Hard Drive Data Security. Chris Bilello Director, Business Development Konica Minolta Business Solutions U.S.A., Inc.
|
|
|
- Sandra Patrick
- 8 years ago
- Views:
Transcription
1 Hard Drive Data Security Chris Bilello Director, Business Development Konica Minolta Business Solutions U.S.A., Inc.
2 Konica Minolta Security Features On April 19, CBS News aired a story that highlighted the public s fear that confidential and private data could be stolen from the hard drive of an MFP During that broadcast, a senior executive at Sharp stated that their products hard drives could be automatically erased by purchasing a $500 security option CBS said that the average American does not want to pay for such protection At Konica Minolta, we re glad to hear that!
3 Konica Minolta Security Features Konica Minolta s standard equipment includes several different ways to protect the data on the bizhub MFP s hard drive
4 One Important Statement from the Story is False! During the broadcast, the following was heard: Nearly every digital copier built since 2002 contains a hard di drive - like the one on your personal computer - storing an image of every document copied, scanned, or ed by the machine. Konica Minolta refutes this statement as completely inaccurate for our MFP technology It is misleading and sensationalistic
5 Konica Minolta MFPs do NOT store copies of print, scan, fax or copy jobs on the MFP s hard drive
6 How it Really Works Print, scan, copy, and fax jobs are normally processed in the MFP s volatile Random Access Memory (RAM) When the MFP is turned off, any remnants of a job processed in RAM are gone forever and cannot be brought back
7 What kind of jobs are stored on the Konica Minolta MFP Hard Drive? Jobs scanned or printed to the BOX feature Think of boxes as electronic folders on a hard drive Scan to Box Public Private Print to Box Public Private Secure Print Box Incoming fax jobs routed to a BOX These functions have to be enabled by MFP Administrators The device can be programmed to overwrite any documents residing in ANY Box after a certain period of time Users should be trained on these features
8 Important Fact Documents cannot be stored unknowingly or by accident
9 How do we protect documents stored in the MFP s HDD? Color bizhubs come standard with a hard drive An HDD may be required for a black & white system The HDD is protected against unauthorized access to its data by the following methods: Automatic Job Overwrite (Temporary Data Overwrite) HDD Encryption HDD Lock Password Automatic Deletion of Jobs Stored in an electronic USER BOX HDD Overwrite (HDD Sanitizing) The administrator of the device has the capability and flexibility to turn each function ON or OFF The default setting for each function is OFF
10 Konica Minolta Hard Drive Data Protection These functions are STANDARD on current and recent models: Automatic Job Overwrite (Temporary Data Overwrite) HDD Encryption HDD Lock Password Automatic Deletion of Jobs Stored in an electronic HDD BOX HDD Overwrite (HDD Sanitizing) Hard Drive Encryption is standard on the current office color line: C220, C280, C360, C452, C552, C652 It is an option on the monochrome and previous generation office color MFPs
11 Hard Drive Standard Security Feature HDD Job Overwrite (Temporary Data Overwrite) The data on the hard drive can be automatically overwritten when: A job is printed out A job is deleted from the User Box Ordinary Job Deletion bizhub Job Deletion
12 Job Overwrite (continued) Automatic HDD Job Overwrite (Temporary Data Overwrite) You can select from 2 modes: Mode 1: Overwrite with 0x00 Mode 2 (3 times overwrite): Overwrite with 0x00 Overwrite with 0xff Overwrite with the letter A (Dx61) Verify These 2 modes support the following standards: US Navy (NAVSO P ) (Mode 1) Department of Defense (DoD M) (Mode 1) US Air Force (AFSSI5020) (Mode 2)
13 Turn ON Automatic Hard Drive Overwrite
14 Set Timers for Automatic Document Deletion from the bizhub s Hard Drive
15 Hard Drive Encryption Electronic documents can be stored in a password-protected box on the hard drive If an organization is concerned about the security of such data, it can be protected by encrypting it with the HD encryption kit The stored data is encrypted using the Advanced Encryption Standard (AES) supporting a 128-bit key Once a hard drive is encrypted, its data cannot be read, even if the HDD is removed from the MFP Standard on the C220, C280, C360, C452, C552, C652
16 Set the Hard Drive Encryption Key
17 More Standard Hard Disk Security HDD Lock Password It s not easy to remove the hard drive from an MFP, however as an extra precaution The bizhub hard disk can be locked with a password (20 alphanumeric characters). The lock password makes it impossible to read or access the hard drive s data if the drive is removed from the device and installed on/connected to a computer or a different MFP The hard drive is locked down and cannot be enabled without the 20 character alphanumeric passcode If someone steals the hard drive from a bizhub MFP: It s a nuisance It s inconvenient Unless they gain access to the password, it s NOT a security threat!
