Battery Authentication Architecture and Implementation for Portable Devices
|
|
|
- Lynn McCarthy
- 1 years ago
- Views:
Transcription
1 Battery Authentication Architecture and Implementation for Portable Devices Todd Vanyo and Jinrong Qian, Texas Instruments ABSTRACT Driven by integrated functionality and shrinking form factors, the demand for portable devices such as cellular phones, PDAs, and DVD players has grown significantly during the last few years. These portable devices need rechargable batteries and peripherals that are typically replaced before the life of the portable devices expires. This has opened a huge market for counterfeiters to supply cheap replacements, which may not meet the manufacturing standards or have the safety and protection circuits required by the original equipment manufacturers (OEMs). These counterfeit batteries may violate both mechanical and electrical safety requirements related to short-circuit protection, charge safety, and other specifications. It is usually impossible for the consumer to determine the quality without making a purchase and possibly learning the hard way, leading to a potentially dangerous situation for the end users. Adding simple and effective authentication technology to the portable system allows the OEMs to ensure customer satisfaction and protect their business. The simple identification (ID) and the more complicated challenge and response CRC and SHA-1/HMAC based battery authentication techniques are discussed in detail. The presented battery authentication architectures meet the counterfeit battery challenges to protect OEM potential business and ensure the end-user safety and satisfication. I. EXISTING AUTHENTICATION TECHNIQUES Several techniques are currently used to identify a battery or peripheral intended for the main battery powered product. The most common is the form factor or physical connection. Every cell phone battery on the market has a different aspect ratio, and the physical size of the battery is not even consistent within all the phones manufactured by one company. This provides a modest level of security for the OEM, until a 3 rd party duplicates the physical dimensions and simply buys the connector from one of the various sources for such physical contacts. Economic considerations make changing the physical size or shape of connectors extremely difficult to do in short design cycles. In fact, it would be more economical to standardize form factors and keep them unchanged. Many original manufacturers are moving towards this economic model today. Electrical techniques can be used to replace the unique physical protection eliminated by standardized form factors. The two main electrical authentication techniques available are identification based and challenge/response based. Each technique has strengths and weaknesses that must be considered when designing systems requiring authentication. 3-1
2 II. IDENTIFICATION (ID) BASED AUTHENTICATION TECHNIQUE The most basic form of electrical authentication is an ID based system. Fig. 1 shows an ID authentication functional block diagram. The challenger, or host, sends a command to read the ID data from the device (responder). The data returned from the responder may include a product family code, identification number (ID), and cyclic redundancy check (CRC) value. Typically this technique requires that each device have a unique ID number. The response data is checked for validity by the host. If the information is valid, then the host enables system operation. Otherwise, it may inhibit system operation and provide an error code or warning signal to the end-user. Fig. 2 shows the battery pack typical application circuit with the bq2022 and bq2023, which both provide ID based authentication functionality. The host communicates with the ID chip through a dedicated general purpose I/O or UART to determine if an ID is available and valid. The ID authentication technique weeds out a significant number of non-oems. However, the ID issued by the device is available to anyone with an oscilloscope. It is still possible for the counterfeiters to replicate the ID to the issued command. But, it increases the cost to implement a fake ID. Some non- OEMs go after batteries and peripherals for such high volume products that adding a cheap microcontroller to the system is acceptable. To counter this threat, a more robust challenge/ response authentication technique must be employed. Challenger - Host Command Responder Response Validator Response Family Code ID CRC Values Fig. 1. ID authentication functional block diagram. PACK+ PACK+ SDQ PACK- bq2022 VSS SDQ VSS bq27000 Gas Gauge IC Battery Pack + R SNS SDQ TS R1 100 kω RT: 103AT bq2023 PDET SDQ STAT VSS VCC SRP SRN RBI R SNS C1 0.1 μf + Li-Ion Cell Protector Protector TS RT: 103AT Fig. 2. Typical application circuit with ID chip. PACK- Battery Pack 3-2
3 III. CHALLENGE AND RESPONSE BASED AUTHENTICATION TECHNIQUE ID-based authentication increases complexity by forcing the counterfeiter to identify the ID and the command. But this can be done with an oscilloscope and knowledge of the communication protocol; the technique is secure by adding cost to the system. If cost improves security, a non-original manufacturer moves on to a battery or peripheral without this functionality. But for those non-original manufacturers willing to add cost to their system to secure a business opportunity, something more robust than ID-based authentication is needed. The cost-effective and robust approach is based on a challenge/response technique shown in Fig. 3. The major components of this technique are the random challenge and a secret known only to the challenger and responder. In this technique, the host sends a random challenge to the battery pack that contains the identification device, or responder. The challenge consists of random data generated by the host. The secret key is either shared or transmitted securely from one side to another. A shared secret is typically static from responder to responder, minimizing the secure memory requirements on the host. A system that requires each responder to have a different secret would require secure transmission of that secret from the responder to the host. Transmitting the secret securely typically means sending an encrypted version of the secret over a public communication channel. The encrypted secret must be decrypted at the host before it can be used in the authentication calculation. Challenger - Host Secret Authentication Transform Challenge Expected Answer Fail No Match? Yes Authenticated Secret can be shared or transmitted securely from one side to the other Calculated Answer Challenge is a random number that changes each time it is transmitted Secret Authentication Transform Challenge Fig. 3. Challenge and response based authentication technique. 3-3
4 When the authentication device receives the challenge information, it combines the challenge and a plaintext version of the secret, stored in private memory, and performs the authentication transform to calculate the response. On the other side, the host performs the same transform using the challenge and the plaintext version of the secret it stores. The host compares the value it computes against the response obtained from the identification device. If the calculated data from the authentication device matches the expected answer from the host, then the host authenticates the battery and allows the system to start operation. Otherwise, it may inhibit the system operation and provide a warning signal to the end-users. Why is this technique more secure than the straight ID based technique? The single ID authentication technique has a fixed response to a fixed challenge or command. It is relatively easy for the counterfeiters to find out the fixed challenge and command. However, the challenge and response secure technique changes the query and response every time. A relatively large and random challenge makes a look up table solution very expensive in terms of memory, which has a direct correlation with the monetary cost, and is difficult to guess. In addition, part of the transform involves a secret shared between the challenger and the responder. Security then resides in the secret, allowing the technique to use a public authentication transform algorithm. Public authentication transforms are good because they can be thoroughly and properly evaluated for robustness against attacks to reveal the secret. IV. CHALLENGE AND RESPONSE CRC BASED AUTHENTICATION IMPLEMENTATION Fig. 4 shows the bq26150 block diagram of a Cyclic Redundancy Code (CRC) based authentication implementation based on the concept of challenge and response authentication technique discussed above. Private Non-Volatile Memory 96-bit (PI) Plaintext ID 16-bit (PP) Plaintext Poly. 16-bit (PS) Plaintext Seed Public Non-Volatile Memory 96-bit (EI) Encrypted ID 16-bit (EP) Encrypted Poly. 16-bit (ES) Encrypted Seed 128-bit General Use HOST Communication CRC Authentication Public RAM 8-bit Control 32-bit Challenge 16-bit Auth Code Power Control Fig. 4. Response CRC based authentication block diagram. 3-4
