Implementing and using the NetSupport Connectivity Server
|
|
|
- Branden Turner
- 8 years ago
- Views:
Transcription
1 Implementing and using the Connectivity Server Summary With the increased use of the internet, common questions asked by customers using Manager are: Can I connect to and remote control a machine behind a firewall? and Does Manager work with Network Address Translation (NAT)? Both have been possible in previous versions of Manager; however, to do so involved complex configurations of firewalls to allow incoming connections. Now, Manager includes a Connectivity Server (Gateway) component that will simplify the method of connection and remove the need for complex firewall configurations. CONNECTIVITY SERVER What is the Connectivity Server? The Connectivity Server is a component in Manager which provides a stable and secure method for connecting Clients and Controls via the internet using HTTP and delivers web-based remote control without the need for modifications to existing firewall configurations. The Connectivity Server acts as a go, between for a Control and Client - and when using a Connectivity Server there is no direct communication between the Client and Control. When the Client is configured to use the HTTP protocol, the Client connects to the Connectivity Server at start up. A user at a Control can then connect to the Gateway using the HTTP protocol and browse for connected Clients, then connect to any number of Clients that are attached to the Connectivity Server. As there is no direct connection between the Client and Control, and the protocol used is HTTP, it means that each of the machines can be situated behind a firewall configured to use NAT, without the need to make configuration changes to the firewall. In order for the Connectivity Server to connect a Client and Control, both the Control and Client must be able to connect to the Connectivity Server using the HTTP protocol on the Connectivity Server s configured port (the default port is 443). The Connectivity Server can be located in various different network locations as shown in the following example scenarios. A secondary Connectivity Server can also be installed and Clients configured with the secondary Connectivity Server information. This allows for Connectivity Server redundancy. When the primary Connectivity Server is not available, the Clients will automatically switch to using the secondary Connectivity Server. Once the primary Connectivity Server is available, the Clients will switch back to the primary Connectivity Server, and the secondary Connectivity Server will go into a standby mode again. This process does not disrupt any active remote control sessions that are in progress.
2 Scenario 1 Connectivity Server on the public internet Scenario 2 Connectivity Server on the Client network with a Control on the public internet In this scenario, the Connectivity Server is installed on the public internet. In this example, no configuration changes would normally need to be made to either of the firewalls. However, the machine that is running the Connectivity Server is freely available on the internet and could be open to an attack. CONNECTIVITY SERVER In this scenario, the firewall at the Client site would need to be configured to allow incoming HTTP connections to the Connectivity Server (on the configured port number). This would be similar to having a web server installed on the Client network, and making it publicly available to users on the internet. This example could be used to provide remote access to users working from home.
3 Scenario 3 Connectivity Server on a DMZ In this scenario, the firewall at the Control site would need to be configured to allow incoming HTTP connections to the Connectivity Server (on the configured port number). This would be similar to having a web server installed on the DMZ, and making it publicly available to users on the internet. DMZ The advantage of this location for the Connectivity Server is that the machine running the Connectivity Server is now protected from external attack by a firewall. However, this configuration does require some configuration changes to the firewall at the Control site. CONNECTIVITY SERVER Scenario 4 Connectivity Server on the Client network In this scenario, the firewall at the Client site would need to be configured to allow incoming HTTP connections to the Connectivity Server (on the configured port number). This would be similar to having a web server installed on the Client network and making it publicly available to users on the internet. The advantage of this location for the Connectivity Server is that the machine running the Connectivity Server is now protected from external attack by a firewall. CONNECTIVITY SERVER However, this configuration does require some configuration changes to the firewall at the Client site.
4 Installing the Connectivity Server The Connectivity Server can only be installed on an NT based operating system (XP, Vista, 2003, 2008, 2008 R2, Windows 7, Windows 8 and Server 2012) as the Connectivity Server installs as a service. The Connectivity Server is not installed by default. To install the Connectivity Server, run the standard installation package. When prompted for an installation type, choose Custom. The next screen should then display a list of components. From this list of components, select Connectivity Server and continue through the installation. At the end of the installation the Connectivity Server Configuration Utility will be displayed, as shown below: The Connectivity Server can be configured to listen on specified IP interfaces or on all IP interfaces on the machine. CMPI (Secs): When configured for Connectivity Server connections, the Client workstation confirms its availability by periodically polling the Connectivity Server. By default, a network packet is sent every 60 seconds, but you can change this if required. You can also specify the location and maximum size of the Connectivity Server log file. The logging functions of the Connectivity Server are explained in detail later in this document. Keys You can add a Gateway Key by selecting the Keys tab. Gateway Keys are used to authenticate Clients and Controls, therefore ensuring that unauthorised users cannot connect to and use the Connectivity Server. You must set at least one Gateway Key before you can apply the configuration as the Connectivity Server will not accept any connections unless at least one Gateway Key is configured. Operators The Operators tab will allow you to restrict remote control access to a list of specified users. At the Control, a user will be required to configure a username and password in order to browse a Connectivity Server and connect to the Clients. Licenses The Licenses tab displays all of the licenses that have been applied to the Connectivity Server. The Status field shows if the license has been activated. If the license has not been activated the Activate button can be used to initiate the activation process. This activation process is either performed automatically over the internet, or manually by contacting the Technical Support team, or the local reseller who can supply an Activation Code. Security From the Security tab, the option to {Enable encryption of communications to remote computers} is available. When this option is enabled, all communication in the connection process over the Connectivity Server is encrypted. General Here, you can set the port number that the Connectivity Server will accept incoming connections on. The default port is 443, and this number is registered to. When installing the Connectivity Server onto a machine that already has Information Services (IIS) installed, the port number is required to be changed from 443 to either 3085 (also registered to ), or another port number. Note: The remote computers (Controls and Clients) need to be running Manager version or later to use the encryption option. There is an additional option {Block any remote computers not using encrypted communications}. Enabling this option will prevent earlier versions of the Manager Client that do not support the enhanced level of encryption from connecting to the Connectivity Server. The default port for the HTTP protocol on the internet is port 80 and you can configure the Connectivity Server to accept connections on. However, some Service Providers (ISPs) utilise cache or proxy servers that cache HTTP traffic on port 80. If your ISP uses a cache or proxy server, then the Connectivity Server connections will fail.
