User-level processes (clients) request services from the kernel (server) via special protected procedure calls
|
|
|
- Henry Russell Haynes
- 10 years ago
- Views:
Transcription
1 Linux System Call
2 What is System Call? User-level processes (clients) request services from the kernel (server) via special protected procedure calls System calls provide: An abstraction layer between processes and hardware, allowing the kernel to provide access control, arbitration A virtualization of the underlying system A well-defined API for system services
3 System Call Procedure in Linux
4 Add New System Call (Tutorial 1) Download Kernel Source Code Kernel-level modification (1) Allocate an unused system call number (2) Register sys_call_table (3) Program new system call handler (4) Kernel compile and rebooting User-level modification (1) Make library interface (2) Make user program that call the library function
5 Add New System Call (Tutorial 1) Download Kernel Source Code Kernel-level modification (1) Allocate an unused system call number (2) Register sys_call_table (3) Program new system call handler (4) Kernel compile and rebooting User-level modification (1) Make library interface (2) Make user program that call the library function
6 Download Kernel Source Code Tutorial environment 32bit Ubuntu (Kernel Version : 3.2.0) on VMware Download Kernel Source Code (1) $ apt-get source linux-image-$(uname -r) (2) or Download at
7 Add New System Call (Tutorial 1) Download Kernel Source Code Kernel-level modification (1) Allocate an unused system call number (2) Register sys_call_table (3) Program new system call handler (4) Kernel compile and rebooting User-level modification (1) Make library interface (2) Make user program that call the library function
8 Allocate Unused System Call Number /(source code path)/arch/x86/include/asm/unistd_32.h
9 Register sys_call_table /(source code path)/arch/x86/kernel/syscall_table_32.s
10 Program new system call handler /(source code path)/kernel/newsyscall.c
11 Modify Makefile /(source code path)/kernel/makefile
12 Kernel Compile and Rebooting $ apt-get update $ apt-get install build-essential libncurses5 libncurses5-dev /(source code path)/ Follow the below commands to compile the kernel (1) $ make menuconfig (2) $ make bzimage (3) $ make modules (4) $ make modules_install (5) $ make install modify /etc/default/grub like below Change grub configuration Reboot Press esc key to see the grub menu $ update-grub
13 Add New System Call (Tutorial 1) Download Kernel Source Code Kernel-level modification (1) Allocate an unused system call number (2) Register sys_call_table (3) Program new system call handler (4) Kernel compile and rebooting User-level modification (1) Make library interface (2) Make user program that call the library function
14 Make Library Interface and User Program Library Interface If you get the message such as NR_newsyscall is not defined, you can add a line in /usr/include/i386- linux-gnu/asm/unistd_32.h as follow User Program /usr/include/i386-linux-gnu/asm/unistd_32.h
15 Check the Results Check the kernel print message $ dmesg $ tail f /var/log/syslog
16 Linux Kernel Module
17 What is Kernel Module? A Module is a object file that contains code to extend the functionality of the base kernel Modules are used to add support for new hardware and file systems Also used to add new system calls and executable interpreters
18 Linking a Module to the Kernel Reference : Linux Device Drivers 2 nd Edition
19 Make a Kernel Module (Tutorial 2) Write a simple module code Write a Makefile Load the simple module to kernel
20 Simple Module Code
21 Makefile
22 Load the Module
23 Check the Module List $ lsmod $ cat /proc/modules
24 Load a Module at the Boot Time $ make install Add the name of module to the /etc/modules $ depmod Reboot
25 Linux Security Module
26 What is Linux Security Module? LSM(Linux Security Module) is a framework that allows the Linux kernel to support a variety of computer security models while avoiding favoritism toward any single security implementation. The framework is standard part of the Linux kernel since Linux 2.6. AppArmor, SELinux, Smack and TOMOYO Linux are the currently accepted modules in the official kernel. LSM doesn t provide any security rather it add security fields to kernel and provide interface to manage these fields for maintaining security attributes.
27 Design of LSM User Level Process User space LSM is to mediate access to internal kernel objects open system call Kernel space By placing hooks in kernel code just before the access look up inode error checks LSM module provides the functions to be called by these hooks DAC checks LSM hook access inode OK? Yes or No LSM Policy Engine Examine context. Does request pass policy? Grant or Deny.
28 System Call Hook vs. LSM Hook
29 Linux Security Module Architecture LSM의 구조 Security Policy + Security Module = LSM Framework
30 Make a Security Module (Tutorial 3) Write a simple security module code Write a Makefile Modify the kernel Load the security module to kernel
31 Simple Security Module Code include/linux/security.h LSM hook Registration (1) Hooking function pointer is defined in security.h struct security_operations { char name[security_name_max + 1]; int (*socket_connect) (struct socket *sock, struct sockaddr *address, int addrlen);.. omitted.. } 1. security_operation Structure Definition sample.c static struct security_operations sample_ops = {.socket_connect = sample_socket_connect, hooking function is defined for socket_connect.inode_link = sample_inode_link,.inode_unlink = sample_inode_unlink,.inode_symlink = sample_inode_symlink,.inode_mkdir = sample_inode_mkdir, 생략.. } define a hook to security operations structure When we want to add a hook, we can refer to security_operations in include/linux/security.h sample.c 2. security_operation Structure Registration Define a security check function when the connect() is called. sample_socket_connect() { //check permission check_perm(&perm); }
32 Simple Security Module Code LSM hook Registration (2) 2. security_operation Structure Registration security/sample/sample.c static init int sample_init(void) { reset_security_ops(); if (register_security (&sample_ops)) { printk("sample: Unable to register with kernel.\n"); return 0; } Register register_security () function using a predefined structure to register security_operations Defined previously registered sample_ops } printk(kern_info "Sample: Initializing.\n"); return 0; security/security.c int register_security(struct security_operations *ops) {.. Omitted. security_operations is registered as a security function } if (security_ops!= &default_security_ops) return -EAGAIN; security_ops = ops; sample_ops is registered as a security function return 0;
33 Simple Security Module Code Connect System Call Main() { connect() connect system call } User Level net/socket.c Kernel Level SYSCALL_DEFINE3(connect, int, fd, struct sockaddr user *, uservaddr, int, addrlen) connection system call function in Kernel { sockfd_lookup_light (); move_addr_to_kernel(); security_socket_connect(); security check function } sock->ops->connect(); Connection() function security/sample/sample.c security/security.c int security_socket_connect(struct socket *sock, struct sockaddr *address, int addrlen) { return security_ops->socket_connect(sock, address, addrlen); } sample_socket_connect() { //set parameters perm_info.connect_info.sock = sock; perm_info.connect_info.address = address; perm_info.connect_info.addrlen = addrlen; } //check permission check_perm(&perm);
34 Write a Makefile Makefile Explanation obj-m := name of object file KDIR := kernel source directory(symbolic) PWD := module source directory -C : change the directory to next parameter M= module location (SUBDIRS is same meaning with M)
