A Multi-Layered Immune Inspired Approach to Data Mining
|
|
|
- Harriet Johnston
- 9 years ago
- Views:
Transcription
1 A Multi-Layered Immune Inspired Approach to Data Mining Thomas Knight and Jon Timmis Computing Laboratory University of Kent at Canterbury Canterbury, Kent, CT2 7NF, United Kingdom {tpk1, Artificial Immune Systems (AIS) have recently been proposed as an additional soft computing paradigm. This paper presents a new immune inspired algorithm, which has been designed to augment a framework for engineering AIS. Initial results have proven to be promising and are detailed here. The new algorithm has shown that it is capable of data compression, representation and clustering. Keywords: Artificial Immune Systems, Data Mining, Unsupervised Machine Learning, Clonal Selection, Immune Networks, Cluster Analysis, Kohonen Networks 1 Introduction Soft Computing has been described as computational systems that exploit tolerance for imprecision, uncertainty, partial truth and approximation [8]. Such systems include artificial neural networks, fuzzy systems, evolutionary algorithms and probabilistic reasoning. Artificial Immune Systems (AIS) have recently been proposed as an additional soft computing paradigm [5]. It has been argued that AIS exhibit similar characteristics to other soft computing paradigms and therefore can be used to complement and augment existing soft computing techniques. AIS can be defined as adaptive systems, inspired by theoretical immunology and observed immune functions, principles and models which are applied to problem solving [4]. This paper presents a new immune inspired algorithm that augments the AIS framework proposed in [4, 5]. Preliminary results on three numerical data sets are given and future directions are discussed. This paper argues that this new algorithm adheres to the soft computing philosophy and therefore proposes this as a novel algorithm with regard to both soft computing and immune inspired algorithms. 2 Context of Work The motivation for this work was to produce an immune inspired system that is capable of continuous learning, identification of clusters within data, automatic stopping criteria and production of simplified maps of the input data. These goals have been identified from some of the shortfalls of the previous work [11]. An additional aim was to develop an algorithm that would augment the framework described in section 2.2 by expanding on previous work outlined in section 2.1. This is done by re-visiting the immune system and looking for new inspiration that can be abstracted to address shortfalls in the previous work. 2.1 Previous Work The natural immune system is interesting from a computational computing perspective as it is distributed, diverse, self-organizing, dynamic and capable of recognition learning and memory [2]. 266 RASC2002
2 An immune inspired data mining algorithm, AINE (Artificial Immune NEtwork) was proposed by work in [11]. The motivation behind this work was to abstract processes and characteristics from the immune system, more specifically the immune network theory [7] to develop a novel unsupervised machine learning algorithm. The main mechanism of AINE is the co-stimulating and suppressing interactions between B-cells that are inspired by Jerne s Immune Network theory and the resultant response of these B-cells to antigenic stimulation. AINEs artificial immune networks were applied to unsupervised machine learning benchmark data and was reported to perform well on benchmark tasks. It was anticipated by the authors that this algorithm would be suitable for continuous learning with initial work showing that stable populations within the networks could be achieved [11]. However, more recent work has shown that these networks suffer strong evolutionary pressure and converge to the strongest class represented in the data [9]. Whilst this is an interesting development that could potentially be applied to optimization, however, with regard to data mining it would not be a preferential outcome. From a continuous learning point-of-view it is more desirable if all patterns persist over time rather than the strongest. In parallel to the work in this paper [10] has since developed a form of the original algorithm that is capable of finding stable clusters. Here, a different population control mechanism based on exponential decay of stimulation levels has been used. This work uses a new resource allocation mechanism and stimulation level calculations. However, one drawback of this work it that there is poor data compression in the final networks. These observations prompted a step back from the existing work to re-evaluate the approaches taken. It was noted that a more holistic approach may provide a better solution in the search for an immune inspired data mining algorithm capable of continuous learning. 2.2 A Framework for Artificial Immune Systems A framework for engineering artificial immune systems has been proposed by [4] as an attempt to formalise the development of artificial immune systems. Here the basic requirements for a AIS or Biologically inspired algorithm algorithms are stated as: A representation for the components of the system; A set of mechanisms to evaluate the interactions of individuals with the environment and each other. The environment is usually simulated by a set of input stimuli, one or more fitness function(s), or other mean(s); Procedures of adaptation that govern the dynamics of the system, i.e. varies over time. how its behavior When one considers the natural immune system in terms of the framework, the representation can be thought of as B-cells, T-cells, antibodies and antigens; the mechanisms that evaluate the interactions are antigenic binding (affinity measures), shape space, feedback mechanisms and procedures for adaption can be though of as; Negative Selection [12], Clonal Selection [1] and The Immune Network Theory [7]. 2.3 Immunology Here, only parts of the adaptive immune systems are going to be discussed and therefore if the reader wishes to know more about the innate immune system, antigen-presenting cells or T-cells, then they are directed to the description of the immune system in [4]. Our bodies are under constant attack by viruses and bacteria that are foreign to our bodies, these are know as antigens. As part of the adaptive immune system a B-cell is capable of recognising free antigens without the assistance of MHC (Major Histocompatibility Complex) molecules. B-cells have 267 RASC2002
3 surface receptors known as antibodies that are antigen specific (will only respond to a specific antigen). On encountering an antigen the B-cell will become stimulated and will proliferate and differentiate into plasma cells that secrete antibody molecules in high volumes. These neutralize the antigen and lead to the removal of the antigen from the system. Some of these activated B-cells and T-cells differentiate into memory cells which remain in the immune system for long periods of time and help produce a more rapid response in the future. Previous work [11] has concentrated on the interactions of B-cells only as described in the immune network theory, however this paper proposes a new algorithm that draws its inspiration from not only B-cells, but the antibodies and memory cells that they produce. Conceptually it is possible to divide the immune system into layers, with each layer having its own specific interactions. Thus, a multi-layered artificial immune system is proposed in the following section. 