RETTEW Associates, Inc. RISK MANAGEMENT PLAN. for. (client project/rfp number) (date of proposal submission)
|
|
|
- Veronica Shields
- 10 years ago
- Views:
Transcription
1 RISK MANAGEMENT PLAN for (client project/rfp number) (date of proposal submission) This proposal includes data that shall not be disclosed outside the government and shall not be duplicated, used, or disclosed in whole or in part for any purpose other than to evaluate this proposal. If, however, a contract is awarded to this offeror as a result of or in connection with the submission of this data, the government shall have the right to duplicate, use, or disclose the data to the extent provided in the resulting contract. This restriction does not limit the government s right to use information contained in this data if it is obtained from another source without restriction.
2 Table of Contents 1.0 DESCRIPTION INTRODUCTION PURPOSE PROJECT RISK ANALYSIS Risk Analysis Tools Aspects of Risk Severity of Risk... 4 Figure Risk Assessment Assignment Matrix Risk Verification APPROACH TO RISK MANAGEMENT RISK DEFINITIONS Technical Risk Programmatic Risk Supportability Risk Cost and Schedule Risk METHODS OVERVIEW Techniques Applied... 7 Figure Key Indicator Programmatic Risk APPLICATION RISK ASSESSMENT Step 1: Planning for Risk Assessment Step 2: Identifying Program Objectives or Requirements Step 3: Defining Program Risks... 9 Figure Affinity Diagram Step 4: Ranking Program Risks Step 5: Managing Program Risks Step 6: Managing Action Plans Step 7: Continually Assessing Program Risks RISK RESPONSE DEVELOPMENT Avoidance Control Retention RISK RESPONSE CONTROL REFERENCES AND FOUNDATIONAL DATA SOURCES
3 1.0 Description 1.1 Introduction, is proud to offer our Risk Management Plan (RMP) in support of (client RFP number). RETTEW presents a unique blend of private and public sector skills and historical success in identifying, reducing, and managing client project risk to achieve client goals and objectives. Our diverse, talented team incorporates a best-of-breed strategy by using cutting edge risk management tools and methodologies as described within this RMP to maximize our client s resources and RETTEW s value as a world-class contracting partner. 1.2 Purpose Risk Management, according to T.V. Caver, is a method of managing that concentrates on identifying and controlling the areas or events that have a potential of causing unwanted change it is no more and no less than informed management. This RMP presents RETTEW s process for implementing proactive risk management as part of the overall management of the (client RFP number). Risk management is a program management tool used to assess and mitigate events that might adversely impact a project. Successful implementation of risk management will increase the program s likelihood of success. This RMP will: Serve as a basis for identifying alternatives to achieve cost, schedule, and performance goals; Assist in making decisions on schedule and task priorities; Provide risk information for Program Reviews or Milestone decisions; and Allow monitoring the health of the program as it proceeds. The RMP also describes methods for identifying, analyzing, prioritizing, and tracking risk drivers, developing risk-handling plans, and planning for adequate resources to handle risk. It assigns specific responsibilities for the management of risk and prescribes the documenting, monitoring, and reporting processes to be followed. 1.3 Project Risk Analysis Project risk analysis is initially performed in the early stages of a project s lifecycle usually during the planning stage to identify potential risks, the associated impacts, and potential mitigation plans. In addition to performing the initial risk analysis, it is recommended that the analysis be periodically reviewed and updated especially if an identified risk is realized. 3
4 1.3.1 Risk Analysis Tools. Risk analysis is a formal process that can be performed using dedicated tools such as: Strength-Weakness-Opportunity-Threat (SWOT) analysis Risk Priority Number (RPN) or risk priority matrix Failure Mode and Effects Analysis (FMEA) These tools can be combined with other tools like brainstorming to ensure effective coverage for risk identification, analysis of potential impact if the risk is realized, and potential mitigation plans Aspects of Risk. Successful risk analysis depends, in part, on ensuring that appropriate organizations are represented during risk analysis meetings and that all aspects of potential risk are considered. Aspects of risk to consider include, but are not limited to, the potential impact on: Meeting established goals or objectives The planned schedule Identified resources Safety Produceability Serviceability Reliability Meeting customer expectations and requirements Severity of Risk. Risk assessment involves determining the impact of severity if the risk occurs and the probability that the risk will occur. Determining the impact of severity is usually done by performing analysis of like risks from other projects, historical data, and through the use of other methods such as brainstorming. Risk probability is determined based on the likelihood that the risk will occur during the execution of the project. A risk assessment assignment matrix, as shown in Figure below, helps the project by having each risk individually ranked on a color-coded R/Y/G scale for severity and probability. Figure 1.3.3: 4
5 After identification of the risks, risk mitigation and verification are performed throughout the project s lifecycle. Risk mitigation begins with identifying activities the team or organization can perform to reduce the likelihood that an identified risk will occur and/or to reduce its impact. Once risk mitigation planning occurs, the plans are implemented during the project and should be reviewed on a regular basis to assess the status of existing risks and determine whether new risks have been identified or if identified risks were realized Risk Verification. Risk verification is the process of ensuring that the risk mitigation activities reasonably prevent the risk from occurring. An example is the security risk for an automated teller machine the risk that someone else can access your bank account. The mitigation is the additional requirement of a secured numeric password, along with a restriction of three false attempts before the account would freeze, locking out even the owner of the account. The verification is the attempt to access a secured account with an invalid, null, or otherwise compromised password. 5
6 2.0 Approach to Risk Management 2.1 Risk Definitions Risk must be classified in order to make it manageable. Four facets of risk are used to manage cost, schedule, and performance issues faced on a project. Classifying a risk into one or more of the four facets requires examining the source of the risk. The four facets are: Technical Risk. Technical risk (performance related) is the risk associated with evolving a new design or approach either to provide a greater level of performance or to accommodate some new constraints. Many technical risks are borne out of from the always present requirement to minimize or maximize physical properties of processes, systems, and equipment. Describing technical risk is difficult, because when examined at the lowest level of detail, there are many details to examine and consider. As the design architecture, performance, and other requirements and project constraints become known on a given project, a more detailed list of risks should be prepared based on project-specific information Programmatic Risk. Programmatic risk (performance related) is the risk associated with obtaining and using applicable resources and activities that can affect project direction but that may be outside the project manager s control. Programmatic risks are grouped into categories based on the nature and source of factors that have the potential to disrupt the project s implementation plan, such as: Disruptions caused by decisions made at higher levels of authority directly related to the project Disruptions caused by events or actions affecting the project but not directed specifically at it Disruptions caused primarily by a failure to foresee production-related problems Disruptions caused by imperfect capabilities Disruptions caused primarily by a failure to foresee problems other than those included in the first four categories Supportability Risk. Supportability risk (environment related) is the risk associated with fielding and maintaining systems or processes that are currently being developed or that have been developed and are being deployed. Supportability risk comprises both technical and programmatic aspects. 6