18 Lock Down the Hard Drive
19 Standard HDD Overwrite (HDD Sanitizing) Prior to disposal or relocation of a machine, an administrator can overwrite the entire hard disk so that all of its data is completely scrubbed
20 HDD Overwrite (HDD Sanitizing) 8 Methods
21 HDD Overwrite (HDD Sanitizing) The 8 overwriting methods meet the following standards: Mode 1 Japan Electronic and Information Technology Association Russian Standard (GOST) Mode 2 Current NSA (National Security Agency) Standard Mode 3 National Computer Security Center (NCSC-TG- 025) US Navy (NAVSO P ) Department of Defense (DoD M) Mode 4 Army Regulations (AR380-19) Mode 5 Former NSA Standard d Mode 7 German Standard (VISTR) Mode 8 US Air Force (AFSSI5020)
22 Choose the Hard Drive Sanitize Method
23 Current & Recent Models Support Monochrome bizhub 200, 250, , 280, , 420, , 421, , , , 1051, 1200 (confirmed 8 modes of hard drive sanitization) Color bizhub C250, C252, C351, C451 C203, C253, C300, C353 C450, C550, C650 C220, C280, C360 C452, C552, C652 C5501, C6501 (confirmed 8 modes of hard drive sanitization)
24 Additional Information From the Konica Minolta public web site Security White Paper BLI Security Report Link to Common Criteria ISO Documentation Other Security related information Security manuals for bizhub MFP models
This is an example of MFP password entry in the administration mode for hard-disk protection:
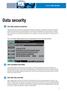 Data security Hard disk password protection The built-in hard disk of the MFP is automatically protected by a password. This password is stored in the hard disk BIOS and prevents access to the hard disk
Data security Hard disk password protection The built-in hard disk of the MFP is automatically protected by a password. This password is stored in the hard disk BIOS and prevents access to the hard disk
Enabling bizhub HDD Security Features
 Hard Disk Drive Security Enabling bizhub HDD Security Features bizhub C652/C552/C452 bizhub C360/C280/C220 bizhub 423/363/283/223 1 Enabling bizhub HDD Security - Overview This guide is intended to assist
Hard Disk Drive Security Enabling bizhub HDD Security Features bizhub C652/C552/C452 bizhub C360/C280/C220 bizhub 423/363/283/223 1 Enabling bizhub HDD Security - Overview This guide is intended to assist
Fundamentals of security. Information Security White Paper
 Fundamentals of security Information Security White Paper Security, Fundamentals of security Fundamentals of security This fundamentals of security guide is a living document this means it is continually
Fundamentals of security Information Security White Paper Security, Fundamentals of security Fundamentals of security This fundamentals of security guide is a living document this means it is continually
Ricoh Security Solutions Comprehensive protection for your documents and information. ecure. proven. trusted
 Ricoh Security Solutions Comprehensive protection for your documents and information ecure proven trusted RICOH Security Solutions Depend on Ricoh for comprehensive document security. RICOH understands
Ricoh Security Solutions Comprehensive protection for your documents and information ecure proven trusted RICOH Security Solutions Depend on Ricoh for comprehensive document security. RICOH understands
User s Guide [Security Operations]
![User s Guide [Security Operations] User s Guide [Security Operations]](/thumbs/24/3393053.jpg) User s Guide [Security Operations] 010. 6 Ver. 1.01 Contents 1 Security 1.1 Introduction... 1- Compliance with the ISO15408 Standard... 1- Operating Precautions... 1- INSTALLATION CHECKLIST... 1-3 1. Security
User s Guide [Security Operations] 010. 6 Ver. 1.01 Contents 1 Security 1.1 Introduction... 1- Compliance with the ISO15408 Standard... 1- Operating Precautions... 1- INSTALLATION CHECKLIST... 1-3 1. Security
Fundamentals of security. Whitepaper. Information Security Whitepaper. *Plesse refer to page 6 in regard to the CCRA certification mark.
 Fundamentals of security Whitepaper * Information Security Whitepaper *Plesse refer to page 6 in regard to the CCRA certification mark. Security, Fundamentals of security Fundamentals of security This
Fundamentals of security Whitepaper * Information Security Whitepaper *Plesse refer to page 6 in regard to the CCRA certification mark. Security, Fundamentals of security Fundamentals of security This
fundamentals of security Whitepaper whitepaper
 fundamentals of security Whitepaper whitepaper SECURITY Fundamentals of security This fundamentals of security guide is a living document this means it is continually updated. This guide is intended solely
fundamentals of security Whitepaper whitepaper SECURITY Fundamentals of security This fundamentals of security guide is a living document this means it is continually updated. This guide is intended solely
AMENDMENT #47 T-437A 06-X-37720 COPIER HARD DRIVE SECURITY -AGENCY RESPONSIBILITIES AND PROCEDURES -CONTRACTOR OPTIONS AND PRICING INFORMATION
 State of New Jersey DEPARTMENT OF THE TREASURY CHRIS CHRISTIE DIVISION OF PURCHASE AND PROPERTY ANDREW P. SIDAMON-ERISTOFF Governor PURCHASE BUREAU State Treasurer P. O. BOX 230 KIM GUADAGNO Trenton, New
State of New Jersey DEPARTMENT OF THE TREASURY CHRIS CHRISTIE DIVISION OF PURCHASE AND PROPERTY ANDREW P. SIDAMON-ERISTOFF Governor PURCHASE BUREAU State Treasurer P. O. BOX 230 KIM GUADAGNO Trenton, New
HP FutureSmart Firmware Device Hard Disk Security
 HP FutureSmart Firmware Device Hard Disk Security Summary: This document discusses hard disk security for HP FutureSmart Firmware printing devices. Contents: Overview... 2 Secure Erase Commands... 2 1.
HP FutureSmart Firmware Device Hard Disk Security Summary: This document discusses hard disk security for HP FutureSmart Firmware printing devices. Contents: Overview... 2 Secure Erase Commands... 2 1.
Copier & MFD under ISO 15408 scheme. 28 th, September, 2005 Konica Minolta Business Technologies. Inc. Takashi Ito
 Copier & MFD under ISO 15408 scheme 28 th, September, 2005 Konica Minolta Business Technologies. Inc. Takashi Ito Contents Copier & MFD; its Market and CC Certification Growth of copier/mfd market (1)
Copier & MFD under ISO 15408 scheme 28 th, September, 2005 Konica Minolta Business Technologies. Inc. Takashi Ito Contents Copier & MFD; its Market and CC Certification Growth of copier/mfd market (1)
SECURITY WITHOUT SACRIFICE
 SECURITY WITHOUT SACRIFICE Konica Minolta security standards INFORMATION SECURITY Industry-leading standard security In the digital age, we have seen global communications undergo unparalleled growth and
SECURITY WITHOUT SACRIFICE Konica Minolta security standards INFORMATION SECURITY Industry-leading standard security In the digital age, we have seen global communications undergo unparalleled growth and
User Authentication Job Tracking Fax Transmission via RightFax Server Secure Printing Functions HDD/Memory Security Fax to Ethernet Connection Data
 User Authentication Job Tracking Fax Transmission via RightFax Server Secure Printing Functions HDD/Memory Security Fax to Ethernet Connection Data Security Kit Outline How do you protect your critical
User Authentication Job Tracking Fax Transmission via RightFax Server Secure Printing Functions HDD/Memory Security Fax to Ethernet Connection Data Security Kit Outline How do you protect your critical
User s Guide. Security Operations. 2013. 5 Ver. 1.02
 User s Guide Security Operations 013. 5 Ver. 1.0 Contents 1 Security 1.1 Introduction... 1- Compliance with the ISO15408 Standard... 1- Operating Precautions... 1- INSTALLATION CHECKLIST... 1-3 1. Security
User s Guide Security Operations 013. 5 Ver. 1.0 Contents 1 Security 1.1 Introduction... 1- Compliance with the ISO15408 Standard... 1- Operating Precautions... 1- INSTALLATION CHECKLIST... 1-3 1. Security
Data Security Kit (E) Operation Guide (for Printer)
 Data Security Kit (E) Operation Guide (for Printer) Introduction This Operation Guide explains the procedures for installing and operating the optional Data Security Kit (E) (hereinafter called Security
Data Security Kit (E) Operation Guide (for Printer) Introduction This Operation Guide explains the procedures for installing and operating the optional Data Security Kit (E) (hereinafter called Security
User Authentication Job Tracking Fax Transmission via RightFax Server Secure Printing Functions HDD/Memory Security Fax to Ethernet Connection
 User Authentication Job Tracking Fax Transmission via RightFax Server Secure Printing Functions HDD/Memory Security Fax to Ethernet Connection Outline How do you protect your critical confidential data?
