Identity Finder: Managing Your Results
|
|
|
- Neil Hampton
- 10 years ago
- Views:
Transcription
1 Identity Finder: Managing Your Results The most important part of running Identity Finder is determining the most effective and secure way of managing the search results. Be sure to carefully read and proceed through each of the following steps. For help with downloading, installing or configuring Identity Finder, please refer to the documentation found at Contents 1. Determine the File s Origin... 2 Where did the file come from?... 2 Carnegie Mellon Business/Academic Operations or Personal Data... 2 Files Left From Previous Owners Actions and the Password Vault... 3 Actions... 3 Shred... 3 Scrub... 4 Secure... 4 Quarantine... 5 Recycle... 5 Ignore... 5 Password Vault (Windows Only)... 6 Accessing the Password Vault Tool Acting on Search Results... 7 Windows... 7 Accessing Your Saved Information Other PII... 8 File Shredder... 9 Open Secure Zip Files Handling Outlook Items Remove Outlook Password... 11
2 1. Determine the File s Origin For each file that contains personally- identifiable information (PII), consider these points: IMPORTANT NOTE: If you are under a litigation hold, contact the Office of General Counsel ( ) or [email protected] or [email protected]) before making any changes. Where did the file come from? Is it your personal file? A file from someone who previously used or owned the computer? A file from Carnegie Mellon business or academic operations? Do you have no idea where it originated? Carnegie Mellon Business/Academic Operations or Personal Data If you are unsure whether you need to retain a file containing PII related to Carnegie Mellon business or academic operations, please consult your supervisor/advisor. If the file does not need to be retained, shred the file. If the file does need to be retained, ask yourself if you need the sensitive PII portions. o If no, then scrub (i.e., replace sensitive PII numbers with XXX while leaving the rest of the file unchanged). o If yes, then ask yourself if you need it on this computer? Yes, then secure the file. No, then quarantine the file. Files Left From Previous Owners If Carnegie Mellon provided the computer for business or academic operations, consult your supervisor/advisor to learn what to do with the file. If your supervisor/advisor does not believe the file was part of Carnegie Mellon business or academic operations AND you share your computer with co- workers, family or friends, please consult the people with whom you share your computer to determine the source of the file and whether it needs to be retained. If you still do not know where the file originated after consulting your supervisor/advisor and the people with whom you share your computer, shred the file. Page 2 of 12
3 2. Actions and the Password Vault Actions After reviewing your search results, you'll need to select the best way to handle this sensitive information. The following actions are available to you: Shred The Shred button is located on the Main ribbon and is enabled for all types of results; however, depending on the location of the result, Shred behaves differently. For files, Shred uses a secure 1pass wipe conforming to Carnegie Mellon's Guidelines for Data Protection - Media Sanitization and Disposal. For other locations, shred removes the information from your computer using other, appropriate methods. Identity matches can be shredded using one of the following methods: Single- click the result with the left mouse button to highlight it and click the Shred button on the Main ribbon. Single- click the result with the right mouse button to highlight it and bring up a context menu, then highlight and left- click on Shred. Highlight the result by single- clicking with the left mouse button or by using the arrow keys and then press the Delete key on your keyboard. Important Note: It is not possible to "undo" a Shred. Shredded results cannot be recovered. Once you shred something, it is gone. To ensure that you did not click on the shred button accidently, Identity Finder will generate a message after you click on the Shred button asking whether you are sure you want to shred the file. Page 3 of 12
4 Scrub (Text, CSV, and HTML files only as of version 8.0) When a text file has sensitive identity match information in it and you wish to keep the file on your computer, but do not need the personally identifiable information (PII), you should use the Scrub feature. Scrubbing (also known as redacting) secures files by removing PII information and leaving all other content in place. Identity Finder will replace the data with multiple X characters by default. You can change the replacement character to a number under Settings>Actions > Options for Scrub. Secure To secure a single text- based file with the Scrub feature, left- click the file result to highlight it and click the Scrub button on the ribbon. To redact multiple text files at one time, check the checkbox of each file and then select Scrub. You can choose to redact the personal information and replace it with your default choice from your File> Settings > Actions>Options for Scrub and check the box on Scrub all characters of a result except for the last four option, or you can select any digit from 0 to 9 or an X. Once you click OK for the Scrub action, the personal information will be permanently overwritten and cannot be undone. Identity Finder for Windows allow users to select from two types of encryption to password- protect a file; Secure with Profile Password allows users to secure a file with Identity Finder File Vault encryption, and Secure with Alternate Password provides an option to select a new password to secure that particular file. Identity Finder for Mac does not offer application- specific encryption and will always use Identity Finder File Vault encryption. Important notes on securing The Secure action will password- protect the selected file using your profile password. Once a file has been password- protected using Identity Finder File Vault encryption, double- clicking it will open Identity Finder to decrypt it and prompt for the password. If you forget the password, you will not be able to recover the document. If you plan to encrypt files for Carnegie Mellon business or academic operations, make sure you write down your profile password, lock it in a secure location and inform your supervisor of the secure location to ensure business continuity. Page 4 of 12
5 Quarantine Securely moves the highlighted file to a quarantine location and permanently shreds it from its original location. Follow these steps to quarantine a file: 1. Highlight the item you want to quarantine and then click on the Quarantine option in the top Actions menu; the Quarantine dialog box appears. 2. Select the Quarantine folder to which you wish to move the file. This should be a folder that is highly secure, such as an encrypted drive or a storage device to which unauthorized individuals do not have access. Note: You can specify a default Quarantine location in Settings. You may also choose to leave behind a warning text document in place of the file as a reminder that the file was moved to another location. Recycle This feature is disabled on the Carnegie Mellon installer. Moving a file to the Recycle Bin does not actually delete the file. To truly remove a file, use Shred. Ignore The Ignore feature allows you to designate certain items to be ignored by Identity Finder to prevent that information from being displayed in the future. Click Ignore and choose from the following: This Item Location: To ignore the currently selected location match of the item(s) selected. Selecting Ignore This Item Location will prevent that location from being searched in the future. This Identity Match: To ignore the currently selected Identity match in ALL locations in which it appears. Identity matches that you add to the Ignore list during a search will be ignored for the reminder of the current search. Page 5 of 12