7 2.1.4 Cost and Schedule Risk. Risk of cost and schedule growth is a major concern. This problem is further complicated because performance and design technical problems are sometimes solved by increasing the planned project scope, thereby increasing project cost and/or schedule. Two major risk areas have an effect on cost and growth schedule: (1) Unreasonably low cost or schedule estimates; and (2) A project not carried out efficiently enough to meet reasonable cost or schedule objectives. Final costs and schedules are primarily a function of the skill of the project manager and project team in accommodating unanticipated problems related to technical, programmatic, and supportability risks. An unrealistically low baseline cost or schedule estimate can result from any of four categories (prior to a pricing decision): (1) Inadequate system description; (2) Inadequate historical cost or schedule database; (3) Lack of sound methods relating historical costs and schedules to new project costs; and (4) Incomplete cost or schedule estimates. 2.2 Methods Overview There are a multitude of risk management engagement methods. There is no onesize-fits-all method for project managers or teams to follow for risk assessment. To the point, it is incumbent for the project manager and team to fully understand their risk environment in order to carry out the risk management process Techniques Applied. There are many techniques to consider when managing risk. The below list represents, but is not limited to, the most often employed techniques: Analogy comparisons Cost risk/wbs simulation modeling Decision analysis Estimating relationships Expert interviews Life-cycle cost analysis Network analysis Performance tracking Plan evaluation Project templates Risk factors 7
8 These techniques are not used in stand-alone fashion; rather they are cross-walked against three other key indicators resource requirements, applications, and output. This cross-walk of techniques and key indicators uses markers (e.g., High, Medium, Low and Difficult, Easy, etc. ) much like the Risk Assessment Assignment Matrix in Figure to develop the key indicator. Figure demonstrates: Resource Requirements Applications Output cost Proper facilities and equipment Implementation time Ease of use Time commitment Project status reporting Major planning decisions Contract strategy selection Milestone preparation Design guidance Source selection Budget submittal Accuracy Level of detail utility Figure Key Indicator Communication. 3.0 Application An important part of executing the RMP, identifying the methodologies, and executing the techniques is the role of communication. If ignored, it can render the best risk assessment and analysis ineffective. Properly communicating risk data to decision makers must be clearly defined. Inherent to clear delivery is the understanding that data must be thoroughly documented in order for risk management processes to be effective. Sources of data, assumptions made about the project, the assessment, analysis, and handling techniques used must be consistently documented and communicated in order for the project leader and project team to accomplish goals and objectives. 3.1 Risk Assessment A good risk assessment and management process is essential to the success of any program. RETTEW s 7-step process consists of: Step 1: Planning for Risk Assessment. Planning the activity. A Project Manager may begin this process by selecting the Risk Assessment Team, setting ground rules, and determining supporting tools. The Risk Assessment Team should include representatives from all affected areas of the project. 8
9 3.1.2 Step 2: Identifying Program Objectives or Requirements. Once the Project Manager identifies the Risk Assessment Team and tools, the team should identify the key project objectives and associated requirements. These objectives and requirements will assist the team in identifying risks Step 3: Defining Program Risks. The Project Manager or facilitator leads the team through a structured brainstorming process to identify the program risks. Once all ideas are heard and vetted, an affinity diagram is created to group, merge, and eliminate duplicate risks and to identify dependent risks. Affinity diagrams are used to produce many possible answers to identified risks, e.g., in an open-ended question such as What are some of the ways to reduce cycle time for process A? Figure shows an example of a notional affinity diagram with five identified risk areas: With an affinity diagram, verbal information can be transformed into a visual pattern. Through grouping and association, identified risks may be merged if similar or dependent, and eliminated if the same. Following the identification of risks, the team assigns various attributes to each risk. At a minimum, relevant time frame, impact, and probability of occurrence are assigned. Then the team sets impact definitions. In a standard Risk Matrix, impact definitions are: C (Critical): If the risk event occurs, the project will fail. Minimum acceptable requirements will not be met. 9
10 S (Serious): If the risk event occurs, the project will encounter major cost or schedule increases. Minimum acceptable requirements will be met. Secondary requirements may not be met. Mo (Moderate): If the risk event occurs, the project will encounter moderate cost or schedule increases. Minimum acceptable requirements will be met. Some secondary requirements may not be met. Mi (Minor): If the risk event occurs, the project will encounter small cost or schedule increases. Minimum acceptable requirements will be met. Most secondary requirements will be met. N (Negligible): If the risk event occurs, it will have no effect on the project. All requirements will be met. Probability of occurrence is the team s assessment of the likelihood of a risk happening. In a standard Risk Matrix, it is sufficient to estimate probabilities using a relative scale: 0-10%: very unlikely the risk event will occur 11-40%: unlikely the risk event will occur 41-60%: even likelihood the risk event will occur 61-90%: likely the risk event will occur %: very likely the risk event will occur This approach may be used to translate subjective probability estimates into numbers in the absence of hard data. However, if hard data is available for some risks, the other probability estimates must be chosen to be consistent with the hard data Step 4: Ranking Program Risks. At this point, the team should have all the information needed to rank the risks. If using a Risk Matrix tool, this process is simple and automated. A popular, easy to use ranking method is the Borda Voting Method. For the Borda Count Method, each risk (or risk solution) gets 1 point for each last place vote received, 2 points for each next-to-last point vote, etc., all the way up to N points for each first place vote (where N is the number of risks/solutions). The risk or risk solution with the largest point total wins the election. For instance, in a 4 candidate election, each 4th place vote is worth 1 point, each 3rd place vote is worth 2 points, each 2nd place vote is worth 3 points, and each 1st place vote is worth 4 points. The Borda Count Method, or some variation of it, is often used for things like polls which rank sporting teams or academic institutions. If the team chooses not to use an automated tool, an alternative is to use a multivoting technique such as sticky dots or weighted voting. Multi-voting narrows a large list of possibilities to a smaller list of the top priorities or to a final 10
11 selection. Multi-voting is preferable to straight voting because it allows an item that is favored by all, but not the top choice of any, to rise to the top. A good time to use multi-voting is after a brainstorming session, when a list must be narrowed down, or when a decision must be made by group judgment Step 5: Managing Program Risks. All risks require some form of management, whether it involves a plan for handling risks (action plan) or merely keeping status. After risks are ranked, the team should identify the risks that are high priority, need to be managed, and require resources. Working with the Project Manager, some risks will be eliminated because of changing requirements and others will be transferred out of the organization due to lack of internal resources Step 6: Managing Action Plans. Whenever feasible, usually after a baseline assessment, the project team should develop detailed action plans and enter an initial status, assign primary responsibility, and determine criteria surrounding the risk event. The status of each action plan should be reviewed and assessed periodically as risk rankings are adjusted accordingly Step 7: Continuously Assessing Program Risks. Continuously assessing risks is essential to good program risk management. As a project progresses, risks should be reassessed periodically to determine whether their level of importance has changed or whether new risks have developed that should be identified, assessed, ranked, and managed. 3.2 Risk Response Development Risk response development is a critical element in the risk management process that determines what action (if any) will be taken to address risk issues evaluated in identification and quantification efforts. Generally, response strategies fall into one of the following categories: Avoidance. In many situations, a lower risk choice is available from a range of risk alternatives. Selecting a lower risk option represents a risk avoidance decision. Not all risk should be avoided, however. On occasion, a higher risk can be deemed more appropriate because of design flexibility, enhanced performance, or the capacity for expansion. 11