User Authentication Job Tracking Fax Transmission via RightFax Server Secure Printing Functions HDD/Memory Security Fax to Ethernet Connection Outline How do you protect your critical confidential data?
Security Solutions. Concerned about information security? You should be!
 Security Solutions Concerned about information security? You should be! Various security threats surrounding the office Ricoh s proposal for a security management system. Information technology is the
Security Solutions Concerned about information security? You should be! Various security threats surrounding the office Ricoh s proposal for a security management system. Information technology is the
SECURITY. Konica Minolta s industry-leading security standards SECURITY
 Konica Minolta s industry-leading security standards In the digital age, we have seen global communications undergo unprecedented growth and the potential for security breaches has grown in parallel. In
Konica Minolta s industry-leading security standards In the digital age, we have seen global communications undergo unprecedented growth and the potential for security breaches has grown in parallel. In
ADVANCED SOLUTIONS FOR. Financial Services. compliance and security effective cost control increased efficiency improved customer information
 ADVANCED SOLUTIONS FOR Financial Services compliance and security effective cost control increased efficiency improved customer information New solutions for today s financial services challenges. Processing
ADVANCED SOLUTIONS FOR Financial Services compliance and security effective cost control increased efficiency improved customer information New solutions for today s financial services challenges. Processing
Simple defence for your business
 Simple defence for your business SECURITY Canon (UK) Ltd Woodhatch, Reigate Surrey RH2 8BF Telephone No: 08000 353535 Facsimile No: 01737 220022 www.canon.co.uk Canon Ireland Arena Road, Sandyford Industrial
Simple defence for your business SECURITY Canon (UK) Ltd Woodhatch, Reigate Surrey RH2 8BF Telephone No: 08000 353535 Facsimile No: 01737 220022 www.canon.co.uk Canon Ireland Arena Road, Sandyford Industrial
Lexmark Printers and Multifunction Products: Hard Disk and Non-Volatile Memory Guide
 Lexmark Printers and Multifunction Products: Hard Disk and Non-Volatile Memory Guide This guide applies to the following Lexmark devices: Printers C780 C782 C935 T640 T642 T644 Multifunction Products X646
Lexmark Printers and Multifunction Products: Hard Disk and Non-Volatile Memory Guide This guide applies to the following Lexmark devices: Printers C780 C782 C935 T640 T642 T644 Multifunction Products X646
you can count on! Develop s security standards
 Security you can count on! Develop s security standards Industry-leading security standards In today s business company data has to cross a lot of different data highways. These different highways offer
Security you can count on! Develop s security standards Industry-leading security standards In today s business company data has to cross a lot of different data highways. These different highways offer
Copier Data Security:
 Copier Data Security: A Guide for Businesses Federal Trade Commission business.ftc.gov Does your company keep sensitive data Social Security numbers, credit reports, account numbers, health records, or
Copier Data Security: A Guide for Businesses Federal Trade Commission business.ftc.gov Does your company keep sensitive data Social Security numbers, credit reports, account numbers, health records, or
Copier Data Security:
 Copier Data Security: A Guide for Businesses Federal Trade Commission business.ftc.gov Does your company keep sensitive data Social Security numbers, credit reports, account numbers, health records, or
Copier Data Security: A Guide for Businesses Federal Trade Commission business.ftc.gov Does your company keep sensitive data Social Security numbers, credit reports, account numbers, health records, or
Canon imagerunner Hard Disk Drive Data Security Options. Data Encryption and Overwrite
 Canon imagerunner Hard Disk Drive Data Security Options Data Encryption and Overwrite Canon imagerunner Hard Disk Drive Data Security Kits Powerful protection for your most important information. Canon
Canon imagerunner Hard Disk Drive Data Security Options Data Encryption and Overwrite Canon imagerunner Hard Disk Drive Data Security Kits Powerful protection for your most important information. Canon
SeCUritY. Safeguarding information Within Documents and Devices. imagerunner ADVANCE Solutions. ADVANCE to Canon MFP security solutions.
 imagerunner ADVANCE Solutions SeCUritY Safeguarding information Within Documents and Devices ADVANCE to Canon MFP security solutions. Whether your business relies on paper documents, electronic documents,
imagerunner ADVANCE Solutions SeCUritY Safeguarding information Within Documents and Devices ADVANCE to Canon MFP security solutions. Whether your business relies on paper documents, electronic documents,
SOLUTIONS FOR LEGAL PROFESSIONALS
 SOLUTIONS FOR LEGAL PROFESSIONALS The verdict is in: legal professionals trust Konica Minolta. Our EnvisionIT Legal solutions assist legal departments of all sizes envision how they can work smarter and
SOLUTIONS FOR LEGAL PROFESSIONALS The verdict is in: legal professionals trust Konica Minolta. Our EnvisionIT Legal solutions assist legal departments of all sizes envision how they can work smarter and
Common Criteria Certification for Samsung Multifunction Printers
 Common Criteria Certification for Samsung Multifunction Printers WHITE PAPER Common Criteria Certification for Samsung Multifunction Printers Introduction This white paper describes the Common Criteria
Common Criteria Certification for Samsung Multifunction Printers WHITE PAPER Common Criteria Certification for Samsung Multifunction Printers Introduction This white paper describes the Common Criteria
HIPAA Security Compliance for Konica Minolta bizhub MFPs
 HIPAA Security Compliance for Konica Minolta bizhub MFPs Table of Contents Introduction... 1 What is HIPAA?... 1 HIPAA Security Standards that are applicable to Konica Minolta bizhub Multi-Functional Printers...
HIPAA Security Compliance for Konica Minolta bizhub MFPs Table of Contents Introduction... 1 What is HIPAA?... 1 HIPAA Security Standards that are applicable to Konica Minolta bizhub Multi-Functional Printers...