5 It combines a 32-bit challenge (transmitted from the host) and a 96-bit secret key (ID) through a CRC defined by a 16-bit secret polynomial and 16-bit secret initialization (seed) value to generate a 16-bit response. The 96-bit ID, 16-bit polynomial, and 16-bit seed correspond to the box labeled Secret in the Responder of Fig. 3 and may be unique to each device. The plaintext version of the ID, polynomial, and seed are stored in private memory that can only be read by the bq The 128-bit of secret information may be stored on the host as plaintext or stored with the bq26150 in encrypted form to be read and decrypted by the host at the time of authentication. The encryption method used to store the polynomial coefficients and the device ID can be selected by the manufacturer. To authenticate a battery pack, the host reads the encrypted device ID, polynomial, and seed values from the public memory. It decrypts those values using the appropriate decryption method and then generates a 32-bit random challenge. The generated random challenge is transmitted to the authentication device, which uses the plaintext version of the polynomial coefficients, seed, and device ID, along with the 32-bit random challenge from the host to calculate the authentication CRC value. The host uses the polynomial coefficients, seed, and device ID it has in memory, along with the 32-bit random challenge that it sent to the authentication device to calculate the authentication CRC value. When the host and the authentication device have completed the calculation, the host reads the authentication CRC value from the authentication device and compares it to its own value. If the values match, the battery pack is authenticated and the host can initiate the system start command and communicate with other devices in the battery pack such as a gas gauge. If the authentication fails, the host may provide a warning signal to the end user and not initiate the system start command. Fig. 5 shows the battery pack typical application circuit with the bq26150, CRC based battery authentication. The authentication chip has an internal regulator powered by the communication line and it can communicate to the gas gauge IC. If the authentication fails, the host may not allow charging the battery and provide a warning signal to the user. The CRC based authentication provides a simple and cost effective solution to authenticate battery packs for end equipment. PACK+ HDQ R1 5 kω bq26150 HDQ HDQP R2 100 kω BAT VCC SRP + VSS PWR HDQ R SNS VSS C1 0.1 μf VSS SRN bq27000 Protector TS RT: 103AT PACK- Fig. 5. Response CRC based authentication block diagram. 3-5 Battery Pack
6 V. CHALLENGE AND RESPONSE SHA-1 BASED AUTHENTICATION IMPLEMENTATION In order to achieve high level of authentication, a more sophisticated algorithm such as SHA-1/HMAC can be used. The SHA-1/HMAC has been used for a number of years to authenticate Internet transactions for Virtual Private Networks, banking, and digital certificates. The algorithm used in SHA-1/HMAC is iterative. One way hash functions can process a message to produce a condensed representation called a message digest. It enables the determination of a message s integrity. Any change to the message results in a different message digest with a very high probability. This property is useful in the generation and verification of digital signatures and message authentication codes. Fig. 6 shows the block diagram of the bq26100, a SHA-1/HMAC based authentication device. The authentication principle is similar to the CRC based except the algorithm is different. To authenticate a battery pack, the host generates a 160-bit random challenge and transmits to the authentication device. Both the host and the authentication device combine the plaintext version of the 128-bit secret along with the 160- bit random challenge to calculate the authentication digest value. The 128-bit secret can be stored in secure memory on the host or read in encrypted form from the authentication device for decryption at authentication time. As with the CRC based device, the encryption/ decryption method for the secret is up to the discretion of the system designer. When the host and the authentication device have completed the calculation, the host reads the authentication digest value from the authentication device. It then compares to its own value. If the values match, the battery pack is authenticated. Otherwise, the host may not initiate the system start-up command or provide a warning signal to the end user. Since there is a 160 bit random challenge, it generates possibilities. This significantly improves the security level. However, SHA-1/HMAC algorithm requires more memory, which increases the cost. Private Non-Volatile Memory 128-bit Plaintext Key Public Non-Volatile Memory 128-bit Encrypted Key 1024-bit General Use HOST Communication SHA-1/HMAC Authentication Public RAM 8-bit Control 160-bit Challenge 160-bit Digest Power Control Fig. 6. Challenge and response SHA-1/HMAC based authentication diagram. 3-6
7 VI. CONCLUSIONS As portable products become more commonplace, techniques need to be put in place to ensure that batteries and peripherals used by those products meet the original manufacturer s safety requirements. The selection of a battery authentication depends on the security level needed and cost for the applications. The simple ID authentication is cheapest, but can be replicated easily. The challenge and response based authentication techniques are more expensive. However, they have highest security and are good for the highend portable applications. 3-7
8 VII. APPENDIX A. Cyclic Redundancy Code (CRC) Computation Example An 8-bit CRC is used here as an example to show how to calculate a CRC value. Assume the CRC seed (Initial CRC value) is 0x00, and initial CRC data input, or the first byte of the challenge, is 0x0F. The CRC polynomial is 1+x 4 +x 5 +x 8, where x 8 only indicates that it is an 8-bit CRC. This polynomial coefficient is represented as 0x8C. Here are four steps to calculate the CRC value. Step Action 1 Compare LSB of the CRC value with CRC data. 2 If they are not equal, then shift right both values and then add polynomial coefficient to CRC value with XOR after being shifted. 3 If they are equal, shift right CRC value and CRC data. 4 Repeat procedure until 8 sets of LSB bits have been compared. 5 The last CRC value is final CRC value Table 1 shows step-by-step CRC calculation based on the assumptions above. The expected final CRC value is 0x41. Table 1 shows step-by-step CRC calculation based on the assumptions above. The expected final CRC value is 0x
9 TABLE 1: STEP-BY-STEP CRC CALCULATION Byte Action Bit 7 Bit 6 Bit 5 Bit 4 Bit 3 Bit 2 Bit 1 Bit 0 CRC Seed Initial Data value Initial Data value After 1st shift CRC After 1st shift Poly CRC After Adding Data value Data value After 2nd shift CRC After 2nd shift Poly CRC After Adding Data value Data value After 3rd shift CRC After 3rd shift Poly CRC After Adding Data value CRC After 4th shift Data value After 4th shift CRC After 5th shift Data value After 5th shift CRC After 6th shift Data value After 6th shift Data value After 7th shift CRC After 7th shift Poly CRC After Adding Data value Data value After 8th Shift CRC After 8th Shift The steps for CRC computation outlined above can also be expressed in pseudo-c code as shown in Table 2. TABLE 2 PSEUDO-C CODE FOR CRC GENERATION for (i = 0; i < 8; i++) { if (crc[0] ^ input[i]) crc = (crc >> 1) ^ poly; else crc = crc >> 1; } 3-9
10 B. System Level Flow for Challenge/Response Based System If the Host has prior knowledge of the plaintext secret stored in the Responder: Step Action 1 Host microcontroller generates challenge of appropriate length and transmits it to the Responder. 2 Host issues authentication command to the Responder. 3 Host computes the expected response based on the generated challenge, known plaintext secret, and the authentication algorithm. 4 Host queries Responder for authentication response. 5 Host compares the response from the Responder to the expected response computed locally. If the Host does not have prior knowledge of the plaintext secret stored in the Responder: Step Action 1 Host microcontroller generates challenge of appropriate length and transmits it to the Responder. 2 Host issues authentication command to the Responder. 3 Host reads the encrypted secret from the Responder. 4 Host decrypts the encrypted secret to recover the plaintext secret. 5 Host computes the expected response based on the generated challenge, known plaintext secret, and the authentication algorithm. 6 Host queries Responder for authentication response. 7 Host compares the response from the Responder to the expected response computed locally. 3-10
Measurement and Analysis Introduction of ISO7816 (Smart Card)
