Magic Quadrant for Data Masking Technology, Worldwide
|
|
|
- Rosanna West
- 10 years ago
- Views:
Transcription
1 G Magic Quadrant for Data Masking Technology, Worldwide Published: 22 December 2015 Analyst(s): Ayal Tirosh, Marc-Antoine Meunier Organizations should use data masking to protect sensitive data at rest and in transit from insiders' and outsiders' attacks. In 2015, continuous data breaches has, once again, demonstrated the growing importance of this technology market. Market Definition/Description Data masking (DM) is a technology aimed at preventing the abuse of sensitive data by giving users fictitious (yet realistic) data instead of real sensitive data. It aims to deter the misuse of data at rest, typically in nonproduction databases (static data masking [SDM]), and data in transit, typically in production databases (dynamic data masking [DDM]). SDM for relational databases remains the most demanded technology, and, in this research, we highly value vendors' Ability to Execute in the SDM space (that is, to demonstrate maturity, quality and scalability of SDM technology, as well as the high revenue from and broad adoption of it). From a Completeness of Vision viewpoint, we highly value vendors' ability to offer DDM, the masking of the big data platform and suites with multiple data security technologies, and assurance of the strength and accuracy of protection. DM is not the same as encryption or tokenization, although masking vendors may also offer encryption or tokenization. Static masking is a nonreversible process in which the data undergoes a one-way transformation. Tokenization and format-preserving encryption (FPE) are alternative methods that are designed to be reversible, but this reversibility may increase the risk of secrecy and privacy violations. DM technologies are one aspect of a broader data security governance strategy that may include other technologies, such as database audit and protection (DAP). DAP is technology focused on the implementation of data security policy, data classification and discovery, access privilege management, activity monitoring, and audit and data protection. For further information, see "Market Guide for Data-Centric Audit and Protection."
2 Magic Quadrant Figure 1. Magic Quadrant for Data Masking Technology, Worldwide Source: Gartner (December 2015) Vendor Strengths and CA Technologies (Grid-Tools) On 4 June 2015, CA Technologies announced that it had acquired Grid-Tools. CA offers an SDM tool and subsetting tool, CA Test Data Manager for Masking and Subsetting; it also offers a full test Page 2 of 27 Gartner, Inc. G
3 data management (TDM) suite, Test Data Manager, which includes DM, test data discovery, design, creation, refreshment, comparison and data management. The vendor offers SDM technology aimed at complex and large environments with a multiplicity of various, interconnected databases on mainframe relational DBMSs (RDBMSs) and Oracle NoSQL. Strengths CA (Grid-Tools) is one of the most referenced SDM vendors by Gartner clients, and is one of the major competitors to Leaders in the SDM space. CA is proven for projects that require high scalability, and also for agile development projects. CA has global reach and clientele in EMEA, the Asia/Pacific region, North America and Latin America. CA offers synthetic data generation as an alternative or addition to DM, in which case it serves to increase the completeness and accuracy of data representation in a subset of to-be-masked data. CA Test Data Manager offers highly scalable batch processing executed in parallel on multiple databases by local agents. The visual interface for CA Test Data Manager for Masking and Subsetting tool is user-friendly and attractive to clients with simpler masking needs. CA does not have its own Hadoop DM and partners with Syncsort to address this. Data is taken from the Syncsort DMX-h product, transformed into a suitable format, masked in the SDM tool and then placed back into Syncsort. This makes the masking process more complex. CA recently acquired Grid-Tools, requiring customers to monitor how well the company is integrated into CA's organization. CA offers limited DDM functionality that is applicable mostly to reporting use cases. The tool creates a parallel schema of masked data that is accessed by users who are not entitled to live data. Its stronger focus on TDM than on data security inhibits its ability to grow faster in the security space, and to compete with Leaders that have technologies besides SDM. Camouflage Camouflage packages its DM technologies into the Camouflage Xpert suite, which includes the SDM tool CX-Mask, the data discovery tool CX-Discover, the TDM tool CX-TDM and the data virtualization tool CX-Virtual (the latter in partnership with Actifio). Additionally, Camouflage offers its DDM tool CX-Dynamic and a data subsetting software solution. Gartner, Inc. G Page 3 of 27
4 The vendor provides reliable SDM, some DDM, and masking of big data that is affordable to larger and smaller enterprises. Camouflage offers DDM for Oracle Database and for XML messaging systems, and offers SDM for RDBMSs, Apache Hadoop and Cloudera distributions. Strengths Camouflage offers managed discovery as a service (called CX-DaaS) and DM as a service (called CX-MaaS), where Camouflage's experts conduct discovery and/or masking on behalf of its clients, either on-premises or in the cloud. The vendor's CX-Virtual product offers DM of virtualized subsets, where data is masked only once in the virtualized (shared) data and in any changed data, while retaining storage space savings and enabling repeatable delivery of once-masked data. Camouflage offers a pricing model based on the volume of only the data targeted for masking, which often lowers total pricing and makes SDM more affordable. Camouflage needs to scale its operations, enhance its sales and expand its presence outside of North America. An OEM partnership whereby Imperva will be selling Camouflage SDM products could be an answer to these concerns, and Gartner will be monitoring the progress of this new relationship. Although the vendor offers DDM, it is limited to Oracle 11g only, and, while it offers masking of the big data platform, it is limited to Apache Hadoop and Cloudera distributions. Camouflage does not offer data management and DAP, as the Leaders and some other Challengers in this Magic Quadrant do. Compuware Compuware is exclusively focused on delivering software solutions (including SDM) that help customers preserve and extend their mainframe investments. Compuware's SDM, Test Data Privacy, makes an appealing case for its use in large, enterprisewide projects on a mainframe platform, or in a mixed mainframe and distributed platform with a focus on the mainframe. Strengths Compuware is an expert in large-scale SDM deployments on mainframe platforms. It has a well-defined, extensive, best-practice-based methodology and maturity model for SDM implementations, which are well-integrated into the SDM tool. SDM is often used as part of the data management process, and Compuware offers mainframe TDM solutions into which its SDM can be integrated. Page 4 of 27 Gartner, Inc. G
5 The vendor reaches beyond North America, and provides support for Unicode, which is important to those markets. Compuware lacks comprehensive discovery technology, which is critical to SDM. However, the vendor augments this through a nonexclusive partnership with Dataguise. Compuware does not demonstrate DM innovations for big data platforms and DDM. It lacks a focus on and reputation in the security space. Compuware's SDM reputation is limited to mainframe platforms. Typically, enterprises that prefer its SDM are heavy mainframe users, while users of mainly distributed platforms usually look at other SDM vendors. Dataguise Dataguise sells DgSecure for Hadoop, DgSecure for DBMS, DgSecure for NoSQL Cassandra, DgSecure for Files and DgSecure for the Cloud. Dataguise is suitable for organizations that are looking for user-friendly products with a flexible masking rule engine and good performance characteristics at a reasonable price. It should also be considered by enterprises that need discovery, masking and encryption (regular and format-preserving, National Institute of Standards and Technology [NIST]-recognized) for sensitive data (structured and unstructured) in a big data platform. Strengths Dataguise has strong discovery technology for RDBMSs, mainframes, files, SharePoint and Hadoop. The technology is designed to be fully automated and provides reporting on the security status of discovered data. It focuses on the emerging DM for Hadoop, and is one of the DM pioneers for MapR, Cloudera, Hortonworks, Pivotal Greenplum, IBM InfoSphere BigInsights, Amazon Elastic MapReduce (EMR), Pivotal HD and Apache Hadoop distributions, with a good reputation earned among emerging clientele. The vendor innovates by offering discovery, auditing and DDM for Cassandra. Aiming at securing data in the cloud, Dataguise offers the creation of a Hadoop cluster in Amazon Web Services (AWS). It also offers DgSecure for Hadoop as a service to Altiscale and Qubole. Dataguise launched a relationship with Microsoft Azure to provide an integrated solution with HDInsight for discovery, encryption and masking of Azure data. In revenue, market share and mind share, Dataguise lags behind the Leaders and some other Visionaries in this Magic Quadrant. It needs to expand its visibility beyond North America. Gartner, Inc. G Page 5 of 27
6 Dataguise does not offer data security technologies, such as DAP and data tokenization, which are available from some Leaders and other Visionaries in this Magic Quadrant. It does not offer data subsetting and TDM technologies, which are offered by the Leaders and some Challengers in this Magic Quadrant. The vendor masks a limited number of databases, compared with the Leaders and some Challengers in this Magic Quadrant. These databases include Oracle, Microsoft SQL Server, IBM DB2 (distributed and mainframe), MySQL, Sybase, Greenplum, Teradata and PostgreSQL. Delphix (Axis) In May 2015, data-as-a-service vendor Delphix announced its acquisition of Axis Technology Software. Delphix's SDM, called the Delphix Masking Engine (formerly Axis DMSuite), is for users that need to mask data on various platforms, in distributed environments and through user-friendly centralized dashboards. The Delphix Masking Engine is often bundled with the Delphix Data as a Service platform. Delphix additionally offers technologies for static masking of big data platforms and masking data for use in the cloud. Strengths The Delphix Masking Engine supports a large number of RDBMSs, as well as unstructured and nonrelational data stores. Delphix offers masking of virtualized data (as an alternative to masking data subsets), an approach that saves data storage and simplifies data subset management. It also offers the ability to save lightweight, virtualized copies of masked data from any point in time, such as before and after an application or database upgrade, for testing and analysis. For big data, the vendor offers sensitive data discovery and SDM for Cloudera and Hortonworks Hadoop distributions. It offers masking for big data by running masking MapReduce jobs, or by first masking then uploading masked data into Hadoop. It offers its SDM at a reasonable price, and provides strong technical support and professional services. Delphix has recently acquired Axis Technology Software, raising questions regarding integration into Delphix's organization. Delphix only resells DDM technology from its partner, GreenSQL, and also only offers a custom integration with its standard SDM suite that includes profiling, reporting and auditing. The DDM and SDM solutions share some user interfaces for discovery, definition of rule sets and algorithms, but also use separate interfaces for configuring some functionality for DDM. The vendor's DDM solution does not mask for big data distributions. Page 6 of 27 Gartner, Inc. G
7 GreenSQL GreenSQL offers security technologies for database real-time protection, including the GreenSQL Dynamic Data Masking tool for on-premises and cloud databases, as well as Database Activity Monitoring, Database Firewall, Sensitive Data Discovery, Segregation of Duties and a database intrusion prevention system. In addition, GreenSQL provides Dynamic DM for Database as a Service. Its technology is a good fit for organizations seeking a suite of real-time database security technologies, affordable pricing and ease of implementation. Strengths GreenSQL addresses a broad spectrum of security needs by offering DAP and DDM (including DDM of stored procedures and DDM for separation-of-duty use cases). It integrates the policy management of DDM and DAP policies through a single console. The vendor demonstrates vision by addressing the protection of cloud-based databases (for example, Amazon Relational Database Service [RDS], Azure SQL and Google Cloud). GreenSQL offers DDM for nonproduction (for example, test) databases a valuable capability when SDM is too slow for masking frequent refreshes of test data. Its technology is user-friendly and automates DDM processes through the dynamic discovery of sensitive data and automated generation of DM rules. The vendor does not offer SDM, although it partners with Axis for joint sales of GreenSQL's DDM and Axis' SDM. GreenSQL does not offer support for masking of big data, although it is on its roadmap. It focuses exclusively on SQL types of databases (for example, Microsoft SQL Server, MySQL, and PostgreSQL). GreenSQL does not offer data redaction, and lacks the data management technologies that the Leaders and some Challengers in this Magic Quadrant have. HPE (Voltage Security) In 1H15, Hewlett Packard Enterprise (HPE) acquired Voltage Security, placed it in the HPE Security software business and combined it with HPE Atalla to form a new business called HPE Security - Data Security, which offers tokenization and encryption for personally identifiable information, structured and unstructured data, payment data, and payment processes. The engineering, sales and marketing resources of Voltage Security and Atalla have been merged and expanded. The Voltage Security product line has been renamed HPE SecureData. Gartner, Inc. G Page 7 of 27
