User Authentication Platform using Provisioning in Cloud Computing Environment
|
|
|
- Bryan Rodgers
- 8 years ago
- Views:
Transcription
1 User Authentication Platform using Provisioning in Cloud Computing Environment Hyosik Ahn, Hyokyung Chang, Changbok Jang, Euiin Choi Dept. Of Computer Engineering, Hannam University, Daejeon, Korea {hsahn, hkjang, Abstract. Cloud computing is a computing environment centered on users and can use programs or documents stored respectivily in servers by operating an applied software such as Web browser through diverse devices on where users can access Internet as an on-demand outsourcing service of IT resources using Internet. In order to use these cloud computing service, a user authentication is needed. This paper proposed the platform for user authentication using provisioning in Cloud computing environment. Keywords: Cloud Computing, User Authentication, Provisioning, Security 1 Introduction Gartner announced Top 10 of IT strategy technologies of the year of 2010 in 2009, October. Strategy technologies Gartner mentioned are the technologies which importantly affect enterprises for the next 3 years and have a powerful effect on IT and business. They may affect long-term plans, programs, and major projects of enterprises and help enterprises get strategic advantages if enterprises adopt them a head start. Cloud Computing got the top rank (2nd rank in 2009)[1][2]. Cloud Computing is a model of performance business and also infrastructure management methodology. It lets users use hardware, software and network resources as much as possible so as to provide innovative services through Web in these business performance models and also enables to provision a server according to needs of the logical by using automated advanced tools[3][4]. Also, Cloud Computing models offer both users and IT managers user interface which helps manage provisioned resources easy through the entire life cycle of a service request[5][6]. When resources requested by the user arrives through Cloud, the user can track the order consisted of a certain number of servers and software and operate jobs such as checking the state of the resources provided, adding a server, changing the installed software, removing a server, increasing or decreasing allocated processing power and memory or storage, even starting, aborting, and restarting server[7]. Corresponding Author
2 However, the diffusion of cloud computing incites users desires for more improved, faster and more secure service delivery. Hence, security issues in the Cloud Computing environment are constantly emerging and authentication and access control has been studying. A user in the Cloud Computing environment has to complete the personal authentication process required by the service provider whenever using a new Cloud service. In this process, in the case that the characteristic and safety have been invaded by any attack, there will be a severe damage because personal information stored in the database and business processing service have been exposed or information related to individuals or organizations will be exposed as well. Therefore, this paper designs a platform for user authentication using provisioning in the Cloud Computing environment. 2 Related Works 2.1 Definition of Cloud computing and the Appearance Background Cloud Computing is a kind of on-demand computing method that lets users use IT resources such as network, server, storage, service, application, and so on via Internet when needing them rather than owning them[5]. Cloud Computing can be considered as a sum of SaaS (Software as a Service) and utility computing and Figure 1 shows the roles of users or providers in the Cloud Computing under the concept[9]. Figure 1. Users and Providers of Cloud Computing 2.2 Provisioning Provisioning is a procedure and behavior that prepares required knowledge in advance and provides by requests in order to find the best thing. That is, it allocates, deploys,
3 and distributes infrastructure resources to meet the needs of users or business and helps use the resources in the system[9]. Server Resources Provisioning: prepares resources like the CPU of the server and memory by allocating and placing the resources appropriately OS Provisioning: prepares OS operative by installing OS in the server and configuring tasks Software Provisioning: prepares to operate by installing/distributing Software(WAS, DBMS, Application, etc.) in the system and doing configuration settings needed Storage Provisioning: enables to identify wasted or unused storage and put it into a common pool. If there is a request of storage since then, the administrator gets one out of the pool and uses. Possible to construct infrastructure to heighten the efficiency of storage Account Provisioning: the process that HR manager and IT manager take the appropriate approval process and then generate accounts needed for various applications such as . groupware, ERP, etc. or change the access authorities when the category of the resources that users access changes[10] Figure 2 shows such a provisioning service. Figure 2. Provisioning Service 2.3 Security Technology in the Cloud computing Environment There are no concrete security technologies in Cloud Computing, however, if we regard Cloud Computing as an extension of the existing IT technologies, it is possible to divide some of them by each component of Cloud Computing and apply to[12]. Access control and user authentication are representative as security technologies used for platforms. Access control is the technology that controls a process in the operating system not to approach the area of another process. There are DAC
4 (Discretionary Access Control), MAC (Media Access Control), and RBAC (Role- Based Access Control). DAC helps a user establish the access authority to the resources that he/she owns as he/she pleases. MAC establishes the vertical/horizontal access rules in the system at the standard of security level and area for the resources and uses them. RBAC gives an access authority to a user group based on the role the user group plays in the organization, not to a user. RBAC is widely used because it is fit for the commercial organizations. Technologies used to authenticate a user are Id/password, Public Key Infrastructure, multi-factor authentication, SSO (Single Sign On), MTM (Mobile Trusted Module), and i-pin[11]. 3 User Authentication in the Cloud computing Environment 3.1 User Authentication Technology in the Cloud computing Environment Users in the Cloud Computing environment have to complete the user authentication process required by the service provider whenever they use new Cloud service. Generally a user registers with offering personal information and a service provider provides a user s own ID (identification) and an authentication method for user authentication after a registration is done. Then the user uses the ID and the authentication method to operate the user authentication when the user accesses to use a Cloud Computing service[13]. Unfortunately, there is a possibility that the characteristics and safety of authentication method can be invaded by an attack during the process of authentication, and then it could cause severe damages. Hence, there must be not only security but also interoperability for user authentication of Cloud Computing. 3.2 Weakness of User Authentication Technology in Cloud computing The representative user authentication security technologies described above have some weaknesses[11][12]. Id/password: the representative user authentication method. It is simple and easy to use, but it has to have a certain level of complication and regular renewal to keep the security. PKI(Public Key Infrastructure): an authentication means using a public-key cryptography. It enables to authenticate the other party based on the certificate without shared secret information. In PKI structure, it is impossible to manage and inspect the process of client side. Multi-factor: a method to heighten the security intensity by combining a few means of authentication. Id, password, biometrics like fingerprint and iris, certificate, OTP (One Tome Pad), etc. are used. OTP information as well as Id/password can be disclosed to an attacker.
5 SSO (Single Sign On): a kind of passport if it gets authentication from a site, then it can go through to other sites with assertion and has no authentication process. The representative standard of assertion is SAML. MTM (Mobile Trusted Module): a hardware-based security module. It is a proposed standard by TCG (Trusted Computing Group) which Nokia, Samsung, France Telecom, Ericson, etc. take part in. It is mainly applied to authenticate terminals from telecommunications, however, it is being considered as a Cloud Computing authentication method with SIM (Subscriber Identity Module) because of generalization of smartphone[15]. i-pin: a technique to use to confirm a user s identification when the user uses Internet in Korea now. It operates in a way that the organization which itself performed the identification of the user issues the assertion. 4 Platform Design for user authentication using Provisioning in Cloud Computing Environment 4.1 User Authentication using Provisioning User authentication platform using provisioning first authenticates by using ID/Password, PKI, SSO, etc. which a user input. Second, it authenticates with Authentication Manager through the user profile and patterns and stores the changes of the state via Monitor. When using Cloud Computing services, to solve the inconvenience of user authentication, user s information is stored in the User Information. Figure 3 shows a conceptual architecture. Figure 3. Conceptual Architecture
6 For user authentication, Authentication Module has the previous user profile and log data record by Provisioning strategy. 4.2 Design of User Authentication Platform Using Provisioning Figure 4 shows the composition of User authentication platform using provisioning proposed in this paper. Figure 4. Authentication Platform To authenticate a user first, Analyzer analyzes information such as ID/Password, Time, Position, Place, etc. it analyzes user pattern by using Rules for user authentication. To analyze user pattern, it authenticates a user by analyzing with current status and Rules of Profile DB. Profile DB stores user profile like existing user login time, location, position, etc. Also, it monitors the changes of user s status and situations via Status Monitor, records them in the database, and puts user information into User Information. That is how the user authentication process which the service provider asks to users whenever they use Cloud Computing services. 5 Conclusions In this paper, user authentication platform using Provisioning in Cloud Computing environment was proposed and the features of this proposal are as follows. There is some troublesome for users to get user authentication in the existing Cloud Computing environment because they have to go through the user authentication process to use the service every single time by using an ID and authentication method that the service provider provided. So, user authentication platform using Provisioning solves the existing inconvenience and helps use Cloud Computing services easily.