3 A Multi-layered Artificial Immune System Much of the previous work in the field of artificial immune systems for data mining has been in developing systems based on the interactions of B-cells. Both clonal selection and the immune network theory have been tried with some success [3, 6, 11]. As an addition to these existing techniques, this paper proposes a multi-layered algorithm that is inspired by the clonal selection theory and incorporates a feedback mechanism much like the co-stimulation that is seen in the immune network theory model. The proposed algorithm also incorporates the idea of a primary immune response to handle the event of unknown data being presented to the system. At a more abstract level the immune system can be though of in terms of layers. The algorithm is divided into three layers; A free-antibody layer, a B-cell layer and a memory cell layer. In order to simplify the algorithm T-cell, MHC and APC (Antigen Presenting Cell) interactions are not directly considered within the model, however the signaling action that they employ has been incorporated in part to the feedback mechanism between the free-antibody layer and the B-cell layer. The first level of interactions an antigen has is with the free antibodies generated by the B-cells. This interaction occurs in the free-antibody layer. At the next level we consider the antigen interacting with the B-cells which occurs in the B-cell layer. Finally the memory cells that are produced by the B-cells interact in a memory cell layer. The interactions between the layers are described in Figure 1. A more detailed description of each layer is given in the following sections. Throughout the description of the new algorithm training data will be referred to as antigens, and the free antibodies, B-cells and memory cells all have data items which exist in the same shape space. 3.1 Free-antibody Layer In the free-antibody layer (Figure 1a) the analogy that, upon entry to the immune system an antigenic substance does not get presented to the entire system, only part of it, has been used. As the antigen travels through the system it comes in contact with numerous free-antibodies, some of which are sufficiently similar to bind to the antigen. Whether a free-antibody binds to the antigen is determined by a user defined affinity threshold (σ fab ). Once the antigen pattern has been presented to a percentage of the population (ζ) it is then transferred from the free-antibody layer to the B-cell layer. 3.2 B-cell Layer On entering the B-cell layer (Figure 1b) the antigen is randomly presented each to cell in the B- cell population until it can bind (where the Euclidean distance between the two cells is less than a predefined threshold) to a B-cell. Binding is determined by a user defined affinity threshold 268 RASC2002
4 Free Antibody Layer antibodies B cell Layer Memory Layer antigen antigen memory cells antibodies (a) (b) (c) Figure 1: The three layers of the new algorithm showing the flow of cells between each layer (σ bcell ). The antigen stimulates the B-cell that it is attached to, the amount of stimulation is determined by how many of the free antibodies are attached to that antigen. If the stimulation level exceeds a predefined threshold (σ stim ) then the B-cell will produce a clone that is then mutated using guided affinity maturation. The B-cell also produces a clone that becomes a memory cell which is then added to the memory layer. After stimulation a B-cell will produce free antibodies according to the equation: n f =(S max a (ag,bcell) ) K where n f is the number of free antibodies produced, S max is the maximum possible distance in the data space between two cells, a (ag,bcell) is the affinity between the antigen (ag) and the B-cell (bcell) and K is a constant. Each free antibody is a slight mutant of the original B-cell. If an antigen does not find a B-cell with sufficient affinity to elicit a response then it undergoes a primary response where the antigen data is copied into a new B-cell and added to the B-cell population. This provides new data with an opportunity to be incorporated into the system. 3.3 Memory Layer On entering the memory layer (Figure 1c) the new memory cell binds to all cells in the layer. This is to ascertain if there are any cells that have an affinity below the memory threshold (σ mem ). On encountering the first cell that has an affinity less than σ mem the existing cell is replaced by the new one if the new one has a lower affinity with the antigen that created it in the B-cell layer. 3.4 Population Control A death threshold (σ death ) exists in all layers of the system. If the length of time between the last stimulation of a cell and the current time is greater than σ death, it is removed from the population. 4 Results This section details the preliminary testing that has been performed on the algorithm. The algorithm has been tested on 3 data sets detailed in Table 1. A plot of the 3Circle data can be seen in Figure 2 and the 3D data set known as the doughnut data originates from [3]. The algorithm was run for 500 iterations using a default set of parameters. The parameters used were empirically defined during the initial development of the algorithm. The experiments were repeated 50 times and the population sizes for each layer were recorded on each iteration. The mean population size for each data set was then calculated and the standard deviation recorded. These results are presented in Table 2. Figure 3 shows the resulting pattern in the Memory 269 RASC2002
5 Table 1: Test Data Name Type Dimensions size classes Simulated numeric Circle numeric Doughnut numeric Table 2: Average Mean ( x) and Standard Deviation (σ) of populations sizes within the three layers. Layer Simulated Data 3 Circle Data Doughnuts Data σ x σ x σ x Free Antibody B Cell Memory Layer after 5 iterations of the algorithm. It can be seen that after a short period of time the pattern is visually representative of the original data. By looking at the mean number of cells in the Memory Layer and the comparing with the original number of data items in the data set we can see that the algorithm achieves good compression ratios (91.6% for the 3 circle data and 66.5% for the doughnut data). The tests have also showed that over 500 iterations the system does not suffer from the loss of information as seen in the AINE system. Figure 2: The 3 circle training data set (600 items) in normalised form Figure 3: Patterns in the memory layer evolved by the new algorithm after 5 iterations (58 items) 5 Discussion Previous work has shown that aspects of the human immune system lend themselves to solving computational problems such as data mining. Previously, an artificial immune system for data mining (AINE) [11] was created and was used with some success on benchmark data. However, more recent work has shown that AINE does not perform as the the authors intended it to. It was identified that there were problems concerning the stability of networks produced and how an AIS that produces stable networks is desirable. Parallel to this work [10] has re-designed AINE and succeeded in producing the performance originally intended. The relative youth of the field also has identified that there may well be benefits from trying different solutions to those that already exist. To this end, a new algorithm has been devised that seeks to produce stable results and explores new ideas. The design has also been based on the framework for developing AIS and is proposed as an augmentation for the Procedures for Adaption. It can also be said to adhere to the Soft Computing philosophy because it exploits the imprecision, 270 RASC2002
