Document Control Software
|
|
|
- Jeffrey Barrett
- 10 years ago
- Views:
Transcription
1 Document Control Software Complying with AS9100 requirements A document control software system ensures that good manufacturing methods are adopted and improved upon. According to ISO standards, only authorized personnel can impart changes to the documentation directing manufacturing methods. Besides, all changes need to be recorded for future verification. Therefore, any organization following ISO norms is required to have a system in place to control document changes. Getting an ISO certification is fine but being able to continuously maintain the system is a challenge. For example, a process involving paper or hybrid electronic / paper systems requires meticulous maintenance from both the company in general and the senior management in particular. It is common practice for a system to be left unattended once certification has been accomplished. The process of upgradation is again considered only when an audit is at hand. This is because most organizations consider an ISO certification too time consuming to maintain. If manual systems are put in place to maintain processes, they can be error prone and employees may have a free hand with documents. In addition, new versions may not be available on time. In order to get rid of the above problems, organizations look forward to quality management software systems. This article highlights the document control concepts of a quality management system and on how its processes allow a company to positively influence the following: Maintaining its processes Controlling the distribution of documents Improving profitability A document control software system encompasses various features, as highlighted in the following paragraphs. Restrictive Access Document Management Automatic Version Control Simple System Administration User Friendliness Document Grouping/Access Rights
2 Restrictive access User/Password protection All systems require a unique Username / Password combination for each user having access to the system. In addition, the password needs to be alphanumeric to ensure that it cannot be logically recreated. Intruder lockout An account needs to be automatically locked out if a user attempts to login using an inaccurate Username / Password combination. The locking out function is activated when a preconfigured number of false attempts have occurred. This protects against attempts by unauthorized individuals to access the system. The System Administrator is the only individual who can re-set a locked out account. Document access restrictions An organization runs on the strength of its workforce. Each person within this workforce has a unique role, which may or may not require him or her to interact with a person having a different role. Therefore, it is imperative to set up foolproof documentation procedures to ensure restricted access to the system. Usually, access verification enables the following: Viewing or Read Access Authoring or Write Access Approving Users can be given access to one or more of these functions depending on their role. Document management To improve the efficiency of running an organization, processes that have iterative elements need to be automated. Document management enhances the functioning of an ISO system. The following points highlight the importance of a document management system. Application independence A system needs to control documents from a variety of commonly used applications such as Word and Excel. In addition, the system needs to handle audio and video files. Lifecycle management Documents follow a lifecycle that begins at a draft, passes through publishing and ends at archiving. It is important that access is restricted to the documents at each stage of its lifecycle. Document history All events pertaining to a document need to be automatically recorded. Accessibility of document history can be given to approved users. Central and safe storage Documents need to be stored in a secure manner to ensure only authorized access on one hand while shielding against loss or destruction on the other.
3 Automatic version control Version control of a document is both time consuming and can lead to embarrassing mistakes when a new version replaces an older one. A document control system can provide key automation benefits as listed below: Availability of the latest version There should be no doubts about the document being available in the latest version to rule out any confusion that may arise. Automatic routing When document needs approval, reviewing or other changes, the concerned persons need to be automatically notified. Automatic document replacement Newer approved versions of a document need to automatically replace older versions. The obsolete version needs to be archived. Automatic notifications notifications, which can be deactivated, can be provided to inform users when they are required to perform a task or need to be aware of an event. There should also be another notification system in place, which cannot be deactivated. Tasks such as reviews, approvals and change requests can be informed through such notifications. Events such as publishing, confirmed rejections and rejected change requests could also be notified. Approval history A document can be in any stage of its life cycle. Managers should be able to view the complete approval status and history of any document at any stage. Automatic publishing on approval Once a document is approved, it should be published automatically to users who have its access rights. Older versions need to be replaced and archived.
4 Simple system administration An easy to use system administration ensures that any user can understand the document control procedures while having a minimal understanding of technology. An effective form of system administration encompasses the following: Preconfigured routing Routing rules should depend on document types or approval type. They can be set and fixed under the bonnet with easy to understand attributes. Configurable user access rights The system administrator should be able to configure read and write access rights by grouping documents together. System reporting A simple report builder should be incorporated into the system. This would help administrators create reports with flexibility. In addition, the option of standard built in reports would enhance information. User Friendliness A document control system should provide users with an easy to learn experience. The following list focuses on the importance of keeping a document control system simple. Platform independence The system should work irrespective of the platform to enable it to merge with different databases. Eliminate installation The system can eliminate the need to install applications by means of user friendly software such as flash. Web-based client access A user should be able to connect to the system from any Internet connection regardless of physical location. This enables geographically dispersed clients and suppliers / customers to access the system without additional software or hardware. Search capability Documents need to be keyword friendly. Users should be able to search for documents using keywords. Only those documents that meet the search criteria and the user s access rights need to be displayed. Grouping of documents Once documents are grouped, they provide easier search options. An easy to use graphical interface, such as Windows Treeview, with folders and sub-folders enable documents to be grouped and searched logically. Training for system administrators and regular users Easy and interactive Web based training, in parts, can be made available to users depending on their convenience.
5 Document grouping and access rights When a document control system has been put in place, the responsibility for each document group or class needs to be demarcated. This enhances the efficacy of the system and the resources cater to the people who play a role. Grouping of both users and documents are discussed in the following list. Document Grouping Documents within a document control system serve a purpose. Many other documents may also serve the same purpose and can be logically grouped. This ensures that only specific users need to be given access to the documents groups. Documents Readers Access to documents needs to be restricted to users who need to view or make changes to the documents as part of their responsibility. Document grouping plays a major role in determining access rights. Time invested in grouping yields rich rewards. Certain software systems provide access only to users groups. Before being given access, the users too need to be grouped. Documents Writers Writers have management responsibility over documents. They are the originators or authors of the documents and are responsible for updating them. They also need to report alterations made in a document and the reasons for making the changes. Writers may also be readers of the documents. This accountability may be at a department / functional level or at an organization level depending on the company. Documents Approvers Certain documents need go through a review and approval process. Approvers ensure that documents are accurate. They are experts in their relative fields and may be required only to review and approve documents in functional areas. They may also function as document readers and writers. The structure of the document control system is based on the above four classifications. Such a group enables a system to run smoothly and ensures that document control software can be configured easily. Spending time on people and document grouping is time well spent. Conclusion Companies that have graduated from a manual system to an electronic document control system may be of the opinion that: day-to-day tasks are easily completed. return on investment has been made. However, the companies will agree that transition has required an important investment in time. This investment will ensure that the new document control system has been well planned. Finally, organizations are bound to heave a sigh of relief that a hosted document control system does not require upgrades in infrastructure.
