Documentation for Configuration of BeCrypt Removable Media Encryption
|
|
|
- Alban Norton
- 10 years ago
- Views:
Transcription
1 Documentation for Configuration of BeCrypt Removable Media Encryption Laptop Configuration Procedure and Details. Laptops were to be configured with BeCrypt encryption application in such a manner that allows the users to save work/data to USB drive only. This was achieved by using BeCrypt in conjunction with Microsoft Steady State ; this utility is used to restrict user access in the desired manner. Steady State is configurable via the XP User administrator account. Partition Magic was used to create a partition to facilitate key export/import (and image storage if necessary) for users. (BeCrypt needs access to keys to import). See note below:- It was necessary to create a partition to export the key to so that the Becrypt utility could access the key to then import it. It was found that this couldn t be achieved by saving said key to the C: drive or a share(on the C: drive) that could be mapped to a drive, it was thought that Steady State prevented this by applying restrictions necessary to lock down the laptop. Appropriate NTFS permissions can then be applied to the partition or folder/files therein. XP User has full permissions to the X drive (XP User only), the IAF User should have/has read only access. Currently keys that are active on the D610 image are exported/saved to Stuart s system on root of C: in a directory called Encryption Keys. Install Partition Magic and configure as necessary before installing Becrypt or Steady State. (Remember to untick use simple file sharing to get access to the permissions. Place Social Work Word Templates in Word Templates directory, in this instance it is C:\Documents and Settings\IAF User\Application Data\Microsoft\Templates and C:\Documents and Settings\XP User\Application Data\Microsoft\Templates.Templates can be found in J:\Technicians\Social Work Encryption Back Up Files and Documents\Templates\Social Work Templates. Users will access the templates from within Word new>. Create XP User and IAF User with robust passwords. Install and configure Steady State as required. Configure logon message (how-to in Technicians dir on network) Install BeCrypt Removable Media Encryption and reboot PC. Log in as an Administrator (XP User) For future reference the IAF User password Open up DISK Protect Management Tool. Note: Contact Mary Timpany for passwords.
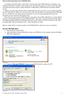
2 Right click on the XP User and select Add Key
3 Ensure that Generate a random key is selected and that a suitably indicative name is given to the Key Description. For our purposes we have named the key description as swencryptionkey. Select Generate Key, which will invoke the key generation procedure. You will notice the text next to Generate Key states Key successfully generated Select OK Key Recovery option is presented
4 The Recovery File name should again be indicatively named and for our purposes we have called it swencryptionkey_recoveryfile. Select Save As and save to an intermediate location i.e. memory stick. Select OK IMMEDIATELY (well relatively quickly) COPY THIS KEY TO THE CENTRAL ADMINISTRATIVE LOCATION. TYPICALLY AN ADMINISTRATOR S PC. The above dialogue will appear showing that the encryption key has been generated and successfully imported and saved. Select OK.
5 On returning to the opening screen you will notice that the swencryptionkey is now a valid key for the XP User. Notice that there is an option here to Disable Removable Media Encryption. This is self-explanatory. Only available to the administrator. IT SHOULD BE NOTED THAT ANY USB DEVICE (IPOD, OTHER MEMORY DEVICES ETC) PLUGGED INTO THIS DEVICE WHEN LOGGED IN AS THIS USER AND ENCRYPTION IS ENABLED WILL AUTOMATICALLY HAVE ALL THE DATA ON THIS DEVICE ENCRYPTED MAKING IT UNUSABLE AND RECOVERABLE. Exporting and Importing Key/s We now require to export the key that we have generated as XP User to make it available to a group of users (IAF Users). This will then be imported per user. Invoke the Becrypt application. On the DISK Protect Management Tool screen right click on the swencryptionkey and select export keys.
6 You will see the above screen. Enter the XP User s password Enter the password to secure the exported keys. Select Export Keys. Select an area to Save To where it can be accessed by the intended recipients (A safe accessible location. For our purposes we named the key swencryptionkey and saved it to the root of C:) The above screen should appear. Importing Previously Saved Keys After rebooting and logging in as IAF User, open up the DISK Protect Management Tool either from START/Programs or by double clicking the padlock icon in the system tray (next to the time).
7 Right click on IAF User and select Add Key. From the screen select Import a key or keys from a key file. Select Browse and navigate to where the key was previously saved. Input the password for the key file, established earlier. Select OK and you should see a 1 media key(s) successfully imported. After inputting the key for a given user, if it s not already, remove the USB stick and re-insert. You will then be prompted for the key to be used to encrypt the device. From the pull down for our purposes this was: swencryptionkey. This was the key we exported earlier. It was observed that when a key is imported the key name is modified (prepended) with a prefix, in this instance it was FFFE, this is normal. After selecting the key to encrypt data for the user you will be prompted to format the USB drive. This is normal and should be done. The USB device is now encrypted and data will not be visible on another PC unless equipped with the same key. The administrator will now have the key also and will be able to un-encrypt the data on the memory stick and manipulate it as required
8 Recovery Console ****Remove the Disk Protection on the laptop so that changes can be saved.**** Install the Recovery Console component of BeCrypt on the Administrators PC/System and ensure that the.brf file for that key is on on that Administrator s PC/System (this can be copied over from AN Other System). When the IAF User logs in they will be asked to type in their Windows password and then be given a challenge code. On the admin PC run Recovery Console and in Recovery Console Tab select new and set up a new recovery database. Then select Import and point to the.brf file. Then select Password Recovery, this will ask for the last 6 digits of the Challenge Code from the laptop. After adding the digits press the response button. This will generate a response code enquiry on the laptop, re-apply the disk protection once finished. Procedure when new/non encrypted USB Device is inserted. User will get prompt asking for key to be used to encrypt device. Select the socialwork key (actual name may differ slightly, ie; may be prepended by hex characters) User will also be prompted by the dialog below, select start, this is normal.