6 approximation and uncertainty of the natural immune system. 6 Future Work Future work will comprise of further evaluation and testing of algorithm on more benchmark data sets. Comparisons with other techniques will be made and a full investigation of the parameters undertaken. Analysis of the clusters generated will also be undertaken to establish how accurate the results are. 7 Acknowledgements Thomas Knight would like to thank SUN TM Microsystems for their continued financial support for his PhD Studies. References [1] F M Burnet. The Clonal Selection Theory of Immunity. Vanderbilt University Press, Nashville, TN, [2] D Dasgupta. Artificial Immune Systems and their Applications, chapter An overview of Artificial Immune Systems and their Applications, pages Springer, [3] L N de Castro and F J Von Zuben. Data Mining: A Heuristic Approach, chapter ainet: An Artificial Immune Network for Data Analysis, pages Idea Group Publishing, London, UK, [4] L.N. de Castro and J. Timmis. Artificial Immune Systems: A New Computational Approach. Springer-Verlag, London. UK., September [5] L.N de Castro and J. Timmis. Artificial Immune Systems as a Novel Soft Computing Paradigm. Soft Computing, 7(7), July [6] J E Hunt and D E Cooke. Learning using an artificial immune system. Journal of Network and Computer Applications, 19: , [7] N K Jerne. Towards a Network theory of the Immune System. Annals of Immunology, 125c: , [8] Jin. What is soft computing [9] T Knight and J Timmis. AINE: An Immunological Approach to Data Mining. In N Cercone, T Lin, and Xindon Wu, editors, IEEE International Conference on Data Mining, pages , San Jose, CA. USA, December IEEE. [10] M Neal. An artificial immune system for continuous analysis of time-varying data. In 1st International Conference on Artificial Immune Systems (ICARIS), pages 0 2, Canterbury, UK, [11] J Timmis and M Neal. A resource limited artificial immune system for data analysis. Knowledge Based Systems, 14(3-4): , June [12] I R Tizzard. Immunolgy An Introduction. Saunders College Publishing, 4th edition, RASC2002
Artificial Immune Systems and Applications for Computer Security
 Università degli Studi di Milano Dipartimento di Tecnologie dell Informazione Artificial Immune Systems and Applications for Computer Security Antonia Azzini and Stefania Marrara Artificial Immune System
Università degli Studi di Milano Dipartimento di Tecnologie dell Informazione Artificial Immune Systems and Applications for Computer Security Antonia Azzini and Stefania Marrara Artificial Immune System
Computational intelligence in intrusion detection systems
 Computational intelligence in intrusion detection systems --- An introduction to an introduction Rick Chang @ TEIL Reference The use of computational intelligence in intrusion detection systems : A review
Computational intelligence in intrusion detection systems --- An introduction to an introduction Rick Chang @ TEIL Reference The use of computational intelligence in intrusion detection systems : A review
specific B cells Humoral immunity lymphocytes antibodies B cells bone marrow Cell-mediated immunity: T cells antibodies proteins
 Adaptive Immunity Chapter 17: Adaptive (specific) Immunity Bio 139 Dr. Amy Rogers Host defenses that are specific to a particular infectious agent Can be innate or genetic for humans as a group: most microbes
Adaptive Immunity Chapter 17: Adaptive (specific) Immunity Bio 139 Dr. Amy Rogers Host defenses that are specific to a particular infectious agent Can be innate or genetic for humans as a group: most microbes
[email protected]. Keywords - Algorithm, Artificial immune system, E-mail Classification, Non-Spam, Spam
 An Improved AIS Based E-mail Classification Technique for Spam Detection Ismaila Idris Dept of Cyber Security Science, Fed. Uni. Of Tech. Minna, Niger State [email protected] Abdulhamid Shafi i
An Improved AIS Based E-mail Classification Technique for Spam Detection Ismaila Idris Dept of Cyber Security Science, Fed. Uni. Of Tech. Minna, Niger State [email protected] Abdulhamid Shafi i
2) Macrophages function to engulf and present antigen to other immune cells.
 Immunology The immune system has specificity and memory. It specifically recognizes different antigens and has memory for these same antigens the next time they are encountered. The Cellular Components
Immunology The immune system has specificity and memory. It specifically recognizes different antigens and has memory for these same antigens the next time they are encountered. The Cellular Components
T Cell Maturation,Activation and Differentiation
 T Cell Maturation,Activation and Differentiation Positive Selection- In thymus, permits survival of only those T cells whose TCRs recognize self- MHC molecules (self-mhc restriction) Negative Selection-
T Cell Maturation,Activation and Differentiation Positive Selection- In thymus, permits survival of only those T cells whose TCRs recognize self- MHC molecules (self-mhc restriction) Negative Selection-
Chapter 43: The Immune System
 Name Period Our students consider this chapter to be a particularly challenging and important one. Expect to work your way slowly through the first three concepts. Take particular care with Concepts 43.2
Name Period Our students consider this chapter to be a particularly challenging and important one. Expect to work your way slowly through the first three concepts. Take particular care with Concepts 43.2
Name (print) Name (signature) Period. (Total 30 points)
 AP Biology Worksheet Chapter 43 The Immune System Lambdin April 4, 2011 Due Date: Thurs. April 7, 2011 You may use the following: Text Notes Power point Internet One other person in class "On my honor,
AP Biology Worksheet Chapter 43 The Immune System Lambdin April 4, 2011 Due Date: Thurs. April 7, 2011 You may use the following: Text Notes Power point Internet One other person in class "On my honor,
Optimization Algorithms in Function of Binary Character Recognition
 Optimization Algorithms in Function of Binary Character Recognition Petar Čisar 1, Sanja Maravić Čisar 2, Dane Subošić 1, Predrag Đikanović 3, Slaviša Đukanović 3 1 Academy of Criminalistic and Police
Optimization Algorithms in Function of Binary Character Recognition Petar Čisar 1, Sanja Maravić Čisar 2, Dane Subošić 1, Predrag Đikanović 3, Slaviša Đukanović 3 1 Academy of Criminalistic and Police
The Body s Defenses CHAPTER 24
 CHAPTER 24 The Body s Defenses PowerPoint Lectures for Essential Biology, Third Edition Neil Campbell, Jane Reece, and Eric Simon Essential Biology with Physiology, Second Edition Neil Campbell, Jane Reece,
CHAPTER 24 The Body s Defenses PowerPoint Lectures for Essential Biology, Third Edition Neil Campbell, Jane Reece, and Eric Simon Essential Biology with Physiology, Second Edition Neil Campbell, Jane Reece,
An Artificial Immune Model for Network Intrusion Detection
 An Artificial Immune Model for Network Intrusion Detection Jungwon Kim and Peter Bentley Department of Computer Science, University Collge London Gower Street, London, WC1E 6BT, U. K. Phone: +44-171-380-7329,
An Artificial Immune Model for Network Intrusion Detection Jungwon Kim and Peter Bentley Department of Computer Science, University Collge London Gower Street, London, WC1E 6BT, U. K. Phone: +44-171-380-7329,
Self Organizing Maps: Fundamentals
 Self Organizing Maps: Fundamentals Introduction to Neural Networks : Lecture 16 John A. Bullinaria, 2004 1. What is a Self Organizing Map? 2. Topographic Maps 3. Setting up a Self Organizing Map 4. Kohonen
Self Organizing Maps: Fundamentals Introduction to Neural Networks : Lecture 16 John A. Bullinaria, 2004 1. What is a Self Organizing Map? 2. Topographic Maps 3. Setting up a Self Organizing Map 4. Kohonen
The Immune System: A Tutorial
 The Immune System: A Tutorial Modeling and Simulation of Biological Systems 21-366B Shlomo Ta asan Images taken from http://rex.nci.nih.gov/behindthenews/uis/uisframe.htm http://copewithcytokines.de/ The
The Immune System: A Tutorial Modeling and Simulation of Biological Systems 21-366B Shlomo Ta asan Images taken from http://rex.nci.nih.gov/behindthenews/uis/uisframe.htm http://copewithcytokines.de/ The
Comparison of Supervised and Unsupervised Learning Classifiers for Travel Recommendations
 Volume 3, No. 8, August 2012 Journal of Global Research in Computer Science REVIEW ARTICLE Available Online at www.jgrcs.info Comparison of Supervised and Unsupervised Learning Classifiers for Travel Recommendations
Volume 3, No. 8, August 2012 Journal of Global Research in Computer Science REVIEW ARTICLE Available Online at www.jgrcs.info Comparison of Supervised and Unsupervised Learning Classifiers for Travel Recommendations
International Journal of Advance Foundation and Research in Computer (IJAFRC) Volume 1, Issue 9, September 2014. ISSN 2348 4853.