5 Configuring Clients to use the Connectivity Server To configure a Client to use the HTTP protocol, you will need to run the Manager Configurator. Run the Manager Configurator and select the Advanced option Expand the Connectivity group and select HTTP ; you should then see the HTTP configuration shown below: To enable HTTP you will need to check the Use HTTP option Enter the port number which the Connectivity Server you are going to use is configured for, the default being 443 Enter the IP address of the primary Connectivity Server Enter the optional secondary Connectivity Server IP address and port number Press the Set button to enter the Gateway Key. The Gateway Key entered must be identical to one of the Gateway Keys added to the Connectivity Server Enter the proxy server details if the Client is connecting to the internet via a proxy server. Once the required configuration details have been entered, click OK to save the configuration and restart the Client. The Client should then connect to the Connectivity Server. The entire configuration for a Client is stored in the client32.ini configuration file. This file can be easily copied or Deployed (using the Manager Deploy tool) to other Client machines. For further details relating to Manager deploy, see the Online Help or the Manager User Manual.
6 Configuring the Control to use the Connectivity Server Before you can connect to a Client using a Connectivity Server, you must add the Connectivity Server to your Control Console. To do this, follow the steps below: Run the Manager Control In the left hand pane, select the Gateways group Double click on the Add a Gateway icon On the first window, enter the name and description and click Next. Here, you can enter any details you wish that describe the Connectivity Server Enter the IP address of the Connectivity Server and the port number that the Connectivity Server is configured to use (default is 443) If required, check the Use Proxy Server box and enter the proxy server IP address and port number. Click Next. Click the Set button and enter the Gateway Key Note: If the Connectivity Server is configured with multiple Gateway Keys, when you browse for Clients on this Gateway you will only see the Clients that are using the same Gateway Key as entered If Operators have been configured on the Connectivity Server, click Set and enter in the matching username and password. Click Finish. It is possible to configure multiple Connectivity Servers in the Control Console with the same IP address but with different Gateway Keys. Once you have a Gateway configured in the Control Console the browse option can be used to display the list of Client machines currently connected to the Connectivity Server. Securing the Connectivity Server The Connectivity Server will support multiple Gateway Keys. Each Gateway Key must be a minimum of 8 characters, Gateway Keys can be added to the Connectivity Server dynamically without disrupting any current Client connections. The Connectivity Server will not accept connections from a Control or Client unless a matching Gateway Key configured the Client or Control has also been entered on the Connectivity Server. Clients can only be configured with one Gateway Key, whereas the Control Console is able to support multiple Connectivity Servers, each with a different Gateway Key. All Gateway Key data is sent encrypted between the Client, Control and Connectivity Server. Once connected to the Connectivity Server, all Client and Control security such as User Validation, Security Keys etc will function normally. A Control can only connect and browse for Clients that are using the same Gateway Key as the Control. Gateway Key Connection Matrix Control Gateway Key Gateway Gateway Keys Client Gateway Key Result Testing1 Testing2 Test1 No connection from Client or Control Testing2 Testing1 Testing2 Testing1 Client connects to Connectivity Server but Control cannot connect to this Client or see the Client in a browse Testing1 Testing1 Testing1 Client connects, Control can connect to the Client and see the Client in a browse Testing2 Testing1 Testing2 No connection from Client or Control Testing2 Testing1 Testing2 Test3 Client connects, Control can connect to the Client and see the Client in a browse
7 Logging and monitoring the Connectivity Server The Connectivity Server runs as a Gateway32 service and is displayed as an icon in the system tray. Right clicking on the icon will display a shortcut menu with options for Open, Configure Connectivity Server or About. Selecting Open will display the Connectivity Server Console window as shown below. The Clients tab shows a list of all the Clients currently connected to the Connectivity Server. The Active Sessions tab displays a list of current connections between a Control and a Client, with the date and time that the connection started. The Connectivity Server creates a log file that records activity for the Connectivity Server. The log file name is GWxxx.log, and it is stored in the location specified in the Connectivity Server configuration window. GW001.log example: 29-Jan-14, 16:11:20, V12.00, running on Windows NT 6.0 Service Pack 1 (build 6001), platform 2 29-Jan-14, 16:11:20, Connectivity Server started, Max. Licensed connections: 5, Listening port: Jan-14, 16:15:32, Connectivity Server stopped
8 The following is a list of events that are written to the Connectivity Server log file: <product_name> <product_version>, running on <operating_system> <operating_system_version> <operating_system_ service_ pack> (build <build_number>), platform <platform_number> This event is logged when the Connectivity Server is first started. A typical example would be as follows: V12.00, running on Windows NT 6.0 Service Pack 1 (build 6001), platform 2 Gateway started. Mac licensed connections: <max_connections> This event is logged when the Connectivity Server is first started. Failed to start Gateway This event is logged when the Connectivity Server fails to start. Gateway stopped This event is logged when the Connectivity Server is stopped. Listening on port <port_number> This event is logged when the Connectivity Server starts listening on the specified port. This occurs during start-up and when a change in the Connectivity Server port is applied in the Connectivity Server Configurator. Failed to bind to listening port <port_number> This event is logged when the Connectivity Server fails to assign the specified port to listen for incoming connections. The port is probably being used by another application. Reloading configuration This event is logged by the Connectivity Server when the administrator has used the Connectivity Server Configurator to apply configuration changes. Listen port has changed. All current connections and sessions will be terminated. This event is logged by the Connectivity Server when the administrator modifies the listening port in the Connectivity Server Configurator and then applies the change whilst the gateway is running. Reloading Gateway Keys This event is logged by the Connectivity Server when the administrator has used the Gateway Configurator to apply configuration changes which may have included additions or removals to the list of Gateway keys. Client <Clientname> connected This event is logged when a Client connects to the Connectivity Server. Client <Clientname> Disconnected This event is logged when a Client disconnects from the Connectivity Server. Control <controlname> connected to Client <Clientname> This event is logged when a Control connects to a Client. Control <controlname> disconnected from Client <Clientname> This event is logged when a Control disconnects from a Client. Licence exceed. Rejecting connection from Client <Clientname> (<real_ip_address>, <public_ip_address>) This event is logged when a Client connecting to the Connectivity Server would exceed the licensed number of Clients. Security check failed for Client <Clientname> (<real_ip_address>). Terminating connection from <public_ip_address> This event is logged when a new Client connection fails to provide a valid Gateway Key. Security check failed for Control browse. Terminating connection from <public_ip_address> This event is logged when a Control fails to provide a valid Gateway Key during a browse Clients request. Security check failed for Control <controlname>. Rejecting connection request to Client <Clientname> from <public_ip_address> This event is logged when a Control fails to provide a valid Gateway Key during a connection request to a Client. Client/Control security check failed for Control <controlname>. Rejecting connection request to Client <Clientname> from <public_ip_address> This event is logged when the Gateway Key provided by the Control during a connection request to a Client does not match the Gateway Key supplied by the Client.