6 Manage 'Ignore List': The settings window that appears will allow you to add or remove identity information or file locations from Identity Finder's Ignore list. By selecting Manage Ignore List, the View and manage Ignore List option in the Settings window is displayed. 1. To add identity information, select the identity type from the list under Ignore Identity; enter the identity value in the field next to the type list and then click the corresponding Add button. For example a string of numbers that Identity Finder identifies as a license number when in actuality the number is used as dummy data for training. 2. To add a file location, type or browse to the file next to Ignore Location. Click Add. 3. To remove an item from the Ignore list, highlight it and click the Remove button, the Remove All button clears the entire list. Password Vault (Windows Only) The Password Vault tool allows you to securely store and manage usernames and passwords for websites, encrypted files and other locations inside of your password- protected Identity Finder profile. In other words, the Identity Finder profile password is a single master password that allows you to gain access to the Password Vault. Once you've gained access, the Password Vault houses your list of files or accounts and their respective passwords. Note: The Password Vault tool is not available for Mac operating systems. Consider using Mac OS X's Keychain Access as an alternative. Accessing the Password Vault Tool To access the Password Vault tool, click the Password Vault button on the Tools ribbon. Another option to access Identity Finder Password Vault without launching Identity Finder search is through Windows All Programs>Identity Finder Folder>Password Vault. Page 6 of 12
7 3. Acting on Search Results Follow these steps to manage any PII- related files through Identity Finder. Windows With the Identity Finder Search Summary box displayed, click one of the following options: Wizard - Choose this option to have Identity Finder help you manage the results using the wizard. Advanced - Choose this option to manage the results manually. Save As - See the "Securely Saving Your Results" section of this page. Reminder - Choose this option to set a reminder to deal with the scan results at a later time. Mac The results window will be displayed after the search is complete. 1. For each item, select it and then choose the action you want to apply from the top menu items. For more detailed instruction, refer to the Actions section in this document. 2. If you wish to repeat the scan and select additional identities and locations to clean (e.g. external storage media or folder), select the Start Search Wizard from the Start button s drop down arrow, and then follow the steps included in this Manage Your Results document. Page 7 of 12
8 Securely Saving Your Results If your list of PII is extensive, you can securely save your results and manage them at a later time. The results file is automatically password- protected by your Identity Finder profile password. Follow these steps: 1. Click the Save icon (Mac: File > Save) and browse to the location where you wish to save the Identity Finder (.idf) file. The Save As dialog box appears. 2. Enter a name for your file and click Save. 3. Close the Identity Finder window. Accessing Your Saved Information 1. Ensure Identity Finder is not running. 2. Double- click the results file you previously saved. 3. Enter your Identity Finder profile password when prompted. 4. Other PII Identity Finder may not recognize some custom file formats; however, Identity Finder cleanup features can still be used to handle these files. Use the following Identity Finder Security Tools to handle files NOT listed in the Identity Finder search results: File Vault The File Vault tool allows you to secure any file on your computer even if no identity match is found in that file. To use the File Vault tool: 1. Click the Add to File Vault button on the Tools ribbon. The File Vault dialog opens. 2. Click the browse button to launch a dialog box that allows you to select any file on your computer. 3. After navigating to your desired location, click the Open button and the full path to your selected file will be displayed. 4. Then click Encrypt and you will be asked to secure the file with your profile password or other password. Page 8 of 12
9 5. Choose the appropriate options and click OK to secure your file. To open an Identity Finder File Vault file, double- click it to launch Identity Finder and then enter your profile password. File Shredder The File Shredder allows you to shred any file or folder (and all subfolders and files) on your computer, even if no Identity Match is found. 1. Click the File Shredder button. 2. When the File Shredder dialog box opens, browse to the folder or file(s) that you want to shred. IMPORTANT: YOU CANNOT UNDO THIS ACTION! Open Secure Zip Files Other Tools features include the Open secure zip files tool which allows you to open and extract (unzip) the contents of any secure zip file on your computer. This is a very useful feature if you used Secure a Compressed File or Secure a Text Based or Other File in conjunction with the Strong or Stronger encryption setting in a previous version of Identity Finder (the Secure Zip encryption from Identity Finder and prior has been replaced by File Vault encryption). To open a secure zip file: Page 9 of 12
10 1. On the Tools ribbon, click Other Tools > Other Tools. The Identity Finder Security Tools dialog appears. 2. Under the Open secure zip files section, browse to the location of the zip file, then click Open. The full path to your selected file will be displayed. 3. Browse to the desired target location for the unzipped files. After navigating to your desired location, click OK and the full path to your selected folder will be displayed. 4. Type your password and click Extract. Your files will be extracted to the desired location and a window will open to display the extracted files. 5. Click Close to exit the Identity Finder Security Tools window. Note (Mac Only): Identity Finder for Mac doesn't offer the Shred File tool for shredding files that aren't found in search results, although it does offer file encryption/decryption. By clicking on the Vault icon on the tool bar, you can encrypt and decrypt any file using the Identity Finder Vault format. The Identity Finder Vault file type is automatically associated with Identity Finder, so double clicking an Identity Finder Vault file will open it in Identity Finder and prompt you for the password. Page 10 of 12
11 5. Handling Outlook Items If you are using Outlook (prior to outlook 2010) or other Exchange clients, Identity Finder will locate PII stored in your Cyrus account. Follow these steps to handle your Outlook items: 1. When the Identity Finder scan completes, files and data locations that contain PII are listed. Click Next. 2. You will be prompted to establish a password for your Outlook Data File, select No and then click Next. 3. To view more information for each item, select it; details appear in the Preview pane. You can also select the item, and then select Open from the menu bar to view details. 4. You can choose to Secure, Shred or Ignore each item. Note: If the messages you shred are from a Cyrus account, the message will be marked for deletion, but not erased. To delete the messages, launch Outlook, select your Cyrus Inbox, and then select Edit > Purge Deleted Messages. 5. If you need to retain the content of s that contain PII, we suggest that you save the Outlook message as a text file or an MS Word document and use Identity Finder's Secure File option. Note: The Quarantine clean up action is not available for Outlook messages. Remove Outlook Password Once you are finished handling your Outlook items, be sure to remove your Outlook password; follow these steps: 1. Launch Outlook. 2. Select Tools > Account settings. 3. The Account Settings dialog box appears. Select your Cyrus account and then click Change. Page 11 of 12
12 4. The Change account dialog box appears. Under the Logon information, deselect the Remember password checkbox. 5. Click Next. 6. Click Finish. Page 12 of 12
Identity Finder Setup
 Identity Finder Information Sheet for MAC This document will walk you through how to install, scan, and secure any SI found on your computer, or storage devices using the Identity Finder Software. This
Identity Finder Information Sheet for MAC This document will walk you through how to install, scan, and secure any SI found on your computer, or storage devices using the Identity Finder Software. This
MS Word 2007. Microsoft Outlook 2010 Mailbox Maintenance
 MS Word 2007 Microsoft Outlook 2010 Mailbox Maintenance INTRODUCTION... 1 Understanding the MS Outlook Mailbox... 1 BASIC MAILBOX MAINTENANCE... 1 Mailbox Cleanup... 1 Check Your Mailbox Size... 1 AutoDelete
MS Word 2007 Microsoft Outlook 2010 Mailbox Maintenance INTRODUCTION... 1 Understanding the MS Outlook Mailbox... 1 BASIC MAILBOX MAINTENANCE... 1 Mailbox Cleanup... 1 Check Your Mailbox Size... 1 AutoDelete
To successfully initialize Microsoft Outlook (Outlook) the first time, email settings need to be verified.