8 The HPE SecureData Enterprise product appeals to customers that want to protect nonproduction and production data with FPE-based SDM and DDM; it also appeals to those that need to protect structured and unstructured data via encryption, DM and tokenization. Strengths HPE SecureData Enterprise SDM provides scalable masking across large, geographically distributed systems on a broad variety of platforms. HPE SecureData Enterprise's FPE-based SDM can be reversed or, if required, made irreversible by using one-time 256-bit FPE keys. Its 256-bit FPE is NIST standard recognized. In data security, HPE SecureData reaches beyond DM, and also offers Secure Stateless Tokenization (SST) for PCI Data Security Standard (DSS) scope reduction. HPE Security - Data Security is one of the innovators in big data security. It offers big data SDM and DDM, and is certified on Hadoop distributions such as Hortonworks, Cloudera, MapR, IBM InfoSphere BigInsights, and is integrated with HPE Vertica. HPE SecureData Enterprise offers just one of several components of SDM technology: DM via FPE. For other components, HPE intends to rely on technologies that are not part of its Data Security Group: (1) HP Structured Data Manager, with its non-fpe-based DM, TDM (including subsetting), and data archiving and retirement; and (2) Discovery from Autonomy Intelligent Data Operating Layer (IDOL). HPE relies on its partnership with Informatica (for discovery and subsetting; SDM templates for packaged systems; extraction, transformation and loading [ETL]; and data integration). There is some overlap with partner Informatica and that may yield some competitive situations, but HPE's partnership with Informatica is broader than DM and that should help maintain the stability of the partnership. HPE SecureData only provides DDM functions via user-defined functions (UDFs) and APIs, which increases the complexity of the masking process. It also offers a DDM tool through its partnership with Informatica. HPE SecureData does not offer a complete DAP solution, which is often offered by some of the Leaders and Challengers in this Magic Quadrant. IBM IBM markets its SDM product as InfoSphere Optim Data Privacy. Its DDM can be acquired as part of IBM Security Guardium Data Activity Monitor Advanced Edition (an appliance), or as part of InfoSphere Optim Data Privacy (a software package). IBM has resources available to operate globally. Its technology is for enterprises with homogeneous or heterogeneous environments, and also with many and various databases and files that need strong discovery and data protection features. Page 8 of 27 Gartner, Inc. G
9 Strengths IBM has a strong SDM reputation and the largest client base. It is one of the most frequently referenced SDM vendors by Gartner clients, especially large ones. IBM offers its IBM Security Guardium for Applications, which conducts DDM of HTTP flows between the application and the browser. IBM provides DM for Cloudera, Hortonworks and InfoSphere BigInsights Hadoop distributions, and also for NoSQL sources such as MongoDB, Hive, HBase and Cassandra. It provides security technologies that are often requested along with DM: TDM, data archiving, application retirement, ETL, e-discovery, data management, DBMS, and application development and testing technologies. It provides a strong DAP and broader data-centric audit and protection (DCAP) capability for its coverage of RDBMSs, several big data platforms and (as recently announced) unstructured file storage environments. Its DDM, offered by InfoSphere Optim Data Privacy, is not an always-present monitoring/ protecting agent instrumented into the database, but a feature available only through the programming of UDFs, thus increasing the complexity of the masking process. Its DDM, offered by IBM Security Guardium Data Activity Monitor Advanced Edition, does not require UDF programming. It is an appliance that uses agents installed on data source host machines. Data subsetting requires acquisition of Optim TDM for multi-table-based subsetting (which will increase pricing by approximately 20%). User satisfaction with IBM's SDM is substantially higher than with its DDM. IBM has limited native support of SDM for MySQL, which is offered by other Leaders in this Magic Quadrant. Informatica Informatica markets its SDM product as Informatica Persistent Data Masking, and its DDM product as Informatica Dynamic Data Masking, appealing to clients that need a suite of SDM and DDM for RDBMSs, legacy platforms and Hadoop. Besides DM, Informatica also leads with its technology offerings in other markets often requested by clients in conjunction with DM: customer MDM, data quality, data integration, enterprise integration platform as a service, and structured data archiving and application retirement. In 3Q15, Informatica was taken private through its acquisition by a group of investors controlled by the Permira funds and Canada Pension Plan Investment Board, with Microsoft and Salesforce Ventures (Salesforce's corporate investment group) also strategic investors in the company. Gartner, Inc. G Page 9 of 27
10 Strengths Informatica complements DM with a product that provides enterprisewide discovery, gathering and contextual security analytics of granular sensitive data elements. Informatica has a strong SDM reputation and a demonstrated track record of delivering SDM in a variety of use cases and verticals, resulting in one of the largest installed SDM customer bases for RDBMSs and legacy platforms. Informatica's DDM supports RDBMS and Hadoop platforms. Its clients implement large-scale, mission-critical DDM projects. The vendor offers strong support for big data platforms. It provides SDM for Hadoop distributions: Cloudera, MapR, Hortonworks, IBM InfoSphere BigInsights and Pivotal. Its DDM supports Cloudera and Hive. In addition to selling DM tools, Informatica provides SDM as part of its Cloud Test Data Management subscription service, which includes prebuilt connectors and templates for applications such as Salesforce. Informatica does not offer its own DAP (which is offered by other Leaders in this Magic Quadrant); instead, it relies on its partnership with Imperva for that. These solutions are standalone, with no integration of policies. Informatica's partner Voltage Security (now HPE Security - Data Security) was acquired by HPE in the beginning of This leaves open the question of whether Informatica (which partners with the HPE SecureData offering for FPE) will develop its own FPE. Some clients have stated that Informatica's data security portfolio, although powerful and sophisticated, requires a long time to learn, and that the skills of Informatica's DM technical support personnel do not equal the vendor's traditionally good skills in data management. Informatica's acquisition by a group of investors presents a risk that the vendor's business strategy will be altered, including cost cutting, slowing development, exploiting core assets and jettisoning noncore business. Informatica is telling customers that its product roadmap and R&D funding will remain the same as prior to the acquisition, but this deserves additional monitoring. Mentis The Mentis portfolio includes SDM (iscramble), data discovery (part of the Mentis platform), data access monitoring (imonitor), DDM and data redaction (imask), database intrusion prevention (iprotect), and sensitive data retirement (iretire). Mentis is for enterprises looking for a suite of several data security technologies, strong discovery, friendly support, mentoring and a willingness to accommodate client requirements. Page 10 of 27 Gartner, Inc. G
11 Strengths As a demonstration of its vision, Mentis' DDM incorporates user location data and allows the creation of location-aware masking policies. Its data security offering reaches beyond SDM and also includes DDM and DAP. Mentis innovates in securing sensitive data by offering the retirement of inactive sensitive data. To increase the accuracy of discovery and identify the best masking algorithm for each data classification, Mentis analyzes not only data, but also the application codes that access data, and then shares this intelligence across the platform. The vendor's offering provides useful templates for packaged systems, such as Oracle E- Business Suite (EBS) and PeopleSoft. Mentis needs to scale its operations, enhance its sales and grow its market visibility. Its masking technology for big data platforms is still in the early stages of client implementation, and should prove its effectiveness. It masks a limited number of RDBMSs: Oracle, SQL Server, DB2, Sybase and Teradata. Oracle Database is a mandatory part of the Mentis product (it can be a database owned by the enterprise or a free, downloadable Oracle version), although there are plans to end this reliance. Net 2000 Net 2000 offers its broadly adopted Data Masker SDM tool, accompanied by its DataBee subsetting tool. The Data Masker SDM tool works for Oracle and SQL Server databases, and is often a good fit for relatively simple environments. This enables Net 2000 to challenge most vendors in that niche of the SDM market. Strengths Data Masker is easy to install and use, and it has an intuitive GUI. Data Masker is one of the lowest-priced tools on the market. Net 2000 has amassed a large number of clients, comparable with the number that market Leaders in this Magic Quadrant have. Its clients span the U.S., Europe and the Asia/Pacific region. Net 2000 offers strong technical support, as well as frequent product improvements that can be downloaded from its website. Gartner, Inc. G Page 11 of 27
12 The vendor does not offer masking for big data platforms. The vendor does not offer DDM and data redaction. Net 2000 lacks enterprise-class capabilities across multiple OSs and databases. DM, discovery and subsetting are available only for Oracle and SQL Server databases. The vendor does not offer "on the fly" SDM, but rather masks a clone of the production database. Data subsetting is provided by a separate tool (DataBee). The vendor does not offer data management, nor does Data Masker integrate with data management or software life cycle (SLC) tools. Its masking templates are available only for Oracle EBS and Microsoft Dynamics CRM. Oracle Oracle is a global provider of business applications, software infrastructure, and middleware and hardware products. Oracle's SDM tool, Data Masking and Subsetting Pack, also includes sensitive data discovery and application templates. Oracle's SDM tool is available with Oracle Enterprise Manager, which also includes data management functionality such as provisioning, cloning and archiving. Oracle's DDM, Data Redaction, is licensed as a feature of Oracle Advanced Security. Oracle's DM offerings mostly appeal to organizations that leverage much of the Oracle technology stack that is, database, middleware and packaged applications. Strengths Oracle has one of the market's largest DM clientele. The vendor has global reach, and there are numerous Oracle experts among IT professionals worldwide. Oracle exhibits high performance in masking and subsetting data in Oracle Database. As Oracle DDM is part of the Oracle Database, no installation is needed (only DDM licensing). Oracle's DDM takes into account real-time contextual information available to the database (such as users, roles, IP addresses, etc.), which increases its accuracy. The vendor offers a unified UI to manage data discovery, SDM, DDM, and subsetting for databases hosted on-premises and in Oracle Cloud. Users can create and manage DM across on-premises and cloud environments. Its broad data security reach is demonstrated by offering other data security technologies, such as encryption, key management (called Oracle Key Vault), DAP (called Oracle Audit Vault and Database Firewall) and privileged user access control (called Oracle Database Vault). For non-oracle Database SDM, an Oracle RDBMS and Oracle Database Gateway must be part of the data discovery and SDM. To address users' needs, a restricted use license for Oracle Page 12 of 27 Gartner, Inc. G
