Memorandum of Understanding
|
|
|
- Bennett Jennings
- 8 years ago
- Views:
Transcription
1 Stichting NLnet Science Park XH Amsterdam The Netherlands phone: +31 (0) xmpp/sip: www: Number: The parties: and Memorandum of Understanding "Unhosted/RemoteStorage" Project Stichting NLnet, domiciled in Science Park 400, 1098 XH Amsterdam, The Netherlands, referred to as "NLnet" in this document, represented by Jos Alsters, Unhosted Project, domiciled in De Wickelaan 29, 2265DG Leidschendam, referred to as "Unhosted" in this document, given that: RemoteStorage is a draft internet protocol currently being standardised in the Internet Engineering Task Force Unhosted wants to empower users of cloud applications to control their own data, by building a suite of open source tools around the RemoteStorage (draft) protocol NLnet wishes to contribute to the development and maturisation of RemoteStorage; Unhosted is committed to advance both the RemoteStorage draft protocol and Unhosted applications; agree to the following: 1. Unhosted has written the proposal "Unhosted/RemoteStorage" which is attached to this document as Appendix Unhosted is understood to be responsible for all aspects of the project including coordinating the project and allocating funds - in line with the terms of this MoU. Appendix 1 forms an integral part of this Memorandum of Understanding. If and where statements in these Appendix or other appendices are in contradiction with one or more statements in the main memorandum text, the statement or statements in the main memorandum text will prevail. 3. Unhosted commits to publicly reporting its progress on at least a monthly basis (more often is encouraged) and to maintain a public status page for the project. When technical, legal or personal circumstances require so, Unhosted may Page 1 of 6
2 alternatively send non-public updates about the status of the project to NLnet. 4. Overall project management shall be directed by Michiel B. de Jong, acting as project manager and shall be run under the oversight of Unhosted. 5. NLnet commits to donate an amount of maximum Euro to Michiel B. de Jong in order to support the "Unhosted/RemoteStorage" Project. Amounts will be paid when the specified milestones or partial deliveries have been completed. The payment will be made by wire transfer into a bank account to be designated by Michiel B. de Jong, where the account holder is Unhosted Project or Michiel B. de Jong. 6. The source code and documentation of the Project will be made publicly available as open source under the GNU Affero General Public License version 3 or higher. 7. When appropriate, NLnet and Unhosted might issue one or more joint public statements announcing the project and NLnet's financial support. Unhosted is also encouraged to visibly and vocally acknowledge NLnet's contribution where possible - e.g. through its website, promotional materials, in presentations and in source code. 8. Funding to any particular group or person will be on the understanding that they coordinate their activities in agreement with Unhosted, in the spirit of cooperation, and in an effort to achieve the successful release of the results of the "Unhosted/RemoteStorage" Project. 9. This Memorandum of Understanding cannot be seen as any kind of employment agreement. All donation payments are made as a grant payments to the Unhosted project. Unhosted is responsible for paying any and all taxes with regard to this grant. On behalf of NLnet On behalf of Unhosted Jos Alsters Michiel B. de Jong (Place) (Date) (Place) (Date) Page 2 of 6
3 Annex I: Project plan 1 Steps towards RFC status The remotestorage spec is currently published as an IETF internet draft. At IETF 87 in Berlin there was a dedicated BoF which raised industry interest. Mark Nottingham (Chair of the IETF HTTPbis Working Group), Paul Hoffman and other senior internet technologists stated that an upgrade from Internet Draft status to Request For Comments status would not only be possible, but even desirable. They also indicated that market parties such as Akamai, Cisco and Rackspace would be potentially interested. We want to improve the specification based on the comments given to us. We need to test the interoperability of the various implementations of the remotestorage spec, and make sure we resolve any issues that come up. It is obviously hard to predict whether we can reach this goal within the 6 month renewal requested here, but we will definitely be able to take the most important first steps on the path to RFC status. a) write and submit a new version of the internet draft (draft-dejong-remotestorage- 02 spec) to the IETF (2.500 euro) b) write -02 compliant server as an npm module (2.500 euro) 2 Adding extensible support for "legacy" and hosted accounts to remotestorage.js Users need to work with both existing data, and with data from other people and data stored in resources they do not fully control themselves. Therefore it makes sense for Unhosted users to be able to access popular services such as Dropbox and GoogleDrive through Unhosted, utilising the (provider-specific) javascript API's. We want to make sure that the Unhosted framework is made extensible so that users and developers can add any resource that can be accessed cross-origin (with CORS headers). Given that a lot of users may have their personal data currently hosted on a Dropbox or GoogleDrive account, some developers may want to publish their unhosted web apps in such a way that it offers an alternative for people who do not (yet) have a remotestorage account. For instance, the option could be given: "Connect to your remotestorage" / "Connect to your Dropbox". Even if our goal is to have everybody on remotestorage, providing an alternative Dropbox option may make the library more useful to application developers. Also, the option to register for a remotestorage account from the application provider can make a lot of sense. Users could sign up for a hosted account at the app they use first, and then reuse that account at another app provider later if they wish. This is feedback we have received from app developers, and we are listening to their request. Page 3 of 6
4 : a) Design pluggable extensibility mechanism for remotestorage.js (1.250 euro) b) Add working examples (Google Drive, Dropbox) (1.250 euro) 3 Documentation for users and developers In order to position the remotestorage.js library and unhosted web apps as viable alternatives to end users and developers, we need to better document the many features of the library and the example apps. a) update remotestorage.io documentation (1.250 euro) b) create an app store for Unhosted apps (1.250 euro) 4 Community and marketing of remotestorage/unhosted web apps The remotestorage spec is reaching an ever higher level of maturity. Many "bugs" have been fixed in it over the last 2 years, and it is now on its way to its 6th improved version. Incorporating the corrections from Mark Nottingham (the current chief editor of HTTP) will boost both its quality and its credibility when talking to personal data storage providers like Rackspace, Cisco, Dropbox, Google, Microsoft, as well as to players who are interested in disrupting the current market power. Orange, Huawei and PhoneGap have already approached us, but we will also pro-actively contact other prospective supporters and implementers of our spec. We will also contact key industry players, and offer to give a presentation at their respective offices (in Silicon Valley or elsewhere). End users do not want to scourge code repositories like github. We want to make it easy for end users to start using unhosted apps, an so we aim to create a 'store' for web apps where people can find out which applications have been deployed on 5apps. We will encourage authors of unhosted web apps to make their apps available there as well as in other ways that end users can easily find them. We want to contact existing small storage providers about offering remotestorage. for instance owncloud providers would be good targets. In addition we want to talk with big industry partners about remotestorage. a) Talks at Leiden university, Complicity, QConsSF, 30C3 b) Organize PDX, Unhos and Unhost meetup c) Write another 10 episodes of the Unhosted Adventures blog, and make the complete blog cycle available as one downloadable, CC-licensed html-book. Page 4 of 6