12 3.2.2 Control. Risk control is the most common of all the risk-handling strategies. It is the process of taking specific courses of action to reduce the probability, reduce the impact, or deflect the risk to another party. This often involves using reviews, risk reduction milestones, development of fallback positions, and other similar management actions. The project manager must develop risk reduction plans and then track activities based upon those plans. Action plans are generally built into the project plan and, ultimately, into the work breakdown structure (WBS). Through risk control, the project manager may emphasize minimizing the probability that the risk will occur or minimizing the impact if the risk does occur. Risk may also be controlled through means of deflection by sharing with other organizations Retention. Risk retention is a decision to accept the consequences if the event occurs. Projects inherently involve retention of some risk. The project manager must determine what level of risk can be safely assumed in each situation as it evolves. 3.3 Risk Response Control After risks are identified and quantified, and clear responses developed, those responses must be put into action. Risk response control is the daily active management of risk. It takes place as the project progresses. Risk response control involves implementing the RMP, which should be part of the project plan. The challenge is dealing with risk events as they occur. Flaws in carefully structured plans become evident when those plans are implemented. Some strategies work very effectively; others prove far less effective. Thus, it often becomes necessary to begin the cycle anew, which involves either reconsidering risk responses or migrating even further back in the process to reevaluate identified risks. 12
13 4.0 References and Foundational Data Attributed to: 4.1 The American Society for Quality 4.2 The MITRE Corporation 4.3 Risk Management, ESI International 4.4 Department of Defense M, Transition from Development to Production Solving the Risk Equation 13
Appendix V Risk Management Plan Template
 Appendix V Risk Management Plan Template Version 2 March 7, 2005 This page is intentionally left blank. Version 2 March 7, 2005 Title Page Document Control Panel Table of Contents List of Acronyms Definitions
Appendix V Risk Management Plan Template Version 2 March 7, 2005 This page is intentionally left blank. Version 2 March 7, 2005 Title Page Document Control Panel Table of Contents List of Acronyms Definitions
DRAFT RESEARCH SUPPORT BUILDING AND INFRASTRUCTURE MODERNIZATION RISK MANAGEMENT PLAN. April 2009 SLAC I 050 07010 002
 DRAFT RESEARCH SUPPORT BUILDING AND INFRASTRUCTURE MODERNIZATION RISK MANAGEMENT PLAN April 2009 SLAC I 050 07010 002 Risk Management Plan Contents 1.0 INTRODUCTION... 1 1.1 Scope... 1 2.0 MANAGEMENT
DRAFT RESEARCH SUPPORT BUILDING AND INFRASTRUCTURE MODERNIZATION RISK MANAGEMENT PLAN April 2009 SLAC I 050 07010 002 Risk Management Plan Contents 1.0 INTRODUCTION... 1 1.1 Scope... 1 2.0 MANAGEMENT
Risk Management Primer
 Risk Management Primer Purpose: To obtain strong project outcomes by implementing an appropriate risk management process Audience: Project managers, project sponsors, team members and other key stakeholders
Risk Management Primer Purpose: To obtain strong project outcomes by implementing an appropriate risk management process Audience: Project managers, project sponsors, team members and other key stakeholders
Project Zeus. Risk Management Plan
 Project Zeus Risk Management Plan 1 Baselined: 5/7/1998 Last Modified: N/A Owner: David Jones/Zeus Project Manager Page Section 1. Introduction 3 1.1 Assumptions, Constraints, and Policies 3 1.2 Related
Project Zeus Risk Management Plan 1 Baselined: 5/7/1998 Last Modified: N/A Owner: David Jones/Zeus Project Manager Page Section 1. Introduction 3 1.1 Assumptions, Constraints, and Policies 3 1.2 Related
PROJECT RISK MANAGEMENT
 PROJECT RISK MANAGEMENT DEFINITION OF A RISK OR RISK EVENT: A discrete occurrence that may affect the project for good or bad. DEFINITION OF A PROBLEM OR UNCERTAINTY: An uncommon state of nature, characterized
PROJECT RISK MANAGEMENT DEFINITION OF A RISK OR RISK EVENT: A discrete occurrence that may affect the project for good or bad. DEFINITION OF A PROBLEM OR UNCERTAINTY: An uncommon state of nature, characterized
P3M3 Portfolio Management Self-Assessment
 Procurement Programmes & Projects P3M3 v2.1 Self-Assessment Instructions and Questionnaire P3M3 Portfolio Management Self-Assessment P3M3 is a registered trade mark of AXELOS Limited Contents Introduction
Procurement Programmes & Projects P3M3 v2.1 Self-Assessment Instructions and Questionnaire P3M3 Portfolio Management Self-Assessment P3M3 is a registered trade mark of AXELOS Limited Contents Introduction
PROJECT MANAGEMENT PLAN Outline VERSION 0.0 STATUS: OUTLINE DATE:
 PROJECT MANAGEMENT PLAN Outline VERSION 0.0 STATUS: OUTLINE DATE: Project Name Project Management Plan Document Information Document Title Version Author Owner Project Management Plan Amendment History
PROJECT MANAGEMENT PLAN Outline VERSION 0.0 STATUS: OUTLINE DATE: Project Name Project Management Plan Document Information Document Title Version Author Owner Project Management Plan Amendment History
Negative Risk. Risk Can Be Positive. The Importance of Project Risk Management
 The Importance of Project Risk Management Project risk management is the art and science of identifying, analyzing, and responding to risk throughout the life of a project and in the best interests t of
The Importance of Project Risk Management Project risk management is the art and science of identifying, analyzing, and responding to risk throughout the life of a project and in the best interests t of
IT Project Management Methodology. Project Scope Management Support Guide
 NATIONAL INFORMATION TECHNOLOGY AUTHORITY - UGANDA IT Project Management Methodology Project Scope Management Support Guide Version 0.3 Version Date Author Change Description 0.1 23 rd Mar, 2013 Gerald
NATIONAL INFORMATION TECHNOLOGY AUTHORITY - UGANDA IT Project Management Methodology Project Scope Management Support Guide Version 0.3 Version Date Author Change Description 0.1 23 rd Mar, 2013 Gerald
Value Engineering VE with Risk Assessment RA
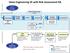 Preparation Conclude & Report Value Engineering VE with Risk Assessment RA yes START Plan for VE and RA Value Engineering Job Plan 1 2 Function Information Analysis 3 Creative 4 Evaluation 5 Develop recommendations
Preparation Conclude & Report Value Engineering VE with Risk Assessment RA yes START Plan for VE and RA Value Engineering Job Plan 1 2 Function Information Analysis 3 Creative 4 Evaluation 5 Develop recommendations
Procurement Programmes & Projects P3M3 v2.1 Self-Assessment Instructions and Questionnaire. P3M3 Project Management Self-Assessment
 Procurement Programmes & Projects P3M3 v2.1 Self-Assessment Instructions and Questionnaire P3M3 Project Management Self-Assessment Contents Introduction 3 User Guidance 4 P3M3 Self-Assessment Questionnaire
Procurement Programmes & Projects P3M3 v2.1 Self-Assessment Instructions and Questionnaire P3M3 Project Management Self-Assessment Contents Introduction 3 User Guidance 4 P3M3 Self-Assessment Questionnaire
Risk Management approach for Cultural Heritage Projects Based on Project Management Body of Knowledge
 1 Extreme Heritage, 2007 Australia, 19-21 July 2007, James Cook University, Cairns, Australia Theme 6: Heritage disasters and risk preparedness approach for Cultural Heritage Projects Based on Project
1 Extreme Heritage, 2007 Australia, 19-21 July 2007, James Cook University, Cairns, Australia Theme 6: Heritage disasters and risk preparedness approach for Cultural Heritage Projects Based on Project
PROJECT RISK MANAGEMENT
 11 PROJECT RISK MANAGEMENT Project Risk Management includes the processes concerned with identifying, analyzing, and responding to project risk. It includes maximizing the results of positive events and
11 PROJECT RISK MANAGEMENT Project Risk Management includes the processes concerned with identifying, analyzing, and responding to project risk. It includes maximizing the results of positive events and
Project Management Plan for
 Project Management Plan for [Project ID] Prepared by: Date: [Name], Project Manager Approved by: Date: [Name], Project Sponsor Approved by: Date: [Name], Executive Manager Table of Contents Project Summary...
