WHITE PAPER: ENTERPRISE SOLUTIONS. Security and Availability Implementing Security and Archiving Solutions from Symantec
|
|
|
- Agnes Lee
- 10 years ago
- Views:
Transcription
1 WHITE PAPER: ENTERPRISE SOLUTIONS Security and Availability Implementing Security and Archiving Solutions from Symantec By Nick Wade Senior Product Manager, Enterprise Vault Now from Symantec
2
3 White Paper: Symantec Enterprise Solutions Security and Availability Implementing Security and Archiving Solutions from Symantec Contents Executive summary Introduction Symantec integrated solutions security archiving Available solutions How to integrate security and archiving Scenario 1: Acme Corporation (Acme Corp.) Deploying Symantec Mail Security 8100 Series Deploying Symantec Mail Security 8200 Series Deploying Symantec Mail Security for Microsoft Exchange Deploying Veritas Enterprise Vault Deploying additional components Scenario 2. Beta Corporation (Beta Corp.) Deploying Symantec Mail Security 8100 Series Deploying Symantec Mail Security 8200 Series Deploying Symantec Mail Security for Microsoft Exchange Deploying Veritas Enterprise Vault Deploying additional components Tested Solutions Summary
4 Executive summary usage has transformed how we conduct business and directly affects how rapidly and efficiently we may exchange information. Consequently, has become a critical application service in the organization. As a result, security and integrity are paramount concerns, as are service availability and optimization technologies, including archiving. Additionally, businesses face increasing regulatory requirements that mandate appropriate levels of record retention and management, including business records comprising varied forms of electronic messaging. This white paper details, at a high level, how to achieve an advantageous combination of best-of-breed security and archiving technologies from Symantec Corporation. These technologies can assist with satisfying the varying needs of security, archiving, and records retention associated with and electronic messages. The hypothetical Acme Corporation and Beta Corporation that are discussed illustrate the example challenges and solutions associated with security as pertains to: Inbound hygiene at the network perimeter and inside the organization content compliance with regard to outbound and intra-organizational archiving for storage management and optimization of Exchange Server services, as well as journaling and compliance-related capture of messages passing through the organization to meet regulatory and/or privacy requirements This white paper describes how two businesses (Acme and Beta Corporations) can deploy Symantec Mail Security appliances and software both within and without the organization to achieve security and content compliance goals. It further describes how to integrate the Symantec technology with Veritas Enterprise Vault to ensure that necessary messages are captured and retained in a cost-effective and usable manner, optionally including any necessary antivirus- and antispam-related messages that may need to be captured and retained in an appropriate low-cost and secured archive for compliance or privacy reasons. 2
5 Introduction Electronic mail ( ) has transformed how we conduct business in the modern day how we exchange thoughts, ideas, proposals, and information as well as the speed and efficiency with which we can conduct business. has become as important, if not more important, in our personal and business lives as the telephone itself. Over the past 10 years, we have gone from leveraging as an alternative communications vehicle to depending on it as our most mission-critical application. According to the Enterprise Strategy Group, more than 60 percent of mid- and enterprise-tier businesses together believe that is the number one mission-critical business application for their organization (Enterprise Strategy Group, March 2004, Case Study: Exchange Storage, Information and Protection). The fact that also serves as a detailed transaction record for a company makes it valuable as evidence in a court of law, proof that companies are following regulations, and a source for identifying violations of internal company policies. As a result, more companies are deciding to preserve for longer periods of time, in a verifiable and non-repudiated archive format. However, the very things that make valuable to an organization also expose it to a great deal of risk and liability. Its ubiquity and simplicity have consequently made it the preferred method for transferring: Any data between users, including non-business content such as multimedia files and executables, or even company confidential information outside corporate walls Threats and disruptions to thousands of users, such as viruses and spam, at high anonymity, high volume, and very low cost Consequently, we spend countless hours, budget, and resources defending and worrying about how to keep running smoothly. To this end, IT professionals look at security issues such as reducing spam or blocking viruses and at availability issues such as making sure the application, systems, and data are there when needed even in the event of a disaster or long after the s were sent. However, as the checklist of what it takes to keep an system grows, IT is now looking for a more holistic solution to balancing the cost and risk associated with . Coupled with this view is the emerging need to retain high-threat content such as virusloaded or spam s in regulated industries as part of the corporate record, with a strong desire to retain such s in a quarantined yet searchable fashion. 3
6 Simultaneously, businesses and IT professionals are being driven to consider how to reduce management costs associated with the infrastructure. The increase in volume of s coming into the corporate network introduces an exponential growth in associated hard costs by regularly exceeding available capacity of traditional gateway systems, mail transfer agents, storage servers, groupware servers, and network bandwidths. Symantec offers integrated, best-of-breed, and market-leading security and archiving solutions. Symantec integrated solutions Symantec is now able to offer a comprehensive solution that enables security and availability. These unique technologies and services control and manage the flow of information from start to finish, helping protect an organization against risks, ensuring uptime of systems and users, satisfying compliance and document retention requirements, while at the same time minimizing the total cost of ownership for . See Figure 1 for how Symantec s technology and service offerings map to the layered approach described in Symantec s Security and Availability white paper ( Security _wp_EN.pdf). security Resilient foundation Perimeter scan Groupware scan archiving Archiving Indexing Search Retrieval Resilient foundation Backup Recovery Storage Clustering Figure 1. Overview Symantec s security and availability approach 4
7 security Historically, antivirus and antispam technologies have been defined largely as security services. In fact, integrated mail scanning is commonly referred to as security, although this is not entirely accurate. For example, a security threat like a mass-mailer worm has the potential to take end-user systems, even network segments, offline indefinitely. Clearly, this also impacts the availability of , especially for those users and their business. archiving In the same way that security tools act as the first lines of defense in keeping unwanted out of the messaging system environment, archiving works on the back end to move saved messages out of the environment, while at the same time maintaining the availability of the data should it need to be accessed by end users, legal personnel, or HR. Although often used for regulatory purposes, archiving can be an important tool simply to maintain the availability of infrastructure by controlling the amount of data in the primary messaging systems and, as a result, additionally affecting management costs positively. Available solutions Solutions available from Symantec for security include Symantec Mail Security for Microsoft Exchange, Symantec Mail Security for Domino, Symantec Mail Security 8100 Series and 8200 Series appliance systems, Symantec AntiVirus Corporate Edition, and Symantec Brightmail AntiSpam. Solutions available for archiving include its flagship market-leading product, Enterprise Vault. Veritas Enterprise Vault (now from Symantec) is a software-based archiving framework enabling the discovery of content in Microsoft Exchange, SharePoint Portal Server, Lotus Notes, SMTP, IM, and file server environments, while reducing storage and management. Enterprise Vault manages content via policy-controlled archiving to online stores for active retention and seamless retrieval of information. The combination and interaction of these proven, market-leading technologies into a holistic solution for achieving the desired overall goals of security, availability, optimization of ongoing management costs, and satisfaction of regulatory requirements can be very powerful. This white paper details some practical, integrated, and tested security and archiving solutions using the above-mentioned products that our customers can deploy today to derive these benefits. 5
8 How to integrate security and archiving To understand how to potentially leverage the synergy from deploying a combined and proven security and archiving solution from Symantec, consider the following example scenarios: Scenario 1: Acme Corporation (Acme Corp.) uses Microsoft Exchange 2003, and wishes to: Journal all legitimate messages for regulatory purposes Ensure appropriate levels of antivirus and antispam defenses Optionally archive selected spam messages to more cost-effective storage Monitor policy compliance and block s that are out of policy Scenario 2: Beta Corporation (Beta Corp.) also uses Microsoft Exchange 2003, and wishes to: Avoid journaling of all messages due to the load (Beta Corp. is non-regulated) Archive messages for users after 90 days for server optimization Archive spam to a cost-effective temporary location for 60 days, and provide a full text search Archive a copy of inbound or outbound messages where target words and phrases are found Ensure appropriate levels of antivirus and antispam defenses Microsoft Exchange 2003 Symantec Mail Security for Microsoft Exchange MTA and VSAPI Delete or Quarantine Internet Reduce Spam and viruses Symantec Mail Security 8160 Firewall Monitor policy Symantec Mail Security 8260 Less bad traffic Mailbox Store 1 Mailbox Store 2 Journal Store Clean client traffic Throttle spam network traffic Delete or Quarantine Archive; selective spam jounaling Quarantine Archive Archive; mailbox policy and/or journaling User Archives Journal Archives Search, Discover, Review, Audit Veritas Enterprise Vault for Exchange Figure 2. Overview components of implementing security and archiving solutions from Symantec 6
9 Scenario 1: Acme Corporation (Acme Corp.) Acme Corporation (Acme Corp.) runs a clustered Microsoft Exchange Server 2003 messaging and groupware system. Acme Corp. wants to journal and archive all legitimate for three years, but also wants to ensure appropriate levels of antivirus and antispam defenses including a significant reduction in network traffic associated with spam before it reaches the organization. They also want to be able to optionally archive certain selected spam messages because their regulatory requirements state that they need to maintain such s for 180 days in case they were used to obfuscate any illegal communications. Additionally, Acme Corp. needs the ability to monitor compliance with policy and stop serious breaches of policy before even leaves the organization s boundary. Firewall Bridgehead Server Mail server antivirus Internet Microsoft Exchange 2003 Some quarantined Application Storage SAN: Fibre Channel Figure 3. Existing and groupware topology at Acme Corp. 7
10 Solution: To achieve the stated goals in this scenario, Acme Corp. can implement the following solution where Symantec Mail Security and Veritas Enterprise Vault work together: Desired goal Journal and archive all legitimate records Reduce network traffic due to spam before the network perimeter Further reduce spam and virus-infected after acceptance, archive spam messages, and enforce policy Ensure appropriate levels of antivirus for Exchange servers and clients Regularly review a sample of traffic sent and received by users Search, review, and produce messages as evidential records Solution chosen for deployment Microsoft Exchange Server 2003 Journaling, with Veritas Enterprise Vault for Exchange Journal Archiving Symantec Mail Security 8160 appliance with SMTP Traffic Shaping Symantec Mail Security 8260 appliance with Veritas Enterprise Vault for SMTP Archiving Symantec Mail Security for Microsoft Exchange and Symantec AntiVirus Corporate Edition Veritas Enterprise Vault Compliance Accelerator Veritas Enterprise Vault Discovery Accelerator Accordingly, the following products are chosen for deployment at Acme Corp. Vendor Product Version/Type Symantec Mail Security 8100 Series 8160/Appliance Symantec Mail Security 8200 Series 8260/Appliance Symantec Mail Security for Microsoft Exchange 5.0/Cluster Aware Symantec Enterprise Vault for Exchange 6.0/Server + Standby Optional products below are also chosen for deployment at Acme Corp. Vendor Product Version/Type Symantec Enterprise Vault Compliance Accelerator 6.0/Server Symantec Enterprise Vault Discovery Accelerator 5.0/Server 8
