The Cybersecurity Research Alliance
|
|
|
- Collin Rice
- 8 years ago
- Views:
Transcription
1 The Cybersecurity Research Alliance Executive Summary Motivation is a national priority that must be addressed to defend our society economy from attacks that undermine their digital foundation. A coherent cyber security R&D strategy that encourages public private partnerships is the foundation for addressing these challenges. Public private R&D partnerships are critically important because roughly ninety percent of the United States critical infrastructure, as identified by the Department of Homel Security, is privately owned operated [3]. Government, industry academic research institutions are motivated by the same set of fundamental cyber security challenges. Yet, as illustrated in Figure 1, each has largely different perceptions of the relative priorities vastly divergent processes to define their research agendas. Govt Per Agency, Government R&D Policy Priorities RFIs RFPs BAAs Government funding Projects address Govt critical I/S protection Security Solutions to protect the Critical Infrastructure Fundamental Long-sting Problems Industry Industry Projection Of Priorities Markets Funding from Industry, Venture Capital, Government Sources Projects target industry profits Technologies solutions to fuel enterprise growth Academia Academic Research Agenda Funding from Government Industry Sources Projects target publishable innovation & prototypes Inventions, Stards Best Practices Silo ed uncoordinated strategies policies Lack of large investment in key game Changing technologies Multiple, silo ed disconnected R&D initiatives Point, Technologies, Stards Best Practices Figure 1: The Status Quo Government invests primarily in R&D that is critically important to the security of the nation but cannot ensure the commercial applicability productization of the technologies developed.
2 Corporate research focuses on developing innovations to fuel the organic growth of their enterprises. These innovations are viewed as strategic assets for competing in the marketplace. But industry is not motivated to invest in cyber security research development that does not have near-term tangible economic benefits. Academia primarily engages in long-term basic applied research in cyber security which pushes the frontier of what is known possible. However, this frontier is often disconnected from the operational reality. Members of this community often find it difficult to move beyond first-level deliverables, such as research papers limited prototypes. Cyber Security Research Alliance (CSRA) Fundamental Long-sting Cyber Security Problems Govt Industry Academia Per Agency, Government Cyber Security R&D Policy Priorities Industry Projection Of Cyber Security Priorities Markets Academic Cyber Security Research Agenda RFIs Government RFPs BAAs Government funding Academia Industry Industry Private Funding (e.g. Venture Capital) EXPECTATION: projects address fundamental problems, receive significant investment lead to Innovative, practical publishable results that can create future markets Security Solutions to protect the Critical Infrastructure Technologies Solutions Inventions, Stards Best Practices Innovation Timeline Figure 2 : Improving Collaboration in Cyber Security R&D A novel approach is needed to move the focus of cyber security research from applied, incremental disconnected projects to game changing cyber security technologies (see Figure 2 above). Such an approach should address inefficiencies in current cyber security R&D, amplify investments made by stakeholders, enable stronger more action-oriented collaboration alliances. In addition, this approach needs to be helpful in devising novel collaboration models among stakeholders at the international level. An ad-hoc group of stakeholders from industry has joined together to propose the idea of the Research Alliance (CSRA) to serve as a forum to achieve fundamental game change in cyber security to facilitate public-private partnerships that orchestrate a more focused, coordinated concerted approach to cybersecurity R&D. The CSRA mission statement is as follows:
3 Foster the research development of game changing solutions to critical cyber security challenges through effective government, industry, academia partnerships CSRA will have a long term (e.g. one decade) view of what industry, government academia need to do in order to make game change happen. CSRA will identify areas of cyber security research where game changing approaches could have a significant impact. CSRA will seek input from stakeholders across government, academia, industry to identify promising research methodologies directions that may have been underemphasized as a result of insufficient funding, fragmented engagement by the stakeholders, imperfect collaboration models in cyber security R&D. CSRA will define a consistent multidisciplinary view of the area of research in question organize scoping exercises to define it further, e.g., via workshops that develop recommendations to inform supporting research or development. CSRA will socialize these research agendas developed by the stakeholders obtain the support necessary to define, implement facilitate the deployment of these game changing solutions. Bringing different stakeholders together in a shared collaborative environment is an essential first step. CSRA will be organized to support agile operations in order to enable stakeholders to work on the orchestration