Written & Presented by Darren Fuller SecQuest Information Security Ltd.
|
|
|
- Clemence Tucker
- 10 years ago
- Views:
Transcription
1 SecQuest INFORMATION SECURITY 44Con 2012: Toppling Domino Testing security in a Lotus Notes environment Written & Presented by Darren Fuller SecQuest Information Security Ltd.
2 About this Presentation This presentation was originally given at 44Con 2012 in London and had a number of interactive demos which obviously cannot be included. If you or your company would like further information about Domino security or to arrange a re-run of this talk on your premises please contact us. Tel:
3 Who Am I? Darren Fuller Lotus PCLP * Security Consultant Ex IBM Notes developer Ex IBM EMEA X-Force Run a company called SecQuest Been using Notes since V3 on IBM OS/2 * Domino R5
4 What I m Talking About Today Although there have been a number of technical papers published by different researchers covering Lotus Notes/Domino security it is rarely covered by the wider pen testing community. In this presentation I ll aim to give a general overview of Domino security and demonstrate ways of breaking in. This will cover security issues from the point of view of the web server, native Domino server and demonstrate some tricks you can use from the client side of things.
5 Typical! Nothing about Notes/Domino for a while then William Dawson talked about it at BSides Vegas this year! Interesting talk about Domino hashes which we ll cover in a bit of detail later Link to talks:
6 Used By More than half of Fortune 100 companies & more
7 Lotus Notes/Domino: History Created by Ray Ozzie/Iris Associates V1 Shipped in 1989 Included public key cryptography 3 major editions available in the early days V8.5.4 is currently in beta
8 Crypto Background Information US Edition used 64 bit keys International keys restricted to 40 bits due to US export rules before 1997 Deal with US.gov to allow 64 bit international keys after 1997 providing they had the first 24 bits France didn t like this! A French edition was made with 40 bit encryption keys These days 128 and 256 bit AES can be used
9 Security Overview ID Files Database ACL (Access control list) Execution Control List (ECL) NAB Groups
10 Security Overview Encryption Layers Database Encryption Document Encryption Field Encryption Transport Layer Encryption
11 C mon! We re h4x0rs.. Can we whack it?
12 Yes we Can! Examples given in this presentation are based on real world tests. These techniques have been used a number of times to compromise various client sites. Obviously root is nice but the data is the thing to go for, the right Notes user will give you the keys to the kingdom!
13 Breaking In Externally What to look for names.nsf database with anonymous access domlog.nsf with anonymous access webadmin.nsf (you ll be lucky!)
14 Checking out the /hacker Domain Anonymous access to domlog.nsf can give you a session ID, these default to 30 minute expiry
15 NAB Access!
16 Because.. The admins have messed up and granted anonymous reader access
17 HTTPPassword in Document Source Vulnerability documented in 2005 Still overlooked by a lot of admins
18 HTTPPassword in Document Source <input name="fullname" type="hidden" value="milexa Crozzd/hacker; Milexa Crozzd"> <input name="shortname" type="hidden" value="milexa"> <input name="httppassword" type="hidden" value="(gbzjmlbtihzbxts0tcil)"> <input name="dsphttppassword" type="hidden" value="(gbzjmlbtihzbxts0tcil)"> Metasploit can automate hash gathering
19 Cracking Passwords Grab password hashes from the document source Domino has two types of password hashes for internet passwords; normal and more secure Use JTR with Jumbo Patch normal = lotus5 more secure = dominosec
20 Cracking Passwords: results
21 Targeting Interesting Users Once you have cracked some passwords you should be able to authenticate and access catalog.nsf If internet authentication is set to Fewer name variations with higher security you need to use the full canonical username: Joe King/hacker catalog.nsf contains a list of all databases on the server + access control information The By Name view will give you a list of databases your user can access
22 Targeting Interesting Users
23 Access Control List Info
24 Check group members in names.nsf JTR popped this one earlier!
25 Getting More Access Running Commands webadmin.nsf allows an administrator to run server commands.
26 Getting More Access You can run O/S commands using load but can t see the results when using quick console. For some reason writing output to a web accessible directory didn t work on Linux Solution: upload a Notes database shell!
27 Introducing shell.nsf aka D99Shell You may get a certificate error after uploading..
28 D99Shell in action!
29 Also works on Windows servers
30 Demo: Breaking In! Oh Noez! U R demoin dis live!?!
31 Breaking in from the Inside - Objectives Find ID files on the network Crack passwords Get in to the NAB on the server Find ID files with higher levels of access Pw0nage!
32 Are Employees the Biggest Threat? Many breaches of security are done by insiders - Katherine Spanbauer, Domino senior product manager
33 Gaining A Toehold Since R5 you need an ID file to access the client ID file needs to be valid and not in a deny access group in the NAB. Shared directories FTW!
34 Gaining A Toehold It used to be hard to crack native Notes passwords! There are a number of products available to crack ID file passwords Huge thanks to Nataly at Passware * for the software being used in the following demo.. *
35 Demo: Notes ID Password Cracking I can haz beerz after, right?
36 We re going after the payroll Our freshly cracked ID file gives catalog.nsf & names.nsf access
37 Check the NAB (names.nsf) for group members Oops!
38 The result..
39 Client-side Tricks Spoofing mail.. Removing restrictions of local access LotusScript can access the Windows API! Declare Function GetClipboardData Lib "User32" (Byval wformat As Long) As Long
40 Mail spoofing; getting a payrise! SMTP mail can be easily spoofed using telnet but document properties are a dead giveaway
41 The Spoof Memo Form This is all that is required:
42 The result Create a new mail using the evil form and copy/paste it in to the mail.box database on the spoofed user s server The only giveaway.. Looks Good..
43 Local Access Protection Lotus Notes has an ACL setting to Enforce consistent ACL Opening a protected database locally gives an error like this: Not this ->
44 I Can t Access It Locally Eh! There are companies out there selling various unlock solutions Prices for software range from $49 to $657!! I ve tested a few versions of these life saving products.. One of them changed 4 bytes, another changed 6!
45 I Can t Access It Locally Eh! I mentioned to IBM in 2004 that you could change 1 byte to remove protection These apps are doing 75% too much work! Sorry guys, the secret s out: Changing 0x000002C4 from 20 to 00 could save $700!
