CS112 Lecture: Searching and Sorting
|
|
|
- Jane Logan
- 7 years ago
- Views:
Transcription
1 CS112 Lecture: Searching and Sorting Objectives: 1. To introduce the linear search algorithm. 2. To introduce the binary search algorithm. 3. To show superiority of O(log n) vs O(n) 4. To take note of searching methods discussed in book (selection, bubble, heap) and preview coming attractions. 5. To discuss idea of maintaining a list in order by inserting at proper place. I. Introduction/Motivation A. Many computer applications require the ability to search a list of items to find some particular item. EXAMPLES: 1. When students register for courses, the computer program used by the registrar must locate the appropriate course records (identified by course ID) to be sure there is room in the course, and then the appropriate student record (identified by student ID) to record that the student is registered in these courses. 2. Entering a URL in a web browser results in several searches - e.g.: a) One or more name servers perform searches to translate the server s name into an IP number b) One or more routers perform searches to find a physical path from the requesting computer to the server. c) The server performs one or more searches in various directories to locate the file containing the requested page. 3. Others? ASK B. Likewise, many computer applications require the ability to sort a list of items into some order. 1
2 1. We shall see shortly that one motivation for this is improved search performance - it is faster to search for an item in an appropriately-ordered list than in a list that is not ordered. Example: Which is easier - to look up a person in a conventional phone book given their last name, or to look up a person in a conventional phone book given their street address? Why? ASK 2. A second motivation is human convenience - in many cases, humans prefer information to be presented in some rational order. Example: The course schedule booklets you are given at registration time contains two lists of courses: a) One sorted by course ID (department + number) b) One sorted by time 3. A third motivation for sorting is that there are some operations which depend on working with sorted lists - e.g. computer matching. a) Consider the process used by state tax authorities to match information you supply on your state tax return with information supplied on your federal return. Basically what they do is sort the information they get from taxpayers by social security number, and likewise sort the information they get on Massachusetts residents from the federal government by social security number. Now they repeat the following process as long as the lists are not empty. (1) If the first entry on both lists has the same ssn, they compare the information for consistency and move on the the next item on both lists. (2) If the first entry on the federal list has a smaller ssn, then some Massachusetts taxpayer may not have filed a state tax return. (In this case, they take appropriate action and then move on to the next item on the federal list, keeping the same item on the state list.) (3) If the first entry on the state list has a smaller ssn, then some Massachusetts taxpayer may not have filed a federal tax return. (In this case, they take appropriate action and then move on to the next item on the state list, keeping the same item on the federal list.) 2
3 b) While people who pay their taxes conscientiously should appreciate the use of matching in this case as a tool for catching people who fail to carry their fair share of the load, matching can also be used in less socially-desirable ways - e.g. to match (say) a list of subscribers to some subversive periodical against a list of employees in a company that doesn t want their employees reading such material. II. Searching Algorithms A. The simplest and most generally applicable search strategy is a strategy called linear or sequential search. 1. Basic algorithm: Start searching with the first item while there are still items to search and we haven t found the one we want move on to the next item if we have found what we want return it else return some failure code (e.g. null or -1) 2. Example: Do a sequential search of the class as seated for a person with a particular name. 3. Time complexity: takes time proportional to the number of items in the list. We call this O(n). Note that average case for item found examines half the items in the list; item not found or worst case for item found examines all of them. B. An alternative, and much better, searching strategy becomes possible if the entries are kept in order on the key we are searching for - e.g. here alphabetical order of name. This strategy is called binary search. 1. Demo using searching for a page in a book 2. Basic algorithm 3
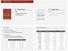
4 lo = index of start of list (e.g. 0); hi = index of last item (e.g. length - 1); Calculate position of middle item: mid = (lo+hi)/2; while (lo <= hi && middle item is not what we want) if middle item is bigger than what we want hi = mid - 1; else lo = mid + 1; mid = (lo + hi) / 2; if (lo > hi) item we want is not in list; else item at position mid is what we want; 3. Time complexity: ASK a) At each time through the loop, we cut the number of items under consideration in half. Thus, after k iterations on a list starting with n items, we are still considering n / 2k. If we get down to the last item, we are done in any case - thus the maximum number of comparisons before this time is given by n / 2k = 1, or 2k = n, or k = log2 (n). Total comparisons is 1 more (for last item). b) 3 AM phone call fact. Note, too, that computer scientists almost always mean base 2 when talking about the log of n. c) How much better is this than sequential search? For small n, somewhat better - for large n vastly better: 4
5 n Sequential search Binary search Average Worst (both) Note that binary search only works if the list is ordered on the key we are using for the search. (E.g. if a list of people were in alphabetical order of name, we wouldn t be able to use binary search to look up a person by zip code.). In all other cases, we still have to use sequential search. 5. The need to maintain the list in order has a performance price tag of its own, of course, which we will consider shortly. C. We won t discuss these now, but it should be noted that there are searching strategies other than sequential or binary search available to us, which depend on other strategies for ordering the list. One such strategy - which is the one used by the class java.util.hashtable - potentially yields O(1) performance (time independent of list size) in the average case, but can degenerate to O(n) - the same as sequential search - in the worst case. We will consider this strategy further in CS212. III. Sorting A. We said earlier that there are a number of reasons why we might find it desirable to keep a series of entries in some kind of order. 1. We have just considered one - vastly improved search performance. 2. Another motivation, of perhaps even greater importance, is user convenience. 3. There are other operations whose performance is also improved by keeping one or more lists in order - e.g. computer matching. B. For a variety of reasons, then, we are interested in algorithms that can be used to sort a list of items. 1. Terminology: 5