Project Management Plan for [Project ID] Prepared by: Date: [Name], Project Manager Approved by: Date: [Name], Project Sponsor Approved by: Date: [Name], Executive Manager Table of Contents Project Summary...
Summary of GAO Cost Estimate Development Best Practices and GAO Cost Estimate Audit Criteria
 Characteristic Best Practice Estimate Package Component / GAO Audit Criteria Comprehensive Step 2: Develop the estimating plan Documented in BOE or Separate Appendix to BOE. An analytic approach to cost
Characteristic Best Practice Estimate Package Component / GAO Audit Criteria Comprehensive Step 2: Develop the estimating plan Documented in BOE or Separate Appendix to BOE. An analytic approach to cost
Project Management Process
 Project Management Process Description... 1 STAGE/STEP/TASK SUMMARY LIST... 2 Project Initiation 2 Project Control 4 Project Closure 5 Project Initiation... 7 Step 01: Project Kick Off 10 Step 02: Project
Project Management Process Description... 1 STAGE/STEP/TASK SUMMARY LIST... 2 Project Initiation 2 Project Control 4 Project Closure 5 Project Initiation... 7 Step 01: Project Kick Off 10 Step 02: Project
Development, Acquisition, Implementation, and Maintenance of Application Systems
 Development, Acquisition, Implementation, and Maintenance of Application Systems Part of a series of notes to help Centers review their own Center internal management processes from the point of view of
Development, Acquisition, Implementation, and Maintenance of Application Systems Part of a series of notes to help Centers review their own Center internal management processes from the point of view of
Develop Project Charter. Develop Project Management Plan
 Develop Charter Develop Charter is the process of developing documentation that formally authorizes a project or a phase. The documentation includes initial requirements that satisfy stakeholder needs
Develop Charter Develop Charter is the process of developing documentation that formally authorizes a project or a phase. The documentation includes initial requirements that satisfy stakeholder needs
Project Risk Management. Presented by Stephen Smith
 Project Risk Management Presented by Stephen Smith Introduction Risk Management Insurance Business Financial Project Risk Management Project A temporary endeavour undertaken to create a unique product
Project Risk Management Presented by Stephen Smith Introduction Risk Management Insurance Business Financial Project Risk Management Project A temporary endeavour undertaken to create a unique product
CPM -100: Principles of Project Management
 CPM -100: Principles of Project Management Lesson E: Risk and Procurement Management Presented by Sam Lane [email protected] Ph: 703-883-7149 Presented at the IPM 2002 Fall Conference Prepared by the Washington,
CPM -100: Principles of Project Management Lesson E: Risk and Procurement Management Presented by Sam Lane [email protected] Ph: 703-883-7149 Presented at the IPM 2002 Fall Conference Prepared by the Washington,
Motivations. spm - 2014 adolfo villafiorita - introduction to software project management
 Risk Management Motivations When we looked at project selection we just took into account financial data In the scope management document we emphasized the importance of making our goals achievable, i.e.
Risk Management Motivations When we looked at project selection we just took into account financial data In the scope management document we emphasized the importance of making our goals achievable, i.e.
GUIDELINE NO. 22 REGULATORY AUDITS OF ENERGY BUSINESSES
 Level 37, 2 Lonsdale Street Melbourne 3000, Australia Telephone.+61 3 9302 1300 +61 1300 664 969 Facsimile +61 3 9302 1303 GUIDELINE NO. 22 REGULATORY AUDITS OF ENERGY BUSINESSES ENERGY INDUSTRIES JANUARY
Level 37, 2 Lonsdale Street Melbourne 3000, Australia Telephone.+61 3 9302 1300 +61 1300 664 969 Facsimile +61 3 9302 1303 GUIDELINE NO. 22 REGULATORY AUDITS OF ENERGY BUSINESSES ENERGY INDUSTRIES JANUARY
Project Risk Management
 Project Risk Management Study Notes PMI, PMP, CAPM, PMBOK, PM Network and the PMI Registered Education Provider logo are registered marks of the Project Management Institute, Inc. Points to Note Risk Management
Project Risk Management Study Notes PMI, PMP, CAPM, PMBOK, PM Network and the PMI Registered Education Provider logo are registered marks of the Project Management Institute, Inc. Points to Note Risk Management
Measurement Information Model
 mcgarry02.qxd 9/7/01 1:27 PM Page 13 2 Information Model This chapter describes one of the fundamental measurement concepts of Practical Software, the Information Model. The Information Model provides
mcgarry02.qxd 9/7/01 1:27 PM Page 13 2 Information Model This chapter describes one of the fundamental measurement concepts of Practical Software, the Information Model. The Information Model provides
RISK MANAGEMENT OVERVIEW - APM Project Pathway (Draft) RISK MANAGEMENT JUST A PART OF PROJECT MANAGEMENT
 RISK MANAGEMENT OVERVIEW - APM Project Pathway (Draft) Risk should be defined as An uncertain event that, should it occur, would have an effect (positive or negative) on the project or business objectives.
RISK MANAGEMENT OVERVIEW - APM Project Pathway (Draft) Risk should be defined as An uncertain event that, should it occur, would have an effect (positive or negative) on the project or business objectives.
Introduction to the ITS Project Management Methodology
 Introduction to the ITS Project Management Methodology In September 1999 the Joint Legislative Committee on Performance Evaluation and Expenditure Review (PEER) produced a report entitled Major Computer
Introduction to the ITS Project Management Methodology In September 1999 the Joint Legislative Committee on Performance Evaluation and Expenditure Review (PEER) produced a report entitled Major Computer
pm4dev, 2007 management for development series The Project Management Processes PROJECT MANAGEMENT FOR DEVELOPMENT ORGANIZATIONS
 pm4dev, 2007 management for development series The Project Management Processes PROJECT MANAGEMENT FOR DEVELOPMENT ORGANIZATIONS PROJECT MANAGEMENT FOR DEVELOPMENT ORGANIZATIONS A methodology to manage
pm4dev, 2007 management for development series The Project Management Processes PROJECT MANAGEMENT FOR DEVELOPMENT ORGANIZATIONS PROJECT MANAGEMENT FOR DEVELOPMENT ORGANIZATIONS A methodology to manage
FMEA and FTA Analysis
 FMEA and FTA Analysis Why it is Coming to Your Hospital and Your Laboratory Tina A. Krenc Director, R&D Phase Systems Abbott Laboratories 1 Agenda Background on requirements for risk management Tools to
FMEA and FTA Analysis Why it is Coming to Your Hospital and Your Laboratory Tina A. Krenc Director, R&D Phase Systems Abbott Laboratories 1 Agenda Background on requirements for risk management Tools to
PMI Risk Management Professional (PMI-RMP ) - Practice Standard and Certification Overview
 PMI Risk Management Professional (PMI-RMP ) - Practice Standard and Certification Overview Sante Torino PMI-RMP, IPMA Level B Head of Risk Management Major Programmes, Selex ES / Land&Naval Systems Division
PMI Risk Management Professional (PMI-RMP ) - Practice Standard and Certification Overview Sante Torino PMI-RMP, IPMA Level B Head of Risk Management Major Programmes, Selex ES / Land&Naval Systems Division
September 2005 Report No. 06-009
 An Audit Report on The Health and Human Services Commission s Consolidation of Administrative Support Functions Report No. 06-009 John Keel, CPA State Auditor An Audit Report on The Health and Human Services
An Audit Report on The Health and Human Services Commission s Consolidation of Administrative Support Functions Report No. 06-009 John Keel, CPA State Auditor An Audit Report on The Health and Human Services
Strategic Risk Management for School Board Trustees
 Strategic Management for School Board Trustees A Management Process Framework May, 2012 Table of Contents Introduction Page I. Purpose....................................... 3 II. Applicability and Scope............................
