Virtualization for Security
|
|
|
- Sabina Parker
- 10 years ago
- Views:
Transcription
1 Virtualization for Security t j Including Sandboxing, Disaster Recovery, High Availability, Forensic Analysis, and Honeypotting John Hoopes Technical Editor Aaron Bawcom Paul Kenealy Wesley J. Noonan Craig A. Schiller Fred Shore Andreas Turriff Mario Vuksan Carsten Willems David Williams
2 Contents Chapter 1 An Introduction to Virtualization 1 Introduction 2 What Is Virtualization? 2 The History of Virtualization 3 The Atlas Computer 3 The M44/44X Project 4 CP/CMS 4 Other Time-Sharing Projects 5 Virtualization Explosion of the 1990s and Early 2000s 6 The Answer: Virtualization Is 8 Why Virtualize? 9 Decentralization versus Centralization 9 True Tangible Benefits 13 Consolidation 15 Reliability 17 Security 18 How Does Virtualization Work? 19 OS Relationships with the CPU Architecture 20 The Virtual Machine Monitor and Ring-0 Presentation 22 The VMM Role Explored 23 The Popek and Goldberg Requirements 24 The Challenge:VMMs for the x86 Architecture 25 Types of Virtualization 26 Server Virtualization 26 Storage Virtualization 29 Network Virtualization V Application Virtualization 31 Common Use Cases for Virtualization 32 Technology Refresh 32 Business Continuity and Disaster Recovery 34 Proof of Concept Deployments 35 Virtual Desktops 35 Rapid Development, Test Lab, and Software Configuration Management 36 xi
3 xii Contents Summary 38 Solutions Fast Track 38 Frequently Asked Questions 42 Chapter 2 Choosing the Right Solution for the Task 45 Introduction 46 Issues and Considerations That Affect Virtualization Implementations 46 Performance 47 Redundancy 47 Operations 48 Backups 48 Security 48 'Evolution^ 49 Discovery 49 Testing 49 Production 49 Mobility 50 Grid 50 Distinguishing One Type of Virtualization from Another 51 Library Emulation 51 Wine 52 Cygwin 53 Processor Emulation 53 Operating System Virtualization 54 Application Virtualization 54 Presentation Virtualization 55 Server Virtualization 55 Dedicated Hardware 55 Hardware Compatibility 56 Paravirtualization 57 I/O Virtualization 58 Hardware Virtualization 58 Summary 60 Solutions Fast Track 61 Frequently Asked Questions 62 Chapter 3 Building a Sandbox 63 Introduction 64 Sandbox Background 64
4 Contents xiii The Visible Sandbox 65 cwsandbox.exe 68 cwmonitor.dll 69 Existing Sandbox Implementations 72 Describing CWSandbox 74 Creating a Live-DVD with VMware and CWSandbox 78 Setting Up Linux 78 Setting UpVMware Server vl Setting Up a Virtual Machine invmware Server 80 Setting Up Windows XP Professional in the Virtual Machine 81 Setting Up CWSandbox v2.x in Windows XP Professional 82 Configuring Linux andvmware Server for Live-DVD Creation 83 Updating Your Live-DVD 85 Summary 86 Solutions Fast Track 86 Frequently Asked Questions 89 Notes 90 Bibliography 90 Chapter 4 Configuring the Virtual Machine 91 Introduction 92 Resource Management 92 Hard Drive and Network Configurations 92 Hard Drive Configuration 93 Growing Disk Sizes 93 Virtual Disk Types 93 Using Snapshots 94 Network Configuration 94 Creating an Interface 94 Bridged.* ч 95 Host-Only 96 Natted 97 Multiple Interfaces 98 Physical Hardware Access 99 Physical Disks 99 USB Devices 103 Interfacing with the Host 104 Cut and Paste 104 How to Install the VM ware Tools in a Virtual Machine 105 How to Install the Virtual Machine Additions in Virtual PC 112
5 xiv Contents Summary 113 Solutions Fast Track 113 Frequently Asked Questions 115 Chapter 5 Honeypotting 117 Introduction 118 Herding of Sheep 118 Honeynets 120 Gen I 120 Genii 121 Gen III 121 Where to Put It 121 Local Network 122 Distributed Network 122 Layer 2 Bridges 123 Honeymole 125 Multiple Remote Networks 126 Detecting the Attack 130 Intrusion Detection 130 Network Traffic Capture 131 Monitoring on the Box 132 How to Set Up a Realistic Environment 133 Nepenthes 134 Setting Up the Network 134 Keeping the Bad Stuff in 140 Summary 141 Solutions Fast Track 141 Frequently Asked Questions 143 Note 143 Chapter б Malware Analysis 145 Introduction 146 Setting the Stage 146 How Should Network Access Be Limited? 147 Don't Propagate It Yourself 147 The Researcher May Get Discovered 148 Create a "Victim" That Is as Close to Real as Possible 148 You Should Have a Variety of Content to Offer 148 Give It That Lived-in Look 149 Making the Local Network More Real 149 Testing on VMware Workstation 151 Microsoft Virtual PC 153
6 Contents xv Looking for Effects of Malware 154 What Is the Malware 's Purpose? 154 How Does It Propagate? 155 Does the Malware Phone Home for Updates? 155 Does the Malware Participate in a Bot-Net? 156 Does the Malware Send the Spoils Anywhere? 156 Does the Malware Behave Differently Depending on the Domain? 157 How Does the Malware Hide and How Can It Be Detected? 157 How Do You Recover from It? 158 Examining a Sample Analysis Report 159 The <Analysis> Section 159 Analysis Of82f78a89bde09a71ef99b3cedb991bcc.exe 160 Analysis ofarman.exe 162 Interpreting an Analysis Report 167 How Does the Bot Install? 168 Finding Out How New Hosts Are Infected 169 How Does the Bot Protect the Local Host and Itself? 171 Determing How/Which C&C Servers Are Contacted 174 How Does the Bot Get Binary Updates? 175 What Malicious Operations Are Performed? 176 Bot-Related Findings of Our Live Sandbox 181 Antivirtualization Techniques 183 Detecting You Are in avirtual Environment 184 Virtualization Utilities 184 VMware I/O Port 184 Emulated Hardware Detection 185 Hardware Identifiers 185 MAC Addresses 185 Hard Drives *. 186 PCI Identifiers Ч Detecting You Are in a Hypervisor Environment 187 Summary 188 Solutions Fast Track 188 Frequently Asked Questions 189 Chapter 7 Application Testing 191 Introduction 192 Getting Up to Speed Quickly 192 Default Platform 193 Copying a Machine in VMware Server 193 Registering a Machine in Microsoft Virtual Server 195
