Selecting Controllers For Networking Environment
|
|
|
- Sheena Edwards
- 10 years ago
- Views:
Transcription
1 Selecting Controllers For Networking Environment Prof. Dr. Alaa AL-Hamami* Soukaena Hassan Hashem** Abstract: Internet is network of networks; the Internet has numerous numbers of Internet sites. Many of these sites are sensitive and protected against the intentional hostile intrusion by strong protection systems. Most of these sites used the firewall protection system to protect them although the protected sites, networks, differs in architectures, addressing, computations and another maters. This paper concentrates on implementation of a proposed protection system on any Internet site with high performance, by control and detects most of networking environment parameters. Such as ports, listening to ports, IP addresses, IP conversion, IP scanning, ping, ping listening, online/offline operations, times of synchronization, TCP/IP requirement, routing operations, Application Programming Interface (API) calls. Keywords: Internet, protection, control, detect. 1- Introduction: To contact with the proposed networking controller first we must identify the important parameters of the proposed controller. Site is a piece of land; exploited for some benefits work. Internet site may be computer, Local Area Network (LAN), or multiple LAN(s) over a piece of land such as university, collage, government agency, office, company, organization, or individual [2,1]. Ports usually ports predefined (0 to 255) to well known applications (i.e., FTP and ). Undefined ports are provided as well, allowing operating system to define their own ports when necessary [3]. For example TELNET connection has number 23 [4]. * Department of Computer Science of Al-Rafidian University College. 1
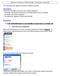
2 ** Department of Computer Science and Information System of the University Of Technology. IP Addressing Each 32-bit IP address is divided into two parts: a prefix and suffix; the two-level hierarchy is designed to make routing efficient. An IP address is a 32-bit long and is commonly expressed as a four decimal number ranging from 0 to 255, with each number separated by a dot [5]. The address prefix identifies the physical network to which the computer attached, while the suffix identifies an individual computer on network [6]. Ping is an Internet Control Message Protocol (ICMP) echo request and replay packets, where ICMP is a protocol used by IP when sends an error message and ICMP uses IP to transport messages [6]. Online/ Offline operations detect the computation of specified host was online or offline. Routing When connecting networks together to form the Internet, the most important protocol is called, not surprising Internet protocol (IP). The Internet protocol is responsible for getting packets of information moved from one network to another, via process called routing. The IP protocol depends 32-bit addressed that uniquely identify each computer (called host) and network. Application programming Interface The interface an application uses when it interacts with transport protocol software is known as an Application Programming Interface (API), it is a bare-bones set of functions provided by the operating system, also is a specific method prescribed by a computer operating system so that a programmer writing an application program can make request of the operating system. An API can be contrasted with an interactive user interface or a command interface as an interface to an operating system. So it represent interface between an application program and the communication protocols in an operating system [6]. 2- The Proposed System Controllers: The proposed system controllers contained in a main menu. This part is the basic level to implement the proposed protection system, the main menu contains all the controllers. It has ten controllers on the right side and other tens on the left side, as shown in figure (1). In addition there are two menu controllers bars in the top of the main menu has the following fields. FILE which contain only Exiting option, View which contain the setting controller and tool bars, TOOLS which contain all the controllers with their specific keys, HELP contain all the information related with the proposed system and the addresses of the site developed the proposed system. The bottom bar contains the product's copyright, IP address of the computer, and the host name of the computer. As shown in figure (2). 2
3 Bandwidth Monitor IP Address Scanner IP Calculator IP Converter Dot/Long Net State Online/Offline Checker Ping Ping Listener Port Scanner Resolve Host or IP TCP/IP Configuration Time Synch Trace Route Whois & MX lookup States Setting Check for Update Web Page About Software Exit Figure (1) Main menu with arrows detects the names of all the controllers. Figure (2) The main menu with menu bars at the top and bottom Bandwidth Monitor Controller menu: This menu detect the most important physical parameter, bandwidth, which determine rate of data transmitting ( sent & received) in kilobyte per second. Estimate both the speed for upload and download. By this controller the system regulates the sent and received packets by the direct and dial up connections. See figure (3). 3
4 Figure (3) The bandwidth monitor menu IP Address Scanner Controller menu: This menu present the start address for scanning as the address of the computer installed on it, and the end address is the last address scanned on the network. The range of the scanned addresses determined by the class of IP address, for example the start IP address is and the class was C then the end address is This controller response to detect all nodes related with the network and mentions their host name if the user want that. There are two buttons in the bottom of the menu the first named Begin Scan response to activate the scanning operation ( through scanning operation the name of the button changed to Stop Scan if the user want to end the scan before it complete) and after the scanning complete would display a message detect the numbers of the nodes related with it. The second button named Close response to close the menu. See figure (4). Figure (4) display the IP scanner when IP scanner operation activated and detected IP Calculator Controller menu: This menu detect the IP address of the computer installed on it, the subnet mask related with the IP address, and the network identification connected to it this computer, see figure (5). This controller is a tool for administrator control, it check if the IP address and subnet mask they are suitable with the network or not. 4
5 This menu has five buttons. The button named Compute Now response to the following operations: Calculate binary information for the IP address, subnet mask, and network ID. Calculate networking information represented by detect the IP Address Class, Address Type, and last ask if the IP address suitable with the host and give the reason. Calculate subnetting information represented by detect the numbers of the subnetworks, numbers of the host, and last the range. Calculate the network ID and the broadcast ID. The second button named Reset response to repeat the work on the menu from beginning. The third Default Mask detected according the IP address if the IP address was class C then the default mask is The fourth button named Save To File save all the information in the IP calculation menu to file. The five button Close response to close the IP calculation menu. In the proposed system this menu gives all the information related to the host connected to a network. Figure (5) The IP calculation menu IP Converter - Dot IP to Long / Long IP to Dot- Controller menu: This menu response to convert the Dot IP address to long IP address and vice versa, also detect IP information, network information which include network class / network number / local host number, and represent the both Dot IP address and Long IP address to binary, see figure (6). This controller convert the doted IP to long IP to perform all the computation operation related with it. This menu have three buttons, the first button named Dot IP address to "long" response to convert the doted IP address to long IP address. The second button named "long" To Dot 5