Password Expiration Passwords require a maximum expiration age of 60 days. Previously used passwords may not be reused.
 DRAFT 6.1 Information Systems Passwords OVERVIEW Passwords are an important aspect of information security. They are the front line of protection for user accounts. A poorly chosen password may result
DRAFT 6.1 Information Systems Passwords OVERVIEW Passwords are an important aspect of information security. They are the front line of protection for user accounts. A poorly chosen password may result
USERS MANUAL FOR OWL A DOCUMENT REPOSITORY SYSTEM
 USERS MANUAL FOR OWL A DOCUMENT REPOSITORY SYSTEM User Manual Table of Contents Introducing OWL...3 Starting to use Owl...4 The Logging in page...4 Using the browser...6 Folder structure...6 Title Bar...6
USERS MANUAL FOR OWL A DOCUMENT REPOSITORY SYSTEM User Manual Table of Contents Introducing OWL...3 Starting to use Owl...4 The Logging in page...4 Using the browser...6 Folder structure...6 Title Bar...6
Access Control and Audit Trail Software
 Varian, Inc. 2700 Mitchell Drive Walnut Creek, CA 94598-1675/USA Access Control and Audit Trail Software Operation Manual Varian, Inc. 2002 03-914941-00:3 Table of Contents Introduction... 1 Access Control
Varian, Inc. 2700 Mitchell Drive Walnut Creek, CA 94598-1675/USA Access Control and Audit Trail Software Operation Manual Varian, Inc. 2002 03-914941-00:3 Table of Contents Introduction... 1 Access Control
Workflow Templates Library
 Workflow s Library Table of Contents Intro... 2 Active Directory... 3 Application... 5 Cisco... 7 Database... 8 Excel Automation... 9 Files and Folders... 10 FTP Tasks... 13 Incident Management... 14 Security
Workflow s Library Table of Contents Intro... 2 Active Directory... 3 Application... 5 Cisco... 7 Database... 8 Excel Automation... 9 Files and Folders... 10 FTP Tasks... 13 Incident Management... 14 Security
ALM - Key benefits. t: +31(0) 88 1221 800 f: +31(0) 88 1221 899. Oude Oeverstraat 120-5 6811 JZ Arnhem The Netherlands. ALM Key benefits 01/01/2014 1
 ALM - Key benefits Oude Oeverstraat 120-5 6811 JZ Arnhem The Netherlands t: +31(0) 88 1221 800 f: +31(0) 88 1221 899 ALM Key benefits 01/01/2014 1 Key benefits What problems are we solving? Active Login
ALM - Key benefits Oude Oeverstraat 120-5 6811 JZ Arnhem The Netherlands t: +31(0) 88 1221 800 f: +31(0) 88 1221 899 ALM Key benefits 01/01/2014 1 Key benefits What problems are we solving? Active Login
Using Contactless Smart Cards for Secure Applications
 Using Contactless Smart Cards for Secure Applications Classification: Public (Info Level 1) Document No.: LA-11-005d-en Edition: 2010 www.legic.com LEGIC Identsystems Ltd Binzackerstrasse 41, CH-8620 Wetzikon,
Using Contactless Smart Cards for Secure Applications Classification: Public (Info Level 1) Document No.: LA-11-005d-en Edition: 2010 www.legic.com LEGIC Identsystems Ltd Binzackerstrasse 41, CH-8620 Wetzikon,
Service Asset & Configuration Management PinkVERIFY
 -11-G-001 General Criteria Does the tool use ITIL 2011 Edition process terms and align to ITIL 2011 Edition workflows and process integrations? -11-G-002 Does the tool have security controls in place to
-11-G-001 General Criteria Does the tool use ITIL 2011 Edition process terms and align to ITIL 2011 Edition workflows and process integrations? -11-G-002 Does the tool have security controls in place to
RECORDS AND INFORMATION MANAGEMENT AND RETENTION
 RECORDS AND INFORMATION MANAGEMENT AND RETENTION Policy The Health Science Center recognizes the need for orderly management and retrieval of all official records and a documented records retention and
RECORDS AND INFORMATION MANAGEMENT AND RETENTION Policy The Health Science Center recognizes the need for orderly management and retrieval of all official records and a documented records retention and
INFORMATION TECHNOLOGY CONTROLS
 CHAPTER 14 INFORMATION TECHNOLOGY CONTROLS SCOPE This chapter addresses requirements common to all financial accounting systems and is not limited to the statewide financial accounting system, ENCOMPASS,
CHAPTER 14 INFORMATION TECHNOLOGY CONTROLS SCOPE This chapter addresses requirements common to all financial accounting systems and is not limited to the statewide financial accounting system, ENCOMPASS,
Asset and Lifecycle Management
 Campbell Robertson, Worldwide Public Sector Solution Leader, IBM ECM August 2014 Asset and Lifecycle Management With enterprise content management from IBM The asset lifecycle Concept Design Tender Build
Campbell Robertson, Worldwide Public Sector Solution Leader, IBM ECM August 2014 Asset and Lifecycle Management With enterprise content management from IBM The asset lifecycle Concept Design Tender Build
SCADA Compliance Tools For NERC-CIP. The Right Tools for Bringing Your Organization in Line with the Latest Standards
 SCADA Compliance Tools For NERC-CIP The Right Tools for Bringing Your Organization in Line with the Latest Standards OVERVIEW Electrical utilities are responsible for defining critical cyber assets which
SCADA Compliance Tools For NERC-CIP The Right Tools for Bringing Your Organization in Line with the Latest Standards OVERVIEW Electrical utilities are responsible for defining critical cyber assets which
CROATIAN PARLIAMENT 1364
 CROATIAN PARLIAMENT 1364 Pursuant to Article 88 of the Constitution of the Republic of Croatia, I hereby pass the DECISION PROMULGATING THE ACT ON PERSONAL DATA PROTECTION I hereby promulgate the Act on
CROATIAN PARLIAMENT 1364 Pursuant to Article 88 of the Constitution of the Republic of Croatia, I hereby pass the DECISION PROMULGATING THE ACT ON PERSONAL DATA PROTECTION I hereby promulgate the Act on
How to set up your NMC Online account. How to set up your NMC Online account
 How to set up your NMC Online account 1 Introduction NMC Online is a secure service which allows you to manage your registration with us online. This guidance explains how you can set up your account.