of technological market forces in support of game change; requisite development of new technologies; support for coordinated cyber security R&D policy focused research agendas aligned with national priorities; defining funding priorities for cyber security R&D. CSRA will benefit from government participation in various ways: government research programs may invest funds or allocate personnel to work at the Institute; the government will also be encouraged to provide experts to serve on the CSRA Technical Advisory Committee participate in planning exercises other workshops. CSRA invites wide participation by government agencies responsible for various components of cybersecurity R&D R&D strategy. In addition to defining research agendas, CSRA will engage in research directly. CSRA will seek funding from government agencies that can be directed specifically toward making progress on these gr challenges or used internally as CSRA developed internal research capabilities. The CSRA stakeholderbased funding allocation responsibility will ensure that participating agencies facilitate projects that will have a stronger likelihood of adoption by industry. Thus, CSRA, from the very beginning, can ensure that all the stakeholders are engaged in order to create new technologies that have an increased opportunity for commercialization for the development of new game-changing business models. In the midterm, CSRA will have a dedicated research staff with the capability to conduct research in house. Complementing in-house research, CSRA will develop novel programs collaboration models for joint projects among industry, academia, government to address these gr challenges. CSRA will also
4 define models that permit international collaboration on projects that yield themselves to this approach, in order to further amplify the impact of the technologies that are developed with CSRA s participation. Tracking CyberSecurity R&D Activities CSRA will track relevant cyber security research activities develop a broad picture of these activities available to CSRA membership affiliates. Tracking relevant cyber security R&D will enable CSRA to become a key focal point for integrating game changing activities in cyber security R&D, by ensuring efficient coverage of the main components in game changing research agendas. Greater awareness of cyber security R&D lscape, in the US internationally, can help CSRA its potential affiliates develop greater agility in approaching the highly dynamic cyber security R&D space. CSRA will also work with government funding agencies to provide input into the definition of cyber security R&D agendas. CSRA can serve as a body to help government assess the quality relevance of research, funding programs initiatives related to cyber security. Technology Transfer CSRA will develop novel models for spurring more effective ideas for commercialization of technology from academia federal research laboratories focusing on game changing technologies that can have a broad impact on multiple technology areas. IP developed during the course of R&D efforts being led supported by CSRA will be made available to CSRA membership according to terms defined in the bylaws. Organizational Structure CSRA is envisioned as a non-profit organization with the organizational structure consisting of (a) industry members, (b) a Board of Directors, (c) dedicated staff, (d) working groups, (e) a Technical Advisory Committee. Members of CSRA will be drawn from industry constituents involved in cyber security R&D, system integrators, owners operators of critical infrastructures, academia. CSRA membership will be tiered to suit the needs goals of the stakeholders a structure that is agile can accommodate multiple collaboration models engagement in diverse cyber security initiatives. Members will pay an annual fee. All members will get preferential access to CSRA deliverables, their roles will be differentiated based on membership tiers defined in bylaws. CSRA will have an open structure, where members can move from tier to tier based on the procedures defined in the bylaws. CSRA can start as a lightweight organization, with minimal engagement of dedicated staff. As CSRA activities develop, the organization will have some dedicated staff that is responsible for the day to day operations of CSRA, including engaging in research, management of the budget funding programs, public relations, special events (such as workshops), other operational matters. The staff will be led by an Executive Director, who is appointed by the Board. Research may be done by Visiting or Permanent Fellows who
5 come from industry, academia, or government, together with CSRAI affiliated groups, for participation in specific research initiatives. CSRA will have a Board of Directors, which will establish broad policies objectives; elect a President; select,, as the organization develops, appoint, support review the performance of the Executive Director; ensure that CSRA has adequate financial resources manage these resources; approve the annual budgets; be accountable to the membership for the organization s performance. The Board of Directors will be comprised of representatives of the highest tier members following the rules defined in the bylaws. CSRA will have a Technical Advisory Committee. The Advisory Committee will advise the Board of Directors working groups on the technical direction that CSRA should be taking including the creation or dissolution of working