6 IP Address response to convert the long IP address to doted IP address. The third button named Close response to close the menu. Figure (6) The IP converter menu after use the Dot IP address To "Long" Net Statistical Controller menu: This menu support two options, as shown in figure (7) they are: Use Net Statistical With API: When using this option the user will use Net Stat which is used with direct API calls to windows. It suitable for the user but its work completely depends on functions written by users so it has lowest fast from the second option. Use Net Statistical Built In To Windows: Use this option if the user have problems with the first option. When using this option it will use the built in Net Stat that comes with windows. It is very fast in the working, but it is bad and difficult for the user because it depend on commands. If the user choose the second option then would appear second menu display the Net Stat in windows. This new menu appear as an empty list when the user click the Update button then the results would appear later. As shown in figure (8). This menu has two buttons the first named OK response to activate the option that it selected by the user. The second named Close response to close the menu. Figure (7) The Net Stat menu. Figure (8) Net Statistical in windows contained in Net Stat menu Online / Offline Checker Controller Menu: This menu determine the connected sites and their statues. The statues either be (Online or Offline). The menu has four buttons. The first button named Check response to check the statues for one site selected by the user. The second button named Check All response to check the statues of all the sites founded in that 6
7 menu., The third button named Edit List has new menu response to add new IP addresses, remove selected IP addresses, and last save and exit as shown in figure (9). Figure (9) The online / offline menu Ping Controller Menu: This menu control the pings call. It contains the IP / Host address, number of the pings and last the number of the packet. The ping controller response to check specific site if it is work or may be has a wrong in physical operation, such as the channel may be destroyed. It contains two buttons, as shown in figure (10). The first one named Ping response to display the information about the pings, as shown in figure (11). The second named Close response to close the menu. Figure (10) The ping menu. Figure (11) The ping information menu contained in ping menu 2.8- Port Listener Controller Menu: This menu to listen to the specific determined ports, related to specific determined protocol such as TCP or UDP, it has three buttons as shown in figure (12). This controller response to detect the port work or not, only make request for communication on specific port. The first button named Listen if it clicked then the server begin to listen to the selected port on choice protocol. As shown in figure 7
8 (13). The second button named Stop response to stop the listen of the server if that needed by the user. The third button named Close response to close the menu. Figure (12) port listener menu Figure (13) The menu of listen on UDP protocol contained in port listener menu 2.9- Port Scanner Controller Menu: This menu makes scanning on all the ports from (1) to (65535) it provide the IP address, and has five buttons, as shown in figure (14). This controller detects each port work or not it very important to check the ports of the protected site from the time to time. Figure (14) port scanner menu The first button named Scan response to activate the port scanning operation and detect the ports in list called open ports. The second button named Stop response to stop the port scanning operation if that needed by the user. The third button named Clear response to clean up the list called open port. The fourth button named Save To File response to record a report about the results of the port scanning operation, The fivth button named Close response to close the menu. 8
9 2.10- Resolve Host Or IP Controller Menu: This menu response to convert the host name of the computer to it is IP address and vice versa. this menu has two buttons, as shown in figure (15). The first button named Get response on converts the Host name of the computer to the corresponding IP address. The second button named Get Host Name response to converts the IP address to the host name of the computer. Figure (15) The Get operations in resolve host or IP TCP/IP Configuration Controller Menu: This menu get all the information and fixed information about the TCP/IP configuration related with host connected to the site, as shown in figure (16). These information are adapter name, adapter type, adapter address, IP address, subnet mask, default gateway, DHCP server it is a technique used to detect if there are servers communicate at the time with our server or not. Primary WINS server and secondary WINS server response for the IP forwarding and direct filtering, lease obtained, lease expires and DHCP enable. Also there are fixed information they are host name, node type, net bios scope ID, DNS server, if IP routing enabled, if WINS proxy enabled. 9
10 Figure (16) TCP / IP configuration menu Time Synchronization Controller Menu: This menu response about detects the synchronization time, as shown in figure (17). In the Internet there is a clock, there is a specific port to communicate with it called clock. It is return the times that we are communicate in it, or detect the real time on the Internet. Figure (17) Time synch menu Trace Route Controller Menu: This menu support two options, as shown in figure (18) they are: Use Trace Route With API: When using this option the user will use trace route used with direct API call to windows. Use Trace Route Built In To Windows: Use this option if the user have a problem with the first option. When using this option it will use the built in trace route that comes with windows. If the user choice the second option then would appear second menu display the Trace Route in windows. This new menu appears as an empty list when the user click the trace route button then the results would appear after moments. As shown in figure (19). This menu has two buttons the first named OK response to activate the option that it selected by the user. The second named Close response to close the menu. 10
11 Figure (18) The trace route menu. Figure (19) Trace route built in to windows contained route menu Whois & MX lookup Controller Menu: This menu store the sites of the internet in the MX lookup and when the user want to communicate with one of these site, only write the name of the site in the space after www. And click the lookup button. Then the built in DNS convert the site name to it is corresponding IP address, as shown in figure (20). Figure (20) The whois & MX lookup menu Statistical Controller Menu: This section declare all the statistically of TCP, IP, ICMP ( IN), ICMP (OUT) protocols, as shown in figure (21). For example in IP the time to live statistical. All these information may be changed and updated continuously. Figure (21) The statistical menu Setting Controller Menu: 11
12 This menu response to set some parameters such as enable sound in the start of the software and shutting down, also begin the software as maximized picture, last enable the bandwidth meter, as shown in figure (22). Figure (22) The setting menu Check For Update Controller Menu: This menu response to checking for the updating of the system for all it is releases and versions. This menu include many fields always would be updated such as current version, update version, update release date, update file name and file size. The button response to activate the checking and updating named Information, when it clicked all the information of updating would be displayed in the list beside it, as shown in figure (23). Figure (23) The check for update menu. This menu also include information on file down load progress such as total size, received size speed, time remaining, elapsed time. The button named update response to file down load progress About CS Internet Tools Controller Menu: This menu response to declare the name of the company, CS Internet Tools, version of the proposed system, the product label, coy rights, and last the web of the 12
13 proposed company, as shown in figure (24). This menu has Information System button response to display all the information related with the proposed controllers, as shown in figure (25). Figure (24) About controller. Figure (25) the information menu contained in about CS internet tools menu. For information about the product connect with the web of the proposed company, as shown in figure (26). Figure (26) The request of information menu Web Page Controller Menu: This menu is response to make the interaction between the users inside the site and the users outside it. This menu would display all the downloaded and uploaded files Exit Controller : This controller response to exit from the proposed system controller. Exit the controller and then return to windows desktop. 3- Conclusions: 13