Strategic Management for School Board Trustees A Management Process Framework May, 2012 Table of Contents Introduction Page I. Purpose....................................... 3 II. Applicability and Scope............................
Project Scope Management in PMBOK made easy
 By Dr. TD Jainendrakumar The main objective of any project is to fulfill the scope of the project on time and within the budget. What is Project Scope? Scope refers to all the work involved in creating
By Dr. TD Jainendrakumar The main objective of any project is to fulfill the scope of the project on time and within the budget. What is Project Scope? Scope refers to all the work involved in creating
Defining change management
 Defining change management Helping others understand change management in relation to project management and organizational change by Tim Creasey Director of Research and Development Prosci and the Change
Defining change management Helping others understand change management in relation to project management and organizational change by Tim Creasey Director of Research and Development Prosci and the Change
System/Data Requirements Definition Analysis and Design
 EXECUTIVE SUMMARY This document provides an overview of the Systems Development Life-Cycle (SDLC) process of the U.S. House of Representatives. The SDLC process consists of seven tailored phases that help
EXECUTIVE SUMMARY This document provides an overview of the Systems Development Life-Cycle (SDLC) process of the U.S. House of Representatives. The SDLC process consists of seven tailored phases that help
Risk Management Guide for DoD Acquisition
 Risk Management Guide for DoD Acquisition March 1998 DEPARTMENT OF DEFENSE DEFENSE ACQUISITION UNIVERSITY DEFENSE SYSTEMS MANAGEMENT COLLEGE PUBLISHED BY THE DEFENSE SYSTEMS MANAGEMENT COLLEGE PRESS FORT
Risk Management Guide for DoD Acquisition March 1998 DEPARTMENT OF DEFENSE DEFENSE ACQUISITION UNIVERSITY DEFENSE SYSTEMS MANAGEMENT COLLEGE PUBLISHED BY THE DEFENSE SYSTEMS MANAGEMENT COLLEGE PRESS FORT
Risk/Issue Management Plan
 Risk/Issue Management Plan Centralized Revenue Opportunity System November 2014 Version 2.0 This page intentionally left blank Table of Contents 1. Overview... 3 1.1 Purpose... 3 1.2 Scope... 3 2. Roles
Risk/Issue Management Plan Centralized Revenue Opportunity System November 2014 Version 2.0 This page intentionally left blank Table of Contents 1. Overview... 3 1.1 Purpose... 3 1.2 Scope... 3 2. Roles
Human Error and Safety Federal Aviation Human Error and Safety Administration Risk Analysis HESRA
 Human Error and Safety Risk Analysis HESRA A Proactive Tool for Assessing the Risk of Human Error Presented to: By: Eurocontrol Safety R&D Seminar Glen Hewitt, FAA Human Factors Research and Engineering
Human Error and Safety Risk Analysis HESRA A Proactive Tool for Assessing the Risk of Human Error Presented to: By: Eurocontrol Safety R&D Seminar Glen Hewitt, FAA Human Factors Research and Engineering
Do you know? "7 Practices" for a Reliable Requirements Management. by Software Process Engineering Inc. translated by Sparx Systems Japan Co., Ltd.
 Do you know? "7 Practices" for a Reliable Requirements Management by Software Process Engineering Inc. translated by Sparx Systems Japan Co., Ltd. In this white paper, we focus on the "Requirements Management,"
Do you know? "7 Practices" for a Reliable Requirements Management by Software Process Engineering Inc. translated by Sparx Systems Japan Co., Ltd. In this white paper, we focus on the "Requirements Management,"
THE ROLE OF PROJECT MANAGEMENT IN KNOWLEDGE MANAGEMENT
 1-04-15 INFORMATION MANAGEMENT: STRATEGY, SYSTEMS, AND TECHNOLOGY THE ROLE OF PROJECT MANAGEMENT IN KNOWLEDGE MANAGEMENT Ralph L. Kliem INSIDE Basics of Knowledge Management and Project Management; Work
1-04-15 INFORMATION MANAGEMENT: STRATEGY, SYSTEMS, AND TECHNOLOGY THE ROLE OF PROJECT MANAGEMENT IN KNOWLEDGE MANAGEMENT Ralph L. Kliem INSIDE Basics of Knowledge Management and Project Management; Work
The Key to a Successful KM Project
 Introduction An integrated PKM methodology enables organizations to maximize their investments by ensuring initiatives are on time and within budget, while sharing project challenges and successes that
Introduction An integrated PKM methodology enables organizations to maximize their investments by ensuring initiatives are on time and within budget, while sharing project challenges and successes that
PROJECT BOEING SGS. Interim Technology Performance Report 1. Company Name: The Boeing Company. Contract ID: DE-OE0000191
 Interim Techlogy Performance Report 1 PROJECT BOEING SGS Contract ID: DE-OE0000191 Project Type: Revision: V2 Company Name: The Boeing Company December 10, 2012 1 Interim Techlogy Performance Report 1
Interim Techlogy Performance Report 1 PROJECT BOEING SGS Contract ID: DE-OE0000191 Project Type: Revision: V2 Company Name: The Boeing Company December 10, 2012 1 Interim Techlogy Performance Report 1
Project Management Guidebook
 METHOD 12 3 empowering managers to succeed Project Management Guidebook ISBN 0-473-10445-8 A bout this e-book This e-book was created by Method123 (see www.method123.com) to help provide you with a simple
METHOD 12 3 empowering managers to succeed Project Management Guidebook ISBN 0-473-10445-8 A bout this e-book This e-book was created by Method123 (see www.method123.com) to help provide you with a simple
FUNBIO PROJECT RISK MANAGEMENT GUIDELINES
 FUNBIO PROJECT RISK MANAGEMENT GUIDELINES OP-09/2013 Responsible Unit: PMO Focal Point OBJECTIVE: This Operational Procedures presents the guidelines for the risk assessment and allocation process in projects.
FUNBIO PROJECT RISK MANAGEMENT GUIDELINES OP-09/2013 Responsible Unit: PMO Focal Point OBJECTIVE: This Operational Procedures presents the guidelines for the risk assessment and allocation process in projects.
