introduction... 3 2. Online access to Clearing Systems... 4 3. Uploading Data... 5 4.
ICE Futures Europe AFTS Technical Guide for Large Position Reporting V1.0 ICE FUTURES EUROPE Page 1 of 7 Contents 1. Introduction... 3 2. Online access to Clearing Systems... 4 3. Uploading Data... 5 4.
.Masr IDN registry system. National Telecom Regulatory Authority Of EGYPT ( NTRA ) ( 20 Min )
 ). مصر (.Masr IDN registry system National Telecom Regulatory Authority Of EGYPT ( NTRA ) ( 20 Min ) If you talk to a man in a language he understands, that goes to his head. If you talk to him in his
). مصر (.Masr IDN registry system National Telecom Regulatory Authority Of EGYPT ( NTRA ) ( 20 Min ) If you talk to a man in a language he understands, that goes to his head. If you talk to him in his
Introduction to The Internet. ISP/IXP Workshops
 Introduction to The Internet ISP/IXP Workshops 1 Introduction to the Internet Topologies and Definitions IP Addressing Internet Hierarchy Gluing it all together 2 Topologies and Definitions What does all
Introduction to The Internet ISP/IXP Workshops 1 Introduction to the Internet Topologies and Definitions IP Addressing Internet Hierarchy Gluing it all together 2 Topologies and Definitions What does all
Pre Delegation Testing (PDT) Frequently Asked Questions (FAQ)
 Pre Delegation Testing (PDT) Frequently Asked Questions (FAQ) [Ver 1.7 2013-06- 04] List of contents General questions Who do I contact with questions about Pre- Delegation Testing?... 3 What is the process
Pre Delegation Testing (PDT) Frequently Asked Questions (FAQ) [Ver 1.7 2013-06- 04] List of contents General questions Who do I contact with questions about Pre- Delegation Testing?... 3 What is the process
Adding Advanced Caching and Replication Techniques to the Apache Web Server
 Adding Advanced Caching and Replication Techniques to the Apache Web Server Joachim Marder, Steffen Rothkugel, Peter Sturm University of Trier D-54286 Trier, Germany Email: [email protected], [email protected],
Adding Advanced Caching and Replication Techniques to the Apache Web Server Joachim Marder, Steffen Rothkugel, Peter Sturm University of Trier D-54286 Trier, Germany Email: [email protected], [email protected],
Part I - Gathering WHOIS Information
 Part I - Gathering WHOIS Information Exercise 1: command-line WHOIS queries: in the following exercise you will use a Linux system to perform WHOIS lookups from a command-line. This requires outbound TCP
Part I - Gathering WHOIS Information Exercise 1: command-line WHOIS queries: in the following exercise you will use a Linux system to perform WHOIS lookups from a command-line. This requires outbound TCP
Integrating Complementary Tools with PopMedNet TM
 Integrating Complementary Tools with PopMedNet TM 27 July 2015 Rich Schaaf [email protected] Introduction Commonwealth Informatics Implements and supports innovative systems for medical product safety
Integrating Complementary Tools with PopMedNet TM 27 July 2015 Rich Schaaf [email protected] Introduction Commonwealth Informatics Implements and supports innovative systems for medical product safety
SiteCelerate white paper
 SiteCelerate white paper Arahe Solutions SITECELERATE OVERVIEW As enterprises increases their investment in Web applications, Portal and websites and as usage of these applications increase, performance
SiteCelerate white paper Arahe Solutions SITECELERATE OVERVIEW As enterprises increases their investment in Web applications, Portal and websites and as usage of these applications increase, performance
APNIC IPv6 Deployment
 APNIC IPv6 Deployment Ulaanbaatar, Mongolia 19 October 2015 Issue Date: Revision: Overview Deployment motivation Network deployment IPv6 Services deployment IPv6 Anycast service IPv6 Cloud service Summary
APNIC IPv6 Deployment Ulaanbaatar, Mongolia 19 October 2015 Issue Date: Revision: Overview Deployment motivation Network deployment IPv6 Services deployment IPv6 Anycast service IPv6 Cloud service Summary
How-to: Single Sign-On
