Hybrid PA-DSS Report on Validation
|
|
|
- Shannon Eileen Richards
- 10 years ago
- Views:
Transcription
1 Hybrid PA-DSS Report on Validation For Applications that Store, Process, or Transmit Payment Card Data but are Not Part of Authorization or Settlement Application Vendor: KomBea Corporation 3400 N. Ashton Blvd. Suite 190 Lehi, UT Application Name and Version: SecureCall 3.0 Copyright
2 Contact Information and Report Date Report Date March 8, 2012 Service Provider Information Organization Name: Contact Name: Address: KomBea Corporation Dave Peachey, VP Product Development 3400 N. Ashton Blvd. Suite 190 Lehi, UT Phone: (801) Assessor Contact Information Bruce Bogdan, CISSP, QSA, PA-QSA Senior Security Analyst SecurityMetrics, Inc West 1600 North Orem, UT (801)
3 Executive Summary Introduction KomBea Corporation is an application vendor specializing in software development geared toward call center environments. Specifically KomBea focuses on call centers where credit card payments are accepted by the call center s customer service representatives (CSRs). Many of KomBea s customers have call centers in locations where fraud and pressure to commit fraud is prevalent. The use of the KomBea SecureCall application can reduce or eliminate the opportunity for fraud to occur. Although CSRs can accept card payments using SecureCall, and card numbers do transit the application it is not in scope for PA-DSS because it is not part of authorization or settlement. This can cause issues with KomBea customers because there is a general understanding that if an application touches cardholder data in any way then it needs to be PA-DSS validated. This assessment was conducted to address the security of SecureCall and to address any questions that customers may have about the applicability of PA-DSS to SecureCall. Overview The KomBea offices are located in Lehi, Utah. Dave Peachey was the primary contact with Kolby Olsen and Matt Mace assisting during testing. Dave heads the product development department and provided the documentation required for the assessment. Kolby is one of the primary developers of SecureCall and Matt is the systems administrator for KomBea. The SecureCall application secures the acceptance of credit card payments by removing the ability of the CSR to see or hear the primary account number (PAN) when a payment is made. This is accomplished in the following manner. When a payment is to be made the CSR clicks a payment icon on their interface and the SecureCall application is started. Control of the system is passed to a multiplexer (KPlexer) that is attached to the agents phone and the customer enters the card number on their phones keypad. The DTMF tones are interpreted by the KPlexer, which encrypts the data stream and passes it either to the back end server where it is forwarded to the call center s payment application or directly to the payment application. No card numbers are ever displayed on the agents screen and the DTMF tones are changed to a monotone so that the PAN cannot be determined from listening to the tones. No cardholder data ever is stored by SecureCall on the CSR s desktop or on the KomBea back end server and all data that transits these systems is encrypted using AES-256 as the encryption algorithm. It was verified by interview with Dave and by observation of SecureCall running in the test lab that there was no ability for a customer service representative to intercept cardholder data in any way. It was also verified that at no time does the application store cardholder data on any system that is in scope for this assessment and that no authorization or settlement actions were performed by SecureCall. The SecureCall components consist of the agent running on the CSR s desktop - 3 -
4 system, the KPlexer device and potentially an agent running on a backend server. KomBea does not provide any other hardware or software with SecureCall and they provide no ability to connect to a processor or payment gateway. It was verified by observing SecureCall in the test lab that it is not a wireless application. Individuals Interviewed During the Assessment Name Dave Peachey Ronnie Johansen Kolby Olsen Matt Mace Title VP Product Development VP Operations Lead Developer Lead Quality Engineer - 4 -
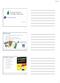
5 Figure 1 Secure Call Configuration A /+$607(.1*0+$&L&M&C-'(.-/1;;&0$*-7.1*-)&H0*8&%-)9*+5&/DG&M&NOPPQR&)'-$1.0+& /1;;&/-$*-.&58+$-&)3)*-,&!" #$%&'()*+,-.&-$*-.)&/.-%0*& '1.%2&)-'(.0*3&'+%-&1$%& &0$6+&()0$7&*8-& 9-351%&+6&1&*+('8:*+$-& *-;-58+$-<& /.-%0*&/1.%&@.+'-))+.& /CD&58+$-& =" >+,?-1&>@;-4-.&'+$A-.*)&*8-& *+$-)&*+&$(,B-.)2&-$'.35*)& *8-,&1$%&)-$%)&*8-,&*+&*8-& C-'(.-/1;;&155;0'1*0+$&.($$0$7& +$&*8-&/CDE)&'+,5(*-.<& F" C-'(.-/1;;&*.1$)6-.)&*8-& -$'.35*-%&%1*1&*+&*8-&& /DG&)+6*H1.-&.($$0$7& +$&*8-&/CDE)&'+,5(*-.<& /CD&/+,5(*-.& >@;-4-.&,1)9)&*8-&*+('8& *+$-)&)+&*8-&/CD& %+-)$E*&8-1.&*8-,<& I" J8-&/DG&)+6*H1.-&%-'.35*)& *8-&%1*1&1$%&)-$%)&0*&1'.+))& *8-&'1;;&'-$*-.&$-*H+.9&*+& *8-&/DG&B1'9-$%&1)&06&0*&81%& B--$&-$*-.-%&0$*+&*8-&/DG& %0.-'*;3<& /DG&?1'9-$%& K" J8-&/DG&B1'9-$%& )-$%)&*8-&*.1$)1'*0+$& *+&*8-&'.-%0*&'1.%& 5.+'-))+.&1$%&.-'+.%)&*8-& *.1$)1'*0+$<& & & - 5 -
6 /1;;&/-$*-.&58+$-&)3)*-,&!" #$%&'()*+,-.&-$*-.)&/.-%0*& '1.%2&)-'(.0*3&'+%-&1$%& &0$6+&()0$7&*8-& 9-351%&+6&1&*+('8:*+$-& *-;-58+$-<& /CD&58+$-& =" *+$-)&*+&$(,B-.)2&-$'.35*)& *8-,&1$%&)-$%)&*8-,&*+&*8-& C-'(.-/1;;&155;0'1*0+$&.($$0$7& +$&*8-&/CDE)&'+,5(*-.<& *+$-)&)+&*8-&/CD& %+-)$E*&8-1.&*8-,<& H" I8-&/DG&B1'9-$%& %-'.35*)&*8-&%1*12& )-$%)&*8-&*.1$)1'*0+$& *+&*8-&'.-%0*&'1.%& 5.+'-))+.&1$%&.-'+.%)&*8-& *.1$)1'*0+$<& F" C-'(.-/1;;&)-$%)&*8-& -$'.35*-%&%1*1&*+&*8-&/DG& B1'9-$%<& & & Figure 2 Secure Call Configuration B /+$607(.1*0+$&?&J&C-'(.-/1;;&0$*-7.1*-)&K0*8&/DG&B1'9-$%&J&L?#II#DM&)'-$1.0+& /.-%0*&/1.%&@.+'-))+.& /CD&/+,5(*-.& /DG&?1'9-$%& - 6 -
7 Scope of Work and Approach Taken Timeframe and Location of Assessment The assessment of the KomBea SecureCall application was conducted from December 2011 to March 2012 with testing occurring in the KomBea labs on February 8, A forensic examination of the collected data occurred the following week in the SecruityMetrics test lab. The SecurityMetrics assessor used version 2.0 of the PA-DSS as a basis for compliance to conduct the assessment of SecureCall. Although SecureCall is not in scope for a PA-DSS assessment the standard provides assurance that the tested application meets all the relevant security requirements of any application that is found on the list of PA-DSS verified applications. Application Specifics Application Tested: - SecureCall Version of Application Tested: Operating Systems Used During Testing: - Windows 7 SP1 - Windows 2008 R2 SP2 Database Used By Application: - SecureCall does not use a database to store cardholder data. Brief Description of Application: - The KomBea SecureCall application is designed to improve the security of a credit card transaction for telephone order transactions. It does this by allowing the customer to enter the PAN on their touchtone phone and translates the DTMF tones that are entered. The call center representative has no interface where they can see the digits being entered nor can they hear the DTMF tones entered. This eliminates the possibility of the CSR stealing the card information because they never have access to it
