Using Code Coverage Tools in the Linux Kernel
|
|
|
- Darcy Watson
- 8 years ago
- Views:
Transcription
1 Using Code Coverage Tools in the Linux Kernel Nigel Hinds Paul Larson Hubertus Franke Marty Ridgeway { nhinds, plars, frankeh, mridge us.ibm.com Defining software reliability is hard enough, let alone ensuring it. However, most all software developers agree on the importance of testing. The often unspoken assumption with testing is that the test programs cover a majority of the source code written. A test covers a line of code if running the test executes the line. Coverage analysis measures how much of the target code is run during a test and is a useful mechanism for evaluating the effectiveness of a system test or benchmark. The GNU development tool gcov allows developers to obtain coverage results for programs compiled with the GNU gcc compiler. In this article, we learn how to instrument the Linux r kernel to generate code coverage data, and how to visualize results with tools from the Linux Test Project (LTP) [4]. 1 Coverage Basics Code coverage analysis is the process that allows us to determine the percentage of code within an application that was executed during the test process. The data gathered by using coverage analysis can be used to measure and improve the test process [6]. Coverage analysis can be performed in a variety of ways for producing different views of how a test process executes the code. A few types of coverage analysis are discussed here. The first and most basic type of coverage analysis is usually called statement coverage analysis [1]. Statement coverage analysis breaks the code down into basic blocks. Basic blocks are the sections of code that exist between branches. Since these basic blocks do not cross branches, we can know that if any instruction in a basic block is executed, then every instruction within the basic block is executed the same number of times. Instrumenting basic blocks with counters provides a more efficient way of showing how many times each line of code in a program has been executed, without having to instrument every line. Statement coverage analysis is what most people generally think of when they think of code coverage analysis, but it isn t flawless on its own. The following example shows one way it can fail: 1
2 int *iptr = NULL; if(conditional) iptr = &i; *iptr = j*10; The example above will work fine when every line is executed (100% coverage). However, if the conditional is ever false, iptr will be null when dereferenced, exposing the bug. With statement coverage, one must know that 100% code coverage in a test process may not necessarily imply that the application is well tested. Another type of coverage analysis is called branch coverage analysis [5]. Instead of generating data about how many times each line or basic block is executed, branch coverage looks at the branches between basic blocks. Branch coverage analyzes each branch to determine the possible paths through it and produces data to show which paths were taken and how often. As an added bonus, by knowing which branches were taken, statement coverage data can be derived. In the example above, branch coverage would have clearly shown that one possible branch (conditional failed) was never tested, exposing a hole in the test process. A more sophisticated form of branch coverage also exists that handles complex conditionals. Many conditionals involve more than a single test that will pass or fail. Some conditionals involve complex logic that requires testing through all combinations. The better form of branch coverage analysis will correctly handle situations like the following example: struct somestructure* p = NULL; if(i == 0 (j == 1 && p->j == 10)) printf("got here\n"); If i is ever non-zero when j is 1, then the NULL pointer p will be dereferenced in the last part of the conditional. There are paths through this branch in both the positive and negative case that will never expose the potential segmentation fault if the conditional is only analyzed as a single pass or fail statement. 1.1 GCOV Although there are many other types of coverage for dealing with a variety of corner cases, gcov only provides statement and branch coverage. In order to get coverage data, programs must be compiled by gcc with the -fprofile-arcs and -ftest-coverage flags. These options cause the compiler to insert additional instructions into the generated object code. This new code increments counters which identify sections of the code being executed. When the program is run these counters are incremented when the specific portions of the code are executed. When the program terminates the counters are dumped to a file. During the postmortem, the actual gcov program is used to process the counter file just created. Unfortunately, until now gcov did not work on kernel code for two primary reasons. Although kernel files can be instrumented with gcc, the kernel never links with the system libraries that provide support 2
3 functions for gcov. Additionally, since the kernel never exits, counter data would never be generated. Getting coverage data from dynamic modules was another obstacle to kernel coverage. In early 2002, the LTP team published a patch to the Linux kernel that addresses these issues and allowed developers to use the existing gcov tools to get coverage data from a running kernel [2]. A detailed description of the functionality provided by the patch can be found in our Ottawa Linux Symposium paper [3]. 2 Using Coverage Tools Once a program has terminated and the gcov counter data (.da files) exist, gcov is capable of analyzing the files and producing coverage output. To see the coverage data for a user space program, one may simply run gcov program.c where program.c is the source file. The.da file must also exist in the same directory. The raw output from gcov is useful, but not very readable or organized for viewing source trees. The lcov toolkit produces a far more user friendly and organized output. lcov automates the process of extracting the coverage data using gcov and producing HTML results based on that data [4]. To produce coverage data with lcov, first download the gcov-kernel and lcov tools from the LTP website at ltp.sourceforge.net. Apply the gcov-kernel patch to a test kernel. patch -p1< gcov-<kernel version>.patch General kernel configuration and compiling instruction is beyond the scope of this article. But, to enable gcov on the entire kernel, verify that the GCOV kernel profiler configuration option is selected. The gcov-kernel README file provides details on how to gcov enable portions of the kernel. After compiling and installing the gcov-kernel, download and install the lcov toolkit. The lcov toolkit provides options for manipulating gcov data. lcov provides scripts to clear the gcov kernel counters. lcov --zerocounters Figure 1: lcov Flowchart 3
4 The developer would run one or more tests to exercise the new kernel code. During the test, gcov-kernel counters are updated. The basic process flow of the lcov tool is illustrated in Figure 1. Capture the gcov data by calling lcov with the capture option (-c), specifying an output file (-o). lcov -c -o kerneltest.info Figure 2: Partial lcov output for fs/jfs Figure 3: Example lcov output for a file The lcov tool first calls gcov to generate the coverage data, then calls the LTP geninfo script to collect that data and produce a.info file to represent the coverage data. Once the.info file has been created, the genhtml script may be used to create HTML output for all of the coverage data collected. The genhtml script will generate both output at a directory level as illustrated in Figure 2 and output on a file level as illustrated in Figure 3. genhtml -o [outputdir] kerneltest.info 4
