The World of Collaborative Auditing
|
|
|
- Melissa Floyd
- 3 years ago
- Views:
Transcription
1 LOCKSS Auditing using the SAFE-Archive System Prepared for PLN2010 Boston College, Boston, MA Jonathan Crabtree October 26, 2010
2 The Odum Institute Oldest Institute or Center at UNC-CH Founded 1924 Mission: Teaching, research, & service for social sciences Cross-disciplinary focus
3 Collaborators Individual collaborators: Mark Abrahamson, Margaret Adams, Micah Altman, Caroline Arms, Ed Bachman, Adam Buchbinder, Ken Bollen, Bryan Beecher, Steve Burling, Darrell Donakowski, Myron Gutmann, Gary King, Patrick King, William Lefurgy, Freeman Lo, Jared Lyle, Marc Maynard, Amy Pienta, Akio Sone, Lois Timms-Ferrarra. Research Support Thanks to the IMLS (LG ) and to the Data-PASS member institutions for support of this research.
4 ICPSR Odum Institute Roper Center The Data-PASS Partners Henry A. Murray Research Archive Harvard-MIT Data Center National Archives and Records Administration
5 Replication Storage alone will not solve the problem of digital preservation. Academic materials have many enemies beyond natural bit rot: ideologies, governments, corporations, and inadequate budgets. It is essential that sound storage and administration practices are complemented with the institution of communities acting together to thwart attacks that are too strong or too extrinsic for such practices to protect against. (Maniatis et al. 2005, 41)
6 SAFE-Archive Project Funded under an IMLS award to IQSS, Harvard U. Open Source TRAC Based Audits Schema Based Policy Web-based Tools Adheres to LOCKSS Trust Model
7 SAFE-Archive Audit Server Components Red Hat LINUX Server Glassfish JAVA Server Faces MySQL Eclipse BIRT Web Viewer Custom Applications
8 What it does Facilitating collaborative replication and preservation with technology Collaborators declare explicit nonuniform resource commitments Policy records commitments, storage network properties Storage layer provides replication, integrity, freshness, versioning SAFE-Archive software provides monitoring, auditing, and provisioning
9 SAFE-Archive Design Central audit server collects network status Information gathered via servlet calls to LOCKSS caches Network status stored in local MySQL tables Audit uses XML schema in comparison with network status tables Policies transformed into schema via user based questionnaire Audit reports stored in both detailed XML file and report tables for presentation Web-based interfaces provided for raw data tables & formatted reports Audit reports are stored in secure file system along with policy schema used Solutions to audit problems automatically initiated by server State of network is compared with policy requirements Additional caches are instructed to harvest collections that are underreplicated
10 Program Design Five Central SAFE Subsystems SAFE Schema Manager SAFE LOCKSS Daemon Status Extractor SAFE Comparison Tool SAFE Web-based Reporting & Interfaces SAFE Preservation Enforcer
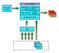
11
12 SAFE LOCKSS Daemon Status Extractor Identify LOCKSS caches to be audited User provided IP s Central Plug-in Registry & LOCKSS.XML User Provided Debug Account Http Servlet Calls to caches LOCKSS Caches return XML XML parsed into MySQL tables
13 Extractor Data Processing Iterations through data from various caches Required audit data stored in summary tables Automated cron jobs refresh data in user defined intervals
14 Inputs Extractor Inputs/Outputs Identity of LOCKSS caches to be audited Web-base user input of individual IP s Location of Plug-in registry & LOCKSS.XML Outputs Audit Summary Tables in MySQL Web-base Audit Table Viewer SAFE LOCKSS Daemon Status Data Viewer Provides input data for Schema Manager and Comparison tools
15 SAFE Schema Manager Web-based questionnaire user interface Policies expressed in human readable text Policies output into XML based schema Schema designed to be TRAC compliant
16 XML Based Questionnaire <?xml version="1.0" encoding="utf-8"?> <questionnaire xmlns:xsi=" xsi:nonamespaceschemalocation="questionnairedefinition.xsd"> <question> <questiontext>what is the name of the private LOCKSS network (PLN) that you would like the SAFE system to audit?</questiontext> <explanation>a private LOCKSS network (PLN) is a set of LOCKSS servers that are joined together to preserve your collections. Please select an existing PLN from the list or <!--LINK:-->define a new PLN<!--:/LINK-->.</explanation> <xpath>//ssp/network/networkidentity/name</xpath> </question> <question> <questiontext>what is the address of the PLN administrator?</questiontext> <answerformat>(\w+@(\w+\.)+\w+ )</answerformat> <xpath>//ssp/network/networkidentity/accessbase/@admin </xpath> <errortext>you must enter a valid address in this field!</errortext> </question> <selectionset> <selector> <!-- Question text if there is an explanation tag for a selector element <questiontext>please select the servers you wish to audit.</questiontext> <explanation>above is the list of LOCKSS servers available to audit the were discovered. Please select the servers that to audit. If a server is missing, you should LINK:reconfigure the PLN:/LINK.</explanation> -->
17 Web-based user interface
18 SAFE-Archive Policy Schema Network level: Identification: name; description; contact; access point URI Capabilities: protocol version; number of replicates maintained; replication frequency; versioning/deletion support Human readable documentation: restrictions on content that may be placed in the network; services guaranteed by the network; Virtual Organization policies relating to network maintenance Host level Identification: name; description; contact; access point URI Capabilities: protocol version; storage available Human readable terms of use: Documentation of hardware, software and operating personnel in support of TRAC criteria Archival unit level Identification: name; description; contact; access point URI Attributes: update frequency, plugin required for harvesting, storage required Terms of use: Required statement of content compliance with network terms. ; Dissemination terms and conditions TRAC Integration A number of elements comprise documentation showing how the replication system itself supports relevant TRAC criteria Other elements that may be use to include text, or reference external text that documents evidence of compliance with TRAC criteria. Specific TRAC criteria are identified implicitly, can be explicitly identified with attributes Schema documentation describes each elements relevance to TRAC, and mapping to particular TRAC criteria
19 Schema Instance <?xml version="1.0" encoding="utf-8" standalone="no"?> <SSP xmlns:xsi=" xsi:nonamespaceschemalocation="sspschema_v1_03.xsd"> <audit audit_id="safe-audit"> <schemeversion/> <auditreportinterval maxdays="1"/> </audit> <network> <networkidentity> <name>safe</name> <accessbase </networkidentity> <networkcapabilities/> <networkterms/> </network> <hosts> <host host_id=" "> <hostidentity> <name>fong.irss.unc.edu</name> </hostidentity> <hostcapabilities> <storageavailable max_size="10"/> </hostcapabilities> <hostterms/> </host>
20 Schema Manager Inputs/Outputs Inputs Web-base user policy selections Network details from Extractor Tool Outputs Schema.xml file
21 SAFE Comparison Tool Retrieves network status from tables Parses Schema.xml from Schema Manager Performs tag by tag comparisons Initiate unit conversions and data cleaning Prepare audit output Generate diff.xml difference report Create reporting tables Store reports in secure file system Schema.xml, diff.xml, birtreportdesign.xml, birtreport text/pdf
22 Current Policy Comparisons AU Level Comparisons Number of Verified Copies Number of copies with100% agreement AU Size Commitment Has the AU grown too large? Verification Frequency Time since last 100% agreement Crawl Frequency Time since last successful crawl Operational reporting Crawl Duration Amount of time during last crawl Host Level Comparisons Disk Space Commitment Are the servers providing correct storage? Network Level Comparisons None
23 Future Policy Comparisons AU Level Comparisons Geographic Distribution Are the AU s in distinct geographic regions? Operational reporting Display Current Agreement less than 100% Host Level Comparisons Geographic Distribution Operational reporting Health of Cache - Min Up Time, Max Unreachable Incidents, ETC Network Level Comparisons Minimum Free Disk Space Policy Minimum Number of Hosts Policy Geographic Distribution Policy
24 SAFE Audit Reporting Item by item detailed XML comparison Customizable BIRT web-based reports Web-based searchable audit history reports Web-based table view of current raw network status data
25 XML Based Reporting <hosts> <host host=" " seq_num="1"> <test> <schema_value> </schema_value> <db_column>ip_address</db_column> <db_value> </db_value> <match>true</match> </test> <test> <schema_value> </schema_value> <db_column>repo_size</db_column> <db_value> </db_value> <match>true</match> </test>
26 Customizable BIRT Reports Eclipse based XML style report design Web-based BIRT viewer provides simple access Required audit report templates included Cron jobs automatically store reports in secure file system Users can run manual reports on demand Advanced users can customize reports Multi-format report output PDF, Word, Excel, Postscript, Powerpoint BIRT Reports
27 Audit Report Snapshots Regular audit reports stored in file system Web-based display of audit materials Search by audit date range to be added Included with report are the associated files used in comparison. Schema.xml, Diff.xml, etc.