9 Further Information If you require any further information regarding Manager, you can contact the Technical Support Team using the following details: UK Office: Limited, Technical Support Department House, Towngate East Market Deeping, Peterborough PE6 8NE United Kingdom Telephone: +44 (0) Visit us:
For paid computer support call 604-518-6695 http://www.netdigix.com contact@netdigix.com
 Setting up your vpn connection on windows 2000 or XP in continuation from installing x.509 certificate on windows (please do not continue if you have not installed your x.509 certificate): Instructions
Setting up your vpn connection on windows 2000 or XP in continuation from installing x.509 certificate on windows (please do not continue if you have not installed your x.509 certificate): Instructions
pcanywhere Advanced Configuration Guide
 Introduction The pcanywhere Solution Advanced Configuration Guide is provided to assist customers with advanced features once they have the Symantec Management Platform with pcanywhere Solution installed.
Introduction The pcanywhere Solution Advanced Configuration Guide is provided to assist customers with advanced features once they have the Symantec Management Platform with pcanywhere Solution installed.
RMS Cloud - Setup Instructions for Windows Computers
 RMS Cloud - Setup Instructions for Windows Computers Please follow these instructions on each windows computer that requires a connection to the RMS Cloud system. If you are using a Mac, please see the
RMS Cloud - Setup Instructions for Windows Computers Please follow these instructions on each windows computer that requires a connection to the RMS Cloud system. If you are using a Mac, please see the
Lab 8.4.2 Configuring Access Policies and DMZ Settings
 Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
How to install and use CrossTec Remote Control or SchoolVue in a Virtual and or Terminal Service environment
 How to install and use CrossTec Remote Control or SchoolVue in a Virtual and or Terminal Service environment 1 P a g e CrossTec Corporation 500 NE Spanish River Blvd. Suite 201 Phone 800.675.0729 Fax 561.391.5820
How to install and use CrossTec Remote Control or SchoolVue in a Virtual and or Terminal Service environment 1 P a g e CrossTec Corporation 500 NE Spanish River Blvd. Suite 201 Phone 800.675.0729 Fax 561.391.5820
Defender EAP Agent Installation and Configuration Guide
 Defender EAP Agent Installation and Configuration Guide Introduction A VPN is an extension of a private network that encompasses links across shared or public networks like the Internet. VPN connections
Defender EAP Agent Installation and Configuration Guide Introduction A VPN is an extension of a private network that encompasses links across shared or public networks like the Internet. VPN connections
Windows XP Exchange Client Installation Instructions
 WINDOWS XP with Outlook 2003 or Outlook 2007 1. Click the Start button and select Control Panel: 2. If your control panel looks like this: Click Switch to Classic View. 3. Double click Mail. 4. Click show
WINDOWS XP with Outlook 2003 or Outlook 2007 1. Click the Start button and select Control Panel: 2. If your control panel looks like this: Click Switch to Classic View. 3. Double click Mail. 4. Click show
Astaro Security Gateway V8. Remote Access via L2TP over IPSec Configuring ASG and Client
 Astaro Security Gateway V8 Remote Access via L2TP over IPSec Configuring ASG and Client 1. Introduction This guide contains complementary information on the Administration Guide and the Online Help. If
Astaro Security Gateway V8 Remote Access via L2TP over IPSec Configuring ASG and Client 1. Introduction This guide contains complementary information on the Administration Guide and the Online Help. If
Information Services. Accessing the University Network using a Virtual Private Network Connection (VPN), with Windows XP Professional
 Information Services Accessing the University Network using a Virtual Private Network Connection (VPN), with Windows XP Professional Amendment & Authorisation History Ver Date Changes Name Author A 29/3/05
Information Services Accessing the University Network using a Virtual Private Network Connection (VPN), with Windows XP Professional Amendment & Authorisation History Ver Date Changes Name Author A 29/3/05
REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER
 NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.1.0.XXX Requirements and Implementation Guide (Rev 4-10209) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis Training Series
NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.1.0.XXX Requirements and Implementation Guide (Rev 4-10209) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis Training Series
Configuring SSL VPN on the Cisco ISA500 Security Appliance
 Application Note Configuring SSL VPN on the Cisco ISA500 Security Appliance This application note describes how to configure SSL VPN on the Cisco ISA500 security appliance. This document includes these
Application Note Configuring SSL VPN on the Cisco ISA500 Security Appliance This application note describes how to configure SSL VPN on the Cisco ISA500 security appliance. This document includes these
Technical Note. Configuring Outlook Web Access with Secure WebMail Proxy for eprism
 Technical Note Configuring Outlook Web Access with Secure WebMail Proxy for eprism Information in this document is subject to change without notice. This document may be distributed freely only in whole,
Technical Note Configuring Outlook Web Access with Secure WebMail Proxy for eprism Information in this document is subject to change without notice. This document may be distributed freely only in whole,
Broadband Router ESG-103. User s Guide
 Broadband Router ESG-103 User s Guide FCC Warning This equipment has been tested and found to comply with the limits for Class A & Class B digital device, pursuant to Part 15 of the FCC rules. These limits
Broadband Router ESG-103 User s Guide FCC Warning This equipment has been tested and found to comply with the limits for Class A & Class B digital device, pursuant to Part 15 of the FCC rules. These limits
Step-by-Step Setup Guide Wireless File Transmitter FTP Mode
 EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Ad Hoc Setup Windows XP 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited. 1
EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Ad Hoc Setup Windows XP 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited. 1
Deploying Windows Streaming Media Servers NLB Cluster and metasan
 Deploying Windows Streaming Media Servers NLB Cluster and metasan Introduction...................................................... 2 Objectives.......................................................
Deploying Windows Streaming Media Servers NLB Cluster and metasan Introduction...................................................... 2 Objectives.......................................................
