|
|
|
- Simon Tucker
- 8 years ago
- Views:
Transcription
1 AdvancedNetworkManagementFunctionalities throughtheuseofmobilesoftwareagents 1DipartimentodiMatematica,UniversitadiMessina C.daPapardo-SalitaSperone,98166Messina-Italy AntonioPuliato1,OrazioTomarchio2 2IstitutodiInformaticaeTelecomunicazioni,UniversitadiCatania VialeA.Doria6,95025Catania-Italy tributedoverthenetwork.consequently,managementstrategiesarebe- comingofcrucialimportanceinordertoguaranteeaneectivecontrolof thesystem,bothintermsofperformanceandreliability.mobileagents Abstract.Computingpowerandstoragespacearemoreandmoredis- plementationbasedonourmobileagentplatformcalledmap. howtotakeadvantageofthistechnologyanddescribeaprototypeim- representachallengingapproachtoprovideadvancednetworkmanagetralizedandactivemonitoringofthesystem.inthispaperwediscusmentfunctionalities,duetothepossibilitytoeasilyimplementadecen- 1Introduction Keywords:networkmanagement,mobileagents,SNMP,Java. haviourofsystemresourcesrepresentthemainfunctionalitiesanetworkman- agementsystemshouldprovide. agementdataarestoredindatabasesmaintainedontheelementstobemanaged. ofthesystem.accordingtothisapproach,themanagementofanetworktends ferredforprovidinghigh-levelinformation,whichareusefulforthemanagement Managementapplicationsrunonacentralstation,wheredataneedtobetrans- Intheapproachescurrentlyadoptedbythemainstandardplatforms,man- Thegrowingcomplexityofcomputernetworksrequirestheuseofsophisticated managementtechniques.monitoring,properlydetectingandcontrollingthebe- torequireaconsiderableamountofbandwidth,particularlywhensometroubles code,inordertoextendsucharchitecturesbymovingaportionofthe"intelligence"tothenodeswheredataareresident.inthisscenario,management agentsareplacedineachnode:theymonitorthestateofthenode,andcan performsimplemanagementfunctionsonthelocalnode.ifagentsndirreg- Inthiswork,ourpurposeisexploitingnewtechnologiesbasedonmobile inthenetworkarise,andanimmediatemanager'sactionisrequired. ularoperationconditions,acommunicationmechanismistriggeredamongthe
2 dierentagents,whichactivatetheappropriaterecoverystrategies.forexample,suchstrategiesconsistofsystemrecongurations,ofnewroutingstrategies, transferlargeamountsofdatafromtheremotenodestoacentralstation.only etc.manyofthemanagementdecisionsmaybetakenlocally,thusavoidingto high-levelinformationwillbetransferredtothecentralstationwherethenetworkmanageroperates.besides,intheproposedinfrastructure,agentsarenot staticallyresidentintheremotedevices.theycanmovefromanodetoanother, canbereplacedifnecessary,canbeequippedwithfunctionalitiesthathadnot beenenvisagedatthetimeofinstallation.allofthemanagementproceduresdo notneedtobemaintainedineachagent;someoftheseprocedureswouldmigratefromacentralnodetotheonewheretheywillbeexecuted,butonlywhen theybecomereallynecessary.suchfunctionalitiesmakethesystemobtained veryexible.besides,themanagementapplicationitselfhasbeenorganizedas amobileagent;inthiswaythemanagerofthenetworknolongerneedsaxed thedevelopmentandthemanagementofmobileagents,whichwascompletely position. implementedbyusingmap3(mobileagentsplatform).itisaplatformfor developedbyusingjavaattheuniversityofcatania[8].thisplatformgivesthe userallthebasictoolsneededforthecreationofagentbasedapplications.it Aprototypeofthenetworkmanagementsystemdescribedbeforehasbeen enablesustocreate,run,suspend,resume,deactivate,reactivatelocalagents,to stoptheirexecution,tomakethemcommunicatewitheachotherandmigrate. enabledustodevelopaplatformabletooperateinheterogeneousenvironments. TheuseofJava(thankstoitsindependencefromhwandswarchitectures) themainstrengthsofanapproachbasedonmobilecode.insection4,aftera mentwhichhavebeencreatedforovercomingsuchproblems:wealsooutline mainlimits.insection3wediscussthemainmodelsofdistributedmanage- basicconceptsoftraditionalnetworkmanagementsystems,andweoutlinetheir Therestofthispaperisorganizedasfollows:inSection2wepresentthe shortdescriptionoftheplatformmap,theagents(expresslycreated)andtheir functionalitiesaredescribed.finally,insection5wepresentourconclusionsand 2Traditionalsystemsofnetworkmanagement thefuturehintsfortheresearch. Currentnetworkmanagementsystemsadoptacentralizedparadigmaccording towhichthemanagementapplicationperiodicallyaccessesthedatacollectedby asetofsoftwaremodulesplacedonthenetworkdevices,byusinganappropriate whilethecommonmanagementinformationprotocol(cmip)[11]proposedby protocol. theisohasbeenusedonlyintheareaofnetworksfortelecommunications. theietfhasbecomethestandardprotocolofmanagementforipnetworks, TheSimpleNetworkManagementProtocol(SNMP)[3,10,11]proposedby 3MAPisavailableathttp://sun195.iit.unict.it/MAP
3 operate.thebasiccomponentsofsuchsystemsofnetworkmanagementarethe followingones: {oneormoremanagementstations(networkmanagementstationornms) Botharchitectureshaveasimilarapproach,andonlydierforthewaythey {somenodes(potentiallymanyofthem).amodulecalledagent4runsoneach {amanagementprotocol,whichisusedfortransferringthemanagementinformationamongthesnmp-agentsandthemanagementstations. node;itmonitorsandcollectsthedataofthenode. workadministratorsnormallyoperate),formonitoringandcontrollingthenet- workelements.theyaredevicessuchashosts,routers,bridges,terminalservers, SomemanagementapplicationsareexecutedintheNMS(onwhichthenet- etc.,whichcanbemonitoredand/orcontrolledbyaccessingtheirmanagement information.themanagementinformationareconsideredasacollectionofmanagedobjects,storedinso-calledmanagementinformationbase(mib)[7].some setsofrelatedobjectsaredenedinthemibmodules.suchmodulesarespecied byusingasubsetofthestandardnotationosiabstractsyntaxnotationone ofthisinfrastructureareentitiesprovidingsuchinformationwithastandardizedinterface.thenmsinteractswiththesesnmp-agents,actingasaclient (ASN.1),calledStructureofManagementInformation(SMI).Thesnmp-agents that(accordingtotheindicationsofthenetworkmanager)askstheagentsfor informationaboutthedierentnetworkdevices. Snmp-agentshaveaverysimplestructure,andusuallycommunicateonlyin responsetotherequestsofvariablescontainedinthemib.theycannotperformmanagementactionsontheirlocaldata.thenetworkmanagementprotocolprovidestheprimitivesforexchangingmanagementinformationsamongthe AlltheapplicationsconcerningthemanagementareexecutedontheNMS. forcontinuingtoexaminethesubsequentvariableinthemib. isverysimple,andprovidesthreebasictypesofoperations:theoperatorsset snmp-agentsandthemanagementstations.theaccesstomibvariablesbythe NMStakesplaceatalowlevel.Forexample,thesetofprimitivesoftheSNMP 2.1LimitationsofthecentralizedparadigmoftheSNMP andgetforsettingorreadingthevalueofavariable,andtheoperatorgetnext workmanagementapplications,butthequickexpansionofnetworkshasposed ThecentralizedparadigmadoptedbytheSNMPisappropriateinseveralnet- theproblemofitsscalability,aswellasforanyothercentralizedmodel.atthe sametime,thecomputationalpowerofthenetworknodestobemanagedhas increased,andhasmadepossiblesignicantfunctionsofmanagementonthe nodesinadistributedmode. 4Theseagentsarenotrelatedwithmobileagentswhichwewilldiscusslaterinthis paper;toavoidconfusionwewillrefertothiskindofagentswiththetermsnmp-