5 The lcov tool can also be used for analyzing the coverage of user space applications, and producing HTML output based on the data collected. Using lcov with applications is similar to kernel usage. In order to analyze coverage, the application must be compiled with gcc using the -fprofile-arcs and -ftest-coverage flags. The application should be executed from the directory in which it was compiled, and for gcov to work on user space programs, the application must exit normally. The process for using lcov with an application is as follows: 1. Run the program following your test procedure, and exit. 2. lcov --directory [dirname] -c -o application.info 3. genhtml -o [outputdir] application.info lcov can also be used to manipulate.info files. Information describing coverage data about files in a.info file may be extracted or removed. Running lcov --extract file.info PATTERN will show just the data in the.info file matching the given pattern. Running lcov --remove file.info PATTERN will show all data in the given.info file except for the records matching the pattern, thus removing that record. Data contained in.info files may also be combined by running lcov -a file1.info -a file2.info -a file3.info... -o output.info, which produces a single file (output.info) containing the data from all files passed to lcov with the -a option. 3 Results & Conclusions The gcov-kernel patch overhead was estimated by comparing compile times for the Linux kernel. Specifically, each test kernel was booted and the time required to compile (execute make bzimage) the Linux kernel was measured. Runtimes, as measured by /bin/time, show seconds of kernel+user time to compile the kernel without the gcov-kernel patch. A patched kernel took seconds to compile. Even though the patch increased the kernel time by about 23%, most applications spend a small percentage of their time in the kernel. In our test, the compile spent less than 10% of the time in the kernel, so the observed overall gcov-kernel patch overhead is about 3% of the combined kernel and user space runtime. See the Ottawa Linux Symposium paper [3] for more on the gcov-kernel patch overhead. The real benefit of code coverage analysis is that it can be used to analyze and improve the coverage provided by a test suite. In this case, the test suite being improved is the Linux Test Project. 100% code coverage is necessary (but not sufficient) for complete functional testing. It is an important goal of the 5
6 LTP to improve coverage by identifying untested regions of kernel code. This section provides a measure of LTP coverage and how the gcov-kernel patch has improved the LTP suite. The gcov-kernel patch and LTP tool and test suite make the valuable gcov software coverage package available to kernel developers. gcov allows developers to measure the effectiveness of their testing efforts. References [1] Code Coverage Analysis. [2] GCOV-kernel. [3] P. Larson, N. Hinds, H. Franke, and R. Ravindran. Improving the linux test project with kernel code coverage analysis. In 2003 Ottawa Linux Symposium, July [4] LCOV. [5] B. Marick. The Craft of Software Testing. Prentice Hall, [6] W. E. Perry. Effective Methods for Software Testing. Wiley Computer Publishing, second edition edition, Legal Statement This work represents the view of the authors and does not necessarily represent the view of IBM. Linux is a registered trademark of Linus Torvalds. Other company, product, and service names may be trademarks or service marks of others. 6
Compaq Storage Performance Monitor HOWTO
 Compaq Storage Performance Monitor HOWTO Chris Lorenz lorenzc@us.ibm.com 2002 07 11 Revision History Revision 1.0 2002 07 11 Revised by: CL This HOWTO provides an overview of the Compaq Storage Performance
Compaq Storage Performance Monitor HOWTO Chris Lorenz lorenzc@us.ibm.com 2002 07 11 Revision History Revision 1.0 2002 07 11 Revised by: CL This HOWTO provides an overview of the Compaq Storage Performance
Code Estimation Tools Directions for a Services Engagement
 Code Estimation Tools Directions for a Services Engagement Summary Black Duck software provides two tools to calculate size, number, and category of files in a code base. This information is necessary
Code Estimation Tools Directions for a Services Engagement Summary Black Duck software provides two tools to calculate size, number, and category of files in a code base. This information is necessary
Pattern Insight Clone Detection
 Pattern Insight Clone Detection TM The fastest, most effective way to discover all similar code segments What is Clone Detection? Pattern Insight Clone Detection is a powerful pattern discovery technology
Pattern Insight Clone Detection TM The fastest, most effective way to discover all similar code segments What is Clone Detection? Pattern Insight Clone Detection is a powerful pattern discovery technology
Jonathan Worthington Scarborough Linux User Group
 Jonathan Worthington Scarborough Linux User Group Introduction What does a Virtual Machine do? Hides away the details of the hardware platform and operating system. Defines a common set of instructions.
Jonathan Worthington Scarborough Linux User Group Introduction What does a Virtual Machine do? Hides away the details of the hardware platform and operating system. Defines a common set of instructions.
Code Coverage: Free Software and Virtualization to the Rescue
 Code Coverage: Free Software and Virtualization to the Rescue Franco Gasperoni, AdaCore gasperoni@adacore.com What is Code Coverage and Why Is It Useful? Your team is developing or updating an embedded
Code Coverage: Free Software and Virtualization to the Rescue Franco Gasperoni, AdaCore gasperoni@adacore.com What is Code Coverage and Why Is It Useful? Your team is developing or updating an embedded
How To Migrate To Redhat Enterprise Linux 4
 Migrating to Red Hat Enterprise Linux 4: Upgrading to the latest Red Hat release By Donald Fischer Abstract Red Hat Enterprise Linux subscribers may choose to deploy any of the supported versions of the
Migrating to Red Hat Enterprise Linux 4: Upgrading to the latest Red Hat release By Donald Fischer Abstract Red Hat Enterprise Linux subscribers may choose to deploy any of the supported versions of the
http://www.vassure.com
 Technical Case Study: Patch Management This is subsequent to Summary of Projects VMware - ESX Server to Facilitate: IMS, Server Consolidation, Storage & Testing with Production Server VAssure Virtualization
Technical Case Study: Patch Management This is subsequent to Summary of Projects VMware - ESX Server to Facilitate: IMS, Server Consolidation, Storage & Testing with Production Server VAssure Virtualization
Browser Testing Framework for LHG
 Browser Testing Framework for LHG Presented by Trevor Woerner, Will Chen Date February, 2015 Outline Overview of the test suite Test category Run the test On Linux On Android Verified platforms Test output
Browser Testing Framework for LHG Presented by Trevor Woerner, Will Chen Date February, 2015 Outline Overview of the test suite Test category Run the test On Linux On Android Verified platforms Test output
NVIDIA CUDA GETTING STARTED GUIDE FOR MAC OS X
 NVIDIA CUDA GETTING STARTED GUIDE FOR MAC OS X DU-05348-001_v6.5 August 2014 Installation and Verification on Mac OS X TABLE OF CONTENTS Chapter 1. Introduction...1 1.1. System Requirements... 1 1.2. About
NVIDIA CUDA GETTING STARTED GUIDE FOR MAC OS X DU-05348-001_v6.5 August 2014 Installation and Verification on Mac OS X TABLE OF CONTENTS Chapter 1. Introduction...1 1.1. System Requirements... 1 1.2. About
Security Testing OpenGGSN: a Case Study