8 Hardware and Software Used During Testing KomBea call center simulation application Phone Factor SonicWall TZ200 Firewall EventSentry Symantec Endpoint Protection Antivirus/Malware Test Matrix OS Configuration Tested Case 0: Windows 7 SP1 Case 1: Windows 2008 R1 SP2 Case 2: Windows 7 SP1 Full Debug Mode Call Center Simulator (Test Environment) How Cardholder Data is Stored by Application No cardholder data is stored by the SecureCall application. Data from each transaction is passed directly to the call centers payment application. Related Software Components There are no related software components required by SecureCall. End-to-End Authentication Methods There is no authentication built into SecureCall. All administrative authentication is managed by the operating system. User accounts for testing were created in the Microsoft Windows systems and were consistent with all requirements outlined in section 8 of the PCI-DSS and section 3 of the PA-DSS. No default system accounts were used during testing, and users are instructed in the implementation guide to never use default accounts on any system that is used in the card environment. Typical Implementation The typical implementation for the KomBea SecureCall application is on systems in call center locations where the customer service representatives take credit card payments over the phone. The location where SecureCall is installed would need to be in a PCI compliant DMZ as outlined in the implementation guide
9 Typical Customer The typical customer for SecureCall would be any call center or other entity that accepts credit card transactions over the telephone. Versioning Methodology KomBea SecureCall uses the form X.X for its versioning methodology with the first octet representing a major version release and the second representing minor changes. An example of a major change might be changes to the encryption of the data flow and a minor change might be changes to the application interface
10 Findings and Observations Because KomBea SecureCall does not store, process, or transmit card data as part of authorization or settlement, a complete and formal PA-DSS Report on Verification was not required. However, as a way to organize the data collected during the on-site visit, the PA-DSS requirement headings will be used to discuss the security of the application. 1) Do not retain full magnetic stripe, card validation code or value, or PIN data. Because it is only used for card not present transactions there is no ability for SecureCall to obtain magnetic stripe data so no such data can be retained. Verified by observation of the running application that it does not support PIN transactions, thus no ability to retain PIN data is possible. Verified by observation of the running application and by a forensic examination of the test systems that SecureCall does not retain CVV data. Verified by interview with Dave that all card data is passed directly to the call centers payment application and is never written to non-volatile memory or other storage locations. 2) Protect stored cardholder data Verified by interview with Dave and by a forensic examination of the test systems that cardholder data is never stored in any form by SecureCall. 3) Provide secure authentication features. Verified by interview with Dave and by observation of SecureCall running in the test lab that there are no built in authentication features. All authentication is managed by the underlying operating system and is thus not applicable to this assessment. Verified by observation of the application running in the test lab that it does not interfere with the operating systems authentication features in any way. 4) Log payment application activity Because of the limited nature of SecureCall s interaction with the host system there is very little that is logged, but the log files that are produced were examined and found to meet the requirements outlined in section 4 of the PA- DSS. Verified by observation of the log files that they can be collected and moved to a central log repository. Verified by observation of the log files that no sensitive information including cardholder data is ever written to the logs
11 5) Develop secure payment applications Verified by interview with Dave and by observation of the KomBea SDLC that they develop applications in accordance with PCI-DSS and PA-DSS requirements and with industry best practices. Verified by interview with Dave and by observation of the development environment that live cardholder data and customer data are not used for testing. Verified by interview with Dave and by observation of the SDLC that code reviews by a person other than the code author are required. Verified by observation of the change control procedures that code review, back out procedures, customer impact and management approval are all included in the process. 6) Protect wireless transmissions Verified by interview with Dave and by observation of the application running in the test lab that SecureCall is not a wireless application. 7) Test payment applications to address vulnerabilities Verified by interview with Dave and by observation of the SDLC that testing is to be conducted to address all common vulnerabilities. Verified by interview with Dave that they subscribe to several resources to identify new security vulnerabilities including Secunia.org, and the OWASP mailing list. 8) Facilitate secure network implementation Verified by observation of SecureCall running in the test lab that it does not interfere with security appliances or applications running in the test environment. These applications and appliances were included in the test lab setup and are listed in the executive summary. 9) Cardholder data must never be stored on a server connected to the Internet Verified by observation of the application running in the test lab and by a forensic examination of the test systems that cardholder data is never stored by the SecureCall application. 10) Facilitate secure remote access to payment application Verified by observation of a remote 2-factor authentication event that SecureCall does not interfere with the ability to make a 2-factor remote connection. The factors observed were a username/password combination and a PhoneFactor token