46 Tool release Local Access Protection Deprotector And No Cash Expected
47 Tool release: lapdance Local Access Protection Deprotector And No Cash Expected (lapdance.pl) Written in Perl (badly), gives some info about the database and can add and remove protection Available from
48 Tool release: lapdance Local Access Protection Deprotector And No Cash Expected (lapdance.pl) Support for ODS versions 16, 17, 20, 41, 43, 48 and 51 (ie. everything from V2 to V8.5) Will display database protection and encryption flags information Can add and remove local access protection
49 Demo: Removing Database Protection! Ohalp! Prayrz 2 Ceilin Cat dat dis workz!
50 To Finish.. In this presentation I ll aim to give a general overview of Domino security and demonstrate ways of breaking in. This will cover security issues from the point of view of the web server, native Domino server and demonstrate some tricks you can use from the client side of things.
51
Penetration: from Application down to OS
 April 13, 2010 Penetration: from Application down to OS Getting OS Access Using Lotus Domino Application Server Vulnerabilities Digitаl Security Research Group (DSecRG) www.dsecrg.com Alexandr Polyakov.
April 13, 2010 Penetration: from Application down to OS Getting OS Access Using Lotus Domino Application Server Vulnerabilities Digitаl Security Research Group (DSecRG) www.dsecrg.com Alexandr Polyakov.
Lotus Domino Security
 An X-Force White Paper Lotus Domino Security December 2002 6303 Barfield Road Atlanta, GA 30328 Tel: 404.236.2600 Fax: 404.236.2626 Introduction Lotus Domino is an Application server that provides groupware
An X-Force White Paper Lotus Domino Security December 2002 6303 Barfield Road Atlanta, GA 30328 Tel: 404.236.2600 Fax: 404.236.2626 Introduction Lotus Domino is an Application server that provides groupware
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
Linux VPS with cpanel. Getting Started Guide
 Linux VPS with cpanel Getting Started Guide First Edition October 2010 Table of Contents Introduction...1 cpanel Documentation...1 Accessing your Server...2 cpanel Users...2 WHM Interface...3 cpanel Interface...3
Linux VPS with cpanel Getting Started Guide First Edition October 2010 Table of Contents Introduction...1 cpanel Documentation...1 Accessing your Server...2 cpanel Users...2 WHM Interface...3 cpanel Interface...3
DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014
 DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014 Contents Overview... 2 System requirements:... 2 Before installing... 3 Download and installation... 3 Configure DESLock+ Enterprise Server...
DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014 Contents Overview... 2 System requirements:... 2 Before installing... 3 Download and installation... 3 Configure DESLock+ Enterprise Server...
IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection
 IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection Description Lab flow At the end of this lab, you should be able to Discover how to harness the power and capabilities
IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection Description Lab flow At the end of this lab, you should be able to Discover how to harness the power and capabilities
EC-Council CAST CENTER FOR ADVANCED SECURITY TRAINING. CAST 619 Advanced SQLi Attacks and Countermeasures. Make The Difference CAST.
 CENTER FOR ADVANCED SECURITY TRAINING 619 Advanced SQLi Attacks and Countermeasures Make The Difference About Center of Advanced Security Training () The rapidly evolving information security landscape
CENTER FOR ADVANCED SECURITY TRAINING 619 Advanced SQLi Attacks and Countermeasures Make The Difference About Center of Advanced Security Training () The rapidly evolving information security landscape
Three Ways to Secure Virtual Applications
 WHITE PAPER Detect, Scan, Prioritize, and Remediate Vulnerabilities Table of Contents Subtitle 1 Headline 3 Headline 3 Sub-Headline 3 ConcIusion 3 About BeyondTrust 4 2 2013. BeyondTrust Software, Inc.
WHITE PAPER Detect, Scan, Prioritize, and Remediate Vulnerabilities Table of Contents Subtitle 1 Headline 3 Headline 3 Sub-Headline 3 ConcIusion 3 About BeyondTrust 4 2 2013. BeyondTrust Software, Inc.
Five Steps to Improve Internal Network Security. Chattanooga ISSA
 Five Steps to Improve Internal Network Security Chattanooga ISSA 1 Find Me AverageSecurityGuy.info @averagesecguy [email protected] github.com/averagesecurityguy ChattSec.org 2 Why? The methodical
Five Steps to Improve Internal Network Security Chattanooga ISSA 1 Find Me AverageSecurityGuy.info @averagesecguy [email protected] github.com/averagesecurityguy ChattSec.org 2 Why? The methodical
Overview of Network Security The need for network security Desirable security properties Common vulnerabilities Security policy designs
 Overview of Network Security The need for network security Desirable security properties Common vulnerabilities Security policy designs Why Network Security? Keep the bad guys out. (1) Closed networks
Overview of Network Security The need for network security Desirable security properties Common vulnerabilities Security policy designs Why Network Security? Keep the bad guys out. (1) Closed networks
INTEGRATION GUIDE. DIGIPASS Authentication for Google Apps using IDENTIKEY Federation Server
 INTEGRATION GUIDE DIGIPASS Authentication for Google Apps using IDENTIKEY Federation Server Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document
INTEGRATION GUIDE DIGIPASS Authentication for Google Apps using IDENTIKEY Federation Server Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document
The Top Web Application Attacks: Are you vulnerable?
 QM07 The Top Web Application Attacks: Are you vulnerable? John Burroughs, CISSP Sr Security Architect, Watchfire Solutions [email protected] Agenda Current State of Web Application Security Understanding
QM07 The Top Web Application Attacks: Are you vulnerable? John Burroughs, CISSP Sr Security Architect, Watchfire Solutions [email protected] Agenda Current State of Web Application Security Understanding
Plunder Pillage & Print
 Plunder Pillage & Print THE ART OF LEVERAGING MULTIFUNCTION PRINTERS DURING PENETRATION TESTING Deral Heiland [email protected] @Percent_x Pete Arzamendi [email protected] @TheBokojan Introduction
Plunder Pillage & Print THE ART OF LEVERAGING MULTIFUNCTION PRINTERS DURING PENETRATION TESTING Deral Heiland [email protected] @Percent_x Pete Arzamendi [email protected] @TheBokojan Introduction
GlobalSign Enterprise Solutions
 GlobalSign Enterprise Solutions Secure Email & Key Recovery Using GlobalSign s Auto Enrollment Gateway (AEG) 1 v.1.2 Table of Contents Table of Contents... 2 Introduction... 3 The Benefits of Secure Email...