35 Have you got this error message? Try to load the sample security module $ tail f /var/log/syslog Check the kernel symbol table
36 Why??? Befor Linux v After Linux v : Built-In Security Modules ex) SELinux, Apparmor, TOMOYO, LSM LSM : Other Modules (User Defined) LSM LSM
37 We Need to Modify the Kernel Basis on Linux Kernel v3.2.0 /include/linux/security.h Line Remove init from void init security_fixup_ops(struct security_operations *ops) 1663 /security/security.c Remove init from static inline int init verify(struct security_operations *ops) 34 int init register_security(struct security_operations *ops) 113 Add EXPORT_SYMBOL() at bottom line EXPORT_SYMBOL(register_security); EXPORT_SYMBOL(reset_security_ops); /security/capability.c Remove init from void init security_fixup_ops(struct security_operations *ops) 875
38 Kernel Compile and Rebooting Follow the below commands to re-compile the kernel (1) make mrproper (2) make menuconfig (3) make clean (4) make bzimage (5) make install Reboot
39 Load the Security Module to Kernel Load the Security Module $ tail f /var/log/syslog Check the kernel symbol table
Migration of Process Credentials
 C H A P T E R - 5 Migration of Process Credentials 5.1 Introduction 5.2 The Process Identifier 5.3 The Mechanism 5.4 Concluding Remarks 100 CHAPTER 5 Migration of Process Credentials 5.1 Introduction Every
C H A P T E R - 5 Migration of Process Credentials 5.1 Introduction 5.2 The Process Identifier 5.3 The Mechanism 5.4 Concluding Remarks 100 CHAPTER 5 Migration of Process Credentials 5.1 Introduction Every
Kernel Intrusion Detection System
 Kernel Intrusion Detection System Rodrigo Rubira Branco [email protected] [email protected] Monica's Team!! Brazilian famous H.Q. story Amazon Forest Yeah, Brazilian country! Soccer Brazilian
Kernel Intrusion Detection System Rodrigo Rubira Branco [email protected] [email protected] Monica's Team!! Brazilian famous H.Q. story Amazon Forest Yeah, Brazilian country! Soccer Brazilian
Lab 6: Building Your Own Firewall
 CS498 Systems and Networking Lab Spring 2012 Lab 6: Building Your Own Firewall Instructor: Matthew Caesar Due: Firewalls are widely deployed technologies for protecting networks from unauthorized access
CS498 Systems and Networking Lab Spring 2012 Lab 6: Building Your Own Firewall Instructor: Matthew Caesar Due: Firewalls are widely deployed technologies for protecting networks from unauthorized access
Linux Distributed Security Module 1
 Linux Distributed Security Module 1 By Miroslaw Zakrzewski and Ibrahim Haddad This article describes the implementation of Mandatory Access Control through a Linux kernel module that is targeted for Linux
Linux Distributed Security Module 1 By Miroslaw Zakrzewski and Ibrahim Haddad This article describes the implementation of Mandatory Access Control through a Linux kernel module that is targeted for Linux
USB Driver. Installation Guide for LTE Devices
 USB Driver Installation Guide for LTE Devices USB DRIVER INSTALLATION GUIDE USB Driver Installation Guide For the following devices: MTSMC-LEU1-U, MTSMC-LAT1-U, MTSMC-LVW2-U S000616, Version 1.0.3 Copyright
USB Driver Installation Guide for LTE Devices USB DRIVER INSTALLATION GUIDE USB Driver Installation Guide For the following devices: MTSMC-LEU1-U, MTSMC-LAT1-U, MTSMC-LVW2-U S000616, Version 1.0.3 Copyright
Linux Firewall Lab. 1 Overview. 2 Lab Tasks. 2.1 Task 1: Firewall Policies. Laboratory for Computer Security Education 1
 Laboratory for Computer Security Education 1 Linux Firewall Lab Copyright c 2006-2011 Wenliang Du, Syracuse University. The development of this document is funded by the National Science Foundation s Course,
Laboratory for Computer Security Education 1 Linux Firewall Lab Copyright c 2006-2011 Wenliang Du, Syracuse University. The development of this document is funded by the National Science Foundation s Course,
Linux LKM Firewall v 0.95 (2/5/2010)
 600/650.424 Network Security Linux LKM Firewall 1 1 Overview Linux LKM Firewall v 0.95 (2/5/2010) The learning objective of this project is for you to understand how firewalls work by designing and implementing
600/650.424 Network Security Linux LKM Firewall 1 1 Overview Linux LKM Firewall v 0.95 (2/5/2010) The learning objective of this project is for you to understand how firewalls work by designing and implementing
CSE543 - Introduction to Computer and Network Security. Module: Operating System Security
 CSE543 - Introduction to Computer and Network Security Module: Operating System Security Professor Trent Jaeger 1 OS Security So, you have built an operating system that enables user-space processes to
CSE543 - Introduction to Computer and Network Security Module: Operating System Security Professor Trent Jaeger 1 OS Security So, you have built an operating system that enables user-space processes to
Linux Kernel Architecture
 Linux Kernel Architecture Amir Hossein Payberah [email protected] Contents What is Kernel? Kernel Architecture Overview User Space Kernel Space Kernel Functional Overview File System Process Management
Linux Kernel Architecture Amir Hossein Payberah [email protected] Contents What is Kernel? Kernel Architecture Overview User Space Kernel Space Kernel Functional Overview File System Process Management
Remote PC Guide Series - Volume 2a
 Document Version: 2013-03-04 This guide provides hardware model-specific guidance in server configuration, with BIOS and RAID configuration instructions for the Dell R710. This guide is part of a multi-volume
Document Version: 2013-03-04 This guide provides hardware model-specific guidance in server configuration, with BIOS and RAID configuration instructions for the Dell R710. This guide is part of a multi-volume
Ubuntu Professional Training Course Overview (E-learning, Ubuntu 10.04 LTS)
 Ubuntu Professional Training Course Overview (E-learning, Ubuntu 10.04 LTS) 1 of 7 Ubuntu Professional Course Overview (E-learning, Ubuntu 10.04 LTS) About the Course and Objectives The Ubuntu Professional
Ubuntu Professional Training Course Overview (E-learning, Ubuntu 10.04 LTS) 1 of 7 Ubuntu Professional Course Overview (E-learning, Ubuntu 10.04 LTS) About the Course and Objectives The Ubuntu Professional
Performance Monitor on PowerQUICC II Pro Processors
 Freescale Semiconductor Application Note Document Number: AN3359 Rev. 0, 05/2007 Performance Monitor on PowerQUICC II Pro Processors by Harinder Rai Network Computing Systems Group Freescale Semiconductor,
Freescale Semiconductor Application Note Document Number: AN3359 Rev. 0, 05/2007 Performance Monitor on PowerQUICC II Pro Processors by Harinder Rai Network Computing Systems Group Freescale Semiconductor,
How to Restore a Linux Server Using Bare Metal Restore
 How to Restore a Linux Server Using Bare Metal Restore This article refers to firmware version 5.4 and higher, and the Barracuda Linux Backup Agent 5.4 and higher. Use the steps in this article to restore
How to Restore a Linux Server Using Bare Metal Restore This article refers to firmware version 5.4 and higher, and the Barracuda Linux Backup Agent 5.4 and higher. Use the steps in this article to restore
Operating Systems Design 16. Networking: Sockets
 Operating Systems Design 16. Networking: Sockets Paul Krzyzanowski [email protected] 1 Sockets IP lets us send data between machines TCP & UDP are transport layer protocols Contain port number to identify
Operating Systems Design 16. Networking: Sockets Paul Krzyzanowski [email protected] 1 Sockets IP lets us send data between machines TCP & UDP are transport layer protocols Contain port number to identify
Embedded Linux development training 4 days session