12 11) Encrypt sensitive traffic over public networks Verified by observation of the application running in the test lab that it never sends cardholder data over public networks. However, the data sent by SecureCall to the call centers payment application is encrypted using AES-256 encryption even though it only transits the call centers private network. 12) Encrypt all non-console administrative access Verified by observation of the installation guide that customers are instructed to encrypt all non-console administrative access. The method suggested is to turn encryption on when using RDP to access the systems remotely. 13) Maintain instructional documentation and training programs Verified by interview with Dave and by observation of the installation guide that instruction is given to customers for the installation of SecureCall in a PCI-DSS compliant environment. Also, that KomBea provides training either in their offices in Lehi or on site at the customers location
13 Conclusion Not all applications that touch cardholder data are in scope for PA-DSS because they are not part of authorization or settlement and as such cannot be listed on the PCI Councils list of validated payment applications, but security concerns still exist regarding these applications. KomBea wished to address these concerns by having their application validated in the same manner as any payment application. SecureCall was assessed against the Payment Application Data Security Standard version 2.0 and was found to be in compliance with all the requirements that were applicable. In essence using SecureCall poses no greater security risk than any application that is listed on the PCI Councils web site. After conducting an assessment of the KomBea SecureCall v2.0 application and visiting the KomBea offices located in Lehi, Utah and observing their development practices it was determined that using the SecureCall application does not compromise the PCI- DSS compliance of the environment where it is installed in any way. It was further found that not only does it not interfere with PCI compliance but also it has the ability to greatly enhance the security of the environment it is installed in, as well as reducing the scope of the environments PCI assessment. Bruce Bogdan, CISSP, QSA, PA-QSA SecurityMetrics Inc. Senior Security Analyst
Payment Application Data Security Standard
 Payment Card Industry (PCI) Payment Application Data Security Standard ROV Reporting Instructions for PA-DSS v2.0 March 2012 Changes Date March 2012 Version Description Pages 1.0 To introduce PA-DSS ROV
Payment Card Industry (PCI) Payment Application Data Security Standard ROV Reporting Instructions for PA-DSS v2.0 March 2012 Changes Date March 2012 Version Description Pages 1.0 To introduce PA-DSS ROV
PLACE GROUP UK LONDON STUDENT HOUSING GROUP PAYMENT CARD INDUSTRY DATA SECURITY STANDARD COMPLIANCE STATEMENT PCI DSS (09) VERSION: 2009PCIDSSP4S01
 PLACE GROUP UK LONDON STUDENT HOUSING GROUP PAYMENT CARD INDUSTRY DATA SECURITY STANDARD COMPLIANCE STATEMENT PCI DSS (09) VERSION: 2009PCIDSSP4S01 Information updated: 21 October 2012 SAFEGUARDING CARDHOLDER
PLACE GROUP UK LONDON STUDENT HOUSING GROUP PAYMENT CARD INDUSTRY DATA SECURITY STANDARD COMPLIANCE STATEMENT PCI DSS (09) VERSION: 2009PCIDSSP4S01 Information updated: 21 October 2012 SAFEGUARDING CARDHOLDER
A MERCHANTS GUIDE TO THE PAYMENT APPLICATION DATA SECURITY STANDARD (PA-DSS)
 A MERCHANTS GUIDE TO THE PAYMENT APPLICATION DATA SECURITY STANDARD (PA-DSS) The mandatory guide for storing, processing or transmitting cardholder information Overview and applicability Any application
A MERCHANTS GUIDE TO THE PAYMENT APPLICATION DATA SECURITY STANDARD (PA-DSS) The mandatory guide for storing, processing or transmitting cardholder information Overview and applicability Any application
Credit Card Processing Overview
 CardControl 3.0 Credit Card Processing Overview Overview Credit card processing is a very complex and important system for anyone that sells goods. This guide will hopefully help educate and inform new
CardControl 3.0 Credit Card Processing Overview Overview Credit card processing is a very complex and important system for anyone that sells goods. This guide will hopefully help educate and inform new
PCI DSS Compliance for Cloud-Based Contact Centers Mitigating Liability through the Standardization of Processes for cloud-based contact centers.
 PCI DSS Compliance for Cloud-Based Contact Centers Mitigating Liability through the Standardization of Processes for cloud-based contact centers. White Paper January 2013 1 INTRODUCTION The PCI SSC (Payment
PCI DSS Compliance for Cloud-Based Contact Centers Mitigating Liability through the Standardization of Processes for cloud-based contact centers. White Paper January 2013 1 INTRODUCTION The PCI SSC (Payment
CardControl. Credit Card Processing 101. Overview. Contents
 CardControl Credit Card Processing 101 Overview Credit card processing is a very complex and important system for anyone that sells goods. This guide will hopefully help educate and inform new and old
CardControl Credit Card Processing 101 Overview Credit card processing is a very complex and important system for anyone that sells goods. This guide will hopefully help educate and inform new and old
PCI Assessments 3.0 What Will the Future Bring? Matt Halbleib, SecurityMetrics
 PCI Assessments 3.0 What Will the Future Bring? Matt Halbleib, SecurityMetrics About Us Matt Halbleib CISSP, QSA, PA-QSA Manager PCI-DSS assessments With SecurityMetrics for 6+ years SecurityMetrics Security
PCI Assessments 3.0 What Will the Future Bring? Matt Halbleib, SecurityMetrics About Us Matt Halbleib CISSP, QSA, PA-QSA Manager PCI-DSS assessments With SecurityMetrics for 6+ years SecurityMetrics Security
Implementation Guide
 Implementation Guide PayLINK Implementation Guide Version 2.1.252 Released September 17, 2013 Copyright 2011-2013, BridgePay Network Solutions, Inc. All rights reserved. The information contained herein
Implementation Guide PayLINK Implementation Guide Version 2.1.252 Released September 17, 2013 Copyright 2011-2013, BridgePay Network Solutions, Inc. All rights reserved. The information contained herein
Josiah Wilkinson Internal Security Assessor. Nationwide