14 The study shows that, to protect an Internet site by any proposed protection system at first we must have powerful knowledge about the site environment. By using the proposed controller system. The site administrators would detect numbers of nodes in the site, the type of the addressing and all the information related with it. Also the open ports, the statistically of transmission protocols, TCP/IP configuration for each node, routing information, information about any site the administrators want to communicate with it and another important parameters. All that would simplify the implementation of the proposed protection systems on any site. 4- References: 1- IDG S 3D Visual series, Internet and World Wide Web Simplified, Maran Graphics, Ins, Halsall.F., Data Communication,Computer Networks and Open System, Fourth Edition, Addision-wesley Publishing Company Inc., Russell.T., Telecommunication Protocols, Second Edition, Mc- Graw Hill Companies,Inc., Buchanan.W., Advanced Data Communications and Networks, First Edition,Chapman,Hall, Held.G., Understanding Data Communication, Fifth Edition, Prentice-Hall, Comer.D.E., Computer Network and Internets with Internet Application,Third Edition, Prentice-Hall, Inc.,
15 الخالصة: Selecting Controllers For Networking Environment أ.د عالء حسين الحمامي* سكينة حسن هاشم** االنترنيت شبكة من الشبكات. يتكون من عدد اكثرهاا المواقع من جدا" كبير تكاون محمياة ضد التطفل الحتوائها على معلومات سرية وذلك على االغلب أنظماة بواساطة جادران الناار على الرغم من اختالف المواقع في معمارياتها وعنونتها و قضايا اخرى. هذا البحث يركز علاى أي امكانياة تنفياذ نظاا حماياة مرتارل علاى أي موقاع ماع فعالياة عالياة مان خاالس السايطر علاى بي اة الشابكة فاي الموقاع و تحدياد كال العوامال والتاي بهاا المتعلراة تشمل ports, listening to ports, IP addresses, IP conversion, IP scanning, ping, ping listening, online/offline operations, times of synchronization, TCP/IP requirement, routing operations, Application Programming Interface (API) calls.and aothers. 15
16 قسم علم احلاسبات يف كلية الرافدين اجلامعة. قسم علم احلاسبات و نظم املعلومات يف اجلامعة التكنولوجية. * ** 16
CS 326e F2002 Lab 1. Basic Network Setup & Ethereal Time: 2 hrs
 CS 326e F2002 Lab 1. Basic Network Setup & Ethereal Time: 2 hrs Tasks: 1 (10 min) Verify that TCP/IP is installed on each of the computers 2 (10 min) Connect the computers together via a switch 3 (10 min)
CS 326e F2002 Lab 1. Basic Network Setup & Ethereal Time: 2 hrs Tasks: 1 (10 min) Verify that TCP/IP is installed on each of the computers 2 (10 min) Connect the computers together via a switch 3 (10 min)
1 Data information is sent onto the network cable using which of the following? A Communication protocol B Data packet
 Review questions 1 Data information is sent onto the network cable using which of the following? A Communication protocol B Data packet C Media access method D Packages 2 To which TCP/IP architecture layer
Review questions 1 Data information is sent onto the network cable using which of the following? A Communication protocol B Data packet C Media access method D Packages 2 To which TCP/IP architecture layer
Firewall Defaults and Some Basic Rules
 Firewall Defaults and Some Basic Rules ProSecure UTM Quick Start Guide This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSecure Unified
Firewall Defaults and Some Basic Rules ProSecure UTM Quick Start Guide This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSecure Unified
Firewall VPN Router. Quick Installation Guide M73-APO09-380
 Firewall VPN Router Quick Installation Guide M73-APO09-380 Firewall VPN Router Overview The Firewall VPN Router provides three 10/100Mbit Ethernet network interface ports which are the Internal/LAN, External/WAN,
Firewall VPN Router Quick Installation Guide M73-APO09-380 Firewall VPN Router Overview The Firewall VPN Router provides three 10/100Mbit Ethernet network interface ports which are the Internal/LAN, External/WAN,
Multi-Homing Dual WAN Firewall Router
 Multi-Homing Dual WAN Firewall Router Quick Installation Guide M73-APO09-400 Multi-Homing Dual WAN Firewall Router Overview The Multi-Homing Dual WAN Firewall Router provides three 10/100Mbit Ethernet
Multi-Homing Dual WAN Firewall Router Quick Installation Guide M73-APO09-400 Multi-Homing Dual WAN Firewall Router Overview The Multi-Homing Dual WAN Firewall Router provides three 10/100Mbit Ethernet
Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0
 Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0 Course length: 5 Days Course No. 688 - Five days - Instructor-led Introduction This course provides students with the knowledge and skills required
Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0 Course length: 5 Days Course No. 688 - Five days - Instructor-led Introduction This course provides students with the knowledge and skills required
Multi-Homing Security Gateway
 Multi-Homing Security Gateway MH-5000 Quick Installation Guide 1 Before You Begin It s best to use a computer with an Ethernet adapter for configuring the MH-5000. The default IP address for the MH-5000
Multi-Homing Security Gateway MH-5000 Quick Installation Guide 1 Before You Begin It s best to use a computer with an Ethernet adapter for configuring the MH-5000. The default IP address for the MH-5000
H0/H2/H4 -ECOM100 DHCP & HTML Configuration. H0/H2/H4--ECOM100 DHCP Disabling DHCP and Assigning a Static IP Address Using HTML Configuration
 H0/H2/H4 -ECOM100 DHCP & HTML 6 H0/H2/H4--ECOM100 DHCP Disabling DHCP and Assigning a Static IP Address Using HTML 6-2 H0/H2/H4 -ECOM100 DHCP DHCP Issues The H0/H2/H4--ECOM100 is configured at the factory
H0/H2/H4 -ECOM100 DHCP & HTML 6 H0/H2/H4--ECOM100 DHCP Disabling DHCP and Assigning a Static IP Address Using HTML 6-2 H0/H2/H4 -ECOM100 DHCP DHCP Issues The H0/H2/H4--ECOM100 is configured at the factory
Multi-Homing Gateway. User s Manual
 Multi-Homing Gateway User s Manual Contents System 5 Admin Setting Date/Time Multiple Subnet Hack Alert Route Table DHCP DNS Proxy Dynamic DNS Language Permitted IPs Logout Software Update 8 12 21 22 33
Multi-Homing Gateway User s Manual Contents System 5 Admin Setting Date/Time Multiple Subnet Hack Alert Route Table DHCP DNS Proxy Dynamic DNS Language Permitted IPs Logout Software Update 8 12 21 22 33
Firewall Firewall August, 2003
 Firewall August, 2003 1 Firewall and Access Control This product also serves as an Internet firewall, not only does it provide a natural firewall function (Network Address Translation, NAT), but it also
Firewall August, 2003 1 Firewall and Access Control This product also serves as an Internet firewall, not only does it provide a natural firewall function (Network Address Translation, NAT), but it also
LAN TCP/IP and DHCP Setup
 CHAPTER 2 LAN TCP/IP and DHCP Setup 2.1 Introduction In this chapter, we will explain in more detail the LAN TCP/IP and DHCP Setup. 2.2 LAN IP Network Configuration In the Vigor 2900 router, there are
CHAPTER 2 LAN TCP/IP and DHCP Setup 2.1 Introduction In this chapter, we will explain in more detail the LAN TCP/IP and DHCP Setup. 2.2 LAN IP Network Configuration In the Vigor 2900 router, there are
10.3.1.8 Lab - Configure a Windows 7 Firewall
 5.0 10.3.1.8 Lab - Configure a Windows 7 Firewall Print and complete this lab. In this lab, you will explore the Windows 7 Firewall and configure some advanced settings. Recommended Equipment Step 1 Two
5.0 10.3.1.8 Lab - Configure a Windows 7 Firewall Print and complete this lab. In this lab, you will explore the Windows 7 Firewall and configure some advanced settings. Recommended Equipment Step 1 Two
Ethernet Port Quick Start Manual
 Ethernet Port Quick Start Manual THIS MANUAL CONTAINS TECHNICAL INFORMATION FOR THE ETHERNET PORT OF EDI SIGNAL MONITORS with Ethernet Version 1.5 firmware. DETAILS OF THE ECCOM OPERATION ARE DESCRIBED
Ethernet Port Quick Start Manual THIS MANUAL CONTAINS TECHNICAL INFORMATION FOR THE ETHERNET PORT OF EDI SIGNAL MONITORS with Ethernet Version 1.5 firmware. DETAILS OF THE ECCOM OPERATION ARE DESCRIBED
FortKnox Personal Firewall
 FortKnox Personal Firewall User Manual Document version 1.4 EN ( 15. 9. 2009 ) Copyright (c) 2007-2009 NETGATE Technologies s.r.o. All rights reserved. This product uses compression library zlib Copyright
FortKnox Personal Firewall User Manual Document version 1.4 EN ( 15. 9. 2009 ) Copyright (c) 2007-2009 NETGATE Technologies s.r.o. All rights reserved. This product uses compression library zlib Copyright
In this lab you will explore the Windows XP Firewall and configure some advanced settings.
 16.3.2 Lab: Configure Windows XP Firewall Print and complete this lab. In this lab you will explore the Windows XP Firewall and configure some advanced settings. Recommended Equipment Two computers directly
16.3.2 Lab: Configure Windows XP Firewall Print and complete this lab. In this lab you will explore the Windows XP Firewall and configure some advanced settings. Recommended Equipment Two computers directly
Version 0.1 June 2010. Xerox WorkCentre 7120 Fax over Internet Protocol (FoIP)
 Version 0.1 June 2010 Xerox WorkCentre 7120 Fax over Internet Protocol (FoIP) Thank you for choosing the Xerox WorkCentre 7120. Table of Contents Introduction.........................................