13 Database Gateway is included with Oracle Data Masking and Subsetting Pack for non-oracle Databases at no extra charge. SDM for big data requires loading Hadoop data into Oracle, masking it there and then loading it back into Hadoop. Support for Hadoop beyond Oracle Big Data Appliance is planned. DDM for Hadoop also requires Oracle Big Data Appliance. Hadoop plugs into Oracle RDBMS as an external table, Oracle queries it and responses come back to Oracle, and then Oracle masks them dynamically. For unstructured data outside the database, Oracle does not offer a data redaction tool, but rather a set of APIs for operating on unstructured data. The vendor does provide this functionality as part of a different product line, Oracle WebCenter. Privacy Analytics Privacy Analytics offers risk-based solutions to address privacy risks. Privacy Analytics' software measures and manages the risk of reidentification of structured and unstructured data. Its software deals with not only direct identifiers, but also quasi identifiers, which can put even masked databases at risk. Privacy Analytics' software provides risk analysis based on an enterprise's security and privacy practices, the sensitivity of the dataset, and the possibility of reidentification. The vendor's technology and methods are primarily aimed at healthcare, financial and telecommunications organizations seeking quantifiable and defensible proof that deidentified sensitive data can withstand attacks and the scrutiny of audits. Strengths The vendor's unique offer includes risk metrics to measure the risk of reidentification and privacy disclosure. Its risk-based methodology enables setting the appropriate level of masking. Privacy Analytics' software helps to manage the risk of exposure by defining the threshold for deidentification breaches, which is based on an analysis of existing regulations and protection measures. For greater flexibility, Privacy Analytics' deidentification algorithm is adjustable to minimize distortion of the original data. Privacy Analytics' anonymization methods reach beyond structured data with Privacy Analytics Text. Text masks and deidentifies unstructured data formats, such as PDF, Microsoft Word, plain text and XML. The vendor's SDM is limited to Microsoft Access, Microsoft SQL Server, Oracle, commaseparated values (CSV) and XML files. It does not offer data management, such as TDM or archiving. Privacy Analytics Core masks data on the Windows platform only, but Linux support is planned. Gartner, Inc. G Page 13 of 27
14 The vendor does not offer DDM. The vendor does not mask big data platforms; however, this capability is planned for Privacy Analytics' sales are limited mostly to North America (especially the U.S.), and it targets mainly the healthcare industry, with additional clients in the financial services and telecommunications industry. Solix Technologies Solix Technologies' SDM, called EDMS Data Masking, is part of the Enterprise Data Management Suite (EDMS), which also includes database subsetting, archiving and application retirement. Solix Technologies also offers a free EDMS Standard Edition. The vendor is well-suited for the needs of clients that already use it for capabilities other than SDM, and for users that need to easily and inexpensively add and start conducting SDM. With Solix Technologies, clients will find flexible pricing (perpetual, subscription or per-masked-data volume), the offering of a software tool and a managed service, a user-friendly GUI, and wizard-driven search and masking. Strengths Solix Technologies provides archiving, data management, subsetting and application retirement, which serve as opportunities to sell DM to existing clientele. For enterprises that lack DM expertise, the vendor offers managed service DM and data management. Solix Technologies reaches beyond RDBMS security by offering masking of a MongoDB NoSQL database. The vendor's sales have global reach. Solix Technologies does not offer its own DDM, but rather resells DDM functionality that can be invoked from within an application. It does not offer masking for the Hadoop platform, although it has offered big data management for Hadoop and has plans to add masking. The vendor does not offer DAP or data redaction, which is typically offered by some Leaders and other Challengers in this Magic Quadrant. Solix Technologies still needs to get stronger SDM awareness and stronger overall data security awareness. A substantial number of its clients are users of its other technologies. TCS Tata Consultancy Services (TCS), a well-known global consultancy and IT services organization, has founded its own tool/technology division, which has begun offering DM tools. TCS offers TCS MasterCraft Data Masker (SDM), TCS MasterCraft Dynamic Data Masker (DDM) and TCS Page 14 of 27 Gartner, Inc. G
15 MasterCraft Volume Data Generator for synthetic data generation. The vendor has global reach and offers tools as well as professional services. TCS will appeal to organizations looking for a suite of data management and DM tools supported by the professional services of TCS consulting. Strengths TCS innovates by offering DDM between the application server and the browser. It offers redaction of unstructured data (in Word, Excel, PDF and text documents). The data redaction feature extracts data from the source document, redacts it in memory and creates a redacted copy. Demonstrating its reach beyond RDBMS, TCS has recently launched SDM for Hadoop supporting Hortonworks and Cloudera. In addition to DM, TCS offers data management solutions that are often requested alongside DM, such as synthetic data generation, TDM, data profiling and governance of enterprise data. TCS has a strong global reputation for professional services and has the capacity to provide DM services for its existing clientele. The TCS DM products lack a reputation, and the vendor needs to grow awareness of them. TCS needs to grow its installed base, scale its operations, enhance its sales and grow its market visibility. TCS MasterCraft Dynamic Data Masker does not support big data, although it is planned for The DDM and SDM tools are sold separately and do not share information. They are not integrated, but do have common masking rules. Vendors Added and Dropped We review and adjust our inclusion criteria for Magic Quadrants as markets change. As a result of these adjustments, the mix of vendors in any Magic Quadrant may change over time. A vendor's appearance in a Magic Quadrant one year and not the next does not necessarily indicate that we have changed our opinion of that vendor. It may be a reflection of a change in the market and, therefore, changed evaluation criteria, or of a change of focus by that vendor. Added TCS, with its suite of data DM technologies Dropped No vendors were dropped from this Magic Quadrant. Gartner, Inc. G Page 15 of 27
16 Inclusion and Exclusion Criteria Inclusion Criteria Vendors must provide SDM technology or DDM technology. Aside from core DM capabilities, eligible products should include features that ensure application and database integrity; discover sensitive data enterprisewide; provide rule engines for discovery and masking enterprisewide; provide templates and predefined rules; provide reporting and management capabilities; provide integration with application development/ testing, data management processes and platforms; and enable DM for heterogeneous platforms. Vendors must be determined by Gartner to be significant players in the market because of their market presence or technology innovation. Vendors must have at least $3 million in yearly revenue from DM-related products, or more than 30 clients, or they must demonstrate a futuristic, visionary approach in the DM space. Vendors must have products that were generally available (not in beta) before 28 February Exclusion Criteria We excluded open-source technologies due to the lack of enterprise-class capabilities, services and support. We excluded rudimentary solutions that focus on DM techniques, but lack other critical capabilities of a full-fledged DM technology. DM solutions are available in most (if not all) IT organizations, consultancies and vendor organizations; thus, we excluded vendors that do not offer full-fledged DM technology, and vendors that provide DM only for some particular application/system. We excluded external service providers that offer DM as one of the solutions in their portfolio of services (such as application development or testing), but not as a full-fledged technology product. Evaluation Criteria Ability to Execute Product or Service: This criterion evaluates the vendor's DM product. It includes current product or service capabilities, quality, and feature sets. We give higher ratings for proven performance in competitive assessments and for appeal to a breadth of users (such as information security specialists, quality assurance and application testing specialists, and data management specialists). We give higher ratings to vendors that offer SDM and DDM technologies. We give higher ratings to vendors that offer masking for big data platforms. We evaluate a vendor's ability to offer data Page 16 of 27 Gartner, Inc. G
17 redaction. We evaluate a vendor's data security intelligence offering. We give higher ratings to vendors whose DM technologies do not depend on other vendors' technologies. We also give higher ratings to vendors whose DM technologies do not depend on their own non-dm-related components. Overall Viability: This criterion is an assessment of the organization's or business unit's overall financial health; the likelihood of the vendor's strategy to continue investments in the DM market, and in the broader data/application security space; the vendor's ability to offer security technologies (especially data security technologies) other than DM; the DM revenue amount; the sufficiency of funding sources and staffing; DM expertise; the number of DM customers; and the number of installed and used DM products. We evaluate a vendor's DM market share and overall mind share, including the number of times the vendor appears on Gartner clients' shortlists. Sales Execution/Pricing: We account for the DM growth rate, the company's global reach, its pricing model and its product/service/support/mentoring bundling. We account for the clarity and transparency of the pricing model. We account for the reasons to expect that the vendor's strategy will result in sales volume and revenue growth. We account for sales outside the vendor's home country/region and sales to multiple vertical industries. Market Responsiveness/Record: We look at the vendor's ability to respond, change direction, be flexible and achieve competitive success as opportunities develop, competitors act, customer needs evolve and market dynamics change. We evaluate the reputation of the product, the match of the vendor's DM (and broader data/application security, compliance, and also development/test and data management) offering to the enterprise's functional requirements, and the vendor's track record in delivering innovative features when the market demands them. Marketing Execution: We evaluate market awareness, and the vendor's reputation and clout among security and compliance specialists, as well as among application development, testing and operation specialists. We account for the vendor's ability to clearly state objectives that have given rise to the reputation and growth of its market share and mind share in the DM and data/application security space. Customer Experience: This criterion evaluates the tool's functioning in production environments. The evaluation includes customer satisfaction with the product's technical capabilities, and ease of deployment, operation, administration, stability, scalability and vendor support capabilities. It also includes relationships, products and services/programs that enable clients to be successful with the evaluated products. Specifically, this includes the ways customers receive technical support, as well as the vendor's willingness to work with its clients to customize the product or service, develop specific features requested by the client, and offer personalized customer support, mentoring and consulting. We evaluate whether clients find the price of the technology and the total cost of deployment and operation to be reasonable. We also review the vendor's capabilities in all presales activities and the structures that supports them. Operations: This is the organization's ability to meet its goals and commitments. Factors include the quality of the organizational structure, skills, experiences, programs, systems and other vehicles that enable the organization to operate effectively and efficiently on an ongoing basis. We evaluate Gartner, Inc. G Page 17 of 27
18 the vendor's ability to provide methodology, best practices, mentoring and consulting to its clients, as well as its ability to successfully run partnerships for sales and technology co-development. Table 1. Ability to Execute Evaluation Criteria Evaluation Criteria Product or Service Overall Viability Sales Execution/Pricing Market Responsiveness/Record Marketing Execution Customer Experience Operations Weighting High High Medium High High Medium Medium Source: Gartner (December 2015) Completeness of Vision Market Understanding: We evaluate the vendor's ability to understand buyers' needs and translate them into products and services. DM vendors that show a high degree of market understanding are offering enterprisewide sensitive data discovery for structured and unstructured data, and are also providing masking enterprisewide. They offer templates and predefined discovery and masking rules, reporting and management capabilities, integration with application development/testing, and data management processes and platforms. They enable DM for heterogeneous enterprises, and evolve the scalability, productivity and user-friendliness of DM tools. Marketing Strategy: This criterion looks at whether the vendor has a clear, differentiated set of messages that is consistently communicated throughout the organization, and is externalized through the website, advertising, customer programs and positioning statements. We give a higher rating to vendors that clearly state their dedication to DM, security and compliance markets specifically, data and application security; clearly define their target audience; and market appropriate packaging of their products and/or services. Offering (Product) Strategy: We assess the vendor's approach to product development and delivery. This criterion addresses the vendor's focus on security and compliance; its positioning of DM as an important technology with full-fledged capabilities; its ability to create a network of partners; the optimal balance between satisfying the needs of Type A (leading-edge) enterprises and Type B (mainstream) and Type C (risk-averse) enterprises; and satisfying general/simple requirements and environments, as well as sophisticated/advanced requirements and environments. We give higher ratings to vendors that address broader security markets with more than one data security technology. We give higher ratings to vendors that offer multiple DM tools (for SDM, DDM Page 18 of 27 Gartner, Inc. G
