Windows 7 Forensic Analysis. H. Carvey Chief Forensics Scientist, ASI
|
|
|
- Meryl Bradford
- 9 years ago
- Views:
Transcription
1 Windows 7 Forensic Analysis H. Carvey Chief Forensics Scientist, ASI
2 Introduction Who am I? Chief Forensics Scientist at ASI. Forensic Nerd. Published Author. Why are we here? To talk about Windows 7 Forensic Analysis 2
3 What s in the next version? Every time MS has released a new version of Windows, there has been anxiety and trepidation within the DFIR community. If we take a deep breath, relax, and follow our processes, we find each new version of Windows brings with it even more potential sources of evidence, many of which persist even in the face of counter-forensics techniques being used. 3
4 Core Analysis Concepts View the system as a system of interconnected components Something that occurs on one component affects others User launches application, UserAssist entry is created/modified, Prefetch file is created/modified, LNK/Jump List file created/modified, etc. Locard s Exchange Principle Transfer of digital material when two systems interact, or when user interacts with system The absence of an artifact where you would expect to find one is itself an artifact. Least Frequency of Occurrence (LFO) 4
5 Analysis What is analysis? What is it today, and where do we need to go? Analysis = Data extraction/collection/correlation + interpretation Start with goals and an acquired image Snapshot of a system, frozen in time Identification and correlation of data sources in order to develop context pursuant to our analysis goals We re mostly familiar with Windows XP, but Windows 7 is now hitting analysts desks 5
6 System Similarities: XP & Win7 MFT little difference Updating file last access time disabled by default starting with Vista Registry same binary structure Prefetch files (different offsets, similar format, same data) Many apps still maintain (text) logs OLE structured storage, file-system-within-a-file Office 97 (later versions use different format) Jump Lists, Sticky Notes, IE session restore files Hibernation files 6
7 System Differences: XP vs. Win7 Directory structure C:\Users vs. C:\Documents and Settings XP Restore Points => VSCs/ Previous Versions (Vista+) MRUs moved from Registry to Jump Lists CustomDestinations: Header + appended LNK streams AutomaticDestinations: LNK streams managed via OLE file format (+ DestList stream) Windows Event Logs (where do we begin??) The usual: Application, System, Security LOTS more! Win7 includes more artifacts More tracking of user/system activity 7
8 Virtualization Does XP go away? I say, nay, nay! WinXP can be installed on some versions of Windows 7 and run in a virtual environment called XPMode. VirtualPC can be installed for free. Comedian John Pinette 8
9 Registry Not only is additional information recorded in Win7 Registry regarding USB devices connected to the system, and WAPs the system was connected to, but we also have sources of historical data: RegIdleBackup (every 10 days; doesn t include NTUSER.DAT) VSCs NTUSER.DAT from image Thu Jan 21 03:10: Z UEME_RUNPATH:C:\Program Files\Skype\Phone\Skype.exe (14) NTUSER.DAT from VSC Fri Jan 8 04:13: Z UEME_RUNPATH:C:\Program Files\Skype\Phone\Skype.exe (8) 9
10 Registry Wi-Fi Geo-location Windows records the MAC address of WAPs to which the system has connected. Extract this information, and perform lookups to get lat./long., for plotting on Google Maps/Earth. DATE LAST CONNECTED: MON FEB 18 11:02: DATE CREATED: SAT FEB 16 12:02: DEFAULT GATEWAY MAC: 00-0F ED 10
11 Registry Wi-Fi Geo-location 11
12 Artifacts More sources of time stamped data Usual suspects New files and/or formats that contain metadata (i.e., Jump Lists, etc.) New Registry keys/values New locations where data is stored, new structures to hold that data Pertinent to timeline analysis More focus has been put toward understanding available data sources Ex: Finding MAC addresses in the Registry Finding additional time stamped data (again timelines) Finding additional sources of data that relate to various categories of activity (i.e., file accesses, program execution, etc.) 12
13 Artifacts Windows tracks a great deal of user and system activity. Many artifacts: are created automatically by the operating system persist beyond application removal/file deletion previous versions of those artifacts can be found in VSCs 13
14 Answering Questions There is more data available to answer questions: Which application used/accessed this file? Registry analysis (RecentDocs), Jump Lists, etc. File Accesses Jump Lists, LNK files, Registry MRUs, log files, etc. USB device analysis Registry (Software, System, NTUSER.DAT hives) + setupapi.dev.log + Windows Event Log (System) Who put those files there? Trojan Defense -> Registry + Jump Lists + Prefetch + etc. Program Execution Did the user burn a CD/DVD? Registry + Prefetch +? 14
15 Summary What to look forward to Look at Windows as a system Intentional activity in one part of the system can create unintentional artifacts in another part More data sources More metadata embedded in some file formats What do we need? More research More community involvement Share your questions someone may have an answer 15
16 What does the future hold? Windows 8 New file system (ReFS) New Registry stuff TypedURLsTime key IE: index.dat -> ESE database Other browsers already use databases (SQLite) Access via Windows Live Account (also used to access MS s cloud ) Already some great work done by Kenneth Johnson and Amanda Thomson 16
17 Questions? H. Carvey 17
Operating Systems Forensics
 Operating Systems Forensics Section II. Basic Forensic Techniques and Tools CSF: Forensics Cyber-Security MSIDC, Spring 2015 Nuno Santos Summary! Windows boot sequence! Relevant Windows data structures!
Operating Systems Forensics Section II. Basic Forensic Techniques and Tools CSF: Forensics Cyber-Security MSIDC, Spring 2015 Nuno Santos Summary! Windows boot sequence! Relevant Windows data structures!
Registry Analysis SANS Forensic Summit 2009
 Registry Analysis SANS Forensic Summit 2009 Allow myself to introduce myself 2 What is Registry Analysis?? More than just opening Registry files in a viewer and finding values Registry analysis involves:
Registry Analysis SANS Forensic Summit 2009 Allow myself to introduce myself 2 What is Registry Analysis?? More than just opening Registry files in a viewer and finding values Registry analysis involves:
1! Registry. Windows System Artifacts. Understanding the Windows Registry. Organization of the Windows Registry. Windows Registry Viewer
 1! Registry Understanding the Windows Registry! A database that stores hardware and software configuration information, network connections, user preferences, and setup information Windows System Artifacts
1! Registry Understanding the Windows Registry! A database that stores hardware and software configuration information, network connections, user preferences, and setup information Windows System Artifacts
GOOGLE DESKTOP FORENSICS WIN!
