Reducing Your Patch Cycle to Less Than 5 Days A Vulnerabilities Exposed Webcast
|
|
|
- Rosa Elliott
- 7 years ago
- Views:
Transcription
1 Reducing Your Patch Cycle to Less Than 5 Days A Vulnerabilities Exposed Webcast Paul Asadoorian & Jack Daniel
2 Skepticism I can reduce my patch cycle to less than 5 days? And spoons don t really sound like airplanes?
3 Who, What, When, Where, Why, How? Who: You, management, administrators Why: Yes, you can, but first, why should you? How: Then, how can you reduce your patch cycle? What: Finally, what can you use to make it easier? When: Now is good. Well, at least after you finish watching this webcast.
4 Why?
5 Known Vulnerabilities Cause Problems Most exploits are used against known vulnerabilities with a known patch Attacks using zero-day exploits aren t main pain point for organizations Mandiant M-Trends, Trustwave GSR, and Verizon DBIR tell us to patch our stuff
6 Third Parties.
7 Third-party Software Hurts Us March 14, 2013: 86% of vulnerabilities discovered in the most popular 50 programs in 2012 were in non-microsoft (or third-party ) programs. The result was published today in the Secunia Vulnerability Review o
8 First, a Story The Needle in the Haystack Draws Blood o By Paul Asadoorian and Jack Daniel
9 Attacker on Your Network It happens! (Malware, Physical Access, Compromise, Social Engineering, etc ) First Goal: Find users and high-profile target systems o Domain controllers o File servers o Domain administrators
10 Enumerate Local Accounts
11 Seek Out Easy Vulnerabilities One of the best choices: MS Penetration testers celebrate its birthday Exploits are super reliable and give attacker system-level privileges
12 Dump Hashes & Crack Passwords Re-use local administrator credentials/hashes to gain access to other systems
13 Enumerate Domain Admins
14 Impersonate a Domain Admin
15 Game Over
16 Moral of the Story You must keep up with patches on ALL of your systems You must identify easily-exploitable vulnerabilities and patch them FAST
17 Who?
18 Step 1 Define Policy What you will do and where you will do it Procedures How you will do it and who you will do it with Get management to sign off on both of the above
19 Step 2 Communication & Process Communicate your policy and procedures to the right people! Management, security, administrators, and end users
20 How? (Not Magic)
21 Step 3 Find Them All Scan your network (frequently) Perform authenticated vulnerability scans o Servers & desktops o Network infrastructure o Virtualization platform o Storage systems Sniff your network for vulnerabilities Mine your logs for data Ninja convention
22 Application Discovery Get rid of applications not supported or not in use Reduce your attack platform Less stuff to patch
23 Passively Detect Applications
24 The Patch Management Struggle Our systems are missing patches! Security Guy Sysadmin
25 Patch Management Integrate vulnerability scanning with Patch Management Reduces troubleshooting time
26 Detect Early Vulnerability detection happens in many ways o Active scanning o Credentialed scanning o Passive scanning o Log analysis Find smaller issues now, before they become larger ones
27 Step 4 Prioritize & Fix Patch fewer things faster with more impact Group your vulnerabilities by: o Exploitability o Severity * o Critical Systems * o Software o Age * Warning! Danger!
28 Testing Your Patches Look at what has been patched first, are they working? Testing done for you! Microsoft also does A LOT of testing for you o Microsoft also pulls patches back Your ability to rollback a patch needs to be equal or greater than your ability to apply a patch
29 Step 5 Lather, Rinse, & Repeat While :; do o Discover Find all vulnerabilities o Test Make sure patches work o Apply Implement patches o Discover Ensure remediation worked
30 What? Nessus Active and credentialed scanning Passive Vulnerability Scanner (PVS ) Find the leaks SecurityCenter Continuous View Logs as a source for vulnerability information
31 Nessus Credentialed patch auditing Patch management Integration Detect mobile vulnerabilities Discover remotely-exploitable vulnerabilities
32 PVS Passively detect o Hosts o Mobile devices o Services o Applications o Vulnerabilities o Connections and trust relationships
33 SecurityCenter Complete, real-time enterprise vulnerability management Combine data from Nessus, PVS, LCE, and other sources Hundreds of pre-built dashboards and reports Workflow management with process automation and ticketing
34 Tenable Resources Blog: Podcast: Videos: Discussion portal: Buy Nessus, Perimeter Service, Training, & Bundles: Become a Tenable Partner:
35 Try SecurityCenter and Nessus now For more information or to evaluate SecurityCenter Continuous View: Evaluate Nessus free for 15 days:
36 Questions?
37 Thank You Contact us: Paul Asadoorian Jack Daniel Vulnerabilities Exposed webcast #2: September 24 at 2 pm EDT Addressing the Challenges of Virtualization
WHITEPAPER. Nessus Exploit Integration
 Nessus Exploit Integration v2 Tenable Network Security has committed to providing context around vulnerabilities, and correlating them to other sources, such as available exploits. We currently pull information
Nessus Exploit Integration v2 Tenable Network Security has committed to providing context around vulnerabilities, and correlating them to other sources, such as available exploits. We currently pull information
Tenable Enterprise Product Training
 Tenable Enterprise Product Training Tenable Unified Security Monitoring for Analysts (5MD) This hands-on instructor led course provides security analysts with the skills and knowledge necessary to discover
Tenable Enterprise Product Training Tenable Unified Security Monitoring for Analysts (5MD) This hands-on instructor led course provides security analysts with the skills and knowledge necessary to discover
Pass-the-Hash. Solution Brief
 Solution Brief What is Pass-the-Hash? The tools and techniques that hackers use to infiltrate an organization are constantly evolving. Credential theft is a consistent concern as compromised credentials
Solution Brief What is Pass-the-Hash? The tools and techniques that hackers use to infiltrate an organization are constantly evolving. Credential theft is a consistent concern as compromised credentials
Tenable Network Security Support Portal. January 12, 2015 (Revision 14)
 Tenable Network Security Support Portal January 12, 2015 (Revision 14) Table of Contents Introduction... 3 Activate Tenable Support Portal... 3 Locate Your Customer ID... 6 Manage Your Activation Codes...
Tenable Network Security Support Portal January 12, 2015 (Revision 14) Table of Contents Introduction... 3 Activate Tenable Support Portal... 3 Locate Your Customer ID... 6 Manage Your Activation Codes...