 Measurement and Analysis Introduction of ISO7816 (Smart Card) ISO 7816 is an international standard related to electronic identification cards with contacts, especially smart cards, managed jointly by
Measurement and Analysis Introduction of ISO7816 (Smart Card) ISO 7816 is an international standard related to electronic identification cards with contacts, especially smart cards, managed jointly by
The Misuse of RC4 in Microsoft Word and Excel
 The Misuse of RC4 in Microsoft Word and Excel Hongjun Wu Institute for Infocomm Research, Singapore hongjun@i2r.a-star.edu.sg Abstract. In this report, we point out a serious security flaw in Microsoft
The Misuse of RC4 in Microsoft Word and Excel Hongjun Wu Institute for Infocomm Research, Singapore hongjun@i2r.a-star.edu.sg Abstract. In this report, we point out a serious security flaw in Microsoft
IPsec Details 1 / 43. IPsec Details
 Header (AH) AH Layout Other AH Fields Mutable Parts of the IP Header What is an SPI? What s an SA? Encapsulating Security Payload (ESP) ESP Layout Padding Using ESP IPsec and Firewalls IPsec and the DNS
Header (AH) AH Layout Other AH Fields Mutable Parts of the IP Header What is an SPI? What s an SA? Encapsulating Security Payload (ESP) ESP Layout Padding Using ESP IPsec and Firewalls IPsec and the DNS
Security (II) ISO 7498-2: Security Architecture of OSI Reference Model. Outline. Course Outline: Fundamental Topics. EE5723/EE4723 Spring 2012
 Course Outline: Fundamental Topics System View of Network Security Network Security Model Security Threat Model & Security Services Model Overview of Network Security Security Basis: Cryptography Secret
Course Outline: Fundamental Topics System View of Network Security Network Security Model Security Threat Model & Security Services Model Overview of Network Security Security Basis: Cryptography Secret
SSL A discussion of the Secure Socket Layer
 www.harmonysecurity.com info@harmonysecurity.com SSL A discussion of the Secure Socket Layer By Stephen Fewer Contents 1 Introduction 2 2 Encryption Techniques 3 3 Protocol Overview 3 3.1 The SSL Record
www.harmonysecurity.com info@harmonysecurity.com SSL A discussion of the Secure Socket Layer By Stephen Fewer Contents 1 Introduction 2 2 Encryption Techniques 3 3 Protocol Overview 3 3.1 The SSL Record
Fixity Checks: Checksums, Message Digests and Digital Signatures Audrey Novak, ILTS Digital Preservation Committee November 2006
 Fixity Checks: Checksums, Message Digests and Digital Signatures Audrey Novak, ILTS Digital Preservation Committee November 2006 Introduction: Fixity, in preservation terms, means that the digital object
Fixity Checks: Checksums, Message Digests and Digital Signatures Audrey Novak, ILTS Digital Preservation Committee November 2006 Introduction: Fixity, in preservation terms, means that the digital object
Secure Network Communications FIPS 140 2 Non Proprietary Security Policy
 Secure Network Communications FIPS 140 2 Non Proprietary Security Policy 21 June 2010 Table of Contents Introduction Module Specification Ports and Interfaces Approved Algorithms Test Environment Roles
Secure Network Communications FIPS 140 2 Non Proprietary Security Policy 21 June 2010 Table of Contents Introduction Module Specification Ports and Interfaces Approved Algorithms Test Environment Roles
Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion
 Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion By Kerry Maletsky, Business Unit Director Crypto Products Summary There is a growing need for strong hardware security devices
Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion By Kerry Maletsky, Business Unit Director Crypto Products Summary There is a growing need for strong hardware security devices
Keywords Cloud Computing, CRC, RC4, RSA, Windows Microsoft Azure
 Volume 3, Issue 11, November 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Cloud Computing
Volume 3, Issue 11, November 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Cloud Computing
Overview of Cryptographic Tools for Data Security. Murat Kantarcioglu
 UT DALLAS Erik Jonsson School of Engineering & Computer Science Overview of Cryptographic Tools for Data Security Murat Kantarcioglu Pag. 1 Purdue University Cryptographic Primitives We will discuss the
UT DALLAS Erik Jonsson School of Engineering & Computer Science Overview of Cryptographic Tools for Data Security Murat Kantarcioglu Pag. 1 Purdue University Cryptographic Primitives We will discuss the
Fighting product clones through digital signatures
 Paul Curtis, Katrin Berkenkopf Embedded Experts Team, SEGGER Microcontroller Fighting product clones through digital signatures Product piracy and forgery are growing problems that not only decrease turnover
Paul Curtis, Katrin Berkenkopf Embedded Experts Team, SEGGER Microcontroller Fighting product clones through digital signatures Product piracy and forgery are growing problems that not only decrease turnover
Chapter 6 CDMA/802.11i
 Chapter 6 CDMA/802.11i IC322 Fall 2014 Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Some material copyright 1996-2012 J.F Kurose and K.W. Ross,
Chapter 6 CDMA/802.11i IC322 Fall 2014 Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Some material copyright 1996-2012 J.F Kurose and K.W. Ross,
Part I. Universität Klagenfurt - IWAS Multimedia Kommunikation (VK) M. Euchner; Mai 2001. Siemens AG 2001, ICN M NT
 Part I Contents Part I Introduction to Information Security Definition of Crypto Cryptographic Objectives Security Threats and Attacks The process Security Security Services Cryptography Cryptography (code
Part I Contents Part I Introduction to Information Security Definition of Crypto Cryptographic Objectives Security Threats and Attacks The process Security Security Services Cryptography Cryptography (code
USB Portable Storage Device: Security Problem Definition Summary
 USB Portable Storage Device: Security Problem Definition Summary Introduction The USB Portable Storage Device (hereafter referred to as the device or the TOE ) is a portable storage device that provides
USB Portable Storage Device: Security Problem Definition Summary Introduction The USB Portable Storage Device (hereafter referred to as the device or the TOE ) is a portable storage device that provides
SkyRecon Cryptographic Module (SCM)
 SkyRecon Cryptographic Module (SCM) FIPS 140-2 Documentation: Security Policy Abstract This document specifies the security policy for the SkyRecon Cryptographic Module (SCM) as described in FIPS PUB 140-2.
SkyRecon Cryptographic Module (SCM) FIPS 140-2 Documentation: Security Policy Abstract This document specifies the security policy for the SkyRecon Cryptographic Module (SCM) as described in FIPS PUB 140-2.
Current and Future Trends in Medical Electronics
 Current and Future Trends in Medical Electronics By Steven Dean, Medical Marketing Director, Texas Instruments www.arrownac.com 800.833.3557 Current and Future Trends in Medical Electronics By Steven Dean,
Current and Future Trends in Medical Electronics By Steven Dean, Medical Marketing Director, Texas Instruments www.arrownac.com 800.833.3557 Current and Future Trends in Medical Electronics By Steven Dean,
CIS 6930 Emerging Topics in Network Security. Topic 2. Network Security Primitives
 CIS 6930 Emerging Topics in Network Security Topic 2. Network Security Primitives 1 Outline Absolute basics Encryption/Decryption; Digital signatures; D-H key exchange; Hash functions; Application of hash
CIS 6930 Emerging Topics in Network Security Topic 2. Network Security Primitives 1 Outline Absolute basics Encryption/Decryption; Digital signatures; D-H key exchange; Hash functions; Application of hash
PUF Physical Unclonable Functions
 Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
An Introduction to Cryptography as Applied to the Smart Grid
 An Introduction to Cryptography as Applied to the Smart Grid Jacques Benoit, Cooper Power Systems Western Power Delivery Automation Conference Spokane, Washington March 2011 Agenda > Introduction > Symmetric
An Introduction to Cryptography as Applied to the Smart Grid Jacques Benoit, Cooper Power Systems Western Power Delivery Automation Conference Spokane, Washington March 2011 Agenda > Introduction > Symmetric
Victor Shoup Avi Rubin. fshoup,rubing@bellcore.com. Abstract
 Session Key Distribution Using Smart Cards Victor Shoup Avi Rubin Bellcore, 445 South St., Morristown, NJ 07960 fshoup,rubing@bellcore.com Abstract In this paper, we investigate a method by which smart
Session Key Distribution Using Smart Cards Victor Shoup Avi Rubin Bellcore, 445 South St., Morristown, NJ 07960 fshoup,rubing@bellcore.com Abstract In this paper, we investigate a method by which smart
Wireless LAN Security Mechanisms
 Wireless LAN Security Mechanisms Jingan Xu, Andreas Mitschele-Thiel Technical University of Ilmenau, Integrated Hard- and Software Systems Group jingan.xu@tu-ilmenau.de, mitsch@tu-ilmenau.de Abstract.
Wireless LAN Security Mechanisms Jingan Xu, Andreas Mitschele-Thiel Technical University of Ilmenau, Integrated Hard- and Software Systems Group jingan.xu@tu-ilmenau.de, mitsch@tu-ilmenau.de Abstract.