 TO: UAN CLIENTS FROM: UAN STAFF DATE: OCTOBER 8, 2008 SUBJECT: Steps for Initial Setup of Microsoft Outlook To successfully initialize Microsoft Outlook (Outlook) the first time, email settings need to
TO: UAN CLIENTS FROM: UAN STAFF DATE: OCTOBER 8, 2008 SUBJECT: Steps for Initial Setup of Microsoft Outlook To successfully initialize Microsoft Outlook (Outlook) the first time, email settings need to
To add files to your email, first create the email. When you have opened a new email:
 Email attachments You can send files, folders and other items within an email along with the mail message itself. Items which have been added to emails are called attachments. Adding an attachment to an
Email attachments You can send files, folders and other items within an email along with the mail message itself. Items which have been added to emails are called attachments. Adding an attachment to an
REDUCING YOUR MICROSOFT OUTLOOK MAILBOX SIZE
 There are several ways to eliminate having too much email on the Exchange mail server. To reduce your mailbox size it is recommended that you practice the following tasks: Delete items from your Mailbox:
There are several ways to eliminate having too much email on the Exchange mail server. To reduce your mailbox size it is recommended that you practice the following tasks: Delete items from your Mailbox:
NTFS Undelete User Manual
 NTFS Undelete User Manual What is NTFS Undelete? NTFS Undelete is a small utility that scans your hard drive for all files that can be undeleted and attempts to recover them for you. Sounds like magic?
NTFS Undelete User Manual What is NTFS Undelete? NTFS Undelete is a small utility that scans your hard drive for all files that can be undeleted and attempts to recover them for you. Sounds like magic?
Archiving and Managing Your Mailbox
 Archiving and Managing Your Mailbox We Need You to Do Your Part We ask everyone to participate in routinely cleaning out their mailbox. Large mailboxes with thousands of messages impact backups and may
Archiving and Managing Your Mailbox We Need You to Do Your Part We ask everyone to participate in routinely cleaning out their mailbox. Large mailboxes with thousands of messages impact backups and may
Creating Digital Signatures
 About Security You can secure a PDF using any of the following security methods: Add passwords and set security options to restrict opening, editing, and printing PDFs. Encrypt a document so that only
About Security You can secure a PDF using any of the following security methods: Add passwords and set security options to restrict opening, editing, and printing PDFs. Encrypt a document so that only
Check current version of Remote Desktop Connection for Mac.. Page 2. Remove Old Version Remote Desktop Connection..Page 8
 CONTENTS SECTION 1 Check current version of Remote Desktop Connection for Mac.. Page 2 SECTION 2 Remove Old Version Remote Desktop Connection..Page 8 SECTION 3 Download and Install Remote Desktop Connection
CONTENTS SECTION 1 Check current version of Remote Desktop Connection for Mac.. Page 2 SECTION 2 Remove Old Version Remote Desktop Connection..Page 8 SECTION 3 Download and Install Remote Desktop Connection
You may have been given a download link on your trial software email. Use this link to download the software.
 BackupVault / Attix5 Server Quickstart Guide This document takes about 5 minutes to read and will show you how to: Download the software Install the Attix5 Professional Backup software Backup your files
BackupVault / Attix5 Server Quickstart Guide This document takes about 5 minutes to read and will show you how to: Download the software Install the Attix5 Professional Backup software Backup your files
How to install and use the File Sharing Outlook Plugin
 How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
Importing Contacts to Outlook
 Importing Contacts to Outlook 1. The first step is to create a file of your contacts from the National Chapter Database. 2. You create this file under Reporting, Multiple. You will follow steps 1 and 2
Importing Contacts to Outlook 1. The first step is to create a file of your contacts from the National Chapter Database. 2. You create this file under Reporting, Multiple. You will follow steps 1 and 2
Salesforce Training Logging into Salesforce SALESFORCE LOGIN
 SALESFORCE LOGIN These instructions are for new users of Salesforce. Complete all the instructions below for proper functionality. If using multiple computers to access Salesforce, it is necessary to complete
SALESFORCE LOGIN These instructions are for new users of Salesforce. Complete all the instructions below for proper functionality. If using multiple computers to access Salesforce, it is necessary to complete
Online Backup Client User Manual
 For Mac OS X Software version 4.1.7 Version 2.2 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by other means.
For Mac OS X Software version 4.1.7 Version 2.2 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by other means.
Outlook 2013 ~ e Mail Quick Tips
 The Ribbon: Home tab New Email to send a new mail New Items to send a new mail, a new appointment, a new meeting, a new contact, a new task, a new Lync Meeting Ignore to ignore a request Clean Up to clean
The Ribbon: Home tab New Email to send a new mail New Items to send a new mail, a new appointment, a new meeting, a new contact, a new task, a new Lync Meeting Ignore to ignore a request Clean Up to clean
Instructions to connect to GRCC Remote Access using a Macintosh computer
 Instructions to connect to GRCC Remote Access using a Macintosh computer 1. Install client: Download and install the Citrix ICA Client for Mac. 2. Import certificates: Download the current GlobalSign root
Instructions to connect to GRCC Remote Access using a Macintosh computer 1. Install client: Download and install the Citrix ICA Client for Mac. 2. Import certificates: Download the current GlobalSign root
Configuring Mozilla Thunderbird to Access Your SAS Email Account
 Configuring Mozilla Thunderbird to Access Your SAS Email Account 1. When you launch Thunderbird for the first time, the Import Wizard will appear: If Thunderbird detects that another email program was
Configuring Mozilla Thunderbird to Access Your SAS Email Account 1. When you launch Thunderbird for the first time, the Import Wizard will appear: If Thunderbird detects that another email program was
User guide. Business Email
 User guide Business Email June 2013 Contents Introduction 3 Logging on to the UC Management Centre User Interface 3 Exchange User Summary 4 Downloading Outlook 5 Outlook Configuration 6 Configuring Outlook
User guide Business Email June 2013 Contents Introduction 3 Logging on to the UC Management Centre User Interface 3 Exchange User Summary 4 Downloading Outlook 5 Outlook Configuration 6 Configuring Outlook
Backing up Microsoft Outlook Email For the PC Using MS Outlook 2000 Keith Roberts
 WIN1020 November 2003 Backing up Microsoft Outlook Email For the PC Using MS Outlook 2000 Keith Roberts INTRODUCTION... 1 PREPARATION... 1 BACKING UP EMAIL... 2 RESTORING EMAIL FROM A PERSONAL FILE FOLDER...