Version 0.1 June 2010 Xerox WorkCentre 7120 Fax over Internet Protocol (FoIP) Thank you for choosing the Xerox WorkCentre 7120. Table of Contents Introduction.........................................
SIP Proxy Server. Administrator Installation and Configuration Guide. V2.31b. 09SIPXM.SY2.31b.EN3
 SIP Proxy Server Administrator Installation and Configuration Guide V2.31b 09SIPXM.SY2.31b.EN3 DSG, DSG logo, InterPBX, InterServer, Blaze Series, VG5000, VG7000, IP590, IP580, IP500, IP510, InterConsole,
SIP Proxy Server Administrator Installation and Configuration Guide V2.31b 09SIPXM.SY2.31b.EN3 DSG, DSG logo, InterPBX, InterServer, Blaze Series, VG5000, VG7000, IP590, IP580, IP500, IP510, InterConsole,
Networking Basics for Automation Engineers
 Networking Basics for Automation Engineers Page 1 of 10 mac-solutions.co.uk v1.0 Oct 2014 1. What is Transmission Control Protocol/Internet Protocol (TCP/IP)------------------------------------------------------------
Networking Basics for Automation Engineers Page 1 of 10 mac-solutions.co.uk v1.0 Oct 2014 1. What is Transmission Control Protocol/Internet Protocol (TCP/IP)------------------------------------------------------------
10.3.1.10 Lab - Configure a Windows XP Firewall
 5.0 10.3.1.10 Lab - Configure a Windows XP Firewall Print and complete this lab. In this lab, you will explore the Windows XP Firewall and configure some advanced settings. Recommended Equipment Step 1
5.0 10.3.1.10 Lab - Configure a Windows XP Firewall Print and complete this lab. In this lab, you will explore the Windows XP Firewall and configure some advanced settings. Recommended Equipment Step 1
Configuring the WT-4 for ftp (Ad-hoc Mode)
 En Configuring the WT-4 for ftp (Ad-hoc Mode) Windows XP Introduction This document provides basic instructions on configuring the WT-4 wireless transmitter and a Windows XP Professional SP2 ftp server
En Configuring the WT-4 for ftp (Ad-hoc Mode) Windows XP Introduction This document provides basic instructions on configuring the WT-4 wireless transmitter and a Windows XP Professional SP2 ftp server
EXPLORER. TFT Filter CONFIGURATION
 EXPLORER TFT Filter Configuration Page 1 of 9 EXPLORER TFT Filter CONFIGURATION Thrane & Thrane Author: HenrikMøller Rev. PA4 Page 1 6/15/2006 EXPLORER TFT Filter Configuration Page 2 of 9 1 Table of Content
EXPLORER TFT Filter Configuration Page 1 of 9 EXPLORER TFT Filter CONFIGURATION Thrane & Thrane Author: HenrikMøller Rev. PA4 Page 1 6/15/2006 EXPLORER TFT Filter Configuration Page 2 of 9 1 Table of Content
Optimum Business SIP Trunk Set-up Guide
 Optimum Business SIP Trunk Set-up Guide For use with IP PBX only. SIPSetup 07.13 FOR USE WITH IP PBX ONLY Important: If your PBX is configured to use a PRI connection, do not use this guide. If you need
Optimum Business SIP Trunk Set-up Guide For use with IP PBX only. SIPSetup 07.13 FOR USE WITH IP PBX ONLY Important: If your PBX is configured to use a PRI connection, do not use this guide. If you need
Broadband Phone Gateway BPG510 Technical Users Guide
 Broadband Phone Gateway BPG510 Technical Users Guide (Firmware version 0.14.1 and later) Revision 1.0 2006, 8x8 Inc. Table of Contents About your Broadband Phone Gateway (BPG510)... 4 Opening the BPG510's
Broadband Phone Gateway BPG510 Technical Users Guide (Firmware version 0.14.1 and later) Revision 1.0 2006, 8x8 Inc. Table of Contents About your Broadband Phone Gateway (BPG510)... 4 Opening the BPG510's
UIP1868P User Interface Guide
 UIP1868P User Interface Guide (Firmware version 0.13.4 and later) V1.1 Monday, July 8, 2005 Table of Contents Opening the UIP1868P's Configuration Utility... 3 Connecting to Your Broadband Modem... 4 Setting
UIP1868P User Interface Guide (Firmware version 0.13.4 and later) V1.1 Monday, July 8, 2005 Table of Contents Opening the UIP1868P's Configuration Utility... 3 Connecting to Your Broadband Modem... 4 Setting
Introduction to Network Security Lab 1 - Wireshark
 Introduction to Network Security Lab 1 - Wireshark Bridges To Computing 1 Introduction: In our last lecture we discussed the Internet the World Wide Web and the Protocols that are used to facilitate communication
Introduction to Network Security Lab 1 - Wireshark Bridges To Computing 1 Introduction: In our last lecture we discussed the Internet the World Wide Web and the Protocols that are used to facilitate communication
Firewall Defaults, Public Server Rule, and Secondary WAN IP Address
 Firewall Defaults, Public Server Rule, and Secondary WAN IP Address This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSafe Wireless-N
Firewall Defaults, Public Server Rule, and Secondary WAN IP Address This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSafe Wireless-N
About Firewall Protection
 1. This guide describes how to configure basic firewall rules in the UTM to protect your network. The firewall then can provide secure, encrypted communications between your local network and a remote
1. This guide describes how to configure basic firewall rules in the UTM to protect your network. The firewall then can provide secure, encrypted communications between your local network and a remote
PART IV. Network Layer
 PART IV Network Layer Position of network layer Network layer duties Internetworking : heterogeneous Physical Networks To look Like a single network to he upper layers The address at Network layer must
PART IV Network Layer Position of network layer Network layer duties Internetworking : heterogeneous Physical Networks To look Like a single network to he upper layers The address at Network layer must
Computer Networks I Laboratory Exercise 1
 Computer Networks I Laboratory Exercise 1 The lab is divided into two parts where the first part is a basic PC network TCP/IP configuration and connection to the Internet. The second part is building a
Computer Networks I Laboratory Exercise 1 The lab is divided into two parts where the first part is a basic PC network TCP/IP configuration and connection to the Internet. The second part is building a
Transport and Network Layer
 Transport and Network Layer 1 Introduction Responsible for moving messages from end-to-end in a network Closely tied together TCP/IP: most commonly used protocol o Used in Internet o Compatible with a
Transport and Network Layer 1 Introduction Responsible for moving messages from end-to-end in a network Closely tied together TCP/IP: most commonly used protocol o Used in Internet o Compatible with a
TCP/IP works on 3 types of services (cont.): TCP/IP protocols are divided into three categories:
 Due to the number of hardware possibilities for a network, there must be a set of rules for how data should be transmitted across the connection media. A protocol defines how the network devices and computers
Due to the number of hardware possibilities for a network, there must be a set of rules for how data should be transmitted across the connection media. A protocol defines how the network devices and computers
Device Installer User Guide
 Device Installer User Guide Part Number 900-325 Revision B 12/08 Table Of Contents 1. Overview... 1 2. Devices... 2 Choose the Network Adapter for Communication... 2 Search for All Devices on the Network...
Device Installer User Guide Part Number 900-325 Revision B 12/08 Table Of Contents 1. Overview... 1 2. Devices... 2 Choose the Network Adapter for Communication... 2 Search for All Devices on the Network...