Review On Incremental Encrypted Backup For Cloud
 Review On Incremental Encrypted Backup For Cloud Rohini Ghenand, Pooja Kute, Swapnil Shinde, Amit Shinde, Mahesh Pavaskar, Shitalkumar Jain Department of Computer Engineering MIT AOE rohinighenand26@gmail.com
Review On Incremental Encrypted Backup For Cloud Rohini Ghenand, Pooja Kute, Swapnil Shinde, Amit Shinde, Mahesh Pavaskar, Shitalkumar Jain Department of Computer Engineering MIT AOE rohinighenand26@gmail.com
Chapter 6 Electronic Mail Security
 Cryptography and Network Security Chapter 6 Electronic Mail Security Lectured by Nguyễn Đức Thái Outline Pretty Good Privacy S/MIME 2 Electronic Mail Security In virtually all distributed environments,
Cryptography and Network Security Chapter 6 Electronic Mail Security Lectured by Nguyễn Đức Thái Outline Pretty Good Privacy S/MIME 2 Electronic Mail Security In virtually all distributed environments,
Welcome to the Introduction to Controller Area Network web seminar My name is William Stuart, and I am a Applications Engineer for the Automotive
 Welcome to the Introduction to Controller Area Network web seminar My name is William Stuart, and I am a Applications Engineer for the Automotive Products Group within Microchip. This web seminar today
Welcome to the Introduction to Controller Area Network web seminar My name is William Stuart, and I am a Applications Engineer for the Automotive Products Group within Microchip. This web seminar today
KeyStone Architecture Security Accelerator (SA) User Guide
 KeyStone Architecture Security Accelerator (SA) User Guide Literature Number: SPRUGY6B January 2013 Release History www.ti.com Release Date Description/Comments SPRUGY6B January 2013 Added addition engine
KeyStone Architecture Security Accelerator (SA) User Guide Literature Number: SPRUGY6B January 2013 Release History www.ti.com Release Date Description/Comments SPRUGY6B January 2013 Added addition engine
Smart Card Technology Capabilities
 Smart Card Technology Capabilities Won J. Jun Giesecke & Devrient (G&D) July 8, 2003 Smart Card Technology Capabilities 1 Table of Contents Smart Card Basics Current Technology Requirements and Standards
Smart Card Technology Capabilities Won J. Jun Giesecke & Devrient (G&D) July 8, 2003 Smart Card Technology Capabilities 1 Table of Contents Smart Card Basics Current Technology Requirements and Standards
USB Portable Storage Device: Security Problem Definition Summary
 USB Portable Storage Device: Security Problem Definition Summary Introduction The USB Portable Storage Device (hereafter referred to as the device or the TOE ) is a portable storage device that provides
USB Portable Storage Device: Security Problem Definition Summary Introduction The USB Portable Storage Device (hereafter referred to as the device or the TOE ) is a portable storage device that provides
The Research and Design of 3G terminal data confidentiality services
 2010 International Conference on E-Business and E-Government The Research and Design of 3G terminal data confidentiality services Fangzhou, Zhang, Xiaoge,Dong Dan, Wang, Xibao,Ma, Chen,Chen School of Computer
2010 International Conference on E-Business and E-Government The Research and Design of 3G terminal data confidentiality services Fangzhou, Zhang, Xiaoge,Dong Dan, Wang, Xibao,Ma, Chen,Chen School of Computer
Chair for Network Architectures and Services Department of Informatics TU München Prof. Carle. Network Security. Chapter 13
 Chair for Network Architectures and Services Department of Informatics TU München Prof. Carle Network Security Chapter 13 Some More Secure Channel Issues Outline In the course we have yet only seen catastrophic
Chair for Network Architectures and Services Department of Informatics TU München Prof. Carle Network Security Chapter 13 Some More Secure Channel Issues Outline In the course we have yet only seen catastrophic
NXP & Security Innovation Encryption for ARM MCUs
 NXP & Security Innovation Encryption for ARM MCUs Presenters Gene Carter- International Product Manager, NXP Semiconductors Gene is responsible for marketing of the ARM7 and Cortex-M3 microcontrollers.
NXP & Security Innovation Encryption for ARM MCUs Presenters Gene Carter- International Product Manager, NXP Semiconductors Gene is responsible for marketing of the ARM7 and Cortex-M3 microcontrollers.
FIPS 140-2 Non- Proprietary Security Policy. McAfee SIEM Cryptographic Module, Version 1.0
 FIPS 40-2 Non- Proprietary Security Policy McAfee SIEM Cryptographic Module, Version.0 Document Version.4 December 2, 203 Document Version.4 McAfee Page of 6 Prepared For: Prepared By: McAfee, Inc. 282
FIPS 40-2 Non- Proprietary Security Policy McAfee SIEM Cryptographic Module, Version.0 Document Version.4 December 2, 203 Document Version.4 McAfee Page of 6 Prepared For: Prepared By: McAfee, Inc. 282
Paillier Threshold Encryption Toolbox
 Paillier Threshold Encryption Toolbox October 23, 2010 1 Introduction Following a desire for secure (encrypted) multiparty computation, the University of Texas at Dallas Data Security and Privacy Lab created
Paillier Threshold Encryption Toolbox October 23, 2010 1 Introduction Following a desire for secure (encrypted) multiparty computation, the University of Texas at Dallas Data Security and Privacy Lab created
Network Security CS 5490/6490 Fall 2015 Lecture Notes 8/26/2015
 Network Security CS 5490/6490 Fall 2015 Lecture Notes 8/26/2015 Chapter 2: Introduction to Cryptography What is cryptography? It is a process/art of mangling information in such a way so as to make it
Network Security CS 5490/6490 Fall 2015 Lecture Notes 8/26/2015 Chapter 2: Introduction to Cryptography What is cryptography? It is a process/art of mangling information in such a way so as to make it
CS 393 Network Security. Nasir Memon Polytechnic University Module 11 Secure Email
 CS 393 Network Security Nasir Memon Polytechnic University Module 11 Secure Email Course Logistics HW 5 due Thursday Graded exams returned and discussed. Read Chapter 5 of text 4/2/02 Module 11 - Secure
CS 393 Network Security Nasir Memon Polytechnic University Module 11 Secure Email Course Logistics HW 5 due Thursday Graded exams returned and discussed. Read Chapter 5 of text 4/2/02 Module 11 - Secure
Network Security. Security of Wireless Local Area Networks. Chapter 15. Network Security (WS 2002): 15 Wireless LAN Security 1 Dr.-Ing G.
