Locking a Door Unlocked by a Schedule using a Card
|
|
|
- Ronald Herbert Lyons
- 9 years ago
- Views:
Transcription
1 Objective Locking a Door Unlocked by a Schedule using a Card This document shows you how to configure EntraPass to unlock a door using a schedule (with or without the First Man In feature) and re-lock before the schedule ends by presenting a card to the reader and pressing a button. An external alarm system will be used to illustrate our purpose. Requirements Running EntraPass software with defined access levels Door connected to a KT-300 controller An external button installed next to the reader (or keypad button such as * or # with the P225KP or P325KP) 2 pieces of wire (Jumpers) Steps 1. Connect the hardware as shown below 2. Connect the controller, then configure the controller using the Express Setup utility 3. Define the desired schedules (Definition > Schedules 4. Define the required relays (Devices > Relays) 5. Define the required inputs (Devices > Inputs). 6. Define the door and external alarm system options (Devices >Doors). Telephone: 1 (450) Toll free: Fax: 1 (450) Internet: page 1 / 8
2 Step by Step Instructions 1. Connect the external push button and the 2 jumpers as illustrated by the following diagram. 2. Access EntraPass to configure the KT-300 controller and define door contacts and REX (refer to the EntraPass reference manual for details on how to configure controllers using Express setup). Telephone: 1 (450) Toll free: Fax: 1 (450) Internet: page 2 / 8
3 3. Define the schedule during which the door will be unlocked: Definition > Schedule. 4. Define the two (2) onboard output relays: Devices > Relays. Identify the first one as Request to arm (lock) and the second as Request to disarm (unlock). Leave the default values. Telephone: 1 (450) Toll free: Fax: 1 (450) Internet: page 3 / 8
4 5. Define the three (3) required inputs: Devices > Input. Assign an Always valid schedule to all the defined inputs. 5.1 Select input # 5 and label it Request to arm input. Leave the default value unchanged and save. 5.2 Select input # 6 and identify it as an Arming status input, set it for normally Opened and save. Telephone: 1 (450) Toll free: Fax: 1 (450) Internet: page 4 / 8
5 5.3 Select input # 7 and label it Shunt request to arm. Leave it to normally Closed Select the Relay and Input tab and select relay 1 for the Activate relay field, then assign Input 6 as the Shunt input and save. Telephone: 1 (450) Toll free: Fax: 1 (450) Internet: page 5 / 8
6 6 Go to Devices > Door to bring up the door definition window. Select the door you want to define for this application. 6.1 Assign the Unlock schedule for this door. This is the schedule defined earlier in Step 3. Select the Options and alarm system tab. 6.2 Check the Unlock door by schedule after first access granted option. Telephone: 1 (450) Toll free: Fax: 1 (450) Internet: page 6 / 8
7 6.3 Click the External alarm system options button. 6.4 Assign Input 5 as the Arming request input. 6.5 Select the Always valid schedule as the Enable Arming request schedule. 6.6 Under the Arming access level field, select the access level or the group of access levels for the cardholders who will have permission to relock the door after the door was unlocked by a schedule. 6.7 Check the Wait for access granted to arm checkbox. 6.8 Check the Re-Lock door on request to arm checkbox. 6.9 Select Input 6 as the External alarm system panel status input Select the Input tab Check the Shunted on exit and Shunted on disarm checkbox for input 7. Telephone: 1 (450) Toll free: Fax: 1 (450) Internet: page 7 / 8
8 6.12 Select the Postpone arming tab Assign the access level or group of access level of the cardholders who will be allowed to unlock the door by schedule (first people in) under the Postpone or disarm access level field Select the Relay tab Assign relay # 1 as the Arming alarm panel Exit delay Assign relay # 2 as the Disarming alarm panel Entry delay Click OK and save the door definition. Telephone: 1 (450) Toll free: Fax: 1 (450) Internet: page 8 / 8
Access Control & Burglar Alarm Integration with KT-300
 Purpose Access Control & Burglar Alarm Integration with KT-300 The purpose of this document is to provide Installers and System Administrators instructions on integrating access control to their burglar
Purpose Access Control & Burglar Alarm Integration with KT-300 The purpose of this document is to provide Installers and System Administrators instructions on integrating access control to their burglar
MTP: Continuous User Authentication on Android Using Face Recognition
 MTP: Continuous User Authentication on Android Using Face Recognition Testing of FaceApp Application This experiment is being conducted to find out the accuracy rate of face recognition algorithm used
MTP: Continuous User Authentication on Android Using Face Recognition Testing of FaceApp Application This experiment is being conducted to find out the accuracy rate of face recognition algorithm used
AS-525. AxTrax Access Control Management Software. Software Manual
 AS-525 AxTrax Access Control Management Software Software Manual August 2010 Table of Contents Table of Contents 1. Introduction... 5 1.1 System Features... 5 1.1.1. Access Control... 6 1.1.2. Access
AS-525 AxTrax Access Control Management Software Software Manual August 2010 Table of Contents Table of Contents 1. Introduction... 5 1.1 System Features... 5 1.1.1. Access Control... 6 1.1.2. Access
5.6.2 Optional Lab: Restore Points in Windows Vista
 5.6.2 Optional Lab: Restore Points in Windows Vista Introduction Print and complete this lab. In this lab, you will create a restore point and return your computer back to that point in time. Recommended
5.6.2 Optional Lab: Restore Points in Windows Vista Introduction Print and complete this lab. In this lab, you will create a restore point and return your computer back to that point in time. Recommended