How to set up your NMC Online account 1 Introduction NMC Online is a secure service which allows you to manage your registration with us online. This guidance explains how you can set up your account.
05.0 Application Development
 Number 5.0 Policy Owner Information Security and Technology Policy Application Development Effective 01/01/2014 Last Revision 12/30/2013 Department of Innovation and Technology 5. Application Development
Number 5.0 Policy Owner Information Security and Technology Policy Application Development Effective 01/01/2014 Last Revision 12/30/2013 Department of Innovation and Technology 5. Application Development
Kofax Transformation Modules Generic Versus Specific Online Learning
 Kofax Transformation Modules Generic Versus Specific Online Learning Date June 27, 2011 Applies To Kofax Transformation Modules 3.5, 4.0, 4.5, 5.0 Summary This application note provides information about
Kofax Transformation Modules Generic Versus Specific Online Learning Date June 27, 2011 Applies To Kofax Transformation Modules 3.5, 4.0, 4.5, 5.0 Summary This application note provides information about
Document Control in an ISO Environment
 AN INTRODUCTORY GUIDE: Document Control in an ISO Environment How to maintain an up-to-date Quality System Why is Document Control Important? Document control has the ability to ensure that all end users
AN INTRODUCTORY GUIDE: Document Control in an ISO Environment How to maintain an up-to-date Quality System Why is Document Control Important? Document control has the ability to ensure that all end users
NETWRIX IDENTITY MANAGEMENT SUITE
 NETWRIX IDENTITY MANAGEMENT SUITE FEATURES AND REQUIREMENTS Product Version: 3.3 February 2013. Legal Notice The information in this publication is furnished for information use only, and does not constitute
NETWRIX IDENTITY MANAGEMENT SUITE FEATURES AND REQUIREMENTS Product Version: 3.3 February 2013. Legal Notice The information in this publication is furnished for information use only, and does not constitute
ATTACHMENT III Tender No. 10000265-HD-48009. Laboratory Information Management System (LIMS)
 Objective: ATTACHMENT III Tender No. 10000265-HD-48009 Laboratory Information Management System (LIMS) HPCL Mumbai refinery is looking for LIMS system to automate the Refinery Laboratory operation and
Objective: ATTACHMENT III Tender No. 10000265-HD-48009 Laboratory Information Management System (LIMS) HPCL Mumbai refinery is looking for LIMS system to automate the Refinery Laboratory operation and
CBI s Corporate Internet Banking Inquiry Services gives you the ability to view account details and transactions anytime, anywhere.
 Benefits & Features CBI s Corporate Internet Banking Inquiry Services gives you the ability to view account details and transactions anytime, anywhere. What can I do with Internet Banking? You can inquire
Benefits & Features CBI s Corporate Internet Banking Inquiry Services gives you the ability to view account details and transactions anytime, anywhere. What can I do with Internet Banking? You can inquire
ArtfulBits Password Reset Web Part
 User Guide ArtfulBits Password Reset Web Part for Microsoft SharePoint Overview... 1 Feature List... 2 Why ArtfulBits Password Reset Web Part?... 2 How to Use... 2 Password Reset Process Flow... 2 Password
User Guide ArtfulBits Password Reset Web Part for Microsoft SharePoint Overview... 1 Feature List... 2 Why ArtfulBits Password Reset Web Part?... 2 How to Use... 2 Password Reset Process Flow... 2 Password
What Is Ad-Aware Update Server?