9 Format confirmation. Settings For Windows Steady State (For BeCrypt Encryption) The following are settings for Windows Steady State for the Social Work laptops. There is an image available for this.
10
11
12 On the above screen place a tick in the Hide Drives section in Local Disk (C:).
13
14
15
BitLocker To Go User Guide
 BitLocker To Go User Guide 1. Introduction BitLocker To Go a new feature of Windows 7 is a full-disk encryption protection technology for removable storage devices that are connected to one of the USB
BitLocker To Go User Guide 1. Introduction BitLocker To Go a new feature of Windows 7 is a full-disk encryption protection technology for removable storage devices that are connected to one of the USB
Royal Mail Group. getting started. with Symantec Endpoint Encryption. A user guide from Royal Mail Technology
 getting started with Symantec Endpoint Encryption A user guide from Royal Mail Technology For further help, contact the IT Helpdesk on 5415 2555 (01246 282555) March 2010 Contents 1 Introduction to Symantec
getting started with Symantec Endpoint Encryption A user guide from Royal Mail Technology For further help, contact the IT Helpdesk on 5415 2555 (01246 282555) March 2010 Contents 1 Introduction to Symantec
Symantec PGP Whole Disk Encryption Hands-On Lab V 3.7
 Symantec PGP Whole Disk Encryption Hands-On Lab V 3.7 Description This hands-on lab session covers the hard drive encryption technologies from PGP. Students will administer a typical Whole Disk Encryption
Symantec PGP Whole Disk Encryption Hands-On Lab V 3.7 Description This hands-on lab session covers the hard drive encryption technologies from PGP. Students will administer a typical Whole Disk Encryption
Encrypting with BitLocker for disk volumes under Windows 7
 Encrypting with BitLocker for disk volumes under Windows 7 Summary of the contents 1 Introduction 2 Hardware requirements for BitLocker Driver Encryption 3 Encrypting drive 3.1 Operating System Drive 3.1.1
Encrypting with BitLocker for disk volumes under Windows 7 Summary of the contents 1 Introduction 2 Hardware requirements for BitLocker Driver Encryption 3 Encrypting drive 3.1 Operating System Drive 3.1.1
How to Encrypt your Windows 7 SDS Machine with Bitlocker
 How to Encrypt your Windows 7 SDS Machine with Bitlocker ************************************ IMPORTANT ******************************************* Before encrypting your SDS Windows 7 Machine it is highly
How to Encrypt your Windows 7 SDS Machine with Bitlocker ************************************ IMPORTANT ******************************************* Before encrypting your SDS Windows 7 Machine it is highly
FuseMail- Exchange ControlPanel Admin Guide Feb.27-14 V1.0. Exchange ControlPanel Administration Guide
 Exchange ControlPanel Administration Guide Table of Contents Top Level Portal Administration... 4 Signing In to Control Panel... 4 Restoring Account Password... 5 Change Account Details... 7 Viewing Account
Exchange ControlPanel Administration Guide Table of Contents Top Level Portal Administration... 4 Signing In to Control Panel... 4 Restoring Account Password... 5 Change Account Details... 7 Viewing Account
Prerequisite. Getting Started. Email Signing and Encryption using Microsoft outlook 2007
 Email Signing and Encryption using Microsoft outlook 2007 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Email Signing and Encryption using Microsoft outlook 2007 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
HOW TO SETUP EVOKO ROOM MANAGER EVO WITH EXCHANGE 2007-2010-2013.
 HOW TO SETUP EVOKO ROOM MANAGER EVO WITH EXCHANGE 2007-2010-2013. AUTHOR: CONNY ISAKSSON (HEAD TECHNICIAN) REV. 01-2013 / 2013-08-16 This will describe how to do a basic setup Room Manager for New/Existing
HOW TO SETUP EVOKO ROOM MANAGER EVO WITH EXCHANGE 2007-2010-2013. AUTHOR: CONNY ISAKSSON (HEAD TECHNICIAN) REV. 01-2013 / 2013-08-16 This will describe how to do a basic setup Room Manager for New/Existing
Yale Software Library
 Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, [email protected] Two-factor authentication: Installation and configuration instructions for
Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, [email protected] Two-factor authentication: Installation and configuration instructions for
Windows XP Exchange Client Installation Instructions
 WINDOWS XP with Outlook 2003 or Outlook 2007 1. Click the Start button and select Control Panel: 2. If your control panel looks like this: Click Switch to Classic View. 3. Double click Mail. 4. Click show
WINDOWS XP with Outlook 2003 or Outlook 2007 1. Click the Start button and select Control Panel: 2. If your control panel looks like this: Click Switch to Classic View. 3. Double click Mail. 4. Click show
Here is a guide on how to encrypt a part of your USB flash drive and access it on any computer:
 How to password protect your USB flash drive. According to the XXX agency reports 80% of all lost and stolen USB flash drives contained a very important information: business or government data. The following
How to password protect your USB flash drive. According to the XXX agency reports 80% of all lost and stolen USB flash drives contained a very important information: business or government data. The following
Step by step guide how to password protect your USB flash drive
 Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
Massey University Wireless Network Client Configuration Windows 7
 Massey University Wireless Network Client Configuration Windows 7 Windows 7 wireless network Requirements You must have an active Massey network account, i.e. you should already be able to log onto the
Massey University Wireless Network Client Configuration Windows 7 Windows 7 wireless network Requirements You must have an active Massey network account, i.e. you should already be able to log onto the
Step-by-step installation guide for monitoring untrusted servers using Operations Manager ( Part 3 of 3)
 Step-by-step installation guide for monitoring untrusted servers using Operations Manager ( Part 3 of 3) Manual installation of agents and importing the SCOM certificate to the servers to be monitored:
Step-by-step installation guide for monitoring untrusted servers using Operations Manager ( Part 3 of 3) Manual installation of agents and importing the SCOM certificate to the servers to be monitored:
Working with Office Applications and ProjectWise
 Working with Office Applications and ProjectWise The main Microsoft Office Applications (Word, Excel, PowerPoint and Outlook) are all integrated with ProjectWise. These applications are aware that ProjectWise
Working with Office Applications and ProjectWise The main Microsoft Office Applications (Word, Excel, PowerPoint and Outlook) are all integrated with ProjectWise. These applications are aware that ProjectWise
STATISTICA VERSION 9 STATISTICA ENTERPRISE INSTALLATION INSTRUCTIONS FOR USE WITH TERMINAL SERVER
 Notes: STATISTICA VERSION 9 STATISTICA ENTERPRISE INSTALLATION INSTRUCTIONS FOR USE WITH TERMINAL SERVER 1. These instructions focus on installation on Windows Terminal Server (WTS), but are applicable
Notes: STATISTICA VERSION 9 STATISTICA ENTERPRISE INSTALLATION INSTRUCTIONS FOR USE WITH TERMINAL SERVER 1. These instructions focus on installation on Windows Terminal Server (WTS), but are applicable
CWOPA Broadband Users. Windows Operating System
 CWOPA Broadband Users Windows Operating System October 2012 Background These instructions are to be used for VPN users who have been assigned a CWOPA username and password. If your machine has Internet
CWOPA Broadband Users Windows Operating System October 2012 Background These instructions are to be used for VPN users who have been assigned a CWOPA username and password. If your machine has Internet
HGC SUPERHUB HOSTED EXCHANGE EMAIL
 HGC SUPERHUB HOSTED EXCHANGE EMAIL OUTLOOK 2010 POP3 SETUP GUIDE MICROSOFT HOSTED COMMUNICATION SERVICE V2013.5 Table of Contents 1. Get Started... 1 1.1 Start from Setting up an Email account... 1 1.2
HGC SUPERHUB HOSTED EXCHANGE EMAIL OUTLOOK 2010 POP3 SETUP GUIDE MICROSOFT HOSTED COMMUNICATION SERVICE V2013.5 Table of Contents 1. Get Started... 1 1.1 Start from Setting up an Email account... 1 1.2
BounceBack User Guide
 Table Of Contents 1. Table of Contents... 2 2. 1-0 Introduction... 3 2.1 1-0: Introduction... 4 2.2 1-1: BounceBack Software Overview... 6 3. 2-0 Navigating the BounceBack Control Center... 9 3.1 2-0:
Table Of Contents 1. Table of Contents... 2 2. 1-0 Introduction... 3 2.1 1-0: Introduction... 4 2.2 1-1: BounceBack Software Overview... 6 3. 2-0 Navigating the BounceBack Control Center... 9 3.1 2-0:
1. Set Daylight Savings Time... 3. 2. Create Migrator Account... 3. 3. Assign Migrator Account to Administrator group... 4
 1. Set Daylight Savings Time... 3 a. Have client log into Novell/Local Machine with Administrator Account...3 b. Access Adjust Date/Time...3 c. Make sure the time zone is set to Central Time...3 2. Create
1. Set Daylight Savings Time... 3 a. Have client log into Novell/Local Machine with Administrator Account...3 b. Access Adjust Date/Time...3 c. Make sure the time zone is set to Central Time...3 2. Create
A. I do not have my own personal certificate I am a new client or want to download a new certificate
 This user guide will help you to create your personal certificate in file/browser or smart card certificate. If you already own a personal certificate in file that you have saved on your computer, you
This user guide will help you to create your personal certificate in file/browser or smart card certificate. If you already own a personal certificate in file that you have saved on your computer, you
Remote Access End User Guide (Cisco VPN Client)
 Remote Access End User Guide (Cisco VPN Client) Contents 1 INTRODUCTION... 3 2 AUDIENCE... 3 3 CONNECTING TO N3 VPN (N3-12-1) OR EXTENDED VPN CLIENT... 3 4 DISCONNECTING FROM N3 VPN (N3-12-1) AND EXTENDED
Remote Access End User Guide (Cisco VPN Client) Contents 1 INTRODUCTION... 3 2 AUDIENCE... 3 3 CONNECTING TO N3 VPN (N3-12-1) OR EXTENDED VPN CLIENT... 3 4 DISCONNECTING FROM N3 VPN (N3-12-1) AND EXTENDED
DataTraveler Secure - Privacy Edition
 DataTraveler Secure - Privacy Edition This document is designed to help users become familiar with the DataTraveler Secure - Privacy Edition. For additional support, please visit our on-line technical
DataTraveler Secure - Privacy Edition This document is designed to help users become familiar with the DataTraveler Secure - Privacy Edition. For additional support, please visit our on-line technical
Apple Mac VPN Service Setting up Remote Desktop
 Apple Mac VPN Service Setting up Remote Desktop After you have successfully connected via the VPN client to the University network you will then need to make the connection to your machine. To do this
Apple Mac VPN Service Setting up Remote Desktop After you have successfully connected via the VPN client to the University network you will then need to make the connection to your machine. To do this
SMS for Outlook. Installation, Configuration and Usage Guide
 SMS for Outlook Installation, Configuration and Usage Guide INTRODUCTION Installing TxTStream s SMS for Outlook is easy and will only take a minute or two. We will be using screen shots from a Windows
SMS for Outlook Installation, Configuration and Usage Guide INTRODUCTION Installing TxTStream s SMS for Outlook is easy and will only take a minute or two. We will be using screen shots from a Windows
Installing the Gerber P2C Plotter USB Driver
 Installing the Gerber P2C Plotter USB Driver 1 You can install a Gerber P2C plotter using a USB connection and communicate with it using compatible design software. The following procedures describe installing
Installing the Gerber P2C Plotter USB Driver 1 You can install a Gerber P2C plotter using a USB connection and communicate with it using compatible design software. The following procedures describe installing
2. To encrypt the drive for future use, click Yes (Fig 1, 2). This will start the encryption process.
 Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
In order to enable BitLocker, your hard drive must be partitioned in a particular manner.