7 xvi Contents Known Good Starting Point 196 Downloading Preconfigured Appliances 197 VMware's Appliance Program 197 Microsoft's Test Drive Program 198 Debugging 199 Kernel Level Debugging 199 The Advantage of Open Source Virtualization 207 Summary 208 Solutions Fast Track 208 Frequently Asked Questions 209 Chapter 8 Fuzzing 211 Introduction 212 What Is Fuzzing? 212 Virtualization and Fuzzing 214 Choosing an Effective Starting Point 214 Using a Clean Slate 214 Reducing Startup Time 215 Setting Up the Debugging Tools 215 Preparing to Take Input 217 Preparing for External Interaction 218 Taking the Snapshot 218 Executing the Test 219 Scripting Snapshot Startup 219 Interacting with the Application 220 Selecting Test Data 221 Checking for Exceptions 222 Saving the Results 223 Running Concurrent Tests 223 Summary 225 Solutions Fast Track 225 Frequently Asked Questions 227 Chapter 9 Forensic Analysis 229 Introduction 230 Preparing Your Forensic Environment 231 Capturing the Machine 232 Preparing the Captured Machine to Boot on New Hardware 238 What Can Be Gained by Booting the Captured Machine? 239 Virtualization May Permit You to Observe Behavior That Is Only Visible While Live 242
8 Contents xvii Using the System to Demonstrate the Meaning of the Evidence 242 The System May Have Proprietary/Old Files That Require Special Software 242 Analyzing Time Bombs and Booby Traps 243 Easier to Get in the Mind-Set of the Suspect 243 Collecting Intelligence about Botnets or Virus-Infected Systems 244 Collecting Intelligence about a Case 244 Capturing Processes and Data in Memory 245 Performing Forensics of a Virtual Machine 245 Caution: VM-Aware Malware Ahead 247 Summary 249 Solutions Fast Track 249 Frequently Asked Questions 253 Chapter 10 Disaster Recovery 255 Introduction 256 Disaster Recovery in a Virtual Environment 256 Simplifying Backup and Recovery 257 File Level Backup and Restore 257 System-Level Backup and Restore 258 Shared Storage Backup and Restore 259 Allowing Greater Variation in Hardware Restoration 261 Different Number of Servers 262 Using Virtualization for Recovery of Physical Systems 262 Using Virtualization for Recovery of Virtual Systems 263 Recovering from Hardware Failures 265 Redistributing the Data Center 265 Summary 267 Solutions Fast Track 268 Frequently Asked Questions * ч Chapter 11 High Availability: Reset to Good 271 Introduction 272 Understanding High Availability 272 Providing High Availability for Planned Downtime 273 Providing High Availability for Unplanned Downtime 274 Reset to Good 275 Utilizing Vendor Tools to Reset to Good 275 Utilizing Scripting or Other Mechanisms to Reset to Good 277 Degrading over Time 277
9 xviii Contents Configuring High Availability 278 Configuring Shared Storage 278 Configuring the Network 278 Setting Up a Pool or Cluster of Servers 279 Maintaining High Availability 280 Monitoring for Overcommitment of Resources 280 Security Implications 281 Performing Maintenance on a High Availability System 282 Summary 284 Solutions Fast Track 285 Frequently Asked Questions 287 Chapter 12 Best of Both Worlds: Dual Booting 289 Introduction 290 How to Set Up Linux to Run Both Natively and Virtually 290 Creating a Partition for Linux on an Existing Drive 291 Setting Up Dual Hardware Profiles 295 Issues with Running Windows Both Natively andvirtualized 296 Precautions When Running an Operating System on Both Physical andvirtualized Platforms 296 Booting a Suspended Partition 296 Deleting the Suspended State 297 Changing Hardware Configurations Can Affect Your Software 297 Summary 299 Solutions Fast Track 299 Frequently Asked Questions 300 Chapter 13 Protection in Untrusted Environments 301 Introduction 302 Meaningful Uses of Virtualization in Untrusted Environments 302 Levels of Malware Analysis Paranoia 308 Using Virtual Machines to Segregate Data 316 Using Virtual Machines to Run Software You Don't Trust 318 Using Virtual Machines for Users You Don't Trust 321 Setting up the Client Machine 322 Installing Only What You Need 322 Restricting Hardware Access 322 Restricting Software Access 322 Scripting the Restore 323
10 Contents xix Summary 325 Solutions Fast Track 325 Frequently Asked Questions 327 Notes 328 Chapter 14 Training 329 Introduction 330 Setting Up Scanning Servers 330 Advantages of Using a Virtual Machine instead of a Live-CD Distribution 331 Persistence 331 Customization 331 Disadvantages of Using a Virtual Machine instead of a Live-CD 332 Default Platforms 332 Scanning Servers in a Virtual Environment 333 Setting Up Target Servers 334 Very "Open" Boxes for Demonstrating during Class 335 Suggested Vulnerabilities for Windows 335 Suggested Vulnerabilities for Linux 336 Suggested Vulnerabilities for Application Vulnerability Testing 336 Creating the Capture-the-Flag Scenario 339 Harder Targets 339 Snapshots Saved Us 340 Require Research to Accomplish the Task 341 Introduce Firewalls 341 Multiple Servers Requiring Chained Attacks 341 Adding Some Realism 342 Loose Points for Damaging the Environment 342 Demonstrate What the Attack Looks Like on IDS 343 Out Brief. * 343 Cleaning up Afterward 343 Saving Your Back 344 Summary 345 Solutions Fast Track 345 Frequently Asked Questions 347 Index 349
Virtualization Technology
 Virtualization Technology A Manifold Arms Race Michael H. Warfield Senior Researcher and Analyst [email protected] 2008 IBM Corporation Food for Thought Is Virtual Reality an oxymoron or is it the
Virtualization Technology A Manifold Arms Race Michael H. Warfield Senior Researcher and Analyst [email protected] 2008 IBM Corporation Food for Thought Is Virtual Reality an oxymoron or is it the
Professional Xen Visualization
 Professional Xen Visualization William von Hagen WILEY Wiley Publishing, Inc. Acknowledgments Introduction ix xix Chapter 1: Overview of Virtualization : 1 What Is Virtualization? 2 Application Virtualization
Professional Xen Visualization William von Hagen WILEY Wiley Publishing, Inc. Acknowledgments Introduction ix xix Chapter 1: Overview of Virtualization : 1 What Is Virtualization? 2 Application Virtualization
Intro to Virtualization
 Cloud@Ceid Seminars Intro to Virtualization Christos Alexakos Computer Engineer, MSc, PhD C. Sysadmin at Pattern Recognition Lab 1 st Seminar 19/3/2014 Contents What is virtualization How it works Hypervisor
Cloud@Ceid Seminars Intro to Virtualization Christos Alexakos Computer Engineer, MSc, PhD C. Sysadmin at Pattern Recognition Lab 1 st Seminar 19/3/2014 Contents What is virtualization How it works Hypervisor
COS 318: Operating Systems. Virtual Machine Monitors
 COS 318: Operating Systems Virtual Machine Monitors Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318/ Introduction u Have