6 a) Sort key - the value that is used to establish the ordering. (Can be composite - e.g. sort by last name, and by first name within the same last name.). b) The key must be capable of being compared by a < operation, which must be transitive (A < B and B < C implies A < C) (1) In Java, primitive types (ints etc.) have a < operator which meets this requirement. (2) In Java, < cannot be used with objects. However, many classes (e.g. String) define an appropriate compareto() method that can be used to compare two objects of that class - e.g. if s and t are strings, we can ask if s alphabetically precedes t as follows: if (s.compareto(t) < 0)... (3) For our discussion now, we will simply use the < operator generically - i.e. to stand for < or compareto(...) < 0 as appropriate. c) A list is said to be sorted if, for all i: 0 <= i < list length - 1 the key of item [i] <= the key of item [i + 1] d) The task of sorting is to find a sorted permutation of the original list. Note that, if no two entries have the same key, the sorting of a given list is unique. 2. Over the years, many sorting algorithms have been developed. We will consider these in detail in CS212. For now, note that the book discussed three: ASK a) Selection sort b) Bubble sort c) Heapsort 6
7 3. The first two have performance that is O(n2). The third is O(n log2 n), which is as good as one can do except in some very unusual cases. Note that both costs are very high - e.g. sorting a list of a million items using an O(n2) sort will take on the order of 1 trillion comparisons, though most algorithms can cut that by a factor of 2 to only 500 billion!. (The same list, using an O(n log2 n) algorithm, can be sorted in only about 20 million comparisons!) 4. Because sorting is costly - at least for large lists - we want to be sure it is worth doing. a) For example, if sorting a list allows us to use binary search, we have to compare the cost of sorting the list in the first place versus the savings we realize on searches. (The answer may depend on how many searches we need to do.) b) Human convenience or the need to be able to perform some operation like matching may justify the cost of sorting. IV. An Alternative to Sorting - Maintaining an Ordered List A. As an alternative to sorting a list, we consider the possibility of keeping a list in order at all times. 1. This means that, when we insert an item, we move all the items that belong after it down one place. 2. When we delete an item, we move all the items after it up one place. 3. What we gain is the ability to use binary search to find an item (needed both in its own right and to support delete). We can also use a modification of binary search to find where an item about to be inserted would belong. (Basically, the binary search algorithm will end by examining the item that belongs either just before or just after the item we plan to insert, so one more comparison will let us determine where the new item belongs.) B. Complexity. ASK for each. 1. Look up an item: O(log n). 2. Insert a new item: O(log n) to find space, plus O(n) to shift = O(n). 7
8 Note: the cost of building up a list of n items from scratch by inserting each new item this way is n x O(n) = O(n 2). This is, in fact, the basis of a sorting algorithm called insertion sort. 3. Delete an item: O(log n) to find, plus O(n) to shift = O(n). C. In contrasting this strategy with an unordered list, we note that it has a major advantage in cost to search gained at a higher cost of maintaining the list. 1. If searches are frequent relative to changes, this cost is worth it. 2. It may also be worth it for the sake of user convenience. 8
Zabin Visram Room CS115 CS126 Searching. Binary Search
 Zabin Visram Room CS115 CS126 Searching Binary Search Binary Search Sequential search is not efficient for large lists as it searches half the list, on average Another search algorithm Binary search Very
Zabin Visram Room CS115 CS126 Searching Binary Search Binary Search Sequential search is not efficient for large lists as it searches half the list, on average Another search algorithm Binary search Very
Symbol Tables. Introduction
 Symbol Tables Introduction A compiler needs to collect and use information about the names appearing in the source program. This information is entered into a data structure called a symbol table. The
Symbol Tables Introduction A compiler needs to collect and use information about the names appearing in the source program. This information is entered into a data structure called a symbol table. The
Data Structures Fibonacci Heaps, Amortized Analysis
 Chapter 4 Data Structures Fibonacci Heaps, Amortized Analysis Algorithm Theory WS 2012/13 Fabian Kuhn Fibonacci Heaps Lacy merge variant of binomial heaps: Do not merge trees as long as possible Structure:
Chapter 4 Data Structures Fibonacci Heaps, Amortized Analysis Algorithm Theory WS 2012/13 Fabian Kuhn Fibonacci Heaps Lacy merge variant of binomial heaps: Do not merge trees as long as possible Structure:
Analysis of Binary Search algorithm and Selection Sort algorithm
 Analysis of Binary Search algorithm and Selection Sort algorithm In this section we shall take up two representative problems in computer science, work out the algorithms based on the best strategy to
Analysis of Binary Search algorithm and Selection Sort algorithm In this section we shall take up two representative problems in computer science, work out the algorithms based on the best strategy to
Krishna Institute of Engineering & Technology, Ghaziabad Department of Computer Application MCA-213 : DATA STRUCTURES USING C
 Tutorial#1 Q 1:- Explain the terms data, elementary item, entity, primary key, domain, attribute and information? Also give examples in support of your answer? Q 2:- What is a Data Type? Differentiate
Tutorial#1 Q 1:- Explain the terms data, elementary item, entity, primary key, domain, attribute and information? Also give examples in support of your answer? Q 2:- What is a Data Type? Differentiate
CS104: Data Structures and Object-Oriented Design (Fall 2013) October 24, 2013: Priority Queues Scribes: CS 104 Teaching Team
 CS104: Data Structures and Object-Oriented Design (Fall 2013) October 24, 2013: Priority Queues Scribes: CS 104 Teaching Team Lecture Summary In this lecture, we learned about the ADT Priority Queue. A
CS104: Data Structures and Object-Oriented Design (Fall 2013) October 24, 2013: Priority Queues Scribes: CS 104 Teaching Team Lecture Summary In this lecture, we learned about the ADT Priority Queue. A
Binary Search Trees. Data in each node. Larger than the data in its left child Smaller than the data in its right child
 Binary Search Trees Data in each node Larger than the data in its left child Smaller than the data in its right child FIGURE 11-6 Arbitrary binary tree FIGURE 11-7 Binary search tree Data Structures Using
Binary Search Trees Data in each node Larger than the data in its left child Smaller than the data in its right child FIGURE 11-6 Arbitrary binary tree FIGURE 11-7 Binary search tree Data Structures Using
Introduction to Algorithms March 10, 2004 Massachusetts Institute of Technology Professors Erik Demaine and Shafi Goldwasser Quiz 1.
 Introduction to Algorithms March 10, 2004 Massachusetts Institute of Technology 6.046J/18.410J Professors Erik Demaine and Shafi Goldwasser Quiz 1 Quiz 1 Do not open this quiz booklet until you are directed
Introduction to Algorithms March 10, 2004 Massachusetts Institute of Technology 6.046J/18.410J Professors Erik Demaine and Shafi Goldwasser Quiz 1 Quiz 1 Do not open this quiz booklet until you are directed