5 Total amount for these milestones: (2.500 euro) 5 Core remotestorage modules The current contacts module is not adequate, and needs to be upgraded. a) get the contacts module working properly (2.000 euro) 6 New feature: shared notification In order to make users switch to unhosted applications these should be able to give the same level of platform integration across separate applications that 'bundled' applications from monolithic origin can and do provide. Currently there is no canonical way for unhosted applications to 'talk' to the user unless they are opened in their own window and the user is actively logged in to the application. Adding a shared notification mechanism will greatly improve the integrated user experience of Unhosted web apps. a) Design extensible shared notification mechanism (2.500 euro) b) Implement shared notification mechanism in remotestorage.js (2.500 euro) 7 New feature: portability Von Munchausen-style If the license of an Unhosted app allows it, the user might want to pick up code he or she likes and store that code with his or her remotestorage provider and/or his local storage in the browser. That way he or she no longer is exposed to changes at the source, and no longer 'burdens' the original source of the code using expensive bandwidth. The user is free to run the application directly from the localstorage (for offline use) or remotestorage location (with possible advantages like lower latency, availability of TLS). We call this Portability Von Munchausen-style. There are advanced use cases for running apps from remotestorage like sharing/provisioning the application and/or its helper scripts with other users, cloning applications and their configurations across different unhosted accounts from the same user (similar to what dotfiles do for unix applications), automated scanning for known malicious scripts by the Unhosted provider etc. In general, it would help to prevent unnecessary dependencies as well as privacy and security risks. Self stored apps also mean the user doesn't have to remember all the unique locations of his or her favorite unhosted apps -- logging into a single instance would be enough to gain a path to access all of them. Page 5 of 6
6 a) Portability Von Munchausen-style (2.000 euro) 8 New feature: Hood.ie integration The "NoBackend" movement is rapidly gaining popularity among web developers, with Hood.ie currently being the most popular implementation of a so-called app-agnostic backend server. We will combine the power of unhosted web apps and Hoodie servers by defining a discovery and authentication procedure that allows the user of a Hoodiebased web app to connect to their own Hoodie instance instead of the default one. a) Hoodie integration (1.250 euro) 9 New feature: Sockethub integration In order for Sockethub and Unhosted apps to integrate easily, Sockethub integration with the core Unhosted platform needs to be investigated. Sockethub platforms are already good in quality, but their scope is still not complete. There are still a number of platforms we need to add, and verbs we need to add to existing platforms. a) Sockethub integration (1.850 euro) 10 New feature: Inbox Functionality In order for a user to receive messages while the user herself is not online, it is necessary to have something like an "inbox" on a publically addressable port. We will implement a working proof-of-concept of a server-side service that implements this functionality, publish its source code under an MIT/AGPL dual license, and write a report about the findings and conclusions encountered in the process. a) Explore inbox functionality (1.300 euro) Page 6 of 6
Interoperable Cloud Storage with the CDMI Standard
 Interoperable Cloud Storage with the CDMI Standard Storage and Data Management in a post-filesystem World Mark Carlson, SNIA TC and Oracle Co-Chair, SNIA Cloud Storage TWG and Initiative Author: Mark Carlson,
Interoperable Cloud Storage with the CDMI Standard Storage and Data Management in a post-filesystem World Mark Carlson, SNIA TC and Oracle Co-Chair, SNIA Cloud Storage TWG and Initiative Author: Mark Carlson,
Developing ASP.NET MVC 4 Web Applications MOC 20486
 Developing ASP.NET MVC 4 Web Applications MOC 20486 Course Outline Module 1: Exploring ASP.NET MVC 4 The goal of this module is to outline to the students the components of the Microsoft Web Technologies
Developing ASP.NET MVC 4 Web Applications MOC 20486 Course Outline Module 1: Exploring ASP.NET MVC 4 The goal of this module is to outline to the students the components of the Microsoft Web Technologies
owncloud 8 What is New?
 owncloud 8 What is New? Version 8 owncloud introduces a number of improvements and new features with version 8 which include file sharing across different owncloud server installations (Federated Cloud),
owncloud 8 What is New? Version 8 owncloud introduces a number of improvements and new features with version 8 which include file sharing across different owncloud server installations (Federated Cloud),
Developing ASP.NET MVC 4 Web Applications
 Course M20486 5 Day(s) 30:00 Hours Developing ASP.NET MVC 4 Web Applications Introduction In this course, students will learn to develop advanced ASP.NET MVC applications using.net Framework 4.5 tools
Course M20486 5 Day(s) 30:00 Hours Developing ASP.NET MVC 4 Web Applications Introduction In this course, students will learn to develop advanced ASP.NET MVC applications using.net Framework 4.5 tools
Building a Continuous Integration Pipeline with Docker
 Building a Continuous Integration Pipeline with Docker August 2015 Table of Contents Overview 3 Architectural Overview and Required Components 3 Architectural Components 3 Workflow 4 Environment Prerequisites
Building a Continuous Integration Pipeline with Docker August 2015 Table of Contents Overview 3 Architectural Overview and Required Components 3 Architectural Components 3 Workflow 4 Environment Prerequisites
VMware Software Manager - Download Service User's Guide
 VMware Software Manager - Download Service User's Guide VMware Software Manager 1.1 This document supports the version of each product listed and supports all subsequent versions until the document is
VMware Software Manager - Download Service User's Guide VMware Software Manager 1.1 This document supports the version of each product listed and supports all subsequent versions until the document is
Introduction to the Mobile Access Gateway
 Introduction to the Mobile Access Gateway This document provides an overview of the AirWatch Mobile Access Gateway (MAG) architecture and security and explains how to enable MAG functionality in the AirWatch
Introduction to the Mobile Access Gateway This document provides an overview of the AirWatch Mobile Access Gateway (MAG) architecture and security and explains how to enable MAG functionality in the AirWatch
TEST AUTOMATION FRAMEWORK
 TEST AUTOMATION FRAMEWORK Twister Topics Quick introduction Use cases High Level Description Benefits Next steps Twister How to get Twister is an open source test automation framework. The code, user guide
TEST AUTOMATION FRAMEWORK Twister Topics Quick introduction Use cases High Level Description Benefits Next steps Twister How to get Twister is an open source test automation framework. The code, user guide
EXECUTIVE OFFICE OF THE PRESIDENT OFFICE OF MANAGEMENT AND BUDGET WASHINGTON, D.C. 20503. June 8, 2015
 EXECUTIVE OFFICE OF THE PRESIDENT OFFICE OF MANAGEMENT AND BUDGET WASHINGTON, D.C. 20503 June 8, 2015 M-15-13 MEMORANDUM FOR THE HEADS OF EXECUTIVE DEP FROM: SUBJECT: Tony Scott Federal Chief Information
EXECUTIVE OFFICE OF THE PRESIDENT OFFICE OF MANAGEMENT AND BUDGET WASHINGTON, D.C. 20503 June 8, 2015 M-15-13 MEMORANDUM FOR THE HEADS OF EXECUTIVE DEP FROM: SUBJECT: Tony Scott Federal Chief Information
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2. Feature and Technical Overview
 BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2 Feature and Technical Overview Published: 2010-06-16 SWDT305802-1108946-0615123042-001 Contents 1 Overview: BlackBerry Enterprise
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2 Feature and Technical Overview Published: 2010-06-16 SWDT305802-1108946-0615123042-001 Contents 1 Overview: BlackBerry Enterprise
Finding and Preventing Cross- Site Request Forgery. Tom Gallagher Security Test Lead, Microsoft
 Finding and Preventing Cross- Site Request Forgery Tom Gallagher Security Test Lead, Microsoft Agenda Quick reminder of how HTML forms work How cross-site request forgery (CSRF) attack works Obstacles
Finding and Preventing Cross- Site Request Forgery Tom Gallagher Security Test Lead, Microsoft Agenda Quick reminder of how HTML forms work How cross-site request forgery (CSRF) attack works Obstacles
This course provides students with the knowledge and skills to develop ASP.NET MVC 4 web applications.