11 Deploying the Symantec Mail Security 8100 Series Deployment of Symantec Mail Security 8160 appliances allows Acme Corp. to employ a bestof-breed appliance that leverages market-leading unique antispam traffic-shaping technology. Acme Corp is able to reduce infrastructure costs by restricting connections from spamsending servers and significantly reducing the received amounts of spam before they are even accepted into the corporate system at the network boundary. Their objective is to significantly reduce the transfer capacity available to spammers, while continuing to maintain it for legitimate sources of . Symantec Mail Security 8160 appliances may be configured in one of two modes: Virtual Bridge or Router. A Virtual Bridge is well-suited when one IP subnet exists where the appliance is deployed, and a Router is well-suited when the appliance is routing between two different subnets. Acme Corp. has one external DMZ subnet and will install the 8160 appliances in Virtual Bridge mode as a result. 1. Install and initialize 8160 appliances. Before beginning installation, Acme Corp. needs the following: For Virtual Bridge mode: Valid license file from Symantec Host name, including domain (FQDN) IP address and netmask for the appliance (in Virtual Bridge mode, only one IP per appliance is needed) If implementing a high-availability cluster at the same location IP address and netmask for the second appliance VRID for both appliances Domain Name Servers (DNS) NTP Servers (optional) List of protected servers 9
12 2. Configure network settings, and user/management access. Acme Corp. can then specify the IP address, host name, new administrator password, and other user and management access levels within the Control Center for the 8160 appliance installation. 3. Specify and configure any base settings. The 8160 appliances are then configured with any base settings as needed by Acme Corp. Network routes Protected servers (internal hosts and their gateways) Exempt IPs (internal hosts for which no SMTP traffic shaping is done) Connection shaping (SMTP traffic shaping) Necessary SNMP data collection For further details on any aspect, refer to the Symantec Mail Security 8100 Series Implementation Guide, available at Deploying the Symantec Mail Security 8200 Series Deployment of Symantec Mail Security security appliances allows Acme Corp. to further employ best-of-breed appliance technology that leverages over 20 spam prevention techniques, including Symantec Brightmail AntiSpam, Directory Harvest Attack Prevention, and Sender Reputation techniques. These techniques reduce infrastructure costs by significantly reducing the received amounts of accepted spam, after initial spam reduction is effected by 8160 appliances. Additionally, content compliance features allow administrators to gain control over inbound and outbound content so they can enforce internal or regulatory content policies, before an issue even arises. To derive the full potential benefits of such a solution, an appliance deployment is required both outside the network perimeter (8160 appliances reducing spam and associated network traffic before entry to the network) and inside the organization (8260 appliances further antispam, antivirus, content compliance, and policy enforcement). 10
13 Symantec Mail Security 8260 appliances may be configured in a number of roles, and all of these may be needed in a larger implementation: Scanner: Performs filtering. You can set up one or many Scanner appliances. Control Center: Manages your system. Each Symantec Mail Security 8200 Series installation has exactly one Control Center appliance. The Control Center can manage multiple Scanner appliances. Control Center and Scanner: Performs both functions. Suitable for smaller installations. The Control Center appliance also hosts Quarantine, a component that stores spam messages and provides end users access to their spam messages. You can also configure Quarantine for administrator-only access. Use of Quarantine is optional. 1. Install the first Symantec Mail Security 8260 appliance in the organization. This is known as the Control Center and is where Acme Corp. also configures their initial set of policies. The Control Center further serves as the administrative console to add any additional appliances into the site. The first Symantec Mail Security 8260 appliance will be installed inside the corporate network behind Acme Corp. s firewalls. 11
14 2. Install additional Symantec Mail Security 8260 appliances. Any additional internal Scanner appliances may be installed and configured with Acme Corp. s content compliance policies, directly from the Control Center. External appliances may also be installed outside the company s firewalls in the DMZ, and configured with appropriate security policies. Symantec Mail Security 8260 appliances are hardened, self-contained units designed for operation in an unsecured network in front of the company s firewalls and Exchange servers. 3. Configure all internal Scanner appliances with Acme Corp. s content compliance policies. Symantec Mail Security 8260 appliances provide a wide variety of actions for filtering and allow Acme Corp. to either set identical options for all users or specify different actions for different groups of users. Groups of users can be specified based on addresses, domain names, or LDAP groups. For each group, Acme Corp. can specify an action or group of actions to perform, given a particular verdict on an message that is being checked by the appliance. Some examples are shown in the table below; Symantec Mail Desired Goal Security 8260 Action Details Allow messages that Deliver Normally Messages that do not meet any filter criteria defined in the meet policy to pass system will be allowed to pass as normal. This may be the majority of messages being sent from the organization. Archive a copy of Archive, or BCC Messages that contain certain phrases or words, attachment policy medium-risk types, or are addressed to certain destinations may meet messages internal policy conditions allowing them to pass normally, but also may be archived to Veritas Enterprise Vault additionally for records management purposes. Block and Archive a Archive + Delete Messages that are outside policy may be deleted and copy of policy high-risk stopped from leaving the organization. Additionally, they messages may be archived to Veritas Enterprise Vault and placed into a review queue to ensure that they are examined by the organization to determine the policy breach that has occurred. 12
15 4. Configure all Scanner appliances with Acme Corp. s security policies. Again, for each group of users, Acme Corp. can specify actions and groups of actions to perform given a particular verdict. Given Acme Corp. s goals of providing appropriate security for the business at the perimeter of the network, while still retaining the ability to archive selected spam messages to Veritas Enterprise Vault, some examples are given below Symantec Mail Desired Goal Security 8260 Action Details Allow messages that Deliver Normally Messages that do not meet any filter criteria defined in the meet policy to pass system will be allowed to pass as normal. Clean virus-infected Clean Where possible, messages that are infected with a virus will s and pass be cleaned and delivered normally. Where the message normally contains a virus that cannot be cleaned, it will be deleted and prevented from entering the organization. Prevent Directory Firewall s may be flagged because an attempt is under way Harvest attacks, and to mass-mail the organization and correlate NDRs with other virus/spam attacks messages sent, or because a certain number of infected or spam messages are received from the same IP address. Symantec Mail Security 8260 appliances block these events effectively from the business. Reduce network traffic Throttle Attack Network connections from sources that are sending certain associated with SMTP levels of spam may be throttled and restricted so as to connections for spam reduce the amount of bandwidth and data that is associated delivery with these connections. For example, connections from a known spammer may be restricted to 9.6 kb/s to mimic the effect of a poor modem connection. Archive spam Archive (+ optional messages flagged as spam by filters messages Delete or Quarantine) available from Symantec, or as suspected spam by configurable spam scoring levels, may be treated in a number of optional ways: 1. Forwarded to Quarantine (optionally notifying the user) 2. Forwarded to the user s Spam Folder in Exchange (optionally annotated as Spam or Suspected Spam ) later deleted or archived 3. Archived to an administrative SMTP address in Enterprise Vault (optionally a percentage of these may be reviewed) for compliance or privacy purposes 4. Blocked and deleted at the appliance before entering the organization (can be useful for known spam messages) 13
16 5. Configure 8260 appliances to forward spam to Enterprise Vault for archiving. Acme Corp. needs to retain messages that are not delivered to end users for a period of 180 days, as described above. There are two options that allow Acme Corp. to easily achieve this: a. Configure spam forwarding ( Archive action in Symantec Mail Security 8260) to Enterprise Vault via SMTP archiving Acme Corp. can simply archive messages that are flagged by Symantec Mail Security as spam, by administratively forwarding them directly to an SMTP capture address in Enterprise Vault. These will then be archived for each recipient at Acme Corp. into an administrative set of spam retention archives as necessary, and can be immediately searched, reviewed, and exported as necessary (please refer to the section Deploying Enterprise Vault below for further details). b. Configure spam forwarding ( Archive action in Symantec Mail Security 8260) to a Microsoft Exchange journal mailbox, with Enterprise Vault for Exchange Journal Archiving Acme Corp. can also archive spam messages by administratively forwarding them to a designated journal mailbox in Microsoft Exchange, dedicated to the task. These will then be archived into a flat journal archive for retention as necessary, and can immediately be searched, reviewed, and exported as necessary. This option may be beneficial if Acme Corp. also wish to regularly review a random-percentage sample of spam messages on a daily or weekly basis, by combining Enterprise Vault for Exchange Journal Archiving with Enterprise Vault Compliance Accelerator (please refer to the section Deploying Enterprise Vault below for further details). 6. Configure routing from 8160 appliances to deliver messages to 8260 appliances. This step effects the in-stream deployment of the 8260 appliances for incoming messages. Note: Symantec Mail Security 8260 appliances are not the final delivery point for messages being received by Acme Corp., and 8260 appliances will forward legitimate messages for final distribution to the Microsoft Exchange Server 2003 Organization. 7. Reconfigure the Exchange Organization to send outgoing to internal Symantec Mail Security 8260 appliances. This step completes the deployment of Symantec Mail Security 8200 Series appliances for Acme Corp. by submitting all outgoing messages to the content compliance and policy checks as chosen and configured by Acme Corp. (see step 3 above). For further details on any aspect, refer to the Symantec Mail Security 8200 Series Implementation Guide, available at 14