7 The proposed platform architecture analyzes user information and authenticates a user through user profile. Also, it has user information stored through user monitoring and there is an advantage that the user authentication process required by the service provider can be omitted when using other Cloud Computing services. As further study, there should be a study on protection of user information, which is profile and log data in the platform proposed by this paper. Acknowledgments. This work was supported by the Security Engineering Research Center, granted by the Korea Ministry of Knowledge Economy References 1. Lee, T.: Features of Cloud Computing and Offered Service State by Individual Vender. In: Broadcasting and Communication Policy, vol. 22, pp (2000) Lee, J., Choi, D.: New trend of IT led by Cloud Computing. In: LG Economic Research Institute, (2010) 4. Lee, H., Chung, M.: Context-Aware Security for Cloud Computing Environment. In: IEEK, vol. 47, pp (2010) 5. Kim, J., Kim, H.: Cloud Computing Industry Trend and Introduction Effect. In: IT Insight, National IT Industry promotion Agency (2010) Dikaiakos, M.D., et al.: Cloud Computing Distributed Internet Computing for IT and Scientific Research. In: IEEEInternet Computing, pp , September/October (2009) 8. Harauz, J., et al.: Data Security in the World of Cloud Computing. In: IEEE Security & Privacy, pp (2009) 9. Lee, J.: Cloud Compting, Changes IT Industry Paradigm. In: LG Business Insight, pp (2009) 10. Kim, H., Park, C.: Cloud Computing and Personal Authentication Service. In: KIISC, vol. 20, pp (2010) 11. Armbust, M., et al.: Above the Clouds: A Berkeley View of Cloud Computing. In: Technical Report. (2009) 12. Un, S., et al.: Cloud Computing Security Technology. In: ETRI, vol. 24, no. 4, pp (2009)
A Study on User Access Control Method using Multi-Factor Authentication for EDMS
 , pp.327-334 http://dx.doi.org/10.14257/ijsia.2013.7.6.33 A Study on User Access Control Method using Multi-Factor Authentication for EDMS Keunwang Lee 1* 1 Dept.of Multimedia Science, Chungwoon University
, pp.327-334 http://dx.doi.org/10.14257/ijsia.2013.7.6.33 A Study on User Access Control Method using Multi-Factor Authentication for EDMS Keunwang Lee 1* 1 Dept.of Multimedia Science, Chungwoon University
A Survey on Security Threats and Security Technology Analysis for Secured Cloud Services
 , pp.21-30 http://dx.doi.org/10.14257/ijsia.2013.7.6.03 A Survey on Security Threats and Security Technology Analysis for Secured Cloud Services Changsoo Lee 1, Daewon Jung 2 and Keunwang Lee 3 1 Dept.
, pp.21-30 http://dx.doi.org/10.14257/ijsia.2013.7.6.03 A Survey on Security Threats and Security Technology Analysis for Secured Cloud Services Changsoo Lee 1, Daewon Jung 2 and Keunwang Lee 3 1 Dept.
Dynamic Query Updation for User Authentication in cloud Environment
 Dynamic Query Updation for User Authentication in cloud Environment Gaurav Shrivastava 1, Dr. S. Prabakaran 2 1 Research Scholar, Department of Computer Science, SRM University, Kattankulathur, Tamilnadu,
Dynamic Query Updation for User Authentication in cloud Environment Gaurav Shrivastava 1, Dr. S. Prabakaran 2 1 Research Scholar, Department of Computer Science, SRM University, Kattankulathur, Tamilnadu,
API-Security Gateway Dirk Krafzig
 API-Security Gateway Dirk Krafzig Intro Digital transformation accelerates application integration needs Dramatically increasing number of integration points Speed Security Industrial robustness Increasing
API-Security Gateway Dirk Krafzig Intro Digital transformation accelerates application integration needs Dramatically increasing number of integration points Speed Security Industrial robustness Increasing
Enhancing Web Application Security
 Enhancing Web Application Security Using Another Authentication Factor Karen Lu and Asad Ali Gemalto, Inc. Technology & Innovations Austin, TX, USA Overview Introduction Current Statet Smart Cards Two-Factor
Enhancing Web Application Security Using Another Authentication Factor Karen Lu and Asad Ali Gemalto, Inc. Technology & Innovations Austin, TX, USA Overview Introduction Current Statet Smart Cards Two-Factor
IDENTITY MANAGEMENT. February 2008. The Government of the Hong Kong Special Administrative Region
 IDENTITY MANAGEMENT February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in part without
IDENTITY MANAGEMENT February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in part without
Access Control of Cloud Service Based on UCON
 Access Control of Cloud Service Based on UCON Chen Danwei, Huang Xiuli, and Ren Xunyi Nanjing University of posts & Telecommunications, New Model Street No.66, 210003, Nanjing, China chendw@njupt.edu.cn,
Access Control of Cloud Service Based on UCON Chen Danwei, Huang Xiuli, and Ren Xunyi Nanjing University of posts & Telecommunications, New Model Street No.66, 210003, Nanjing, China chendw@njupt.edu.cn,
Security Considerations for Public Mobile Cloud Computing
 Security Considerations for Public Mobile Cloud Computing Ronnie D. Caytiles 1 and Sunguk Lee 2* 1 Society of Science and Engineering Research Support, Korea rdcaytiles@gmail.com 2 Research Institute of
Security Considerations for Public Mobile Cloud Computing Ronnie D. Caytiles 1 and Sunguk Lee 2* 1 Society of Science and Engineering Research Support, Korea rdcaytiles@gmail.com 2 Research Institute of
Security Challenges. in Moving to Externalized Datacenters. (Focusing on SaaS) Eran Birk, Spring 2014. Business. Intelligence
 Business Intelligence Security Challenges in Moving to Externalized Datacenters (Focusing on SaaS) Eran Birk, Spring 2014 Grid Computing Cloud Computing Compute Networks Storage Information provided in
Business Intelligence Security Challenges in Moving to Externalized Datacenters (Focusing on SaaS) Eran Birk, Spring 2014 Grid Computing Cloud Computing Compute Networks Storage Information provided in
A Survey on Cloud Security Issues and Techniques
 A Survey on Cloud Security Issues and Techniques Garima Gupta 1, P.R.Laxmi 2 and Shubhanjali Sharma 3 1 Department of Computer Engineering, Government Engineering College, Ajmer Guptagarima09@gmail.com
A Survey on Cloud Security Issues and Techniques Garima Gupta 1, P.R.Laxmi 2 and Shubhanjali Sharma 3 1 Department of Computer Engineering, Government Engineering College, Ajmer Guptagarima09@gmail.com
Context Model Based on Ontology in Mobile Cloud Computing
 Context Model Based on Ontology in Mobile Cloud Computing Changbok Jang, Euiin Choi * Dept. Of Computer Engineering, Hannam University, Daejeon, Korea chbjang@dblab.hannam.ac.kr, eichoi@hnu.kr Abstract.