Scenario: IPsec Remote-Access VPN Configuration
 CHAPTER 3 Scenario: IPsec Remote-Access VPN Configuration This chapter describes how to use the security appliance to accept remote-access IPsec VPN connections. A remote-access VPN enables you to create
CHAPTER 3 Scenario: IPsec Remote-Access VPN Configuration This chapter describes how to use the security appliance to accept remote-access IPsec VPN connections. A remote-access VPN enables you to create
Kepware Technologies Remote OPC DA Quick Start Guide (DCOM)
 Kepware Technologies Remote OPC DA Quick Start Guide (DCOM) March, 2013 Ref. 03.10 Kepware Technologies Table of Contents 1. Overview... 1 1.1 What is DCOM?... 1 1.2 What is OPCEnum?... 1 2. Users and
Kepware Technologies Remote OPC DA Quick Start Guide (DCOM) March, 2013 Ref. 03.10 Kepware Technologies Table of Contents 1. Overview... 1 1.1 What is DCOM?... 1 1.2 What is OPCEnum?... 1 2. Users and
Barracuda Link Balancer Administrator s Guide
 Barracuda Link Balancer Administrator s Guide Version 1.0 Barracuda Networks Inc. 3175 S. Winchester Blvd. Campbell, CA 95008 http://www.barracuda.com Copyright Notice Copyright 2008, Barracuda Networks
Barracuda Link Balancer Administrator s Guide Version 1.0 Barracuda Networks Inc. 3175 S. Winchester Blvd. Campbell, CA 95008 http://www.barracuda.com Copyright Notice Copyright 2008, Barracuda Networks
Setting Up VPN Connection to use Internet Access. 2. Right click on the appropriate VPN connection and click properties
 Setting Up VPN Connection to use Internet Access 1. Right click on My Network Places and click on Properties 2. Right click on the appropriate VPN connection and click properties 3. Click on the Networking
Setting Up VPN Connection to use Internet Access 1. Right click on My Network Places and click on Properties 2. Right click on the appropriate VPN connection and click properties 3. Click on the Networking
How to set up Outlook Anywhere on your home system
 How to set up Outlook Anywhere on your home system The Outlook Anywhere feature for Microsoft Exchange Server 2007 allows Microsoft Office Outlook 2007 and Outlook 2003 users to connect to their Outlook
How to set up Outlook Anywhere on your home system The Outlook Anywhere feature for Microsoft Exchange Server 2007 allows Microsoft Office Outlook 2007 and Outlook 2003 users to connect to their Outlook
Email client configuration guide. Business Email
 Email client configuration guide Business Email August 2013 Contents 1. Mac Email Clients 1.1 Downloading Microsoft Outlook (Professional Plan Users) 1.2 Configuring Microsoft Outlook (Full Exchange Server
Email client configuration guide Business Email August 2013 Contents 1. Mac Email Clients 1.1 Downloading Microsoft Outlook (Professional Plan Users) 1.2 Configuring Microsoft Outlook (Full Exchange Server
Remote Access End User Guide (Cisco VPN Client)
 Remote Access End User Guide (Cisco VPN Client) Contents 1 INTRODUCTION... 3 2 AUDIENCE... 3 3 CONNECTING TO N3 VPN (N3-12-1) OR EXTENDED VPN CLIENT... 3 4 DISCONNECTING FROM N3 VPN (N3-12-1) AND EXTENDED
Remote Access End User Guide (Cisco VPN Client) Contents 1 INTRODUCTION... 3 2 AUDIENCE... 3 3 CONNECTING TO N3 VPN (N3-12-1) OR EXTENDED VPN CLIENT... 3 4 DISCONNECTING FROM N3 VPN (N3-12-1) AND EXTENDED
WhatsUp Gold v16.3 Installation and Configuration Guide
 WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
WHITE PAPER Citrix Secure Gateway Startup Guide
 WHITE PAPER Citrix Secure Gateway Startup Guide www.citrix.com Contents Introduction... 2 What you will need... 2 Preparing the environment for Secure Gateway... 2 Installing a CA using Windows Server
WHITE PAPER Citrix Secure Gateway Startup Guide www.citrix.com Contents Introduction... 2 What you will need... 2 Preparing the environment for Secure Gateway... 2 Installing a CA using Windows Server
DameWare Server. Administrator Guide
 DameWare Server Administrator Guide About DameWare Contact Information Team Contact Information Sales 1.866.270.1449 General Support Technical Support Customer Service User Forums http://www.dameware.com/customers.aspx
DameWare Server Administrator Guide About DameWare Contact Information Team Contact Information Sales 1.866.270.1449 General Support Technical Support Customer Service User Forums http://www.dameware.com/customers.aspx
Hosted Microsoft Exchange Client Setup & Guide Book
 Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows Mobile Phone ActiveSync setup & configuration Section 3 - Apple iphone
Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows Mobile Phone ActiveSync setup & configuration Section 3 - Apple iphone
CONNECT-TO-CHOP USER GUIDE
 CONNECT-TO-CHOP USER GUIDE VERSION V8 Table of Contents 1 Overview... 3 2 Requirements... 3 2.1 Security... 3 2.2 Computer... 3 2.3 Application... 3 2.3.1 Web Browser... 3 2.3.2 Prerequisites... 3 3 Logon...
CONNECT-TO-CHOP USER GUIDE VERSION V8 Table of Contents 1 Overview... 3 2 Requirements... 3 2.1 Security... 3 2.2 Computer... 3 2.3 Application... 3 2.3.1 Web Browser... 3 2.3.2 Prerequisites... 3 3 Logon...
Pearl Echo Installation Checklist
 Pearl Echo Installation Checklist Use this checklist to enter critical installation and setup information that will be required to install Pearl Echo in your network. For detailed deployment instructions
Pearl Echo Installation Checklist Use this checklist to enter critical installation and setup information that will be required to install Pearl Echo in your network. For detailed deployment instructions
Sophos Anti-Virus for NetApp Storage Systems startup guide
 Sophos Anti-Virus for NetApp Storage Systems startup guide Runs on Windows 2000 and later Product version: 1 Document date: April 2012 Contents 1 About this guide...3 2 About Sophos Anti-Virus for NetApp
Sophos Anti-Virus for NetApp Storage Systems startup guide Runs on Windows 2000 and later Product version: 1 Document date: April 2012 Contents 1 About this guide...3 2 About Sophos Anti-Virus for NetApp
User Manual. Onsight Management Suite Version 5.1. Another Innovation by Librestream
 User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
Trend Micro Worry-Free Remote Manager Agent Installation Guide
 Trend Micro Worry-Free Remote Manager Agent Installation Guide Agent Installation Guide The Agent Installation Guide contains information about the Worry-Free Remote Manager (WFRM) agent installation process
Trend Micro Worry-Free Remote Manager Agent Installation Guide Agent Installation Guide The Agent Installation Guide contains information about the Worry-Free Remote Manager (WFRM) agent installation process
Lab 8.4.2 Configuring Access Policies and DMZ Settings
 Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Global VPN Client Getting Started Guide
 Global VPN Client Getting Started Guide PROTECTION AT THE SPEED OF BUSINESS Introduction The SonicWALL Global VPN Client creates a Virtual Private Network (VPN) connection between your computer and the
Global VPN Client Getting Started Guide PROTECTION AT THE SPEED OF BUSINESS Introduction The SonicWALL Global VPN Client creates a Virtual Private Network (VPN) connection between your computer and the
1. Open the preferences screen by opening the Mail menu and selecting Preferences...
 Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
NSi Mobile Installation Guide. Version 6.2
 NSi Mobile Installation Guide Version 6.2 Revision History Version Date 1.0 October 2, 2012 2.0 September 18, 2013 2 CONTENTS TABLE OF CONTENTS PREFACE... 5 Purpose of this Document... 5 Version Compatibility...