NetworX TM NX-8E Alarm Panel. Application Note. NetworX NX-8E. 1.0 The NetworX NX-8E Alarm Panel
 The PXL-510 tiger controller can be connected with the NetworX 1 NX-8E Alarm panel to allow arming and disarming of the alarm system by using the alarm panel keypad, using a wireless Wiegand device, or
The PXL-510 tiger controller can be connected with the NetworX 1 NX-8E Alarm panel to allow arming and disarming of the alarm system by using the alarm panel keypad, using a wireless Wiegand device, or
Configuring Network Load Balancing with Cerberus FTP Server
 Configuring Network Load Balancing with Cerberus FTP Server May 2016 Version 1.0 1 Introduction Purpose This guide will discuss how to install and configure Network Load Balancing on Windows Server 2012
Configuring Network Load Balancing with Cerberus FTP Server May 2016 Version 1.0 1 Introduction Purpose This guide will discuss how to install and configure Network Load Balancing on Windows Server 2012
Using triggers and actions
 Using triggers and actions Important For Triggers and Actions to function correctly, the server PC must be running at all times. Triggers and Actions is a powerful feature. It can be used to report on
Using triggers and actions Important For Triggers and Actions to function correctly, the server PC must be running at all times. Triggers and Actions is a powerful feature. It can be used to report on
Access Control Interface Module D9210C. Program Entry Guide
 Access Control Interface Module D9210C en Program Entry Guide Access Control Interface Module Table of Contents en 3 Table of Contents 1 Trademarks 4 2 Door Profile 5 3 Strike Profile 9 4 Event Profile
Access Control Interface Module D9210C en Program Entry Guide Access Control Interface Module Table of Contents en 3 Table of Contents 1 Trademarks 4 2 Door Profile 5 3 Strike Profile 9 4 Event Profile
Configuring Napco Integration
 Configuring Napco Integration The following instructions will guide you through the CardAccess Napco Integration with TCP/IP communication setup. Note: It is assumed that Napco Panel (including TCP/IP
Configuring Napco Integration The following instructions will guide you through the CardAccess Napco Integration with TCP/IP communication setup. Note: It is assumed that Napco Panel (including TCP/IP
Connection and Configuration of Baudisch SIP unit with Display and RFID Reader Module
 Connection and Configuration of Baudisch SIP unit with Display and RFID Reader Module This document explains connection and configuration of the Baudisch sip door module with the display and RFID reader
Connection and Configuration of Baudisch SIP unit with Display and RFID Reader Module This document explains connection and configuration of the Baudisch sip door module with the display and RFID reader
Intelli-M Access Quick Start Guide
 Intelli-M Access Quick Start Guide Before You Begin The Intelli-M Access software can be used in conjunction with the eidc. Use Intelli-M Access to manage, view, and report activity through an eidc controlled
Intelli-M Access Quick Start Guide Before You Begin The Intelli-M Access software can be used in conjunction with the eidc. Use Intelli-M Access to manage, view, and report activity through an eidc controlled
Access Control in Surveillance Station 7.0
 Access Control in Surveillance Station 7.0 With Axis Network Door Controller A1001 Synology Inc. Synology_ACISS_20150305 Table of Contents Chapter 1: Introduction... 3 1.1 What Is Access Control?... 3
Access Control in Surveillance Station 7.0 With Axis Network Door Controller A1001 Synology Inc. Synology_ACISS_20150305 Table of Contents Chapter 1: Introduction... 3 1.1 What Is Access Control?... 3
OnGuard Online User Guide
 OnGuard Online User Guide T81165/Rev ER-7991-40 Jan 2005 Contents 1 Introduction Related documents 1 1 Navigation of the software 1 2 How to use this guide 1 4 2 Managing Access Holidays and Timezones
OnGuard Online User Guide T81165/Rev ER-7991-40 Jan 2005 Contents 1 Introduction Related documents 1 1 Navigation of the software 1 2 How to use this guide 1 4 2 Managing Access Holidays and Timezones
Access Control Unit User s Guide
 NetAXS Access Control Unit User s Guide The configurations described in this document have not been reviewed by Underwriters Laboratories Inc. June 2007 2007 Honeywell. All rights reserved. 800-00233,
NetAXS Access Control Unit User s Guide The configurations described in this document have not been reviewed by Underwriters Laboratories Inc. June 2007 2007 Honeywell. All rights reserved. 800-00233,
Allegion PIM-400/485 and AD-400 Installation Application Note. 1.0 Hardware Requirements. 2.0 Software/Licensing Requirements
 This document explains how to setup and use the Allegion AD-400 wireless locks with the NXT Mercury Powered controllers and the Doors.NET software. These locks have extensive functionality and operating
This document explains how to setup and use the Allegion AD-400 wireless locks with the NXT Mercury Powered controllers and the Doors.NET software. These locks have extensive functionality and operating
Vehicle Security System VSS3 - Alarm system remote. System Setting Guide - English
 Vehicle Security System VSS3 - Alarm system remote System Setting Guide - English Dear Customer, In this guide you will find the information and operations necessary in order to activate and deactivate
Vehicle Security System VSS3 - Alarm system remote System Setting Guide - English Dear Customer, In this guide you will find the information and operations necessary in order to activate and deactivate
YOUR INTERACTIVE SECURITY
 YOUR INTERACTIVE SECURITY MyFrontpoint.com: Setup & Features SECURITY THE WAY YOU WANT IT After your activation call, you ll receive your MyFrontpoint.com login and password via email. Log on at www.myfrontpoint.com.
YOUR INTERACTIVE SECURITY MyFrontpoint.com: Setup & Features SECURITY THE WAY YOU WANT IT After your activation call, you ll receive your MyFrontpoint.com login and password via email. Log on at www.myfrontpoint.com.