 How-to: Single Sign-On Document version: 1.02 nirva systems [email protected] nirva-systems.com How-to: Single Sign-On - page 2 This document describes how to use the Single Sign-On (SSO) features
How-to: Single Sign-On Document version: 1.02 nirva systems [email protected] nirva-systems.com How-to: Single Sign-On - page 2 This document describes how to use the Single Sign-On (SSO) features
Introduction to The Internet
 Introduction to The Internet ISP Workshops Last updated 5 September 2014 1 Introduction to the Internet p Topologies and Definitions p IP Addressing p Internet Hierarchy p Gluing it all together 2 Topologies
Introduction to The Internet ISP Workshops Last updated 5 September 2014 1 Introduction to the Internet p Topologies and Definitions p IP Addressing p Internet Hierarchy p Gluing it all together 2 Topologies
S y s t e m A r c h i t e c t u r e
 S y s t e m A r c h i t e c t u r e V e r s i o n 5. 0 Page 1 Enterprise etime automates and streamlines the management, collection, and distribution of employee hours, and eliminates the use of manual
S y s t e m A r c h i t e c t u r e V e r s i o n 5. 0 Page 1 Enterprise etime automates and streamlines the management, collection, and distribution of employee hours, and eliminates the use of manual
Lab 8.3.2 Conducting a Network Capture with Wireshark
 Lab 8.3.2 Conducting a Network Capture with Wireshark Objectives Perform a network traffic capture with Wireshark to become familiar with the Wireshark interface and environment. Analyze traffic to a web
Lab 8.3.2 Conducting a Network Capture with Wireshark Objectives Perform a network traffic capture with Wireshark to become familiar with the Wireshark interface and environment. Analyze traffic to a web
FortiGate Multi-Threat Security Systems I
 FortiGate Multi-Threat Security Systems I Module 9: Web Filtering 2013 Fortinet Inc. All rights reserved. The information contained herein is subject to change without notice. No part of this publication
FortiGate Multi-Threat Security Systems I Module 9: Web Filtering 2013 Fortinet Inc. All rights reserved. The information contained herein is subject to change without notice. No part of this publication
Layer Four Traceroute (and related tools) A modern, flexible path-discovery solution with advanced features for network (reverse) engineers
 Layer Four Traceroute (and related tools) A modern, flexible path-discovery solution with advanced features for network (reverse) engineers So, what is path discovery and why is it important? Path discovery
Layer Four Traceroute (and related tools) A modern, flexible path-discovery solution with advanced features for network (reverse) engineers So, what is path discovery and why is it important? Path discovery
Tools for penetration tests 1. Carlo U. Nicola, HT FHNW With extracts from documents of : Google; Wireshark; nmap; Nessus.
 Tools for penetration tests 1 Carlo U. Nicola, HT FHNW With extracts from documents of : Google; Wireshark; nmap; Nessus. What is a penetration test? Goals: 1. Analysis of an IT-environment and search
Tools for penetration tests 1 Carlo U. Nicola, HT FHNW With extracts from documents of : Google; Wireshark; nmap; Nessus. What is a penetration test? Goals: 1. Analysis of an IT-environment and search
DNS Basics. DNS Basics
 DNS Basics 1 A quick introduction to the Domain Name System (DNS). Shows the basic purpose of DNS, hierarchy of domain names, and an example of how the DNS protocol is used. There are many details of DNS
DNS Basics 1 A quick introduction to the Domain Name System (DNS). Shows the basic purpose of DNS, hierarchy of domain names, and an example of how the DNS protocol is used. There are many details of DNS
How to use the UNIX commands for incident handling. June 12, 2013 Koichiro (Sparky) Komiyama Sam Sasaki JPCERT Coordination Center, Japan
 How to use the UNIX commands for incident handling June 12, 2013 Koichiro (Sparky) Komiyama Sam Sasaki JPCERT Coordination Center, Japan Agenda Training Environment Commands for incident handling network