 Security Testing OpenGGSN: a Case Study Esa Tikkala, Mikko Rapeli, Kaarina Karppinen, Hannu Honkanen VTT Technical Research Centre of Finland, Oulu, Finland Abstract As systems today are more and more
Security Testing OpenGGSN: a Case Study Esa Tikkala, Mikko Rapeli, Kaarina Karppinen, Hannu Honkanen VTT Technical Research Centre of Finland, Oulu, Finland Abstract As systems today are more and more
Oracle Solaris Studio Code Analyzer
 Oracle Solaris Studio Code Analyzer The Oracle Solaris Studio Code Analyzer ensures application reliability and security by detecting application vulnerabilities, including memory leaks and memory access
Oracle Solaris Studio Code Analyzer The Oracle Solaris Studio Code Analyzer ensures application reliability and security by detecting application vulnerabilities, including memory leaks and memory access
Yocto Project ADT, Eclipse plug-in and Developer Tools
 Yocto Project ADT, Eclipse plug-in and Developer Tools Jessica Zhang LinuxCon - Japan Tokyo 2013 Agenda The Application Development Toolkit Usage Flow And Roles Yocto Project Eclipse Plug-in Interacts
Yocto Project ADT, Eclipse plug-in and Developer Tools Jessica Zhang LinuxCon - Japan Tokyo 2013 Agenda The Application Development Toolkit Usage Flow And Roles Yocto Project Eclipse Plug-in Interacts
ARMSDK-VM Virtual Appliance A preconfigured Linux system
 ARMSDK-VM Virtual Appliance A preconfigured Linux system Ka-Ro electronics GmbH - Pascalstr. 22, D-52076 Aachen, Germany - Tel.: +49 2408 1402-0 (FAX -10) www.karo-electronics.de Disclaimer The information
ARMSDK-VM Virtual Appliance A preconfigured Linux system Ka-Ro electronics GmbH - Pascalstr. 22, D-52076 Aachen, Germany - Tel.: +49 2408 1402-0 (FAX -10) www.karo-electronics.de Disclaimer The information
Supported platforms & compilers Required software Where to download the packages Geant4 toolkit installation (release 9.6)
 Supported platforms & compilers Required software Where to download the packages Geant4 toolkit installation (release 9.6) Configuring the environment manually Using CMake CLHEP full version installation
Supported platforms & compilers Required software Where to download the packages Geant4 toolkit installation (release 9.6) Configuring the environment manually Using CMake CLHEP full version installation
SAS, Excel, and the Intranet
 SAS, Excel, and the Intranet Peter N. Prause, The Hartford, Hartford CT Charles Patridge, The Hartford, Hartford CT Introduction: The Hartford s Corporate Profit Model (CPM) is a SAS based multi-platform
SAS, Excel, and the Intranet Peter N. Prause, The Hartford, Hartford CT Charles Patridge, The Hartford, Hartford CT Introduction: The Hartford s Corporate Profit Model (CPM) is a SAS based multi-platform
Leak Check Version 2.1 for Linux TM
 Leak Check Version 2.1 for Linux TM User s Guide Including Leak Analyzer For x86 Servers Document Number DLC20-L-021-1 Copyright 2003-2009 Dynamic Memory Solutions LLC www.dynamic-memory.com Notices Information
Leak Check Version 2.1 for Linux TM User s Guide Including Leak Analyzer For x86 Servers Document Number DLC20-L-021-1 Copyright 2003-2009 Dynamic Memory Solutions LLC www.dynamic-memory.com Notices Information
SOFTWARE TESTING TRAINING COURSES CONTENTS
 SOFTWARE TESTING TRAINING COURSES CONTENTS 1 Unit I Description Objectves Duration Contents Software Testing Fundamentals and Best Practices This training course will give basic understanding on software
SOFTWARE TESTING TRAINING COURSES CONTENTS 1 Unit I Description Objectves Duration Contents Software Testing Fundamentals and Best Practices This training course will give basic understanding on software
Introduction to Linux and Cluster Basics for the CCR General Computing Cluster
 Introduction to Linux and Cluster Basics for the CCR General Computing Cluster Cynthia Cornelius Center for Computational Research University at Buffalo, SUNY 701 Ellicott St Buffalo, NY 14203 Phone: 716-881-8959
Introduction to Linux and Cluster Basics for the CCR General Computing Cluster Cynthia Cornelius Center for Computational Research University at Buffalo, SUNY 701 Ellicott St Buffalo, NY 14203 Phone: 716-881-8959
NVIDIA CUDA GETTING STARTED GUIDE FOR MAC OS X
 NVIDIA CUDA GETTING STARTED GUIDE FOR MAC OS X DU-05348-001_v5.5 July 2013 Installation and Verification on Mac OS X TABLE OF CONTENTS Chapter 1. Introduction...1 1.1. System Requirements... 1 1.2. About
NVIDIA CUDA GETTING STARTED GUIDE FOR MAC OS X DU-05348-001_v5.5 July 2013 Installation and Verification on Mac OS X TABLE OF CONTENTS Chapter 1. Introduction...1 1.1. System Requirements... 1 1.2. About
National University of Ireland, Maynooth MAYNOOTH, CO. KILDARE, IRELAND. Testing Guidelines for Student Projects
 National University of Ireland, Maynooth MAYNOOTH, CO. KILDARE, IRELAND. DEPARTMENT OF COMPUTER SCIENCE, TECHNICAL REPORT SERIES Testing Guidelines for Student Projects Stephen Brown and Rosemary Monahan
National University of Ireland, Maynooth MAYNOOTH, CO. KILDARE, IRELAND. DEPARTMENT OF COMPUTER SCIENCE, TECHNICAL REPORT SERIES Testing Guidelines for Student Projects Stephen Brown and Rosemary Monahan
Project No. 2: Process Scheduling in Linux Submission due: April 28, 2014, 11:59pm
 Project No. 2: Process Scheduling in Linux Submission due: April 28, 2014, 11:59pm PURPOSE Getting familiar with the Linux kernel source code. Understanding process scheduling and how different parameters
Project No. 2: Process Scheduling in Linux Submission due: April 28, 2014, 11:59pm PURPOSE Getting familiar with the Linux kernel source code. Understanding process scheduling and how different parameters
Using InstallAware 7. To Patch Software Products. August 2007
 Using InstallAware 7 To Patch Software Products August 2007 The information contained in this document represents the current view of InstallAware Software Corporation on the issues discussed as of the
Using InstallAware 7 To Patch Software Products August 2007 The information contained in this document represents the current view of InstallAware Software Corporation on the issues discussed as of the
Fully Automated Static Analysis of Fedora Packages
 Fully Automated Static Analysis of Fedora Packages Red Hat Kamil Dudka August 9th, 2014 Abstract There are static analysis tools (such as Clang or Cppcheck) that are able to find bugs in Fedora packages
Fully Automated Static Analysis of Fedora Packages Red Hat Kamil Dudka August 9th, 2014 Abstract There are static analysis tools (such as Clang or Cppcheck) that are able to find bugs in Fedora packages
Interfacing SAS Software, Excel, and the Intranet without SAS/Intrnet TM Software or SAS Software for the Personal Computer
 Interfacing SAS Software, Excel, and the Intranet without SAS/Intrnet TM Software or SAS Software for the Personal Computer Peter N. Prause, The Hartford, Hartford CT Charles Patridge, The Hartford, Hartford
Interfacing SAS Software, Excel, and the Intranet without SAS/Intrnet TM Software or SAS Software for the Personal Computer Peter N. Prause, The Hartford, Hartford CT Charles Patridge, The Hartford, Hartford
Threat Modelling for Web Application Deployment. Ivan Ristic ivanr@webkreator.com (Thinking Stone)
 Threat Modelling for Web Application Deployment Ivan Ristic ivanr@webkreator.com (Thinking Stone) Talk Overview 1. Introducing Threat Modelling 2. Real-world Example 3. Questions Who Am I? Developer /
Threat Modelling for Web Application Deployment Ivan Ristic ivanr@webkreator.com (Thinking Stone) Talk Overview 1. Introducing Threat Modelling 2. Real-world Example 3. Questions Who Am I? Developer /
Monitoring, Tracing, Debugging (Under Construction)
 Monitoring, Tracing, Debugging (Under Construction) I was already tempted to drop this topic from my lecture on operating systems when I found Stephan Siemen's article "Top Speed" in Linux World 10/2003.