Quick Installation Guide LCD GSM ALARM SYSTEM LH http://www.usmartbuy.com
 A. Manipulation Specification Quick Installation Guide 1. Arming Arming means all-around guarded when there is no person at home. All detectors are working. Once something triggers any of the detectors,
A. Manipulation Specification Quick Installation Guide 1. Arming Arming means all-around guarded when there is no person at home. All detectors are working. Once something triggers any of the detectors,
GSM Autodialer Professional GJD700 Speech & Text Autodialer
 Text Edit message GSM Autodialer Professional GJD700 Speech & Text Autodialer Introduction The GSM Autodialer Professional works in conjunction with standard alarm systems and makes use of your preferred
Text Edit message GSM Autodialer Professional GJD700 Speech & Text Autodialer Introduction The GSM Autodialer Professional works in conjunction with standard alarm systems and makes use of your preferred
HAI Access Control. The HAI Access Control Card Reader can be used for:
 HAI Access Control HAI Access Control allows you to access doors by opening an electric or magnetic lock, arm and disarm the security system, and achieve many home automation functions such as controlling
HAI Access Control HAI Access Control allows you to access doors by opening an electric or magnetic lock, arm and disarm the security system, and achieve many home automation functions such as controlling
How to Configure Alarm Notification
 Introduction How to Configure Alarm Notification Alarm notification function makes ivms-4500 a professional and powerful private security guard for 7X24 surveillance. Once there are events occurring, notification
Introduction How to Configure Alarm Notification Alarm notification function makes ivms-4500 a professional and powerful private security guard for 7X24 surveillance. Once there are events occurring, notification
Config software for D2 systems USER S MANUAL
 DT-CONFIG SOFTWARE Config software for D2 systems USER S MANUAL CONTENTS 1. Introductions ------------------------------------------------------------------- 3 2. System Requirement and Connection ----------------------------------------
DT-CONFIG SOFTWARE Config software for D2 systems USER S MANUAL CONTENTS 1. Introductions ------------------------------------------------------------------- 3 2. System Requirement and Connection ----------------------------------------
AC-115 Compact Networked Single Door Controller. Installation and User Manual
 AC-115 Compact Networked Single Controller Installation and User Manual December 2007 Table of Contents Table of Contents 1. Introduction...5 1.1 Key Features... 6 1.2 Technical Specifications... 7 2.
AC-115 Compact Networked Single Controller Installation and User Manual December 2007 Table of Contents Table of Contents 1. Introduction...5 1.1 Key Features... 6 1.2 Technical Specifications... 7 2.
Versions Addressed: Microsoft Office Outlook 2010/2013. Document Updated: 2014. Copyright 2014 Smarsh, Inc. All right reserved
 Versions Addressed: Microsoft Office Outlook 2010/2013 Document Updated: 2014 Copyright 2014 Smarsh, Inc. All right reserved Table of Contents Getting Started 3 Add Your New Account 3 Account Setup 5 Basic
Versions Addressed: Microsoft Office Outlook 2010/2013 Document Updated: 2014 Copyright 2014 Smarsh, Inc. All right reserved Table of Contents Getting Started 3 Add Your New Account 3 Account Setup 5 Basic
Setting Up the EntraPass Mirror Database and Redundant Server
 Setting Up the EntraPass Mirror Database and Redundant Server The purpose of this document is to help EntraPass system installers and administrators define and install the Mirror Database and Redundant
Setting Up the EntraPass Mirror Database and Redundant Server The purpose of this document is to help EntraPass system installers and administrators define and install the Mirror Database and Redundant
Outlook Profile Setup Guide Exchange 2010 Quick Start and Detailed Instructions
 HOSTING Administrator Control Panel / Quick Reference Guide Page 1 of 9 Outlook Profile Setup Guide Exchange 2010 Quick Start and Detailed Instructions Exchange 2010 Outlook Profile Setup Page 2 of 9 Exchange
HOSTING Administrator Control Panel / Quick Reference Guide Page 1 of 9 Outlook Profile Setup Guide Exchange 2010 Quick Start and Detailed Instructions Exchange 2010 Outlook Profile Setup Page 2 of 9 Exchange
Seamless and Secure Access (SSA) Manual Configuration Guide for Windows Mobile 6.1
 Seamless and Secure Access (SSA) Manual Configuration Guide for Windows Mobile 6.1 Page 1 1 Connect to Wireless@SG via SSA 1.1 Turn on Wi-Fi Before connecting to Wireless@SGx hotspot, Wi-Fi must be turned
Seamless and Secure Access (SSA) Manual Configuration Guide for Windows Mobile 6.1 Page 1 1 Connect to Wireless@SG via SSA 1.1 Turn on Wi-Fi Before connecting to Wireless@SGx hotspot, Wi-Fi must be turned
16.4.3 Lab: Data Backup and Recovery in Windows XP
 16.4.3 Lab: Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment The
16.4.3 Lab: Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment The
2012 November. AxTraxNG Access Control Management Software Software Manual (Version 21.x)
 2012 November AxTraxNG Access Control Management Software Software Manual (Version 21.x) Copyright 2012 by Rosslare. All rights reserved. This manual and the information contained herein are proprietary
2012 November AxTraxNG Access Control Management Software Software Manual (Version 21.x) Copyright 2012 by Rosslare. All rights reserved. This manual and the information contained herein are proprietary
Rational Quality Manager. Quick Start Tutorial
 Rational Quality Manager Quick Start Tutorial 1 Contents 1. Introduction... 2 2. Terminology... 3 3. Project Area Preparation... 4 3.1 Adding Users and specifying Roles... 4 3.2 Managing Tool Associations...
Rational Quality Manager Quick Start Tutorial 1 Contents 1. Introduction... 2 2. Terminology... 3 3. Project Area Preparation... 4 3.1 Adding Users and specifying Roles... 4 3.2 Managing Tool Associations...
INSTALLATION MANUAL XM3 Reader
 INSTALLATION MANUAL XM3 Reader Conditions Transactions, deliveries et cetera will be according to the general terms of delivery as deposited at the Chamber of Commerce at Meppel, The Netherlands. Registration
INSTALLATION MANUAL XM3 Reader Conditions Transactions, deliveries et cetera will be according to the general terms of delivery as deposited at the Chamber of Commerce at Meppel, The Netherlands. Registration
Outlook 2010 Setup Guide (POP3)
 Versions Addressed: Microsoft Office Outlook 2010 Document Updated: 8/31/2012 Copyright 2012 Smarsh, Inc. All rights Purpose: This document will assist the end user in configuring Outlook 2010 to access
Versions Addressed: Microsoft Office Outlook 2010 Document Updated: 8/31/2012 Copyright 2012 Smarsh, Inc. All rights Purpose: This document will assist the end user in configuring Outlook 2010 to access
Sensi TM. Wi-Fi Programmable Thermostat MANUAL OPERATION. Version: March 2016 2016 Emerson Electric Co. All rights reserved.