 20486B: Developing ASP.NET MVC 4 Web Applications Course Overview This course provides students with the knowledge and skills to develop ASP.NET MVC 4 web applications. Course Introduction Course Introduction
20486B: Developing ASP.NET MVC 4 Web Applications Course Overview This course provides students with the knowledge and skills to develop ASP.NET MVC 4 web applications. Course Introduction Course Introduction
About Network Data Collector
 CHAPTER 2 About Network Data Collector The Network Data Collector is a telnet and SNMP-based data collector for Cisco devices which is used by customers to collect data for Net Audits. It provides a robust
CHAPTER 2 About Network Data Collector The Network Data Collector is a telnet and SNMP-based data collector for Cisco devices which is used by customers to collect data for Net Audits. It provides a robust
Developing ASP.NET MVC 4 Web Applications Course 20486A; 5 Days, Instructor-led
 Developing ASP.NET MVC 4 Web Applications Course 20486A; 5 Days, Instructor-led Course Description In this course, students will learn to develop advanced ASP.NET MVC applications using.net Framework 4.5
Developing ASP.NET MVC 4 Web Applications Course 20486A; 5 Days, Instructor-led Course Description In this course, students will learn to develop advanced ASP.NET MVC applications using.net Framework 4.5
PaperStream Connect. Setup Guide. Version 1.0.0.0. Copyright Fujitsu
 PaperStream Connect Setup Guide Version 1.0.0.0 Copyright Fujitsu 2014 Contents Introduction to PaperStream Connect... 2 Setting up PaperStream Capture to Release to Cloud Services... 3 Selecting a Cloud
PaperStream Connect Setup Guide Version 1.0.0.0 Copyright Fujitsu 2014 Contents Introduction to PaperStream Connect... 2 Setting up PaperStream Capture to Release to Cloud Services... 3 Selecting a Cloud
Elgg 1.8 Social Networking
 Elgg 1.8 Social Networking Create, customize, and deploy your very networking site with Elgg own social Cash Costello PACKT PUBLISHING open source* community experience distilled - BIRMINGHAM MUMBAI Preface
Elgg 1.8 Social Networking Create, customize, and deploy your very networking site with Elgg own social Cash Costello PACKT PUBLISHING open source* community experience distilled - BIRMINGHAM MUMBAI Preface
PRIVACY AWARE ACCESS CONTROL FOR CLOUD-BASED DATA PLATFORMS
 www.openi-ict.eu Open-Source, Web-Based, Framework for Integrating Applications with Social Media Services and Personal Cloudlets PRIVACY AWARE ACCESS CONTROL FOR CLOUD-BASED DATA PLATFORMS Open-Source,
www.openi-ict.eu Open-Source, Web-Based, Framework for Integrating Applications with Social Media Services and Personal Cloudlets PRIVACY AWARE ACCESS CONTROL FOR CLOUD-BASED DATA PLATFORMS Open-Source,
MaaSter Microsoft Ecosystem Management with MaaS360. Chuck Brown Jimmy Tsang www.maas360.com
 MaaSter Microsoft Ecosystem Management with MaaS360 Chuck Brown Jimmy Tsang www.maas360.com Introductions Chuck Brown Product Management IBM MaaS360 Jimmy Tsang Director of Product Marketing IBM MaaS360
MaaSter Microsoft Ecosystem Management with MaaS360 Chuck Brown Jimmy Tsang www.maas360.com Introductions Chuck Brown Product Management IBM MaaS360 Jimmy Tsang Director of Product Marketing IBM MaaS360
Server-Virtualisierung mit Windows Server Hyper-V und System Center MOC 20409
 Server-Virtualisierung mit Windows Server Hyper-V und System Center MOC 20409 Course Outline Module 1: Evaluating the Environment for Virtualization This module provides an overview of Microsoft virtualization
Server-Virtualisierung mit Windows Server Hyper-V und System Center MOC 20409 Course Outline Module 1: Evaluating the Environment for Virtualization This module provides an overview of Microsoft virtualization
Installing and Administering VMware vsphere Update Manager
 Installing and Administering VMware vsphere Update Manager Update 1 vsphere Update Manager 5.1 This document supports the version of each product listed and supports all subsequent versions until the document
Installing and Administering VMware vsphere Update Manager Update 1 vsphere Update Manager 5.1 This document supports the version of each product listed and supports all subsequent versions until the document
SSO Plugin. Release notes. J System Solutions. http://www.javasystemsolutions.com Version 3.6
 SSO Plugin Release notes J System Solutions Version 3.6 JSS SSO Plugin v3.6 Release notes What's new... 3 Improved Integrated Windows Authentication... 3 BMC ITSM self service... 3 Improved BMC ITSM Incident
SSO Plugin Release notes J System Solutions Version 3.6 JSS SSO Plugin v3.6 Release notes What's new... 3 Improved Integrated Windows Authentication... 3 BMC ITSM self service... 3 Improved BMC ITSM Incident
Oracle9i Application Server: Options for Running Active Server Pages. An Oracle White Paper July 2001
 Oracle9i Application Server: Options for Running Active Server Pages An Oracle White Paper July 2001 Oracle9i Application Server: Options for Running Active Server Pages PROBLEM SUMMARY...3 INTRODUCTION...3
Oracle9i Application Server: Options for Running Active Server Pages An Oracle White Paper July 2001 Oracle9i Application Server: Options for Running Active Server Pages PROBLEM SUMMARY...3 INTRODUCTION...3
HTTPS Inspection with Cisco CWS
 White Paper HTTPS Inspection with Cisco CWS What is HTTPS? Hyper Text Transfer Protocol Secure (HTTPS) is a secure version of the Hyper Text Transfer Protocol (HTTP). It is a combination of HTTP and a
White Paper HTTPS Inspection with Cisco CWS What is HTTPS? Hyper Text Transfer Protocol Secure (HTTPS) is a secure version of the Hyper Text Transfer Protocol (HTTP). It is a combination of HTTP and a