groups, evaluation of the progress of the working groups. The Advisory Committee will consist of participants from industry, academia, government, will be appointed by the Board of Directors. CSRA will organize activities by Working Groups, which are focused on a particular gr challenge, typically defined in the course of a series of workshops. The working groups will be responsible for the creation of deliverables including: Technical reports white papers Policy recommendations Prototypes Specifications to support stards development Testbeds or data repositories Software Workshops other events Intellectual Property Each working group will be chaired or co-chaired by a CSRA Board member. Participation in the working groups is open to all members associate members from industry, academia or government, subject to the Board s approval. The intent is to get the most capable people involved, who are the most knowledgeable about the particular topic being addressed. Stages of Development CSRA intends to progress rapidly through three phases of growth In order to progress beyond the status quo (shown in Figure 1): Coordination testing of approaches to cyber security R&D. The initial ramp-up period starts when the organization is formed, begins to grow starts participation in activities described in this document. CSRA will implement a coordination infrastructure approach that supports greater cohesion in cyber security R&D provides a forum to facilitate the exploratory execution stages of research where game change is a viable approach. CSRA will establish
6 relationships with agencies departments responsible for strategy funding of cyber security R&D. CSRA will also provide awareness of related cyber security research initiatives that are conducted by other entities worldwide establish a relationship with them as permitted by US law. CSRA will work to increase membership, ensure that members with critical expertise capabilities have the opportunity to participate in specific initiatives. Initially, CSRA will be largely a virtual organization with minimal permanent staff engaged primarily in coordination of activities. CSRA will be run mostly through the efforts of initial industry members. In this, CSRA will not be different from the path adopted by many industry consortia. A Board of Directors a Technical Advisory Committee will be established in this first year. CSRA will select one game change-related topic to explore in depth, by running a workshop establishing a working group to make progress against that topic. The output of this effort will be a document which will define the gr challenges in this area a research agenda required to make progress on the problem. CSRA will then work with the appropriate stakeholders to ensure that some initial progress is made on executing this research agenda. During the initial period, CSRA will finalize its long term strategy, including strategy for R&D agenda building, international collaboration, research execution. CSRA will establish relationships with the main stakeholders in cyber security R&D seek sponsorship funding for an exped research agenda. During this phase, CSRA will also seek to provide industry input for cyber security R&D strategy development. Development of Game Changing Agenda in Cyber Security. CSRA will mature to become a forum for formulating a shared cyber security R&D agenda focusing on hard problems in cyber security that can be addressed via game change. CSRA members will collaborate among themselves with other organizations in order to assess prioritize fundamental cyber security problems. The resulting consensus view will be presented in the form of a Cyber Security Research Outlook (CRO) to inform direct concrete planning for the advancement of key game change initiatives. The CRO will be an evolving roadmap that reflects the sequence of pressing technology, policy, operational deployment obstacles that need to be overcome in order to remove the advantage from attackers strengthen cyber security defenses. It will be a living document updated regularly. CSRA will build on its work during phase 1 by executing on the research agenda defined during that phase selecting new gr challenge problems to explore. CSRA will create populate a database of relevant cyber security activities, which will be made available to CSRA membership. CSRA will redirect some small amount of funding to at least one strategically important target, seek more substantial funding starting from Phase 3. CSRA will also begin to execute the international collaboration strategy. In Phase 2, CSRA will have a physical presence, an Executive Director, a small administrative staff.
7 Execution of the Shared R&D Agenda. In order to break the cycle of incremental improvements to security that struggle to keep pace with the innovativeness of attackers, CSRA will evolve to become a facilitator for the development technology transfer of game changing solutions to hard broadly applicable cyber security problems. CSRA supported efforts will have a scope ranging from the concept stage of potentially game changing approaches to research, development, productization, deployment of these solutions, drawing on the expertise of CSRA s members, stakeholders, collaborators. Academia government participation as well as significant levels of government funding are necessary at this stage. By Phase 3, CSRA will be a mature, fully staffed organization with the ability to perform in house research.