Seven Practical Steps to Delivering More Secure Software. January 2011
 Seven Practical Steps to Delivering More Secure Software January 2011 Table of Contents Actions You Can Take Today 3 Delivering More Secure Code: The Seven Steps 4 Step 1: Quick Evaluation and Plan 5 Step
Seven Practical Steps to Delivering More Secure Software January 2011 Table of Contents Actions You Can Take Today 3 Delivering More Secure Code: The Seven Steps 4 Step 1: Quick Evaluation and Plan 5 Step
RISK MANAGEMENT STRATEGY
 RISK MANAGEMENT STRATEGY 1 Introduction The purpose of this document is to outline a which facilitates the effective recognition and management of risks facing the University. The Combined Code on Corporate
RISK MANAGEMENT STRATEGY 1 Introduction The purpose of this document is to outline a which facilitates the effective recognition and management of risks facing the University. The Combined Code on Corporate
Crosswalk Between Current and New PMP Task Classifications
 Crosswalk Between Current and New PMP Task Classifications Domain 01 Initiating the Project Conduct project selection methods (e.g., cost benefit analysis, selection criteria) through meetings with the
Crosswalk Between Current and New PMP Task Classifications Domain 01 Initiating the Project Conduct project selection methods (e.g., cost benefit analysis, selection criteria) through meetings with the
Design Failure Modes and Effects Analysis DFMEA with Suppliers
 Design Failure Modes and Effects Analysis DFMEA with Suppliers Copyright 2003-2007 Raytheon Company. All rights reserved. R6σ is a Raytheon trademark registered in the United States and Europe. Raytheon
Design Failure Modes and Effects Analysis DFMEA with Suppliers Copyright 2003-2007 Raytheon Company. All rights reserved. R6σ is a Raytheon trademark registered in the United States and Europe. Raytheon
Knowledge Base Data Warehouse Methodology
 Knowledge Base Data Warehouse Methodology Knowledge Base's data warehousing services can help the client with all phases of understanding, designing, implementing, and maintaining a data warehouse. This
Knowledge Base Data Warehouse Methodology Knowledge Base's data warehousing services can help the client with all phases of understanding, designing, implementing, and maintaining a data warehouse. This
Risk Assessment for Medical Devices. Linda Braddon, Ph.D. Bring your medical device to market faster 1
 Risk Assessment for Medical Devices Linda Braddon, Ph.D. Bring your medical device to market faster 1 My Perspective Work with start up medical device companies Goal: Making great ideas into profitable
Risk Assessment for Medical Devices Linda Braddon, Ph.D. Bring your medical device to market faster 1 My Perspective Work with start up medical device companies Goal: Making great ideas into profitable
PROCESS FOR RISK ASSESSMENT
 NHS Cambridgeshire Risk Assessment Framework INTRODUCTION The National Patient Safety Agency (NPSA) defines risk management as the process of identifying, assessing, analysing and managing all potential
NHS Cambridgeshire Risk Assessment Framework INTRODUCTION The National Patient Safety Agency (NPSA) defines risk management as the process of identifying, assessing, analysing and managing all potential
Effective Software Security Management
 Effective Software Security Management choosing the right drivers for applying application security Author: Dharmesh M Mehta [email protected] / [email protected] Table of Contents Abstract... 1
Effective Software Security Management choosing the right drivers for applying application security Author: Dharmesh M Mehta [email protected] / [email protected] Table of Contents Abstract... 1
Swirl. Multiplayer Gaming Simplified. CS4512 Systems Analysis and Design. Assignment 1 2010. Marque Browne 0814547. Manuel Honegger - 0837997
 1 Swirl Multiplayer Gaming Simplified CS4512 Systems Analysis and Design Assignment 1 2010 Marque Browne 0814547 Manuel Honegger - 0837997 Kieran O' Brien 0866946 2 BLANK MARKING SCHEME 3 TABLE OF CONTENTS
1 Swirl Multiplayer Gaming Simplified CS4512 Systems Analysis and Design Assignment 1 2010 Marque Browne 0814547 Manuel Honegger - 0837997 Kieran O' Brien 0866946 2 BLANK MARKING SCHEME 3 TABLE OF CONTENTS
The purpose of Capacity and Availability Management (CAM) is to plan and monitor the effective provision of resources to support service requirements.
 CAPACITY AND AVAILABILITY MANAGEMENT A Project Management Process Area at Maturity Level 3 Purpose The purpose of Capacity and Availability Management (CAM) is to plan and monitor the effective provision
CAPACITY AND AVAILABILITY MANAGEMENT A Project Management Process Area at Maturity Level 3 Purpose The purpose of Capacity and Availability Management (CAM) is to plan and monitor the effective provision
M-MIS. Comptroller of the Currency Administrator of National Banks. Management Information Systems. Comptroller s Handbook. May 1995.
 M-MIS Comptroller of the Currency Administrator of National Banks Management Information Systems Comptroller s Handbook May 1995 M Management Management Information Systems Table of Contents Introduction
M-MIS Comptroller of the Currency Administrator of National Banks Management Information Systems Comptroller s Handbook May 1995 M Management Management Information Systems Table of Contents Introduction
How Do I know If I Need RCx HOW TO CHOOSE A MANAGED SERVICES PROVIDER. www.netsolus.com
 How Do I know If I Need RCx HOW TO CHOOSE A MANAGED SERVICES PROVIDER www.netsolus.com Shifting your IT operations to a managed services provider (MSP) offers a multitude of benefits. Collaborating with
How Do I know If I Need RCx HOW TO CHOOSE A MANAGED SERVICES PROVIDER www.netsolus.com Shifting your IT operations to a managed services provider (MSP) offers a multitude of benefits. Collaborating with
IT Project Management Methodology. Project Risk Management Guide. Version 0.3
 NATIONAL INFORMATION TECHNOLOGY AUTHORITY - UGANDA IT Project Management Methodology Project Risk Management Guide Version 0.3 Project Risk Management Support Guide version 0.3 Page 1 Version Date Author
NATIONAL INFORMATION TECHNOLOGY AUTHORITY - UGANDA IT Project Management Methodology Project Risk Management Guide Version 0.3 Project Risk Management Support Guide version 0.3 Page 1 Version Date Author
Project Risk Management Basics: Cost and Schedule Impacts
 Project Risk Management Basics: Cost and Schedule Impacts CSVA 2011 Conference Toronto, Ontario Nov 14-16, 2011 Robert E. Rocco 1 Contents Background Fundamentals Process Tools/Supporting Documentation
Project Risk Management Basics: Cost and Schedule Impacts CSVA 2011 Conference Toronto, Ontario Nov 14-16, 2011 Robert E. Rocco 1 Contents Background Fundamentals Process Tools/Supporting Documentation
RISK MANAGEMENT GUIDE FOR DOD ACQUISITION
 RISK MANAGEMENT GUIDE FOR DOD ACQUISITION Sixth Edition (Version 1.0) August, 2006 Department of Defense Preface The Department of Defense (DoD) recognizes that risk management is critical to acquisition
RISK MANAGEMENT GUIDE FOR DOD ACQUISITION Sixth Edition (Version 1.0) August, 2006 Department of Defense Preface The Department of Defense (DoD) recognizes that risk management is critical to acquisition
U.S. Dept. of Defense Systems Engineering & Implications for SE Implementation in Other Domains
 U.S. Dept. of Defense Systems Engineering & Implications for SE Implementation in Other Domains Mary J. Simpson System Concepts 6400 32 nd Northwest, #9 Seattle, WA 98107 USA Joseph J. Simpson System Concepts
U.S. Dept. of Defense Systems Engineering & Implications for SE Implementation in Other Domains Mary J. Simpson System Concepts 6400 32 nd Northwest, #9 Seattle, WA 98107 USA Joseph J. Simpson System Concepts
Risk Assessment Worksheet and Management Plan
 Customer/Project Name: The Basics There are four steps to assessing and managing risks, and effective risk management requires all four of them. 1. Identify the risks 2. Qualify the risks a. Assess each
Customer/Project Name: The Basics There are four steps to assessing and managing risks, and effective risk management requires all four of them. 1. Identify the risks 2. Qualify the risks a. Assess each
Development Methodologies Compared
 N CYCLES software solutions Development Methodologies Compared Why different projects require different development methodologies. December 2002 Dan Marks 65 Germantown Court 1616 West Gate Circle Suite
N CYCLES software solutions Development Methodologies Compared Why different projects require different development methodologies. December 2002 Dan Marks 65 Germantown Court 1616 West Gate Circle Suite
SCOPE MANAGEMENT PLAN <PROJECT NAME>
 SCOPE MANAGEMENT PLAN TEMPLATE This Project Scope Management Plan Template is free for you to copy and use on your project and within your organization. We hope that you find this template useful and welcome
SCOPE MANAGEMENT PLAN TEMPLATE This Project Scope Management Plan Template is free for you to copy and use on your project and within your organization. We hope that you find this template useful and welcome
Requirements engineering
 Learning Unit 2 Requirements engineering Contents Introduction............................................... 21 2.1 Important concepts........................................ 21 2.1.1 Stakeholders and
Learning Unit 2 Requirements engineering Contents Introduction............................................... 21 2.1 Important concepts........................................ 21 2.1.1 Stakeholders and
Your Software Quality is Our Business. INDEPENDENT VERIFICATION AND VALIDATION (IV&V) WHITE PAPER Prepared by Adnet, Inc.