Step by step guide how to password protect your USB flash drive
 Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
Secure Installation and Operation of Your Xerox Multi-Function Device. Version 1.0 August 6, 2012
 Secure Installation and Operation of Your Xerox Multi-Function Device Version 1.0 August 6, 2012 Secure Installation and Operation of Your Xerox Multi-Function Device Purpose and Audience This document
Secure Installation and Operation of Your Xerox Multi-Function Device Version 1.0 August 6, 2012 Secure Installation and Operation of Your Xerox Multi-Function Device Purpose and Audience This document
IMAGER security solutions. Protect Your Business with Sharp s Comprehensive Document Security Solutions
 IMAGER security solutions TM Protect Your Business with Sharp s Comprehensive Document Security Solutions Sharp. Leading the industry with the first Common Criteria Validated Solution for document and
IMAGER security solutions TM Protect Your Business with Sharp s Comprehensive Document Security Solutions Sharp. Leading the industry with the first Common Criteria Validated Solution for document and
Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines
 Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious programs,
Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious programs,
bizhub C754 Series/ C554 Series/C364 Series FULL COLOR PRINTER/COPIER/SCANNER/FAX FAX JOB SHOPS
 bizhub C754 Series/ C554 Series/C364 Series FULL COLOR PRINTER/COPIER/SCANNER/FAX FAX JOB SHOPS table of contents Methods of Faxing... 1 Line Parameter Settings... 4 Fax TX/RX Settings.... 6 Registering
bizhub C754 Series/ C554 Series/C364 Series FULL COLOR PRINTER/COPIER/SCANNER/FAX FAX JOB SHOPS table of contents Methods of Faxing... 1 Line Parameter Settings... 4 Fax TX/RX Settings.... 6 Registering
LAVASOFT FILE SHREDDER FILE SHREDDER
 LAVASOFT FILE SHREDDER FILE SHREDDER SOFTWARE MANUAL Table of Contents Install and Uninstall 1 Install Using a CD 1 Install Using a File 1 Uninstall the Application 1 Activation 2 What is the Subscription
LAVASOFT FILE SHREDDER FILE SHREDDER SOFTWARE MANUAL Table of Contents Install and Uninstall 1 Install Using a CD 1 Install Using a File 1 Uninstall the Application 1 Activation 2 What is the Subscription
Are your multi-function printers a security risk? Here are five key strategies for safeguarding your data
 Are your multi-function printers a security risk? Here are five key strategies for safeguarding your data Printer Security Challenges Executive Summary Security breaches can damage both your operations
Are your multi-function printers a security risk? Here are five key strategies for safeguarding your data Printer Security Challenges Executive Summary Security breaches can damage both your operations
Security for Mac Computers in the Enterprise
 Security for Mac Computers in the Enterprise October, 2012 Mountain Lion 10.8 Contents Introduction 3 Service and App Protection 4 Gatekeeper 4 Digital Signatures and Developer IDs 4 App Sandboxing 5 Mandatory
Security for Mac Computers in the Enterprise October, 2012 Mountain Lion 10.8 Contents Introduction 3 Service and App Protection 4 Gatekeeper 4 Digital Signatures and Developer IDs 4 App Sandboxing 5 Mandatory
Product Security Data Protection: Image Overwrite, Encryption and Disk Removal. Version 10.1 October 22. 2015
 Product Security Data Protection: Image Overwrite, and Removal Version 10.1 October 22. 2015 Disclaimer The information provided in this Xerox Product Response is provided "as is" without warranty of
Product Security Data Protection: Image Overwrite, and Removal Version 10.1 October 22. 2015 Disclaimer The information provided in this Xerox Product Response is provided "as is" without warranty of
Sharp s MFP Security Suite The best of the best in the Market
 Sharp s MFP Security Suite The best of the best in the Market April 2010 Specifications are subject to change without notice. 6 Sharp s MFP Security Suite The best of the best in the Market 2004 2009 Topics
Sharp s MFP Security Suite The best of the best in the Market April 2010 Specifications are subject to change without notice. 6 Sharp s MFP Security Suite The best of the best in the Market 2004 2009 Topics
Legal Notes. Regarding Trademarks. 2011 KYOCERA MITA Corporation
 Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable for any problems arising from
Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable for any problems arising from
Identity Finder: Managing Your Results
 Identity Finder: Managing Your Results The most important part of running Identity Finder is determining the most effective and secure way of managing the search results. Be sure to carefully read and
Identity Finder: Managing Your Results The most important part of running Identity Finder is determining the most effective and secure way of managing the search results. Be sure to carefully read and
Securing MFPs in a CAC Environment: Today and Tomorrow Critical Considerations
 WHITE PAPER Securing MFPs in a CAC Environment: Today and Tomorrow Critical Considerations Contents The Mandate for Increased Security...1 Key Considerations...1 Critical Security Level Considerations...1
WHITE PAPER Securing MFPs in a CAC Environment: Today and Tomorrow Critical Considerations Contents The Mandate for Increased Security...1 Key Considerations...1 Critical Security Level Considerations...1
ADVANCED SOLUTIONS FOR. Healthcare. patient safety quality of care Meaningful Use unstructured documents
 ADVANCED SOLUTIONS FOR Healthcare patient safety quality of care Meaningful Use unstructured documents New solutions for today s healthcare challenges. Few industries are undergoing as many changes as
ADVANCED SOLUTIONS FOR Healthcare patient safety quality of care Meaningful Use unstructured documents New solutions for today s healthcare challenges. Few industries are undergoing as many changes as
Samsung Data Migration v.3.0 Introduction and Installation Guide
 Samsung Data Migration v.3.0 Introduction and Installation Guide 2015.09 (Rev 3.0.) Legal Disclaimer SAMSUNG ELECTRONICS RESERVES THE RIGHT TO CHANGE PRODUCTS, INFORMATION AND SPECIFICATIONS WITHOUT NOTICE.
Samsung Data Migration v.3.0 Introduction and Installation Guide 2015.09 (Rev 3.0.) Legal Disclaimer SAMSUNG ELECTRONICS RESERVES THE RIGHT TO CHANGE PRODUCTS, INFORMATION AND SPECIFICATIONS WITHOUT NOTICE.