 Embedded Linux development training 4 days session Title Overview Duration Trainer Language Audience Prerequisites Embedded Linux development training Understanding the Linux kernel Building the Linux
Embedded Linux development training 4 days session Title Overview Duration Trainer Language Audience Prerequisites Embedded Linux development training Understanding the Linux kernel Building the Linux
Safety measures in Linux
 S a f e t y m e a s u r e s i n L i n u x Safety measures in Linux Krzysztof Lichota [email protected] A g e n d a Standard Unix security measures: permissions, capabilities, ACLs, chroot Linux kernel
S a f e t y m e a s u r e s i n L i n u x Safety measures in Linux Krzysztof Lichota [email protected] A g e n d a Standard Unix security measures: permissions, capabilities, ACLs, chroot Linux kernel
Restoring a Suse Linux Enterprise Server 9 64 Bit on Dissimilar Hardware with CBMR for Linux 1.02
 Cristie Bare Machine Recovery Restoring a Suse Linux Enterprise Server 9 64 Bit on Dissimilar Hardware with CBMR for Linux 1.02 This documentation shows how to restore or migrate a Linux system on dissimilar
Cristie Bare Machine Recovery Restoring a Suse Linux Enterprise Server 9 64 Bit on Dissimilar Hardware with CBMR for Linux 1.02 This documentation shows how to restore or migrate a Linux system on dissimilar
ITRAINONLINE MMTK WIRELESS CLIENT INSTALLATION HANDOUT
 ITRAINONLINE MMTK WIRELESS CLIENT INSTALLATION HANDOUT Developed by: Tomas B. Krag (Linux) Bruno Roger, ESMT (Windows) Edited by: Alberto Escudero Pascual, IT +46 Table of Contents 1.
ITRAINONLINE MMTK WIRELESS CLIENT INSTALLATION HANDOUT Developed by: Tomas B. Krag (Linux) Bruno Roger, ESMT (Windows) Edited by: Alberto Escudero Pascual, IT +46 Table of Contents 1.
How to Add a New System Call for Minix 3
 How to Add a New System Call for Minix 3 Karthick Jayaraman Department of Electrical Engineering & Computer Science Syracuse University, Syracuse, New York 1. Introduction Minix3 has the micro-kernel architecture.
How to Add a New System Call for Minix 3 Karthick Jayaraman Department of Electrical Engineering & Computer Science Syracuse University, Syracuse, New York 1. Introduction Minix3 has the micro-kernel architecture.
NSA Security-Enhanced Linux (SELinux)
 NSA Security-Enhanced Linux (SELinux) http://www.nsa.gov/selinux Stephen Smalley [email protected] Information Assurance Research Group National Security Agency Information Assurance Research Group 1
NSA Security-Enhanced Linux (SELinux) http://www.nsa.gov/selinux Stephen Smalley [email protected] Information Assurance Research Group National Security Agency Information Assurance Research Group 1
An Embedded Wireless Mini-Server with Database Support
 An Embedded Wireless Mini-Server with Database Support Hungchi Chang, Sy-Yen Kuo and Yennun Huang Department of Electrical Engineering National Taiwan University Taipei, Taiwan, R.O.C. Abstract Due to
An Embedded Wireless Mini-Server with Database Support Hungchi Chang, Sy-Yen Kuo and Yennun Huang Department of Electrical Engineering National Taiwan University Taipei, Taiwan, R.O.C. Abstract Due to
Linux Kernel Rootkit : Virtual Terminal Key Logger
 Linux Kernel Rootkit : Virtual Terminal Key Logger Jeena Kleenankandy Roll No. P140066CS Depatment of Computer Science and Engineering National Institute of Technology Calicut jeena [email protected]
Linux Kernel Rootkit : Virtual Terminal Key Logger Jeena Kleenankandy Roll No. P140066CS Depatment of Computer Science and Engineering National Institute of Technology Calicut jeena [email protected]
www.cristie.com CBMR for Linux v6.2.2 User Guide
 www.cristie.com CBMR for Linux v6.2.2 User Guide Contents CBMR for Linux User Guide - Version: 6.2.2 Section No. Section Title Page 1.0 Using this Guide 3 1.1 Version 3 1.2 Limitations 3 2.0 About CBMR
www.cristie.com CBMR for Linux v6.2.2 User Guide Contents CBMR for Linux User Guide - Version: 6.2.2 Section No. Section Title Page 1.0 Using this Guide 3 1.1 Version 3 1.2 Limitations 3 2.0 About CBMR
Linux Server (Web, FTP, File) on Vmware
 Linux Server (Web, FTP, File) on Vmware Purposes Many people want to use Linux but don't want to spend all their weekend in order to be familiar with this operating system. This file allows to share the
Linux Server (Web, FTP, File) on Vmware Purposes Many people want to use Linux but don't want to spend all their weekend in order to be familiar with this operating system. This file allows to share the
Assignment 5: Adding and testing a new system call to Linux kernel
 Assignment 5: Adding and testing a new system call to Linux kernel Antonis Papadogiannakis HY345 Operating Systems Course 1 Outline Introduction: system call and Linux kernel Emulators and Virtual Machines
Assignment 5: Adding and testing a new system call to Linux kernel Antonis Papadogiannakis HY345 Operating Systems Course 1 Outline Introduction: system call and Linux kernel Emulators and Virtual Machines
Create a virtual machine at your assigned virtual server. Use the following specs
 CIS Networking Installing Ubuntu Server on Windows hyper-v Much of this information was stolen from http://www.isummation.com/blog/installing-ubuntu-server-1104-64bit-on-hyper-v/ Create a virtual machine
CIS Networking Installing Ubuntu Server on Windows hyper-v Much of this information was stolen from http://www.isummation.com/blog/installing-ubuntu-server-1104-64bit-on-hyper-v/ Create a virtual machine
Remote PC Guide Series - Volume 2b
 Document Version: 2013-09-06 R720 This guide provides hardware model-specific guidance in server configuration, with BIOS and RAID configuration instructions for the Dell R720. This guide is part of a
Document Version: 2013-09-06 R720 This guide provides hardware model-specific guidance in server configuration, with BIOS and RAID configuration instructions for the Dell R720. This guide is part of a
UNIX Sockets. COS 461 Precept 1
 UNIX Sockets COS 461 Precept 1 Clients and Servers Client program Running on end host Requests service E.g., Web browser Server program Running on end host Provides service E.g., Web server GET /index.html
UNIX Sockets COS 461 Precept 1 Clients and Servers Client program Running on end host Requests service E.g., Web browser Server program Running on end host Provides service E.g., Web server GET /index.html
Minix Mini Unix (Minix) basically, a UNIX - compatible operating system. Minix is small in size, with microkernel-based design. Minix has been kept
 Minix Mini Unix (Minix) basically, a UNIX - compatible operating system. Minix is small in size, with microkernel-based design. Minix has been kept (relatively) small and simple. Minix is small, it is
Minix Mini Unix (Minix) basically, a UNIX - compatible operating system. Minix is small in size, with microkernel-based design. Minix has been kept (relatively) small and simple. Minix is small, it is
How do Users and Processes interact with the Operating System? Services for Processes. OS Structure with Services. Services for the OS Itself
 How do Users and Processes interact with the Operating System? Users interact indirectly through a collection of system programs that make up the operating system interface. The interface could be: A GUI,
How do Users and Processes interact with the Operating System? Users interact indirectly through a collection of system programs that make up the operating system interface. The interface could be: A GUI,
Step By Step Guide for Starting "Hello, World!" on OpenWRT
 Step By Step Guide for Starting "Hello, World!" on OpenWRT Installation. All actions of this step should be performed by a non-root user. Directories with spaces in their full path are not allowed. 1.