 Sensi TM Wi-Fi Programmable Thermostat MANUAL OPERATION Version: March 2016 2016 Emerson Electric Co. All rights reserved. Contents MANUAL OPERATION GUIDE Buttons and Icons 3 Basic Functionality 4 Manual
Sensi TM Wi-Fi Programmable Thermostat MANUAL OPERATION Version: March 2016 2016 Emerson Electric Co. All rights reserved. Contents MANUAL OPERATION GUIDE Buttons and Icons 3 Basic Functionality 4 Manual
Yale Software Library http://www.yale.edu/software/
 e/ Yale Software Library http://www.yale.edu/software/ For assistance contact the ITS Help Desk 785-3200, 432-9000, [email protected] Windows XP Firewall Windows XP SP2 includes the new Windows Firewall,
e/ Yale Software Library http://www.yale.edu/software/ For assistance contact the ITS Help Desk 785-3200, 432-9000, [email protected] Windows XP Firewall Windows XP SP2 includes the new Windows Firewall,
Allegion AD-300 Installation Application Note. 1.0 Hardware Requirements. 2.0 Software/Licensing Requirements
 Allegion Schlage AD-300 networked, hardwired locks can be integrated seamlessly with the Doors.NET software when used with the NXT-MSC (Mercury-Powered controllers). You can connect and communicate with
Allegion Schlage AD-300 networked, hardwired locks can be integrated seamlessly with the Doors.NET software when used with the NXT-MSC (Mercury-Powered controllers). You can connect and communicate with
7. Lenel Job Aid: Running Reports
 1. There will be four reports identified here, you will have access to many more reports, but these should help you in your day to day work. Access Denial Events, By Reader: Access Denied Events, grouped
1. There will be four reports identified here, you will have access to many more reports, but these should help you in your day to day work. Access Denial Events, By Reader: Access Denied Events, grouped
How to Configure Alarm Notification
 Introduction How to Configure Alarm Notification Alarm notification function makes ivms-4500 a professional and powerful private security guard for 7X24 surveillance. Once there are events occurring, notification
Introduction How to Configure Alarm Notification Alarm notification function makes ivms-4500 a professional and powerful private security guard for 7X24 surveillance. Once there are events occurring, notification
User Guide for TASKE Desktop
 User Guide for TASKE Desktop For Avaya Aura Communication Manager with Aura Application Enablement Services Version: 8.9 Date: 2013-03 This document is provided to you for informational purposes only.
User Guide for TASKE Desktop For Avaya Aura Communication Manager with Aura Application Enablement Services Version: 8.9 Date: 2013-03 This document is provided to you for informational purposes only.
INF-USB2 and SI-USB Quick Start Guide
 INF-USB2 and SI-USB Quick Start Guide Please follow these instructions carefully. DO NOT connect the INF-USB2 or SI-USB module to your computer before running the setup program. After running Setup and
INF-USB2 and SI-USB Quick Start Guide Please follow these instructions carefully. DO NOT connect the INF-USB2 or SI-USB module to your computer before running the setup program. After running Setup and
10.3.1.6 Lab - Data Backup and Recovery in Windows XP
 5.0 10.3.1.6 Lab - Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment
5.0 10.3.1.6 Lab - Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment
Using Bluetooth-Enabled PosiTector 6000 with Statistical Process Control Software
 Using Bluetooth-Enabled PosiTector 6000 with Statistical Process Control Software SPC programs are available from third party vendors that enhance the measurement capabilities of the PosiTector 6000. With
Using Bluetooth-Enabled PosiTector 6000 with Statistical Process Control Software SPC programs are available from third party vendors that enhance the measurement capabilities of the PosiTector 6000. With
SECURITY SYSTEM MANAGEMENT SOFTWARE FOR WINDOWS. Quick Start Instructions
 TM SECURITY SYSTEM MANAGEMENT SOFTWARE FOR WINDOWS Quick Start Instructions Introduction WinLoad for Windows was developed to simplify and speed up the task of programming Paradox control panels. Remote
TM SECURITY SYSTEM MANAGEMENT SOFTWARE FOR WINDOWS Quick Start Instructions Introduction WinLoad for Windows was developed to simplify and speed up the task of programming Paradox control panels. Remote
800-02577-TC 3/10 Rev. A
 800-02577-TC 3/10 Rev. A Total Connect Online Help Guide TRADEMARKS Honeywell is a registered trademark of Honeywell International Inc. Windows and Windows Vista are trademarks, or registered trademarks
800-02577-TC 3/10 Rev. A Total Connect Online Help Guide TRADEMARKS Honeywell is a registered trademark of Honeywell International Inc. Windows and Windows Vista are trademarks, or registered trademarks
NT500 Offline Getting Started Guide
 NT500 Offline Getting Started Guide Copyright 2007 Stanley Security Solutions, Inc. and Stanley Logistics, Inc. All rights reserved. Printed in the United States of America. Information in this document
NT500 Offline Getting Started Guide Copyright 2007 Stanley Security Solutions, Inc. and Stanley Logistics, Inc. All rights reserved. Printed in the United States of America. Information in this document
FALCON WORLD CLASS SECURITY. Advanced Alarm System for Vehicles with CAN-Bus. Installer Manual NATIONWIDE INSTALLATION SERVICE 0800 622 474
 FALCON WORLD CLASS SECURITY FALCON PREDATOR CAN-BUS ALARM Advanced Alarm System for Vehicles with CAN-Bus Installer Manual NATIONWIDE INSTALLATION SERVICE 0800 622 474 HELPLINE: 0906 700 10 20 (All calls