GlobalSign Enterprise Solutions Secure Email & Key Recovery Using GlobalSign s Auto Enrollment Gateway (AEG) 1 v.1.2 Table of Contents Table of Contents... 2 Introduction... 3 The Benefits of Secure Email...
Email to Alfresco Folder
 Email to Alfresco Folder notes 009 Created 03/21/2011 T. Patrick Bailey Email to Alfresco Folder A lot of the notes from here are derived from http://wiki.alfresco.com/wiki/inbound_smtp_email_server_configur
Email to Alfresco Folder notes 009 Created 03/21/2011 T. Patrick Bailey Email to Alfresco Folder A lot of the notes from here are derived from http://wiki.alfresco.com/wiki/inbound_smtp_email_server_configur
IT HEALTHCHECK TOP TIPS WHITEPAPER
 WHITEPAPER PREPARED BY MTI TECHNOLOGY LTD w: mti.com t: 01483 520200 f: 01483 520222 MTI Technology have been specifying and conducting IT Healthcheck s across numerous sectors including commercial, public
WHITEPAPER PREPARED BY MTI TECHNOLOGY LTD w: mti.com t: 01483 520200 f: 01483 520222 MTI Technology have been specifying and conducting IT Healthcheck s across numerous sectors including commercial, public
Egress Switch Reader. User Guide 2.3
 Egress Switch Reader User Guide 2.3 November 2015 Confidentiality statement This document contains information confidential and proprietary to Egress Software Technologies. It shall not be disclosed in
Egress Switch Reader User Guide 2.3 November 2015 Confidentiality statement This document contains information confidential and proprietary to Egress Software Technologies. It shall not be disclosed in
WHMCS LUXCLOUD MODULE
 èè WHMCS LUXCLOUD MODULE Update: 02.02.2015 Version 2.0 This information is only valid for partners who use the WHMCS module (v2.0 and higher). 1.1 General overview 1.2 Installing the plugin Go to your
èè WHMCS LUXCLOUD MODULE Update: 02.02.2015 Version 2.0 This information is only valid for partners who use the WHMCS module (v2.0 and higher). 1.1 General overview 1.2 Installing the plugin Go to your
BlackBerry Business Cloud Services. Administration Guide
 BlackBerry Business Cloud Services Administration Guide Published: 2012-07-25 SWD-20120725193410416 Contents 1 About BlackBerry Business Cloud Services... 8 BlackBerry Business Cloud Services feature overview...
BlackBerry Business Cloud Services Administration Guide Published: 2012-07-25 SWD-20120725193410416 Contents 1 About BlackBerry Business Cloud Services... 8 BlackBerry Business Cloud Services feature overview...
Hack Your SQL Server Database Before the Hackers Do
 Note: This article was edited in Oct. 2013, from numerous Web Sources. TJS At the Install: The default install for SQL server makes it is as secure as it will ever be. DBAs and developers will eventually
Note: This article was edited in Oct. 2013, from numerous Web Sources. TJS At the Install: The default install for SQL server makes it is as secure as it will ever be. DBAs and developers will eventually
NotifyMDM Device Application User Guide Installation and Configuration for Windows Mobile 6 Devices
 NotifyMDM Device Application User Guide Installation and Configuration for Windows Mobile 6 Devices End-of-Life Notice Please note that GO!Enterprise MDM server version 3.6.3 is the last to officially
NotifyMDM Device Application User Guide Installation and Configuration for Windows Mobile 6 Devices End-of-Life Notice Please note that GO!Enterprise MDM server version 3.6.3 is the last to officially
Still Aren't Doing. Frank Kim
 Ten Things Web Developers Still Aren't Doing Frank Kim Think Security Consulting Background Frank Kim Consultant, Think Security Consulting Security in the SDLC SANS Author & Instructor DEV541 Secure Coding
Ten Things Web Developers Still Aren't Doing Frank Kim Think Security Consulting Background Frank Kim Consultant, Think Security Consulting Security in the SDLC SANS Author & Instructor DEV541 Secure Coding
Five Steps to Improve Internal Network Security. Chattanooga Information security Professionals
 Five Steps to Improve Internal Network Security Chattanooga Information security Professionals Who Am I? Security Analyst: Sword & Shield Blogger: averagesecurityguy.info Developer: github.com/averagesecurityguy
Five Steps to Improve Internal Network Security Chattanooga Information security Professionals Who Am I? Security Analyst: Sword & Shield Blogger: averagesecurityguy.info Developer: github.com/averagesecurityguy
INTEGRATION GUIDE. DIGIPASS Authentication for Salesforce using IDENTIKEY Federation Server
 INTEGRATION GUIDE DIGIPASS Authentication for Salesforce using IDENTIKEY Federation Server Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is
INTEGRATION GUIDE DIGIPASS Authentication for Salesforce using IDENTIKEY Federation Server Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is
Outlook 2010 Setup Guide (POP3)
 Versions Addressed: Microsoft Office Outlook 2010 Document Updated: 8/31/2012 Copyright 2012 Smarsh, Inc. All rights Purpose: This document will assist the end user in configuring Outlook 2010 to access
Versions Addressed: Microsoft Office Outlook 2010 Document Updated: 8/31/2012 Copyright 2012 Smarsh, Inc. All rights Purpose: This document will assist the end user in configuring Outlook 2010 to access
Xerox DocuShare Security Features. Security White Paper
 Xerox DocuShare Security Features Security White Paper Xerox DocuShare Security Features Businesses are increasingly concerned with protecting the security of their networks. Any application added to a
Xerox DocuShare Security Features Security White Paper Xerox DocuShare Security Features Businesses are increasingly concerned with protecting the security of their networks. Any application added to a
Centrify Cloud Connector Deployment Guide
 C E N T R I F Y D E P L O Y M E N T G U I D E Centrify Cloud Connector Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as
C E N T R I F Y D E P L O Y M E N T G U I D E Centrify Cloud Connector Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as
Open Mic on IBM Notes Traveler Best Practices. Date: 11 July, 2013
 Open Mic on IBM Notes Traveler Best Practices Date: 11 July, 2013 Open Mic Team Jayesh Parmar - IBM ICS Support engineer Presenter Shrikant Ahire - IBM ICS Support engineer Presenter Ranjit Rai - IBM ICS