How to use the UNIX commands for incident handling June 12, 2013 Koichiro (Sparky) Komiyama Sam Sasaki JPCERT Coordination Center, Japan Agenda Training Environment Commands for incident handling network
Interoperable Cloud Storage with the CDMI Standard
 Interoperable Cloud Storage with the CDMI Standard Storage and Data Management in a post-filesystem World Mark Carlson, SNIA TC and Oracle Co-Chair, SNIA Cloud Storage TWG and Initiative Author: Mark Carlson,
Interoperable Cloud Storage with the CDMI Standard Storage and Data Management in a post-filesystem World Mark Carlson, SNIA TC and Oracle Co-Chair, SNIA Cloud Storage TWG and Initiative Author: Mark Carlson,
Glossary of Technical Terms Related to IPv6
 AAAA Record An AAAA record stores a 128-bit Internet Protocol version 6 (IPv6) address, which does not fit the standard A record format. For example, 2007:0db6:85a3:0000:0000:6a2e:0371:7234 is a valid
AAAA Record An AAAA record stores a 128-bit Internet Protocol version 6 (IPv6) address, which does not fit the standard A record format. For example, 2007:0db6:85a3:0000:0000:6a2e:0371:7234 is a valid
IPv6 The Big Picture. Rob Evans, Janet [email protected]
 IPv6 The Big Picture Rob Evans, Janet [email protected] Where are we? IPv4 32 bit addresses 4,294,967,296 possible addresses In practice much less than this. History of large allocations /8s Inefficiency
IPv6 The Big Picture Rob Evans, Janet [email protected] Where are we? IPv4 32 bit addresses 4,294,967,296 possible addresses In practice much less than this. History of large allocations /8s Inefficiency
Practical Essbase Web Services
 Practical Essbase Web Services For Fun and Profit Jason Jones Jason Jones l Essbase l Programming l Mobile development l ODI l Blogging l Open source Agenda l Web services in a nutshell l Essbase connectivity
Practical Essbase Web Services For Fun and Profit Jason Jones Jason Jones l Essbase l Programming l Mobile development l ODI l Blogging l Open source Agenda l Web services in a nutshell l Essbase connectivity
From the Monolith to Microservices: Evolving Your Architecture to Scale. Randy Shoup @randyshoup linkedin.com/in/randyshoup
 From the Monolith to Microservices: Evolving Your Architecture to Scale Randy Shoup @randyshoup linkedin.com/in/randyshoup Background Consulting CTO at Randy Shoup Consulting o o Helping companies from
From the Monolith to Microservices: Evolving Your Architecture to Scale Randy Shoup @randyshoup linkedin.com/in/randyshoup Background Consulting CTO at Randy Shoup Consulting o o Helping companies from
RESTful or RESTless Current State of Today's Top Web APIs
 RESTful or RESTless Current State of Today's Top Web APIs Frederik Buelthoff, Maria Maleshkova AIFB, Karlsruhe Ins-tute of Technology (KIT), Germany [1] Growing Number of Web APIs Challenges Scalability
RESTful or RESTless Current State of Today's Top Web APIs Frederik Buelthoff, Maria Maleshkova AIFB, Karlsruhe Ins-tute of Technology (KIT), Germany [1] Growing Number of Web APIs Challenges Scalability
GravityLab Multimedia Inc. Windows Media Authentication Administration Guide
 GravityLab Multimedia Inc. Windows Media Authentication Administration Guide Token Auth Menu GravityLab Multimedia supports two types of authentication to accommodate customers with content that requires
GravityLab Multimedia Inc. Windows Media Authentication Administration Guide Token Auth Menu GravityLab Multimedia supports two types of authentication to accommodate customers with content that requires
Designing RESTful Web Applications
 Ben Ramsey php works About Me: Ben Ramsey Proud father of 7-month-old Sean Organizer of Atlanta PHP user group Founder of PHP Groups Founding principal of PHP Security Consortium Original member of PHPCommunity.org
Ben Ramsey php works About Me: Ben Ramsey Proud father of 7-month-old Sean Organizer of Atlanta PHP user group Founder of PHP Groups Founding principal of PHP Security Consortium Original member of PHPCommunity.org