Nessus and Mobile Device Scanning. November 7, 2014 (Revision 12)
 Nessus and Mobile Device Scanning November 7, 2014 (Revision 12) Table of Contents Introduction... 3 Standards and Conventions... 3 Overview... 3 Scanning for Mobile Devices with Nessus... 4 Creating a
Nessus and Mobile Device Scanning November 7, 2014 (Revision 12) Table of Contents Introduction... 3 Standards and Conventions... 3 Overview... 3 Scanning for Mobile Devices with Nessus... 4 Creating a
Using Nessus In Web Application Vulnerability Assessments
 Using Nessus In Web Application Vulnerability Assessments Paul Asadoorian Product Evangelist Tenable Network Security pasadoorian@tenablesecurity.com About Tenable Nessus vulnerability scanner, ProfessionalFeed
Using Nessus In Web Application Vulnerability Assessments Paul Asadoorian Product Evangelist Tenable Network Security pasadoorian@tenablesecurity.com About Tenable Nessus vulnerability scanner, ProfessionalFeed
June 19, 2012. (Revision 1)
 Boosting Your Network Defenses with Tenable s Integral Attack Path Analytics June 19, 2012 (Revision 1) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed
Boosting Your Network Defenses with Tenable s Integral Attack Path Analytics June 19, 2012 (Revision 1) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed
Speed Up Incident Response with Actionable Forensic Analytics
 WHITEPAPER DATA SHEET Speed Up Incident Response with Actionable Forensic Analytics Close the Gap between Threat Detection and Effective Response with Continuous Monitoring January 15, 2015 Table of Contents
WHITEPAPER DATA SHEET Speed Up Incident Response with Actionable Forensic Analytics Close the Gap between Threat Detection and Effective Response with Continuous Monitoring January 15, 2015 Table of Contents
VULNERABILITY MANAGEMENT
 Vulnerability Management (VM) software differ in the richness of reporting, and the capabilities for application and security configuration assessment. Companies must consider how a VM technology will
Vulnerability Management (VM) software differ in the richness of reporting, and the capabilities for application and security configuration assessment. Companies must consider how a VM technology will
24/7 Visibility into Advanced Malware on Networks and Endpoints
 WHITEPAPER DATA SHEET 24/7 Visibility into Advanced Malware on Networks and Endpoints Leveraging threat intelligence to detect malware and exploitable vulnerabilities Oct. 24, 2014 Table of Contents Introduction
WHITEPAPER DATA SHEET 24/7 Visibility into Advanced Malware on Networks and Endpoints Leveraging threat intelligence to detect malware and exploitable vulnerabilities Oct. 24, 2014 Table of Contents Introduction
SecureGRC TM - Cloud based SaaS
 - Cloud based SaaS Single repository for regulations and standards Centralized repository for compliance related organizational data Electronic workflow to speed up communications between various entries
- Cloud based SaaS Single repository for regulations and standards Centralized repository for compliance related organizational data Electronic workflow to speed up communications between various entries
Comprehensive Malware Detection with SecurityCenter Continuous View and Nessus. February 3, 2015 (Revision 4)
 Comprehensive Malware Detection with SecurityCenter Continuous View and Nessus February 3, 2015 (Revision 4) Table of Contents Overview... 3 Malware, Botnet Detection, and Anti-Virus Auditing... 3 Malware
Comprehensive Malware Detection with SecurityCenter Continuous View and Nessus February 3, 2015 (Revision 4) Table of Contents Overview... 3 Malware, Botnet Detection, and Anti-Virus Auditing... 3 Malware
SESSION 507 Thursday, March 26, 11:15 AM - 12:15 PM Track: Desktop Support
 SESSION 507 Thursday, March 26, 11:15 AM - 12:15 PM Track: Desktop Support Desktop Support and Data Breaches: The Unknown Dangers Bryan Hood Senior Solutions Engineer, Bomgar bhood@bomgar.com Session Description
SESSION 507 Thursday, March 26, 11:15 AM - 12:15 PM Track: Desktop Support Desktop Support and Data Breaches: The Unknown Dangers Bryan Hood Senior Solutions Engineer, Bomgar bhood@bomgar.com Session Description
Unified Security Monitoring Best Practices
 Unified Security Monitoring Best Practices This white paper outlines several best practices when deploying and optimizing a USM platform to perform security and compliance monitoring for enterprise networks.
Unified Security Monitoring Best Practices This white paper outlines several best practices when deploying and optimizing a USM platform to perform security and compliance monitoring for enterprise networks.