19 and data redaction), and to vendors that offer masking for multiple platforms (such as relational databases, mainframe files/databases and big data platforms). We value vendors that offer DAP technologies in addition to DM. Vertical/Industry Strategy: This criterion looks at the vendor's strategy to direct resources, skills and offerings to meet the specific needs of individual market segments and vertical industries. We give higher ratings to vendors that target multiple vertical industries. Innovation: We evaluate the vendor's development and delivery of a solution that is differentiated from the competition in a way that uniquely addresses critical customer requirements. We give higher ratings to vendors that develop methods that make DM more accurate, scalable, and userand process-friendly. We give higher ratings to vendors that offer solutions that reach into DDM; tokenization; data redaction; FPE; cloud access security brokers; data security for big data platforms; synthetic data generation; statistical methods to measure, increase and ensure the accuracy and strength of masking; data virtualization; security as a service; integration with identity and access management solutions; and data security intelligence. Table 2. Completeness of Vision Evaluation Criteria Evaluation Criteria Market Understanding Marketing Strategy Sales Strategy Offering (Product) Strategy Business Model Vertical/Industry Strategy Innovation Geographic Strategy Weighting High Medium Not Rated High Not Rated Medium High Not Rated Source: Gartner (December 2015) Quadrant Descriptions Leaders Leaders demonstrate balanced progress in execution and vision. Their actions raise the competitive bar for all vendors and solutions in the market, and they tend to set the pace for the industry. A Leader's strategy is focused on data security and compliance. Its offering addresses the needs of security specialists within the SLC and data management processes. Leaders' brands are broadly Gartner, Inc. G Page 19 of 27
20 recognized in the data security space. Leaders reach beyond SDM capabilities and encompass the broader data security discipline, including technologies such as DDM, masking data for big data platforms, data redaction capabilities and security intelligence. At the same time, Leaders are able to amass a relatively large clientele and revenue in this evolving market. However, a leading vendor is not a default choice for every buyer, and clients are cautioned not to assume that they should buy only from Leaders. Some clients may find that vendors in other quadrants better-address their specific needs. Challengers Challengers are efficient choices to address more narrowly defined problems. They have solid technologies that primarily address users' SDM needs, and they compete with Leaders in this area. However, Challengers often lack recognition beyond the SDM space, they lag behind Leaders and Visionaries in the emerging data security use cases, and they lack coverage of broader data security needs, such as DDM and security for big data platforms. Visionaries Visionaries invest in the leading-edge features that will be significant in the next generation of data security solutions, and give buyers early access to greater security assurance and advanced capabilities. Visionaries can affect the course of technological developments in the market (for example, by offering DDM and other dynamic data security technologies, static and dynamic masking of big data, FPE and tokenization, statistical assurance for DM, security intelligence repositories for the analysis of security and contextual information, synthetic data generation, and integration with DAP/DCAP and DM cloud services); however, they currently lack the Ability to Execute against their visions compared with the market Leaders. Enterprises typically choose Visionaries for their best-of-breed evolving features. Other vendors watch Visionaries as indicators of innovation and thought leadership, and attempt to copy or acquire their technologies. Niche Players Niche Players offer viable, dependable solutions that meet the needs of specific buyers, and they fare well when considered for business and technical cases that match their areas of focus. Niche Players may address subsets of the overall market, and often can do so efficiently and effectively (for example, by providing SDM only for one or two databases, or by offering only SDM or only DDM). Enterprises tend to choose Niche Players when the focus is on a few important functions or on specific vendor expertise, or when they have an established relationship with the vendors. Context The past few years have demonstrated to enterprises and government organizations that their data is not safe, but rather is the target for outsider and most damaging insider attacks. Adopting DM helps enterprises raise the level of security and privacy assurance. At the same time, DM helps them meet compliance requirements with the security and privacy standards Page 20 of 27 Gartner, Inc. G
21 recommended by regulating/auditing authorities (for example, the PCI DSS and the Health Insurance Portability and Accountability Act [HIPAA]). Potential abusers, who DM aims to deter, are often enterprise employees or employees of outsourcing firms, such as users of test databases (programmers, testers and database administrators) or users of analytical and training databases (analysts, researchers and trainees). DM is purposely designed to provide fine-granularity data protection, while retaining the usability of protected data. This is necessary for application testing (when testing should be done with fictitious [yet realistic] data instead of real sensitive data) and for analytics (that involve the use of aggregate data for scoring, model building and statistical reporting, but do not require identifiers that should be kept private). A growing number of enterprises make DM a mandatory part of their overall security strategies. This research helps security, privacy, compliance, application development and testing managers evaluate evolving DM trends and implementation practices for their DM strategies. Market Overview The year 2015 had us witnessing an exceptionally high volume of acquisitions in the DM space. Four vendors were acquired over first three quarters of the year. Market Leader Informatica has been taken private through its acquisition by a group of investors controlled by the Permira funds and Canada Pension Plan Investment Board, with Microsoft and Salesforce Ventures (Salesforce's corporate investment group) also strategic investors in the company. Market Challenger Grid-Tools has been acquired by CA Technologies. Another Challenger, Axis, has been acquired by Delphix, and market Visionary Voltage Security has been acquired by HPE. This spree of DM vendor acquisitions by large vendors signifies the growing importance of DM for security and privacy of sensitive data. Acquired vendors will have more resources to conduct R&D and enjoy larger sales networks, thus offering more advanced DM technologies to a larger number of enterprises. At the same time, they will face the challenge of immersing into the culture of these larger vendors. They will also face technological issues of integration into existing technology portfolios of the vendors that acquired them. Yet, acquisitions carry strong potential to better serve existing and future clients, expanding DM adoption. Gartner will closely watch those new, larger DM vendors. This spree of acquisitions challenges remaining smaller vendors. In the 2014 "Magic Quadrant for Data Masking Technology," we wrote: "More than 75% of this 2014 revenue has been earned by the three Leaders, while less than 25% has been earned by the other 11 vendors. This disproportion is worrisome to smaller IT vendors because it demonstrates their lack of ability to reach their target audiences, even though some of them have strong technical features with which to challenge Leaders." Responding to our warnings, three smaller vendors (Axis, Grid-Tools and Voltage Security) were acquired, and are no longer small. The remaining smaller vendors should find ways to either rapidly grow or enter the merger and acquisition process. In 2016, we expect more acquisitions. Driven by user requirements, in 2016, DM technologies will be challenged to: Gartner, Inc. G Page 21 of 27
22 Raise the maturity of DDM, in addition to the already mature SDM, and offer suites of DM tools. Requirements for DM have evolved toward breadth and sophistication of coverage: from masking nonproduction data not in real time to also masking production data in real time. Interest in and demand for DDM are the important trends in the DM market. Recently, we have even witnessed new business cases in which DDM was used to mask nonproduction data in real time. This occurred when SDM was too slow to meet the challenge of several-times-a-day refreshment and masking of test data. In that case, DDM provided real-time masking of test data, so that testers could see only masked data. Among the vendors that offer DDM are Camouflage, GreenSQL, IBM, Informatica, Mentis and Oracle. A number of DM vendors now offer both SDM and DDM. Organizations should consider suites that offer both technologies. Mask big data platforms, in addition to already mature masking of RDBMSs. The DM market has emerged to address use cases for relational databases and mainframe-based databases and files. Recently, DM has been requested to address big data platforms. Unlike RDBMS and mainframe platforms, where SDM was demanded and emerged much earlier than DDM, in big data platforms, we see almost simultaneous emergence of both SDM and DDM. Users apply SDM to mask data used for application development with big data, as well as for masking data used for analytics. DDM is used to mask production data, based on users' entitlements. Vendors such as Dataguise, Delphix (through its acquisition of Axis), IBM, Oracle and HPE (through its acquisition of Voltage Security) offer SDM for big data. Informatica, an innovator in the DDM space, has introduced DDM for Hadoop. A few more DM vendors have plans to add SDM for big data to their tools. As utilization of big data platforms grows, we expect masking for this platform to be in high demand. Mask unstructured content. Organizations should protect sensitive unstructured content with data redaction technology. Data redaction is another business case for DM implementation. It masks unstructured content (e.g., PDF, Word and Excel files). Those files often contain sensitive information (e.g., board of directors meetings' projected growth numbers or medical patients' registration sheets). Popular systems such as SharePoint can contain thousands of such documents. Redacting those files might be necessary. Demand for data redaction is not as strong as demand for SDM and DDM for relational and big data platforms, yet some vendors (such as IBM, Informatica and IRI's CoSort) offer it so that organizations and enterprises can find them in the market when the need arises. Mask data for cloud platforms, in addition to already mature masking data on enterprises' premises. As enterprises adopt the cloud paradigm, they move their data into cloud to use it in development and production. A typical use with an infrastructure as a service (IaaS) case is when an enterprise creates a full copy or a subset copy of it on an on-premises database in the cloud infrastructure, and needs to mask it before developers or data analysts start using it. Another case is when a platform as a service (PaaS) needs an input of masked data via a set of APIs. DM users should review and explore a few areas of innovation that have emerged to address DM use for application development/testing and data analytics: Evaluating Deidentification Assurances of the Masked Data: Some organizations, when they mask sensitive data, ask about the degree of security assurances provided by DM. They wish to measure and manage the risk of sensitive data reidentification, limiting the possibility of Page 22 of 27 Gartner, Inc. G