 INDEPENDENT VERIFICATION AND VALIDATION (IV&V) WHITE PAPER Prepared by Adnet, Inc. February 2013 1 Executive Summary Adnet is pleased to provide this white paper, describing our approach to performing
INDEPENDENT VERIFICATION AND VALIDATION (IV&V) WHITE PAPER Prepared by Adnet, Inc. February 2013 1 Executive Summary Adnet is pleased to provide this white paper, describing our approach to performing
Criteria for Flight Project Critical Milestone Reviews
 Criteria for Flight Project Critical Milestone Reviews GSFC-STD-1001 Baseline Release February 2005 Approved By: Original signed by Date: 2/19/05 Richard M. Day Director, Independent Technical Authority
Criteria for Flight Project Critical Milestone Reviews GSFC-STD-1001 Baseline Release February 2005 Approved By: Original signed by Date: 2/19/05 Richard M. Day Director, Independent Technical Authority
BODY OF KNOWLEDGE CERTIFIED SIX SIGMA YELLOW BELT
 BODY OF KNOWLEDGE CERTIFIED SIX SIGMA YELLOW BELT The topics in this Body of Knowledge include additional detail in the form of subtext explanations and the cognitive level at which test questions will
BODY OF KNOWLEDGE CERTIFIED SIX SIGMA YELLOW BELT The topics in this Body of Knowledge include additional detail in the form of subtext explanations and the cognitive level at which test questions will
PROJECT PLAN FOR. Project Name Here
 PROJECT PLAN FOR Project Name Here Version # DatE Reviewed and Approved for submittal to Executive Sponsor , Project Manager Project Plan Approved for submittal to Executive Sponsor: , Project
PROJECT PLAN FOR Project Name Here Version # DatE Reviewed and Approved for submittal to Executive Sponsor , Project Manager Project Plan Approved for submittal to Executive Sponsor: , Project
Risk Management (3C05/D22) Unit 3: Risk Management. What is risk?
 Risk Management (3C05/D22) Unit 3: Risk Management Objectives To explain the concept of risk & to develop its role within the software development process To introduce the use of risk management as a means
Risk Management (3C05/D22) Unit 3: Risk Management Objectives To explain the concept of risk & to develop its role within the software development process To introduce the use of risk management as a means
ENTERPRISE ARCHITECTUE OFFICE
 ENTERPRISE ARCHITECTUE OFFICE Date: 12/8/2010 Enterprise Architecture Guiding Principles 1 Global Architecture Principles 1.1 GA1: Statewide Focus 1.1.1 Principle Architecture decisions will be made based
ENTERPRISE ARCHITECTUE OFFICE Date: 12/8/2010 Enterprise Architecture Guiding Principles 1 Global Architecture Principles 1.1 GA1: Statewide Focus 1.1.1 Principle Architecture decisions will be made based
Program Management Toolkit Concept and Contents
 Program Management Toolkit Concept and Contents Audrey Taub Charlene McMahon 15 Feb 2001 Organization: W063 Project: 01CCG100 Purpose of PM Toolkit The purpose of the this Toolkit is to provide convenient
Program Management Toolkit Concept and Contents Audrey Taub Charlene McMahon 15 Feb 2001 Organization: W063 Project: 01CCG100 Purpose of PM Toolkit The purpose of the this Toolkit is to provide convenient
NZ Transport Agency Page 1 of 23
 NZ Transport Agency Page 1 of 23 Risk Management 1 Introduction The Highways and Network Operations (HNO) group supports the NZ Transport Agencies strategic objectives through the delivery of Capital Projects
NZ Transport Agency Page 1 of 23 Risk Management 1 Introduction The Highways and Network Operations (HNO) group supports the NZ Transport Agencies strategic objectives through the delivery of Capital Projects
Space project management
 ECSS-M-ST-80C Space project management Risk management ECSS Secretariat ESA-ESTEC Requirements & Standards Division Noordwijk, The Netherlands Foreword This Standard is one of the series of ECSS Standards
ECSS-M-ST-80C Space project management Risk management ECSS Secretariat ESA-ESTEC Requirements & Standards Division Noordwijk, The Netherlands Foreword This Standard is one of the series of ECSS Standards
http://www.io4pm.org IO4PM - International Organization for Project Management
 THE ONLY BOOK CAN SIMPLY LEARN PROJECT MANAGEMENT! Page 1 Contents ABOUT THE AUTHOR... 3 WHAT IS PROJECT MANAGEMENT?... 5 ORGANIZATIONAL INFLUENCES AND PROJECT LIFECYCLE... 11 PROJECT MANAGEMENT PROCESSES...
THE ONLY BOOK CAN SIMPLY LEARN PROJECT MANAGEMENT! Page 1 Contents ABOUT THE AUTHOR... 3 WHAT IS PROJECT MANAGEMENT?... 5 ORGANIZATIONAL INFLUENCES AND PROJECT LIFECYCLE... 11 PROJECT MANAGEMENT PROCESSES...
Building Business Case for the Enterprise From Vision to Outcomes IIBA Boston Sept. 20, 2012 Joseph Raynus ShareDynamics, Inc.