 A Review on Optimization in Web Page Classification. Nikita Sahu, Dr. R. K. Kapoor Department of Computer Engineering & Application, NITTTR, Bhopal M.P., INDIA Associate Professor, Department of Computer
A Review on Optimization in Web Page Classification. Nikita Sahu, Dr. R. K. Kapoor Department of Computer Engineering & Application, NITTTR, Bhopal M.P., INDIA Associate Professor, Department of Computer
EFFICIENT DATA PRE-PROCESSING FOR DATA MINING
 EFFICIENT DATA PRE-PROCESSING FOR DATA MINING USING NEURAL NETWORKS JothiKumar.R 1, Sivabalan.R.V 2 1 Research scholar, Noorul Islam University, Nagercoil, India Assistant Professor, Adhiparasakthi College
EFFICIENT DATA PRE-PROCESSING FOR DATA MINING USING NEURAL NETWORKS JothiKumar.R 1, Sivabalan.R.V 2 1 Research scholar, Noorul Islam University, Nagercoil, India Assistant Professor, Adhiparasakthi College
Microbiology AN INTRODUCTION EIGHTH EDITION
 TORTORA FUNKE CASE Microbiology AN INTRODUCTION EIGHTH EDITION Differentiate between innate and acquired immunity. Chapter 17 Specific Defenses of the Host: The Immune Response B.E Pruitt & Jane J. Stein
TORTORA FUNKE CASE Microbiology AN INTRODUCTION EIGHTH EDITION Differentiate between innate and acquired immunity. Chapter 17 Specific Defenses of the Host: The Immune Response B.E Pruitt & Jane J. Stein
Chapter 12 Discovering New Knowledge Data Mining
 Chapter 12 Discovering New Knowledge Data Mining Becerra-Fernandez, et al. -- Knowledge Management 1/e -- 2004 Prentice Hall Additional material 2007 Dekai Wu Chapter Objectives Introduce the student to
Chapter 12 Discovering New Knowledge Data Mining Becerra-Fernandez, et al. -- Knowledge Management 1/e -- 2004 Prentice Hall Additional material 2007 Dekai Wu Chapter Objectives Introduce the student to
HUMORAL IMMUNE RE- SPONSES: ACTIVATION OF B CELLS AND ANTIBODIES JASON CYSTER SECTION 13
 SECTION 13 HUMORAL IMMUNE RE- SPONSES: ACTIVATION OF B CELLS AND ANTIBODIES CONTACT INFORMATION Jason Cyster, PhD (Email) READING Basic Immunology: Functions and Disorders of the Immune System. Abbas,
SECTION 13 HUMORAL IMMUNE RE- SPONSES: ACTIVATION OF B CELLS AND ANTIBODIES CONTACT INFORMATION Jason Cyster, PhD (Email) READING Basic Immunology: Functions and Disorders of the Immune System. Abbas,
A DETECTOR GENERATING ALGORITHM FOR INTRUSION DETECTION INSPIRED BY ARTIFICIAL IMMUNE SYSTEM
 A DETECTOR GENERATING ALGORITHM FOR INTRUSION DETECTION INSPIRED BY ARTIFICIAL IMMUNE SYSTEM Walid Mohamed Alsharafi and Mohd Nizam Omar Inter Networks Research Laboratory, School of Computing, College
A DETECTOR GENERATING ALGORITHM FOR INTRUSION DETECTION INSPIRED BY ARTIFICIAL IMMUNE SYSTEM Walid Mohamed Alsharafi and Mohd Nizam Omar Inter Networks Research Laboratory, School of Computing, College
LESSON 3: ANTIBODIES/BCR/B-CELL RESPONSES
 Introduction to immunology. LESSON 3: ANTIBODIES/BCR/B-CELL RESPONSES Today we will get to know: The antibodies How antibodies are produced, their classes and their maturation processes Antigen recognition
Introduction to immunology. LESSON 3: ANTIBODIES/BCR/B-CELL RESPONSES Today we will get to know: The antibodies How antibodies are produced, their classes and their maturation processes Antigen recognition
MANAGING QUEUE STABILITY USING ART2 IN ACTIVE QUEUE MANAGEMENT FOR CONGESTION CONTROL
 MANAGING QUEUE STABILITY USING ART2 IN ACTIVE QUEUE MANAGEMENT FOR CONGESTION CONTROL G. Maria Priscilla 1 and C. P. Sumathi 2 1 S.N.R. Sons College (Autonomous), Coimbatore, India 2 SDNB Vaishnav College
MANAGING QUEUE STABILITY USING ART2 IN ACTIVE QUEUE MANAGEMENT FOR CONGESTION CONTROL G. Maria Priscilla 1 and C. P. Sumathi 2 1 S.N.R. Sons College (Autonomous), Coimbatore, India 2 SDNB Vaishnav College
Modelling and analysis of T-cell epitope screening data.