 Contents What Is Ad-Aware Update Server?...2 Installation and Removal...3 System Requirements...3 Obtaining the Installation File...3 Installing Ad-Aware Update Server...3 Upgrade...4 Repairing, Modifying
Contents What Is Ad-Aware Update Server?...2 Installation and Removal...3 System Requirements...3 Obtaining the Installation File...3 Installing Ad-Aware Update Server...3 Upgrade...4 Repairing, Modifying
Managing FactoryTalk Security for Multiple FactoryTalk View Studio Applications
 Managing FactoryTalk Security for Multiple FactoryTalk View Studio Applications Relevant Products - FactoryTalk View Machine Edition 5.0 - RSView Machine Edition 4.0 - FactoryTalk View Supervisory Edition
Managing FactoryTalk Security for Multiple FactoryTalk View Studio Applications Relevant Products - FactoryTalk View Machine Edition 5.0 - RSView Machine Edition 4.0 - FactoryTalk View Supervisory Edition
Cypress Connexion HELP Guide www.cypressconnexion.com
 Welcome to Cypress Connexion your one-stop-shop for accessing and managing your Cypress Communications account online, at your convenience. The following guide will provide you with helpful information
Welcome to Cypress Connexion your one-stop-shop for accessing and managing your Cypress Communications account online, at your convenience. The following guide will provide you with helpful information
Cross-Media Electronic Reporting Regulation (CROMERR)
 Cross-Media Electronic Reporting Regulation (CROMERR) Electronic Signature Agreement Guide Electronic Signature Agreement Requirements... 2 Electronic Signature Agreement Example... 4 Electronic Signature
Cross-Media Electronic Reporting Regulation (CROMERR) Electronic Signature Agreement Guide Electronic Signature Agreement Requirements... 2 Electronic Signature Agreement Example... 4 Electronic Signature
Footprints Customer Interface Guide
 Footprints Customer Interface Guide Introduction Each support group in MIS has its own Service Desk within the Footprints System, and each service desk has its own colors and banner. Within each service
Footprints Customer Interface Guide Introduction Each support group in MIS has its own Service Desk within the Footprints System, and each service desk has its own colors and banner. Within each service
The Internet and e-mail 2 Acceptable use 2 Unacceptable use 2 Downloads 3 Copyrights 3 Monitoring 3. Computer Viruses 3
 Table of Contents 1 Acceptable use 1 Violations 1 Administration 1 Director and Supervisor Responsibilities 1 MIS Director Responsibilities 1 The Internet and e-mail 2 Acceptable use 2 Unacceptable use
Table of Contents 1 Acceptable use 1 Violations 1 Administration 1 Director and Supervisor Responsibilities 1 MIS Director Responsibilities 1 The Internet and e-mail 2 Acceptable use 2 Unacceptable use
Life Cycle of Records
 Discard Create Inactive Life Cycle of Records Current Retain Use Semi-current Records Management Policy April 2014 Document title Records Management Policy April 2014 Document author and department Responsible
Discard Create Inactive Life Cycle of Records Current Retain Use Semi-current Records Management Policy April 2014 Document title Records Management Policy April 2014 Document author and department Responsible
CAREER TRACKS PHASE 1 UCSD Information Technology Family Function and Job Function Summary
 UCSD Applications Programming Involved in the development of server / OS / desktop / mobile applications and services including researching, designing, developing specifications for designing, writing,
UCSD Applications Programming Involved in the development of server / OS / desktop / mobile applications and services including researching, designing, developing specifications for designing, writing,
Document Control. DOWNLOADED AND/OR HARD COPY UNCONTROLLED Verify that this is the correct version before use.
 DOWNLOADED AND/OR HARD COPY UNCONTROLLED Verify that this is the correct version before use. AUTHORITY DATE Jeffrey Northey (original signature on file) IMS Manager 10/16/2014 Richard Grigg (original signature
DOWNLOADED AND/OR HARD COPY UNCONTROLLED Verify that this is the correct version before use. AUTHORITY DATE Jeffrey Northey (original signature on file) IMS Manager 10/16/2014 Richard Grigg (original signature
An Introduction to Transparent Records Management
 Records Management Focus White Paper An Introduction to Transparent Records Management Learn More Inside: Meet the needs of both records managers and general users. Easily manage multiple departments information
Records Management Focus White Paper An Introduction to Transparent Records Management Learn More Inside: Meet the needs of both records managers and general users. Easily manage multiple departments information
Minimum Requirements for Cencon 4 with Microsoft R SQL 2008 R2 Standard
 Minimum Requirements for Cencon 4 with Microsoft R SQL 2008 R2 Standard SQL 2008 R2 Standard Restrictions 4 CPU 64 GB Ram Use Limit 524 PB Database Size High Availability Options Limited Database Mirroring,
Minimum Requirements for Cencon 4 with Microsoft R SQL 2008 R2 Standard SQL 2008 R2 Standard Restrictions 4 CPU 64 GB Ram Use Limit 524 PB Database Size High Availability Options Limited Database Mirroring,
Minimum Requirements for Cencon 4 with Microsoft R SQL 2008 R2 Express
 Minimum Requirements for Cencon 4 with Microsoft R SQL 2008 R2 Express SQL 2008 R2 Express Restrictions 1 CPU 1 GB Ram Use Limit 10 GB Database Size High Availability Options None (No Database Mirroring,
Minimum Requirements for Cencon 4 with Microsoft R SQL 2008 R2 Express SQL 2008 R2 Express Restrictions 1 CPU 1 GB Ram Use Limit 10 GB Database Size High Availability Options None (No Database Mirroring,
Digital Asset Management
 A collaborative digital asset management system for marketing organizations that improves performance, saves time and reduces costs. MarketingPilot provides powerful digital asset management software for
A collaborative digital asset management system for marketing organizations that improves performance, saves time and reduces costs. MarketingPilot provides powerful digital asset management software for
Guide to Automating Workflows Quickly and Easily
 Guide to Automating Workflows Quickly and Easily Part 3 Back to Contents 1 2012 Nintex USA LLC, All rights reserved. Errors and omissions excepted. Table of Contents Introduction... 3 Handling the Full
Guide to Automating Workflows Quickly and Easily Part 3 Back to Contents 1 2012 Nintex USA LLC, All rights reserved. Errors and omissions excepted. Table of Contents Introduction... 3 Handling the Full
onesource workflow manager
 onesource workflow manager for Wealth Management TAX & ACCOUNTING improve processes for full compliance The more efficient your office, the better you can serve your clients and comply with regulations.
onesource workflow manager for Wealth Management TAX & ACCOUNTING improve processes for full compliance The more efficient your office, the better you can serve your clients and comply with regulations.
ORACLE FORMS APPLICATIONS?
 WHY UPGRADE/MIGRATE ORACLE FORMS APPLICATIONS? A WHITEPAPER The information provided in this white paper is for general information only. It is not a specific guide to any particular upgrade/migration.
WHY UPGRADE/MIGRATE ORACLE FORMS APPLICATIONS? A WHITEPAPER The information provided in this white paper is for general information only. It is not a specific guide to any particular upgrade/migration.