 Network Security Chapter 15 Security of Wireless Local Area Networks Network Security WS 2002: 15 Wireless LAN Security 1 IEEE 802.11 IEEE 802.11 standardizes medium access control MAC and physical characteristics
Network Security Chapter 15 Security of Wireless Local Area Networks Network Security WS 2002: 15 Wireless LAN Security 1 IEEE 802.11 IEEE 802.11 standardizes medium access control MAC and physical characteristics
Cryptography and Network Security Chapter 12
 Cryptography and Network Security Chapter 12 Fifth Edition by William Stallings Lecture slides by Lawrie Brown (with edits by RHB) Chapter 12 Message Authentication Codes At cats' green on the Sunday he
Cryptography and Network Security Chapter 12 Fifth Edition by William Stallings Lecture slides by Lawrie Brown (with edits by RHB) Chapter 12 Message Authentication Codes At cats' green on the Sunday he
Strengthen RFID Tags Security Using New Data Structure
 International Journal of Control and Automation 51 Strengthen RFID Tags Security Using New Data Structure Yan Liang and Chunming Rong Department of Electrical Engineering and Computer Science, University
International Journal of Control and Automation 51 Strengthen RFID Tags Security Using New Data Structure Yan Liang and Chunming Rong Department of Electrical Engineering and Computer Science, University
Encryption, Data Integrity, Digital Certificates, and SSL. Developed by. Jerry Scott. SSL Primer-1-1
 Encryption, Data Integrity, Digital Certificates, and SSL Developed by Jerry Scott 2002 SSL Primer-1-1 Ideas Behind Encryption When information is transmitted across intranets or the Internet, others can
Encryption, Data Integrity, Digital Certificates, and SSL Developed by Jerry Scott 2002 SSL Primer-1-1 Ideas Behind Encryption When information is transmitted across intranets or the Internet, others can
Message Authentication Codes. Lecture Outline
 Message Authentication Codes Murat Kantarcioglu Based on Prof. Ninghui Li s Slides Message Authentication Code Lecture Outline 1 Limitation of Using Hash Functions for Authentication Require an authentic
Message Authentication Codes Murat Kantarcioglu Based on Prof. Ninghui Li s Slides Message Authentication Code Lecture Outline 1 Limitation of Using Hash Functions for Authentication Require an authentic
Three attacks in SSL protocol and their solutions
 Three attacks in SSL protocol and their solutions Hong lei Zhang Department of Computer Science The University of Auckland zhon003@ec.auckland.ac.nz Abstract Secure Socket Layer (SSL) and Transport Layer
Three attacks in SSL protocol and their solutions Hong lei Zhang Department of Computer Science The University of Auckland zhon003@ec.auckland.ac.nz Abstract Secure Socket Layer (SSL) and Transport Layer
CSC474/574 - Information Systems Security: Homework1 Solutions Sketch
 CSC474/574 - Information Systems Security: Homework1 Solutions Sketch February 20, 2005 1. Consider slide 12 in the handout for topic 2.2. Prove that the decryption process of a one-round Feistel cipher
CSC474/574 - Information Systems Security: Homework1 Solutions Sketch February 20, 2005 1. Consider slide 12 in the handout for topic 2.2. Prove that the decryption process of a one-round Feistel cipher
Network Security Technology Network Management
 COMPUTER NETWORKS Network Security Technology Network Management Source Encryption E(K,P) Decryption D(K,C) Destination The author of these slides is Dr. Mark Pullen of George Mason University. Permission
COMPUTER NETWORKS Network Security Technology Network Management Source Encryption E(K,P) Decryption D(K,C) Destination The author of these slides is Dr. Mark Pullen of George Mason University. Permission
FIPS 140 2 Non Proprietary Security Policy: IBM Internet Security Systems Proventia GX Series Security
 FIPS 140 2 Non Proprietary Security Policy IBM Internet Security Systems Proventia GX Series Security Document Version 1.2 January 31, 2013 Document Version 1.2 IBM Internet Security Systems Page 1 of
FIPS 140 2 Non Proprietary Security Policy IBM Internet Security Systems Proventia GX Series Security Document Version 1.2 January 31, 2013 Document Version 1.2 IBM Internet Security Systems Page 1 of
Rfid Authentication Protocol for security and privacy Maintenance in Cloud Based Employee Management System
 Rfid Authentication Protocol for security and privacy Maintenance in Cloud Based Employee Management System ArchanaThange Post Graduate Student, DKGOI s COE, Swami Chincholi, Maharashtra, India archanathange7575@gmail.com,
Rfid Authentication Protocol for security and privacy Maintenance in Cloud Based Employee Management System ArchanaThange Post Graduate Student, DKGOI s COE, Swami Chincholi, Maharashtra, India archanathange7575@gmail.com,
Privacy and Security in library RFID Issues, Practices and Architecture
 Privacy and Security in library RFID Issues, Practices and Architecture David Molnar and David Wagner University of California, Berkeley CCS '04 October 2004 Overview Motivation RFID Background Library
Privacy and Security in library RFID Issues, Practices and Architecture David Molnar and David Wagner University of California, Berkeley CCS '04 October 2004 Overview Motivation RFID Background Library
Gemalto Mifare 1K Datasheet
 Gemalto Mifare 1K Datasheet Contents 1. Overview...3 1.1 User convenience and speed...3 1.2 Security...3 1.3 Anticollision...3 2. Gemalto Mifare Features...4 2.1 Compatibility with norms...4 2.2 Electrical...4
Gemalto Mifare 1K Datasheet Contents 1. Overview...3 1.1 User convenience and speed...3 1.2 Security...3 1.3 Anticollision...3 2. Gemalto Mifare Features...4 2.1 Compatibility with norms...4 2.2 Electrical...4
CS 758: Cryptography / Network Security
 CS 758: Cryptography / Network Security offered in the Fall Semester, 2003, by Doug Stinson my office: DC 3122 my email address: dstinson@uwaterloo.ca my web page: http://cacr.math.uwaterloo.ca/~dstinson/index.html
CS 758: Cryptography / Network Security offered in the Fall Semester, 2003, by Doug Stinson my office: DC 3122 my email address: dstinson@uwaterloo.ca my web page: http://cacr.math.uwaterloo.ca/~dstinson/index.html
Symantec Corporation Symantec Enterprise Vault Cryptographic Module Software Version: 1.0.0.2
 Symantec Corporation Symantec Enterprise Vault Cryptographic Module Software Version: 1.0.0.2 FIPS 140 2 Non Proprietary Security Policy FIPS Security Level: 1 Document Version: 1.1 Prepared for: Prepared
Symantec Corporation Symantec Enterprise Vault Cryptographic Module Software Version: 1.0.0.2 FIPS 140 2 Non Proprietary Security Policy FIPS Security Level: 1 Document Version: 1.1 Prepared for: Prepared
Authentication and Encryption: How to order them? Motivation
 Authentication and Encryption: How to order them? Debdeep Muhopadhyay IIT Kharagpur Motivation Wide spread use of internet requires establishment of a secure channel. Typical implementations operate in
Authentication and Encryption: How to order them? Debdeep Muhopadhyay IIT Kharagpur Motivation Wide spread use of internet requires establishment of a secure channel. Typical implementations operate in
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 6. Wireless Network Security
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 6 Wireless Network Security Objectives Overview of IEEE 802.11 wireless security Define vulnerabilities of Open System Authentication,
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 6 Wireless Network Security Objectives Overview of IEEE 802.11 wireless security Define vulnerabilities of Open System Authentication,
1. INTRODUCTION. Keywords SMS, GSM network, electrical device, encryption, control.
 Secure Control of Remote Electrical Devices Using Mobile SMS Services Kishor T. Mane 1, G.A. Patil 2 1. Asst. Professor, 2. Head and Asst. Professor D. Y. Patil college of Engg. & Tech. Kolhapur, Maharashtra,
Secure Control of Remote Electrical Devices Using Mobile SMS Services Kishor T. Mane 1, G.A. Patil 2 1. Asst. Professor, 2. Head and Asst. Professor D. Y. Patil college of Engg. & Tech. Kolhapur, Maharashtra,
Project: Simulated Encrypted File System (SEFS)
 Project: Simulated Encrypted File System (SEFS) Omar Chowdhury Fall 2015 CS526: Information Security 1 Motivation Traditionally files are stored in the disk in plaintext. If the disk gets stolen by a perpetrator,
Project: Simulated Encrypted File System (SEFS) Omar Chowdhury Fall 2015 CS526: Information Security 1 Motivation Traditionally files are stored in the disk in plaintext. If the disk gets stolen by a perpetrator,
Northrop Grumman M5 Network Security SCS Linux Kernel Cryptographic Services. FIPS Security Policy Version 2.42. www.northropgrumman.