Monitoring, Tracing, Debugging (Under Construction) I was already tempted to drop this topic from my lecture on operating systems when I found Stephan Siemen's article "Top Speed" in Linux World 10/2003.
Delphi-Windows Digital Signature Library Interface
 Delphi-Windows Digital Signature Library Interface Joseph Snyder SW Process Engineer snyderj@osehra.org Purpose The purpose of these three files is to provide the interface between Delphi executables and
Delphi-Windows Digital Signature Library Interface Joseph Snyder SW Process Engineer snyderj@osehra.org Purpose The purpose of these three files is to provide the interface between Delphi executables and
IBM SAP International Competence Center. Load testing SAP ABAP Web Dynpro applications with IBM Rational Performance Tester
 IBM SAP International Competence Center Load testing SAP ABAP Web Dynpro applications with IBM Rational Performance Tester Ease of use, excellent technical support from the IBM Rational team and, of course,
IBM SAP International Competence Center Load testing SAP ABAP Web Dynpro applications with IBM Rational Performance Tester Ease of use, excellent technical support from the IBM Rational team and, of course,
McAfee VirusScan Enterprise for Linux 1.7.0 Software
 Configuration Guide McAfee VirusScan Enterprise for Linux 1.7.0 Software For use with epolicy Orchestrator 4.5.0 and 4.6.0 COPYRIGHT Copyright 2011 McAfee, Inc. All Rights Reserved. No part of this publication
Configuration Guide McAfee VirusScan Enterprise for Linux 1.7.0 Software For use with epolicy Orchestrator 4.5.0 and 4.6.0 COPYRIGHT Copyright 2011 McAfee, Inc. All Rights Reserved. No part of this publication
Automatic System for Linux Kernel Performance Testing
 Automatic System for Linux Kernel Performance Testing Alexander Ufimtsev University College Dublin alexu@ucd.ie Liam Murphy University College Dublin Liam.Murphy@ucd.ie Abstract We introduce an automatic
Automatic System for Linux Kernel Performance Testing Alexander Ufimtsev University College Dublin alexu@ucd.ie Liam Murphy University College Dublin Liam.Murphy@ucd.ie Abstract We introduce an automatic
Introduction to Software Testing Chapter 8.1 Building Testing Tools Instrumentation. Chapter 8 Outline
 Introduction to Software Testing Chapter 8. Building Testing Tools Instrumentation Paul Ammann & Jeff Offutt www.introsoftwaretesting.com Chapter 8 Outline. Instrumentation for Graph and Logical Expression
Introduction to Software Testing Chapter 8. Building Testing Tools Instrumentation Paul Ammann & Jeff Offutt www.introsoftwaretesting.com Chapter 8 Outline. Instrumentation for Graph and Logical Expression
SheevaPlug Development Kit README Rev. 1.2
 SheevaPlug Development Kit README Rev. 1.2 Introduction... 3 Flow to use the Software Development Kit packages... 3 Appendix A... 5 GCC cross-compiler... 5 Appendix B... 6 Mini-USB debug driver installation
SheevaPlug Development Kit README Rev. 1.2 Introduction... 3 Flow to use the Software Development Kit packages... 3 Appendix A... 5 GCC cross-compiler... 5 Appendix B... 6 Mini-USB debug driver installation
GDB Tutorial. A Walkthrough with Examples. CMSC 212 - Spring 2009. Last modified March 22, 2009. GDB Tutorial
 A Walkthrough with Examples CMSC 212 - Spring 2009 Last modified March 22, 2009 What is gdb? GNU Debugger A debugger for several languages, including C and C++ It allows you to inspect what the program
A Walkthrough with Examples CMSC 212 - Spring 2009 Last modified March 22, 2009 What is gdb? GNU Debugger A debugger for several languages, including C and C++ It allows you to inspect what the program
Lotus Sametime. FIPS Support for IBM Lotus Sametime 8.0. Version 8.0 SC23-8760-00
 Lotus Sametime Version 8.0 FIPS Support for IBM Lotus Sametime 8.0 SC23-8760-00 Disclaimer THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS PROVIDED FOR INFORMATIONAL PURPOSES ONLY. WHILE EFFORTS WERE
Lotus Sametime Version 8.0 FIPS Support for IBM Lotus Sametime 8.0 SC23-8760-00 Disclaimer THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS PROVIDED FOR INFORMATIONAL PURPOSES ONLY. WHILE EFFORTS WERE
Eliminate Memory Errors and Improve Program Stability
 Eliminate Memory Errors and Improve Program Stability with Intel Parallel Studio XE Can running one simple tool make a difference? Yes, in many cases. You can find errors that cause complex, intermittent
Eliminate Memory Errors and Improve Program Stability with Intel Parallel Studio XE Can running one simple tool make a difference? Yes, in many cases. You can find errors that cause complex, intermittent
Using SNMP to Obtain Port Counter Statistics During Live Migration of a Virtual Machine. Ronny L. Bull Project Writeup For: CS644 Clarkson University
 Using SNMP to Obtain Port Counter Statistics During Live Migration of a Virtual Machine Ronny L. Bull Project Writeup For: CS644 Clarkson University Fall 2012 Abstract If a managed switch is used during
Using SNMP to Obtain Port Counter Statistics During Live Migration of a Virtual Machine Ronny L. Bull Project Writeup For: CS644 Clarkson University Fall 2012 Abstract If a managed switch is used during
Levels of Software Testing. Functional Testing
 Levels of Software Testing There are different levels during the process of Testing. In this chapter a brief description is provided about these levels. Levels of testing include the different methodologies
Levels of Software Testing There are different levels during the process of Testing. In this chapter a brief description is provided about these levels. Levels of testing include the different methodologies
Software configuration management
 Software Engineering Theory Software configuration management Lena Buffoni/ Kristian Sandahl Department of Computer and Information Science 2015-09-30 2 Maintenance Requirements System Design (Architecture,
Software Engineering Theory Software configuration management Lena Buffoni/ Kristian Sandahl Department of Computer and Information Science 2015-09-30 2 Maintenance Requirements System Design (Architecture,
Setting Up a CLucene and PostgreSQL Federation
 Federated Desktop and File Server Search with libferris Ben Martin Abstract How to federate CLucene personal document indexes with PostgreSQL/TSearch2. The libferris project has two major goals: mounting
Federated Desktop and File Server Search with libferris Ben Martin Abstract How to federate CLucene personal document indexes with PostgreSQL/TSearch2. The libferris project has two major goals: mounting
Nick Ashley TOOLS. The following table lists some additional and possibly more unusual tools used in this paper.