5. A full binary tree with n leaves contains [A] n nodes. [B] log n 2 nodes. [C] 2n 1 nodes. [D] n 2 nodes.
![5. A full binary tree with n leaves contains [A] n nodes. [B] log n 2 nodes. [C] 2n 1 nodes. [D] n 2 nodes. 5. A full binary tree with n leaves contains [A] n nodes. [B] log n 2 nodes. [C] 2n 1 nodes. [D] n 2 nodes.](/thumbs/40/21353779.jpg) 1. The advantage of.. is that they solve the problem if sequential storage representation. But disadvantage in that is they are sequential lists. [A] Lists [B] Linked Lists [A] Trees [A] Queues 2. The
1. The advantage of.. is that they solve the problem if sequential storage representation. But disadvantage in that is they are sequential lists. [A] Lists [B] Linked Lists [A] Trees [A] Queues 2. The
- Easy to insert & delete in O(1) time - Don t need to estimate total memory needed. - Hard to search in less than O(n) time
 Skip Lists CMSC 420 Linked Lists Benefits & Drawbacks Benefits: - Easy to insert & delete in O(1) time - Don t need to estimate total memory needed Drawbacks: - Hard to search in less than O(n) time (binary
Skip Lists CMSC 420 Linked Lists Benefits & Drawbacks Benefits: - Easy to insert & delete in O(1) time - Don t need to estimate total memory needed Drawbacks: - Hard to search in less than O(n) time (binary
Lecture Notes on Linear Search
 Lecture Notes on Linear Search 15-122: Principles of Imperative Computation Frank Pfenning Lecture 5 January 29, 2013 1 Introduction One of the fundamental and recurring problems in computer science is
Lecture Notes on Linear Search 15-122: Principles of Imperative Computation Frank Pfenning Lecture 5 January 29, 2013 1 Introduction One of the fundamental and recurring problems in computer science is
Chapter 2 Time value of money
 Chapter 2 Time value of money Interest: the cost of money Economic equivalence Interest formulas single cash flows Equal-payment series Dealing with gradient series Composite cash flows. Power-Ball Lottery
Chapter 2 Time value of money Interest: the cost of money Economic equivalence Interest formulas single cash flows Equal-payment series Dealing with gradient series Composite cash flows. Power-Ball Lottery
B-Trees. Algorithms and data structures for external memory as opposed to the main memory B-Trees. B -trees
 B-Trees Algorithms and data structures for external memory as opposed to the main memory B-Trees Previous Lectures Height balanced binary search trees: AVL trees, red-black trees. Multiway search trees:
B-Trees Algorithms and data structures for external memory as opposed to the main memory B-Trees Previous Lectures Height balanced binary search trees: AVL trees, red-black trees. Multiway search trees:
Binary search algorithm
 Binary search algorithm Definition Search a sorted array by repeatedly dividing the search interval in half. Begin with an interval covering the whole array. If the value of the search key is less than
Binary search algorithm Definition Search a sorted array by repeatedly dividing the search interval in half. Begin with an interval covering the whole array. If the value of the search key is less than
Outline. Introduction Linear Search. Transpose sequential search Interpolation search Binary search Fibonacci search Other search techniques
 Searching (Unit 6) Outline Introduction Linear Search Ordered linear search Unordered linear search Transpose sequential search Interpolation search Binary search Fibonacci search Other search techniques
Searching (Unit 6) Outline Introduction Linear Search Ordered linear search Unordered linear search Transpose sequential search Interpolation search Binary search Fibonacci search Other search techniques
Binary Heap Algorithms
 CS Data Structures and Algorithms Lecture Slides Wednesday, April 5, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org 2005 2009 Glenn G. Chappell
CS Data Structures and Algorithms Lecture Slides Wednesday, April 5, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org 2005 2009 Glenn G. Chappell
Questions 1 through 25 are worth 2 points each. Choose one best answer for each.
 Questions 1 through 25 are worth 2 points each. Choose one best answer for each. 1. For the singly linked list implementation of the queue, where are the enqueues and dequeues performed? c a. Enqueue in
Questions 1 through 25 are worth 2 points each. Choose one best answer for each. 1. For the singly linked list implementation of the queue, where are the enqueues and dequeues performed? c a. Enqueue in
TREE BASIC TERMINOLOGIES
 TREE Trees are very flexible, versatile and powerful non-liner data structure that can be used to represent data items possessing hierarchical relationship between the grand father and his children and
TREE Trees are very flexible, versatile and powerful non-liner data structure that can be used to represent data items possessing hierarchical relationship between the grand father and his children and
Record Storage and Primary File Organization
 Record Storage and Primary File Organization 1 C H A P T E R 4 Contents Introduction Secondary Storage Devices Buffering of Blocks Placing File Records on Disk Operations on Files Files of Unordered Records
Record Storage and Primary File Organization 1 C H A P T E R 4 Contents Introduction Secondary Storage Devices Buffering of Blocks Placing File Records on Disk Operations on Files Files of Unordered Records
DATA STRUCTURES USING C
 DATA STRUCTURES USING C QUESTION BANK UNIT I 1. Define data. 2. Define Entity. 3. Define information. 4. Define Array. 5. Define data structure. 6. Give any two applications of data structures. 7. Give
DATA STRUCTURES USING C QUESTION BANK UNIT I 1. Define data. 2. Define Entity. 3. Define information. 4. Define Array. 5. Define data structure. 6. Give any two applications of data structures. 7. Give
1) The postfix expression for the infix expression A+B*(C+D)/F+D*E is ABCD+*F/DE*++
 Answer the following 1) The postfix expression for the infix expression A+B*(C+D)/F+D*E is ABCD+*F/DE*++ 2) Which data structure is needed to convert infix notations to postfix notations? Stack 3) The
Answer the following 1) The postfix expression for the infix expression A+B*(C+D)/F+D*E is ABCD+*F/DE*++ 2) Which data structure is needed to convert infix notations to postfix notations? Stack 3) The
What Is Recursion? Recursion. Binary search example postponed to end of lecture
 Recursion Binary search example postponed to end of lecture What Is Recursion? Recursive call A method call in which the method being called is the same as the one making the call Direct recursion Recursion
Recursion Binary search example postponed to end of lecture What Is Recursion? Recursive call A method call in which the method being called is the same as the one making the call Direct recursion Recursion
APP INVENTOR. Test Review
 APP INVENTOR Test Review Main Concepts App Inventor Lists Creating Random Numbers Variables Searching and Sorting Data Linear Search Binary Search Selection Sort Quick Sort Abstraction Modulus Division
APP INVENTOR Test Review Main Concepts App Inventor Lists Creating Random Numbers Variables Searching and Sorting Data Linear Search Binary Search Selection Sort Quick Sort Abstraction Modulus Division
Binary Heaps. CSE 373 Data Structures
 Binary Heaps CSE Data Structures Readings Chapter Section. Binary Heaps BST implementation of a Priority Queue Worst case (degenerate tree) FindMin, DeleteMin and Insert (k) are all O(n) Best case (completely
Binary Heaps CSE Data Structures Readings Chapter Section. Binary Heaps BST implementation of a Priority Queue Worst case (degenerate tree) FindMin, DeleteMin and Insert (k) are all O(n) Best case (completely
Vodafone Hosted Services - A Guide to Selecting and Preparing Your Own Domain
 Vodafone Hosted Services Domain and email packages User guide Welcome. This guide will help you to choose and purchase your Vodafone Hosted Services packages. From here you can select and buy your own