Step By Step Guide for Starting "Hello, World!" on OpenWRT Installation. All actions of this step should be performed by a non-root user. Directories with spaces in their full path are not allowed. 1.
Chapter 2 System Structures
 Chapter 2 System Structures Operating-System Structures Goals: Provide a way to understand an operating systems Services Interface System Components The type of system desired is the basis for choices
Chapter 2 System Structures Operating-System Structures Goals: Provide a way to understand an operating systems Services Interface System Components The type of system desired is the basis for choices
Example of Standard API
 16 Example of Standard API System Call Implementation Typically, a number associated with each system call System call interface maintains a table indexed according to these numbers The system call interface
16 Example of Standard API System Call Implementation Typically, a number associated with each system call System call interface maintains a table indexed according to these numbers The system call interface
EXPLORING LINUX KERNEL: THE EASY WAY!
 EXPLORING LINUX KERNEL: THE EASY WAY! By: Ahmed Bilal Numan 1 PROBLEM Explore linux kernel TCP/IP stack Solution Try to understand relative kernel code Available text Run kernel in virtualized environment
EXPLORING LINUX KERNEL: THE EASY WAY! By: Ahmed Bilal Numan 1 PROBLEM Explore linux kernel TCP/IP stack Solution Try to understand relative kernel code Available text Run kernel in virtualized environment
Five standard procedures for building the android system. Figure1. Procedures for building android embedded systems
 Standard Operating Procedures for Android Embedded Systems Anupama M. Kulkarni, Shang-Yang Chang, Ying-Dar Lin National Chiao Tung University, Hsinchu, Taiwan November 2012 Android is considered to be
Standard Operating Procedures for Android Embedded Systems Anupama M. Kulkarni, Shang-Yang Chang, Ying-Dar Lin National Chiao Tung University, Hsinchu, Taiwan November 2012 Android is considered to be
Virtualization for Cloud Computing
 Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
Analysis of the Linux Audit System 1
 Analysis of the Linux Audit System 1 Authors Bruno Morisson, MSc (Royal Holloway, 2014) Stephen Wolthusen, ISG, Royal Holloway Overview Audit mechanisms on an operating system (OS) record relevant system
Analysis of the Linux Audit System 1 Authors Bruno Morisson, MSc (Royal Holloway, 2014) Stephen Wolthusen, ISG, Royal Holloway Overview Audit mechanisms on an operating system (OS) record relevant system
USB Driver. Installation Guide for H5 Devices
 USB Driver Installation Guide for H5 Devices USB DRIVER INSTALLATION GUIDE USB Driver Installation Guide For the following devices: MTSMC-H5-U, MTD-H5, MTPCIE-H5, MT100UCC-H5, MTC-H5-B03, MTCBA-H5-U S000553,
USB Driver Installation Guide for H5 Devices USB DRIVER INSTALLATION GUIDE USB Driver Installation Guide For the following devices: MTSMC-H5-U, MTD-H5, MTPCIE-H5, MT100UCC-H5, MTC-H5-B03, MTCBA-H5-U S000553,
Project Adding a System Call to the Linux Kernel
 74 Chapter 2 Operating-System Structures 2.15 Why is a just-in-time compiler useful for executing Java programs? 2.16 What is the relationship between a guest operating system and a host operating system
74 Chapter 2 Operating-System Structures 2.15 Why is a just-in-time compiler useful for executing Java programs? 2.16 What is the relationship between a guest operating system and a host operating system
Q N X S O F T W A R E D E V E L O P M E N T P L A T F O R M v 6. 4. 10 Steps to Developing a QNX Program Quickstart Guide
 Q N X S O F T W A R E D E V E L O P M E N T P L A T F O R M v 6. 4 10 Steps to Developing a QNX Program Quickstart Guide 2008, QNX Software Systems GmbH & Co. KG. A Harman International Company. All rights
Q N X S O F T W A R E D E V E L O P M E N T P L A T F O R M v 6. 4 10 Steps to Developing a QNX Program Quickstart Guide 2008, QNX Software Systems GmbH & Co. KG. A Harman International Company. All rights
WES 9.2 DRIVE CONFIGURATION WORKSHEET
 WES 9.2 DRIVE CONFIGURATION WORKSHEET This packet will provide you with a paper medium external to your WES box to write down the device names, partitions, and mount points within your machine. You may
WES 9.2 DRIVE CONFIGURATION WORKSHEET This packet will provide you with a paper medium external to your WES box to write down the device names, partitions, and mount points within your machine. You may
PiFace Control & Display
 PiFace Control & Display A Plug and Play Device to control Raspberry Pi Exclusively From Quick Start Guide Version 1.0 Dated: 30 th Oct 2013 Table Of Contents Page No 1. Overview 2 2. Fitting the PiFace
PiFace Control & Display A Plug and Play Device to control Raspberry Pi Exclusively From Quick Start Guide Version 1.0 Dated: 30 th Oct 2013 Table Of Contents Page No 1. Overview 2 2. Fitting the PiFace
Survey of Filesystems for Embedded Linux. Presented by Gene Sally CELF
 Survey of Filesystems for Embedded Linux Presented by Gene Sally CELF Presentation Filesystems In Summary What is a filesystem Kernel and User space filesystems Picking a root filesystem Filesystem Round-up
Survey of Filesystems for Embedded Linux Presented by Gene Sally CELF Presentation Filesystems In Summary What is a filesystem Kernel and User space filesystems Picking a root filesystem Filesystem Round-up
Trusted RUBIX TM. Version 6. Installation and Quick Start Guide Red Hat Enterprise Linux 6 SELinux Platform. Revision 6
 Trusted RUBIX TM Version 6 Installation and Quick Start Guide Red Hat Enterprise Linux 6 SELinux Platform Revision 6 RELATIONAL DATABASE MANAGEMENT SYSTEM Infosystems Technology, Inc. 4 Professional Dr
Trusted RUBIX TM Version 6 Installation and Quick Start Guide Red Hat Enterprise Linux 6 SELinux Platform Revision 6 RELATIONAL DATABASE MANAGEMENT SYSTEM Infosystems Technology, Inc. 4 Professional Dr
Tutorial. Reference http://www.openflowswitch.org/foswiki/bin/view/openflow/mininetgettingstarted for more thorough Mininet walkthrough if desired