FALCON WORLD CLASS SECURITY FALCON PREDATOR CAN-BUS ALARM Advanced Alarm System for Vehicles with CAN-Bus Installer Manual NATIONWIDE INSTALLATION SERVICE 0800 622 474 HELPLINE: 0906 700 10 20 (All calls
Windows XP Manual Installation
 Windows XP Manual Installation Installation of the drivers for your video card can be fairly easy if the following steps are followed carefully. There are a few things to keep in mind before proceeding
Windows XP Manual Installation Installation of the drivers for your video card can be fairly easy if the following steps are followed carefully. There are a few things to keep in mind before proceeding
How to Set Up Outlook 2007 and Outlook 2010 for Hosted Microsoft Exchange if the Program is Already Installed
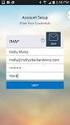 How to Set Up Outlook 2007 and Outlook 2010 for Hosted Microsoft Exchange if the Program is Already Installed 1. If you received your copy of Outlook from Cbeyond (via a CD or by downloading it from CbeyondOnline)
How to Set Up Outlook 2007 and Outlook 2010 for Hosted Microsoft Exchange if the Program is Already Installed 1. If you received your copy of Outlook from Cbeyond (via a CD or by downloading it from CbeyondOnline)
B.A.S.I.S. Offline Setup Guide
 B.A.S.I.S. Offline Setup Guide Copyright 2004 Stanley Security Solutions, Inc. and Stanley Logistics, Inc. All rights reserved. Printed in the United States of America. Information in this document is
B.A.S.I.S. Offline Setup Guide Copyright 2004 Stanley Security Solutions, Inc. and Stanley Logistics, Inc. All rights reserved. Printed in the United States of America. Information in this document is
High Performance Access Control and Integrated Security Systems
 High Performance Access Control and Integrated Security Systems High Performance Access Control and Integrated Security Systems EntraPass Corporate Edition is a powerful multi-user access control system
High Performance Access Control and Integrated Security Systems High Performance Access Control and Integrated Security Systems EntraPass Corporate Edition is a powerful multi-user access control system
The Access Engine. Building Integration System - The Access Engine. Security Systems
 The Access Engine 1 What is BIS Access Engine? It is one of the central software modules of the Building Integration System It s a fully integrated access control solution with corresponding access hardware
The Access Engine 1 What is BIS Access Engine? It is one of the central software modules of the Building Integration System It s a fully integrated access control solution with corresponding access hardware
MONAHRQ Installation Permissions Guide. Version 2.0.4
 MONAHRQ Installation Permissions Guide Version 2.0.4 March 19, 2012 Check That You Have all Necessary Permissions It is important to make sure you have full permissions to run MONAHRQ. The following instructions
MONAHRQ Installation Permissions Guide Version 2.0.4 March 19, 2012 Check That You Have all Necessary Permissions It is important to make sure you have full permissions to run MONAHRQ. The following instructions
GSM Voice Auto Dialer& SMS sender JC-999. User Manual
 1. Description 1.1 Main features GSM Voice Auto Dialer& SMS sender JC-999 User Manual (1) Large LCD display,integrated keypad, human-friendly programming; (2) Support 12 alarm receiving numbers; (3) Triggering
1. Description 1.1 Main features GSM Voice Auto Dialer& SMS sender JC-999 User Manual (1) Large LCD display,integrated keypad, human-friendly programming; (2) Support 12 alarm receiving numbers; (3) Triggering
11.4.5 Optional Lab: Install, Configure, and Partition a Second Hard Drive in Windows Vista
 11.4.5 Optional Lab: Install, Configure, and Partition a Second Hard Drive in Windows Vista Introduction Print and complete this lab. In this lab, you will change the boot order, install a second hard
11.4.5 Optional Lab: Install, Configure, and Partition a Second Hard Drive in Windows Vista Introduction Print and complete this lab. In this lab, you will change the boot order, install a second hard
PAC1 Door Access Controller
 PAC1 Door Access Controller Series 2 IMPORTANT DIFFERENCES FROM SERIES 1 1. A PACDL data logger revision 4.0 or higher attached to the DLOG terminal is able to program all features (i.e. times, relay type,
PAC1 Door Access Controller Series 2 IMPORTANT DIFFERENCES FROM SERIES 1 1. A PACDL data logger revision 4.0 or higher attached to the DLOG terminal is able to program all features (i.e. times, relay type,
Apps for Android. Apps for iphone & ipad INS584-3
 Apps for iphone & ipad INS584-3 Apps for Android Android is a trademark of Google Inc. iphone is a trademark of Apple Inc., registered in the U.S. and other countries. ipad is a trademark of Apple Inc.,
Apps for iphone & ipad INS584-3 Apps for Android Android is a trademark of Google Inc. iphone is a trademark of Apple Inc., registered in the U.S. and other countries. ipad is a trademark of Apple Inc.,
D8X / D16X IPHONE INTERFACE
 Ness icomms App D8X / D16X IPHONE INTERFACE SETUP GUIDE Revision 1.0.0 Table of Contents Copyright Notice... 3 1. Important Information... 4 2. Wiring Diagram... 5 2.1 RS232 Wiring Setup... 5 2.2 IP232
Ness icomms App D8X / D16X IPHONE INTERFACE SETUP GUIDE Revision 1.0.0 Table of Contents Copyright Notice... 3 1. Important Information... 4 2. Wiring Diagram... 5 2.1 RS232 Wiring Setup... 5 2.2 IP232
If you are unable to set up your Linksys Router by using one of the above options, use the steps below to manually configure your router.