Vodafone Hosted Services Domain and email packages User guide Welcome. This guide will help you to choose and purchase your Vodafone Hosted Services packages. From here you can select and buy your own
Ordered Lists and Binary Trees
 Data Structures and Algorithms Ordered Lists and Binary Trees Chris Brooks Department of Computer Science University of San Francisco Department of Computer Science University of San Francisco p.1/62 6-0:
Data Structures and Algorithms Ordered Lists and Binary Trees Chris Brooks Department of Computer Science University of San Francisco Department of Computer Science University of San Francisco p.1/62 6-0:
Data Structures. Topic #12
 Data Structures Topic #12 Today s Agenda Sorting Algorithms insertion sort selection sort exchange sort shell sort radix sort As we learn about each sorting algorithm, we will discuss its efficiency Sorting
Data Structures Topic #12 Today s Agenda Sorting Algorithms insertion sort selection sort exchange sort shell sort radix sort As we learn about each sorting algorithm, we will discuss its efficiency Sorting
Heaps & Priority Queues in the C++ STL 2-3 Trees
 Heaps & Priority Queues in the C++ STL 2-3 Trees CS 3 Data Structures and Algorithms Lecture Slides Friday, April 7, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks
Heaps & Priority Queues in the C++ STL 2-3 Trees CS 3 Data Structures and Algorithms Lecture Slides Friday, April 7, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks
Class Overview. CSE 326: Data Structures. Goals. Goals. Data Structures. Goals. Introduction
 Class Overview CSE 326: Data Structures Introduction Introduction to many of the basic data structures used in computer software Understand the data structures Analyze the algorithms that use them Know
Class Overview CSE 326: Data Structures Introduction Introduction to many of the basic data structures used in computer software Understand the data structures Analyze the algorithms that use them Know
Chapter 2: Algorithm Discovery and Design. Invitation to Computer Science, C++ Version, Third Edition
 Chapter 2: Algorithm Discovery and Design Invitation to Computer Science, C++ Version, Third Edition Objectives In this chapter, you will learn about: Representing algorithms Examples of algorithmic problem
Chapter 2: Algorithm Discovery and Design Invitation to Computer Science, C++ Version, Third Edition Objectives In this chapter, you will learn about: Representing algorithms Examples of algorithmic problem
6. Standard Algorithms
 6. Standard Algorithms The algorithms we will examine perform Searching and Sorting. 6.1 Searching Algorithms Two algorithms will be studied. These are: 6.1.1. inear Search The inear Search The Binary
6. Standard Algorithms The algorithms we will examine perform Searching and Sorting. 6.1 Searching Algorithms Two algorithms will be studied. These are: 6.1.1. inear Search The inear Search The Binary
Algorithms. Margaret M. Fleck. 18 October 2010
 Algorithms Margaret M. Fleck 18 October 2010 These notes cover how to analyze the running time of algorithms (sections 3.1, 3.3, 4.4, and 7.1 of Rosen). 1 Introduction The main reason for studying big-o
Algorithms Margaret M. Fleck 18 October 2010 These notes cover how to analyze the running time of algorithms (sections 3.1, 3.3, 4.4, and 7.1 of Rosen). 1 Introduction The main reason for studying big-o
Analysis of a Search Algorithm
 CSE 326 Lecture 4: Lists and Stacks 1. Agfgd 2. Dgsdsfd 3. Hdffdsf 4. Sdfgsfdg 5. Tefsdgass We will review: Analysis: Searching a sorted array (from last time) List ADT: Insert, Delete, Find, First, Kth,
CSE 326 Lecture 4: Lists and Stacks 1. Agfgd 2. Dgsdsfd 3. Hdffdsf 4. Sdfgsfdg 5. Tefsdgass We will review: Analysis: Searching a sorted array (from last time) List ADT: Insert, Delete, Find, First, Kth,
CSE373: Data Structures and Algorithms Lecture 3: Math Review; Algorithm Analysis. Linda Shapiro Winter 2015
 CSE373: Data Structures and Algorithms Lecture 3: Math Review; Algorithm Analysis Linda Shapiro Today Registration should be done. Homework 1 due 11:59 pm next Wednesday, January 14 Review math essential
CSE373: Data Structures and Algorithms Lecture 3: Math Review; Algorithm Analysis Linda Shapiro Today Registration should be done. Homework 1 due 11:59 pm next Wednesday, January 14 Review math essential
http://algs4.cs.princeton.edu dictionary find definition word definition book index find relevant pages term list of page numbers
 ROBERT SEDGEWICK KEVI WAYE F O U R T H E D I T I O ROBERT SEDGEWICK KEVI WAYE ROBERT SEDGEWICK KEVI WAYE Symbol tables Symbol table applications Key-value pair abstraction. Insert a value with specified.
ROBERT SEDGEWICK KEVI WAYE F O U R T H E D I T I O ROBERT SEDGEWICK KEVI WAYE ROBERT SEDGEWICK KEVI WAYE Symbol tables Symbol table applications Key-value pair abstraction. Insert a value with specified.
1. The memory address of the first element of an array is called A. floor address B. foundation addressc. first address D.
 1. The memory address of the first element of an array is called A. floor address B. foundation addressc. first address D. base address 2. The memory address of fifth element of an array can be calculated
1. The memory address of the first element of an array is called A. floor address B. foundation addressc. first address D. base address 2. The memory address of fifth element of an array can be calculated
send and receive MMS
 send and receive MMS 1 Contents Page 3 Page 4 Page 7 Page 8 Page 12 Page 13 Page 15 An introduction to MMS messaging How to send MMS messages How much does it cost to send MMS? Receiving MMS How much does
send and receive MMS 1 Contents Page 3 Page 4 Page 7 Page 8 Page 12 Page 13 Page 15 An introduction to MMS messaging How to send MMS messages How much does it cost to send MMS? Receiving MMS How much does
ConvincingMail.com Email Marketing Solution Manual. Contents
 1 ConvincingMail.com Email Marketing Solution Manual Contents Overview 3 Welcome to ConvincingMail World 3 System Requirements 3 Server Requirements 3 Client Requirements 3 Edition differences 3 Which
1 ConvincingMail.com Email Marketing Solution Manual Contents Overview 3 Welcome to ConvincingMail World 3 System Requirements 3 Server Requirements 3 Client Requirements 3 Edition differences 3 Which
Managing Your Class. Managing Users
 13 Managing Your Class Now that we ve covered all the learning tools in Moodle, we ll look at some of the administrative functions that are necessary to keep your course and students organized. This chapter
13 Managing Your Class Now that we ve covered all the learning tools in Moodle, we ll look at some of the administrative functions that are necessary to keep your course and students organized. This chapter
chapter >> Consumer and Producer Surplus Section 3: Consumer Surplus, Producer Surplus, and the Gains from Trade
 chapter 6 >> Consumer and Producer Surplus Section 3: Consumer Surplus, Producer Surplus, and the Gains from Trade One of the nine core principles of economics we introduced in Chapter 1 is that markets
chapter 6 >> Consumer and Producer Surplus Section 3: Consumer Surplus, Producer Surplus, and the Gains from Trade One of the nine core principles of economics we introduced in Chapter 1 is that markets
cs2010: algorithms and data structures
 cs2010: algorithms and data structures Lecture 11: Symbol Table ADT. Vasileios Koutavas 28 Oct 2015 School of Computer Science and Statistics Trinity College Dublin Algorithms ROBERT SEDGEWICK KEVIN WAYNE
cs2010: algorithms and data structures Lecture 11: Symbol Table ADT. Vasileios Koutavas 28 Oct 2015 School of Computer Science and Statistics Trinity College Dublin Algorithms ROBERT SEDGEWICK KEVIN WAYNE
Using Microsoft Expression Web to Upload Your Site