 Josiah Wilkinson Internal Security Assessor Nationwide Payment Card Industry Overview PCI Governance/Enforcement Agenda PCI Data Security Standard Penalties for Non-Compliance Keys to Compliance Challenges
Josiah Wilkinson Internal Security Assessor Nationwide Payment Card Industry Overview PCI Governance/Enforcement Agenda PCI Data Security Standard Penalties for Non-Compliance Keys to Compliance Challenges
PCI PA - DSS. Point XSA Implementation Guide. Atos Worldline Banksys XENTA SA. Version 1.00
 PCI PA - DSS Point XSA Implementation Guide Atos Worldline Banksys XENTA SA Version 1.00 POINT TRANSACTION SYSTEMS AB Box 92031, 120 06 Stockholm, Tel. +46 8 566 287 00 www.point.se Page number 2 (16)
PCI PA - DSS Point XSA Implementation Guide Atos Worldline Banksys XENTA SA Version 1.00 POINT TRANSACTION SYSTEMS AB Box 92031, 120 06 Stockholm, Tel. +46 8 566 287 00 www.point.se Page number 2 (16)
Payment Card Industry Security Standards PCI DSS, PCI-PTS and PA-DSS
 The PCI Security Standards Council http://www.pcisecuritystandards.org The OWASP Foundation http://www.owasp.org Payment Card Industry Security Standards PCI DSS, PCI-PTS and PA-DSS Omar F. Khandaker,
The PCI Security Standards Council http://www.pcisecuritystandards.org The OWASP Foundation http://www.owasp.org Payment Card Industry Security Standards PCI DSS, PCI-PTS and PA-DSS Omar F. Khandaker,
Qualified Integrators and Resellers (QIR) Implementation Statement
 Qualified Integrators and Resellers (QIR) Implementation Statement For each Qualified Installation performed, the QIR Employee must complete this document and confirm whether the validated payment application
Qualified Integrators and Resellers (QIR) Implementation Statement For each Qualified Installation performed, the QIR Employee must complete this document and confirm whether the validated payment application
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
PCI Requirements Coverage Summary Table
 StillSecure PCI Complete Managed PCI Compliance Solution PCI Requirements Coverage Summary Table January 2013 Table of Contents Introduction... 2 Coverage assumptions for PCI Complete deployments... 2
StillSecure PCI Complete Managed PCI Compliance Solution PCI Requirements Coverage Summary Table January 2013 Table of Contents Introduction... 2 Coverage assumptions for PCI Complete deployments... 2
PCI PA - DSS. Point ipos Implementation Guide. Version 1.01. VeriFone Vx820 using the Point ipos Payment Core
 PCI PA - DSS Point ipos Implementation Guide VeriFone Vx820 using the Point ipos Payment Core Version 1.01 POINT TRANSACTION SYSTEMS AB Box 92031, 120 06 Stockholm, Tel. +46 8 566 287 00 www.point.se Page
PCI PA - DSS Point ipos Implementation Guide VeriFone Vx820 using the Point ipos Payment Core Version 1.01 POINT TRANSACTION SYSTEMS AB Box 92031, 120 06 Stockholm, Tel. +46 8 566 287 00 www.point.se Page
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire D Service Providers For use with PCI DSS Version 3.1 Revision 1.1 July 2015 Section 1: Assessment
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire D Service Providers For use with PCI DSS Version 3.1 Revision 1.1 July 2015 Section 1: Assessment
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
PCI PA - DSS. Point BKX Implementation Guide. Version 2.01. Atos Xenta, Atos Xenteo and Atos Yomani using the Point BKX Payment Core
 PCI PA - DSS Point BKX Implementation Guide Atos Xenta, Atos Xenteo and Atos Yomani using the Point BKX Payment Core Version 2.01 POINT TRANSACTION SYSTEMS AB Box 92031, 120 06 Stockholm, Tel. +46 8 566
PCI PA - DSS Point BKX Implementation Guide Atos Xenta, Atos Xenteo and Atos Yomani using the Point BKX Payment Core Version 2.01 POINT TRANSACTION SYSTEMS AB Box 92031, 120 06 Stockholm, Tel. +46 8 566
TNHFMA 2011 Fall Institute October 12, 2011 TAKING OUR CUSTOMERS BUSINESS FORWARD. The Cost of Payment Card Data Theft and Your Business
 TAKING OUR CUSTOMERS BUSINESS FORWARD The Cost of Payment Card Data Theft and Your Business Aaron Lego Director of Business Development Presentation Agenda Items we will cover: 1. Background on Payment
TAKING OUR CUSTOMERS BUSINESS FORWARD The Cost of Payment Card Data Theft and Your Business Aaron Lego Director of Business Development Presentation Agenda Items we will cover: 1. Background on Payment
SecurityMetrics Introduction to PCI Compliance
 SecurityMetrics Introduction to PCI Compliance Card Data Compromise What is a card data compromise? A card data compromise occurs when payment card information is stolen from a merchant. Some examples
SecurityMetrics Introduction to PCI Compliance Card Data Compromise What is a card data compromise? A card data compromise occurs when payment card information is stolen from a merchant. Some examples
PCI Requirements Coverage Summary Table
 StillSecure PCI Complete Managed PCI Compliance Solution PCI Requirements Coverage Summary Table December 2011 Table of Contents Introduction... 2 Coverage assumptions for PCI Complete deployments... 2
StillSecure PCI Complete Managed PCI Compliance Solution PCI Requirements Coverage Summary Table December 2011 Table of Contents Introduction... 2 Coverage assumptions for PCI Complete deployments... 2
Ruby VASC Instructor Guide
 Ruby VASC Instructor Guide Client Services, Training 300 S. Park Place Blvd. Suite 100 727.953.4000 Main Reception 727.953.4270 Training Administration 727.953.4001 - Fax [email protected]
Ruby VASC Instructor Guide Client Services, Training 300 S. Park Place Blvd. Suite 100 727.953.4000 Main Reception 727.953.4270 Training Administration 727.953.4001 - Fax [email protected]
AIS Webinar. Payment Application Security. Hap Huynh Business Leader Visa Inc. 1 April 2009
 AIS Webinar Payment Application Security Hap Huynh Business Leader Visa Inc. 1 April 2009 1 Agenda Security Environment Payment Application Security Overview Questions and Comments Payment Application
AIS Webinar Payment Application Security Hap Huynh Business Leader Visa Inc. 1 April 2009 1 Agenda Security Environment Payment Application Security Overview Questions and Comments Payment Application
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
Need to be PCI DSS compliant and reduce the risk of fraud?
 Need to be PCI DSS compliant and reduce the risk of fraud? NCR Security lessens your PCI compliance burden and protects the integrity of your network An NCR White Paper Experience a new world of interaction
Need to be PCI DSS compliant and reduce the risk of fraud? NCR Security lessens your PCI compliance burden and protects the integrity of your network An NCR White Paper Experience a new world of interaction
Project Title slide Project: PCI. Are You At Risk?