COS 318: Operating Systems Virtual Machine Monitors Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318/ Introduction u Have
VMWARE VSPHERE 5.0 WITH ESXI AND VCENTER
 VMWARE VSPHERE 5.0 WITH ESXI AND VCENTER CORPORATE COLLEGE SEMINAR SERIES Date: April 15-19 Presented by: Lone Star Corporate College Format: Location: Classroom instruction 8 a.m.-5 p.m. (five-day session)
VMWARE VSPHERE 5.0 WITH ESXI AND VCENTER CORPORATE COLLEGE SEMINAR SERIES Date: April 15-19 Presented by: Lone Star Corporate College Format: Location: Classroom instruction 8 a.m.-5 p.m. (five-day session)
Contents. vii. Preface. P ART I THE HONEYNET 1 Chapter 1 The Beginning 3. Chapter 2 Honeypots 17. xix
 Honeynet2_bookTOC.fm Page vii Monday, May 3, 2004 12:00 PM Contents Preface Foreword xix xxvii P ART I THE HONEYNET 1 Chapter 1 The Beginning 3 The Honeynet Project 3 The Information Security Environment
Honeynet2_bookTOC.fm Page vii Monday, May 3, 2004 12:00 PM Contents Preface Foreword xix xxvii P ART I THE HONEYNET 1 Chapter 1 The Beginning 3 The Honeynet Project 3 The Information Security Environment
Virtualization. Dr. Yingwu Zhu
 Virtualization Dr. Yingwu Zhu What is virtualization? Virtualization allows one computer to do the job of multiple computers. Virtual environments let one computer host multiple operating systems at the
Virtualization Dr. Yingwu Zhu What is virtualization? Virtualization allows one computer to do the job of multiple computers. Virtual environments let one computer host multiple operating systems at the
Virtualization and Cloud Computing
 Virtualization and Cloud Computing Security is a Process, not a Product Guillermo Macias CIP Security Auditor, Sr. Virtualization Purpose of Presentation: To inform entities about the importance of assessing
Virtualization and Cloud Computing Security is a Process, not a Product Guillermo Macias CIP Security Auditor, Sr. Virtualization Purpose of Presentation: To inform entities about the importance of assessing
Implementing and Managing Windows Server 2008 Hyper-V
 Course 6422A: Implementing and Managing Windows Server 2008 Hyper-V Length: 3 Days Language(s): English Audience(s): IT Professionals Level: 300 Technology: Windows Server 2008 Type: Course Delivery Method:
Course 6422A: Implementing and Managing Windows Server 2008 Hyper-V Length: 3 Days Language(s): English Audience(s): IT Professionals Level: 300 Technology: Windows Server 2008 Type: Course Delivery Method:
Virtual Machines. www.viplavkambli.com
 1 Virtual Machines A virtual machine (VM) is a "completely isolated guest operating system installation within a normal host operating system". Modern virtual machines are implemented with either software
1 Virtual Machines A virtual machine (VM) is a "completely isolated guest operating system installation within a normal host operating system". Modern virtual machines are implemented with either software
The Art of Virtualization with Free Software
 Master on Free Software 2009/2010 {mvidal,jfcastro}@libresoft.es GSyC/Libresoft URJC April 24th, 2010 (cc) 2010. Some rights reserved. This work is licensed under a Creative Commons Attribution-Share Alike
Master on Free Software 2009/2010 {mvidal,jfcastro}@libresoft.es GSyC/Libresoft URJC April 24th, 2010 (cc) 2010. Some rights reserved. This work is licensed under a Creative Commons Attribution-Share Alike
nanohub.org An Overview of Virtualization Techniques
 An Overview of Virtualization Techniques Renato Figueiredo Advanced Computing and Information Systems (ACIS) Electrical and Computer Engineering University of Florida NCN/NMI Team 2/3/2006 1 Outline Resource
An Overview of Virtualization Techniques Renato Figueiredo Advanced Computing and Information Systems (ACIS) Electrical and Computer Engineering University of Florida NCN/NMI Team 2/3/2006 1 Outline Resource
Basics in Energy Information (& Communication) Systems Virtualization / Virtual Machines
 Basics in Energy Information (& Communication) Systems Virtualization / Virtual Machines Dr. Johann Pohany, Virtualization Virtualization deals with extending or replacing an existing interface so as to
Basics in Energy Information (& Communication) Systems Virtualization / Virtual Machines Dr. Johann Pohany, Virtualization Virtualization deals with extending or replacing an existing interface so as to
6422: Implementing and Managing Windows Server 2008 Hyper-V (3 Days)
 www.peaklearningllc.com 6422: Implementing and Managing Windows Server 2008 Hyper-V (3 Days) Introduction This three-day instructor-led course teaches students how to implement and manage Windows Server
www.peaklearningllc.com 6422: Implementing and Managing Windows Server 2008 Hyper-V (3 Days) Introduction This three-day instructor-led course teaches students how to implement and manage Windows Server
What is virtualization
 Virtualization Concepts Virtualization Virtualization is the process of presenting computing resources in ways that users and applications can easily get value out of them, rather than presenting them
Virtualization Concepts Virtualization Virtualization is the process of presenting computing resources in ways that users and applications can easily get value out of them, rather than presenting them
Hypervisors. Introduction. Introduction. Introduction. Introduction. Introduction. Credits:
 Hypervisors Credits: P. Chaganti Xen Virtualization A practical handbook D. Chisnall The definitive guide to Xen Hypervisor G. Kesden Lect. 25 CS 15-440 G. Heiser UNSW/NICTA/OKL Virtualization is a technique
Hypervisors Credits: P. Chaganti Xen Virtualization A practical handbook D. Chisnall The definitive guide to Xen Hypervisor G. Kesden Lect. 25 CS 15-440 G. Heiser UNSW/NICTA/OKL Virtualization is a technique
Virtual Machine Monitors. Dr. Marc E. Fiuczynski Research Scholar Princeton University
 Virtual Machine Monitors Dr. Marc E. Fiuczynski Research Scholar Princeton University Introduction Have been around since 1960 s on mainframes used for multitasking Good example VM/370 Have resurfaced
Virtual Machine Monitors Dr. Marc E. Fiuczynski Research Scholar Princeton University Introduction Have been around since 1960 s on mainframes used for multitasking Good example VM/370 Have resurfaced
Virtual Machines and Security Paola Stone Martinez East Carolina University November, 2013.