Open Mic on IBM Notes Traveler Best Practices Date: 11 July, 2013 Open Mic Team Jayesh Parmar - IBM ICS Support engineer Presenter Shrikant Ahire - IBM ICS Support engineer Presenter Ranjit Rai - IBM ICS
GO!Enterprise MDM Device Application User Guide Installation and Configuration for Android with TouchDown
 GO!Enterprise MDM Device Application User Guide Installation and Configuration for Android with TouchDown GO!Enterprise MDM for Android, Version 3.x GO!Enterprise MDM for Android with TouchDown 1 Table
GO!Enterprise MDM Device Application User Guide Installation and Configuration for Android with TouchDown GO!Enterprise MDM for Android, Version 3.x GO!Enterprise MDM for Android with TouchDown 1 Table
VERALAB LDAP Configuration Guide
 VERALAB LDAP Configuration Guide VeraLab Suite is a client-server application and has two main components: a web-based application and a client software agent. Web-based application provides access to
VERALAB LDAP Configuration Guide VeraLab Suite is a client-server application and has two main components: a web-based application and a client software agent. Web-based application provides access to
Cloudwork Dashboard User Manual
 STUDENTNET Cloudwork Dashboard User Manual Make the Cloud Yours! Studentnet Technical Support 10/28/2015 User manual for the Cloudwork Dashboard introduced in January 2015 and updated in October 2015 with
STUDENTNET Cloudwork Dashboard User Manual Make the Cloud Yours! Studentnet Technical Support 10/28/2015 User manual for the Cloudwork Dashboard introduced in January 2015 and updated in October 2015 with
MS Enterprise Library 5.0 (Logging Application Block)
 International Journal of Scientific and Research Publications, Volume 4, Issue 8, August 2014 1 MS Enterprise Library 5.0 (Logging Application Block) Anubhav Tiwari * R&D Dept., Syscom Corporation Ltd.
International Journal of Scientific and Research Publications, Volume 4, Issue 8, August 2014 1 MS Enterprise Library 5.0 (Logging Application Block) Anubhav Tiwari * R&D Dept., Syscom Corporation Ltd.
How to Setup your E-mail Account -Apple Mail for Mac OS X 1- Open Mail
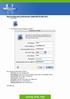 How to Setup your E-mail Account -Apple Mail for Mac OS X 1- Open Mail 2- The welcome screen will appear as follow: Fill in the above information as follow Full Name: type your display name E-Mail address:
How to Setup your E-mail Account -Apple Mail for Mac OS X 1- Open Mail 2- The welcome screen will appear as follow: Fill in the above information as follow Full Name: type your display name E-Mail address:
Livezilla How to Install on Shared Hosting http://www.jonathanmanning.com By: Jon Manning
 Livezilla How to Install on Shared Hosting By: Jon Manning This is an easy to follow tutorial on how to install Livezilla 3.2.0.2 live chat program on a linux shared hosting server using cpanel, linux
Livezilla How to Install on Shared Hosting By: Jon Manning This is an easy to follow tutorial on how to install Livezilla 3.2.0.2 live chat program on a linux shared hosting server using cpanel, linux
CHARTER BUSINESS custom hosting faqs 2010 INTERNET. Q. How do I access my email? Q. How do I change or reset a password for an email account?
 Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
Installing Certificates on Spectralink 8400 Handsets
 Introduction For the purposes of this document we will be showing you how to load certificates onto the Spectralink wireless telephone in a couple of different ways. We will start with the preferred method,
Introduction For the purposes of this document we will be showing you how to load certificates onto the Spectralink wireless telephone in a couple of different ways. We will start with the preferred method,
Pentesting for fun... and profit! David M. N. Bryan and Rob Havelt
 Pentesting for fun... and profit! David M. N. Bryan and Rob Havelt Agenda Who are David & Rob? Why are we experts? Why do penetration tests? What is a penetration test? What is the goal? Some says it s
Pentesting for fun... and profit! David M. N. Bryan and Rob Havelt Agenda Who are David & Rob? Why are we experts? Why do penetration tests? What is a penetration test? What is the goal? Some says it s
STABLE & SECURE BANK lab writeup. Page 1 of 21
 STABLE & SECURE BANK lab writeup 1 of 21 Penetrating an imaginary bank through real present-date security vulnerabilities PENTESTIT, a Russian Information Security company has launched its new, eighth
STABLE & SECURE BANK lab writeup 1 of 21 Penetrating an imaginary bank through real present-date security vulnerabilities PENTESTIT, a Russian Information Security company has launched its new, eighth
How to configure the TopCloudXL WHMCS plugin (version 2+) Update: 16-09-2015 Version: 2.2
 èè How to configure the TopCloudXL WHMCS plugin (version 2+) Update: 16-09-2015 Version: 2.2 Table of Contents 1. General overview... 3 1.1. Installing the plugin... 3 1.2. Testing the plugin with the
èè How to configure the TopCloudXL WHMCS plugin (version 2+) Update: 16-09-2015 Version: 2.2 Table of Contents 1. General overview... 3 1.1. Installing the plugin... 3 1.2. Testing the plugin with the
DESlock+ Basic Setup Guide ENTERPRISE SERVER ESSENTIAL/STANDARD/PRO
 DESlock+ Basic Setup Guide ENTERPRISE SERVER ESSENTIAL/STANDARD/PRO Contents Overview...1 System requirements...1 Enterprise Server:...1 Client PCs:...1 Section 1: Before installing...1 Section 2: Download
DESlock+ Basic Setup Guide ENTERPRISE SERVER ESSENTIAL/STANDARD/PRO Contents Overview...1 System requirements...1 Enterprise Server:...1 Client PCs:...1 Section 1: Before installing...1 Section 2: Download
Terms you ll need to understand:
 14 Managing Servers............................................... Terms you ll need to understand: Transaction logging Activity logging Policy documents Administrator access Network names Directory deployment
14 Managing Servers............................................... Terms you ll need to understand: Transaction logging Activity logging Policy documents Administrator access Network names Directory deployment
Administration Guide. . All right reserved. For more information about Specops Password Sync and other Specops products, visit www.specopssoft.