bizhub C3850/C3350 USER S GUIDE Applied Functions
 bizhub C3850/C3350 USER S GUIDE Applied Functions Table of contents 1 Using Web Connection 1.1 Web Connection... 1-3 Web Connection... 1-3 Operating environment... 1-3 1.2 Operations required to use this
bizhub C3850/C3350 USER S GUIDE Applied Functions Table of contents 1 Using Web Connection 1.1 Web Connection... 1-3 Web Connection... 1-3 Operating environment... 1-3 1.2 Operations required to use this
User s Guide [Network Scan/Fax/Network Fax Operations]
![User s Guide [Network Scan/Fax/Network Fax Operations] User s Guide [Network Scan/Fax/Network Fax Operations]](/thumbs/27/11353988.jpg) User s Guide [Network Scan/Fax/Network Fax Operations] Table of contents 1 Introduction 1.1 Welcome... 1-2 1.1.1 User's guides... 1-2 1.1.2 User's Guide... 1-3 1.2 Conventions used in this manual... 1-4
User s Guide [Network Scan/Fax/Network Fax Operations] Table of contents 1 Introduction 1.1 Welcome... 1-2 1.1.1 User's guides... 1-2 1.1.2 User's Guide... 1-3 1.2 Conventions used in this manual... 1-4
HDD Password Tool. User s Manual. English
 HDD Password Tool User s Manual English 1 Table of Contents Chapter 1: Introduction... 3 Trademarks... 3 Chapter 2: Required Operating System... 5 - HDD Password Tool for Windows... 5 - HDD Password Tool
HDD Password Tool User s Manual English 1 Table of Contents Chapter 1: Introduction... 3 Trademarks... 3 Chapter 2: Required Operating System... 5 - HDD Password Tool for Windows... 5 - HDD Password Tool
Desktop and Laptop Security Policy
 Desktop and Laptop Security Policy Appendix A Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious
Desktop and Laptop Security Policy Appendix A Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious
Product Security. Data Protection: Image Overwrite, Encryption and Disk Removal
 Product Security Data Protection: Image, Encryption and Disk Removal Version 10.2 July 14, 2016 Disclaimer The information provided in this Xerox Product Response is provided "as is" without warranty of
Product Security Data Protection: Image, Encryption and Disk Removal Version 10.2 July 14, 2016 Disclaimer The information provided in this Xerox Product Response is provided "as is" without warranty of
PageScope Enterprise Suite: interlocking solutions to manage your printer and MFP fleet more productively.
 PageScope Enterprise Suite gives you a powerful set of management tools to get a grip on managing print output, tracking costs and accounts, authenticating users, even customizing individual preferences
PageScope Enterprise Suite gives you a powerful set of management tools to get a grip on managing print output, tracking costs and accounts, authenticating users, even customizing individual preferences
WorkCentre 7425/7428/7435 Security Function Supplementary Guide
 WorkCentre 7425/7428/7435 Security Function Supplementary Guide Version 1.0, August 2009 Table of Contents Before Using the Security Function...5 Preface...5 Security Features...6 Settings for the Secure
WorkCentre 7425/7428/7435 Security Function Supplementary Guide Version 1.0, August 2009 Table of Contents Before Using the Security Function...5 Preface...5 Security Features...6 Settings for the Secure
OPERATION MANUAL. (for image send) LASER PRINTER
 OPERATION MANUAL (for image send) LASER PRINTER INTRODUCTION This manual explains the scanner function, the Internet fax function, and the metadata send function of the machine. To use these functions,
OPERATION MANUAL (for image send) LASER PRINTER INTRODUCTION This manual explains the scanner function, the Internet fax function, and the metadata send function of the machine. To use these functions,
PRIVAZER USER GUIDE Version 1.2 Dated 08 June 2013
 PRIVAZER USER GUIDE Version 1.2 Dated 08 June 2013 CONTENTS Introduction... 3 System Requirements... 4 Install PrivaZer... 5 Uninstall PrivaZer... 9 Scan and Clean C Drive... 11 Scan Options... 20 Cleanup
PRIVAZER USER GUIDE Version 1.2 Dated 08 June 2013 CONTENTS Introduction... 3 System Requirements... 4 Install PrivaZer... 5 Uninstall PrivaZer... 9 Scan and Clean C Drive... 11 Scan Options... 20 Cleanup
bizhub C360 / bizhub C552 / bizhub C220 PKI Card System Control Software Security Target
 bizhub C360 / bizhub C280 / bizhub C220 PKI Card System Control Software This document is a translation of the evaluated and certified security target written in Japanese Version: 1.02 Issued on: June
bizhub C360 / bizhub C280 / bizhub C220 PKI Card System Control Software This document is a translation of the evaluated and certified security target written in Japanese Version: 1.02 Issued on: June
Konica Minolta Unity Document Suite. Powerful integrated document processing. Document capture & distribution Unity Document Suite
 Konica Minolta Unity Document Suite Powerful integrated document processing Document capture & distribution Unity Document Suite Unity Document Suite, document capture & distribution Streamlined document
Konica Minolta Unity Document Suite Powerful integrated document processing Document capture & distribution Unity Document Suite Unity Document Suite, document capture & distribution Streamlined document
technical brief browsing to an installation of HP Web Jetadmin. Internal Access HTTP Port Access List User Profiles HTTP Port
 technical brief in HP Overview HP is a powerful webbased software utility for installing, configuring, and managing networkconnected devices. Since it can install and configure devices, it must be able
technical brief in HP Overview HP is a powerful webbased software utility for installing, configuring, and managing networkconnected devices. Since it can install and configure devices, it must be able
ACER ProShield. Table of Contents
 ACER ProShield Table of Contents Revision History... 3 Legal Notices... 4 Executive Summary... 5 Introduction... 5 Protection against unauthorized access... 6 Why ACER ProShield... 7 ACER ProShield...
ACER ProShield Table of Contents Revision History... 3 Legal Notices... 4 Executive Summary... 5 Introduction... 5 Protection against unauthorized access... 6 Why ACER ProShield... 7 ACER ProShield...
DiamondStream Data Security Policy Summary
 DiamondStream Data Security Policy Summary Overview This document describes DiamondStream s standard security policy for accessing and interacting with proprietary and third-party client data. This covers
DiamondStream Data Security Policy Summary Overview This document describes DiamondStream s standard security policy for accessing and interacting with proprietary and third-party client data. This covers
Security White Paper. for KYOCERA MFPs and Printers
 White Paper for KYOCERA MFPs and Printers 2014 KYOCERA Document Solutions Inc. i Table of Contents 1. INTRODUCTION... 1 2. IDENTIFICATION, AUTHENTICATION AND AUTHORIZATION... 2 2.1 IDENTIFICATION AND AUTHENTICATION...
White Paper for KYOCERA MFPs and Printers 2014 KYOCERA Document Solutions Inc. i Table of Contents 1. INTRODUCTION... 1 2. IDENTIFICATION, AUTHENTICATION AND AUTHORIZATION... 2 2.1 IDENTIFICATION AND AUTHENTICATION...