WIN1020 November 2003 Backing up Microsoft Outlook Email For the PC Using MS Outlook 2000 Keith Roberts INTRODUCTION... 1 PREPARATION... 1 BACKING UP EMAIL... 2 RESTORING EMAIL FROM A PERSONAL FILE FOLDER...
Introduction to the MISD Web FTP Client
 Introduction to the MISD Web FTP Client What is FTP? FTP stands for File Transfer Protocol. It is an Internet service that allows users to copy files to or from computers which hold collections of files.
Introduction to the MISD Web FTP Client What is FTP? FTP stands for File Transfer Protocol. It is an Internet service that allows users to copy files to or from computers which hold collections of files.
Information & Communication Technologies FTP and GroupWise Archives Wilfrid Laurier University
 Instructions for MAC users MAC users have not been joined to the Active Directory Domain. ICT is unable to capture GroupWise archives you may have on your computer automatically or confirm if you have
Instructions for MAC users MAC users have not been joined to the Active Directory Domain. ICT is unable to capture GroupWise archives you may have on your computer automatically or confirm if you have
USER GUIDE. Unit 2: Synergy. Chapter 2: Using Schoolwires Synergy
 USER GUIDE Unit 2: Synergy Chapter 2: Using Schoolwires Synergy Schoolwires Synergy & Assist Version 2.0 TABLE OF CONTENTS Introductions... 1 Audience... 1 Objectives... 1 Before You Begin... 1 Getting
USER GUIDE Unit 2: Synergy Chapter 2: Using Schoolwires Synergy Schoolwires Synergy & Assist Version 2.0 TABLE OF CONTENTS Introductions... 1 Audience... 1 Objectives... 1 Before You Begin... 1 Getting
Outlook Email. Moving and deleting email. Moving emails
 Moving and deleting email Email is stored in a series of folders within your email account. To make it easier to find and manage important emails, you may wish to move them between folders. For less important
Moving and deleting email Email is stored in a series of folders within your email account. To make it easier to find and manage important emails, you may wish to move them between folders. For less important
Baylor Secure Messaging. For Non-Baylor Users
 Baylor Secure Messaging For Non-Baylor Users TABLE OF CONTENTS SECTION ONE: GETTING STARTED...4 Receiving a Secure Message for the First Time...4 Password Configuration...5 Logging into Baylor Secure Messaging...7
Baylor Secure Messaging For Non-Baylor Users TABLE OF CONTENTS SECTION ONE: GETTING STARTED...4 Receiving a Secure Message for the First Time...4 Password Configuration...5 Logging into Baylor Secure Messaging...7
Outlook 2013 ~ Advanced
 Mail Using Categories 1. Select the message that for the category. 2. Select the appropriate category. 3. The category color displays next to the message. Renaming Categories 1. Select a message. 2. Select
Mail Using Categories 1. Select the message that for the category. 2. Select the appropriate category. 3. The category color displays next to the message. Renaming Categories 1. Select a message. 2. Select
Online Backup Client User Manual Mac OS
 Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS
 Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Creating a New Digital ID or Signature for Adobe Acrobat
 Creating a New Digital ID or Signature for Adobe Acrobat If you are not using a third-party digital ID, you can create your own in Adobe Acrobat Professional or in Adobe Reader 9, 10 or X. Follow these
Creating a New Digital ID or Signature for Adobe Acrobat If you are not using a third-party digital ID, you can create your own in Adobe Acrobat Professional or in Adobe Reader 9, 10 or X. Follow these
Configuring Outlook 2013 For IMAP Connections
 Configuring Outlook 2013 For IMAP Connections VERSION 1.0 1 P a g e U A C o n n e c t C o n f i g u r i n g O u t l o o k 2013 f o r I M A P 12/2013 Configuring Outlook 2013 for IMAP Connections Overview
Configuring Outlook 2013 For IMAP Connections VERSION 1.0 1 P a g e U A C o n n e c t C o n f i g u r i n g O u t l o o k 2013 f o r I M A P 12/2013 Configuring Outlook 2013 for IMAP Connections Overview
Email Basics. a. Click the arrow to the right of the Options button, and then click Bcc.
 Email Basics Add CC or BCC You can display the Bcc box in all new messages that you compose. In a new message, do one of the following: 1. If Microsoft Word is your e-mail editor a. Click the arrow to
Email Basics Add CC or BCC You can display the Bcc box in all new messages that you compose. In a new message, do one of the following: 1. If Microsoft Word is your e-mail editor a. Click the arrow to
CONTENTS. Introduction... 3. Outlook at a glance... 3. Configure Outlook 2010 on-campus... 3. Creating Folders... 4. Sorting Emails...
 OFFICE OF INFORMATION TECHNOLOGY Academic Technology Unit Microsoft Outlook 2010 Basics Workbook CONTENTS Introduction... 3 Outlook at a glance... 3 Configure Outlook 2010 on-campus... 3 Creating Folders...
OFFICE OF INFORMATION TECHNOLOGY Academic Technology Unit Microsoft Outlook 2010 Basics Workbook CONTENTS Introduction... 3 Outlook at a glance... 3 Configure Outlook 2010 on-campus... 3 Creating Folders...
Division of School Facilities OUTLOOK WEB ACCESS
 Division of School Facilities OUTLOOK WEB ACCESS New York City Department of Education Office of Enterprise Development and Support Applications Support Group 2011 HELPFUL HINTS OWA Helpful Hints was created
Division of School Facilities OUTLOOK WEB ACCESS New York City Department of Education Office of Enterprise Development and Support Applications Support Group 2011 HELPFUL HINTS OWA Helpful Hints was created
owncloud Configuration and Usage Guide
 owncloud Configuration and Usage Guide This guide will assist you with configuring and using YSUʼs Cloud Data storage solution (owncloud). The setup instructions will include how to navigate the web interface,
owncloud Configuration and Usage Guide This guide will assist you with configuring and using YSUʼs Cloud Data storage solution (owncloud). The setup instructions will include how to navigate the web interface,
Primavera P6 Professional Windows 8 Installation Instructions. Primavera P6. Installation Instructions. For Windows 8 Users
 Primavera P6 Installation Instructions For Windows 8 Users 1 IMPORTANT: READ THESE INSTRUCTIONS CAREFULLY AND FOLLOW THEM EXACTLY. The following is provided for your convenience only. Ten Six Consulting
Primavera P6 Installation Instructions For Windows 8 Users 1 IMPORTANT: READ THESE INSTRUCTIONS CAREFULLY AND FOLLOW THEM EXACTLY. The following is provided for your convenience only. Ten Six Consulting
Contents. Getting Started...1. Managing Your Drives...14. Backing Up & Restoring Folders...28. Synchronizing Folders...48. Managing Security...
 Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
Outlook Web Access Tipsheets
 You can use a Web browser to access your Outlook mailbox from any computer with an Internet connection. You can use Outlook Web Access with Microsoft Internet Explorer, Mozilla Firefox and many other browsers.