NSi Mobile Installation Guide Version 6.2 Revision History Version Date 1.0 October 2, 2012 2.0 September 18, 2013 2 CONTENTS TABLE OF CONTENTS PREFACE... 5 Purpose of this Document... 5 Version Compatibility...
Last modified on 03-01-2010 for application version 4.4.4
 Last modified on 03-01-2010 for application version 4.4.4 RemotePC User Manual Table of Contents Introduction... 3 Features... 3 Install the Remote Access Host application... 4 Install the Remote Access
Last modified on 03-01-2010 for application version 4.4.4 RemotePC User Manual Table of Contents Introduction... 3 Features... 3 Install the Remote Access Host application... 4 Install the Remote Access
Endpoint Security VPN for Windows 32-bit/64-bit
 Endpoint Security VPN for Windows 32-bit/64-bit E75.20 User Guide 13 September 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
Endpoint Security VPN for Windows 32-bit/64-bit E75.20 User Guide 13 September 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
Global VPN Client Getting Started Guide
 Global VPN Client Getting Started Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential
Global VPN Client Getting Started Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential
Hosted Microsoft Exchange Client Setup & Guide Book
 Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows 10 Mail App setup & configuration Section 3 Windows Mobile Phone ActiveSync
Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows 10 Mail App setup & configuration Section 3 Windows Mobile Phone ActiveSync
How To Connect To A University Of Cyprus Vpn 3000 From Your Computer To A Computer With A Password Protected Connection
 VPN 3000 Client for Windows XP & VISTA Information Security office University Of Cyprus October 11, 2007 Table of Contents 1. What is VPN 3000? 2. How To Use VPN 3000 3. Installing the VPN 3000 Client
VPN 3000 Client for Windows XP & VISTA Information Security office University Of Cyprus October 11, 2007 Table of Contents 1. What is VPN 3000? 2. How To Use VPN 3000 3. Installing the VPN 3000 Client
2X ApplicationServer & LoadBalancer Manual
 2X ApplicationServer & LoadBalancer Manual 2X ApplicationServer & LoadBalancer Contents 1 URL: www.2x.com E-mail: info@2x.com Information in this document is subject to change without notice. Companies,
2X ApplicationServer & LoadBalancer Manual 2X ApplicationServer & LoadBalancer Contents 1 URL: www.2x.com E-mail: info@2x.com Information in this document is subject to change without notice. Companies,
Millbeck Communications. Secure Remote Access Service. Internet VPN Access to N3. VPN Client Set Up Guide Version 6.0
 Millbeck Communications Secure Remote Access Service Internet VPN Access to N3 VPN Client Set Up Guide Version 6.0 COPYRIGHT NOTICE Copyright 2013 Millbeck Communications Ltd. All Rights Reserved. Introduction
Millbeck Communications Secure Remote Access Service Internet VPN Access to N3 VPN Client Set Up Guide Version 6.0 COPYRIGHT NOTICE Copyright 2013 Millbeck Communications Ltd. All Rights Reserved. Introduction
Installing NetSupport School for use with the NetSupport School Student extension for Google Chrome
 Installing NetSupport School for use with the NetSupport School Student extension for Google Chrome NetSupport School delivers the tools you need to help maximise the effectiveness of computer led teaching
Installing NetSupport School for use with the NetSupport School Student extension for Google Chrome NetSupport School delivers the tools you need to help maximise the effectiveness of computer led teaching
Installation and Configuration Guide
 Installation and Configuration Guide Overview This document is designed to provide a quick installation and configuration guide for WinGate using the client NAT connection. WinGate Internet Gateway and
Installation and Configuration Guide Overview This document is designed to provide a quick installation and configuration guide for WinGate using the client NAT connection. WinGate Internet Gateway and
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies C 2001-2003 Kerio Technologies. All Rights Reserved. Printing Date: December 17, 2003 This guide provides detailed description on configuration of the local
Step-by-Step Configuration Kerio Technologies C 2001-2003 Kerio Technologies. All Rights Reserved. Printing Date: December 17, 2003 This guide provides detailed description on configuration of the local
Biznet GIO Cloud Connecting VM via Windows Remote Desktop
 Biznet GIO Cloud Connecting VM via Windows Remote Desktop Introduction Connecting to your newly created Windows Virtual Machine (VM) via the Windows Remote Desktop client is easy but you will need to make
Biznet GIO Cloud Connecting VM via Windows Remote Desktop Introduction Connecting to your newly created Windows Virtual Machine (VM) via the Windows Remote Desktop client is easy but you will need to make
Immotec Systems, Inc. SQL Server 2005 Installation Document
 SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
Installation Guide for Microsoft SQL Server 2008 R2 Express. October 2011 (GUIDE 1)
 Installation Guide for Microsoft SQL Server 2008 R2 Express October 2011 (GUIDE 1) Copyright 2011 Lucid Innovations Limited. All Rights Reserved This guide only covers the installation and configuration
Installation Guide for Microsoft SQL Server 2008 R2 Express October 2011 (GUIDE 1) Copyright 2011 Lucid Innovations Limited. All Rights Reserved This guide only covers the installation and configuration
GlobalSCAPE DMZ Gateway, v1. User Guide
 GlobalSCAPE DMZ Gateway, v1 User Guide GlobalSCAPE, Inc. (GSB) Address: 4500 Lockhill-Selma Road, Suite 150 San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800) 290-5054 Technical
GlobalSCAPE DMZ Gateway, v1 User Guide GlobalSCAPE, Inc. (GSB) Address: 4500 Lockhill-Selma Road, Suite 150 San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800) 290-5054 Technical
Securing the NetSupport Client
 Securing the NetSupport Client Environments, Considerations & Requirements. Overview This document is designed to provide an overview of the security features available within NetSupport Manager and NetSupport
Securing the NetSupport Client Environments, Considerations & Requirements. Overview This document is designed to provide an overview of the security features available within NetSupport Manager and NetSupport
Download/Install IDENTD
 Download/Install IDENTD IDENTD is the small software program that must be installed on each user s computer if multiple filters are to be used in ComSifter. The program may be installed and executed locally
Download/Install IDENTD IDENTD is the small software program that must be installed on each user s computer if multiple filters are to be used in ComSifter. The program may be installed and executed locally
Step-by-Step Setup Guide Wireless File Transmitter FTP Mode
 EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure Setup Windows 7 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited.
EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure Setup Windows 7 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited.
How To Create An Easybelle History Database On A Microsoft Powerbook 2.5.2 (Windows)
 Introduction EASYLABEL 6 has several new features for saving the history of label formats. This history can include information about when label formats were edited and printed. In order to save this history,
Introduction EASYLABEL 6 has several new features for saving the history of label formats. This history can include information about when label formats were edited and printed. In order to save this history,
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies Kerio Technologies. All Rights Reserved. Printing Date: August 15, 2007 This guide provides detailed description on configuration of the local network which
Step-by-Step Configuration Kerio Technologies Kerio Technologies. All Rights Reserved. Printing Date: August 15, 2007 This guide provides detailed description on configuration of the local network which
MobileStatus Server Installation and Configuration Guide
 MobileStatus Server Installation and Configuration Guide Guide to installing and configuring the MobileStatus Server for Ventelo Mobilstatus Version 1.2 June 2010 www.blueposition.com All company names,
MobileStatus Server Installation and Configuration Guide Guide to installing and configuring the MobileStatus Server for Ventelo Mobilstatus Version 1.2 June 2010 www.blueposition.com All company names,
Sophos Anti-Virus standalone startup guide. For Windows and Mac OS X
 Sophos Anti-Virus standalone startup guide For Windows and Mac OS X Document date: June 2007 Contents 1 What you need for installation...4 2 Installing Sophos Anti-Virus for Windows...5 3 Installing Sophos
Sophos Anti-Virus standalone startup guide For Windows and Mac OS X Document date: June 2007 Contents 1 What you need for installation...4 2 Installing Sophos Anti-Virus for Windows...5 3 Installing Sophos
Configuring VPN Using Windows XP
 Configuring VPN Using Windows XP How to Create a VPN Connection What is VPN? Connecting to VPN Create a VPN Connection Connect to Your Work Computer Copying Files What is VPN? Virtual Private Networks
Configuring VPN Using Windows XP How to Create a VPN Connection What is VPN? Connecting to VPN Create a VPN Connection Connect to Your Work Computer Copying Files What is VPN? Virtual Private Networks
Configuring Security for FTP Traffic
 2 Configuring Security for FTP Traffic Securing FTP traffic Creating a security profile for FTP traffic Configuring a local traffic FTP profile Assigning an FTP security profile to a local traffic FTP
2 Configuring Security for FTP Traffic Securing FTP traffic Creating a security profile for FTP traffic Configuring a local traffic FTP profile Assigning an FTP security profile to a local traffic FTP
Remote Access Technical Guide To Setting up RADIUS
 Remote Access Technical Guide To Setting up RADIUS V 2.4 Published: 09 May 2006 1 Index 1 Index...2 1.1 Other Relevant Documents...2 2 Introduction...3 2.1 Authentication realms...3 2.2 Installing IAS...4
Remote Access Technical Guide To Setting up RADIUS V 2.4 Published: 09 May 2006 1 Index 1 Index...2 1.1 Other Relevant Documents...2 2 Introduction...3 2.1 Authentication realms...3 2.2 Installing IAS...4
How to Configure Outlook 2010 E-mail Client for Exchange
 LAUSD IT Help Desk How to Configure Outlook 2010 E-mail Client for Exchange (03/04/2012) LAUSD IT Help Desk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Table of Contents Configure Outlook 2010 for
LAUSD IT Help Desk How to Configure Outlook 2010 E-mail Client for Exchange (03/04/2012) LAUSD IT Help Desk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Table of Contents Configure Outlook 2010 for
E-Mail: SupportCenter@uhcl.edu Phone: 281-283-2828 Fax: 281-283-2969 Box: 230 http://www.uhcl.edu/uct
 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
How To - Implement Clientless Single Sign On Authentication with Active Directory
 How To Implement Clientless Single Sign On in Single Active Directory Domain Controller Environment How To - Implement Clientless Single Sign On Authentication with Active Directory Applicable Version:
How To Implement Clientless Single Sign On in Single Active Directory Domain Controller Environment How To - Implement Clientless Single Sign On Authentication with Active Directory Applicable Version:
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Network Connect Installation and Usage Guide
 Network Connect Installation and Usage Guide I. Installing the Network Connect Client..2 II. Launching Network Connect from the Desktop.. 9 III. Launching Network Connect Pre-Windows Login 11 IV. Installing
Network Connect Installation and Usage Guide I. Installing the Network Connect Client..2 II. Launching Network Connect from the Desktop.. 9 III. Launching Network Connect Pre-Windows Login 11 IV. Installing
MultiSite Manager. Setup Guide
 MultiSite Manager Setup Guide Contents 1. Introduction... 2 How MultiSite Manager works... 2 How MultiSite Manager is implemented... 2 2. MultiSite Manager requirements... 3 Operating System requirements...
MultiSite Manager Setup Guide Contents 1. Introduction... 2 How MultiSite Manager works... 2 How MultiSite Manager is implemented... 2 2. MultiSite Manager requirements... 3 Operating System requirements...
Installation Troubleshooting Guide
 Installation Troubleshooting Guide Firebird Database Connection Errors DBA Next Generation uses the Firebird Database server for connections to the database. If you have a connection error when launching
Installation Troubleshooting Guide Firebird Database Connection Errors DBA Next Generation uses the Firebird Database server for connections to the database. If you have a connection error when launching
1. Open the preferences screen by opening the Mail menu and selecting Preferences...
 Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
nexvortex Setup Template
 nexvortex Setup Template ZULTYS, INC. April 2013 5 1 0 S P R I N G S T R E E T H E R N D O N V A 2 0 1 7 0 + 1 8 5 5. 6 3 9. 8 8 8 8 Introduction This document is intended only for nexvortex customers
nexvortex Setup Template ZULTYS, INC. April 2013 5 1 0 S P R I N G S T R E E T H E R N D O N V A 2 0 1 7 0 + 1 8 5 5. 6 3 9. 8 8 8 8 Introduction This document is intended only for nexvortex customers
Campus VPN. Version 1.0 September 22, 2008
 Campus VPN Version 1.0 September 22, 2008 University of North Texas 1 9/22/2008 Introduction This is a guide on the different ways to connect to the University of North Texas Campus VPN. There are several
Campus VPN Version 1.0 September 22, 2008 University of North Texas 1 9/22/2008 Introduction This is a guide on the different ways to connect to the University of North Texas Campus VPN. There are several
4-441-095-12 (1) Network Camera
 4-441-095-12 (1) Network Camera SNC easy IP setup Guide Software Version 1.0 Before operating the unit, please read this manual thoroughly and retain it for future reference. 2012 Sony Corporation Table
4-441-095-12 (1) Network Camera SNC easy IP setup Guide Software Version 1.0 Before operating the unit, please read this manual thoroughly and retain it for future reference. 2012 Sony Corporation Table
Iridium Extreme TM Satellite Phone. Data Services Manual
 Iridium Extreme TM Satellite Phone Data Services Manual Table of Contents 1 OVERVIEW... 1 2 HOW IT WORKS... 1 3 BEFORE INSTALLING... 2 4 USB DRIVER INSTALLATION... 3 5 MODEM INSTALLATION AND CONFIGURATION...