17 Deploying Symantec Mail Security for Microsoft Exchange Despite having solid perimeter protection in place, it is still necessary for Acme Corp. to inspect internal mail traffic. There are many reasons why this is valuable: Scanning for viruses that enter through other vectors, such as personal Web-based , removable media, remote laptop users whose virus definitions are not current, and more. Preventing unwanted or oversized content from being sent through the internal mail system s Exchange servers. Messages with confidential or inappropriate content can be removed from the store before anyone can view the message. Post-attack, performing virus cleanup of message stores using the latest antivirus definitions. Groupware protection allows viruses and content violations within the message store to be removed without end-user intervention. As a result, mail server protection solutions, such as those for Microsoft Exchange and Lotus Domino, should be able to inspect content in real time during submission and also on later client access, along with regularly scheduled sweeps of content stored within the system. Symantec Mail Security for Microsoft Exchange gives Acme Corp. these required benefits and more. 1. Install Symantec Mail Security for Microsoft Exchange remotely manage multiple installations of Symantec Mail Security for Microsoft Exchange Symantec Mail Security for Microsoft Exchange can be installed as a console to remotely manage multiple servers on an individual basis or as a group. A console installation of Symantec Mail Security for Microsoft Exchange is typically installed on a client machine (Windows XP or Windows 2000) and used to manage product settings remotely. Groups can be created of servers with similar functions for easier management. 2. Install Symantec Mail Security for Exchange on Exchange 2003 cluster nodes Symantec Mail Security for Microsoft Exchange is fully cluster aware when installed in a Windows cluster environment and also supports Veritas clustering. Symantec Mail Security should be installed onto Exchange Cluster nodes while they are in a passive state to ensure that working Exchange Virtual Servers are not affected negatively by the installation processes. Note: It is important that each node in the Microsoft Exchange Server 2003 cluster have Symantec Mail Security for Microsoft Exchange binaries installed in the same location on the applications disk drive. It is also important that the latest updates and definitions for Symantec Mail Security for Microsoft Exchange are installed by the administrator as installation is completed. 15
18 3. Install Symantec AntiVirus Corporate Client on Exchange cluster nodes It is also recommended that Symantec AntiVirus with LiveUpdate is installed on each Exchange cluster node. LiveUpdate will ensure that antivirus definitions and Symantec Mail Security for Microsoft Exchange updates are downloaded and installed automatically as soon as they are available. In order to successfully install and bring online a working Microsoft Exchange 2003 Virtual Server with Symantec Mail Security for Microsoft Exchange and Symantec AntiVirus, exclusions should be added to Symantec AntiVirus for the working directories used by Symantec Mail Security for Microsoft Exchange, and for certain Exchange directories. This is covered in a Symantec Knowledge Base Document (ID: ). (Search for this ID at the following url: 4. Install ( or renew) license files to remote servers Acme Corp. must install a license file on each server that is running Symantec Mail Security for Microsoft Exchange in order to activate a content license. This ensures that each server can receive the latest virus definitions updates. Acme Corp. can install a license file from the console for a remote server group or for a remote single server, or they can install it on each individual server directly. 5. Install Spam Folder Agent for Exchange This agent lets Acme Corp. additionally route spam messages to a spam folder in each recipient s mailbox. This option is available for Microsoft Exchange Server 2000/2003 installations. The Spam Folder Agent should be installed on Exchange servers where mailboxes physically reside. The agent creates a spam folder in each user s mailbox automatically. When spam messages are tagged for Spam Folder Agent delivery, the messages are delivered to the spam folder. Tagging may be accomplished by the Symantec Mail Security 8260 appliances at Acme Corp. Acme Corp. may use spam folders as a means of archiving suspected spam that is delivered directly to end users for review. To ensure that such messages are not left in Exchange mailboxes for more than a few days, apply a folder-level mailbox archiving policy in Enterprise Vault to the spam folder for each user that archives all messages after a short time (e.g., five days). This can be separate from, and override, any other default mailbox archiving policy for the users (refer to the section Deploying Enterprise Vault below for further details). 16
19 6. Enable event forwarding to Symantec Enterprise Security Architecture (optional) Symantec Mail Security for Microsoft Exchange supports event forwarding to Symantec Enterprise Security Architecture (SESA ). SESA is an event management system that employs data collection services for events that Symantec security products generate. When a product is SESA enabled, you can use the SESA Console to view the events that it forwards to SESA. The SESA Console provides a central location from which to view and manage the reporting of event data across multiple SESA enabled security products. For more information on SESA, see the Symantec Enterprise Security Architecture Installation Guide and the Symantec Enterprise Security Architecture Administrator s Guide. Acme Corp. also needs to configure antivirus, further antispam, and other policy aspects of Symantec Mail Security for Microsoft Exchange appropriately. For further details on any aspect, refer to the Symantec Mail Security for Exchange Implementation Guide, available at Deploying Veritas Enterprise Vault Enterprise Vault 6.0 is installed on Windows Server 2003 to host the archive for Exchange servers at Acme Corp., as well as the archive for any spam messages captured directly from the Symantec Mail Security 8260 appliances, and a variety of other information within the business. The Enterprise Vault data is stored on a near-line NAS device (or SAN, DAS, SATA, etc.), initially to ensure rapid access to archived content, while providing storage cost benefits desired by Acme Corp. at the same time. Later during the lifecycle of archived messages (and other information), they may be moved by Enterprise Vault onto other storage devices such as tape or optical libraries for long-term retention. Messages retained in users mailboxes will be archived as they age and become subject to predefined, configurable archiving policies. This ensures that Exchange Server 2003 mailboxes never grow beyond manageable levels; that Exchange servers remain optimized as a result; that backup windows are maintained, and SLAs are achievable; and end users receive a better mailbox service overall. Additionally Acme Corp. can automatically locate, associate (with the owning user), and archive the contents of user PST files on the network. This not only removes the files from the organization but also ensures that Acme Corp. can disclose the records within by consolidating them into one central, scalable, searchable archive. 17
20 Every message being sent to, from, or within Acme Corp. s server environment will be journaled and archived into Enterprise Vault. Generally, Enterprise Vault compresses all items down to 50 percent of their original size (some compressed file formats, such as.zip,.jpg, and.gif, cannot be further compressed) and further reduces archive storage needs by single instancing objects that are the same, regardless of their source (across multiple Exchange servers and PST files, across distributed file systems, and across multiple SharePoint servers and sites). 1. Install Enterprise Vault servers into the internal server network. A number of Enterprise Vault servers commensurate with the archiving throughput needs of Acme Corp. are installed in the company s internal networks. Enterprise Vault servers host a number of services and tasks that run on the Windows Server platform, and address archiving needs for target Exchange servers, including Journal archiving, Mailbox archiving, Public Folder archiving, and SMTP capture and archiving. Enterprise Vault services and tasks run under a security account context in the Active Directory domain, so a service account is created for each Acme Corp. domain housing Exchange servers that need to be archived and managed. 2. Configure Exchange Server 2003 journaling (optional). Exchange is configured to support envelope journaling. If the current mailbox server is running Exchange Server 2003 Enterprise Edition and has sufficient memory, disk volumes, and processing power to support an additional mailbox store, then Acme Corp. may create an additional Storage Group to host a single database that will support the journaling mailbox(es). Note: Message journaling or envelope journaling may be used for this purpose and are both supported by Veritas Enterprise Vault. For every 12,500 items journaled per hour in Exchange Server, the load on the Exchange server increases approximately 10 percent (from Integrated Solutions for Regulatory Compliance with Windows Server Technologies, Microsoft Corporation, 2004). If the current Exchange servers are heavily used or are running Exchange Server 2003 Standard Edition, Acme Corp. may consider deployment of an additional server to host the journaling mailbox(es). 18
21 3. Configure SQL Server SQL Server 2000 supports configuration data and metadata for Enterprise Vault, and enables Discovery Accelerator and other search applications to quickly find and retrieve previously saved search and case information. One SQL server is necessary to support four to five Enterprise Vault servers of an equivalent size. Acme Corp. chooses to use a currently deployed SQL Server 2000 cluster to support Enterprise Vault application database needs. No end-user information is stored in SQL Server. 4. Configure Windows Storage Server 2003 (or other suitable storage for archives). Windows Storage Server 2003 is chosen to host the data being managed by Enterprise Vault at Acme Corp. Approximate data storage needs for Enterprise Vault may be determined using the following formula: ((Number of items) * (Average item size) * 0.5)/(Average single instance storage ratio) + (Number of items)/(average single instance storage ratio) * 7 + (Number of items) * 2 For example, suppose Acme Corp. has 500 items, with an average item size of 10 KB and an average single instance storage ratio of 2.2. The data storage needs would be approximated thus: ((500) * (10 KB) * 0.5)/(2.2) + ((500)/(2.2)) * 7 + (500) * 2 = KB Single instance storage on Exchange servers is very similar to the single instance storage of messages within Enterprise Vault, and current single instance storage ratios are a reasonable indicator of how messages will be shared within Enterprise Vault. Acme Corp. may also choose to utilize tape media storage infrastructure later in the life of archived material (see above), and may do so via the integration of Veritas Enterprise Vault 6.0 and Veritas NetBackup 6.0. This allows tape media in libraries under NetBackup control to provide storage to archive Vault Stores directly within Enterprise Vault. Note: Windows Storage Server 2003 may not be used to host the Enterprise Vault application services and tasks as this is contrary to Microsoft licensing terms. Only the archive and index data stored by Enterprise Vault may reside on Windows Storage Server
22 5. Configure mailbox archiving. Enterprise Vault servers are responsible for various archiving tasks (mailbox, journal, public folder, PST file migration, etc.) that are dedicated to certain Exchange servers. Acme Corp. needs to configure an appropriate number of Enterprise Vault servers to perform scheduled mailbox archiving for all Exchange Virtual Servers being managed. As a guideline, one Enterprise Vault server may be generally required for every three to four equivalent mailbox home Exchange servers (depending on mailbox numbers per server and utilization rates). Once configured for each Exchange server, the archiving tasks are started and will then synchronize the initial list of mailbox users and their associated properties from the Exchange Organization and Active Directory. Users must then be enabled for archiving, which may include configuration of a Vault Store for user archives, deployment and configuration of any necessary client components (optional), configuration of the mailbox archiving policies for various user groups (globally, by OU, or by grouping via various unique LDAP properties), and final scheduled enablement of users mailboxes for archiving services. Users may be enabled in groups to allow appropriate phasing of archiving services into Acme Corp. s organization. Finally, archiving tasks should be scheduled to run at appropriate times, after completion of Acme Corp. s Exchange Server backup windows. Figure 4. Exchange mailbox archiving policies in Veritas Enterprise Vault 20