28 SAFE Preservation Enforcer Reads Schema.xml Reads Diff.xml audit report Determines policy Red Flags Determines provisioning solution Format query to LOCKSS cache Request harvest of AU Initiate a poll an Administrator Etc
29 SAFE Archive Challenges Integrate tools in user friendly web interface Audit time synchronization Schema versioning/instances AU/Collection/Plug-in management AU scalability Bulk file restoration Hardware level policy enforcement Streamline SAFE Audit Server installation and distribution Integrate and streamline PLN & LOCKSS creation & installation
30 Current Development Schedule Exposing Content and Policies [OCTOBER] Extensions to the Dataverse Network Systems -- easily enable curators to expose their content for LOCKSS harvesting [Fall 2010] Version 1.0 of the Safe-Archive schema and related documentation Support for policy based auditing [February 2011] Version 1.0 BETA of the SAFE-Archive system, -- policy creation, and auditing of LOCKSS network [March 2011] Version 1.0, release -- including Amazon AMI-based installation Automatic Provisioning [Fall 2011] Version supporting auto-reconfiguration of LOCKSS networks to reflect changes to policy schema Training [Fall 2011] Online courses and written guide
31 Contact Information data-pass.org Jonathan Crabtree
Data Management Resources at UNC: The Carolina Digital Repository and Dataverse Network
 Data Management Resources at UNC: The Carolina Digital Repository and Dataverse Network November 16, 2010 Data Management Short Course Series Sponsored by the Odum Institute and the UNC Libraries Campus
Data Management Resources at UNC: The Carolina Digital Repository and Dataverse Network November 16, 2010 Data Management Short Course Series Sponsored by the Odum Institute and the UNC Libraries Campus
Using Dataverse Virtual Archive Technology for Research Data Management. Jonathan Crabtree Thu-Mai Christian Amanda Gooch
 Using Dataverse Virtual Archive Technology for Research Data Management Jonathan Crabtree Thu-Mai Christian Amanda Gooch H. W. Odum Institute Archive Services The Howard W. Odum Institute was founded in
Using Dataverse Virtual Archive Technology for Research Data Management Jonathan Crabtree Thu-Mai Christian Amanda Gooch H. W. Odum Institute Archive Services The Howard W. Odum Institute was founded in
Data-PASS: Data Preservation Alliance for the Social Sciences
 P 1 Data-PASS: Data Preservation Alliance for the Social Sciences Articles of Collaboration The Data Preservation Alliance for the Social Sciences (Data-PASS) is a partnership sponsored by the Library
P 1 Data-PASS: Data Preservation Alliance for the Social Sciences Articles of Collaboration The Data Preservation Alliance for the Social Sciences (Data-PASS) is a partnership sponsored by the Library
TSM Studio Server User Guide 2.9.0.0
 TSM Studio Server User Guide 2.9.0.0 1 Table of Contents Disclaimer... 4 What is TSM Studio Server?... 5 System Requirements... 6 Database Requirements... 6 Installing TSM Studio Server... 7 TSM Studio
TSM Studio Server User Guide 2.9.0.0 1 Table of Contents Disclaimer... 4 What is TSM Studio Server?... 5 System Requirements... 6 Database Requirements... 6 Installing TSM Studio Server... 7 TSM Studio
Part A Odum Archive Operational Overview
 The Odum Institute Background Paper International Data Technology Alliance Workshop July 2009 Version: 7/01/2009 Introduction This background paper outlines the data archiving operation and technical schematics
The Odum Institute Background Paper International Data Technology Alliance Workshop July 2009 Version: 7/01/2009 Introduction This background paper outlines the data archiving operation and technical schematics
HP Insight Diagnostics Online Edition. Featuring Survey Utility and IML Viewer
 Survey Utility HP Industry Standard Servers June 2004 HP Insight Diagnostics Online Edition Technical White Paper Featuring Survey Utility and IML Viewer Table of Contents Abstract Executive Summary 3
Survey Utility HP Industry Standard Servers June 2004 HP Insight Diagnostics Online Edition Technical White Paper Featuring Survey Utility and IML Viewer Table of Contents Abstract Executive Summary 3
Technical Specification. Solutions created by knowledge and needs
 Technical Specification Solutions created by knowledge and needs The industrial control and alarm management system that integrates video, voice and data Technical overview Process Architechture OPC-OCI
Technical Specification Solutions created by knowledge and needs The industrial control and alarm management system that integrates video, voice and data Technical overview Process Architechture OPC-OCI
Data Publishing Workflows with Dataverse
 Data Publishing Workflows with Dataverse Mercè Crosas, Ph.D. Twitter: @mercecrosas Director of Data Science Institute for Quantitative Social Science, Harvard University MIT, May 6, 2014 Intro to our Data
Data Publishing Workflows with Dataverse Mercè Crosas, Ph.D. Twitter: @mercecrosas Director of Data Science Institute for Quantitative Social Science, Harvard University MIT, May 6, 2014 Intro to our Data
INTRODUCTION TO THE DATAVERSE NETWORK
 INTRODUCTION TO THE DATAVERSE NETWORK JANUARY 7, 2015 Jonathan Crabtree Assistant Director of Computing and Archival Research THE ODUM INSTITUTE FOR RESEARCH IN SOCIAL SCIENCE 228 DAVIS LIBRARY, CB# 3355
INTRODUCTION TO THE DATAVERSE NETWORK JANUARY 7, 2015 Jonathan Crabtree Assistant Director of Computing and Archival Research THE ODUM INSTITUTE FOR RESEARCH IN SOCIAL SCIENCE 228 DAVIS LIBRARY, CB# 3355
IBM Rational Asset Manager
 Providing business intelligence for your software assets IBM Rational Asset Manager Highlights A collaborative software development asset management solution, IBM Enabling effective asset management Rational
Providing business intelligence for your software assets IBM Rational Asset Manager Highlights A collaborative software development asset management solution, IBM Enabling effective asset management Rational
9 th ETD Conference - 2006
 9 th ETD Conference - 2006 A Prototype for Preservation and Harvesting of International ETDs using LOCKSS and OAI-PMH Kamini Santhanagopalan Department of Computer Science, Virginia Tech ksanthan@vt.edu
9 th ETD Conference - 2006 A Prototype for Preservation and Harvesting of International ETDs using LOCKSS and OAI-PMH Kamini Santhanagopalan Department of Computer Science, Virginia Tech ksanthan@vt.edu
The Data Management Plan with. Dataverse. Mercè Crosas, Ph.D. Director of Product Development
 The Data Management Plan with Dataverse Mercè Crosas, Ph.D. Director of Product Development The Dataverse The Data Management Plan The Data Management Plan with Dataverse The Dataverse The Data Management
The Data Management Plan with Dataverse Mercè Crosas, Ph.D. Director of Product Development The Dataverse The Data Management Plan The Data Management Plan with Dataverse The Dataverse The Data Management
WEBAPP PATTERN FOR APACHE TOMCAT - USER GUIDE
 WEBAPP PATTERN FOR APACHE TOMCAT - USER GUIDE Contents 1. Pattern Overview... 3 Features 3 Getting started with the Web Application Pattern... 3 Accepting the Web Application Pattern license agreement...