23 reversing masked data back to the original personal data. The DM market has begun offering risk assessment technologies and methods that enable setting the appropriate level of masking (balancing the data protection strengths and usability/utility of masked data) and offering risk metrics to measure the risk of reidentification and privacy disclosure. Using analysis of the existing regulations and protection measures, such methods define the threshold for deidentification breaches and help to ensure that the risk of exposure is lower than a userspecified threshold. As an example, we can point to Privacy Analytics, a vendor that pioneers such technology and methods for, currently, the healthcare industry's business cases to meet requirements such as those for HIPAA. Combining Data Virtualization Technologies With SDM: Very often, organizations don't need to mask the entire database, but just a subset of it. These subsets are numerous; they occupy a substantial amount of storage, and require time for their creation and management. Recently, vendors such as Delphix have introduced data virtualization as a replacement or supplement for the physical data subsetting. Its implementations differ but, as an example, data virtualization transparently resides between RDBMS and database storage. It creates a full copy of the database and keeps it up-to-date. It provides user access to the requested blocks of data instead of making full copies of the database. These copies are compressed, with a substantial savings of the data storage. Combining DM with data virtualization saves time and storage; data is masked only once in the virtualized (shared) data and in any changed data, while retaining storage space savings. Data virtualization technology can also save time by keeping copies of the masked data blocks and serving them by request. Combining Process Virtualization Technologies With SDM: Process (or service) virtualization enables a virtual environment for testing applications that are under development, and may miss some components that have not been developed yet. This technology simulates missing application components by receiving necessary requests for data provided by the missing components and sending back requested data, thus pretending to be the real component. That data can and should be masked for security and privacy reasons. For example, CA Technologies offers its Lisa Virtual Service Environment (VSE) process virtualization technology, where data is masked by SDM technology from the acquisition of Grid-Tools. IBM has process virtualization Rational Test Workbench and Rational Test Virtualization Server (from the acquisition of Green Hat). For DM, IBM offers its InfoSphere Optim Data Privacy SDM technology. Application development and testing specialists should consider process virtualization, combined with DM. Gartner Recommended Reading Some documents may not be available as part of your current Gartner subscription. "How Markets and Vendors Are Evaluated in Gartner Magic Quadrants" "Hype Cycle for Application Security, 2015" "Static and Dynamic Data Masking Explained" Gartner, Inc. G Page 23 of 27
24 "How Data Masking Evolves to Protect Data From Insiders and Outsiders" "Market Guide for Data-Centric Audit and Protection" "Toolkit: Static Data-Masking Vendor Evaluation Criteria" Evidence Gartner used the following input in developing this Magic Quadrant: Analysis of over 250 client inquiries we received during the past two years Vendors' responses to our detailed Magic Quadrant survey Surveys of 77 clients that vendors introduced as typical or best adopters of their DM technologies Product demonstrations Product briefings Evaluation Criteria Definitions Ability to Execute Product/Service: Core goods and services offered by the vendor for the defined market. This includes current product/service capabilities, quality, feature sets, skills and so on, whether offered natively or through OEM agreements/partnerships as defined in the market definition and detailed in the subcriteria. Overall Viability: Viability includes an assessment of the overall organization's financial health, the financial and practical success of the business unit, and the likelihood that the individual business unit will continue investing in the product, will continue offering the product and will advance the state of the art within the organization's portfolio of products. Sales Execution/Pricing: The vendor's capabilities in all presales activities and the structure that supports them. This includes deal management, pricing and negotiation, presales support, and the overall effectiveness of the sales channel. Market Responsiveness/Record: Ability to respond, change direction, be flexible and achieve competitive success as opportunities develop, competitors act, customer needs evolve and market dynamics change. This criterion also considers the vendor's history of responsiveness. Marketing Execution: The clarity, quality, creativity and efficacy of programs designed to deliver the organization's message to influence the market, promote the brand and business, increase awareness of the products, and establish a positive identification with the product/brand and organization in the minds of buyers. This "mind share" can Page 24 of 27 Gartner, Inc. G
25 be driven by a combination of publicity, promotional initiatives, thought leadership, word of mouth and sales activities. Customer Experience: Relationships, products and services/programs that enable clients to be successful with the products evaluated. Specifically, this includes the ways customers receive technical support or account support. This can also include ancillary tools, customer support programs (and the quality thereof), availability of user groups, service-level agreements and so on. Operations: The ability of the organization to meet its goals and commitments. Factors include the quality of the organizational structure, including skills, experiences, programs, systems and other vehicles that enable the organization to operate effectively and efficiently on an ongoing basis. Completeness of Vision Market Understanding: Ability of the vendor to understand buyers' wants and needs and to translate those into products and services. Vendors that show the highest degree of vision listen to and understand buyers' wants and needs, and can shape or enhance those with their added vision. Marketing Strategy: A clear, differentiated set of messages consistently communicated throughout the organization and externalized through the website, advertising, customer programs and positioning statements. Sales Strategy: The strategy for selling products that uses the appropriate network of direct and indirect sales, marketing, service, and communication affiliates that extend the scope and depth of market reach, skills, expertise, technologies, services and the customer base. Offering (Product) Strategy: The vendor's approach to product development and delivery that emphasizes differentiation, functionality, methodology and feature sets as they map to current and future requirements. Business Model: The soundness and logic of the vendor's underlying business proposition. Vertical/Industry Strategy: The vendor's strategy to direct resources, skills and offerings to meet the specific needs of individual market segments, including vertical markets. Innovation: Direct, related, complementary and synergistic layouts of resources, expertise or capital for investment, consolidation, defensive or pre-emptive purposes. Geographic Strategy: The vendor's strategy to direct resources, skills and offerings to meet the specific needs of geographies outside the "home" or native geography, either Gartner, Inc. G Page 25 of 27
26 directly or through partners, channels and subsidiaries as appropriate for that geography and market. Page 26 of 27 Gartner, Inc. G
27 GARTNER HEADQUARTERS Corporate Headquarters 56 Top Gallant Road Stamford, CT USA Regional Headquarters AUSTRALIA BRAZIL JAPAN UNITED KINGDOM For a complete list of worldwide locations, visit Gartner, Inc. and/or its affiliates. All rights reserved. Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form without Gartner s prior written permission. If you are authorized to access this publication, your use of it is subject to the Usage Guidelines for Gartner Services posted on gartner.com. The information contained in this publication has been obtained from sources believed to be reliable. Gartner disclaims all warranties as to the accuracy, completeness or adequacy of such information and shall have no liability for errors, omissions or inadequacies in such information. This publication consists of the opinions of Gartner s research organization and should not be construed as statements of fact. The opinions expressed herein are subject to change without notice. Although Gartner research may include a discussion of related legal issues, Gartner does not provide legal advice or services and its research should not be construed or used as such. Gartner is a public company, and its shareholders may include firms and funds that have financial interests in entities covered in Gartner research. Gartner s Board of Directors may include senior managers of these firms or funds. Gartner research is produced independently by its research organization without input or influence from these firms, funds or their managers. For further information on the independence and integrity of Gartner research, see Guiding Principles on Independence and Objectivity. Gartner, Inc. G Page 27 of 27
Protecting Data in a Spooky world Data Masking Technologies DAMA RMC Oct. 29, 2014
 Business Glossary Business Intelligence Data Architecture Master Data Management Protecting Data in a Spooky world Data Masking Technologies DAMA RMC Oct. 29, 2014 Aspen Information Solutions, Inc Lowell
Business Glossary Business Intelligence Data Architecture Master Data Management Protecting Data in a Spooky world Data Masking Technologies DAMA RMC Oct. 29, 2014 Aspen Information Solutions, Inc Lowell
CA Technologies Big Data Infrastructure Management Unified Management and Visibility of Big Data
 Research Report CA Technologies Big Data Infrastructure Management Executive Summary CA Technologies recently exhibited new technology innovations, marking its entry into the Big Data marketplace with
Research Report CA Technologies Big Data Infrastructure Management Executive Summary CA Technologies recently exhibited new technology innovations, marking its entry into the Big Data marketplace with
IBM InfoSphere Guardium Data Activity Monitor for Hadoop-based systems
 IBM InfoSphere Guardium Data Activity Monitor for Hadoop-based systems Proactively address regulatory compliance requirements and protect sensitive data in real time Highlights Monitor and audit data activity
IBM InfoSphere Guardium Data Activity Monitor for Hadoop-based systems Proactively address regulatory compliance requirements and protect sensitive data in real time Highlights Monitor and audit data activity
Data Integration Checklist
 The need for data integration tools exists in every company, small to large. Whether it is extracting data that exists in spreadsheets, packaged applications, databases, sensor networks or social media
The need for data integration tools exists in every company, small to large. Whether it is extracting data that exists in spreadsheets, packaged applications, databases, sensor networks or social media
Data-Centric Security vs. Database-Level Security
 TECHNICAL BRIEF Data-Centric Security vs. Database-Level Security Contrasting Voltage SecureData to solutions such as Oracle Advanced Security Transparent Data Encryption Introduction This document provides
TECHNICAL BRIEF Data-Centric Security vs. Database-Level Security Contrasting Voltage SecureData to solutions such as Oracle Advanced Security Transparent Data Encryption Introduction This document provides
Magic Quadrant for Global Enterprise Desktops and Notebooks
 Magic Quadrant for Global Enterprise Desktops and Notebooks Gartner RAS Core Research Note G00207470, Stephen Kleynhans, 10 November 2010, R3553 11302011 In the general PC market, price is often the main
Magic Quadrant for Global Enterprise Desktops and Notebooks Gartner RAS Core Research Note G00207470, Stephen Kleynhans, 10 November 2010, R3553 11302011 In the general PC market, price is often the main
Why Add Data Masking to Your IBM DB2 Application Environment
 Why Add Data Masking to Your IBM DB2 Application Environment dataguise inc. 2010. All rights reserved. Dataguise, Inc. 2201 Walnut Ave., #260 Fremont, CA 94538 (510) 824-1036 www.dataguise.com dataguise
Why Add Data Masking to Your IBM DB2 Application Environment dataguise inc. 2010. All rights reserved. Dataguise, Inc. 2201 Walnut Ave., #260 Fremont, CA 94538 (510) 824-1036 www.dataguise.com dataguise
Case Study & POC & Demos Information
 Case Study & POC & Demos Information Type: Case Study Name: Multichannel Campaign Management (MCCM) Description: The IBM Company seeks, as vendor, through the multichannel campaign management (MCCM) services,
Case Study & POC & Demos Information Type: Case Study Name: Multichannel Campaign Management (MCCM) Description: The IBM Company seeks, as vendor, through the multichannel campaign management (MCCM) services,
Vulnerability Management
 Vulnerability Management Buyer s Guide Buyer s Guide 01 Introduction 02 Key Components 03 Other Considerations About Rapid7 01 INTRODUCTION Exploiting weaknesses in browsers, operating systems and other
Vulnerability Management Buyer s Guide Buyer s Guide 01 Introduction 02 Key Components 03 Other Considerations About Rapid7 01 INTRODUCTION Exploiting weaknesses in browsers, operating systems and other
Ability to Execute. What You Need to Know
 1 of 10 11/30/2010 1:00 PM 28 July 2010 Bern Elliot, Steve Blood Gartner RAS Core Research Note G00201349 Unified communications offers the ability to improve how individuals, groups and companies interact
1 of 10 11/30/2010 1:00 PM 28 July 2010 Bern Elliot, Steve Blood Gartner RAS Core Research Note G00201349 Unified communications offers the ability to improve how individuals, groups and companies interact
Luncheon Webinar Series May 13, 2013
 Luncheon Webinar Series May 13, 2013 InfoSphere DataStage is Big Data Integration Sponsored By: Presented by : Tony Curcio, InfoSphere Product Management 0 InfoSphere DataStage is Big Data Integration
Luncheon Webinar Series May 13, 2013 InfoSphere DataStage is Big Data Integration Sponsored By: Presented by : Tony Curcio, InfoSphere Product Management 0 InfoSphere DataStage is Big Data Integration
Data Masking: A baseline data security measure
 Imperva Camouflage Data Masking Reduce the risk of non-compliance and sensitive data theft Sensitive data is embedded deep within many business processes; it is the foundational element in Human Relations,
Imperva Camouflage Data Masking Reduce the risk of non-compliance and sensitive data theft Sensitive data is embedded deep within many business processes; it is the foundational element in Human Relations,
Mike Maxey. Senior Director Product Marketing Greenplum A Division of EMC. Copyright 2011 EMC Corporation. All rights reserved.