 Using Microsoft Expression Web to Upload Your Site Using Microsoft Expression Web to Upload Your Web Site This article briefly describes how to use Microsoft Expression Web to connect to your Web server
Using Microsoft Expression Web to Upload Your Site Using Microsoft Expression Web to Upload Your Web Site This article briefly describes how to use Microsoft Expression Web to connect to your Web server
CSC148 Lecture 8. Algorithm Analysis Binary Search Sorting
 CSC148 Lecture 8 Algorithm Analysis Binary Search Sorting Algorithm Analysis Recall definition of Big Oh: We say a function f(n) is O(g(n)) if there exists positive constants c,b such that f(n)
CSC148 Lecture 8 Algorithm Analysis Binary Search Sorting Algorithm Analysis Recall definition of Big Oh: We say a function f(n) is O(g(n)) if there exists positive constants c,b such that f(n)
AP Computer Science Java Mr. Clausen Program 9A, 9B
 AP Computer Science Java Mr. Clausen Program 9A, 9B PROGRAM 9A I m_sort_of_searching (20 points now, 60 points when all parts are finished) The purpose of this project is to set up a program that will
AP Computer Science Java Mr. Clausen Program 9A, 9B PROGRAM 9A I m_sort_of_searching (20 points now, 60 points when all parts are finished) The purpose of this project is to set up a program that will
Data Structures. Chapter 8
 Chapter 8 Data Structures Computer has to process lots and lots of data. To systematically process those data efficiently, those data are organized as a whole, appropriate for the application, called a
Chapter 8 Data Structures Computer has to process lots and lots of data. To systematically process those data efficiently, those data are organized as a whole, appropriate for the application, called a
Learning Outcomes. COMP202 Complexity of Algorithms. Binary Search Trees and Other Search Trees
 Learning Outcomes COMP202 Complexity of Algorithms Binary Search Trees and Other Search Trees [See relevant sections in chapters 2 and 3 in Goodrich and Tamassia.] At the conclusion of this set of lecture
Learning Outcomes COMP202 Complexity of Algorithms Binary Search Trees and Other Search Trees [See relevant sections in chapters 2 and 3 in Goodrich and Tamassia.] At the conclusion of this set of lecture
Lecture Notes on Binary Search Trees
 Lecture Notes on Binary Search Trees 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 17 October 23, 2014 1 Introduction In this lecture, we will continue considering associative
Lecture Notes on Binary Search Trees 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 17 October 23, 2014 1 Introduction In this lecture, we will continue considering associative
Converting a Number from Decimal to Binary
 Converting a Number from Decimal to Binary Convert nonnegative integer in decimal format (base 10) into equivalent binary number (base 2) Rightmost bit of x Remainder of x after division by two Recursive
Converting a Number from Decimal to Binary Convert nonnegative integer in decimal format (base 10) into equivalent binary number (base 2) Rightmost bit of x Remainder of x after division by two Recursive
Node-Based Structures Linked Lists: Implementation
 Linked Lists: Implementation CS 311 Data Structures and Algorithms Lecture Slides Monday, March 30, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org
Linked Lists: Implementation CS 311 Data Structures and Algorithms Lecture Slides Monday, March 30, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org
Searching Algorithms
 Searching Algorithms The Search Problem Problem Statement: Given a set of data e.g., int [] arr = {10, 2, 7, 9, 7, 4}; and a particular value, e.g., int val = 7; Find the first index of the value in the
Searching Algorithms The Search Problem Problem Statement: Given a set of data e.g., int [] arr = {10, 2, 7, 9, 7, 4}; and a particular value, e.g., int val = 7; Find the first index of the value in the
Lecture 1. Basic Concepts of Set Theory, Functions and Relations
 September 7, 2005 p. 1 Lecture 1. Basic Concepts of Set Theory, Functions and Relations 0. Preliminaries...1 1. Basic Concepts of Set Theory...1 1.1. Sets and elements...1 1.2. Specification of sets...2
September 7, 2005 p. 1 Lecture 1. Basic Concepts of Set Theory, Functions and Relations 0. Preliminaries...1 1. Basic Concepts of Set Theory...1 1.1. Sets and elements...1 1.2. Specification of sets...2
The Tower of Hanoi. Recursion Solution. Recursive Function. Time Complexity. Recursive Thinking. Why Recursion? n! = n* (n-1)!
 The Tower of Hanoi Recursion Solution recursion recursion recursion Recursive Thinking: ignore everything but the bottom disk. 1 2 Recursive Function Time Complexity Hanoi (n, src, dest, temp): If (n >
The Tower of Hanoi Recursion Solution recursion recursion recursion Recursive Thinking: ignore everything but the bottom disk. 1 2 Recursive Function Time Complexity Hanoi (n, src, dest, temp): If (n >
The ADT Binary Search Tree
 The ADT Binary Search Tree The Binary Search Tree is a particular type of binary tree that enables easy searching for specific items. Definition The ADT Binary Search Tree is a binary tree which has an
The ADT Binary Search Tree The Binary Search Tree is a particular type of binary tree that enables easy searching for specific items. Definition The ADT Binary Search Tree is a binary tree which has an
IP Phone Service Administration and Subscription
 CHAPTER 6 IP Phone Service Administration and Subscription Cisco CallManager administrators maintain the list of services to which users can subscribe. These sections provide details about administering
CHAPTER 6 IP Phone Service Administration and Subscription Cisco CallManager administrators maintain the list of services to which users can subscribe. These sections provide details about administering
Previous Lectures. B-Trees. External storage. Two types of memory. B-trees. Main principles
 B-Trees Algorithms and data structures for external memory as opposed to the main memory B-Trees Previous Lectures Height balanced binary search trees: AVL trees, red-black trees. Multiway search trees:
B-Trees Algorithms and data structures for external memory as opposed to the main memory B-Trees Previous Lectures Height balanced binary search trees: AVL trees, red-black trees. Multiway search trees:
CSE 135: Introduction to Theory of Computation Decidability and Recognizability
 CSE 135: Introduction to Theory of Computation Decidability and Recognizability Sungjin Im University of California, Merced 04-28, 30-2014 High-Level Descriptions of Computation Instead of giving a Turing
CSE 135: Introduction to Theory of Computation Decidability and Recognizability Sungjin Im University of California, Merced 04-28, 30-2014 High-Level Descriptions of Computation Instead of giving a Turing
Binary Heaps * * * * * * * / / \ / \ / \ / \ / \ * * * * * * * * * * * / / \ / \ / / \ / \ * * * * * * * * * *
 Binary Heaps A binary heap is another data structure. It implements a priority queue. Priority Queue has the following operations: isempty add (with priority) remove (highest priority) peek (at highest
Binary Heaps A binary heap is another data structure. It implements a priority queue. Priority Queue has the following operations: isempty add (with priority) remove (highest priority) peek (at highest
CSE 2123 Collections: Sets and Iterators (Hash functions and Trees) Jeremy Morris
 CSE 2123 Collections: Sets and Iterators (Hash functions and Trees) Jeremy Morris 1 Collections - Set What is a Set? A Set is an unordered sequence of data with no duplicates Not like a List where you
CSE 2123 Collections: Sets and Iterators (Hash functions and Trees) Jeremy Morris 1 Collections - Set What is a Set? A Set is an unordered sequence of data with no duplicates Not like a List where you
CSE 326, Data Structures. Sample Final Exam. Problem Max Points Score 1 14 (2x7) 2 18 (3x6) 3 4 4 7 5 9 6 16 7 8 8 4 9 8 10 4 Total 92.