Hunting for Indicators of Compromise
 Hunting for Indicators of Compromise Lucas Zaichkowsky Mandiant Session ID: END-R31 Session Classification: Intermediate Agenda Threat brief Defensive strategy overview Hunting for Indicators of Compromise
Hunting for Indicators of Compromise Lucas Zaichkowsky Mandiant Session ID: END-R31 Session Classification: Intermediate Agenda Threat brief Defensive strategy overview Hunting for Indicators of Compromise
Tenable Webcast Summary Managing Vulnerabilities in Virtualized and Cloud-based Deployments
 Tenable Webcast Summary Managing Vulnerabilities in Virtualized and Cloud-based Deployments Introduction Server virtualization and private cloud services offer compelling benefits, including hardware consolidation,
Tenable Webcast Summary Managing Vulnerabilities in Virtualized and Cloud-based Deployments Introduction Server virtualization and private cloud services offer compelling benefits, including hardware consolidation,
Penetration Testing Report Client: Business Solutions June 15 th 2015
 Penetration Testing Report Client: Business Solutions June 15 th 2015 Acumen Innovations 80 S.W 8 th St Suite 2000 Miami, FL 33130 United States of America Tel: 1-888-995-7803 Email: info@acumen-innovations.com
Penetration Testing Report Client: Business Solutions June 15 th 2015 Acumen Innovations 80 S.W 8 th St Suite 2000 Miami, FL 33130 United States of America Tel: 1-888-995-7803 Email: info@acumen-innovations.com
Cybersecurity Health Check At A Glance
 This cybersecurity health check provides a quick view of compliance gaps and is not intended to replace a professional HIPAA Security Risk Analysis. Failing to have more than five security measures not
This cybersecurity health check provides a quick view of compliance gaps and is not intended to replace a professional HIPAA Security Risk Analysis. Failing to have more than five security measures not
Patch Management Integration
 Patch Management Integration January 10, 2012 (Revision 5) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks of Tenable
Patch Management Integration January 10, 2012 (Revision 5) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks of Tenable
Pass-the-Hash II: Admin s Revenge. Skip Duckwall & Chris Campbell
 Pass-the-Hash II: Admin s Revenge Skip Duckwall & Chris Campbell Do you know who I am? Skip Co-presented PTH talk last year at BH, Derbycon http://passing-the-hash.blogspot.com @passingthehash on twitter
Pass-the-Hash II: Admin s Revenge Skip Duckwall & Chris Campbell Do you know who I am? Skip Co-presented PTH talk last year at BH, Derbycon http://passing-the-hash.blogspot.com @passingthehash on twitter
Penetration Testing //Vulnerability Assessment //Remedy
 A Division Penetration Testing //Vulnerability Assessment //Remedy In Penetration Testing, part of a security assessment practice attempts to simulate the techniques adopted by an attacker in compromising
A Division Penetration Testing //Vulnerability Assessment //Remedy In Penetration Testing, part of a security assessment practice attempts to simulate the techniques adopted by an attacker in compromising
Implementing Security Update Management
 Implementing Security Update Management Wayne Harris MCSE Senior Consultant Certified Security Solutions Business Case for Update Management When determining the potential financial impact of poor update
Implementing Security Update Management Wayne Harris MCSE Senior Consultant Certified Security Solutions Business Case for Update Management When determining the potential financial impact of poor update
Penetration Testing Walkthrough
 Penetration Testing Walkthrough Table of Contents Penetration Testing Walkthrough... 3 Practical Walkthrough of Phases 2-5... 4 Chose Tool BackTrack (Armitage)... 5 Choose Target... 6 Phase 2 - Basic Scan...
Penetration Testing Walkthrough Table of Contents Penetration Testing Walkthrough... 3 Practical Walkthrough of Phases 2-5... 4 Chose Tool BackTrack (Armitage)... 5 Choose Target... 6 Phase 2 - Basic Scan...
Data Security and Healthcare
 Data Security and Healthcare Complex data flows Millions of electronic medical records across many systems New and emerging business relationships Changing and maturing compliance frameworks Diverse population
Data Security and Healthcare Complex data flows Millions of electronic medical records across many systems New and emerging business relationships Changing and maturing compliance frameworks Diverse population
Vulnerability management lifecycle: defining vulnerability management
 Framework for building a vulnerability management lifecycle program http://searchsecurity.techtarget.com/magazinecontent/framework-for-building-avulnerability-management-lifecycle-program August 2011 By
Framework for building a vulnerability management lifecycle program http://searchsecurity.techtarget.com/magazinecontent/framework-for-building-avulnerability-management-lifecycle-program August 2011 By
THE TOP 4 CONTROLS. www.tripwire.com/20criticalcontrols
 THE TOP 4 CONTROLS www.tripwire.com/20criticalcontrols THE TOP 20 CRITICAL SECURITY CONTROLS ARE RATED IN SEVERITY BY THE NSA FROM VERY HIGH DOWN TO LOW. IN THIS MINI-GUIDE, WE RE GOING TO LOOK AT THE
THE TOP 4 CONTROLS www.tripwire.com/20criticalcontrols THE TOP 20 CRITICAL SECURITY CONTROLS ARE RATED IN SEVERITY BY THE NSA FROM VERY HIGH DOWN TO LOW. IN THIS MINI-GUIDE, WE RE GOING TO LOOK AT THE
ITEC441- IS Security. Chapter 15 Performing a Penetration Test
 1 ITEC441- IS Security Chapter 15 Performing a Penetration Test The PenTest A penetration test (pentest) simulates methods that intruders use to gain unauthorized access to an organization s network and
1 ITEC441- IS Security Chapter 15 Performing a Penetration Test The PenTest A penetration test (pentest) simulates methods that intruders use to gain unauthorized access to an organization s network and
April 11, 2011. (Revision 2)
 Passive Vulnerability Scanning Overview April 11, 2011 (Revision 2) Copyright 2011. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of
Passive Vulnerability Scanning Overview April 11, 2011 (Revision 2) Copyright 2011. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of
Penetration testing. A step beyond missing patches and weak passwords
 Penetration testing A step beyond missing patches and weak passwords June 25 th, 2012 Eirik Thormodsrud Graduated from the ISG in 2006 Employed by Ernst & Young Norway ever since (5 ½ years) Manager at
Penetration testing A step beyond missing patches and weak passwords June 25 th, 2012 Eirik Thormodsrud Graduated from the ISG in 2006 Employed by Ernst & Young Norway ever since (5 ½ years) Manager at
What s Wrong with Information Security Today? You are looking in the wrong places for the wrong things.
 What s Wrong with Information Security Today? You are looking in the wrong places for the wrong things. AGENDA Current State of Information Security Data Breach Statics Data Breach Case Studies Why current
What s Wrong with Information Security Today? You are looking in the wrong places for the wrong things. AGENDA Current State of Information Security Data Breach Statics Data Breach Case Studies Why current
Making the difference between read to output, and read to copy GOING BEYOND BASIC FILE AUDITING FOR DATA PROTECTION
 Making the difference between read to output, and read to copy GOING BEYOND BASIC FILE AUDITING FOR DATA PROTECTION MOST OF THE IMPORTANT DATA LOSS VECTORS DEPEND ON COPYING files in order to compromise
Making the difference between read to output, and read to copy GOING BEYOND BASIC FILE AUDITING FOR DATA PROTECTION MOST OF THE IMPORTANT DATA LOSS VECTORS DEPEND ON COPYING files in order to compromise
Compliance Guide ISO 27002. Compliance Guide. September 2015. Contents. Introduction 1. Detailed Controls Mapping 2.