 This article describes how to manually configure a Linksys Router for broadband DSL that uses PPPoE (Point-to-Point Protocol over Ethernet) for authentication. For automatic configuration options, please
This article describes how to manually configure a Linksys Router for broadband DSL that uses PPPoE (Point-to-Point Protocol over Ethernet) for authentication. For automatic configuration options, please
Quick Start Guide. GV-AS Controller
 Quick Start Guide GV-AS Controller Thank you for purchasing GV-AS Controller (GV-AS100 / AS110 / AS120 / AS210 / AS400 / AS810). This guide is designed to assist the new user in getting immediate results
Quick Start Guide GV-AS Controller Thank you for purchasing GV-AS Controller (GV-AS100 / AS110 / AS120 / AS210 / AS400 / AS810). This guide is designed to assist the new user in getting immediate results
BioWin Network Installation
 BioWin Network Installation Introduction This document outlines the procedures for installing the network version of BioWin. There are three parts to the network version installation: 1. The installation
BioWin Network Installation Introduction This document outlines the procedures for installing the network version of BioWin. There are three parts to the network version installation: 1. The installation
Installation Guide and Machine Setup
 Installation Guide and Machine Setup Page 1 Browser Configurations Installation Guide and Machine Setup The first requirement for using CURA is to ensure that your browser is set up accurately. 1. Once
Installation Guide and Machine Setup Page 1 Browser Configurations Installation Guide and Machine Setup The first requirement for using CURA is to ensure that your browser is set up accurately. 1. Once
DC-8706K Auto Dial Alarm System
 DC-8706K Auto Dial Alarm System User Guide Basic Contents: 1x the host unit; 1x wireless door (window) magnet; 1x wireless infrared detector; 2x remote control; 1x siren; 1x phone core; 1x AC to DC power
DC-8706K Auto Dial Alarm System User Guide Basic Contents: 1x the host unit; 1x wireless door (window) magnet; 1x wireless infrared detector; 2x remote control; 1x siren; 1x phone core; 1x AC to DC power
CipherLab 5100 Time Attendance Utility Manual
 CipherLab 5100 Time Attendance Utility Manual K:\Products\Product Technical\BI\BI-PC5100T\CipherLab5100TimeAttendnaceUtilityManual0707-process.doc Page 1 / 13 1 Login A popup form as follows will appear
CipherLab 5100 Time Attendance Utility Manual K:\Products\Product Technical\BI\BI-PC5100T\CipherLab5100TimeAttendnaceUtilityManual0707-process.doc Page 1 / 13 1 Login A popup form as follows will appear
e-ask electronic Access Security Keyless-entry
 e-ask electronic Access Security Keyless-entry e-fob Keyless-entry entry System Full-Function Function Installation Manual FCC ID: TV2EFOB1 (UM20 ~ 22793-02) Table of Contents Introduction... 1 e-fob Operation
e-ask electronic Access Security Keyless-entry e-fob Keyless-entry entry System Full-Function Function Installation Manual FCC ID: TV2EFOB1 (UM20 ~ 22793-02) Table of Contents Introduction... 1 e-fob Operation
Bosch Alarm Panel Interface Manual
 This document is a System Galaxy Product Interface manual. Information in this document is subject to change without notice. No part of this document may be reproduced, copied, adapted, or transmitted,
This document is a System Galaxy Product Interface manual. Information in this document is subject to change without notice. No part of this document may be reproduced, copied, adapted, or transmitted,
Doors in a Network Environment
 in a Network Environment 1.0 Purpose of this Document Doors is designed for use in stand-alone computer applications; no network functionality has been built into the program. However, with the prevalence
in a Network Environment 1.0 Purpose of this Document Doors is designed for use in stand-alone computer applications; no network functionality has been built into the program. However, with the prevalence
THRUST CURVE LOGGER V-4.200
 THRUST CURVE LOGGER V-4.200 There are several items that must be addressed prior to actual firing of the motor for data acquisition. These will be required in the Propellant Characterization process: Weigh
THRUST CURVE LOGGER V-4.200 There are several items that must be addressed prior to actual firing of the motor for data acquisition. These will be required in the Propellant Characterization process: Weigh
SCORPION. micron security products
 SCORPION 4120 6020 & 8020 USER INSTRUCTIONS Thank you for purchasing a Quality Micron Security Alarm Controller. Micron product is manufactured to exacting quality standards. We understand the importance
SCORPION 4120 6020 & 8020 USER INSTRUCTIONS Thank you for purchasing a Quality Micron Security Alarm Controller. Micron product is manufactured to exacting quality standards. We understand the importance
AVS A4 alarm Owner s manual
 AVS A4 alarm Owner s manual Thank you for choosing an AVS A4 car security system. It has been designed to provide a superior level of security for you and your vehicle. Please read this guide carefully
AVS A4 alarm Owner s manual Thank you for choosing an AVS A4 car security system. It has been designed to provide a superior level of security for you and your vehicle. Please read this guide carefully
1. Make sure that no client accounts are open. 2. Click on Setup, then click Modem. The Modem Setup window will appear.
 SECURITY SYSTEM MANAGEMENT SOFTWARE FOR WINDOWS WINLOAD MODEM SETUP The modem setup is a very important step in the connection process. If the modem setup is not properly completed communication between
SECURITY SYSTEM MANAGEMENT SOFTWARE FOR WINDOWS WINLOAD MODEM SETUP The modem setup is a very important step in the connection process. If the modem setup is not properly completed communication between
LiNC-Ez iam TM Programming Manual 33-10038-001 REV: H
 LiNC-Ez iam TM Programming Manual 33-10038-001 REV: H FOR iam FIRMWARE VERSION GREATER THAN 4.00.00 FOR IQX FIRMWARE VERSION GREATER THAN 2.00.00 FOR NRX FIRMWARE VERSION GREATER THAN 3.00.00 PCSC 3541
LiNC-Ez iam TM Programming Manual 33-10038-001 REV: H FOR iam FIRMWARE VERSION GREATER THAN 4.00.00 FOR IQX FIRMWARE VERSION GREATER THAN 2.00.00 FOR NRX FIRMWARE VERSION GREATER THAN 3.00.00 PCSC 3541
PRODUCTIVITY THROUGH INNOVATION 600 CONTROL DIRECT DRIVE TECHNICAL/OPERATION MANUAL
 Rev. D PRODUCTIVITY THROUGH INNOVATION 600 CONTROL DIRECT DRIVE TECHNICAL/OPERATION MANUAL 10 BORIGHT AVENUE, KENILWORTH NEW JERSEY 07033 TELEPHONE: 800-524-0273 FAX: 908-686-9317 TABLE OF CONTENTS Page
Rev. D PRODUCTIVITY THROUGH INNOVATION 600 CONTROL DIRECT DRIVE TECHNICAL/OPERATION MANUAL 10 BORIGHT AVENUE, KENILWORTH NEW JERSEY 07033 TELEPHONE: 800-524-0273 FAX: 908-686-9317 TABLE OF CONTENTS Page
Installation Instructions
 Installation Instructions For WiFi/LAN Video Intercom Manual Version 2 BFT Americas 6100 Broken Sound Parkway N.W. Suite 14, Boca Raton, FL 33487 www.bft-usa.com Toll Free: 877-995-8155 Office: 561-995-8155
Installation Instructions For WiFi/LAN Video Intercom Manual Version 2 BFT Americas 6100 Broken Sound Parkway N.W. Suite 14, Boca Raton, FL 33487 www.bft-usa.com Toll Free: 877-995-8155 Office: 561-995-8155
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7.
 Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
LP 2844 Thermal Printer
 Quick Installation Guide FedEx Ship Manager Software FedEx Ship Manager at fedex.com LP 2844 Thermal Printer Step 1: Confirm Printer Kit Contents Your printer kit contains: 1. Thermal Printer 4. Serial
Quick Installation Guide FedEx Ship Manager Software FedEx Ship Manager at fedex.com LP 2844 Thermal Printer Step 1: Confirm Printer Kit Contents Your printer kit contains: 1. Thermal Printer 4. Serial
APPLICATION NOTE. The DMP Software Family DMP COMPUTER SOFTWARE PROGRAMS
 APPLICATION NOTE Contents The DMP Software Family... 1 Stand-Alone Link Software... 1 Add-on Modules for Link Software... 1 System Link End-User Panel Management Software... 2 Simple Registration and Activation...
APPLICATION NOTE Contents The DMP Software Family... 1 Stand-Alone Link Software... 1 Add-on Modules for Link Software... 1 System Link End-User Panel Management Software... 2 Simple Registration and Activation...
Volume. EverAccess. User s Manual
 Volume 1 EverAccess User s Manual FLEX Series Access Control Management Software Flex1.0 EVERFOCUS ELECTRONICS CORPORATION Flex1.0 Instruction Guide 2004 Everfocus Electronics Corp 1801 Highland Ave Duarte
Volume 1 EverAccess User s Manual FLEX Series Access Control Management Software Flex1.0 EVERFOCUS ELECTRONICS CORPORATION Flex1.0 Instruction Guide 2004 Everfocus Electronics Corp 1801 Highland Ave Duarte
EMBEDDED ACCESS CONTROL Hardware Installation Guide
 EMBEDDED ACCESS CONTROL Hardware Installation Guide Lenel goentry Hardware Installation Guide, product version 1.00. This guide is item number DOC- ENHW-ENU, revision 1.003, April 2009 Copyright 2009 Lenel
EMBEDDED ACCESS CONTROL Hardware Installation Guide Lenel goentry Hardware Installation Guide, product version 1.00. This guide is item number DOC- ENHW-ENU, revision 1.003, April 2009 Copyright 2009 Lenel
2 4PI175 issue 1_6/01. How to unset system in alarm. Programs 1, 2 and 3. Access codes. How to operate Personal Attack
 Access codes Contents Unset system indications - - - - - - - - - - - System indication - - - - - - - - - - - - Access codes - - - - - - - - - - - - - - - - How to operate Personal - - - - - - How to unset
Access codes Contents Unset system indications - - - - - - - - - - - System indication - - - - - - - - - - - - Access codes - - - - - - - - - - - - - - - - How to operate Personal - - - - - - How to unset
Access Control Management Software
 ACCESS CONTROL MANAGEMENT SOFTWARE Access Control Management Software System VII - meeting today s demands and tomorrow s challenges. Supports multiple-monitor workstations Compatible with Microsoft s
ACCESS CONTROL MANAGEMENT SOFTWARE Access Control Management Software System VII - meeting today s demands and tomorrow s challenges. Supports multiple-monitor workstations Compatible with Microsoft s
User s Manual for Fingerprint Door Control Software
 User s Manual for Fingerprint Door Control Software Foreword The naissance of F7 indicated that fingerprint reader enters into professional door control domain. That s why we developed this software to
User s Manual for Fingerprint Door Control Software Foreword The naissance of F7 indicated that fingerprint reader enters into professional door control domain. That s why we developed this software to
INS580. Apps for Android. Android is a trademark of Google Inc.
 INS580 Apps for Android Android is a trademark of Google Inc. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons
INS580 Apps for Android Android is a trademark of Google Inc. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons
Matrix 424/832/832+ ICON & LCD User Manual. Software Version 5 RINS915-2. EN50131-1 Security Grade 2 Environmental Class 2
 Matrix 424/832/832+ ICON & LCD User Manual Software Version 5 RINS915-2 EN50131-1 Security Grade 2 Environmental Class 2 CONTENTS CHAPTER 1: INTRODUCTION... 1 CHAPTER 2: REPLACING THE BATTERIES... 2 CHAPTER
Matrix 424/832/832+ ICON & LCD User Manual Software Version 5 RINS915-2 EN50131-1 Security Grade 2 Environmental Class 2 CONTENTS CHAPTER 1: INTRODUCTION... 1 CHAPTER 2: REPLACING THE BATTERIES... 2 CHAPTER
B.A.S.I.S. G and V Offline Setup Guide
 B.A.S.I.S. G and V Offline Setup Guide Copyright 2006 Stanley Security Solutions, Inc. and Stanley Logistics, Inc. All rights reserved. Printed in the United States of America. Information in this document
B.A.S.I.S. G and V Offline Setup Guide Copyright 2006 Stanley Security Solutions, Inc. and Stanley Logistics, Inc. All rights reserved. Printed in the United States of America. Information in this document
S-IA-PRO Intelli-M Access Professional V4.0
 S-IA-PRO Intelli-M Access Professional V4.0 An Addendum to the Intelli-M Access V4.0 User Guide For SKU: S-IA-PRO ACCESS Professional PLEASE READ THIS MANUAL BEFORE USING YOUR INTELLI-M ACCESS PROFESSIONAL
S-IA-PRO Intelli-M Access Professional V4.0 An Addendum to the Intelli-M Access V4.0 User Guide For SKU: S-IA-PRO ACCESS Professional PLEASE READ THIS MANUAL BEFORE USING YOUR INTELLI-M ACCESS PROFESSIONAL
Configuring Your Network s Security
 Configuring Your Network s Security Security is an important issue when using a wireless home network. Because radio waves are used to transfer information between your networked computers, it's possible
Configuring Your Network s Security Security is an important issue when using a wireless home network. Because radio waves are used to transfer information between your networked computers, it's possible
TCP/IP MODULE CA-ETHR-A INSTALLATION MANUAL
 TCP/IP MODULE CA-ETHR-A INSTALLATION MANUAL w w w. c d v g r o u p. c o m CA-ETHR-A: TCP/IP Module Installation Manual Page Table of Contents Introduction...5 Hardware Components... 6 Technical Specifications...
TCP/IP MODULE CA-ETHR-A INSTALLATION MANUAL w w w. c d v g r o u p. c o m CA-ETHR-A: TCP/IP Module Installation Manual Page Table of Contents Introduction...5 Hardware Components... 6 Technical Specifications...