 Administration Guide. All right reserved. For more information about Specops Password Sync and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Password Sync is a trademark
Administration Guide. All right reserved. For more information about Specops Password Sync and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Password Sync is a trademark
RoomWizard Synchronization Software Manual Installation Instructions
 2 RoomWizard Synchronization Software Manual Installation Instructions Table of Contents Exchange Server Configuration... 4 RoomWizard Synchronization Software Installation and Configuration... 5 System
2 RoomWizard Synchronization Software Manual Installation Instructions Table of Contents Exchange Server Configuration... 4 RoomWizard Synchronization Software Installation and Configuration... 5 System
Unifying Information Security. Implementing TLS on the CLEARSWIFT SECURE Email Gateway
 Unifying Information Security Implementing TLS on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 3 2 Understanding TLS... 4 3 Clearswift s Application of TLS... 5 3.1 Opportunistic TLS...
Unifying Information Security Implementing TLS on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 3 2 Understanding TLS... 4 3 Clearswift s Application of TLS... 5 3.1 Opportunistic TLS...
EVERYTHING LDAP. Gabriella Davis [email protected]
 EVERYTHING LDAP Gabriella Davis [email protected] Agenda What is LDAP? LDAP structure and behavior Domino and LDAP LDAP tools Notes as an LDAP client IBM Lotus Sametime, Quickr, Connections,
EVERYTHING LDAP Gabriella Davis [email protected] Agenda What is LDAP? LDAP structure and behavior Domino and LDAP LDAP tools Notes as an LDAP client IBM Lotus Sametime, Quickr, Connections,
How to configure your email client
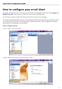 How to configure your email client This guide will teach you how to set up your email client. In this guide we will cover both Outlook and Windows Live mail, which are two of the major email clients used
How to configure your email client This guide will teach you how to set up your email client. In this guide we will cover both Outlook and Windows Live mail, which are two of the major email clients used
Acano solution. Security Considerations. August 2015 76-1026-01-E
 Acano solution Security Considerations August 2015 76-1026-01-E Contents Contents 1 Introduction... 3 2 Acano Secure Development Lifecycle... 3 3 Acano Security Points... 4 Acano solution: Security Consideration
Acano solution Security Considerations August 2015 76-1026-01-E Contents Contents 1 Introduction... 3 2 Acano Secure Development Lifecycle... 3 3 Acano Security Points... 4 Acano solution: Security Consideration
SY0-201. system so that an unauthorized individual can take over an authorized session, or to disrupt service to authorized users.
 system so that an unauthorized individual can take over an authorized session, or to disrupt service to authorized users. From a high-level standpoint, attacks on computer systems and networks can be grouped
system so that an unauthorized individual can take over an authorized session, or to disrupt service to authorized users. From a high-level standpoint, attacks on computer systems and networks can be grouped
Passcape Software. DPAPI flaw. Vulnerability of DPAPI data protection in Win2K, Win2K3, Windows Server 2008, and Windows Server 2012
 DPAPI flaw Vulnerability of DPAPI data protection in Win2K, Win2K3, Windows Server 2008, and Windows Server 2012 Content 1 Brief description of the vulnerability 2 1.1 The... problem 2 1.2 Affected...
DPAPI flaw Vulnerability of DPAPI data protection in Win2K, Win2K3, Windows Server 2008, and Windows Server 2012 Content 1 Brief description of the vulnerability 2 1.1 The... problem 2 1.2 Affected...
Quick Start Policy Patrol Disclaimers 10
 Quick Start Policy Patrol Disclaimers 10 This guide will help you start using Policy Patrol Disclaimers as quickly as possible. For more detailed instructions, consult the Policy Patrol manual. Step 1.
Quick Start Policy Patrol Disclaimers 10 This guide will help you start using Policy Patrol Disclaimers as quickly as possible. For more detailed instructions, consult the Policy Patrol manual. Step 1.
Anatomy of an ethical penetration test
 toolsmith Core Impact 6.2: Anatomy of an ethical penetration test By Russ McRee Prerequisites CORE IMPACT is lean and can run on minimal systems with limited resources and requires either Windows 2000
toolsmith Core Impact 6.2: Anatomy of an ethical penetration test By Russ McRee Prerequisites CORE IMPACT is lean and can run on minimal systems with limited resources and requires either Windows 2000
How To Send Mail From A Macbook Access To A Pc Or Ipad With A Password Protected Email Address (Monroe Access) On A Pc (For Macbook) Or Ipa (For Ipa) On Pc Or Macbook (For
 Email client settings: Incoming Mail (IMAP) Server requires SSL: Outgoing Mail (SMTP) Server requires TLS or SSL: Account Name: Email Address: Password: imap.gmail.com Use SSL: Yes Port: 993 smtp.gmail.com
Email client settings: Incoming Mail (IMAP) Server requires SSL: Outgoing Mail (SMTP) Server requires TLS or SSL: Account Name: Email Address: Password: imap.gmail.com Use SSL: Yes Port: 993 smtp.gmail.com
CMT for Notes. Installation Guide
 CMT for Notes Installation Guide October 2014 Table of Contents CMT for Notes Install Instructions... 3 Environment for an Exchange Server-to-Server Migration... 3 Operating System and Software Requirements
CMT for Notes Installation Guide October 2014 Table of Contents CMT for Notes Install Instructions... 3 Environment for an Exchange Server-to-Server Migration... 3 Operating System and Software Requirements
Security Awareness For Server Administrators. State of Illinois Central Management Services Security and Compliance Solutions
 Security Awareness For Server Administrators State of Illinois Central Management Services Security and Compliance Solutions Purpose and Scope To present a best practice approach to securing your servers
Security Awareness For Server Administrators State of Illinois Central Management Services Security and Compliance Solutions Purpose and Scope To present a best practice approach to securing your servers
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail
 Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
GO!Enterprise MDM Device Application User Guide Installation and Configuration for BlackBerry
 GO!Enterprise MDM Device Application User Guide Installation and Configuration for BlackBerry GO!Enterprise MDM Version 4.11.x GO!Enterprise MDM for BlackBerry 1 Table of Contents GO!Enterprise MDM for
GO!Enterprise MDM Device Application User Guide Installation and Configuration for BlackBerry GO!Enterprise MDM Version 4.11.x GO!Enterprise MDM for BlackBerry 1 Table of Contents GO!Enterprise MDM for
Web Engineering Web Application Security Issues
 Security Issues Dec 14 2009 Katharina Siorpaes Copyright 2009 STI - INNSBRUCK www.sti-innsbruck.at It is NOT Network Security It is securing: Custom Code that drives a web application Libraries Backend
Security Issues Dec 14 2009 Katharina Siorpaes Copyright 2009 STI - INNSBRUCK www.sti-innsbruck.at It is NOT Network Security It is securing: Custom Code that drives a web application Libraries Backend
Penetration Testing Walkthrough
 Penetration Testing Walkthrough Table of Contents Penetration Testing Walkthrough... 3 Practical Walkthrough of Phases 2-5... 4 Chose Tool BackTrack (Armitage)... 5 Choose Target... 6 Phase 2 - Basic Scan...