 Mike Maxey Senior Director Product Marketing Greenplum A Division of EMC 1 Greenplum Becomes the Foundation of EMC s Big Data Analytics (July 2010) E M C A C Q U I R E S G R E E N P L U M For three years,
Mike Maxey Senior Director Product Marketing Greenplum A Division of EMC 1 Greenplum Becomes the Foundation of EMC s Big Data Analytics (July 2010) E M C A C Q U I R E S G R E E N P L U M For three years,
Building Confidence in Big Data Innovations in Information Integration & Governance for Big Data
 Building Confidence in Big Data Innovations in Information Integration & Governance for Big Data IBM Software Group Important Disclaimer THE INFORMATION CONTAINED IN THIS PRESENTATION IS PROVIDED FOR INFORMATIONAL
Building Confidence in Big Data Innovations in Information Integration & Governance for Big Data IBM Software Group Important Disclaimer THE INFORMATION CONTAINED IN THIS PRESENTATION IS PROVIDED FOR INFORMATIONAL
Beyond the Single View with IBM InfoSphere
 Ian Bowring MDM & Information Integration Sales Leader, NE Europe Beyond the Single View with IBM InfoSphere We are at a pivotal point with our information intensive projects 10-40% of each initiative
Ian Bowring MDM & Information Integration Sales Leader, NE Europe Beyond the Single View with IBM InfoSphere We are at a pivotal point with our information intensive projects 10-40% of each initiative
Market Guide for Data-Centric Audit and Protection
 G00263059 Market Guide for Data-Centric Audit and Protection Published: 21 November 2014 Analyst(s): Brian Lowans, Earl Perkins Organizations that have not developed data-centric security policies to coordinate
G00263059 Market Guide for Data-Centric Audit and Protection Published: 21 November 2014 Analyst(s): Brian Lowans, Earl Perkins Organizations that have not developed data-centric security policies to coordinate
IBM Software InfoSphere Guardium. Planning a data security and auditing deployment for Hadoop
 Planning a data security and auditing deployment for Hadoop 2 1 2 3 4 5 6 Introduction Architecture Plan Implement Operationalize Conclusion Key requirements for detecting data breaches and addressing
Planning a data security and auditing deployment for Hadoop 2 1 2 3 4 5 6 Introduction Architecture Plan Implement Operationalize Conclusion Key requirements for detecting data breaches and addressing
Well packaged sets of preinstalled, integrated, and optimized software on select hardware in the form of engineered systems and appliances
 INSIGHT Oracle's All- Out Assault on the Big Data Market: Offering Hadoop, R, Cubes, and Scalable IMDB in Familiar Packages Carl W. Olofson IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA
INSIGHT Oracle's All- Out Assault on the Big Data Market: Offering Hadoop, R, Cubes, and Scalable IMDB in Familiar Packages Carl W. Olofson IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA
SELLING PROJECTS ON THE MICROSOFT BUSINESS ANALYTICS PLATFORM
 David Chappell SELLING PROJECTS ON THE MICROSOFT BUSINESS ANALYTICS PLATFORM A PERSPECTIVE FOR SYSTEMS INTEGRATORS Sponsored by Microsoft Corporation Copyright 2014 Chappell & Associates Contents Business
David Chappell SELLING PROJECTS ON THE MICROSOFT BUSINESS ANALYTICS PLATFORM A PERSPECTIVE FOR SYSTEMS INTEGRATORS Sponsored by Microsoft Corporation Copyright 2014 Chappell & Associates Contents Business
Simplify and Automate IT
 Simplify and Automate IT The current state of IT INCIDENT SERVICE LEVEL DATA SERVICE REQUEST ASSET RELEASE CONFIGURATION GOVERNANCE AND COMPLIANCE EVENT AND IMPACT ENTERPRISE SCHEDULING DASHBOARDS CAPACITY
Simplify and Automate IT The current state of IT INCIDENT SERVICE LEVEL DATA SERVICE REQUEST ASSET RELEASE CONFIGURATION GOVERNANCE AND COMPLIANCE EVENT AND IMPACT ENTERPRISE SCHEDULING DASHBOARDS CAPACITY
Forecast of Big Data Trends. Assoc. Prof. Dr. Thanachart Numnonda Executive Director IMC Institute 3 September 2014
 Forecast of Big Data Trends Assoc. Prof. Dr. Thanachart Numnonda Executive Director IMC Institute 3 September 2014 Big Data transforms Business 2 Data created every minute Source http://mashable.com/2012/06/22/data-created-every-minute/
Forecast of Big Data Trends Assoc. Prof. Dr. Thanachart Numnonda Executive Director IMC Institute 3 September 2014 Big Data transforms Business 2 Data created every minute Source http://mashable.com/2012/06/22/data-created-every-minute/
IBM AND NEXT GENERATION ARCHITECTURE FOR BIG DATA & ANALYTICS!
 The Bloor Group IBM AND NEXT GENERATION ARCHITECTURE FOR BIG DATA & ANALYTICS VENDOR PROFILE The IBM Big Data Landscape IBM can legitimately claim to have been involved in Big Data and to have a much broader
The Bloor Group IBM AND NEXT GENERATION ARCHITECTURE FOR BIG DATA & ANALYTICS VENDOR PROFILE The IBM Big Data Landscape IBM can legitimately claim to have been involved in Big Data and to have a much broader
Overview and Frequently Asked Questions
 Overview and Frequently Asked Questions OVERVIEW Oracle is pleased to announce that we have completed our acquisition of Siebel Systems and we are now operating as one. As the leader in customer relationship
Overview and Frequently Asked Questions OVERVIEW Oracle is pleased to announce that we have completed our acquisition of Siebel Systems and we are now operating as one. As the leader in customer relationship
The Future of Data Management
 The Future of Data Management with Hadoop and the Enterprise Data Hub Amr Awadallah (@awadallah) Cofounder and CTO Cloudera Snapshot Founded 2008, by former employees of Employees Today ~ 800 World Class
The Future of Data Management with Hadoop and the Enterprise Data Hub Amr Awadallah (@awadallah) Cofounder and CTO Cloudera Snapshot Founded 2008, by former employees of Employees Today ~ 800 World Class
I D C V E N D O R S P O T L I G H T. W o r k l o a d Management Enables Big Data B u s i n e s s Process Optimization
 I D C V E N D O R S P O T L I G H T W o r k l o a d Management Enables Big Data B u s i n e s s Process Optimization November 2015 Adapted from Worldwide Workload Management Software Market Shares, 2014:
I D C V E N D O R S P O T L I G H T W o r k l o a d Management Enables Big Data B u s i n e s s Process Optimization November 2015 Adapted from Worldwide Workload Management Software Market Shares, 2014:
Data-Centric security and HP NonStop-centric ecosystems. Andrew Price, XYPRO Technology Corporation Mark Bower, Voltage Security
 Title Data-Centric security and HP NonStop-centric ecosystems A breakthrough strategy for neutralizing sensitive data against advanced threats and attacks Andrew Price, XYPRO Technology Corporation Mark
Title Data-Centric security and HP NonStop-centric ecosystems A breakthrough strategy for neutralizing sensitive data against advanced threats and attacks Andrew Price, XYPRO Technology Corporation Mark
TAMING THE BIG CHALLENGE OF BIG DATA MICROSOFT HADOOP
 Pythian White Paper TAMING THE BIG CHALLENGE OF BIG DATA MICROSOFT HADOOP ABSTRACT As companies increasingly rely on big data to steer decisions, they also find themselves looking for ways to simplify
Pythian White Paper TAMING THE BIG CHALLENGE OF BIG DATA MICROSOFT HADOOP ABSTRACT As companies increasingly rely on big data to steer decisions, they also find themselves looking for ways to simplify
Big Data Technologies Compared June 2014
 Big Data Technologies Compared June 2014 Agenda What is Big Data Big Data Technology Comparison Summary Other Big Data Technologies Questions 2 What is Big Data by Example The SKA Telescope is a new development
Big Data Technologies Compared June 2014 Agenda What is Big Data Big Data Technology Comparison Summary Other Big Data Technologies Questions 2 What is Big Data by Example The SKA Telescope is a new development
Introducing the Reimagined Power BI Platform. Jen Underwood, Microsoft
 Introducing the Reimagined Power BI Platform Jen Underwood, Microsoft Thank You Sponsors Empower users with new insights through familiar tools while balancing the need for IT to monitor and manage user
Introducing the Reimagined Power BI Platform Jen Underwood, Microsoft Thank You Sponsors Empower users with new insights through familiar tools while balancing the need for IT to monitor and manage user
Next-Generation Cloud Analytics with Amazon Redshift
 Next-Generation Cloud Analytics with Amazon Redshift What s inside Introduction Why Amazon Redshift is Great for Analytics Cloud Data Warehousing Strategies for Relational Databases Analyzing Fast, Transactional
Next-Generation Cloud Analytics with Amazon Redshift What s inside Introduction Why Amazon Redshift is Great for Analytics Cloud Data Warehousing Strategies for Relational Databases Analyzing Fast, Transactional
Test Data Management for Security and Compliance
 White Paper Test Data Management for Security and Compliance Reducing Risk in the Era of Big Data WHITE PAPER This document contains Confidential, Proprietary and Trade Secret Information ( Confidential
White Paper Test Data Management for Security and Compliance Reducing Risk in the Era of Big Data WHITE PAPER This document contains Confidential, Proprietary and Trade Secret Information ( Confidential
IBM 000-281 EXAM QUESTIONS & ANSWERS
 IBM 000-281 EXAM QUESTIONS & ANSWERS Number: 000-281 Passing Score: 800 Time Limit: 120 min File Version: 58.8 http://www.gratisexam.com/ IBM 000-281 EXAM QUESTIONS & ANSWERS Exam Name: Foundations of
IBM 000-281 EXAM QUESTIONS & ANSWERS Number: 000-281 Passing Score: 800 Time Limit: 120 min File Version: 58.8 http://www.gratisexam.com/ IBM 000-281 EXAM QUESTIONS & ANSWERS Exam Name: Foundations of
The 3 questions to ask yourself about BIG DATA
 The 3 questions to ask yourself about BIG DATA Do you have a big data problem? Companies looking to tackle big data problems are embarking on a journey that is full of hype, buzz, confusion, and misinformation.
The 3 questions to ask yourself about BIG DATA Do you have a big data problem? Companies looking to tackle big data problems are embarking on a journey that is full of hype, buzz, confusion, and misinformation.
Harnessing the Power of the Microsoft Cloud for Deep Data Analytics
 1 Harnessing the Power of the Microsoft Cloud for Deep Data Analytics Today's Focus How you can operate your business more efficiently and effectively by tapping into Cloud based data analytics solutions
1 Harnessing the Power of the Microsoft Cloud for Deep Data Analytics Today's Focus How you can operate your business more efficiently and effectively by tapping into Cloud based data analytics solutions
IBM InfoSphere Optim Test Data Management
 IBM InfoSphere Optim Test Data Management Highlights Create referentially intact, right-sized test databases or data warehouses Automate test result comparisons to identify hidden errors and correct defects
IBM InfoSphere Optim Test Data Management Highlights Create referentially intact, right-sized test databases or data warehouses Automate test result comparisons to identify hidden errors and correct defects
Detecting Anomalous Behavior with the Business Data Lake. Reference Architecture and Enterprise Approaches.