You can use a Web browser to access your Outlook mailbox from any computer with an Internet connection. You can use Outlook Web Access with Microsoft Internet Explorer, Mozilla Firefox and many other browsers.
1. Open Thunderbird. If the Import Wizard window opens, select Don t import anything and click Next and go to step 3.
 Thunderbird The changes that need to be made in the email programs will be the following: Incoming mail server: newmail.one-eleven.net Outgoing mail server (SMTP): newmail.one-eleven.net You will also
Thunderbird The changes that need to be made in the email programs will be the following: Incoming mail server: newmail.one-eleven.net Outgoing mail server (SMTP): newmail.one-eleven.net You will also
Understanding Files and Folders
 Windows Files and Folders Overview Before I get into Windows XP's method of file management, let's spend a little space on a files and folder refresher course. (Just in case you forgot, of course.) The
Windows Files and Folders Overview Before I get into Windows XP's method of file management, let's spend a little space on a files and folder refresher course. (Just in case you forgot, of course.) The
OUTLOOK WEB APP (OWA): MAIL
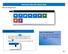 Office 365 Navigation Pane: Navigating in Office 365 Click the App Launcher and then choose the application (i.e. Outlook, Calendar, People, etc.). To modify your personal account settings, click the Logon
Office 365 Navigation Pane: Navigating in Office 365 Click the App Launcher and then choose the application (i.e. Outlook, Calendar, People, etc.). To modify your personal account settings, click the Logon
For example, you might want to create a folder to collect together all emails relating to a particular project or subject.
 Email folders Outlook uses a series of folders such as the inbox, outbox, drafts and sent items to sort your email into collections according to the status of the message. If the folders which are already
Email folders Outlook uses a series of folders such as the inbox, outbox, drafts and sent items to sort your email into collections according to the status of the message. If the folders which are already
Lenovo Online Data Backup User Guide Version 1.8.14
 Lenovo Online Data Backup User Guide Version 1.8.14 Contents Chapter 1: Installing Lenovo Online Data Backup...5 Downloading the Lenovo Online Data Backup Client...5 Installing the Lenovo Online Data
Lenovo Online Data Backup User Guide Version 1.8.14 Contents Chapter 1: Installing Lenovo Online Data Backup...5 Downloading the Lenovo Online Data Backup Client...5 Installing the Lenovo Online Data
Instructions for Importing (migrating) Data
 Instructions for Importing (migrating) Data from CTAS Version 7 to CTAS Version 8 For Windows 8 and 8.1 CTAS Version 8 is designed to work with your Version 7 data if you choose to. These instructions
Instructions for Importing (migrating) Data from CTAS Version 7 to CTAS Version 8 For Windows 8 and 8.1 CTAS Version 8 is designed to work with your Version 7 data if you choose to. These instructions
Clean Up Email Rules Quick Steps Search Tools Change Views Export Data Convert email to tasks Contact Groups. Outlook Functions
 Clean Up Email Rules Quick Steps Search Tools Change Views Export Data Convert email to tasks Contact Groups Outlook Functions Clean Up: New ways to manage conversations and remove redundant emails: Email
Clean Up Email Rules Quick Steps Search Tools Change Views Export Data Convert email to tasks Contact Groups Outlook Functions Clean Up: New ways to manage conversations and remove redundant emails: Email
MS Outlook 2002/2003. V1.0 BullsEye Telecom Email
 IMAP Settings Manual Our application allows you to access your email in many different ways. For those of you who do not wish to use the Webmail interface, you may also manage your email and custom folder
IMAP Settings Manual Our application allows you to access your email in many different ways. For those of you who do not wish to use the Webmail interface, you may also manage your email and custom folder
Outlook 2010 Archiving Email CPAC Workshop Summer 2014
 Outlook 2010 Archiving Email CPAC Workshop Summer 2014 Presenters: Kaleo Kelikani and Linda Holdzkom, ITS Technical Services Contents Tips and Tools for the Desktop Version of Outlook Page 2-4 What is
Outlook 2010 Archiving Email CPAC Workshop Summer 2014 Presenters: Kaleo Kelikani and Linda Holdzkom, ITS Technical Services Contents Tips and Tools for the Desktop Version of Outlook Page 2-4 What is
How To Restore Your Data On A Backup By Mozy (Windows) On A Pc Or Macbook Or Macintosh (Windows 2) On Your Computer Or Mac) On An Pc Or Ipad (Windows 3) On Pc Or Pc Or Micro
 Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Email at Bradford - Outlook
 This document provides guidance for staff using Office 365 with Microsoft Outlook 2010 for email at the University of Bradford. The University of Bradford retains copyright for this material, which may
This document provides guidance for staff using Office 365 with Microsoft Outlook 2010 for email at the University of Bradford. The University of Bradford retains copyright for this material, which may
Outlook Archiving and Storage
 Outlook Archiving and Storage This document provides information related to storing and archiving e-mail in Outlook, including Outlook s auto archive feature, techniques for avoiding reaching your mailbox
Outlook Archiving and Storage This document provides information related to storing and archiving e-mail in Outlook, including Outlook s auto archive feature, techniques for avoiding reaching your mailbox
VPN Remote Access Installation and Configuration Guide Operating System: Windows (XP, Vista, 7 and 8)
 INFORMATION SYSTEMS SERVICE NETWORKS AND COMMUNICATIONS SECTOR VPN Remote Access Installation and Configuration Guide Operating System: Windows (XP, Vista, 7 and 8) ΥΠΣ ΕΔ/50 November 2012 A. INSTALLATION
INFORMATION SYSTEMS SERVICE NETWORKS AND COMMUNICATIONS SECTOR VPN Remote Access Installation and Configuration Guide Operating System: Windows (XP, Vista, 7 and 8) ΥΠΣ ΕΔ/50 November 2012 A. INSTALLATION
Outlook Web Access An Introductory Guide
 Outlook Web Access An Introductory Guide IT Training & Assessment Unit, Queen s University Belfast 1 Contents Logging on... 3 Email... 3 Compose a Message... 4 Saving an Email Attachment... 5 Saving a
Outlook Web Access An Introductory Guide IT Training & Assessment Unit, Queen s University Belfast 1 Contents Logging on... 3 Email... 3 Compose a Message... 4 Saving an Email Attachment... 5 Saving a
MANAGING OUTLOOK PERSONAL DATA FILES
 MANAGING OUTLOOK PERSONAL DATA FILES 21 March 2009, Version 1.1 CONTENTS This document covers the following topics: Background Automatically Associating Old Data Files with Current Outlook Profile Manually
MANAGING OUTLOOK PERSONAL DATA FILES 21 March 2009, Version 1.1 CONTENTS This document covers the following topics: Background Automatically Associating Old Data Files with Current Outlook Profile Manually