 Name: Email ID: CSE 326, Data Structures Section: Sample Final Exam Instructions: The exam is closed book, closed notes. Unless otherwise stated, N denotes the number of elements in the data structure
Name: Email ID: CSE 326, Data Structures Section: Sample Final Exam Instructions: The exam is closed book, closed notes. Unless otherwise stated, N denotes the number of elements in the data structure
6 March 2007 1. Array Implementation of Binary Trees
 Heaps CSE 0 Winter 00 March 00 1 Array Implementation of Binary Trees Each node v is stored at index i defined as follows: If v is the root, i = 1 The left child of v is in position i The right child of
Heaps CSE 0 Winter 00 March 00 1 Array Implementation of Binary Trees Each node v is stored at index i defined as follows: If v is the root, i = 1 The left child of v is in position i The right child of
Data storage Tree indexes
 Data storage Tree indexes Rasmus Pagh February 7 lecture 1 Access paths For many database queries and updates, only a small fraction of the data needs to be accessed. Extreme examples are looking or updating
Data storage Tree indexes Rasmus Pagh February 7 lecture 1 Access paths For many database queries and updates, only a small fraction of the data needs to be accessed. Extreme examples are looking or updating
Partitioning under the hood in MySQL 5.5
 Partitioning under the hood in MySQL 5.5 Mattias Jonsson, Partitioning developer Mikael Ronström, Partitioning author Who are we? Mikael is a founder of the technology behind NDB
Partitioning under the hood in MySQL 5.5 Mattias Jonsson, Partitioning developer Mikael Ronström, Partitioning author Who are we? Mikael is a founder of the technology behind NDB
From Last Time: Remove (Delete) Operation
 CSE 32 Lecture : More on Search Trees Today s Topics: Lazy Operations Run Time Analysis of Binary Search Tree Operations Balanced Search Trees AVL Trees and Rotations Covered in Chapter of the text From
CSE 32 Lecture : More on Search Trees Today s Topics: Lazy Operations Run Time Analysis of Binary Search Tree Operations Balanced Search Trees AVL Trees and Rotations Covered in Chapter of the text From
Course: Programming II - Abstract Data Types. The ADT Stack. A stack. The ADT Stack and Recursion Slide Number 1
 Definition Course: Programming II - Abstract Data Types The ADT Stack The ADT Stack is a linear sequence of an arbitrary number of items, together with access procedures. The access procedures permit insertions
Definition Course: Programming II - Abstract Data Types The ADT Stack The ADT Stack is a linear sequence of an arbitrary number of items, together with access procedures. The access procedures permit insertions
Using SVN to Manage Source RTL
 Using SVN to Manage Source RTL CS250 Tutorial 1 (Version 083010a) August 30, 2010 Yunsup Lee In this tutorial you will gain experience using the Subversion (SVN) to manage your source RTL and code. You
Using SVN to Manage Source RTL CS250 Tutorial 1 (Version 083010a) August 30, 2010 Yunsup Lee In this tutorial you will gain experience using the Subversion (SVN) to manage your source RTL and code. You
c 2008 Je rey A. Miron We have described the constraints that a consumer faces, i.e., discussed the budget constraint.
 Lecture 2b: Utility c 2008 Je rey A. Miron Outline: 1. Introduction 2. Utility: A De nition 3. Monotonic Transformations 4. Cardinal Utility 5. Constructing a Utility Function 6. Examples of Utility Functions
Lecture 2b: Utility c 2008 Je rey A. Miron Outline: 1. Introduction 2. Utility: A De nition 3. Monotonic Transformations 4. Cardinal Utility 5. Constructing a Utility Function 6. Examples of Utility Functions
Binary Search Trees. A Generic Tree. Binary Trees. Nodes in a binary search tree ( B-S-T) are of the form. P parent. Key. Satellite data L R
 Binary Search Trees A Generic Tree Nodes in a binary search tree ( B-S-T) are of the form P parent Key A Satellite data L R B C D E F G H I J The B-S-T has a root node which is the only node whose parent
Binary Search Trees A Generic Tree Nodes in a binary search tree ( B-S-T) are of the form P parent Key A Satellite data L R B C D E F G H I J The B-S-T has a root node which is the only node whose parent
Lecture 6: Binary Search Trees CSCI 700 - Algorithms I. Andrew Rosenberg
 Lecture 6: Binary Search Trees CSCI 700 - Algorithms I Andrew Rosenberg Last Time Linear Time Sorting Counting Sort Radix Sort Bucket Sort Today Binary Search Trees Data Structures Data structure is a
Lecture 6: Binary Search Trees CSCI 700 - Algorithms I Andrew Rosenberg Last Time Linear Time Sorting Counting Sort Radix Sort Bucket Sort Today Binary Search Trees Data Structures Data structure is a
The Union-Find Problem Kruskal s algorithm for finding an MST presented us with a problem in data-structure design. As we looked at each edge,
 The Union-Find Problem Kruskal s algorithm for finding an MST presented us with a problem in data-structure design. As we looked at each edge, cheapest first, we had to determine whether its two endpoints
The Union-Find Problem Kruskal s algorithm for finding an MST presented us with a problem in data-structure design. As we looked at each edge, cheapest first, we had to determine whether its two endpoints
AP Computer Science A - Syllabus Overview of AP Computer Science A Computer Facilities
 AP Computer Science A - Syllabus Overview of AP Computer Science A Computer Facilities The classroom is set up like a traditional classroom on the left side of the room. This is where I will conduct my
AP Computer Science A - Syllabus Overview of AP Computer Science A Computer Facilities The classroom is set up like a traditional classroom on the left side of the room. This is where I will conduct my
Hypercosm. Studio. www.hypercosm.com
 Hypercosm Studio www.hypercosm.com Hypercosm Studio Guide 3 Revision: November 2005 Copyright 2005 Hypercosm LLC All rights reserved. Hypercosm, OMAR, Hypercosm 3D Player, and Hypercosm Studio are trademarks
Hypercosm Studio www.hypercosm.com Hypercosm Studio Guide 3 Revision: November 2005 Copyright 2005 Hypercosm LLC All rights reserved. Hypercosm, OMAR, Hypercosm 3D Player, and Hypercosm Studio are trademarks
Common Data Structures
 Data Structures 1 Common Data Structures Arrays (single and multiple dimensional) Linked Lists Stacks Queues Trees Graphs You should already be familiar with arrays, so they will not be discussed. Trees
Data Structures 1 Common Data Structures Arrays (single and multiple dimensional) Linked Lists Stacks Queues Trees Graphs You should already be familiar with arrays, so they will not be discussed. Trees
Page 18. Using Software To Make More Money With Surveys. Visit us on the web at: www.takesurveysforcash.com
 Page 18 Page 1 Using Software To Make More Money With Surveys by Jason White Page 2 Introduction So you re off and running with making money by taking surveys online, good for you! The problem, as you