 Detecting Anomalous Behavior with the Business Data Lake Reference Architecture and Enterprise Approaches. 2 Detecting Anomalous Behavior with the Business Data Lake Pivotal the way we see it Reference
Detecting Anomalous Behavior with the Business Data Lake Reference Architecture and Enterprise Approaches. 2 Detecting Anomalous Behavior with the Business Data Lake Pivotal the way we see it Reference
Magic Quadrant for Application Platform Suites, 2Q03
 Markets, Y. Natis, M. Pezzini, G. Phifer, C. Haight, M. Driver Research Note 5 May 2003 Magic Quadrant for Application Platform Suites, 2Q03 Application platform suites are incrementally assembled or bought
Markets, Y. Natis, M. Pezzini, G. Phifer, C. Haight, M. Driver Research Note 5 May 2003 Magic Quadrant for Application Platform Suites, 2Q03 Application platform suites are incrementally assembled or bought
Real-Time Database Protection and. Overview. 2010 IBM Corporation
 Real-Time Database Protection and Monitoring: IBM InfoSphere Guardium Overview Agenda Business drivers for database security InfoSphere Guardium architecture Common applications The InfoSphere portfolio
Real-Time Database Protection and Monitoring: IBM InfoSphere Guardium Overview Agenda Business drivers for database security InfoSphere Guardium architecture Common applications The InfoSphere portfolio
Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail
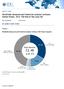 MARKET SHARE Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail Alys Woodward Dan Vesset IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Advanced and Predictive
MARKET SHARE Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail Alys Woodward Dan Vesset IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Advanced and Predictive
TABLE OF CONTENTS 1 Chapter 1: Introduction 2 Chapter 2: Big Data Technology & Business Case 3 Chapter 3: Key Investment Sectors for Big Data
 TABLE OF CONTENTS 1 Chapter 1: Introduction 1.1 Executive Summary 1.2 Topics Covered 1.3 Key Findings 1.4 Target Audience 1.5 Companies Mentioned 2 Chapter 2: Big Data Technology & Business Case 2.1 Defining
TABLE OF CONTENTS 1 Chapter 1: Introduction 1.1 Executive Summary 1.2 Topics Covered 1.3 Key Findings 1.4 Target Audience 1.5 Companies Mentioned 2 Chapter 2: Big Data Technology & Business Case 2.1 Defining
Ubuntu and Hadoop: the perfect match
 WHITE PAPER Ubuntu and Hadoop: the perfect match February 2012 Copyright Canonical 2012 www.canonical.com Executive introduction In many fields of IT, there are always stand-out technologies. This is definitely
WHITE PAPER Ubuntu and Hadoop: the perfect match February 2012 Copyright Canonical 2012 www.canonical.com Executive introduction In many fields of IT, there are always stand-out technologies. This is definitely
Data processing goes big
 Test report: Integration Big Data Edition Data processing goes big Dr. Götz Güttich Integration is a powerful set of tools to access, transform, move and synchronize data. With more than 450 connectors,
Test report: Integration Big Data Edition Data processing goes big Dr. Götz Güttich Integration is a powerful set of tools to access, transform, move and synchronize data. With more than 450 connectors,
How To Understand The Business Case For Big Data
 Brochure More information from http://www.researchandmarkets.com/reports/2643647/ Big Data and Telecom Analytics Market: Business Case, Market Analysis & Forecasts 2014-2019 Description: Big Data refers
Brochure More information from http://www.researchandmarkets.com/reports/2643647/ Big Data and Telecom Analytics Market: Business Case, Market Analysis & Forecasts 2014-2019 Description: Big Data refers
Requirements Checklist for Choosing a Cloud Backup and Recovery Service Provider
 Whitepaper: Requirements Checklist for Choosing a Cloud Backup and Recovery Service Provider WHITEPAPER Requirements Checklist for Choosing a Cloud Backup and Recovery Service Provider Requirements Checklist
Whitepaper: Requirements Checklist for Choosing a Cloud Backup and Recovery Service Provider WHITEPAPER Requirements Checklist for Choosing a Cloud Backup and Recovery Service Provider Requirements Checklist
Hadoop in the Hybrid Cloud
 Presented by Hortonworks and Microsoft Introduction An increasing number of enterprises are either currently using or are planning to use cloud deployment models to expand their IT infrastructure. Big
Presented by Hortonworks and Microsoft Introduction An increasing number of enterprises are either currently using or are planning to use cloud deployment models to expand their IT infrastructure. Big
Simplify and Automate IT
 Simplify and Automate IT Expectations have never been higher Reduce IT Costs 30% increase in staff efficiency Reduce support costs by 25% Improve Quality of Service Reduce downtime by 75% 70% faster MTTR
Simplify and Automate IT Expectations have never been higher Reduce IT Costs 30% increase in staff efficiency Reduce support costs by 25% Improve Quality of Service Reduce downtime by 75% 70% faster MTTR
White Paper: Datameer s User-Focused Big Data Solutions
 CTOlabs.com White Paper: Datameer s User-Focused Big Data Solutions May 2012 A White Paper providing context and guidance you can use Inside: Overview of the Big Data Framework Datameer s Approach Consideration
CTOlabs.com White Paper: Datameer s User-Focused Big Data Solutions May 2012 A White Paper providing context and guidance you can use Inside: Overview of the Big Data Framework Datameer s Approach Consideration
IBM Data Security Services for endpoint data protection endpoint data loss prevention solution
 Automating policy enforcement to prevent endpoint data loss IBM Data Security Services for endpoint data protection endpoint data loss prevention solution Highlights Facilitate policy-based expertise and
Automating policy enforcement to prevent endpoint data loss IBM Data Security Services for endpoint data protection endpoint data loss prevention solution Highlights Facilitate policy-based expertise and
Top 5 reasons to choose HP Information Archiving
 Technical white paper Top 5 reasons to choose HP Information Archiving Proven, market-leading archiving solutions The value of intelligent archiving The requirements around managing information are becoming
Technical white paper Top 5 reasons to choose HP Information Archiving Proven, market-leading archiving solutions The value of intelligent archiving The requirements around managing information are becoming
Logentries Insights: The State of Log Management & Analytics for AWS
 Logentries Insights: The State of Log Management & Analytics for AWS Trevor Parsons Ph.D Co-founder & Chief Scientist Logentries 1 1. Introduction The Log Management industry was traditionally driven by
Logentries Insights: The State of Log Management & Analytics for AWS Trevor Parsons Ph.D Co-founder & Chief Scientist Logentries 1 1. Introduction The Log Management industry was traditionally driven by
Using Cloud Services for Test Environments A case study of the use of Amazon EC2
 Using Cloud Services for Test Environments A case study of the use of Amazon EC2 Lee Hawkins (Quality Architect) Quest Software, Melbourne Copyright 2010 Quest Software We are gathered here today to talk
Using Cloud Services for Test Environments A case study of the use of Amazon EC2 Lee Hawkins (Quality Architect) Quest Software, Melbourne Copyright 2010 Quest Software We are gathered here today to talk
TRANSFORM BIG DATA INTO ACTIONABLE INFORMATION
 TRANSFORM BIG DATA INTO ACTIONABLE INFORMATION Make Big Available for Everyone Syed Rasheed Solution Marketing Manager January 29 th, 2014 Agenda Demystifying Big Challenges Getting Bigger Red Hat Big
TRANSFORM BIG DATA INTO ACTIONABLE INFORMATION Make Big Available for Everyone Syed Rasheed Solution Marketing Manager January 29 th, 2014 Agenda Demystifying Big Challenges Getting Bigger Red Hat Big
Microsoft Big Data. Solution Brief
 Microsoft Big Data Solution Brief Contents Introduction... 2 The Microsoft Big Data Solution... 3 Key Benefits... 3 Immersive Insight, Wherever You Are... 3 Connecting with the World s Data... 3 Any Data,
Microsoft Big Data Solution Brief Contents Introduction... 2 The Microsoft Big Data Solution... 3 Key Benefits... 3 Immersive Insight, Wherever You Are... 3 Connecting with the World s Data... 3 Any Data,
Key Steps to Meeting PCI DSS 2.0 Requirements Using Sensitive Data Discovery and Masking
 Key Steps to Meeting PCI DSS 2.0 Requirements Using Sensitive Data Discovery and Masking SUMMARY The Payment Card Industry Data Security Standard (PCI DSS) defines 12 high-level security requirements directed
Key Steps to Meeting PCI DSS 2.0 Requirements Using Sensitive Data Discovery and Masking SUMMARY The Payment Card Industry Data Security Standard (PCI DSS) defines 12 high-level security requirements directed
Achieving Business Value through Big Data Analytics Philip Russom
 Achieving Business Value through Big Data Analytics Philip Russom TDWI Research Director for Data Management October 3, 2012 Sponsor 2 Speakers Philip Russom Research Director, Data Management, TDWI Brian
Achieving Business Value through Big Data Analytics Philip Russom TDWI Research Director for Data Management October 3, 2012 Sponsor 2 Speakers Philip Russom Research Director, Data Management, TDWI Brian
Tap into Hadoop and Other No SQL Sources
 Tap into Hadoop and Other No SQL Sources Presented by: Trishla Maru What is Big Data really? The Three Vs of Big Data According to Gartner Volume Volume Orders of magnitude bigger than conventional data
Tap into Hadoop and Other No SQL Sources Presented by: Trishla Maru What is Big Data really? The Three Vs of Big Data According to Gartner Volume Volume Orders of magnitude bigger than conventional data
WHITE PAPER. Data Migration and Access in a Cloud Computing Environment INTELLIGENT BUSINESS STRATEGIES
 INTELLIGENT BUSINESS STRATEGIES WHITE PAPER Data Migration and Access in a Cloud Computing Environment By Mike Ferguson Intelligent Business Strategies March 2014 Prepared for: Table of Contents Introduction...
INTELLIGENT BUSINESS STRATEGIES WHITE PAPER Data Migration and Access in a Cloud Computing Environment By Mike Ferguson Intelligent Business Strategies March 2014 Prepared for: Table of Contents Introduction...
IBM BigInsights for Apache Hadoop
 IBM BigInsights for Apache Hadoop Efficiently manage and mine big data for valuable insights Highlights: Enterprise-ready Apache Hadoop based platform for data processing, warehousing and analytics Advanced
IBM BigInsights for Apache Hadoop Efficiently manage and mine big data for valuable insights Highlights: Enterprise-ready Apache Hadoop based platform for data processing, warehousing and analytics Advanced
Unlike the general notebook market, in which
 Magic Quadrant for Global Enterprise Notebook PCs, 2H05 Gartner RAS Core Research Note G00133054, Mikako Kitagawa, Brian Gammage, Leslie Fiering, 12 January 2006, R1662 07222006. Unlike the general notebook
Magic Quadrant for Global Enterprise Notebook PCs, 2H05 Gartner RAS Core Research Note G00133054, Mikako Kitagawa, Brian Gammage, Leslie Fiering, 12 January 2006, R1662 07222006. Unlike the general notebook
QlikView Business Discovery Platform. Algol Consulting Srl
 QlikView Business Discovery Platform Algol Consulting Srl Business Discovery Applications Application vs. Platform Application Designed to help people perform an activity Platform Provides infrastructure
QlikView Business Discovery Platform Algol Consulting Srl Business Discovery Applications Application vs. Platform Application Designed to help people perform an activity Platform Provides infrastructure
Data Governance in the Hadoop Data Lake. Michael Lang May 2015
 Data Governance in the Hadoop Data Lake Michael Lang May 2015 Introduction Product Manager for Teradata Loom Joined Teradata as part of acquisition of Revelytix, original developer of Loom VP of Sales
Data Governance in the Hadoop Data Lake Michael Lang May 2015 Introduction Product Manager for Teradata Loom Joined Teradata as part of acquisition of Revelytix, original developer of Loom VP of Sales
Data Virtualization A Potential Antidote for Big Data Growing Pains
 perspective Data Virtualization A Potential Antidote for Big Data Growing Pains Atul Shrivastava Abstract Enterprises are already facing challenges around data consolidation, heterogeneity, quality, and
perspective Data Virtualization A Potential Antidote for Big Data Growing Pains Atul Shrivastava Abstract Enterprises are already facing challenges around data consolidation, heterogeneity, quality, and
Top 5 reasons to choose HP Information Archiving
 Technical white paper Top 5 reasons to choose HP Information Archiving Intelligent, scalable, and proven archiving solutions Table of Contents The value of intelligent archiving... 2 Top 5 reasons to choose