 ENABLE BITLOCKER ON WINDOWS VISTA - WITHOUT A TPM Requirements: You must be running Vista Enterprise or Vista Ultimate to enable BitLocker. Any other version of Vista is not compatible. It is recommended
ENABLE BITLOCKER ON WINDOWS VISTA - WITHOUT A TPM Requirements: You must be running Vista Enterprise or Vista Ultimate to enable BitLocker. Any other version of Vista is not compatible. It is recommended
Instructions for connecting to the FDIBA Wireless Network. (Windows XP)
 Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Prerequisite. Getting Started. Email Signing and Encryption using Microsoft outlook 2010
 Email Signing and Encryption using Microsoft outlook 2010 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Email Signing and Encryption using Microsoft outlook 2010 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Wireless Network Configuration Guide
 CIT Table of Contents Introduction... 1 General Wireless Settings... 1 1. Windows XP Wireless Configuration... 2 2. Windows XP Intel Pro Wireless Tool... 7 3. Windows Vista Using the Windows Wireless Tools...
CIT Table of Contents Introduction... 1 General Wireless Settings... 1 1. Windows XP Wireless Configuration... 2 2. Windows XP Intel Pro Wireless Tool... 7 3. Windows Vista Using the Windows Wireless Tools...
Beckhoff TwinCAT. Creating Boot Projects for TwinCAT
 Beckhoff TwinCAT Creating Boot Projects for TwinCAT Revision: 1.1 Updated: 06 December 2004 Table of Contents 1. Introduction...3 2. TwinCAT System Boot Project (V2.9.0 and later)...4 2.1. TwinCAT System
Beckhoff TwinCAT Creating Boot Projects for TwinCAT Revision: 1.1 Updated: 06 December 2004 Table of Contents 1. Introduction...3 2. TwinCAT System Boot Project (V2.9.0 and later)...4 2.1. TwinCAT System
How to enable Disk Encryption on a laptop
 How to enable Disk Encryption on a laptop Skills and pre-requisites Intermediate IT skills required. You need to: have access to, and know how to change settings in the BIOS be confident that your data
How to enable Disk Encryption on a laptop Skills and pre-requisites Intermediate IT skills required. You need to: have access to, and know how to change settings in the BIOS be confident that your data
Connecting to eduroam using Windows 8
 Connecting to eduroam using Windows 8 GUIDE User Services IT Services University of Malta 2013 User Services IT Services University of Malta Msida MSD 2080 Malta May only be reproduced with permission.
Connecting to eduroam using Windows 8 GUIDE User Services IT Services University of Malta 2013 User Services IT Services University of Malta Msida MSD 2080 Malta May only be reproduced with permission.
Egress Switch Client Deployment Guide V4.x
 Egress Switch Client Deployment Guide V4.x www.egress.com 2007-2013 Egress Software Technologies Ltd Table of Contents System Requirements... 4 Deployment Process... 4 Computer & User Based Policy Application...
Egress Switch Client Deployment Guide V4.x www.egress.com 2007-2013 Egress Software Technologies Ltd Table of Contents System Requirements... 4 Deployment Process... 4 Computer & User Based Policy Application...
Copyright. Disclaimer. Introduction 1. System Requirements... 3. Installing the software 4
 Digital Signatures User Guide Revision 1.2 build 1, Document Revision 1.12 Published 31. Octover 2011 ii Contents Copyright Disclaimer iii iii Introduction 1 System Requirements... 3 Installing the software
Digital Signatures User Guide Revision 1.2 build 1, Document Revision 1.12 Published 31. Octover 2011 ii Contents Copyright Disclaimer iii iii Introduction 1 System Requirements... 3 Installing the software
ICE.TCP Pro Update Installation Notes
 ICE.TCP Pro Update Installation Notes Important Note: Based on customer comments, we are providing these revised installation instructions. They supercede the instructions in the manual. For previous users
ICE.TCP Pro Update Installation Notes Important Note: Based on customer comments, we are providing these revised installation instructions. They supercede the instructions in the manual. For previous users
BitLocker to Go: Encryption for personal USB flash drives (Windows 7 and 8)
 BitLocker to Go: Encryption for personal USB flash drives (Windows 7 and 8) Encryption is an effective method of protecting data stored on portable devices such as USB flash drives and external hard drives.
BitLocker to Go: Encryption for personal USB flash drives (Windows 7 and 8) Encryption is an effective method of protecting data stored on portable devices such as USB flash drives and external hard drives.