Using Adobe Acrobat X to enhance collaboration with Microsoft SharePoint and Microsoft Office
 Using Adobe Acrobat X to enhance collaboration with Microsoft SharePoint and Microsoft Office Accelerate project review cycles by integrating PDF-based workflows into the SharePoint and Office platform
Using Adobe Acrobat X to enhance collaboration with Microsoft SharePoint and Microsoft Office Accelerate project review cycles by integrating PDF-based workflows into the SharePoint and Office platform
Product Data Management
 Product Data Management Introduction to Product Data Management Product data means in this context in principle all the information that is somehow relevant to the product. Under here are examples of product
Product Data Management Introduction to Product Data Management Product data means in this context in principle all the information that is somehow relevant to the product. Under here are examples of product
THIRD PARTY USER GUIDE
 THIRD PARTY USER GUIDE Third Party User Guide Page 1 of 12 CONTENTS 1. INTRODUCTION... 3 2. INTENDED AUDIENCE... 3 3. ABOUT SiD... 3 4. HARDWARE & SOFTWARE REQUIREMENTS... 3 6. HOW TO ACCESS SiD VIA INTERNET...
THIRD PARTY USER GUIDE Third Party User Guide Page 1 of 12 CONTENTS 1. INTRODUCTION... 3 2. INTENDED AUDIENCE... 3 3. ABOUT SiD... 3 4. HARDWARE & SOFTWARE REQUIREMENTS... 3 6. HOW TO ACCESS SiD VIA INTERNET...
Access Control BUSINESS REQUIREMENTS FOR ACCESS CONTROL
 AU7087_C013.fm Page 173 Friday, April 28, 2006 9:45 AM 13 Access Control The Access Control clause is the second largest clause, containing 25 controls and 7 control objectives. This clause contains critical
AU7087_C013.fm Page 173 Friday, April 28, 2006 9:45 AM 13 Access Control The Access Control clause is the second largest clause, containing 25 controls and 7 control objectives. This clause contains critical
PRISM Compliance Management Vendor Rollout Series PRISM Vendor User Training
 PRISM Compliance Management Vendor Rollout Series PRISM Vendor User Training Agenda 1. Introduction 2. PRISM Overview 3. Accessing PRISMCompliance.com 4. PRISM Compliance Management Prime & Sub Responsibilities
PRISM Compliance Management Vendor Rollout Series PRISM Vendor User Training Agenda 1. Introduction 2. PRISM Overview 3. Accessing PRISMCompliance.com 4. PRISM Compliance Management Prime & Sub Responsibilities
Overview. Timeline Cloud Features and Technology
 Overview Timeline Cloud is a backup software that creates continuous real time backups of your system and data to provide your company with a scalable, reliable and secure backup solution. Storage servers
Overview Timeline Cloud is a backup software that creates continuous real time backups of your system and data to provide your company with a scalable, reliable and secure backup solution. Storage servers
GxP Process Management Software. White Paper: Ten Most Common Reasons for FDA 483 Observations and Warning Letter Citations
 GxP Process Management Software : Ten Most Common Reasons for FDA 483 Observations and Warning Letter Citations Most FDA violations involve one of the following: Not having procedures in a regulated area
GxP Process Management Software : Ten Most Common Reasons for FDA 483 Observations and Warning Letter Citations Most FDA violations involve one of the following: Not having procedures in a regulated area
An Oracle White Paper December 2010. Leveraging Oracle Enterprise Single Sign-On Suite Plus to Achieve HIPAA Compliance
 An Oracle White Paper December 2010 Leveraging Oracle Enterprise Single Sign-On Suite Plus to Achieve HIPAA Compliance Executive Overview... 1 Health Information Portability and Accountability Act Security
An Oracle White Paper December 2010 Leveraging Oracle Enterprise Single Sign-On Suite Plus to Achieve HIPAA Compliance Executive Overview... 1 Health Information Portability and Accountability Act Security
How to save money with Document Control software
 How to save money with Document Control software A guide for getting the most out of your investment in a document control software package and some tips on what to look out for By Christopher Stainow
How to save money with Document Control software A guide for getting the most out of your investment in a document control software package and some tips on what to look out for By Christopher Stainow
IT Service Desk Manual Ver. 2.0. Document Prepared By: IT Department. Page 1 of 12
 Document Prepared By: Page 1 of 12 INDEX 1. Introduction. 3 2. Home Page..... 4 2.1 My Request Summary..... 4 2.2 Announcement....... 5 2.3 Submit your Request...... 5 2.4 Report a Problem...... 6 2.5
Document Prepared By: Page 1 of 12 INDEX 1. Introduction. 3 2. Home Page..... 4 2.1 My Request Summary..... 4 2.2 Announcement....... 5 2.3 Submit your Request...... 5 2.4 Report a Problem...... 6 2.5
Spillemyndigheden s Certification Programme Information Security Management System
 SCP.03.00.EN.1.0 Table of contents Table of contents... 2 1 Objectives of the... 3 1.1 Scope of this document... 3 1.2 Version... 3 2 Certification... 3 2.1 Certification frequency... 3 2.1.1 Initial certification...
SCP.03.00.EN.1.0 Table of contents Table of contents... 2 1 Objectives of the... 3 1.1 Scope of this document... 3 1.2 Version... 3 2 Certification... 3 2.1 Certification frequency... 3 2.1.1 Initial certification...
Procedure Title: TennDent HIPAA Security Awareness and Training
 Procedure Title: TennDent HIPAA Security Awareness and Training Number: TD-QMP-P-7011 Subject: Security Awareness and Training Primary Department: TennDent Effective Date of Procedure: 9/23/2011 Secondary
Procedure Title: TennDent HIPAA Security Awareness and Training Number: TD-QMP-P-7011 Subject: Security Awareness and Training Primary Department: TennDent Effective Date of Procedure: 9/23/2011 Secondary
ImageMaster. ECM Solutions.
 Contact: T-Systems Enterprise Services GmbH Fasanenweg 5 70771 Leinfelden-Echterdingen Germany Phone: +49 711 972 47779 e-mail: [email protected] www.t-systems.de/imagemaster ImageMaster. ECM Solutions.
Contact: T-Systems Enterprise Services GmbH Fasanenweg 5 70771 Leinfelden-Echterdingen Germany Phone: +49 711 972 47779 e-mail: [email protected] www.t-systems.de/imagemaster ImageMaster. ECM Solutions.