 Setup Tutorial Reference http://www.openflowswitch.org/foswiki/bin/view/openflow/mininetgettingstarted for more thorough Mininet walkthrough if desired Necessary Downloads 1. Download VM at http://www.cs.princeton.edu/courses/archive/fall10/cos561/assignments/cos561tutorial.zip
Setup Tutorial Reference http://www.openflowswitch.org/foswiki/bin/view/openflow/mininetgettingstarted for more thorough Mininet walkthrough if desired Necessary Downloads 1. Download VM at http://www.cs.princeton.edu/courses/archive/fall10/cos561/assignments/cos561tutorial.zip
sys socketcall: Network systems calls on Linux
 sys socketcall: Network systems calls on Linux Daniel Noé April 9, 2008 The method used by Linux for system calls is explored in detail in Understanding the Linux Kernel. However, the book does not adequately
sys socketcall: Network systems calls on Linux Daniel Noé April 9, 2008 The method used by Linux for system calls is explored in detail in Understanding the Linux Kernel. However, the book does not adequately
Quick Deployment Step-by-step instructions to deploy Oracle Big Data Lite Virtual Machine
 Quick Deployment Step-by-step instructions to deploy Oracle Big Data Lite Virtual Machine Version 3.0 Please note: This appliance is for testing and educational purposes only; it is unsupported and not
Quick Deployment Step-by-step instructions to deploy Oracle Big Data Lite Virtual Machine Version 3.0 Please note: This appliance is for testing and educational purposes only; it is unsupported and not
Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY. 6.828 Operating System Engineering: Fall 2005
 Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.828 Operating System Engineering: Fall 2005 Quiz II Solutions Average 84, median 83, standard deviation
Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.828 Operating System Engineering: Fall 2005 Quiz II Solutions Average 84, median 83, standard deviation
The Linux CryptoAPI A User s Perspective
 The Linux CryptoAPI A User s Perspective David Bryson May 31, 2002 Abstract Today we are going to talk about using strong cryptography inside Linux. With currently available kernel patches discussed in
The Linux CryptoAPI A User s Perspective David Bryson May 31, 2002 Abstract Today we are going to talk about using strong cryptography inside Linux. With currently available kernel patches discussed in
Operating Systems Project: Device Drivers
 Operating Systems Project: Device Drivers Jordi Garcia and Yolanda Becerra 1 Department of Computer Architecture Universitat Politècnica de Catalunya 1. Introduction September 2012 The main aim of this
Operating Systems Project: Device Drivers Jordi Garcia and Yolanda Becerra 1 Department of Computer Architecture Universitat Politècnica de Catalunya 1. Introduction September 2012 The main aim of this
Cosmic Board for phycore AM335x System on Module and Carrier Board. Application Development User Manual
 Cosmic Board for phycore AM335x System on Module and Carrier Board Application Development User Manual Product No: PCL-051/POB-002 SOM PCB No: 1397.0 CB PCB No: 1396.1 Edition: October,2013 In this manual
Cosmic Board for phycore AM335x System on Module and Carrier Board Application Development User Manual Product No: PCL-051/POB-002 SOM PCB No: 1397.0 CB PCB No: 1396.1 Edition: October,2013 In this manual
Installing VMware Tools on Clearswift v4 Gateways
 Technical Guide Version 2.0 January 2016 Contents 1 Introduction... 3 2 Scope... 3 3 Installation and Setup... 4 3.1 Overview... 4 3.2 Installation... 4 4 Performance Impact... 8 4.1 Overview... 8 4.2
Technical Guide Version 2.0 January 2016 Contents 1 Introduction... 3 2 Scope... 3 3 Installation and Setup... 4 3.1 Overview... 4 3.2 Installation... 4 4 Performance Impact... 8 4.1 Overview... 8 4.2
Yosemite Server Backup Installation Guide
 Yosemite Server Backup Installation Guide Part number: First edition: October, 2010 Legal and notice information Copyright 2004, 2012 Barracuda Networks, Inc. Under copyright laws, the contents of this
Yosemite Server Backup Installation Guide Part number: First edition: October, 2010 Legal and notice information Copyright 2004, 2012 Barracuda Networks, Inc. Under copyright laws, the contents of this
Linux Embedded devices with PicoDebian Martin Noha 28.9.2006
 Embedded systems Linux Embedded devices with PicoDebian Martin Noha 28.9.2006 24.03.2005 1 Agenda Why did I look in this stuff? What is an embedded device? Characteristic hardware global requirements for
Embedded systems Linux Embedded devices with PicoDebian Martin Noha 28.9.2006 24.03.2005 1 Agenda Why did I look in this stuff? What is an embedded device? Characteristic hardware global requirements for
Libmonitor: A Tool for First-Party Monitoring
 Libmonitor: A Tool for First-Party Monitoring Mark W. Krentel Dept. of Computer Science Rice University 6100 Main St., Houston, TX 77005 [email protected] ABSTRACT Libmonitor is a library that provides
Libmonitor: A Tool for First-Party Monitoring Mark W. Krentel Dept. of Computer Science Rice University 6100 Main St., Houston, TX 77005 [email protected] ABSTRACT Libmonitor is a library that provides
SETTING UP A LAMP SERVER REMOTELY
 SETTING UP A LAMP SERVER REMOTELY It s been said a million times over Linux is awesome on servers! With over 60 per cent of the Web s servers gunning away on the mighty penguin, the robust, resilient,
SETTING UP A LAMP SERVER REMOTELY It s been said a million times over Linux is awesome on servers! With over 60 per cent of the Web s servers gunning away on the mighty penguin, the robust, resilient,
HW (Fat001) TPM. Figure 1. Computing Node
 1. Overview Two major components exist in our current prototype systems: the management node, including the Cloud Controller, Cluster Controller, Walrus and EBS, and the computing node, i.e. the Node Controller
1. Overview Two major components exist in our current prototype systems: the management node, including the Cloud Controller, Cluster Controller, Walrus and EBS, and the computing node, i.e. the Node Controller
Linux Driver Devices. Why, When, Which, How?