Context Model Based on Ontology in Mobile Cloud Computing Changbok Jang, Euiin Choi * Dept. Of Computer Engineering, Hannam University, Daejeon, Korea chbjang@dblab.hannam.ac.kr, eichoi@hnu.kr Abstract.
White Paper. Authentication and Access Control - The Cornerstone of Information Security. Vinay Purohit September 2007. Trianz 2008 White Paper Page 1
 White Paper Authentication and Access Control - The Cornerstone of Information Security Vinay Purohit September 2007 Trianz 2008 White Paper Page 1 Table of Contents 1 Scope and Objective --------------------------------------------------------------------------------------------------------
White Paper Authentication and Access Control - The Cornerstone of Information Security Vinay Purohit September 2007 Trianz 2008 White Paper Page 1 Table of Contents 1 Scope and Objective --------------------------------------------------------------------------------------------------------
What s wrong with SAAS login?
 Patented What s wrong with SAAS login? Nikos Leoutsarakos Tiny bio Nikos has a Physics background and a M.Sc. in Computer science from McGill University in Montreal, Canada, where he lives with his wife
Patented What s wrong with SAAS login? Nikos Leoutsarakos Tiny bio Nikos has a Physics background and a M.Sc. in Computer science from McGill University in Montreal, Canada, where he lives with his wife
Development of Integrated Management System based on Mobile and Cloud Service for Preventing Various Hazards
 , pp. 143-150 http://dx.doi.org/10.14257/ijseia.2015.9.7.15 Development of Integrated Management System based on Mobile and Cloud Service for Preventing Various Hazards Ryu HyunKi 1, Yeo ChangSub 1, Jeonghyun
, pp. 143-150 http://dx.doi.org/10.14257/ijseia.2015.9.7.15 Development of Integrated Management System based on Mobile and Cloud Service for Preventing Various Hazards Ryu HyunKi 1, Yeo ChangSub 1, Jeonghyun
State of Michigan Single Sign-On Registration Instructions for First Time Users
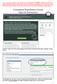 Once you have created a user id/password combination you MUST remember it for future logins. DNR employees cannot help with user id/password assistance. You will need to call the Client Service Center
Once you have created a user id/password combination you MUST remember it for future logins. DNR employees cannot help with user id/password assistance. You will need to call the Client Service Center
A Study on Information Technology Plan and Status of University 2013
 , pp. 47-54 http://dx.doi.org/10.14257/ijseia.2014.8.10.05 A Study on Information Technology Plan and Status of University 2013 Tae-Yong Shim 1, Il-Jun Choi 2, Jin Kim 3 and Young-Hun Lee 4 1 Department
, pp. 47-54 http://dx.doi.org/10.14257/ijseia.2014.8.10.05 A Study on Information Technology Plan and Status of University 2013 Tae-Yong Shim 1, Il-Jun Choi 2, Jin Kim 3 and Young-Hun Lee 4 1 Department
A Study on Analysis and Implementation of a Cloud Computing Framework for Multimedia Convergence Services
 A Study on Analysis and Implementation of a Cloud Computing Framework for Multimedia Convergence Services Ronnie D. Caytiles and Byungjoo Park * Department of Multimedia Engineering, Hannam University
A Study on Analysis and Implementation of a Cloud Computing Framework for Multimedia Convergence Services Ronnie D. Caytiles and Byungjoo Park * Department of Multimedia Engineering, Hannam University
Profile for Effective Service Management on Mobile Cloud Computing
 Profile for Effective Service Management on Mobile Cloud Computing Changbok Jang, Hyokyung Chang, Hyosik Ahn, Yongho Kang, Euiin Choi * Dept. Of Computer Engineering, Hannam University, Daejeon, Korea
Profile for Effective Service Management on Mobile Cloud Computing Changbok Jang, Hyokyung Chang, Hyosik Ahn, Yongho Kang, Euiin Choi * Dept. Of Computer Engineering, Hannam University, Daejeon, Korea
IMAV: An Intelligent Multi-Agent Model Based on Cloud Computing for Resource Virtualization
 2011 International Conference on Information and Electronics Engineering IPCSIT vol.6 (2011) (2011) IACSIT Press, Singapore IMAV: An Intelligent Multi-Agent Model Based on Cloud Computing for Resource
2011 International Conference on Information and Electronics Engineering IPCSIT vol.6 (2011) (2011) IACSIT Press, Singapore IMAV: An Intelligent Multi-Agent Model Based on Cloud Computing for Resource
Design and Implementation of Automatic Attendance Check System Using BLE Beacon
 , pp.177-186 http://dx.doi.org/10.14257/ijmue.2015.10.10.19 Design and Implementation of Automatic Attendance Check System Using BLE Beacon Mi-Young Bae and Dae-Jea Cho * Dept. Of Multimedia Engineering,
, pp.177-186 http://dx.doi.org/10.14257/ijmue.2015.10.10.19 Design and Implementation of Automatic Attendance Check System Using BLE Beacon Mi-Young Bae and Dae-Jea Cho * Dept. Of Multimedia Engineering,
Improving Online Security with Strong, Personalized User Authentication
 Improving Online Security with Strong, Personalized User Authentication July 2014 Secure and simplify your digital life. Table of Contents Online Security -- Safe or Easy, But Not Both?... 3 The Traitware
Improving Online Security with Strong, Personalized User Authentication July 2014 Secure and simplify your digital life. Table of Contents Online Security -- Safe or Easy, But Not Both?... 3 The Traitware
Keywords Mobile Cloud Operating System (MCOS), Distributed Cloud Operating System, Garbage mobile phone, Cloud Operating System
 Volume 5, Issue 5, May 2015 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com A Futuristic Approach:
Volume 5, Issue 5, May 2015 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com A Futuristic Approach:
A Study of Key management Protocol for Secure Communication in Personal Cloud Environment
 , pp.51-58 http://dx.doi.org/10.14257/ijsia.2014.8.4.05 A Study of Key management Protocol for Secure Communication in Personal Cloud Environment ByungWook Jin 1 and Keun-Wang Lee 2,* 1 Dept. of Computer
, pp.51-58 http://dx.doi.org/10.14257/ijsia.2014.8.4.05 A Study of Key management Protocol for Secure Communication in Personal Cloud Environment ByungWook Jin 1 and Keun-Wang Lee 2,* 1 Dept. of Computer
Chapter 1: Introduction
 Chapter 1 Introduction 1 Chapter 1: Introduction 1.1 Inspiration Cloud Computing Inspired by the cloud computing characteristics like pay per use, rapid elasticity, scalable, on demand self service, secure
Chapter 1 Introduction 1 Chapter 1: Introduction 1.1 Inspiration Cloud Computing Inspired by the cloud computing characteristics like pay per use, rapid elasticity, scalable, on demand self service, secure
Biometric SSO Authentication Using Java Enterprise System
 Biometric SSO Authentication Using Java Enterprise System Edward Clay Security Architect edward.clay@sun.com & Ramesh Nagappan CISSP Java Technology Architect ramesh.nagappan@sun.com Agenda Part 1 : Identity