 The Quarterly Magazine for Digital Forensics Practitioners WIN! A STEGALYZER USB FROM SARC ISSUE 15 MAY 2013 INSIDE / Cryptographic Key Recovery / Tunnelling Out: Data Extraction / Fuzzing Risks in Software
The Quarterly Magazine for Digital Forensics Practitioners WIN! A STEGALYZER USB FROM SARC ISSUE 15 MAY 2013 INSIDE / Cryptographic Key Recovery / Tunnelling Out: Data Extraction / Fuzzing Risks in Software
Windows File Analyser Guidance Allan S Hay
 Windows File Analyser Guidance Allan S Hay ** The following information is a guide to understanding the Prefetch Folder and Windows Shortcut File Format ( LNK) and all work undertaken in my research, should
Windows File Analyser Guidance Allan S Hay ** The following information is a guide to understanding the Prefetch Folder and Windows Shortcut File Format ( LNK) and all work undertaken in my research, should
Detection of Data Hiding in Computer Forensics. About Your Presenter
 Detection of Data Hiding in Computer Forensics NEbraskaCERT Conference August 22nd, 2008 James E. Martin CISSP, JD About Your Presenter 2008-Present: Security Engineer, West Corporation 2004-2008: Senior
Detection of Data Hiding in Computer Forensics NEbraskaCERT Conference August 22nd, 2008 James E. Martin CISSP, JD About Your Presenter 2008-Present: Security Engineer, West Corporation 2004-2008: Senior
A Day in the Life of a Cyber Tool Developer
 A Day in the Life of a Cyber Tool Developer by Jonathan Tomczak [email protected] Jonathan Tomczak ( Front Man ) Software Engineer w/ over 7 years experience working in software and web development Dave
A Day in the Life of a Cyber Tool Developer by Jonathan Tomczak [email protected] Jonathan Tomczak ( Front Man ) Software Engineer w/ over 7 years experience working in software and web development Dave
EnCase 7 - Basic + Intermediate Topics
 EnCase 7 - Basic + Intermediate Topics Course Objectives This 4 day class is designed to familiarize the student with the many artifacts left behind on Windows based media and how to conduct a forensic
EnCase 7 - Basic + Intermediate Topics Course Objectives This 4 day class is designed to familiarize the student with the many artifacts left behind on Windows based media and how to conduct a forensic
Determining VHD s in Windows 7 Dustin Hurlbut
 Introduction Windows 7 has the ability to create and mount virtual machines based upon launching a single file. The Virtual Hard Disk (VHD) format permits creation of virtual drives that can be used for
Introduction Windows 7 has the ability to create and mount virtual machines based upon launching a single file. The Virtual Hard Disk (VHD) format permits creation of virtual drives that can be used for
TZWorks Windows Event Log Viewer (evtx_view) Users Guide
 TZWorks Windows Event Log Viewer (evtx_view) Users Guide Abstract evtx_view is a standalone, GUI tool used to extract and parse Event Logs and display their internals. The tool allows one to export all
TZWorks Windows Event Log Viewer (evtx_view) Users Guide Abstract evtx_view is a standalone, GUI tool used to extract and parse Event Logs and display their internals. The tool allows one to export all
CLOUD STORAGE FORENSICS MATTIA EPIFANI SANS EUROPEAN DIGITAL FORENSICS SUMMIT PRAGUE, 7 OCTOBER 2013
 CLOUD STORAGE FORENSICS MATTIA EPIFANI SANS EUROPEAN DIGITAL FORENSICS SUMMIT PRAGUE, 7 OCTOBER 2013 SUMMARY Cloud Storage services Testing environment and methodology Forensics artifacts left by Cloud
CLOUD STORAGE FORENSICS MATTIA EPIFANI SANS EUROPEAN DIGITAL FORENSICS SUMMIT PRAGUE, 7 OCTOBER 2013 SUMMARY Cloud Storage services Testing environment and methodology Forensics artifacts left by Cloud
Digital Forensics with Open Source Tools
 Digital Forensics with Open Source Tools Cory Altheide Harlan Carvey Technical Editor Ray Davidson AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY TOKYO
Digital Forensics with Open Source Tools Cory Altheide Harlan Carvey Technical Editor Ray Davidson AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY TOKYO
Forensically Determining the Presence and Use of Virtual Machines in Windows 7
 Forensically Determining the Presence and Use of Virtual Machines in Windows 7 Introduction Dustin Hurlbut Windows 7 has the ability to create and mount virtual machines based upon launching a single file.
Forensically Determining the Presence and Use of Virtual Machines in Windows 7 Introduction Dustin Hurlbut Windows 7 has the ability to create and mount virtual machines based upon launching a single file.