Version: Modified By: Date: Approved By: Date: 1.0 Michael Hawkins October 29, 2013 Dan Bowden November 2013
 Version: Modified By: Date: Approved By: Date: 1.0 Michael Hawkins October 29, 2013 Dan Bowden November 2013 Rule 4-004L Payment Card Industry (PCI) Physical Security (proposed) 01.1 Purpose The purpose
Version: Modified By: Date: Approved By: Date: 1.0 Michael Hawkins October 29, 2013 Dan Bowden November 2013 Rule 4-004L Payment Card Industry (PCI) Physical Security (proposed) 01.1 Purpose The purpose
Central Agency for Information Technology
 Central Agency for Information Technology Kuwait National IT Governance Framework Information Security Agenda 1 Manage security policy 2 Information security management system procedure Agenda 3 Manage
Central Agency for Information Technology Kuwait National IT Governance Framework Information Security Agenda 1 Manage security policy 2 Information security management system procedure Agenda 3 Manage
GE Intelligent Platforms. Meeting NERC Change Control Requirements for HMI/SCADA and Control Systems
 GE Intelligent Platforms Meeting NERC Change Control Requirements for HMI/SCADA and Control Systems Meeting NERC Change Control Requirements for HMI/SCADA and Control Systems Overview There is a lot of
GE Intelligent Platforms Meeting NERC Change Control Requirements for HMI/SCADA and Control Systems Meeting NERC Change Control Requirements for HMI/SCADA and Control Systems Overview There is a lot of
Quality Enhancement Unit Environmental Management System Module 6. Document Control
 Quality Enhancement Unit Environmental Management System Module 6 Document Control Module 6 Objectives What is EMS Documentation? What are Documents and Records? ISO 14001 Requirements for Documents NCDOT
Quality Enhancement Unit Environmental Management System Module 6 Document Control Module 6 Objectives What is EMS Documentation? What are Documents and Records? ISO 14001 Requirements for Documents NCDOT
Unleash the Full Value of Identity Data with an Identity-Aware Business Service Management Approach
 Unleash the Full Value of Identity Data with an Identity-Aware Business Service Approach best practices WHITE PAPER Table of Contents Executive Summary...1 The Evolution of Identity...2 > From User Account...2
Unleash the Full Value of Identity Data with an Identity-Aware Business Service Approach best practices WHITE PAPER Table of Contents Executive Summary...1 The Evolution of Identity...2 > From User Account...2
GENERAL PLATFORM CRITERIA. General Platform Criterion Assessment Question
 GENERAL PLATFORM CRITERIA SACM-V3-G-001 Comment: Does the tool use ITIL V3 process terms and align to ITIL V3 workflows and process integrations? SACM-V3-G-002 (OGC ISS 5.1.10) Access Controls Does the
GENERAL PLATFORM CRITERIA SACM-V3-G-001 Comment: Does the tool use ITIL V3 process terms and align to ITIL V3 workflows and process integrations? SACM-V3-G-002 (OGC ISS 5.1.10) Access Controls Does the
itrust Medical Records System: Requirements for Technical Safeguards
 itrust Medical Records System: Requirements for Technical Safeguards Physicians and healthcare practitioners use Electronic Health Records (EHR) systems to obtain, manage, and share patient information.
itrust Medical Records System: Requirements for Technical Safeguards Physicians and healthcare practitioners use Electronic Health Records (EHR) systems to obtain, manage, and share patient information.
IT Security Standard: Computing Devices
 IT Security Standard: Computing Devices Revision History: Date By Action Pages 09/30/10 ITS Release of New Document Initial Draft Review Frequency: Annually Responsible Office: ITS Responsible Officer:
IT Security Standard: Computing Devices Revision History: Date By Action Pages 09/30/10 ITS Release of New Document Initial Draft Review Frequency: Annually Responsible Office: ITS Responsible Officer:
Gatekeeper PKI Framework. February 2009. Registration Authority Operations Manual Review Criteria
 Gatekeeper PKI Framework ISBN 1 921182 24 5 Department of Finance and Deregulation Australian Government Information Management Office Commonwealth of Australia 2009 This work is copyright. Apart from
Gatekeeper PKI Framework ISBN 1 921182 24 5 Department of Finance and Deregulation Australian Government Information Management Office Commonwealth of Australia 2009 This work is copyright. Apart from
Table of Contents INTRODUCTION... 2 HOME PAGE... 3. Announcements... 7 Personalize & Change Password... 8 Reminders... 9 SERVICE CATALOG...
 Table of Contents INTRODUCTION... 2 HOME PAGE... 3 Announcements... 7 Personalize & Change Password... 8 Reminders... 9 SERVICE CATALOG... 11 Raising a Service Request... 12 Edit the Service Request...
Table of Contents INTRODUCTION... 2 HOME PAGE... 3 Announcements... 7 Personalize & Change Password... 8 Reminders... 9 SERVICE CATALOG... 11 Raising a Service Request... 12 Edit the Service Request...
QuickBooks 2010 Installation Guide
 QuickBooks 2010 Installation Guide This article provides instructions for installing QuickBooks 2010 on a single computer and in a network environment. QuickBooks Elements Several elements are involved
QuickBooks 2010 Installation Guide This article provides instructions for installing QuickBooks 2010 on a single computer and in a network environment. QuickBooks Elements Several elements are involved
The Peer Reviewer s Guide to Editorial Manager
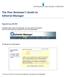 The Peer Reviewer s Guide to Editorial Manager Registering with EM The Register option is found in the main toolbar. New users simply click on REGISTER. [Note: You may have been proxy registered as a review
The Peer Reviewer s Guide to Editorial Manager Registering with EM The Register option is found in the main toolbar. New users simply click on REGISTER. [Note: You may have been proxy registered as a review
The Document Review Process: Automation of your document review and approval. A White Paper. BP Logix, Inc.