 Virtual Machines and Security Paola Stone Martinez East Carolina University November, 2013. Keywords: virtualization, virtual machine, security. 1. Virtualization The rapid growth of technologies, nowadays,
Virtual Machines and Security Paola Stone Martinez East Carolina University November, 2013. Keywords: virtualization, virtual machine, security. 1. Virtualization The rapid growth of technologies, nowadays,
Week Overview. Installing Linux Linux on your Desktop Virtualization Basic Linux system administration
 ULI101 Week 06b Week Overview Installing Linux Linux on your Desktop Virtualization Basic Linux system administration Installing Linux Standalone installation Linux is the only OS on the computer Any existing
ULI101 Week 06b Week Overview Installing Linux Linux on your Desktop Virtualization Basic Linux system administration Installing Linux Standalone installation Linux is the only OS on the computer Any existing
Virtualization. Types of Interfaces
 Virtualization Virtualization: extend or replace an existing interface to mimic the behavior of another system. Introduced in 1970s: run legacy software on newer mainframe hardware Handle platform diversity
Virtualization Virtualization: extend or replace an existing interface to mimic the behavior of another system. Introduced in 1970s: run legacy software on newer mainframe hardware Handle platform diversity
9/26/2011. What is Virtualization? What are the different types of virtualization.
 CSE 501 Monday, September 26, 2011 Kevin Cleary [email protected] What is Virtualization? What are the different types of virtualization. Practical Uses Popular virtualization products Demo Question,
CSE 501 Monday, September 26, 2011 Kevin Cleary [email protected] What is Virtualization? What are the different types of virtualization. Practical Uses Popular virtualization products Demo Question,
SAN Conceptual and Design Basics
 TECHNICAL NOTE VMware Infrastructure 3 SAN Conceptual and Design Basics VMware ESX Server can be used in conjunction with a SAN (storage area network), a specialized high speed network that connects computer
TECHNICAL NOTE VMware Infrastructure 3 SAN Conceptual and Design Basics VMware ESX Server can be used in conjunction with a SAN (storage area network), a specialized high speed network that connects computer
VIRTUALIZATION SECURITY IN THE REAL WORLD
 VIRTUALIZATION SECURITY IN THE REAL WORLD Growing Technology Virtualization has become the standard for many corporate IT departments. The market for server virtualization infrastructure has matured, surpassing
VIRTUALIZATION SECURITY IN THE REAL WORLD Growing Technology Virtualization has become the standard for many corporate IT departments. The market for server virtualization infrastructure has matured, surpassing
"Charting the Course... ... to Your Success!" MOC 50331 D Windows 7 Enterprise Desktop Support Technician Course Summary
 Description Course Summary This course provides students with the knowledge and skills needed to isolate, document and resolve problems on a Windows 7 desktop or laptop computer. It will also help test
Description Course Summary This course provides students with the knowledge and skills needed to isolate, document and resolve problems on a Windows 7 desktop or laptop computer. It will also help test
VMware vsphere 5.1 Advanced Administration
 Course ID VMW200 VMware vsphere 5.1 Advanced Administration Course Description This powerful 5-day 10hr/day class is an intensive introduction to VMware vsphere 5.0 including VMware ESX 5.0 and vcenter.
Course ID VMW200 VMware vsphere 5.1 Advanced Administration Course Description This powerful 5-day 10hr/day class is an intensive introduction to VMware vsphere 5.0 including VMware ESX 5.0 and vcenter.
CS 356 Lecture 25 and 26 Operating System Security. Spring 2013
 CS 356 Lecture 25 and 26 Operating System Security Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control
CS 356 Lecture 25 and 26 Operating System Security Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control
IOS110. Virtualization 5/27/2014 1
 IOS110 Virtualization 5/27/2014 1 Agenda What is Virtualization? Types of Virtualization. Advantages and Disadvantages. Virtualization software Hyper V What is Virtualization? Virtualization Refers to
IOS110 Virtualization 5/27/2014 1 Agenda What is Virtualization? Types of Virtualization. Advantages and Disadvantages. Virtualization software Hyper V What is Virtualization? Virtualization Refers to
Virtualization for Cloud Computing
 Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
Anh Quach, Matthew Rajman, Bienvenido Rodriguez, Brian Rodriguez, Michael Roefs, Ahmed Shaikh
 Anh Quach, Matthew Rajman, Bienvenido Rodriguez, Brian Rodriguez, Michael Roefs, Ahmed Shaikh Introduction History, Advantages, Common Uses OS-Level Virtualization Hypervisors Type 1 vs. type 2 hypervisors
Anh Quach, Matthew Rajman, Bienvenido Rodriguez, Brian Rodriguez, Michael Roefs, Ahmed Shaikh Introduction History, Advantages, Common Uses OS-Level Virtualization Hypervisors Type 1 vs. type 2 hypervisors
[email protected] 2009 STREAM FRBC
 Virtualization ti Dave Balka [email protected] Examination Elements Architecture Management Processes Integrity Availability Security 2 Datacenter Consolidation 3 What is Virtualization A framework
Virtualization ti Dave Balka [email protected] Examination Elements Architecture Management Processes Integrity Availability Security 2 Datacenter Consolidation 3 What is Virtualization A framework
Networking for Caribbean Development
 Networking for Caribbean Development BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n o g. o r g Virtualization: Architectural Considerations and Implementation Options Virtualization Virtualization is the
Networking for Caribbean Development BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n o g. o r g Virtualization: Architectural Considerations and Implementation Options Virtualization Virtualization is the
Outline SSS6422 - Microsoft Windows Server 2008 Hyper-V Virtualization
 Outline SSS6422 - Microsoft Windows Server 2008 Hyper-V Virtualization Duration: Three consecutive Saturdays About this Course This instructor led course teaches students how to implement and manage Windows
Outline SSS6422 - Microsoft Windows Server 2008 Hyper-V Virtualization Duration: Three consecutive Saturdays About this Course This instructor led course teaches students how to implement and manage Windows
Study Guide. Professional vsphere 4. VCP VMware Certified. (ExamVCP4IO) Robert Schmidt. IVIC GratAf Hill
 VCP VMware Certified Professional vsphere 4 Study Guide (ExamVCP4IO) Robert Schmidt McGraw-Hill is an independent entity from VMware Inc. and is not affiliated with VMware Inc. in any manner.this study/training
VCP VMware Certified Professional vsphere 4 Study Guide (ExamVCP4IO) Robert Schmidt McGraw-Hill is an independent entity from VMware Inc. and is not affiliated with VMware Inc. in any manner.this study/training
Virtualization of CBORD Odyssey PCS and Micros 3700 servers. The CBORD Group, Inc. January 13, 2007
 Virtualization of CBORD Odyssey PCS and Micros 3700 servers January 13, 2007 61 Brown Road Ithaca, NY 14850 (607) 257-2410 Document Revision: 2 Last revised: January 13, 2007 Changes are periodically made
Virtualization of CBORD Odyssey PCS and Micros 3700 servers January 13, 2007 61 Brown Road Ithaca, NY 14850 (607) 257-2410 Document Revision: 2 Last revised: January 13, 2007 Changes are periodically made
VMware Server 2.0 Essentials. Virtualization Deployment and Management
 VMware Server 2.0 Essentials Virtualization Deployment and Management . This PDF is provided for personal use only. Unauthorized use, reproduction and/or distribution strictly prohibited. All rights reserved.