Iridium Extreme TM Satellite Phone Data Services Manual Table of Contents 1 OVERVIEW... 1 2 HOW IT WORKS... 1 3 BEFORE INSTALLING... 2 4 USB DRIVER INSTALLATION... 3 5 MODEM INSTALLATION AND CONFIGURATION...
VNC Server 4.4. Enterprise Edition for Mac OS X. User Guide
 VNC Server 4.4 Enterprise Edition for Mac OS X User Guide Copyright and Confidentiality Copyright Statement Copyright RealVNC Ltd, 2008. All rights reserved. No part of this documentation may be reproduced
VNC Server 4.4 Enterprise Edition for Mac OS X User Guide Copyright and Confidentiality Copyright Statement Copyright RealVNC Ltd, 2008. All rights reserved. No part of this documentation may be reproduced
Global VPN Client Getting Started Guide
 Global VPN Client Getting Started Guide PROTECTION AT THE SPEED OF BUSINESS Introduction The SonicWALL Global VPN Client creates a Virtual Private Network (VPN) connection between your computer and the
Global VPN Client Getting Started Guide PROTECTION AT THE SPEED OF BUSINESS Introduction The SonicWALL Global VPN Client creates a Virtual Private Network (VPN) connection between your computer and the
NEFSIS DEDICATED SERVER
 NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.2.0.XXX (DRAFT Document) Requirements and Implementation Guide (Rev5-113009) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis
NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.2.0.XXX (DRAFT Document) Requirements and Implementation Guide (Rev5-113009) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis
Citrix Access on SonicWALL SSL VPN
 Citrix Access on SonicWALL SSL VPN Document Scope This document describes how to configure and use Citrix bookmarks to access Citrix through SonicWALL SSL VPN 5.0. It also includes information about configuring
Citrix Access on SonicWALL SSL VPN Document Scope This document describes how to configure and use Citrix bookmarks to access Citrix through SonicWALL SSL VPN 5.0. It also includes information about configuring
How to Set Up Outlook 2007 and Outlook 2010 for Hosted Microsoft Exchange if the Program is Already Installed
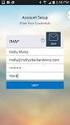 How to Set Up Outlook 2007 and Outlook 2010 for Hosted Microsoft Exchange if the Program is Already Installed 1. If you received your copy of Outlook from Cbeyond (via a CD or by downloading it from CbeyondOnline)
How to Set Up Outlook 2007 and Outlook 2010 for Hosted Microsoft Exchange if the Program is Already Installed 1. If you received your copy of Outlook from Cbeyond (via a CD or by downloading it from CbeyondOnline)
Installation and Connection Guide to the simulation environment GLOBAL VISION
 Installation and Connection Guide to the simulation environment GLOBAL VISION Hardware and Software Requirements The following hardware specification is recommended for client machines: 2 GHz Pentium class
Installation and Connection Guide to the simulation environment GLOBAL VISION Hardware and Software Requirements The following hardware specification is recommended for client machines: 2 GHz Pentium class
Setting up Remote Access
 Setting up Remote Access NOTE This document shows the steps in order for a user to set up a remote connection from scratch. Bypass any of the 6 steps that have already been done. Ie, if you have VPN connection
Setting up Remote Access NOTE This document shows the steps in order for a user to set up a remote connection from scratch. Bypass any of the 6 steps that have already been done. Ie, if you have VPN connection
Technical Support Information
 Technical Support Information Broadband Module/Broadband Module Plus Configuration Guidance Setting up Remote Access to a Network Device (Mail/File Server/Camera Etc) connected to the LAN port of the Broadband
Technical Support Information Broadband Module/Broadband Module Plus Configuration Guidance Setting up Remote Access to a Network Device (Mail/File Server/Camera Etc) connected to the LAN port of the Broadband
Step-by-Step Setup Guide Wireless File Transmitter FTP Mode
 EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure Setup Windows XP 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited.
EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure Setup Windows XP 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited.
Introduction. What is a Remote Console? What is the Server Service? A Remote Control Enabled (RCE) Console
 Contents Introduction... 3 What is a Remote Console?... 3 What is the Server Service?... 3 A Remote Control Enabled (RCE) Console... 3 Differences Between the Server Service and an RCE Console... 4 Configuring
Contents Introduction... 3 What is a Remote Console?... 3 What is the Server Service?... 3 A Remote Control Enabled (RCE) Console... 3 Differences Between the Server Service and an RCE Console... 4 Configuring
MN-700 Base Station Configuration Guide
 MN-700 Base Station Configuration Guide Contents pen the Base Station Management Tool...3 Log ff the Base Station Management Tool...3 Navigate the Base Station Management Tool...4 Current Base Station
MN-700 Base Station Configuration Guide Contents pen the Base Station Management Tool...3 Log ff the Base Station Management Tool...3 Navigate the Base Station Management Tool...4 Current Base Station
2X ApplicationServer & LoadBalancer Manual
 2X ApplicationServer & LoadBalancer Manual 2X ApplicationServer & LoadBalancer Contents 1 URL: www.2x.com E-mail: info@2x.com Information in this document is subject to change without notice. Companies,
2X ApplicationServer & LoadBalancer Manual 2X ApplicationServer & LoadBalancer Contents 1 URL: www.2x.com E-mail: info@2x.com Information in this document is subject to change without notice. Companies,
Guide to Setting up Internet Connection Sharing for Windows
 Guide to Setting up Internet Connection Sharing for Windows Document Date: December 20, 2005 Document Version: Version: 1.0 Disclaimer: Please note that this document is provided on an as is where is basis
Guide to Setting up Internet Connection Sharing for Windows Document Date: December 20, 2005 Document Version: Version: 1.0 Disclaimer: Please note that this document is provided on an as is where is basis
Purple Sturgeon Standard VPN Installation Manual for Windows XP
 A. Preparations In order to install Purple Sturgeon Standard VPN you need the following details: 1. Your username 2. Your password 3. The server's IP address 4. The server's pre-shared key This information
A. Preparations In order to install Purple Sturgeon Standard VPN you need the following details: 1. Your username 2. Your password 3. The server's IP address 4. The server's pre-shared key This information