Using an Automatic Back Up for Outlook 2003 and Outlook 2007 Personal Folders
 Using an Automatic Back Up for Outlook 2003 and Outlook 2007 Personal Folders Part 1 Install the Personal Folder Backup Utility Note: You should close Outlook and any other applications before installing
Using an Automatic Back Up for Outlook 2003 and Outlook 2007 Personal Folders Part 1 Install the Personal Folder Backup Utility Note: You should close Outlook and any other applications before installing
Initial Setup of Mozilla Thunderbird with IMAP for OS X Lion
 Initial Setup of Mozilla Thunderbird Concept This document describes the procedures for setting up the Mozilla Thunderbird email client to download messages from Google Mail using Internet Message Access
Initial Setup of Mozilla Thunderbird Concept This document describes the procedures for setting up the Mozilla Thunderbird email client to download messages from Google Mail using Internet Message Access
ProjectWise Explorer V8i User Manual for Subconsultants & Team Members
 ProjectWise Explorer V8i User Manual for Subconsultants & Team Members submitted to Michael Baker International Subconsultants & Team Members submitted by Michael Baker International ProjectWise Support
ProjectWise Explorer V8i User Manual for Subconsultants & Team Members submitted to Michael Baker International Subconsultants & Team Members submitted by Michael Baker International ProjectWise Support
1. Product Information
 ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
Archiving Your Mail in Outlook 2010
 About Archiving Archiving Your Mail in Outlook 2010 All messages, contact information, calendars and other data you create in Microsoft Outlook 2010 are kept in your mailbox on the Exchange server. But
About Archiving Archiving Your Mail in Outlook 2010 All messages, contact information, calendars and other data you create in Microsoft Outlook 2010 are kept in your mailbox on the Exchange server. But
Email User Manual. [Outlook Web App 2013]
![Email User Manual. [Outlook Web App 2013] Email User Manual. [Outlook Web App 2013]](/thumbs/30/14055838.jpg) [Outlook Web App 2013] Central Information Systems Division March 2014 Table of Contents 1. To Login... 4 2. To Logout... 5 3. Change Password... 5 4. Email Messaging... 6 4.1 Create a New Mail... 6 4.2
[Outlook Web App 2013] Central Information Systems Division March 2014 Table of Contents 1. To Login... 4 2. To Logout... 5 3. Change Password... 5 4. Email Messaging... 6 4.1 Create a New Mail... 6 4.2
OS X 10.6 SNOW LEOPARD: KEYCHAIN ACCESS MANAGING & UNDERSTANDING KEYCHAIN
 OS X 10.6 SNOW LEOPARD: KEYCHAIN ACCESS MANAGING & UNDERSTANDING KEYCHAIN MANAGING KEYCHAINS Mac OS X features a sophisticated system that automatically protects all your authentication assets in encrypted
OS X 10.6 SNOW LEOPARD: KEYCHAIN ACCESS MANAGING & UNDERSTANDING KEYCHAIN MANAGING KEYCHAINS Mac OS X features a sophisticated system that automatically protects all your authentication assets in encrypted
Online Backup Client User Manual Linux
 Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
CHARTER BUSINESS custom hosting faqs 2010 INTERNET. Q. How do I access my email? Q. How do I change or reset a password for an email account?
 Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
BitLocker to Go: Encryption for personal USB flash drives (Windows 7 and 8)
 BitLocker to Go: Encryption for personal USB flash drives (Windows 7 and 8) Encryption is an effective method of protecting data stored on portable devices such as USB flash drives and external hard drives.
BitLocker to Go: Encryption for personal USB flash drives (Windows 7 and 8) Encryption is an effective method of protecting data stored on portable devices such as USB flash drives and external hard drives.
Using the City of Stamford / Stamford Public Schools. Web Email System
 Using the City of Stamford / Stamford Public Schools Web Email System Open the Login Screen: Go to the following site: www.stamfordct.gov/mail and choose the login link. The login screen will look like
Using the City of Stamford / Stamford Public Schools Web Email System Open the Login Screen: Go to the following site: www.stamfordct.gov/mail and choose the login link. The login screen will look like
Neoteris IVE Integration Guide
 Neoteris IVE Integration Guide Published Date July 2015 The Secure Email Client upgrade option enables Neoteris IVE users to use standards based email clients to access corporate email from remote locations.
Neoteris IVE Integration Guide Published Date July 2015 The Secure Email Client upgrade option enables Neoteris IVE users to use standards based email clients to access corporate email from remote locations.
Junk E-mail Settings. Options
 Outlook 2003 includes a new Junk E-mail Filter. It is active, by default, and the protection level is set to low. The most obvious junk e-mail messages are caught and moved to the Junk E-Mail folder. Use
Outlook 2003 includes a new Junk E-mail Filter. It is active, by default, and the protection level is set to low. The most obvious junk e-mail messages are caught and moved to the Junk E-Mail folder. Use
Microsoft Outlook 2010 Managing E-mail Disk Quotas
 CALIFORNIA STATE UNIVERSITY, LOS ANGELES INFORMATION TECHNOLOGY SERVICES Microsoft Outlook 2010 Managing E-mail Disk Quotas Spring 2013, Version 1.0 Table of Contents Introduction...2 Working With Outlook
CALIFORNIA STATE UNIVERSITY, LOS ANGELES INFORMATION TECHNOLOGY SERVICES Microsoft Outlook 2010 Managing E-mail Disk Quotas Spring 2013, Version 1.0 Table of Contents Introduction...2 Working With Outlook
SecureZIP User Guide
 SecureZIP User Guide SecureZIP is an application for zipping files to save storage space as well as encrypting files with password control to protect information. SecureZIP not only works alone to perform
SecureZIP User Guide SecureZIP is an application for zipping files to save storage space as well as encrypting files with password control to protect information. SecureZIP not only works alone to perform
USING STUFFIT DELUXE THE STUFFIT START PAGE CREATING ARCHIVES (COMPRESSED FILES)
 USING STUFFIT DELUXE StuffIt Deluxe provides many ways for you to create zipped file or archives. The benefit of using the New Archive Wizard is that it provides a way to access some of the more powerful
USING STUFFIT DELUXE StuffIt Deluxe provides many ways for you to create zipped file or archives. The benefit of using the New Archive Wizard is that it provides a way to access some of the more powerful
WHAT S NEW IN OUTLOOK 2010 & HOW TO CUSTOMIZE IT
 WHAT S NEW IN OUTLOOK 2010 & HOW TO CUSTOMIZE IT THE RIBBON... 2 CONTEXTUAL TABS... 4 THE FILE TAB... 4 DIALOG BOXES... 5 MINIMIZING THE RIBBON... 5 CUSTOMIZING THE RIBBON... 6 CUSTOMIZING THE QUICK ACCESS
WHAT S NEW IN OUTLOOK 2010 & HOW TO CUSTOMIZE IT THE RIBBON... 2 CONTEXTUAL TABS... 4 THE FILE TAB... 4 DIALOG BOXES... 5 MINIMIZING THE RIBBON... 5 CUSTOMIZING THE RIBBON... 6 CUSTOMIZING THE QUICK ACCESS
Online Backup and Recovery Manager Setup for Microsoft Windows.