Windows 10 Forensics. 175 Lakeside Ave, Room 300A Phone: (802)865-5744 Fax: (802)865-6446 http://www.lcdi.champlain.edu
 Windows 10 Forensics 175 Lakeside Ave, Room 300A Phone: (802)865-5744 Fax: (802)865-6446 http://www.lcdi.champlain.edu 4/22/2015 Disclaimer: This document contains information based on research that has
Windows 10 Forensics 175 Lakeside Ave, Room 300A Phone: (802)865-5744 Fax: (802)865-6446 http://www.lcdi.champlain.edu 4/22/2015 Disclaimer: This document contains information based on research that has
CSN08101 Digital Forensics Lecture 10: Windows Registry. Module Leader: Dr Gordon Russell Lecturers: Robert Ludwiniak
 CSN08101 Digital Forensics Lecture 10: Windows Registry Module Leader: Dr Gordon Russell Lecturers: Robert Ludwiniak Lecture Objectives Windows Registry Structure Properties Examples Timeline Analysis
CSN08101 Digital Forensics Lecture 10: Windows Registry Module Leader: Dr Gordon Russell Lecturers: Robert Ludwiniak Lecture Objectives Windows Registry Structure Properties Examples Timeline Analysis
An Overview of the Jumplist Configuration File in Windows 7
 An Overview of the Jumplist Configuration File in Windows 7 Harjinder Singh Lalli University of Warwick, International Digital Laboratory (WMG), University of Warwick, Coventry, CV4 7AL, UK; [email protected]
An Overview of the Jumplist Configuration File in Windows 7 Harjinder Singh Lalli University of Warwick, International Digital Laboratory (WMG), University of Warwick, Coventry, CV4 7AL, UK; [email protected]
Advanced Registry Forensics with Registry Decoder. Dr. Vico Marziale Sleuth Kit and Open Source Digital Forensics Conference 2012 10/03/2012
 Advanced Registry Forensics with Registry Decoder Dr. Vico Marziale Sleuth Kit and Open Source Digital Forensics Conference 2012 10/03/2012 Who am I? Senior Security Researcher @ DFS Published Researcher
Advanced Registry Forensics with Registry Decoder Dr. Vico Marziale Sleuth Kit and Open Source Digital Forensics Conference 2012 10/03/2012 Who am I? Senior Security Researcher @ DFS Published Researcher
Automated Identification and Reconstruction of YouTube Video Access
 Automated Identification and Reconstruction of YouTube Video Access Jonathan Patterson 1, Christopher Hargreaves 2 Centre for Forensic Computing, Cranfield University, Shrivenham SN6 8LA 1 [email protected],
Automated Identification and Reconstruction of YouTube Video Access Jonathan Patterson 1, Christopher Hargreaves 2 Centre for Forensic Computing, Cranfield University, Shrivenham SN6 8LA 1 [email protected],
Digital Forensic Analyses of Web Browser Records
 Digital Forensic Analyses of Web Browser Records Erhan Akbal1*, Fatma Güneş1, Ayhan Akbal2 1 Department of Digital Forensics Engineering, Fırat University Technology Faculty, 23119, Elazig, Turkey. Department
Digital Forensic Analyses of Web Browser Records Erhan Akbal1*, Fatma Güneş1, Ayhan Akbal2 1 Department of Digital Forensics Engineering, Fırat University Technology Faculty, 23119, Elazig, Turkey. Department
Just EnCase. Presented By Larry Russell CalCPA State Technology Committee May 18, 2012
 Just EnCase Presented By Larry Russell CalCPA State Technology Committee May 18, 2012 What is e-discovery Electronically Stored Information (ESI) Discover or Monitor for Fraudulent Activity Tools used
Just EnCase Presented By Larry Russell CalCPA State Technology Committee May 18, 2012 What is e-discovery Electronically Stored Information (ESI) Discover or Monitor for Fraudulent Activity Tools used
TeamViewer Forensics
 TeamViewer Forensics Written by: Colby Lahaie Researched by: Colby Lahaie & David Leberfinger The Senator Patrick Leahy Center for Digital Investigation Champlain College Date Jan 29, 2013 Disclaimer:
TeamViewer Forensics Written by: Colby Lahaie Researched by: Colby Lahaie & David Leberfinger The Senator Patrick Leahy Center for Digital Investigation Champlain College Date Jan 29, 2013 Disclaimer:
Cloud Hosted Data in Digital Forensics
 Cloud Hosted Data in Digital Forensics Session overview What is cloud storage? Do we need to worry about it? Collection considerations Forensic artefacts from: Google Drive Office 365/OneDrive Forensic
Cloud Hosted Data in Digital Forensics Session overview What is cloud storage? Do we need to worry about it? Collection considerations Forensic artefacts from: Google Drive Office 365/OneDrive Forensic
The Meaning. Linkfiles In Forensic Examinations
 The Meaning of Linkfiles In Forensic Examinations A look at the practical value to forensic examinations of dates and times, and object identifiers in Windows shortcut files. Harry Parsonage September
The Meaning of Linkfiles In Forensic Examinations A look at the practical value to forensic examinations of dates and times, and object identifiers in Windows shortcut files. Harry Parsonage September
Forensic Analysis of Internet Explorer Activity Files
 Forensic Analysis of Internet Explorer Activity Files by Keith J. Jones [email protected] 3/19/03 Table of Contents 1. Introduction 4 2. The Index.dat File Header 6 3. The HASH Table 10 4. The
Forensic Analysis of Internet Explorer Activity Files by Keith J. Jones [email protected] 3/19/03 Table of Contents 1. Introduction 4 2. The Index.dat File Header 6 3. The HASH Table 10 4. The
Automating the Computer Forensic Triage Process With MantaRay
 Automating the Computer Forensic Triage Process With MantaRay Senior Computer Forensic Analysts Doug Koster & Kevin Murphy Worlds best Summer Intern Chapin Bryce GMU RCFG Conference August 2013 1 MantaRay
Automating the Computer Forensic Triage Process With MantaRay Senior Computer Forensic Analysts Doug Koster & Kevin Murphy Worlds best Summer Intern Chapin Bryce GMU RCFG Conference August 2013 1 MantaRay
Windows 7: Current Events in the World of Windows Forensics
 Windows 7: Current Events in the World of Windows Forensics Troy Larson Senior Forensic Program Manager Network Security, Microsoft Corp. Where Are We Now? Vista & Windows 2008 BitLocker. Format-Wipes
Windows 7: Current Events in the World of Windows Forensics Troy Larson Senior Forensic Program Manager Network Security, Microsoft Corp. Where Are We Now? Vista & Windows 2008 BitLocker. Format-Wipes
owncloud Configuration and Usage Guide
 owncloud Configuration and Usage Guide This guide will assist you with configuring and using YSUʼs Cloud Data storage solution (owncloud). The setup instructions will include how to navigate the web interface,
owncloud Configuration and Usage Guide This guide will assist you with configuring and using YSUʼs Cloud Data storage solution (owncloud). The setup instructions will include how to navigate the web interface,