 ISO 27002 Compliance Guide September 2015 Contents Compliance Guide 01 02 03 Introduction 1 Detailed Controls Mapping 2 About Rapid7 7 01 INTRODUCTION If you re looking for a comprehensive, global framework
ISO 27002 Compliance Guide September 2015 Contents Compliance Guide 01 02 03 Introduction 1 Detailed Controls Mapping 2 About Rapid7 7 01 INTRODUCTION If you re looking for a comprehensive, global framework
Nessus Enterprise Cloud User Guide. October 2, 2014 (Revision 9)
 Nessus Enterprise Cloud User Guide October 2, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Enterprise Cloud... 3 Subscription and Activation... 3 Multi Scanner Support... 4 Customer Scanning
Nessus Enterprise Cloud User Guide October 2, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Enterprise Cloud... 3 Subscription and Activation... 3 Multi Scanner Support... 4 Customer Scanning
SANS Institute First Five Quick Wins
 #1 QUICK WIN- APPLICATION WHITELISTING SANS Critical Controls: #2: Inventory of Authorized and Unauthorized Software 1) Deploy application whitelisting technology that allows systems to run software only
#1 QUICK WIN- APPLICATION WHITELISTING SANS Critical Controls: #2: Inventory of Authorized and Unauthorized Software 1) Deploy application whitelisting technology that allows systems to run software only
Is Penetration Testing recommended for Industrial Control Systems?
 Is Penetration Testing recommended for Industrial Control Systems? By Ngai Chee Ban, CISSP, Honeywell Process Solutions, Asia Pacific Cyber Security Assessment for Industrial Automation Conducting a cyber-security
Is Penetration Testing recommended for Industrial Control Systems? By Ngai Chee Ban, CISSP, Honeywell Process Solutions, Asia Pacific Cyber Security Assessment for Industrial Automation Conducting a cyber-security
Nessus Cloud User Registration
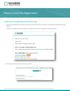 Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
1. Why is the customer having the penetration test performed against their environment?
 General Questions 1. Why is the customer having the penetration test performed against their environment? Assess vulnerabilities in order to improve security and protect client information. 2. Is the penetration
General Questions 1. Why is the customer having the penetration test performed against their environment? Assess vulnerabilities in order to improve security and protect client information. 2. Is the penetration
Managing Privileged Identities in the Cloud. How Privileged Identity Management Evolved to a Service Platform
 Managing Privileged Identities in the Cloud How Privileged Identity Management Evolved to a Service Platform Managing Privileged Identities in the Cloud Contents Overview...3 Management Issues...3 Real-World
Managing Privileged Identities in the Cloud How Privileged Identity Management Evolved to a Service Platform Managing Privileged Identities in the Cloud Contents Overview...3 Management Issues...3 Real-World
Tenable for Google Cloud Platform
 HOW-TO GUIDE Tenable for Google Cloud Platform Introduction This document describes how to deploy Tenable SecurityCenter Continuous View (Security Center CV ) for integration with Google Cloud Platform.
HOW-TO GUIDE Tenable for Google Cloud Platform Introduction This document describes how to deploy Tenable SecurityCenter Continuous View (Security Center CV ) for integration with Google Cloud Platform.
PENETRATION TESTING GUIDE. www.tbgsecurity.com 1
 PENETRATION TESTING GUIDE www.tbgsecurity.com 1 Table of Contents What is a... 3 What is the difference between Ethical Hacking and other types of hackers and testing I ve heard about?... 3 How does a
PENETRATION TESTING GUIDE www.tbgsecurity.com 1 Table of Contents What is a... 3 What is the difference between Ethical Hacking and other types of hackers and testing I ve heard about?... 3 How does a
4. Getting started: Performing an audit
 4. Getting started: Performing an audit Introduction Security scans enable systems administrators to identify and assess possible risks within a network. Through GFI LANguard N.S.S. this is performed automatically,
4. Getting started: Performing an audit Introduction Security scans enable systems administrators to identify and assess possible risks within a network. Through GFI LANguard N.S.S. this is performed automatically,
2012 Data Breach Investigations Report
 2012 Data Breach Investigations Report A study conducted by the Verizon RISK Team with cooperation from the Australian Federal Police, Dutch National High Tech Crime Unit, Irish Reporting & Information
2012 Data Breach Investigations Report A study conducted by the Verizon RISK Team with cooperation from the Australian Federal Police, Dutch National High Tech Crime Unit, Irish Reporting & Information
Secrets of Vulnerability Scanning: Nessus, Nmap and More. Ron Bowes - Researcher, Tenable Network Security
 Secrets of Vulnerability Scanning: Nessus, Nmap and More Ron Bowes - Researcher, Tenable Network Security 1 About me Ron Bowes (@iagox86) My affiliations (note: I m here to educate, not sell) 2 SkullSpace
Secrets of Vulnerability Scanning: Nessus, Nmap and More Ron Bowes - Researcher, Tenable Network Security 1 About me Ron Bowes (@iagox86) My affiliations (note: I m here to educate, not sell) 2 SkullSpace
Penetration Testing and Vulnerability Scanning
 Penetration Testing and Vulnerability Scanning Presented by Steve Spearman VP of HIPAA Compliance Services, Healthicity 20 years in Health Information Technology HIPAA Expert and Speaker Disclaimer: Nothing
Penetration Testing and Vulnerability Scanning Presented by Steve Spearman VP of HIPAA Compliance Services, Healthicity 20 years in Health Information Technology HIPAA Expert and Speaker Disclaimer: Nothing
IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE
 IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE Solution Brief SUMMARY New security threats demand a new approach to security management. Security teams need a security analytics architecture that can handle
IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE Solution Brief SUMMARY New security threats demand a new approach to security management. Security teams need a security analytics architecture that can handle
Tenable for CyberArk