Internet Banking System Web Application Penetration Test Report
 Internet Banking System Web Application Penetration Test Report Kiev - 2014 1. Executive Summary This report represents the results of the Bank (hereinafter the Client) Internet Banking Web Application
Internet Banking System Web Application Penetration Test Report Kiev - 2014 1. Executive Summary This report represents the results of the Bank (hereinafter the Client) Internet Banking Web Application
Server Virtualization with Windows Server Hyper-V and System Center
 Course 20409B: Server Virtualization with Windows Server Hyper-V and System Center Course Details Course Outline Module 1: Evaluating the Environment for Virtualization This module provides an overview
Course 20409B: Server Virtualization with Windows Server Hyper-V and System Center Course Details Course Outline Module 1: Evaluating the Environment for Virtualization This module provides an overview
THE TOP 4 CONTROLS. www.tripwire.com/20criticalcontrols
 THE TOP 4 CONTROLS www.tripwire.com/20criticalcontrols THE TOP 20 CRITICAL SECURITY CONTROLS ARE RATED IN SEVERITY BY THE NSA FROM VERY HIGH DOWN TO LOW. IN THIS MINI-GUIDE, WE RE GOING TO LOOK AT THE
THE TOP 4 CONTROLS www.tripwire.com/20criticalcontrols THE TOP 20 CRITICAL SECURITY CONTROLS ARE RATED IN SEVERITY BY THE NSA FROM VERY HIGH DOWN TO LOW. IN THIS MINI-GUIDE, WE RE GOING TO LOOK AT THE
Cloud Computing in the Enterprise An Overview. For INF 5890 IT & Management Ben Eaton 24/04/2013
 Cloud Computing in the Enterprise An Overview For INF 5890 IT & Management Ben Eaton 24/04/2013 Cloud Computing in the Enterprise Background Defining the Cloud Issues of Cloud Governance Issue of Cloud
Cloud Computing in the Enterprise An Overview For INF 5890 IT & Management Ben Eaton 24/04/2013 Cloud Computing in the Enterprise Background Defining the Cloud Issues of Cloud Governance Issue of Cloud
Middleware- Driven Mobile Applications
 Middleware- Driven Mobile Applications A motwin White Paper When Launching New Mobile Services, Middleware Offers the Fastest, Most Flexible Development Path for Sophisticated Apps 1 Executive Summary
Middleware- Driven Mobile Applications A motwin White Paper When Launching New Mobile Services, Middleware Offers the Fastest, Most Flexible Development Path for Sophisticated Apps 1 Executive Summary
Solution Guide. Optimizing Microsoft SharePoint 2013 with Citrix NetScaler. citrix.com
 Solution Guide Optimizing Microsoft SharePoint 2013 with Citrix NetScaler Table of Contents Overview of SharePoint 2013 3 Why NetScaler Optimization Solution for SharePoint 2013? 3 Product Versions and
Solution Guide Optimizing Microsoft SharePoint 2013 with Citrix NetScaler Table of Contents Overview of SharePoint 2013 3 Why NetScaler Optimization Solution for SharePoint 2013? 3 Product Versions and
MAPI Connector Overview
 The CommuniGate Pro Server can be used as a "service provider" for Microsoft Windows applications supporting the MAPI (Microsoft Messaging API). To use this service, a special Connector library (CommuniGate
The CommuniGate Pro Server can be used as a "service provider" for Microsoft Windows applications supporting the MAPI (Microsoft Messaging API). To use this service, a special Connector library (CommuniGate
DEPLOYMENT GUIDE Version 1.2. Deploying the BIG-IP system v10 with Microsoft Exchange Outlook Web Access 2007
 DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP system v10 with Microsoft Exchange Outlook Web Access 2007 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Microsoft Outlook Web
DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP system v10 with Microsoft Exchange Outlook Web Access 2007 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Microsoft Outlook Web
Google Apps Deployment Guide
 CENTRIFY DEPLOYMENT GUIDE Google Apps Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical component of your corporate
CENTRIFY DEPLOYMENT GUIDE Google Apps Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical component of your corporate
How To Manage Web Content Management System (Wcm)
 WEB CONTENT MANAGEMENT SYSTEM February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in
WEB CONTENT MANAGEMENT SYSTEM February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in
NetBeans IDE Field Guide
 NetBeans IDE Field Guide Copyright 2005 Sun Microsystems, Inc. All rights reserved. Table of Contents Introduction to J2EE Development in NetBeans IDE...1 Configuring the IDE for J2EE Development...2 Getting
NetBeans IDE Field Guide Copyright 2005 Sun Microsystems, Inc. All rights reserved. Table of Contents Introduction to J2EE Development in NetBeans IDE...1 Configuring the IDE for J2EE Development...2 Getting
Collaborative Open Market to Place Objects at your Service
 Collaborative Open Market to Place Objects at your Service D8.2.3.2 Training actions report Project Acronym Project Title COMPOSE Project Number 317862 Work Package WP8 Dissemination, Training, and Stakeholders
Collaborative Open Market to Place Objects at your Service D8.2.3.2 Training actions report Project Acronym Project Title COMPOSE Project Number 317862 Work Package WP8 Dissemination, Training, and Stakeholders
Single Sign-On Framework in Tizen Contributors: Alexander Kanavin, Jussi Laako, Jaska Uimonen
 Single Sign-On Framework in Tizen Contributors: Alexander Kanavin, Jussi Laako, Jaska Uimonen Introduction Architecture Demonstration 2 What is the problem that Single Sign-on systems are aiming to solve?
Single Sign-On Framework in Tizen Contributors: Alexander Kanavin, Jussi Laako, Jaska Uimonen Introduction Architecture Demonstration 2 What is the problem that Single Sign-on systems are aiming to solve?