1. Firewall Configuration
 1. Firewall Configuration A firewall is a method of implementing common as well as user defined security policies in an effort to keep intruders out. Firewalls work by analyzing and filtering out IP packets
1. Firewall Configuration A firewall is a method of implementing common as well as user defined security policies in an effort to keep intruders out. Firewalls work by analyzing and filtering out IP packets
Setting up and creating a Local Area Network (LAN) within Windows XP by Buzzons
 Setting up and creating a Local Area Network (LAN) within Windows XP by Buzzons Step 1) Open the start menu, navigate to control panel, and select your network card: Step 2) Click the network card, to
Setting up and creating a Local Area Network (LAN) within Windows XP by Buzzons Step 1) Open the start menu, navigate to control panel, and select your network card: Step 2) Click the network card, to
E-Mon Communication Gateway Utility Instructions for BACnet/mstp
 E-Mon Communication Gateway Utility Instructions for BACnet/mstp The E-Mon Communication Gateway utility will allow you to configure the Device Instance (Node ID) and other parameters needed for your BACnet/mstp
E-Mon Communication Gateway Utility Instructions for BACnet/mstp The E-Mon Communication Gateway utility will allow you to configure the Device Instance (Node ID) and other parameters needed for your BACnet/mstp
Basic Network Configuration
 Basic Network Configuration 2 Table of Contents Basic Network Configuration... 25 LAN (local area network) vs WAN (wide area network)... 25 Local Area Network... 25 Wide Area Network... 26 Accessing the
Basic Network Configuration 2 Table of Contents Basic Network Configuration... 25 LAN (local area network) vs WAN (wide area network)... 25 Local Area Network... 25 Wide Area Network... 26 Accessing the
10.3.1.9 Lab - Configure a Windows Vista Firewall
 5.0 10.3.1.9 Lab - Configure a Windows Vista Firewall Print and complete this lab. In this lab, you will explore the Windows Vista Firewall and configure some advanced settings. Recommended Equipment Step
5.0 10.3.1.9 Lab - Configure a Windows Vista Firewall Print and complete this lab. In this lab, you will explore the Windows Vista Firewall and configure some advanced settings. Recommended Equipment Step
Protecting the Home Network (Firewall)
 Protecting the Home Network (Firewall) Basic Tab Setup Tab DHCP Tab Advanced Tab Options Tab Port Forwarding Tab Port Triggers Tab DMZ Host Tab Firewall Tab Event Log Tab Status Tab Software Tab Connection
Protecting the Home Network (Firewall) Basic Tab Setup Tab DHCP Tab Advanced Tab Options Tab Port Forwarding Tab Port Triggers Tab DMZ Host Tab Firewall Tab Event Log Tab Status Tab Software Tab Connection
How to configure DVR and computer for running Remote Viewer via IP network
 How to configure DVR and computer for running Remote Viewer via IP network Follow these steps to configure a network DVR and a computer with Remote Viewer software to see live pictures via IP network.
How to configure DVR and computer for running Remote Viewer via IP network Follow these steps to configure a network DVR and a computer with Remote Viewer software to see live pictures via IP network.
Chapter 4 Managing Your Network
 Chapter 4 Managing Your Network This chapter describes how to perform network management tasks with your ADSL2+ Modem Wireless Router. Backing Up, Restoring, or Erasing Your Settings The configuration
Chapter 4 Managing Your Network This chapter describes how to perform network management tasks with your ADSL2+ Modem Wireless Router. Backing Up, Restoring, or Erasing Your Settings The configuration
DO NOT REPLICATE. Analyze IP. Given a Windows Server 2003 computer, you will use Network Monitor to view and analyze all the fields of IP.
 Advanced TCP/IP Overview There is one primary set of protocols that runs networks and the Internet today. In this lesson, you will work with those protocols: the Transmission Control Protocol (TCP) and
Advanced TCP/IP Overview There is one primary set of protocols that runs networks and the Internet today. In this lesson, you will work with those protocols: the Transmission Control Protocol (TCP) and
Implementing Network Address Translation and Port Redirection in epipe
 Implementing Network Address Translation and Port Redirection in epipe Contents 1 Introduction... 2 2 Network Address Translation... 2 2.1 What is NAT?... 2 2.2 NAT Redirection... 3 2.3 Bimap... 4 2.4
Implementing Network Address Translation and Port Redirection in epipe Contents 1 Introduction... 2 2 Network Address Translation... 2 2.1 What is NAT?... 2 2.2 NAT Redirection... 3 2.3 Bimap... 4 2.4
IP Filter/Firewall Setup
 IP Filter/Firewall Setup Introduction The IP Filter/Firewall function helps protect your local network against attack from outside. It also provides a method of restricting users on the local network from
IP Filter/Firewall Setup Introduction The IP Filter/Firewall function helps protect your local network against attack from outside. It also provides a method of restricting users on the local network from
Network Configuration Settings
 Network Configuration Settings Many small businesses already have an existing firewall device for their local network when they purchase Microsoft Windows Small Business Server 2003. Often, these devices
Network Configuration Settings Many small businesses already have an existing firewall device for their local network when they purchase Microsoft Windows Small Business Server 2003. Often, these devices
Lab 8.3.2 Conducting a Network Capture with Wireshark
 Lab 8.3.2 Conducting a Network Capture with Wireshark Objectives Perform a network traffic capture with Wireshark to become familiar with the Wireshark interface and environment. Analyze traffic to a web
Lab 8.3.2 Conducting a Network Capture with Wireshark Objectives Perform a network traffic capture with Wireshark to become familiar with the Wireshark interface and environment. Analyze traffic to a web
Networking Test 4 Study Guide
 Networking Test 4 Study Guide True/False Indicate whether the statement is true or false. 1. IPX/SPX is considered the protocol suite of the Internet, and it is the most widely used protocol suite in LANs.
Networking Test 4 Study Guide True/False Indicate whether the statement is true or false. 1. IPX/SPX is considered the protocol suite of the Internet, and it is the most widely used protocol suite in LANs.
Prestige 202H Plus. Quick Start Guide. ISDN Internet Access Router. Version 3.40 12/2004
 Prestige 202H Plus ISDN Internet Access Router Quick Start Guide Version 3.40 12/2004 Table of Contents 1 Introducing the Prestige...3 2 Hardware Installation...4 2.1 Rear Panel...4 2.2 The Front Panel
Prestige 202H Plus ISDN Internet Access Router Quick Start Guide Version 3.40 12/2004 Table of Contents 1 Introducing the Prestige...3 2 Hardware Installation...4 2.1 Rear Panel...4 2.2 The Front Panel
BASIC ANALYSIS OF TCP/IP NETWORKS
 BASIC ANALYSIS OF TCP/IP NETWORKS INTRODUCTION Communication analysis provides powerful tool for maintenance, performance monitoring, attack detection, and problems fixing in computer networks. Today networks
BASIC ANALYSIS OF TCP/IP NETWORKS INTRODUCTION Communication analysis provides powerful tool for maintenance, performance monitoring, attack detection, and problems fixing in computer networks. Today networks
Configuring the WT-4 for Upload to a Computer (Ad-hoc Mode)
 En Configuring the WT-4 for Upload to a Computer (Ad-hoc Mode) This document provides basic instructions on configuring the WT-4 wireless transmitter and a computer for transmission over an ad-hoc (peer-to-peer)
En Configuring the WT-4 for Upload to a Computer (Ad-hoc Mode) This document provides basic instructions on configuring the WT-4 wireless transmitter and a computer for transmission over an ad-hoc (peer-to-peer)
Network Terminology Review
 Network Terminology Review For those of you who have experience with IP networks, this document may serve as a reminder of the current lexicon of terms used in our industry. If you re new to it or specialized
Network Terminology Review For those of you who have experience with IP networks, this document may serve as a reminder of the current lexicon of terms used in our industry. If you re new to it or specialized
Follow these steps to prepare the module and evaluation board for testing.