How to Program a Commander or Scout to Connect to Pilot Software
 How to Program a Commander or Scout to Connect to Pilot Software Commander and Scout are monitoring and control products that can transfer physical environmental conditions and alarm sensor electrical
How to Program a Commander or Scout to Connect to Pilot Software Commander and Scout are monitoring and control products that can transfer physical environmental conditions and alarm sensor electrical
The FlexiSchools Online Order Management System Installation Guide
 The FlexiSchools Online Order Management System Installation Guide FlexiSchools May 2012 Page 1 of 16 Installation Pack Welcome to the FlexiSchools system. You will have received a disc containing: Sato
The FlexiSchools Online Order Management System Installation Guide FlexiSchools May 2012 Page 1 of 16 Installation Pack Welcome to the FlexiSchools system. You will have received a disc containing: Sato
Vantage Point Access Control Software
 Contents Ch.1 Preparation... 5 Vantage Point Software Selection.. 5 Vantage Point Software Structure.. 5 Vantage Point System Configuration. 6 Ch.2 Installation..7 Vantage Point Program Installation 7
Contents Ch.1 Preparation... 5 Vantage Point Software Selection.. 5 Vantage Point Software Structure.. 5 Vantage Point System Configuration. 6 Ch.2 Installation..7 Vantage Point Program Installation 7
Active Directory (AD) Self-Service
 Active Directory (AD) Self-Service TETRA IT has implemented a way for you to: 1. Set-Up/Maintain AD Contact Information (Use this option to create an AD Self-Serve Account and/or Maintain your AD Contact
Active Directory (AD) Self-Service TETRA IT has implemented a way for you to: 1. Set-Up/Maintain AD Contact Information (Use this option to create an AD Self-Serve Account and/or Maintain your AD Contact
Reference Manual Access Control and Security Management Software
 Reference Manual Access Control and Security Management Software DN1420 1208/ Version 5.02 Copyright 2012 Tyco International Ltd. and its Respective Companies. All Rights Reserved. All specifications were
Reference Manual Access Control and Security Management Software DN1420 1208/ Version 5.02 Copyright 2012 Tyco International Ltd. and its Respective Companies. All Rights Reserved. All specifications were
GE Simon XT Quick User Guide
 GE Simon XT Quick User Guide GE Simon XT Quick User Guide Page 1 Before Calling Is the keypad beeping? Press STATUS. This will silence the beeping and let you know where the trouble is. Is there a flashing
GE Simon XT Quick User Guide GE Simon XT Quick User Guide Page 1 Before Calling Is the keypad beeping? Press STATUS. This will silence the beeping and let you know where the trouble is. Is there a flashing
Please refer to the guide below to use the latest Android version of the UCam247Live app.
 Please refer to the guide below to use the latest Android version of the UCam247Live app. IMPORTANT: If you already have a camera installed and working on your network using our older app please follow
Please refer to the guide below to use the latest Android version of the UCam247Live app. IMPORTANT: If you already have a camera installed and working on your network using our older app please follow
WIRING HARNESS FOR AS635P4. BLUE PLUG RED, BLUE, BLACK, WHITE - Plug in dual stage sensor harness
 WIRING HARNESS FOR AS635P4 ANTENNA NOT USED 5 PIN WHITE PLUG 2 PIN WHITE PLUG GREEN - PARKING BRAKE INPUT (-) BLUE - NOT USED 3 PIN BLUE PLUG RED, BLUE, BLACK, WHITE - Plug in dual stage sensor harness
WIRING HARNESS FOR AS635P4 ANTENNA NOT USED 5 PIN WHITE PLUG 2 PIN WHITE PLUG GREEN - PARKING BRAKE INPUT (-) BLUE - NOT USED 3 PIN BLUE PLUG RED, BLUE, BLACK, WHITE - Plug in dual stage sensor harness
2.0 Installation 1. Remove the cover using a small flat blade screwdriver. Figure 2: Cover Removal
 O N DS160/DS161 Installation Guide High Performance Request-to-Exit Sensors 1.0 Description The DS160/161 is a passive-infrared (PIR) detector designed for Request to Exit (REX) interior applications.
O N DS160/DS161 Installation Guide High Performance Request-to-Exit Sensors 1.0 Description The DS160/161 is a passive-infrared (PIR) detector designed for Request to Exit (REX) interior applications.
GLOSSARY of SECURITY TERMS
 GLOSSARY of SECURITY TERMS ACAMS (Access Control and Alarm Monitoring System) An electronic system or network of integrated systems designed to control physical access and monitor events such as intrusion.
GLOSSARY of SECURITY TERMS ACAMS (Access Control and Alarm Monitoring System) An electronic system or network of integrated systems designed to control physical access and monitor events such as intrusion.
Basic Mercury Powered NXT Configuration in Doors.NET TM Application Note. 1.0 Adding an NXT-MSC Controller to the NXT Gateway
 Doors.NET installation and controller configuration is a three step process. Each of these steps has its own document, with controller configuration broken into separate documents per hardware type. software
Doors.NET installation and controller configuration is a three step process. Each of these steps has its own document, with controller configuration broken into separate documents per hardware type. software
Cloud Services ADM. Agent Deployment Guide
 Cloud Services ADM Agent Deployment Guide 10/15/2014 CONTENTS System Requirements... 1 Hardware Requirements... 1 Installation... 2 SQL Connection... 4 AD Mgmt Agent... 5 MMC... 7 Service... 8 License
Cloud Services ADM Agent Deployment Guide 10/15/2014 CONTENTS System Requirements... 1 Hardware Requirements... 1 Installation... 2 SQL Connection... 4 AD Mgmt Agent... 5 MMC... 7 Service... 8 License
Keypad Programming Instructions for the Profile Series LK and v.g1 Locks
 Keypad Programming Instructions for the Profile Series LK and v.g1 Locks A7716B www.sargentlock.com 1 2 3 4 5 6 Table of Contents Page LK Programming...14 Transaction Log for LK...4 G1LU, G1PA, G1PK, G1TU,
Keypad Programming Instructions for the Profile Series LK and v.g1 Locks A7716B www.sargentlock.com 1 2 3 4 5 6 Table of Contents Page LK Programming...14 Transaction Log for LK...4 G1LU, G1PA, G1PK, G1TU,