 Blank slide Project Title slide Project: PCI Are You At Risk? Agenda Are You At Risk? Video What is the PCI SSC? Agenda What are the requirements of the PCI DSS? What Steps Can You Take? Available Services
Blank slide Project Title slide Project: PCI Are You At Risk? Agenda Are You At Risk? Video What is the PCI SSC? Agenda What are the requirements of the PCI DSS? What Steps Can You Take? Available Services
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
Visa U.S.A Cardholder Information Security Program (CISP) Payment Application Best Practices
 This document is to be used to verify that a payment application has been validated against Visa U.S.A. Payment Application Best Practices and to create the Report on Validation. Please note that payment
This document is to be used to verify that a payment application has been validated against Visa U.S.A. Payment Application Best Practices and to create the Report on Validation. Please note that payment
Point Secure Commerce Application (SCA) 2.x PCI PA-DSS Out of Scope White Paper
 Point Secure Commerce Application (SCA) 2.x PCI PA-DSS Out of Scope White Paper Executive Summary Lyle Miller: CISSP, QSA PA-QSA December 3, 2013 VeriFone, Inc. (VeriFone) engaged Coalfire Systems Inc.
Point Secure Commerce Application (SCA) 2.x PCI PA-DSS Out of Scope White Paper Executive Summary Lyle Miller: CISSP, QSA PA-QSA December 3, 2013 VeriFone, Inc. (VeriFone) engaged Coalfire Systems Inc.
The Cost of Payment Card Data Theft and Your Business. Aaron Lego Director of Business Development
 The Cost of Payment Card Data Theft and Your Business Aaron Lego Director of Business Development Presentation Agenda Items we will cover: 1. Background on Payment Card Industry Data Security Standards
The Cost of Payment Card Data Theft and Your Business Aaron Lego Director of Business Development Presentation Agenda Items we will cover: 1. Background on Payment Card Industry Data Security Standards
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Standard Attestation of Compliance for Self-Assessment Questionnaire D Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Standard Attestation of Compliance for Self-Assessment Questionnaire D Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Payment Application Data Security Standard
 Payment Card Industry (PCI) Payment Application Data Security Standard Requirements and Security Assessment Procedures Version 2.0 October 2010 Document Changes Date Version Description Pages October 1,
Payment Card Industry (PCI) Payment Application Data Security Standard Requirements and Security Assessment Procedures Version 2.0 October 2010 Document Changes Date Version Description Pages October 1,
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
PA-DSS Implementation Guide. Version 1.2.1. Document Owners. Approval Date: January 2012
 v Tuition Express PA-DSS Implementation Guide Version 1.2.1 Approval Date: January 2012 Document Owners Brad Olson Operations Director Darren Gapp Chief System/Software Engineer Procare Software Tuition
v Tuition Express PA-DSS Implementation Guide Version 1.2.1 Approval Date: January 2012 Document Owners Brad Olson Operations Director Darren Gapp Chief System/Software Engineer Procare Software Tuition
ARE YOU REALLY PCI DSS COMPLIANT? Case Studies of PCI DSS Failure! Jeff Foresman, PCI-QSA, CISSP Partner PONDURANCE
 ARE YOU REALLY PCI DSS COMPLIANT? Case Studies of PCI DSS Failure! Jeff Foresman, PCI-QSA, CISSP Partner PONDURANCE AGENDA PCI DSS Basics Case Studies of PCI DSS Failure! Common Problems with PCI DSS Compliance
ARE YOU REALLY PCI DSS COMPLIANT? Case Studies of PCI DSS Failure! Jeff Foresman, PCI-QSA, CISSP Partner PONDURANCE AGENDA PCI DSS Basics Case Studies of PCI DSS Failure! Common Problems with PCI DSS Compliance
To ensure independence, PSC does not represent, resell or receive commissions from any third party hardware, software or solutions vendors.
 About PSC With offices in the USA, Canada, UK and Australia, PSC is a leading PCI, PA DSS, and P2PE assessor, PCI Forensics Company and Approved Scanning Vendor. PSC is one of an elite few companies qualified
About PSC With offices in the USA, Canada, UK and Australia, PSC is a leading PCI, PA DSS, and P2PE assessor, PCI Forensics Company and Approved Scanning Vendor. PSC is one of an elite few companies qualified
Case 2:13-cv-01887-ES-JAD Document 282-2 Filed 12/09/15 Page 1 of 116 PageID: 4879. Appendix A
 Case 2:13-cv-01887-ES-JAD Document 282-2 Filed 12/09/15 Page 1 of 116 PageID: 4879 Appendix A Case 2:13-cv-01887-ES-JAD Document 282-2 Filed 12/09/15 Page 2 of 116 PageID: 4880 Payment Card Industry (PCI)
Case 2:13-cv-01887-ES-JAD Document 282-2 Filed 12/09/15 Page 1 of 116 PageID: 4879 Appendix A Case 2:13-cv-01887-ES-JAD Document 282-2 Filed 12/09/15 Page 2 of 116 PageID: 4880 Payment Card Industry (PCI)
Security Breaches and Vulnerability Experiences Overview of PCI DSS Initiative and CISP Payment Application Best Practices Questions and Comments
 Security in the Payment Card Industry OWASP AppSec Seattle Oct 2006 Hap Huynh, Information Security Specialist, Visa USA [email protected] Copyright 2006 - The OWASP Foundation Permission is granted to copy,
Security in the Payment Card Industry OWASP AppSec Seattle Oct 2006 Hap Huynh, Information Security Specialist, Visa USA [email protected] Copyright 2006 - The OWASP Foundation Permission is granted to copy,
Four Keys to Preparing for a PCI DSS 3.0 Assessment
 A division of Sikich LLP Four Keys to Preparing for a PCI DSS 3.0 Assessment Jeff Tucker, QSA [email protected] September 16, 2014 NEbraskaCERT Cyber Security Forum About 403 Labs 403 Labs, a division
A division of Sikich LLP Four Keys to Preparing for a PCI DSS 3.0 Assessment Jeff Tucker, QSA [email protected] September 16, 2014 NEbraskaCERT Cyber Security Forum About 403 Labs 403 Labs, a division
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Key Steps to Meeting PCI DSS 2.0 Requirements Using Sensitive Data Discovery and Masking
 Key Steps to Meeting PCI DSS 2.0 Requirements Using Sensitive Data Discovery and Masking SUMMARY The Payment Card Industry Data Security Standard (PCI DSS) defines 12 high-level security requirements directed
Key Steps to Meeting PCI DSS 2.0 Requirements Using Sensitive Data Discovery and Masking SUMMARY The Payment Card Industry Data Security Standard (PCI DSS) defines 12 high-level security requirements directed
paypoint implementation guide
 paypoint implementation guide PCI PA-DSS Implementation guide 1. Introduction This PA-DSS Implementation Guide contains information for proper use of the paypoint application. Point Transaction Systems
paypoint implementation guide PCI PA-DSS Implementation guide 1. Introduction This PA-DSS Implementation Guide contains information for proper use of the paypoint application. Point Transaction Systems