Web Development. Owen Sacco. ICS2205/ICS2230 Web Intelligence
 Web Development Owen Sacco ICS2205/ICS2230 Web Intelligence Brief Course Overview An introduction to Web development Server-side Scripting Web Servers PHP Client-side Scripting HTML & CSS JavaScript &
Web Development Owen Sacco ICS2205/ICS2230 Web Intelligence Brief Course Overview An introduction to Web development Server-side Scripting Web Servers PHP Client-side Scripting HTML & CSS JavaScript &
Setup Guide Access Manager 3.2 SP3
 Setup Guide Access Manager 3.2 SP3 August 2014 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE
Setup Guide Access Manager 3.2 SP3 August 2014 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE
Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ MEng. Nguyễn CaoĐạt
 Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ MEng. Nguyễn CaoĐạt 1 Lecture 10: Application Layer 2 Application Layer Where our applications are running Using services provided by
Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ MEng. Nguyễn CaoĐạt 1 Lecture 10: Application Layer 2 Application Layer Where our applications are running Using services provided by
OpenID Single Sign On and OAuth Data Access for Google Apps. Ryan Boyd @ryguyrg Dave Primmer May 2010
 OpenID Single Sign On and OAuth Data Access for Google Apps Ryan Boyd @ryguyrg Dave Primmer May 2010 Why? View live notes and questions about this session on Google Wave: http://bit.ly/magicwave Agenda
OpenID Single Sign On and OAuth Data Access for Google Apps Ryan Boyd @ryguyrg Dave Primmer May 2010 Why? View live notes and questions about this session on Google Wave: http://bit.ly/magicwave Agenda
Testing the API behind a mobile app. Tutorial Marc van t Veer
 Testing the API behind a mobile app Tutorial Marc van t Veer Content What is an API Why use an API How to use an API How-to test an API Exercises Group exercises (learning concepts 7) Individual exercises
Testing the API behind a mobile app Tutorial Marc van t Veer Content What is an API Why use an API How to use an API How-to test an API Exercises Group exercises (learning concepts 7) Individual exercises
Amazon Web Services Primer. William Strickland COP 6938 Fall 2012 University of Central Florida
 Amazon Web Services Primer William Strickland COP 6938 Fall 2012 University of Central Florida AWS Overview Amazon Web Services (AWS) is a collection of varying remote computing provided by Amazon.com.
Amazon Web Services Primer William Strickland COP 6938 Fall 2012 University of Central Florida AWS Overview Amazon Web Services (AWS) is a collection of varying remote computing provided by Amazon.com.
How To Use Netiq Access Manager 4.0.1.1 (Netiq) On A Pc Or Mac Or Macbook Or Macode (For Pc Or Ipad) On Your Computer Or Ipa (For Mac) On An Ip
 Setup Guide Access Manager 4.0 SP1 May 2014 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE
Setup Guide Access Manager 4.0 SP1 May 2014 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE
HTTP connections can use transport-layer security (SSL or its successor, TLS) to provide data integrity
 Improving File Sharing Security: A Standards Based Approach A Xythos Software White Paper January 2, 2003 Abstract Increasing threats to enterprise networks coupled with an ever-growing dependence upon
Improving File Sharing Security: A Standards Based Approach A Xythos Software White Paper January 2, 2003 Abstract Increasing threats to enterprise networks coupled with an ever-growing dependence upon
Methods for Sharing Dynamic IP Address Space Information with Others
 MAAWG Recommendation Methods for Sharing Dynamic IP Address Space Information with Others Introduction While MAAWG is on record as recommending that the best option for controlling the flow of unwanted
MAAWG Recommendation Methods for Sharing Dynamic IP Address Space Information with Others Introduction While MAAWG is on record as recommending that the best option for controlling the flow of unwanted
Get Success in Passing Your Certification Exam at first attempt!