 TAKING CONTROL OF YOUR DATABASE DEVELOPMENT Nick Ashley While language-oriented toolsets become more advanced the range of development and deployment tools for databases remains primitive. How often is
TAKING CONTROL OF YOUR DATABASE DEVELOPMENT Nick Ashley While language-oriented toolsets become more advanced the range of development and deployment tools for databases remains primitive. How often is
Installation Guide for Basler pylon 2.3.x for Linux
 Installation Guide for Basler pylon 2.3.x for Linux Version 2.3.x Document ID Number: AW00100401000 Revision Date: May 27, 2011 Subject to Change Without Notice Basler Vision Technologies Installation
Installation Guide for Basler pylon 2.3.x for Linux Version 2.3.x Document ID Number: AW00100401000 Revision Date: May 27, 2011 Subject to Change Without Notice Basler Vision Technologies Installation
Building CHAOS: an Operating System for Livermore Linux Clusters
 UCRL-ID-151968 Building CHAOS: an Operating System for Livermore Linux Clusters Jim E. Garlick Chris M. Dunlap February 21, 2002 Approved for public release; further dissemination unlimited DISCLAIMER
UCRL-ID-151968 Building CHAOS: an Operating System for Livermore Linux Clusters Jim E. Garlick Chris M. Dunlap February 21, 2002 Approved for public release; further dissemination unlimited DISCLAIMER
Backing up the Embedded Oracle database of a Red Hat Network Satellite
 Backing up the Embedded Oracle database of a Red Hat Network Satellite By Melissa Goldin and Vladimir Zlatkin Abstract This document will help you create a backup of the Oracle database of a Red Hat Network
Backing up the Embedded Oracle database of a Red Hat Network Satellite By Melissa Goldin and Vladimir Zlatkin Abstract This document will help you create a backup of the Oracle database of a Red Hat Network
RPC and TI-RPC Test Suite Test Plan Document
 RPC and TI-RPC Test Suite Test Plan Document Cyril LACABANNE Bull S.A.S. Version 1.3 12 July 2007 Revision history Version Description 1.0 First release 1.1 Several correction on 1, 5, 8, 14 1.2 Add first
RPC and TI-RPC Test Suite Test Plan Document Cyril LACABANNE Bull S.A.S. Version 1.3 12 July 2007 Revision history Version Description 1.0 First release 1.1 Several correction on 1, 5, 8, 14 1.2 Add first
Installing and Configuring Adobe LiveCycle 9.5 Connector for Microsoft SharePoint
 What s new Installing and Configuring Adobe LiveCycle 9.5 Connector for Microsoft SharePoint Contents Introduction What s new on page 1 Introduction on page 1 Installation Overview on page 2 System requirements
What s new Installing and Configuring Adobe LiveCycle 9.5 Connector for Microsoft SharePoint Contents Introduction What s new on page 1 Introduction on page 1 Installation Overview on page 2 System requirements
Trustworthy Computing
 Stefan Thom Senior Software Development Engineer and Security Architect for IEB, Microsoft Rob Spiger, Senior Security Strategist Trustworthy Computing Agenda Windows 8 TPM Scenarios Hardware Choices with
Stefan Thom Senior Software Development Engineer and Security Architect for IEB, Microsoft Rob Spiger, Senior Security Strategist Trustworthy Computing Agenda Windows 8 TPM Scenarios Hardware Choices with
Structural Health Monitoring Tools (SHMTools)
 Structural Health Monitoring Tools (SHMTools) Getting Started LANL/UCSD Engineering Institute LA-CC-14-046 c Copyright 2014, Los Alamos National Security, LLC All rights reserved. May 30, 2014 Contents
Structural Health Monitoring Tools (SHMTools) Getting Started LANL/UCSD Engineering Institute LA-CC-14-046 c Copyright 2014, Los Alamos National Security, LLC All rights reserved. May 30, 2014 Contents
Example of Standard API
 16 Example of Standard API System Call Implementation Typically, a number associated with each system call System call interface maintains a table indexed according to these numbers The system call interface
16 Example of Standard API System Call Implementation Typically, a number associated with each system call System call interface maintains a table indexed according to these numbers The system call interface
Migrating LAMP stack from x86 to Power using the Server Consolidation Tool
 Migrating LAMP stack from x86 to Power using the Server Consolidation Tool Naveen N. Rao Lucio J.H. Correia IBM Linux Technology Center November 2014 Version 3.0 1 of 24 Table of Contents 1.Introduction...3
Migrating LAMP stack from x86 to Power using the Server Consolidation Tool Naveen N. Rao Lucio J.H. Correia IBM Linux Technology Center November 2014 Version 3.0 1 of 24 Table of Contents 1.Introduction...3
1 FCS Project Submission System
 1 FCS Project Submission System Teachers at FCS currently accept digital homework via email. However, email is cumbersome, because teachers must individually download the attached homework from every student,
1 FCS Project Submission System Teachers at FCS currently accept digital homework via email. However, email is cumbersome, because teachers must individually download the attached homework from every student,
X05. An Overview of Source Code Scanning Tools. Loulwa Salem. Las Vegas, NV. IBM Corporation 2006. IBM System p, AIX 5L & Linux Technical University
 X05 An Overview of Source Code Scanning Tools Loulwa Salem Las Vegas, NV Objectives This session will introduce better coding practices and tools available to aid developers in producing more secure code.
X05 An Overview of Source Code Scanning Tools Loulwa Salem Las Vegas, NV Objectives This session will introduce better coding practices and tools available to aid developers in producing more secure code.
Minimizing code defects to improve software quality and lower development costs.