Option nv, Gaston Geenslaan 14, B-3001 Leuven Tel +32 16 317 411 Fax +32 16 207 164 http://www.option.com Page 1 of 14
 Page 1 of 14 ! " #!"#$ % &&' Page 2 of 14 1 INTRODUCTION One of the highly desirable features of the GlobeSurfer III device is the ability to network together Printers and External Hard Disk drives (aka
Page 1 of 14 ! " #!"#$ % &&' Page 2 of 14 1 INTRODUCTION One of the highly desirable features of the GlobeSurfer III device is the ability to network together Printers and External Hard Disk drives (aka
eadvantage Certificate Enrollment Procedures
 eadvantage Certificate Enrollment Procedures Purpose: Instructions for members to obtain a digital certificate which is a requirement to conduct financial transactions with the Federal Home Loan Bank of
eadvantage Certificate Enrollment Procedures Purpose: Instructions for members to obtain a digital certificate which is a requirement to conduct financial transactions with the Federal Home Loan Bank of
ProjectWise Explorer V8i User Manual for Subconsultants & Team Members
 ProjectWise Explorer V8i User Manual for Subconsultants & Team Members submitted to Michael Baker International Subconsultants & Team Members submitted by Michael Baker International ProjectWise Support
ProjectWise Explorer V8i User Manual for Subconsultants & Team Members submitted to Michael Baker International Subconsultants & Team Members submitted by Michael Baker International ProjectWise Support
Xythos on Demand Quick Start Guide For Xythos Drive
 Xythos on Demand Quick Start Guide For Xythos Drive What is Xythos on Demand? Xythos on Demand is not your ordinary online storage or file sharing web site. Instead, it is an enterprise-class document
Xythos on Demand Quick Start Guide For Xythos Drive What is Xythos on Demand? Xythos on Demand is not your ordinary online storage or file sharing web site. Instead, it is an enterprise-class document
HP RDX Continuous Data Protection Software Quickstart Guide
 HP RDX Continuous Data Protection Software Quickstart Guide *5697-3351* HP Part Number: 5697-3351 Published: May 2014 Edition: Fourth Copyright 2008 2014 Hewlett-Packard Development Company, L.P. Microsoft,
HP RDX Continuous Data Protection Software Quickstart Guide *5697-3351* HP Part Number: 5697-3351 Published: May 2014 Edition: Fourth Copyright 2008 2014 Hewlett-Packard Development Company, L.P. Microsoft,
Importing your personal certificate(s) to Microsoft Internet Explorer from a Back-up (or export) file
 Importing your personal certificate(s) to Microsoft Internet Explorer from a Back-up (or export) file You may use your Medium Assurance Certificate(s) on any computer that you wish to by importing them
Importing your personal certificate(s) to Microsoft Internet Explorer from a Back-up (or export) file You may use your Medium Assurance Certificate(s) on any computer that you wish to by importing them
Supplement I.B: Installing and Configuring JDK 1.6
 Supplement I.B: Installing and Configuring JDK 1.6 For Introduction to Java Programming Y. Daniel Liang This supplement covers the following topics: Downloading JDK 1.6 ( 1.2) Installing JDK 1.6 ( 1.3)
Supplement I.B: Installing and Configuring JDK 1.6 For Introduction to Java Programming Y. Daniel Liang This supplement covers the following topics: Downloading JDK 1.6 ( 1.2) Installing JDK 1.6 ( 1.3)
www.faronics.com Deep Freeze - Retaining User Data TECHNICAL PAPER Last modified: June, 2012
 Deep Freeze - Retaining User Data TECHNICAL PAPER Last modified: June, 2012 Faronics Toll Free Tel: 800-943-6422 Toll Free Fax: 800-943-6488 International Tel: +1 604-637-3333 International Fax: +1 604-637-8188
Deep Freeze - Retaining User Data TECHNICAL PAPER Last modified: June, 2012 Faronics Toll Free Tel: 800-943-6422 Toll Free Fax: 800-943-6488 International Tel: +1 604-637-3333 International Fax: +1 604-637-8188
SafeGuard Enterprise Web Helpdesk. Product version: 6 Document date: February 2012
 SafeGuard Enterprise Web Helpdesk Product version: 6 Document date: February 2012 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Helpdesk
SafeGuard Enterprise Web Helpdesk Product version: 6 Document date: February 2012 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Helpdesk
Encrypting a USB Drive Using TrueCrypt
 Encrypting a USB Drive Using TrueCrypt This document details the steps to encrypt a USB Pen drive using TrueCrypt. TrueCrypt is free and open-source security software allowing encryption of documents and
Encrypting a USB Drive Using TrueCrypt This document details the steps to encrypt a USB Pen drive using TrueCrypt. TrueCrypt is free and open-source security software allowing encryption of documents and
APNS Certificate generating and installation
 APNS Certificate generating and installation Quick Guide for generating and installing an Apple APNS Certificate Version: x.x MobiDM Quick Guide for APNS Certificate Page 1 Index 1. APPLE APNS CERTIFICATE...
APNS Certificate generating and installation Quick Guide for generating and installing an Apple APNS Certificate Version: x.x MobiDM Quick Guide for APNS Certificate Page 1 Index 1. APPLE APNS CERTIFICATE...
Export the address book from the Blackberry handheld to MS Outlook 2003, using the synchronize utility in Blackberry Desktop Manager.
 Export the address book from the Blackberry handheld to MS Outlook 2003, using the synchronize utility in Blackberry Desktop Manager. Revised 2/25/07 Creating a New Contacts Folder in Outlook Open Outlook
Export the address book from the Blackberry handheld to MS Outlook 2003, using the synchronize utility in Blackberry Desktop Manager. Revised 2/25/07 Creating a New Contacts Folder in Outlook Open Outlook
16.4.3 Lab: Data Backup and Recovery in Windows XP
 16.4.3 Lab: Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment The
16.4.3 Lab: Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment The
Signup instructions for the End User
 Wellnomics Risk Management Server Hosted by Wellnomics Ltd Signup instructions for the End User Wellnomics Risk Management is a series of assessments, designed to help you to manage your exposure to computer-based
Wellnomics Risk Management Server Hosted by Wellnomics Ltd Signup instructions for the End User Wellnomics Risk Management is a series of assessments, designed to help you to manage your exposure to computer-based
How to Connect to Berkeley College Virtual Lab Using Windows
 How to Connect to Berkeley College Virtual Lab Using Windows Minimum Requirements Create and Save a Remote Desktop Services Connection Connecting to a Remote Desktop Services session Copy Files between
How to Connect to Berkeley College Virtual Lab Using Windows Minimum Requirements Create and Save a Remote Desktop Services Connection Connecting to a Remote Desktop Services session Copy Files between
BorderGuard Client. Version 4.4. November 2013
 BorderGuard Client Version 4.4 November 2013 Blue Ridge Networks 14120 Parke Long Court, Suite 103 Chantilly, Virginia 20151 703-631-0700 WWW.BLUERIDGENETWORKS.COM All Products are provided with RESTRICTED
BorderGuard Client Version 4.4 November 2013 Blue Ridge Networks 14120 Parke Long Court, Suite 103 Chantilly, Virginia 20151 703-631-0700 WWW.BLUERIDGENETWORKS.COM All Products are provided with RESTRICTED
Centran Version 4 Getting Started Guide KABA MAS. Table Of Contents
 Page 1 Centran Version 4 Getting Started Guide KABA MAS Kaba Mas Welcome Kaba Mas, part of the world-wide Kaba group, is the world's leading manufacturer and supplier of high security, electronic safe
Page 1 Centran Version 4 Getting Started Guide KABA MAS Kaba Mas Welcome Kaba Mas, part of the world-wide Kaba group, is the world's leading manufacturer and supplier of high security, electronic safe
Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18
 Contents Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18 Automatic Setup 1. Click on the Wireless icon in your system tray that looks like. 2. You will see a list of available
Contents Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18 Automatic Setup 1. Click on the Wireless icon in your system tray that looks like. 2. You will see a list of available
ECA IIS Instructions. January 2005
 ECA IIS Instructions January 2005 THIS PAGE INTENTIONALLY BLANK ECA IIS Instructions ii July 22, 2005 Table of Contents 1. Install Certificate in IIS 5.0... 1 2. Obtain and Install the ECA Root Certificate
ECA IIS Instructions January 2005 THIS PAGE INTENTIONALLY BLANK ECA IIS Instructions ii July 22, 2005 Table of Contents 1. Install Certificate in IIS 5.0... 1 2. Obtain and Install the ECA Root Certificate
Table of Contents. TPM Configuration Procedure... 2. 1. Configuring the System BIOS... 2
 Table of Contents TPM Configuration Procedure... 2 1. Configuring the System BIOS... 2 2. Installing the Infineon TPM Driver and the GIGABYTE Ultra TPM Utility... 3 3. Initializing the TPM Chip... 4 3.1.