4 needfordistributedcontrol,donotrequireafrequentpollingofmibvariables, andneedonlyalimitedamountofinformation.thetypicalexampleofthisis themonitoringandtherelateddisplayingofsomemibvariables.forexample, thestateoftheinterfaceofarouter,orthestateofalinkinvolveonlythequery Centralizationisgenerallyappropriatefortheapplicationswithalimited foracentralizedmanagement. andthedisplayingofalimitednumberofmibvariables,andisthereforesuitable thevariationsonahighnumberofmibvariables.inthesecases,themonitoring amountofinformation.anexamplecouldbethecomputationofafunctionthat severalmibvariables,whichneedtoperformsomecomputationsonalarge indicatesthefunctionalitylevelofthenetwork,whichmustfrequentlydetect Ontheotherendwehavesomeapplicationsrequiringafrequentpollingof inthetracquiteclosetothecongestedpartofnetwork. centralizedapproacharemoreevidentintheperiodsofnetworkcongestion, managementoperationsrequiredforovercomingthecongestioncauseanincrease whenthemanager'sactionisveryimportant.infact,duringthoseperiods,the andthecontrolshouldbeveryclosetothedevice.thesedrawbacksofthe 3Distributedmanagement Thedisadvantagesofatotallycentralizedarchitectureastheonedescribedbeforehavebeenadmittedbythesameorganizationsthathadintroducedit.A formofdecentralization(providedintherstversionofsnmp)isthemechanismofnoticationofasynchronousevents.infact,snmp-agentscansendtraps assimpleaspossible,theeventsthatanagentcancommunicatetothenms (thatis,messagestothenms)notasresultofarequest,butwhensomespecic usingtrapsareverysimple:typicalexamplesincludethechangeinthestateof eventsoccur.sincethebasicpurposeintheietfwasthatofmaintainingagents acomponent(forexample,fromactivetoinactive,andviceversa).inanycase, thetaskofsnmp-agentisonlythenoticationoftheevent:nomanagement actioncanbeperformedlocally,becauseanydecisionismadecentrallybythe NMS. aswidelyastherstversion,duetothefewimplementationsavailable,andto wheninteractingwithsuchdevices.however,thesnmpv2hasnotbeenused ofproxyagent,whichleadstoastructureofhierarchicalmanagement.aproxy agentisresponsibleforasetofdevices,andthenmssendstherequeststoit, TheSNMPv2[11]introducesanotherdecentralizationfeature:theconcept theexistenceofappropriatedevicescalledprobes,whosetaskistoprovideindicationsconcerningthenetworktracinaspecicsub-network,andconcerningthe theintroductionofthermon(remotemonitoring)[12].thermonassumes stateofsomedevices.thermonprovidesanapproachorientedtotheanalysis AnotherapproachtodecentralizationhasbeenproposedbytheIETFwith thecriticismmadeaboutthesecuritymodelintroduced. oftrac,ratherthantothedevice,asinthecaseoftheordinarysnmp-agents. Anyway,thebenetsoftheRMONconcernthesemanticcompressionofdata,
5 tothenms. 3.1Approachesbasedonmobilecode preprocessingallthecollectedinformation,andsendingonlythesignicantones toovercomesomelimitationsofcurrentcentralizedmanagementsystems.in Theuseofapproachesbasedonmobilecodefornetworkmanagementallows general,suchapproachesarebasedontheideaofreversingthelogicaccording micromanagementoperations,andreducingtheworkloadforthemanagement towhichthedataproducedbynetworkdevicesareperiodicallytransferredto stationandtheoverheadinthenetwork[2]. applicationscanbemovedtothenetworkdevices,thusperforming(locally)some thecentralmanagementstation.thankstosuchtechnologies,themanagement showsanarchitecturewherethemanagementstation,sendssomecommands delegatingtheremoteagenttotheactualexecution.ofcourse,remotedevices totheremotedevice(insteadoflimitingtotherequestformibvariables), code.infact,theideaofmanagementbydelegation,whichispresentin[6,5], Thisideawasexpressedbeforedevelopingtherstsystemsbasedonmobile includeaso-calledelasticprocessruntimesupport,whichcanprovidefornew servicesanddynamicallyextendtheonespresentinthedevice. thatcantakeadvantagefromtheadoptionofaspecicschemebasedonthe aremoreexible. delegationasaparticularcase,sincetheireldofapplicationiswider,andthey Inthefollowingparagraphswewillexaminethemanagementfunctionalities Theapproachesbasedonamobilecodemayincludethemanagementby considerablyimprovestheexibilityprovidedbyanetworkmanagementsystem. mobilityofthecode. UseofCodeonDemandTheuseofaparadigmbasedonCodeonDemand Infact,thestructureoftheMIBintheSNMPapproach(aswellasthetypeof followedwhiledevelopingthesnmp,duetothelimitedcomputationcapabilities managementagentsassimpleaspossiblewasoneoftheprojectrestrictions andcannotbemodied.thesnmp-agentcaninnowaymanageeventsdened bytheuser,noritcanactlocallywithoutinvolvingthenms.maintaining eventsthatcanbenotiedtothecentralstation)iscodiedinthesnmp-agent, inanagent.infact,afunction(duetothespecicnatureofsuchapplications) think(thisisnoteective)ofstaticallycodifyingallthemanagementfunctions morepowerfulprocessors,andhigheramountsofmemory.however,wecannot ofnetworkdevices.thiswastrueuntilsomeyearsago.now,suchdeviceshave mightberequestedonlyonsomedevices.onotherdevicesitcouldbeseldom devicesitcouldnotbenecessary.itisthereforeclearthatthestaticinclusionof requested;onotheronesitmightberequestedmorefrequently,whileinother suchfunctionsinanagentwouldleadtoaconsiderablewasteofresources. ofthesystem,andmaintainsagentssimpleandsmallatthesametime.only TheuseofanapproachbasedonCodeonDemandincreasestheexibility
6 serveranddynamicallyexecuted[9,8].inthesameway,eachsoftwareupdate whenafunctionbecomesnecessaryonanode,itcanbedownloadedfromacode withtheissueofthebandwidthwastethatoccursinacentralizedsystemwhen UseofRemoteEvaluationTheuseofRemoteEvaluationallowstodeal requestedbytheagentcanbeobtainedthroughthisapproach. thedataofthedevice,theyhavetobemovedfromtheagenttothenms,where micromanagementoperationsareneeded. wheretheywillbeexecutedwithoutgeneratingtracinthenetwork(except theyareprocessed.conversely,thankstothemechanismofremoteevaluation, theactionstobeperformedcanbedevelopedandsenttotheremotedevice, Inatraditionalsystem,nomatterwhichprocessinghastobeperformedon theinitialoneforsendingthecodetobeexecuted). ofthisfunctionisperformedbytransferringthevariablesinvolvedtothenms elementarymanagementvariables.eachvariableprovidesaparticularmeasure 4].Ingeneral,byhealthfunctionwemeananexpressionconsistingofseveral concerningthedevicetobecontrolled.intraditionalsystemsthecomputation Atypicalexampleisthecomputationoftheso-calledhealthfunctions[5,8, bandwidthoccupiedonthenetwork(andthecomputationalloadproducedon thenms)willbe.evenifthisfunctioncanbecodiedwithintheagent,this frequencyatwhichsuchfunctionhastobecomputed),thelargertheamountof onsite.inthisway,thehigherthenumberofthevariablesinvolved(orthe (throughpollingoperationsatregulartimeintervals),anddoingthecomputation isnotconvenientforthefollowingreasons:theincreaseinthesizeoftheagent beseldomused. andtheineciencyofthesystemduetothefactthatagenericfunctionmight formssuchcomputationswillbesentbythenmsanddynamicallyexecuted. Thisapproachallowstoobtainwhatiscalled"semanticcompressionofdata". functionsdirectlyonthedevices,andonlywhennecessary.thecodethatper- Infact,generallythemanagerofanetworkisnotinterestedinthesinglevalueof ByusingatechnologybasedonRemoteEvaluation,wecancomputethese amibvariable,butinaggregatevaluescontaininghigher-level"informations". Wecanthereforedevelopasysteminwhichthemanagerwritesitsmanagement functions(ortheymightbealreadyavailable),andtheninvokestheirremote morebenetstotheonesthatcanbeobtainedwithremoteevaluation.infact, UseofmobileagentsTheuseofapproachesbasedonmobileagentsadds executiononspecicdevices,whennecessary. inthiscasetheactiononadeviceisalwaysexpresslystartedbythenms. themovementsallowstodevelopapplicationsinwhichtheagentmovesfroma Conversely,inthecaseofmobileagents,theabilitytostorethestateduring devicetoanother,performingthemanagementfunctionsrequired.besides,the agentcanbedelegatedthetaskofdecidingwhereandwhentomigrateaccording toitscurrentstate,thusreducingtheinteractionwiththenms,andmaking processingsmoredistributed.