User Manual. Onsight Management Suite Version 5.1. Another Innovation by Librestream
 User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
Microsoft Vista: Serious Challenges for Digital Investigations
 Proceedings of Student-Faculty Research Day, CSIS, Pace University, May 2 nd, 2008 Microsoft Vista: Serious Challenges for Digital Investigations Darren R. Hayes and Shareq Qureshi Seidenberg School of
Proceedings of Student-Faculty Research Day, CSIS, Pace University, May 2 nd, 2008 Microsoft Vista: Serious Challenges for Digital Investigations Darren R. Hayes and Shareq Qureshi Seidenberg School of
GUIDE A GUIDE TO FINDING IMPORTANT BUSINESS APPLICATIONS & OS ARTIFACTS FOR YOUR DIGITAL FORENSICS INVESTIGATIONS
 GUIDE A GUIDE TO FINDING IMPORTANT BUSINESS APPLICATIONS & OS ARTIFACTS FOR YOUR DIGITAL FORENSICS INVESTIGATIONS TABLE OF CONTENTS A GUIDE TO FINDING IMPORTANT BUSINESS APPLICATION & OS ARTIFACTS FOR
GUIDE A GUIDE TO FINDING IMPORTANT BUSINESS APPLICATIONS & OS ARTIFACTS FOR YOUR DIGITAL FORENSICS INVESTIGATIONS TABLE OF CONTENTS A GUIDE TO FINDING IMPORTANT BUSINESS APPLICATION & OS ARTIFACTS FOR
Seagate Dashboard User Guide
 Seagate Dashboard User Guide Seagate Dashboard User Guide 2013 Seagate Technology LLC. All rights reserved. Seagate, Seagate Technology, the Wave logo, and FreeAgent are trademarks or registered trademarks
Seagate Dashboard User Guide Seagate Dashboard User Guide 2013 Seagate Technology LLC. All rights reserved. Seagate, Seagate Technology, the Wave logo, and FreeAgent are trademarks or registered trademarks
SMART Active Directory Migrator. Desired End State and Project Prerequisites
 SMART Active Directory Migrator Desired End State and Project Prerequisites uthor Title Table of Contents Introduction... 3 Purpose... 3 About SMART Active Directory Migrator... 3 Components of SMART AD
SMART Active Directory Migrator Desired End State and Project Prerequisites uthor Title Table of Contents Introduction... 3 Purpose... 3 About SMART Active Directory Migrator... 3 Components of SMART AD
RECOVERING FROM SHAMOON
 Executive Summary Fidelis Threat Advisory #1007 RECOVERING FROM SHAMOON November 1, 2012 Document Status: FINAL Last Revised: 2012-11-01 The Shamoon malware has received considerable coverage in the past
Executive Summary Fidelis Threat Advisory #1007 RECOVERING FROM SHAMOON November 1, 2012 Document Status: FINAL Last Revised: 2012-11-01 The Shamoon malware has received considerable coverage in the past
Redline Users Guide. Version 1.12
 Redline Users Guide Version 1.12 Contents Contents 1 About Redline 5 Timeline 5 Malware Risk Index (MRI) Score 5 Indicators of Compromise (IOCs) 5 Whitelists 5 Installation 6 System Requirements 6 Install
Redline Users Guide Version 1.12 Contents Contents 1 About Redline 5 Timeline 5 Malware Risk Index (MRI) Score 5 Indicators of Compromise (IOCs) 5 Whitelists 5 Installation 6 System Requirements 6 Install
Simple Computer Backup
 Title: Simple Computer Backup (Win 7 and 8) Author: Nancy DeMarte Date Created: 11/10/13 Date(s) Revised: 1/20/15 Simple Computer Backup This tutorial includes these methods of backing up your PC files:
Title: Simple Computer Backup (Win 7 and 8) Author: Nancy DeMarte Date Created: 11/10/13 Date(s) Revised: 1/20/15 Simple Computer Backup This tutorial includes these methods of backing up your PC files:
Creating a generic user-password application profile
 Chapter 4 Creating a generic user-password application profile Overview If you d like to add applications that aren t in our Samsung KNOX EMM App Catalog, you can create custom application profiles using
Chapter 4 Creating a generic user-password application profile Overview If you d like to add applications that aren t in our Samsung KNOX EMM App Catalog, you can create custom application profiles using
Backup and Restore of CONFIGURATION Object on Windows 2008
 Backup and Restore of CONFIGURATION Object on Windows 2008 Technical Whitepaper Contents Introduction... 3 CONFIGURATION Backup... 3 Windows configuration objects... 3 Active Directory... 4 DFS... 4 DHCP
Backup and Restore of CONFIGURATION Object on Windows 2008 Technical Whitepaper Contents Introduction... 3 CONFIGURATION Backup... 3 Windows configuration objects... 3 Active Directory... 4 DFS... 4 DHCP
Computer Forensic Capabilities
 Computer Forensic Capabilities Agenda What is computer forensics? Where to find computer evidence Forensic imaging Forensic analysis What is Computer Forensics? The preservation, identification, extraction,
Computer Forensic Capabilities Agenda What is computer forensics? Where to find computer evidence Forensic imaging Forensic analysis What is Computer Forensics? The preservation, identification, extraction,
Understanding NTFS Hard Links, Junctions and Symbolic Links
 Understanding NTFS Hard Links, Junctions and Symbolic Links Author: Conrad Chung, 2BrightSparks Introduction Microsoft has implemented linking tools in its NTFS operating file systems since Windows NT
Understanding NTFS Hard Links, Junctions and Symbolic Links Author: Conrad Chung, 2BrightSparks Introduction Microsoft has implemented linking tools in its NTFS operating file systems since Windows NT
2013 Open Source Digital Forensics Conference
 4 TH ANNUAL OSDF 2013 Open Source Digital Forensics Conference Doing More with Less Willi Ballenthin Consultant MANDIANT Introduc4on: Willi Ballenthin Professionally Incident response Malware analysis
4 TH ANNUAL OSDF 2013 Open Source Digital Forensics Conference Doing More with Less Willi Ballenthin Consultant MANDIANT Introduc4on: Willi Ballenthin Professionally Incident response Malware analysis
Cybercrime myths, challenges and how to protect our business. Vladimir Kantchev Managing Partner Service Centrix
 Cybercrime myths, challenges and how to protect our business Vladimir Kantchev Managing Partner Service Centrix Agenda Cybercrime today Sources and destinations of the attacks Breach techniques How to
Cybercrime myths, challenges and how to protect our business Vladimir Kantchev Managing Partner Service Centrix Agenda Cybercrime today Sources and destinations of the attacks Breach techniques How to
LIBRARY MEMBER USER GUIDE
 LIBRARY MEMBER USER GUIDE CONTENTS PAGE Part 1) How to create a new account... 2 Part 2) How to checkout a magazine issue... 4 Part 3) How to download and use Zinio Reader 4... 8 a) For your PC... 8 b)
LIBRARY MEMBER USER GUIDE CONTENTS PAGE Part 1) How to create a new account... 2 Part 2) How to checkout a magazine issue... 4 Part 3) How to download and use Zinio Reader 4... 8 a) For your PC... 8 b)