Table of Contents TPM Configuration Procedure... 2 1. Configuring the System BIOS... 2 2. Installing the Infineon TPM Driver and the GIGABYTE Ultra TPM Utility... 3 3. Initializing the TPM Chip... 4 3.1.
Bosco Internet Setup Guide For Zest Apartments. Windows XP, Vista and Mac OS X
 Bosco Internet Setup Guide For Zest Apartments Windows XP, Vista and Mac OS X Contents Page Windows XP... 3 Windows Vista... 19 Mac OS X... 25 Bosco Internet Setup Guide - Page 2 How to get connected at
Bosco Internet Setup Guide For Zest Apartments Windows XP, Vista and Mac OS X Contents Page Windows XP... 3 Windows Vista... 19 Mac OS X... 25 Bosco Internet Setup Guide - Page 2 How to get connected at
PGP Desktop Encrypting Removable Media. May 1 2012 Version 1.3
 PGP Desktop Encrypting Removable Media May 1 2012 Version 1.3 Table of Contents Introduction... 3 Installation Notes... 3 Encrypting Removable Media... 5 Adding and Deleting Users... 10 Changing a Passphrase...
PGP Desktop Encrypting Removable Media May 1 2012 Version 1.3 Table of Contents Introduction... 3 Installation Notes... 3 Encrypting Removable Media... 5 Adding and Deleting Users... 10 Changing a Passphrase...
Trend ScanMail. for Microsoft Exchange. Quick Start Guide
 Trend ScanMail for Microsoft Exchange Quick Start Guide Trend ScanMail for Microsoft Exchange ScanMail for Exchange This Quick Start Guide provides a step-by-step guide to installing ScanMail for Exchange,
Trend ScanMail for Microsoft Exchange Quick Start Guide Trend ScanMail for Microsoft Exchange ScanMail for Exchange This Quick Start Guide provides a step-by-step guide to installing ScanMail for Exchange,
StarWind iscsi SAN Software: Tape Drives Using StarWind and Symantec Backup Exec
 StarWind iscsi SAN Software: Tape Drives Using StarWind and Symantec Backup Exec www.starwindsoftware.com Copyright 2008-2011. All rights reserved. COPYRIGHT Copyright 2008-2011. All rights reserved. No
StarWind iscsi SAN Software: Tape Drives Using StarWind and Symantec Backup Exec www.starwindsoftware.com Copyright 2008-2011. All rights reserved. COPYRIGHT Copyright 2008-2011. All rights reserved. No
NICCA User Guide for digitally signing email Using Digital Signature Certificate (DSC) in Outlook Express
 NICCA User Guide for digitally signing email Using Digital Signature Certificate (DSC) in Outlook Express 1. DESCRIPTION This guide explains the procedure for using the NICCA issued digital certificate
NICCA User Guide for digitally signing email Using Digital Signature Certificate (DSC) in Outlook Express 1. DESCRIPTION This guide explains the procedure for using the NICCA issued digital certificate
Installation Manual (MSI Version)
 Installation Manual (MSI Version) 1. SYSTEM REQUIREMENTS... 2 2. INSTALLATION INSTRUCTIONS... 2 2.1 REMOTE INSTALLATION USING GROUP POLICY... 2 2.1.1 Assigning Software...2 2.1.2 Publishing Software...2
Installation Manual (MSI Version) 1. SYSTEM REQUIREMENTS... 2 2. INSTALLATION INSTRUCTIONS... 2 2.1 REMOTE INSTALLATION USING GROUP POLICY... 2 2.1.1 Assigning Software...2 2.1.2 Publishing Software...2
GoldKey Software. User s Manual. Revision 7.12. WideBand Corporation www.goldkey.com. Copyright 2007-2014 WideBand Corporation. All Rights Reserved.
 GoldKey Software User s Manual Revision 7.12 WideBand Corporation www.goldkey.com 1 Table of Contents GoldKey Installation and Quick Start... 5 Initial Personalization... 5 Creating a Primary Secure Drive...
GoldKey Software User s Manual Revision 7.12 WideBand Corporation www.goldkey.com 1 Table of Contents GoldKey Installation and Quick Start... 5 Initial Personalization... 5 Creating a Primary Secure Drive...