BAE Systems PCI Essentail. PCI Requirements Coverage Summary Table
 BAE Systems PCI Essentail PCI Requirements Coverage Summary Table Introduction BAE Systems PCI Essential solution can help your company significantly reduce the costs and complexity of meeting PCI compliance
BAE Systems PCI Essentail PCI Requirements Coverage Summary Table Introduction BAE Systems PCI Essential solution can help your company significantly reduce the costs and complexity of meeting PCI compliance
Data Security for the Hospitality
 M&T Bank and SecurityMetrics Present: Data Security for the Hospitality Industry Featuring Lee Pierce, SecurityMetricsStrategicStrategic Accounts Dave Ellis, SecurityMetrics Forensic Investigator Doug
M&T Bank and SecurityMetrics Present: Data Security for the Hospitality Industry Featuring Lee Pierce, SecurityMetricsStrategicStrategic Accounts Dave Ellis, SecurityMetrics Forensic Investigator Doug
PCI DSS FAQ. The twelve requirements of the PCI DSS are defined as follows:
 What is PCI DSS? PCI DSS is an acronym for Payment Card Industry Data Security Standards. PCI DSS is a global initiative intent on securing credit and banking transactions by merchants & service providers
What is PCI DSS? PCI DSS is an acronym for Payment Card Industry Data Security Standards. PCI DSS is a global initiative intent on securing credit and banking transactions by merchants & service providers
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
PA-DSS Implementation Guide for. Sage MAS 90 and 200 ERP. Credit Card Processing
 for Sage MAS 90 and 200 ERP Credit Card Processing Version 4.30.0.18 and 4.40.0.1 - January 28, 2010 Sage, the Sage logos and the Sage product and service names mentioned herein are registered trademarks
for Sage MAS 90 and 200 ERP Credit Card Processing Version 4.30.0.18 and 4.40.0.1 - January 28, 2010 Sage, the Sage logos and the Sage product and service names mentioned herein are registered trademarks
3M SelfCheck Self-Pay Software. Implementation Guide
 3M SelfCheck Self-Pay Software Implementation Guide 3M SelfCheck Self-Pay Software Implementation Guide, 78-8800-0302-1a 3M 2014. All rights reserved. 3M is a trademark of 3M. Microsoft, Windows, Vista,
3M SelfCheck Self-Pay Software Implementation Guide 3M SelfCheck Self-Pay Software Implementation Guide, 78-8800-0302-1a 3M 2014. All rights reserved. 3M is a trademark of 3M. Microsoft, Windows, Vista,
University of Sunderland Business Assurance PCI Security Policy
 University of Sunderland Business Assurance PCI Security Policy Document Classification: Public Policy Reference Central Register IG008 Policy Reference Faculty / Service IG 008 Policy Owner Chief Financial
University of Sunderland Business Assurance PCI Security Policy Document Classification: Public Policy Reference Central Register IG008 Policy Reference Faculty / Service IG 008 Policy Owner Chief Financial
PDQ Guide for the PCI Data Security Standard Self-Assessment Questionnaire C (Version 1.1)
 PDQ has created an Answer Guide for the Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire C to help wash operators complete questionnaires. Part of the Access Customer Management
PDQ has created an Answer Guide for the Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire C to help wash operators complete questionnaires. Part of the Access Customer Management
Payment Card Industry Data Security Standard (PCI DSS) and Payment Application Data Security Standard (PA-DSS) Frequently Asked Questions
 PCI/PA-DSS FAQs Payment Card Industry Data Security Standard (PCI DSS) and Payment Application Data Security Standard (PA-DSS) Frequently Asked Questions What is PCI DSS? The Payment Card Industry Data
PCI/PA-DSS FAQs Payment Card Industry Data Security Standard (PCI DSS) and Payment Application Data Security Standard (PA-DSS) Frequently Asked Questions What is PCI DSS? The Payment Card Industry Data
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
PCI-DSS: A Step-by-Step Payment Card Security Approach. Amy Mushahwar & Mason Weisz
 PCI-DSS: A Step-by-Step Payment Card Security Approach Amy Mushahwar & Mason Weisz The PCI-DSS in a Nutshell It mandates security processes for handling, processing, storing and transmitting payment card
PCI-DSS: A Step-by-Step Payment Card Security Approach Amy Mushahwar & Mason Weisz The PCI-DSS in a Nutshell It mandates security processes for handling, processing, storing and transmitting payment card
PCI Compliance for Cloud Applications
 What Is It? The Payment Card Industry Data Security Standard (PCIDSS), in particular v3.0, aims to reduce credit card fraud by minimizing the risks associated with the transmission, processing, and storage
What Is It? The Payment Card Industry Data Security Standard (PCIDSS), in particular v3.0, aims to reduce credit card fraud by minimizing the risks associated with the transmission, processing, and storage
What are the PCI DSS requirements? PCI DSS comprises twelve requirements, often referred to as the digital dozen. These define the need to:
 What is the PCI standards council? The Payment Card Industry Standards Council is an institution set-up by American Express, Discover Financial Services, JCB, MasterCard Worldwide and Visa International
What is the PCI standards council? The Payment Card Industry Standards Council is an institution set-up by American Express, Discover Financial Services, JCB, MasterCard Worldwide and Visa International
PCI PA-DSS Requirements. For hardware vendors
 PCI PA-DSS Requirements For hardware vendors PCI security services UL's streamlined PCI PA-DSS certification services get your product to market faster. UL is world leader in advancing safety. Through
PCI PA-DSS Requirements For hardware vendors PCI security services UL's streamlined PCI PA-DSS certification services get your product to market faster. UL is world leader in advancing safety. Through
PCI Compliance Training
 PCI Compliance Training 1 PCI Training Topics Applicable PCI Standards Compliance Requirements Compliance of Unitec products Requirements for compliant installation and use of products 2 PCI Standards
PCI Compliance Training 1 PCI Training Topics Applicable PCI Standards Compliance Requirements Compliance of Unitec products Requirements for compliant installation and use of products 2 PCI Standards
PCI Compliance Overview
 PCI Compliance Overview 1 PCI DSS Payment Card Industry Data Security Standard Standard that is applied to: Merchants Service Providers (Banks, Third party vendors, gateways) Systems (Hardware, software)
PCI Compliance Overview 1 PCI DSS Payment Card Industry Data Security Standard Standard that is applied to: Merchants Service Providers (Banks, Third party vendors, gateways) Systems (Hardware, software)