Biometric SSO Authentication Using Java Enterprise System Edward Clay Security Architect edward.clay@sun.com & Ramesh Nagappan CISSP Java Technology Architect ramesh.nagappan@sun.com Agenda Part 1 : Identity
Mobile multifactor security
 Mobile multifactor security A revolution in authentication and digital signing Mobile multifactor security A revolution in authentication and digital signing Smartphones will continue to ship in high volumes,
Mobile multifactor security A revolution in authentication and digital signing Mobile multifactor security A revolution in authentication and digital signing Smartphones will continue to ship in high volumes,
An Innovative Two Factor Authentication Method: The QRLogin System
 An Innovative Two Factor Authentication Method: The QRLogin System Soonduck Yoo*, Seung-jung Shin and Dae-hyun Ryu Dept. of IT, University of Hansei, 604-5 Dangjung-dong Gunpo city, Gyeonggi do, Korea,
An Innovative Two Factor Authentication Method: The QRLogin System Soonduck Yoo*, Seung-jung Shin and Dae-hyun Ryu Dept. of IT, University of Hansei, 604-5 Dangjung-dong Gunpo city, Gyeonggi do, Korea,
Mobile Cloud Computing Security Considerations
 보안공학연구논문지 (Journal of Security Engineering), 제 9권 제 2호 2012년 4월 Mobile Cloud Computing Security Considerations Soeung-Kon(Victor) Ko 1), Jung-Hoon Lee 2), Sung Woo Kim 3) Abstract Building applications
보안공학연구논문지 (Journal of Security Engineering), 제 9권 제 2호 2012년 4월 Mobile Cloud Computing Security Considerations Soeung-Kon(Victor) Ko 1), Jung-Hoon Lee 2), Sung Woo Kim 3) Abstract Building applications
Advanced Authentication
 White Paper Advanced Authentication Introduction In this paper: Introduction 1 User Authentication 2 Device Authentication 3 Message Authentication 4 Advanced Authentication 5 Advanced Authentication is
White Paper Advanced Authentication Introduction In this paper: Introduction 1 User Authentication 2 Device Authentication 3 Message Authentication 4 Advanced Authentication 5 Advanced Authentication is
Security Model for VM in Cloud
 Security Model for VM in Cloud 1 Venkataramana.Kanaparti, 2 Naveen Kumar R, 3 Rajani.S, 4 Padmavathamma M, 5 Anitha.C 1,2,3,5 Research Scholars, 4Research Supervisor 1,2,3,4,5 Dept. of Computer Science,
Security Model for VM in Cloud 1 Venkataramana.Kanaparti, 2 Naveen Kumar R, 3 Rajani.S, 4 Padmavathamma M, 5 Anitha.C 1,2,3,5 Research Scholars, 4Research Supervisor 1,2,3,4,5 Dept. of Computer Science,
CompTIA Security+ Certification SY0-301
 CompTIA Security+ Certification SY0-301 Centro Latino, Inc. Computer Technology Program Prof: Nestor Uribe, nuribe@centrolatino.org www.centrolatino.org 267 Broadway, Chelsea, MA 02150 Tel. (617) 884-3238
CompTIA Security+ Certification SY0-301 Centro Latino, Inc. Computer Technology Program Prof: Nestor Uribe, nuribe@centrolatino.org www.centrolatino.org 267 Broadway, Chelsea, MA 02150 Tel. (617) 884-3238
Multi Factor Authentication API
 GEORGIA INSTITUTE OF TECHNOLOGY Multi Factor Authentication API Yusuf Nadir Saghar Amay Singhal CONTENTS Abstract... 3 Motivation... 3 Overall Design:... 4 MFA Architecture... 5 Authentication Workflow...
GEORGIA INSTITUTE OF TECHNOLOGY Multi Factor Authentication API Yusuf Nadir Saghar Amay Singhal CONTENTS Abstract... 3 Motivation... 3 Overall Design:... 4 MFA Architecture... 5 Authentication Workflow...
Development of Integrated Management System based on Mobile and Cloud service for preventing various dangerous situations
 Development of Integrated Management System based on Mobile and Cloud service for preventing various dangerous situations Ryu HyunKi, Moon ChangSoo, Yeo ChangSub, and Lee HaengSuk Abstract In this paper,
Development of Integrated Management System based on Mobile and Cloud service for preventing various dangerous situations Ryu HyunKi, Moon ChangSoo, Yeo ChangSub, and Lee HaengSuk Abstract In this paper,
How To Secure Cloud Computing
 Next Generation Cloud Computing Issues and Solutions Jeon SeungHwan 1, Yvette E. Gelogo 1 and Byungjoo Park 1 * 1 Department of Multimedia Engineering, Hannam University 133 Ojeong-dong, Daeduk-gu, Daejeon,
Next Generation Cloud Computing Issues and Solutions Jeon SeungHwan 1, Yvette E. Gelogo 1 and Byungjoo Park 1 * 1 Department of Multimedia Engineering, Hannam University 133 Ojeong-dong, Daeduk-gu, Daejeon,
Cloud Database Storage Model by Using Key-as-a-Service (KaaS)
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 4 Issue 7 July 2015, Page No. 13284-13288 Cloud Database Storage Model by Using Key-as-a-Service (KaaS) J.Sivaiah
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 4 Issue 7 July 2015, Page No. 13284-13288 Cloud Database Storage Model by Using Key-as-a-Service (KaaS) J.Sivaiah
MULTI-DIMENSIONAL PASSWORD GENERATION TECHNIQUE FOR ACCESSING CLOUD SERVICES
 MULTI-DIMENSIONAL PASSWORD GENERATION TECHNIQUE FOR ACCESSING CLOUD SERVICES Dinesha H A 1 and Dr.V.K Agrawal 2 1 Assistant Professor, Department of ISE & CORI, PES Institute of Technology, Bangalore,
MULTI-DIMENSIONAL PASSWORD GENERATION TECHNIQUE FOR ACCESSING CLOUD SERVICES Dinesha H A 1 and Dr.V.K Agrawal 2 1 Assistant Professor, Department of ISE & CORI, PES Institute of Technology, Bangalore,
Data Integrity Check using Hash Functions in Cloud environment
 Data Integrity Check using Hash Functions in Cloud environment Selman Haxhijaha 1, Gazmend Bajrami 1, Fisnik Prekazi 1 1 Faculty of Computer Science and Engineering, University for Business and Tecnology
Data Integrity Check using Hash Functions in Cloud environment Selman Haxhijaha 1, Gazmend Bajrami 1, Fisnik Prekazi 1 1 Faculty of Computer Science and Engineering, University for Business and Tecnology
Introduction to SAML
 Introduction to THE LEADER IN API AND CLOUD GATEWAY TECHNOLOGY Introduction to Introduction In today s world of rapidly expanding and growing software development; organizations, enterprises and governments
Introduction to THE LEADER IN API AND CLOUD GATEWAY TECHNOLOGY Introduction to Introduction In today s world of rapidly expanding and growing software development; organizations, enterprises and governments
Public Auditing & Automatic Protocol Blocking with 3-D Password Authentication for Secure Cloud Storage
 Public Auditing & Automatic Protocol Blocking with 3-D Password Authentication for Secure Cloud Storage P. Selvigrija, Assistant Professor, Department of Computer Science & Engineering, Christ College
Public Auditing & Automatic Protocol Blocking with 3-D Password Authentication for Secure Cloud Storage P. Selvigrija, Assistant Professor, Department of Computer Science & Engineering, Christ College
KEYSTROKE DYNAMIC BIOMETRIC AUTHENTICATION FOR WEB PORTALS
 KEYSTROKE DYNAMIC BIOMETRIC AUTHENTICATION FOR WEB PORTALS Plurilock Security Solutions Inc. www.plurilock.com info@plurilock.com 2 H IGHLIGHTS: PluriPass is Plurilock static keystroke dynamic biometric
KEYSTROKE DYNAMIC BIOMETRIC AUTHENTICATION FOR WEB PORTALS Plurilock Security Solutions Inc. www.plurilock.com info@plurilock.com 2 H IGHLIGHTS: PluriPass is Plurilock static keystroke dynamic biometric