 Bertrand Mermet Sylvain Ract Linux Driver Devices. Why, When, Which, How? Since its creation in the early 1990 s Linux has been installed on millions of computers or embedded systems. These systems may
Bertrand Mermet Sylvain Ract Linux Driver Devices. Why, When, Which, How? Since its creation in the early 1990 s Linux has been installed on millions of computers or embedded systems. These systems may
Load Balancing - Single Multipath Route HOWTO
 Load Balancing - Single Multipath Route HOWTO Shakthi Kannan, shaks_wants_no_spam_at_shakthimaan_dot_com January 5, 2007 Revision: 1.2 Abstract This documentation provides the steps to setup load-balancing
Load Balancing - Single Multipath Route HOWTO Shakthi Kannan, shaks_wants_no_spam_at_shakthimaan_dot_com January 5, 2007 Revision: 1.2 Abstract This documentation provides the steps to setup load-balancing
10 STEPS TO YOUR FIRST QNX PROGRAM. QUICKSTART GUIDE Second Edition
 10 STEPS TO YOUR FIRST QNX PROGRAM QUICKSTART GUIDE Second Edition QNX QUICKSTART GUIDE A guide to help you install and configure the QNX Momentics tools and the QNX Neutrino operating system, so you can
10 STEPS TO YOUR FIRST QNX PROGRAM QUICKSTART GUIDE Second Edition QNX QUICKSTART GUIDE A guide to help you install and configure the QNX Momentics tools and the QNX Neutrino operating system, so you can
SELinux. Security Enhanced Linux
 SELinux Security Enhanced Linux Introduction and brief overview. Copyright 2005 by Paweł J. Sawicki http://www.pawel-sawicki.com/ Agenda DAC Discretionary Access Control ACL Access Control Lists MAC Mandatory
SELinux Security Enhanced Linux Introduction and brief overview. Copyright 2005 by Paweł J. Sawicki http://www.pawel-sawicki.com/ Agenda DAC Discretionary Access Control ACL Access Control Lists MAC Mandatory
I Control Your Code Attack Vectors Through the Eyes of Software-based Fault Isolation. Mathias Payer, ETH Zurich
 I Control Your Code Attack Vectors Through the Eyes of Software-based Fault Isolation Mathias Payer, ETH Zurich Motivation Applications often vulnerable to security exploits Solution: restrict application
I Control Your Code Attack Vectors Through the Eyes of Software-based Fault Isolation Mathias Payer, ETH Zurich Motivation Applications often vulnerable to security exploits Solution: restrict application
Eaton NetWatch NetWatch installation and configuration guide VMware ESX 3 Virtual architecture
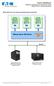 Eaton NetWatch NetWatch installation and configuration guide VMware ESX 3 Virtual architecture VMware ESX server host and guest operating systems architecture Virtual/ Guest OS 1 (Windows) Applications,
Eaton NetWatch NetWatch installation and configuration guide VMware ESX 3 Virtual architecture VMware ESX server host and guest operating systems architecture Virtual/ Guest OS 1 (Windows) Applications,
Newton2 Developers Guide
 Newton2 Developers Guide Date: Jan. 2015 Newton2 Developers Guide Release history Date Revision Revision History Jan. 12, 2015 1.0 - First released Disclaimer This documentation is provided for use with
Newton2 Developers Guide Date: Jan. 2015 Newton2 Developers Guide Release history Date Revision Revision History Jan. 12, 2015 1.0 - First released Disclaimer This documentation is provided for use with
Using the NicheStack TCP/IP Stack - Nios II Edition Tutorial
 Using the NicheStack TCP/IP Stack - Nios II Edition Tutorial Using the NicheStack TCP/IP Stack - Nios II Edition Tutorial 101 Innovation Drive San Jose, CA 95134 www.altera.com TU-01001-3.0 Subscribe Copyright
Using the NicheStack TCP/IP Stack - Nios II Edition Tutorial Using the NicheStack TCP/IP Stack - Nios II Edition Tutorial 101 Innovation Drive San Jose, CA 95134 www.altera.com TU-01001-3.0 Subscribe Copyright
Acronis Backup & Recovery 10 Server for Linux. Quick Start Guide
 Acronis Backup & Recovery 10 Server for Linux Quick Start Guide Table of contents 1 Supported operating systems...3 2 What you need to get started...3 3 Installing and starting to use the product...3 3.1
Acronis Backup & Recovery 10 Server for Linux Quick Start Guide Table of contents 1 Supported operating systems...3 2 What you need to get started...3 3 Installing and starting to use the product...3 3.1
Objectives. Chapter 2: Operating-System Structures. Operating System Services (Cont.) Operating System Services. Operating System Services (Cont.