 Modelling and analysis of T-cell epitope screening data. Tim Beißbarth 2, Jason A. Tye-Din 1, Gordon K. Smyth 1, Robert P. Anderson 1 and Terence P. Speed 1 1 WEHI, 1G Royal Parade, Parkville, VIC 3050,
Modelling and analysis of T-cell epitope screening data. Tim Beißbarth 2, Jason A. Tye-Din 1, Gordon K. Smyth 1, Robert P. Anderson 1 and Terence P. Speed 1 1 WEHI, 1G Royal Parade, Parkville, VIC 3050,
Core Topic 2. The immune system and how vaccines work
 Core Topic 2 The immune system and how vaccines work Learning outcome To be able to describe in outline the immune system and how vaccines work in individuals and populations Learning objectives Explain
Core Topic 2 The immune system and how vaccines work Learning outcome To be able to describe in outline the immune system and how vaccines work in individuals and populations Learning objectives Explain
THREE DIMENSIONAL REPRESENTATION OF AMINO ACID CHARAC- TERISTICS
 THREE DIMENSIONAL REPRESENTATION OF AMINO ACID CHARAC- TERISTICS O.U. Sezerman 1, R. Islamaj 2, E. Alpaydin 2 1 Laborotory of Computational Biology, Sabancı University, Istanbul, Turkey. 2 Computer Engineering
THREE DIMENSIONAL REPRESENTATION OF AMINO ACID CHARAC- TERISTICS O.U. Sezerman 1, R. Islamaj 2, E. Alpaydin 2 1 Laborotory of Computational Biology, Sabancı University, Istanbul, Turkey. 2 Computer Engineering
2006 7.012 Problem Set 6 KEY
 2006 7.012 Problem Set 6 KEY ** Due before 5 PM on WEDNESDAY, November 22, 2006. ** Turn answers in to the box outside of 68-120. PLEASE WRITE YOUR ANSWERS ON THIS PRINTOUT. 1. You create an artificial
2006 7.012 Problem Set 6 KEY ** Due before 5 PM on WEDNESDAY, November 22, 2006. ** Turn answers in to the box outside of 68-120. PLEASE WRITE YOUR ANSWERS ON THIS PRINTOUT. 1. You create an artificial
Open Access Research on Application of Neural Network in Computer Network Security Evaluation. Shujuan Jin *
 Send Orders for Reprints to [email protected] 766 The Open Electrical & Electronic Engineering Journal, 2014, 8, 766-771 Open Access Research on Application of Neural Network in Computer Network
Send Orders for Reprints to [email protected] 766 The Open Electrical & Electronic Engineering Journal, 2014, 8, 766-771 Open Access Research on Application of Neural Network in Computer Network
Introduction. Swarm Intelligence - Thiemo Krink EVALife Group, Dept. of Computer Science, University of Aarhus
 Swarm Intelligence - Thiemo Krink EVALife Group, Dept. of Computer Science, University of Aarhus Why do we need new computing techniques? The computer revolution changed human societies: communication
Swarm Intelligence - Thiemo Krink EVALife Group, Dept. of Computer Science, University of Aarhus Why do we need new computing techniques? The computer revolution changed human societies: communication
Basics of Immunology
 Basics of Immunology 2 Basics of Immunology What is the immune system? Biological mechanism for identifying and destroying pathogens within a larger organism. Pathogens: agents that cause disease Bacteria,
Basics of Immunology 2 Basics of Immunology What is the immune system? Biological mechanism for identifying and destroying pathogens within a larger organism. Pathogens: agents that cause disease Bacteria,
Artificial Intelligence and Machine Learning Models
 Using Artificial Intelligence and Machine Learning Techniques. Some Preliminary Ideas. Presentation to CWiPP 1/8/2013 ICOSS Mark Tomlinson Artificial Intelligence Models Very experimental, but timely?
Using Artificial Intelligence and Machine Learning Techniques. Some Preliminary Ideas. Presentation to CWiPP 1/8/2013 ICOSS Mark Tomlinson Artificial Intelligence Models Very experimental, but timely?
An Efficient Three-phase Email Spam Filtering Technique
 An Efficient Three-phase Email Filtering Technique Tarek M. Mahmoud 1 *, Alaa Ismail El-Nashar 2 *, Tarek Abd-El-Hafeez 3 *, Marwa Khairy 4 * 1, 2, 3 Faculty of science, Computer Sci. Dept., Minia University,
An Efficient Three-phase Email Filtering Technique Tarek M. Mahmoud 1 *, Alaa Ismail El-Nashar 2 *, Tarek Abd-El-Hafeez 3 *, Marwa Khairy 4 * 1, 2, 3 Faculty of science, Computer Sci. Dept., Minia University,
How To Use Neural Networks In Data Mining
 International Journal of Electronics and Computer Science Engineering 1449 Available Online at www.ijecse.org ISSN- 2277-1956 Neural Networks in Data Mining Priyanka Gaur Department of Information and
International Journal of Electronics and Computer Science Engineering 1449 Available Online at www.ijecse.org ISSN- 2277-1956 Neural Networks in Data Mining Priyanka Gaur Department of Information and
NEUROEVOLUTION OF AUTO-TEACHING ARCHITECTURES
 NEUROEVOLUTION OF AUTO-TEACHING ARCHITECTURES EDWARD ROBINSON & JOHN A. BULLINARIA School of Computer Science, University of Birmingham Edgbaston, Birmingham, B15 2TT, UK [email protected] This
NEUROEVOLUTION OF AUTO-TEACHING ARCHITECTURES EDWARD ROBINSON & JOHN A. BULLINARIA School of Computer Science, University of Birmingham Edgbaston, Birmingham, B15 2TT, UK [email protected] This
D A T A M I N I N G C L A S S I F I C A T I O N
 D A T A M I N I N G C L A S S I F I C A T I O N FABRICIO VOZNIKA LEO NARDO VIA NA INTRODUCTION Nowadays there is huge amount of data being collected and stored in databases everywhere across the globe.
D A T A M I N I N G C L A S S I F I C A T I O N FABRICIO VOZNIKA LEO NARDO VIA NA INTRODUCTION Nowadays there is huge amount of data being collected and stored in databases everywhere across the globe.
Hapten - a small molecule that is antigenic but not (by itself) immunogenic.
 Chapter 3. Antigens Terminology: Antigen: Substances that can be recognized by the surface antibody (B cells) or by the TCR (T cells) when associated with MHC molecules Immunogenicity VS Antigenicity:
Chapter 3. Antigens Terminology: Antigen: Substances that can be recognized by the surface antibody (B cells) or by the TCR (T cells) when associated with MHC molecules Immunogenicity VS Antigenicity:
NEURAL NETWORK FUNDAMENTALS WITH GRAPHS, ALGORITHMS, AND APPLICATIONS
 NEURAL NETWORK FUNDAMENTALS WITH GRAPHS, ALGORITHMS, AND APPLICATIONS N. K. Bose HRB-Systems Professor of Electrical Engineering The Pennsylvania State University, University Park P. Liang Associate Professor
NEURAL NETWORK FUNDAMENTALS WITH GRAPHS, ALGORITHMS, AND APPLICATIONS N. K. Bose HRB-Systems Professor of Electrical Engineering The Pennsylvania State University, University Park P. Liang Associate Professor
B Cell Generation, Activation & Differentiation. B cell maturation
 B Cell Generation, Activation & Differentiation Naïve B cells- have not encountered Ag. Have IgM and IgD on cell surface : have same binding VDJ regions but different constant region leaves bone marrow
B Cell Generation, Activation & Differentiation Naïve B cells- have not encountered Ag. Have IgM and IgD on cell surface : have same binding VDJ regions but different constant region leaves bone marrow
Candy Antigens and Antibodies
 LAB ACTIVITY: Candy Antigens and Antibodies TEACHER S EDITION Curricular Links: Biology 20, Science 30 Class Time: 1 period Suggested Answers: Question 1: What is the main function of red blood cells?
LAB ACTIVITY: Candy Antigens and Antibodies TEACHER S EDITION Curricular Links: Biology 20, Science 30 Class Time: 1 period Suggested Answers: Question 1: What is the main function of red blood cells?