BlackBerry Enterprise Server Express System Requirements
 BlackBerry Enterprise Server Express System s For information about calculating hardware requirements, visit www.blackberry.com/go/serverdocs to see the BlackBerry Enterprise Server Capacity Calculator
BlackBerry Enterprise Server Express System s For information about calculating hardware requirements, visit www.blackberry.com/go/serverdocs to see the BlackBerry Enterprise Server Capacity Calculator
Kopano product strategy & roadmap
 Kopano product strategy & roadmap 11 January 2016 INTRODUCING KOPANO For many years Zarafa has provided software solutions for organising the lives of busy professionals. Emailing and advanced calendaring
Kopano product strategy & roadmap 11 January 2016 INTRODUCING KOPANO For many years Zarafa has provided software solutions for organising the lives of busy professionals. Emailing and advanced calendaring
Xerox Mobile Print Cloud
 September 2012 702P00860 Xerox Mobile Print Cloud Information Assurance Disclosure 2012 Xerox Corporation. All rights reserved. Xerox and Xerox and Design are trademarks of Xerox Corporation in the United
September 2012 702P00860 Xerox Mobile Print Cloud Information Assurance Disclosure 2012 Xerox Corporation. All rights reserved. Xerox and Xerox and Design are trademarks of Xerox Corporation in the United
View Point. Overcoming Challenges associated with SaaS Testing. Abstract. www.infosys.com. - Vijayanathan Naganathan, Sreesankar Sankarayya
 View Point Overcoming Challenges associated with SaaS - Vijayanathan Naganathan, Sreesankar Sankarayya Abstract In today s volatile economy, organizations can meet business demands of faster time to market
View Point Overcoming Challenges associated with SaaS - Vijayanathan Naganathan, Sreesankar Sankarayya Abstract In today s volatile economy, organizations can meet business demands of faster time to market
Cloud Standards. Sam Johnston <sj@google.com> Google Zürich
 Cloud Standards Sam Johnston Google Zürich Disclaimer Personal opinion May/may not reflect official Google position Cloud Computing Internet-based computing, whereby shared resources, software,
Cloud Standards Sam Johnston Google Zürich Disclaimer Personal opinion May/may not reflect official Google position Cloud Computing Internet-based computing, whereby shared resources, software,
owncloud Architecture Overview
 owncloud Architecture Overview owncloud, Inc. 57 Bedford Street, Suite 102 Lexington, MA 02420 United States phone: +1 (877) 394-2030 www.owncloud.com/contact owncloud GmbH Schloßäckerstraße 26a 90443
owncloud Architecture Overview owncloud, Inc. 57 Bedford Street, Suite 102 Lexington, MA 02420 United States phone: +1 (877) 394-2030 www.owncloud.com/contact owncloud GmbH Schloßäckerstraße 26a 90443
ITL BULLETIN FOR JANUARY 2011
 ITL BULLETIN FOR JANUARY 2011 INTERNET PROTOCOL VERSION 6 (IPv6): NIST GUIDELINES HELP ORGANIZATIONS MANAGE THE SECURE DEPLOYMENT OF THE NEW NETWORK PROTOCOL Shirley Radack, Editor Computer Security Division
ITL BULLETIN FOR JANUARY 2011 INTERNET PROTOCOL VERSION 6 (IPv6): NIST GUIDELINES HELP ORGANIZATIONS MANAGE THE SECURE DEPLOYMENT OF THE NEW NETWORK PROTOCOL Shirley Radack, Editor Computer Security Division
Security of information systems secure file transfer
 Security of information systems secure file transfer Who? Mateusz Grotek, 186816 Paweł Tarasiuk, 186875 When? October 30, 2012 Introduction SSH Different solutions Summary Questions Table of contents Problem
Security of information systems secure file transfer Who? Mateusz Grotek, 186816 Paweł Tarasiuk, 186875 When? October 30, 2012 Introduction SSH Different solutions Summary Questions Table of contents Problem
District of Columbia Courts Attachment 1 Video Conference Bridge Infrastructure Equipment Performance Specification
 1.1 Multipoint Control Unit (MCU) A. The MCU shall be capable of supporting (20) continuous presence HD Video Ports at 720P/30Hz resolution and (40) continuous presence ports at 480P/30Hz resolution. B.
1.1 Multipoint Control Unit (MCU) A. The MCU shall be capable of supporting (20) continuous presence HD Video Ports at 720P/30Hz resolution and (40) continuous presence ports at 480P/30Hz resolution. B.
Mobile Application Platform
 Mobile Application Platform from FeedHenry Next generation cloud-based solution that simplifies the development, deployment and management of mobile apps for enterprise. Develop native, hybrid and HTML5
Mobile Application Platform from FeedHenry Next generation cloud-based solution that simplifies the development, deployment and management of mobile apps for enterprise. Develop native, hybrid and HTML5
FileRunner Security Overview. An overview of the security protocols associated with the FileRunner file delivery application
 FileRunner Security Overview An overview of the security protocols associated with the FileRunner file delivery application Overview Sohonet FileRunner is a secure high-speed transfer application that
FileRunner Security Overview An overview of the security protocols associated with the FileRunner file delivery application Overview Sohonet FileRunner is a secure high-speed transfer application that
System Requirement Specification for A Distributed Desktop Search and Document Sharing Tool for Local Area Networks
 System Requirement Specification for A Distributed Desktop Search and Document Sharing Tool for Local Area Networks OnurSoft Onur Tolga Şehitoğlu November 10, 2012 v1.0 Contents 1 Introduction 3 1.1 Purpose..............................
System Requirement Specification for A Distributed Desktop Search and Document Sharing Tool for Local Area Networks OnurSoft Onur Tolga Şehitoğlu November 10, 2012 v1.0 Contents 1 Introduction 3 1.1 Purpose..............................
StriderCD Book. Release 1.4. Niall O Higgins
 StriderCD Book Release 1.4 Niall O Higgins August 22, 2015 Contents 1 Introduction 3 1.1 What Is Strider.............................................. 3 1.2 What Is Continuous Integration.....................................
StriderCD Book Release 1.4 Niall O Higgins August 22, 2015 Contents 1 Introduction 3 1.1 What Is Strider.............................................. 3 1.2 What Is Continuous Integration.....................................