VMware Server 2.0 Essentials Virtualization Deployment and Management . This PDF is provided for personal use only. Unauthorized use, reproduction and/or distribution strictly prohibited. All rights reserved.
VMware vsphere 5.0 Boot Camp
 VMware vsphere 5.0 Boot Camp This powerful 5-day 10hr/day class is an intensive introduction to VMware vsphere 5.0 including VMware ESX 5.0 and vcenter. Assuming no prior virtualization experience, this
VMware vsphere 5.0 Boot Camp This powerful 5-day 10hr/day class is an intensive introduction to VMware vsphere 5.0 including VMware ESX 5.0 and vcenter. Assuming no prior virtualization experience, this
How To Protect A Virtual Desktop From Attack
 Endpoint Security: Become Aware of Virtual Desktop Infrastructures! An Ogren Group Special Report May 2011 Executive Summary Virtual desktops infrastructures, VDI, present IT with the unique opportunity
Endpoint Security: Become Aware of Virtual Desktop Infrastructures! An Ogren Group Special Report May 2011 Executive Summary Virtual desktops infrastructures, VDI, present IT with the unique opportunity
Uses for Virtual Machines. Virtual Machines. There are several uses for virtual machines:
 Virtual Machines Uses for Virtual Machines Virtual machine technology, often just called virtualization, makes one computer behave as several computers by sharing the resources of a single computer between
Virtual Machines Uses for Virtual Machines Virtual machine technology, often just called virtualization, makes one computer behave as several computers by sharing the resources of a single computer between
RED HAT ENTERPRISE VIRTUALIZATION
 Giuseppe Paterno' Solution Architect Jan 2010 Red Hat Milestones October 1994 Red Hat Linux June 2004 Red Hat Global File System August 2005 Red Hat Certificate System & Dir. Server April 2006 JBoss April
Giuseppe Paterno' Solution Architect Jan 2010 Red Hat Milestones October 1994 Red Hat Linux June 2004 Red Hat Global File System August 2005 Red Hat Certificate System & Dir. Server April 2006 JBoss April
Server Virtualization with VMWare
 Server Virtualization with VMware Information Technology Server Virtualization with VMWare A look at server virtualization, what it is and why it should be considered. By Alex Dewar, Head of IT & IM Solutions,
Server Virtualization with VMware Information Technology Server Virtualization with VMWare A look at server virtualization, what it is and why it should be considered. By Alex Dewar, Head of IT & IM Solutions,
Solution Brief Availability and Recovery Options: Microsoft Exchange Solutions on VMware
 Introduction By leveraging the inherent benefits of a virtualization based platform, a Microsoft Exchange Server 2007 deployment on VMware Infrastructure 3 offers a variety of availability and recovery
Introduction By leveraging the inherent benefits of a virtualization based platform, a Microsoft Exchange Server 2007 deployment on VMware Infrastructure 3 offers a variety of availability and recovery
Virtualization with Windows
 Virtualization with Windows at CERN Juraj Sucik, Emmanuel Ormancey Internet Services Group Agenda Current status of IT-IS group virtualization service Server Self Service New virtualization features in
Virtualization with Windows at CERN Juraj Sucik, Emmanuel Ormancey Internet Services Group Agenda Current status of IT-IS group virtualization service Server Self Service New virtualization features in
Server Virtualization A Game-Changer For SMB Customers
 Whitepaper Server Virtualization A Game-Changer For SMB Customers Introduction Everyone in the IT world has heard of server virtualization, and some stunning achievements by datacenter and Enterprise customers
Whitepaper Server Virtualization A Game-Changer For SMB Customers Introduction Everyone in the IT world has heard of server virtualization, and some stunning achievements by datacenter and Enterprise customers
Full and Para Virtualization
 Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Windows Server8 2008. R2 Hyper-V. Microsoft's Hypervisor. Insiders Guide to. Wiley Publishing, Inc. John Kelbley. Mike Sterling WILEY
 Windows Server8 2008 R2 Hyper-V Insiders Guide to Microsoft's Hypervisor John Kelbley Mike Sterling WILEY Wiley Publishing, Inc. Contents Introduction xix Chapter l Introducing Hyper-V l Scenarios for
Windows Server8 2008 R2 Hyper-V Insiders Guide to Microsoft's Hypervisor John Kelbley Mike Sterling WILEY Wiley Publishing, Inc. Contents Introduction xix Chapter l Introducing Hyper-V l Scenarios for
Chapter 16: Virtual Machines. Operating System Concepts 9 th Edition
 Chapter 16: Virtual Machines Silberschatz, Galvin and Gagne 2013 Chapter 16: Virtual Machines Overview History Benefits and Features Building Blocks Types of Virtual Machines and Their Implementations
Chapter 16: Virtual Machines Silberschatz, Galvin and Gagne 2013 Chapter 16: Virtual Machines Overview History Benefits and Features Building Blocks Types of Virtual Machines and Their Implementations
What s New with VMware Virtual Infrastructure
 What s New with VMware Virtual Infrastructure Virtualization: Industry-Standard Way of Computing Early Adoption Mainstreaming Standardization Test & Development Server Consolidation Infrastructure Management
What s New with VMware Virtual Infrastructure Virtualization: Industry-Standard Way of Computing Early Adoption Mainstreaming Standardization Test & Development Server Consolidation Infrastructure Management
Virtualization. Explain how today s virtualization movement is actually a reinvention
 Virtualization Learning Objectives Explain how today s virtualization movement is actually a reinvention of the past. Explain how virtualization works. Discuss the technical challenges to virtualization.
Virtualization Learning Objectives Explain how today s virtualization movement is actually a reinvention of the past. Explain how virtualization works. Discuss the technical challenges to virtualization.