7 inwhichthenmshastomanagedierentlansandislinkedtothemby unreliableand/orlowbandwidthlinks.inthesecases,atraditionalapproach, whichrequirestheexchangeofseveralmessagesamongthenmsandremote devicesforasingleoperation,wouldmeandelaysintheexecutionofmanagement ThereducedinteractionwiththeNMSisanadvantageifwerefertosituations agivenoperation(whichhasbeendevelopedaccordingtothisnewmodelasa operations,aswellastheirunreliability.conversely,ifweusemobileagents,once mobilecomponent)issenttotheremotelan,itcanberunthere.evenifthe agent'ssizeincreases,therewillbenonegativeeect,sinceinalanwecan alwaysassumetohavelargebandwidthsavailable. implemented.mapisaplatformforthedevelopmentandthemanagementof InthissectionweintroducetheagentsystemMAP[8]thatwedevelopedand mobileagentsthatgivesalltheprimitivesneededfortheircreation,execution, 4NetworkmanagementusingMAP communication,migration,etc. onthedierenthardwareandsoftwarearchitectures.javaisalsousedasa languageforprogrammingagents:theprogrammerwillnotthereforeneedto bytheplatform. learnseveraland/orspeciclanguages,butonlytheapithataremadeavailable IthasbeenentirelydevelopedinJava,andthisguaranteesitstotalportability areabletocarrythedatastatewiththem,butnottheexecutionstate.besides, theexploitationofthejavamechanismsofclassesdynamicloading.agraphic interfacemanagestheagentsinexecution:thisinterfaceallowstoverifywhich itintegratestheparadigmsofremoteexecutionandcodeondemand,thanksto ThemigrationfacilityimplementedinMAPisaweakmigration:theagents Besides,throughthisinterfacewecantriggertheexecutionofanyagentpresent inthesystem,independentlyofwheretheagentcodeisresident. agentsareactiveinthelocalserver,andwhichonesarepresentinremoteservers. operationsofanetwork.thepurposeoftheimplementedagentsistoprovethe havedevelopedanagent-basedapplicationforperformingthebasicmanagement oftheissuesdescribedbefore.inparticular,usingthedevelopedagentsweare eectivenessofanapproachbasedonthemobilityofthecodeforsolvingsome Inthissectionweshowhow,byusingtheservicesoftheMAPplatform,we goingtodealwiththefollowingissues: {collectionofinformationaboutthestateofthenetwork andrun,hasbeenstructuredasanagent(calledsnmp-monitoring).throughthe {micromanagementofnetworkdevicesthroughthemonitoringofhealthfunctionsdenedbytheuser. graphicalinterfaceofthisagent(showninfigure1)wecanselecttheagentsto Theapplicationthroughwhichtheactualmanagementagentsaretriggered evaluatetheinformationcollectedbytheagentsthathavenishedtheirtask. besenttothenetwork,controlthelistoftheactiveagentsinthenetwork,and
8 , Throughthisbox,thetypicalparametersforakindofagentcanbespecied. Accordingtothetypeofagentselected,anappropriatedialogboxisviewed. Fig.1.Graphicalinterfaceoftheapplicationsnmp-monitoring Therearesomeadvantagesinstructuringthe"snmp-monitoring"applicationas MAPserverispresent,thusreleasingthemanagerfromtheconsoleoftheNMS. anagent:themanagementapplicationcanbeactivatedfromanynodewherea integrationandcompatibilitywiththesnmpworld.forthisreason,inour systemwehaveintegratedandusedsomeclassescreatedbyadvent[1],which implementthesnmpstack.inthisway,wehavehadtheopportunitytointeract withthedierentnodesofthenetworkthroughstandardmibvariables.atthe Oneofourpurposesinthecreationoftheplatformhasbeenthecomplete sametimethedevelopedframeworkallowsustomonitornon-standardquantities 4.1Agentsforthemanagement (notdenedbyamib)denedbytheuser. Wehavedevelopedthefollowingbasictypesofmobileagentsforthemanagement: {browseragent {daemonagent {messengeragent
9 performevenverycomplexactionsofmanagement.however,ourpurposeisnot creatingacompletemanagementsystem,butshowinghowtheideaspresented {verieragent beforecanbeeasilyimplementedbyouragentssystem. Theyperformverysimpletasks,butthecombinationoftheiractionsallowsto carriedout. BrowseragentThebrowseragentcollectssomeMIBvariablesfromasetof Belowwedescribethedetailsandthefunctionalitiesofeachtypeofagent nodesspeciedbytheuser.boththevariablesofthemib-treetobecollected reachestherstnodetobevisited,opensasnmplocalcommunicationsession, (Figure2)oftheapplication"snmp-monitoring".Afterbeingstarted,theagent andtheserverstobevisitedareselectedthroughanappropriatedialogbox buildsapdu-requestcontainingthemibvariablestobesearched,waitsfor thereplyfromthesnmpdaemon,andsavesthedataobtainedinaninternal structure.then,ifothernodesneedtobevisited,itreachesthem,andrepeats ithasbeenlaunched,wheretheresultsoftheresearchareshown. theprocedurementionedabove.otherwise,itreturnstotheplatformfromwhich, inanordinarymibbrowser,afteractivatingaconnectionwithaspecicnode, ThisagentrealizesthefunctionalitiesofanextendedMIBbrowser.Infact, Fig.2.Graphicalinterfaceofthebrowseragent wecanviewthecontentsofthemibvariables,bysendingasnmprequesttothe nodeinquestionforeachvariable.conversely,throughthebrowseragent,such
10 DaemonagentThedaemonagentmonitorsa"healthfunction"denedbythe requestsarerstgiventotheagent,which(bymovingfromanodetoanother) interactswiththemlocallyandreportstheglobalresulttotheinitialstation. agentmovestothenodeinquestion,whereitrecordsthevalueofthefunction: user.forstartingtheagent,thefunctiontobecomputedandthenodeofthe network(wherethecomputationhastobedone)mustbeprovided.thenthis ifthevalueishigherthanaxedthreshold(denedbytheuser),anotication messageissenttotheserverfromwhichtheagenthasdeparted. canimplement(bymeansofthisagent)amechanismofgeneralizedtrap,where haveanythingpreinstalled. theeventsinwhichthenmsisnotiedcanbefreelyandveryexiblysetby theuser.remotenodes(thankstotheuseofthemobilecode)donotneedto Figure3showsthebasicfunctioningmechanismsofthedaemonagent.We (1) Migration and execution on the remote node of AgentDaemon 1100 (2) Warning message:, threshold value exceeded (1) (1) AgentDaemon: (1) Fig.3.Computingcustomizedhealthfunctionsbymeansofdaemonagents (1) Y1 (2) AgentDaemon: Y2 (2) Snmp-monitoring (1) application MessengeragentThetwoagentsdescribedbeforedirectlyinteractwiththe Snmpdaemonpresentinthedierentnodes(throughtheAdventclasses).Conversely,themessengeragent,duringitsmigrationthroughthenodesofthe (1) theserverswheretheyhavetobesearched,and(ifnecessary)alsothenumberof network,interactswithotheragentsforcollectingspecicinformationproduced timestheagenthastocontactsuchagents.thus,themessengeragentperforms bythem. Infact,sincedaemonagentscanperformthecomputationofanyfunctiononthe operationsatahigherabstractionlevelthanthemereretrievalofmibvariables. Duringthecongurationweneedtoselecttheagentstobecontactedand thusobtainingageneraldescriptionaboutthestateofthenetwork. dierentnodesofthenetwork,themessengerallowstocollectsuchinformation,
11 ure4.itmustbenoticedthatthemodeloftheagentsinvolvedinthisarchi- tectureisalwaysthesame.thefunctionstobecomputedoneachnode,which clearlydependonthespecicenvironmentwhereweoperate,needtobechanged forobtainingsignicantinformationaboutthenetwork(belowwewillshowthe TheschematicbehaviourofamessengeragentisgraphicallyshowninFig- simplestepstobefollowedforinsertingnewmonitoringfunctionsinthesystem). Agent Messenger: on each node interacts with the local agents, executing on that node Fig.4.Messengeragent:interactionwithothersystemagents AgentDaemon: health function Y1 AgentDaemon: health function Y2 Snmp-monitoring application agementaction.itstaskisthatofbringingimportantinformationtothebase, VerieragentTheverieragentdoesnotperformanactualnetworkman- whichmightbeusefulforfurtheroperationsofnetworkmanagement.itvisits poseistheevaluationofthepresenceofaspecicpropertyofthesystemvisited thenodesselectedduringtheconguration,andcomputesafunctionwhosepur- (forexample,wemightthinkofthevericationofasoftwareversion,orthe availablespaceondisknotbelowaxedthreshold,orthevericationofsome logles,etc.).theverieragentthenreportstheserver,fromwhichitdeparted, thelistofthenodesthatcorrespondtothisproperty. 4.2Addingnewfunctionstothesystem cancomputeonthedierentnodes.thesystemproposedallowstodevelopand Intheagentsdescribedbeforewehavereferredtoseveralfunctionsthatthey addnewfunctionsveryeasily.infact,byrespectingsomeverysimplerules,any functioncanbeinsertedinthesystem.fromthepointofviewoftheimplementation,anabstractclassfunctionispresent,whichisasortoftemplatefor abstractpublicclassfunctionimplementsserializable{ buildingnewfunctions. Thisisthedenitionofthisclass:
12 abstractpublicvoidinitfun(stringmf); extenderthisclass,byimplementingthetwomethodsinitfun(whichiscalled }Auserwhowishestowritehis/herownmonitoringfunction,onlyneedsto abstractpublicvectorcalc(); onlyoncebeforestartingthefunction)andcalc(whichperformstheactualcomputation).besides,theusercanaccessthemibvariablesthroughappropriate classesineachnode. thedescriptionclasshastobeginbydfun. theclassmustbeginbyfunfollowedbyanystring.thenaclassofdescription class,whoseonlymethodcalledgetdesneedstobeimplemented.thenameof mustbecreatedforeachfunction.eveninthiscasewehavecreatedanabstract Then,inordertousethisfunctioninthemanagementsystem,thenameof wewillbeabletodistinguishfunctionsanddescriptionsfromalltheremaining inanynodewherethemapserverisactive.theagentswillbeabletouse classespresentinthesystem.wewillhavetheopportunitytostoresuchclasses themanyway,thankstothedynamicloadingoftheclassespresentintheagent Ifwefollowsuchsimplerulesinthecongurationdialogboxesoftheagents, platform. 5Conclusions Inthispaperwehavepresentedasystemofnetworkmanagementbasedon ofthedierentprogrammingparadigms,basedonamobilecode. theadoptionofthesetechnologies,comparingandevaluatingtheapplicability mobileagentstechnologies.wehavediscussedthemainbenetsderivingfrom browser.thepossibilityofcustomizingthenetworkfunctionstobemonitored formingbasicnetworkmanagementfunctionalities,includingageneralizedmib mentsinthisworkconcernthedenitionofmorecomplexhealthfunctions,and isoneofthemostinterestingaspectsoftheproposedapproach.futuredevelop- ByusingtheMAPagentsplatform,wehavedevelopedsomeagentsforper- ofagentsthatcouldadapttheirmigrationdynamicallyaccordingtothetypeof tasktheyhavebeenrequested. Acknowledgments ThisworkhasbeencarriedoutunderthenancialsupportoftheItalianMinisterodell'UniversitaedellaRicercaScienticaeTecnologica(MURST)inthe References mancesystemsfordistributedapplications)project. frameworkofthemosaico(designmethodologiesandtoolsofhighperfor- 1.AdventNet.AdventNetSNMPtools.