Technology Services Group Procedures. IH Anywhere guide. 0 P a g e
 VDI Pilot Technology Services Group Procedures IH Anywhere guide 0 P a g e Installation Disable Apple Security Table of Contents IH Anywhere for Apple OSX (MAC)... 2 1. Installation... 2 Disable Apple
VDI Pilot Technology Services Group Procedures IH Anywhere guide 0 P a g e Installation Disable Apple Security Table of Contents IH Anywhere for Apple OSX (MAC)... 2 1. Installation... 2 Disable Apple
User Guide Microsoft Exchange Remote Test Instructions
 User Guide Microsoft Exchange Remote Test Instructions University of Louisville Information Technology 1.1 Who Should Use It This guide is intended for University of Louisville Faculty and Staff participating
User Guide Microsoft Exchange Remote Test Instructions University of Louisville Information Technology 1.1 Who Should Use It This guide is intended for University of Louisville Faculty and Staff participating
Cloud based Storage Drive Forensics
 Cloud based Storage Drive Forensics Prashant Bhatt 1, Mr. Naresh Kumar Gardas 2, Ms. Shweta Chawla 3, Moin Khorajiya 4 1 PG Student, Network Security, GTU PG School, Ahmedabad, Gujarat, India 2 Course-Coordinator,
Cloud based Storage Drive Forensics Prashant Bhatt 1, Mr. Naresh Kumar Gardas 2, Ms. Shweta Chawla 3, Moin Khorajiya 4 1 PG Student, Network Security, GTU PG School, Ahmedabad, Gujarat, India 2 Course-Coordinator,
Computer Forensics Principles and Practices
 Computer Forensics Principles and Practices by Volonino, Anzaldua, and Godwin Chapter 7: Investigating Windows, Linux, and Graphics Files Objectives Conduct efficient and effective investigations of Windows
Computer Forensics Principles and Practices by Volonino, Anzaldua, and Godwin Chapter 7: Investigating Windows, Linux, and Graphics Files Objectives Conduct efficient and effective investigations of Windows
AN INVESTIGATION INTO THE METHODS USED FOR TRAFFICKING OF CHILD ABUSE MATERIAL
 AN INVESTIGATION INTO THE METHODS USED FOR TRAFFICKING OF CHILD ABUSE MATERIAL Dr. Allan Charles Watt, PhD, CFCE, CFE Macquarie University, Sydney, Australia Session ID: CLE W02 Session Classification:
AN INVESTIGATION INTO THE METHODS USED FOR TRAFFICKING OF CHILD ABUSE MATERIAL Dr. Allan Charles Watt, PhD, CFCE, CFE Macquarie University, Sydney, Australia Session ID: CLE W02 Session Classification:
Redline User Guide. Release 1.14
 Redline User Guide Release 1.14 FireEye and the FireEye logo are registered trademarks of FireEye, Inc. in the United States and other countries. All other trademarks are the property of their respective
Redline User Guide Release 1.14 FireEye and the FireEye logo are registered trademarks of FireEye, Inc. in the United States and other countries. All other trademarks are the property of their respective
APPLICATION VIRTUALIZATION TECHNOLOGIES WHITEPAPER
 APPLICATION VIRTUALIZATION TECHNOLOGIES WHITEPAPER Oct 2013 INTRODUCTION TWO TECHNOLOGY CATEGORIES Application virtualization technologies can be divided into two main categories: those that require an
APPLICATION VIRTUALIZATION TECHNOLOGIES WHITEPAPER Oct 2013 INTRODUCTION TWO TECHNOLOGY CATEGORIES Application virtualization technologies can be divided into two main categories: those that require an
Frequently Asked Questions
 Frequently Asked Questions Share Drive Frequently Asked Questions Table of Contents How do I change my password?... How do I reset my password if I forgot it?... How do I share files/folders with Groups
Frequently Asked Questions Share Drive Frequently Asked Questions Table of Contents How do I change my password?... How do I reset my password if I forgot it?... How do I share files/folders with Groups
Web Browser Session Restore Forensics A valuable record of a user s internet activity for computer forensic examinations
 A valuable record of a user s internet activity for computer forensic examinations Each session of activity in a Mozilla browser is recorded by the browser so that in the event of the browser crashing
A valuable record of a user s internet activity for computer forensic examinations Each session of activity in a Mozilla browser is recorded by the browser so that in the event of the browser crashing
Blackberry Forensics. Shafik G. Punja Cindy Murphy. SANS DFIR Summit 2014 Austin TX. June-9-14 Copyright QuByte Logic Ltd
 1 Blackberry Forensics SANS DFIR Summit 2014 Austin TX Shafik G. Punja Cindy Murphy 2 SPEAKER BACKGROUND - Shafik G. Punja - Active duty LE, performing digital forensics since Nov 2003 - Instructor for
1 Blackberry Forensics SANS DFIR Summit 2014 Austin TX Shafik G. Punja Cindy Murphy 2 SPEAKER BACKGROUND - Shafik G. Punja - Active duty LE, performing digital forensics since Nov 2003 - Instructor for
s@lm@n Microsoft Exam MB2-702 Microsoft Dynamics CRM 2013 Deployment Version: 6.1 [ Total Questions: 90 ]
![s@lm@n Microsoft Exam MB2-702 Microsoft Dynamics CRM 2013 Deployment Version: 6.1 [ Total Questions: 90 ] s@lm@n Microsoft Exam MB2-702 Microsoft Dynamics CRM 2013 Deployment Version: 6.1 [ Total Questions: 90 ]](/thumbs/29/13404345.jpg) s@lm@n Microsoft Exam MB2-702 Microsoft Dynamics CRM 2013 Deployment Version: 6.1 [ Total Questions: 90 ] Question No : 1 You install Microsoft Dynamics CRM on-premises. The Microsoft Dynamics CRM environment
s@lm@n Microsoft Exam MB2-702 Microsoft Dynamics CRM 2013 Deployment Version: 6.1 [ Total Questions: 90 ] Question No : 1 You install Microsoft Dynamics CRM on-premises. The Microsoft Dynamics CRM environment
10 Ways to Not Get Caught Hacking On Your Mac
 10 Ways to Not Get Caught Hacking On Your Mac Three18 is a Comprehensive Technology Solutions Provider Apple Certified Partner Microsoft Gold Partner Symantec Security Solutions Partner Novell and RedHat
10 Ways to Not Get Caught Hacking On Your Mac Three18 is a Comprehensive Technology Solutions Provider Apple Certified Partner Microsoft Gold Partner Symantec Security Solutions Partner Novell and RedHat
LIBRARY MEMBER USER GUIDE
 LIBRARY MEMBER USER GUIDE CONTENTS PAGE Part 1) How to create a new account... 2 Part 2) How to checkout a magazine issue... 4 Part 3) How to download Zinio Reader 4... 10 a) For your PC... 10 b) For your
LIBRARY MEMBER USER GUIDE CONTENTS PAGE Part 1) How to create a new account... 2 Part 2) How to checkout a magazine issue... 4 Part 3) How to download Zinio Reader 4... 10 a) For your PC... 10 b) For your
ANALYSING SERVER LOG FILE USING WEB LOG EXPERT IN WEB DATA MINING
 International Journal of Science, Environment and Technology, Vol. 2, No 5, 2013, 1008 1016 ISSN 2278-3687 (O) ANALYSING SERVER LOG FILE USING WEB LOG EXPERT IN WEB DATA MINING 1 V. Jayakumar and 2 Dr.