Page 18 Page 1 Using Software To Make More Money With Surveys by Jason White Page 2 Introduction So you re off and running with making money by taking surveys online, good for you! The problem, as you
Introduction to Data Structures
 Introduction to Data Structures Albert Gural October 28, 2011 1 Introduction When trying to convert from an algorithm to the actual code, one important aspect to consider is how to store and manipulate
Introduction to Data Structures Albert Gural October 28, 2011 1 Introduction When trying to convert from an algorithm to the actual code, one important aspect to consider is how to store and manipulate
Web Forms for Marketers 2.3 for Sitecore CMS 6.5 and
 Web Forms for Marketers 2.3 for Sitecore CMS 6.5 and later User Guide Rev: 2013-02-01 Web Forms for Marketers 2.3 for Sitecore CMS 6.5 and later User Guide A practical guide to creating and managing web
Web Forms for Marketers 2.3 for Sitecore CMS 6.5 and later User Guide Rev: 2013-02-01 Web Forms for Marketers 2.3 for Sitecore CMS 6.5 and later User Guide A practical guide to creating and managing web
INTRODUCTION The collection of data that makes up a computerized database must be stored physically on some computer storage medium.
 Chapter 4: Record Storage and Primary File Organization 1 Record Storage and Primary File Organization INTRODUCTION The collection of data that makes up a computerized database must be stored physically
Chapter 4: Record Storage and Primary File Organization 1 Record Storage and Primary File Organization INTRODUCTION The collection of data that makes up a computerized database must be stored physically
Lecture Notes on Binary Search Trees
 Lecture Notes on Binary Search Trees 15-122: Principles of Imperative Computation Frank Pfenning Lecture 17 March 17, 2010 1 Introduction In the previous two lectures we have seen how to exploit the structure
Lecture Notes on Binary Search Trees 15-122: Principles of Imperative Computation Frank Pfenning Lecture 17 March 17, 2010 1 Introduction In the previous two lectures we have seen how to exploit the structure
DATABASE DESIGN - 1DL400
 DATABASE DESIGN - 1DL400 Spring 2015 A course on modern database systems!! http://www.it.uu.se/research/group/udbl/kurser/dbii_vt15/ Kjell Orsborn! Uppsala Database Laboratory! Department of Information
DATABASE DESIGN - 1DL400 Spring 2015 A course on modern database systems!! http://www.it.uu.se/research/group/udbl/kurser/dbii_vt15/ Kjell Orsborn! Uppsala Database Laboratory! Department of Information
How to test and debug an ASP.NET application
 Chapter 4 How to test and debug an ASP.NET application 113 4 How to test and debug an ASP.NET application If you ve done much programming, you know that testing and debugging are often the most difficult
Chapter 4 How to test and debug an ASP.NET application 113 4 How to test and debug an ASP.NET application If you ve done much programming, you know that testing and debugging are often the most difficult
IP Phone Services Configuration
 CHAPTER 96 Using Cisco Unified Communications Manager Administration, you define and maintain the list of IP phone services to which users can subscribe at their site. IP phone services comprise XML applications
CHAPTER 96 Using Cisco Unified Communications Manager Administration, you define and maintain the list of IP phone services to which users can subscribe at their site. IP phone services comprise XML applications
Class Notes CS 3137. 1 Creating and Using a Huffman Code. Ref: Weiss, page 433
 Class Notes CS 3137 1 Creating and Using a Huffman Code. Ref: Weiss, page 433 1. FIXED LENGTH CODES: Codes are used to transmit characters over data links. You are probably aware of the ASCII code, a fixed-length
Class Notes CS 3137 1 Creating and Using a Huffman Code. Ref: Weiss, page 433 1. FIXED LENGTH CODES: Codes are used to transmit characters over data links. You are probably aware of the ASCII code, a fixed-length
Version Control! Scenarios, Working with Git!
 Version Control! Scenarios, Working with Git!! Scenario 1! You finished the assignment at home! VC 2 Scenario 1b! You finished the assignment at home! You get to York to submit and realize you did not
Version Control! Scenarios, Working with Git!! Scenario 1! You finished the assignment at home! VC 2 Scenario 1b! You finished the assignment at home! You get to York to submit and realize you did not
Data Structures and Algorithms Written Examination
 Data Structures and Algorithms Written Examination 22 February 2013 FIRST NAME STUDENT NUMBER LAST NAME SIGNATURE Instructions for students: Write First Name, Last Name, Student Number and Signature where
Data Structures and Algorithms Written Examination 22 February 2013 FIRST NAME STUDENT NUMBER LAST NAME SIGNATURE Instructions for students: Write First Name, Last Name, Student Number and Signature where
A Method for Cleaning Clinical Trial Analysis Data Sets
 A Method for Cleaning Clinical Trial Analysis Data Sets Carol R. Vaughn, Bridgewater Crossings, NJ ABSTRACT This paper presents a method for using SAS software to search SAS programs in selected directories
A Method for Cleaning Clinical Trial Analysis Data Sets Carol R. Vaughn, Bridgewater Crossings, NJ ABSTRACT This paper presents a method for using SAS software to search SAS programs in selected directories
Sorting revisited. Build the binary search tree: O(n^2) Traverse the binary tree: O(n) Total: O(n^2) + O(n) = O(n^2)
 Sorting revisited How did we use a binary search tree to sort an array of elements? Tree Sort Algorithm Given: An array of elements to sort 1. Build a binary search tree out of the elements 2. Traverse
Sorting revisited How did we use a binary search tree to sort an array of elements? Tree Sort Algorithm Given: An array of elements to sort 1. Build a binary search tree out of the elements 2. Traverse
Basic Programming and PC Skills: Basic Programming and PC Skills:
 Texas University Interscholastic League Contest Event: Computer Science The contest challenges high school students to gain an understanding of the significance of computation as well as the details of
Texas University Interscholastic League Contest Event: Computer Science The contest challenges high school students to gain an understanding of the significance of computation as well as the details of
7 AGGREGATE SUPPLY AND AGGREGATE DEMAND* Chapter. Key Concepts
 Chapter 7 AGGREGATE SUPPLY AND AGGREGATE DEMAND* Key Concepts Aggregate Supply The aggregate production function shows that the quantity of real GDP (Y ) supplied depends on the quantity of labor (L ),
Chapter 7 AGGREGATE SUPPLY AND AGGREGATE DEMAND* Key Concepts Aggregate Supply The aggregate production function shows that the quantity of real GDP (Y ) supplied depends on the quantity of labor (L ),
Linked Lists, Stacks, Queues, Deques. It s time for a chainge!