13 2.M.Baldi,S.Gai,andG.P.Picco.ExploitingCodeMobilityinDecentralizedand 3.J.D.Caseetal.ASimpleNetworkManagementProtocol(SNMP).RFC1157, FlexibleNetworkManagement.InProceedingsoftheFirstInt.WorkshoponMobileAgents(MA97),Berlin,Germany,April G.GoldszmidtandY.Yemini.DistributedManagementbyDelegation.Proc.of 4.G.Goldszmidt.OnDistributedSystemManagement.ProceedingsoftheIFIP the15thinternationalconferenceondistributedcomputingsystems,1995. InternationalSymposiumonIntegratedNetworkManagement, G.Goldszmidt,Y.Yemini,K.Meyer,M.Erlinger,J.Betser,andC.Sunshine.DecentralizingControlandIntelligenceinNetworkManagement.Proc.ofthe4th InternationalSymposiumonIntegratedNetworkManagement,May1995. mentoftcp/ip-basedinternets:mib-ii.rfc1213, K.McCloghrieandM.Rose.ManagementInformationBaseforNetworkManage- 8.A.Puliato,O.Tomarchio,andL.Vita.MAP:DesignandImplementationofa 10.MarshallT.Rose.NetworkManagementisSimple:youjustneedtheRightFrame- 9.A.Puliato,O.Tomarchio,andL.Vita.AJava-basedDistributedNetworkMan- MobileAgentPlatform.JournalofSystemArchitecture.tobepublished. agementarchitecture.in3rdint.conferenceoncomputerscienceandinformat- ics(csi'97),durham(usa),march W.Stallings.SNMP,SNMPv2,andCMIP.Thepracticalguidetonetworkmanagementstandards.AddisonWesley, S.Waldbusser.RemoteNetworkMonitoringManagementInformationBase.RFC work.proceedingsoftheifipsecondinternationalsymposiumonintegratednet- workmanagement, ,1995. ThisarticlewasprocessedusingtheLATEXmacropackagewithLLNCSstyle
Network Management System (NMS) FAQ
 Network Management System (NMS) FAQ Q: How does the NMS work? A: The Cooper NMS is a powerful, flexible and highly scalable wireless and fixed network management solution for thousands of network nodes
Network Management System (NMS) FAQ Q: How does the NMS work? A: The Cooper NMS is a powerful, flexible and highly scalable wireless and fixed network management solution for thousands of network nodes
Setting up DCOM for Windows XP. Research
 Setting up DCOM for Windows XP Research 1- Setting up DCOM for Windows XP This document has been produced as a guide to configuring DCOM settings on machines with Windows XP SP2 installed. You must make
Setting up DCOM for Windows XP Research 1- Setting up DCOM for Windows XP This document has been produced as a guide to configuring DCOM settings on machines with Windows XP SP2 installed. You must make
Top-Down Network Design
 Top-Down Network Design Chapter Nine Developing Network Management Strategies Copyright 2010 Cisco Press & Priscilla Oppenheimer 29 Network Management Design A good design can help an organization achieve
Top-Down Network Design Chapter Nine Developing Network Management Strategies Copyright 2010 Cisco Press & Priscilla Oppenheimer 29 Network Management Design A good design can help an organization achieve
TELE 301 Network Management
 TELE 301 Network Management Lecture 20: Management Tools and Protocols Haibo Zhang Computer Science, University of Otago TELE301 Lecture 20: Management tools and protocols 1 What is Network Management?
TELE 301 Network Management Lecture 20: Management Tools and Protocols Haibo Zhang Computer Science, University of Otago TELE301 Lecture 20: Management tools and protocols 1 What is Network Management?
Deployment for Network Proxy in Simpana Environment
 Deployment for Network Proxy in Simpana Environment There are multiple ways you can use the proxy for Simpana communication. 1. Use proxy to communicate for CommNet DataCenter CS will also have CommNet
Deployment for Network Proxy in Simpana Environment There are multiple ways you can use the proxy for Simpana communication. 1. Use proxy to communicate for CommNet DataCenter CS will also have CommNet
www.dumpspdf.com 70-647 Get Success in Passing Your
 www.dumpspdf.com 70-647 Get Success in Passing Your Certification at first attempt! Vendor: Microsoft Exam Code: 70-647 Exam Name: Windows Server 2008,Enterprise Administrator Version: Demo www.dumpspdf.com
www.dumpspdf.com 70-647 Get Success in Passing Your Certification at first attempt! Vendor: Microsoft Exam Code: 70-647 Exam Name: Windows Server 2008,Enterprise Administrator Version: Demo www.dumpspdf.com
Monitoring MySQL database with Verax NMS
 Monitoring MySQL database with Verax NMS Table of contents Abstract... 3 1. Adding MySQL database to device inventory... 4 2. Adding sensors for MySQL database... 7 3. Adding performance counters for MySQL
Monitoring MySQL database with Verax NMS Table of contents Abstract... 3 1. Adding MySQL database to device inventory... 4 2. Adding sensors for MySQL database... 7 3. Adding performance counters for MySQL
Backup / migration of a Coffalyser.Net database
 Backup / migration of a Coffalyser.Net database There are two main procedures for backup or migration of your Coffalyser.Net database. One of these procedures makes use of the SQL management studio software
Backup / migration of a Coffalyser.Net database There are two main procedures for backup or migration of your Coffalyser.Net database. One of these procedures makes use of the SQL management studio software
HITACHI NAS PLATFORM F1140 CUSTOMER OVERVIEW
 HITACHI NAS PLATFORM F1140 CUSTOMER OVERVIEW JUNE 2013 1 Hitachi Data Systems Corporation 2013. All Rights Reserved. HOW CAN I ADDRESS MY SMALLER FILE SERVING NEEDS TODAY AND TOMORROW? My remote, branch
HITACHI NAS PLATFORM F1140 CUSTOMER OVERVIEW JUNE 2013 1 Hitachi Data Systems Corporation 2013. All Rights Reserved. HOW CAN I ADDRESS MY SMALLER FILE SERVING NEEDS TODAY AND TOMORROW? My remote, branch
Lecture 18: Telecommunications Management Network (TMN)
 Lecture 18: Telecommunications (TMN) Prof. Shervin Shirmohammadi SITE, University of Ottawa Prof. Shervin Shirmohammadi CEG 4395 18-1 TMN Necessity for interoperability Need for management of more than
Lecture 18: Telecommunications (TMN) Prof. Shervin Shirmohammadi SITE, University of Ottawa Prof. Shervin Shirmohammadi CEG 4395 18-1 TMN Necessity for interoperability Need for management of more than
CA Nimsoft Monitor. Probe Guide for E2E Application Response Monitoring. e2e_appmon v2.2 series
 CA Nimsoft Monitor Probe Guide for E2E Application Response Monitoring e2e_appmon v2.2 series Copyright Notice This online help system (the "System") is for your informational purposes only and is subject
CA Nimsoft Monitor Probe Guide for E2E Application Response Monitoring e2e_appmon v2.2 series Copyright Notice This online help system (the "System") is for your informational purposes only and is subject
Simple Network Management Protocol (SNMP) Amar J. Desai Graduate Student University of Southern California Computer Science
 Simple Network Management Protocol (SNMP) Amar J. Desai Graduate Student University of Southern California Computer Science 1 Outline Background SNMP Basics SNMP Version 1 SNMP Version 2 SNMP Management,
Simple Network Management Protocol (SNMP) Amar J. Desai Graduate Student University of Southern California Computer Science 1 Outline Background SNMP Basics SNMP Version 1 SNMP Version 2 SNMP Management,
RUGGEDCOM NMS. Monitor Availability Quick detection of network failures at the port and
 RUGGEDCOM NMS is fully-featured enterprise grade network management software based on the OpenNMS platform. Specifically for the rugged communications industry, RNMS provides a comprehensive platform for
RUGGEDCOM NMS is fully-featured enterprise grade network management software based on the OpenNMS platform. Specifically for the rugged communications industry, RNMS provides a comprehensive platform for
Sonus SBC 2000 Web Based Management
 Sonus SBC 2000 Web Based Management Sonus SBC 2000 Web Based Management Today IT organizations need a cost effective way of managing branch office appliances. The Sonus SBC 2000 web based management tool
Sonus SBC 2000 Web Based Management Sonus SBC 2000 Web Based Management Today IT organizations need a cost effective way of managing branch office appliances. The Sonus SBC 2000 web based management tool
DNP Serial SCADA to SCADA Over IP: Standards, Regulations Security and Best Practices
 DNP SCADA to SCADA Over : Standards, Regulations Security and Best Practices Earl Emerson, Director Systems Engineering RAD Data Communications 2014 Utilities Telecom Council of Canada Motivations for
DNP SCADA to SCADA Over : Standards, Regulations Security and Best Practices Earl Emerson, Director Systems Engineering RAD Data Communications 2014 Utilities Telecom Council of Canada Motivations for
Set Up Certificate Validation
 About Certificate Validation, page 1 About Certificate Validation Cisco Jabber uses certificate validation to establish secure connections with servers. When attempting to establish secure connections,
About Certificate Validation, page 1 About Certificate Validation Cisco Jabber uses certificate validation to establish secure connections with servers. When attempting to establish secure connections,
TSM Studio Server User Guide 2.9.0.0
 TSM Studio Server User Guide 2.9.0.0 1 Table of Contents Disclaimer... 4 What is TSM Studio Server?... 5 System Requirements... 6 Database Requirements... 6 Installing TSM Studio Server... 7 TSM Studio
TSM Studio Server User Guide 2.9.0.0 1 Table of Contents Disclaimer... 4 What is TSM Studio Server?... 5 System Requirements... 6 Database Requirements... 6 Installing TSM Studio Server... 7 TSM Studio
Parallels Automation. Overview of New Features and Enhancements in Version 6.0. White Paper. www.parallels.com
 Parallels Automation White Paper Overview of New Features and Enhancements in Version 6.0 www.parallels.com Table of Contents Introduction... 3 New Feature Highlights... 3 Transfer Subscriptions between
Parallels Automation White Paper Overview of New Features and Enhancements in Version 6.0 www.parallels.com Table of Contents Introduction... 3 New Feature Highlights... 3 Transfer Subscriptions between
Knowledge Base Article: Article 218 Revision 2 How to connect BAI to a Remote SQL Server Database?