Cloud Computing Security Issues and Access Control Solutions
 보안공학연구논문지 (Journal of Security Engineering), 제 9권 제 2호 2012년 4월 Cloud Computing Security Issues and Access Control Solutions Young-Gi Min 1), Hyo-Jin Shin 2), Young-Hwan Bang 3) Abstract Cloud computing
보안공학연구논문지 (Journal of Security Engineering), 제 9권 제 2호 2012년 4월 Cloud Computing Security Issues and Access Control Solutions Young-Gi Min 1), Hyo-Jin Shin 2), Young-Hwan Bang 3) Abstract Cloud computing
The Top 5 Federated Single Sign-On Scenarios
 The Top 5 Federated Single Sign-On Scenarios Table of Contents Executive Summary... 1 The Solution: Standards-Based Federation... 2 Service Provider Initiated SSO...3 Identity Provider Initiated SSO...3
The Top 5 Federated Single Sign-On Scenarios Table of Contents Executive Summary... 1 The Solution: Standards-Based Federation... 2 Service Provider Initiated SSO...3 Identity Provider Initiated SSO...3
Mobile Hybrid Cloud Computing Issues and Solutions
 , pp.341-345 http://dx.doi.org/10.14257/astl.2013.29.72 Mobile Hybrid Cloud Computing Issues and Solutions Yvette E. Gelogo *1 and Haeng-Kon Kim 1 1 School of Information Technology, Catholic University
, pp.341-345 http://dx.doi.org/10.14257/astl.2013.29.72 Mobile Hybrid Cloud Computing Issues and Solutions Yvette E. Gelogo *1 and Haeng-Kon Kim 1 1 School of Information Technology, Catholic University
Studying Security Weaknesses of Android System
 , pp. 7-12 http://dx.doi.org/10.14257/ijsia.2015.9.3.02 Studying Security Weaknesses of Android System Jae-Kyung Park* and Sang-Yong Choi** *Chief researcher at Cyber Security Research Center, Korea Advanced
, pp. 7-12 http://dx.doi.org/10.14257/ijsia.2015.9.3.02 Studying Security Weaknesses of Android System Jae-Kyung Park* and Sang-Yong Choi** *Chief researcher at Cyber Security Research Center, Korea Advanced
Evaluation of different Open Source Identity management Systems
 Evaluation of different Open Source Identity management Systems Ghasan Bhatti, Syed Yasir Imtiaz Linkoping s universitetet, Sweden [ghabh683, syeim642]@student.liu.se 1. Abstract Identity management systems
Evaluation of different Open Source Identity management Systems Ghasan Bhatti, Syed Yasir Imtiaz Linkoping s universitetet, Sweden [ghabh683, syeim642]@student.liu.se 1. Abstract Identity management systems
Contents. The Genesis of i-pin. The Concept of i-pin & Integrated IDM. The Trust Foundation of i-pin. The Function of i-pin. The Future of i-pin
 i-pin Service (internet-personal Identification Number Service) Identity Management across the Public and Private Sectors in Korea 1 Contents The Genesis of i-pin The Concept of i-pin & Integrated IDM
i-pin Service (internet-personal Identification Number Service) Identity Management across the Public and Private Sectors in Korea 1 Contents The Genesis of i-pin The Concept of i-pin & Integrated IDM
One-Time Password Contingency Access Process
 Multi-Factor Authentication: One-Time Password Contingency Access Process Presenter: John Kotolski HRS Security Officer Topics Contingency Access Scenarios Requesting a Temporary One-Time Password Reporting
Multi-Factor Authentication: One-Time Password Contingency Access Process Presenter: John Kotolski HRS Security Officer Topics Contingency Access Scenarios Requesting a Temporary One-Time Password Reporting
Alaa Hussein Al-Hamami, Jalal Yousef AL-Juneidi Department of Computer Sciences and Informatics Amman Arab University Amman, Jordan
 World of Computer Science and Information Technology Journal (WCSIT) ISSN: 2221-0741 Vol. 5, No. 2, 23-27, 2015 Secure Mobile Cloud Computing Based-On Fingerprint Alaa Hussein Al-Hamami, Jalal Yousef AL-Juneidi
World of Computer Science and Information Technology Journal (WCSIT) ISSN: 2221-0741 Vol. 5, No. 2, 23-27, 2015 Secure Mobile Cloud Computing Based-On Fingerprint Alaa Hussein Al-Hamami, Jalal Yousef AL-Juneidi
2013 AWS Worldwide Public Sector Summit Washington, D.C.
 Washington, D.C. Next Generation Privileged Identity Management Control and Audit Privileged Access Across Hybrid Cloud Environments Ken Ammon, Chief Strategy Officer Who We Are Security software company
Washington, D.C. Next Generation Privileged Identity Management Control and Audit Privileged Access Across Hybrid Cloud Environments Ken Ammon, Chief Strategy Officer Who We Are Security software company
Educational Requirement Analysis for Information Security Professionals in Korea
 Educational Requirement Analysis for Information Security Professionals in Korea Sehun Kim Dept. of Industrial Engineering, KAIST, 373-1, Kusong-dong, Yusong-gu, Taejon, 305-701, Korea shkim@kaist.ac.kr
Educational Requirement Analysis for Information Security Professionals in Korea Sehun Kim Dept. of Industrial Engineering, KAIST, 373-1, Kusong-dong, Yusong-gu, Taejon, 305-701, Korea shkim@kaist.ac.kr
A Study on Service Oriented Network Virtualization convergence of Cloud Computing
 A Study on Service Oriented Network Virtualization convergence of Cloud Computing 1 Kajjam Vinay Kumar, 2 SANTHOSH BODDUPALLI 1 Scholar(M.Tech),Department of Computer Science Engineering, Brilliant Institute
A Study on Service Oriented Network Virtualization convergence of Cloud Computing 1 Kajjam Vinay Kumar, 2 SANTHOSH BODDUPALLI 1 Scholar(M.Tech),Department of Computer Science Engineering, Brilliant Institute
WIRELESS PUBLIC KEY INFRASTRUCTURE FOR MOBILE PHONES
 WIRELESS PUBLIC KEY INFRASTRUCTURE FOR MOBILE PHONES Balachandra Muniyal 1 Krishna Prakash 2 Shashank Sharma 3 1 Dept. of Information and Communication Technology, Manipal Institute of Technology, Manipal
WIRELESS PUBLIC KEY INFRASTRUCTURE FOR MOBILE PHONES Balachandra Muniyal 1 Krishna Prakash 2 Shashank Sharma 3 1 Dept. of Information and Communication Technology, Manipal Institute of Technology, Manipal
OPENIAM ACCESS MANAGER. Web Access Management made Easy
 OPENIAM ACCESS MANAGER Web Access Management made Easy TABLE OF CONTENTS Introduction... 3 OpenIAM Access Manager Overview... 4 Access Gateway... 4 Authentication... 5 Authorization... 5 Role Based Access
OPENIAM ACCESS MANAGER Web Access Management made Easy TABLE OF CONTENTS Introduction... 3 OpenIAM Access Manager Overview... 4 Access Gateway... 4 Authentication... 5 Authorization... 5 Role Based Access
QR-SSO : Towards a QR-Code based Single Sign-On system
 QR-SSO : Towards a QR-Code based Single Sign-On system Syamantak Mukhopadhyay School of Electronics and Computer Science University of Southampton Southampton, UK sm19g10@ecs.soton.ac.uk David Argles School
QR-SSO : Towards a QR-Code based Single Sign-On system Syamantak Mukhopadhyay School of Electronics and Computer Science University of Southampton Southampton, UK sm19g10@ecs.soton.ac.uk David Argles School
Account Management: A Deployment and Usability Problem Phillip Hallam- Baker VP & Principal Scientist, Comodo Group Inc.