 Online Backup and Recovery Manager Setup for Microsoft Windows. Backup Wizard Default Interface Recovery Wizard Online Backup and Recovery Manager Setup Backup Wizard After installing and launching the
Online Backup and Recovery Manager Setup for Microsoft Windows. Backup Wizard Default Interface Recovery Wizard Online Backup and Recovery Manager Setup Backup Wizard After installing and launching the
PGP Zip Self-Decrypting Archive (SDA) 5/29/2012 Version 1.1
 PGP Zip Self-Decrypting Archive (SDA) 5/29/2012 Version 1.1 Table of Contents 1 Self Decrypting Archives (SDA)... 1-2 2 Setting Windows to Display File Extensions... 2-3 3 Creating PGP Zip SDA... 3-4
PGP Zip Self-Decrypting Archive (SDA) 5/29/2012 Version 1.1 Table of Contents 1 Self Decrypting Archives (SDA)... 1-2 2 Setting Windows to Display File Extensions... 2-3 3 Creating PGP Zip SDA... 3-4
HADS 2.1.0e Installation and migration
 Ageing, Disability and Home Care, Department of Family and Community Services MDS fact sheet - February 2012 HADS 2.1.0e Installation and migration Caution! If at any stage during this process you receive
Ageing, Disability and Home Care, Department of Family and Community Services MDS fact sheet - February 2012 HADS 2.1.0e Installation and migration Caution! If at any stage during this process you receive
A Presentation of TeachUcomp Incorporated. Copyright TeachUcomp, Inc. 2013. Mastering Outlook Made Easy for Lawyers CPE Edition v.2.
 A Presentation of TeachUcomp Incorporated. Copyright TeachUcomp, Inc. 2013 Mastering Outlook Made Easy for Lawyers CPE Edition v.2.0 TeachUcomp, Inc. it s all about you Copyright: Copyright 2013 by TeachUcomp,
A Presentation of TeachUcomp Incorporated. Copyright TeachUcomp, Inc. 2013 Mastering Outlook Made Easy for Lawyers CPE Edition v.2.0 TeachUcomp, Inc. it s all about you Copyright: Copyright 2013 by TeachUcomp,
Sample- for evaluation purposes only! Advanced Outlook. TeachUcomp, Inc. A Presentation of TeachUcomp Incorporated. Copyright TeachUcomp, Inc.
 A Presentation of TeachUcomp Incorporated. Copyright TeachUcomp, Inc. 2012 Advanced Outlook TeachUcomp, Inc. it s all about you Copyright: TeachUcomp, Inc. Phone: (877) 925-8080 Web: http://www.teachucomp.com
A Presentation of TeachUcomp Incorporated. Copyright TeachUcomp, Inc. 2012 Advanced Outlook TeachUcomp, Inc. it s all about you Copyright: TeachUcomp, Inc. Phone: (877) 925-8080 Web: http://www.teachucomp.com
Live@edu User Guide. Please visit the Helpdesk website for more information: http://www.smu.edu.sg/iits/helpdesk_support/index.asp
 IITS Main Office SINGAPORE MANAGEMENT UNIVERSITY Administration Building, Level 11 81, Victoria Street Singapore 188065 Phone: 65-6828 1930 Email: [email protected] Please visit the Helpdesk website for
IITS Main Office SINGAPORE MANAGEMENT UNIVERSITY Administration Building, Level 11 81, Victoria Street Singapore 188065 Phone: 65-6828 1930 Email: [email protected] Please visit the Helpdesk website for
Changes to Skillnet Group Emails. Outlook and Outlook Express Users
 Changes to Skillnet Group Emails Skillnet Group emails are moving from the current provider to our own exchange mail server. This will mean that you will have a much improved web-mail system and almost
Changes to Skillnet Group Emails Skillnet Group emails are moving from the current provider to our own exchange mail server. This will mean that you will have a much improved web-mail system and almost
Neoteris IVE Integration Guide
 Neoteris IVE Integration Guide NESD-00090-00 CAY051402 The Secure Email Client upgrade option enables Neoteris IVE users to use standardsbased email clients to access corporate email from remote locations.
Neoteris IVE Integration Guide NESD-00090-00 CAY051402 The Secure Email Client upgrade option enables Neoteris IVE users to use standardsbased email clients to access corporate email from remote locations.
The online email environment
 The online email environment These are the options for the selected application. Navigation Pane is comprised of a folders list and oneclick access to your Inbox, Calendar, Contacts, and Tasks folders
The online email environment These are the options for the selected application. Navigation Pane is comprised of a folders list and oneclick access to your Inbox, Calendar, Contacts, and Tasks folders
ACS EPF Download Manager Technical Guide. Table of Contents
 Table of Contents Introduction... 3 Administration... 3 Disclaimer... 3 System Requirements... 3 Software Download... 3 Software Installation... 4 Preparing for the Installation... 4 Unzip the Software
Table of Contents Introduction... 3 Administration... 3 Disclaimer... 3 System Requirements... 3 Software Download... 3 Software Installation... 4 Preparing for the Installation... 4 Unzip the Software
Instructions For Opening UHA Encrypted Email
 Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
Working With Your FTP Site
 Working With Your FTP Site Welcome to your FTP Site! The UnlimitedFTP (UFTP) software will allow you to run from any web page using Netscape, Internet Explorer, Opera, Mozilla or Safari browsers. It can
Working With Your FTP Site Welcome to your FTP Site! The UnlimitedFTP (UFTP) software will allow you to run from any web page using Netscape, Internet Explorer, Opera, Mozilla or Safari browsers. It can
MAC/OSX - How to Encrypt Data using TrueCrypt. v.05201011
 MAC/OSX - How to Encrypt Data using TrueCrypt v.05201011 This chapter contains step-by-step instructions on how to create, mount, and use a TrueCrypt volume. We strongly recommend that you read the entire
MAC/OSX - How to Encrypt Data using TrueCrypt v.05201011 This chapter contains step-by-step instructions on how to create, mount, and use a TrueCrypt volume. We strongly recommend that you read the entire
Lotus Notes Client Version 8.5 Reference Guide
 Lotus Notes Client Version 8.5 Reference Guide rev. 11/19/2009 1 Lotus Notes Client Version 8.5 Reference Guide Accessing the Lotus Notes Client From your desktop, double click the Lotus Notes icon. Logging
Lotus Notes Client Version 8.5 Reference Guide rev. 11/19/2009 1 Lotus Notes Client Version 8.5 Reference Guide Accessing the Lotus Notes Client From your desktop, double click the Lotus Notes icon. Logging
Motion Computing Tablet PC
 Motion Computing Tablet PC TRUSTED PLATFORM MODULE (TPM) ACTIVATION User Guide Trusted Platform Module Activation With the Infineon Security Platform Tools and the built-in Trusted Computing Group compliant
Motion Computing Tablet PC TRUSTED PLATFORM MODULE (TPM) ACTIVATION User Guide Trusted Platform Module Activation With the Infineon Security Platform Tools and the built-in Trusted Computing Group compliant