6.2.8 Neural networks for data mining
 6.2.8 Neural networks for data mining Walter Kosters 1 In many application areas neural networks are known to be valuable tools. This also holds for data mining. In this chapter we discuss the use of neural
6.2.8 Neural networks for data mining Walter Kosters 1 In many application areas neural networks are known to be valuable tools. This also holds for data mining. In this chapter we discuss the use of neural
Activation and effector functions of HMI
 Activation and effector functions of HMI Hathairat Thananchai, DPhil Department of Microbiology Faculty of Medicine Chiang Mai University 25 August 2015 ว ตถ ประสงค หล งจากช วโมงบรรยายน แล วน กศ กษาสามารถ
Activation and effector functions of HMI Hathairat Thananchai, DPhil Department of Microbiology Faculty of Medicine Chiang Mai University 25 August 2015 ว ตถ ประสงค หล งจากช วโมงบรรยายน แล วน กศ กษาสามารถ
PLAANN as a Classification Tool for Customer Intelligence in Banking
 PLAANN as a Classification Tool for Customer Intelligence in Banking EUNITE World Competition in domain of Intelligent Technologies The Research Report Ireneusz Czarnowski and Piotr Jedrzejowicz Department
PLAANN as a Classification Tool for Customer Intelligence in Banking EUNITE World Competition in domain of Intelligent Technologies The Research Report Ireneusz Czarnowski and Piotr Jedrzejowicz Department
REFLECTIONS ON THE USE OF BIG DATA FOR STATISTICAL PRODUCTION
 REFLECTIONS ON THE USE OF BIG DATA FOR STATISTICAL PRODUCTION Pilar Rey del Castillo May 2013 Introduction The exploitation of the vast amount of data originated from ICT tools and referring to a big variety
REFLECTIONS ON THE USE OF BIG DATA FOR STATISTICAL PRODUCTION Pilar Rey del Castillo May 2013 Introduction The exploitation of the vast amount of data originated from ICT tools and referring to a big variety
Comparison of K-means and Backpropagation Data Mining Algorithms
 Comparison of K-means and Backpropagation Data Mining Algorithms Nitu Mathuriya, Dr. Ashish Bansal Abstract Data mining has got more and more mature as a field of basic research in computer science and
Comparison of K-means and Backpropagation Data Mining Algorithms Nitu Mathuriya, Dr. Ashish Bansal Abstract Data mining has got more and more mature as a field of basic research in computer science and
Data Mining and Soft Computing. Francisco Herrera
 Francisco Herrera Research Group on Soft Computing and Information Intelligent Systems (SCI 2 S) Dept. of Computer Science and A.I. University of Granada, Spain Email: [email protected] http://sci2s.ugr.es
Francisco Herrera Research Group on Soft Computing and Information Intelligent Systems (SCI 2 S) Dept. of Computer Science and A.I. University of Granada, Spain Email: [email protected] http://sci2s.ugr.es
An Introduction to Neural Networks
 An Introduction to Vincent Cheung Kevin Cannons Signal & Data Compression Laboratory Electrical & Computer Engineering University of Manitoba Winnipeg, Manitoba, Canada Advisor: Dr. W. Kinsner May 27,
An Introduction to Vincent Cheung Kevin Cannons Signal & Data Compression Laboratory Electrical & Computer Engineering University of Manitoba Winnipeg, Manitoba, Canada Advisor: Dr. W. Kinsner May 27,
UNSUPERVISED MACHINE LEARNING TECHNIQUES IN GENOMICS
 UNSUPERVISED MACHINE LEARNING TECHNIQUES IN GENOMICS Dwijesh C. Mishra I.A.S.R.I., Library Avenue, New Delhi-110 012 [email protected] What is Learning? "Learning denotes changes in a system that enable
UNSUPERVISED MACHINE LEARNING TECHNIQUES IN GENOMICS Dwijesh C. Mishra I.A.S.R.I., Library Avenue, New Delhi-110 012 [email protected] What is Learning? "Learning denotes changes in a system that enable
The immune system. Bone marrow. Thymus. Spleen. Bone marrow. NK cell. B-cell. T-cell. Basophil Neutrophil. Eosinophil. Myeloid progenitor
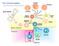 The immune system Basophil Neutrophil Bone marrow Eosinophil Myeloid progenitor Dendritic cell Pluripotent Stem cell Lymphoid progenitor Platelets Bone marrow Thymus NK cell T-cell B-cell Spleen Cancer
The immune system Basophil Neutrophil Bone marrow Eosinophil Myeloid progenitor Dendritic cell Pluripotent Stem cell Lymphoid progenitor Platelets Bone marrow Thymus NK cell T-cell B-cell Spleen Cancer
Supplemental Material CBE Life Sciences Education. Su et al.
 Supplemental Material CBE Life Sciences Education Su et al. APPENDIX Human Body's Immune System Test This test consists of 31 questions, with only 1 answer to be selected for each question. Please select
Supplemental Material CBE Life Sciences Education Su et al. APPENDIX Human Body's Immune System Test This test consists of 31 questions, with only 1 answer to be selected for each question. Please select
Antibody Structure, and the Generation of B-cell Diversity CHAPTER 4 04/05/15. Different Immunoglobulins
 Antibody Structure, and the Generation of B-cell Diversity B cells recognize their antigen without needing an antigen presenting cell CHAPTER 4 Structure of Immunoglobulin G Different Immunoglobulins Differences
Antibody Structure, and the Generation of B-cell Diversity B cells recognize their antigen without needing an antigen presenting cell CHAPTER 4 Structure of Immunoglobulin G Different Immunoglobulins Differences
Immunity. Humans have three types of immunity innate, adaptive, and passive: Innate Immunity
 Immunity Humans have three types of immunity innate, adaptive, and passive: Innate Immunity Everyone is born with innate (or natural) immunity, a type of general protection. Many of the germs that affect
Immunity Humans have three types of immunity innate, adaptive, and passive: Innate Immunity Everyone is born with innate (or natural) immunity, a type of general protection. Many of the germs that affect
Introduction to Machine Learning and Data Mining. Prof. Dr. Igor Trajkovski [email protected]
 Introduction to Machine Learning and Data Mining Prof. Dr. Igor Trakovski [email protected] Neural Networks 2 Neural Networks Analogy to biological neural systems, the most robust learning systems
Introduction to Machine Learning and Data Mining Prof. Dr. Igor Trakovski [email protected] Neural Networks 2 Neural Networks Analogy to biological neural systems, the most robust learning systems
EM Clustering Approach for Multi-Dimensional Analysis of Big Data Set
 EM Clustering Approach for Multi-Dimensional Analysis of Big Data Set Amhmed A. Bhih School of Electrical and Electronic Engineering Princy Johnson School of Electrical and Electronic Engineering Martin
EM Clustering Approach for Multi-Dimensional Analysis of Big Data Set Amhmed A. Bhih School of Electrical and Electronic Engineering Princy Johnson School of Electrical and Electronic Engineering Martin
B cell activation and Humoral Immunity
 B cell activation and Humoral Immunity Humoral immunity is mediated by secreted antibodies and its physiological function is defense against extracellular microbes (including viruses) and microbial exotoxins.