 HOW-TO GUIDE Tenable for CyberArk Introduction This document describes how to deploy Tenable SecurityCenter and Nessus for integration with CyberArk Enterprise Password Vault. Please email any comments
HOW-TO GUIDE Tenable for CyberArk Introduction This document describes how to deploy Tenable SecurityCenter and Nessus for integration with CyberArk Enterprise Password Vault. Please email any comments
SecurityCenter 5.1 with Nessus Agent Support. October 22, 2015
 SecurityCenter 5.1 with Nessus Agent Support October 22, 2015 Table of Contents Introduction... 3 Adding an Agent Repository... 6 Add Agent Scans and Import Agent Scan Results... 7 Tips and Tricks... 8
SecurityCenter 5.1 with Nessus Agent Support October 22, 2015 Table of Contents Introduction... 3 Adding an Agent Repository... 6 Add Agent Scans and Import Agent Scan Results... 7 Tips and Tricks... 8
June 8, 2011. (Revision 1)
 Unified Security Monitoring Best Practices June 8, 2011 (Revision 1) Copyright 2011. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of
Unified Security Monitoring Best Practices June 8, 2011 (Revision 1) Copyright 2011. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of
Enterprise Cybersecurity: Building an Effective Defense
 : Building an Effective Defense Chris Williams Scott Donaldson Abdul Aslam 1 About the Presenters Co Authors of Enterprise Cybersecurity: How to Implement a Successful Cyberdefense Program Against Advanced
: Building an Effective Defense Chris Williams Scott Donaldson Abdul Aslam 1 About the Presenters Co Authors of Enterprise Cybersecurity: How to Implement a Successful Cyberdefense Program Against Advanced
SAST, DAST and Vulnerability Assessments, 1+1+1 = 4
 SAST, DAST and Vulnerability Assessments, 1+1+1 = 4 Gordon MacKay Digital Defense, Inc. Chris Wysopal Veracode Session ID: Session Classification: ASEC-W25 Intermediate AGENDA Risk Management Challenges
SAST, DAST and Vulnerability Assessments, 1+1+1 = 4 Gordon MacKay Digital Defense, Inc. Chris Wysopal Veracode Session ID: Session Classification: ASEC-W25 Intermediate AGENDA Risk Management Challenges
How To Manage A Privileged Account Management
 Four Best Practices for Passing Privileged Account Audits October 2014 1 Table of Contents... 4 1. Discover All Privileged Accounts in Your Environment... 4 2. Remove Privileged Access / Implement Least
Four Best Practices for Passing Privileged Account Audits October 2014 1 Table of Contents... 4 1. Discover All Privileged Accounts in Your Environment... 4 2. Remove Privileged Access / Implement Least
Managing non-microsoft updates
 Managing non-microsoft updates With Microsoft s System Center Configuration Manager secunia.com 1 How to patch all your programs directly in Microsoft System Center 2012 A common perception is that System
Managing non-microsoft updates With Microsoft s System Center Configuration Manager secunia.com 1 How to patch all your programs directly in Microsoft System Center 2012 A common perception is that System
Check Point and Security Best Practices. December 2013 Presented by David Rawle
 Check Point and Security Best Practices December 2013 Presented by David Rawle Housekeeping o Mobiles on Silent o No File Alarms planned o Fire exits are in front and behind and down the stairs o Downstairs
Check Point and Security Best Practices December 2013 Presented by David Rawle Housekeeping o Mobiles on Silent o No File Alarms planned o Fire exits are in front and behind and down the stairs o Downstairs
ETHICAL HACKING 010101010101APPLICATIO 00100101010WIRELESS110 00NETWORK1100011000 101001010101011APPLICATION0 1100011010MOBILE0001010 10101MOBILE0001
 001011 1100010110 0010110001 010110001 0110001011000 011000101100 010101010101APPLICATIO 0 010WIRELESS110001 10100MOBILE00010100111010 0010NETW110001100001 10101APPLICATION00010 00100101010WIRELESS110
001011 1100010110 0010110001 010110001 0110001011000 011000101100 010101010101APPLICATIO 0 010WIRELESS110001 10100MOBILE00010100111010 0010NETW110001100001 10101APPLICATION00010 00100101010WIRELESS110
Vulnerability Management
 Vulnerability Management Buyer s Guide Buyer s Guide 01 Introduction 02 Key Components 03 Other Considerations About Rapid7 01 INTRODUCTION Exploiting weaknesses in browsers, operating systems and other
Vulnerability Management Buyer s Guide Buyer s Guide 01 Introduction 02 Key Components 03 Other Considerations About Rapid7 01 INTRODUCTION Exploiting weaknesses in browsers, operating systems and other
Addressing the United States CIO Office s Cybersecurity Sprint Directives
 RFP Response Addressing the United States CIO Office s Cybersecurity Sprint Directives How BeyondTrust Helps Government Agencies Address Privileged Account Management and Improve Security July 2015 Addressing
RFP Response Addressing the United States CIO Office s Cybersecurity Sprint Directives How BeyondTrust Helps Government Agencies Address Privileged Account Management and Improve Security July 2015 Addressing
Assuring Application Security: Deploying Code that Keeps Data Safe
 Assuring Application Security: Deploying Code that Keeps Data Safe Assuring Application Security: Deploying Code that Keeps Data Safe 2 Introduction There s an app for that has become the mantra of users,
Assuring Application Security: Deploying Code that Keeps Data Safe Assuring Application Security: Deploying Code that Keeps Data Safe 2 Introduction There s an app for that has become the mantra of users,
IBM Security QRadar Vulnerability Manager Version 7.2.6. User Guide IBM
 IBM Security QRadar Vulnerability Manager Version 7.2.6 User Guide IBM Note Before using this information and the product that it supports, read the information in Notices on page 91. Product information
IBM Security QRadar Vulnerability Manager Version 7.2.6 User Guide IBM Note Before using this information and the product that it supports, read the information in Notices on page 91. Product information
A Penetration Testing Maturity and Scoring Model
 A Penetration Testing Maturity and Scoring Model SESSION ID: TECH-W02 Dave Shackleford Founder & Principal Consultant Voodoo Security @daveshackleford Introduction Most organizations conduct some variety
A Penetration Testing Maturity and Scoring Model SESSION ID: TECH-W02 Dave Shackleford Founder & Principal Consultant Voodoo Security @daveshackleford Introduction Most organizations conduct some variety