 Get Success in Passing Your Certification Exam at first attempt! Exam : 920-440 Title : nncde wireless lan Version : DEMO 1. A customer wants to access the Microsoft Outlook Web Access application through
Get Success in Passing Your Certification Exam at first attempt! Exam : 920-440 Title : nncde wireless lan Version : DEMO 1. A customer wants to access the Microsoft Outlook Web Access application through
ICE Trade Vault. Public User & Technology Guide June 6, 2014
 ICE Trade Vault Public User & Technology Guide June 6, 2014 This material may not be reproduced or redistributed in whole or in part without the express, prior written consent of IntercontinentalExchange,
ICE Trade Vault Public User & Technology Guide June 6, 2014 This material may not be reproduced or redistributed in whole or in part without the express, prior written consent of IntercontinentalExchange,
Law Enforcement and Internet Governance: An Ounce of Prevention Is Worth a Pound of Cure
 Law Enforcement and Internet Governance: An Ounce of Prevention Is Worth a Pound of Cure Supervisory Special Agent Robert Flaim Federal Bureau of Investigation (FBI) Operational Technology Division Global
Law Enforcement and Internet Governance: An Ounce of Prevention Is Worth a Pound of Cure Supervisory Special Agent Robert Flaim Federal Bureau of Investigation (FBI) Operational Technology Division Global
3. The Domain Name Service
 3. The Domain Name Service n Overview and high level design n Typical operation and the role of caching n Contents of DNS Resource Records n Basic message formats n Configuring/updating Resource Records
3. The Domain Name Service n Overview and high level design n Typical operation and the role of caching n Contents of DNS Resource Records n Basic message formats n Configuring/updating Resource Records
Use Enterprise SSO as the Credential Server for Protected Sites
 Webthority HOW TO Use Enterprise SSO as the Credential Server for Protected Sites This document describes how to integrate Webthority with Enterprise SSO version 8.0.2 or 8.0.3. Webthority can be configured
Webthority HOW TO Use Enterprise SSO as the Credential Server for Protected Sites This document describes how to integrate Webthority with Enterprise SSO version 8.0.2 or 8.0.3. Webthority can be configured
Computer Networking LAB 2 HTTP
 Computer Networking LAB 2 HTTP 1 OBJECTIVES The basic GET/response interaction HTTP message formats Retrieving large HTML files Retrieving HTML files with embedded objects HTTP authentication and security
Computer Networking LAB 2 HTTP 1 OBJECTIVES The basic GET/response interaction HTTP message formats Retrieving large HTML files Retrieving HTML files with embedded objects HTTP authentication and security
KonyOne Server Prerequisites _ MS SQL Server
 KonyOne Server Prerequisites _ MS SQL Server KonyOne Platform Release 5.0 Copyright 2012-2013 Kony Solutions, Inc. All Rights Reserved. Page 1 of 13 Copyright 2012-2013 by Kony Solutions, Inc. All rights
KonyOne Server Prerequisites _ MS SQL Server KonyOne Platform Release 5.0 Copyright 2012-2013 Kony Solutions, Inc. All Rights Reserved. Page 1 of 13 Copyright 2012-2013 by Kony Solutions, Inc. All rights
CHAPTER 24 Communicating with the Web
 CHAPTER 24 Communicating with the Web Figure 24-1. Mobile technology and the ubiquitous nature of the Web have changed the world we live in. You can now sit in the park and do your banking, search Amazon.com
CHAPTER 24 Communicating with the Web Figure 24-1. Mobile technology and the ubiquitous nature of the Web have changed the world we live in. You can now sit in the park and do your banking, search Amazon.com
Network Technologies
 Network Technologies Glenn Strong Department of Computer Science School of Computer Science and Statistics Trinity College, Dublin January 28, 2014 What Happens When Browser Contacts Server I Top view:
Network Technologies Glenn Strong Department of Computer Science School of Computer Science and Statistics Trinity College, Dublin January 28, 2014 What Happens When Browser Contacts Server I Top view:
Security Testing For RESTful Applications
 Security Testing For RESTful Applications Ofer Shezaf, HP Enterprise Security Products [email protected] What I do for a living? Product Manager, Security Solutions, HP ArcSight Led security research and product
Security Testing For RESTful Applications Ofer Shezaf, HP Enterprise Security Products [email protected] What I do for a living? Product Manager, Security Solutions, HP ArcSight Led security research and product
REST web services. Representational State Transfer Author: Nemanja Kojic
 REST web services Representational State Transfer Author: Nemanja Kojic What is REST? Representational State Transfer (ReST) Relies on stateless, client-server, cacheable communication protocol It is NOT
REST web services Representational State Transfer Author: Nemanja Kojic What is REST? Representational State Transfer (ReST) Relies on stateless, client-server, cacheable communication protocol It is NOT
IETF Update on RDAP. ICANN52 Singapore CCTLD Tech Day. Marc Blanchet Viagénie [email protected]
 IETF Update on RDAP ICANN52 Singapore CCTLD Tech Day Marc Blanchet Viagénie [email protected] February 9th 2015 From Whois to RDAP RDAP: Registration Data Access Protocol replacement of whois structured
IETF Update on RDAP ICANN52 Singapore CCTLD Tech Day Marc Blanchet Viagénie [email protected] February 9th 2015 From Whois to RDAP RDAP: Registration Data Access Protocol replacement of whois structured
tibbr Now, the Information Finds You.