 Linked Lists, Stacks, Queues, Deques It s time for a chainge! Learning Goals After this unit, you should be able to... Differentiate an abstraction from an implementation. Define and give examples of problems
Linked Lists, Stacks, Queues, Deques It s time for a chainge! Learning Goals After this unit, you should be able to... Differentiate an abstraction from an implementation. Define and give examples of problems
CSE373: Data Structures and Algorithms Lecture 1: Introduction; ADTs; Stacks/Queues. Linda Shapiro Spring 2016
 CSE373: Data Structures and Algorithms Lecture 1: Introduction; ADTs; Stacks/Queues Linda Shapiro Registration We have 180 students registered and others who want to get in. If you re thinking of dropping
CSE373: Data Structures and Algorithms Lecture 1: Introduction; ADTs; Stacks/Queues Linda Shapiro Registration We have 180 students registered and others who want to get in. If you re thinking of dropping
KS3 Computing Group 1 Programme of Study 2015 2016 2 hours per week
 1 07/09/15 2 14/09/15 3 21/09/15 4 28/09/15 Communication and Networks esafety Obtains content from the World Wide Web using a web browser. Understands the importance of communicating safely and respectfully
1 07/09/15 2 14/09/15 3 21/09/15 4 28/09/15 Communication and Networks esafety Obtains content from the World Wide Web using a web browser. Understands the importance of communicating safely and respectfully
Chapter 13: Query Processing. Basic Steps in Query Processing
 Chapter 13: Query Processing! Overview! Measures of Query Cost! Selection Operation! Sorting! Join Operation! Other Operations! Evaluation of Expressions 13.1 Basic Steps in Query Processing 1. Parsing
Chapter 13: Query Processing! Overview! Measures of Query Cost! Selection Operation! Sorting! Join Operation! Other Operations! Evaluation of Expressions 13.1 Basic Steps in Query Processing 1. Parsing
A binary search tree or BST is a binary tree that is either empty or in which the data element of each node has a key, and:
 Binary Search Trees 1 The general binary tree shown in the previous chapter is not terribly useful in practice. The chief use of binary trees is for providing rapid access to data (indexing, if you will)
Binary Search Trees 1 The general binary tree shown in the previous chapter is not terribly useful in practice. The chief use of binary trees is for providing rapid access to data (indexing, if you will)
Network-Wide Capacity Planning with Route Analytics
 with Route Analytics Executive Summary Capacity planning is an important business process in large IP networks for ensuring reliable application and service delivery. In the days of fixed circuits and
with Route Analytics Executive Summary Capacity planning is an important business process in large IP networks for ensuring reliable application and service delivery. In the days of fixed circuits and
Object-Oriented Design Lecture 4 CSU 370 Fall 2007 (Pucella) Tuesday, Sep 18, 2007
 Object-Oriented Design Lecture 4 CSU 370 Fall 2007 (Pucella) Tuesday, Sep 18, 2007 The Java Type System By now, you have seen a fair amount of Java. Time to study in more depth the foundations of the language,
Object-Oriented Design Lecture 4 CSU 370 Fall 2007 (Pucella) Tuesday, Sep 18, 2007 The Java Type System By now, you have seen a fair amount of Java. Time to study in more depth the foundations of the language,
Level 2 Routing: LAN Bridges and Switches
 Level 2 Routing: LAN Bridges and Switches Norman Matloff University of California at Davis c 2001, N. Matloff September 6, 2001 1 Overview In a large LAN with consistently heavy traffic, it may make sense
Level 2 Routing: LAN Bridges and Switches Norman Matloff University of California at Davis c 2001, N. Matloff September 6, 2001 1 Overview In a large LAN with consistently heavy traffic, it may make sense
Hash Tables. Computer Science E-119 Harvard Extension School Fall 2012 David G. Sullivan, Ph.D. Data Dictionary Revisited
 Hash Tables Computer Science E-119 Harvard Extension School Fall 2012 David G. Sullivan, Ph.D. Data Dictionary Revisited We ve considered several data structures that allow us to store and search for data
Hash Tables Computer Science E-119 Harvard Extension School Fall 2012 David G. Sullivan, Ph.D. Data Dictionary Revisited We ve considered several data structures that allow us to store and search for data
Regular Expressions and Automata using Haskell
 Regular Expressions and Automata using Haskell Simon Thompson Computing Laboratory University of Kent at Canterbury January 2000 Contents 1 Introduction 2 2 Regular Expressions 2 3 Matching regular expressions
Regular Expressions and Automata using Haskell Simon Thompson Computing Laboratory University of Kent at Canterbury January 2000 Contents 1 Introduction 2 2 Regular Expressions 2 3 Matching regular expressions
Data Types. Abstract Data Types. ADTs as Design Tool. Abstract Data Types. Integer ADT. Principle of Abstraction
 bstract ata Types Previous lectures: algorithms and their efficiency analysis. oming lectures: data structures In this lecture: bstract data types Ts as a design tool Examples: integer T, List T ata Types
bstract ata Types Previous lectures: algorithms and their efficiency analysis. oming lectures: data structures In this lecture: bstract data types Ts as a design tool Examples: integer T, List T ata Types
6.080 / 6.089 Great Ideas in Theoretical Computer Science Spring 2008
 MIT OpenCourseWare http://ocw.mit.edu 6.080 / 6.089 Great Ideas in Theoretical Computer Science Spring 2008 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms.
MIT OpenCourseWare http://ocw.mit.edu 6.080 / 6.089 Great Ideas in Theoretical Computer Science Spring 2008 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms.
Pseudo code Tutorial and Exercises Teacher s Version
 Pseudo code Tutorial and Exercises Teacher s Version Pseudo-code is an informal way to express the design of a computer program or an algorithm in 1.45. The aim is to get the idea quickly and also easy
Pseudo code Tutorial and Exercises Teacher s Version Pseudo-code is an informal way to express the design of a computer program or an algorithm in 1.45. The aim is to get the idea quickly and also easy