Puzzled about PCI compliance? Proactive ways to navigate through the standard for compliance
 Puzzled about PCI compliance? Proactive ways to navigate through the standard for compliance March 29, 2012 1:00 p.m. ET If you experience any technical difficulties, please contact 888.228.0988 or [email protected]
Puzzled about PCI compliance? Proactive ways to navigate through the standard for compliance March 29, 2012 1:00 p.m. ET If you experience any technical difficulties, please contact 888.228.0988 or [email protected]
Payment Card Industry (PCI) Data Security Standard ROC Reporting Instructions for PCI DSS v2.0
 Payment Card Industry (PCI) Data Security Standard ROC Reporting Instructions for PCI DSS v2.0 September 2011 Changes Date September 2011 Version Description 1.0 To introduce PCI DSS ROC Reporting Instructions
Payment Card Industry (PCI) Data Security Standard ROC Reporting Instructions for PCI DSS v2.0 September 2011 Changes Date September 2011 Version Description 1.0 To introduce PCI DSS ROC Reporting Instructions
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire B and Attestation of Compliance
 Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire B and Attestation of Compliance Imprint Machines or Stand-alone Dial-out Terminals Only, no Electronic Cardholder Data Storage
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire B and Attestation of Compliance Imprint Machines or Stand-alone Dial-out Terminals Only, no Electronic Cardholder Data Storage
Payment Card Industry (PCI) Data Security Standard. Attestation of Compliance for Self-Assessment Questionnaire C-VT. Version 2.0
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire C-VT Version 2.0 October 2010 Attestation of Compliance, SAQ C-VT Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire C-VT Version 2.0 October 2010 Attestation of Compliance, SAQ C-VT Instructions for Submission
Frequently Asked Questions
 PCI Compliance Frequently Asked Questions Table of Content GENERAL INFORMATION... 2 PAYMENT CARD INDUSTRY DATA SECURITY STANDARD (PCI DSS)...2 Are all merchants and service providers required to comply
PCI Compliance Frequently Asked Questions Table of Content GENERAL INFORMATION... 2 PAYMENT CARD INDUSTRY DATA SECURITY STANDARD (PCI DSS)...2 Are all merchants and service providers required to comply
Retour d'expérience PCI DSS
 Retour d'expérience PCI DSS Frédéric Charpentier OSSIR : Retour d'expérience PCI DSS - 1 XMCO PARTNERS : Who are we? Xmco Partners is a consulting company specialized in IT security and advisory Xmco Partners
Retour d'expérience PCI DSS Frédéric Charpentier OSSIR : Retour d'expérience PCI DSS - 1 XMCO PARTNERS : Who are we? Xmco Partners is a consulting company specialized in IT security and advisory Xmco Partners
Attestation of Compliance for Onsite Assessments Service Providers
 Attestation of Compliance Service Providers Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 2.0 October 2010 Instructions for
Attestation of Compliance Service Providers Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 2.0 October 2010 Instructions for
Are You Ready For PCI v 3.0. Speaker: Corbin DelCarlo Institution: McGladrey LLP Date: October 6, 2014
 Are You Ready For PCI v 3.0 Speaker: Corbin DelCarlo Institution: McGladrey LLP Date: October 6, 2014 Today s Presenter Corbin Del Carlo QSA, PA QSA Director, National Leader PCI Services Practice 847.413.6319
Are You Ready For PCI v 3.0 Speaker: Corbin DelCarlo Institution: McGladrey LLP Date: October 6, 2014 Today s Presenter Corbin Del Carlo QSA, PA QSA Director, National Leader PCI Services Practice 847.413.6319
Technical breakout session
 Technical breakout session Small leaks sink great ships Managing data security, fraud and privacy risks Tarlok Birdi, Deloitte Ron Borsholm, WTS May 27, 2009 Agenda 1. PCI overview: the technical intent
Technical breakout session Small leaks sink great ships Managing data security, fraud and privacy risks Tarlok Birdi, Deloitte Ron Borsholm, WTS May 27, 2009 Agenda 1. PCI overview: the technical intent
8/17/2010. Over 90% of all compromised merchants are PCI level 4 (small) merchants or merchants with less than 1 million transactions per year
 Over 90% of all compromised merchants are PCI level 4 (small) merchants or merchants with less than 1 million transactions per year Over 80% of compromised systems were card present or in-person transactions
Over 90% of all compromised merchants are PCI level 4 (small) merchants or merchants with less than 1 million transactions per year Over 80% of compromised systems were card present or in-person transactions
1/18/10. Walt Conway. PCI DSS in Context. Some History The Digital Dozen Key Players Cardholder Data Outsourcing Conclusions. PCI in Higher Education
 PCI in Higher Education Walter Conway, QSA 403 Labs, LLC Walt Conway PCI consultant, blogger, trainer, speaker, author Former Visa VP Help schools become PCI compliant Represent Higher Education at PCI
PCI in Higher Education Walter Conway, QSA 403 Labs, LLC Walt Conway PCI consultant, blogger, trainer, speaker, author Former Visa VP Help schools become PCI compliant Represent Higher Education at PCI
Miami University. Payment Card Data Security Policy
 Miami University Payment Card Data Security Policy IT Policy IT Standard IT Guideline IT Procedure IT Informative Issued by: IT Services SCOPE: This policy covers all units within Miami University that
Miami University Payment Card Data Security Policy IT Policy IT Standard IT Guideline IT Procedure IT Informative Issued by: IT Services SCOPE: This policy covers all units within Miami University that
Attestation of Compliance for Onsite Assessments Service Providers
 Attestation of Compliance Service Providers Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 2.0 October 2010 Instructions for
Attestation of Compliance Service Providers Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 2.0 October 2010 Instructions for
Visa Asia Pacific Account Information Security (AIS) Program Payment Application Best Practices (PABP)
 Visa Asia Pacific Account Information Security (AIS) Program Payment Application Best Practices (PABP) This document is to be used for payment application vendors to validate that the payment application
Visa Asia Pacific Account Information Security (AIS) Program Payment Application Best Practices (PABP) This document is to be used for payment application vendors to validate that the payment application
Network Segmentation
 Network Segmentation The clues to switch a PCI DSS compliance s nightmare into an easy path Although best security practices should be implemented in all systems of an organization, whether critical or