 Northrop Grumman M5 Network Security SCS Linux Kernel Cryptographic Services FIPS Security Policy Version 2.42 www.northropgrumman.com/m5/ SCS Linux Kernel Cryptographic Services Security Policy Version
Northrop Grumman M5 Network Security SCS Linux Kernel Cryptographic Services FIPS Security Policy Version 2.42 www.northropgrumman.com/m5/ SCS Linux Kernel Cryptographic Services Security Policy Version
SECURE USB FLASH DRIVE. Non-Proprietary Security Policy
 SECURE USB FLASH DRIVE Non-Proprietary Security Policy FIPS 140-2 SECURITY POLICY VERSION 9 Page 1 of 10 Definitions and Acronyms AES Advanced Encryption Standard CBC Cipher Block Chaining CRC Cyclic Redundancy
SECURE USB FLASH DRIVE Non-Proprietary Security Policy FIPS 140-2 SECURITY POLICY VERSION 9 Page 1 of 10 Definitions and Acronyms AES Advanced Encryption Standard CBC Cipher Block Chaining CRC Cyclic Redundancy
FIPS 140 2 Non Proprietary Security Policy: Kingston Technology DataTraveler DT4000 Series USB Flash Drive
 FIPS 140 2 Non Proprietary Security Policy Kingston Technology Company, Inc. DataTraveler DT4000 G2 Series USB Flash Drive Document Version 1.8 December 3, 2014 Document Version 1.8 Kingston Technology
FIPS 140 2 Non Proprietary Security Policy Kingston Technology Company, Inc. DataTraveler DT4000 G2 Series USB Flash Drive Document Version 1.8 December 3, 2014 Document Version 1.8 Kingston Technology
Security design for a new local area Network AULWLAN
 International Conference on Computer Systems and Technologies CompSysTech 2003 Security design for a new local area Network AULWLAN Ahmed Abdo Ali ABSTRACT : This paper presents a security scheme for a
International Conference on Computer Systems and Technologies CompSysTech 2003 Security design for a new local area Network AULWLAN Ahmed Abdo Ali ABSTRACT : This paper presents a security scheme for a
Designing a Secure Client-Server System Master of Science Thesis in the Programme Software Engineering & Technology
 Designing a Secure Client-Server System Master of Science Thesis in the Programme Software Engineering & Technology FREDRIK ANDERSSON Department of Computer Science and Engineering CHALMERS UNIVERSITY
Designing a Secure Client-Server System Master of Science Thesis in the Programme Software Engineering & Technology FREDRIK ANDERSSON Department of Computer Science and Engineering CHALMERS UNIVERSITY
Secure SCADA Communication Protocol Performance Test Results
 PNNL-17118 Secure SCADA Communication Protocol Performance Test Results M.D. Hadley K.A. Huston August 2007 Prepared for U.S. Department of Energy Office of Electricity Delivery and Energy Reliability
PNNL-17118 Secure SCADA Communication Protocol Performance Test Results M.D. Hadley K.A. Huston August 2007 Prepared for U.S. Department of Energy Office of Electricity Delivery and Energy Reliability
MP3 Player CSEE 4840 SPRING 2010 PROJECT DESIGN. zl2211@columbia.edu. ml3088@columbia.edu
 MP3 Player CSEE 4840 SPRING 2010 PROJECT DESIGN Zheng Lai Zhao Liu Meng Li Quan Yuan zl2215@columbia.edu zl2211@columbia.edu ml3088@columbia.edu qy2123@columbia.edu I. Overview Architecture The purpose
MP3 Player CSEE 4840 SPRING 2010 PROJECT DESIGN Zheng Lai Zhao Liu Meng Li Quan Yuan zl2215@columbia.edu zl2211@columbia.edu ml3088@columbia.edu qy2123@columbia.edu I. Overview Architecture The purpose
8051 MICROCONTROLLER COURSE
 8051 MICROCONTROLLER COURSE Objective: 1. Familiarization with different types of Microcontroller 2. To know 8051 microcontroller in detail 3. Programming and Interfacing 8051 microcontroller Prerequisites:
8051 MICROCONTROLLER COURSE Objective: 1. Familiarization with different types of Microcontroller 2. To know 8051 microcontroller in detail 3. Programming and Interfacing 8051 microcontroller Prerequisites:
E-commerce. business. technology. society. Kenneth C. Laudon Carol Guercio Traver. Second Edition. Copyright 2007 Pearson Education, Inc.
 Copyright 2007 Pearson Education, Inc. Slide 5-1 E-commerce business. technology. society. Second Edition Kenneth C. Laudon Carol Guercio Traver Copyright 2007 Pearson Education, Inc. Slide 5-2 Chapter
Copyright 2007 Pearson Education, Inc. Slide 5-1 E-commerce business. technology. society. Second Edition Kenneth C. Laudon Carol Guercio Traver Copyright 2007 Pearson Education, Inc. Slide 5-2 Chapter
Key Management Interoperability Protocol (KMIP)
 (KMIP) Addressing the Need for Standardization in Enterprise Key Management Version 1.0, May 20, 2009 Copyright 2009 by the Organization for the Advancement of Structured Information Standards (OASIS).
(KMIP) Addressing the Need for Standardization in Enterprise Key Management Version 1.0, May 20, 2009 Copyright 2009 by the Organization for the Advancement of Structured Information Standards (OASIS).
Security Policy. Trapeze Networks
 MP-422F Mobility Point Security Policy Trapeze Networks August 14, 2009 Copyright Trapeze Networks 2007. May be reproduced only in its original entirety [without revision]. TABLE OF CONTENTS 1. MODULE
MP-422F Mobility Point Security Policy Trapeze Networks August 14, 2009 Copyright Trapeze Networks 2007. May be reproduced only in its original entirety [without revision]. TABLE OF CONTENTS 1. MODULE
Surveillance System Using Wireless Sensor Networks
 Surveillance System Using Wireless Sensor Networks Dan Nguyen, Leo Chang Computer Engineering, Santa Clara University Santa Clara, California, USA dantnguyen84@gmail.com chihshun@gmail.com Abstract The
Surveillance System Using Wireless Sensor Networks Dan Nguyen, Leo Chang Computer Engineering, Santa Clara University Santa Clara, California, USA dantnguyen84@gmail.com chihshun@gmail.com Abstract The
SecureMessageRecoveryandBatchVerificationusingDigitalSignature
 Global Journal of Computer Science and Technology: F Graphics & Vision Volume 14 Issue 4 Version 1.0 Year 2014 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals
Global Journal of Computer Science and Technology: F Graphics & Vision Volume 14 Issue 4 Version 1.0 Year 2014 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals
CS5490/6490: Network Security- Lecture Notes - November 9 th 2015
 CS5490/6490: Network Security- Lecture Notes - November 9 th 2015 Wireless LAN security (Reference - Security & Cooperation in Wireless Networks by Buttyan & Hubaux, Cambridge Univ. Press, 2007, Chapter
CS5490/6490: Network Security- Lecture Notes - November 9 th 2015 Wireless LAN security (Reference - Security & Cooperation in Wireless Networks by Buttyan & Hubaux, Cambridge Univ. Press, 2007, Chapter
Chapter 8. Network Security
 Chapter 8 Network Security Cryptography Introduction to Cryptography Substitution Ciphers Transposition Ciphers One-Time Pads Two Fundamental Cryptographic Principles Need for Security Some people who
Chapter 8 Network Security Cryptography Introduction to Cryptography Substitution Ciphers Transposition Ciphers One-Time Pads Two Fundamental Cryptographic Principles Need for Security Some people who
Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked Questions. July, 2006. Developed by: Smart Card Alliance Identity Council
 Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked Questions July, 2006 Developed by: Smart Card Alliance Identity Council Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked
Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked Questions July, 2006 Developed by: Smart Card Alliance Identity Council Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked
Authentication in WLAN
 Authentication in WLAN Flaws in WEP (Wired Equivalent Privacy) Wi-Fi Protected Access (WPA) Based on draft 3 of the IEEE 802.11i. Provides stronger data encryption and user authentication (largely missing
Authentication in WLAN Flaws in WEP (Wired Equivalent Privacy) Wi-Fi Protected Access (WPA) Based on draft 3 of the IEEE 802.11i. Provides stronger data encryption and user authentication (largely missing
(C) Global Journal of Engineering Science and Research Management
 DEPENDABLE STORAGE FOR VEHICLE INSURANCE MANAGEMENT THROUGH SECURED ENCRYPTION IN CLOUD COMPUTING Prof.Abhijeet A.Chincholkar *1, Ms.Najuka Todekar 2 *1 M.E. Digital Electronics, JCOET Yavatmal, India.