File Management Utility User Guide
 File Management Utility User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held
File Management Utility User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held
Xerox WorkCentre 5325/5330/5335 Security Function Supplementary Guide
 Xerox WorkCentre 5325/5330/5335 Security Function Supplementary Guide Version 1.0, September 2011 Table of Contents GuideCopyright 2011 by Fuji Xerox Co., Ltd. All rights reserved. 2 Before Using the Security
Xerox WorkCentre 5325/5330/5335 Security Function Supplementary Guide Version 1.0, September 2011 Table of Contents GuideCopyright 2011 by Fuji Xerox Co., Ltd. All rights reserved. 2 Before Using the Security
User Guide. Version Number 3.0
 User Guide Version Number 3.0 Copyright 2003, LSOFT TECHNOLOGIES INC. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work
User Guide Version Number 3.0 Copyright 2003, LSOFT TECHNOLOGIES INC. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work
Cyber Self Assessment
 Cyber Self Assessment According to Protecting Personal Information A Guide for Business 1 a sound data security plan is built on five key principles: 1. Take stock. Know what personal information you have
Cyber Self Assessment According to Protecting Personal Information A Guide for Business 1 a sound data security plan is built on five key principles: 1. Take stock. Know what personal information you have
Security White Paper for KYOCERA MFPs and Printers
 Security White Paper for KYOCERA MFPs and Printers Version 1.04 January 22, 2016 KYOCERA Document Solutions Inc. TABLE OF CONTENTS 1. INTRODUCTION... 4 2. IDENTIFICATION, AUTHENTICATION AND AUTHORIZATION...
Security White Paper for KYOCERA MFPs and Printers Version 1.04 January 22, 2016 KYOCERA Document Solutions Inc. TABLE OF CONTENTS 1. INTRODUCTION... 4 2. IDENTIFICATION, AUTHENTICATION AND AUTHORIZATION...
Xerox Product Security
 Version 1.0 May 7, 2010 Xerox Product Security Data Protection: Image Overwrite, and Removal Disclaimer The information provided in this Xerox Product Response is provided "as is" without warranty of any
Version 1.0 May 7, 2010 Xerox Product Security Data Protection: Image Overwrite, and Removal Disclaimer The information provided in this Xerox Product Response is provided "as is" without warranty of any
MULTIFUNCTIONAL DIGITAL COLOR SYSTEMS / MULTIFUNCTIONAL DIGITAL SYSTEMS. Remote Scan driver Help
 MULTIFUNCTIONAL DIGITAL COLOR SYSTEMS / MULTIFUNCTIONAL DIGITAL SYSTEMS Remote Scan driver Help 2012, 2013 TOSHIBA TEC CORPORATION All rights reserved Under the copyright laws, this manual cannot be reproduced
MULTIFUNCTIONAL DIGITAL COLOR SYSTEMS / MULTIFUNCTIONAL DIGITAL SYSTEMS Remote Scan driver Help 2012, 2013 TOSHIBA TEC CORPORATION All rights reserved Under the copyright laws, this manual cannot be reproduced
Information Security Policy
 Information Security Policy Contents Version: 1 Contents... 1 Introduction... 2 Anti-Virus Software... 3 Media Classification... 4 Media Handling... 5 Media Retention... 6 Media Disposal... 7 Service Providers...
Information Security Policy Contents Version: 1 Contents... 1 Introduction... 2 Anti-Virus Software... 3 Media Classification... 4 Media Handling... 5 Media Retention... 6 Media Disposal... 7 Service Providers...
1 of 10 1/31/2014 4:08 PM
 1 of 10 1/31/2014 4:08 PM copyright 2014 How to backup Microsoft SQL Server with Nordic Backup Pro Before creating a SQL backup set within Nordic Backup Pro it is first necessary to verify that the settings
1 of 10 1/31/2014 4:08 PM copyright 2014 How to backup Microsoft SQL Server with Nordic Backup Pro Before creating a SQL backup set within Nordic Backup Pro it is first necessary to verify that the settings
Information Security Awareness Training Gramm-Leach-Bliley Act (GLB Act)
 Information Security Awareness Training Gramm-Leach-Bliley Act (GLB Act) The GLB Act training packet is part of the Information Security Awareness Training that must be completed by employees. Please visit
Information Security Awareness Training Gramm-Leach-Bliley Act (GLB Act) The GLB Act training packet is part of the Information Security Awareness Training that must be completed by employees. Please visit
Plain-paper digital Fax/Copier/Printer/Scanner Scanner and Fax Guide
 Plain-paper digital Fax/Copier/Printer/Scanner Scanner and Fax Guide Please read this guide before operating this machine. After you finish reading this guide, keep it handy for easy reference. Chapter
Plain-paper digital Fax/Copier/Printer/Scanner Scanner and Fax Guide Please read this guide before operating this machine. After you finish reading this guide, keep it handy for easy reference. Chapter
Industrial Flash Storage Trends in Software and Security
 January 22, 2013 Industrial Flash Storage Trends in Software and Security Many flash storage devices in embedded applications are used to save data but also function as disks for the OS. Most users are
January 22, 2013 Industrial Flash Storage Trends in Software and Security Many flash storage devices in embedded applications are used to save data but also function as disks for the OS. Most users are
Nuance ecopy ShareScan 5 and ecopy PDF Pro Office 5 Reviewers' Guide
 Nuance ecopy ShareScan 5 and ecopy PDF Pro Office 5 Reviewers' Guide Thank you for your interest in the ecopy multifunction peripheral (MFP) document scanning and workflow software. We hope that the following
Nuance ecopy ShareScan 5 and ecopy PDF Pro Office 5 Reviewers' Guide Thank you for your interest in the ecopy multifunction peripheral (MFP) document scanning and workflow software. We hope that the following
WipeDrive & WipeDrive PRO Quick Start Guide 2-6. Copyright 2006 WhiteCanyon Inc. All rights reserved
 WipeDrive & WipeDrive PRO Quick Start Guide 2-6 Copyright 2006 WhiteCanyon Inc. All rights reserved WipeDrive User Guide 1. INTRODUCTION. 3 1.1 Purpose..... 3 1.2 System Requirements.. 3 2. BEFORE WIPING
WipeDrive & WipeDrive PRO Quick Start Guide 2-6 Copyright 2006 WhiteCanyon Inc. All rights reserved WipeDrive User Guide 1. INTRODUCTION. 3 1.1 Purpose..... 3 1.2 System Requirements.. 3 2. BEFORE WIPING
White Paper. Security: Cortado Corporate Server for BlackBerry. Information on the Cortado infrastructure and Bluetooth printing
 White Paper Security: Cortado Corporate Server for BlackBerry Information on the Cortado infrastructure and Bluetooth printing This white paper provides information about the security of BlackBerry and