WEBAPP PATTERN FOR APACHE TOMCAT - USER GUIDE Contents 1. Pattern Overview... 3 Features 3 Getting started with the Web Application Pattern... 3 Accepting the Web Application Pattern license agreement...
ODUM INSTITUTE ARCHIVE SERVICES OVERVIEW IASSIST 2015
 ODUM INSTITUTE ARCHIVE SERVICES OVERVIEW IASSIST 2015 JONATHAN CRABTREE Assistant Director of Computing and Archival Research The Odum Institute for Research in Social Science Davis Library, 2nd Floor,
ODUM INSTITUTE ARCHIVE SERVICES OVERVIEW IASSIST 2015 JONATHAN CRABTREE Assistant Director of Computing and Archival Research The Odum Institute for Research in Social Science Davis Library, 2nd Floor,
Tech Notes. Corporate Headquarters EMEA Headquarters Asia-Pacific Headquarters 100 California Street, 12th Floor San Francisco, California 94111
 Tech Notes Faster Application Development via Improved Database Change Management Integrating Database Change Management with Software Development to Reduce Errors, Re-Work, and Testing Efforts Embarcadero
Tech Notes Faster Application Development via Improved Database Change Management Integrating Database Change Management with Software Development to Reduce Errors, Re-Work, and Testing Efforts Embarcadero
PUBLISH YOUR COLLECTIONS TO THE WEB
 emuseum PUBLISH YOUR COLLECTIONS TO THE WEB Easily Integrates with TMS Powerful Searching Fully Customizable User Created Collections Mobile Enabled Multiple Media Support Visit www.gallerysystems.com/emuseum
emuseum PUBLISH YOUR COLLECTIONS TO THE WEB Easily Integrates with TMS Powerful Searching Fully Customizable User Created Collections Mobile Enabled Multiple Media Support Visit www.gallerysystems.com/emuseum
#define. What is #define
 #define What is #define #define is CGI s production system for Application Management and Development, offered in the context of software as a service. It is a project management tool, configuration management
#define What is #define #define is CGI s production system for Application Management and Development, offered in the context of software as a service. It is a project management tool, configuration management
Open Source Backup with Amanda
 Open Source Backup with Amanda Peninsula Linux Users Group (Jan 2008) Paddy Sreenivasan paddy@zmanda.com Copyright 2007 Zmanda, Inc. All rights reserved. 1 Amanda network backup and recovery Easy to use
Open Source Backup with Amanda Peninsula Linux Users Group (Jan 2008) Paddy Sreenivasan paddy@zmanda.com Copyright 2007 Zmanda, Inc. All rights reserved. 1 Amanda network backup and recovery Easy to use
About Network Data Collector
 CHAPTER 2 About Network Data Collector The Network Data Collector is a telnet and SNMP-based data collector for Cisco devices which is used by customers to collect data for Net Audits. It provides a robust
CHAPTER 2 About Network Data Collector The Network Data Collector is a telnet and SNMP-based data collector for Cisco devices which is used by customers to collect data for Net Audits. It provides a robust
visual interface dependency or relationship model of systems workflow engine comparator function poller
 discovery dependency or relationship model of systems Metric Store visual interface workflow comparator function poller Model of system polling/threshold/state system state state state state data) state
discovery dependency or relationship model of systems Metric Store visual interface workflow comparator function poller Model of system polling/threshold/state system state state state state data) state
Requirement Priority Name Requirement Text Response Comment
 N-Tiered Architecture Accessibility Application architecture shall consist of a minimum of four tiers: proxy, presentation, application, and data [base]. Each of the fours tiers shall be separated with
N-Tiered Architecture Accessibility Application architecture shall consist of a minimum of four tiers: proxy, presentation, application, and data [base]. Each of the fours tiers shall be separated with
V7 Reporting. Highlights
 V7 Reporting Highlights 12/22/2008 Highlight V7 Reporting Functionality Ease of Use Configurability Security Performance Enabling You to Analyze the Powerful V7 Data to make the best Business Decisions
V7 Reporting Highlights 12/22/2008 Highlight V7 Reporting Functionality Ease of Use Configurability Security Performance Enabling You to Analyze the Powerful V7 Data to make the best Business Decisions
Symantec Integrated Enforcer for Microsoft DHCP Servers Getting Started Guide
 Symantec Integrated Enforcer for Microsoft DHCP Servers Getting Started Guide Legal Notice Copyright 2006 Symantec Corporation. All rights reserved. Federal acquisitions: Commercial Software - Government
Symantec Integrated Enforcer for Microsoft DHCP Servers Getting Started Guide Legal Notice Copyright 2006 Symantec Corporation. All rights reserved. Federal acquisitions: Commercial Software - Government
Adding Web 2.0 features to a Fleet Monitoring Dashboard
 SpaceOps 2010 ConferenceDelivering on the DreamHosted by NASA Mars 25-30 April 2010, Huntsville, Alabama AIAA 2010-2249 Adding Web 2.0 features to a Fleet Monitoring Dashboard
SpaceOps 2010 ConferenceDelivering on the DreamHosted by NASA Mars 25-30 April 2010, Huntsville, Alabama AIAA 2010-2249 Adding Web 2.0 features to a Fleet Monitoring Dashboard
NTP and Syslog in Linux. Kevin Breit
 NTP and Syslog in Linux Kevin Breit Network Time Protocol (NTP) Synchronizes computer time with highly accurate time services NTP Architecture Utilizes time server hierarchy. Each level is called a stratum.