 Knowledge Base Article: Article 218 Revision 2 How to connect BAI to a Remote SQL Server Database? Date: January 11th, 2011 Last Update: January 21st, 2013 (see Section 2, C, 4) Problem: You want to create
Knowledge Base Article: Article 218 Revision 2 How to connect BAI to a Remote SQL Server Database? Date: January 11th, 2011 Last Update: January 21st, 2013 (see Section 2, C, 4) Problem: You want to create
Simulation of an SNMP Agent: Operations, Analysis and Results
 International Journal of Electronics and Computer Science Engineering 1919 Available Online at www.ijecse.org ISSN- 2277-1956 Simulation of an SNMP Agent: Operations, Analysis and Results Pradeep Kumar
International Journal of Electronics and Computer Science Engineering 1919 Available Online at www.ijecse.org ISSN- 2277-1956 Simulation of an SNMP Agent: Operations, Analysis and Results Pradeep Kumar
Designing a Windows Server 2008 Applications Infrastructure
 Designing a Windows Server 2008 Applications Infrastructure Course Number: 6437A Course Length: 3 Days Course Overview This three day course will prepare IT professionals for the role of Enterprise Administrator.
Designing a Windows Server 2008 Applications Infrastructure Course Number: 6437A Course Length: 3 Days Course Overview This three day course will prepare IT professionals for the role of Enterprise Administrator.
SolarWinds Certified Professional. Exam Preparation Guide
 SolarWinds Certified Professional Exam Preparation Guide Introduction The SolarWinds Certified Professional (SCP) exam is designed to test your knowledge of general networking management topics and how
SolarWinds Certified Professional Exam Preparation Guide Introduction The SolarWinds Certified Professional (SCP) exam is designed to test your knowledge of general networking management topics and how
WINDOWS SERVER MONITORING
 WINDOWS SERVER Server uptime, all of the time CNS Windows Server Monitoring provides organizations with the ability to monitor the health and availability of their Windows server infrastructure. Through
WINDOWS SERVER Server uptime, all of the time CNS Windows Server Monitoring provides organizations with the ability to monitor the health and availability of their Windows server infrastructure. Through
Migrating WebEx Connect Users to Cisco Jabber
 Planning Guide Migrating WebEx Connect Users to Cisco Jabber Information for System Administrators Introduction The Cisco WebEx Messenger service provides an instant messaging / chat based collaboration
Planning Guide Migrating WebEx Connect Users to Cisco Jabber Information for System Administrators Introduction The Cisco WebEx Messenger service provides an instant messaging / chat based collaboration
NMS300 Network Management System
 NMS300 Network Management System User Manual June 2013 202-11289-01 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing your device, locate
NMS300 Network Management System User Manual June 2013 202-11289-01 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing your device, locate
Advanced Fire Protection in Data Centres
 Advanced Fire Protection in Data Centres Jeff Klein, Honeywell Life Safety, 26 June 2012, Copyright 2012 System Sensor Europe. All rights reserved. The Challenge for Mission Critical Data Centres Fuel
Advanced Fire Protection in Data Centres Jeff Klein, Honeywell Life Safety, 26 June 2012, Copyright 2012 System Sensor Europe. All rights reserved. The Challenge for Mission Critical Data Centres Fuel
Appendix G: MAS and MSS reports
 Appendix G: MAS and MSS reports Administrators can use the Reporting Tool application to generate predefined Messaging Application Server (MAS) reports. These reports are useful for monitoring system usage,
Appendix G: MAS and MSS reports Administrators can use the Reporting Tool application to generate predefined Messaging Application Server (MAS) reports. These reports are useful for monitoring system usage,
Monitor network traffic in the Dashboard tab
 As a network analyzer (aka. packet sniffer & protocol analyzer), Capsa makes it easy for us to monitor and analyze network traffic in its intuitive and information-rich tab views. With Capsa's network
As a network analyzer (aka. packet sniffer & protocol analyzer), Capsa makes it easy for us to monitor and analyze network traffic in its intuitive and information-rich tab views. With Capsa's network
SystemWatch SM. Remote Network Monitoring
 SystemWatch SM Remote Network Monitoring SystemWatch Network Monitoring Service: Real World Experience Sony s SystemWatch network monitoring service uses device and networking monitoring software in conjunction
SystemWatch SM Remote Network Monitoring SystemWatch Network Monitoring Service: Real World Experience Sony s SystemWatch network monitoring service uses device and networking monitoring software in conjunction
CLI Commands and Disaster Recovery System
 CLI Commands on Cisco Prime Collaboration Deployment, page 1 CLI Commands on Cisco Prime Collaboration Deployment The main functions of Cisco Prime Collaboration Deployment (such as creating migration,
CLI Commands on Cisco Prime Collaboration Deployment, page 1 CLI Commands on Cisco Prime Collaboration Deployment The main functions of Cisco Prime Collaboration Deployment (such as creating migration,
R07. IV B.Tech. II Semester Regular Examinations, April, 2011. NETWORK MANAGEMENT SYSTEMS (Information Technology)
 Set No. 1 1. a) Discus about network management goals and functions in detail. b) Explain in detail about current status and future of network management. 2. a) Explain the SNMP network management architecture.
Set No. 1 1. a) Discus about network management goals and functions in detail. b) Explain in detail about current status and future of network management. 2. a) Explain the SNMP network management architecture.
Service Provisioning and Management in Virtual Private Active Networks
 Service Provisioning and Management in Virtual Private Active Networks Fábio Luciano Verdi and Edmundo R. M. Madeira Institute of Computing, University of Campinas (UNICAMP) 13083-970, Campinas-SP, Brazil
Service Provisioning and Management in Virtual Private Active Networks Fábio Luciano Verdi and Edmundo R. M. Madeira Institute of Computing, University of Campinas (UNICAMP) 13083-970, Campinas-SP, Brazil
Syslog Monitoring Feature Pack
 AdventNet Web NMS Syslog Monitoring Feature Pack A dventnet, Inc. 5645 G ibraltar D rive Pleasanton, C A 94588 USA P ho ne: +1-925-924-9500 Fa x : +1-925-924-9600 Em ail:info@adventnet.com http://www.adventnet.com
AdventNet Web NMS Syslog Monitoring Feature Pack A dventnet, Inc. 5645 G ibraltar D rive Pleasanton, C A 94588 USA P ho ne: +1-925-924-9500 Fa x : +1-925-924-9600 Em ail:info@adventnet.com http://www.adventnet.com
TRAVERSE: VIRTUALIZATION AND PRIVATE CLOUD MONITORING
 TRAVERSE: VIRTUALIZATION AND PRIVATE CLOUD MONITORING SUMMARY Given recent advances in distributed computing, virtualization and private cloud technologies, enterprise datacenters have effectively become
TRAVERSE: VIRTUALIZATION AND PRIVATE CLOUD MONITORING SUMMARY Given recent advances in distributed computing, virtualization and private cloud technologies, enterprise datacenters have effectively become
EMS. Trap Collection Active Alarm Alarms sent by E-mail & SMS. Location, status and serial numbers of all assets can be managed and exported
 EMS SmartView TM Superior Design with Real-Time Monitor and Control Trap Collection Active Alarm Alarms sent by E-mail & SMS Network Topology Network Element Discovery Network Element Configuration Location,
EMS SmartView TM Superior Design with Real-Time Monitor and Control Trap Collection Active Alarm Alarms sent by E-mail & SMS Network Topology Network Element Discovery Network Element Configuration Location,
Table of Contents Introduction and System Requirements 9 Installing VMware Server 35
 Table of Contents Introduction and System Requirements 9 VMware Server: Product Overview 10 Features in VMware Server 11 Support for 64-bit Guest Operating Systems 11 Two-Way Virtual SMP (Experimental
Table of Contents Introduction and System Requirements 9 VMware Server: Product Overview 10 Features in VMware Server 11 Support for 64-bit Guest Operating Systems 11 Two-Way Virtual SMP (Experimental
Using Remote Assistance
 Using Remote Assistance With the advent of Windows XP, came Remote Assistance. Briefly described, Remote Assistance allows one individual to control another individual s desktop. Note: Either Microsoft
Using Remote Assistance With the advent of Windows XP, came Remote Assistance. Briefly described, Remote Assistance allows one individual to control another individual s desktop. Note: Either Microsoft
SNMP and OpenNMS. Part 2 OpenNMS
 SNMP and OpenNMS Part 2 OpenNMS Parts of this presentation were shamelessly copied from a presentation by the project's maintainer, Tarus Balog with the author's permission. Zeev Halevi NMS - ISO Definition:
SNMP and OpenNMS Part 2 OpenNMS Parts of this presentation were shamelessly copied from a presentation by the project's maintainer, Tarus Balog with the author's permission. Zeev Halevi NMS - ISO Definition:
SNMP, RMON, and Alarm Configuration
 CHAPTER 6 This chapter contains information on the following system management topics: Simple Network Management Protocol, page 6-1 Remote Monitoring, page 6-4 Alarms, page 6-4 Simple Network Management
CHAPTER 6 This chapter contains information on the following system management topics: Simple Network Management Protocol, page 6-1 Remote Monitoring, page 6-4 Alarms, page 6-4 Simple Network Management
IP Interface for the Somfy Digital Network (SDN) & RS485 URTSII
 IP Interface for the Somfy Digital Network (SDN) & RS485 URTSII Internet Protocol (IP) Interface Product Options Cat # 1810815 IP Interface Only Cat # 1810870: Interface and DB9/RJ45 Adapter (9015028)
IP Interface for the Somfy Digital Network (SDN) & RS485 URTSII Internet Protocol (IP) Interface Product Options Cat # 1810815 IP Interface Only Cat # 1810870: Interface and DB9/RJ45 Adapter (9015028)
Monitoring.NET Framework with Verax NMS
 Monitoring.NET Framework with Verax NMS Table of contents Abstract... 3 1. Adding.NET Framework to device inventory... 4 2. Adding sensors for.net Framework... 7 3. Adding performance counters for.net
Monitoring.NET Framework with Verax NMS Table of contents Abstract... 3 1. Adding.NET Framework to device inventory... 4 2. Adding sensors for.net Framework... 7 3. Adding performance counters for.net