Network Segmentation The clues to switch a PCI DSS compliance s nightmare into an easy path Although best security practices should be implemented in all systems of an organization, whether critical or
Office of Finance and Treasury
 Office of Finance and Treasury How to Accept & Process Credit and Debit Card Transactions Procedure Related Policy Title Credit Card Processing Policy For University Merchant Locations Responsible Executive
Office of Finance and Treasury How to Accept & Process Credit and Debit Card Transactions Procedure Related Policy Title Credit Card Processing Policy For University Merchant Locations Responsible Executive
Don Roeber Vice President, PCI Compliance Manager. Lisa Tedeschi Assistant Vice President, Compliance Officer
 Complying with the PCI DSS All the Moving Parts Don Roeber Vice President, PCI Compliance Manager Lisa Tedeschi Assistant Vice President, Compliance Officer Types of Risk Operational Risk Normal fraud
Complying with the PCI DSS All the Moving Parts Don Roeber Vice President, PCI Compliance Manager Lisa Tedeschi Assistant Vice President, Compliance Officer Types of Risk Operational Risk Normal fraud
Becoming PCI Compliant
 Becoming PCI Compliant Jason Brown - [email protected] Enterprise Security Architect Enterprise Architecture Department of Technology, Management and Budget State of Michigan @jasonbrown17 History
Becoming PCI Compliant Jason Brown - [email protected] Enterprise Security Architect Enterprise Architecture Department of Technology, Management and Budget State of Michigan @jasonbrown17 History
Enforcing PCI Data Security Standard Compliance
 Enforcing PCI Data Security Standard Compliance Marco Misitano, CISSP, CISA, CISM Business Development Manager Security & VideoSurveillance Cisco Italy 2008 Cisco Systems, Inc. All rights reserved. 1 The
Enforcing PCI Data Security Standard Compliance Marco Misitano, CISSP, CISA, CISM Business Development Manager Security & VideoSurveillance Cisco Italy 2008 Cisco Systems, Inc. All rights reserved. 1 The
Customer PCI 3.0 Changes = New Opportunity For You. Giles Witherspoon-Boyd SecurityMetrics
 Customer PCI 3.0 Changes = New Opportunity For You Giles Witherspoon-Boyd SecurityMetrics Who is this guy? Giles Witherspoon-Boyd, PCIP 15 years in technology, 4 years at SecurityMetrics SecurityMetrics
Customer PCI 3.0 Changes = New Opportunity For You Giles Witherspoon-Boyd SecurityMetrics Who is this guy? Giles Witherspoon-Boyd, PCIP 15 years in technology, 4 years at SecurityMetrics SecurityMetrics
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission
PCI DSS 101 FOR CTOs AND BUSINESS EXECUTIVES
 PCI DSS 101 FOR CTOs AND BUSINESS EXECUTIVES CUTTING THROUGH THE COMPLEXITY AND CONFUSION Over the years, South African retailers have come under increased pressure to gain PCI DSS (Payment Card Industry
PCI DSS 101 FOR CTOs AND BUSINESS EXECUTIVES CUTTING THROUGH THE COMPLEXITY AND CONFUSION Over the years, South African retailers have come under increased pressure to gain PCI DSS (Payment Card Industry
PCI Compliance. What is New in Payment Card Industry Compliance Standards. October 2015. cliftonlarsonallen.com. 2015 CliftonLarsonAllen LLP
 cliftonlarsonallen.com PCI Compliance What is New in Payment Card Industry Compliance Standards October 2015 Overview PCI DSS In the beginning Each major card brand had its own separate criteria for implementing
cliftonlarsonallen.com PCI Compliance What is New in Payment Card Industry Compliance Standards October 2015 Overview PCI DSS In the beginning Each major card brand had its own separate criteria for implementing
Top Five Data Security Trends Impacting Franchise Operators. Payment System Risk September 29, 2009
 Top Five Data Security Trends Impacting Franchise Operators Payment System Risk September 29, 2009 Top Five Data Security Trends Agenda Data Security Environment Compromise Overview and Attack Methods
Top Five Data Security Trends Impacting Franchise Operators Payment System Risk September 29, 2009 Top Five Data Security Trends Agenda Data Security Environment Compromise Overview and Attack Methods
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance
 Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance Card-not-present Merchants, All Cardholder Data Functions Fully Outsourced Version 3.0 February
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance Card-not-present Merchants, All Cardholder Data Functions Fully Outsourced Version 3.0 February
Presented By: Bryan Miller CCIE, CISSP
 Presented By: Bryan Miller CCIE, CISSP Introduction Why the Need History of PCI Terminology The Current Standard Who Must Be Compliant and When What Makes this Standard Different Roadmap to Compliance
Presented By: Bryan Miller CCIE, CISSP Introduction Why the Need History of PCI Terminology The Current Standard Who Must Be Compliant and When What Makes this Standard Different Roadmap to Compliance
PCI Compliance. Top 10 Questions & Answers
 PCI Compliance Top 10 Questions & Answers 1. What is PCI Compliance and PCI DSS? 2. Who needs to follow the PCI Data Security Standard? 3. What happens if I don t comply? 4. What are the basic requirements
PCI Compliance Top 10 Questions & Answers 1. What is PCI Compliance and PCI DSS? 2. Who needs to follow the PCI Data Security Standard? 3. What happens if I don t comply? 4. What are the basic requirements
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire B and Attestation of Compliance
 Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire B and Attestation of Compliance Merchants with Only Imprint Machines or Only Standalone, Dial-out Terminals Electronic Cardholder
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire B and Attestation of Compliance Merchants with Only Imprint Machines or Only Standalone, Dial-out Terminals Electronic Cardholder
PCI DSS Overview. By Kishor Vaswani CEO, ControlCase
 PCI DSS Overview By Kishor Vaswani CEO, ControlCase Agenda About PCI DSS PCI DSS Applicability to Banks, Merchants and Service Providers PCI DSS Technical Requirements Overview of PCI DSS 3.0 Changes Key
PCI DSS Overview By Kishor Vaswani CEO, ControlCase Agenda About PCI DSS PCI DSS Applicability to Banks, Merchants and Service Providers PCI DSS Technical Requirements Overview of PCI DSS 3.0 Changes Key
PCI DSS Compliance. 2015 Information Pack for Merchants
 PCI DSS Compliance 2015 Information Pack for Merchants This pack contains general information regarding PCI DSS compliance and does not take into account your business' particular requirements. ANZ recommends
PCI DSS Compliance 2015 Information Pack for Merchants This pack contains general information regarding PCI DSS compliance and does not take into account your business' particular requirements. ANZ recommends