NTP and Syslog in Linux Kevin Breit Network Time Protocol (NTP) Synchronizes computer time with highly accurate time services NTP Architecture Utilizes time server hierarchy. Each level is called a stratum.
DTWMS Required Software Engineers. 1. Senior Java Programmer (3 Positions) Responsibilities:
 DTWMS Required Software Engineers 1. Senior Java Programmer (3 Positions) Responsibilities: Responsible to deliver quality software solutions using standard end to end software development cycle Collaborate
DTWMS Required Software Engineers 1. Senior Java Programmer (3 Positions) Responsibilities: Responsible to deliver quality software solutions using standard end to end software development cycle Collaborate
10CS73:Web Programming
 10CS73:Web Programming Question Bank Fundamentals of Web: 1.What is WWW? 2. What are domain names? Explain domain name conversion with diagram 3.What are the difference between web browser and web server
10CS73:Web Programming Question Bank Fundamentals of Web: 1.What is WWW? 2. What are domain names? Explain domain name conversion with diagram 3.What are the difference between web browser and web server
Web based monitoring in the CMS experiment at CERN
 FERMILAB-CONF-11-765-CMS-PPD International Conference on Computing in High Energy and Nuclear Physics (CHEP 2010) IOP Publishing Web based monitoring in the CMS experiment at CERN William Badgett 1, Irakli
FERMILAB-CONF-11-765-CMS-PPD International Conference on Computing in High Energy and Nuclear Physics (CHEP 2010) IOP Publishing Web based monitoring in the CMS experiment at CERN William Badgett 1, Irakli
2009 ikeep Ltd, Morgenstrasse 129, CH-3018 Bern, Switzerland (www.ikeep.com, info@ikeep.com)
 CSP CHRONOS Compliance statement for ISO 14721:2003 (Open Archival Information System Reference Model) 2009 ikeep Ltd, Morgenstrasse 129, CH-3018 Bern, Switzerland (www.ikeep.com, info@ikeep.com) The international
CSP CHRONOS Compliance statement for ISO 14721:2003 (Open Archival Information System Reference Model) 2009 ikeep Ltd, Morgenstrasse 129, CH-3018 Bern, Switzerland (www.ikeep.com, info@ikeep.com) The international
Case Study. Web Application for Financial & Economic Data Analysis. www.brainvire.com 2013 Brainvire Infotech Pvt. Ltd Page 1 of 1
 Case Study Web Application for Financial & Economic Data Analysis www.brainvire.com 2013 Brainvire Infotech Pvt. Ltd Page 1 of 1 Client Requirement This is a highly customized application for financial
Case Study Web Application for Financial & Economic Data Analysis www.brainvire.com 2013 Brainvire Infotech Pvt. Ltd Page 1 of 1 Client Requirement This is a highly customized application for financial
AXL Troubleshooting. Overview. Architecture
 AXL Troubleshooting This chapter contains the following topics: Overview, page 35 Architecture, page 35 Postinstallation Checklist, page 36 Troubleshooting Tools, page 39 Error Codes, page 43 Overview
AXL Troubleshooting This chapter contains the following topics: Overview, page 35 Architecture, page 35 Postinstallation Checklist, page 36 Troubleshooting Tools, page 39 Error Codes, page 43 Overview
Software. PowerExplorer. Information Management and Platform DATA SHEET
 DATA SHEET PowerExplorer Software Information Management and Platform KEY FEATURES Web-enabled Advanced, ad-hoc query capabilities Spatial E&P data presentation ZGF file import/export Spatializer Tabular
DATA SHEET PowerExplorer Software Information Management and Platform KEY FEATURES Web-enabled Advanced, ad-hoc query capabilities Spatial E&P data presentation ZGF file import/export Spatializer Tabular
Project Orwell: Distributed Document Integrity Verification
 1 Project Orwell: Distributed Document Integrity Verification Tommy MacWilliam tmacwilliam@cs.harvard.edu Abstract Project Orwell is a client and server application designed to facilitate the preservation
1 Project Orwell: Distributed Document Integrity Verification Tommy MacWilliam tmacwilliam@cs.harvard.edu Abstract Project Orwell is a client and server application designed to facilitate the preservation
Pentaho Reporting Overview
 Pentaho Reporting Copyright 2006 Pentaho Corporation. Redistribution permitted. All trademarks are the property of their respective owners. For the latest information, please visit our web site at www.pentaho.org
Pentaho Reporting Copyright 2006 Pentaho Corporation. Redistribution permitted. All trademarks are the property of their respective owners. For the latest information, please visit our web site at www.pentaho.org
LOCKSS on LINUX. CentOS6 Installation Manual 08/22/2013
 LOCKSS on LINUX CentOS6 Installation Manual 08/22/2013 1 Table of Contents Overview... 3 LOCKSS Hardware... 5 Installation Checklist... 6 BIOS Settings... 9 Installation... 10 Firewall Configuration...
LOCKSS on LINUX CentOS6 Installation Manual 08/22/2013 1 Table of Contents Overview... 3 LOCKSS Hardware... 5 Installation Checklist... 6 BIOS Settings... 9 Installation... 10 Firewall Configuration...
Alliance Key Manager Solution Brief
 Alliance Key Manager Solution Brief KEY MANAGEMENT Enterprise Encryption Key Management On the road to protecting sensitive data assets, data encryption remains one of the most difficult goals. A major
Alliance Key Manager Solution Brief KEY MANAGEMENT Enterprise Encryption Key Management On the road to protecting sensitive data assets, data encryption remains one of the most difficult goals. A major
Universal Event Monitor for SOA 5.2.0 Reference Guide
 Universal Event Monitor for SOA 5.2.0 Reference Guide 2015 by Stonebranch, Inc. All Rights Reserved. 1. Universal Event Monitor for SOA 5.2.0 Reference Guide.............................................................
Universal Event Monitor for SOA 5.2.0 Reference Guide 2015 by Stonebranch, Inc. All Rights Reserved. 1. Universal Event Monitor for SOA 5.2.0 Reference Guide.............................................................