 tibbr Now, the Information Finds You. - tibbr Integration 1 tibbr Integration: Get More from Your Existing Enterprise Systems and Improve Business Process tibbr empowers IT to integrate the enterprise
tibbr Now, the Information Finds You. - tibbr Integration 1 tibbr Integration: Get More from Your Existing Enterprise Systems and Improve Business Process tibbr empowers IT to integrate the enterprise
Online Data Services. Security Guidelines. Online Data Services by Esri UK. Security Best Practice
 Online Data Services Security Guidelines Online Data Services by Esri UK Security Best Practice 28 November 2014 Contents Contents... 1 1. Introduction... 2 2. Data Service Accounts, Security and Fair
Online Data Services Security Guidelines Online Data Services by Esri UK Security Best Practice 28 November 2014 Contents Contents... 1 1. Introduction... 2 2. Data Service Accounts, Security and Fair
Advanced Higher Computing. Computer Networks. Homework Sheets
 Advanced Higher Computing Computer Networks Homework Sheets Topic : Network Protocols and Standards. Name the organisation responsible for setting international standards and explain why network standards
Advanced Higher Computing Computer Networks Homework Sheets Topic : Network Protocols and Standards. Name the organisation responsible for setting international standards and explain why network standards
1. When will an IP process drop a datagram? 2. When will an IP process fragment a datagram? 3. When will a TCP process drop a segment?
 Questions 1. When will an IP process drop a datagram? 2. When will an IP process fragment a datagram? 3. When will a TCP process drop a segment? 4. When will a TCP process resend a segment? CP476 Internet
Questions 1. When will an IP process drop a datagram? 2. When will an IP process fragment a datagram? 3. When will a TCP process drop a segment? 4. When will a TCP process resend a segment? CP476 Internet
Programming IoT Gateways With macchina.io
 Programming IoT Gateways With macchina.io Günter Obiltschnig Applied Informatics Software Engineering GmbH Maria Elend 143 9182 Maria Elend Austria [email protected] This article shows how
Programming IoT Gateways With macchina.io Günter Obiltschnig Applied Informatics Software Engineering GmbH Maria Elend 143 9182 Maria Elend Austria [email protected] This article shows how
Safewhere*Identify 3.4. Release Notes
 Safewhere*Identify 3.4 Release Notes Safewhere*identify is a new kind of user identification and administration service providing for externalized and seamless authentication and authorization across organizations.
Safewhere*Identify 3.4 Release Notes Safewhere*identify is a new kind of user identification and administration service providing for externalized and seamless authentication and authorization across organizations.
Setup Guide Access Manager Appliance 3.2 SP3
 Setup Guide Access Manager Appliance 3.2 SP3 August 2014 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS
Setup Guide Access Manager Appliance 3.2 SP3 August 2014 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS
What's inside the cloud?!
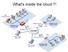 What's inside the cloud?! Initial Arpanet Initial Arpanet Interface Message Processors - DDP-516 mini-computers - 24 Kbyte of Core memory - Store-and-forward packet switching - Predecessors of present
What's inside the cloud?! Initial Arpanet Initial Arpanet Interface Message Processors - DDP-516 mini-computers - 24 Kbyte of Core memory - Store-and-forward packet switching - Predecessors of present
Pass Through Proxy. How-to. Overview:..1 Why PTP?...1
 Pass Through Proxy How-to Overview:..1 Why PTP?...1 Via an SA port...1 Via external DNS resolution...1 Examples of Using Passthrough Proxy...2 Example configuration using virtual host name:...3 Example
Pass Through Proxy How-to Overview:..1 Why PTP?...1 Via an SA port...1 Via external DNS resolution...1 Examples of Using Passthrough Proxy...2 Example configuration using virtual host name:...3 Example
How to Configure Captive Portal
 How to Configure Captive Portal Captive portal is one of the user identification methods available on the Palo Alto Networks firewall. Unknown users sending HTTP or HTTPS 1 traffic will be authenticated,
How to Configure Captive Portal Captive portal is one of the user identification methods available on the Palo Alto Networks firewall. Unknown users sending HTTP or HTTPS 1 traffic will be authenticated,
APNIC Trial of Certification of IP Addresses and ASes
 APNIC Trial of Certification of IP Addresses and ASes RIPE 51 11 October 2005 Geoff Huston 1 Address and Routing Security What we have today is a relatively insecure system that is vulnerable to various