23 6. Configure journal archiving. Exchange servers may host one or more journal mailboxes that receive copies of all messages passing through Exchange Server Stores (refer to 2 above). An Enterprise Vault Journal Archiving Task needs to be configured for each Exchange server and will process one or more journal mailboxes. Journal archiving tasks process journal mailboxes every 60 seconds and, as such, run continuously after the initial startup. Every message and attachment is archived, compressed, single instanced, and indexed immediately. Depending on the desired throughput rates and the number of Exchange servers being journaled, Acme Corp. may optionally configure a dedicated Enterprise Vault server for journal archiving tasks. Depending on regulatory requirements Acme Corp. may be addressing by using journaling, the Vault Store partition devices may need to be WORM (Write-Once-Read-Many) compliant. Enterprise Vault supports several WORM-compliant devices, such as Network Appliance NearStore with SnapLock, EMC Centera, IBM DR550, and Pegasus WORM Optical and WORM UDO media types. 7. Configure Public Folder archiving (optional). Acme Corp. is also storing historical messages, posts, and documents in various Exchange Server Public Folder trees. For Public Folder archiving, an archiving task is configured for one or more Top Level Folder (TLF) tree(s) that Acme Corp. will archive. Public Folder archiving behaves in a similar fashion to mailbox archiving, and similar archiving policies, archiving tasks, and schedules must be configured. 21
24 Figure 5. Various archiving tasks for an Exchange server in Enterprise Vault 8. Configure SMTP archiving to receive spam messages from Symantec Mail Security 8260 appliances. Enterprise Vault can be configured at Acme Corp. to capture and archive (into appropriate spam-retention archives) s sent directly to the archive servers from Symantec Mail Security 8260 appliances deployed at Acme Corp. As described above, these need to be retained for 180 days. (Refer to the section above titled Deploying Symantec Mail Security 8200 Series Appliances for further details on how to configure Symantec Mail Security 8260 appliances to forward spam s to Enterprise Vault.) Acme Corp. can install and configure the Enterprise Vault SMTP Archiving components on the desired Enterprise Vault servers. These make use of IIS SMTP services from the Windows Server platform, and are configured with a list of variables describing the Acme Corp. domains for which spam messages are being archived, and an archive structure (flat journal, or per recipient structured) for these archived domains. Acme Corp. can deploy SMTP archiving to capture for internal domains, where incoming spam has been received and forwarded directly to the archive. Acme Corp. can also deploy SMTP archiving to capture for external domains, where Content Compliance policies may have been triggered and a copy of an outgoing has been forwarded directly to the archive for retention. 22
25 a. Install the Enterprise Vault SMTP Archiving components. SMTP Archiving components must be installed on a Windows SMTP server. This may be the Enterprise Vault server, or a server dedicated to the tasks of capturing SMTP for archiving. Enterprise Vault SMTP Archiving components are installed directly from the Enterprise Vault CD. Consult the SMTP Archiving Guide for further details. b. Configure the SMTP Archiving components. The configuration file specifies the following details: The SMTP virtual server to which SMTP Archiving is to bind The address domains that SMTP Archiving is to process (note that domains not specifically configured will be processed into a default folder) The folders, and folder structure, on the server where SMTP Archiving is to put messages as they are captured for archiving Edit the file using a plain text editor such as Notepad, and save it as a Unicode file. Example Configuration File for Acme Corp.: [Server] Name=Default SMTP Virtual Server Priority=16000 NonDeliveryFolder=d:\EvMailRoot\ServerDefault DiskFullRetryLimit=0 [Domain] Name=acmecorp.com Path=d:\EvMailRoot\AcmeCorp [Domain] Name=acme.com Path=d:\EvMailRoot\Acme AutoEnableMbxFolders=True IndexingLevel=Brief NonDeliveryFolder=d:\EvMailRoot\Acme\NonDelivery 23
26 c. Create the required domain root folders. This is where the SMTP Archiving components queue the messages for archiving into a Vault Store. d. Configure archiving of the messages captured by SMTP Archiving components. Configuration of archiving schedules, target archives and Vault Stores, and other policy-based factors is achieved from the Enterprise Vault Administration Console. Acme Corp. can configure separate target archives, and even separate physical storage, for spam messages that need to be retained in this way as described above. Consult the Enterprise Vault SMTP Archiving Guide for further details. Deploying additional components Veritas Enterprise Vault Discovery Accelerator Discovery Accelerator enables companies to conduct searches of archived mail and documents in response to a legal discovery. Discovery Accelerator enables the company legal team to review items found by the searches to determine their relevance to the case. Items marked as being relevant to the case can be exported to be used as evidential records, as required. Consult the Enterprise Vault Discovery Accelerator Installation and Administration guides for specific details. Veritas Enterprise Vault Compliance Accelerator Compliance Accelerator enables organizations to monitor employees electronic messages (including and instant messages) to ensure compliance to policy, or good business practice. This is typically used at brokerage houses to monitor messages to meet regulation supervision requirements. It provides two main ways of monitoring Random samples of each employee s messages can be captured and sent for review each day; or all messages can be searched against a predefined lexicon for words or phrases that may indicate non-compliance. Consult the Enterprise Vault Compliance Accelerator Installation and Administration guides for specific details. 24
27 Symantec Mail Security 8160 Appliance Symantec Mail Security 8260 Appliance Symantec Mail Security for Microsoft Exchange Internet Gateway spam and content filtering Reduce spam and viruses Outbound content filtering and quarantine Monitor policy Delete or quarantine Mail server antivirus and antispam Application Storage SAN: Fibre Channel Archive; selective spam journaling Archive; real-time journaling archive Veritas Enterprise Vault for Exchange Archive Storage CAS, NAS; SATA Tape, Optical, etc. Figure 6. Final chosen security and archiving deployment topology for Acme Corp., showing new Symantec Mail Security appliances and software, and Veritas Enterprise Vault Scenario 2: Beta Corporation (Beta Corp.) Beta Corporation (Beta Corp.) runs a clustered Microsoft Exchange Server 2003 messaging and groupware system. Beta Corp. wants to avoid message journaling and associated journal archiving in Exchange, but wants to archive a copy of all messages where the words Confidential, Client Privileged, or Internal Only appear, directly to a separate administrative archive for three years for later discovery purposes. Beta Corp also wishes to archive spam s directly to Enterprise Vault for 60 days, instead of a quarantine location, as it provides a lower-cost store to maintain spam in case of false positives, as well as a full text index content search for the spam in temporary hold. Beta Corp. also wants to ensure appropriate levels of antivirus and antispam defenses including a significant reduction in network traffic associated with spam before it reaches the organization. Additionally, Beta Corp. wants to archive the messages retained in users mailboxes after 90 days to ensure optimization of storage associated with, and operational running of, Microsoft Exchange systems. 25
28 Firewall Bridgehead Server Mail server antivirus Internet Microsoft Exchange 2003 Some quarantined Application Storage SAN: Fibre Channel Figure 7. Existing and groupware topology at Beta Corp. Solution: To achieve the stated goals in this scenario, Beta Corp. can implement the following solution where Symantec Mail Security and Veritas Enterprise Vault work together: Desired goal Archive a copy of all external records showing target phrases Reduce network traffic due to spam before the network perimeter Further reduce spam and virus-infected after acceptance, archive spam messages, and enforce policy Ensure appropriate levels of antivirus for Exchange servers and clients Search, review, and produce messages as evidential records Solution chosen for deployment Symantec Mail Security 8260 appliance with Veritas Enterprise Vault for SMTP Archiving Symantec Mail Security 8160 appliance with SMTP Traffic Shaping Symantec Mail Security 8260 appliance with Veritas Enterprise Vault for SMTP Archiving Symantec Mail Security for Microsoft Exchange and Symantec AntiVirus Corporate Edition Veritas Enterprise Vault Discovery Accelerator Accordingly, the following products are chosen for deployment at Beta Corp. Vendor Product Version/Type Symantec Mail Security 8100 Series 8160/Appliance Symantec Mail Security 8200 Series 8260/Appliance Symantec Mail Security for Microsoft Exchange 5.0/Cluster Aware Symantec Enterprise Vault for Exchange 6.0/Server + Standby Optional products below are also chosen for deployment at Beta Corp. Vendor Product Version/Type Symantec Enterprise Vault Discovery Accelerator 5.0/Server 26
29 Deploying the Symantec Mail Security 8100 Series Deployment of Symantec Mail Security 8160 appliances allows Beta Corp. to employ a bestof-breed appliance that leverages market-leading unique antispam traffic shaping technology. This technology reduces infrastructure costs by restricting connections from spam-sending servers and significantly reducing the received amounts of spam before they are even accepted into the corporate system at the network boundary. The objective is to significantly reduce the transfer capacity available to spammers, while continuing to maintain it for legitimate sources of . Refer to the section titled Deploying the Symantec Mail Security 8100 Series on page 10 for general details on this part of the solution. Symantec Mail Security 8160 appliances are configured similarly for Beta Corp. Key differences from Scenario 1, Acme Corp.: None. For further details on any aspect, refer to the Symantec Mail Security 8100 Series Implementation Guide, available at Deploying the Symantec Mail Security 8200 Series Deployment of Symantec Mail Security 8260 antivirus and antispam appliances allows Beta Corp. to further employ best-of-breed appliance technology that leverages over 20 spam prevention techniques, including Symantec Brightmail AntiSpam, Directory Harvest Attack Prevention, and Sender Reputation techniques; all of which reduce infrastructure costs by significantly reducing the received amounts of accepted spam, after initial spam reduction is effected by 8160 appliances. Additionally, Content Compliance features allow administrators to gain control over inbound and outbound content so they can enforce internal or regulatory content policies, before an issue even arises. Beta Corp. will leverage these features to archive copies of messages where certain target phrases arise, directly to Enterprise Vault for SMTP Archiving. Refer to the section titled Deploying the Symantec Mail Security 8200 Series on page 7 for general details on this part of the solution. Symantec Mail Security 8260 appliances are configured similarly for Beta Corp. 27
30 Key differences from Scenario 1, Acme Corp.: 1. Configure all Scanner appliances with Beta Corp. s security policies. Given Beta Corp. s goals of providing appropriate security for the business at the perimeter of the network, while still retaining the ability to archive messages with target words and phrases Confidential, Client Privileged, or Internal Only to Veritas Enterprise Vault, some examples are given below; Symantec Mail Desired Goal Security 8260 Action Details Archive copies of Archive (+ optional messages may be checked against policy compliance messages exhibiting Delete or Quarantine) by Symantec Mail Security 8200 Series appliances, including target phrases by dictionary, content filters, attachment blocking, and property analysis, and then treated in a number of optional ways: 1. Archived to an administrative SMTP address in Enterprise Vault (optionally a percentage of these may be reviewed) for Compliance, Policy, or Privacy purposes 2. Forwarded to Quarantine (optionally notifying the administrator) 3. Blocked and deleted at the appliance before entering or leaving the organization 4. Blocked and archived to an administrative SMTP address in Enterprise Vault 2. Configure 8260 appliances to forward copies of selected messages to Enterprise Vault for archiving. Beta Corp. needs to retain messages that include the target words and phrases Confidential, Client Privileged, or Internal Only, indicating a need to check that the messages are not out of policy boundaries. Enterprise Vault for SMTP Archiving allows Beta Corp. to easily achieve this: a. Configure target forwarding ( Archive action in Symantec Mail Security 8260) to Enterprise Vault via SMTP archiving Beta Corp. can simply archive messages that are found by Symantec Mail Security to contain target words and phrases, by administratively forwarding them directly to an SMTP capture address in Enterprise Vault. These will then be archived for each recipient at Beta Corp. into an administrative set of retention archives as necessary, and can be immediately searched, reviewed, and exported as necessary (refer to the section Deploying Enterprise Vault below for further details). 28