 2 Getting Started 2.1. Hardware Installation Procedure Follow these steps to prepare the module and evaluation board for testing. STEP1: Plug the EG-SR-7100A module into the sockets on the test board.
2 Getting Started 2.1. Hardware Installation Procedure Follow these steps to prepare the module and evaluation board for testing. STEP1: Plug the EG-SR-7100A module into the sockets on the test board.
Computer Networks/DV2 Lab
 Computer Networks/DV2 Lab Room: BB 219 Additional Information: http://www.fb9dv.uni-duisburg.de/ti/en/education/teaching/ss08/netlab Equipment for each group: - 1 Server computer (OS: Windows 2000 Advanced
Computer Networks/DV2 Lab Room: BB 219 Additional Information: http://www.fb9dv.uni-duisburg.de/ti/en/education/teaching/ss08/netlab Equipment for each group: - 1 Server computer (OS: Windows 2000 Advanced
1 PC to WX64 direction connection with crossover cable or hub/switch
 1 PC to WX64 direction connection with crossover cable or hub/switch If a network is not available, or if it is desired to keep the WX64 and PC(s) completely separated from other computers, a simple network
1 PC to WX64 direction connection with crossover cable or hub/switch If a network is not available, or if it is desired to keep the WX64 and PC(s) completely separated from other computers, a simple network
Packet Tracer 3 Lab VLSM 2 Solution
 Packet Tracer 3 Lab VLSM 2 Solution Objective Create a simulated network topology using Packet Tracer Design an IP addressing scheme using a Class B subnetwork address and VLSM Apply IP addresses to the
Packet Tracer 3 Lab VLSM 2 Solution Objective Create a simulated network topology using Packet Tracer Design an IP addressing scheme using a Class B subnetwork address and VLSM Apply IP addresses to the
Chapter 3 LAN Configuration
 Chapter 3 LAN Configuration This chapter describes how to configure the advanced LAN features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. This chapter contains the following sections
Chapter 3 LAN Configuration This chapter describes how to configure the advanced LAN features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. This chapter contains the following sections
SSVP SIP School VoIP Professional Certification
 SSVP SIP School VoIP Professional Certification Exam Objectives The SSVP exam is designed to test your skills and knowledge on the basics of Networking and Voice over IP. Everything that you need to cover
SSVP SIP School VoIP Professional Certification Exam Objectives The SSVP exam is designed to test your skills and knowledge on the basics of Networking and Voice over IP. Everything that you need to cover
Multifunctional Broadband Router User Guide. Copyright Statement
 Copyright Statement is the registered trademark of Shenzhen Tenda Technology Co., Ltd. Other trademark or trade name mentioned herein are the trademark or registered trademark of above company. Copyright
Copyright Statement is the registered trademark of Shenzhen Tenda Technology Co., Ltd. Other trademark or trade name mentioned herein are the trademark or registered trademark of above company. Copyright
Step-by-Step Guide for Setting Up IPv6 in a Test Lab
 Step-by-Step Guide for Setting Up IPv6 in a Test Lab Microsoft Corporation Published: July, 2006 Author: Microsoft Corporation Abstract This guide describes how to configure Internet Protocol version 6
Step-by-Step Guide for Setting Up IPv6 in a Test Lab Microsoft Corporation Published: July, 2006 Author: Microsoft Corporation Abstract This guide describes how to configure Internet Protocol version 6
Technical Support Information Belkin internal use only
 The fundamentals of TCP/IP networking TCP/IP (Transmission Control Protocol / Internet Protocols) is a set of networking protocols that is used for communication on the Internet and on many other networks.
The fundamentals of TCP/IP networking TCP/IP (Transmission Control Protocol / Internet Protocols) is a set of networking protocols that is used for communication on the Internet and on many other networks.
You can probably work with decimal. binary numbers needed by the. Working with binary numbers is time- consuming & error-prone.
 IP Addressing & Subnetting Made Easy Working with IP Addresses Introduction You can probably work with decimal numbers much easier than with the binary numbers needed by the computer. Working with binary
IP Addressing & Subnetting Made Easy Working with IP Addresses Introduction You can probably work with decimal numbers much easier than with the binary numbers needed by the computer. Working with binary
Configuration Guide. DHCP Server. LAN client
 DHCP Server Configuration Guide 4.0 DHCP Server LAN client LAN client LAN client Copyright 2007, F/X Communications. All Rights Reserved. The use and copying of this product is subject to a license agreement.
DHCP Server Configuration Guide 4.0 DHCP Server LAN client LAN client LAN client Copyright 2007, F/X Communications. All Rights Reserved. The use and copying of this product is subject to a license agreement.
Chapter 6 Using Network Monitoring Tools
 Chapter 6 Using Network Monitoring Tools This chapter describes how to use the maintenance features of your Wireless-G Router Model WGR614v9. You can access these features by selecting the items under
Chapter 6 Using Network Monitoring Tools This chapter describes how to use the maintenance features of your Wireless-G Router Model WGR614v9. You can access these features by selecting the items under
Chapter 6 Using Network Monitoring Tools
 Chapter 6 Using Network Monitoring Tools This chapter describes how to use the maintenance features of your RangeMax Wireless-N Gigabit Router WNR3500. You can access these features by selecting the items
Chapter 6 Using Network Monitoring Tools This chapter describes how to use the maintenance features of your RangeMax Wireless-N Gigabit Router WNR3500. You can access these features by selecting the items
Network Scanner Tool R3.1. User s Guide Version 3.0.04
 Network Scanner Tool R3.1 User s Guide Version 3.0.04 Copyright 2000-2004 by Sharp Corporation. All rights reserved. Reproduction, adaptation or translation without prior written permission is prohibited,
Network Scanner Tool R3.1 User s Guide Version 3.0.04 Copyright 2000-2004 by Sharp Corporation. All rights reserved. Reproduction, adaptation or translation without prior written permission is prohibited,
Chapter 8 Router and Network Management
 Chapter 8 Router and Network Management This chapter describes how to use the network management features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. These features can be found by
Chapter 8 Router and Network Management This chapter describes how to use the network management features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. These features can be found by
Installing and Setting up Microsoft DNS Server
 Training Installing and Setting up Microsoft DNS Server Introduction Versions Used Windows Server 2003 Setup Used i. Server Name = martini ii. Credentials: User = Administrator, Password = password iii.
Training Installing and Setting up Microsoft DNS Server Introduction Versions Used Windows Server 2003 Setup Used i. Server Name = martini ii. Credentials: User = Administrator, Password = password iii.