 Account Management: A Deployment and Usability Problem Phillip Hallam- Baker VP & Principal Scientist, Comodo Group Inc. Abstract Account management is the biggest challenge most Web users face today.
Account Management: A Deployment and Usability Problem Phillip Hallam- Baker VP & Principal Scientist, Comodo Group Inc. Abstract Account management is the biggest challenge most Web users face today.
How Secure is Authentication?
 FIDO UAF Tutorial How Secure is Authentication? How Secure is Authentication? How Secure is Authentication? Cloud Authentication Password Issues Password might be entered into untrusted App / Web-site
FIDO UAF Tutorial How Secure is Authentication? How Secure is Authentication? How Secure is Authentication? Cloud Authentication Password Issues Password might be entered into untrusted App / Web-site
Authentication Mechanism for Private Cloud of Enterprise. Abstract
 Authentication Mechanism for Private Cloud of Enterprise Mei-Yu Wu *, and Shih-Pin Lo Department of Information Management, Chung Hua University, Hsinchu, Taiwan {mywu, e10010008}@chu.edu.tw Abstract Enterprises
Authentication Mechanism for Private Cloud of Enterprise Mei-Yu Wu *, and Shih-Pin Lo Department of Information Management, Chung Hua University, Hsinchu, Taiwan {mywu, e10010008}@chu.edu.tw Abstract Enterprises
Implementing Identity Provider on Mobile Phone
 Implementing Identity Provider on Mobile Phone Tsuyoshi Abe, Hiroki Itoh, and Kenji Takahashi NTT Information Sharing Platform Laboratories, NTT Corporation 3-9-11 Midoricho, Musashino-shi, Tokyo 180-8585,
Implementing Identity Provider on Mobile Phone Tsuyoshi Abe, Hiroki Itoh, and Kenji Takahashi NTT Information Sharing Platform Laboratories, NTT Corporation 3-9-11 Midoricho, Musashino-shi, Tokyo 180-8585,
SECURITY MODELS FOR CLOUD 2012. Kurtis E. Minder, CISSP
 SECURITY MODELS FOR CLOUD 2012 Kurtis E. Minder, CISSP INTRODUCTION Kurtis E. Minder, Technical Sales Professional Companies: Roles: Security Design Engineer Systems Engineer Sales Engineer Salesperson
SECURITY MODELS FOR CLOUD 2012 Kurtis E. Minder, CISSP INTRODUCTION Kurtis E. Minder, Technical Sales Professional Companies: Roles: Security Design Engineer Systems Engineer Sales Engineer Salesperson
International Journal of Scientific & Engineering Research, Volume 6, Issue 5, May-2015 1681 ISSN 2229-5518
 International Journal of Scientific & Engineering Research, Volume 6, Issue 5, May-2015 1681 Software as a Model for Security in Cloud over Virtual Environments S.Vengadesan, B.Muthulakshmi PG Student,
International Journal of Scientific & Engineering Research, Volume 6, Issue 5, May-2015 1681 Software as a Model for Security in Cloud over Virtual Environments S.Vengadesan, B.Muthulakshmi PG Student,
TrustedX: eidas Platform
 TrustedX: eidas Platform Identification, authentication and electronic signature platform for Web environments. Guarantees identity via adaptive authentication and the recognition of either corporate,
TrustedX: eidas Platform Identification, authentication and electronic signature platform for Web environments. Guarantees identity via adaptive authentication and the recognition of either corporate,
An Anti-Phishing mechanism for Single Sign-On based on QR-Code
 An Anti-Phishing mechanism for Single Sign-On based on QR-Code Syamantak Mukhopadhyay School of Electronics and Computer Science University of Southampton Southampton, UK sm19g10@ecs.soton.ac.uk David
An Anti-Phishing mechanism for Single Sign-On based on QR-Code Syamantak Mukhopadhyay School of Electronics and Computer Science University of Southampton Southampton, UK sm19g10@ecs.soton.ac.uk David
A Study on Secure Electronic Medical DB System in Hospital Environment
 A Study on Secure Electronic Medical DB System in Hospital Environment Yvette E. Gelogo 1 and Sungwon Park 2 * 1 Catholic University of Daegu, Daegu, Korea 2 Department of Nursing, Hannam University, 133
A Study on Secure Electronic Medical DB System in Hospital Environment Yvette E. Gelogo 1 and Sungwon Park 2 * 1 Catholic University of Daegu, Daegu, Korea 2 Department of Nursing, Hannam University, 133
How To Manage A Plethora Of Identities In A Cloud System (Saas)
 TECHNICAL WHITE PAPER Intel Cloud SSO How Intel Cloud SSO Works Just as security professionals have done for ages, we must continue to evolve our processes, methods, and techniques in light of the opportunities
TECHNICAL WHITE PAPER Intel Cloud SSO How Intel Cloud SSO Works Just as security professionals have done for ages, we must continue to evolve our processes, methods, and techniques in light of the opportunities
SECUREAUTH IDP AND OFFICE 365
 WHITEPAPER SECUREAUTH IDP AND OFFICE 365 STRONG AUTHENTICATION AND SINGLE SIGN-ON FOR THE CLOUD-BASED OFFICE SUITE EXECUTIVE OVERVIEW As more and more enterprises move to the cloud, it makes sense that
WHITEPAPER SECUREAUTH IDP AND OFFICE 365 STRONG AUTHENTICATION AND SINGLE SIGN-ON FOR THE CLOUD-BASED OFFICE SUITE EXECUTIVE OVERVIEW As more and more enterprises move to the cloud, it makes sense that
PortWise Access Management Suite
 Create secure virtual access for your employees, partners and customers from any location and any device. With todays global and homogenous economy, the accuracy and responsiveness of an organization s
Create secure virtual access for your employees, partners and customers from any location and any device. With todays global and homogenous economy, the accuracy and responsiveness of an organization s
Data Protection: From PKI to Virtualization & Cloud
 Data Protection: From PKI to Virtualization & Cloud Raymond Yeung CISSP, CISA Senior Regional Director, HK/TW, ASEAN & A/NZ SafeNet Inc. Agenda What is PKI? And Value? Traditional PKI Usage Cloud Security
Data Protection: From PKI to Virtualization & Cloud Raymond Yeung CISSP, CISA Senior Regional Director, HK/TW, ASEAN & A/NZ SafeNet Inc. Agenda What is PKI? And Value? Traditional PKI Usage Cloud Security
Introduction of Information Security Research Division
 Introduction of Information Security Research Division 2005. 5. 13. Kyo-il Chung, Ph. D. Information Security Infrastructure Research Group Contents Overview - Secure u-it KOREA - Organization of ETRI
Introduction of Information Security Research Division 2005. 5. 13. Kyo-il Chung, Ph. D. Information Security Infrastructure Research Group Contents Overview - Secure u-it KOREA - Organization of ETRI
Case Study: SSO for All: SSOCircle Makes Single Sign-On Available to Everyone
 Case Study: SSO for All: SSOCircle Makes Single Sign-On Available to Everyone Although single sign-on (SSO) technology based on Liberty standards is being rapidly adopted by businesses, governments and
Case Study: SSO for All: SSOCircle Makes Single Sign-On Available to Everyone Although single sign-on (SSO) technology based on Liberty standards is being rapidly adopted by businesses, governments and
AVG Business SSO Partner Getting Started Guide