What is Web Security? Motivation
 brucker@inf.ethz.ch http://www.brucker.ch/ Information Security ETH Zürich Zürich, Switzerland Information Security Fundamentals March 23, 2004 The End Users View The Server Providers View What is Web
brucker@inf.ethz.ch http://www.brucker.ch/ Information Security ETH Zürich Zürich, Switzerland Information Security Fundamentals March 23, 2004 The End Users View The Server Providers View What is Web
Integration of Learning Management Systems with Social Networking Platforms
 Integration of Learning Management Systems with Social Networking Platforms E-learning in a Facebook supported environment Jernej Rožac 1, Matevž Pogačnik 2, Andrej Kos 3 Faculty of Electrical engineering
Integration of Learning Management Systems with Social Networking Platforms E-learning in a Facebook supported environment Jernej Rožac 1, Matevž Pogačnik 2, Andrej Kos 3 Faculty of Electrical engineering
SDN and NFV in the WAN
 WHITE PAPER Hybrid Networking SDN and NFV in the WAN HOW THESE POWERFUL TECHNOLOGIES ARE DRIVING ENTERPRISE INNOVATION rev. 110615 Table of Contents Introduction 3 Software Defined Networking 3 Network
WHITE PAPER Hybrid Networking SDN and NFV in the WAN HOW THESE POWERFUL TECHNOLOGIES ARE DRIVING ENTERPRISE INNOVATION rev. 110615 Table of Contents Introduction 3 Software Defined Networking 3 Network
Understanding Evolution's Architecture A Technical Overview
 Understanding Evolution's Architecture A Technical Overview Contents Introduction Understanding Evolution's Design Evolution Architecture Evolution Server Transports Evolution Benefits How Does Evolution
Understanding Evolution's Architecture A Technical Overview Contents Introduction Understanding Evolution's Design Evolution Architecture Evolution Server Transports Evolution Benefits How Does Evolution
VoiceXML and VoIP. Architectural Elements of Next-Generation Telephone Services. RJ Auburn
 VoiceXML and VoIP Architectural Elements of Next-Generation Telephone Services RJ Auburn Chief Network Architect, Voxeo Corporation Editor, CCXML Version 1.0, W3C Ken Rehor Software Architect, Nuance Communications
VoiceXML and VoIP Architectural Elements of Next-Generation Telephone Services RJ Auburn Chief Network Architect, Voxeo Corporation Editor, CCXML Version 1.0, W3C Ken Rehor Software Architect, Nuance Communications
Network Management Deployment Guide
 Smart Business Architecture Borderless Networks for Midsized organizations Network Management Deployment Guide Revision: H1CY10 Cisco Smart Business Architecture Borderless Networks for Midsized organizations
Smart Business Architecture Borderless Networks for Midsized organizations Network Management Deployment Guide Revision: H1CY10 Cisco Smart Business Architecture Borderless Networks for Midsized organizations
Traitware Authentication Service Integration Document
 Traitware Authentication Service Integration Document February 2015 V1.1 Secure and simplify your digital life. Integrating Traitware Authentication This document covers the steps to integrate Traitware
Traitware Authentication Service Integration Document February 2015 V1.1 Secure and simplify your digital life. Integrating Traitware Authentication This document covers the steps to integrate Traitware
Programming IoT Gateways With macchina.io
 Programming IoT Gateways With macchina.io Günter Obiltschnig Applied Informatics Software Engineering GmbH Maria Elend 143 9182 Maria Elend Austria guenter.obiltschnig@appinf.com This article shows how
Programming IoT Gateways With macchina.io Günter Obiltschnig Applied Informatics Software Engineering GmbH Maria Elend 143 9182 Maria Elend Austria guenter.obiltschnig@appinf.com This article shows how
Whitepaper : Using Unsniff Network Analyzer to analyze SSL / TLS
 Whitepaper : Using Unsniff Network Analyzer to analyze SSL / TLS A number of applications today use SSL and TLS as a security layer. Unsniff allows authorized users to analyze these applications by decrypting
Whitepaper : Using Unsniff Network Analyzer to analyze SSL / TLS A number of applications today use SSL and TLS as a security layer. Unsniff allows authorized users to analyze these applications by decrypting
Final Year Project Interim Report
 2013 Final Year Project Interim Report FYP12016 AirCrypt The Secure File Sharing Platform for Everyone Supervisors: Dr. L.C.K. Hui Dr. H.Y. Chung Students: Fong Chun Sing (2010170994) Leung Sui Lun (2010580058)
2013 Final Year Project Interim Report FYP12016 AirCrypt The Secure File Sharing Platform for Everyone Supervisors: Dr. L.C.K. Hui Dr. H.Y. Chung Students: Fong Chun Sing (2010170994) Leung Sui Lun (2010580058)
A SURVEY OF CLOUD COMPUTING: NETWORK BASED ISSUES PERFORMANCE AND ANALYSIS
 A SURVEY OF CLOUD COMPUTING: NETWORK BASED ISSUES PERFORMANCE AND ANALYSIS *Dr Umesh Sehgal, #Shalini Guleria *Associate Professor,ARNI School of Computer Science,Arni University,KathagarhUmeshsehgalind@gmail.com
A SURVEY OF CLOUD COMPUTING: NETWORK BASED ISSUES PERFORMANCE AND ANALYSIS *Dr Umesh Sehgal, #Shalini Guleria *Associate Professor,ARNI School of Computer Science,Arni University,KathagarhUmeshsehgalind@gmail.com
Web of Things Architecture
 Web of Things Architecture 1. Introduction This document is an explanation about the architecture of Web Of Things (WoT). The purpose of this document is to provide (a) a guideline of the mapping between
Web of Things Architecture 1. Introduction This document is an explanation about the architecture of Web Of Things (WoT). The purpose of this document is to provide (a) a guideline of the mapping between
#define. What is #define
 #define What is #define #define is CGI s production system for Application Management and Development, offered in the context of software as a service. It is a project management tool, configuration management
#define What is #define #define is CGI s production system for Application Management and Development, offered in the context of software as a service. It is a project management tool, configuration management
Leveraging SDN and NFV in the WAN
 Leveraging SDN and NFV in the WAN Introduction Software Defined Networking (SDN) and Network Functions Virtualization (NFV) are two of the key components of the overall movement towards software defined
Leveraging SDN and NFV in the WAN Introduction Software Defined Networking (SDN) and Network Functions Virtualization (NFV) are two of the key components of the overall movement towards software defined
Cross-domain Identity Management System for Cloud Environment
 Cross-domain Identity Management System for Cloud Environment P R E S E N T E D B Y: N A Z I A A K H TA R A I S H A S A J I D M. S O H A I B FA R O O Q I T E A M L E A D : U M M E - H A B I B A T H E S
Cross-domain Identity Management System for Cloud Environment P R E S E N T E D B Y: N A Z I A A K H TA R A I S H A S A J I D M. S O H A I B FA R O O Q I T E A M L E A D : U M M E - H A B I B A T H E S
Building native mobile apps for Digital Factory
 DIGITAL FACTORY 7.0 Building native mobile apps for Digital Factory Rooted in Open Source CMS, Jahia s Digital Industrialization paradigm is about streamlining Enterprise digital projects across channels
DIGITAL FACTORY 7.0 Building native mobile apps for Digital Factory Rooted in Open Source CMS, Jahia s Digital Industrialization paradigm is about streamlining Enterprise digital projects across channels
Outlook Express POP Instructions - Bloomsburg University Students
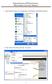 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
Connected Data. Connected Data requirements for SSO
 Chapter 40 Configuring Connected Data The following is an overview of the steps required to configure the Connected Data Web application for single sign-on (SSO) via SAML. Connected Data offers both IdP-initiated
Chapter 40 Configuring Connected Data The following is an overview of the steps required to configure the Connected Data Web application for single sign-on (SSO) via SAML. Connected Data offers both IdP-initiated