 Development solutions White paper October 2008 Minimizing code defects to improve software quality and lower development costs. IBM Rational Software Analyzer and IBM Rational PurifyPlus software Kari
Development solutions White paper October 2008 Minimizing code defects to improve software quality and lower development costs. IBM Rational Software Analyzer and IBM Rational PurifyPlus software Kari
How To Install Acronis Backup & Recovery 11.5 On A Linux Computer
 Acronis Backup & Recovery 11.5 Server for Linux Update 2 Installation Guide Copyright Statement Copyright Acronis International GmbH, 2002-2013. All rights reserved. Acronis and Acronis Secure Zone are
Acronis Backup & Recovery 11.5 Server for Linux Update 2 Installation Guide Copyright Statement Copyright Acronis International GmbH, 2002-2013. All rights reserved. Acronis and Acronis Secure Zone are
PERFORMANCE TOOLS DEVELOPMENTS
 PERFORMANCE TOOLS DEVELOPMENTS Roberto A. Vitillo presented by Paolo Calafiura & Wim Lavrijsen Lawrence Berkeley National Laboratory Future computing in particle physics, 16 June 2011 1 LINUX PERFORMANCE
PERFORMANCE TOOLS DEVELOPMENTS Roberto A. Vitillo presented by Paolo Calafiura & Wim Lavrijsen Lawrence Berkeley National Laboratory Future computing in particle physics, 16 June 2011 1 LINUX PERFORMANCE
kgraft Live patching of the Linux kernel
 kgraft Live patching of the Linux kernel Vojtěch Pavlík Director SUSE Labs vojtech@suse.com Why live patching? Common tiers of change management: 1. Incident response (we're down, actively exploited )
kgraft Live patching of the Linux kernel Vojtěch Pavlík Director SUSE Labs vojtech@suse.com Why live patching? Common tiers of change management: 1. Incident response (we're down, actively exploited )
Introduction. dnotify
 Introduction In a multi-user, multi-process operating system, files are continually being created, modified and deleted, often by apparently unrelated processes. This means that any software that needs
Introduction In a multi-user, multi-process operating system, files are continually being created, modified and deleted, often by apparently unrelated processes. This means that any software that needs
IBM SmartCloud Workload Automation - Software as a Service. Agent Installation and Uninstallation Messages
 IBM SmartCloud Workload Automation - Software as a Service Agent Installation and Uninstallation Messages IBM SmartCloud Workload Automation - Software as a Service Agent Installation and Uninstallation
IBM SmartCloud Workload Automation - Software as a Service Agent Installation and Uninstallation Messages IBM SmartCloud Workload Automation - Software as a Service Agent Installation and Uninstallation
IBM Security QRadar Version 7.2.0. Installing QRadar with a Bootable USB Flash-drive Technical Note
 IBM Security QRadar Version 7.2.0 Installing QRadar with a Bootable USB Flash-drive Technical Note Note: Before using this information and the product that it supports, read the information in Notices
IBM Security QRadar Version 7.2.0 Installing QRadar with a Bootable USB Flash-drive Technical Note Note: Before using this information and the product that it supports, read the information in Notices
2 SYSTEM DESCRIPTION TECHNIQUES
 2 SYSTEM DESCRIPTION TECHNIQUES 2.1 INTRODUCTION Graphical representation of any process is always better and more meaningful than its representation in words. Moreover, it is very difficult to arrange
2 SYSTEM DESCRIPTION TECHNIQUES 2.1 INTRODUCTION Graphical representation of any process is always better and more meaningful than its representation in words. Moreover, it is very difficult to arrange
Confining the Apache Web Server with Security-Enhanced Linux
 Confining the Apache Web Server with Security-Enhanced Linux Michelle J. Gosselin, Jennifer Schommer mgoss@mitre.org, jschommer@mitre.org Keywords: Operating System Security, Web Server Security, Access
Confining the Apache Web Server with Security-Enhanced Linux Michelle J. Gosselin, Jennifer Schommer mgoss@mitre.org, jschommer@mitre.org Keywords: Operating System Security, Web Server Security, Access
Using. DataTrust Secure Online Backup. To Protect Your. Hyper-V Virtual Environment. 1 P a g e
 Using DataTrust Secure Online Backup To Protect Your Hyper-V Virtual Environment. 1 P a g e Table of Contents: 1. Backing Up the Guest OS with DataTrustOBM 3 2. Backing up the Hyper-V virtual machine files
Using DataTrust Secure Online Backup To Protect Your Hyper-V Virtual Environment. 1 P a g e Table of Contents: 1. Backing Up the Guest OS with DataTrustOBM 3 2. Backing up the Hyper-V virtual machine files
Microsoft Visual Basic Scripting Edition and Microsoft Windows Script Host Essentials
 Microsoft Visual Basic Scripting Edition and Microsoft Windows Script Host Essentials 2433: Microsoft Visual Basic Scripting Edition and Microsoft Windows Script Host Essentials (3 Days) About this Course
Microsoft Visual Basic Scripting Edition and Microsoft Windows Script Host Essentials 2433: Microsoft Visual Basic Scripting Edition and Microsoft Windows Script Host Essentials (3 Days) About this Course
WebSphere Business Monitor
 WebSphere Business Monitor Monitor models 2010 IBM Corporation This presentation should provide an overview of monitor models in WebSphere Business Monitor. WBPM_Monitor_MonitorModels.ppt Page 1 of 25
WebSphere Business Monitor Monitor models 2010 IBM Corporation This presentation should provide an overview of monitor models in WebSphere Business Monitor. WBPM_Monitor_MonitorModels.ppt Page 1 of 25
The Benefits of Verio Virtual Private Servers (VPS) Verio Virtual Private Server (VPS) CONTENTS
 Performance, Verio FreeBSD Virtual Control, Private Server and (VPS) Security: v3 CONTENTS Why outsource hosting?... 1 Some alternative approaches... 2 Linux VPS and FreeBSD VPS overview... 3 Verio VPS
Performance, Verio FreeBSD Virtual Control, Private Server and (VPS) Security: v3 CONTENTS Why outsource hosting?... 1 Some alternative approaches... 2 Linux VPS and FreeBSD VPS overview... 3 Verio VPS
nitrobit update server
 nitrobit update server Administrator's Guide 2011 analytiq consulting gmbh. All rights reserved. Page 2 nitrobit update server Administrator's Guide Content I. Introduction... 4 Overview... 4 Components
nitrobit update server Administrator's Guide 2011 analytiq consulting gmbh. All rights reserved. Page 2 nitrobit update server Administrator's Guide Content I. Introduction... 4 Overview... 4 Components
Embed BA into Web Applications
 Embed BA into Web Applications This document supports Pentaho Business Analytics Suite 5.0 GA and Pentaho Data Integration 5.0 GA, documentation revision June 15, 2014, copyright 2014 Pentaho Corporation.
Embed BA into Web Applications This document supports Pentaho Business Analytics Suite 5.0 GA and Pentaho Data Integration 5.0 GA, documentation revision June 15, 2014, copyright 2014 Pentaho Corporation.
UNIVERSITY OF CALIFORNIA, DAVIS Department of Electrical and Computer Engineering. EEC180B Lab 7: MISP Processor Design Spring 1995
 UNIVERSITY OF CALIFORNIA, DAVIS Department of Electrical and Computer Engineering EEC180B Lab 7: MISP Processor Design Spring 1995 Objective: In this lab, you will complete the design of the MISP processor,
UNIVERSITY OF CALIFORNIA, DAVIS Department of Electrical and Computer Engineering EEC180B Lab 7: MISP Processor Design Spring 1995 Objective: In this lab, you will complete the design of the MISP processor,
by Jonathan Kohl and Paul Rogers 40 BETTER SOFTWARE APRIL 2005 www.stickyminds.com
 Test automation of Web applications can be done more effectively by accessing the plumbing within the user interface. Here is a detailed walk-through of Watir, a tool many are using to check the pipes.
Test automation of Web applications can be done more effectively by accessing the plumbing within the user interface. Here is a detailed walk-through of Watir, a tool many are using to check the pipes.