Digital Repository Initiative
 Digital Repository Initiative 01 April 2014 Ray Frohlich Director, Enterprise Systems and Infrastructure with Euan Cochrane Digital Preservation Manager, Preservation Michael Friscia Manager of Digital
Digital Repository Initiative 01 April 2014 Ray Frohlich Director, Enterprise Systems and Infrastructure with Euan Cochrane Digital Preservation Manager, Preservation Michael Friscia Manager of Digital
Leveraging the Eclipse TPTP* Agent Infrastructure
 2005 Intel Corporation; made available under the EPL v1.0 March 3, 2005 Eclipse is a trademark of Eclipse Foundation, Inc 1 Leveraging the Eclipse TPTP* Agent Infrastructure Andy Kaylor Intel Corporation
2005 Intel Corporation; made available under the EPL v1.0 March 3, 2005 Eclipse is a trademark of Eclipse Foundation, Inc 1 Leveraging the Eclipse TPTP* Agent Infrastructure Andy Kaylor Intel Corporation
Combining SAWSDL, OWL DL and UDDI for Semantically Enhanced Web Service Discovery
 Combining SAWSDL, OWL DL and UDDI for Semantically Enhanced Web Service Discovery Dimitrios Kourtesis, Iraklis Paraskakis SEERC South East European Research Centre, Greece Research centre of the University
Combining SAWSDL, OWL DL and UDDI for Semantically Enhanced Web Service Discovery Dimitrios Kourtesis, Iraklis Paraskakis SEERC South East European Research Centre, Greece Research centre of the University
Using SNMP to Obtain Port Counter Statistics During Live Migration of a Virtual Machine. Ronny L. Bull Project Writeup For: CS644 Clarkson University
 Using SNMP to Obtain Port Counter Statistics During Live Migration of a Virtual Machine Ronny L. Bull Project Writeup For: CS644 Clarkson University Fall 2012 Abstract If a managed switch is used during
Using SNMP to Obtain Port Counter Statistics During Live Migration of a Virtual Machine Ronny L. Bull Project Writeup For: CS644 Clarkson University Fall 2012 Abstract If a managed switch is used during
REMOTE INFRASTRUCTURE MANAGEMENT COURSE CURRICULUM
 On a Mission to Transform Talent REMOTE INFRASTRUCTURE MANAGEMENT COURSE CURRICULUM Table of Contents Module 1: Introduction to Hardware and Networking (Duration: 1.5 Weeks)...1 Module 2: Windows XP Professional
On a Mission to Transform Talent REMOTE INFRASTRUCTURE MANAGEMENT COURSE CURRICULUM Table of Contents Module 1: Introduction to Hardware and Networking (Duration: 1.5 Weeks)...1 Module 2: Windows XP Professional
Diagram 1: Islands of storage across a digital broadcast workflow
 XOR MEDIA CLOUD AQUA Big Data and Traditional Storage The era of big data imposes new challenges on the storage technology industry. As companies accumulate massive amounts of data from video, sound, database,
XOR MEDIA CLOUD AQUA Big Data and Traditional Storage The era of big data imposes new challenges on the storage technology industry. As companies accumulate massive amounts of data from video, sound, database,
Actuate Business Intelligence and Reporting Tools (BIRT)
 Product Datasheet Actuate Business Intelligence and Reporting Tools (BIRT) Eclipse s BIRT project is a flexible, open source, and 100% pure Java reporting tool for building and publishing reports against
Product Datasheet Actuate Business Intelligence and Reporting Tools (BIRT) Eclipse s BIRT project is a flexible, open source, and 100% pure Java reporting tool for building and publishing reports against
LoadRunner and Performance Center v11.52 Technical Awareness Webinar Training
 LoadRunner and Performance Center v11.52 Technical Awareness Webinar Training Tony Wong 1 Copyright Copyright 2012 2012 Hewlett-Packard Development Development Company, Company, L.P. The L.P. information
LoadRunner and Performance Center v11.52 Technical Awareness Webinar Training Tony Wong 1 Copyright Copyright 2012 2012 Hewlett-Packard Development Development Company, Company, L.P. The L.P. information
Live Model Pointers A requirement for future model repositories
 Live Model Pointers A requirement for future model repositories Keith Duddy QUT/Smart Services CRC 8 April 2009 1 Introduction Model interoperability is a topic that assumes that models are created and
Live Model Pointers A requirement for future model repositories Keith Duddy QUT/Smart Services CRC 8 April 2009 1 Introduction Model interoperability is a topic that assumes that models are created and
STAT REVIEW/EXECUTIVE DASHBOARD TASK ORDER EXECUTIVE DASHBOARD SYNTHESIS OF BEST PRACTICES
 STAT REVIEW/EXECUTIVE DASHBOARD TASK ORDER EXECUTIVE DASHBOARD SYNTHESIS OF BEST PRACTICES October 26, 2011 This publication was produced for review by the United States Agency for International Development.
STAT REVIEW/EXECUTIVE DASHBOARD TASK ORDER EXECUTIVE DASHBOARD SYNTHESIS OF BEST PRACTICES October 26, 2011 This publication was produced for review by the United States Agency for International Development.
EventSentry Overview. Part I About This Guide 1. Part II Overview 2. Part III Installation & Deployment 4. Part IV Monitoring Architecture 13
 Contents I Part I About This Guide 1 Part II Overview 2 Part III Installation & Deployment 4 1 Installation... with Setup 5 2 Management... Console 6 3 Configuration... 7 4 Remote... Update 10 Part IV
Contents I Part I About This Guide 1 Part II Overview 2 Part III Installation & Deployment 4 1 Installation... with Setup 5 2 Management... Console 6 3 Configuration... 7 4 Remote... Update 10 Part IV
Technical. Overview. ~ a ~ irods version 4.x
 Technical Overview ~ a ~ irods version 4.x The integrated Ru e-oriented DATA System irods is open-source, data management software that lets users: access, manage, and share data across any type or number
Technical Overview ~ a ~ irods version 4.x The integrated Ru e-oriented DATA System irods is open-source, data management software that lets users: access, manage, and share data across any type or number
How To Write A Work Paper
 Payment Card Industry Payment Application Data Security Standard (PA-DSS) FAQs for use with ROV Reporting Instructions for PA-DSS version 2.0 ROV Reporting Instructions for PA-DSS v2.0 Frequently Asked
Payment Card Industry Payment Application Data Security Standard (PA-DSS) FAQs for use with ROV Reporting Instructions for PA-DSS version 2.0 ROV Reporting Instructions for PA-DSS v2.0 Frequently Asked
exobase Discovery Review Platform
 exobase Discovery Review Platform EXPERIENCE Over 20 years of knowledge and experience utilizing technology to provide knowledge management solutions for legal teams and organizations. VALUE Pride is taken
exobase Discovery Review Platform EXPERIENCE Over 20 years of knowledge and experience utilizing technology to provide knowledge management solutions for legal teams and organizations. VALUE Pride is taken
BIRT Document Transform
 BIRT Document Transform BIRT Document Transform is the industry leader in enterprise-class, high-volume document transformation. It transforms and repurposes high-volume documents and print streams such
BIRT Document Transform BIRT Document Transform is the industry leader in enterprise-class, high-volume document transformation. It transforms and repurposes high-volume documents and print streams such
Installation and configuration of Real-Time Monitoring Tool (RTMT)
 Installation and configuration of Real-Time Monitoring Tool (RTMT) How to install and upgrade RTMT, page 1 Services, servlets, and service parameters on server, page 5 Navigation of RTMT, page 6 Nonconfigurable
Installation and configuration of Real-Time Monitoring Tool (RTMT) How to install and upgrade RTMT, page 1 Services, servlets, and service parameters on server, page 5 Navigation of RTMT, page 6 Nonconfigurable
Tier Architectures. Kathleen Durant CS 3200
 Tier Architectures Kathleen Durant CS 3200 1 Supporting Architectures for DBMS Over the years there have been many different hardware configurations to support database systems Some are outdated others
Tier Architectures Kathleen Durant CS 3200 1 Supporting Architectures for DBMS Over the years there have been many different hardware configurations to support database systems Some are outdated others
SOSFTP Managed File Transfer
 Open Source File Transfer SOSFTP Managed File Transfer http://sosftp.sourceforge.net Table of Contents n Introduction to Managed File Transfer n Gaps n Solutions n Architecture and Components n SOSFTP
Open Source File Transfer SOSFTP Managed File Transfer http://sosftp.sourceforge.net Table of Contents n Introduction to Managed File Transfer n Gaps n Solutions n Architecture and Components n SOSFTP
Patch Management Reference
 www.novell.com/documentation Patch Management Reference ZENworks 11 SP3 February 2014 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
www.novell.com/documentation Patch Management Reference ZENworks 11 SP3 February 2014 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