 The Document Review Process: Automation of your document review and approval A White Paper BP Logix, Inc. The Document Review Process A document encompasses many forms technical documentation, product
The Document Review Process: Automation of your document review and approval A White Paper BP Logix, Inc. The Document Review Process A document encompasses many forms technical documentation, product
Windows Operating Systems. Basic Security
 Windows Operating Systems Basic Security Objectives Explain Windows Operating System (OS) common configurations Recognize OS related threats Apply major steps in securing the OS Windows Operating System
Windows Operating Systems Basic Security Objectives Explain Windows Operating System (OS) common configurations Recognize OS related threats Apply major steps in securing the OS Windows Operating System
Supplier IT Security Guide
 Revision Date: 28 November 2012 TABLE OF CONTENT 1. INTRODUCTION... 3 2. PURPOSE... 3 3. GENERAL ACCESS REQUIREMENTS... 3 4. SECURITY RULES FOR SUPPLIER WORKPLACES AT AN INFINEON LOCATION... 3 5. DATA
Revision Date: 28 November 2012 TABLE OF CONTENT 1. INTRODUCTION... 3 2. PURPOSE... 3 3. GENERAL ACCESS REQUIREMENTS... 3 4. SECURITY RULES FOR SUPPLIER WORKPLACES AT AN INFINEON LOCATION... 3 5. DATA
Rensselaer County. Contract Management System
 Rensselaer County Contract Management System VENDOR REFERENCE MANUAL Version 2.0 Table of Contents Getting Started and Logging In...4 The Contract Dashboard Tab...6 Vendor Profile Tab...9 Contract Overview
Rensselaer County Contract Management System VENDOR REFERENCE MANUAL Version 2.0 Table of Contents Getting Started and Logging In...4 The Contract Dashboard Tab...6 Vendor Profile Tab...9 Contract Overview
File Document Management System
 Static or in-motion assets tracking or locating, like a file registry facility or record management facility is always not an easy task. User can instantly determine the general location of tagged assets
Static or in-motion assets tracking or locating, like a file registry facility or record management facility is always not an easy task. User can instantly determine the general location of tagged assets
General Platform Criterion Assessment Question
 Purpose: [E]nsure that the assets required to deliver services are properly controlled, and that accurate and reliable information about those assets is available when and where it is needed. (ST 4.3.1)
Purpose: [E]nsure that the assets required to deliver services are properly controlled, and that accurate and reliable information about those assets is available when and where it is needed. (ST 4.3.1)
Software Requirement Specification for Web Based Integrated Development Environment. DEVCLOUD Web Based Integrated Development Environment.
 Software Requirement Specification for Web Based Integrated Development Environment DEVCLOUD Web Based Integrated Development Environment TinTin Alican Güçlükol Anıl Paçacı Meriç Taze Serbay Arslanhan
Software Requirement Specification for Web Based Integrated Development Environment DEVCLOUD Web Based Integrated Development Environment TinTin Alican Güçlükol Anıl Paçacı Meriç Taze Serbay Arslanhan
Cryptshare for Outlook User Guide
 Cryptshare for Outlook User Guide V1.6.2 Befine Solutions AG Werthmannstr. 15 79098 Freiburg i. Br. Germany Web: https://www.cryptshare.com E-Mail: [email protected] Tel.: +49 761 389 13 0 Fax: +49 761
Cryptshare for Outlook User Guide V1.6.2 Befine Solutions AG Werthmannstr. 15 79098 Freiburg i. Br. Germany Web: https://www.cryptshare.com E-Mail: [email protected] Tel.: +49 761 389 13 0 Fax: +49 761
SUBJECT: SECURITY OF ELECTRONIC MEDICAL RECORDS COMPLIANCE WITH THE HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT OF 1996 (HIPAA)
 UNIVERSITY OF PITTSBURGH POLICY SUBJECT: SECURITY OF ELECTRONIC MEDICAL RECORDS COMPLIANCE WITH THE HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT OF 1996 (HIPAA) DATE: March 18, 2005 I. SCOPE This
UNIVERSITY OF PITTSBURGH POLICY SUBJECT: SECURITY OF ELECTRONIC MEDICAL RECORDS COMPLIANCE WITH THE HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT OF 1996 (HIPAA) DATE: March 18, 2005 I. SCOPE This
ITA Dynamics Waste & Recycling Document Management System enwis) DOCMA
 ITA Dynamics Waste & Recycling Document Management System enwis) DOCMA From a technological point of view, ITA Dynamics enwis) Docma is the optimum product for Microsoft SharePoint and enlarges SharePoint
ITA Dynamics Waste & Recycling Document Management System enwis) DOCMA From a technological point of view, ITA Dynamics enwis) Docma is the optimum product for Microsoft SharePoint and enlarges SharePoint
DeltaV Capabilities for Electronic Records Management
 January 2013 Page 1 DeltaV Capabilities for Electronic Records Management This paper describes DeltaV s integrated solution for meeting FDA 21CFR Part 11 requirements in process automation applications
January 2013 Page 1 DeltaV Capabilities for Electronic Records Management This paper describes DeltaV s integrated solution for meeting FDA 21CFR Part 11 requirements in process automation applications
User Manual for Web. Help Desk Authority 9.0
 User Manual for Web Help Desk Authority 9.0 2011ScriptLogic Corporation ALL RIGHTS RESERVED. ScriptLogic, the ScriptLogic logo and Point,Click,Done! are trademarks and registered trademarks of ScriptLogic
User Manual for Web Help Desk Authority 9.0 2011ScriptLogic Corporation ALL RIGHTS RESERVED. ScriptLogic, the ScriptLogic logo and Point,Click,Done! are trademarks and registered trademarks of ScriptLogic
The Benefits of an Industry Standard Platform for Enterprise Sign-On
 white paper The Benefits of an Industry Standard Platform for Enterprise Sign-On The need for scalable solutions to the growing concerns about enterprise security and regulatory compliance can be addressed
white paper The Benefits of an Industry Standard Platform for Enterprise Sign-On The need for scalable solutions to the growing concerns about enterprise security and regulatory compliance can be addressed
Table of Contents. OpenDrive Drive 2. Installation 4 Standard Installation Unattended Installation
 User Guide for OpenDrive Application v1.6.0.4 for MS Windows Platform 20150430 April 2015 Table of Contents Installation 4 Standard Installation Unattended Installation Installation (cont.) 5 Unattended
User Guide for OpenDrive Application v1.6.0.4 for MS Windows Platform 20150430 April 2015 Table of Contents Installation 4 Standard Installation Unattended Installation Installation (cont.) 5 Unattended
HIPAA Security COMPLIANCE Checklist For Employers
 Compliance HIPAA Security COMPLIANCE Checklist For Employers All of the following steps must be completed by April 20, 2006 (April 14, 2005 for Large Health Plans) Broadly speaking, there are three major
Compliance HIPAA Security COMPLIANCE Checklist For Employers All of the following steps must be completed by April 20, 2006 (April 14, 2005 for Large Health Plans) Broadly speaking, there are three major
DSI File Server Client Documentation
 Updated 11/23/2009 Page 1 of 10 Table Of Contents 1.0 OVERVIEW... 3 1.0.1 CONNECTING USING AN FTP CLIENT... 3 1.0.2 CONNECTING USING THE WEB INTERFACE... 3 1.0.3 GETTING AN ACCOUNT... 3 2.0 TRANSFERRING
Updated 11/23/2009 Page 1 of 10 Table Of Contents 1.0 OVERVIEW... 3 1.0.1 CONNECTING USING AN FTP CLIENT... 3 1.0.2 CONNECTING USING THE WEB INTERFACE... 3 1.0.3 GETTING AN ACCOUNT... 3 2.0 TRANSFERRING
Provide access control with innovative solutions from IBM.