Basic Unix/Linux 1. Software Testing Interview Prep
 Basic Unix/Linux 1 Programming Fundamentals and Concepts 2 1. What is the difference between web application and client server application? Client server application is designed typically to work in a
Basic Unix/Linux 1 Programming Fundamentals and Concepts 2 1. What is the difference between web application and client server application? Client server application is designed typically to work in a
LLVMLinux: Embracing the Dragon
 LLVMLinux: Embracing the Dragon Presented by: Behan Webster ( lead) Presentation Date: 2014.08.22 Clang/LLVM LLVM is a Toolchain Toolkit (libraries from which compilers and related technologies can be
LLVMLinux: Embracing the Dragon Presented by: Behan Webster ( lead) Presentation Date: 2014.08.22 Clang/LLVM LLVM is a Toolchain Toolkit (libraries from which compilers and related technologies can be
IBM TSM DISASTER RECOVERY BEST PRACTICES WITH EMC DATA DOMAIN DEDUPLICATION STORAGE
 White Paper IBM TSM DISASTER RECOVERY BEST PRACTICES WITH EMC DATA DOMAIN DEDUPLICATION STORAGE Abstract This white paper focuses on recovery of an IBM Tivoli Storage Manager (TSM) server and explores
White Paper IBM TSM DISASTER RECOVERY BEST PRACTICES WITH EMC DATA DOMAIN DEDUPLICATION STORAGE Abstract This white paper focuses on recovery of an IBM Tivoli Storage Manager (TSM) server and explores
T14 Thursday, November 4, 1999 1:30 PM
 Presentation Notes Paper Bio Return to Main Menu PRESENTATION T14 Thursday, November 4, 1999 1:30 PM SYSTEM TESTING STRATEGIES FOR HIGHLY AVAILABLE CLUSTERED SYSTEMS Subbarao Jagannatha Sun Microsystems
Presentation Notes Paper Bio Return to Main Menu PRESENTATION T14 Thursday, November 4, 1999 1:30 PM SYSTEM TESTING STRATEGIES FOR HIGHLY AVAILABLE CLUSTERED SYSTEMS Subbarao Jagannatha Sun Microsystems
VirtualCenter Database Maintenance VirtualCenter 2.0.x and Microsoft SQL Server
 Technical Note VirtualCenter Database Maintenance VirtualCenter 2.0.x and Microsoft SQL Server This document discusses ways to maintain the VirtualCenter database for increased performance and manageability.
Technical Note VirtualCenter Database Maintenance VirtualCenter 2.0.x and Microsoft SQL Server This document discusses ways to maintain the VirtualCenter database for increased performance and manageability.
Cross-Platform. Mac OS X ЧЯУ
 Cross-Platform in C++ Mac OS X ЧЯУ Syd Logan Л А- зу Upper Saddle River, NJ Boston Indianapolis San Francisco New York Toronto Montreal London Munich Pans Madrid Cape Town Sydney Tokyo Singapore Mexico
Cross-Platform in C++ Mac OS X ЧЯУ Syd Logan Л А- зу Upper Saddle River, NJ Boston Indianapolis San Francisco New York Toronto Montreal London Munich Pans Madrid Cape Town Sydney Tokyo Singapore Mexico
NVIDIA Tools For Profiling And Monitoring. David Goodwin
 NVIDIA Tools For Profiling And Monitoring David Goodwin Outline CUDA Profiling and Monitoring Libraries Tools Technologies Directions CScADS Summer 2012 Workshop on Performance Tools for Extreme Scale
NVIDIA Tools For Profiling And Monitoring David Goodwin Outline CUDA Profiling and Monitoring Libraries Tools Technologies Directions CScADS Summer 2012 Workshop on Performance Tools for Extreme Scale
Developing tests for the KVM autotest framework
 Lucas Meneghel Rodrigues lmr@redhat.com KVM Forum 2010 August 9, 2010 1 Automated testing Autotest The wonders of virtualization testing 2 How KVM autotest solves the original problem? Features Test structure
Lucas Meneghel Rodrigues lmr@redhat.com KVM Forum 2010 August 9, 2010 1 Automated testing Autotest The wonders of virtualization testing 2 How KVM autotest solves the original problem? Features Test structure
An Embedded Wireless Mini-Server with Database Support
 An Embedded Wireless Mini-Server with Database Support Hungchi Chang, Sy-Yen Kuo and Yennun Huang Department of Electrical Engineering National Taiwan University Taipei, Taiwan, R.O.C. Abstract Due to
An Embedded Wireless Mini-Server with Database Support Hungchi Chang, Sy-Yen Kuo and Yennun Huang Department of Electrical Engineering National Taiwan University Taipei, Taiwan, R.O.C. Abstract Due to
FreeForm Designer. Phone: +972-9-8309999 Fax: +972-9-8309998 POB 8792, Natanya, 42505 Israel www.autofont.com. Document2
 FreeForm Designer FreeForm Designer enables designing smart forms based on industry-standard MS Word editing features. FreeForm Designer does not require any knowledge of or training in programming languages
FreeForm Designer FreeForm Designer enables designing smart forms based on industry-standard MS Word editing features. FreeForm Designer does not require any knowledge of or training in programming languages
BMC BladeLogic Client Automation Installation Guide
 BMC BladeLogic Client Automation Installation Guide Supporting BMC BladeLogic Client Automation 8.2.02 January 2013 www.bmc.com Contacting BMC Software You can access the BMC Software website at http://www.bmc.com.
BMC BladeLogic Client Automation Installation Guide Supporting BMC BladeLogic Client Automation 8.2.02 January 2013 www.bmc.com Contacting BMC Software You can access the BMC Software website at http://www.bmc.com.
10 STEPS TO YOUR FIRST QNX PROGRAM. QUICKSTART GUIDE Second Edition
 10 STEPS TO YOUR FIRST QNX PROGRAM QUICKSTART GUIDE Second Edition QNX QUICKSTART GUIDE A guide to help you install and configure the QNX Momentics tools and the QNX Neutrino operating system, so you can
10 STEPS TO YOUR FIRST QNX PROGRAM QUICKSTART GUIDE Second Edition QNX QUICKSTART GUIDE A guide to help you install and configure the QNX Momentics tools and the QNX Neutrino operating system, so you can
2.2 INFORMATION SERVICES Documentation of computer services, computer system management, and computer network management.
 3 Audit Trail Files Data generated during the creation of a master file or database, used to validate a master file or database during a processing cycle. GS 14020 Retain for 3 backup cycles Computer Run
3 Audit Trail Files Data generated during the creation of a master file or database, used to validate a master file or database during a processing cycle. GS 14020 Retain for 3 backup cycles Computer Run
Fundamentals of LoadRunner 9.0 (2 Days)
 Fundamentals of LoadRunner 9.0 (2 Days) Quality assurance engineers New users of LoadRunner who need to load test their applications and/or executives who will be involved in any part of load testing.
Fundamentals of LoadRunner 9.0 (2 Days) Quality assurance engineers New users of LoadRunner who need to load test their applications and/or executives who will be involved in any part of load testing.