International Journal of Science, Environment and Technology, Vol. 2, No 5, 2013, 1008 1016 ISSN 2278-3687 (O) ANALYSING SERVER LOG FILE USING WEB LOG EXPERT IN WEB DATA MINING 1 V. Jayakumar and 2 Dr.
IONU PRO Product Overview
 Quick View ü You MUST be logged in to access any information inside the IONU system. If you aren t logged in, you will not see the folders and the data and files cannot be accessed and decrypted. ü All
Quick View ü You MUST be logged in to access any information inside the IONU system. If you aren t logged in, you will not see the folders and the data and files cannot be accessed and decrypted. ü All
Beyond files forensic OWADE cloud based forensic
 Beyond files forensic OWADE cloud based forensic Elie Bursztein Stanford University Ivan Fontarensky Cassidian Matthieu Martin Stanford University Jean Michel Picod Cassidian 1 The world is moving to the
Beyond files forensic OWADE cloud based forensic Elie Bursztein Stanford University Ivan Fontarensky Cassidian Matthieu Martin Stanford University Jean Michel Picod Cassidian 1 The world is moving to the
Uncovering the Covered Tracks: Finding What s Left Behind JAD SALIBA FOUNDER & CTO
 Uncovering the Covered Tracks: Finding What s Left Behind JAD SALIBA FOUNDER & CTO Background Teenage geek - IT/Software industry Police officer for 7 years Worked in Tech Crime Unit Started JADsoftware
Uncovering the Covered Tracks: Finding What s Left Behind JAD SALIBA FOUNDER & CTO Background Teenage geek - IT/Software industry Police officer for 7 years Worked in Tech Crime Unit Started JADsoftware
Getting Started Guide: Getting the most out of your Windows Intune cloud
 Getting Started Guide: Getting the most out of your Windows Intune cloud service Contents Overview... 3 Which Configuration is Right for You?... 3 To Sign up or Sign in?... 4 Getting Started with the Windows
Getting Started Guide: Getting the most out of your Windows Intune cloud service Contents Overview... 3 Which Configuration is Right for You?... 3 To Sign up or Sign in?... 4 Getting Started with the Windows
Detecting data loss from cloud sync applications
 Detecting data loss from cloud sync applications Jake Williams CSRgroup Consultants @MalwareJake [email protected] Cloud Synchronization Data Loss - 2013 Jake Williams 1 BLUF Just to level set expectations.
Detecting data loss from cloud sync applications Jake Williams CSRgroup Consultants @MalwareJake [email protected] Cloud Synchronization Data Loss - 2013 Jake Williams 1 BLUF Just to level set expectations.
New Technologies File System (NTFS) Priscilla Oppenheimer. Copyright 2008 Priscilla Oppenheimer
 New Technologies File System (NTFS) Priscilla Oppenheimer NTFS Default file system for Windows NT, 2000, XP, and Windows Server 2003 No published spec from Microsoft that describes the on-disk layout Good
New Technologies File System (NTFS) Priscilla Oppenheimer NTFS Default file system for Windows NT, 2000, XP, and Windows Server 2003 No published spec from Microsoft that describes the on-disk layout Good
How To Use The Tzworks Eventlog Parser (Evtwalk) On A Pc Or Mac Or Mac (Windows) With A Microsoft Powerbook Or Ipad (Windows Xp) With An Ipad Or Ipa (Windows 2
 TZWorks Event Log Parser (evtwalk) Users Guide Abstract evtwalk is a standalone, command-line tool used to extract records from Event logs from. evtwalk can be easily incorporated into any analysts processing
TZWorks Event Log Parser (evtwalk) Users Guide Abstract evtwalk is a standalone, command-line tool used to extract records from Event logs from. evtwalk can be easily incorporated into any analysts processing
How to make a VPN connection to our servers from Windows 7
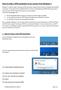 How to make a VPN connection to our servers from Windows 7 Windows 7 is able to make a new type of VPN connection called a Secure Socket Tunnelling Protocol (SSTP) connection. This works just like a traditional
How to make a VPN connection to our servers from Windows 7 Windows 7 is able to make a new type of VPN connection called a Secure Socket Tunnelling Protocol (SSTP) connection. This works just like a traditional
ACQUISITION AND ANALYSIS OF IOS DEVICES MATTIA EPIFANI SANS FORENSICS PRAGUE PRAGUE, 10 OCTOBER 2013
 ACQUISITION AND ANALYSIS OF IOS DEVICES MATTIA EPIFANI SANS FORENSICS PRAGUE PRAGUE, 10 OCTOBER 2013 FORENSIC ACQUISITION.BEFORE STARTING When we are dealing with the forensics acquisition of an ios device
ACQUISITION AND ANALYSIS OF IOS DEVICES MATTIA EPIFANI SANS FORENSICS PRAGUE PRAGUE, 10 OCTOBER 2013 FORENSIC ACQUISITION.BEFORE STARTING When we are dealing with the forensics acquisition of an ios device
FORENSIC ANALYSIS Aleš Padrta
 FORENSIC ANALYSIS Aleš Padrta CESNET, CESNET-CERTS, FLAB CESNET Czech NREN operator CESNET-CERTS 2004 Established 2008 Accredited CSIRT FLAB Forensic LABoratory Established 6/2011 Support team for CESNET-CERTS
FORENSIC ANALYSIS Aleš Padrta CESNET, CESNET-CERTS, FLAB CESNET Czech NREN operator CESNET-CERTS 2004 Established 2008 Accredited CSIRT FLAB Forensic LABoratory Established 6/2011 Support team for CESNET-CERTS
Summer 2013 Cloud Initiative. Release Bulletin
 Summer 2013 Cloud Initiative In this bulletin... July 2013 Summer 2013 Cloud Initiative 1 Getting started with the new Cloud... 2 Cloud Enhancements 3 How To Save Files 7 How to Set Up ipad Access 9 How