DEPENDABLE STORAGE FOR VEHICLE INSURANCE MANAGEMENT THROUGH SECURED ENCRYPTION IN CLOUD COMPUTING Prof.Abhijeet A.Chincholkar *1, Ms.Najuka Todekar 2 *1 M.E. Digital Electronics, JCOET Yavatmal, India.
Chapter 11 Security+ Guide to Network Security Fundamentals, Third Edition Basic Cryptography
 Chapter 11 Security+ Guide to Network Security Fundamentals, Third Edition Basic Cryptography What Is Steganography? Steganography Process of hiding the existence of the data within another file Example:
Chapter 11 Security+ Guide to Network Security Fundamentals, Third Edition Basic Cryptography What Is Steganography? Steganography Process of hiding the existence of the data within another file Example:
AD Image Encryption. Format Version 1.2
 AD Image Encryption Format Version 1.2 17 May 2010 Table of Contents Introduction... 3 Overview... 3 Image Formats... 4 Keys... 4 Credentials... 4 Certificates... 4 Image Key encryption... 5 Appendix A
AD Image Encryption Format Version 1.2 17 May 2010 Table of Contents Introduction... 3 Overview... 3 Image Formats... 4 Keys... 4 Credentials... 4 Certificates... 4 Image Key encryption... 5 Appendix A
Small 7-key User-definable Remote Control User s Guide
 Small 7-key User-definable Remote Control User s Guide RMB-CM11111_Ver1.0 Table of Contents Chapter 1. Overview...1 1.1 Overview... 1 1.2 Features... 1 1.3 Applications... 1 Chapter 2. Key Description...2
Small 7-key User-definable Remote Control User s Guide RMB-CM11111_Ver1.0 Table of Contents Chapter 1. Overview...1 1.1 Overview... 1 1.2 Features... 1 1.3 Applications... 1 Chapter 2. Key Description...2
YubiKey Integration for Full Disk Encryption
 YubiKey Integration for Full Disk Encryption Pre-Boot Authentication Version 1.2 May 7, 2012 Introduction Disclaimer yubico Yubico is the leading provider of simple, open online identity protection. The
YubiKey Integration for Full Disk Encryption Pre-Boot Authentication Version 1.2 May 7, 2012 Introduction Disclaimer yubico Yubico is the leading provider of simple, open online identity protection. The
Kaseya US Sales, LLC Virtual System Administrator Cryptographic Module Software Version: 1.0
 Kaseya US Sales, LLC Virtual System Administrator Cryptographic Module Software Version: 1.0 FIPS 140-2 Non-Proprietary Security Policy FIPS Security Level: 1 Document Version: 1.0 Prepared for: Prepared
Kaseya US Sales, LLC Virtual System Administrator Cryptographic Module Software Version: 1.0 FIPS 140-2 Non-Proprietary Security Policy FIPS Security Level: 1 Document Version: 1.0 Prepared for: Prepared
Computer Networks. Network Security and Ethics. Week 14. College of Information Science and Engineering Ritsumeikan University
 Computer Networks Network Security and Ethics Week 14 College of Information Science and Engineering Ritsumeikan University Security Intro for Admins l Network administrators can break security into two
Computer Networks Network Security and Ethics Week 14 College of Information Science and Engineering Ritsumeikan University Security Intro for Admins l Network administrators can break security into two
Introduction...3 Terms in this Document...3 Conditions for Secure Operation...3 Requirements...3 Key Generation Requirements...
 Hush Encryption Engine White Paper Introduction...3 Terms in this Document...3 Conditions for Secure Operation...3 Requirements...3 Key Generation Requirements...4 Passphrase Requirements...4 Data Requirements...4
Hush Encryption Engine White Paper Introduction...3 Terms in this Document...3 Conditions for Secure Operation...3 Requirements...3 Key Generation Requirements...4 Passphrase Requirements...4 Data Requirements...4
GSM and UMTS security
 2007 Levente Buttyán Why is security more of a concern in wireless? no inherent physical protection physical connections between devices are replaced by logical associations sending and receiving messages
2007 Levente Buttyán Why is security more of a concern in wireless? no inherent physical protection physical connections between devices are replaced by logical associations sending and receiving messages
Key Hopping A Security Enhancement Scheme for IEEE 802.11 WEP Standards
 White Paper Key Hopping A Security Enhancement Scheme for IEEE 802.11 WEP Standards By Dr. Wen-Ping Ying, Director of Software Development, February 2002 Introduction Wireless LAN networking allows the
White Paper Key Hopping A Security Enhancement Scheme for IEEE 802.11 WEP Standards By Dr. Wen-Ping Ying, Director of Software Development, February 2002 Introduction Wireless LAN networking allows the
PACKAGE OUTLINE DALLAS DS2434 DS2434 GND. PR 35 PACKAGE See Mech. Drawings Section
 PRELIMINARY DS2434 Battery Identification Chip FEATURES Provides unique ID number to battery packs PACKAGE OUTLINE Eliminates thermistors by sensing battery temperature on chip DALLAS DS2434 1 2 3 256
PRELIMINARY DS2434 Battery Identification Chip FEATURES Provides unique ID number to battery packs PACKAGE OUTLINE Eliminates thermistors by sensing battery temperature on chip DALLAS DS2434 1 2 3 256
Software Engineering 4C03 Research Project. An Overview of Secure Transmission on the World Wide Web. Sean MacDonald 0043306
 Software Engineering 4C03 Research Project An Overview of Secure Transmission on the World Wide Web Sean MacDonald 0043306 Tuesday April 5, 2005 Introduction Software Engineering 4C03 Research Project
Software Engineering 4C03 Research Project An Overview of Secure Transmission on the World Wide Web Sean MacDonald 0043306 Tuesday April 5, 2005 Introduction Software Engineering 4C03 Research Project
ADVANCED VEHICLE TRACKING SYSTEM USING ARM7
 ADVANCED VEHICLE TRACKING SYSTEM USING ARM7 L. Kishore 1, Arun Raja 2 1 M.E. Embedded Systems Technologies, Sri Ramakrishna Engineering College 2 Assistant Professor, Department of ECE, Sri Ramakrishna
ADVANCED VEHICLE TRACKING SYSTEM USING ARM7 L. Kishore 1, Arun Raja 2 1 M.E. Embedded Systems Technologies, Sri Ramakrishna Engineering College 2 Assistant Professor, Department of ECE, Sri Ramakrishna
Security. Contents. S-72.3240 Wireless Personal, Local, Metropolitan, and Wide Area Networks 1
 Contents Security requirements Public key cryptography Key agreement/transport schemes Man-in-the-middle attack vulnerability Encryption. digital signature, hash, certification Complete security solutions
Contents Security requirements Public key cryptography Key agreement/transport schemes Man-in-the-middle attack vulnerability Encryption. digital signature, hash, certification Complete security solutions
Microsoft Identity Lifecycle Manager & Gemalto.NET Solutions. Jan 23 rd, 2007
 Microsoft Identity Lifecycle Manager & Gemalto.NET Solutions Jan 23 rd, 2007 Microsoft ILM is a comprehensive, integrated, identity and access solution within the Microsoft system architecture. It includes
Microsoft Identity Lifecycle Manager & Gemalto.NET Solutions Jan 23 rd, 2007 Microsoft ILM is a comprehensive, integrated, identity and access solution within the Microsoft system architecture. It includes
Connected from everywhere. Cryptelo completely protects your data. Data transmitted to the server. Data sharing (both files and directory structure)
 Cryptelo Drive Cryptelo Drive is a virtual drive, where your most sensitive data can be stored. Protect documents, contracts, business know-how, or photographs - in short, anything that must be kept safe.
Cryptelo Drive Cryptelo Drive is a virtual drive, where your most sensitive data can be stored. Protect documents, contracts, business know-how, or photographs - in short, anything that must be kept safe.