Kaspersky Anti-Virus 8.0 for Windows Servers Enterprise Edition DEPLOYMENT GUIDE
 Kaspersky Anti-Virus 8.0 for Windows Servers Enterprise Edition DEPLOYMENT GUIDE P R O G R A M V E R S I O N : 8. 0 Dear User! Thank you for choosing our product. We hope that this documentation will help
Kaspersky Anti-Virus 8.0 for Windows Servers Enterprise Edition DEPLOYMENT GUIDE P R O G R A M V E R S I O N : 8. 0 Dear User! Thank you for choosing our product. We hope that this documentation will help
Table of Contents. Cisco Fault Management of ONS 15454 Using Simple Network Management Protocol
 Table of Contents Fault Management of ONS 15454 Using Simple Network Management Protocol...1 Document ID: 5701...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...1
Table of Contents Fault Management of ONS 15454 Using Simple Network Management Protocol...1 Document ID: 5701...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...1
Failsafe Protection for Utility Critical Infrastructure
 Failsafe Protection for Utility Critical Infrastructure Introduction PUCs maintain a crucial part of the nation s CI that provide essential services to the public, business and government. Reliable CI
Failsafe Protection for Utility Critical Infrastructure Introduction PUCs maintain a crucial part of the nation s CI that provide essential services to the public, business and government. Reliable CI
Centralized Auditing in Windows Derek Melber
 Introduction As I have been speaking, evangelizing, educating, and writing about Windows operating systems for the past 15 years, I have heard one common request during that time. How do I centralize the
Introduction As I have been speaking, evangelizing, educating, and writing about Windows operating systems for the past 15 years, I have heard one common request during that time. How do I centralize the
WORKING WITH WINDOWS FIREWALL IN WINDOWS 7
 WORKING WITH WINDOWS FIREWALL IN WINDOWS 7 Firewall in Windows 7 Windows 7 comes with two firewalls that work together. One is the Windows Firewall, and the other is Windows Firewall with Advanced Security
WORKING WITH WINDOWS FIREWALL IN WINDOWS 7 Firewall in Windows 7 Windows 7 comes with two firewalls that work together. One is the Windows Firewall, and the other is Windows Firewall with Advanced Security
MCTS Guide to Microsoft Windows Server 2008 Applications Infrastructure Configuration (Exam # 70-643)
 MCTS Guide to Microsoft Windows Server 2008 Applications Infrastructure Configuration (Exam # 70-643) Chapter Six Configuring Windows Server 2008 Web Services, Part 1 Objectives Create and configure Web
MCTS Guide to Microsoft Windows Server 2008 Applications Infrastructure Configuration (Exam # 70-643) Chapter Six Configuring Windows Server 2008 Web Services, Part 1 Objectives Create and configure Web
Getting Started With Delegated Administration
 Getting Started With Delegated Administration Delegated Administration (available with Websense v6.1 Corporate Editions) is a powerful tool for distributing filtering and reporting responsibilities for
Getting Started With Delegated Administration Delegated Administration (available with Websense v6.1 Corporate Editions) is a powerful tool for distributing filtering and reporting responsibilities for
Data Analysis Load Balancer
 Data Analysis Load Balancer Design Document: Version: 1.0 Last saved by Chris Small April 12, 2010 Abstract: The project is to design a mechanism to load balance network traffic over multiple different
Data Analysis Load Balancer Design Document: Version: 1.0 Last saved by Chris Small April 12, 2010 Abstract: The project is to design a mechanism to load balance network traffic over multiple different
Monitor free disc space on a server. AdRem NetCrunch 6.x Tutorial
 How To Monitor free disc space on a server AdRem NetCrunch 6.x Tutorial 2011 AdRem Software, Inc. This document is written by AdRem Software and represents the views and opinions of AdRem Software regarding
How To Monitor free disc space on a server AdRem NetCrunch 6.x Tutorial 2011 AdRem Software, Inc. This document is written by AdRem Software and represents the views and opinions of AdRem Software regarding
Nexio Connectus Cluster Set Up with SQL Server Backend
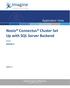 Nexio Connectus Cluster Set Up with SQL Server Backend 2.1.2 3/20/2014 Edition: A 2.1.2 Publication Information 2014 Imagine Communications. Proprietary and Confidential. Imagine Communications considers
Nexio Connectus Cluster Set Up with SQL Server Backend 2.1.2 3/20/2014 Edition: A 2.1.2 Publication Information 2014 Imagine Communications. Proprietary and Confidential. Imagine Communications considers
AN-POV-011 SNMP use with POV
 Introduction This document describes the SNMP Interface provided with Point of View (POV). Simple Network Management Protocol (SNMP) is a popular protocol for network management. It is used for collecting
Introduction This document describes the SNMP Interface provided with Point of View (POV). Simple Network Management Protocol (SNMP) is a popular protocol for network management. It is used for collecting
CHAPTER 2 BACKGROUND AND OBJECTIVE OF PRESENT WORK
 CHAPTER 2 BACKGROUND AND OBJECTIVE OF PRESENT WORK 2.1 Background Today middleware technology is not implemented only in banking and payment system even this is the most important point in the field of
CHAPTER 2 BACKGROUND AND OBJECTIVE OF PRESENT WORK 2.1 Background Today middleware technology is not implemented only in banking and payment system even this is the most important point in the field of
High-Performance, Low-Cost Computational Chemistry: Servers in a Stick, Box, and Cloud. Nathan Vance Polik Group Hope College February 19, 2015
 High-Performance, Low-Cost Computational Chemistry: Servers in a Stick, Box, and Cloud Nathan Vance Polik Group Hope College February 19, 2015 Outline The use and history of computing in chemistry The
High-Performance, Low-Cost Computational Chemistry: Servers in a Stick, Box, and Cloud Nathan Vance Polik Group Hope College February 19, 2015 Outline The use and history of computing in chemistry The
How To Manage A Network With Kepware
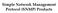 Simple Network Management Protocol (SNMP) Products Kepware Product Offerings from Eternity Sales SNMP OPC Server: SNMP Manager used to poll SNMP Agents/Devices SNMP Agent: used to make KEPServerEX data
Simple Network Management Protocol (SNMP) Products Kepware Product Offerings from Eternity Sales SNMP OPC Server: SNMP Manager used to poll SNMP Agents/Devices SNMP Agent: used to make KEPServerEX data
PRTG Training Standard, Pro & Expert
 Contact +33 (0)1 34 93 35 35 Standard, Pro & Expert Summary INTRODUCTION The offers p.2/3 Your needs : Training Content - Overview - PRTG General Presentation - PRTG Detailed Presentation - Integrated
Contact +33 (0)1 34 93 35 35 Standard, Pro & Expert Summary INTRODUCTION The offers p.2/3 Your needs : Training Content - Overview - PRTG General Presentation - PRTG Detailed Presentation - Integrated
Key Messages of Enterprise Cluster NAS Huawei OceanStor N8500
 Messages of Enterprise Cluster NAS Huawei OceanStor Messages of Enterprise Cluster NAS 1. High performance and high reliability, addressing bid data challenges High performance: In the SPEC benchmark test,
Messages of Enterprise Cluster NAS Huawei OceanStor Messages of Enterprise Cluster NAS 1. High performance and high reliability, addressing bid data challenges High performance: In the SPEC benchmark test,
Cloud Attached Storage 5.0
 Release Notes Cloud Attached Storage 5.0 March 2015 2015 Cloud Attached Storage 5.0 Release Notes 1 1 Release Contents Copyright 2009-2015 CTERA Networks Ltd. All rights reserved. No part of this document
Release Notes Cloud Attached Storage 5.0 March 2015 2015 Cloud Attached Storage 5.0 Release Notes 1 1 Release Contents Copyright 2009-2015 CTERA Networks Ltd. All rights reserved. No part of this document
Remote Monitoring Unit SC8100. Monitoring Unit SC8100
 Monitoring Unit SC8100 Remote Monitoring Unit SC8100 Environmental monitoring of any facilities, control of security breaches, temperatures, smoke, water leakages, voltages and more. Compatible with all
Monitoring Unit SC8100 Remote Monitoring Unit SC8100 Environmental monitoring of any facilities, control of security breaches, temperatures, smoke, water leakages, voltages and more. Compatible with all
Wireless Sensor Network Performance Monitoring
 Wireless Sensor Network Performance Monitoring Yaqoob J. Al-raisi & David J. Parish High Speed Networks Group Loughborough University MSN Coseners 12-13th 13th July 2007 Overview The problem we are trying
Wireless Sensor Network Performance Monitoring Yaqoob J. Al-raisi & David J. Parish High Speed Networks Group Loughborough University MSN Coseners 12-13th 13th July 2007 Overview The problem we are trying
OMC Solution IP Radios
 DATASHEET OMC Solution IP Radios COST EFFECTIVE E2E REMOTE NETWORK MANAGEMENT Intuitive, User Friendly GUI E2E Management of Transmission/Backhaul System Lower Total Cost of Ownership Simplified Remote
DATASHEET OMC Solution IP Radios COST EFFECTIVE E2E REMOTE NETWORK MANAGEMENT Intuitive, User Friendly GUI E2E Management of Transmission/Backhaul System Lower Total Cost of Ownership Simplified Remote
Intelligent Network Management System. Comprehensive Network Visibility and Management for Wireless and Fixed Networks
 Intelligent System Comprehensive Visibility and for Wireless and Fixed s Performance Analysis Made Easy With the increase in wireless network sizes and network complexities and the inter-operation of diverse
Intelligent System Comprehensive Visibility and for Wireless and Fixed s Performance Analysis Made Easy With the increase in wireless network sizes and network complexities and the inter-operation of diverse
Monitoring the NTP Server. eg Enterprise v6.0
 Monitoring the NTP Server eg Enterprise v6.0 Restricted Rights Legend The information contained in this document is confidential and subject to change without notice. No part of this document may be reproduced
Monitoring the NTP Server eg Enterprise v6.0 Restricted Rights Legend The information contained in this document is confidential and subject to change without notice. No part of this document may be reproduced
Neoteris IVE Integration Guide
 Neoteris IVE Integration Guide NESD-00090-00 CAY051402 The Secure Email Client upgrade option enables Neoteris IVE users to use standardsbased email clients to access corporate email from remote locations.