Penetration Testing Walkthrough Table of Contents Penetration Testing Walkthrough... 3 Practical Walkthrough of Phases 2-5... 4 Chose Tool BackTrack (Armitage)... 5 Choose Target... 6 Phase 2 - Basic Scan...
With Great Power comes Great Responsibility: Managing Privileged Users
 With Great Power comes Great Responsibility: Managing Privileged Users Darren Harmer Senior Systems Engineer Agenda What is a Privileged User Privileged User Why is it important? Security Intelligence
With Great Power comes Great Responsibility: Managing Privileged Users Darren Harmer Senior Systems Engineer Agenda What is a Privileged User Privileged User Why is it important? Security Intelligence
Exploiting Transparent User Identification Systems
 Exploiting Transparent User Identification Systems Wayne Murphy Benjamin Burns Version 1.0a 1 CONTENTS 1.0 Introduction... 3 1.1 Project Objectives... 3 2.0 Brief Summary of Findings... 4 3.0 Background
Exploiting Transparent User Identification Systems Wayne Murphy Benjamin Burns Version 1.0a 1 CONTENTS 1.0 Introduction... 3 1.1 Project Objectives... 3 2.0 Brief Summary of Findings... 4 3.0 Background
AD Self Password Reset Installation and configuration
 AD Self Password Reset Installation and configuration AD Self Password Reset Installation 1 Manual v1.4 Table of Contents TABLE OF CONTENTS 2 SUMMARY 3 INSTALLATION 4 REMOVAL 6 AD SELF PASSWORD RESET CONFIGURATION
AD Self Password Reset Installation and configuration AD Self Password Reset Installation 1 Manual v1.4 Table of Contents TABLE OF CONTENTS 2 SUMMARY 3 INSTALLATION 4 REMOVAL 6 AD SELF PASSWORD RESET CONFIGURATION
Hackproofing Lotus Domino Web Server
 A NGSSoftware Insight Security Research Publication Hackproofing Lotus Domino Web Server David Litchfield ([email protected]) 21st October 2001 www.nextgenss.com 1 Introduction Brief This document describes
A NGSSoftware Insight Security Research Publication Hackproofing Lotus Domino Web Server David Litchfield ([email protected]) 21st October 2001 www.nextgenss.com 1 Introduction Brief This document describes
User Guide. DocAve Lotus Notes Migrator for Microsoft Exchange 1.1. Using the DocAve Notes Migrator for Exchange to Perform a Basic Migration
 User Guide DocAve Lotus Notes Migrator for Microsoft Exchange 1.1 Using the DocAve Notes Migrator for Exchange to Perform a Basic Migration This document is intended for anyone wishing to familiarize themselves
User Guide DocAve Lotus Notes Migrator for Microsoft Exchange 1.1 Using the DocAve Notes Migrator for Exchange to Perform a Basic Migration This document is intended for anyone wishing to familiarize themselves
User Guide for the VersaMail Application
 User Guide for the VersaMail Application Copyright and Trademark 2004 palmone, Inc. All rights reserved. palmone, HotSync, the HotSync logo, Palm, Palm OS, the Palm logo, and VersaMail are among the trademarks
User Guide for the VersaMail Application Copyright and Trademark 2004 palmone, Inc. All rights reserved. palmone, HotSync, the HotSync logo, Palm, Palm OS, the Palm logo, and VersaMail are among the trademarks
Articles Fighting SPAM in Lotus Domino
 Page 1 of 5 Articles Fighting SPAM in Lotus Domino For many e-mail administrators these days, the number one complaint from the users and managers is unsolicited emails flooding the system, commonly called
Page 1 of 5 Articles Fighting SPAM in Lotus Domino For many e-mail administrators these days, the number one complaint from the users and managers is unsolicited emails flooding the system, commonly called
Why Should You Care About Security Issues? SySmox WEB security [email protected]. Top seven ColdFusion Security Issues
 SySmox WEB security [email protected] Top seven ColdFusion Security Issues This installment discusses the most prevalent security issues with server configurations and application implementations for ColdFusion.
SySmox WEB security [email protected] Top seven ColdFusion Security Issues This installment discusses the most prevalent security issues with server configurations and application implementations for ColdFusion.
Cryoserver Archive Lotus Notes Configuration
 Lotus Notes Configuration Version 1.0 December 2007 Forensic & Compliance Systems Ltd +44 (0)800 280 0525 [email protected] www.cryoserver.com Contents INTRODUCTION... 3 SMTP ROUTING TO CRYOSERVER...
Lotus Notes Configuration Version 1.0 December 2007 Forensic & Compliance Systems Ltd +44 (0)800 280 0525 [email protected] www.cryoserver.com Contents INTRODUCTION... 3 SMTP ROUTING TO CRYOSERVER...