Configuring a Backup Path Test Using Network Monitoring
 6AOSCG0006-29B February 2011 Configuration Guide Configuring a Backup Path Test Using Network Monitoring This configuration guide describes how to configure a demand routing test call to test the availability
6AOSCG0006-29B February 2011 Configuration Guide Configuring a Backup Path Test Using Network Monitoring This configuration guide describes how to configure a demand routing test call to test the availability
2. IP Networks, IP Hosts and IP Ports
 1. Introduction to IP... 1 2. IP Networks, IP Hosts and IP Ports... 1 3. IP Packet Structure... 2 4. IP Address Structure... 2 Network Portion... 2 Host Portion... 3 Global vs. Private IP Addresses...3
1. Introduction to IP... 1 2. IP Networks, IP Hosts and IP Ports... 1 3. IP Packet Structure... 2 4. IP Address Structure... 2 Network Portion... 2 Host Portion... 3 Global vs. Private IP Addresses...3
Software installation and configuration IEC-line series
 Software installation and configuration IEC-line series update: 04-10-2014 IEC-line by OVERDIGIT overdigit.com Table of contents 1. Installing the software... 3 1.1. Installing CoDeSys... 4 1.2. Installing
Software installation and configuration IEC-line series update: 04-10-2014 IEC-line by OVERDIGIT overdigit.com Table of contents 1. Installing the software... 3 1.1. Installing CoDeSys... 4 1.2. Installing
Guideline for setting up a functional VPN
 Guideline for setting up a functional VPN Why do I want a VPN? VPN by definition creates a private, trusted network across an untrusted medium. It allows you to connect offices and people from around the
Guideline for setting up a functional VPN Why do I want a VPN? VPN by definition creates a private, trusted network across an untrusted medium. It allows you to connect offices and people from around the
MN-700 Base Station Configuration Guide
 MN-700 Base Station Configuration Guide Contents pen the Base Station Management Tool...3 Log ff the Base Station Management Tool...3 Navigate the Base Station Management Tool...4 Current Base Station
MN-700 Base Station Configuration Guide Contents pen the Base Station Management Tool...3 Log ff the Base Station Management Tool...3 Navigate the Base Station Management Tool...4 Current Base Station
Overview of Network Security The need for network security Desirable security properties Common vulnerabilities Security policy designs
 Overview of Network Security The need for network security Desirable security properties Common vulnerabilities Security policy designs Why Network Security? Keep the bad guys out. (1) Closed networks
Overview of Network Security The need for network security Desirable security properties Common vulnerabilities Security policy designs Why Network Security? Keep the bad guys out. (1) Closed networks
Troubleshooting Tools
 Troubleshooting Tools An overview of the main tools for verifying network operation from a host Fulvio Risso Mario Baldi Politecnico di Torino (Technical University of Turin) see page 2 Notes n The commands/programs
Troubleshooting Tools An overview of the main tools for verifying network operation from a host Fulvio Risso Mario Baldi Politecnico di Torino (Technical University of Turin) see page 2 Notes n The commands/programs
How To Check If Your Router Is Working Properly
 Chapter 6 Using Network Monitoring Tools This chapter describes how to use the maintenance features of your RangeMax Dual Band Wireless-N Router WNDR3300. You can access these features by selecting the
Chapter 6 Using Network Monitoring Tools This chapter describes how to use the maintenance features of your RangeMax Dual Band Wireless-N Router WNDR3300. You can access these features by selecting the
How to connect your new virtual machine to the Internet
 This excerpt is taken from book Installing and Configuring SharePoint 2010 2 nd Edition. You can download this FREE ebook from the following link: http://walisystemsinc.com/installing_and_configuring_sharepoint2010_2nd_ed.php
This excerpt is taken from book Installing and Configuring SharePoint 2010 2 nd Edition. You can download this FREE ebook from the following link: http://walisystemsinc.com/installing_and_configuring_sharepoint2010_2nd_ed.php
Chapter 12 Supporting Network Address Translation (NAT)
 [Previous] [Next] Chapter 12 Supporting Network Address Translation (NAT) About This Chapter Network address translation (NAT) is a protocol that allows a network with private addresses to access information
[Previous] [Next] Chapter 12 Supporting Network Address Translation (NAT) About This Chapter Network address translation (NAT) is a protocol that allows a network with private addresses to access information
Windows Server 2008 R2 Initial Configuration Tasks
 Windows Server 2008 R2 Initial Configuration Tasks I am not responsible for your actions or their outcomes, in any way, while reading and/or implementing this tutorial. I will not provide support for the
Windows Server 2008 R2 Initial Configuration Tasks I am not responsible for your actions or their outcomes, in any way, while reading and/or implementing this tutorial. I will not provide support for the
Zarząd (7 osób) F inanse (13 osób) M arketing (7 osób) S przedaż (16 osób) K adry (15 osób)
 QUESTION NO: 8 David, your TestKing trainee, asks you about basic characteristics of switches and hubs for network connectivity. What should you tell him? A. Switches take less time to process frames than
QUESTION NO: 8 David, your TestKing trainee, asks you about basic characteristics of switches and hubs for network connectivity. What should you tell him? A. Switches take less time to process frames than
1:1 NAT in ZeroShell. Requirements. Overview. Network Setup
 1:1 NAT in ZeroShell Requirements The version of ZeroShell used for writing this document is Release 1.0.beta11. This document does not describe installing ZeroShell, it is assumed that the user already
1:1 NAT in ZeroShell Requirements The version of ZeroShell used for writing this document is Release 1.0.beta11. This document does not describe installing ZeroShell, it is assumed that the user already
Connecting to and Setting Up a Network
 Chapter 9 Connecting to and Setting Up a Network Reviewing the Basics 1. How many bits are in a MAC address? 48 bits 2. How many bits are in an IPv4 IP address? In an IPv6 IP address? 32 bits, 128 bits
Chapter 9 Connecting to and Setting Up a Network Reviewing the Basics 1. How many bits are in a MAC address? 48 bits 2. How many bits are in an IPv4 IP address? In an IPv6 IP address? 32 bits, 128 bits
Lab PC Network TCP/IP Configuration
 Lab PC Network TCP/IP Configuration Objective Identify tools used to discover a computer network configuration with various operating systems. Gather information including connection, host name, Layer
Lab PC Network TCP/IP Configuration Objective Identify tools used to discover a computer network configuration with various operating systems. Gather information including connection, host name, Layer
Cisco CNR and DHCP FAQs for Cable Environment
 Table of Contents CNR and DHCP FAQs for Cable Environment...1 Questions...1 Introduction...1 Q. How do I access CNR remotely?...1 Q. How do I access CNR remotely if the CNR server is behind a firewall?...2
Table of Contents CNR and DHCP FAQs for Cable Environment...1 Questions...1 Introduction...1 Q. How do I access CNR remotely?...1 Q. How do I access CNR remotely if the CNR server is behind a firewall?...2
BioStar Config Guide V1.0
 BioStar Config Guide V1.0 Suprema Inc. 16F Parkview Tower 6 Jeongja, Bundang Seongnam 463-863 Korea www.supremainc.com Last edited: 27 December 2011 This document is copyright 27 December 2011 by Suprema
BioStar Config Guide V1.0 Suprema Inc. 16F Parkview Tower 6 Jeongja, Bundang Seongnam 463-863 Korea www.supremainc.com Last edited: 27 December 2011 This document is copyright 27 December 2011 by Suprema
Citrix Access Gateway Plug-in for Windows User Guide
 Citrix Access Gateway Plug-in for Windows User Guide Access Gateway 9.2, Enterprise Edition Copyright and Trademark Notice Use of the product documented in this guide is subject to your prior acceptance
Citrix Access Gateway Plug-in for Windows User Guide Access Gateway 9.2, Enterprise Edition Copyright and Trademark Notice Use of the product documented in this guide is subject to your prior acceptance
Prestige 324. Prestige 324. Intelligent Broadband Sharing Gateway. Version 3.60 January 2003 Quick Start Guide
 Prestige 324 Intelligent Broadband Sharing Gateway Version 3.60 January 2003 Quick Start Guide 1 Introducing the Prestige The Prestige is a broadband sharing gateway with a built-in four-port 10/100 Mbps
Prestige 324 Intelligent Broadband Sharing Gateway Version 3.60 January 2003 Quick Start Guide 1 Introducing the Prestige The Prestige is a broadband sharing gateway with a built-in four-port 10/100 Mbps
Configuration Notes 0215
 Mediatrix Digital and Analog VoIP Gateways DNS SRV Configuration for a Redundant Server Solution (SIP) Introduction... 2 Deployment Scenario... 2 DNS SRV (RFC 2782)... 3 Microsoft Server Configuration...