 Security solutions To support your IT objectives Provide access control with innovative solutions from IBM. Highlights Help protect assets and information from unauthorized access and improve business
Security solutions To support your IT objectives Provide access control with innovative solutions from IBM. Highlights Help protect assets and information from unauthorized access and improve business
BYOD Policy for [AGENCY]
![BYOD Policy for [AGENCY] BYOD Policy for [AGENCY]](/thumbs/24/2163525.jpg) BYOD Policy for [AGENCY] This document provides policies, standards, and rules of behavior for the use of smartphones, tablets and/or other devices ( Device ) owned by [AGENCY] employees personally (herein
BYOD Policy for [AGENCY] This document provides policies, standards, and rules of behavior for the use of smartphones, tablets and/or other devices ( Device ) owned by [AGENCY] employees personally (herein
Interagency Science Working Group. National Archives and Records Administration
 Interagency Science Working Group 1 National Archives and Records Administration Establishing Trustworthy Digital Repositories: A Discussion Guide Based on the ISO Open Archival Information System (OAIS)
Interagency Science Working Group 1 National Archives and Records Administration Establishing Trustworthy Digital Repositories: A Discussion Guide Based on the ISO Open Archival Information System (OAIS)
Applying ITIL v3 Best Practices
 white paper Applying ITIL v3 Best Practices to improve IT processes Rocket bluezone.rocketsoftware.com Applying ITIL v. 3 Best Practices to Improve IT Processes A White Paper by Rocket Software Version
white paper Applying ITIL v3 Best Practices to improve IT processes Rocket bluezone.rocketsoftware.com Applying ITIL v. 3 Best Practices to Improve IT Processes A White Paper by Rocket Software Version
Introduction. PCI DSS Overview
 Introduction Manage Engine Desktop Central is part of ManageEngine family that represents entire IT infrastructure with products such as Network monitoring, Helpdesk management, Application management,
Introduction Manage Engine Desktop Central is part of ManageEngine family that represents entire IT infrastructure with products such as Network monitoring, Helpdesk management, Application management,
YubiKey Authentication Module Design Guideline
 YubiKey Authentication Module Design Guideline Yubico Application Note Version 1.0 May 7, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company
YubiKey Authentication Module Design Guideline Yubico Application Note Version 1.0 May 7, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company
DeltaV Capabilities for Electronic Records Management
 September 2004 Page 1 An integrated solution for meeting FDA 21CFR Part 11 requirements in process automation applications using a configurable off-the-shelf (COTS) solution Emerson Process Management.
September 2004 Page 1 An integrated solution for meeting FDA 21CFR Part 11 requirements in process automation applications using a configurable off-the-shelf (COTS) solution Emerson Process Management.
Security Features: Lettings & Property Management Software
 Security Features: Lettings & Property Management Software V 2.0 (23/02/2015) Table of Contents Introduction to Web Application Security... 2 Potential Security Vulnerabilities for Web Applications...
Security Features: Lettings & Property Management Software V 2.0 (23/02/2015) Table of Contents Introduction to Web Application Security... 2 Potential Security Vulnerabilities for Web Applications...
Protecting Business Information With A SharePoint Data Governance Model. TITUS White Paper
 Protecting Business Information With A SharePoint Data Governance Model TITUS White Paper Information in this document is subject to change without notice. Complying with all applicable copyright laws
Protecting Business Information With A SharePoint Data Governance Model TITUS White Paper Information in this document is subject to change without notice. Complying with all applicable copyright laws
Privacy Policy Version 1.0, 1 st of May 2016
 Privacy Policy Version 1.0, 1 st of May 2016 THIS PRIVACY POLICY APPLIES TO PERSONAL INFORMATION COLLECTED BY GOCIETY SOLUTIONS FROM USERS OF THE GOCIETY SOLUTIONS APPLICATIONS (GoLivePhone and GoLiveAssist)
Privacy Policy Version 1.0, 1 st of May 2016 THIS PRIVACY POLICY APPLIES TO PERSONAL INFORMATION COLLECTED BY GOCIETY SOLUTIONS FROM USERS OF THE GOCIETY SOLUTIONS APPLICATIONS (GoLivePhone and GoLiveAssist)
How To Use Egnyte
 INTRODUCING ON DEMAND FILE SERVER FROM BT WHOLESALE APPLICATION STORE WHAT IS ON DEMAND FILE SERVER? The three most common technology challenges facing every small business are data storage, information
INTRODUCING ON DEMAND FILE SERVER FROM BT WHOLESALE APPLICATION STORE WHAT IS ON DEMAND FILE SERVER? The three most common technology challenges facing every small business are data storage, information