APNIC Trial of Certification of IP Addresses and ASes RIPE 51 11 October 2005 Geoff Huston 1 Address and Routing Security What we have today is a relatively insecure system that is vulnerable to various
January 2011 Maltego 3 User Guide - Transforms Version 3.0
 PATERVA Maltego transforms A reference guide RT 2011/01 Table of Contents 1 Introduction... 7 2 Search engine transforms... 8 2.1 General notes when using search engine transforms... 8 2.2 Problems with
PATERVA Maltego transforms A reference guide RT 2011/01 Table of Contents 1 Introduction... 7 2 Search engine transforms... 8 2.1 General notes when using search engine transforms... 8 2.2 Problems with
SuperLumin Nemesis. Administration Guide. February 2011
 SuperLumin Nemesis Administration Guide February 2011 SuperLumin Nemesis Legal Notices Information contained in this document is believed to be accurate and reliable. However, SuperLumin assumes no responsibility
SuperLumin Nemesis Administration Guide February 2011 SuperLumin Nemesis Legal Notices Information contained in this document is believed to be accurate and reliable. However, SuperLumin assumes no responsibility
Single Sign On. SSO & ID Management for Web and Mobile Applications
 Single Sign On and ID Management Single Sign On SSO & ID Management for Web and Mobile Applications Presenter: Manish Harsh Program Manager for Developer Marketing Platforms of NVIDIA (Visual Computing
Single Sign On and ID Management Single Sign On SSO & ID Management for Web and Mobile Applications Presenter: Manish Harsh Program Manager for Developer Marketing Platforms of NVIDIA (Visual Computing
Web Hosting Features. Small Office Premium. Small Office. Basic Premium. Enterprise. Basic. General
 General Basic Basic Small Office Small Office Enterprise Enterprise RAID Web Storage 200 MB 1.5 MB 3 GB 6 GB 12 GB 42 GB Web Transfer Limit 36 GB 192 GB 288 GB 480 GB 960 GB 1200 GB Mail boxes 0 23 30
General Basic Basic Small Office Small Office Enterprise Enterprise RAID Web Storage 200 MB 1.5 MB 3 GB 6 GB 12 GB 42 GB Web Transfer Limit 36 GB 192 GB 288 GB 480 GB 960 GB 1200 GB Mail boxes 0 23 30
Agenda. How to configure
 [email protected] Agenda Strongly Recommend: Knowledge of ArcGIS Server and Portal for ArcGIS Security in the context of ArcGIS Server/Portal for ArcGIS Access Authentication Authorization: securing web services
[email protected] Agenda Strongly Recommend: Knowledge of ArcGIS Server and Portal for ArcGIS Security in the context of ArcGIS Server/Portal for ArcGIS Access Authentication Authorization: securing web services
From Internet Data Centers to Data Centers in the Cloud
 From Internet Data Centers to Data Centers in the Cloud This case study is a short extract from a keynote address given to the Doctoral Symposium at Middleware 2009 by Lucy Cherkasova of HP Research Labs
From Internet Data Centers to Data Centers in the Cloud This case study is a short extract from a keynote address given to the Doctoral Symposium at Middleware 2009 by Lucy Cherkasova of HP Research Labs
Microsoft Office Web Apps Server 2013 Integration with SharePoint 2013 Setting up Load Balanced Office Web Apps Farm with SSL (HTTPS)
 Microsoft Office Web Apps Server 2013 Integration with SharePoint 2013 Setting up Load Balanced Office Web Apps Farm with SSL (HTTPS) December 25 th, 2015 V.1.0 Prepared by: Manoj Karunarathne MCT, MCSA,
Microsoft Office Web Apps Server 2013 Integration with SharePoint 2013 Setting up Load Balanced Office Web Apps Farm with SSL (HTTPS) December 25 th, 2015 V.1.0 Prepared by: Manoj Karunarathne MCT, MCSA,
Federated Threat Data Sharing with the Collective Intelligence Framework (CIF)
 Federated Threat Data Sharing with the Collective Intelligence Framework (CIF) Gabriel Iovino (REN-ISAC), Kevin Benton (REN-ISAC), Yoshiaki Kasahara (Kyushu University), Yasuichi Kitamura (APAN) TIP2013
Federated Threat Data Sharing with the Collective Intelligence Framework (CIF) Gabriel Iovino (REN-ISAC), Kevin Benton (REN-ISAC), Yoshiaki Kasahara (Kyushu University), Yasuichi Kitamura (APAN) TIP2013
<Insert Picture Here> Oracle Web Cache 11g Overview
 Oracle Web Cache 11g Overview Oracle Web Cache Oracle Web Cache is a secure reverse proxy cache and a compression engine deployed between Browser and HTTP server Browser and Content
Oracle Web Cache 11g Overview Oracle Web Cache Oracle Web Cache is a secure reverse proxy cache and a compression engine deployed between Browser and HTTP server Browser and Content
The full setup includes the server itself, the server control panel, Firebird Database Server, and three sample applications with source code.
