I Know Where You ve Been: Geo-Inference Attacks via the Browser Cache
|
|
|
- Lewis Kelley
- 7 years ago
- Views:
Transcription
1 I Know Where You ve Been: Geo-Inference Attacks via the Browser Cache Yaoqi Jia, Xinshu Dong, Zhenkai Liang, Prateek Saxena School of Computing, National University of Singapore {jiayaoqi, liangzk, Advanced Digital Sciences Center Abstract Many websites customize their services according to different geo-locations of users, to provide more relevant content and better responsiveness, including Google, Craigslist, etc. Recently, mobile devices further allow web applications to directly read users geo-location information from GPS sensors. However, if such websites leave location-sensitive content in the browser cache, other sites can sniff users geo-locations by utilizing timing sidechannels. In this paper, we demonstrate that such geolocation leakage channels are widely open in popular web applications today, including 62% of Alexa Top 100 websites. With geo-inference attacks that measure the timing of browser cache queries, we can locate users countries, cities and neighborhoods in our case studies. We also discuss whether existing defenses can effectively prevent such attacks and additional support required for a better defense deployment. I. INTRODUCTION Geo-location is a type of privacy-sensitive information. Websites have strong interests in obtaining users geo-location information to provide personalized services and advertisements. On the other hand, web attackers [1] misuse victims geo-locations for spear phishing, personally targeted advertisements, or even social engineering attacks. Geo-location leakage can cause tremendous damage to the user s privacy. A traditional way for websites to identify users locations is through IP addresses [2], [3]. However, inferring location from IP addresses is unreliable. First, IP address-based geo-location tracking is not accurate for mobile networks [4]. For example, one recent study shows that more than 90% of the mobile devices in Seattle can be associated with IP addresses that are located over 600 miles away from Seattle [4]. Second, users may intentionally use anonymization services, such as VPN [5] and Tor [6], to hide their real IP addresses [7]. Recent advancement in mobile devices enables websites to obtain geo-location information from GPS sensors. Nevertheless, modern browsers disable the access to geo-location information by default to protect user privacy. Mobile browsers require users explicit permission to access GPS data. In this work, we show that web attackers can utilize side channels to infer the user s geo-location without the user s explicit permission. Prior research has unravelled numerous privacy leakage side-channels via the browser cache [8] [13]. Specifically, timing attacks on browser cache were introduced to sniff browsing history more than a decade ago [8]. Bortz et al. later deployed similar timing attacks on more web applications and scenarios [9]. We demonstrate how such timing side channels caused by browser caches can be utilized to identify a user s geo-location with high accuracy, without permission to access GPS sensors. We term such attacks geo-location inference (or geo-inference) attacks. Our geo-inference attacks are based on a simple assumption that users usually visit location-oriented websites provided for their locations that they live in or plan to visit. For example, when visiting Google s main page, users will be automatically redirected to their specific country page of Google, e.g., in Singapore. As another example, many sites are meant to be accessed by local residents, such as local advertisement websites, e.g., sfbay.craigslist.org for San Francisco Bay Area users. Under this assumption, we conduct experiments on three popular websites, Google, Craigslist and Google Maps. We demonstrate that with geo-inference attacks via the browser cache, attackers can reliably infer a user s country, city, neighborhood, and even home address. Our geo-inference attacks affect all mainstream browsers and a large fraction of popular websites on both desktop and mobile browsers. After running experiments on five mainstream browsers, we find that Chrome, Firefox, Safari, Opera, IE and even TorBrowser (version ) [6], are all vulnerable to geo-inference attacks. Aided by a multi-country proxy service (virtual private network), we ve browsed Alexa Top 100 websites in five different countries (USA, UK, Australia, Japan, and Singapore), and identified the sites that contain location-sensitive resources. Besides the three popular sites, we show that 62% of these sites contain location-sensitive resources and are susceptible to geoinference attacks.
2 Security researchers have proposed various defense solutions against browser cache sniffing [14] [16]. Jackson et al. propose a defense solution by segregating browser cache based on web origins, thus limiting web attackers from observing timing differences between accessing cached and non-cached cross-origin web resources [15]. However, none of today s mainstream browsers have adopted it so far; part of the reason is the significant performance overhead incurred by it. To validate this hypothesis, we implement the same-origin caching policy [15] on Chromium. We find that the policy triggers more than 50% performance overhead among Alexa Top 100 websites. In the context of geoinference attacks, we believe that server-aided cache control, which involves the cooperation of both the server and the browser, is a more practical solution than cache segregation policy at only the browser side. Contributions. In summary, we make the following contributions: We introduce geo-inference attacks that exploit geo-location information leakage channels via the browser cache on desktop and mobile platforms without direct access to GPS or IP address. With such geo-inference attacks, we can reliably track the geo-locations of web users to their countries, cities, and neighborhoods. We show that all five mainstream browsers (Chrome, Firefox, Safari, Opera and IE) on both desktop and mobile platforms as well as TorBrowser are vulnerable to geo-inference attacks. Meanwhile, 62% of Alexa Top 100 websites are susceptible to geo-inference attacks. We discuss existing and potential defenses and propose a more balanced solution to segregate location-sensitive resources instead of caching them in the user s browser. II. A. Threat Model PROBLEM DEFINITION The adversary in a geo-inference attack is a standard web attacker [1], who controls at least one web server and hosts a malicious site, e.g., attacker.com. The web attacker can run JavaScript on the malicious site, but is not capable of compromising the browser code, or bypassing the same-origin policy. To advertise the malicious site, the attacker can promote the popularity of the site via Search Engine Optimization (SEO), and disseminate its shortened URL through s, social networks and advertisements. We assume that Alice is an ordinary web user who does not clear browser cache frequently, and she usually visits geo-location-oriented sites specific to her geolocation, e.g., Google, Craigslist, and Google Maps, Fig. 1: Geo-inference attacks sniff location-sensitive resources left by the location-oriented sites (e.g., Google, Craigslist, and Google Maps) through timing side channels in the browser cache to infer the victim s geolocation. so that she can take advantage of the customized local location-oriented services. When Alice visits the attacker s malicious site in her browser, she denies the unfamiliar site s request to access the device s location. However, the malicious payload in attacker.com can sniff the location-sensitive resources left by the locationoriented sites through side channels in the browser, as Figure 1 shows. If Alice manually changes the location-oriented service to a location different from her location, and she never visits any websites provided for local people, her location will not be leaked to attackers, but she also loses the benefits of customized services for local users. B. Browser Cache Timing Channels In order to reduce the page load time of websites, all present mainstream browsers utilize memory cache or disk cache to save infrequently changed resources such as image files, JavaScript files, CSS files and so on [17]. Once the resources are cached locally, the browser can fetch the resources from local cached copies instead of downloading from the original website. Thus the browser cache reduces the page load time of the website by decreasing the round-trip time. While browser cache provides efficiency in loading pages to users, it also introduces side channels to attackers. In a nutshell, by measuring the resources load time for a specific site twice in a victim s browser, the attacker can calculate the difference in the resources load time. If the difference is smaller than a threshold, it indicates that the user has visited this site previously; otherwise, the user has not. These implicit attacks are called timing attacks on browser cache [8].
3 C. Geo-Inference Attacks via the Browser Cache As a typical case of attacks on browsing history, Wondracek et al. de-anonymize social network users by analyzing users visited URLs [10]. In this paper, we show the implication of timing attacks in deanonymizing the user s geo-location. Our main observation is that to improve user experience, websites usually provide geo-targeting services, e.g., Craigslist maintains city-specific sites to serve users in different cities. In geo-inference attacks, the attacker makes guesses on the victim s geo-location, and then queries the cached resources corresponding to the geo-location. By utilizing the location-sensitive resources left by locationoriented sites in the browser, geo-inference attacks provide an oracle for attackers to verify the user s country, city, or neighborhood. For example, a paper author wants to check which one of the 20 PC members visits the supplementary website provided in an anonymous submission for review. Suppose the PC members are known to be from 20 different cities. The author can mount our geo-inference attacks on the website to locate the PC member, which queries whether the visitor of the website comes from any of the 20 cities. The author has a fare chance to successfully infer the reviewer of the paper, even if the visit is made through a web proxy. III. GEO-INFERENCE ATTACKS: CASE STUDY In this section, we show how to conduct geoinference attacks at various granularity with mainstream browsers, i.e., Chrome, Firefox, Safari, IE and Opera. We set up a web site that contains scripts to explore side channels from browser cache. We use two well-known timing channels, including page load time in frames and resources (e.g., image file) load time. We also utilize two other vectors for querying, which have not been widely explored, i.e., Cross-Origin Resource Sharing (CORS) and <img> s complete property. Together, these channels are practical ways to query cache states in present web browsers. A. Locate Your Country Google has 191 geography-specific domains to provide enhanced service for users. Usually, when a user opens google.com to search, Google will automatically redirect the page to the local Google site hosted in the user s physical location, e.g., google.com.sg. This makes Google a good case study for geo-inference attacks to locate the user s country. In order to infer a user s country, we aim to find out which page from 191 Google s domains hits cache. To achieve this, we utilize Google s logo image, whose URL consists of Google s local domain, e.g., google.com.sg, and /images/srpr/logo11w.png to specify Google s website. We demonstrate three ways to locate the user s country. 1) Geo-Inference Attacks with Image Load Time: Page load time [18] is the period of time from the initiation of the page load (e.g., click on a page link) to its completion in the browser. It usually consists of HTTP/HTTPS request time, response time, and the overhead of parsing and rendering the page in the browser. Image load time is similar to page load time, which is the interval between requesting the image file and finishing rendering the image in the browser. We measured the image load time of Google logos from Google s 191 regional domains to determine the geo-location of the victim. Measurement Techniques. We set the start time as an attribute of the image tag, and set the end time in the onload event handler. We make three measurements of the image load time, the first measurement without cache and the latter two with cache. If the first image load time is significantly larger than the latter two, we infer that the image is not cached in the user s browser. If the time difference is significantly small, e.g., 10 ms, we infer that the image hits cache. Since each logo stands for one local domain, and one domain is hosted in one country, which country s logo out of 191 logos is cached indicates the country the victim lives in. Below is the piece of code to measure the image load time. var image = document.createelement( img ); image.setattribute( starttime, (new Date(). gettime())); image.onload = function() { var endtime = new Date().getTime(); var loadtime = endtime - parseint(this. getattribute( starttime ));... } Listing 1: Measuring the image load time with JavaScript Results. We found that the image load time of each Google s domain without cache is much larger than that with cache. We show the difference in Figure 2 as well as Figure 8 in the Appendix. Because there is only one request for the Google s logo image, when reloading the cached image file, the browser directly reads it from the cache, and the average image load time is usually 1 ms or 0 ms. We have evaluated 191 Google s regional domains on five mainstream browsers, including Chrome, Firefox, Safari, Opera and IE, on both desktop and mobile platforms. We switch the region to US, UK, Australia, Singapore, and Japan with a multi-country proxy service (virtual private network). According to the results, there are no big differences among results from these browsers. Due to the limited space, we only show the Singapore-based results in Chrome as the representative
4 TABLE I: Geo-inference attacks on mainstream browsers I II III IV V Chrome (Linux, Windows & OS X + Android & ios) Firefox (Linux, Windows & OS X + Android) Safari (Windows & OS X + ios) Opera (Linux, Windows & OS X + Android & ios) IE (Windows) I : Locate Your Country with Image Load Time II : Locate Your Country with Cross-Origin Resource Sharing (CORS) III: Locate Your Country with <img> s complete Property IV: Locate Your City with Craigslist V : Locate Your Neighbourhood with Google Maps : Susceptible : Not Susceptible Fig. 2: Difference in image load time (in millisecond): Without Cache (> 129 ms) v.s. With Cache (0 1 ms), for 191 Google s regional domains in Chrome on Mac OS X. in this paper. Table I shows the details of other browsers and platforms. We present the experimental results on Android in the Appendix. 2) Geo-Inference Attacks with Cross-Origin Resource Sharing (CORS): Cross-origin resource sharing (CORS) [19] allows JavaScript to make XMLHttpRequests to another origin. Although Google does not allow JavaScript in other origins to read XMLHttpRequests responses from Google, we can still measure the time interval between sending XMLHttpRequests to Google and receiving the rejection responses. Measurement Techniques. We set the start time in the onloadstart event handler, and set the end time in the onloadend event handler. We measured three rounds of the request load time of Google s logo from Google s 191 regional domains. The big difference between the first round and last two rounds indicates a cache miss for the image. If the request load time is approximately same for three rounds, the image is cached in the user s browser. Below is the piece of code to measure the load time of XMLHttpRequests. var startime, endtime, loadtime; var xmlhttp = new XMLHttpRequest(); xmlhttp.onloadstart = function() { starttime = (new Date()).getTime(); } xmlhttp.onloadend = function() { endtime = (new Date()).getTime(); loadtime = endtime - starttime;... } Listing 2: Measuring the load time for XMLHttpRequests Results. We found that the request load time without cache is larger than that with cache. Similar to Figure 2, Figure 3 shows the difference, which indicates that it is practical to locate users countries in this way. Figure 9 in the Appendix shows that this method is also applicable to mobile browsers. 3) Geo-Inference Attacks with <img> s complete Property: As for the <img> tag in HTML, it has complete property to indicate that the image file finishes loading. We found that this attribute also indicates whether the image file is cached or not in some browsers. Measurement Techniques. We created <img> elements for each URL of Google s regional domains, and check the complete property of each element. If the return value is true, the image is cached in the user s browser; otherwise, the image is not cached. Below is the piece of code to distinguish whether the image file is cached or not.