Neoteris IVE Integration Guide NESD-00090-00 CAY051402 The Secure Email Client upgrade option enables Neoteris IVE users to use standardsbased email clients to access corporate email from remote locations.
MANAGING NETWORK COMPONENTS USING SNMP
 MANAGING NETWORK COMPONENTS USING SNMP Abubucker Samsudeen Shaffi 1 Mohanned Al-Obaidy 2 Gulf College 1, 2 Sultanate of Oman. Email: abobacker.shaffi@gulfcollegeoman.com mohaned@gulfcollegeoman.com Abstract:
MANAGING NETWORK COMPONENTS USING SNMP Abubucker Samsudeen Shaffi 1 Mohanned Al-Obaidy 2 Gulf College 1, 2 Sultanate of Oman. Email: abobacker.shaffi@gulfcollegeoman.com mohaned@gulfcollegeoman.com Abstract:
SPI for MS Active Directory. Replication Monitoring. Introduction. How It Works
 SPI for MS Active Directory Replication Monitoring How It Works Introduction The HP OpenView SMART Plug-In (SPI) for Microsoft Active Directory is a critical add-on to any Windows 2000 or Windows Server
SPI for MS Active Directory Replication Monitoring How It Works Introduction The HP OpenView SMART Plug-In (SPI) for Microsoft Active Directory is a critical add-on to any Windows 2000 or Windows Server
Comprehensive VoIP Evaluation Report
 VoIP Evaluation Report Sample Timeline Tuesday, December 14, 2004 15:13:39 GMT to Saturday, December 18, 2004 11:58:41 GMT Generated on Saturday, December 18, 2004 12:00 PM Total pages 17 1. Evaluation
VoIP Evaluation Report Sample Timeline Tuesday, December 14, 2004 15:13:39 GMT to Saturday, December 18, 2004 11:58:41 GMT Generated on Saturday, December 18, 2004 12:00 PM Total pages 17 1. Evaluation
Clusterix Dynamic Clusters Administration Tutorial
 Clusterix Dynamic Clusters Administration Tutorial Marcin Pawlik , Jan Kwiatkowski IIS, WIZ, PWr Tutorial outline Clusterix and dynamic clusters
Clusterix Dynamic Clusters Administration Tutorial Marcin Pawlik , Jan Kwiatkowski IIS, WIZ, PWr Tutorial outline Clusterix and dynamic clusters
CA Nimsoft Monitor. Probe Guide for iseries System Statistics Monitoring. sysstat v1.1 series
 CA Nimsoft Monitor Probe Guide for iseries System Statistics Monitoring sysstat v1.1 series Legal Notices This online help system (the "System") is for your informational purposes only and is subject to
CA Nimsoft Monitor Probe Guide for iseries System Statistics Monitoring sysstat v1.1 series Legal Notices This online help system (the "System") is for your informational purposes only and is subject to
Utility Communications FOXMAN-UN Network Management System for ABB Communication Equipment
 Utility Communications FOXMAN-UN Network Management System for ABB Communication Equipment A reliable & flexible communication network lies at the heart of successful electrical grid operations. A comprehensive
Utility Communications FOXMAN-UN Network Management System for ABB Communication Equipment A reliable & flexible communication network lies at the heart of successful electrical grid operations. A comprehensive
5 Steps to Avoid Network Alert Overload
 5 Steps to Avoid Network Alert Overload By Avril Salter 1. 8 0 0. 8 1 3. 6 4 1 5 w w w. s c r i p t l o g i c. c o m / s m b I T 2011 ScriptLogic Corporation ALL RIGHTS RESERVED. ScriptLogic, the ScriptLogic
5 Steps to Avoid Network Alert Overload By Avril Salter 1. 8 0 0. 8 1 3. 6 4 1 5 w w w. s c r i p t l o g i c. c o m / s m b I T 2011 ScriptLogic Corporation ALL RIGHTS RESERVED. ScriptLogic, the ScriptLogic
Simple Network Management Protocol
 CHAPTER 4 This chapter gives an overview of (SNMP). It contains the following sections: Overview, page 4-1 SNMP Versioning, page 4-2 SNMP and Cisco Unified CM Basics, page 4-3 SNMP Basic Commands, page
CHAPTER 4 This chapter gives an overview of (SNMP). It contains the following sections: Overview, page 4-1 SNMP Versioning, page 4-2 SNMP and Cisco Unified CM Basics, page 4-3 SNMP Basic Commands, page
Neoteris IVE Integration Guide
 Neoteris IVE Integration Guide Published Date July 2015 The Secure Email Client upgrade option enables Neoteris IVE users to use standards based email clients to access corporate email from remote locations.
Neoteris IVE Integration Guide Published Date July 2015 The Secure Email Client upgrade option enables Neoteris IVE users to use standards based email clients to access corporate email from remote locations.
Simple Network Management Protocol
 56 CHAPTER Chapter Goals Discuss the SNMP Management Information Base. Describe SNMP version 1. Describe SNMP version 2. Background The (SNMP) is an application layer protocol that facilitates the exchange
56 CHAPTER Chapter Goals Discuss the SNMP Management Information Base. Describe SNMP version 1. Describe SNMP version 2. Background The (SNMP) is an application layer protocol that facilitates the exchange
VERITAS Cluster Server v2.0 Technical Overview
 VERITAS Cluster Server v2.0 Technical Overview V E R I T A S W H I T E P A P E R Table of Contents Executive Overview............................................................................1 Why VERITAS
VERITAS Cluster Server v2.0 Technical Overview V E R I T A S W H I T E P A P E R Table of Contents Executive Overview............................................................................1 Why VERITAS
How To Shut Down A Powerchute On A Hyperv V3.2.2 (Powerchute) On A Powerpack V3 (Powerchip) On An Uniden V3 On A Pc Or Mac (Powercheute)
 User Guide PowerChute Network Shutdown v4.1 Hyper-V and SCVMM 990-4595D-001 07/2015 Schneider Electric Legal Disclaimer The information presented in this manual is not warranted by Schneider Electric to
User Guide PowerChute Network Shutdown v4.1 Hyper-V and SCVMM 990-4595D-001 07/2015 Schneider Electric Legal Disclaimer The information presented in this manual is not warranted by Schneider Electric to
Open Source Cloud Software Made in Switzerland. Michael Eichenberger CEO stepping stone GmbH Open Cloud Day 19th of June 2012
 Open Source Cloud Software Made in Switzerland Michael Eichenberger CEO stepping stone GmbH Open Cloud Day 19th of June 2012 Agenda About us Why our own Cloud solution? Technology Distinctive Features
Open Source Cloud Software Made in Switzerland Michael Eichenberger CEO stepping stone GmbH Open Cloud Day 19th of June 2012 Agenda About us Why our own Cloud solution? Technology Distinctive Features
OMU350 Operations Manager 9.x on UNIX/Linux Advanced Administration
 OMU350 Operations Manager 9.x on UNIX/Linux Advanced Administration Instructor-Led Training For versions 9.0, 9.01, & 9.10 OVERVIEW This 5-day instructor-led course focuses on advanced administration topics
OMU350 Operations Manager 9.x on UNIX/Linux Advanced Administration Instructor-Led Training For versions 9.0, 9.01, & 9.10 OVERVIEW This 5-day instructor-led course focuses on advanced administration topics
Secure Transport Service (STS) US Certificate Update Information (SHA2) For External Client Facing Users
 Secure Transport Service (STS) US Certificate Update Information (SHA2) For External Client Facing Users What is changing? The Experian Secure Transport Service (STS), Experian s file transfer application,
Secure Transport Service (STS) US Certificate Update Information (SHA2) For External Client Facing Users What is changing? The Experian Secure Transport Service (STS), Experian s file transfer application,
802.1X AUTHENTICATION IN ACKSYS BRIDGES AND ACCESS POINTS
 APPLICATION NOTE Ref APNUS004 rev. A-0, March 08, 2007 802.1X AUTHENTICATION IN ACKSYS BRIDGES AND ACCESS POINTS Why? In addition to MAC address filtering, ACKSYS products support a more reliable authentication
APPLICATION NOTE Ref APNUS004 rev. A-0, March 08, 2007 802.1X AUTHENTICATION IN ACKSYS BRIDGES AND ACCESS POINTS Why? In addition to MAC address filtering, ACKSYS products support a more reliable authentication
HP StorageWorks Automated Storage Manager User Guide
 HP StorageWorks Automated Storage Manager User Guide Part Number: 5697 0422 First edition: June 2010 Legal and notice information Copyright 2010, 2010 Hewlett-Packard Development Company, L.P. Confidential
HP StorageWorks Automated Storage Manager User Guide Part Number: 5697 0422 First edition: June 2010 Legal and notice information Copyright 2010, 2010 Hewlett-Packard Development Company, L.P. Confidential
Exceed the possibilities
 Exceed the possibilities Clarence Hall Khody Khodayari Bob Boltralik March 2012 Copyright 2012 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice.