Summer 2013 Cloud Initiative In this bulletin... July 2013 Summer 2013 Cloud Initiative 1 Getting started with the new Cloud... 2 Cloud Enhancements 3 How To Save Files 7 How to Set Up ipad Access 9 How
DIGITAL FORENSIC INVESTIGATION OF CLOUD STORAGE SERVICES
 DIGITAL FORENSIC INVESTIGATION OF CLOUD STORAGE SERVICES Hyunji Chung, Jungheum Park, Sangjin Lee, Cheulhoon Kang Presented by: Abdiwahid Abubakar Ahmed, ID #201205820 2 OUTLINE 1. Introduction 2. Cloud
DIGITAL FORENSIC INVESTIGATION OF CLOUD STORAGE SERVICES Hyunji Chung, Jungheum Park, Sangjin Lee, Cheulhoon Kang Presented by: Abdiwahid Abubakar Ahmed, ID #201205820 2 OUTLINE 1. Introduction 2. Cloud
IBM WebSphere Application Server V8.5 lab Basic Liberty profile administration using the job manager
 IBM WebSphere Application Server V8.5 lab Basic Liberty profile administration using the job manager Scenario You are a system administrator responsible for managing web application server installations.
IBM WebSphere Application Server V8.5 lab Basic Liberty profile administration using the job manager Scenario You are a system administrator responsible for managing web application server installations.
Zmanda Cloud Backup Frequently Asked Questions
 Zmanda Cloud Backup Frequently Asked Questions Release 4.1 Zmanda, Inc Table of Contents Terminology... 4 What is Zmanda Cloud Backup?... 4 What is a backup set?... 4 What is amandabackup user?... 4 What
Zmanda Cloud Backup Frequently Asked Questions Release 4.1 Zmanda, Inc Table of Contents Terminology... 4 What is Zmanda Cloud Backup?... 4 What is a backup set?... 4 What is amandabackup user?... 4 What
RingCentral for Desk. Admin Guide
 RingCentral for Desk Admin Guide RingCentral for Desk Admin Guide Contents Contents Introduction... 3 About RingCentral for Desk........................................................... 4 About this
RingCentral for Desk Admin Guide RingCentral for Desk Admin Guide Contents Contents Introduction... 3 About RingCentral for Desk........................................................... 4 About this
BackupAssist v6 quickstart guide
 New features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 3 System State backup... 3 Restore files, applications, System State and mailboxes... 4 Fully cloud ready Internet
New features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 3 System State backup... 3 Restore files, applications, System State and mailboxes... 4 Fully cloud ready Internet
Diver-Office Backup and Restore the Database
 Contents Determine the database type... 1 Backup and RESTORE The Diver-Office SQL CE Database... 1 Backup and Restore the Diver-Office SQL Express database... 2 SQL Server Management Studio Express...
Contents Determine the database type... 1 Backup and RESTORE The Diver-Office SQL CE Database... 1 Backup and Restore the Diver-Office SQL Express database... 2 SQL Server Management Studio Express...
BackupAssist v6 quickstart guide
 Using the new features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 2 Backing up VSS applications... 2 Restoring VSS applications... 3 System State backup and restore...
Using the new features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 2 Backing up VSS applications... 2 Restoring VSS applications... 3 System State backup and restore...
Clickfree Software Frequently Asked Questions (FAQ)
 Clickfree Software (FAQ) Last Revised: Nov 2, 2011 Clickfree_backup_software_FAQ_v1.0 Clickfree and the Clickfree logo are trademarks or registered trademarks of Storage Appliance Corporation. Other product
Clickfree Software (FAQ) Last Revised: Nov 2, 2011 Clickfree_backup_software_FAQ_v1.0 Clickfree and the Clickfree logo are trademarks or registered trademarks of Storage Appliance Corporation. Other product
Forensic analysis of iphone backups
 Forensic analysis of iphone backups The goal of iphone Backup Forensics analysis is extracting data and artefacts from the itunes backups without altering any information. iphone forensics can be performed
Forensic analysis of iphone backups The goal of iphone Backup Forensics analysis is extracting data and artefacts from the itunes backups without altering any information. iphone forensics can be performed
Welcome to Office 365!
 This document includes: Welcome to Office 365! What is Office 365? How do I access Office 365? Create and Access Your Documents from Anywhere with SkyDrive Pro Connect and Collaborate through Office 365
This document includes: Welcome to Office 365! What is Office 365? How do I access Office 365? Create and Access Your Documents from Anywhere with SkyDrive Pro Connect and Collaborate through Office 365
January 2016 Issue #2 Windows Backup
 January 2016 Issue #2 Windows Backup In the prior issue, I preached the virtues of frequent backups. Well, now it s time to detail the how-to of backups, and we will begin with Windows Backups. Built into
January 2016 Issue #2 Windows Backup In the prior issue, I preached the virtues of frequent backups. Well, now it s time to detail the how-to of backups, and we will begin with Windows Backups. Built into
AUT OneDrive for Business. Instructions for Using OneDrive on Windows Platform
 AUT OneDrive for Business Instructions for Using OneDrive on Windows Platform Contents 1 What s OneDrive for Business?... 3 2 Storing Files... 5 1.1 Saving and Opening files from your Office applications...