 AVG Business SSO Partner Getting Started Guide Table of Contents Overview... 2 Getting Started... 3 Web and OS requirements... 3 Supported web and device browsers... 3 Initial Login... 4 Navigation in
AVG Business SSO Partner Getting Started Guide Table of Contents Overview... 2 Getting Started... 3 Web and OS requirements... 3 Supported web and device browsers... 3 Initial Login... 4 Navigation in
Information Technology Plan 2013 of Korea University
 , pp.159-163 http://dx.doi.org/10.14257/astl.2014.51.36 Information Technology Plan 2013 of Korea University Tae-Yong Shim 1, Il-Jun Choi 2, and Jin Kim 3 and Young-Hun Lee 4 1 Department of Information
, pp.159-163 http://dx.doi.org/10.14257/astl.2014.51.36 Information Technology Plan 2013 of Korea University Tae-Yong Shim 1, Il-Jun Choi 2, and Jin Kim 3 and Young-Hun Lee 4 1 Department of Information
Is Consumer-Oriented Strong Authentication Finally Here to Stay? Arshad Noor, CTO, StrongAuth, Inc. Professional Strategies S22
 Is Consumer-Oriented Strong Authentication Finally Here to Stay? Arshad Noor, CTO, StrongAuth, Inc. Professional Strategies S22 Historical Perspective Password-based authentication invented at least 4-5
Is Consumer-Oriented Strong Authentication Finally Here to Stay? Arshad Noor, CTO, StrongAuth, Inc. Professional Strategies S22 Historical Perspective Password-based authentication invented at least 4-5
BM482E Introduction to Computer Security
 BM482E Introduction to Computer Security Lecture 7 Database and Operating System Security Mehmet Demirci 1 Summary of Lecture 6 User Authentication Passwords Password storage Password selection Token-based
BM482E Introduction to Computer Security Lecture 7 Database and Operating System Security Mehmet Demirci 1 Summary of Lecture 6 User Authentication Passwords Password storage Password selection Token-based
FIDO Modern Authentication Rolf Lindemann, Nok Nok Labs
 Rolf Lindemann, Nok Nok Labs cv cryptovision GmbH T: +49 (0) 209.167-24 50 F: +49 (0) 209.167-24 61 info(at)cryptovision.com 1 Authentication in Context Single Sign-On Modern Authentication Federation
Rolf Lindemann, Nok Nok Labs cv cryptovision GmbH T: +49 (0) 209.167-24 50 F: +49 (0) 209.167-24 61 info(at)cryptovision.com 1 Authentication in Context Single Sign-On Modern Authentication Federation
The increasing popularity of mobile devices is rapidly changing how and where we
 Mobile Security BACKGROUND The increasing popularity of mobile devices is rapidly changing how and where we consume business related content. Mobile workforce expectations are forcing organizations to
Mobile Security BACKGROUND The increasing popularity of mobile devices is rapidly changing how and where we consume business related content. Mobile workforce expectations are forcing organizations to
CHAPTER 1 INTRODUCTION
 1 CHAPTER 1 INTRODUCTION 1.1 Introduction Cloud computing as a new paradigm of information technology that offers tremendous advantages in economic aspects such as reduced time to market, flexible computing
1 CHAPTER 1 INTRODUCTION 1.1 Introduction Cloud computing as a new paradigm of information technology that offers tremendous advantages in economic aspects such as reduced time to market, flexible computing
PortWise Access Management Suite
 Create secure virtual access for your employees, partners and customers from any location and any device. With todays global and homogenous economy, the accuracy and responsiveness of an organization s
Create secure virtual access for your employees, partners and customers from any location and any device. With todays global and homogenous economy, the accuracy and responsiveness of an organization s
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 8 Authentication
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 8 Authentication Objectives Define authentication Describe the different types of authentication credentials List and explain the
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 8 Authentication Objectives Define authentication Describe the different types of authentication credentials List and explain the
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 7 Access Control Fundamentals
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 7 Access Control Fundamentals Objectives Define access control and list the four access control models Describe logical access control
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 7 Access Control Fundamentals Objectives Define access control and list the four access control models Describe logical access control
Adding Stronger Authentication to your Portal and Cloud Apps
 SOLUTION BRIEF Cyphercor Inc. Adding Stronger Authentication to your Portal and Cloud Apps Using the logintc April 2012 Adding Stronger Authentication to Portals Corporate and consumer portals, as well
SOLUTION BRIEF Cyphercor Inc. Adding Stronger Authentication to your Portal and Cloud Apps Using the logintc April 2012 Adding Stronger Authentication to Portals Corporate and consumer portals, as well
Cloud-based Identity and Access Control for Diagnostic Imaging Systems
 Cloud-based Identity and Access Control for Diagnostic Imaging Systems Weina Ma and Kamran Sartipi Department of Electrical, Computer and Software Engineering University of Ontario Institute of Technology
Cloud-based Identity and Access Control for Diagnostic Imaging Systems Weina Ma and Kamran Sartipi Department of Electrical, Computer and Software Engineering University of Ontario Institute of Technology
Secure Semantic Web Service Using SAML
 Secure Semantic Web Service Using SAML JOO-YOUNG LEE and KI-YOUNG MOON Information Security Department Electronics and Telecommunications Research Institute 161 Gajeong-dong, Yuseong-gu, Daejeon KOREA
Secure Semantic Web Service Using SAML JOO-YOUNG LEE and KI-YOUNG MOON Information Security Department Electronics and Telecommunications Research Institute 161 Gajeong-dong, Yuseong-gu, Daejeon KOREA
More effective protection for your access control system with end-to-end security
 More effective protection for your access control system with end-to-end security By Jeroen Harmsen The first article on end-to-end security appeared as long ago as 1981. The principle originated in ICT
More effective protection for your access control system with end-to-end security By Jeroen Harmsen The first article on end-to-end security appeared as long ago as 1981. The principle originated in ICT
APPLICATION OF CLOUD COMPUTING IN ACADEMIC INSTITUTION
 APPLICATION OF CLOUD COMPUTING IN ACADEMIC INSTITUTION 1 PRIYANKA DUKLE, 2 TRISHALA PAWAR, 3 SNEH BHAT 1,2,3 Computer, Amrutvahini College of Engineering, Sangamner Email: bhatsneh@gmail.com 1, pawar.trishala@gmail.com
APPLICATION OF CLOUD COMPUTING IN ACADEMIC INSTITUTION 1 PRIYANKA DUKLE, 2 TRISHALA PAWAR, 3 SNEH BHAT 1,2,3 Computer, Amrutvahini College of Engineering, Sangamner Email: bhatsneh@gmail.com 1, pawar.trishala@gmail.com
PRIVACY, SECURITY AND THE VOLLY SERVICE
 PRIVACY, SECURITY AND THE VOLLY SERVICE Delight Delivered by EXECUTIVE SUMMARY The Volly secure digital delivery service from Pitney Bowes is a closed, secure, end-to-end system that consolidates and delivers