FRAFOS GmbH Windscheidstr. 18 Ahoi 10627 Berlin Germany info@frafos.com www.frafos.com
 WebRTC for Service Providers FRAFOS GmbH FRAFOS GmbH Windscheidstr. 18 Ahoi 10627 Berlin Germany info@frafos.com www.frafos.com This document is copyright of FRAFOS GmbH. Duplication or propagation or
WebRTC for Service Providers FRAFOS GmbH FRAFOS GmbH Windscheidstr. 18 Ahoi 10627 Berlin Germany info@frafos.com www.frafos.com This document is copyright of FRAFOS GmbH. Duplication or propagation or
Continuous Integration and Delivery. manage development build deploy / release
 Continuous Integration and Delivery manage development build deploy / release test About the new CI Tool Chain One of the biggest changes on the next releases of XDK, will be the adoption of the New CI
Continuous Integration and Delivery manage development build deploy / release test About the new CI Tool Chain One of the biggest changes on the next releases of XDK, will be the adoption of the New CI
Microsoft Dynamics CRM Online Fall 13 Service Update
 How to Prepare for the Microsoft Dynamics CRM Online Fall 13 Service Update COMPANY: Microsoft Corporation RELEASED: September 2013 VERSION: 1.0 Copyright This document is provided "as-is". Information
How to Prepare for the Microsoft Dynamics CRM Online Fall 13 Service Update COMPANY: Microsoft Corporation RELEASED: September 2013 VERSION: 1.0 Copyright This document is provided "as-is". Information
Solving Monitoring Challenges in the Data Center
 Solving Monitoring Challenges in the Data Center How a network monitoring switch helps IT teams stay proactive White Paper IT teams are under big pressure to improve the performance and security of corporate
Solving Monitoring Challenges in the Data Center How a network monitoring switch helps IT teams stay proactive White Paper IT teams are under big pressure to improve the performance and security of corporate
Kony Mobile Application Management (MAM)
 Kony Mobile Application Management (MAM) Kony s Secure Mobile Application Management Feature Brief Contents What is Mobile Application Management? 3 Kony Mobile Application Management Solution Overview
Kony Mobile Application Management (MAM) Kony s Secure Mobile Application Management Feature Brief Contents What is Mobile Application Management? 3 Kony Mobile Application Management Solution Overview
User Guide. What is AeroFS. Installing AeroFS. Learn How to Install AeroFS and get started syncing and sharing securely INTRODUCTION
 User Guide Learn How to Install AeroFS and get started syncing and sharing securely What is AeroFS INTRODUCTION AeroFS is a file sharing and syncing tool that allows you to share files with other people
User Guide Learn How to Install AeroFS and get started syncing and sharing securely What is AeroFS INTRODUCTION AeroFS is a file sharing and syncing tool that allows you to share files with other people
Lecture 15 - Web Security
 CSE497b Introduction to Computer and Network Security - Spring 2007 - Professor Jaeger Lecture 15 - Web Security CSE497b - Spring 2007 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse497b-s07/
CSE497b Introduction to Computer and Network Security - Spring 2007 - Professor Jaeger Lecture 15 - Web Security CSE497b - Spring 2007 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse497b-s07/
Server Virtualization with Windows Server Hyper-V and System Center
 Server Virtualization with Windows Server Hyper-V and System Center About this Course This five day course will provide you with the knowledge and skills required to design and implement Microsoft Server
Server Virtualization with Windows Server Hyper-V and System Center About this Course This five day course will provide you with the knowledge and skills required to design and implement Microsoft Server
Lumension Endpoint Management and Security Suite
 Lumension Endpoint Management and Security Suite Patch and Remediation Module Evaluation Guide July 2012 Version 1.1 Copyright 2009, Lumension L.E.M.S.S:LPR - Table of Contents Introduction... 3 Module
Lumension Endpoint Management and Security Suite Patch and Remediation Module Evaluation Guide July 2012 Version 1.1 Copyright 2009, Lumension L.E.M.S.S:LPR - Table of Contents Introduction... 3 Module
Mobile Device Management Version 8. Last updated: 17-10-14
 Mobile Device Management Version 8 Last updated: 17-10-14 Copyright 2013, 2X Ltd. http://www.2x.com E mail: info@2x.com Information in this document is subject to change without notice. Companies names
Mobile Device Management Version 8 Last updated: 17-10-14 Copyright 2013, 2X Ltd. http://www.2x.com E mail: info@2x.com Information in this document is subject to change without notice. Companies names
Advanced Server Virtualization: Vmware and Microsoft Platforms in the Virtual Data Center
 Advanced Server Virtualization: Vmware and Microsoft Platforms in the Virtual Data Center Marshall, David ISBN-13: 9780849339318 Table of Contents BASIC CONCEPTS Introduction to Server Virtualization Overview
Advanced Server Virtualization: Vmware and Microsoft Platforms in the Virtual Data Center Marshall, David ISBN-13: 9780849339318 Table of Contents BASIC CONCEPTS Introduction to Server Virtualization Overview
E- SPIN's IPSwitch WhatsUp Gold Network Management System System Administration Advanced Training (5 Day)
 Class Schedule E- SPIN's IPSwitch WhatsUp Gold Network Management System System Administration Advanced Training (5 Day) Date: Specific Pre- Agreed Upon Date Time: 9.00am - 5.00pm Venue: Pre- Agreed Upon
Class Schedule E- SPIN's IPSwitch WhatsUp Gold Network Management System System Administration Advanced Training (5 Day) Date: Specific Pre- Agreed Upon Date Time: 9.00am - 5.00pm Venue: Pre- Agreed Upon
File Share Navigator Online 1
 File Share Navigator Online 1 User Guide Service Pack 3 Issued November 2015 Table of Contents What s New in this Guide... 4 About File Share Navigator Online... 5 Components of File Share Navigator Online...
File Share Navigator Online 1 User Guide Service Pack 3 Issued November 2015 Table of Contents What s New in this Guide... 4 About File Share Navigator Online... 5 Components of File Share Navigator Online...
Description of Microsoft Internet Information Services (IIS) 5.0 and
 Page 1 of 10 Article ID: 318380 - Last Review: July 7, 2008 - Revision: 8.1 Description of Microsoft Internet Information Services (IIS) 5.0 and 6.0 status codes This article was previously published under
Page 1 of 10 Article ID: 318380 - Last Review: July 7, 2008 - Revision: 8.1 Description of Microsoft Internet Information Services (IIS) 5.0 and 6.0 status codes This article was previously published under
DreamFactory on Microsoft SQL Azure
 DreamFactory on Microsoft SQL Azure Account Setup and Installation Guide For general information about the Azure platform, go to http://www.microsoft.com/windowsazure/. For general information about the
DreamFactory on Microsoft SQL Azure Account Setup and Installation Guide For general information about the Azure platform, go to http://www.microsoft.com/windowsazure/. For general information about the
Cisco Cloud Web Security Key Functionality [NOTE: Place caption above figure.]
![Cisco Cloud Web Security Key Functionality [NOTE: Place caption above figure.] Cisco Cloud Web Security Key Functionality [NOTE: Place caption above figure.]](/thumbs/33/15822911.jpg) Cisco Cloud Web Security Cisco IT Methods Introduction Malicious scripts, or malware, are executable code added to webpages that execute when the user visits the site. Many of these seemingly harmless
Cisco Cloud Web Security Cisco IT Methods Introduction Malicious scripts, or malware, are executable code added to webpages that execute when the user visits the site. Many of these seemingly harmless
About This Document 3. Integration and Automation Capabilities 4. Command-Line Interface (CLI) 8. API RPC Protocol 9.