Accessing your Staff (N and O drive) files from off campus
 Accessing your Staff (N and O drive) files from off campus It is possible to access your N and O drive files while you are off campus, for example whilst working from home or travelling. This document
Accessing your Staff (N and O drive) files from off campus It is possible to access your N and O drive files while you are off campus, for example whilst working from home or travelling. This document
Edith Cowan University Information Technology Services Centre
 Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
USING SSL/TLS WITH TERMINAL EMULATION
 USING SSL/TLS WITH TERMINAL EMULATION This document describes how to install and configure SSL or TLS support and verification certificates for the Wavelink Terminal Emulation (TE) Client. SSL/TLS support
USING SSL/TLS WITH TERMINAL EMULATION This document describes how to install and configure SSL or TLS support and verification certificates for the Wavelink Terminal Emulation (TE) Client. SSL/TLS support
Richmond Systems. SupportDesk Quick Start Guide
 Richmond Systems SupportDesk Quick Start Guide Table of Contents SupportDesk Quick Start Guide...1 Introduction...1 Pre-requisites...2 Installation at a Glance...2 Installation...3 Setup Console...13
Richmond Systems SupportDesk Quick Start Guide Table of Contents SupportDesk Quick Start Guide...1 Introduction...1 Pre-requisites...2 Installation at a Glance...2 Installation...3 Setup Console...13
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail
 Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
Yale Software Library. PGP 9.6 for Windows
 PGP 9.6 for Windows How to Add keys to the All Keys key ring: 1. Run the PGP application from Start->All Programs->PGP. 2. In the PGP main application window, click on Search for keys. 3. In the Search
PGP 9.6 for Windows How to Add keys to the All Keys key ring: 1. Run the PGP application from Start->All Programs->PGP. 2. In the PGP main application window, click on Search for keys. 3. In the Search
SafeGuard Enterprise Web Helpdesk
 SafeGuard Enterprise Web Helpdesk Product version: 5.60 Document date: April 2011 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Help Desk
SafeGuard Enterprise Web Helpdesk Product version: 5.60 Document date: April 2011 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Help Desk
BSDI Advanced Fitness & Wellness Software
 BSDI Advanced Fitness & Wellness Software 6 Kellie Ct. Califon, NJ 07830 http://www.bsdi.cc INSTRUCTION SHEET FOR MOVING YOUR DATABASE FROM ONE COMPUTER TO ANOTHER This document will outline the steps
BSDI Advanced Fitness & Wellness Software 6 Kellie Ct. Califon, NJ 07830 http://www.bsdi.cc INSTRUCTION SHEET FOR MOVING YOUR DATABASE FROM ONE COMPUTER TO ANOTHER This document will outline the steps
Downloading and installing SMART Notebook Software
 Connected Classrooms Program: Interactive Classrooms Project 03 June 2009 Downloading and installing SMART Notebook Software Step-by-step instructions for Windows and Apple Macs DET has licensed the SMART
Connected Classrooms Program: Interactive Classrooms Project 03 June 2009 Downloading and installing SMART Notebook Software Step-by-step instructions for Windows and Apple Macs DET has licensed the SMART
DriveLock Quick Start Guide
 Be secure in less than 4 hours CenterTools Software GmbH 2012 Copyright Information in this document, including URL and other Internet Web site references, is subject to change without notice. Unless otherwise
Be secure in less than 4 hours CenterTools Software GmbH 2012 Copyright Information in this document, including URL and other Internet Web site references, is subject to change without notice. Unless otherwise
Basic Use of the SPC Feature on 1100R+/H+ Testers
 Basic Use of the SPC Feature on 1100R+/H+ Testers Basics 1100 SPC Data (Note: SPC data collection is an optional feature only available on 1100R+/H+ testers that are equipped with USB ports For the feature
Basic Use of the SPC Feature on 1100R+/H+ Testers Basics 1100 SPC Data (Note: SPC data collection is an optional feature only available on 1100R+/H+ testers that are equipped with USB ports For the feature
10.3.1.6 Lab - Data Backup and Recovery in Windows XP
 5.0 10.3.1.6 Lab - Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment
5.0 10.3.1.6 Lab - Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment
Tufts VPN Client User Guide for Windows
 Tufts VPN Client User Guide for Windows Introduction The Tufts Virtual Private Network (VPN) implementation is a service that is provided to the faculty and staff of Tufts University to enable secure access
Tufts VPN Client User Guide for Windows Introduction The Tufts Virtual Private Network (VPN) implementation is a service that is provided to the faculty and staff of Tufts University to enable secure access
Windows BitLocker Drive Encryption Step-by-Step Guide
 Windows BitLocker Drive Encryption Step-by-Step Guide Microsoft Corporation Published: September 2006 Abstract Microsoft Windows BitLocker Drive Encryption is a new hardware-enhanced feature in the Microsoft
Windows BitLocker Drive Encryption Step-by-Step Guide Microsoft Corporation Published: September 2006 Abstract Microsoft Windows BitLocker Drive Encryption is a new hardware-enhanced feature in the Microsoft
SA-9600 Surface Area Software Manual
 SA-9600 Surface Area Software Manual Version 4.0 Introduction The operation and data Presentation of the SA-9600 Surface Area analyzer is performed using a Microsoft Windows based software package. The
SA-9600 Surface Area Software Manual Version 4.0 Introduction The operation and data Presentation of the SA-9600 Surface Area analyzer is performed using a Microsoft Windows based software package. The
Getting started with 2c8 plugin for Microsoft Sharepoint Server 2010
 Getting started with 2c8 plugin for Microsoft Sharepoint Server 2010... 1 Introduction... 1 Adding the Content Management Interoperability Services (CMIS) connector... 1 Installing the SharePoint 2010
Getting started with 2c8 plugin for Microsoft Sharepoint Server 2010... 1 Introduction... 1 Adding the Content Management Interoperability Services (CMIS) connector... 1 Installing the SharePoint 2010
CNW Re-Tooling Exercises