Detecting and Removing Spyware From Your Home Computer
 Detecting and Removing Spyware From Your Home Computer Preamble: Spyware are programs that silently monitor and report on computing activities via the Internet. Companies use Spyware to target users with
Detecting and Removing Spyware From Your Home Computer Preamble: Spyware are programs that silently monitor and report on computing activities via the Internet. Companies use Spyware to target users with
PGP Desktop Email Quick Start Guide version 9.6
 What is PGP Desktop Email? PGP Desktop Email is part of the PGP Desktop family of products. You can use PGP Desktop Email to: Automatically and transparently encrypt, sign, decrypt, and verify email messages
What is PGP Desktop Email? PGP Desktop Email is part of the PGP Desktop family of products. You can use PGP Desktop Email to: Automatically and transparently encrypt, sign, decrypt, and verify email messages
Information Systems Services. Getting Started with Enterprise Vault Email Archiving A guide for Outlook/Exchange users March 2008
 Information Systems Services Getting Started with Enterprise Vault Email Archiving March 2008 Contents 1. Introduction... 3 2. Supported operating systems, email clients and browsers... 3 3. Getting started
Information Systems Services Getting Started with Enterprise Vault Email Archiving March 2008 Contents 1. Introduction... 3 2. Supported operating systems, email clients and browsers... 3 3. Getting started
Using Microsoft Office 2013: Outlook. Gerry Kruyer
 Using Microsoft Office 2013: Outlook Table of Contents Outlook 2013 Ribbon... 4 Viewing Inbox... 4 Folders... 4 Home Tab... 5 Background Colour and Themes... 5 Inbox... 6 Reading Pane... 6 Turn off/on
Using Microsoft Office 2013: Outlook Table of Contents Outlook 2013 Ribbon... 4 Viewing Inbox... 4 Folders... 4 Home Tab... 5 Background Colour and Themes... 5 Inbox... 6 Reading Pane... 6 Turn off/on
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE
 CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
Archiving Your Mail in Outlook 2007
 About Archiving Archiving Your Mail in Outlook 2007 All messages, contact information, calendars and other data you create in Microsoft Outlook 2007 are kept in your mailbox on the Exchange (FIUmail) server.
About Archiving Archiving Your Mail in Outlook 2007 All messages, contact information, calendars and other data you create in Microsoft Outlook 2007 are kept in your mailbox on the Exchange (FIUmail) server.
Installing S500 Power Monitor Software and LabVIEW Run-time Engine
 EigenLight S500 Power Monitor Software Manual Software Installation... 1 Installing S500 Power Monitor Software and LabVIEW Run-time Engine... 1 Install Drivers for Windows XP... 4 Install VISA run-time...
EigenLight S500 Power Monitor Software Manual Software Installation... 1 Installing S500 Power Monitor Software and LabVIEW Run-time Engine... 1 Install Drivers for Windows XP... 4 Install VISA run-time...
Before You Begin: NOTE: Please read each step of these instructions carefully as not all steps include accompanying pictures.
 This document will walk you through the process of migrating your existing mail, contacts, and calendar from WOU s Webmail system to the WOU Gmail system. If you are not interested in migrating your mail,
This document will walk you through the process of migrating your existing mail, contacts, and calendar from WOU s Webmail system to the WOU Gmail system. If you are not interested in migrating your mail,
Exporting emails from Outlook Version 1.00
 Exporting emails from Outlook Version 1.00 The rapid growth in volume of emails means that there is a growing need to archive old emails to media such as external hard disks and DVD s. The document will
Exporting emails from Outlook Version 1.00 The rapid growth in volume of emails means that there is a growing need to archive old emails to media such as external hard disks and DVD s. The document will
Outlook basics. Identify user interface elements that you can use to accomplish basic tasks.
 Outlook basics Outlook is a powerful tool for managing your e-mail, contacts, calendars, and tasks. To use it most effectively, you first have to understand the basics. This tutorial introduces some of
Outlook basics Outlook is a powerful tool for managing your e-mail, contacts, calendars, and tasks. To use it most effectively, you first have to understand the basics. This tutorial introduces some of
Connecting to Remote Desktop Windows Users
 Connecting to Remote Desktop Windows Users How to log into the College Network from Home 1. Start the Remote Desktop Connection For Windows XP, Vista and Windows 7 this is found at:- Star t > All Programs
Connecting to Remote Desktop Windows Users How to log into the College Network from Home 1. Start the Remote Desktop Connection For Windows XP, Vista and Windows 7 this is found at:- Star t > All Programs
How to Use JCWHosting Reseller Cloud Storage Solution
 How to Use JCWHosting Reseller Cloud Storage Solution Go to https://www.internetspace.co.za and log in with your Cloud Reseller account username and password. How to Use create a cloud account for your
How to Use JCWHosting Reseller Cloud Storage Solution Go to https://www.internetspace.co.za and log in with your Cloud Reseller account username and password. How to Use create a cloud account for your
16.4.3 Lab: Data Backup and Recovery in Windows XP
 16.4.3 Lab: Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment The
16.4.3 Lab: Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment The
Allowing other users to view email and/or folders in Outlook (i.e., proxy access)
 Allowing other users to view email and/or folders in Outlook (i.e., proxy access) There are two ways to work with another person's Microsoft Outlook folders folder sharing and Delegate Access. 1. Folder
Allowing other users to view email and/or folders in Outlook (i.e., proxy access) There are two ways to work with another person's Microsoft Outlook folders folder sharing and Delegate Access. 1. Folder
NTI CORPORATION. NTI Backup Now EZ v3. User's Guide
 NTI CORPORATION NTI Backup Now EZ v3 NTI Backup Now EZ v3 User's Guide Backup Now EZ v3 User's Guide 2013 NTI Corporation i Table of Contents INTRODUCTION... 3 WELCOME TO NTI BACKUP NOW EZ... 5 OVERVIEW
NTI CORPORATION NTI Backup Now EZ v3 NTI Backup Now EZ v3 User's Guide Backup Now EZ v3 User's Guide 2013 NTI Corporation i Table of Contents INTRODUCTION... 3 WELCOME TO NTI BACKUP NOW EZ... 5 OVERVIEW