Today s Topics. Protect - Detect - Respond A Security-First Strategy. HCCA Compliance Institute April 27, 2009. Concepts.
 Protect - Detect - Respond A Security-First Strategy HCCA Compliance Institute April 27, 2009 1 Today s Topics Concepts Case Study Sound Security Strategy 2 1 Security = Culture!! Security is a BUSINESS
Protect - Detect - Respond A Security-First Strategy HCCA Compliance Institute April 27, 2009 1 Today s Topics Concepts Case Study Sound Security Strategy 2 1 Security = Culture!! Security is a BUSINESS
How Reflection Software Facilitates PCI DSS Compliance
 Reflection How Reflection Software Facilitates PCI DSS Compliance How Reflection Software Facilitates PCI DSS Compliance How Reflection Software Facilitates PCI DSS Compliance In 2004, the major credit
Reflection How Reflection Software Facilitates PCI DSS Compliance How Reflection Software Facilitates PCI DSS Compliance How Reflection Software Facilitates PCI DSS Compliance In 2004, the major credit
The Security of MDM systems. Hack In Paris 2013 Sebastien Andrivet
 The Security of MDM systems Hack In Paris 2013 Sebastien Andrivet Who am I? Sebastien Andrivet Switzerland (Geneva) Specialized in security Mobiles (ios, Android) Forensic Developer C++, x86 and ARM (Cyberfeminist
The Security of MDM systems Hack In Paris 2013 Sebastien Andrivet Who am I? Sebastien Andrivet Switzerland (Geneva) Specialized in security Mobiles (ios, Android) Forensic Developer C++, x86 and ARM (Cyberfeminist
Computer Security: Principles and Practice
 Computer Security: Principles and Practice Chapter 24 Windows and Windows Vista Security First Edition by William Stallings and Lawrie Brown Lecture slides by Lawrie Brown Windows and Windows Vista Security
Computer Security: Principles and Practice Chapter 24 Windows and Windows Vista Security First Edition by William Stallings and Lawrie Brown Lecture slides by Lawrie Brown Windows and Windows Vista Security
Configuring MailArchiva with Insight Server
 Copyright 2009 Bynari Inc., All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopy, recording, or any
Copyright 2009 Bynari Inc., All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopy, recording, or any
Network Security - ISA 656 Email Security
 Network Security - ISA 656 Angelos Stavrou November 13, 2007 The Usual Questions The Usual Questions Assets What are we trying to protect? Against whom? 2 / 33 Assets The Usual Questions Assets Confidentiality
Network Security - ISA 656 Angelos Stavrou November 13, 2007 The Usual Questions The Usual Questions Assets What are we trying to protect? Against whom? 2 / 33 Assets The Usual Questions Assets Confidentiality
mkryptor allows you to easily send secure emails. This document will give you a technical overview of how. mkryptor is a software product from
 Technical Overview mkryptor allows you to easily send secure emails. This document will give you a technical overview of how. mkryptor is a software product from Contents What is mkryptor? 1 Mkryptor VS
Technical Overview mkryptor allows you to easily send secure emails. This document will give you a technical overview of how. mkryptor is a software product from Contents What is mkryptor? 1 Mkryptor VS
Host Hardening. Presented by. Douglas Couch & Nathan Heck Security Analysts for ITaP 1
 Host Hardening Presented by Douglas Couch & Nathan Heck Security Analysts for ITaP 1 Background National Institute of Standards and Technology Draft Guide to General Server Security SP800-123 Server A
Host Hardening Presented by Douglas Couch & Nathan Heck Security Analysts for ITaP 1 Background National Institute of Standards and Technology Draft Guide to General Server Security SP800-123 Server A
IceWarp to IceWarp Server Migration
 IceWarp to IceWarp Server Migration Registered Trademarks iphone, ipad, Mac, OS X are trademarks of Apple Inc., registered in the U.S. and other countries. Microsoft, Windows, Outlook and Windows Phone
IceWarp to IceWarp Server Migration Registered Trademarks iphone, ipad, Mac, OS X are trademarks of Apple Inc., registered in the U.S. and other countries. Microsoft, Windows, Outlook and Windows Phone
IBM Lotus Protector for Mail Encryption. User's Guide
 IBM Lotus Protector for Mail Encryption User's Guide Version Information Lotus Protector for Mail Encryption User's Guide. Lotus Protector for Mail Encryption Version 2.1.0. Released December 2010. This
IBM Lotus Protector for Mail Encryption User's Guide Version Information Lotus Protector for Mail Encryption User's Guide. Lotus Protector for Mail Encryption Version 2.1.0. Released December 2010. This
Critical Issues with Lotus Notes and Domino 8.5 Password Authentication, Security and Management
 Security Comparison Critical Issues with Lotus Notes and Domino 8.5 Password Authentication, Security and Management PistolStar, Inc. PO Box 1226 Amherst, NH 03031 USA Phone: 603.547.1200 Fax: 603.546.2309
Security Comparison Critical Issues with Lotus Notes and Domino 8.5 Password Authentication, Security and Management PistolStar, Inc. PO Box 1226 Amherst, NH 03031 USA Phone: 603.547.1200 Fax: 603.546.2309
SSL for VM: The Hard Way and the Easy Way
 SSL for VM: The Hard Way and the Easy Way David Boyes 2007 Agenda Overview of SSL and the VM Implementation Setup Steps for a DIY Version SSL Enabler, aka the Easy Way A Little Bit About Clients Q&A What
SSL for VM: The Hard Way and the Easy Way David Boyes 2007 Agenda Overview of SSL and the VM Implementation Setup Steps for a DIY Version SSL Enabler, aka the Easy Way A Little Bit About Clients Q&A What
Nevepoint Access Manager 1.2 BETA Documentation
 Nevepoint Access Manager 1.2 BETA Documentation Table of Contents Installation...3 Locating the Installation Wizard URL...3 Step 1: Configure the Administrator...4 Step 2: Connecting to Primary Connector...4
Nevepoint Access Manager 1.2 BETA Documentation Table of Contents Installation...3 Locating the Installation Wizard URL...3 Step 1: Configure the Administrator...4 Step 2: Connecting to Primary Connector...4
Upgrading, Integrating, and Troubleshooting Exchange Server 2003 in Mixed Environments