31 Deploying Symantec Mail Security for Microsoft Exchange Refer to the section titled Deploying Symantec Mail Security for Exchange on page 16 for general details on this part of the solution. Symantec Mail Security for Microsoft Exchange is configured similarly for Beta Corp. Key differences from Scenario 1, Acme Corp.: None. Beta Corp. also needs to configure antivirus, further antispam, and other policy aspects of Symantec Mail Security for Microsoft Exchange appropriately. For further details on any aspect, refer to the Symantec Mail Security for Microsoft Exchange Implementation Guide, available at Deploying Veritas Enterprise Vault Enterprise Vault 6.0 is installed on Windows Server 2003 to host the archive for Exchange servers at Beta Corp., as well as the archive for any messages containing target words and phrases captured directly from the Symantec Mail Security 8260 series appliances, and a variety of other information within the business. The Enterprise Vault data is stored on a near-line NAS device (or SAN, DAS, SATA, etc.) initially to ensure rapid access to archived content, while providing storage cost benefits desired by Beta Corp. at the same time. Later during the lifecycle of archived messages (and other information), they may be moved by Enterprise Vault onto other storage devices such as tape or optical libraries for long-term retention. Refer to the section titled Deploying Veritas Enterprise Vault on page 19 for general details on this part of the solution. Veritas Enterprise Vault is configured similarly for Beta Corp. Key differences from Scenario 1, Acme Corp.: 1. Configure mailbox archiving. Enterprise Vault servers are responsible for various archiving tasks (mailbox, journal, public folder, PST file migration, etc.) that are dedicated to certain Exchange servers. Beta Corp. needs to configure an appropriate number of Enterprise Vault servers to perform scheduled mailbox archiving for all Exchange Virtual Servers being managed. As a guideline, one Enterprise Vault server may be generally required for every three to four equivalent mailbox home Exchange servers (depending on mailbox numbers per server and utilization rates). Once configured for each Exchange server, the archiving tasks are started and will then synchronize the initial list of mailbox users and their associated properties from the Exchange Organization and Active Directory. 29
32 Users must then be enabled for archiving, which may include configuration of a Vault Store for user archives, deployment and configuration of any necessary client components (optional), configuration of the mailbox archiving policies for various user groups (globally, by OU, or by grouping via various unique LDAP properties), and final scheduled enablement of users mailboxes for archiving services. Users may be enabled in groups to allow appropriate phasing of archiving services into Beta Corp. s organization. Finally, archiving tasks should be scheduled to run at appropriate times, after completion of Beta Corp. s Exchange Server backup windows. Figure 8. Exchange mailbox archiving policies in Veritas Enterprise Vault Beta Corp. wants to archive the messages retained in users mailboxes after 90 days to ensure optimization of storage associated with, and operational running of, Microsoft Exchange systems. To do so, Beta Corp. can configure one global mailbox archiving policy for all user mailboxes. 30
33 Figure 9. Age-based mailbox archiving policy for 90-day archiving for Beta Corp. Includes archiving of items larger than 1 MB at 30 days. 2. Configure journal archiving. Exchange servers may host one or more journal mailboxes that receive copies of all messages passing through Exchange Server Stores. An Enterprise Vault journal archiving task needs to be configured for each Exchange server and will process one or more journal mailboxes. Journal archiving tasks process journal mailboxes every 60 seconds and, as such, run continuously after the initial startup. Every message and attachment is archived, compressed, single instanced, and indexed immediately. Beta Corp chooses not to employ Microsoft Exchange Server Journaling, and doesn t require journal archiving. 31
34 3. Configure SMTP archiving to receive messages with target phrases from Symantec Mail Security 8260 appliances. Enterprise Vault is configured at Beta Corp. to capture and archive (into appropriate administrative retention archives) s sent directly to the archive servers from Symantec Mail Security 8260 appliances deployed at Beta Corp. As described above, these need to be retained when the words or phrases Confidential, Client Privileged, or Internal Only appear in an being sent externally or received from external sources. (Refer to the section above titled Deploying the Symantec Mail Security 8200 Series for further details on how to configure Symantec Mail Security 8260 appliances to forward spam s to Enterprise Vault.) Beta Corp. can install and configure the Enterprise Vault SMTP Archiving components on the desired Enterprise Vault servers. These make use of IIS SMTP services from the Windows Server platform, and are configured with a list of variables describing the Beta Corp. domains for which such target messages are being archived, and an archive structure (flat journal, or per recipient structured) for these archived domains. a. Install the Enterprise Vault SMTP Archiving components. SMTP Archiving components must be installed on a Windows SMTP server. This may be the Enterprise Vault server, or a server dedicated to the tasks of capturing SMTP for archiving. Enterprise Vault SMTP Archiving components are installed directly from the Enterprise Vault CD. Consult the SMTP Archiving Guide for further details. b. Configure the SMTP Archiving components. The configuration file specifies the following details: The SMTP virtual server to which SMTP Archiving is to bind The address domains that SMTP Archiving is to process (note that domains not specifically configured will be processed into a default folder) The folders, and folder structure, on the server where SMTP Archiving is to put messages as they are captured for archiving Edit the file using a plain text editor such as Notepad, and save it as a Unicode file. 32
35 Example Configuration File for Beta Corp.: [Server] Name=Default SMTP Virtual Server Priority=16000 NonDeliveryFolder=d:\EvMailRoot\ServerDefault DiskFullRetryLimit=0 [Domain] Name=beta.com Path=d:\EvMailRoot\Beta AutoEnableMbxFolders=True IndexingLevel=Brief NonDeliveryFolder=d:\EvMailRoot\Beta\NonDelivery c. Create the required domain root folders. This is where the SMTP Archiving components queue the messages for archiving into a Vault Store. d. Configure archiving of the messages captured by SMTP Archiving components. Configuration of archiving schedules, target archives and Vault Stores, and other policybased factors is achieved from the Enterprise Vault Administration Console. Beta Corp. can configure separate target archives, and even separate physical storage for messages that need to be retained in this way, as described above. Consult the SMTP Archiving Guide for further details. 33
36 Deploying additional components Veritas Enterprise Vault Discovery Accelerator Discovery Accelerator enables companies to conduct searches of archived mail and documents in response to a legal discovery. Discovery Accelerator enables the company legal team to review items found by the searches to determine their relevance to a particular case. Items marked as being relevant to the case can be exported to be used as evidential records, as required. Consult the Discovery Accelerator Installation and Administration guides for specific details. Symantec Mail Security 8160 Appliance Symantec Mail Security 8260 Appliance Symantec Mail Security for Microsoft Exchange Internet Gateway spam and content filtering Reduce spam and viruses Outbound content filtering and quarantine Monitor policy Delete or quarantine Mail server antivirus and antispam Application Storage SAN: Fibre Channel Archive; selective s with target words Archive; mbx policy 90 days archive Veritas Enterprise Vault for Exchange Archive Storage CAS, NAS; SATA Tape, Optical, etc. Figure 10. Final chosen security and archiving deployment topology for Acme Corp., showing new Symantec Mail Security appliances and software, and Veritas Enterprise Vault. 34
37 Tested solutions The combined, integrated solutions outlined in this white paper have been tested by Symantec Corporation, in the Veritas Software Integration and Functional Test laboratories (SWIFT); May Summary This white paper has described how two businesses (Acme Corporation and Beta Corporation) can deploy Symantec Mail Security appliances and software both within and without the organization to achieve various security and content compliance goals. It further describes how they can integrate Symantec technology with Veritas Enterprise Vault to ensure that necessary messages are captured and retained in a cost-effective and usable manner, optionally including any necessary antivirus- and antispam-related messages that may need to be captured and retained in an appropriate low-cost and secured archive for privacy or compliance reasons. The hypothetical Acme Corporation and Beta Corporation discussed in this white paper illustrate two example challenges and solutions associated with security as pertains to: Inbound hygiene at the network perimeter and inside the organization content compliance with regard to outbound and intra-organizational archiving for storage management and optimization of Exchange Server services, as well as journaling and compliance-related capture of messages passing through the organization to meet regulatory requirements 35
38
39 About Symantec Symantec is the world leader in providing solutions to help individuals and enterprises assure the security, availability, and integrity of their information. Headquartered in Cupertino, Calif., Symantec has operations in more than 40 countries. More information is available at For specific country offices and contact numbers, please visit For additional information in the U.S. call toll-free 1 (800) or visit secureapps. Symantec Corporation World Headquarters Stevens Creek Boulevard Cupertino, CA USA +1 (408) (800) Copyright 2006 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, Symantec AntiVirus, SESA, VERITAS, Brightmail, Enterprise Vault, NetBackup and LiveUpdate are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. 2/
Copyright 2011 Sophos Ltd. Copyright strictly reserved. These materials are not to be reproduced, either in whole or in part, without permissions.
 PureMessage for Microsoft Exchange protects Microsoft Exchange servers and Windows gateways against email borne threats such as from spam, phishing, viruses, spyware. In addition, it controls information
PureMessage for Microsoft Exchange protects Microsoft Exchange servers and Windows gateways against email borne threats such as from spam, phishing, viruses, spyware. In addition, it controls information
Data Sheet: Archiving Symantec Enterprise Vault Store, Manage, and Discover Critical Business Information
 Store, Manage, and Discover Critical Business Information Managing millions of mailboxes for thousands of customers worldwide, Enterprise Vault, the industry leader in email and content archiving, enables
Store, Manage, and Discover Critical Business Information Managing millions of mailboxes for thousands of customers worldwide, Enterprise Vault, the industry leader in email and content archiving, enables
eprism Email Security Appliance 6.0 Release Notes What's New in 6.0
 eprism Email Security Appliance 6.0 Release Notes St. Bernard is pleased to announce the release of version 6.0 of the eprism Email Security Appliance. This release adds several new features while considerably
eprism Email Security Appliance 6.0 Release Notes St. Bernard is pleased to announce the release of version 6.0 of the eprism Email Security Appliance. This release adds several new features while considerably
Solution Brief: Enterprise Security
 Symantec Brightmail Gateway and VMware Solution Brief: Enterprise Security Symantec Brightmail Gateway and VMware Contents Corporate overview......................................................................................