Common Criteria Web Application Security Scoring CCWAPSS
 Criteria Web Application Security Scoring CCWAPSS Author Frédéric Charpentier, security pentester. France. Fcharpentier@xmcopartners.com Releases Version 1.0 : First public release September 2007 Version
Criteria Web Application Security Scoring CCWAPSS Author Frédéric Charpentier, security pentester. France. Fcharpentier@xmcopartners.com Releases Version 1.0 : First public release September 2007 Version
Securing Remote Vendor Access with Privileged Account Security
 Securing Remote Vendor Access with Privileged Account Security Table of Contents Introduction to privileged remote third-party access 3 Do you know who your remote vendors are? 3 The risk: unmanaged credentials
Securing Remote Vendor Access with Privileged Account Security Table of Contents Introduction to privileged remote third-party access 3 Do you know who your remote vendors are? 3 The risk: unmanaged credentials
Recent Developments in PCI DSS. PCI in the Headlines Risks to Higher Education PCI DSS Version 1.2
 Recent Developments in PCI DSS PCI in the Headlines Risks to Higher Education PCI DSS Version 1.2 1 2009 Breach Investigation Who did it? 74% external parties 20% insiders 32% implicated business partners
Recent Developments in PCI DSS PCI in the Headlines Risks to Higher Education PCI DSS Version 1.2 1 2009 Breach Investigation Who did it? 74% external parties 20% insiders 32% implicated business partners
Penetration Testing Corporate Collaboration Portals. Giorgio Fedon, Co-Founder at Minded Security
 Penetration Testing Corporate Collaboration Portals Giorgio Fedon, Co-Founder at Minded Security Something About Me Security Researcher Owasp Italy Member Web Application Security and Malware Research
Penetration Testing Corporate Collaboration Portals Giorgio Fedon, Co-Founder at Minded Security Something About Me Security Researcher Owasp Italy Member Web Application Security and Malware Research
Network Architecture & Active Directory Considerations for the PI System. Bryan Owen - OSIsoft Joel Langill - SCADAhacker
 Network Architecture & Active Directory Considerations for the PI System By: Bryan Owen - OSIsoft Joel Langill - SCADAhacker Agenda Moore s Law Network Architecture Domain Services in a DMZ 2 HD Moore
Network Architecture & Active Directory Considerations for the PI System By: Bryan Owen - OSIsoft Joel Langill - SCADAhacker Agenda Moore s Law Network Architecture Domain Services in a DMZ 2 HD Moore
Information Security Services
 Information Security Services Information Security In 2013, Symantec reported a 62% increase in data breaches over 2012. These data breaches had tremendous impacts on many companies, resulting in intellectual
Information Security Services Information Security In 2013, Symantec reported a 62% increase in data breaches over 2012. These data breaches had tremendous impacts on many companies, resulting in intellectual
Privileged. Account Management. Accounts Discovery, Password Protection & Management. Overview. Privileged. Accounts Discovery
 Overview Password Manager Pro offers a complete solution to control, manage, monitor and audit the entire life-cycle of privileged access. In a single package it offers three solutions - privileged account
Overview Password Manager Pro offers a complete solution to control, manage, monitor and audit the entire life-cycle of privileged access. In a single package it offers three solutions - privileged account
SECURITY RISK MANAGEMENT. FIRST 2007 Seville, Spain
 SECURITY RISK MANAGEMENT FROM TECHNOLOGY VISION TO MARKET REALITY Avi Corfas, VP EMEA Skybox Security FIRST 2007 Seville, Spain Topics The Risk Assessment Challenge What Is IT Security Risk Management?
SECURITY RISK MANAGEMENT FROM TECHNOLOGY VISION TO MARKET REALITY Avi Corfas, VP EMEA Skybox Security FIRST 2007 Seville, Spain Topics The Risk Assessment Challenge What Is IT Security Risk Management?
Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure
 Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system
Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system
Five Steps to Improve Internal Network Security. Chattanooga Information security Professionals
 Five Steps to Improve Internal Network Security Chattanooga Information security Professionals Who Am I? Security Analyst: Sword & Shield Blogger: averagesecurityguy.info Developer: github.com/averagesecurityguy
Five Steps to Improve Internal Network Security Chattanooga Information security Professionals Who Am I? Security Analyst: Sword & Shield Blogger: averagesecurityguy.info Developer: github.com/averagesecurityguy
Rational AppScan & Ounce Products
 IBM Software Group Rational AppScan & Ounce Products Presenters Tony Sisson and Frank Sassano 2007 IBM Corporation IBM Software Group The Alarming Truth CheckFree warns 5 million customers after hack http://infosecurity.us/?p=5168
IBM Software Group Rational AppScan & Ounce Products Presenters Tony Sisson and Frank Sassano 2007 IBM Corporation IBM Software Group The Alarming Truth CheckFree warns 5 million customers after hack http://infosecurity.us/?p=5168
Seven Things To Consider When Evaluating Privileged Account Security Solutions
 Seven Things To Consider When Evaluating Privileged Account Security Solutions Contents Introduction 1 Seven questions to ask every privileged account security provider 4 1. Is the solution really secure?
Seven Things To Consider When Evaluating Privileged Account Security Solutions Contents Introduction 1 Seven questions to ask every privileged account security provider 4 1. Is the solution really secure?
Vulnerability. Management
 Solutions.01 Vulnerability Management.02 Enterprise Security Monitoring.03 Log Analysis & Management.04 Network Access Control.05 Compliance Monitoring Rewterz provides a diverse range of industry centric
Solutions.01 Vulnerability Management.02 Enterprise Security Monitoring.03 Log Analysis & Management.04 Network Access Control.05 Compliance Monitoring Rewterz provides a diverse range of industry centric
Redhawk Network Security, LLC 62958 Layton Ave., Suite One, Bend, OR 97701 sales@redhawksecurity.com 866-605- 6328 www.redhawksecurity.