White Paper Security: Cortado Corporate Server for BlackBerry Information on the Cortado infrastructure and Bluetooth printing This white paper provides information about the security of BlackBerry and
 - - - - - - 601/751 Print To access the print driver in most programs: 1. File Print 2. From the dropdown box next to Name, select the Bizhub 601/751 Printer 3. Click the Properties or Preferences button
- - - - - - 601/751 Print To access the print driver in most programs: 1. File Print 2. From the dropdown box next to Name, select the Bizhub 601/751 Printer 3. Click the Properties or Preferences button
Black & White Scanning Guide
 Black & White Scanning Guide This guide covers the following machines: BH420/BH500/BH600/BH750 Bizhub 250/350 Bizhub 163/211 Bizhub 130F 7145 - IP432 7222/7228/7235 - IP424 (Same configuration as 7145)
Black & White Scanning Guide This guide covers the following machines: BH420/BH500/BH600/BH750 Bizhub 250/350 Bizhub 163/211 Bizhub 130F 7145 - IP432 7222/7228/7235 - IP424 (Same configuration as 7145)
DA-70702 BIOMETRIC FINGERPRINT READER 2,5" HDD ENCLOSURE User Manual
 DA-70702 BIOMETRIC FINGERPRINT READER 2,5" HDD ENCLOSURE User Manual System Requirements System Requirements Recommended Pentium II or higher or other compatible machines. Recommended RAM of at least 128
DA-70702 BIOMETRIC FINGERPRINT READER 2,5" HDD ENCLOSURE User Manual System Requirements System Requirements Recommended Pentium II or higher or other compatible machines. Recommended RAM of at least 128
Office Equipment Disposal Policy
 Office Equipment Disposal Policy R ISK MANAGEMENT HANDOUTS OF L AWYERS MUTUAL LAWYERS MUTUAL LIABILITY INSURANCE COMPANY OF NORTH CAROLINA 5020 Weston Parkway, Suite 200, Cary, North Carolina 27513 Post
Office Equipment Disposal Policy R ISK MANAGEMENT HANDOUTS OF L AWYERS MUTUAL LAWYERS MUTUAL LIABILITY INSURANCE COMPANY OF NORTH CAROLINA 5020 Weston Parkway, Suite 200, Cary, North Carolina 27513 Post
Computer Forensics: Permanent Erasing
 Computer Forensics: Permanent Erasing Prepared By : Yousef T. Aburabie and Mohamd Alomari Supervised By: Dr. Lo ai Tawalbeh, New York Institute of Technology (NYIT)-Jordan s campus-2006 Introduction "Delete"
Computer Forensics: Permanent Erasing Prepared By : Yousef T. Aburabie and Mohamd Alomari Supervised By: Dr. Lo ai Tawalbeh, New York Institute of Technology (NYIT)-Jordan s campus-2006 Introduction "Delete"
Clickfree The Effortless Backup Solution
 Reprint from May 2009 Clickfree The Effortless Backup Solution By Joel P. Bruckenstein One of the fundamental rules of computing is: Back up your data. To that fundamental rule we, at T3 add a few more:
Reprint from May 2009 Clickfree The Effortless Backup Solution By Joel P. Bruckenstein One of the fundamental rules of computing is: Back up your data. To that fundamental rule we, at T3 add a few more:
THE BIG GREEN PICTURE HOW KONICA MINOLTA INNOVATIONS, PROGRAMS & ENERGY-SAVING INITIATIVES PROTECT THE ENVIRONMENT FOR FUTURE GENERATIONS
 THE BIG GREEN PICTURE HOW KONICA MINOLTA INNOVATIONS, PROGRAMS & ENERGY-SAVING INITIATIVES PROTECT THE ENVIRONMENT FOR FUTURE GENERATIONS At Konica Minolta, environmental protection is a top priority.
THE BIG GREEN PICTURE HOW KONICA MINOLTA INNOVATIONS, PROGRAMS & ENERGY-SAVING INITIATIVES PROTECT THE ENVIRONMENT FOR FUTURE GENERATIONS At Konica Minolta, environmental protection is a top priority.
What s the difference between my Home Banking password and my Enhanced Login Security?
 Common Questions about Enhanced Login Security 818-973-4900 or 800-973 - 4989 Mon. - Fri. 8:30 a.m. - 4:00 p.m. Enhanced Login Security is a new online security feature that will provide you additional
Common Questions about Enhanced Login Security 818-973-4900 or 800-973 - 4989 Mon. - Fri. 8:30 a.m. - 4:00 p.m. Enhanced Login Security is a new online security feature that will provide you additional
Konica Minolta Addresses the Legal Market
 February, 2010 Strategic Assessment Konica Minolta Addresses the Legal Market Authors Randy Dazo Abstract This document looks at the trends in the legal market, how solutions can help address some of the
February, 2010 Strategic Assessment Konica Minolta Addresses the Legal Market Authors Randy Dazo Abstract This document looks at the trends in the legal market, how solutions can help address some of the
MULTIFUNCTIONAL DIGITAL SYSTEMS. Operator's Manual for TWAIN Driver/File Downloader
 MULTIFUNCTIONAL DIGITAL SYSTEMS Operator's Manual for TWAIN Driver/File Downloader 2008 KYOCERA MITA Corporation All rights reserved Preface Thank you for purchasing KYOCERA MITA Multifunctional Digital
MULTIFUNCTIONAL DIGITAL SYSTEMS Operator's Manual for TWAIN Driver/File Downloader 2008 KYOCERA MITA Corporation All rights reserved Preface Thank you for purchasing KYOCERA MITA Multifunctional Digital
Xerox D95/D110/D125 Copier/Printer
 Version 1.0 February 2012 Xerox D95/D110/D125 Copier/Printer Security Function Supplementary Guide 2012 Xerox Corporation. All rights reserved. Xerox, Xerox and Design, CentreWare and FreeFlow are trademarks
Version 1.0 February 2012 Xerox D95/D110/D125 Copier/Printer Security Function Supplementary Guide 2012 Xerox Corporation. All rights reserved. Xerox, Xerox and Design, CentreWare and FreeFlow are trademarks
Addressing document imaging security issues
 Addressing document imaging security issues Document imaging makes it possible to integrate paper documents with existing workflow processes and business applications, e.g., e-mail, fax, and electronic
Addressing document imaging security issues Document imaging makes it possible to integrate paper documents with existing workflow processes and business applications, e.g., e-mail, fax, and electronic
Windows Operating Systems. Basic Security
 Windows Operating Systems Basic Security Objectives Explain Windows Operating System (OS) common configurations Recognize OS related threats Apply major steps in securing the OS Windows Operating System
Windows Operating Systems Basic Security Objectives Explain Windows Operating System (OS) common configurations Recognize OS related threats Apply major steps in securing the OS Windows Operating System
MULTIFUNCTIONAL DIGITAL SYSTEMS. Operator s Manual for Backup/Restore Utility