Adobe Flash Player and Adobe AIR security
 Adobe Flash Player and Adobe AIR security Both Adobe Flash Platform runtimes Flash Player and AIR include built-in security and privacy features to provide strong protection for your data and privacy,
Adobe Flash Player and Adobe AIR security Both Adobe Flash Platform runtimes Flash Player and AIR include built-in security and privacy features to provide strong protection for your data and privacy,
Introduction to Automated Testing
 Introduction to Automated Testing What is Software testing? Examination of a software unit, several integrated software units or an entire software package by running it. execution based on test cases
Introduction to Automated Testing What is Software testing? Examination of a software unit, several integrated software units or an entire software package by running it. execution based on test cases
Essential Visual Studio Team System
 Essential Visual Studio Team System Introduction This course helps software development teams successfully deliver complex software solutions with Microsoft Visual Studio Team System (VSTS). Discover how
Essential Visual Studio Team System Introduction This course helps software development teams successfully deliver complex software solutions with Microsoft Visual Studio Team System (VSTS). Discover how
Software Engineering for LabVIEW Applications. Elijah Kerry LabVIEW Product Manager
 Software Engineering for LabVIEW Applications Elijah Kerry LabVIEW Product Manager 1 Ensuring Software Quality and Reliability Goals 1. Deliver a working product 2. Prove it works right 3. Mitigate risk
Software Engineering for LabVIEW Applications Elijah Kerry LabVIEW Product Manager 1 Ensuring Software Quality and Reliability Goals 1. Deliver a working product 2. Prove it works right 3. Mitigate risk
My DevOps Journey by Billy Foss, Engineering Services Architect, CA Technologies
 About the author My DevOps Journey by Billy Foss, Engineering Services Architect, CA Technologies I am going to take you through the journey that my team embarked on as we looked for ways to automate processes,
About the author My DevOps Journey by Billy Foss, Engineering Services Architect, CA Technologies I am going to take you through the journey that my team embarked on as we looked for ways to automate processes,
Web Services for Management Perl Library VMware ESX Server 3.5, VMware ESX Server 3i version 3.5, and VMware VirtualCenter 2.5
 Technical Note Web Services for Management Perl Library VMware ESX Server 3.5, VMware ESX Server 3i version 3.5, and VMware VirtualCenter 2.5 In the VMware Infrastructure (VI) Perl Toolkit 1.5, VMware
Technical Note Web Services for Management Perl Library VMware ESX Server 3.5, VMware ESX Server 3i version 3.5, and VMware VirtualCenter 2.5 In the VMware Infrastructure (VI) Perl Toolkit 1.5, VMware
Using Code Coverage and Multi-event Profiler in Code Composer Studio v2.3 for Robustness and Efficiency Analyses
 Application Report SPRA868A April 2004 Using Code Coverage and Multi-event Profiler in Code Composer Studio v2.3 for Robustness and Efficiency Analyses Amit Rangari, N.Pradeep Software Development Systems
Application Report SPRA868A April 2004 Using Code Coverage and Multi-event Profiler in Code Composer Studio v2.3 for Robustness and Efficiency Analyses Amit Rangari, N.Pradeep Software Development Systems
Getting Started Guide
 Getting Started Guide Operations Center 5.0 March 3, 2014 Legal Notices THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE AGREEMENT
Getting Started Guide Operations Center 5.0 March 3, 2014 Legal Notices THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE AGREEMENT
SVN Authentication and Authorization
 Admin Guide SVN Authentication and Authorization Authentication and Authorization of SVN Users via Active Directory and OpenLDAP Gérard Bieli, Christian Haller Windisch, 14th August 2009 Contents 1 Prerequisites
Admin Guide SVN Authentication and Authorization Authentication and Authorization of SVN Users via Active Directory and OpenLDAP Gérard Bieli, Christian Haller Windisch, 14th August 2009 Contents 1 Prerequisites
Manual NLTP Activities Reporting Tool (web release version 1.0)
 Manual NLTP Activities Reporting Tool (web release version 1.0) Contents 1 Introduction...- 3-2 Before Running the Application...- 3-3 Starting up...- 3 - a. Opening/Saving the Tool...- 3 - b. Opening
Manual NLTP Activities Reporting Tool (web release version 1.0) Contents 1 Introduction...- 3-2 Before Running the Application...- 3-3 Starting up...- 3 - a. Opening/Saving the Tool...- 3 - b. Opening
IBM Tivoli Network Manager 3.8
 IBM Tivoli Network Manager 3.8 Configuring initial discovery 2010 IBM Corporation Welcome to this module for IBM Tivoli Network Manager 3.8 Configuring initial discovery. configuring_discovery.ppt Page
IBM Tivoli Network Manager 3.8 Configuring initial discovery 2010 IBM Corporation Welcome to this module for IBM Tivoli Network Manager 3.8 Configuring initial discovery. configuring_discovery.ppt Page
SQL Server Instance-Level Benchmarks with DVDStore
 SQL Server Instance-Level Benchmarks with DVDStore Dell developed a synthetic benchmark tool back that can run benchmark tests against SQL Server, Oracle, MySQL, and PostgreSQL installations. It is open-sourced
SQL Server Instance-Level Benchmarks with DVDStore Dell developed a synthetic benchmark tool back that can run benchmark tests against SQL Server, Oracle, MySQL, and PostgreSQL installations. It is open-sourced
Performance Management Platform
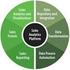 Open EMS Suite by Nokia Performance Management Platform Functional Overview Version 1.4 Nokia Siemens Networks 1 (16) Performance Management Platform The information in this document is subject to change
Open EMS Suite by Nokia Performance Management Platform Functional Overview Version 1.4 Nokia Siemens Networks 1 (16) Performance Management Platform The information in this document is subject to change
Table of Contents. The RCS MINI HOWTO
 Table of Contents The RCS MINI HOWTO...1 Robert Kiesling...1 1. Overview of RCS...1 2. System requirements...1 3. Compiling RCS from Source...1 4. Creating and maintaining archives...1 5. ci(1) and co(1)...1
Table of Contents The RCS MINI HOWTO...1 Robert Kiesling...1 1. Overview of RCS...1 2. System requirements...1 3. Compiling RCS from Source...1 4. Creating and maintaining archives...1 5. ci(1) and co(1)...1
WebSphere Commerce V7 Feature pack 1
 WebSphere Commerce V7 Feature pack 1 Brazil starter store 2010 IBM Corporation This presentation provides an overview of the Brazil starter store in WebSphere Commerce V7.0 feature pack 1. Table of content
WebSphere Commerce V7 Feature pack 1 Brazil starter store 2010 IBM Corporation This presentation provides an overview of the Brazil starter store in WebSphere Commerce V7.0 feature pack 1. Table of content
A Test Suite for Basic CWE Effectiveness. Paul E. Black. paul.black@nist.gov. http://samate.nist.gov/
 A Test Suite for Basic CWE Effectiveness Paul E. Black paul.black@nist.gov http://samate.nist.gov/ Static Analysis Tool Exposition (SATE V) News l We choose test cases by end of May l Tool output uploaded
A Test Suite for Basic CWE Effectiveness Paul E. Black paul.black@nist.gov http://samate.nist.gov/ Static Analysis Tool Exposition (SATE V) News l We choose test cases by end of May l Tool output uploaded
Libmonitor: A Tool for First-Party Monitoring
 Libmonitor: A Tool for First-Party Monitoring Mark W. Krentel Dept. of Computer Science Rice University 6100 Main St., Houston, TX 77005 krentel@rice.edu ABSTRACT Libmonitor is a library that provides
Libmonitor: A Tool for First-Party Monitoring Mark W. Krentel Dept. of Computer Science Rice University 6100 Main St., Houston, TX 77005 krentel@rice.edu ABSTRACT Libmonitor is a library that provides
Red Hat Network Satellite Management and automation of your Red Hat Enterprise Linux environment
 Red Hat Network Satellite Management and automation of your Red Hat Enterprise Linux environment WHAT IS IT? Red Hat Network (RHN) Satellite server is an easy-to-use, advanced systems management platform
Red Hat Network Satellite Management and automation of your Red Hat Enterprise Linux environment WHAT IS IT? Red Hat Network (RHN) Satellite server is an easy-to-use, advanced systems management platform