 Planning Guide for Penetration Testing John Pelley, CISSP, ISSAP, MBCI Long seen as a Payment Card Industry (PCI) best practice, penetration testing has become a requirement for PCI 3.1 effective July
Planning Guide for Penetration Testing John Pelley, CISSP, ISSAP, MBCI Long seen as a Payment Card Industry (PCI) best practice, penetration testing has become a requirement for PCI 3.1 effective July
Intrusion Detection and Cyber Security Monitoring of SCADA and DCS Networks
 Intrusion Detection and Cyber Security Monitoring of SCADA and DCS Networks Dale Peterson Director, Network Security Practice Digital Bond, Inc. 1580 Sawgrass Corporate Parkway, Suite 130 Sunrise, FL 33323
Intrusion Detection and Cyber Security Monitoring of SCADA and DCS Networks Dale Peterson Director, Network Security Practice Digital Bond, Inc. 1580 Sawgrass Corporate Parkway, Suite 130 Sunrise, FL 33323
Network Penetration Testing and Ethical Hacking Scanning/Penetration Testing. SANS Security 560.2. Sans Mentor: Daryl Fallin
 Network Penetration Testing and Ethical Hacking Scanning/Penetration Testing SANS Security 560.2 Sans Mentor: Daryl Fallin http://www.sans.org/info/55868 Copyright 2010, All Rights Reserved Version 4Q10
Network Penetration Testing and Ethical Hacking Scanning/Penetration Testing SANS Security 560.2 Sans Mentor: Daryl Fallin http://www.sans.org/info/55868 Copyright 2010, All Rights Reserved Version 4Q10
Extreme Networks Security Analytics G2 Vulnerability Manager
 DATA SHEET Extreme Networks Security Analytics G2 Vulnerability Manager Improve security and compliance by prioritizing security gaps for resolution HIGHLIGHTS Help prevent security breaches by discovering
DATA SHEET Extreme Networks Security Analytics G2 Vulnerability Manager Improve security and compliance by prioritizing security gaps for resolution HIGHLIGHTS Help prevent security breaches by discovering
Passing PCI Compliance How to Address the Application Security Mandates
 Passing PCI Compliance How to Address the Application Security Mandates The Payment Card Industry Data Security Standards includes several requirements that mandate security at the application layer. These
Passing PCI Compliance How to Address the Application Security Mandates The Payment Card Industry Data Security Standards includes several requirements that mandate security at the application layer. These
QualysGuard WAS. Getting Started Guide Version 4.1. April 24, 2015
 QualysGuard WAS Getting Started Guide Version 4.1 April 24, 2015 Copyright 2011-2015 by Qualys, Inc. All Rights Reserved. Qualys, the Qualys logo and QualysGuard are registered trademarks of Qualys, Inc.
QualysGuard WAS Getting Started Guide Version 4.1 April 24, 2015 Copyright 2011-2015 by Qualys, Inc. All Rights Reserved. Qualys, the Qualys logo and QualysGuard are registered trademarks of Qualys, Inc.
September 2, 2010. (Revision 3)
 Web Application Scanning with Nessus Detecting Web Application Vulnerabilities and Environmental Weaknesses September 2, 2010 (Revision 3) Brian Martin Nessus SME Carole Fennelly Director, Content & Documentation
Web Application Scanning with Nessus Detecting Web Application Vulnerabilities and Environmental Weaknesses September 2, 2010 (Revision 3) Brian Martin Nessus SME Carole Fennelly Director, Content & Documentation
Symantec Client Management Suite 7.6 powered by Altiris technology
 Symantec Client Management Suite 7.6 powered by Altiris technology IT flexibility. User freedom. Data Sheet: Endpoint Management Overview With so many new devices coming into the workplace and users often
Symantec Client Management Suite 7.6 powered by Altiris technology IT flexibility. User freedom. Data Sheet: Endpoint Management Overview With so many new devices coming into the workplace and users often
OWASP Omaha. The Open Web Application Security Project Omaha Chapter
 OWASP Omaha The Open Web Application Security Project Omaha Chapter What is OWASP? The Open Web Application Security Project (OWASP) is a 501(c)(3) worldwide not-for-profit charitable organization focused
OWASP Omaha The Open Web Application Security Project Omaha Chapter What is OWASP? The Open Web Application Security Project (OWASP) is a 501(c)(3) worldwide not-for-profit charitable organization focused
Eliminating Cybersecurity Blind Spots
 Eliminating Cybersecurity Blind Spots Challenges for Business April 15, 2015 Table of Contents Introduction... 3 Risk Management... 3 The Risk Blind Spot... 4 Continuous Asset Visibility... 5 Passive Network
Eliminating Cybersecurity Blind Spots Challenges for Business April 15, 2015 Table of Contents Introduction... 3 Risk Management... 3 The Risk Blind Spot... 4 Continuous Asset Visibility... 5 Passive Network
Closing the Vulnerability Gap of Third- Party Patching
 SOLUTION BRIEF: THIRD-PARTY PATCH MANAGEMENT........................................ Closing the Vulnerability Gap of Third- Party Patching Who should read this paper IT Managers who are trying to manage
SOLUTION BRIEF: THIRD-PARTY PATCH MANAGEMENT........................................ Closing the Vulnerability Gap of Third- Party Patching Who should read this paper IT Managers who are trying to manage
Whitepaper. Security Best Practices for Evaluating Google Apps Marketplace Applications. Introduction. At a Glance
 Whitepaper Security Best Practices for Evaluating Google Apps Marketplace Applications At a Glance Intended Audience: Security Officers CIOs of large enterprises evaluating Google Apps Marketplace applications
Whitepaper Security Best Practices for Evaluating Google Apps Marketplace Applications At a Glance Intended Audience: Security Officers CIOs of large enterprises evaluating Google Apps Marketplace applications
How I Learned to Stop Worrying and Love Compliance Ron Gula, CEO Tenable Network Security
 How I Learned to Stop Worrying and Love Compliance Ron Gula, CEO Tenable Network Security PART 1 - COMPLIANCE STANDARDS PART 2 SECURITY IMPACT THEMES BUILD A MODEL THEMES MONITOR FOR FAILURE THEMES DEMONSTRATE
How I Learned to Stop Worrying and Love Compliance Ron Gula, CEO Tenable Network Security PART 1 - COMPLIANCE STANDARDS PART 2 SECURITY IMPACT THEMES BUILD A MODEL THEMES MONITOR FOR FAILURE THEMES DEMONSTRATE
Using the Tenable Solution to Audit and Protect Firewalls, Routers, and Other Network Devices May 14, 2013 (Revision 1)
 Network Infrastructure Is Not Immune Using the Tenable Solution to Audit and Protect Firewalls, Routers, and Other Network Devices May 14, 2013 (Revision 1) Table of Contents Executive Summary... 3 Network
Network Infrastructure Is Not Immune Using the Tenable Solution to Audit and Protect Firewalls, Routers, and Other Network Devices May 14, 2013 (Revision 1) Table of Contents Executive Summary... 3 Network
Tenable Product Evaluations Application: HIPAA
 Tenable Product Evaluations Application: HIPAA January 23, 2009 (Revision 6) David Breslin Director of Sales Engineering Table of Contents Table Of Contents 2 Introduction 3 Scope 3 Executive Summary 3
Tenable Product Evaluations Application: HIPAA January 23, 2009 (Revision 6) David Breslin Director of Sales Engineering Table of Contents Table Of Contents 2 Introduction 3 Scope 3 Executive Summary 3
3D Tool 2.0 Quick Start Guide
 www.tenable.com sales@tenable.com 3D Tool 2.0 Quick Start Guide ABOUT THE 3D TOOL Tenable s 3D Tool is a Windows application that is used to query data from a SecurityCenter 4 server and present it in
www.tenable.com sales@tenable.com 3D Tool 2.0 Quick Start Guide ABOUT THE 3D TOOL Tenable s 3D Tool is a Windows application that is used to query data from a SecurityCenter 4 server and present it in
IBM Security QRadar Vulnerability Manager
 IBM Security QRadar Vulnerability Manager Improve security and compliance by prioritizing security gaps for resolution Highlights Help prevent security breaches by discovering and highlighting high-risk
IBM Security QRadar Vulnerability Manager Improve security and compliance by prioritizing security gaps for resolution Highlights Help prevent security breaches by discovering and highlighting high-risk
Defending the World s Most Secure Enterprises Roy Duckles EMEA Channel Director
 Defending the World s Most Secure Enterprises Roy Duckles EMEA Channel Director rduckles@liebsoft.com +447900576036 2014 by Lieberman Software Corporation. 1 Breach Fatigue 2 Post Breach Facts 100% Of
Defending the World s Most Secure Enterprises Roy Duckles EMEA Channel Director rduckles@liebsoft.com +447900576036 2014 by Lieberman Software Corporation. 1 Breach Fatigue 2 Post Breach Facts 100% Of
Outcome Based Security Monitoring in a Continuous Monitoring World
 Outcome Based Security Monitoring in a Continuous Monitoring World December 2012 Ron Gula Chief Executive Officer / Chief Technology Officer White Paper Copyright 2002-2012 Tenable Network Security, Inc.