 MULTIFUNCTIONAL DIGITAL SYSTEMS Operator s Manual for Backup/Restore Utility 2009 KYOCERA MITA Corporation All rights reserved Preface Thank you for purchasing Multifunctional Digital Color Systems. Read
MULTIFUNCTIONAL DIGITAL SYSTEMS Operator s Manual for Backup/Restore Utility 2009 KYOCERA MITA Corporation All rights reserved Preface Thank you for purchasing Multifunctional Digital Color Systems. Read
INTENT OF THIS DOCUMENT:
 Version 1.1 August 17, 2010 INTENT OF THIS DOCUMENT: Canon recognizes the importance of information security and the challenges that your organization faces. This white paper provides information security
Version 1.1 August 17, 2010 INTENT OF THIS DOCUMENT: Canon recognizes the importance of information security and the challenges that your organization faces. This white paper provides information security
MULTIFUNCTIONAL DIGITAL SYSTEMS. Operator s Manual for Backup/Restore Utility
 MULTIFUNCTIONAL DIGITAL SYSTEMS Operator s Manual for Backup/Restore Utility 2008 TOSHIBA TEC CORPORATION All rights reserved Under the copyright laws, this manual cannot be reproduced in any form without
MULTIFUNCTIONAL DIGITAL SYSTEMS Operator s Manual for Backup/Restore Utility 2008 TOSHIBA TEC CORPORATION All rights reserved Under the copyright laws, this manual cannot be reproduced in any form without
Multi-Factor Authentication (FMA) A new security feature for Home Banking. Frequently Asked Questions 8/17/2006
 Multi-Factor Authentication (FMA) A new security feature for Home Banking Frequently Asked Questions 8/17/2006 1. Why is MFA being added? We take our obligation to protect our members seriously. To make
Multi-Factor Authentication (FMA) A new security feature for Home Banking Frequently Asked Questions 8/17/2006 1. Why is MFA being added? We take our obligation to protect our members seriously. To make
Stopping Leaks: How to Confront the Challenges of Endpoint Information Security from HDD. Whitepaper
 Stopping Leaks: How to Confront the Challenges of Endpoint Information Security from HDD intimus consulting is a division of the MARTIN YALE GROUP Bergheimer Strasse 6-12 88677 Markdorf / Germany www.intimusconsulting.com
Stopping Leaks: How to Confront the Challenges of Endpoint Information Security from HDD intimus consulting is a division of the MARTIN YALE GROUP Bergheimer Strasse 6-12 88677 Markdorf / Germany www.intimusconsulting.com
Data Access Request Service
 Data Access Request Service Guidance Notes on Security Version: 4.0 Date: 01/04/2015 1 Copyright 2014, Health and Social Care Information Centre. Introduction This security guidance is for organisations
Data Access Request Service Guidance Notes on Security Version: 4.0 Date: 01/04/2015 1 Copyright 2014, Health and Social Care Information Centre. Introduction This security guidance is for organisations
INFORMATION SECURITY GUIDELINES
 INFORMATION SECURITY GUIDELINES TABLE OF CONTENTS: Scope of Document 1 Data Definition Guidelines (Appendix 1).2 Data Protection Guidelines (Appendix 2).3 Protection of Electronic or Machine- Readable
INFORMATION SECURITY GUIDELINES TABLE OF CONTENTS: Scope of Document 1 Data Definition Guidelines (Appendix 1).2 Data Protection Guidelines (Appendix 2).3 Protection of Electronic or Machine- Readable
Information Security. Annual Education 2014. Information Security. 2014 Mission Health System, Inc.
 Annual Education 2014 Why? Protecting patient information is an essential part of providing quality healthcare. As Mission Health grows as a health system and activities become more computerized, new information
Annual Education 2014 Why? Protecting patient information is an essential part of providing quality healthcare. As Mission Health grows as a health system and activities become more computerized, new information
SecureLock. User Manual
 SecureLock User Manual Encryption Application for portable Storage Devices User Manual Version 1.0.0.3 2004-2011 Integral Memory plc Table of Contents Table of Contents... 2 1. Introduction... 3 2. System
SecureLock User Manual Encryption Application for portable Storage Devices User Manual Version 1.0.0.3 2004-2011 Integral Memory plc Table of Contents Table of Contents... 2 1. Introduction... 3 2. System
Legal Notes. Regarding Trademarks. Models supported by the KX printer driver. 2011 KYOCERA MITA Corporation
 Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable for any problems arising from
Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable for any problems arising from
Here is a guide on how to encrypt a part of your USB flash drive and access it on any computer:
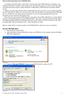 How to password protect your USB flash drive. According to the XXX agency reports 80% of all lost and stolen USB flash drives contained a very important information: business or government data. The following
How to password protect your USB flash drive. According to the XXX agency reports 80% of all lost and stolen USB flash drives contained a very important information: business or government data. The following
RFG Secure FTP. Web Interface
 RFG Secure FTP Web Interface Step 1: Getting to the Secure FTP Web Interface: Open your preferred web browser and type the following address: http://ftp.raddon.com After you hit enter, you will be taken
RFG Secure FTP Web Interface Step 1: Getting to the Secure FTP Web Interface: Open your preferred web browser and type the following address: http://ftp.raddon.com After you hit enter, you will be taken
Architecture. The DMZ is a portion of a network that separates a purely internal network from an external network.
 Architecture The policy discussed suggests that the network be partitioned into several parts with guards between the various parts to prevent information from leaking from one part to another. One part
Architecture The policy discussed suggests that the network be partitioned into several parts with guards between the various parts to prevent information from leaking from one part to another. One part
SafeCom Smart Printing Administrator s Quick Guide
 SafeCom Smart Printing Administrator s Quick Guide D10600-08 March 2012 Trademarks: SafeCom, SafeCom Go, SafeCom P:Go, SafeCom epay and the SafeCom logo are trademarks of SafeCom a/s. Company and product
SafeCom Smart Printing Administrator s Quick Guide D10600-08 March 2012 Trademarks: SafeCom, SafeCom Go, SafeCom P:Go, SafeCom epay and the SafeCom logo are trademarks of SafeCom a/s. Company and product