B cell activation and Humoral Immunity Humoral immunity is mediated by secreted antibodies and its physiological function is defense against extracellular microbes (including viruses) and microbial exotoxins.
Visualization of Breast Cancer Data by SOM Component Planes
 International Journal of Science and Technology Volume 3 No. 2, February, 2014 Visualization of Breast Cancer Data by SOM Component Planes P.Venkatesan. 1, M.Mullai 2 1 Department of Statistics,NIRT(Indian
International Journal of Science and Technology Volume 3 No. 2, February, 2014 Visualization of Breast Cancer Data by SOM Component Planes P.Venkatesan. 1, M.Mullai 2 1 Department of Statistics,NIRT(Indian
Objectives. Immunologic Methods. Objectives. Immunology vs. Serology. Cross Reactivity. Sensitivity and Specificity. Definitions
 Immunologic Methods Part One Definitions Part Two Antigen-Antibody Reactions CLS 420 Clinical Immunology and Molecular Diagnostics Kathy Trudell MLS (ASCP) CM SBB CM [email protected] Discuss the
Immunologic Methods Part One Definitions Part Two Antigen-Antibody Reactions CLS 420 Clinical Immunology and Molecular Diagnostics Kathy Trudell MLS (ASCP) CM SBB CM [email protected] Discuss the
Learning in Abstract Memory Schemes for Dynamic Optimization
 Fourth International Conference on Natural Computation Learning in Abstract Memory Schemes for Dynamic Optimization Hendrik Richter HTWK Leipzig, Fachbereich Elektrotechnik und Informationstechnik, Institut
Fourth International Conference on Natural Computation Learning in Abstract Memory Schemes for Dynamic Optimization Hendrik Richter HTWK Leipzig, Fachbereich Elektrotechnik und Informationstechnik, Institut
Depth and Excluded Courses
 Depth and Excluded Courses Depth Courses for Communication, Control, and Signal Processing EECE 5576 Wireless Communication Systems 4 SH EECE 5580 Classical Control Systems 4 SH EECE 5610 Digital Control
Depth and Excluded Courses Depth Courses for Communication, Control, and Signal Processing EECE 5576 Wireless Communication Systems 4 SH EECE 5580 Classical Control Systems 4 SH EECE 5610 Digital Control
Clustering & Visualization
 Chapter 5 Clustering & Visualization Clustering in high-dimensional databases is an important problem and there are a number of different clustering paradigms which are applicable to high-dimensional data.
Chapter 5 Clustering & Visualization Clustering in high-dimensional databases is an important problem and there are a number of different clustering paradigms which are applicable to high-dimensional data.
A Local Stability of Mathematical Models for Cancer Treatment by Using Gene Therapy
 International Journal of Modeling Optimization, Vol 5, No 3, June 2015 A Local Stability of Mathematical Models for Cancer Treatment by Using Gene Therapy Dwi Lestari Ratnasari Dwi Ambarwati Abstract This
International Journal of Modeling Optimization, Vol 5, No 3, June 2015 A Local Stability of Mathematical Models for Cancer Treatment by Using Gene Therapy Dwi Lestari Ratnasari Dwi Ambarwati Abstract This
Data Mining and Neural Networks in Stata
 Data Mining and Neural Networks in Stata 2 nd Italian Stata Users Group Meeting Milano, 10 October 2005 Mario Lucchini e Maurizo Pisati Università di Milano-Bicocca [email protected] [email protected]
Data Mining and Neural Networks in Stata 2 nd Italian Stata Users Group Meeting Milano, 10 October 2005 Mario Lucchini e Maurizo Pisati Università di Milano-Bicocca [email protected] [email protected]
About the Author. The Role of Artificial Intelligence in Software Engineering. Brief History of AI. Introduction 2/27/2013
 About the Author The Role of Artificial Intelligence in Software Engineering By: Mark Harman Presented by: Jacob Lear Mark Harman is a Professor of Software Engineering at University College London Director
About the Author The Role of Artificial Intelligence in Software Engineering By: Mark Harman Presented by: Jacob Lear Mark Harman is a Professor of Software Engineering at University College London Director
10. T and B cells are types of a. endocrine cells. c. lymphocytes. b. platelets. d. complement cells.
 Virus and Immune System Review Directions: Write your answers on a separate piece of paper. 1. Why does a cut in the skin threaten the body s nonspecific defenses against disease? a. If a cut bleeds, disease-fighting
Virus and Immune System Review Directions: Write your answers on a separate piece of paper. 1. Why does a cut in the skin threaten the body s nonspecific defenses against disease? a. If a cut bleeds, disease-fighting
Network Intrusion Detection System and Its Cognitive Ability based on Artificial Immune Model WangLinjing1, ZhangHan2
 3rd International Conference on Machinery, Materials and Information Technology Applications (ICMMITA 2015) Network Intrusion Detection System and Its Cognitive Ability based on Artificial Immune Model
3rd International Conference on Machinery, Materials and Information Technology Applications (ICMMITA 2015) Network Intrusion Detection System and Its Cognitive Ability based on Artificial Immune Model
Improving Decision Making and Managing Knowledge
 Improving Decision Making and Managing Knowledge Decision Making and Information Systems Information Requirements of Key Decision-Making Groups in a Firm Senior managers, middle managers, operational managers,
Improving Decision Making and Managing Knowledge Decision Making and Information Systems Information Requirements of Key Decision-Making Groups in a Firm Senior managers, middle managers, operational managers,
Online k-means Clustering of Nonstationary Data
 15.097 Prediction Proect Report Online -Means Clustering of Nonstationary Data Angie King May 17, 2012 1 Introduction and Motivation Machine learning algorithms often assume we have all our data before
15.097 Prediction Proect Report Online -Means Clustering of Nonstationary Data Angie King May 17, 2012 1 Introduction and Motivation Machine learning algorithms often assume we have all our data before
3 An Illustrative Example
 Objectives An Illustrative Example Objectives - Theory and Examples -2 Problem Statement -2 Perceptron - Two-Input Case -4 Pattern Recognition Example -5 Hamming Network -8 Feedforward Layer -8 Recurrent
Objectives An Illustrative Example Objectives - Theory and Examples -2 Problem Statement -2 Perceptron - Two-Input Case -4 Pattern Recognition Example -5 Hamming Network -8 Feedforward Layer -8 Recurrent
ultra fast SOM using CUDA
 ultra fast SOM using CUDA SOM (Self-Organizing Map) is one of the most popular artificial neural network algorithms in the unsupervised learning category. Sijo Mathew Preetha Joy Sibi Rajendra Manoj A
ultra fast SOM using CUDA SOM (Self-Organizing Map) is one of the most popular artificial neural network algorithms in the unsupervised learning category. Sijo Mathew Preetha Joy Sibi Rajendra Manoj A
The role of IBV proteins in protection: cellular immune responses. COST meeting WG2 + WG3 Budapest, Hungary, 2015
 The role of IBV proteins in protection: cellular immune responses COST meeting WG2 + WG3 Budapest, Hungary, 2015 1 Presentation include: Laboratory results Literature summary Role of T cells in response
The role of IBV proteins in protection: cellular immune responses COST meeting WG2 + WG3 Budapest, Hungary, 2015 1 Presentation include: Laboratory results Literature summary Role of T cells in response
01219211 Software Development Training Camp 1 (0-3) Prerequisite : 01204214 Program development skill enhancement camp, at least 48 person-hours.