PRIVACY, SECURITY AND THE VOLLY SERVICE Delight Delivered by EXECUTIVE SUMMARY The Volly secure digital delivery service from Pitney Bowes is a closed, secure, end-to-end system that consolidates and delivers
Two-Factor Authentication: Tailor-Made for SMS
 SAP Thought Leadership Paper SAP Mobile Services Two-Factor Authentication: Tailor-Made for SMS Exploring Myths, Misconceptions, and Best Practices for SMS-Based 2FA Table of Contents 4 Understanding Two-Factor
SAP Thought Leadership Paper SAP Mobile Services Two-Factor Authentication: Tailor-Made for SMS Exploring Myths, Misconceptions, and Best Practices for SMS-Based 2FA Table of Contents 4 Understanding Two-Factor
Application Based Access Control on Cloud Networks for Data Security
 Application Based Access Control on Cloud Networks for Data Security Ms. Smitha P M.Tech in DCN, Department of ECE GSSSIETW, Mysuru Karnataka, India Smitha.21sn @gmail.com Mrs. Manjula G Associate. Proffesor,
Application Based Access Control on Cloud Networks for Data Security Ms. Smitha P M.Tech in DCN, Department of ECE GSSSIETW, Mysuru Karnataka, India Smitha.21sn @gmail.com Mrs. Manjula G Associate. Proffesor,
Data Integrity for Secure Dynamic Cloud Storage System Using TPA
 International Journal of Electronic and Electrical Engineering. ISSN 0974-2174, Volume 7, Number 1 (2014), pp. 7-12 International Research Publication House http://www.irphouse.com Data Integrity for Secure
International Journal of Electronic and Electrical Engineering. ISSN 0974-2174, Volume 7, Number 1 (2014), pp. 7-12 International Research Publication House http://www.irphouse.com Data Integrity for Secure
Cloud Computing and Business Intelligence
 Database Systems Journal vol. V, no. 4/2014 49 Cloud Computing and Business Intelligence Alexandru Adrian TOLE Romanian American University, Bucharest, Romania adrian.tole@yahoo.com The complexity of data
Database Systems Journal vol. V, no. 4/2014 49 Cloud Computing and Business Intelligence Alexandru Adrian TOLE Romanian American University, Bucharest, Romania adrian.tole@yahoo.com The complexity of data
The Design of the Network Service Access Control System through Address Control in IPv6 Environments
 174 IJCSNS International Journal of Computer Science and Network Security, VOL.6 No.6, June 2006 The Design of the Network Service Access Control System through Address Control in IPv6 Environments Summary
174 IJCSNS International Journal of Computer Science and Network Security, VOL.6 No.6, June 2006 The Design of the Network Service Access Control System through Address Control in IPv6 Environments Summary
Security Measures of Personal Information of Smart Home PC
 , pp.227-236 http://dx.doi.org/10.14257/ijsh.2013.7.6.22 Security Measures of Personal Information of Smart Home PC Mi-Sook Seo 1 and Dea-Woo Park 2 1, 2 Department of Integrative Engineering, Hoseo Graduate
, pp.227-236 http://dx.doi.org/10.14257/ijsh.2013.7.6.22 Security Measures of Personal Information of Smart Home PC Mi-Sook Seo 1 and Dea-Woo Park 2 1, 2 Department of Integrative Engineering, Hoseo Graduate
WHITEPAPER SECUREAUTH AND CAC HSPD-12 AUTHENTICATION TO WEB, NETWORK, AND CLOUD RESOURCES
 WHITEPAPER SECUREAUTH AND CAC HSPD-12 AUTHENTICATION TO WEB, NETWORK, AND CLOUD RESOURCES Executive Overview U.S. Federal mandates dictates that personal with defense related initiatives must prove access
WHITEPAPER SECUREAUTH AND CAC HSPD-12 AUTHENTICATION TO WEB, NETWORK, AND CLOUD RESOURCES Executive Overview U.S. Federal mandates dictates that personal with defense related initiatives must prove access
Development of a User Management Module for Internet TV Systems
 , pp.43-56 http://dx.doi.org/10.14257/ijmue.2015.10.11.05 Development of a User Management Module for Internet TV Systems Kangjai Lee 1 and Jaegeol Yim 2* 1 Dept. of Computer Information, Suwon Science
, pp.43-56 http://dx.doi.org/10.14257/ijmue.2015.10.11.05 Development of a User Management Module for Internet TV Systems Kangjai Lee 1 and Jaegeol Yim 2* 1 Dept. of Computer Information, Suwon Science
INCREASING THE CLOUD PERFORMANCE WITH LOCAL AUTHENTICATION
 INTERNATIONAL JOURNAL OF RESEARCH IN COMPUTER APPLICATIONS AND ROBOTICS ISSN 2320-7345 INCREASING THE CLOUD PERFORMANCE WITH LOCAL AUTHENTICATION Sanjay Razdan Department of Computer Science and Eng. Mewar
INTERNATIONAL JOURNAL OF RESEARCH IN COMPUTER APPLICATIONS AND ROBOTICS ISSN 2320-7345 INCREASING THE CLOUD PERFORMANCE WITH LOCAL AUTHENTICATION Sanjay Razdan Department of Computer Science and Eng. Mewar
Cloud computing an insight
 Cloud computing an insight Overview IT infrastructure is changing according the fast-paced world s needs. People in the world want to stay connected with Work / Family-Friends. The data needs to be available
Cloud computing an insight Overview IT infrastructure is changing according the fast-paced world s needs. People in the world want to stay connected with Work / Family-Friends. The data needs to be available
Network Services Required for Business Operations Using Smartphones
 Network Services Required for Business Operations Using Smartphones Motoyuki Kimura Studies are in process to make use of smartphones and tablets, which have rapidly become widespread in the consumer market,
Network Services Required for Business Operations Using Smartphones Motoyuki Kimura Studies are in process to make use of smartphones and tablets, which have rapidly become widespread in the consumer market,
Mobility, Security and Trusted Identities: It s Right In The Palm of Your Hands. Ian Wills Country Manager, Entrust Datacard
 Mobility, Security and Trusted Identities: It s Right In The Palm of Your Hands Ian Wills Country Manager, Entrust Datacard WHO IS ENTRUST DATACARD? 2 Entrust DataCard Datacard Corporation. Corporation.
Mobility, Security and Trusted Identities: It s Right In The Palm of Your Hands Ian Wills Country Manager, Entrust Datacard WHO IS ENTRUST DATACARD? 2 Entrust DataCard Datacard Corporation. Corporation.
Groupware / mail / Messenger / Cloud Disk
 http://mofficesuite.com collaboration SOFTWARE FOR YOUR COMPANY Groupware / mail / Messenger / Cloud Disk Hanbiro, Inc. SOFTWARE STRENGTH Around 95% Spam filtering Mail system Stable mail service with
http://mofficesuite.com collaboration SOFTWARE FOR YOUR COMPANY Groupware / mail / Messenger / Cloud Disk Hanbiro, Inc. SOFTWARE STRENGTH Around 95% Spam filtering Mail system Stable mail service with
Cloud security and OpenStack Primož Cigoj Laboratorij za odprte sisteme in mreže IJS-E5. www.kc-class.eu
 Cloud security and OpenStack Primož Cigoj Laboratorij za odprte sisteme in mreže IJS-E5 www.kc-class.eu 1 1 Outline Cloud computing General overview Deployment and service models Security issues Threats
Cloud security and OpenStack Primož Cigoj Laboratorij za odprte sisteme in mreže IJS-E5 www.kc-class.eu 1 1 Outline Cloud computing General overview Deployment and service models Security issues Threats