5 Fig. 3: Difference in load time (in millisecond) for XMLHttpRequests: Without Cache (> 100 ms) v.s. That With Cache (0 1 ms), for 191 Google s regional domains in Chrome on Mac OS X. Fig. 4: The big difference between the page load time (in millisecond) of 100 Craigslist sites without cache (> 1000 ms) and with cache ( 220 ms) indicates geo-inference attacks with Craigslist in Chrome on Mac OS X. function cached(url) { var image = document.createelement( img ); image.src = url; return image.complete image.width+image. height > 0; } Listing 3: Distinguishing whether an image file is cached or not Results. We have evaluated Google s 191 regional domains, and this method can reliably distinguish cache hit from cache miss. This method works on Firefox, Safari and IE, but is not applicable for Chrome and Opera. B. Locate Your City Several websites offer content specific to cities, e.g., Craigslist [20] is a large classified advertisements website that covers 712 cities on the world. Since all the sub-sites are city-oriented and can be loaded in frames, we measured the page load time to locate the user s city. Measurement Techniques. We set the start time as an attribute of the iframe, and set the end time in the onload event handler. We measured the page load time of Craigslist s 712 city-oriented websites in iframes three times. If the difference between the page load time at the first attempt and the latter two is significantly large, e.g., 500 ms, we infer that the page is not cached in the user s browser; otherwise, the page has been visited. From the recently visited page (cached page), we can determine the victim s city. Below is the piece of code to measure the page load time of Craigslist sub-sites. var page = document.createelement( iframe ); page.setattribute( starttime, (new Date()). gettime()); page.onload = function () { var endtime = (new Date()).getTime(); var loadtime = ( endtime - parseint(this. getattribute( starttime )));... } Listing 4: Measuring the page load time of Craigslist sub-sites Results. Our attacks can reliably identify whether a city-specific page is cached in the user s browser. We consider the average page load time of the latter two measurements as the time with cache. As Figure 4 as well as Figure 10 in the Appendix demonstrates, the difference is quite large. Due to more resources that Craigslist contains than Google s logo (only one image file), the page load time with cache is around 220 ms on desktop or 620 ms on mobile, which is much higher than 0 ms in Figure 2 and Figure 8. Since the user buys or sells goods on Craigslist mostly in his/her city, the attacker can reveal the victim s real city with this method, even if they use VPN or Tor. C. Locate Your Neighborhood To extend our study to finer granularity than city level, we exploit the cached resources from online map service websites, e.g., Google Maps.
6 (12627, 23720) Grand Loop Rd, Yellowstone National Park, WY 82190, USA Fig. 5: URLs of map tiles have static mappings to geo-locations in Google Maps. Fig. 6: Difference in page load time (in millisecond): Without Cache (> 50 ms) v.s. With Cache (0 1 ms), for 4,646 map tiles of New York City from Google Maps in Chrome on Mac OS X. Google Maps [21] is a web map service supported by Google, which provides maps and street views at each place. When a user searches one place, Google Maps presents the specific area to the user and the user can zoom in/out to control the map precision. Furthermore, the user can click on the area to see the street views mapping to the area. For all the searching and locating steps, Google Maps will request and fetch numerous map tiles from the web server. In fact, the maps are tessellations of map tiles, and each tile localizes at a predicable URL. After manually analyzing the URLs of the requests for map tiles, we figure out that the URLs have some patterns that are a function of real geo-location coordinates 1. For example, as Figure 5 shows, we can derive the coordinates (12627, 23720) of Grand Loop Rd from the requesting URL. Though the coordinates are not the real geographic coordinates, we can predict the URLs of one specific area s map tiles corresponding with the coordinates. By recording the coordinates of all the vertices on the area, we can traverse all the possible points inside the area. After converting the coordinates to URLs, we measured the image load time of the map tiles in the victim s city, which is verified by Craigslist. As Google Maps usually zooms in to the user s current location when the user starts to browse Google Maps in the browser, by sniffing the victim s 1 We have investigated 11 websites that provide map service, including Google Maps, Bing Maps, Yahoo! Maps, arcgis, HERE, OpenStreetMap, ViaMichelin, MapQuest, WikiMapia, Navionics and Mappy. We found that the URLs of map tiles from these sites are all statically predictable. recently visited map tiles, we can locate the victim s streets and neighborhood. Measurement Techniques. We set the start time as an attribute of the image, and set the end time in the onload event handler. In our experiments, we measured the image load time for all 4,646 map tiles in New York City on Google Maps three times. If the image load time at the first attempt is much larger than the latter two, e.g., 40 ms, it indicates a cache miss for the image. If the difference between each time is quite small, e.g., 10 ms, the image hits cache. Results. We found that the image load time of map tiles from Google Maps without cache is much larger than that with cache. Therefore, we can reliably determine the user s location via measuring the image load time of map tiles in the user s city. As Figure 6 as well as Figure 11 in the Appendix shows, the huge difference makes it quite straightforward to distinguish whether the specific map tile is cached in the browser or not. IV. GEO-TARGETING ON ALEXA TOP 100 WEBSITES In addition to our case studies with Google, Craigslist and Google Maps, we also show that a set of popular websites is susceptible to geo-inference attacks. We present our results from two aspects. A. Reliability of Timing-Based Attacks via the Browser Cache Geo-inference attacks are based on the techniques of timing attacks on the browser cache. We revisit
7 such timing-based attacks by conducting a study for Alexa Top 100 websites on five mainstream browsers (Chrome, Firefox, Safari, Opera and IE) as well as TorBrowser 2. We found that browsing history sniffing is still open to timing-based attacks on these browsers. We measured the page load time three times per site. In Figure 12 and Figure 13 in the Appendix, we consider the average difference between the second measurement and the third measurement as the page load time with cache. The difference between page load time without cache and that with cache is quite large. As Figure 12 and Figure 13 show, our proposed geoinference attacks can reliably measure the page load time of Alexa Top 100 websites and sniff the victim s browsing history. Table I shows that our geo-inference attacks are applicable to all five mainstream browsers. If a website sets X-Frame-Options to SAMEO- RIGIN or DENY in the response headers, the attacker cannot load the site into frames, so the page load time actually equals the request load time and is not reliable. We investigated Alexa Top 100 websites, and found that only 32 sites set X-Frame- Options to SAMEORIGIN, and five sites set it to DENY. Nevertheless, the attacker can utilize a geo-targeting image or other resources that are specific to the site, and measure the resources load time. For example, the URLs of Google s logo images are and respectively for google.com.sg in Singapore and google.co.jp in Japan. As Section III-A shows, geo-inference attacks with resources load time are quite reliable. B. Prevalence of Location-Sensitive Resources To demonstrate the susceptibility of geo-inference attacks, we systematically analyzed Alexa Top 100 websites, and identified the location-sensitive sites and their location-sensitive resources. We exclude 45 domains that are one of the following categories. Sites are highly related to specific countries, e.g., google.de and yahoo.co.jp. Sites are known to contain pornographic content, e.g., xvideos.com and xhamster.com. Sites are unreachable, e.g., akamaihd.net, and googleusercontent.com. Using Hotspot Shield, we visited the 55 websites in five different countries (USA, UK, Australia, Japan and Singapore) and recorded all the URLs of cached resources for each website. As for each site, we automatically compared the collected URLs from different countries with our analysis tool, sorted out the URLs that vary in different countries, and then manually 2 We run the experiments on TorBrowser , which is based on Firefox We discuss TorBrowser in Section V. verified the resource that has the same functionality but the URL changes from country to country. Our study demonstrates that the majority of websites contain location-sensitive resources, which are vulnerable to geo-inference attacks. 62% of these websites have location-sensitive resources, such as domain and logo. The user who recently visited any of these websites is vulnerable to expose his/her geo-location to the attackers who conduct geo-inference attacks. V. DISCUSSION & SOLUTION Beyond its techniques, the geo-inference attack we demonstrate can be an effective attack vector in practice. A. Effectiveness in Locating Victims The geo-inference attacks discussed in this paper do not directly pinpoint the geo-locations of targeted users. Instead, they allow attackers to verify whether the user has been to a given location. Consider one scenario where a paper author wants to check which one of the 20 PC members visits the supplementary website provided in an anonymous submission for review via an IPanonymization VPN service. Suppose the PC members are known to be from 20 different cities. The author can mount our geo-inference attacks on the website, which queries whether the visitor of the website comes from any of the 20 cities. In the previous case, it only needs to issue 20 queries. However, the number of queries may grow significantly depending on different scenarios. Now consider another example where the attacker wants to locate a visitor s neighborhood within the New York City. In this case, Google Maps has 4,646 map tiles for the entire city, i.e., the attacker needs to make 4,646 queries in worst case to locate the visitor. According to our experiments, one web attacker can verify around 5 to 10 geo-locations every second (Figure 4 and Figure 10). This amounts to eight minutes time in a single-threaded execution; of course, the attacker can speed up the process with parallel queries. B. Pros & Cons of Potential Defenses Technically speaking, geo-inference attacks can be prevented by existing defenses against privacy leakage via the browser cache. However, as we discuss next, there are trade-offs we need to consider when deploying such defenses. Private browsing mode is not the cure: The private browsing mode (Private Browsing in Safari and Firefox, Incognito Mode in Chrome, Private Window in Opera, and inprivate Browsing in IE) prevents browsers from permanently storing any history, cookies or other client-side states for websites. However, contrary to what the name naively suggests, the private browsing mode does not prevent caching of web resources during
8 users private browsing [22]. Instead, all cache incurred during the private browsing mode is automatically cleared after the user closes its window. Therefore, users of the private browsing mode are still susceptible to geoinference attacks via the browser cache. Rectifying inconsistent access policy with XML- HttpRequest: Although Cross-Origin Resource Sharing (CORS) has been integrated into modern web browsers, it only allows websites to control which web origins can access the content of XMLHttpRequest responses. It does not, on the other hand, specify whether other origins can get the notification when the response whose content is inaccessible arrives. These error notifications can be a source of timing leakage as shown in Section III-A2. Such an inconsistent policy is one of the root causes that make geo-inference attacks possible. It is also quite different from other timing exposure with image loading (Section III-A1 and III-A3), where no explicit access control policy exists. It thus appears as a necessary rectification step to block the XMLHttpRequest status notifications if the website has denied the request to access it. However, additional analysis and experiments are necessary to figure out whether any valid case that requires access to the status notification of an access-denied XMLHttpRequest. Besides, this is just one of the many existing side-channels that leak users privacy; it is not a holistic solution to defend geo-inference attacks via the browser cache. Segregating browser cache works but is expensive: In current browsers, cache is like a huge repository; there are no explicit boundaries or restrictions among different domains. Jackson et al. [15] deploy Same-Origin Policy on the browser cache to prevent cross-origin sites from loading the resources stored by the original sites. In principal, such a solution would defeat geo-inference attacks. To the authors knowledge, this solution has not been adopted by modern web browsers in the default setting. We speculate that performance could be one of the concerns. Thus, we reimplement their cache segregation policy in Chromium 34 (latest release), and measure the estimated performance overhead incurred from it. Since the most obvious performance overhead comes from loading cross-origin resources, we measure the page load time for Alexa Top 100 websites 3. As shown in Figure 7, the same-origin caching policy triggers more than 50% performance overhead. This indicates that the same-origin caching policy may affect the page load time significantly, although such performance overhead might be mitigated to a certain extent by whitelisting domains as same-origin, such as Content Delivery Network (CDN) domains. We try to whitelist the resources from CDN, and show that the performance 3 Except three unreachable sites, googleusercontent.com, akamaihd. net, thepiratebay.sx. TABLE II: How does whitelisting resources from CDN affect performance overhead? I II google.com 140% 9.09% facebook.com 80.81% 5.05% youtube.com 45.45% 12.59% yahoo.com % 31.03% baidu.com % 6.67% I: Performance Overhead Without Whitelisting Resources From CDN II: Performance Overhead With Whitelisting Resources From CDN overhead is still non-negligible after whitelisting for five sites in Table II 4. We will discuss alternatives to this policy in Section V-C. Can VPN or Tor prevent the attacks?: Geoinference attacks are based on timing attacks against browser cache, so they are not affected by VPN services that replace the original IP addresses of users. Although the current version of Tor Browser Bundle disables disk cache in browsers by default, memory cache is still active. As a result, it is similar to the private browsing mode. Browser cache is available until the user closes the browser, where the cache stored in memory is invalidated. For browser caches, we also find that Tor- Browser adds an additional domain=string property to label every cache entry with the top-level window s domain [23]. Therefore, TorBrowser can protect users from geo-inference attacks when the malicious page s top-level URL is different from the targeted site. However, for mashup websites, all the embedded sites in frames share the same top-level window s domain, i.e., the mashup s domain. The malicious embedded site can query the cache status of other embedded sites cached location-sensitive resources to infer the user s geolocation. Thus only adding domain=string property on the cache entry is insufficient. To prevent timing attacks, Jackson et al consider two observers, i.e., the site embedding the content and the host of the content to label the cache entry. Instead, TorBrowser only uses the top-level window s domain as the domain field to enforce the caching mechanism. Therefore, Jackson s solution defeats geo-inference attacks in the mashup scenario, but TorBrowser does not. We have run our experiments on TorBrowser v as shown in the Appendix, and find that TorBrowser can still leak users geo-location information for mashup websites. Randomizing timing measurements: As with other timing-based attacks, we can add noise into the timing measurement mechanisms related to browser cache queries. However, introduction of such noise needs to be carefully designed and verified to have mini- 4 Table II shows the performance overhead without or with whitelisting resources from CDN comparing with the vanilla version without same-origin caching policy.
9 Fig. 7: Enforcing same-origin caching policy cause 20% to 300% performance overhead to load each site comparing with the vanilla version without policy. mal impact on browser performance and responsiveness. This could be an intricate engineering effort in future. Server-side protection of users geo-locations: Websites may voluntarily switch to a non-geo-targeting mode upon request of users. As part of the reason for deploying geo-targeting is to improve the responsiveness of websites, this will probably degrade website performance. As a middle ground, websites may randomize the URLs for geo-targeting resources periodically. This way, they can still benefit the performance improvement from geo-targeting and cache, at least for a period of time. At the same time, periodical changes of URLs can mitigate geo-inference attacks via the browser cache, as the additional randomness makes it difficult for attackers to predict the URLs to query. C. A Better Defense Solution? The cache segregation proposed by Jackson et al. appears as a promising direction to resolve the geolocation leakage via browser cache. In addition, with collaborative effort from both the browser vendors and web servers, the performance overhead incurred could be significantly reduced for most of use cases. We envision an endeavor similar to Do Not Track [24]. Browsers should provide an option for end users to opt out of caching location-sensitive web resources, such as map tiles in Google Maps and geo-targeting country pages. This way, users can voluntarily protect their geo-location information from geo-inference attacks. In solutions aimed to protect users privacy, such as Tor or private browsing mode, this option should be turned on by default. Such an option can be communicated to web servers as an HTTP request header. At the server side, web developers need to respect this option, and set the Cache-Control: no-cache HTTP response header for location-sensitive resources. However, discerning such resources might be a challenging task for today s web applications. We have experimented with a prototype tool during our study, which can aid web developers in identifying location-sensitive resources. More specifically, the tool collects the URLs of cached resources during our manual testing of the web applications from different geo-locations (behind VPN services). Then it compares such collections and automatically labels the URLs that are potentially locationsensitive. Web developers can further verify resources corresponding to this scaled-down set of potentially location-sensitive URLs, and confirm the locationsensitive resources. In the future, we can integrate the no caching support for location-sensitive resources into web application generation frameworks. VI. RELATED WORK There has been extensive research on both privacy leakage attacks and defense solutions. We discuss the most closely related work in this section. A. Privacy Leakage Jang et al. study popular privacy violation practices in websites and third-party JavaScript libraries [25]. Researchers further present another way to sniff browsing history with the CSS visited pseudoclass [26], [27]. In addition to traditional leakage channels via DOM or CSS primitives, user interactions can also be misused to reveal users browsing history [11]. More recently, new primitives introduced into browsers also expose new attack vectors of privacy leakage, including CSS filters [12] and SVG filters [13]. On the other hand, side channels, such as timing attacks that were previously used to crack crypto systems or protocol implementations [28] [30] have also been explored for privacy leakage in browsers. Felten et al. [8] first introduced timing-based attacks to detect browser cache. Bortz et al. [9] apply timing attacks to more web applications and scenarios. With the popularity of social networks, user privacy becomes a serious concern. Wondracek et al. show that by analyzing the group memberships of social network users, attackers can potentially identify the identities of users [10]. This paper presents a different view into privacy leakage in browsers. Instead of proposing new leakage channels, we provide a more in-depth evaluation of the implications of existing leakage channels. We specifically demonstrate that many of the timing-based attack vectors still exist today, and they are open to attackers to sniff users geo-locations.
10 B. Defense To prevent direct privacy leakage channels, L.D. Baron proposes a fix to misused CSS visited styles that leak browsing history, which has been incorporated into all popular web browsers [14]. As a more fundamental endeavor, Jackson et al. [15] analyze various degrees of cooperation between sites to track users and apply a refined same-origin policy on browser cookie and cache to protect browser states. Jakobsson et al. [16] neutralize browser sniffing by performing URL personalization on the fly at the server side. As more social networking gadgets are also used to track users, Roesner et al. propose a browser extension to allow users to prevent such gadgets to track them without their explicit interactions [31]. As we discuss in Section V-B, we expect more practical solutions with a better balance between performance and privacy preservation. C. Location Privacy The privacy of geo-locations has attained significant attention from security researchers. Gedik et al. propose a personalized k-anonymity model to protect location privacy with mobile clients [32]. Nevertheless, recent boom in location-based web and mobile services also demonstrates that users are generally willing to reveal partial geo-location information for better services. Duckham et al. thus propose a formal model that allows efficient balancing between the two competing needs, the need for high quality location-based services and that for location privacy [33]. Similarly, Beresford et al. develop a refined method, called the mixed zone, to achieve enhanced location privacy in location-based services [34]. In this paper, we primarily consider empirical geo-location leakage on the present web, where location information is explicitly available without anonymized protection. VII. CONCLUSION In this paper, we present geo-inference attacks via the browser cache, which utilize the cached locationsensitive resources left by location-based websites. Our geo-inference attacks provide an oracle for web attackers to verify guessed geo-locations of victims. In our case studies, we demonstrate the reliability and the power of our geo-inference attacks to track the victim s country, city, and neighborhood. Furthermore, we analyze Alexa Top 100 websites for their susceptibility of geo-inference attacks. We discuss the effectiveness in locating victims and potential defenses for geoinference attacks, and suggest collaborative solutions between browser vendors and web applications to prevent such geo-location leakage channels. ACKNOWLEDGEMENTS We thank the anonymous reviewers of this paper for their insightful feedback. We thank Chunwang Zhang, Hong Hu, and Shweta Shinde for their comments on an early presentation of this work. We also thank Roger Dingledine and Georg Koppen for their feedback on our experiments on TorBrowser. This work is supported by the Ministry of Education, Singapore under Grant No. R Any opinions, findings, and conclusions or recommendations expressed in this paper are those of the authors and do not necessarily reflect the views of the Ministry of Education, Singapore. REFERENCES [1] D. Akhawe, A. Barth, P. E. Lam, J. Mitchell, and D. Song, Towards a formal foundation of web security, in Computer Security Foundations Symposium (CSF), rd IEEE, [2] E. Katz-Bassett, J. P. John, A. Krishnamurthy, D. Wetherall, T. Anderson, and Y. Chawathe, Towards ip geolocation using delay and topology measurements, in Proceedings of the 6th ACM SIGCOMM conference on Internet measurement, [3] I. Poese, S. Uhlig, M. A. Kaafar, B. Donnet, and B. Gueye, Ip geolocation databases: unreliable? ACM SIGCOMM Computer Communication Review, [4] M. Balakrishnan, I. Mohomed, and V. Ramasubramanian, Where s that phone?: geolocating ip addresses on 3g networks, in Proceedings of the 9th ACM SIGCOMM conference on Internet measurement conference, [5] Virtual private network, private network. [6] Tor, [7] revolution 2.0 : How social media toppled a dictator, revolution-2-0-how-social-media-toppled-a-dictator. [8] E. W. Felten and M. A. Schneider, Timing attacks on web privacy, in Proceedings of the 7th ACM conference on Computer and communications security, [9] A. Bortz and D. Boneh, Exposing private information by timing web applications, in Proceedings of the 16th international conference on World Wide Web, [10] G. Wondracek, T. Holz, E. Kirda, and C. Kruegel, A practical attack to de-anonymize social network users, in Security and Privacy (SP), 2010 IEEE Symposium on, [11] Z. Weinberg, E. Y. Chen, P. R. Jayaraman, and C. Jackson, I still know what you visited last summer: Leaking browsing history via user interaction and side channel attacks, in Security and Privacy (SP), 2011 IEEE Symposium on, [12] R. Kotcher, Y. Pei, P. Jumde, and C. Jackson, Cross-origin pixel stealing: timing attacks using css filters, in Proceedings of the 2013 ACM SIGSAC conference on Computer & communications security, [13] P. Stone, Pixel perfect timing attacks with html5, Online at contextis. com/files/browser Timing Attacks. pdf, [14] L. D. Baron, Preventing attacks on a user s history through css :visited selectors, [15] C. Jackson, A. Bortz, D. Boneh, and J. C. Mitchell, Protecting browser state from web privacy attacks, in Proceedings of the 15th international conference on World Wide Web, [16] M. Jakobsson and S. Stamm, Invasive browser sniffing and countermeasures, in Proceedings of the 15th international conference on World Wide Web, [17] Optimize caching, best-practices/caching. [18] Interpret site speed, answer/ ?hl=en.
11 [19] Cross-origin resource sharing, Cross-origin resource sharing. [20] Craigslist, [21] Google maps, [22] G. Aggarwal, E. Bursztein, C. Jackson, and D. Boneh, An analysis of private browsing modes in modern browsers, in Proceedings of the 19th USENIX Conference on Security, ser. USENIX Security 10, [23] M. Perry, E. Clark, and S. Murdoch, The design and implementation of the tor browser, projects/torbrowser/design/#identifier-linkability. [24] J. Mayer and A. Narayanan, Do not track - universal web tracking opt out, [25] D. Jang, R. Jhala, S. Lerner, and H. Shacham, An empirical study of privacy-violating information flows in javascript web applications, in Proceedings of the 17th ACM conference on Computer and communications security, [26] A. Janc and L. Olejnik, Feasibility and real-world implications of web browser history detection, Proceedings of W2SP, [27] S. Stamm, Plugging the css history leak, org/security/2010/03/31/plugging-the-css-history-leak/. [28] P. C. Kocher, Timing attacks on implementations of diffiehellman, rsa, dss, and other systems, in Advances in CryptologyCRYPTO96, [29] D. Brumley and D. Boneh, Remote timing attacks are practical, Computer Networks, [30] O. Aciiçmez, W. Schindler, and Ç. K. Koç, Improving brumley and boneh timing attack on unprotected ssl implementations, in Proceedings of the 12th ACM conference on Computer and communications security, [31] F. Roesner, T. Kohno, and D. Wetherall, Detecting and defending against third-party tracking on the web, in Proceedings of the 9th USENIX Conference on Networked Systems Design and Implementation, ser. NSDI 12, [32] B. Gedik and L. Liu, Protecting location privacy with personalized k-anonymity: Architecture and algorithms, IEEE Transactions on Mobile Computing, [33] M. Duckham and L. Kulik, A formal model of obfuscation and negotiation for location privacy, in Proceedings of the Third International Conference on Pervasive Computing, ser. PERVASIVE 05, [34] A. R. Beresford and F. Stajano, Mix zones: User privacy in location-aware services, in Proceedings of the Second IEEE Annual Conference on Pervasive Computing and Communications Workshops, ser. PERCOMW 04, Exploit Example: Suppose a user is an Argentinean, when visiting the sub-page for Godaddy in the igoogleportal s page 5, he switches the country to Argentina. TorBrowser caches the Godaddy s logo in Argentina with setting the domain field in the cache entry as After that, when the user visits the geo-inference page, the scrips in the page will create and measure the image load time of all Godaddy s logos for different countries. Since the geo-inference page is also under the top-level window s domain ( thus TorBrowser will directly load the cached logo image for the Godaddy s logo in Argentina. Therefore, the scripts can figure out the minor time difference to create the Godaddy s logo for Argentina, and infer that the user is in Argentina. Suggested Solutions: To completely defeat such attacks, we suggest two solutions for TorBrowser. First, TorBrowser can disable memory cache by default like TorBrowser Second, TorBrowser can set the top-level window s domain together with the frame s domain as the additional field in the cache entry instead of only using the top-level window s domain. Either one can help to mitigate geo-inference attacks. In fact, it is more practical for website developers to set cachecontrol: no-cache for the location-sensitive resources, e.g., logos, as we discussed in Section V-C. APPENDIX A. Geo-Inference Attacks on TorBrowser As we discussed in Section V, TorBrowser adds an additional domain field for each cache entry to prevent the cross-origin timing channels [23]. However, when a user uses a mashup site on TorBrowser, e.g., igoogleportal.com, the domain field for each cache entry of all the embedded sites in iframes is the mashup site s domain. Therefore, the embedded malicious site can utilize the timing channels to query the cache status of other embedded sites cached resources to infer the user s geo-location. We demonstrate a working exploit example and provide suggestions below. We have tested this example on TorBrowser v The user logins with the account s name: aliceisnotbob1@gmail.com and password: aliceisbob.
12 Fig. 8: Difference in image load time (in millisecond): Without Cache (> 200 ms) v.s. With Cache (0 1 ms), for 191 Google s geo-targeting domains in Chrome on Android Fig. 9: Difference in load time (in millisecond) for XMLHttpRequests: Without Cache (> 400 ms) v.s. With Cache (20 30 ms), for 191 Google s geo-targeting domains in Chrome on Android Without Cache With Cache Fig. 10: The page load time (in millisecond) of 100 Craigslist sites without cache (> 1300 ms) is substantially larger than the time with cache ( 620 ms) in Chrome on Android Fig. 11: Difference in page load time (in millisecond): Without Cache (> 50 ms) v.s. With Cache (0 5 ms), for 4,646 map tiles of New York City from Google Maps in Chrome on Android Without Cache With Cache Fig. 12: The difference between the page load time (in millisecond) of Alexa Top 100 websites without cache and with cache indicates that it is effortless for timing-based attacks to distinguish whether the site is cached or not in Chrome on desktop Without Cache With Cache Fig. 13: The page load time (in millisecond) of Alexa Top 100 websites without cache is much larger than the time with cache in Chrome on Android.
I Know Where You ve Been:! Geo-Inference Attacks via the Browser Cache!
 I Know Where You ve Been:! Geo-Inference Attacks via the Browser Cache! Yaoqi Jia, Xinshu Dong, Zhenkai Liang, Prateek Saxena! School of Computing, National University of Singapore! Advanced Digital Sciences
I Know Where You ve Been:! Geo-Inference Attacks via the Browser Cache! Yaoqi Jia, Xinshu Dong, Zhenkai Liang, Prateek Saxena! School of Computing, National University of Singapore! Advanced Digital Sciences
A Server and Browser-Transparent CSRF Defense for Web 2.0 Applications. Slides by Connor Schnaith
 A Server and Browser-Transparent CSRF Defense for Web 2.0 Applications Slides by Connor Schnaith Cross-Site Request Forgery One-click attack, session riding Recorded since 2001 Fourth out of top 25 most
A Server and Browser-Transparent CSRF Defense for Web 2.0 Applications Slides by Connor Schnaith Cross-Site Request Forgery One-click attack, session riding Recorded since 2001 Fourth out of top 25 most
Scriptless Timing Attacks on Web Browser Privacy
 2014 44th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Scriptless Timing Attacks on Web Browser Privacy Bin Liang, Wei You, Liangkun Liu, Wenchang Shi Renmin University
2014 44th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Scriptless Timing Attacks on Web Browser Privacy Bin Liang, Wei You, Liangkun Liu, Wenchang Shi Renmin University
Recent Advances in Web Application Security
 Recent Advances in Web Application Security Author: Neelay S Shah Principal Security Consultant Foundstone Professional Services Table of Contents Introduction 3 Content Security Policy 3 Best Practices
Recent Advances in Web Application Security Author: Neelay S Shah Principal Security Consultant Foundstone Professional Services Table of Contents Introduction 3 Content Security Policy 3 Best Practices
Cleaning Encrypted Traffic
 Optenet Documentation Cleaning Encrypted Traffic Troubleshooting Guide iii Version History Doc Version Product Date Summary of Changes V6 OST-6.4.300 01/02/2015 English editing Optenet Documentation
Optenet Documentation Cleaning Encrypted Traffic Troubleshooting Guide iii Version History Doc Version Product Date Summary of Changes V6 OST-6.4.300 01/02/2015 English editing Optenet Documentation
RTC-Web Security Considerations
 RTC-Web Security Considerations IETF 80 Eric Rescorla ekr@rtfm.com IETF 80 RTC-Web Security Issues 1 The Browser Threat Model Core Web Security Guarantee: users can safely visit arbitrary web sites and
RTC-Web Security Considerations IETF 80 Eric Rescorla ekr@rtfm.com IETF 80 RTC-Web Security Issues 1 The Browser Threat Model Core Web Security Guarantee: users can safely visit arbitrary web sites and
Front-End Performance Testing and Optimization
 Front-End Performance Testing and Optimization Abstract Today, web user turnaround starts from more than 3 seconds of response time. This demands performance optimization on all application levels. Client
Front-End Performance Testing and Optimization Abstract Today, web user turnaround starts from more than 3 seconds of response time. This demands performance optimization on all application levels. Client
Workday Mobile Security FAQ
 Workday Mobile Security FAQ Workday Mobile Security FAQ Contents The Workday Approach 2 Authentication 3 Session 3 Mobile Device Management (MDM) 3 Workday Applications 4 Web 4 Transport Security 5 Privacy
Workday Mobile Security FAQ Workday Mobile Security FAQ Contents The Workday Approach 2 Authentication 3 Session 3 Mobile Device Management (MDM) 3 Workday Applications 4 Web 4 Transport Security 5 Privacy
Exposing Private Information by Timing Web Applications
 Exposing Private Information by Timing Web Applications Andrew Bortz Stanford University abortz@cs.stanford.edu Dan Boneh Stanford University dabo@cs.stanford.edu Palash Nandy palashn@gmail.com ABSTRACT
Exposing Private Information by Timing Web Applications Andrew Bortz Stanford University abortz@cs.stanford.edu Dan Boneh Stanford University dabo@cs.stanford.edu Palash Nandy palashn@gmail.com ABSTRACT
CS 558 Internet Systems and Technologies
 CS 558 Internet Systems and Technologies Dimitris Deyannis deyannis@csd.uoc.gr 881 Heat seeking Honeypots: Design and Experience Abstract Compromised Web servers are used to perform many malicious activities.
CS 558 Internet Systems and Technologies Dimitris Deyannis deyannis@csd.uoc.gr 881 Heat seeking Honeypots: Design and Experience Abstract Compromised Web servers are used to perform many malicious activities.
DNS REBINDING DENIS BARANOV, POSITIVE TECHNOLOGIES
 DNS REBINDING DENIS BARANOV, POSITIVE TECHNOLOGIES TABLE OF CONTENTS 1 Bypassing The Restrictions 3 2 Putting It into Practice 5 3 Actual Load 7 4 Detection Of The Application Version 5 Guessing A/The
DNS REBINDING DENIS BARANOV, POSITIVE TECHNOLOGIES TABLE OF CONTENTS 1 Bypassing The Restrictions 3 2 Putting It into Practice 5 3 Actual Load 7 4 Detection Of The Application Version 5 Guessing A/The
Exposing Private Information by Timing Web Applications
 Exposing Private Information by Timing Web Applications Andrew Bortz Stanford University abortz@cs.stanford.edu Dan Boneh Stanford University dabo@cs.stanford.edu Palash Nandy palashn@gmail.com ABSTRACT
Exposing Private Information by Timing Web Applications Andrew Bortz Stanford University abortz@cs.stanford.edu Dan Boneh Stanford University dabo@cs.stanford.edu Palash Nandy palashn@gmail.com ABSTRACT
Criteria for web application security check. Version 2015.1
 Criteria for web application security check Version 2015.1 i Content Introduction... iii ISC- P- 001 ISC- P- 001.1 ISC- P- 001.2 ISC- P- 001.3 ISC- P- 001.4 ISC- P- 001.5 ISC- P- 001.6 ISC- P- 001.7 ISC-
Criteria for web application security check Version 2015.1 i Content Introduction... iii ISC- P- 001 ISC- P- 001.1 ISC- P- 001.2 ISC- P- 001.3 ISC- P- 001.4 ISC- P- 001.5 ISC- P- 001.6 ISC- P- 001.7 ISC-
Relax Everybody: HTML5 Is Securer Than You Think
 Relax Everybody: HTML5 Is Securer Than You Think Martin Johns (@datenkeller) SAP AG Session ID: ADS-W08 Session Classification: Advanced Motivation For some reason, there is a preconception that HTML5
Relax Everybody: HTML5 Is Securer Than You Think Martin Johns (@datenkeller) SAP AG Session ID: ADS-W08 Session Classification: Advanced Motivation For some reason, there is a preconception that HTML5
Feasibility and Real-World Implications of Web Browser History Detection
 Feasibility and Real-World Implications of Web Browser History Detection Artur Janc artur@lingro.com Lukasz Olejnik lukasz.olejnik@man.poznan.pl ABSTRACT Browser history detection through the Cascading
Feasibility and Real-World Implications of Web Browser History Detection Artur Janc artur@lingro.com Lukasz Olejnik lukasz.olejnik@man.poznan.pl ABSTRACT Browser history detection through the Cascading
A Practical Attack to De Anonymize Social Network Users
 A Practical Attack to De Anonymize Social Network Users Gilbert Wondracek () Thorsten Holz () Engin Kirda (Institute Eurecom) Christopher Kruegel (UC Santa Barbara) http://iseclab.org 1 Attack Overview
A Practical Attack to De Anonymize Social Network Users Gilbert Wondracek () Thorsten Holz () Engin Kirda (Institute Eurecom) Christopher Kruegel (UC Santa Barbara) http://iseclab.org 1 Attack Overview
Network Security Web Security
 Network Security Web Security Anna Sperotto, Ramin Sadre Design and Analysis of Communication Systems Group University of Twente, 2012 Cross Site Scripting Cross Side Scripting (XSS) XSS is a case of (HTML)
Network Security Web Security Anna Sperotto, Ramin Sadre Design and Analysis of Communication Systems Group University of Twente, 2012 Cross Site Scripting Cross Side Scripting (XSS) XSS is a case of (HTML)
Client vs. Server Implementations of Mitigating XSS Security Threats on Web Applications
 Journal of Basic and Applied Engineering Research pp. 50-54 Krishi Sanskriti Publications http://www.krishisanskriti.org/jbaer.html Client vs. Server Implementations of Mitigating XSS Security Threats
Journal of Basic and Applied Engineering Research pp. 50-54 Krishi Sanskriti Publications http://www.krishisanskriti.org/jbaer.html Client vs. Server Implementations of Mitigating XSS Security Threats
Portals and Hosted Files
 12 Portals and Hosted Files This chapter introduces Progress Rollbase Portals, portal pages, portal visitors setup and management, portal access control and login/authentication and recommended guidelines
12 Portals and Hosted Files This chapter introduces Progress Rollbase Portals, portal pages, portal visitors setup and management, portal access control and login/authentication and recommended guidelines
Web Application Worms & Browser Insecurity
 Web Application Worms & Browser Insecurity Mike Shema Welcome Background Hacking Exposed: Web Applications The Anti-Hacker Toolkit Hack Notes: Web Security Currently working at Qualys
Web Application Worms & Browser Insecurity Mike Shema Welcome Background Hacking Exposed: Web Applications The Anti-Hacker Toolkit Hack Notes: Web Security Currently working at Qualys
WompMobile Technical FAQ
 WompMobile Technical FAQ What are the technical benefits of WompMobile? The mobile site has the same exact URL as the desktop website. The mobile site automatically and instantly syncs with the desktop
WompMobile Technical FAQ What are the technical benefits of WompMobile? The mobile site has the same exact URL as the desktop website. The mobile site automatically and instantly syncs with the desktop
Where every interaction matters.
 Where every interaction matters. Peer 1 Vigilant Web Application Firewall Powered by Alert Logic The Open Web Application Security Project (OWASP) Top Ten Web Security Risks and Countermeasures White Paper
Where every interaction matters. Peer 1 Vigilant Web Application Firewall Powered by Alert Logic The Open Web Application Security Project (OWASP) Top Ten Web Security Risks and Countermeasures White Paper
Gateway Apps - Security Summary SECURITY SUMMARY
 Gateway Apps - Security Summary SECURITY SUMMARY 27/02/2015 Document Status Title Harmony Security summary Author(s) Yabing Li Version V1.0 Status draft Change Record Date Author Version Change reference
Gateway Apps - Security Summary SECURITY SUMMARY 27/02/2015 Document Status Title Harmony Security summary Author(s) Yabing Li Version V1.0 Status draft Change Record Date Author Version Change reference
A Tale of the Weaknesses of Current Client-Side XSS Filtering
 Call To Arms: A Tale of the Weaknesses of Current Client-Side XSS Filtering Martin Johns, Ben Stock, Sebastian Lekies About us Martin Johns, Ben Stock, Sebastian Lekies Security Researchers at SAP, Uni
Call To Arms: A Tale of the Weaknesses of Current Client-Side XSS Filtering Martin Johns, Ben Stock, Sebastian Lekies About us Martin Johns, Ben Stock, Sebastian Lekies Security Researchers at SAP, Uni
Concur Travel & Expense
 Concur Travel & Expense Supported Configurations Client Version Contents Supported Configurations... 1 Section 1: About Concur Travel & Expense... 1 Section 2: Read This First... 1 Browser Settings General...
Concur Travel & Expense Supported Configurations Client Version Contents Supported Configurations... 1 Section 1: About Concur Travel & Expense... 1 Section 2: Read This First... 1 Browser Settings General...
How To Protect Yourself From A Phisher From A Browser History Sniffer
 Invasive Browser Sniffing and Countermeasures Markus Jakobsson Indiana University Bloomington, Indiana USA markus@indiana.edu Sid Stamm Indiana University Bloomington, Indiana USA sstamm@cs.indiana.edu
Invasive Browser Sniffing and Countermeasures Markus Jakobsson Indiana University Bloomington, Indiana USA markus@indiana.edu Sid Stamm Indiana University Bloomington, Indiana USA sstamm@cs.indiana.edu
Drag and Drop in HTML5
 Drag and Drop in HTML5 T-111.5502 Seminar on Media Technology B P Final Report Hannu Järvinen Department of Media Technology Aalto University, P.O. Box 15400, 00076 Aalto hannu.jarvinen@aalto.fi Abstract
Drag and Drop in HTML5 T-111.5502 Seminar on Media Technology B P Final Report Hannu Järvinen Department of Media Technology Aalto University, P.O. Box 15400, 00076 Aalto hannu.jarvinen@aalto.fi Abstract
2X Cloud Portal v10.5
 2X Cloud Portal v10.5 URL: www.2x.com E-mail: info@2x.com Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless otherwise
2X Cloud Portal v10.5 URL: www.2x.com E-mail: info@2x.com Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless otherwise
WEB ATTACKS AND COUNTERMEASURES
 WEB ATTACKS AND COUNTERMEASURES February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in
WEB ATTACKS AND COUNTERMEASURES February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in
An Insight into Cookie Security
 An Insight into Cookie Security Today most websites and web based applications use cookies. Cookies are primarily used by the web server to track an authenticated user or other user specific details. This
An Insight into Cookie Security Today most websites and web based applications use cookies. Cookies are primarily used by the web server to track an authenticated user or other user specific details. This
Next Generation Clickjacking
 Next Generation Clickjacking New attacks against framed web pages Black Hat Europe, 14 th April 2010 Paul Stone paul.stone@contextis.co.uk Coming Up Quick Introduction to Clickjacking Four New Cross-Browser
Next Generation Clickjacking New attacks against framed web pages Black Hat Europe, 14 th April 2010 Paul Stone paul.stone@contextis.co.uk Coming Up Quick Introduction to Clickjacking Four New Cross-Browser
Web Application Security
 Web Application Security The OWASP Foundation Securing the application Input validation Authorization Session mgmt Config mgmt Authenticatio n Error handling Web server App server DB server Secure storage
Web Application Security The OWASP Foundation Securing the application Input validation Authorization Session mgmt Config mgmt Authenticatio n Error handling Web server App server DB server Secure storage
We are still vulnerable to clickjacking attacks: about 99% of Korean websites are dangerous
 We are still vulnerable to clickjacking attacks: about 99% of Korean websites are dangerous Daehyun Kim and Hyoungshick Kim Department of Computer Science and Engineering, Sungkyunkwan University, Republic
We are still vulnerable to clickjacking attacks: about 99% of Korean websites are dangerous Daehyun Kim and Hyoungshick Kim Department of Computer Science and Engineering, Sungkyunkwan University, Republic
Cross Site Scripting Prevention
 Project Report CS 649 : Network Security Cross Site Scripting Prevention Under Guidance of Prof. Bernard Menezes Submitted By Neelamadhav (09305045) Raju Chinthala (09305056) Kiran Akipogu (09305074) Vijaya
Project Report CS 649 : Network Security Cross Site Scripting Prevention Under Guidance of Prof. Bernard Menezes Submitted By Neelamadhav (09305045) Raju Chinthala (09305056) Kiran Akipogu (09305074) Vijaya
Adobe Flash Player and Adobe AIR security
 Adobe Flash Player and Adobe AIR security Both Adobe Flash Platform runtimes Flash Player and AIR include built-in security and privacy features to provide strong protection for your data and privacy,
Adobe Flash Player and Adobe AIR security Both Adobe Flash Platform runtimes Flash Player and AIR include built-in security and privacy features to provide strong protection for your data and privacy,
KUB Website Troubleshooting
 KUB Website Troubleshooting Are you having problems getting to the KUB website at http://www.kub.org/? If you type in your user ID and password and press the login button, are you routed right back to
KUB Website Troubleshooting Are you having problems getting to the KUB website at http://www.kub.org/? If you type in your user ID and password and press the login button, are you routed right back to
The Prevalence of Flash Vulnerabilities on the Web
 TECHNICAL BRIEF FLASH FLOODING The Prevalence of Flash Vulnerabilities on the Web Adobe Flash Player is a cross-platform, browser plugin that provides uncompromised viewing of expressive applications,
TECHNICAL BRIEF FLASH FLOODING The Prevalence of Flash Vulnerabilities on the Web Adobe Flash Player is a cross-platform, browser plugin that provides uncompromised viewing of expressive applications,
Web Tracking for You. Gregory Fleischer
 Web Tracking for You Gregory Fleischer 1 INTRODUCTION 2 Me Gregory Fleischer Senior Security Consultant at FishNet Security 3 Disclaimer Why do you hate? 4 Reasons For Tracking TradiFonal reasons for tracking
Web Tracking for You Gregory Fleischer 1 INTRODUCTION 2 Me Gregory Fleischer Senior Security Consultant at FishNet Security 3 Disclaimer Why do you hate? 4 Reasons For Tracking TradiFonal reasons for tracking
SSL VPN Technology White Paper
 SSL VPN Technology White Paper Keywords: SSL VPN, HTTPS, Web access, TCP access, IP access Abstract: SSL VPN is an emerging VPN technology based on HTTPS. This document describes its implementation and
SSL VPN Technology White Paper Keywords: SSL VPN, HTTPS, Web access, TCP access, IP access Abstract: SSL VPN is an emerging VPN technology based on HTTPS. This document describes its implementation and
What is Web Security? Motivation
 brucker@inf.ethz.ch http://www.brucker.ch/ Information Security ETH Zürich Zürich, Switzerland Information Security Fundamentals March 23, 2004 The End Users View The Server Providers View What is Web
brucker@inf.ethz.ch http://www.brucker.ch/ Information Security ETH Zürich Zürich, Switzerland Information Security Fundamentals March 23, 2004 The End Users View The Server Providers View What is Web
Client Side Filter Enhancement using Web Proxy
 Client Side Filter Enhancement using Web Proxy Santosh Kumar Singh 1, Rahul Shrivastava 2 1 M Tech Scholar, Computer Technology (CSE) RCET, Bhilai (CG) India, 2 Assistant Professor, CSE Department, RCET
Client Side Filter Enhancement using Web Proxy Santosh Kumar Singh 1, Rahul Shrivastava 2 1 M Tech Scholar, Computer Technology (CSE) RCET, Bhilai (CG) India, 2 Assistant Professor, CSE Department, RCET
Five Tips to Reduce Risk From Modern Web Threats
 Five Tips to Reduce Risk From Modern Web Threats By Chris McCormack, Senior Product Marketing Manager and Chester Wisniewski, Senior Security Advisor Modern web threats can infect your network, subvert
Five Tips to Reduce Risk From Modern Web Threats By Chris McCormack, Senior Product Marketing Manager and Chester Wisniewski, Senior Security Advisor Modern web threats can infect your network, subvert
Concur Travel & Expense
 Concur Travel & Expense Supported Configurations Client Version Contents Supported Configurations... 1 Section 1: About Concur Travel & Expense... 1 Section 2: Read This First... 1 Browser Settings General...
Concur Travel & Expense Supported Configurations Client Version Contents Supported Configurations... 1 Section 1: About Concur Travel & Expense... 1 Section 2: Read This First... 1 Browser Settings General...
Web Application Security
 Web Application Security A Beginner's Guide Bryan Sullivan Vincent Liu Mc r New York Chicago San Francisco Lisbon London Madrid Mexico City Milan New Delhi San Juan Seoul Singapore Sydney Toronto Contents
Web Application Security A Beginner's Guide Bryan Sullivan Vincent Liu Mc r New York Chicago San Francisco Lisbon London Madrid Mexico City Milan New Delhi San Juan Seoul Singapore Sydney Toronto Contents
Google Analytics for Robust Website Analytics. Deepika Verma, Depanwita Seal, Atul Pandey
 1 Google Analytics for Robust Website Analytics Deepika Verma, Depanwita Seal, Atul Pandey 2 Table of Contents I. INTRODUCTION...3 II. Method for obtaining data for web analysis...3 III. Types of metrics
1 Google Analytics for Robust Website Analytics Deepika Verma, Depanwita Seal, Atul Pandey 2 Table of Contents I. INTRODUCTION...3 II. Method for obtaining data for web analysis...3 III. Types of metrics
Online Data Services. Security Guidelines. Online Data Services by Esri UK. Security Best Practice
 Online Data Services Security Guidelines Online Data Services by Esri UK Security Best Practice 28 November 2014 Contents Contents... 1 1. Introduction... 2 2. Data Service Accounts, Security and Fair
Online Data Services Security Guidelines Online Data Services by Esri UK Security Best Practice 28 November 2014 Contents Contents... 1 1. Introduction... 2 2. Data Service Accounts, Security and Fair
Michael Seltzer COMP 116: Security Final Paper. Client Side Encryption in the Web Browser Mentor: Ming Chow
 Michael Seltzer COMP 116: Security Final Paper Client Side Encryption in the Web Browser Mentor: Ming Chow 1 Abstract Web service providers generally look to encryption as a means of ensuring data privacy
Michael Seltzer COMP 116: Security Final Paper Client Side Encryption in the Web Browser Mentor: Ming Chow 1 Abstract Web service providers generally look to encryption as a means of ensuring data privacy
M86 Web Filter USER GUIDE for M86 Mobile Security Client. Software Version: 5.0.00 Document Version: 02.01.12
 M86 Web Filter USER GUIDE for M86 Mobile Security Client Software Version: 5.0.00 Document Version: 02.01.12 M86 WEB FILTER USER GUIDE FOR M86 MOBILE SECURITY CLIENT 2012 M86 Security All rights reserved.
M86 Web Filter USER GUIDE for M86 Mobile Security Client Software Version: 5.0.00 Document Version: 02.01.12 M86 WEB FILTER USER GUIDE FOR M86 MOBILE SECURITY CLIENT 2012 M86 Security All rights reserved.
Information Supplement: Requirement 6.6 Code Reviews and Application Firewalls Clarified
 Standard: Data Security Standard (DSS) Requirement: 6.6 Date: February 2008 Information Supplement: Requirement 6.6 Code Reviews and Application Firewalls Clarified Release date: 2008-04-15 General PCI
Standard: Data Security Standard (DSS) Requirement: 6.6 Date: February 2008 Information Supplement: Requirement 6.6 Code Reviews and Application Firewalls Clarified Release date: 2008-04-15 General PCI
The Devil is Phishing: Rethinking Web Single Sign On Systems Security. Chuan Yue USENIX Workshop on Large Scale Exploits
 The Devil is Phishing: Rethinking Web Single Sign On Systems Security Chuan Yue USENIX Workshop on Large Scale Exploits and Emergent Threats (LEET 2013) Web Single Sign On (SSO) systems Sign in multiple
The Devil is Phishing: Rethinking Web Single Sign On Systems Security Chuan Yue USENIX Workshop on Large Scale Exploits and Emergent Threats (LEET 2013) Web Single Sign On (SSO) systems Sign in multiple
An Evaluation of the Google Chrome Extension Security Architecture
 An Evaluation of the Google Chrome Extension Security Architecture Nicholas Carlini, Adrienne Porter Felt, and David Wagner University of California, Berkeley nicholas.carlini@berkeley.edu, apf@cs.berkeley.edu,
An Evaluation of the Google Chrome Extension Security Architecture Nicholas Carlini, Adrienne Porter Felt, and David Wagner University of California, Berkeley nicholas.carlini@berkeley.edu, apf@cs.berkeley.edu,
Chapter-1 : Introduction 1 CHAPTER - 1. Introduction
 Chapter-1 : Introduction 1 CHAPTER - 1 Introduction This thesis presents design of a new Model of the Meta-Search Engine for getting optimized search results. The focus is on new dimension of internet
Chapter-1 : Introduction 1 CHAPTER - 1 Introduction This thesis presents design of a new Model of the Meta-Search Engine for getting optimized search results. The focus is on new dimension of internet
FIVE WAYS TO OPTIMIZE MOBILE WEBSITE PERFORMANCE WITH PAGE SPEED
 WHITE PAPER: MOBILE WEBSITE PERFORMANCE FIVE WAYS TO OPTIMIZE MOBILE WEBSITE PERFORMANCE WITH PAGE SPEED SNOOZE, YOU LOSE. TODAY S MOBILE USERS EXPECT PERFORMANCE DELIVERED FAST. For those of us who depend
WHITE PAPER: MOBILE WEBSITE PERFORMANCE FIVE WAYS TO OPTIMIZE MOBILE WEBSITE PERFORMANCE WITH PAGE SPEED SNOOZE, YOU LOSE. TODAY S MOBILE USERS EXPECT PERFORMANCE DELIVERED FAST. For those of us who depend
Sophistication of attacks will keep improving, especially APT and zero-day exploits
 FAQ Isla Q&A General What is Isla? Isla is an innovative, enterprise-class web malware isolation system that prevents all browser-borne malware from penetrating corporate networks and infecting endpoint
FAQ Isla Q&A General What is Isla? Isla is an innovative, enterprise-class web malware isolation system that prevents all browser-borne malware from penetrating corporate networks and infecting endpoint
Cryptography for Software and Web Developers
 Cryptography for Software and Web Developers Part 1: Web and Crypto Hanno Böck 2014-05-28 1 / 14 HTTP and HTTPS SSL Stripping Cookies Mixed content HTTPS content, HTTP images Many webpages use some kind
Cryptography for Software and Web Developers Part 1: Web and Crypto Hanno Böck 2014-05-28 1 / 14 HTTP and HTTPS SSL Stripping Cookies Mixed content HTTPS content, HTTP images Many webpages use some kind
[state of the internet] / SEO Attacks. Threat Advisory: Continuous Uptick in SEO Attacks
![[state of the internet] / SEO Attacks. Threat Advisory: Continuous Uptick in SEO Attacks [state of the internet] / SEO Attacks. Threat Advisory: Continuous Uptick in SEO Attacks](/thumbs/36/17600806.jpg) TLP: GREEN Issue Date: 1.12.16 Threat Advisory: Continuous Uptick in SEO Attacks Risk Factor High The Akamai Threat Research Team has identified a highly sophisticated Search Engine Optimization (SEO)
TLP: GREEN Issue Date: 1.12.16 Threat Advisory: Continuous Uptick in SEO Attacks Risk Factor High The Akamai Threat Research Team has identified a highly sophisticated Search Engine Optimization (SEO)
Cache Cookies for Browser Authentication (Extended Abstract)
 Cache Cookies for Browser Authentication (Extended Abstract) Ari Juels Markus Jakobsson Tom N. Jagatic RSA Laboratories and Indiana University and Indiana University RavenWhite Inc. RavenWhite Inc. ajuels@rsasecurity.com
Cache Cookies for Browser Authentication (Extended Abstract) Ari Juels Markus Jakobsson Tom N. Jagatic RSA Laboratories and Indiana University and Indiana University RavenWhite Inc. RavenWhite Inc. ajuels@rsasecurity.com
LASTLINE WHITEPAPER. Large-Scale Detection of Malicious Web Pages
 LASTLINE WHITEPAPER Large-Scale Detection of Malicious Web Pages Abstract Malicious web pages that host drive-by-download exploits have become a popular means for compromising hosts on the Internet and,
LASTLINE WHITEPAPER Large-Scale Detection of Malicious Web Pages Abstract Malicious web pages that host drive-by-download exploits have become a popular means for compromising hosts on the Internet and,
Web-Application Security
 Web-Application Security Kristian Beilke Arbeitsgruppe Sichere Identität Fachbereich Mathematik und Informatik Freie Universität Berlin 29. Juni 2011 Overview Web Applications SQL Injection XSS Bad Practice
Web-Application Security Kristian Beilke Arbeitsgruppe Sichere Identität Fachbereich Mathematik und Informatik Freie Universität Berlin 29. Juni 2011 Overview Web Applications SQL Injection XSS Bad Practice
Installation and usage of SSL certificates: Your guide to getting it right
 Installation and usage of SSL certificates: Your guide to getting it right So, you ve bought your SSL Certificate(s). Buying your certificate is only the first of many steps involved in securing your website.
Installation and usage of SSL certificates: Your guide to getting it right So, you ve bought your SSL Certificate(s). Buying your certificate is only the first of many steps involved in securing your website.
A more detailed list of types of fingerprinting is included below. A similar definition is provided by [[RFC6973]].
![A more detailed list of types of fingerprinting is included below. A similar definition is provided by [[RFC6973]]. A more detailed list of types of fingerprinting is included below. A similar definition is provided by [[RFC6973]].](/thumbs/33/16290060.jpg) This is the abstract for your specification. What is fingerprinting? In short, browser fingerprinting is the capability of a site to identify or re-identify a visiting user, user agent or device via configuration
This is the abstract for your specification. What is fingerprinting? In short, browser fingerprinting is the capability of a site to identify or re-identify a visiting user, user agent or device via configuration
Cross-Site Scripting
 Cross-Site Scripting (XSS) Computer and Network Security Seminar Fabrice Bodmer (fabrice.bodmer@unifr.ch) UNIFR - Winter Semester 2006-2007 XSS: Table of contents What is Cross-Site Scripting (XSS)? Some
Cross-Site Scripting (XSS) Computer and Network Security Seminar Fabrice Bodmer (fabrice.bodmer@unifr.ch) UNIFR - Winter Semester 2006-2007 XSS: Table of contents What is Cross-Site Scripting (XSS)? Some
DRIVE-BY DOWNLOAD WHAT IS DRIVE-BY DOWNLOAD? A Typical Attack Scenario
 DRIVE-BY DOWNLOAD WHAT IS DRIVE-BY DOWNLOAD? Drive-by Downloads are a common technique used by attackers to silently install malware on a victim s computer. Once a target website has been weaponized with
DRIVE-BY DOWNLOAD WHAT IS DRIVE-BY DOWNLOAD? Drive-by Downloads are a common technique used by attackers to silently install malware on a victim s computer. Once a target website has been weaponized with
Protecting Browser State from Web Privacy Attacks. Collin Jackson, Andrew Bortz, Dan Boneh, John Mitchell Stanford University
 Protecting Browser State from Web Privacy Attacks Collin Jackson, Andrew Bortz, Dan Boneh, John Mitchell Stanford University Context-aware Phishing Bank of America customers see: Wells Fargo customers
Protecting Browser State from Web Privacy Attacks Collin Jackson, Andrew Bortz, Dan Boneh, John Mitchell Stanford University Context-aware Phishing Bank of America customers see: Wells Fargo customers
EVALUATING COMMERCIAL WEB APPLICATION SECURITY. By Aaron Parke
 EVALUATING COMMERCIAL WEB APPLICATION SECURITY By Aaron Parke Outline Project background What and why? Targeted sites Testing process Burp s findings Technical talk My findings and thoughts Questions Project
EVALUATING COMMERCIAL WEB APPLICATION SECURITY By Aaron Parke Outline Project background What and why? Targeted sites Testing process Burp s findings Technical talk My findings and thoughts Questions Project
Enterprise Application Security Workshop Series
 Enterprise Application Security Workshop Series Phone 877-697-2434 fax 877-697-2434 www.thesagegrp.com Defending JAVA Applications (3 Days) In The Sage Group s Defending JAVA Applications workshop, participants
Enterprise Application Security Workshop Series Phone 877-697-2434 fax 877-697-2434 www.thesagegrp.com Defending JAVA Applications (3 Days) In The Sage Group s Defending JAVA Applications workshop, participants
Content Filtering Client Policy & Reporting Administrator s Guide
 Content Filtering Client Policy & Reporting Administrator s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION
Content Filtering Client Policy & Reporting Administrator s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION
End User Devices Security Guidance: Apple ios 8
 GOV.UK Guidance End User Devices Security Guidance: Apple ios 8 Published Contents 1. Changes since previous guidance 2. Usage scenario 3. Summary of platform security 4. How the platform can best satisfy
GOV.UK Guidance End User Devices Security Guidance: Apple ios 8 Published Contents 1. Changes since previous guidance 2. Usage scenario 3. Summary of platform security 4. How the platform can best satisfy
User s guide. Version 2.0. August 2010 1 / 23
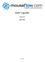 User s guide Version 2.0 August 2010 1 / 23 1 CONTENTS 2 Introduction... 3 2.1 What is Mouseflow?... 3 2.2 What can Mouseflow be used for?... 3 2.3 How does Mouseflow work?... 3 2.4 Who is the target audience?...
User s guide Version 2.0 August 2010 1 / 23 1 CONTENTS 2 Introduction... 3 2.1 What is Mouseflow?... 3 2.2 What can Mouseflow be used for?... 3 2.3 How does Mouseflow work?... 3 2.4 Who is the target audience?...
Release Notes for Websense Web Endpoint (32- and 64-bit OS)
 Release Notes for Websense Web Endpoint (32- and 64-bit OS) Updated: 8-Feb-2013 Applies To: Websense Cloud Web Security solutions Use the Release Notes to learn about: What s new in Websense Web Endpoint?
Release Notes for Websense Web Endpoint (32- and 64-bit OS) Updated: 8-Feb-2013 Applies To: Websense Cloud Web Security solutions Use the Release Notes to learn about: What s new in Websense Web Endpoint?
Web Security: SSL/TLS
 CSE 484 / CSE M 584: Computer Security and Privacy Web Security: SSL/TLS Spring 2015 Franziska (Franzi) Roesner franzi@cs.washington.edu Thanks to Dan Boneh, Dieter Gollmann, Dan Halperin, Yoshi Kohno,
CSE 484 / CSE M 584: Computer Security and Privacy Web Security: SSL/TLS Spring 2015 Franziska (Franzi) Roesner franzi@cs.washington.edu Thanks to Dan Boneh, Dieter Gollmann, Dan Halperin, Yoshi Kohno,
Microsoft TMG Replacement with NetScaler
 Microsoft TMG Replacement with NetScaler Replacing Microsoft Forefront TMG with NetScaler for Optimization This deployment guide focuses on replacing Microsoft Forefront Threat Management Gateway (TMG)
Microsoft TMG Replacement with NetScaler Replacing Microsoft Forefront TMG with NetScaler for Optimization This deployment guide focuses on replacing Microsoft Forefront Threat Management Gateway (TMG)
Recommended Practice Case Study: Cross-Site Scripting. February 2007
 Recommended Practice Case Study: Cross-Site Scripting February 2007 iii ACKNOWLEDGEMENT This document was developed for the U.S. Department of Homeland Security to provide guidance for control system cyber
Recommended Practice Case Study: Cross-Site Scripting February 2007 iii ACKNOWLEDGEMENT This document was developed for the U.S. Department of Homeland Security to provide guidance for control system cyber
Web Browsing Quality of Experience Score
 Web Browsing Quality of Experience Score A Sandvine Technology Showcase Contents Executive Summary... 1 Introduction to Web QoE... 2 Sandvine s Web Browsing QoE Metric... 3 Maintaining a Web Page Library...
Web Browsing Quality of Experience Score A Sandvine Technology Showcase Contents Executive Summary... 1 Introduction to Web QoE... 2 Sandvine s Web Browsing QoE Metric... 3 Maintaining a Web Page Library...
Password Managers: Attacks and Defenses
 Password Managers: Attacks and Defenses David Silver, Suman Jana, and Dan Boneh, Stanford University; Eric Chen and Collin Jackson, Carnegie Mellon University https://www.usenix.org/conference/usenixsecurity14/technical-sessions/presentation/silver
Password Managers: Attacks and Defenses David Silver, Suman Jana, and Dan Boneh, Stanford University; Eric Chen and Collin Jackson, Carnegie Mellon University https://www.usenix.org/conference/usenixsecurity14/technical-sessions/presentation/silver
Enterprise Apps: Bypassing the Gatekeeper
 Enterprise Apps: Bypassing the Gatekeeper By Avi Bashan and Ohad Bobrov Executive Summary The Apple App Store is a major part of the ios security paradigm, offering a central distribution process that
Enterprise Apps: Bypassing the Gatekeeper By Avi Bashan and Ohad Bobrov Executive Summary The Apple App Store is a major part of the ios security paradigm, offering a central distribution process that
SAFE-T RSACCESS REPLACEMENT FOR MICROSOFT FOREFRONT UNIFIED ACCESS GATEWAY (UAG)
 SAFE-T RSACCESS REPLACEMENT FOR MICROSOFT FOREFRONT UNIFIED ACCESS GATEWAY (UAG) A RSACCESS WHITE PAPER 1 Microsoft Forefront Unified Access Gateway Overview 2 Safe-T RSAccess Secure Front-end Overview
SAFE-T RSACCESS REPLACEMENT FOR MICROSOFT FOREFRONT UNIFIED ACCESS GATEWAY (UAG) A RSACCESS WHITE PAPER 1 Microsoft Forefront Unified Access Gateway Overview 2 Safe-T RSAccess Secure Front-end Overview
Phishing by data URI
 Phishing by data URI Henning Klevjer henning@klevjers.com October 22, 2012 1 Abstract Historically, phishing web pages have been hosted by web servers that are either compromised or owned by the attacker.
Phishing by data URI Henning Klevjer henning@klevjers.com October 22, 2012 1 Abstract Historically, phishing web pages have been hosted by web servers that are either compromised or owned by the attacker.
Web Forms for Marketers 2.3 for Sitecore CMS 6.5 and
 Web Forms for Marketers 2.3 for Sitecore CMS 6.5 and later User Guide Rev: 2013-02-01 Web Forms for Marketers 2.3 for Sitecore CMS 6.5 and later User Guide A practical guide to creating and managing web
Web Forms for Marketers 2.3 for Sitecore CMS 6.5 and later User Guide Rev: 2013-02-01 Web Forms for Marketers 2.3 for Sitecore CMS 6.5 and later User Guide A practical guide to creating and managing web
Why Johnny Can t Browse in Peace: On the Uniqueness of Web Browsing History Patterns
 Why Johnny Can t Browse in Peace: On the Uniqueness of Web Browsing History Patterns Łukasz Olejnik 1, Claude Castelluccia 2, Artur Janc 3 1 INRIA, Grenoble, France, lukasz.olejnik@inria.fr 2 INRIA, Grenoble,
Why Johnny Can t Browse in Peace: On the Uniqueness of Web Browsing History Patterns Łukasz Olejnik 1, Claude Castelluccia 2, Artur Janc 3 1 INRIA, Grenoble, France, lukasz.olejnik@inria.fr 2 INRIA, Grenoble,
Locking down a Hitachi ID Suite server
 Locking down a Hitachi ID Suite server 2016 Hitachi ID Systems, Inc. All rights reserved. Organizations deploying Hitachi ID Identity and Access Management Suite need to understand how to secure its runtime
Locking down a Hitachi ID Suite server 2016 Hitachi ID Systems, Inc. All rights reserved. Organizations deploying Hitachi ID Identity and Access Management Suite need to understand how to secure its runtime
Sophos Mobile Control as a Service Startup guide. Product version: 3.5
 Sophos Mobile Control as a Service Startup guide Product version: 3.5 Document date: August 2013 Contents 1 About this guide...3 2 What are the key steps?...4 3 First login...5 4 Change your administrator
Sophos Mobile Control as a Service Startup guide Product version: 3.5 Document date: August 2013 Contents 1 About this guide...3 2 What are the key steps?...4 3 First login...5 4 Change your administrator
How To Protect A Web Application From Attack From A Trusted Environment
 Standard: Version: Date: Requirement: Author: PCI Data Security Standard (PCI DSS) 1.2 October 2008 6.6 PCI Security Standards Council Information Supplement: Application Reviews and Web Application Firewalls
Standard: Version: Date: Requirement: Author: PCI Data Security Standard (PCI DSS) 1.2 October 2008 6.6 PCI Security Standards Council Information Supplement: Application Reviews and Web Application Firewalls
DESTINATION MELBOURNE PRIVACY POLICY
 DESTINATION MELBOURNE PRIVACY POLICY 2 Destination Melbourne Privacy Policy Statement Regarding Privacy Policy Destination Melbourne Limited recognises the importance of protecting the privacy of personally
DESTINATION MELBOURNE PRIVACY POLICY 2 Destination Melbourne Privacy Policy Statement Regarding Privacy Policy Destination Melbourne Limited recognises the importance of protecting the privacy of personally
Cookies and Your Privacy
 White Paper - October 2009 Cookies and Your Privacy Anyone who uses computers today should be concerned about privacy and security. Any time your computer connects to the outside world, you run the risk
White Paper - October 2009 Cookies and Your Privacy Anyone who uses computers today should be concerned about privacy and security. Any time your computer connects to the outside world, you run the risk
Windows Remote Access
 Windows Remote Access A newsletter for IT Professionals Education Sector Updates Issue 1 I. Background of Remote Desktop for Windows Remote Desktop Protocol (RDP) is a proprietary protocol developed by
Windows Remote Access A newsletter for IT Professionals Education Sector Updates Issue 1 I. Background of Remote Desktop for Windows Remote Desktop Protocol (RDP) is a proprietary protocol developed by
Technical Guide for Remote access
 Technical Guide for Remote access Frequently Asked Questions about using EZ Proxy to access Library resources off campus. Login Help Who is allowed access? I m having trouble logging in. Finding Articles
Technical Guide for Remote access Frequently Asked Questions about using EZ Proxy to access Library resources off campus. Login Help Who is allowed access? I m having trouble logging in. Finding Articles
Architecture and Data Flow Overview. BlackBerry Enterprise Service 10 721-08877-123 Version: 10.2. Quick Reference
 Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Bypassing Internet Explorer s XSS Filter
 Bypassing Internet Explorer s XSS Filter Or: Oops, that s not supposed to happen. Carlos @RTWaysea About Me Mechanical Drafting Background Engine parts, Architectural fixtures, etc. Friend said Try This
Bypassing Internet Explorer s XSS Filter Or: Oops, that s not supposed to happen. Carlos @RTWaysea About Me Mechanical Drafting Background Engine parts, Architectural fixtures, etc. Friend said Try This
Administrator s Guide
 SEO Toolkit 1.3.0 for Sitecore CMS 6.5 Administrator s Guide Rev: 2011-06-07 SEO Toolkit 1.3.0 for Sitecore CMS 6.5 Administrator s Guide How to use the Search Engine Optimization Toolkit to optimize your
SEO Toolkit 1.3.0 for Sitecore CMS 6.5 Administrator s Guide Rev: 2011-06-07 SEO Toolkit 1.3.0 for Sitecore CMS 6.5 Administrator s Guide How to use the Search Engine Optimization Toolkit to optimize your
Mobile Application Performance Report
 Mobile Application Performance Report Optimization Recommendations and Performance Analysis Report Prepared for - http://www.google.com VS http://www.yahoo.com Emulated Device Type: ipad OVERALL PERFORMANCE
Mobile Application Performance Report Optimization Recommendations and Performance Analysis Report Prepared for - http://www.google.com VS http://www.yahoo.com Emulated Device Type: ipad OVERALL PERFORMANCE
Sitefinity Security and Best Practices
 Sitefinity Security and Best Practices Table of Contents Overview The Ten Most Critical Web Application Security Risks Injection Cross-Site-Scripting (XSS) Broken Authentication and Session Management
Sitefinity Security and Best Practices Table of Contents Overview The Ten Most Critical Web Application Security Risks Injection Cross-Site-Scripting (XSS) Broken Authentication and Session Management
Using a Malicious Proxy to Pilfer Data & Wreak Havoc. Edward J. Zaborowski ed@thezees.net
 Using a Malicious Proxy to Pilfer Data & Wreak Havoc Edward J. Zaborowski ed@thezees.net Abstract...3 Malicious Web Proxy...3 Becoming the Proxy...3 ARP Spoofing...3 Static Configuration...3 Web Proxy
Using a Malicious Proxy to Pilfer Data & Wreak Havoc Edward J. Zaborowski ed@thezees.net Abstract...3 Malicious Web Proxy...3 Becoming the Proxy...3 ARP Spoofing...3 Static Configuration...3 Web Proxy
Websense Web Security Solutions. Websense Web Security Gateway Websense Web Security Websense Web Filter Websense Hosted Web Security
 Web Security Gateway Web Security Web Filter Hosted Web Security Web Security Solutions The Approach In the past, most Web content was static and predictable. But today s reality is that Web content even
Web Security Gateway Web Security Web Filter Hosted Web Security Web Security Solutions The Approach In the past, most Web content was static and predictable. But today s reality is that Web content even
VMware Identity Manager Administration
 VMware Identity Manager Administration VMware Identity Manager 2.6 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
VMware Identity Manager Administration VMware Identity Manager 2.6 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
WHITE PAPER. FortiWeb and the OWASP Top 10 Mitigating the most dangerous application security threats
 WHITE PAPER FortiWeb and the OWASP Top 10 PAGE 2 Introduction The Open Web Application Security project (OWASP) Top Ten provides a powerful awareness document for web application security. The OWASP Top
WHITE PAPER FortiWeb and the OWASP Top 10 PAGE 2 Introduction The Open Web Application Security project (OWASP) Top Ten provides a powerful awareness document for web application security. The OWASP Top
Deltek Touch Time & Expense for Vision 1.3. Release Notes
 Deltek Touch Time & Expense for Vision 1.3 Release Notes June 25, 2014 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or technical
Deltek Touch Time & Expense for Vision 1.3 Release Notes June 25, 2014 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or technical
Security Guide. BlackBerry Enterprise Service 12. for ios, Android, and Windows Phone. Version 12.0
 Security Guide BlackBerry Enterprise Service 12 for ios, Android, and Windows Phone Version 12.0 Published: 2015-02-06 SWD-20150206130210406 Contents About this guide... 6 What is BES12?... 7 Key features
Security Guide BlackBerry Enterprise Service 12 for ios, Android, and Windows Phone Version 12.0 Published: 2015-02-06 SWD-20150206130210406 Contents About this guide... 6 What is BES12?... 7 Key features
of firms with remote users say Web-borne attacks impacted company financials.
 Introduction As the number of users working from outside of the enterprise perimeter increases, the need for more efficient methods of securing the corporate network grows exponentially. In Part 1 of this
Introduction As the number of users working from outside of the enterprise perimeter increases, the need for more efficient methods of securing the corporate network grows exponentially. In Part 1 of this
App Isolation: Get the Security of Multiple Browsers with Just One
 App Isolation: Get the Security of Multiple Browsers with Just One Charles Reis Google, Inc. Seattle, WA creis@google.com Eric Y. Chen Carnegie Mellon University Mountain View, CA eric.chen@sv.cmu.edu
App Isolation: Get the Security of Multiple Browsers with Just One Charles Reis Google, Inc. Seattle, WA creis@google.com Eric Y. Chen Carnegie Mellon University Mountain View, CA eric.chen@sv.cmu.edu