Technical white paper Top 5 reasons to choose HP Information Archiving Intelligent, scalable, and proven archiving solutions Table of Contents The value of intelligent archiving... 2 Top 5 reasons to choose
Assignment # 1 (Cloud Computing Security)
 Assignment # 1 (Cloud Computing Security) Group Members: Abdullah Abid Zeeshan Qaiser M. Umar Hayat Table of Contents Windows Azure Introduction... 4 Windows Azure Services... 4 1. Compute... 4 a) Virtual
Assignment # 1 (Cloud Computing Security) Group Members: Abdullah Abid Zeeshan Qaiser M. Umar Hayat Table of Contents Windows Azure Introduction... 4 Windows Azure Services... 4 1. Compute... 4 a) Virtual
Big Data Architectures. Tom Cahill, Vice President Worldwide Channels, Jaspersoft
 Big Data Architectures Tom Cahill, Vice President Worldwide Channels, Jaspersoft Jaspersoft + Big Data = Fast Insights Success in the Big Data era is more than about size. It s about getting insight from
Big Data Architectures Tom Cahill, Vice President Worldwide Channels, Jaspersoft Jaspersoft + Big Data = Fast Insights Success in the Big Data era is more than about size. It s about getting insight from
How Transactional Analytics is Changing the Future of Business A look at the options, use cases, and anti-patterns
 How Transactional Analytics is Changing the Future of Business A look at the options, use cases, and anti-patterns Table of Contents Abstract... 3 Introduction... 3 Definition... 3 The Expanding Digitization
How Transactional Analytics is Changing the Future of Business A look at the options, use cases, and anti-patterns Table of Contents Abstract... 3 Introduction... 3 Definition... 3 The Expanding Digitization
CIO Update: Gartner s IT Security Management Magic Quadrant Lacks a Leader
 IGG-04092003-04 M. Nicolett Article 9 April 2003 CIO Update: Gartner s IT Security Management Magic Quadrant Lacks a Leader Vendors in the Gartner IT Security Management Magic Quadrant for 1H03 are driven
IGG-04092003-04 M. Nicolett Article 9 April 2003 CIO Update: Gartner s IT Security Management Magic Quadrant Lacks a Leader Vendors in the Gartner IT Security Management Magic Quadrant for 1H03 are driven
Mind Commerce. http://www.marketresearch.com/mind Commerce Publishing v3122/ Publisher Sample
 Mind Commerce http://www.marketresearch.com/mind Commerce Publishing v3122/ Publisher Sample Phone: 800.298.5699 (US) or +1.240.747.3093 or +1.240.747.3093 (Int'l) Hours: Monday - Thursday: 5:30am - 6:30pm
Mind Commerce http://www.marketresearch.com/mind Commerce Publishing v3122/ Publisher Sample Phone: 800.298.5699 (US) or +1.240.747.3093 or +1.240.747.3093 (Int'l) Hours: Monday - Thursday: 5:30am - 6:30pm
Synergic Partners: Spanish big-data pioneer
 Synergic Partners: Spanish big-data pioneer Analyst: Katy Ring 20 Mar, 2015 Synergic Partners offers a services portfolio around data engineering, big data and data science. The company focuses on business
Synergic Partners: Spanish big-data pioneer Analyst: Katy Ring 20 Mar, 2015 Synergic Partners offers a services portfolio around data engineering, big data and data science. The company focuses on business
Collab references in Gartner
 Collab references in Gartner Publications Hype Cycle for Contact Center Infrastructure 2014 Hype Cycle for Unifed Communications and Collaboration 2014 Magic Quadrant for Workforce Optimization 2014 Magic
Collab references in Gartner Publications Hype Cycle for Contact Center Infrastructure 2014 Hype Cycle for Unifed Communications and Collaboration 2014 Magic Quadrant for Workforce Optimization 2014 Magic
Reference Architecture, Requirements, Gaps, Roles
 Reference Architecture, Requirements, Gaps, Roles The contents of this document are an excerpt from the brainstorming document M0014. The purpose is to show how a detailed Big Data Reference Architecture
Reference Architecture, Requirements, Gaps, Roles The contents of this document are an excerpt from the brainstorming document M0014. The purpose is to show how a detailed Big Data Reference Architecture
Test Data Management Concepts
 Test Data Management Concepts BIZDATAX IS AN EKOBIT BRAND Executive Summary Test Data Management (TDM), as a part of the quality assurance (QA) process is more than ever in the focus among IT organizations
Test Data Management Concepts BIZDATAX IS AN EKOBIT BRAND Executive Summary Test Data Management (TDM), as a part of the quality assurance (QA) process is more than ever in the focus among IT organizations
Securing and protecting the organization s most sensitive data
 Securing and protecting the organization s most sensitive data A comprehensive solution using IBM InfoSphere Guardium Data Activity Monitoring and InfoSphere Guardium Data Encryption to provide layered
Securing and protecting the organization s most sensitive data A comprehensive solution using IBM InfoSphere Guardium Data Activity Monitoring and InfoSphere Guardium Data Encryption to provide layered
Proact whitepaper on Big Data
 Proact whitepaper on Big Data Summary Big Data is not a definite term. Even if it sounds like just another buzz word, it manifests some interesting opportunities for organisations with the skill, resources
Proact whitepaper on Big Data Summary Big Data is not a definite term. Even if it sounds like just another buzz word, it manifests some interesting opportunities for organisations with the skill, resources
TRANSFORM YOUR BUSINESS: BIG DATA AND ANALYTICS WITH VCE AND EMC
 TRANSFORM YOUR BUSINESS: BIG DATA AND ANALYTICS WITH VCE AND EMC Vision Big data and analytic initiatives within enterprises have been rapidly maturing from experimental efforts to production-ready deployments.
TRANSFORM YOUR BUSINESS: BIG DATA AND ANALYTICS WITH VCE AND EMC Vision Big data and analytic initiatives within enterprises have been rapidly maturing from experimental efforts to production-ready deployments.
A Next-Generation Analytics Ecosystem for Big Data. Colin White, BI Research September 2012 Sponsored by ParAccel
 A Next-Generation Analytics Ecosystem for Big Data Colin White, BI Research September 2012 Sponsored by ParAccel BIG DATA IS BIG NEWS The value of big data lies in the business analytics that can be generated
A Next-Generation Analytics Ecosystem for Big Data Colin White, BI Research September 2012 Sponsored by ParAccel BIG DATA IS BIG NEWS The value of big data lies in the business analytics that can be generated
Step by Step: Big Data Technology. Assoc. Prof. Dr. Thanachart Numnonda Executive Director IMC Institute 25 August 2015
 Step by Step: Big Data Technology Assoc. Prof. Dr. Thanachart Numnonda Executive Director IMC Institute 25 August 2015 Data Sources IT Infrastructure Analytics 2 B y 2015, 20% of Global 1000 organizations
Step by Step: Big Data Technology Assoc. Prof. Dr. Thanachart Numnonda Executive Director IMC Institute 25 August 2015 Data Sources IT Infrastructure Analytics 2 B y 2015, 20% of Global 1000 organizations
Cloud Ready Data: Speeding Your Journey to the Cloud
 Cloud Ready Data: Speeding Your Journey to the Cloud Hybrid Cloud first Born to the cloud 3 Am I part of a Cloud First organization? Am I part of a Cloud First agency? The cloud applications questions
Cloud Ready Data: Speeding Your Journey to the Cloud Hybrid Cloud first Born to the cloud 3 Am I part of a Cloud First organization? Am I part of a Cloud First agency? The cloud applications questions
Data Warehouse Appliances: The Next Wave of IT Delivery. Private Cloud (Revocable Access and Support) Applications Appliance. (License/Maintenance)
 Appliances are rapidly becoming a preferred purchase option for large and small businesses seeking to meet expanding workloads and deliver ROI in the face of tightening budgets. TBR is reporting the results
Appliances are rapidly becoming a preferred purchase option for large and small businesses seeking to meet expanding workloads and deliver ROI in the face of tightening budgets. TBR is reporting the results
RED HAT OPENSTACK PLATFORM A COST-EFFECTIVE PRIVATE CLOUD FOR YOUR BUSINESS
 WHITEPAPER RED HAT OPENSTACK PLATFORM A COST-EFFECTIVE PRIVATE CLOUD FOR YOUR BUSINESS INTRODUCTION The cloud is more than a marketing concept. Cloud computing is an intentional, integrated architecture
WHITEPAPER RED HAT OPENSTACK PLATFORM A COST-EFFECTIVE PRIVATE CLOUD FOR YOUR BUSINESS INTRODUCTION The cloud is more than a marketing concept. Cloud computing is an intentional, integrated architecture
Datenverwaltung im Wandel - Building an Enterprise Data Hub with
 Datenverwaltung im Wandel - Building an Enterprise Data Hub with Cloudera Bernard Doering Regional Director, Central EMEA, Cloudera Cloudera Your Hadoop Experts Founded 2008, by former employees of Employees
Datenverwaltung im Wandel - Building an Enterprise Data Hub with Cloudera Bernard Doering Regional Director, Central EMEA, Cloudera Cloudera Your Hadoop Experts Founded 2008, by former employees of Employees
Dell Cloudera Syncsort Data Warehouse Optimization ETL Offload
 Dell Cloudera Syncsort Data Warehouse Optimization ETL Offload Drive operational efficiency and lower data transformation costs with a Reference Architecture for an end-to-end optimization and offload
Dell Cloudera Syncsort Data Warehouse Optimization ETL Offload Drive operational efficiency and lower data transformation costs with a Reference Architecture for an end-to-end optimization and offload
IBM InfoSphere Optim Test Data Management Solution
 IBM InfoSphere Optim Test Data Management Solution Highlights Create referentially intact, right-sized test databases Automate test result comparisons to identify hidden errors Easily refresh and maintain
IBM InfoSphere Optim Test Data Management Solution Highlights Create referentially intact, right-sized test databases Automate test result comparisons to identify hidden errors Easily refresh and maintain
Workday Big Data Analytics
 Workday Big Data Analytics Today s fast-paced business climate demands that decision-makers stay informed. Having access to key information gives them the best insight into their business. However, many
Workday Big Data Analytics Today s fast-paced business climate demands that decision-makers stay informed. Having access to key information gives them the best insight into their business. However, many
Il mondo dei DB Cambia : Tecnologie e opportunita`
 Il mondo dei DB Cambia : Tecnologie e opportunita` Giorgio Raico Pre-Sales Consultant Hewlett-Packard Italiana 2011 Hewlett-Packard Development Company, L.P. The information contained herein is subject
Il mondo dei DB Cambia : Tecnologie e opportunita` Giorgio Raico Pre-Sales Consultant Hewlett-Packard Italiana 2011 Hewlett-Packard Development Company, L.P. The information contained herein is subject
IBM Global Business Services Microsoft Dynamics CRM solutions from IBM
 IBM Global Business Services Microsoft Dynamics CRM solutions from IBM Power your productivity 2 Microsoft Dynamics CRM solutions from IBM Highlights Win more deals by spending more time on selling and
IBM Global Business Services Microsoft Dynamics CRM solutions from IBM Power your productivity 2 Microsoft Dynamics CRM solutions from IBM Highlights Win more deals by spending more time on selling and
HP Structured Data Manager
 Data sheet HP Structured Data Manager Manage explosive application information growth HP SDM at work at HP HP, one of the world s largest IT companies, was experiencing similar challenges to those described
Data sheet HP Structured Data Manager Manage explosive application information growth HP SDM at work at HP HP, one of the world s largest IT companies, was experiencing similar challenges to those described
White Paper: Evaluating Big Data Analytical Capabilities For Government Use
 CTOlabs.com White Paper: Evaluating Big Data Analytical Capabilities For Government Use March 2012 A White Paper providing context and guidance you can use Inside: The Big Data Tool Landscape Big Data
CTOlabs.com White Paper: Evaluating Big Data Analytical Capabilities For Government Use March 2012 A White Paper providing context and guidance you can use Inside: The Big Data Tool Landscape Big Data
Dell Information Management solutions
 Dell Information Management solutions Uday Tekumalla Solutions Marketing, Information Management 1 10/28/2013 Information Management Solutions My introduction Uday Tekumalla, the ponytail guy Information
Dell Information Management solutions Uday Tekumalla Solutions Marketing, Information Management 1 10/28/2013 Information Management Solutions My introduction Uday Tekumalla, the ponytail guy Information
InfoSphere Governance Solutions Maximizing your Information Supply Chain
 Kimberly Madia, IBM InfoSphere Product Marketing [email protected], 412-667-3256 InfoSphere Governance Solutions Maximizing your Information Supply Chain Information Management Version 2010.09.03 What
Kimberly Madia, IBM InfoSphere Product Marketing [email protected], 412-667-3256 InfoSphere Governance Solutions Maximizing your Information Supply Chain Information Management Version 2010.09.03 What