Solution Recipe: Improve PC Security and Reliability with Intel Virtualization Technology
 Solution Recipe: Improve PC Security and Reliability with Intel Virtualization Technology 30406_VT_Brochure.indd 1 6/20/06 4:01:14 PM Preface Intel has developed a series of unique Solution Recipes designed
Solution Recipe: Improve PC Security and Reliability with Intel Virtualization Technology 30406_VT_Brochure.indd 1 6/20/06 4:01:14 PM Preface Intel has developed a series of unique Solution Recipes designed
Intelligent Laptop Virtualization No compromises for IT or end users. VMware Mirage [email protected]
 Intelligent Laptop Virtualization No compromises for IT or end users VMware Mirage [email protected] Little video to start with... The Problem with Laptops Windows XP support is expiring
Intelligent Laptop Virtualization No compromises for IT or end users VMware Mirage [email protected] Little video to start with... The Problem with Laptops Windows XP support is expiring
Chapter 14 Virtual Machines
 Operating Systems: Internals and Design Principles Chapter 14 Virtual Machines Eighth Edition By William Stallings Virtual Machines (VM) Virtualization technology enables a single PC or server to simultaneously
Operating Systems: Internals and Design Principles Chapter 14 Virtual Machines Eighth Edition By William Stallings Virtual Machines (VM) Virtualization technology enables a single PC or server to simultaneously
Virtualization. Jukka K. Nurminen 23.9.2015
 Virtualization Jukka K. Nurminen 23.9.2015 Virtualization Virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms,
Virtualization Jukka K. Nurminen 23.9.2015 Virtualization Virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms,
Distributed and Cloud Computing
 Distributed and Cloud Computing K. Hwang, G. Fox and J. Dongarra Chapter 3: Virtual Machines and Virtualization of Clusters and datacenters Adapted from Kai Hwang University of Southern California March
Distributed and Cloud Computing K. Hwang, G. Fox and J. Dongarra Chapter 3: Virtual Machines and Virtualization of Clusters and datacenters Adapted from Kai Hwang University of Southern California March
Distributed Systems. Virtualization. Paul Krzyzanowski [email protected]
 Distributed Systems Virtualization Paul Krzyzanowski [email protected] Except as otherwise noted, the content of this presentation is licensed under the Creative Commons Attribution 2.5 License. Virtualization
Distributed Systems Virtualization Paul Krzyzanowski [email protected] Except as otherwise noted, the content of this presentation is licensed under the Creative Commons Attribution 2.5 License. Virtualization
CSE 501 Monday, September 09, 2013 Kevin Cleary [email protected]
 CSE 501 Monday, September 09, 2013 Kevin Cleary [email protected] What is Virtualization? Practical Uses What can be virtualized Popular virtualization products Demo Question, answer, discussion Can
CSE 501 Monday, September 09, 2013 Kevin Cleary [email protected] What is Virtualization? Practical Uses What can be virtualized Popular virtualization products Demo Question, answer, discussion Can
APPLICATION OF SERVER VIRTUALIZATION IN PLATFORM TESTING
 APPLICATION OF SERVER VIRTUALIZATION IN PLATFORM TESTING Application testing remains a complex endeavor as Development and QA managers need to focus on delivering projects on schedule, controlling costs,
APPLICATION OF SERVER VIRTUALIZATION IN PLATFORM TESTING Application testing remains a complex endeavor as Development and QA managers need to focus on delivering projects on schedule, controlling costs,
INCIDENT RESPONSE CHECKLIST
 INCIDENT RESPONSE CHECKLIST The purpose of this checklist is to provide clients of Kivu Consulting, Inc. with guidance in the initial stages of an actual or possible data breach. Clients are encouraged
INCIDENT RESPONSE CHECKLIST The purpose of this checklist is to provide clients of Kivu Consulting, Inc. with guidance in the initial stages of an actual or possible data breach. Clients are encouraged
CPET 581 Cloud Computing: Technologies and Enterprise IT Strategies. Virtualization of Clusters and Data Centers
 CPET 581 Cloud Computing: Technologies and Enterprise IT Strategies Lecture 4 Virtualization of Clusters and Data Centers Text Book: Distributed and Cloud Computing, by K. Hwang, G C. Fox, and J.J. Dongarra,
CPET 581 Cloud Computing: Technologies and Enterprise IT Strategies Lecture 4 Virtualization of Clusters and Data Centers Text Book: Distributed and Cloud Computing, by K. Hwang, G C. Fox, and J.J. Dongarra,
Stephen Coty Director, Threat Research
 Emerging threats facing Cloud Computing Stephen Coty Director, Threat Research Cloud Environments 101 Cloud Adoption is Gaining Momentum Cloud market revenue will increase at a 36% annual rate Analyst
Emerging threats facing Cloud Computing Stephen Coty Director, Threat Research Cloud Environments 101 Cloud Adoption is Gaining Momentum Cloud market revenue will increase at a 36% annual rate Analyst
MODULE 3 VIRTUALIZED DATA CENTER COMPUTE
 MODULE 3 VIRTUALIZED DATA CENTER COMPUTE Module 3: Virtualized Data Center Compute Upon completion of this module, you should be able to: Describe compute virtualization Discuss the compute virtualization
MODULE 3 VIRTUALIZED DATA CENTER COMPUTE Module 3: Virtualized Data Center Compute Upon completion of this module, you should be able to: Describe compute virtualization Discuss the compute virtualization
Parallels Virtuozzo Containers
 Parallels Virtuozzo Containers White Paper Top Ten Considerations For Choosing A Server Virtualization Technology www.parallels.com Version 1.0 Table of Contents Introduction... 3 Technology Overview...
Parallels Virtuozzo Containers White Paper Top Ten Considerations For Choosing A Server Virtualization Technology www.parallels.com Version 1.0 Table of Contents Introduction... 3 Technology Overview...
Networking. Sixth Edition. A Beginner's Guide BRUCE HALLBERG
 Networking A Beginner's Guide Sixth Edition BRUCE HALLBERG Mc Graw Hill Education New York Chicago San Francisco Athens London Madrid Mexico City Milan New Delhi Singapore Sydney Toronto Contents Acknowledgments
Networking A Beginner's Guide Sixth Edition BRUCE HALLBERG Mc Graw Hill Education New York Chicago San Francisco Athens London Madrid Mexico City Milan New Delhi Singapore Sydney Toronto Contents Acknowledgments
www.see-grid-sci.eu Regional SEE-GRID-SCI Training for Site Administrators Institute of Physics Belgrade March 5-6, 2009
 SEE-GRID-SCI Virtualization and Grid Computing with XEN www.see-grid-sci.eu Regional SEE-GRID-SCI Training for Site Administrators Institute of Physics Belgrade March 5-6, 2009 Milan Potocnik University
SEE-GRID-SCI Virtualization and Grid Computing with XEN www.see-grid-sci.eu Regional SEE-GRID-SCI Training for Site Administrators Institute of Physics Belgrade March 5-6, 2009 Milan Potocnik University
Enterprise Storage Solution for Hyper-V Private Cloud and VDI Deployments using Sanbolic s Melio Cloud Software Suite April 2011
 Enterprise Storage Solution for Hyper-V Private Cloud and VDI Deployments using Sanbolic s Melio Cloud Software Suite April 2011 Executive Summary Large enterprise Hyper-V deployments with a large number
Enterprise Storage Solution for Hyper-V Private Cloud and VDI Deployments using Sanbolic s Melio Cloud Software Suite April 2011 Executive Summary Large enterprise Hyper-V deployments with a large number
M.Sc. IT Semester III VIRTUALIZATION QUESTION BANK 2014 2015 Unit 1 1. What is virtualization? Explain the five stage virtualization process. 2.