 Parallels Panel Contents About This Document 3 Integration and Automation Capabilities 4 Command-Line Interface (CLI) 8 API RPC Protocol 9 Event Handlers 11 Panel Notifications 13 APS Packages 14 C H A
Parallels Panel Contents About This Document 3 Integration and Automation Capabilities 4 Command-Line Interface (CLI) 8 API RPC Protocol 9 Event Handlers 11 Panel Notifications 13 APS Packages 14 C H A
The Incremental Advantage:
 The Incremental Advantage: MIGRATE TRADITIONAL APPLICATIONS FROM YOUR ON-PREMISES VMWARE ENVIRONMENT TO THE HYBRID CLOUD IN FIVE STEPS CONTENTS Introduction..................... 2 Five Steps to the Hybrid
The Incremental Advantage: MIGRATE TRADITIONAL APPLICATIONS FROM YOUR ON-PREMISES VMWARE ENVIRONMENT TO THE HYBRID CLOUD IN FIVE STEPS CONTENTS Introduction..................... 2 Five Steps to the Hybrid
TREASURY INSPECTOR GENERAL FOR TAX ADMINISTRATION
 TREASURY INSPECTOR GENERAL FOR TAX ADMINISTRATION Standard Database Security Configurations Are Adequate, Although Much Work Is Needed to Ensure Proper Implementation August 22, 2007 Reference Number:
TREASURY INSPECTOR GENERAL FOR TAX ADMINISTRATION Standard Database Security Configurations Are Adequate, Although Much Work Is Needed to Ensure Proper Implementation August 22, 2007 Reference Number:
OnCommand Performance Manager 1.1
 OnCommand Performance Manager 1.1 Installation and Setup Guide For Red Hat Enterprise Linux NetApp, Inc. 495 East Java Drive Sunnyvale, CA 94089 U.S. Telephone: +1 (408) 822-6000 Fax: +1 (408) 822-4501
OnCommand Performance Manager 1.1 Installation and Setup Guide For Red Hat Enterprise Linux NetApp, Inc. 495 East Java Drive Sunnyvale, CA 94089 U.S. Telephone: +1 (408) 822-6000 Fax: +1 (408) 822-4501
Writing for Developers: The New Customers. Amruta Ranade
 Writing for Developers: The New Customers Amruta Ranade 1 First, let s discuss the difference between User Docs and Developer Docs 2 Let s consider an example. Suppose we are writing the user docs for
Writing for Developers: The New Customers Amruta Ranade 1 First, let s discuss the difference between User Docs and Developer Docs 2 Let s consider an example. Suppose we are writing the user docs for
Easy, practical and affordable
 Easy, practical and affordable Piilo software is focused on making talent and human capital management easy, practical and affordable for small, medium and large businesses. Piilo software helps you manage
Easy, practical and affordable Piilo software is focused on making talent and human capital management easy, practical and affordable for small, medium and large businesses. Piilo software helps you manage
3. Broken Account and Session Management. 4. Cross-Site Scripting (XSS) Flaws. Web browsers execute code sent from websites. Account Management
 What is an? s Ten Most Critical Web Application Security Vulnerabilities Anthony LAI, CISSP, CISA Chapter Leader (Hong Kong) anthonylai@owasp.org Open Web Application Security Project http://www.owasp.org
What is an? s Ten Most Critical Web Application Security Vulnerabilities Anthony LAI, CISSP, CISA Chapter Leader (Hong Kong) anthonylai@owasp.org Open Web Application Security Project http://www.owasp.org
FRAFOS GmbH Windscheidstr. 18 Ahoi 10627 Berlin Germany info@frafos.com www.frafos.com
 WebRTC for the Enterprise FRAFOS GmbH FRAFOS GmbH Windscheidstr. 18 Ahoi 10627 Berlin Germany info@frafos.com www.frafos.com This document is copyright of FRAFOS GmbH. Duplication or propagation or extracts
WebRTC for the Enterprise FRAFOS GmbH FRAFOS GmbH Windscheidstr. 18 Ahoi 10627 Berlin Germany info@frafos.com www.frafos.com This document is copyright of FRAFOS GmbH. Duplication or propagation or extracts
Analyzing the Different Attributes of Web Log Files To Have An Effective Web Mining
 Analyzing the Different Attributes of Web Log Files To Have An Effective Web Mining Jaswinder Kaur #1, Dr. Kanwal Garg #2 #1 Ph.D. Scholar, Department of Computer Science & Applications Kurukshetra University,
Analyzing the Different Attributes of Web Log Files To Have An Effective Web Mining Jaswinder Kaur #1, Dr. Kanwal Garg #2 #1 Ph.D. Scholar, Department of Computer Science & Applications Kurukshetra University,
A state-of-the-art solution that brings mobility to SCADA alarms
 A state-of-the-art solution that brings mobility to SCADA alarms SCADA-Aware Mobile far exceeds the capabilities of SMS, e-mail, and pagers, and delivers alarms to the mobile device in the most reliable
A state-of-the-art solution that brings mobility to SCADA alarms SCADA-Aware Mobile far exceeds the capabilities of SMS, e-mail, and pagers, and delivers alarms to the mobile device in the most reliable
WhiteWave's Integrated Managed File Transfer (MFT)
 WhiteWave's Integrated Managed File Transfer (MFT) Spotlight on webmethods ActiveTransfer Scott Jaynes ecommerce Architect, WhiteWave Foods Ramesh Venkat Director, Product Management, Software AG 10/17/12
WhiteWave's Integrated Managed File Transfer (MFT) Spotlight on webmethods ActiveTransfer Scott Jaynes ecommerce Architect, WhiteWave Foods Ramesh Venkat Director, Product Management, Software AG 10/17/12
BlackBerry Enterprise Service 10 version 10.2 preinstallation and preupgrade checklist
 BlackBerry Enterprise Service version.2 preinstallation and preupgrade checklist Verify that the following requirements are met before you install or upgrade to BlackBerry Enterprise Service version.2.
BlackBerry Enterprise Service version.2 preinstallation and preupgrade checklist Verify that the following requirements are met before you install or upgrade to BlackBerry Enterprise Service version.2.
3Si Managed Authentication Services Service Description
 3Si Managed Authentication Services Service Description [Pick the date] 3Si Managed Authentication Services Service Description [Type the document subtitle] JT www.3sicloud.com www.3sicloud.com enquiry@3sicloud.com
3Si Managed Authentication Services Service Description [Pick the date] 3Si Managed Authentication Services Service Description [Type the document subtitle] JT www.3sicloud.com www.3sicloud.com enquiry@3sicloud.com
HP ProLiant Essentials Vulnerability and Patch Management Pack Planning Guide
 HP ProLiant Essentials Vulnerability and Patch Management Pack Planning Guide Product overview... 3 Vulnerability scanning components... 3 Vulnerability fix and patch components... 3 Checklist... 4 Pre-installation
HP ProLiant Essentials Vulnerability and Patch Management Pack Planning Guide Product overview... 3 Vulnerability scanning components... 3 Vulnerability fix and patch components... 3 Checklist... 4 Pre-installation
The Education Fellowship Finance Centralisation IT Security Strategy
 The Education Fellowship Finance Centralisation IT Security Strategy Introduction This strategy outlines the security systems in place to optimise, manage and protect The Education Fellowship data and
The Education Fellowship Finance Centralisation IT Security Strategy Introduction This strategy outlines the security systems in place to optimise, manage and protect The Education Fellowship data and