AUT OneDrive for Business Instructions for Using OneDrive on Windows Platform Contents 1 What s OneDrive for Business?... 3 2 Storing Files... 5 1.1 Saving and Opening files from your Office applications...
Safe Haven User Guide
 Safe Haven User Guide Date: October 2015 Version: 2.1 21/10/15 Health Informatics Centre Safe Haven VDI 1 Contents Safe Haven VDI... 3 Introduction... 3 Key Features and Benefits... 3 VDI Portal... 3 VMware
Safe Haven User Guide Date: October 2015 Version: 2.1 21/10/15 Health Informatics Centre Safe Haven VDI 1 Contents Safe Haven VDI... 3 Introduction... 3 Key Features and Benefits... 3 VDI Portal... 3 VMware
Common SofTest Troubleshooting Techniques
 Black Screen and Internet Restoration (Windows) On the rare occasion that SofTest Windows experiences an abnormality either during or immediately following an exam, it may not be capable of automatically
Black Screen and Internet Restoration (Windows) On the rare occasion that SofTest Windows experiences an abnormality either during or immediately following an exam, it may not be capable of automatically
STUDENT EMAIL: Guide for Students
 STUDENT EMAIL: Guide for Students This guide will introduce you to Gmail, which is the student email platform for ACT Public Schools. Gmail is part of our Google Apps for Education offering and will provide
STUDENT EMAIL: Guide for Students This guide will introduce you to Gmail, which is the student email platform for ACT Public Schools. Gmail is part of our Google Apps for Education offering and will provide
Password Depot for ios
 Password Depot for ios Table Of Contents First steps... 1 Creating a password file... 1 Creating new entries... 3 Adding entries / groups... 3 Copying or relocating entries / groups... 3 Deleting entries
Password Depot for ios Table Of Contents First steps... 1 Creating a password file... 1 Creating new entries... 3 Adding entries / groups... 3 Copying or relocating entries / groups... 3 Deleting entries
Installing the Panini Universal Scanner Driver
 Installing the Panini Universal Scanner Driver The following steps should be followed for installation of a Panini scanner. The user installing the scanner on his/her PC should have local administrative
Installing the Panini Universal Scanner Driver The following steps should be followed for installation of a Panini scanner. The user installing the scanner on his/her PC should have local administrative
Feature List for Kaspersky Password Manager
 Feature List for Kaspersky Password Manager Overview... Features by Platform...3 Feature Descriptions...4 Glossary...7 PAGE Feature List for Kaspersky Password Manager Overview Kaspersky Password Manager
Feature List for Kaspersky Password Manager Overview... Features by Platform...3 Feature Descriptions...4 Glossary...7 PAGE Feature List for Kaspersky Password Manager Overview Kaspersky Password Manager
Dynamic Learning Maps Consortium Technical Liaison Webinar
 Dynamic Learning Maps Consortium Technical Liaison Webinar Fall 2015 James Herynk Audio will be streamed through Skype for Business/Lync. Please hold questions until the end. All questions must be asked
Dynamic Learning Maps Consortium Technical Liaison Webinar Fall 2015 James Herynk Audio will be streamed through Skype for Business/Lync. Please hold questions until the end. All questions must be asked
What is PC Matic?...4. System Requirements...4. Launching PC Matic.5. How to Purchase a PC Matic Subscription..6. Additional Installations.
 USER Manual Table of Contents Getting Started What is PC Matic?...4 System Requirements....4 Launching PC Matic.5 How to Purchase a PC Matic Subscription..6 Additional Installations. 6 Registration...6
USER Manual Table of Contents Getting Started What is PC Matic?...4 System Requirements....4 Launching PC Matic.5 How to Purchase a PC Matic Subscription..6 Additional Installations. 6 Registration...6
FreeFlow Accxes Print Server V15.0 August 2010 701P50924. Xerox FreeFlow Accxes Print Server Drivers and Client Tools Software Installation Guide
 FreeFlow Accxes Print Server V15.0 August 2010 701P50924 Xerox FreeFlow Accxes Print Server Drivers and Client Tools Software 2010 Xerox Corporation. All rights reserved. XEROX and Xerox and Design, 6204,
FreeFlow Accxes Print Server V15.0 August 2010 701P50924 Xerox FreeFlow Accxes Print Server Drivers and Client Tools Software 2010 Xerox Corporation. All rights reserved. XEROX and Xerox and Design, 6204,
Avira Rescue System. HowTo
 Avira Rescue System HowTo Table of contents 1. Introduction... 3 2. System Requirements... 4 3. Product availability... 4 4. Product features... 5 5. Using the Rescue System... 6 5.1 The BIOS setup...6
Avira Rescue System HowTo Table of contents 1. Introduction... 3 2. System Requirements... 4 3. Product availability... 4 4. Product features... 5 5. Using the Rescue System... 6 5.1 The BIOS setup...6
Sticky Password 7. Sticky Password 7 is the latest, most advanced, portable, cross platform version of the powerful yet
 Sticky Password 7 Reviewer Guide Introduction Sticky Password 7 is the latest, most advanced, portable, cross platform version of the powerful yet simple password manager and form-filler. Its main goal
Sticky Password 7 Reviewer Guide Introduction Sticky Password 7 is the latest, most advanced, portable, cross platform version of the powerful yet simple password manager and form-filler. Its main goal
Mobile Communicator for Mobile Devices
 Mobile Communicator for Mobile Devices Quick Reference Guide Hosted Voice Customer Resource Center www.earthlinkbusiness.com/hostedvoice 2015 EarthLink. Trademarks are property of their respective owners.
Mobile Communicator for Mobile Devices Quick Reference Guide Hosted Voice Customer Resource Center www.earthlinkbusiness.com/hostedvoice 2015 EarthLink. Trademarks are property of their respective owners.
TECHNICAL SUPPORT GUIDE
 TECHNICAL SUPPORT GUIDE INTRODUCTION This document has been developed to provide a guideline for assisting our clients and their technicians with a standard Console Gateway Live configuration. IS THIS
TECHNICAL SUPPORT GUIDE INTRODUCTION This document has been developed to provide a guideline for assisting our clients and their technicians with a standard Console Gateway Live configuration. IS THIS