Symantec Brightmail Gateway and VMware Solution Brief: Enterprise Security Symantec Brightmail Gateway and VMware Contents Corporate overview......................................................................................
Email Migration Project Plan for Cisco Cloud Email Security
 Sales Tool Email Migration Project Plan for Cisco Cloud Email Security 2014 Cisco and/or its affiliates. All rights reserv ed. This document is Cisco Conf idential. For Channel Partner use only. Not f
Sales Tool Email Migration Project Plan for Cisco Cloud Email Security 2014 Cisco and/or its affiliates. All rights reserv ed. This document is Cisco Conf idential. For Channel Partner use only. Not f
Securing enterprise collaboration through email and file sharing on a unified platform
 Axway MailGate SC Securing enterprise collaboration through email and file sharing on a unified platform Email is the primary collaboration tool employees use to share information and send large files.
Axway MailGate SC Securing enterprise collaboration through email and file sharing on a unified platform Email is the primary collaboration tool employees use to share information and send large files.
Symantec Hosted Mail Security Getting Started Guide
 Symantec Hosted Mail Security Getting Started Guide Redirecting Your MX Record You have successfully activated your domain within the Symantec Hosted Mail Security Console. In order to begin the filtration
Symantec Hosted Mail Security Getting Started Guide Redirecting Your MX Record You have successfully activated your domain within the Symantec Hosted Mail Security Console. In order to begin the filtration
Eiteasy s Enterprise Email Filter
 Eiteasy s Enterprise Email Filter Eiteasy s Enterprise Email Filter acts as a shield for companies, small and large, who are being inundated with Spam, viruses and other malevolent outside threats. Spammer
Eiteasy s Enterprise Email Filter Eiteasy s Enterprise Email Filter acts as a shield for companies, small and large, who are being inundated with Spam, viruses and other malevolent outside threats. Spammer
Data Sheet: Endpoint Security Symantec Protection Suite Enterprise Edition Trusted protection for endpoints and messaging environments
 Trusted protection for endpoints and messaging environments Overview Symantec Protection Suite Enterprise Edition creates a protected endpoint and messaging environment that is secure against today s complex
Trusted protection for endpoints and messaging environments Overview Symantec Protection Suite Enterprise Edition creates a protected endpoint and messaging environment that is secure against today s complex
Symantec Mail Security for Domino
 Getting Started Symantec Mail Security for Domino About Symantec Mail Security for Domino Symantec Mail Security for Domino is a complete, customizable, and scalable solution that scans Lotus Notes database
Getting Started Symantec Mail Security for Domino About Symantec Mail Security for Domino Symantec Mail Security for Domino is a complete, customizable, and scalable solution that scans Lotus Notes database
Installing GFI MailEssentials
 Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter explains the procedure on how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in
Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter explains the procedure on how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in
FortiMail Email Filtering. Course 221 (for FortiMail v5.0) Course Overview
 FortiMail Email Filtering Course 221 (for FortiMail v5.0) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221 (for FortiMail v5.0) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
Symantec AntiVirus Enterprise Edition
 Symantec AntiVirus Enterprise Edition Comprehensive threat protection for every network tier, including client-based spyware prot e c t i o n, in a single product suite Overview Symantec AntiVirus Enterprise
Symantec AntiVirus Enterprise Edition Comprehensive threat protection for every network tier, including client-based spyware prot e c t i o n, in a single product suite Overview Symantec AntiVirus Enterprise
Installing GFI MailEssentials
 Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter shows you how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in two ways: Installation
Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter shows you how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in two ways: Installation
FortiMail Email Filtering. Course 221 (for FortiMail v4.2) Course Overview
 FortiMail Email Filtering Course 221 (for FortiMail v4.2) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221 (for FortiMail v4.2) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
How To Configure Forefront Threat Management Gateway (Forefront) For An Email Server
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
PureMessage for Microsoft Exchange Help. Product version: 4.0
 PureMessage for Microsoft Exchange Help Product version: 4.0 Document date: July 2013 Contents 1 About PureMessage for Microsoft Exchange...3 2 Key concepts...4 3 Administration console...7 4 Monitoring...9
PureMessage for Microsoft Exchange Help Product version: 4.0 Document date: July 2013 Contents 1 About PureMessage for Microsoft Exchange...3 2 Key concepts...4 3 Administration console...7 4 Monitoring...9
Configuration Information
 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
Technical Note. ISP Protection against BlackListing. FORTIMAIL Deployment for Outbound Spam Filtering. Rev 2.2
 Technical Note ISP Protection against BlackListing FORTIMAIL Deployment for Outbound Spam Filtering Rev 2.2 April 14, 2009 Table of Contents 1 Objective IP address protection... 3 1.1 Context... 3 1.2
Technical Note ISP Protection against BlackListing FORTIMAIL Deployment for Outbound Spam Filtering Rev 2.2 April 14, 2009 Table of Contents 1 Objective IP address protection... 3 1.1 Context... 3 1.2
Evaluation Guide. eprism Messaging Security Suite. 800-782-3762 www.edgewave.com V8.200
 800-782-3762 www.edgewave.com Welcome to EdgeWave Messaging Security! This short guide is intended to help administrators setup and test the EdgeWave Messaging Security Suite for evaluation purposes. A
800-782-3762 www.edgewave.com Welcome to EdgeWave Messaging Security! This short guide is intended to help administrators setup and test the EdgeWave Messaging Security Suite for evaluation purposes. A
Securing enterprise collaboration through email and file sharing on a unified platform
 Axway MailGate SC Securing enterprise collaboration through email and file sharing on a unified platform Email is the primary collaboration tool employees use to share information and send large files.
Axway MailGate SC Securing enterprise collaboration through email and file sharing on a unified platform Email is the primary collaboration tool employees use to share information and send large files.
V1.4. Spambrella Email Continuity SaaS. August 2
 V1.4 August 2 Spambrella Email Continuity SaaS Easy to implement, manage and use, Message Continuity is a scalable, reliable and secure service with no set-up fees. Built on a highly reliable and scalable
V1.4 August 2 Spambrella Email Continuity SaaS Easy to implement, manage and use, Message Continuity is a scalable, reliable and secure service with no set-up fees. Built on a highly reliable and scalable
SERVICE LEVEL AGREEMENT
 SERVICE LEVEL AGREEMENT This Service Level Agreement (SLA) is provided by ECS and is intended to define services and responsibilities between ECS and customer. ECS along with contracted 3 rd party partners
SERVICE LEVEL AGREEMENT This Service Level Agreement (SLA) is provided by ECS and is intended to define services and responsibilities between ECS and customer. ECS along with contracted 3 rd party partners
Symantec Messaging Gateway 10.5
 Powerful email gateway protection Data Sheet: Messaging Security Overview Symantec Messaging Gateway enables organizations to secure their email and productivity infrastructure with effective and accurate
Powerful email gateway protection Data Sheet: Messaging Security Overview Symantec Messaging Gateway enables organizations to secure their email and productivity infrastructure with effective and accurate
Websense Email Security Transition Guide
 Websense Email Security Transition Guide Websense Email Security Gateway v7.6 2011, Websense Inc. All rights reserved. 10240 Sorrento Valley Rd., San Diego, CA 92121, USA R140611760 Published August 2011
Websense Email Security Transition Guide Websense Email Security Gateway v7.6 2011, Websense Inc. All rights reserved. 10240 Sorrento Valley Rd., San Diego, CA 92121, USA R140611760 Published August 2011
250-310. Administration of Symantec Enterprise Vault 10.0 for Exchange. Version: Demo. Page <<1/12>>
 250-310 Administration of Symantec Enterprise Vault 10.0 for Exchange Version: Demo Page 1.Enterprise Vault converts mail message attachments to text or HTML. What is a benefit of changing the
250-310 Administration of Symantec Enterprise Vault 10.0 for Exchange Version: Demo Page 1.Enterprise Vault converts mail message attachments to text or HTML. What is a benefit of changing the
FortiMail Email Filtering Course 221-v2.2 Course Overview
 FortiMail Email Filtering Course 221-v2.2 Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed to design, configure,
FortiMail Email Filtering Course 221-v2.2 Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed to design, configure,
E-MAIL AND SERVER SECURITY
 E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 2. Deployment scenarios 5 2.1 Stand-alone server 5 2.2 Deploying the product with F-Secure
E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 2. Deployment scenarios 5 2.1 Stand-alone server 5 2.2 Deploying the product with F-Secure
Symantec Brightmail Gateway Real-time protection backed by the largest investment in security infrastructure
 Real-time protection backed by the largest investment in security infrastructure Overview delivers inbound and outbound messaging security, with effective and accurate real-time antispam and antivirus
Real-time protection backed by the largest investment in security infrastructure Overview delivers inbound and outbound messaging security, with effective and accurate real-time antispam and antivirus
E-MAIL AND SERVER SECURITY
 E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 1.1 How the product works 3 1.2 Product contents 4 2. Deployment scenarios 5 2.1 Stand-alone
E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 1.1 How the product works 3 1.2 Product contents 4 2. Deployment scenarios 5 2.1 Stand-alone
Enterprise Email Archive Managed Archiving & ediscovery Services User Manual
 Enterprise Email Archive Managed Archiving & ediscovery Services User Manual Copyright (C) 2012 MessageSolution Inc. All Rights Reserved Table of Contents Chapter 1: Introduction... 3 1.1 About MessageSolution
Enterprise Email Archive Managed Archiving & ediscovery Services User Manual Copyright (C) 2012 MessageSolution Inc. All Rights Reserved Table of Contents Chapter 1: Introduction... 3 1.1 About MessageSolution
Symantec Mail Security Appliance Version 7.5 Administration Guide
 Symantec Mail Security Appliance Version 7.5 Administration Guide Symantec Information Foundation 12617000 Symantec Mail Security Appliance Version 7.5 Administration Guide The software described in this
Symantec Mail Security Appliance Version 7.5 Administration Guide Symantec Information Foundation 12617000 Symantec Mail Security Appliance Version 7.5 Administration Guide The software described in this
Cisco IronPort C370 for Medium-Sized Enterprises and Satellite Offices
 Data Sheet Cisco IronPort C370 for Medium-Sized Enterprises and Satellite Offices Medium-sized enterprises face the same daunting challenges as the Fortune 500 and Global 2000 - higher mail volumes and
Data Sheet Cisco IronPort C370 for Medium-Sized Enterprises and Satellite Offices Medium-sized enterprises face the same daunting challenges as the Fortune 500 and Global 2000 - higher mail volumes and
FortiMail Email Filtering. Course 221 - for FortiMail v4.0. Course Overview
 FortiMail Email Filtering Course 221 - for FortiMail v4.0 Course Overview FortiMail Email Filtering is a 3-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221 - for FortiMail v4.0 Course Overview FortiMail Email Filtering is a 3-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
REDCENTRIC MANAGED ARCHIVE SERVICE SERVICE DEFINITION
 REDCENTRIC MANAGED ARCHIVE SERVICE SERVICE DEFINITION SD005 V2.0 Issue Date 02 July 2014 1) SERVICE OVERVIEW Redcentric's Managed Archive Service allows customers to regain control of their Microsoft Exchange
REDCENTRIC MANAGED ARCHIVE SERVICE SERVICE DEFINITION SD005 V2.0 Issue Date 02 July 2014 1) SERVICE OVERVIEW Redcentric's Managed Archive Service allows customers to regain control of their Microsoft Exchange
Symantec Messaging Gateway 10.6
 Powerful email gateway protection Data Sheet: Messaging Security Overview Symantec Messaging Gateway enables organizations to secure their email and productivity infrastructure with effective and accurate
Powerful email gateway protection Data Sheet: Messaging Security Overview Symantec Messaging Gateway enables organizations to secure their email and productivity infrastructure with effective and accurate
Trend Micro Hosted Email Security Stop Spam. Save Time.