SQL Server Training Course Content
 SQL Server Training Course Content SQL Server Training Objectives Installing Microsoft SQL Server Upgrading to SQL Server Management Studio Monitoring the Database Server Database and Index Maintenance
SQL Server Training Course Content SQL Server Training Objectives Installing Microsoft SQL Server Upgrading to SQL Server Management Studio Monitoring the Database Server Database and Index Maintenance
Smartphone Enterprise Application Integration
 WHITE PAPER MARCH 2011 Smartphone Enterprise Application Integration Rhomobile - Mobilize Your Enterprise Overview For more information on optimal smartphone development please see the Rhomobile White
WHITE PAPER MARCH 2011 Smartphone Enterprise Application Integration Rhomobile - Mobilize Your Enterprise Overview For more information on optimal smartphone development please see the Rhomobile White
6231A - Maintaining a Microsoft SQL Server 2008 Database
 6231A - Maintaining a Microsoft SQL Server 2008 Database Course Number: 6231A Course Length: 5 Days Certification Exam This course will help you prepare for the following Microsoft Certified Professional
6231A - Maintaining a Microsoft SQL Server 2008 Database Course Number: 6231A Course Length: 5 Days Certification Exam This course will help you prepare for the following Microsoft Certified Professional
Functional Requirements for Digital Asset Management Project version 3.0 11/30/2006
 /30/2006 2 3 4 5 6 7 8 9 0 2 3 4 5 6 7 8 9 20 2 22 23 24 25 26 27 28 29 30 3 32 33 34 35 36 37 38 39 = required; 2 = optional; 3 = not required functional requirements Discovery tools available to end-users:
/30/2006 2 3 4 5 6 7 8 9 0 2 3 4 5 6 7 8 9 20 2 22 23 24 25 26 27 28 29 30 3 32 33 34 35 36 37 38 39 = required; 2 = optional; 3 = not required functional requirements Discovery tools available to end-users:
Getting Started with Android Programming (5 days) with Android 4.3 Jelly Bean
 Getting Started with Android Programming (5 days) with Android 4.3 Jelly Bean Course Description Getting Started with Android Programming is designed to give students a strong foundation to develop apps
Getting Started with Android Programming (5 days) with Android 4.3 Jelly Bean Course Description Getting Started with Android Programming is designed to give students a strong foundation to develop apps
Synchronization Agent Configuration Guide
 SafeNet Authentication Service Synchronization Agent Configuration Guide 1 Document Information Document Part Number 007-012476-001, Revision A Release Date July 2014 Trademarks All intellectual property
SafeNet Authentication Service Synchronization Agent Configuration Guide 1 Document Information Document Part Number 007-012476-001, Revision A Release Date July 2014 Trademarks All intellectual property
Mission-Critical Database with Real-Time Search for Big Data
 Mission-Critical Database with Real-Time Search for Big Data February 17, 2012 Slide 1 Overview About MarkLogic Why MarkLogic Case Studies Technology and Features Slide 2 About MarkLogic 10 years in business
Mission-Critical Database with Real-Time Search for Big Data February 17, 2012 Slide 1 Overview About MarkLogic Why MarkLogic Case Studies Technology and Features Slide 2 About MarkLogic 10 years in business
19. Exercise: CERT participation in incident handling related to the Article 13a obligations
 CERT Exercises Handbook 223 223 19. Exercise: CERT participation in incident handling related to the Article 13a obligations Main Objective Targeted Audience Total Duration This exercise provides students
CERT Exercises Handbook 223 223 19. Exercise: CERT participation in incident handling related to the Article 13a obligations Main Objective Targeted Audience Total Duration This exercise provides students
The PIRUS Code of Practice for recording and reporting usage at the individual article level
 PIRUS A COUNTER Standard The PIRUS Code of Practice for recording and reporting usage at the individual article level (Note: this draft is for public consultation only and is not yet ready for full implementation)
PIRUS A COUNTER Standard The PIRUS Code of Practice for recording and reporting usage at the individual article level (Note: this draft is for public consultation only and is not yet ready for full implementation)
TimePictra Release 10.0
 DATA SHEET Release 100 Next Generation Synchronization System Key Features Web-based multi-tier software architecture Comprehensive FCAPS management functions Software options for advanced FCAPS features
DATA SHEET Release 100 Next Generation Synchronization System Key Features Web-based multi-tier software architecture Comprehensive FCAPS management functions Software options for advanced FCAPS features
CAREER TRACKS PHASE 1 UCSD Information Technology Family Function and Job Function Summary
 UCSD Applications Programming Involved in the development of server / OS / desktop / mobile applications and services including researching, designing, developing specifications for designing, writing,
UCSD Applications Programming Involved in the development of server / OS / desktop / mobile applications and services including researching, designing, developing specifications for designing, writing,
Using the Adobe Access Server for Protected Streaming
 Adobe Access April 2014 Version 4.0 Using the Adobe Access Server for Protected Streaming Copyright 2012-2014 Adobe Systems Incorporated. All rights reserved. This guide is protected under copyright law,
Adobe Access April 2014 Version 4.0 Using the Adobe Access Server for Protected Streaming Copyright 2012-2014 Adobe Systems Incorporated. All rights reserved. This guide is protected under copyright law,
Document Management Server - Overview
 Introduction The Document Management System (DMS) is a web-based application designed to allow for storage and retrieval of documents with user-defined document types, document groups, and keywords. The
Introduction The Document Management System (DMS) is a web-based application designed to allow for storage and retrieval of documents with user-defined document types, document groups, and keywords. The
Best Practices for Deploying and Managing Linux with Red Hat Network
 Best Practices for Deploying and Managing Linux with Red Hat Network Abstract This technical whitepaper provides a best practices overview for companies deploying and managing their open source environment
Best Practices for Deploying and Managing Linux with Red Hat Network Abstract This technical whitepaper provides a best practices overview for companies deploying and managing their open source environment
Open Journal Systems and Dataverse Integration-- Helping Journals to Upgrade Data Publication for Reusable Research
 Open Journal Systems and Dataverse Integration-- Helping Journals to Upgrade Data Publication for Reusable Research Micah Altman Director of Research, MIT Libraries http://informatics.mit.edu
Open Journal Systems and Dataverse Integration-- Helping Journals to Upgrade Data Publication for Reusable Research Micah Altman Director of Research, MIT Libraries http://informatics.mit.edu
Day 1 - Technology Introduction & Digital Asset Management
 SharePoint Developers Academy 2010 Course Syllabus Introduction Day 1 - Technology Introduction & Digital Asset Management 1. Kick Start a. Participant Introductions b. Course Overview c. Training Goals
SharePoint Developers Academy 2010 Course Syllabus Introduction Day 1 - Technology Introduction & Digital Asset Management 1. Kick Start a. Participant Introductions b. Course Overview c. Training Goals
SysAid Cloud Architecture Including Security and Disaster Recovery Plan
 SysAid Cloud Architecture Including Security and Disaster Recovery Plan This document covers three aspects of SysAid Cloud: Datacenters Network, Hardware, and Software Components Disaster Recovery Plan
SysAid Cloud Architecture Including Security and Disaster Recovery Plan This document covers three aspects of SysAid Cloud: Datacenters Network, Hardware, and Software Components Disaster Recovery Plan
Cross-domain Identity Management System for Cloud Environment
 Cross-domain Identity Management System for Cloud Environment P R E S E N T E D B Y: N A Z I A A K H TA R A I S H A S A J I D M. S O H A I B FA R O O Q I T E A M L E A D : U M M E - H A B I B A T H E S
Cross-domain Identity Management System for Cloud Environment P R E S E N T E D B Y: N A Z I A A K H TA R A I S H A S A J I D M. S O H A I B FA R O O Q I T E A M L E A D : U M M E - H A B I B A T H E S
EPICenter Network Management Software
 EPICenter Network Management Software EPICenter management suite is a scalable full-featured network management tool that simplifies configuring, troubleshooting and status monitoring of IP-based networks.