 (International Program) 01219141 Object-Oriented Modeling and Programming 3 (3-0) Object concepts, object-oriented design and analysis, object-oriented analysis relating to developing conceptual models
(International Program) 01219141 Object-Oriented Modeling and Programming 3 (3-0) Object concepts, object-oriented design and analysis, object-oriented analysis relating to developing conceptual models
Overview of the Cattle Immune System 1
 Oregon State University BEEF043 Beef Cattle Library Beef Cattle Sciences Overview of the Cattle Immune System 1 Reinaldo F. Cooke 2 Introduction On average, the U.S. cattle industry loses more than $1
Oregon State University BEEF043 Beef Cattle Library Beef Cattle Sciences Overview of the Cattle Immune System 1 Reinaldo F. Cooke 2 Introduction On average, the U.S. cattle industry loses more than $1
Bio-inspired mechanisms for efficient and adaptive network security
 Bio-inspired mechanisms for efficient and adaptive network security Falko Dressler Computer Networks and Communication Systems University of Erlangen-Nuremberg, Germany [email protected]
Bio-inspired mechanisms for efficient and adaptive network security Falko Dressler Computer Networks and Communication Systems University of Erlangen-Nuremberg, Germany [email protected]
HYBRID GENETIC ALGORITHM PARAMETER EFFECTS FOR OPTIMIZATION OF CONSTRUCTION RESOURCE ALLOCATION PROBLEM. Jin-Lee KIM 1, M. ASCE
 1560 HYBRID GENETIC ALGORITHM PARAMETER EFFECTS FOR OPTIMIZATION OF CONSTRUCTION RESOURCE ALLOCATION PROBLEM Jin-Lee KIM 1, M. ASCE 1 Assistant Professor, Department of Civil Engineering and Construction
1560 HYBRID GENETIC ALGORITHM PARAMETER EFFECTS FOR OPTIMIZATION OF CONSTRUCTION RESOURCE ALLOCATION PROBLEM Jin-Lee KIM 1, M. ASCE 1 Assistant Professor, Department of Civil Engineering and Construction
Effect of Using Neural Networks in GA-Based School Timetabling
 Effect of Using Neural Networks in GA-Based School Timetabling JANIS ZUTERS Department of Computer Science University of Latvia Raina bulv. 19, Riga, LV-1050 LATVIA [email protected] Abstract: - The school
Effect of Using Neural Networks in GA-Based School Timetabling JANIS ZUTERS Department of Computer Science University of Latvia Raina bulv. 19, Riga, LV-1050 LATVIA [email protected] Abstract: - The school
Data Security Strategy Based on Artificial Immune Algorithm for Cloud Computing
 Appl. Math. Inf. Sci. 7, No. 1L, 149-153 (2013) 149 Applied Mathematics & Information Sciences An International Journal Data Security Strategy Based on Artificial Immune Algorithm for Cloud Computing Chen
Appl. Math. Inf. Sci. 7, No. 1L, 149-153 (2013) 149 Applied Mathematics & Information Sciences An International Journal Data Security Strategy Based on Artificial Immune Algorithm for Cloud Computing Chen
Segmentation of stock trading customers according to potential value
 Expert Systems with Applications 27 (2004) 27 33 www.elsevier.com/locate/eswa Segmentation of stock trading customers according to potential value H.W. Shin a, *, S.Y. Sohn b a Samsung Economy Research
Expert Systems with Applications 27 (2004) 27 33 www.elsevier.com/locate/eswa Segmentation of stock trading customers according to potential value H.W. Shin a, *, S.Y. Sohn b a Samsung Economy Research
14.10.2014. Overview. Swarms in nature. Fish, birds, ants, termites, Introduction to swarm intelligence principles Particle Swarm Optimization (PSO)
 Overview Kyrre Glette kyrrehg@ifi INF3490 Swarm Intelligence Particle Swarm Optimization Introduction to swarm intelligence principles Particle Swarm Optimization (PSO) 3 Swarms in nature Fish, birds,
Overview Kyrre Glette kyrrehg@ifi INF3490 Swarm Intelligence Particle Swarm Optimization Introduction to swarm intelligence principles Particle Swarm Optimization (PSO) 3 Swarms in nature Fish, birds,
One of the more complex systems we re looking at. An immune response (a response to a pathogen) can be of two types:
 Immune system. One of the more complex systems we re looking at. An immune response (a response to a pathogen) can be of two types: (pathogen - disease causing organism) 1) Non specific. Anything foreign
Immune system. One of the more complex systems we re looking at. An immune response (a response to a pathogen) can be of two types: (pathogen - disease causing organism) 1) Non specific. Anything foreign
Trust, Reputation and Fairness in Online Auctions
 Trust, Reputation and Fairness in Online Auctions Adam Wierzbicki 21/11/2006 Polish-Japanese Institute of Information Technology Plan of the talk Background Online auctions Trust management Reputation
Trust, Reputation and Fairness in Online Auctions Adam Wierzbicki 21/11/2006 Polish-Japanese Institute of Information Technology Plan of the talk Background Online auctions Trust management Reputation
Method of Combining the Degrees of Similarity in Handwritten Signature Authentication Using Neural Networks
 Method of Combining the Degrees of Similarity in Handwritten Signature Authentication Using Neural Networks Ph. D. Student, Eng. Eusebiu Marcu Abstract This paper introduces a new method of combining the
Method of Combining the Degrees of Similarity in Handwritten Signature Authentication Using Neural Networks Ph. D. Student, Eng. Eusebiu Marcu Abstract This paper introduces a new method of combining the