Mediatrix Digital and Analog VoIP Gateways DNS SRV Configuration for a Redundant Server Solution (SIP) Introduction... 2 Deployment Scenario... 2 DNS SRV (RFC 2782)... 3 Microsoft Server Configuration...
CREATING AN IKE IPSEC TUNNEL BETWEEN AN INTERNET SECURITY ROUTER AND A WINDOWS 2000/XP PC
 CREATING AN IKE IPSEC TUNNEL BETWEEN AN INTERNET SECURITY ROUTER AND A WINDOWS 2000/XP PC 1 Introduction Release date: 11/12/2003 This application note details the steps for creating an IKE IPSec VPN tunnel
CREATING AN IKE IPSEC TUNNEL BETWEEN AN INTERNET SECURITY ROUTER AND A WINDOWS 2000/XP PC 1 Introduction Release date: 11/12/2003 This application note details the steps for creating an IKE IPSec VPN tunnel
Information Security Practice II. Installation and set-up of Web Server and FTP accounts
 Information Security Practice II Installation and set-up of Web Server and FTP accounts Installation of IIS Setup of laboratory 3 virtual machines are required in this laboratory: 1. Win2003 the web server
Information Security Practice II Installation and set-up of Web Server and FTP accounts Installation of IIS Setup of laboratory 3 virtual machines are required in this laboratory: 1. Win2003 the web server
Setting Up Your FTP Server
 Requirements:! A computer dedicated to FTP server only! Linksys router! TCP/IP internet connection Steps: Getting Started Configure Static IP on the FTP Server Computer: Setting Up Your FTP Server 1. This
Requirements:! A computer dedicated to FTP server only! Linksys router! TCP/IP internet connection Steps: Getting Started Configure Static IP on the FTP Server Computer: Setting Up Your FTP Server 1. This
Part A:Background/Preparation
 Lab no 1 PC Network TCP/IP Configuration In this lab we will learn about Computer Networks Configuration Introduction to IP addressing Identify tools used for discovering a computer s network configuration
Lab no 1 PC Network TCP/IP Configuration In this lab we will learn about Computer Networks Configuration Introduction to IP addressing Identify tools used for discovering a computer s network configuration
cnds@napier Slide 1 Introduction cnds@napier 1 Lecture 6 (Network Layer)
 Slide 1 Introduction In today s and next week s lecture we will cover two of the most important areas in networking and the Internet: IP and TCP. These cover the network and transport layer of the OSI
Slide 1 Introduction In today s and next week s lecture we will cover two of the most important areas in networking and the Internet: IP and TCP. These cover the network and transport layer of the OSI
THE HONG KONG POLYTECHNIC UNIVERSITY Department of Electronic and Information Engineering
 THE HONG KONG POLYTECHNIC UNIVERSITY Department of Electronic and Information Engineering ENG 224 Information Technology Laboratory 6: Internet Connection Sharing Objectives: Build a private network that
THE HONG KONG POLYTECHNIC UNIVERSITY Department of Electronic and Information Engineering ENG 224 Information Technology Laboratory 6: Internet Connection Sharing Objectives: Build a private network that
Appendix D: Configuring Firewalls and Network Address Translation
 Appendix D: Configuring Firewalls and Network Address Translation The configuration information in this appendix will help the network administrator plan and configure the network architecture for Everserve.
Appendix D: Configuring Firewalls and Network Address Translation The configuration information in this appendix will help the network administrator plan and configure the network architecture for Everserve.
MaxSea TimeZero NN3D Radar Connection Checklist
 MaxSea TimeZero NN3D Radar Connection Checklist This TechNote only applies to MaxSea TimeZero Explorer. Description Follow this TechNote if you have any of these symptoms: - The Radar Tab (Radar WorkSpace)
MaxSea TimeZero NN3D Radar Connection Checklist This TechNote only applies to MaxSea TimeZero Explorer. Description Follow this TechNote if you have any of these symptoms: - The Radar Tab (Radar WorkSpace)
Question 3.1.1. Question 3.2.1. Question 3.3.1. EdTech 552: Lab 3 Answer Sheet
 Question 3.1.1 Question Answers a. 123 01111011 b. 202 11001010 c. 67 01000011 d. 7 00000111 e. 252 11111100 f. 91 01011011 g. 116.127.71.3 01110100.01111111.01010001.00000011 h. 255.255.255.0 11111111.11111111.11111111.00000000
Question 3.1.1 Question Answers a. 123 01111011 b. 202 11001010 c. 67 01000011 d. 7 00000111 e. 252 11111100 f. 91 01011011 g. 116.127.71.3 01110100.01111111.01010001.00000011 h. 255.255.255.0 11111111.11111111.11111111.00000000
Use this guide if you are no longer able to scan to Sharpdesk. Begin with section 1 (easiest) and complete all sections only if necessary.
 Use this guide if you are no longer able to scan to Sharpdesk Instructions: Begin with section 1 (easiest) and complete all sections only if necessary. 1 Section 1 Complete pages 3-5. Scan to the desired
Use this guide if you are no longer able to scan to Sharpdesk Instructions: Begin with section 1 (easiest) and complete all sections only if necessary. 1 Section 1 Complete pages 3-5. Scan to the desired
Configuring the WT-4 for ftp (Ad-hoc Mode)
 En Configuring the WT-4 for ftp (Ad-hoc Mode) Mac OS X Introduction This document provides basic instructions on configuring the WT-4 wireless transmitter and a Mac OS X (10.5.2) ftp server for transmission
En Configuring the WT-4 for ftp (Ad-hoc Mode) Mac OS X Introduction This document provides basic instructions on configuring the WT-4 wireless transmitter and a Mac OS X (10.5.2) ftp server for transmission
Debugging Network Communications. 1 Check the Network Cabling
 Debugging Network Communications Situation: you have a computer and your NetBurner device on a network, but you cannot communicate between the two. This application note provides a set of debugging steps
Debugging Network Communications Situation: you have a computer and your NetBurner device on a network, but you cannot communicate between the two. This application note provides a set of debugging steps
7 TRANSMISSION CONTROL PROTOCOL/ INTERNET PROTOCOL (TCP/IP)
 7 TRANSMISSION CONTROL PROTOCOL/ INTERNET PROTOCOL (TCP/IP) PROJECTS Project 7.1 Project 7.2 Project 7.3 Project 7.4 Project 7.5 Understanding Key Concepts Configuring TCP/IP Properties Comparing Name
7 TRANSMISSION CONTROL PROTOCOL/ INTERNET PROTOCOL (TCP/IP) PROJECTS Project 7.1 Project 7.2 Project 7.3 Project 7.4 Project 7.5 Understanding Key Concepts Configuring TCP/IP Properties Comparing Name