 M.Sc. IT Semester III VIRTUALIZATION QUESTION BANK 2014 2015 Unit 1 1. What is virtualization? Explain the five stage virtualization process. 2. What are the different types of virtualization? Explain
M.Sc. IT Semester III VIRTUALIZATION QUESTION BANK 2014 2015 Unit 1 1. What is virtualization? Explain the five stage virtualization process. 2. What are the different types of virtualization? Explain
In addition to their professional experience, students who attend this training should have technical knowledge in the following areas.
 6422A - Implementing and Managing Windows Server 2008 Hyper-V Course Number: 6422A Course Length: 3 Days Course Overview This three-day instructor-led course teaches students how to implement and manage
6422A - Implementing and Managing Windows Server 2008 Hyper-V Course Number: 6422A Course Length: 3 Days Course Overview This three-day instructor-led course teaches students how to implement and manage
Streamlining Patch Testing and Deployment
 Streamlining Patch Testing and Deployment Using VMware GSX Server with LANDesk Management Suite to improve patch deployment speed and reliability Executive Summary As corporate IT departments work to keep
Streamlining Patch Testing and Deployment Using VMware GSX Server with LANDesk Management Suite to improve patch deployment speed and reliability Executive Summary As corporate IT departments work to keep
Solution Guide Parallels Virtualization for Linux
 Solution Guide Parallels Virtualization for Linux Overview Created in 1991, Linux was designed to be UNIX-compatible software that was composed entirely of open source or free software components. Linux
Solution Guide Parallels Virtualization for Linux Overview Created in 1991, Linux was designed to be UNIX-compatible software that was composed entirely of open source or free software components. Linux
A Survey on Virtual Machine Security
 A Survey on Virtual Machine Security Jenni Susan Reuben Helsinki University of Technology [email protected] Abstract Virtualization plays a major role in helping the organizations to reduce the operational
A Survey on Virtual Machine Security Jenni Susan Reuben Helsinki University of Technology [email protected] Abstract Virtualization plays a major role in helping the organizations to reduce the operational
Virtualization. Michael Tsai 2015/06/08
 Virtualization Michael Tsai 2015/06/08 What is virtualization? Let s first look at a video from VMware http://bcove.me/x9zhalcl Problems? Low utilization Different needs DNS DHCP Web mail 5% 5% 15% 8%
Virtualization Michael Tsai 2015/06/08 What is virtualization? Let s first look at a video from VMware http://bcove.me/x9zhalcl Problems? Low utilization Different needs DNS DHCP Web mail 5% 5% 15% 8%
Acronis Backup & Recovery 10 Workstation. Installation Guide
 Acronis Backup & Recovery 10 Workstation Installation Guide Table of Contents 1. Installation of Acronis Backup & Recovery 10... 3 1.1. Acronis Backup & Recovery 10 components... 3 1.1.1. Agent for Windows...
Acronis Backup & Recovery 10 Workstation Installation Guide Table of Contents 1. Installation of Acronis Backup & Recovery 10... 3 1.1. Acronis Backup & Recovery 10 components... 3 1.1.1. Agent for Windows...
Protecting Virtual Servers with Acronis True Image Echo
 Protecting Virtual Servers with Acronis True Image Echo IT organizations have discovered that virtualization technology can simplify server management and reduce total operating costs. Despite the technical
Protecting Virtual Servers with Acronis True Image Echo IT organizations have discovered that virtualization technology can simplify server management and reduce total operating costs. Despite the technical
VMWare Workstation 11 Installation MICROSOFT WINDOWS SERVER 2008 R2 STANDARD ENTERPRISE ED.
 VMWare Workstation 11 Installation MICROSOFT WINDOWS SERVER 2008 R2 STANDARD ENTERPRISE ED. Starting Vmware Workstation Go to the start menu and start the VMware Workstation program. *If you are using
VMWare Workstation 11 Installation MICROSOFT WINDOWS SERVER 2008 R2 STANDARD ENTERPRISE ED. Starting Vmware Workstation Go to the start menu and start the VMware Workstation program. *If you are using
CA ARCserve Family r15
 CA ARCserve Family r15 Rami Nasser EMEA Principal Consultant, Technical Sales [email protected] The ARCserve Family More than Backup The only solution that: Gives customers control over their changing
CA ARCserve Family r15 Rami Nasser EMEA Principal Consultant, Technical Sales [email protected] The ARCserve Family More than Backup The only solution that: Gives customers control over their changing
Security. Environments. Dave Shackleford. John Wiley &. Sons, Inc. s j}! '**»* t i j. l:i. in: i««;
 Security N Environments '' J J H -. i ^ s j}! Dave Shackleford '**»* t i j i««; l:i in: John Wiley &. Sons, Inc. Contents Introduction.. : xix Chapter l Fundamentals of Virtualization Security Virtualization
Security N Environments '' J J H -. i ^ s j}! Dave Shackleford '**»* t i j i««; l:i in: John Wiley &. Sons, Inc. Contents Introduction.. : xix Chapter l Fundamentals of Virtualization Security Virtualization
Paragon Protect & Restore
 Paragon Protect & Restore ver. 3 Centralized and Disaster Recovery for virtual and physical environments Tight Integration with hypervisors for agentless backups, VM replication and seamless restores Paragon
Paragon Protect & Restore ver. 3 Centralized and Disaster Recovery for virtual and physical environments Tight Integration with hypervisors for agentless backups, VM replication and seamless restores Paragon
Virtualisation. A newsletter for IT Professionals. Issue 2. I. Background of Virtualisation. Hardware
 Virtualisation A newsletter for IT Professionals Issue 2 UEducation Sector Updates I. Background of Virtualisation Virtualisation is the separation of resource or request for a service from the underlying
Virtualisation A newsletter for IT Professionals Issue 2 UEducation Sector Updates I. Background of Virtualisation Virtualisation is the separation of resource or request for a service from the underlying
Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide
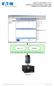 Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide Hyper-V 6.0 NetWatch Main operating system: 2008 Enterprise x64 (hosting Hyper-V) Eaton UPS Eaton NetWatch
Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide Hyper-V 6.0 NetWatch Main operating system: 2008 Enterprise x64 (hosting Hyper-V) Eaton UPS Eaton NetWatch
Remote PC Guide Series - Volume 1
 Introduction and Planning for Remote PC Implementation with NETLAB+ Document Version: 2016-02-01 What is a remote PC and how does it work with NETLAB+? This educational guide will introduce the concepts