EPICenter Network Management Software EPICenter management suite is a scalable full-featured network management tool that simplifies configuring, troubleshooting and status monitoring of IP-based networks.
Altiris Monitor Solution for Servers 7.1 SP1 and Event Console 7.1 MR1 from Symantec Release Notes
 Altiris Monitor Solution for Servers 7.1 SP1 and Event Console 7.1 MR1 from Symantec Release Notes Altiris Monitor Solution for Servers 7.1 SP1 and Event Console 7.1 MR1 from Symantec Release Notes The
Altiris Monitor Solution for Servers 7.1 SP1 and Event Console 7.1 MR1 from Symantec Release Notes Altiris Monitor Solution for Servers 7.1 SP1 and Event Console 7.1 MR1 from Symantec Release Notes The
6.2 Reporting BIPublisher Improvements
 6.2 Reporting BIPublisher Improvements Paul Hamill Senior Director, OTM Development 2011 OTM SIG Philadelphia, PA August 16-18, 2011 Safe Harbor Statements The following is intended
6.2 Reporting BIPublisher Improvements Paul Hamill Senior Director, OTM Development 2011 OTM SIG Philadelphia, PA August 16-18, 2011 Safe Harbor Statements The following is intended
identity management in Linux and UNIX environments
 Whitepaper identity management in Linux and UNIX environments EXECUTIVE SUMMARY In today s IT environments everything is growing, especially the number of users, systems, services, applications, and virtual
Whitepaper identity management in Linux and UNIX environments EXECUTIVE SUMMARY In today s IT environments everything is growing, especially the number of users, systems, services, applications, and virtual
<Insert Picture Here> Oracle Database Directions Fred Louis Principal Sales Consultant Ohio Valley Region
 Oracle Database Directions Fred Louis Principal Sales Consultant Ohio Valley Region 1977 Oracle Database 30 Years of Sustained Innovation Database Vault Transparent Data Encryption
Oracle Database Directions Fred Louis Principal Sales Consultant Ohio Valley Region 1977 Oracle Database 30 Years of Sustained Innovation Database Vault Transparent Data Encryption
Investigating Hadoop for Large Spatiotemporal Processing Tasks
 Investigating Hadoop for Large Spatiotemporal Processing Tasks David Strohschein dstrohschein@cga.harvard.edu Stephen Mcdonald stephenmcdonald@cga.harvard.edu Benjamin Lewis blewis@cga.harvard.edu Weihe
Investigating Hadoop for Large Spatiotemporal Processing Tasks David Strohschein dstrohschein@cga.harvard.edu Stephen Mcdonald stephenmcdonald@cga.harvard.edu Benjamin Lewis blewis@cga.harvard.edu Weihe
Semantic based Web Application Firewall (SWAF V 1.6) Operations and User Manual. Document Version 1.0
 Semantic based Web Application Firewall (SWAF V 1.6) Operations and User Manual Document Version 1.0 Table of Contents 1 SWAF... 4 1.1 SWAF Features... 4 2 Operations and User Manual... 7 2.1 SWAF Administrator
Semantic based Web Application Firewall (SWAF V 1.6) Operations and User Manual Document Version 1.0 Table of Contents 1 SWAF... 4 1.1 SWAF Features... 4 2 Operations and User Manual... 7 2.1 SWAF Administrator
Load and Performance Load Testing. RadView Software October 2015 www.radview.com
 Load and Performance Load Testing RadView Software October 2015 www.radview.com Contents Introduction... 3 Key Components and Architecture... 4 Creating Load Tests... 5 Mobile Load Testing... 9 Test Execution...
Load and Performance Load Testing RadView Software October 2015 www.radview.com Contents Introduction... 3 Key Components and Architecture... 4 Creating Load Tests... 5 Mobile Load Testing... 9 Test Execution...