 Content Introduction... 2 Data Access Server Control Panel... 2 Running the Sample Client Applications... 4 Sample Applications Code... 7 Server Side Objects... 8 Sample Usage of Server Side Objects...
Content Introduction... 2 Data Access Server Control Panel... 2 Running the Sample Client Applications... 4 Sample Applications Code... 7 Server Side Objects... 8 Sample Usage of Server Side Objects...
DNSSEC in your workflow
 DNSSEC in your workflow Presentation roadmap Overview of problem space Architectural changes to allow for DNSSEC deployment Deployment tasks Key maintenance DNS server infrastructure Providing secure delegations
DNSSEC in your workflow Presentation roadmap Overview of problem space Architectural changes to allow for DNSSEC deployment Deployment tasks Key maintenance DNS server infrastructure Providing secure delegations
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 W H I T E P A P E R A p p l i c a t i o n D e l i v e r y f o r C l o u d S e r v i c e s : C u s t o m i z i n g S e r v i c e C r e a t i o n i n V i r t u a l E n v i r o n m e n t s Sponsored by: Brocade
W H I T E P A P E R A p p l i c a t i o n D e l i v e r y f o r C l o u d S e r v i c e s : C u s t o m i z i n g S e r v i c e C r e a t i o n i n V i r t u a l E n v i r o n m e n t s Sponsored by: Brocade
Eucalyptus 3.4.2 User Console Guide
 Eucalyptus 3.4.2 User Console Guide 2014-02-23 Eucalyptus Systems Eucalyptus Contents 2 Contents User Console Overview...4 Install the Eucalyptus User Console...5 Install on Centos / RHEL 6.3...5 Configure
Eucalyptus 3.4.2 User Console Guide 2014-02-23 Eucalyptus Systems Eucalyptus Contents 2 Contents User Console Overview...4 Install the Eucalyptus User Console...5 Install on Centos / RHEL 6.3...5 Configure
API documentation - 1 -
 API documentation - 1 - Table of Contents 1. Introduction 1.1. What is an API 2. API Functions 2.1. Purge list of files 2.1.1 Description 2.1.2 Implementation 2.2. Purge of whole cache (all files on all
API documentation - 1 - Table of Contents 1. Introduction 1.1. What is an API 2. API Functions 2.1. Purge list of files 2.1.1 Description 2.1.2 Implementation 2.2. Purge of whole cache (all files on all
SIP Protocol as a Communication Bus to Control Embedded Devices
 229 SIP Protocol as a Communication Bus to Control Embedded Devices Ramunas DZINDZALIETA Institute of Mathematics and Informatics Akademijos str. 4, Vilnius Lithuania [email protected] Abstract.
229 SIP Protocol as a Communication Bus to Control Embedded Devices Ramunas DZINDZALIETA Institute of Mathematics and Informatics Akademijos str. 4, Vilnius Lithuania [email protected] Abstract.
architecture: what the pieces are and how they fit together names and addresses: what's your name and number?
 Communications and networking history and background telephone system local area networks Internet architecture: what the pieces are and how they fit together names and addresses: what's your name and
Communications and networking history and background telephone system local area networks Internet architecture: what the pieces are and how they fit together names and addresses: what's your name and