Introduction and Planning for Remote PC Implementation with NETLAB+ Document Version: 2016-02-01 What is a remote PC and how does it work with NETLAB+? This educational guide will introduce the concepts
Planning and Designing Microsoft Virtualization Solutions
 Planning and Designing Microsoft Virtualization Solutions 50273: Planning and Designing Microsoft Virtualization Solutions (5 days) About this Course This five-day instructor-led course provides students
Planning and Designing Microsoft Virtualization Solutions 50273: Planning and Designing Microsoft Virtualization Solutions (5 days) About this Course This five-day instructor-led course provides students
Best Practices for Virtualised SharePoint
 Best Practices for Virtualised SharePoint Brendan Law [email protected] @FlamerNZ Flamer.co.nz/spag/ Nathan Mercer [email protected] @NathanM blogs.technet.com/nmercer/ Agenda Why Virtualise? Hardware
Best Practices for Virtualised SharePoint Brendan Law [email protected] @FlamerNZ Flamer.co.nz/spag/ Nathan Mercer [email protected] @NathanM blogs.technet.com/nmercer/ Agenda Why Virtualise? Hardware
Virtual Desktop Infrastructure
 Virtual Desktop Infrastructure Improved manageability and availability spur move to virtualize desktops Many companies have turned to virtualization technologies for their servers and in their data centers
Virtual Desktop Infrastructure Improved manageability and availability spur move to virtualize desktops Many companies have turned to virtualization technologies for their servers and in their data centers
MS-6422A - Implement and Manage Microsoft Windows Server Hyper-V
 MS-6422A - Implement and Manage Microsoft Windows Server Hyper-V Table of Contents Introduction Audience At Completion Prerequisites Microsoft Certified Professional Exams Student Materials Outline Introduction
MS-6422A - Implement and Manage Microsoft Windows Server Hyper-V Table of Contents Introduction Audience At Completion Prerequisites Microsoft Certified Professional Exams Student Materials Outline Introduction
RED HAT ENTERPRISE VIRTUALIZATION FOR SERVERS: COMPETITIVE FEATURES
 RED HAT ENTERPRISE VIRTUALIZATION FOR SERVERS: COMPETITIVE FEATURES RED HAT ENTERPRISE VIRTUALIZATION FOR SERVERS Server virtualization offers tremendous benefits for enterprise IT organizations server
RED HAT ENTERPRISE VIRTUALIZATION FOR SERVERS: COMPETITIVE FEATURES RED HAT ENTERPRISE VIRTUALIZATION FOR SERVERS Server virtualization offers tremendous benefits for enterprise IT organizations server
Virtual Machines Fact Sheet
 Terms Virtual Machines Fact Sheet T1: Host The underlying hardware systems that runs a virtual machine. T2: Virtual Machine Manager (VMM) Also known as a hypervisor, the VMM provides an interface that
Terms Virtual Machines Fact Sheet T1: Host The underlying hardware systems that runs a virtual machine. T2: Virtual Machine Manager (VMM) Also known as a hypervisor, the VMM provides an interface that
Course 50273B: Planning and Designing Microsoft Virtualization Solutions. Level: 300. About this Course
 Course 50273B: Planning and Designing Microsoft Virtualization Solutions Length: 5 Day(s) Level: 300 About this Course This five-day instructor-led course provides students with the knowledge and skills
Course 50273B: Planning and Designing Microsoft Virtualization Solutions Length: 5 Day(s) Level: 300 About this Course This five-day instructor-led course provides students with the knowledge and skills
Protecting Virtual Servers with Acronis True Image
 Protecting Virtual Servers with Acronis True Image Protecting Virtual Servers with Acronis True Image In This Paper Protecting Virtual Servers with Acronis True Image...3 Virtual Machines: The Data Protection
Protecting Virtual Servers with Acronis True Image Protecting Virtual Servers with Acronis True Image In This Paper Protecting Virtual Servers with Acronis True Image...3 Virtual Machines: The Data Protection
VMware Virtual Infrastucture From the Virtualized to the Automated Data Center
 VMware Virtual Infrastucture From the Virtualized to the Automated Data Center Senior System Engineer VMware Inc. [email protected] Agenda Vision VMware Enables Datacenter Automation VMware Solutions
VMware Virtual Infrastucture From the Virtualized to the Automated Data Center Senior System Engineer VMware Inc. [email protected] Agenda Vision VMware Enables Datacenter Automation VMware Solutions
HBA Virtualization Technologies for Windows OS Environments
 HBA Virtualization Technologies for Windows OS Environments FC HBA Virtualization Keeping Pace with Virtualized Data Centers Executive Summary Today, Microsoft offers Virtual Server 2005 R2, a software
HBA Virtualization Technologies for Windows OS Environments FC HBA Virtualization Keeping Pace with Virtualized Data Centers Executive Summary Today, Microsoft offers Virtual Server 2005 R2, a software
Server-centric client virtualization model reduces costs while improving security and flexibility.
 BUSINESS SOLUTIONS Desktop Demystified Server-centric client virtualization model reduces costs while improving security and flexibility. Virtualization is transforming the data center. It s eliminating
BUSINESS SOLUTIONS Desktop Demystified Server-centric client virtualization model reduces costs while improving security and flexibility. Virtualization is transforming the data center. It s eliminating
What s new in Hyper-V 2012 R2
 What s new in Hyper-V 2012 R2 Carsten Rachfahl MVP Virtual Machine Rachfahl IT-Solutions GmbH & Co KG www.hyper-v-server.de Thomas Maurer Cloud Architect & MVP itnetx gmbh www.thomasmaurer.ch Before Windows
What s new in Hyper-V 2012 R2 Carsten Rachfahl MVP Virtual Machine Rachfahl IT-Solutions GmbH & Co KG www.hyper-v-server.de Thomas Maurer Cloud Architect & MVP itnetx gmbh www.thomasmaurer.ch Before Windows
Course Syllabus. Implementing and Managing Windows Server 2008 Hyper-V. Key Data. Audience. At Course Completion. Prerequisites
 Course Syllabus Implementing and Managing Windows Server 2008 Hyper-V Key Data Product #: 3961 Elements of this syllabus are subject to change. This three-day instructor-led course teaches students how
Course Syllabus Implementing and Managing Windows Server 2008 Hyper-V Key Data Product #: 3961 Elements of this syllabus are subject to change. This three-day instructor-led course teaches students how
Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies
 Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies Kurt Klemperer, Principal System Performance Engineer [email protected] Agenda Session Length:
Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies Kurt Klemperer, Principal System Performance Engineer [email protected] Agenda Session Length:
