NY/NJ Intergovernmental Audit Forum
|
|
|
- Jayson Melton
- 7 years ago
- Views:
Transcription
1 NY/NJ Intergovernmental Audit Forum Trends in Data Analytics Fraud Detection May 4, 2016
2 Discussion Topics Introduction 5 min 2016 EY Fraud Survey 10 min Data Analytics Methodology 30 min Analytics Design Data Collection Data Analytics Explore & Risk Rank Findings & Observations Case Study 45 min Questions & Answers 10 min Page 2
3 Data and analytics core businesses will be disrupted! 1.7 MB 80% 50 billion Information is growing exponentially New info. created every minute for every human being Data is unstructured; invisible to traditional computers Things will be connected to the internet by months 14 months Computing power is increasing while cost is decreasing For computing power (analytics) to double For cost per gigabyte of storage to go down by half 30% 47% 50% The nature of work is changing Of consulting will be replaced by cognitive/ai technology Of today s job could be automated in the next two decades 94% probability for accounting and Tax Of professional services will be procured as managed service As a result of Open Data Initiative, government agency data are becoming more accessible Human beings tend to overestimate in the near term but under-estimate in the longer term I think there is a world market for maybe five computers. There is no reason for any individual to have a computer in their home. Ken Olsen Co-founder and former President of Digital Equipment Touchscreen e-readers will never catch on. The growth of the Internet will slow drastically most people have nothing to say to each other! By 2005 or so, it will become clear that the Internet s impact on the economy has been no greater than the fax machine s. Thomas Watson Chairman of IBM Bill Gates Co-founder of Microsoft Paul Krugman Economist Page 3
4 2016 EY Fraud Survey Page 4
5 Current and emerging risks driving demand The fastest-growing threat in the fraud and investigative risk universe is from cyber breaches and insider threats. FDA demand is also being driven by increasing government and public scrutiny of fraud risk. At the SEC, we have made great strides in leveraging data and technology to detect and pursue misconduct. In the enforcement arena, the Commission is using data analytics to help identify wrongdoers and conduct streamlined investigations to optimize our resources. Chair Mary Jo White, opening remarks at the 21st Annual International Institute for Securities Enforcement and Market Oversight, 2 November 2015 C-suite respondents have shown a stronger tendency toward FDA adoption than other executives. While 69% overall agree, we need to do more to improve our current anti-fraud procedures, including the use of FDA tools, this number jumps to 74% for the C-suite cohort. 74% of C-suite respondents We need to do more to improve our current anti-fraud procedures, including the use of FDA tools. Page 5
6 FDA demand is also driven by increasing government and public scrutiny of fraud risk Response to growing cybercrime risks 53% Increased regulatory scrutiny 43% Increased risk of fraud in emerging markets 32% Pressure from the board or management team Seeking greater cost efficiency in the fraud risk management process Recent fraud risk assessment findings in the organization Need for more robust third-party due diligence 26% 25% 31% 30% Increasing merger and acquisition activities 13% Increased calls to your whistle-blower line 9% Other main reasons 4% 0% 10% 20% 30% 40% 50% 60% Q. What are the main reasons that you are planning to increase your investment in FDA capabilities? Base: Respondents who plan to increase investment in FDA (405) Multiple answers allowed, may exceed 100%. Page 6
7 Growing sophistication in technology and the use of data The use of visualization tools has doubled since our 2014 survey. There has also been increasing use of social and web monitoring tools and statistical analysis and data mining packages. 75% of respondents routinely analyze a wide range of structured and unstructured data. Visualization 12% 25% Social media 21% 25% 2016 Statistical analysis 11% 18% % 5% 10% 15% 20% 25% 30% Q. Which FDA tools do you utilize in managing fraud risk? Base: 2016 all respondents (665); 2014 all respondents (466) Multiple answers allowed, may exceed 100%. Page 7
8 Key challenges: building teams with the right skills Successful deployment requires three distinct skill sets: Technical skills to understand the organization s systems and advise on acquiring additional technology Domain knowledge familiarity with the relevant risk areas in the business and the ability to interpret analytics results in the context of the organization Data analytics (e.g., data science) expertise mathematical, computer science and business intelligence techniques, such as pattern recognition, statistical analysis, query design and data visualization According to Gartner, the need for data scientists is growing at about three times that for statisticians and business intelligence analysts, and there is an anticipated talent shortage of 100,000 or more analytics personnel through Page 8
9 Key challenges: deploying the right technology Respondents continue to rate challenges in combining data sources as the top issue to overcome when implementing FDA. Building data sets that talk to one another is the first step to successful analytics. One key obstacle to moving to more advanced tools appears to be the lack of funding. However, analytics technology has improved, making deployment and accessibility easier. More self-service applications are available via cloud that require less customization to implement. Significant improvements in computing power and scalability (i.e., Hadoop) combined with ever-decreasing storage costs make the use of FDA more cost effective. Page 9
10 Many have reported positive results or recoveries from the FDA tools 56% agree We currently get positive results or recoveries from the FDA tools that we use. Page 10
11 Data Analytics Methodology Page 11
12 Analytics Implementation Methodology Management Ownership and Involvement Analytics Design Data Collection Data Analytics Explore & Risk Rank Findings & Observations ACTIVITIES DELIVERABLE Identify risks based on industry and client knowledge Understand data systems and business processes Develop workplan to define tests Refine engagement timeline Analytics work plan Work with client IT to identify & export and validate data Asses data integrity and completeness Perform data reasonableness checks Load, normalize, cleanse, and transform data, as needed Data requests Control totals and inventory Execute previously identified analytics plan Modify analytics as appropriate based on data received, client feedback and preliminary results Preliminary results for QC Visualize analytical results and develop dashboards Develop scoring model to risk rank transactions Visualized dashboards Risk model Identify trends and risk areas Quantify potential risks Conduct a briefing with key stakeholders Determine remediation actions and track dispositions Findings and observations Action plan Page 12
13 (1) Analytics Design Page 13
14 Risk quadrants Macro view 1 Analytics Design Page 14
15 ACFE 2014 Report to the Nations and fraud scheme discussion 1 Analytics Design Page 15
16 Transparency International 2014 Corruption Perceptions Index 1 Analytics Design Page 16
17 1 Trends and leading practices in analytics What we are seeing Analytics Design More precision in compliance program and operational assessments by sophisticated clients Increased operationalizing of compliance processes for specific risks Advanced data analytics to facilitate risk based continuous monitoring Legal and regulatory risks Bribery and corruption Third-party integrity Export controls/itar US Government business risks Cost accounting DFARS business systems Mandatory disclosure Cost structure simplification and cost reduction Claims and disputes Suppliers and pricing Technology risks Data privacy Cyber security Cloud computing and big data Data management requirements for investigations Page 17
18 (2) Data Collection Page 18
19 Addressing risks by combining multiple data sources 2 Data Collection Payments (ERP system) Travel and entertainment systems Compliance analysis platform Contract Management Systems Third- Party Systems Business Systems Page 19
20 Other external data sources 2 Data Collection Global watch lists, state-owned enterprises and adverse media Over 1.2 million named individuals and entities Over 160 sanction lists Enhanced country list addressing Presidential Executive Orders (e.g., stateowned entities, subsidiaries, vessels, etc.) Over 250 official lists (e.g., World Bank, Asian Development Bank, etc.) People who have been formally accused, arrested, or convicted in white-collar and terrorism crimes Relatives and known associates Entities in the news for adverse media Social data Direct Access Managed Public API Page 20
21 (2) Data Analysis Page 21
22 Applied Data Analytics Purpose Why? 3 Data Analytics Assess and quantify potential areas of risk Analyze large volumes of data which would be timeconsuming for manual review Identify exceptions and anomalies Find patterns and trends through periodic testing Page 22
23 Applied Data Analytics Approaches What? 3 Data Analytics Rules-based analytics Risk scoring Testing data against known behaviors/patterns Using scoring models to identify and determine areas of higher risk Suited to well-defined processes Ideal for anomaly testing Used for identifying data not meeting expected behavior Using rules-based tests with weighted scores Combining weighted scores from different datasets to determine high risk areas Text analytics Analyzing natural language text: Keyword searching Concept analysis Sentiment analysis Search against keywords, e.g., fraud, bribery and corruption, black lists Analyze text to determine concepts discussed Analyze s for emotional tone insight Visual analytics Using interactive dashboards for reporting and trend analysis Visualizing facilitates understanding Makes comparative analysis easier Aids in spotting unusual trends Page 23
24 Applying the right techniques using the right tools 3 Data Analytics In our experience, no one tool or technique does it all. It s about having the capacity and capabilities to develop a customized solution + the domain knowledge to contextualize results. Techniques Visualization Rules-based Rules-based Rules-based Text mining Text mining Data augmentation Entity matching Entity matching Sample Counter Fraud Tests Stratify transactions by attributes to visualize trends and patterns Identify split and duplicate expenses among employees Identify anomalous mileage reimbursements Reimbursements to employees not in master table Mine free-text fields for fraud/corruption keywords Term frequency analysis (unsupervised) Identify employees/attendees that may be sanctioned or politically exposed Employees that share same attributes as vendors Identify frequently entertained attendees Predictive modeling Quantitative analysis Text analytics Geospatial analysis Rules based tests Stratifications COMPLEXITIES FALSE POSITIVES Page 24
25 Applied Data Analytics Applications Where? 3 Data Analytics Travel & Expense Identify high risk employees through rules and text based analytics. Analyze findings in a dynamic risk scoring dashboard. Expense reports Meal attendee information Employee master Conflict of Interest Employees Appearing in Vendor Master Procurement Identify high risk vendors through rules and text based analytics. Analyze findings in a dynamic risk scoring dashboard. Accounts payable ledger Vendor Master Labor and Payroll Identify anomalies and exceptions in labor charging and payroll. Time sheets Contract information Payroll General Ledger / Accounting Identify anomalous trends and patterns across time, geographies, and business units. General ledger Chart of accounts Page 25
26 Entity resolution and link analysis 3 Data Analytics Automatically match and disambiguate individuals and entities in your master reference data. Vast improvements over fuzzy matching. Better conflict of interest tests, fewer false positives. More accurate network link analysis with deeper degrees of separation. Page 26
27 (4) Explore and Risk Rank Page 27
28 Transactional risk scoring 4 Explore & Risk Rank Per analytic: x 5 1 (yes/no flag) (1-5 metric weight multiplier) 5 (analytic score) A fully loaded transaction score takes into account the sum of analytic scores that all hit on that transaction (e.g. 1-duplicate, 2-wkend, 3-round payment 5+5+5=15). Page 28
29 Using analytics to enable continuous monitoring 4 Explore & Risk Rank Continuous monitoring works when a defined, repeatable transactional tests are applied to a wide range of data. Risk scores are aggregated and compared to better focus resources based on evolving risks. Aggregate risk scores as compared to previous analyses to help focus on higher risk areas EY has partnered with IBM to leverage the power of big data platform Summary of scope Detail analyses of each domain Page 29
30 (5) Findings & Observations Page 30
31 Example #1 Summary analysis 5 Findings & Observations Page 31
32 Example #2 Social Media Analysis 5 Findings & Observations Page 32 32
33 Example #3 Time charging and contract analytics 5 Findings & Observations Contract analytics Identification of high risk contracts based on attribute-based risk ranking methodology Interactive tool allows for analysis and filtering by customer attributes including: Contract Contract type Period of performance and percent complete Customer Financial performance (e.g. profit, billed accounts receivable, billings in excess of revenue, revenue in excess of funding) Time charging analytics Comparison of labor data to contract qualification requirements Identification of unusual trends in straight time and overtime labor charging Detection of charges made to multiple categories by the same employee Comparison of billed rates to contracted rates Trending of time charging practices by employee, contract, cost center and labor category Page 33
34 Contact Information Ken Feinstein Senior Manager, Forensic Technology & Discovery Services Page 34
Global EY FIDS Forensic Data Analytics Survey 2014
 Global EY FIDS Forensic Data Analytics Survey 2014 Big risks require big data thinking The Eighth International Pharmaceutical Compliance Congress Dubai, United Arab Emirates Vincent Walden Partner, EY
Global EY FIDS Forensic Data Analytics Survey 2014 Big risks require big data thinking The Eighth International Pharmaceutical Compliance Congress Dubai, United Arab Emirates Vincent Walden Partner, EY
Fraud Prevention, Detection and Response. Dean Bunch, Ernst & Young Fraud Investigation & Dispute Services
 Fraud Prevention, Detection and Response. Dean Bunch, Ernst & Young Fraud Investigation & Dispute Services Agenda Fraud Overview Fraud Prevention Fraud Detection Fraud Response Questions Page 2 Fraud Overview
Fraud Prevention, Detection and Response. Dean Bunch, Ernst & Young Fraud Investigation & Dispute Services Agenda Fraud Overview Fraud Prevention Fraud Detection Fraud Response Questions Page 2 Fraud Overview
Data Mining/Fraud Detection. April 28, 2014 Jonathan Meyer, CPA KPMG, LLP
 Data Mining/Fraud Detection April 28, 2014 Jonathan Meyer, CPA KPMG, LLP 1 Agenda Overview of Data Analytics & Fraud Getting Started with Data Analytics Where to Look & Why? What is Possible? 2 D&A Business
Data Mining/Fraud Detection April 28, 2014 Jonathan Meyer, CPA KPMG, LLP 1 Agenda Overview of Data Analytics & Fraud Getting Started with Data Analytics Where to Look & Why? What is Possible? 2 D&A Business
Board Matters Quarterly Critical insights for today s audit committee
 EY Center for Board Matters Board Matters Quarterly Critical insights for today s audit committee In this issue Dealing with big data 02 The board s role in addressing data and analytics Directors need
EY Center for Board Matters Board Matters Quarterly Critical insights for today s audit committee In this issue Dealing with big data 02 The board s role in addressing data and analytics Directors need
Demystifying Big Data Analytics
 Demystifying Big Data Analytics Practical approaches to business intelligence and forensic analytics 9 May 2013 Discussion topics Big Data & Big Data Analytics Current fraud risks - industry research Components
Demystifying Big Data Analytics Practical approaches to business intelligence and forensic analytics 9 May 2013 Discussion topics Big Data & Big Data Analytics Current fraud risks - industry research Components
ISOLATE AND ELIMINATE FRAUD THROUGH ADVANCED ANALYTICS. BENJAMIN CHIANG, CFE, CISA, CA Partner, Ernst and Young Advisory Singapore
 With ever-increasing data volumes, more sophisticated fraud patterns, and a drive for strong corporate governance, how can organisations build a culture of integrity and compliance? Learn how data analytics
With ever-increasing data volumes, more sophisticated fraud patterns, and a drive for strong corporate governance, how can organisations build a culture of integrity and compliance? Learn how data analytics
AGA Kansas City Chapter Data Analytics & Continuous Monitoring
 AGA Kansas City Chapter Data Analytics & Continuous Monitoring Agenda Market Overview & Drivers for Change Key challenges that organizations face Data Analytics What is data analytics and how can it help
AGA Kansas City Chapter Data Analytics & Continuous Monitoring Agenda Market Overview & Drivers for Change Key challenges that organizations face Data Analytics What is data analytics and how can it help
Taking Data Analytics to the Next Level
 Taking Data Analytics to the Next Level Implementing and Supporting Big Data Initiatives What Is Big Data and How Is It Applicable to Anti-Fraud Efforts? 2 of 20 Definition Gartner: Big data is high-volume,
Taking Data Analytics to the Next Level Implementing and Supporting Big Data Initiatives What Is Big Data and How Is It Applicable to Anti-Fraud Efforts? 2 of 20 Definition Gartner: Big data is high-volume,
Using Data Analytics to Detect Fraud. Other Data Analysis Techniques
 Using Data Analytics to Detect Fraud Other Data Analysis Techniques Qualitative Data Analysis Most data analysis techniques require the use of data in the form of numbers. Qualitative data analysis is
Using Data Analytics to Detect Fraud Other Data Analysis Techniques Qualitative Data Analysis Most data analysis techniques require the use of data in the form of numbers. Qualitative data analysis is
Certified Identity and Access Manager (CIAM) Overview & Curriculum
 Identity and access management (IAM) is the most important discipline of the information security field. It is the foundation of any information security program and one of the information security management
Identity and access management (IAM) is the most important discipline of the information security field. It is the foundation of any information security program and one of the information security management
ACL WHITEPAPER. Automating Fraud Detection: The Essential Guide. John Verver, CA, CISA, CMC, Vice President, Product Strategy & Alliances
 ACL WHITEPAPER Automating Fraud Detection: The Essential Guide John Verver, CA, CISA, CMC, Vice President, Product Strategy & Alliances Contents EXECUTIVE SUMMARY..................................................................3
ACL WHITEPAPER Automating Fraud Detection: The Essential Guide John Verver, CA, CISA, CMC, Vice President, Product Strategy & Alliances Contents EXECUTIVE SUMMARY..................................................................3
Warranty Fraud Detection & Prevention
 Warranty Fraud Detection & Prevention Venky Rao North American Predictive Analytics Segment Leader Agenda IBM SPSS Predictive Analytics for Warranties: Case Studies Why address the Warranties process:
Warranty Fraud Detection & Prevention Venky Rao North American Predictive Analytics Segment Leader Agenda IBM SPSS Predictive Analytics for Warranties: Case Studies Why address the Warranties process:
KNOW YOUR THIRD PARTY
 Thomson Reuters KNOW YOUR THIRD PARTY EXECUTIVE SUMMARY The drive to improve profitability and streamline operations motivates many organizations to collaborate with other businesses, increase outsourcing
Thomson Reuters KNOW YOUR THIRD PARTY EXECUTIVE SUMMARY The drive to improve profitability and streamline operations motivates many organizations to collaborate with other businesses, increase outsourcing
Kroll Ontrack Data Analytics. Forensic analysis and visualization of complex data sets to provide intelligence around investigations
 Trade Date: 2013-08-14 11:57:00 Sum of Total Value: 287,663,728 Trade Date: 2013-08-14 11:51:00 Trader Name: Susan Wright Sum of Total Value: 443,382,018 Kroll Ontrack Data Analytics Trade Date: 2013-08-14
Trade Date: 2013-08-14 11:57:00 Sum of Total Value: 287,663,728 Trade Date: 2013-08-14 11:51:00 Trader Name: Susan Wright Sum of Total Value: 443,382,018 Kroll Ontrack Data Analytics Trade Date: 2013-08-14
www.pwc.fi We believe successful global organisations can confront fraud, corruption and abuse PwC Finland Forensic Services
 www.pwc.fi We believe successful global organisations can confront fraud, corruption and abuse Finland Who are we? Bring a robust forensics team to the table to support your organisation Our practice can
www.pwc.fi We believe successful global organisations can confront fraud, corruption and abuse Finland Who are we? Bring a robust forensics team to the table to support your organisation Our practice can
Strategic Solutions that Make Your Work Easier. Projects Made Easier Decisions Made Easier Business Made Easier
 Strategic Solutions that Make Your Work Easier Projects Made Easier Decisions Made Easier Business Made Easier Have You Outgrown Your Systems? Buyers Say the Partner and the Product are More Important
Strategic Solutions that Make Your Work Easier Projects Made Easier Decisions Made Easier Business Made Easier Have You Outgrown Your Systems? Buyers Say the Partner and the Product are More Important
LGMA Qld Governance and Corporate Planning Village Forum
 www.pwc.com.au Fraud Risk Management Fraud Risk Assessments LGMA Qld Governance and Corporate Planning Village Forum March 2015 Agenda Introductions Fraud Risk Management Fraud Statistics s Global Economic
www.pwc.com.au Fraud Risk Management Fraud Risk Assessments LGMA Qld Governance and Corporate Planning Village Forum March 2015 Agenda Introductions Fraud Risk Management Fraud Statistics s Global Economic
Forensic Services. Third Party Risks. March 2013
 Forensic Services Third Party Risks Landscape of third party risk Focus on third parties that: perform functions on behalf of the company provide products and services that the company does not originate
Forensic Services Third Party Risks Landscape of third party risk Focus on third parties that: perform functions on behalf of the company provide products and services that the company does not originate
IBM's Fraud and Abuse, Analytics and Management Solution
 Government Efficiency through Innovative Reform IBM's Fraud and Abuse, Analytics and Management Solution Service Definition Copyright IBM Corporation 2014 Table of Contents Overview... 1 Major differentiators...
Government Efficiency through Innovative Reform IBM's Fraud and Abuse, Analytics and Management Solution Service Definition Copyright IBM Corporation 2014 Table of Contents Overview... 1 Major differentiators...
Integrating a Big Data Platform into Government:
 Integrating a Big Data Platform into Government: Drive Better Decisions for Policy and Program Outcomes John Haddad, Senior Director Product Marketing, Informatica Digital Government Institute s Government
Integrating a Big Data Platform into Government: Drive Better Decisions for Policy and Program Outcomes John Haddad, Senior Director Product Marketing, Informatica Digital Government Institute s Government
Italy. EY s Global Information Security Survey 2013
 Italy EY s Global Information Security Survey 2013 EY s Global Information Security Survey 2013 This year s survey our 16th edition captures the responses of 1,909 C-suite and senior level IT and information
Italy EY s Global Information Security Survey 2013 EY s Global Information Security Survey 2013 This year s survey our 16th edition captures the responses of 1,909 C-suite and senior level IT and information
SAS Fraud Framework for Banking
 SAS Fraud Framework for Banking Including Social Network Analysis John C. Brocklebank, Ph.D. Vice President, SAS Solutions OnDemand Advanced Analytics Lab SAS Fraud Framework for Banking Agenda Introduction
SAS Fraud Framework for Banking Including Social Network Analysis John C. Brocklebank, Ph.D. Vice President, SAS Solutions OnDemand Advanced Analytics Lab SAS Fraud Framework for Banking Agenda Introduction
Social Media Implementations
 SEM Experience Analytics Social Media Implementations SEM Experience Analytics delivers real sentiment, meaning and trends within social media for many of the world s leading consumer brand companies.
SEM Experience Analytics Social Media Implementations SEM Experience Analytics delivers real sentiment, meaning and trends within social media for many of the world s leading consumer brand companies.
Finding Fraud at a Fortune 500 Company
 About Luminescent is a consulting firm based in Minneapolis, MN, focused on forensic accounting, governance and financial integrity. The firm has performed hundreds of forensic accounting engagements involving
About Luminescent is a consulting firm based in Minneapolis, MN, focused on forensic accounting, governance and financial integrity. The firm has performed hundreds of forensic accounting engagements involving
OPTIMUS SBR. Optimizing Results with Business Intelligence Governance CHOICE TOOLS. PRECISION AIM. BOLD ATTITUDE.
 OPTIMUS SBR CHOICE TOOLS. PRECISION AIM. BOLD ATTITUDE. Optimizing Results with Business Intelligence Governance This paper investigates the importance of establishing a robust Business Intelligence (BI)
OPTIMUS SBR CHOICE TOOLS. PRECISION AIM. BOLD ATTITUDE. Optimizing Results with Business Intelligence Governance This paper investigates the importance of establishing a robust Business Intelligence (BI)
FRAUD PREVENTION STRATEGIES FOR HEALTH CARE A FORENSIC ACCOUNTANT S PERSPECTIVE
 FRAUD PREVENTION STRATEGIES FOR HEALTH CARE A FORENSIC ACCOUNTANT S PERSPECTIVE CPAs & ADVISORS experience reach // S. Todd Burchett, CPA, ABV, ASA, CFF, CFE Partner tburchett@bkd.com 210.268.1932 AGENDA
FRAUD PREVENTION STRATEGIES FOR HEALTH CARE A FORENSIC ACCOUNTANT S PERSPECTIVE CPAs & ADVISORS experience reach // S. Todd Burchett, CPA, ABV, ASA, CFF, CFE Partner tburchett@bkd.com 210.268.1932 AGENDA
customer care solutions
 customer care solutions from Nuance white paper :: A Guide to Successful Intelligent Virtual Assistants Why Best-in-Class Technology Alone Is Not Enough NUANCE :: customer care solutions More than ever
customer care solutions from Nuance white paper :: A Guide to Successful Intelligent Virtual Assistants Why Best-in-Class Technology Alone Is Not Enough NUANCE :: customer care solutions More than ever
Introducing SAP Fraud Management. Jérôme Pugnet
 Introducing SAP Fraud Management Jérôme Pugnet LEARNING POINTS Impacts and Challenges of Fraud How Big is the Problem? Fraud is Typically Found Without Technology: an Undetected Potential! What are the
Introducing SAP Fraud Management Jérôme Pugnet LEARNING POINTS Impacts and Challenges of Fraud How Big is the Problem? Fraud is Typically Found Without Technology: an Undetected Potential! What are the
THE ANALYTICS HUB LEVERAGING A SHARED SERVICES MODEL TO UNLOCK BIG DATA. Thomas Roland Managing Director. David Roggen Director CONTENTS
 THE ANALYTICS HUB LEVERAGING A SHARED SERVICES MODEL TO UNLOCK BIG DATA David Roggen Director Thomas Roland Managing Director CONTENTS Shared Services Today 2 What Is an Analytics Hub? 3 Analytics Hub
THE ANALYTICS HUB LEVERAGING A SHARED SERVICES MODEL TO UNLOCK BIG DATA David Roggen Director Thomas Roland Managing Director CONTENTS Shared Services Today 2 What Is an Analytics Hub? 3 Analytics Hub
Advanced Data Analytics, the Fraudsters Worst Enemy
 Advanced Data Analytics, the Fraudsters Worst Enemy Introducing Powerful Tools and Techniques to Uncover Fraud Agenda Overview of data analytics in the anti-fraud and fraud investigation context Capability
Advanced Data Analytics, the Fraudsters Worst Enemy Introducing Powerful Tools and Techniques to Uncover Fraud Agenda Overview of data analytics in the anti-fraud and fraud investigation context Capability
www.pwc.com Third Party Risk Management 12 April 2012
 www.pwc.com Third Party Risk Management 12 April 2012 Agenda 1. Introductions 2. Drivers of Increased Focus on Third Parties 3. Governance 4. Third Party Risks and Scope 5. Third Party Risk Profiling 6.
www.pwc.com Third Party Risk Management 12 April 2012 Agenda 1. Introductions 2. Drivers of Increased Focus on Third Parties 3. Governance 4. Third Party Risks and Scope 5. Third Party Risk Profiling 6.
Choosing the Right ERP Solution:
 Choosing the Right ERP Solution: 3 CRITERIA FOR SUCCESS Table of Contents 1 2 Who We Are 3 The Key to Better Business Performance 4 ERP as the Focal Point of Your Business 5 Why Some ERP Solutions Fail
Choosing the Right ERP Solution: 3 CRITERIA FOR SUCCESS Table of Contents 1 2 Who We Are 3 The Key to Better Business Performance 4 ERP as the Focal Point of Your Business 5 Why Some ERP Solutions Fail
Simply Sophisticated. Information Security and Compliance
 Simply Sophisticated Information Security and Compliance Simple Sophistication Welcome to Your New Strategic Advantage As technology evolves at an accelerating rate, risk-based information security concerns
Simply Sophisticated Information Security and Compliance Simple Sophistication Welcome to Your New Strategic Advantage As technology evolves at an accelerating rate, risk-based information security concerns
Whitepaper. Beyond Compliance: Implementing Effective Whistleblower Hotline Reporting Systems
 Whitepaper Beyond Compliance: Implementing Effective Whistleblower Hotline Reporting Systems Introduction Hotline reporting systems have been in use for more than two decades, and have proven an effective
Whitepaper Beyond Compliance: Implementing Effective Whistleblower Hotline Reporting Systems Introduction Hotline reporting systems have been in use for more than two decades, and have proven an effective
Business Intelligence and Big Data Analytics: Speeding the Cycle from Insights to Action Four Steps to More Profitable Customer Engagement
 white paper Business Intelligence and Big Data Analytics: Speeding the Cycle from Insights to Action Four Steps to More Profitable Customer Engagement»» Summary For business intelligence analysts the era
white paper Business Intelligence and Big Data Analytics: Speeding the Cycle from Insights to Action Four Steps to More Profitable Customer Engagement»» Summary For business intelligence analysts the era
NCOE whitepaper Master Data Deployment and Management in a Global ERP Implementation
 NCOE whitepaper Master Data Deployment and Management in a Global ERP Implementation Market Offering: Package(s): Oracle Authors: Rick Olson, Luke Tay Date: January 13, 2012 Contents Executive summary
NCOE whitepaper Master Data Deployment and Management in a Global ERP Implementation Market Offering: Package(s): Oracle Authors: Rick Olson, Luke Tay Date: January 13, 2012 Contents Executive summary
SIGNIFICANCE OF BUSINESS INTELLIGENCE APPLICATIONS FOR BETTER DECISION MAKING & BUSINESS PERFORMANCE
 SIGNIFICANCE OF BUSINESS INTELLIGENCE APPLICATIONS FOR BETTER DECISION MAKING & BUSINESS PERFORMANCE Dr. Nitin P. Mankar Professor (Director), Jayawantrao Sawant Institute of Management & Research (JSIMR).
SIGNIFICANCE OF BUSINESS INTELLIGENCE APPLICATIONS FOR BETTER DECISION MAKING & BUSINESS PERFORMANCE Dr. Nitin P. Mankar Professor (Director), Jayawantrao Sawant Institute of Management & Research (JSIMR).
IBM Counter Fraud Signature Solutions
 IBM Counter Fraud Signature Solutions November 5th, 2013 Athens Carmen Ene, VP IBM Global Business Services, Europe Leader Counter Fraud & Financial Crimes Provider ID Theft o Claim for routine services
IBM Counter Fraud Signature Solutions November 5th, 2013 Athens Carmen Ene, VP IBM Global Business Services, Europe Leader Counter Fraud & Financial Crimes Provider ID Theft o Claim for routine services
Keith Barger MFS, MCSE, CCE
 Keith Barger MFS, MCSE, CCE Principal/Practice Leader Advisory Services Keith Barger is a Principal in the Advisory Services practice with Grant Thornton and the Practice Leader for Forensic Accounting
Keith Barger MFS, MCSE, CCE Principal/Practice Leader Advisory Services Keith Barger is a Principal in the Advisory Services practice with Grant Thornton and the Practice Leader for Forensic Accounting
This Symposium brought to you by www.ttcus.com
 This Symposium brought to you by www.ttcus.com Linkedin/Group: Technology Training Corporation @Techtrain Technology Training Corporation www.ttcus.com Big Data Analytics as a Service (BDAaaS) Big Data
This Symposium brought to you by www.ttcus.com Linkedin/Group: Technology Training Corporation @Techtrain Technology Training Corporation www.ttcus.com Big Data Analytics as a Service (BDAaaS) Big Data
THIRD PARTY. T i m L i e t z R e g i o n a l P r a c t i c e L e a d e r R i s k A d v i s o r y S e r v i c e s
 MANAGING THIRD PARTY RISK T i m L i e t z R e g i o n a l P r a c t i c e L e a d e r R i s k A d v i s o r y S e r v i c e s Experis -- a different kind of talent company. Experis Tuesday, January 08,
MANAGING THIRD PARTY RISK T i m L i e t z R e g i o n a l P r a c t i c e L e a d e r R i s k A d v i s o r y S e r v i c e s Experis -- a different kind of talent company. Experis Tuesday, January 08,
ACEDS Membership Benefits Training, Resources and Networking for the E-Discovery Community
 ACEDS Membership Benefits Training, Resources and Networking for the E-Discovery Community! Exclusive News and Analysis! Weekly Web Seminars! Podcasts! On- Demand Training! Networking! Resources! Jobs
ACEDS Membership Benefits Training, Resources and Networking for the E-Discovery Community! Exclusive News and Analysis! Weekly Web Seminars! Podcasts! On- Demand Training! Networking! Resources! Jobs
WHITE PAPER SPLUNK SOFTWARE AS A SIEM
 SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
Self-Service Big Data Analytics for Line of Business
 I D C A N A L Y S T C O N N E C T I O N Dan Vesset Program Vice President, Business Analytics and Big Data Self-Service Big Data Analytics for Line of Business March 2015 Big data, in all its forms, is
I D C A N A L Y S T C O N N E C T I O N Dan Vesset Program Vice President, Business Analytics and Big Data Self-Service Big Data Analytics for Line of Business March 2015 Big data, in all its forms, is
Solve Your Toughest Challenges with Data Mining
 IBM Software Business Analytics IBM SPSS Modeler Solve Your Toughest Challenges with Data Mining Use predictive intelligence to make good decisions faster Solve Your Toughest Challenges with Data Mining
IBM Software Business Analytics IBM SPSS Modeler Solve Your Toughest Challenges with Data Mining Use predictive intelligence to make good decisions faster Solve Your Toughest Challenges with Data Mining
JOB ANNOUNCEMENT. Chief Security Officer, Cheniere Energy, Inc.
 JOB ANNOUNCEMENT Chief Security Officer, Cheniere Energy, Inc. Position Overview The Vice President and Chief Security Risk Officer (CSRO) reports to the Chairman, Chief Executive Officer and President
JOB ANNOUNCEMENT Chief Security Officer, Cheniere Energy, Inc. Position Overview The Vice President and Chief Security Risk Officer (CSRO) reports to the Chairman, Chief Executive Officer and President
Advanced Case Management. Chris den Hoedt
 Advanced Case Management Chris den Hoedt New market demands for achieving outcomes require new approaches...like advanced case management Increased costs and risks from unpredictable processes Higher
Advanced Case Management Chris den Hoedt New market demands for achieving outcomes require new approaches...like advanced case management Increased costs and risks from unpredictable processes Higher
Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail
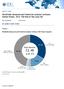 MARKET SHARE Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail Alys Woodward Dan Vesset IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Advanced and Predictive
MARKET SHARE Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail Alys Woodward Dan Vesset IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Advanced and Predictive
mysap ERP FINANCIALS SOLUTION OVERVIEW
 mysap ERP FINANCIALS SOLUTION OVERVIEW EFFECTIVE FINANCIAL MANAGEMENT ... IS KEY TO BUSINESS SUCCESS mysap ERP FINANCIALS YOUR BUSINESS, YOUR FUTURE, YOUR SUCCESS mysap ERP is the world s most complete
mysap ERP FINANCIALS SOLUTION OVERVIEW EFFECTIVE FINANCIAL MANAGEMENT ... IS KEY TO BUSINESS SUCCESS mysap ERP FINANCIALS YOUR BUSINESS, YOUR FUTURE, YOUR SUCCESS mysap ERP is the world s most complete
Risk Considerations for Internal Audit
 Risk Considerations for Internal Audit Cecile Galvez, Deloitte & Touche LLP Enterprise Risk Services Director Traci Mizoguchi, Deloitte & Touche LLP Enterprise Risk Services Senior Manager February 2013
Risk Considerations for Internal Audit Cecile Galvez, Deloitte & Touche LLP Enterprise Risk Services Director Traci Mizoguchi, Deloitte & Touche LLP Enterprise Risk Services Senior Manager February 2013
How To Create An Insight Analysis For Cyber Security
 IBM i2 Enterprise Insight Analysis for Cyber Analysis Protect your organization with cyber intelligence Highlights Quickly identify threats, threat actors and hidden connections with multidimensional analytics
IBM i2 Enterprise Insight Analysis for Cyber Analysis Protect your organization with cyber intelligence Highlights Quickly identify threats, threat actors and hidden connections with multidimensional analytics
Cyber Threat Intelligence Move to an intelligencedriven cybersecurity model
 Cyber Threat Intelligence Move to an intelligencedriven cybersecurity model Stéphane Hurtaud Partner Governance Risk & Compliance Deloitte Laurent De La Vaissière Director Governance Risk & Compliance
Cyber Threat Intelligence Move to an intelligencedriven cybersecurity model Stéphane Hurtaud Partner Governance Risk & Compliance Deloitte Laurent De La Vaissière Director Governance Risk & Compliance
Solve your toughest challenges with data mining
 IBM Software IBM SPSS Modeler Solve your toughest challenges with data mining Use predictive intelligence to make good decisions faster Solve your toughest challenges with data mining Imagine if you could
IBM Software IBM SPSS Modeler Solve your toughest challenges with data mining Use predictive intelligence to make good decisions faster Solve your toughest challenges with data mining Imagine if you could
Cisco Data Preparation
 Data Sheet Cisco Data Preparation Unleash your business analysts to develop the insights that drive better business outcomes, sooner, from all your data. As self-service business intelligence (BI) and
Data Sheet Cisco Data Preparation Unleash your business analysts to develop the insights that drive better business outcomes, sooner, from all your data. As self-service business intelligence (BI) and
Trade risk management: a global approach
 World Customs Journal Trade risk management: a global approach Abstract Lorraine Trapani This article discusses IBM s global approach to managing risk associated with importing product into more than 170
World Customs Journal Trade risk management: a global approach Abstract Lorraine Trapani This article discusses IBM s global approach to managing risk associated with importing product into more than 170
Understanding Your Customer Journey by Extending Adobe Analytics with Big Data
 SOLUTION BRIEF Understanding Your Customer Journey by Extending Adobe Analytics with Big Data Business Challenge Today s digital marketing teams are overwhelmed by the volume and variety of customer interaction
SOLUTION BRIEF Understanding Your Customer Journey by Extending Adobe Analytics with Big Data Business Challenge Today s digital marketing teams are overwhelmed by the volume and variety of customer interaction
Food & Beverage Industry Brief
 KudzuCreative Content Creation Food & Beverage Industry Brief KudzuCreative kudzucreative.com Content Created for, Microsoft Dynamics AX Gold Partner laurenparker@kudzucreative.com NOT YOUR FATHER S FUNCTIONALITY
KudzuCreative Content Creation Food & Beverage Industry Brief KudzuCreative kudzucreative.com Content Created for, Microsoft Dynamics AX Gold Partner laurenparker@kudzucreative.com NOT YOUR FATHER S FUNCTIONALITY
The Role of Data & Analytics in Your Digital Transformation. Michael Corcoran Sr. Vice President & CMO
 The Role of Data & Analytics in Your Digital Transformation Michael Corcoran Sr. Vice President & CMO 1 The Role of Data & Analytics in Your Digital Transformation Agenda Strategies for Success Potential
The Role of Data & Analytics in Your Digital Transformation Michael Corcoran Sr. Vice President & CMO 1 The Role of Data & Analytics in Your Digital Transformation Agenda Strategies for Success Potential
IBM Tivoli Netcool network management solutions for enterprise
 IBM Netcool network management solutions for enterprise The big picture view that focuses on optimizing complex enterprise environments Highlights Enhance network functions in support of business goals
IBM Netcool network management solutions for enterprise The big picture view that focuses on optimizing complex enterprise environments Highlights Enhance network functions in support of business goals
Industrial Cyber Security Risk Manager. Proactively Monitor, Measure and Manage Industrial Cyber Security Risk
 Industrial Cyber Security Risk Manager Proactively Monitor, Measure and Manage Industrial Cyber Security Risk Industrial Attacks Continue to Increase in Frequency & Sophistication Today, industrial organizations
Industrial Cyber Security Risk Manager Proactively Monitor, Measure and Manage Industrial Cyber Security Risk Industrial Attacks Continue to Increase in Frequency & Sophistication Today, industrial organizations
Value of a Purpose-Built Third-Party Compliance Solution
 Value of a Purpose-Built Third-Party Compliance Solution Introduction Multinational corporations routinely engage third parties such as sales agents, consultants, brokers, distributors, resellers, suppliers,
Value of a Purpose-Built Third-Party Compliance Solution Introduction Multinational corporations routinely engage third parties such as sales agents, consultants, brokers, distributors, resellers, suppliers,
QRadar SIEM and Zscaler Nanolog Streaming Service
 QRadar SIEM and Zscaler Nanolog Streaming Service February 2014 1 QRadar SIEM: Security Intelligence Platform QRadar SIEM provides full visibility and actionable insight to protect networks and IT assets
QRadar SIEM and Zscaler Nanolog Streaming Service February 2014 1 QRadar SIEM: Security Intelligence Platform QRadar SIEM provides full visibility and actionable insight to protect networks and IT assets
Game Changer The Impact of Cognitive Technology on Business and Financial Reporting. May 23, 2016
 Game Changer The Impact of Cognitive Technology on Business and Financial Reporting May 23, 2016 Today s presenter Marc Macaulay, Cognitive Technology Audit Leader, KPMG LLP Marc Macaulay is KPMG s Cognitive
Game Changer The Impact of Cognitive Technology on Business and Financial Reporting May 23, 2016 Today s presenter Marc Macaulay, Cognitive Technology Audit Leader, KPMG LLP Marc Macaulay is KPMG s Cognitive
Business ByDesign. The SAP Business ByDesign solution helps you optimize project management
 SAP Functions in Detail SAP Solutions for Small Businesses and Midsize Companies Efficient Project Management Drive Project Success with SAP Business ByDesign The SAP Business ByDesign solution helps you
SAP Functions in Detail SAP Solutions for Small Businesses and Midsize Companies Efficient Project Management Drive Project Success with SAP Business ByDesign The SAP Business ByDesign solution helps you
April 2016 JPoint Moscow, Russia. How to Apply Big Data Analytics and Machine Learning to Real Time Processing. Kai Wähner. kwaehner@tibco.
 April 2016 JPoint Moscow, Russia How to Apply Big Data Analytics and Machine Learning to Real Time Processing Kai Wähner kwaehner@tibco.com @KaiWaehner www.kai-waehner.de LinkedIn / Xing Please connect!
April 2016 JPoint Moscow, Russia How to Apply Big Data Analytics and Machine Learning to Real Time Processing Kai Wähner kwaehner@tibco.com @KaiWaehner www.kai-waehner.de LinkedIn / Xing Please connect!
Oracle Cloud: Enterprise Resource Planning
 Oracle Cloud: Enterprise Resource Planning Rondy Ng Senior Vice President Applications Development Safe Harbor Statement "Safe Harbor" Statement: Statements in this presentation relating to Oracle's future
Oracle Cloud: Enterprise Resource Planning Rondy Ng Senior Vice President Applications Development Safe Harbor Statement "Safe Harbor" Statement: Statements in this presentation relating to Oracle's future
www.pwc.com Being protected Using data analytics to detect fraud
 www.pwc.com Being protected Using data analytics to detect fraud Are you currently exposed to fraudulent activities? It will surprise few to learn that occupational fraud, IP infringement, corruption,
www.pwc.com Being protected Using data analytics to detect fraud Are you currently exposed to fraudulent activities? It will surprise few to learn that occupational fraud, IP infringement, corruption,
A New Era Of Analytic
 Penang egovernment Seminar 2014 A New Era Of Analytic Megat Anuar Idris Head, Project Delivery, Business Analytics & Big Data Agenda Overview of Big Data Case Studies on Big Data Big Data Technology Readiness
Penang egovernment Seminar 2014 A New Era Of Analytic Megat Anuar Idris Head, Project Delivery, Business Analytics & Big Data Agenda Overview of Big Data Case Studies on Big Data Big Data Technology Readiness
Fraud Triangle Analytics Anti-Fraud Research and Methodologies
 Fraud Triangle Analytics Anti-Fraud Research and Methodologies Risk Management Committee Meeting American Hotel & Lodging Association November 18, 2009 Topics for discussion Why incorporate fraud detection
Fraud Triangle Analytics Anti-Fraud Research and Methodologies Risk Management Committee Meeting American Hotel & Lodging Association November 18, 2009 Topics for discussion Why incorporate fraud detection
InforCloudSuite. Business. Overview INFOR CLOUDSUITE BUSINESS 1
 InforCloudSuite Business Overview INFOR CLOUDSUITE BUSINESS 1 What if... You could implement a highly flexible ERP solution that was built to manage all of your business needs, from financials and human
InforCloudSuite Business Overview INFOR CLOUDSUITE BUSINESS 1 What if... You could implement a highly flexible ERP solution that was built to manage all of your business needs, from financials and human
Building the business case for continuity and resiliency
 Global Technology Services Research Analysis Risk Management Building the business case for continuity and resiliency The economics of IT risk and reputation and their importance to business continuity
Global Technology Services Research Analysis Risk Management Building the business case for continuity and resiliency The economics of IT risk and reputation and their importance to business continuity
Viewpoint ediscovery Services
 Xerox Legal Services Viewpoint ediscovery Platform Technical Brief Viewpoint ediscovery Services Viewpoint by Xerox delivers a flexible approach to ediscovery designed to help you manage your litigation,
Xerox Legal Services Viewpoint ediscovery Platform Technical Brief Viewpoint ediscovery Services Viewpoint by Xerox delivers a flexible approach to ediscovery designed to help you manage your litigation,
Leveraging Big Data to Mitigate Health Care Fraud Risk
 Leveraging Big Data to Mitigate Health Care Fraud Risk Jeremy Clopton, CPA, CFE, ACDA Senior Managing Consultant BKD, LLP Forensics & Valuation Services Introduction Health Care Is Victimized by Fraud
Leveraging Big Data to Mitigate Health Care Fraud Risk Jeremy Clopton, CPA, CFE, ACDA Senior Managing Consultant BKD, LLP Forensics & Valuation Services Introduction Health Care Is Victimized by Fraud
Enhancing Safeguards Through Information Analysis: Business Analytics Tools. IAEA, Vienna, 09/10/2014. General Use
 Enhancing Safeguards Through Information Analysis: Business Analytics Tools IAEA, Vienna, 09/10/2014 Julian Midwinter - Business Unit Executive i2, Threat and Counter Fraud General Use 2014 IBM Corporation
Enhancing Safeguards Through Information Analysis: Business Analytics Tools IAEA, Vienna, 09/10/2014 Julian Midwinter - Business Unit Executive i2, Threat and Counter Fraud General Use 2014 IBM Corporation
SAP Agile Data Preparation
 SAP Agile Data Preparation Speaker s Name/Department (delete if not needed) Month 00, 2015 Internal Legal disclaimer The information in this presentation is confidential and proprietary to SAP and may
SAP Agile Data Preparation Speaker s Name/Department (delete if not needed) Month 00, 2015 Internal Legal disclaimer The information in this presentation is confidential and proprietary to SAP and may
Aligning Quality Management Processes to Compliance Goals
 Aligning Quality Management Processes to Compliance Goals MetricStream.com Smart Consulting Group Joint Webinar February 23 rd 2012 Nigel J. Smart, Ph.D. Smart Consulting Group 20 E. Market Street West
Aligning Quality Management Processes to Compliance Goals MetricStream.com Smart Consulting Group Joint Webinar February 23 rd 2012 Nigel J. Smart, Ph.D. Smart Consulting Group 20 E. Market Street West
IBM Global Business Services Microsoft Dynamics CRM solutions from IBM
 IBM Global Business Services Microsoft Dynamics CRM solutions from IBM Power your productivity 2 Microsoft Dynamics CRM solutions from IBM Highlights Win more deals by spending more time on selling and
IBM Global Business Services Microsoft Dynamics CRM solutions from IBM Power your productivity 2 Microsoft Dynamics CRM solutions from IBM Highlights Win more deals by spending more time on selling and
OUTGROWING MICROSOFT DYNAMICS GP
 OUTGROWING MICROSOFT DYNAMICS GP Why Companies Move Up to Microsoft Dynamics AX AN ARMANINO WHITE PAPER ARE YOU TOO SUCCESSFUL FOR YOUR CURRENT ERP SYSTEM? Whether you re expanding your product lines,
OUTGROWING MICROSOFT DYNAMICS GP Why Companies Move Up to Microsoft Dynamics AX AN ARMANINO WHITE PAPER ARE YOU TOO SUCCESSFUL FOR YOUR CURRENT ERP SYSTEM? Whether you re expanding your product lines,
Transforming Analytics for Cognitive Business
 Transforming Analytics for Cognitive Business Alistair Rennie General Manager Solutions, IBM Analytics @alistair_rennie IBM Chief Data Officer Strategy Summit Data fuels innovative offerings 28% of car
Transforming Analytics for Cognitive Business Alistair Rennie General Manager Solutions, IBM Analytics @alistair_rennie IBM Chief Data Officer Strategy Summit Data fuels innovative offerings 28% of car
QRadar SIEM and FireEye MPS Integration
 QRadar SIEM and FireEye MPS Integration March 2014 1 IBM QRadar Security Intelligence Platform Providing actionable intelligence INTELLIGENT Correlation, analysis and massive data reduction AUTOMATED Driving
QRadar SIEM and FireEye MPS Integration March 2014 1 IBM QRadar Security Intelligence Platform Providing actionable intelligence INTELLIGENT Correlation, analysis and massive data reduction AUTOMATED Driving
Big Data: Key Concepts The three Vs
 Big Data: Key Concepts The three Vs Big data in general has context in three Vs: Sheer quantity of data Speed with which data is produced, processed, and digested Diversity of sources inside and outside.
Big Data: Key Concepts The three Vs Big data in general has context in three Vs: Sheer quantity of data Speed with which data is produced, processed, and digested Diversity of sources inside and outside.
POWERFUL SOFTWARE. FIGHTING HIGH CONSEQUENCE CYBER CRIME. KEY SOLUTION HIGHLIGHTS
 ADVANCED CYBER THREAT ANALYTICS POWERFUL SOFTWARE. FIGHTING HIGH CONSEQUENCE CYBER CRIME. Wynyard Advanced Cyber Threat Analytics (ACTA) is a Pro-active Cyber Forensics solution that helps protect organisations
ADVANCED CYBER THREAT ANALYTICS POWERFUL SOFTWARE. FIGHTING HIGH CONSEQUENCE CYBER CRIME. Wynyard Advanced Cyber Threat Analytics (ACTA) is a Pro-active Cyber Forensics solution that helps protect organisations
2014 Financial Services Industry Compliance Benchmark Study
 2014 Financial Services Industry Compliance Benchmark Study Presented By: and Executive Summary Beginning in early December 2013, SAI Global Compliance conducted a survey among compliance professionals
2014 Financial Services Industry Compliance Benchmark Study Presented By: and Executive Summary Beginning in early December 2013, SAI Global Compliance conducted a survey among compliance professionals
Strong Corporate Governance & Internal Controls: Internal Auditing in Higher Education
 Strong Corporate Governance & Internal Controls: Internal Auditing in Higher Education Contents Introduction Internal Audit as Trusted Advisor & Business Partner Big Ticket Items: Fraud, Revenue Leakage
Strong Corporate Governance & Internal Controls: Internal Auditing in Higher Education Contents Introduction Internal Audit as Trusted Advisor & Business Partner Big Ticket Items: Fraud, Revenue Leakage
Direct-to-Company Feedback Implementations
 SEM Experience Analytics Direct-to-Company Feedback Implementations SEM Experience Analytics Listening System for Direct-to-Company Feedback Implementations SEM Experience Analytics delivers real sentiment,
SEM Experience Analytics Direct-to-Company Feedback Implementations SEM Experience Analytics Listening System for Direct-to-Company Feedback Implementations SEM Experience Analytics delivers real sentiment,
Better planning and forecasting with IBM Predictive Analytics
 IBM Software Business Analytics SPSS Predictive Analytics Better planning and forecasting with IBM Predictive Analytics Using IBM Cognos TM1 with IBM SPSS Predictive Analytics to build better plans and
IBM Software Business Analytics SPSS Predictive Analytics Better planning and forecasting with IBM Predictive Analytics Using IBM Cognos TM1 with IBM SPSS Predictive Analytics to build better plans and
White Paper Achieving GLBA Compliance through Security Information Management. White Paper / GLBA
 White Paper Achieving GLBA Compliance through Security Information Management White Paper / GLBA Contents Executive Summary... 1 Introduction: Brief Overview of GLBA... 1 The GLBA Challenge: Securing Financial
White Paper Achieving GLBA Compliance through Security Information Management White Paper / GLBA Contents Executive Summary... 1 Introduction: Brief Overview of GLBA... 1 The GLBA Challenge: Securing Financial
Performance Management
 Performance Management Be enterprising. The speed, complexity, and global nature of business today presents challenges for even the best-managed organizations. To adapt to this constantly changing environment,
Performance Management Be enterprising. The speed, complexity, and global nature of business today presents challenges for even the best-managed organizations. To adapt to this constantly changing environment,
End to End Solution to Accelerate Data Warehouse Optimization. Franco Flore Alliance Sales Director - APJ
 End to End Solution to Accelerate Data Warehouse Optimization Franco Flore Alliance Sales Director - APJ Big Data Is Driving Key Business Initiatives Increase profitability, innovation, customer satisfaction,
End to End Solution to Accelerate Data Warehouse Optimization Franco Flore Alliance Sales Director - APJ Big Data Is Driving Key Business Initiatives Increase profitability, innovation, customer satisfaction,
Delivering Customer Value Faster With Big Data Analytics
 Delivering Customer Value Faster With Big Data Analytics Tackle the challenges of Big Data and real-time analytics with a cloud-based Decision Management Ecosystem James Taylor CEO Customer data is more
Delivering Customer Value Faster With Big Data Analytics Tackle the challenges of Big Data and real-time analytics with a cloud-based Decision Management Ecosystem James Taylor CEO Customer data is more
Building a Global Payroll Model. Charlotte N. Hodges, CPP
 Building a Global Payroll Model Charlotte N. Hodges, CPP Virginia Statewide Payroll Conference October 9-10, 2014 Agenda Challenges Strategic Factors Global Payroll Strategy Global Payroll Model Key Partnerships
Building a Global Payroll Model Charlotte N. Hodges, CPP Virginia Statewide Payroll Conference October 9-10, 2014 Agenda Challenges Strategic Factors Global Payroll Strategy Global Payroll Model Key Partnerships
ENTERPRISE MANAGEMENT AND SUPPORT IN THE TELECOMMUNICATIONS INDUSTRY
 ENTERPRISE MANAGEMENT AND SUPPORT IN THE TELECOMMUNICATIONS INDUSTRY The Telecommunications Industry Companies in the telecommunications industry face a number of challenges as market saturation, slow
ENTERPRISE MANAGEMENT AND SUPPORT IN THE TELECOMMUNICATIONS INDUSTRY The Telecommunications Industry Companies in the telecommunications industry face a number of challenges as market saturation, slow
Beyond listening Driving better decisions with business intelligence from social sources
 Beyond listening Driving better decisions with business intelligence from social sources From insight to action with IBM Social Media Analytics State of the Union Opinions prevail on the Internet Social
Beyond listening Driving better decisions with business intelligence from social sources From insight to action with IBM Social Media Analytics State of the Union Opinions prevail on the Internet Social
2011 Cyber Security and the Advanced Persistent Threat A Holistic View
 2011 Cyber and the Advanced Persistent Threat A Holistic View Thomas Varney Cybersecurity & Privacy BM Global Business Services 1 31/10/11 Agenda The Threat We Face A View to Addressing the Four Big Problem
2011 Cyber and the Advanced Persistent Threat A Holistic View Thomas Varney Cybersecurity & Privacy BM Global Business Services 1 31/10/11 Agenda The Threat We Face A View to Addressing the Four Big Problem
NICE Systems and Avaya provide businesses with Insight from Interactions
 IP Telephony Contact Centers Mobility Services OVERVIEW NICE Systems and Avaya provide businesses with Insight from Interactions Supports Avaya Communication Manager Application Enablement Services (AES)
IP Telephony Contact Centers Mobility Services OVERVIEW NICE Systems and Avaya provide businesses with Insight from Interactions Supports Avaya Communication Manager Application Enablement Services (AES)
Digital Marketplace - G-Cloud
 Digital Marketplace - G-Cloud CRM Services Core offer 9 services in this area: 1. Dynamics CRM Upgrade Services Utilising this service, Core will undertake an evaluation of your current CRM platform. We
Digital Marketplace - G-Cloud CRM Services Core offer 9 services in this area: 1. Dynamics CRM Upgrade Services Utilising this service, Core will undertake an evaluation of your current CRM platform. We
IBM Content Analytics: Rapid insight for crime investigation
 IBM Content Analytics: Rapid insight for crime investigation Discover insights in structured and unstructured information to speed case and identity resolution Highlights Reduces investigation time from
IBM Content Analytics: Rapid insight for crime investigation Discover insights in structured and unstructured information to speed case and identity resolution Highlights Reduces investigation time from
Anti-Fraud Management Example In Accounts Payable. Michael Heckner October 12, 2012
 Anti-Fraud Management Example In Accounts Payable Michael Heckner October 12, 2012 GRC Top Reasons Customers Invest Today Business Process Improvements Systematic, reliable processes Improve predictability
Anti-Fraud Management Example In Accounts Payable Michael Heckner October 12, 2012 GRC Top Reasons Customers Invest Today Business Process Improvements Systematic, reliable processes Improve predictability