 Objectives To describe the services an operating system provides to users, processes, and other systems To discuss the various ways of structuring an operating system Chapter 2: Operating-System Structures
Objectives To describe the services an operating system provides to users, processes, and other systems To discuss the various ways of structuring an operating system Chapter 2: Operating-System Structures
Building a Python Plugin
 Building a Python Plugin QGIS Tutorials and Tips Author Ujaval Gandhi http://google.com/+ujavalgandhi This work is licensed under a Creative Commons Attribution 4.0 International License. Building a Python
Building a Python Plugin QGIS Tutorials and Tips Author Ujaval Gandhi http://google.com/+ujavalgandhi This work is licensed under a Creative Commons Attribution 4.0 International License. Building a Python
Systemd for Embedded Linux. Challenges and Opportunities
 Systemd for Embedded Linux Challenges and Opportunities Embedded Linux Conference Europe Düsseldorf, 2014-10-14 Michael Olbrich Slide 1 - Pengutronix - http://www.pengutronix.de
Systemd for Embedded Linux Challenges and Opportunities Embedded Linux Conference Europe Düsseldorf, 2014-10-14 Michael Olbrich Slide 1 - Pengutronix - http://www.pengutronix.de
Introduction. dnotify
 Introduction In a multi-user, multi-process operating system, files are continually being created, modified and deleted, often by apparently unrelated processes. This means that any software that needs
Introduction In a multi-user, multi-process operating system, files are continually being created, modified and deleted, often by apparently unrelated processes. This means that any software that needs
Freescale Semiconductor, I
 nc. Application Note 6/2002 8-Bit Software Development Kit By Jiri Ryba Introduction 8-Bit SDK Overview This application note describes the features and advantages of the 8-bit SDK (software development
nc. Application Note 6/2002 8-Bit Software Development Kit By Jiri Ryba Introduction 8-Bit SDK Overview This application note describes the features and advantages of the 8-bit SDK (software development
Toasterkit - A NetBSD Rootkit. Anthony Martinez Thomas Bowen http://mrtheplague.net/toasterkit/
 Toasterkit - A NetBSD Rootkit Anthony Martinez Thomas Bowen http://mrtheplague.net/toasterkit/ Toasterkit - A NetBSD Rootkit 1. Who we are 2. What is NetBSD? Why NetBSD? 3. Rootkits on NetBSD 4. Architectural
Toasterkit - A NetBSD Rootkit Anthony Martinez Thomas Bowen http://mrtheplague.net/toasterkit/ Toasterkit - A NetBSD Rootkit 1. Who we are 2. What is NetBSD? Why NetBSD? 3. Rootkits on NetBSD 4. Architectural
How To Run A Password Manager On A 32 Bit Computer (For 64 Bit) On A 64 Bit Computer With A Password Logger (For 32 Bit) (For Linux) ( For 64 Bit (Foramd64) (Amd64 (For Pc
 SafeNet Authentication Client (Linux) Administrator s Guide Version 8.1 Revision A Copyright 2011, SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document
SafeNet Authentication Client (Linux) Administrator s Guide Version 8.1 Revision A Copyright 2011, SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document
8 Tutorial: Using ASN.1
 8 Tutorial: Using ASN.1 Data Types This tutorial describes how to use ASN.1 types and values in the SDL suite. You will learn how to import and use ASN.1 modules in your SDL diagrams, how to generate code
8 Tutorial: Using ASN.1 Data Types This tutorial describes how to use ASN.1 types and values in the SDL suite. You will learn how to import and use ASN.1 modules in your SDL diagrams, how to generate code
Image Acquisition Toolbox Adaptor Kit User's Guide
 Image Acquisition Toolbox Adaptor Kit User's Guide R2015b How to Contact MathWorks Latest news: www.mathworks.com Sales and services: www.mathworks.com/sales_and_services User community: www.mathworks.com/matlabcentral
Image Acquisition Toolbox Adaptor Kit User's Guide R2015b How to Contact MathWorks Latest news: www.mathworks.com Sales and services: www.mathworks.com/sales_and_services User community: www.mathworks.com/matlabcentral
IT6204 Systems & Network Administration. (Optional)
 Systems & Network Administration (Optional) INTRODUCTION This is one of the Optional courses designed for Semester 6 of the Bachelor of Information Technology Degree program. This course on Systems & Network
Systems & Network Administration (Optional) INTRODUCTION This is one of the Optional courses designed for Semester 6 of the Bachelor of Information Technology Degree program. This course on Systems & Network
CS197U: A Hands on Introduction to Unix
 CS197U: A Hands on Introduction to Unix Lecture 4: My First Linux System J.D. DeVaughn-Brown University of Massachusetts Amherst Department of Computer Science [email protected] 1 Reminders After
CS197U: A Hands on Introduction to Unix Lecture 4: My First Linux System J.D. DeVaughn-Brown University of Massachusetts Amherst Department of Computer Science [email protected] 1 Reminders After
CPSC 226 Lab Nine Fall 2015
 CPSC 226 Lab Nine Fall 2015 Directions. Our overall lab goal is to learn how to use BBB/Debian as a typical Linux/ARM embedded environment, program in a traditional Linux C programming environment, and
CPSC 226 Lab Nine Fall 2015 Directions. Our overall lab goal is to learn how to use BBB/Debian as a typical Linux/ARM embedded environment, program in a traditional Linux C programming environment, and
A Design of Video Acquisition and Transmission Based on ARM. Ziqiang Hao a, Hongzuo Li b
 A Design of Video Acquisition and Transmission Based on ARM Ziqiang Hao a, Hongzuo Li b Changchun University of Science & Technology, Changchun, Jilin, China a [email protected], b [email protected] Keywords:video
A Design of Video Acquisition and Transmission Based on ARM Ziqiang Hao a, Hongzuo Li b Changchun University of Science & Technology, Changchun, Jilin, China a [email protected], b [email protected] Keywords:video
ORACLE BUSINESS INTELLIGENCE WORKSHOP. Prerequisites for Oracle BI Workshop
 ORACLE BUSINESS INTELLIGENCE WORKSHOP Prerequisites for Oracle BI Workshop Introduction...2 Hardware Requirements...2 Minimum Hardware configuration:...2 Software Requirements...2 Virtual Machine: Runtime...2
ORACLE BUSINESS INTELLIGENCE WORKSHOP Prerequisites for Oracle BI Workshop Introduction...2 Hardware Requirements...2 Minimum Hardware configuration:...2 Software Requirements...2 Virtual Machine: Runtime...2
AlienVault Unified Security Management (USM) 4.x-5.x. Deploying HIDS Agents to Linux Hosts
 AlienVault Unified Security Management (USM) 4.x-5.x Deploying HIDS Agents to Linux Hosts USM 4.x-5.x Deploying HIDS Agents to Linux Hosts, rev. 2 Copyright 2015 AlienVault, Inc. All rights reserved. AlienVault,
AlienVault Unified Security Management (USM) 4.x-5.x Deploying HIDS Agents to Linux Hosts USM 4.x-5.x Deploying HIDS Agents to Linux Hosts, rev. 2 Copyright 2015 AlienVault, Inc. All rights reserved. AlienVault,
Implementing SAN & NAS with Linux by Mark Manoukian & Roy Koh
 Implementing SAN & NAS with Linux by Mark Manoukian & Roy Koh Housekeeping Evaluations OSS2 Be Honest Comments Questions? Raise your hand, wait for the Microphone. Check the on-line version of this presentation
Implementing SAN & NAS with Linux by Mark Manoukian & Roy Koh Housekeeping Evaluations OSS2 Be Honest Comments Questions? Raise your hand, wait for the Microphone. Check the on-line version of this presentation
Last Class: OS and Computer Architecture. Last Class: OS and Computer Architecture
 Last Class: OS and Computer Architecture System bus Network card CPU, memory, I/O devices, network card, system bus Lecture 3, page 1 Last Class: OS and Computer Architecture OS Service Protection Interrupts
Last Class: OS and Computer Architecture System bus Network card CPU, memory, I/O devices, network card, system bus Lecture 3, page 1 Last Class: OS and Computer Architecture OS Service Protection Interrupts
Operating System Structures
 COP 4610: Introduction to Operating Systems (Spring 2015) Operating System Structures Zhi Wang Florida State University Content Operating system services User interface System calls System programs Operating
COP 4610: Introduction to Operating Systems (Spring 2015) Operating System Structures Zhi Wang Florida State University Content Operating system services User interface System calls System programs Operating
One-Stop Intel TXT Activation Guide
 One-Stop Intel TXT Activation Guide DELL* PowerEdge 12G Server Systems Intel Trusted Execution Technology (Intel TXT) for Intel Xeon processor-based servers is commonly used to enhance platform security
One-Stop Intel TXT Activation Guide DELL* PowerEdge 12G Server Systems Intel Trusted Execution Technology (Intel TXT) for Intel Xeon processor-based servers is commonly used to enhance platform security
Getting Started with the Linux Intrusion Detection
 1 of 7 6/18/2006 9:07 PM Getting Started with the Linux Intrusion Detection System Irfan Habib Abstract Sometimes file permissions aren't enough. LIDS gives you kernel-level access control that goes beyond
1 of 7 6/18/2006 9:07 PM Getting Started with the Linux Intrusion Detection System Irfan Habib Abstract Sometimes file permissions aren't enough. LIDS gives you kernel-level access control that goes beyond
How to Create, Setup, and Configure an Ubuntu Router with a Transparent Proxy.