 3 Upgrading, Integrating, and Troubleshooting Exchange Server 2003 in Mixed Environments............................................... Terms you ll need to understand: Domain controller Global catalog
3 Upgrading, Integrating, and Troubleshooting Exchange Server 2003 in Mixed Environments............................................... Terms you ll need to understand: Domain controller Global catalog
Analyzing the Security Schemes of Various Cloud Storage Services
 Analyzing the Security Schemes of Various Cloud Storage Services ECE 646 Project Presentation Fall 2014 12/09/2014 Team Members Ankita Pandey Gagandeep Singh Bamrah Pros and Cons of Cloud Storage Services
Analyzing the Security Schemes of Various Cloud Storage Services ECE 646 Project Presentation Fall 2014 12/09/2014 Team Members Ankita Pandey Gagandeep Singh Bamrah Pros and Cons of Cloud Storage Services
Lepide Active Directory Self Service. Configuration Guide. Follow the simple steps given in this document to start working with
 Lepide Active Directory Self Service Configuration Guide 2014 Follow the simple steps given in this document to start working with Lepide Active Directory Self Service Table of Contents 1. Introduction...3
Lepide Active Directory Self Service Configuration Guide 2014 Follow the simple steps given in this document to start working with Lepide Active Directory Self Service Table of Contents 1. Introduction...3
Populating Your Domino Directory (Or ANY Domino Database) With Tivoli Directory Integrator. Marie Scott Thomas Duffbert Duff
 Populating Your Domino Directory (Or ANY Domino Database) With Tivoli Directory Integrator Marie Scott Thomas Duffbert Duff Agenda Introduction to TDI architecture/concepts Discuss TDI entitlement Examples
Populating Your Domino Directory (Or ANY Domino Database) With Tivoli Directory Integrator Marie Scott Thomas Duffbert Duff Agenda Introduction to TDI architecture/concepts Discuss TDI entitlement Examples
Web Application Security
 Chapter 1 Web Application Security In this chapter: OWASP Top 10..........................................................2 General Principles to Live By.............................................. 4
Chapter 1 Web Application Security In this chapter: OWASP Top 10..........................................................2 General Principles to Live By.............................................. 4
Cloud Server powered by Mac OS X. Getting Started Guide. Cloud Server. powered by Mac OS X. AKJZNAzsqknsxxkjnsjx Getting Started Guide Page 1
 Getting Started Guide Cloud Server powered by Mac OS X Getting Started Guide Page 1 Getting Started Guide: Cloud Server powered by Mac OS X Version 1.0 (02.16.10) Copyright 2010 GoDaddy.com Software, Inc.
Getting Started Guide Cloud Server powered by Mac OS X Getting Started Guide Page 1 Getting Started Guide: Cloud Server powered by Mac OS X Version 1.0 (02.16.10) Copyright 2010 GoDaddy.com Software, Inc.
How to Pop Email to Outlook
 Webmail Access How to Pop Email to Outlook You can access your email account through the following URL: http://webmail.usalocalbiz.com. The login is your full email address and your account password. We
Webmail Access How to Pop Email to Outlook You can access your email account through the following URL: http://webmail.usalocalbiz.com. The login is your full email address and your account password. We
GO!Enterprise MDM Device Application User Guide Installation and Configuration for ios with TouchDown
 GO!Enterprise MDM Device Application User Guide Installation and Configuration for ios with TouchDown GO!Enterprise MDM for ios Devices, Version 3.x GO!Enterprise MDM for ios with TouchDown 1 Table of
GO!Enterprise MDM Device Application User Guide Installation and Configuration for ios with TouchDown GO!Enterprise MDM for ios Devices, Version 3.x GO!Enterprise MDM for ios with TouchDown 1 Table of
SecureVault Online Backup Service FAQ
 SecureVault Online Backup Service FAQ C0110 SecureVault FAQ (EN) - 1 - Rev. 19-Nov-2007 Table of Contents 1. General 4 Q1. Can I exchange the client type between SecureVault PC Backup Manager and SecureVault
SecureVault Online Backup Service FAQ C0110 SecureVault FAQ (EN) - 1 - Rev. 19-Nov-2007 Table of Contents 1. General 4 Q1. Can I exchange the client type between SecureVault PC Backup Manager and SecureVault
Professional Penetration Testing Techniques and Vulnerability Assessment ...
 Course Introduction Today Hackers are everywhere, if your corporate system connects to internet that means your system might be facing with hacker. This five days course Professional Vulnerability Assessment
Course Introduction Today Hackers are everywhere, if your corporate system connects to internet that means your system might be facing with hacker. This five days course Professional Vulnerability Assessment
Email Update Instructions
 1 Email Update Instructions Contents Email Client Settings The Basics... 3 Outlook 2013... 4 Outlook 2007... 6 Outlook Express... 7 Windows Mail... 8 Thunderbird 3... 9 Apple Mail... 10 2 Email Client
1 Email Update Instructions Contents Email Client Settings The Basics... 3 Outlook 2013... 4 Outlook 2007... 6 Outlook Express... 7 Windows Mail... 8 Thunderbird 3... 9 Apple Mail... 10 2 Email Client
DIRECTORY PASSWORD V1.2 Quick Start Guide
 DIRECTORY PASSWORD V1.2 Quick Start Guide Directory Password is a self-service password reset / account unlock tool that is an optional add-on for Directory Update v2.5. Directory Update must be installed
DIRECTORY PASSWORD V1.2 Quick Start Guide Directory Password is a self-service password reset / account unlock tool that is an optional add-on for Directory Update v2.5. Directory Update must be installed
QTEL MOBILE EMAIL CORPORATE EDITION
 QTEL MOBILE EMAIL CORPORATE EDITION Overview With Qtel Mobile Email Corporate Edition, you ve got a secure, easy mobile email solution you can deploy across your entire organization, keeping your employees
QTEL MOBILE EMAIL CORPORATE EDITION Overview With Qtel Mobile Email Corporate Edition, you ve got a secure, easy mobile email solution you can deploy across your entire organization, keeping your employees