 Trend Micro Hosted Email Security Stop Spam. Save Time. How it Works: Trend Micro Hosted Email Security A Trend Micro White Paper l March 2010 Table of Contents Introduction...3 Solution Overview...4 Industry-Leading
Trend Micro Hosted Email Security Stop Spam. Save Time. How it Works: Trend Micro Hosted Email Security A Trend Micro White Paper l March 2010 Table of Contents Introduction...3 Solution Overview...4 Industry-Leading
74% 96 Action Items. Compliance
 Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Installing GFI MailSecurity
 Installing GFI MailSecurity Introduction This chapter explains how to install and configure GFI MailSecurity. You can install GFI MailSecurity directly on your mail server or you can choose to install
Installing GFI MailSecurity Introduction This chapter explains how to install and configure GFI MailSecurity. You can install GFI MailSecurity directly on your mail server or you can choose to install
FortiMail Email Filtering Course 221-v2.0. Course Overview. Course Objectives
 FortiMail Email Filtering Course 221-v2.0 Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed to configure,
FortiMail Email Filtering Course 221-v2.0 Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed to configure,
The GlobalCerts TM SecureMail Gateway TM
 Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
Installing Policy Patrol on a separate machine
 Policy Patrol 3.0 technical documentation July 23, 2004 Installing Policy Patrol on a separate machine If you have Microsoft Exchange Server 2000 or 2003 it is recommended to install Policy Patrol on the
Policy Patrol 3.0 technical documentation July 23, 2004 Installing Policy Patrol on a separate machine If you have Microsoft Exchange Server 2000 or 2003 it is recommended to install Policy Patrol on the
THE INFOCROSSING SECURE EMAIL BOUNDARY SERVICE
 THE INFOCROSSING SECURE EMAIL BOUNDARY SERVICE EMAIL BORNE THREATS An Escalating Problem for Every Business More than three out of four emails contain spam, viruses or other malicious content and that
THE INFOCROSSING SECURE EMAIL BOUNDARY SERVICE EMAIL BORNE THREATS An Escalating Problem for Every Business More than three out of four emails contain spam, viruses or other malicious content and that
TEAL: Transparent Email Archiving Library
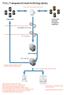 TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
IBM Lotus Protector for Mail Security. Administrator Guide. Version 2.8 Release 2.8.1 SC27-3829-01
 IBM Lotus Protector for Mail Security Administrator Guide Version 2.8 Release 2.8.1 SC27-3829-01 Copyright statement Copyright IBM Corporation 2006, 2013. U.S. Government Users Restricted Rights Use, duplication
IBM Lotus Protector for Mail Security Administrator Guide Version 2.8 Release 2.8.1 SC27-3829-01 Copyright statement Copyright IBM Corporation 2006, 2013. U.S. Government Users Restricted Rights Use, duplication
Quick Start Policy Patrol Spam Filter 5
 Quick Start Policy Patrol Spam Filter 5 This guide will help you start using Policy Patrol Spam Filter as quickly as possible. For more detailed instructions, consult the Policy Patrol manual. Step 1.
Quick Start Policy Patrol Spam Filter 5 This guide will help you start using Policy Patrol Spam Filter as quickly as possible. For more detailed instructions, consult the Policy Patrol manual. Step 1.
Cisco IronPort X1070 Email Security System
 Data Sheet Cisco IronPort X1070 Email Security System As the battle to protect the email perimeter continues, two predominant trends emerge: higher mail volumes and more resource-intensive scanning. The
Data Sheet Cisco IronPort X1070 Email Security System As the battle to protect the email perimeter continues, two predominant trends emerge: higher mail volumes and more resource-intensive scanning. The
Scan Sequence and Action in Microsoft Forefront Protection 2010 for Exchange Server
 Scan Sequence and Action in Microsoft Forefront Protection 2010 for Exchange Server Published: October, 2009 Software version: Forefront Protection 2010 for Exchange Server Carolyn Liu Introduction...
Scan Sequence and Action in Microsoft Forefront Protection 2010 for Exchange Server Published: October, 2009 Software version: Forefront Protection 2010 for Exchange Server Carolyn Liu Introduction...
Features and benefits guide for partners and their customers
 and benefits guide for partners and their customers Version 3.0 and Guide for Partners and their customers Security Anti Virus Proofpoint s own threat detection technology enables our email Anti-Virus
and benefits guide for partners and their customers Version 3.0 and Guide for Partners and their customers Security Anti Virus Proofpoint s own threat detection technology enables our email Anti-Virus
Data Sheet: Archiving Symantec Enterprise Vault Discovery Accelerator Accelerate e-discovery and simplify review
 Accelerate e-discovery and simplify review Overview provides IT/Legal liaisons, investigators, lawyers, paralegals and HR professionals the ability to search, preserve and review information across the
Accelerate e-discovery and simplify review Overview provides IT/Legal liaisons, investigators, lawyers, paralegals and HR professionals the ability to search, preserve and review information across the
Symantec Enterprise Vault for Lotus Domino
 Symantec Enterprise Vault for Lotus Domino Store, Manage and Discover Critical Business Information Overview Industry-leading email archiving for Lotus Domino With the recognition that email has become
Symantec Enterprise Vault for Lotus Domino Store, Manage and Discover Critical Business Information Overview Industry-leading email archiving for Lotus Domino With the recognition that email has become
Spam Testing Methodology Opus One, Inc. March, 2007
 Spam Testing Methodology Opus One, Inc. March, 2007 This document describes Opus One s testing methodology for anti-spam products. This methodology has been used, largely unchanged, for four tests published
Spam Testing Methodology Opus One, Inc. March, 2007 This document describes Opus One s testing methodology for anti-spam products. This methodology has been used, largely unchanged, for four tests published
PureMessage for Microsoft Exchange Help. Product version: 3.1
 PureMessage for Microsoft Exchange Help Product version: 3.1 Document date: June 2015 Contents 1 About PureMessage for Microsoft Exchange...4 2 Key concepts...5 2.1 Key concepts overview...5 2.2 Inbound,
PureMessage for Microsoft Exchange Help Product version: 3.1 Document date: June 2015 Contents 1 About PureMessage for Microsoft Exchange...4 2 Key concepts...5 2.1 Key concepts overview...5 2.2 Inbound,
PureMessage for Microsoft Exchange startup guide
 PureMessage for Microsoft Exchange startup guide Product version: 3.1 Document date: May 2010 Contents 1 About this guide...3 2 Planning your PureMessage deployment...4 3 Installing PureMessage...6 4 Starting
PureMessage for Microsoft Exchange startup guide Product version: 3.1 Document date: May 2010 Contents 1 About this guide...3 2 Planning your PureMessage deployment...4 3 Installing PureMessage...6 4 Starting
K7 Mail Security FOR MICROSOFT EXCHANGE SERVERS. v.109
 K7 Mail Security FOR MICROSOFT EXCHANGE SERVERS v.109 1 The Exchange environment is an important entry point by which a threat or security risk can enter into a network. K7 Mail Security is a complete
K7 Mail Security FOR MICROSOFT EXCHANGE SERVERS v.109 1 The Exchange environment is an important entry point by which a threat or security risk can enter into a network. K7 Mail Security is a complete
Configuration Information
 Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
IronPort C-Series Overview High performance email security appliances. Carrier-proven technology, enterprise-class management.
 Overview IronPort C-Series Overview High performance email security appliances. Carrier-proven technology, enterprise-class management. The IronPort C-Series email security appliances provide advanced
Overview IronPort C-Series Overview High performance email security appliances. Carrier-proven technology, enterprise-class management. The IronPort C-Series email security appliances provide advanced
Reviewer s Guide. PureMessage for Windows/Exchange Product tour 1
 Reviewer s Guide PureMessage for Windows/Exchange Product tour 1 REVIEWER S GUIDE: SOPHOS PUREMESSAGE FOR LOTUS DOMINO WELCOME Welcome to the reviewer s guide for Sophos PureMessage for Lotus Domino, one
Reviewer s Guide PureMessage for Windows/Exchange Product tour 1 REVIEWER S GUIDE: SOPHOS PUREMESSAGE FOR LOTUS DOMINO WELCOME Welcome to the reviewer s guide for Sophos PureMessage for Lotus Domino, one
Trend Micro Hosted Email Security Stop Spam. Save Time.
 Trend Micro Hosted Email Security Stop Spam. Save Time. How Hosted Email Security Inbound Filtering Adds Value to Your Existing Environment A Trend Micro White Paper l March 2010 1 Table of Contents Introduction...3
Trend Micro Hosted Email Security Stop Spam. Save Time. How Hosted Email Security Inbound Filtering Adds Value to Your Existing Environment A Trend Micro White Paper l March 2010 1 Table of Contents Introduction...3
Enterprise Vault Installing and Configuring
 Enterprise Vault Installing and Configuring Enterprise Vault 6.0 Legal Notice Copyright 2005 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, VERITAS, the VERITAS Logo, and Enterprise
Enterprise Vault Installing and Configuring Enterprise Vault 6.0 Legal Notice Copyright 2005 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, VERITAS, the VERITAS Logo, and Enterprise
PRO: Deploying Messaging Solutions with Microsoft Exchange Server 2007 by Exambie
 PRO: Deploying Messaging Solutions with Microsoft Exchange Server 2007 by Exambie Number: 70-238 Passing Score: 700 Time Limit: 120 min File Version: 2.73 Pass4Sure V2.73 Microsoft 70-238 Pro:Deploying
PRO: Deploying Messaging Solutions with Microsoft Exchange Server 2007 by Exambie Number: 70-238 Passing Score: 700 Time Limit: 120 min File Version: 2.73 Pass4Sure V2.73 Microsoft 70-238 Pro:Deploying
Barracuda Spam Firewall Administrator s Guide
 Barracuda Spam Firewall Administrator s Guide 1 Copyright Copyright 2005, Barracuda Networks www.barracudanetworks.com v3.2.22 All rights reserved. Use of this product and this manual is subject to license.