Exceed the possibilities Clarence Hall Khody Khodayari Bob Boltralik March 2012 Copyright 2012 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice.
Monitoring PostgreSQL database with Verax NMS
 Monitoring PostgreSQL database with Verax NMS Table of contents Abstract... 3 1. Adding PostgreSQL database to device inventory... 4 2. Adding sensors for PostgreSQL database... 7 3. Adding performance
Monitoring PostgreSQL database with Verax NMS Table of contents Abstract... 3 1. Adding PostgreSQL database to device inventory... 4 2. Adding sensors for PostgreSQL database... 7 3. Adding performance
Table of Contents. 1. Introduction...1. 2. PDU Package...2. 3. Function...3. 4. Installation...5. 5. Web Interface...7
 PDU User Manual Table of Contents 1. Introduction...1 2. PDU Package...2 3. Function...3 4. Installation...5 5. Web Interface...7 1. Introduction The PDU is an Internet ready device designed and is equipped
PDU User Manual Table of Contents 1. Introduction...1 2. PDU Package...2 3. Function...3 4. Installation...5 5. Web Interface...7 1. Introduction The PDU is an Internet ready device designed and is equipped
Network Monitoring. Chu-Sing Yang. Department of Electrical Engineering National Cheng Kung University
 Network Monitoring Chu-Sing Yang Department of Electrical Engineering National Cheng Kung University Outline Introduction Network monitoring architecture Performance monitoring Fault monitoring Accounting
Network Monitoring Chu-Sing Yang Department of Electrical Engineering National Cheng Kung University Outline Introduction Network monitoring architecture Performance monitoring Fault monitoring Accounting
Monitoring ESX/ESXi servers with Verax NMS & APM
 Monitoring ESX/ESXi servers with Verax NMS & APM Table of contents Abstract... 3 Preparing VMware server for monitoring... 3 1. Adding a VMware ESX/ESXi server to device inventory... 4 2. Adding sensors
Monitoring ESX/ESXi servers with Verax NMS & APM Table of contents Abstract... 3 Preparing VMware server for monitoring... 3 1. Adding a VMware ESX/ESXi server to device inventory... 4 2. Adding sensors
BROWSER-BASED HOME MONITOR USING ZIGBEE SENSORS
 Review of the Air Force Academy No 2 (24) 2013 BROWSER-BASED HOME MONITOR USING ZIGBEE SENSORS Marian ALEXANDRU, Vlad URSU Transilvania University of Brasov, Romania Abstract: A study of how to implement
Review of the Air Force Academy No 2 (24) 2013 BROWSER-BASED HOME MONITOR USING ZIGBEE SENSORS Marian ALEXANDRU, Vlad URSU Transilvania University of Brasov, Romania Abstract: A study of how to implement
Moving the TRITON Reporting Databases
 Moving the TRITON Reporting Databases Topic 50530 Web, Data, and Email Security Versions 7.7.x, 7.8.x Updated 06-Nov-2013 If you need to move your Microsoft SQL Server database to a new location (directory,
Moving the TRITON Reporting Databases Topic 50530 Web, Data, and Email Security Versions 7.7.x, 7.8.x Updated 06-Nov-2013 If you need to move your Microsoft SQL Server database to a new location (directory,
RPM Utility Software. User s Manual
 RPM Utility Software User s Manual Table of Contents 1. Introduction...1 2. Installation...2 3. RPM Utility Interface...4 1. Introduction General RPM Utility program is an RPM monitoring, and management
RPM Utility Software User s Manual Table of Contents 1. Introduction...1 2. Installation...2 3. RPM Utility Interface...4 1. Introduction General RPM Utility program is an RPM monitoring, and management
TECH TIPS 4 STEPS TO FORECAST AND PLAN YOUR NETWORK CAPACITY NEEDS
 4 STEPS TO FORECAST AND PLAN YOUR NETWORK CAPACITY NEEDS Using SolarWinds Network Performance Monitor One of the most likely causes of network slowdowns is excessive capacity utilization. Network engineers
4 STEPS TO FORECAST AND PLAN YOUR NETWORK CAPACITY NEEDS Using SolarWinds Network Performance Monitor One of the most likely causes of network slowdowns is excessive capacity utilization. Network engineers
Edge Configuration Series Reporting Overview
 Reporting Edge Configuration Series Reporting Overview The Reporting portion of the Edge appliance provides a number of enhanced network monitoring and reporting capabilities. WAN Reporting Provides detailed
Reporting Edge Configuration Series Reporting Overview The Reporting portion of the Edge appliance provides a number of enhanced network monitoring and reporting capabilities. WAN Reporting Provides detailed
Migrating VSMs & Performing disaster recovery
 Migrating VSMs & Performing disaster recovery In CloudByte ElastiStor 2015 CloudByte Inc. 1 Contents Migrating VSMs and performing disaster recovery in CloudByte ElastiStor... 3 Introduction... 3 VSM migration...
Migrating VSMs & Performing disaster recovery In CloudByte ElastiStor 2015 CloudByte Inc. 1 Contents Migrating VSMs and performing disaster recovery in CloudByte ElastiStor... 3 Introduction... 3 VSM migration...
Implementing and Managing Windows Server 2008 Hyper-V
 Course 6422A: Implementing and Managing Windows Server 2008 Hyper-V Length: 3 Days Language(s): English Audience(s): IT Professionals Level: 300 Technology: Windows Server 2008 Type: Course Delivery Method:
Course 6422A: Implementing and Managing Windows Server 2008 Hyper-V Length: 3 Days Language(s): English Audience(s): IT Professionals Level: 300 Technology: Windows Server 2008 Type: Course Delivery Method:
Dragon Medical Enterprise Network Edition Technical Note: Requirements for DMENE Networks with virtual servers
 Dragon Medical Enterprise Network Edition Technical Note: Requirements for DMENE Networks with virtual servers This section includes system requirements for DMENE Network configurations that utilize virtual
Dragon Medical Enterprise Network Edition Technical Note: Requirements for DMENE Networks with virtual servers This section includes system requirements for DMENE Network configurations that utilize virtual
Extending Ethernet over 2-wire Copper Networks
 Extending Ethernet over 2-wire Copper Networks Executive Summary To improve the efficiency of industrial automation systems, many operators are considering the possibility of IP upgrades to provide centralised
Extending Ethernet over 2-wire Copper Networks Executive Summary To improve the efficiency of industrial automation systems, many operators are considering the possibility of IP upgrades to provide centralised
Defender EAP Agent Installation and Configuration Guide
 Defender EAP Agent Installation and Configuration Guide Introduction A VPN is an extension of a private network that encompasses links across shared or public networks like the Internet. VPN connections
Defender EAP Agent Installation and Configuration Guide Introduction A VPN is an extension of a private network that encompasses links across shared or public networks like the Internet. VPN connections
Softalk Share Server Quick Start Guide Micro-business scenario
 Softalk Share Server Quick Start Guide Micro-business scenario Introduction Softalk Share Server lets Outlook users share personal and/or public folders with one another. This scenario assumes you have
Softalk Share Server Quick Start Guide Micro-business scenario Introduction Softalk Share Server lets Outlook users share personal and/or public folders with one another. This scenario assumes you have
TEAL: Transparent Email Archiving Library
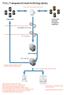 TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
2.1 What are distributed systems? What are systems? Different kind of systems How to distribute systems? 2.2 Communication concepts
 Chapter 2 Introduction to Distributed systems 1 Chapter 2 2.1 What are distributed systems? What are systems? Different kind of systems How to distribute systems? 2.2 Communication concepts Client-Server
Chapter 2 Introduction to Distributed systems 1 Chapter 2 2.1 What are distributed systems? What are systems? Different kind of systems How to distribute systems? 2.2 Communication concepts Client-Server
Git - Working with Remote Repositories
 Git - Working with Remote Repositories Handout New Concepts Working with remote Git repositories including setting up remote repositories, cloning remote repositories, and keeping local repositories in-sync
Git - Working with Remote Repositories Handout New Concepts Working with remote Git repositories including setting up remote repositories, cloning remote repositories, and keeping local repositories in-sync