Outcome Based Security Monitoring in a Continuous Monitoring World December 2012 Ron Gula Chief Executive Officer / Chief Technology Officer White Paper Copyright 2002-2012 Tenable Network Security, Inc.
AIS Online Tools. Sophia Chen Manager, Account Information Security Singapore August 18, 2005
 AIS Online Tools Sophia Chen Manager, Account Information Security Singapore August 18, 2005 Objectives Vulnerability Scanning what is it? Scanning Technology Overview Step-by-Step Simplified AIS Validation
AIS Online Tools Sophia Chen Manager, Account Information Security Singapore August 18, 2005 Objectives Vulnerability Scanning what is it? Scanning Technology Overview Step-by-Step Simplified AIS Validation
BEST PRACTICES. Systems Management. www.kaspersky.com
 BEST PRACTICES www.kaspersky.com 2 YOUR GUIDE TO SYSTEMS MANAGEMENT BEST PRACTICES. Enhance security and manage complexity using centralized IT management tools. Unpatched vulnerabilities in popular applications
BEST PRACTICES www.kaspersky.com 2 YOUR GUIDE TO SYSTEMS MANAGEMENT BEST PRACTICES. Enhance security and manage complexity using centralized IT management tools. Unpatched vulnerabilities in popular applications
Securing OS Legacy Systems Alexander Rau
 Securing OS Legacy Systems Alexander Rau National Information Security Strategist Sample Agenda 1 Today s IT Challenges 2 Popular OS End of Support & Challenges for IT 3 How to protect Legacy OS systems
Securing OS Legacy Systems Alexander Rau National Information Security Strategist Sample Agenda 1 Today s IT Challenges 2 Popular OS End of Support & Challenges for IT 3 How to protect Legacy OS systems
CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL
 CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL WHAT IS CDM? The continuous stream of high profile cybersecurity breaches demonstrates the need to move beyond purely periodic, compliance-based approaches to
CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL WHAT IS CDM? The continuous stream of high profile cybersecurity breaches demonstrates the need to move beyond purely periodic, compliance-based approaches to
Secunia Vulnerability Intelligence Manager (VIM) 4.0
 Secunia Vulnerability Intelligence Manager (VIM) 4.0 In depth Real-time vulnerability intelligence brought to you on time, every time, by Secunia s renowned research team Introduction Secunia is the world-leading
Secunia Vulnerability Intelligence Manager (VIM) 4.0 In depth Real-time vulnerability intelligence brought to you on time, every time, by Secunia s renowned research team Introduction Secunia is the world-leading
Real World Healthcare Security Exposures. Brian Selfridge, Partner, Meditology Services
 Real World Healthcare Security Exposures Brian Selfridge, Partner, Meditology Services 2 Agenda Introduction Background and Industry Context Anatomy of a Pen Test Top 10 Healthcare Security Exposures Lessons
Real World Healthcare Security Exposures Brian Selfridge, Partner, Meditology Services 2 Agenda Introduction Background and Industry Context Anatomy of a Pen Test Top 10 Healthcare Security Exposures Lessons
Nessus Enterprise for Amazon Web Services (AWS) Installation and Configuration Guide. July 16, 2014 (Revision 2)
 Nessus Enterprise for Amazon Web Services (AWS) Installation and Configuration Guide July 16, 2014 (Revision 2) Table of Contents Introduction... 3 Requirements... 3 Standards and Conventions... 3 Nessus
Nessus Enterprise for Amazon Web Services (AWS) Installation and Configuration Guide July 16, 2014 (Revision 2) Table of Contents Introduction... 3 Requirements... 3 Standards and Conventions... 3 Nessus
Website Security: How to Avoid a Website Breach. Jeff Bell, CISSP, CPHIMS, ACHE Director, IT Security and Risk Services CareTech Solutions
 Website Security: How to Avoid a Website Breach Jeff Bell, CISSP, CPHIMS, ACHE Director, IT Security and Risk Services CareTech Solutions www.caretech.com > 877.700.8324 An enterprise s website is now
Website Security: How to Avoid a Website Breach Jeff Bell, CISSP, CPHIMS, ACHE Director, IT Security and Risk Services CareTech Solutions www.caretech.com > 877.700.8324 An enterprise s website is now
Secret Server Qualys Integration Guide
 Secret Server Qualys Integration Guide Table of Contents Secret Server and Qualys Cloud Platform... 2 Authenticated vs. Unauthenticated Scanning... 2 What are the Advantages?... 2 Integrating Secret Server
Secret Server Qualys Integration Guide Table of Contents Secret Server and Qualys Cloud Platform... 2 Authenticated vs. Unauthenticated Scanning... 2 What are the Advantages?... 2 Integrating Secret Server