Application Note. Atmel CryptoAuthentication Product Uses. Atmel ATSHA204. Abstract. Overview
 Application Note Atmel CryptoAuthentication Product Uses Atmel Abstract Companies are continuously searching for ways to protect property using various security implementations; however, the cost of security
Application Note Atmel CryptoAuthentication Product Uses Atmel Abstract Companies are continuously searching for ways to protect property using various security implementations; however, the cost of security
ETSI TS 102 176-2 V1.2.1 (2005-07)
 TS 102 176-2 V1.2.1 (2005-07) Technical Specification Electronic Signatures and Infrastructures (ESI); Algorithms and Parameters for Secure Electronic Signatures; Part 2: Secure channel protocols and algorithms
TS 102 176-2 V1.2.1 (2005-07) Technical Specification Electronic Signatures and Infrastructures (ESI); Algorithms and Parameters for Secure Electronic Signatures; Part 2: Secure channel protocols and algorithms
Lecture N -1- PHYS 3330. Microcontrollers
 Lecture N -1- PHYS 3330 Microcontrollers If you need more than a handful of logic gates to accomplish the task at hand, you likely should use a microcontroller instead of discrete logic gates 1. Microcontrollers
Lecture N -1- PHYS 3330 Microcontrollers If you need more than a handful of logic gates to accomplish the task at hand, you likely should use a microcontroller instead of discrete logic gates 1. Microcontrollers
WebService Security. A guide to set up highly secured client-server communications using WS-Security extensions to the SOAP protocol
 WebService Security A guide to set up highly secured client-server communications using WS-Security extensions to the SOAP protocol Jam Hamidi Senior Technical Analyst BCcampus, Victoria, British Columbia,
WebService Security A guide to set up highly secured client-server communications using WS-Security extensions to the SOAP protocol Jam Hamidi Senior Technical Analyst BCcampus, Victoria, British Columbia,
MF1 IC S50. 1. General description. Functional specification. 1.1 Contactless Energy and Data Transfer. 1.2 Anticollision. Energy
 Rev. 5.2 15 January 2007 Product data sheet 001052 PUBLIC 1. General description NXP has developed the Mifare to be used in contactess smart cards according to ISO/IEC 14443A. The communication layer (
Rev. 5.2 15 January 2007 Product data sheet 001052 PUBLIC 1. General description NXP has developed the Mifare to be used in contactess smart cards according to ISO/IEC 14443A. The communication layer (
SECURITY IMPROVMENTS TO THE DIFFIE-HELLMAN SCHEMES
 www.arpapress.com/volumes/vol8issue1/ijrras_8_1_10.pdf SECURITY IMPROVMENTS TO THE DIFFIE-HELLMAN SCHEMES Malek Jakob Kakish Amman Arab University, Department of Computer Information Systems, P.O.Box 2234,
www.arpapress.com/volumes/vol8issue1/ijrras_8_1_10.pdf SECURITY IMPROVMENTS TO THE DIFFIE-HELLMAN SCHEMES Malek Jakob Kakish Amman Arab University, Department of Computer Information Systems, P.O.Box 2234,
Intelligent Home Automation and Security System
 Intelligent Home Automation and Security System Ms. Radhamani N Department of Electronics and communication, VVIET, Mysore, India ABSTRACT: In todays scenario safer home security is required, As the technology
Intelligent Home Automation and Security System Ms. Radhamani N Department of Electronics and communication, VVIET, Mysore, India ABSTRACT: In todays scenario safer home security is required, As the technology
SECUDE AG. FinallySecure Enterprise Cryptographic Module. FIPS 140-2 Security Policy
 SECUDE AG FinallySecure Enterprise Cryptographic Module (SW Version: 1.0) FIPS 140-2 Security Policy Document Version 2.4 04/22/2010 Copyright SECUDE AG, 2010. May be reproduced only in its original entirety
SECUDE AG FinallySecure Enterprise Cryptographic Module (SW Version: 1.0) FIPS 140-2 Security Policy Document Version 2.4 04/22/2010 Copyright SECUDE AG, 2010. May be reproduced only in its original entirety
WHITE PAPER AUGUST 2014. Preventing Security Breaches by Eliminating the Need to Transmit and Store Passwords
 WHITE PAPER AUGUST 2014 Preventing Security Breaches by Eliminating the Need to Transmit and Store Passwords 2 WHITE PAPER: PREVENTING SECURITY BREACHES Table of Contents on t Become the Next Headline
WHITE PAPER AUGUST 2014 Preventing Security Breaches by Eliminating the Need to Transmit and Store Passwords 2 WHITE PAPER: PREVENTING SECURITY BREACHES Table of Contents on t Become the Next Headline
Final Design Report 19 April 2011. Project Name: utouch
 EEL 4924 Electrical Engineering Design (Senior Design) Final Design Report 19 April 2011 Project Name: utouch Team Members: Name: Issam Bouter Name: Constantine Metropulos Email: sambouter@gmail.com Email:
EEL 4924 Electrical Engineering Design (Senior Design) Final Design Report 19 April 2011 Project Name: utouch Team Members: Name: Issam Bouter Name: Constantine Metropulos Email: sambouter@gmail.com Email:
Elements of Security
 Elements of Security Dr. Bill Young Department of Computer Sciences University of Texas at Austin Last updated: April 15, 2015 Slideset 8: 1 Some Poetry Mary had a little key (It s all she could export)
Elements of Security Dr. Bill Young Department of Computer Sciences University of Texas at Austin Last updated: April 15, 2015 Slideset 8: 1 Some Poetry Mary had a little key (It s all she could export)
SubmitedBy: Name Reg No Email Address. Mirza Kashif Abrar 790604-T079 kasmir07 (at) student.hh.se
 SubmitedBy: Name Reg No Email Address Mirza Kashif Abrar 790604-T079 kasmir07 (at) student.hh.se Abid Hussain 780927-T039 abihus07 (at) student.hh.se Imran Ahmad Khan 770630-T053 imrakh07 (at) student.hh.se
SubmitedBy: Name Reg No Email Address Mirza Kashif Abrar 790604-T079 kasmir07 (at) student.hh.se Abid Hussain 780927-T039 abihus07 (at) student.hh.se Imran Ahmad Khan 770630-T053 imrakh07 (at) student.hh.se
Computer Security: Principles and Practice
 Computer Security: Principles and Practice Chapter 20 Public-Key Cryptography and Message Authentication First Edition by William Stallings and Lawrie Brown Lecture slides by Lawrie Brown Public-Key Cryptography
Computer Security: Principles and Practice Chapter 20 Public-Key Cryptography and Message Authentication First Edition by William Stallings and Lawrie Brown Lecture slides by Lawrie Brown Public-Key Cryptography
Data Acquisition Module with I2C interface «I2C-FLEXEL» User s Guide
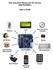 Data Acquisition Module with I2C interface «I2C-FLEXEL» User s Guide Sensors LCD Real Time Clock/ Calendar DC Motors Buzzer LED dimming Relay control I2C-FLEXEL PS2 Keyboards Servo Motors IR Remote Control
Data Acquisition Module with I2C interface «I2C-FLEXEL» User s Guide Sensors LCD Real Time Clock/ Calendar DC Motors Buzzer LED dimming Relay control I2C-FLEXEL PS2 Keyboards Servo Motors IR Remote Control
802.11 Security (WEP, WPA\WPA2) 19/05/2009. Giulio Rossetti Unipi Giulio.Rossetti@gmail.com
 802.11 Security (WEP, WPA\WPA2) 19/05/2009 Giulio Rossetti Unipi Giulio.Rossetti@gmail.com 802.11 Security Standard: WEP Wired Equivalent Privacy The packets are encrypted, before sent, with a Secret Key
802.11 Security (WEP, WPA\WPA2) 19/05/2009 Giulio Rossetti Unipi Giulio.Rossetti@gmail.com 802.11 Security Standard: WEP Wired Equivalent Privacy The packets are encrypted, before sent, with a Secret Key