Overview Document Framework Version 1.0 December 12, 2005
 Document Framework Version 1.0 December 12, 2005 Document History Date Author Version Description October 5, 2005 Carl Yestrau 1.0 First complete version December 12, 2005 Page A Table of Contents 1.0
Document Framework Version 1.0 December 12, 2005 Document History Date Author Version Description October 5, 2005 Carl Yestrau 1.0 First complete version December 12, 2005 Page A Table of Contents 1.0
Features IT Perspective. www.eset.com
 Features IT Perspective www.eset.com Endpoint Protection Antivirus / Antispyware Host-based Intrusion Prevention System (HIPS) Auto-Scan of Removable Media Component-based Installation Client Antispam
Features IT Perspective www.eset.com Endpoint Protection Antivirus / Antispyware Host-based Intrusion Prevention System (HIPS) Auto-Scan of Removable Media Component-based Installation Client Antispam
Migration and Disaster Recovery Underground in the NEC / Iron Mountain National Data Center with the RackWare Management Module
 Migration and Disaster Recovery Underground in the NEC / Iron Mountain National Data Center with the RackWare Management Module WHITE PAPER May 2015 Contents Advantages of NEC / Iron Mountain National
Migration and Disaster Recovery Underground in the NEC / Iron Mountain National Data Center with the RackWare Management Module WHITE PAPER May 2015 Contents Advantages of NEC / Iron Mountain National
Features Business Perspective. www.eset.com
 Features Business Perspective www.eset.com Endpoint Protection Antivirus / Antispyware Auto-Scan of Removable Media Host-based Intrusion Prevention System (HIPS) Client Antispam Cross-platform Protection
Features Business Perspective www.eset.com Endpoint Protection Antivirus / Antispyware Auto-Scan of Removable Media Host-based Intrusion Prevention System (HIPS) Client Antispam Cross-platform Protection
Evaluation of Nagios for Real-time Cloud Virtual Machine Monitoring
 University of Victoria Faculty of Engineering Fall 2009 Work Term Report Evaluation of Nagios for Real-time Cloud Virtual Machine Monitoring Department of Physics University of Victoria Victoria, BC Michael
University of Victoria Faculty of Engineering Fall 2009 Work Term Report Evaluation of Nagios for Real-time Cloud Virtual Machine Monitoring Department of Physics University of Victoria Victoria, BC Michael
Key Steps to Meeting PCI DSS 2.0 Requirements Using Sensitive Data Discovery and Masking
 Key Steps to Meeting PCI DSS 2.0 Requirements Using Sensitive Data Discovery and Masking SUMMARY The Payment Card Industry Data Security Standard (PCI DSS) defines 12 high-level security requirements directed
Key Steps to Meeting PCI DSS 2.0 Requirements Using Sensitive Data Discovery and Masking SUMMARY The Payment Card Industry Data Security Standard (PCI DSS) defines 12 high-level security requirements directed
What s New in Centrify Server Suite 2014
 CENTRIFY SERVER SUITE 2014 WHAT S NEW What s New in Centrify Server Suite 2014 The new Centrify Server Suite 2014 introduces major new features that simplify risk management and make regulatory compliance
CENTRIFY SERVER SUITE 2014 WHAT S NEW What s New in Centrify Server Suite 2014 The new Centrify Server Suite 2014 introduces major new features that simplify risk management and make regulatory compliance
Web Application s Performance Testing
 Web Application s Performance Testing B. Election Reddy (07305054) Guided by N. L. Sarda April 13, 2008 1 Contents 1 Introduction 4 2 Objectives 4 3 Performance Indicators 5 4 Types of Performance Testing
Web Application s Performance Testing B. Election Reddy (07305054) Guided by N. L. Sarda April 13, 2008 1 Contents 1 Introduction 4 2 Objectives 4 3 Performance Indicators 5 4 Types of Performance Testing
IBM Rational Web Developer for WebSphere Software Version 6.0
 Rapidly build, test and deploy Web, Web services and Java applications with an IDE that is easy to learn and use IBM Rational Web Developer for WebSphere Software Version 6.0 Highlights Accelerate Web,
Rapidly build, test and deploy Web, Web services and Java applications with an IDE that is easy to learn and use IBM Rational Web Developer for WebSphere Software Version 6.0 Highlights Accelerate Web,
Cross Platform Software Release Capabilities
 Cross Platform Software Release Capabilities Larry Aube ClearPath Portfolio Management ClearPath Briefings 2015 Grove/UK Agenda Data Exchange ClearPath Integration Services ClearPath IDEs 2015 Unisys Corporation.
Cross Platform Software Release Capabilities Larry Aube ClearPath Portfolio Management ClearPath Briefings 2015 Grove/UK Agenda Data Exchange ClearPath Integration Services ClearPath IDEs 2015 Unisys Corporation.
Setting up Remote Replication on SNC NAS Series
 Setting up Remote Replication on SNC NAS Series Application Note Abstract This application note describes how to set up remote replication on SNC NAS systems. Table of Contents Product Models Covered by
Setting up Remote Replication on SNC NAS Series Application Note Abstract This application note describes how to set up remote replication on SNC NAS systems. Table of Contents Product Models Covered by
Documenting the research life cycle: one data model, many products
 Documenting the research life cycle: one data model, many products Mary Vardigan, 1 Peter Granda, 2 Sue Ellen Hansen, 3 Sanda Ionescu 4 and Felicia LeClere 5 Introduction Technical documentation for social
Documenting the research life cycle: one data model, many products Mary Vardigan, 1 Peter Granda, 2 Sue Ellen Hansen, 3 Sanda Ionescu 4 and Felicia LeClere 5 Introduction Technical documentation for social
RED HAT CLOUDFORMS ENTERPRISE- GRADE MANAGEMENT FOR AMAZON WEB SERVICES
 TECHNOLOGY DETAIL RED HAT CLOUDFORMS ENTERPRISE- GRADE MANAGEMENT FOR AMAZON WEB SERVICES ABSTRACT Do you want to use public clouds like Amazon Web Services (AWS) to flexibly extend your datacenter capacity,
TECHNOLOGY DETAIL RED HAT CLOUDFORMS ENTERPRISE- GRADE MANAGEMENT FOR AMAZON WEB SERVICES ABSTRACT Do you want to use public clouds like Amazon Web Services (AWS) to flexibly extend your datacenter capacity,
HP Intelligent Management Center Enterprise Software. Platform. Key features. Data sheet
 Data sheet HP Intelligent Management Center Enterprise Software Platform Key features Highly flexible and scalable deployment options Powerful administration control Rich resource management Detailed performance
Data sheet HP Intelligent Management Center Enterprise Software Platform Key features Highly flexible and scalable deployment options Powerful administration control Rich resource management Detailed performance
SOA @ ebay : How is it a hit
 SOA @ ebay : How is it a hit Sastry Malladi Distinguished Architect. ebay, Inc. Agenda The context : SOA @ebay Brief recap of SOA concepts and benefits Challenges encountered in large scale SOA deployments
SOA @ ebay : How is it a hit Sastry Malladi Distinguished Architect. ebay, Inc. Agenda The context : SOA @ebay Brief recap of SOA concepts and benefits Challenges encountered in large scale SOA deployments
70-646 R3: Windows Server 2008 Administration. Course Overview. Course Outline. Course Length: 4 Day
 70-646 R3: Windows Server 2008 Administration Course Length: 4 Day Course Overview This course will prepare the student for Exam 70-646: Pro: Windows Server 2008, Server Administrator. Topics covered include
70-646 R3: Windows Server 2008 Administration Course Length: 4 Day Course Overview This course will prepare the student for Exam 70-646: Pro: Windows Server 2008, Server Administrator. Topics covered include
There are numerous ways to access monitors:
 Remote Monitors REMOTE MONITORS... 1 Overview... 1 Accessing Monitors... 1 Creating Monitors... 2 Monitor Wizard Options... 11 Editing the Monitor Configuration... 14 Status... 15 Location... 17 Alerting...
Remote Monitors REMOTE MONITORS... 1 Overview... 1 Accessing Monitors... 1 Creating Monitors... 2 Monitor Wizard Options... 11 Editing the Monitor Configuration... 14 Status... 15 Location... 17 Alerting...