 In this tutorial I am going to explain how to setup a home router with transparent proxy using Linux Ubuntu and Virtualbox. Before we begin to delve into the heart of installing software and typing in
In this tutorial I am going to explain how to setup a home router with transparent proxy using Linux Ubuntu and Virtualbox. Before we begin to delve into the heart of installing software and typing in
Operating System Overview. Otto J. Anshus
 Operating System Overview Otto J. Anshus A Typical Computer CPU... CPU Memory Chipset I/O bus ROM Keyboard Network A Typical Computer System CPU. CPU Memory Application(s) Operating System ROM OS Apps
Operating System Overview Otto J. Anshus A Typical Computer CPU... CPU Memory Chipset I/O bus ROM Keyboard Network A Typical Computer System CPU. CPU Memory Application(s) Operating System ROM OS Apps
RocketRAID 2640/2642 SAS Controller Ubuntu Linux Installation Guide
 RocketRAID 2640/2642 SAS Controller Ubuntu Linux Installation Guide Version 1.2 Copyright 2012 HighPoint Technologies, Inc. All rights reserved. Last updated on June 14, 2012 Table of Contents 1 Overview...
RocketRAID 2640/2642 SAS Controller Ubuntu Linux Installation Guide Version 1.2 Copyright 2012 HighPoint Technologies, Inc. All rights reserved. Last updated on June 14, 2012 Table of Contents 1 Overview...
The POSIX Socket API
 The POSIX Giovanni Agosta Piattaforme Software per la Rete Modulo 2 G. Agosta The POSIX Outline Sockets & TCP Connections 1 Sockets & TCP Connections 2 3 4 G. Agosta The POSIX TCP Connections Preliminaries
The POSIX Giovanni Agosta Piattaforme Software per la Rete Modulo 2 G. Agosta The POSIX Outline Sockets & TCP Connections 1 Sockets & TCP Connections 2 3 4 G. Agosta The POSIX TCP Connections Preliminaries
Creating a DUO MFA Service in AWS
 Amazon AWS is a cloud based development environment with a goal to provide many options to companies wishing to leverage the power and convenience of cloud computing within their organisation. In 2013
Amazon AWS is a cloud based development environment with a goal to provide many options to companies wishing to leverage the power and convenience of cloud computing within their organisation. In 2013
Using Red Hat Enterprise Linux with Georgia Tech's RHN Satellite Server Installing Red Hat Enterprise Linux
 Using Red Hat Enterprise Linux with Georgia Tech's RHN Satellite Server Installing Red Hat Enterprise Linux NOTE: If you need more information regarding the installation process for other distributions
Using Red Hat Enterprise Linux with Georgia Tech's RHN Satellite Server Installing Red Hat Enterprise Linux NOTE: If you need more information regarding the installation process for other distributions
Installing Proview on an Windows XP machine
 Installing Proview on an Windows XP machine This is a guide for the installation of Proview on an WindowsXP machine using VirtualBox. VirtualBox makes it possible to create virtual computers and allows
Installing Proview on an Windows XP machine This is a guide for the installation of Proview on an WindowsXP machine using VirtualBox. VirtualBox makes it possible to create virtual computers and allows
Chapter 3 Operating-System Structures
 Contents 1. Introduction 2. Computer-System Structures 3. Operating-System Structures 4. Processes 5. Threads 6. CPU Scheduling 7. Process Synchronization 8. Deadlocks 9. Memory Management 10. Virtual
Contents 1. Introduction 2. Computer-System Structures 3. Operating-System Structures 4. Processes 5. Threads 6. CPU Scheduling 7. Process Synchronization 8. Deadlocks 9. Memory Management 10. Virtual
QuickBooks Enterprise Solutions. Linux Database Server Manager Installation and Configuration Guide
 QuickBooks Enterprise Solutions Linux Database Server Manager Installation and Configuration Guide Copyright Copyright 2007 Intuit Inc. All rights reserved. STATEMENTS IN THIS DOCUMENT REGARDING THIRD-PARTY
QuickBooks Enterprise Solutions Linux Database Server Manager Installation and Configuration Guide Copyright Copyright 2007 Intuit Inc. All rights reserved. STATEMENTS IN THIS DOCUMENT REGARDING THIRD-PARTY
Upgrade ProTracker Advantage Access database to a SQL database
 Many of our customers run the process themselves with great success. We are available to run the process for you or we can be available on standby from 9:00-5:00(Eastern) to provide assistance if needed.
Many of our customers run the process themselves with great success. We are available to run the process for you or we can be available on standby from 9:00-5:00(Eastern) to provide assistance if needed.
PetaLinux SDK User Guide. Application Development Guide
 PetaLinux SDK User Guide Application Development Guide Notice of Disclaimer The information disclosed to you hereunder (the "Materials") is provided solely for the selection and use of Xilinx products.
PetaLinux SDK User Guide Application Development Guide Notice of Disclaimer The information disclosed to you hereunder (the "Materials") is provided solely for the selection and use of Xilinx products.
Installing Java (Windows) and Writing your First Program
 Appendix Installing Java (Windows) and Writing your First Program We will be running Java from the command line and writing Java code in Notepad++ (or similar). The first step is to ensure you have installed
Appendix Installing Java (Windows) and Writing your First Program We will be running Java from the command line and writing Java code in Notepad++ (or similar). The first step is to ensure you have installed
CS 377: Operating Systems. Outline. A review of what you ve learned, and how it applies to a real operating system. Lecture 25 - Linux Case Study
 CS 377: Operating Systems Lecture 25 - Linux Case Study Guest Lecturer: Tim Wood Outline Linux History Design Principles System Overview Process Scheduling Memory Management File Systems A review of what
CS 377: Operating Systems Lecture 25 - Linux Case Study Guest Lecturer: Tim Wood Outline Linux History Design Principles System Overview Process Scheduling Memory Management File Systems A review of what