 CNW Re-Tooling Exercises I Exercise 1: VPN... 1 Scenario... 1 Detail Steps to perform exercise:... 1 Exercise 2: Install and Configure a Certificate to Web Server... 4 Scenario... 4 Detail Steps to perform
CNW Re-Tooling Exercises I Exercise 1: VPN... 1 Scenario... 1 Detail Steps to perform exercise:... 1 Exercise 2: Install and Configure a Certificate to Web Server... 4 Scenario... 4 Detail Steps to perform
DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication
 DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication Certificate Based 2010 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 31 Disclaimer Disclaimer of
DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication Certificate Based 2010 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 31 Disclaimer Disclaimer of
Florida Atlantic University VPN Client Installation Guide
 Florida Atlantic University VPN Client Installation Guide VPN Client Installation Guide Page 1 Cisco VPN Client Installation Guide Please read the instructions below to assist with the process of downloading,
Florida Atlantic University VPN Client Installation Guide VPN Client Installation Guide Page 1 Cisco VPN Client Installation Guide Please read the instructions below to assist with the process of downloading,
File Management and File Storage
 File Management and File Storage http://training.usask.ca Information Technology Services Division Table of Contents File Management at the University of Saskatchewan...3 Introduction...3 Creating Files
File Management and File Storage http://training.usask.ca Information Technology Services Division Table of Contents File Management at the University of Saskatchewan...3 Introduction...3 Creating Files
SECURE EMAIL USER GUIDE OUTLOOK 2000
 WELLS FARGO AUTHENTICATION SERVICES DATED: MAY 2003 TABLE OF CONTENTS GENERAL INFORMATION... 1 INSTALLING THE WELLS FARGO ROOT CERTIFICATE CHAIN.. 2 INSTALLING THE CERTIFICATES INTO IE... 3 SETTING UP
WELLS FARGO AUTHENTICATION SERVICES DATED: MAY 2003 TABLE OF CONTENTS GENERAL INFORMATION... 1 INSTALLING THE WELLS FARGO ROOT CERTIFICATE CHAIN.. 2 INSTALLING THE CERTIFICATES INTO IE... 3 SETTING UP
Best Practice Document Hints and Tips
 Marshal Ltd. Date: 02/06/2007 Marshal EndPoint Security From Best Practice Document Hints and Tips Marshal Software Ltd CSL 005 Marshal EndPoint Security Best Practice (2) Privacy Control: None Version:
Marshal Ltd. Date: 02/06/2007 Marshal EndPoint Security From Best Practice Document Hints and Tips Marshal Software Ltd CSL 005 Marshal EndPoint Security Best Practice (2) Privacy Control: None Version:
Motion Computing Tablet PC
 Motion Computing Tablet PC TRUSTED PLATFORM MODULE (TPM) ACTIVATION User Guide Trusted Platform Module Activation With the Infineon Security Platform Tools and the built-in Trusted Computing Group compliant
Motion Computing Tablet PC TRUSTED PLATFORM MODULE (TPM) ACTIVATION User Guide Trusted Platform Module Activation With the Infineon Security Platform Tools and the built-in Trusted Computing Group compliant
Hyper-V Protection. User guide
 Hyper-V Protection User guide Contents 1. Hyper-V overview... 2 Documentation... 2 Licensing... 2 Hyper-V requirements... 2 2. Hyper-V protection features... 3 Windows 2012 R1/R2 Hyper-V support... 3 Custom
Hyper-V Protection User guide Contents 1. Hyper-V overview... 2 Documentation... 2 Licensing... 2 Hyper-V requirements... 2 2. Hyper-V protection features... 3 Windows 2012 R1/R2 Hyper-V support... 3 Custom
Guide how to protect your private data with Rohos Disk Encryption
 Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options
Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options
How To Restore Your Data On A Backup By Mozy (Windows) On A Pc Or Macbook Or Macintosh (Windows 2) On Your Computer Or Mac) On An Pc Or Ipad (Windows 3) On Pc Or Pc Or Micro
 Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Sync Tool for Clarion NX700/NX509/NP509 Series
 1 Introduction Sync Tool for Clarion NX700/NX509/NP509 Series User Guide The Sync Tool is a downloadable application that enables you to update the navigation software, maps and other content included
1 Introduction Sync Tool for Clarion NX700/NX509/NP509 Series User Guide The Sync Tool is a downloadable application that enables you to update the navigation software, maps and other content included
Connect to the Sheridan College / Gillette College - STUDENT Secure Wireless Network with the PEAP Client (Windows XP Pro)
 Contents Connect to the Sheridan College / Gillette College - STUDENT Secure Wireless Network with the PEAP Client (Windows XP Pro) 1. Introduction 2. Configuring the Sheridan College / Gillette College
Contents Connect to the Sheridan College / Gillette College - STUDENT Secure Wireless Network with the PEAP Client (Windows XP Pro) 1. Introduction 2. Configuring the Sheridan College / Gillette College
Comodo Disk Encryption
 Comodo Disk Encryption Version 2.0 User Guide Version 2.0.122010 Versi Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1.Comodo Disk Encryption Introduction... 3
Comodo Disk Encryption Version 2.0 User Guide Version 2.0.122010 Versi Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1.Comodo Disk Encryption Introduction... 3
For paid computer support call 604-518-6695 http://www.netdigix.com [email protected]
 Setting up your vpn connection on windows 2000 or XP in continuation from installing x.509 certificate on windows (please do not continue if you have not installed your x.509 certificate): Instructions
Setting up your vpn connection on windows 2000 or XP in continuation from installing x.509 certificate on windows (please do not continue if you have not installed your x.509 certificate): Instructions
SupportDesk Extensions Installation Guide Extension Service - Versions 6.9 8.5
 SupportDesk Extensions Installation Guide Extension Service - Versions 6.9 8.5 Richmond Systems Ltd, West House, West Street, Haslemere, Surrey, GU27 2AB Tel: +44 (0)1428 641616 - Fax: +44 (0)1428 641717
SupportDesk Extensions Installation Guide Extension Service - Versions 6.9 8.5 Richmond Systems Ltd, West House, West Street, Haslemere, Surrey, GU27 2AB Tel: +44 (0)1428 641616 - Fax: +44 (0)1428 641717