Barracuda Spam Firewall Administrator s Guide 1 Copyright Copyright 2005, Barracuda Networks www.barracudanetworks.com v3.2.22 All rights reserved. Use of this product and this manual is subject to license.
Data Sheet: Backup & Recovery Symantec Backup Exec 12.5 for Windows Servers The gold standard in Windows data protection
 The gold standard in Windows data protection Overview Symantec Backup Exec 12.5 delivers market-leading backup and recovery protection from server to desktop, providing complete data protection for the
The gold standard in Windows data protection Overview Symantec Backup Exec 12.5 delivers market-leading backup and recovery protection from server to desktop, providing complete data protection for the
Symantec Messaging Gateway powered by Brightmail
 The first name in messaging security powered by Brightmail Overview, delivers inbound and outbound messaging security, with effective and accurate real-time antispam and antivirus protection, advanced
The first name in messaging security powered by Brightmail Overview, delivers inbound and outbound messaging security, with effective and accurate real-time antispam and antivirus protection, advanced
Did you know your security solution can help with PCI compliance too?
 Did you know your security solution can help with PCI compliance too? High-profile data losses have led to increasingly complex and evolving regulations. Any organization or retailer that accepts payment
Did you know your security solution can help with PCI compliance too? High-profile data losses have led to increasingly complex and evolving regulations. Any organization or retailer that accepts payment
PureMessage for Microsoft Exchange startup guide. Product version: 3.1
 PureMessage for Microsoft Exchange startup guide Product version: 3.1 Document date: June 2015 Contents 1 About this guide...4 2 Planning your PureMessage deployment...5 2.1 Deploying PureMessage to Exchange
PureMessage for Microsoft Exchange startup guide Product version: 3.1 Document date: June 2015 Contents 1 About this guide...4 2 Planning your PureMessage deployment...5 2.1 Deploying PureMessage to Exchange
The Leading Email Security Suites
 The Leading Email Security Suites What is SpamSniper? The Leading Email Security Suites for Your Secure Messaging SpamSniper is the leading email security solution which locates in front of mail server
The Leading Email Security Suites What is SpamSniper? The Leading Email Security Suites for Your Secure Messaging SpamSniper is the leading email security solution which locates in front of mail server
INLINE INGUARD E-MAIL GUARDIAN
 INLINE INGUARD E-MAIL GUARDIAN Activation Guide December 8, 2008 600 Lakeshore Parkway, AL 35209 888.3InLine [email protected] 1 InLine InGuard E-Mail Guardian Activation Guide The InLine InGuard E-Mail
INLINE INGUARD E-MAIL GUARDIAN Activation Guide December 8, 2008 600 Lakeshore Parkway, AL 35209 888.3InLine [email protected] 1 InLine InGuard E-Mail Guardian Activation Guide The InLine InGuard E-Mail
70-662: Deploying Microsoft Exchange Server 2010
 70-662: Deploying Microsoft Exchange Server 2010 Course Introduction Course Introduction Chapter 01 - Active Directory and Supporting Infrastructure Active Directory and Supporting Infrastructure Network
70-662: Deploying Microsoft Exchange Server 2010 Course Introduction Course Introduction Chapter 01 - Active Directory and Supporting Infrastructure Active Directory and Supporting Infrastructure Network
Deployment Guide. For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php
 Deployment Guide For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php ExchangeDefender Introduction The purpose of this guide is to familiarize you with
Deployment Guide For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php ExchangeDefender Introduction The purpose of this guide is to familiarize you with
GFI Product Manual. Administration and Configuration Manual
 GFI Product Manual Administration and Configuration Manual http://www.gfi.com [email protected] The information and content in this document is provided for informational purposes only and is provided "as is"
GFI Product Manual Administration and Configuration Manual http://www.gfi.com [email protected] The information and content in this document is provided for informational purposes only and is provided "as is"
How To Set Up A Barcuda Email Server On A Pc Or Mac Or Mac (For Free) With A Webmail Server (For A Limited Time) With An Ipad Or Ipad (For An Ipa) With The Ip
 Version Barracuda Spam Firewall Administrator s Guide Barracuda Networks Inc. 385 Ravendale Drive Mountain View, CA 94043 http://www.barracudanetworks.com 1 Copyright Notice Copyright 2005, Barracuda Networks
Version Barracuda Spam Firewall Administrator s Guide Barracuda Networks Inc. 385 Ravendale Drive Mountain View, CA 94043 http://www.barracudanetworks.com 1 Copyright Notice Copyright 2005, Barracuda Networks
Proactively protecting your messaging infrastructure with the IBM Lotus Protector for Mail Security solution.
 Security capabilities To support your business objectives Proactively protecting your messaging infrastructure with the IBM Lotus Protector for Mail Security solution. Preemptive protection and spam control
Security capabilities To support your business objectives Proactively protecting your messaging infrastructure with the IBM Lotus Protector for Mail Security solution. Preemptive protection and spam control
Symantec Messaging Gateway 10.0 Installation Guide. powered by Brightmail
 Symantec Messaging Gateway 10.0 Installation Guide powered by Brightmail The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of
Symantec Messaging Gateway 10.0 Installation Guide powered by Brightmail The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of
Comprehensive Anti-Spam Service
 Comprehensive Anti-Spam Service Chapter 1: Document Scope This document describes how to implement and manage the Comprehensive Anti-Spam Service. This document contains the following sections: Comprehensive
Comprehensive Anti-Spam Service Chapter 1: Document Scope This document describes how to implement and manage the Comprehensive Anti-Spam Service. This document contains the following sections: Comprehensive
Data Sheet: Backup & Recovery Symantec Backup Exec System Recovery Windows Small Business Server Edition
 Symantec Backup Exec System Recovery Windows Small Business Server Edition Overview Regardless of the size of your company, data drives your business. Your ability to keep that data available can often
Symantec Backup Exec System Recovery Windows Small Business Server Edition Overview Regardless of the size of your company, data drives your business. Your ability to keep that data available can often
ARCHITECTURAL OVERVIEW E-mail Availability Service (EAS) with ActiveMailbox
 ARCHITECTURAL OVERVIEW E-mail Availability Service () with ActiveMailbox E-mail Availability Service () with ActiveMailbox For Microsoft Exchange -Centric Environments The Market Need for Through direct
ARCHITECTURAL OVERVIEW E-mail Availability Service () with ActiveMailbox E-mail Availability Service () with ActiveMailbox For Microsoft Exchange -Centric Environments The Market Need for Through direct
E-mail Filter. SurfControl E-mail Filter 5.0 for SMTP Getting Started Guide. www.surfcontrol.com. The World s #1 Web & E-mail Filtering Company
 E-mail Filter SurfControl E-mail Filter 5.0 for SMTP Getting Started Guide www.surfcontrol.com The World s #1 Web & E-mail Filtering Company CONTENTS CONTENTS INTRODUCTION About This Document...2 Product
E-mail Filter SurfControl E-mail Filter 5.0 for SMTP Getting Started Guide www.surfcontrol.com The World s #1 Web & E-mail Filtering Company CONTENTS CONTENTS INTRODUCTION About This Document...2 Product
WHITE PAPER. Safeguarding your Email Infrastructure INSIDE MODUS TECHNOLOGY
 WHITE PAPER Safeguarding your Email Infrastructure INSIDE MODUS TECHNOLOGY Table of Contents Executive Summary............................................................. 3 Vircom s modus Technology....................................................
WHITE PAPER Safeguarding your Email Infrastructure INSIDE MODUS TECHNOLOGY Table of Contents Executive Summary............................................................. 3 Vircom s modus Technology....................................................
THIS SERVICE LEVEL AGREEMENT DEFINES THE SERVICE LEVELS PROVIDED TO YOU BY THE COMPANY ( Exchange My Mail ).
 THIS SERVICE LEVEL AGREEMENT DEFINES THE SERVICE LEVELS PROVIDED TO YOU BY THE COMPANY ( Exchange My Mail ). I. Service Definition. Exchange My Mail will provide Hosted Exchange and other Application Services
THIS SERVICE LEVEL AGREEMENT DEFINES THE SERVICE LEVELS PROVIDED TO YOU BY THE COMPANY ( Exchange My Mail ). I. Service Definition. Exchange My Mail will provide Hosted Exchange and other Application Services
Mimecast Email Security
 DATA SHEET Mimecast Email Security A fully integrated email security, continuity and archiving cloud based solution that delivers total end-to-end control of your email, mitigating email risks and reducing
DATA SHEET Mimecast Email Security A fully integrated email security, continuity and archiving cloud based solution that delivers total end-to-end control of your email, mitigating email risks and reducing
Email Security Solutions
 TECHNOLOGY REPORT Email Security Solutions 1 TECHNOLOGY REPORT SUPPLEMENT EMAIL SECURITY TECHNOLOGY REPORT IF YOUR EMAIL IS SO CRITICAL, CAN YOU BE SURE IT S REALLY REALLY PRIVATE? FIND THE FULL RESULTS
TECHNOLOGY REPORT Email Security Solutions 1 TECHNOLOGY REPORT SUPPLEMENT EMAIL SECURITY TECHNOLOGY REPORT IF YOUR EMAIL IS SO CRITICAL, CAN YOU BE SURE IT S REALLY REALLY PRIVATE? FIND THE FULL RESULTS
IronPort X1000 Email Security System
 I r o n P o r t A p p l i a n c e s T H E U LT I M AT E E M A I L S E C U R I T Y S Y S T E M F O R T H E W O R L D S M O S T D E M A N D I N G N E T W O R K S. IronPort X1000 Email Security System O v
I r o n P o r t A p p l i a n c e s T H E U LT I M AT E E M A I L S E C U R I T Y S Y S T E M F O R T H E W O R L D S M O S T D E M A N D I N G N E T W O R K S. IronPort X1000 Email Security System O v