 Building Business Case for the Enterprise From Vision to Outcomes IIBA Boston Sept. 20, 2012 Joseph Raynus ShareDynamics, Inc. Presentation Focus Business Situation Risk Assessment Sensitivity Analysis
Building Business Case for the Enterprise From Vision to Outcomes IIBA Boston Sept. 20, 2012 Joseph Raynus ShareDynamics, Inc. Presentation Focus Business Situation Risk Assessment Sensitivity Analysis
The Systems Engineering Tool Box
 The ystems Engineering Tool Box Dr tuart Burge Give us the tools and we will finish the job Winston Churchill Pugh Matrix (PM) What is it and what does it do? The Pugh Matrix (PM) is a type of Matrix Diagram
The ystems Engineering Tool Box Dr tuart Burge Give us the tools and we will finish the job Winston Churchill Pugh Matrix (PM) What is it and what does it do? The Pugh Matrix (PM) is a type of Matrix Diagram
U.S. Department of the Treasury. Treasury IT Performance Measures Guide
 U.S. Department of the Treasury Treasury IT Performance Measures Guide Office of the Chief Information Officer (OCIO) Enterprise Architecture Program June 2007 Revision History June 13, 2007 (Version 1.1)
U.S. Department of the Treasury Treasury IT Performance Measures Guide Office of the Chief Information Officer (OCIO) Enterprise Architecture Program June 2007 Revision History June 13, 2007 (Version 1.1)
HOW NOT TO ATTRACT AN ENTREPRENEURIAL PM
 HOW NOT TO ATTRACT AN ENTREPRENEURIAL PM FORTUNE 500 HIGH-TECH EQUIPMENT AND SERVICES COMPANY Process-focused job description indicates low potential for career enhancement and discourages talent from
HOW NOT TO ATTRACT AN ENTREPRENEURIAL PM FORTUNE 500 HIGH-TECH EQUIPMENT AND SERVICES COMPANY Process-focused job description indicates low potential for career enhancement and discourages talent from
A Risk Assessment Methodology (RAM) for Physical Security
 A Risk Assessment Methodology (RAM) for Physical Security Violence, vandalism, and terrorism are prevalent in the world today. Managers and decision-makers must have a reliable way of estimating risk to
A Risk Assessment Methodology (RAM) for Physical Security Violence, vandalism, and terrorism are prevalent in the world today. Managers and decision-makers must have a reliable way of estimating risk to
Ready, Set, Go! A Game Plan for Talent Management in the Midmarket
 Ready, Set, Go! A Game Plan for Talent Management in the Midmarket Introduction Organizations that have survived the global economy of the past few years have experienced the new business reality: the
Ready, Set, Go! A Game Plan for Talent Management in the Midmarket Introduction Organizations that have survived the global economy of the past few years have experienced the new business reality: the
Choosing the Right Project and Portfolio Management Solution
 Choosing the Right Project and Portfolio Management Solution Executive Summary In too many organizations today, innovation isn t happening fast enough. Within these businesses, skills are siloed and resources
Choosing the Right Project and Portfolio Management Solution Executive Summary In too many organizations today, innovation isn t happening fast enough. Within these businesses, skills are siloed and resources
Risk Management Strategy and Guidelines
 Swale Borough Council Risk Management Strategy and Guidelines Status: Final Originating Date: January 2008 Date Ratified: February 2008 (Audit Committee) Next Review Date: January 2009 Accountable Member:
Swale Borough Council Risk Management Strategy and Guidelines Status: Final Originating Date: January 2008 Date Ratified: February 2008 (Audit Committee) Next Review Date: January 2009 Accountable Member:
RISK MANAGEMENT GUIDE FOR DOD ACQUISITION
 RISK MANAGEMENT GUIDE FOR DOD ACQUISITION Sixth Edition (Version 1.0) August, 2006 Department of Defense Preface The Department of Defense (DoD) recognizes that risk management is critical to acquisition
RISK MANAGEMENT GUIDE FOR DOD ACQUISITION Sixth Edition (Version 1.0) August, 2006 Department of Defense Preface The Department of Defense (DoD) recognizes that risk management is critical to acquisition
3.B METHODOLOGY SERVICE PROVIDER
 3.B METHODOLOGY SERVICE PROVIDER Approximately four years ago, the American Institute of Certified Public Accountants (AICPA) issued Statement on Standards for Attestation Engagements (SSAE) No. 16, Reporting
3.B METHODOLOGY SERVICE PROVIDER Approximately four years ago, the American Institute of Certified Public Accountants (AICPA) issued Statement on Standards for Attestation Engagements (SSAE) No. 16, Reporting
Enterprise Security Tactical Plan
 Enterprise Security Tactical Plan Fiscal Years 2011 2012 (July 1, 2010 to June 30, 2012) Prepared By: State Chief Information Security Officer The Information Security Council State of Minnesota Enterprise
Enterprise Security Tactical Plan Fiscal Years 2011 2012 (July 1, 2010 to June 30, 2012) Prepared By: State Chief Information Security Officer The Information Security Council State of Minnesota Enterprise
Transportation Risk Management: International Practices for Program Development and Project Delivery
 Transportation Risk Management: International Practices for Program Development and Project Delivery Sponsored by: In cooperation with: American Association of State Highway and Transportation Officials
Transportation Risk Management: International Practices for Program Development and Project Delivery Sponsored by: In cooperation with: American Association of State Highway and Transportation Officials
EIOPACP 13/011. Guidelines on PreApplication of Internal Models
 EIOPACP 13/011 Guidelines on PreApplication of Internal Models EIOPA Westhafen Tower, Westhafenplatz 1 60327 Frankfurt Germany Tel. + 49 6995111920; Fax. + 49 6995111919; site: www.eiopa.europa.eu Guidelines
EIOPACP 13/011 Guidelines on PreApplication of Internal Models EIOPA Westhafen Tower, Westhafenplatz 1 60327 Frankfurt Germany Tel. + 49 6995111920; Fax. + 49 6995111919; site: www.eiopa.europa.eu Guidelines
Software Risk Management
 Software Risk Management Former US Deputy Assistant Secretary of the Air Force Lloyd Mosemann said: Software is so vital to military system that, without it, most could not operate at all. Its importance
Software Risk Management Former US Deputy Assistant Secretary of the Air Force Lloyd Mosemann said: Software is so vital to military system that, without it, most could not operate at all. Its importance
NASCIO EA Development Tool-Kit Solution Architecture. Version 3.0
 NASCIO EA Development Tool-Kit Solution Architecture Version 3.0 October 2004 TABLE OF CONTENTS SOLUTION ARCHITECTURE...1 Introduction...1 Benefits...3 Link to Implementation Planning...4 Definitions...5
NASCIO EA Development Tool-Kit Solution Architecture Version 3.0 October 2004 TABLE OF CONTENTS SOLUTION ARCHITECTURE...1 Introduction...1 Benefits...3 Link to Implementation Planning...4 Definitions...5
Basic Unified Process: A Process for Small and Agile Projects
 Basic Unified Process: A Process for Small and Agile Projects Ricardo Balduino - Rational Unified Process Content Developer, IBM Introduction Small projects have different process needs than larger projects.
Basic Unified Process: A Process for Small and Agile Projects Ricardo Balduino - Rational Unified Process Content Developer, IBM Introduction Small projects have different process needs than larger projects.
Certified Software Quality Engineer (CSQE) Body of Knowledge
 Certified Software Quality Engineer (CSQE) Body of Knowledge The topics in this Body of Knowledge include additional detail in the form of subtext explanations and the cognitive level at which the questions
Certified Software Quality Engineer (CSQE) Body of Knowledge The topics in this Body of Knowledge include additional detail in the form of subtext explanations and the cognitive level at which the questions
PROJECT SCOPE MANAGEMENT
 5 PROJECT SCOPE MANAGEMENT Project Scope Management includes the processes required to ensure that the project includes all the work required, and only the work required, to complete the project successfully
5 PROJECT SCOPE MANAGEMENT Project Scope Management includes the processes required to ensure that the project includes all the work required, and only the work required, to complete the project successfully
San Francisco International Airport Enterprise Risk Management
 San Francisco International Airport Enterprise Risk Management Mike Warren Airport Risk Manager WHAT IS ENTERPRISE RISK MANAGEMENT (ERM) It is a comprehensive program that focuses on a continuous and sustainable
San Francisco International Airport Enterprise Risk Management Mike Warren Airport Risk Manager WHAT IS ENTERPRISE RISK MANAGEMENT (ERM) It is a comprehensive program that focuses on a continuous and sustainable
ITS Project Management Methodology
 ITS Project Management Methodology Information Technology Services Project Management Group 11/17/2014 Version 2.1 Author: ITS Project Management Group Document Control Change Record Date Author Version
ITS Project Management Methodology Information Technology Services Project Management Group 11/17/2014 Version 2.1 Author: ITS Project Management Group Document Control Change Record Date Author Version
SOFTWARE DEVELOPMENT STANDARD FOR SPACECRAFT
 SOFTWARE DEVELOPMENT STANDARD FOR SPACECRAFT Mar 31, 2014 Japan Aerospace Exploration Agency This is an English translation of JERG-2-610. Whenever there is anything ambiguous in this document, the original
SOFTWARE DEVELOPMENT STANDARD FOR SPACECRAFT Mar 31, 2014 Japan Aerospace Exploration Agency This is an English translation of JERG-2-610. Whenever there is anything ambiguous in this document, the original