LRDC Computing Services
 LRDC Computing Services Remote Access to the LRDC Fileservers Windows XP* April 5, 2005 *While these instructions have been created for and tested on a Windows XP computer, they may also work for your
LRDC Computing Services Remote Access to the LRDC Fileservers Windows XP* April 5, 2005 *While these instructions have been created for and tested on a Windows XP computer, they may also work for your
Installing GFI MailSecurity
 Installing GFI MailSecurity Introduction This chapter explains how to install and configure GFI MailSecurity. You can install GFI MailSecurity directly on your mail server or you can choose to install
Installing GFI MailSecurity Introduction This chapter explains how to install and configure GFI MailSecurity. You can install GFI MailSecurity directly on your mail server or you can choose to install
Aventail Connect Client with Smart Tunneling
 Aventail Connect Client with Smart Tunneling User s Guide Windows v8.7.0 1996-2006 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
Aventail Connect Client with Smart Tunneling User s Guide Windows v8.7.0 1996-2006 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
Security perimeter white paper. Configuring a security perimeter around JEP(S) with IIS SMTP
 Security perimeter white paper Configuring a security perimeter around JEP(S) with IIS SMTP Document control Document name: JEP(S) Security perimeter Author: Proxmea, Proxmea Last update: March 23, 2008
Security perimeter white paper Configuring a security perimeter around JEP(S) with IIS SMTP Document control Document name: JEP(S) Security perimeter Author: Proxmea, Proxmea Last update: March 23, 2008
Configuring SonicWALL TSA on Citrix and Terminal Services Servers
 Configuring on Citrix and Terminal Services Servers Document Scope This solutions document describes how to install, configure, and use the SonicWALL Terminal Services Agent (TSA) on a multi-user server,
Configuring on Citrix and Terminal Services Servers Document Scope This solutions document describes how to install, configure, and use the SonicWALL Terminal Services Agent (TSA) on a multi-user server,
for Networks Installation Guide for the application on the server July 2014 (GUIDE 2) Lucid Rapid Version 6.05-N and later
 for Networks Installation Guide for the application on the server July 2014 (GUIDE 2) Lucid Rapid Version 6.05-N and later Copyright 2014, Lucid Innovations Limited. All Rights Reserved Lucid Research
for Networks Installation Guide for the application on the server July 2014 (GUIDE 2) Lucid Rapid Version 6.05-N and later Copyright 2014, Lucid Innovations Limited. All Rights Reserved Lucid Research
How to Setup PPTP VPN Between a Windows PPTP Client and the DIR-130.
 Note: DIR-130 FW: 1.21 How to Setup PPTP VPN Between a Windows PPTP Client and the DIR-130. This setup example uses the following network settings: D-Link Technical Support PPTP VPN Between Windows PPTP
Note: DIR-130 FW: 1.21 How to Setup PPTP VPN Between a Windows PPTP Client and the DIR-130. This setup example uses the following network settings: D-Link Technical Support PPTP VPN Between Windows PPTP
WhatsUpGold. v3.0. WhatsConnected User Guide
 WhatsUpGold v3.0 WhatsConnected User Guide Contents CHAPTER 1 Welcome to WhatsConnected Finding more information and updates... 2 Sending feedback... 3 CHAPTER 2 Installing and Configuring WhatsConnected
WhatsUpGold v3.0 WhatsConnected User Guide Contents CHAPTER 1 Welcome to WhatsConnected Finding more information and updates... 2 Sending feedback... 3 CHAPTER 2 Installing and Configuring WhatsConnected
Web Security Service
 Webroot Web Security Service Desktop Web Proxy Configuration Guide Webroot Software, Inc. 385 Interlocken Crescent Suite 800 Broomfield, CO 80021 www.webroot.com Desktop Web Proxy Configuration Guide September
Webroot Web Security Service Desktop Web Proxy Configuration Guide Webroot Software, Inc. 385 Interlocken Crescent Suite 800 Broomfield, CO 80021 www.webroot.com Desktop Web Proxy Configuration Guide September
ReadyNAS Remote. User Manual. June 2013 202-11078-03. 350 East Plumeria Drive San Jose, CA 95134 USA
 User Manual June 2013 202-11078-03 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for selecting this NETGEAR product. After installing your device, locate the serial number on the label
User Manual June 2013 202-11078-03 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for selecting this NETGEAR product. After installing your device, locate the serial number on the label
Hallpass Instructions for Connecting to Mac with a Mac
 Hallpass Instructions for Connecting to Mac with a Mac The following instructions explain how to enable screen sharing with your Macintosh computer using another Macintosh computer. Note: You must leave
Hallpass Instructions for Connecting to Mac with a Mac The following instructions explain how to enable screen sharing with your Macintosh computer using another Macintosh computer. Note: You must leave
Sophos Endpoint Security and Control standalone startup guide
 Sophos Endpoint Security and Control standalone startup guide Sophos Endpoint Security and Control version 9 Sophos Anti-Virus for Mac OS X, version 7 Document date: October 2009 Contents 1 Before you
Sophos Endpoint Security and Control standalone startup guide Sophos Endpoint Security and Control version 9 Sophos Anti-Virus for Mac OS X, version 7 Document date: October 2009 Contents 1 Before you
Wireless Network Configuration Guide
 CIT Table of Contents Introduction... 1 General Wireless Settings... 1 1. Windows XP Wireless Configuration... 2 2. Windows XP Intel Pro Wireless Tool... 7 3. Windows Vista Using the Windows Wireless Tools...
CIT Table of Contents Introduction... 1 General Wireless Settings... 1 1. Windows XP Wireless Configuration... 2 2. Windows XP Intel Pro Wireless Tool... 7 3. Windows Vista Using the Windows Wireless Tools...
2X SecureRemoteDesktop. Version 1.1
 2X SecureRemoteDesktop Version 1.1 Website: www.2x.com Email: info@2x.com Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious
2X SecureRemoteDesktop Version 1.1 Website: www.2x.com Email: info@2x.com Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious
Dell SonicWALL SRA 7.5 Citrix Access
 Dell SonicWALL SRA 7.5 Citrix Access Document Scope This document describes how to configure and use Citrix bookmarks to access Citrix through Dell SonicWALL SRA 7.5. It also includes information about
Dell SonicWALL SRA 7.5 Citrix Access Document Scope This document describes how to configure and use Citrix bookmarks to access Citrix through Dell SonicWALL SRA 7.5. It also includes information about