Request for Information National Network for Manufacturing Innovation (NNMI)
 Request for Information National Network for Manufacturing Innovation (NNMI) At the College of Engineering at the University of California, Berkeley, we believe that advanced manufacturing has tremendous
Request for Information National Network for Manufacturing Innovation (NNMI) At the College of Engineering at the University of California, Berkeley, we believe that advanced manufacturing has tremendous
NIST Cloud Computing Program Activities
 NIST Cloud Computing Program Overview The NIST Cloud Computing Program includes Strategic and Tactical efforts which were initiated in parallel, and are integrated as shown below: NIST Cloud Computing
NIST Cloud Computing Program Overview The NIST Cloud Computing Program includes Strategic and Tactical efforts which were initiated in parallel, and are integrated as shown below: NIST Cloud Computing
HEP Software Consortium
 HEP Software Consortium Lothar Bauerdick, Paolo Calafiura, Peter Elmer, Liz Sexton-Kennedy, Panagiotis Spentzouris, Torre Wenaus, Avi Yagil May 28, 2014 1 Objective HEP computing is facing many challenges
HEP Software Consortium Lothar Bauerdick, Paolo Calafiura, Peter Elmer, Liz Sexton-Kennedy, Panagiotis Spentzouris, Torre Wenaus, Avi Yagil May 28, 2014 1 Objective HEP computing is facing many challenges
Comments in response to:
 From: Downing, Christopher C [mailto:chris.downing@innovate.gatech.edu] Sent: Tuesday, September 20, 2011 1:20 PM To: amtech Cc: 'Stephen Cross'; 'Monique Tavares'; 'ben wang' Subject: AMTech Comments
From: Downing, Christopher C [mailto:chris.downing@innovate.gatech.edu] Sent: Tuesday, September 20, 2011 1:20 PM To: amtech Cc: 'Stephen Cross'; 'Monique Tavares'; 'ben wang' Subject: AMTech Comments
IPROVE Innovation Partnership for a Roadmapon VaccinesinEurope
 IPROVE Innovation Partnership for a Roadmapon VaccinesinEurope IPROVE IN BRIEF What is IPROVE? Whydo we need IPROVE? IPROVE in actions (How?) Partnership (Who?) WHAT An EU project (FP7) financed by the
IPROVE Innovation Partnership for a Roadmapon VaccinesinEurope IPROVE IN BRIEF What is IPROVE? Whydo we need IPROVE? IPROVE in actions (How?) Partnership (Who?) WHAT An EU project (FP7) financed by the
Adopting a Continuous Integration / Continuous Delivery Model to Improve Software Delivery
 Customer Success Stories TEKsystems Global Services Adopting a Continuous Integration / Continuous Delivery Model to Improve Software Delivery COMMUNICATIONS AGILE TRANSFORMATION SERVICES Executive Summary
Customer Success Stories TEKsystems Global Services Adopting a Continuous Integration / Continuous Delivery Model to Improve Software Delivery COMMUNICATIONS AGILE TRANSFORMATION SERVICES Executive Summary
CALIFORNIA GIS COUNCIL CHARTER
 CALIFORNIA GIS COUNCIL CHARTER ADOPTED JANUARY 7, 2015 SECTION 1: FINDING AND DECLARATIONS WHEREAS: A. Geographic Information Systems (GIS) are a critical tool for improving the quality, accuracy and responsiveness
CALIFORNIA GIS COUNCIL CHARTER ADOPTED JANUARY 7, 2015 SECTION 1: FINDING AND DECLARATIONS WHEREAS: A. Geographic Information Systems (GIS) are a critical tool for improving the quality, accuracy and responsiveness
Cybersecurity: Mission integration to protect your assets
 Cybersecurity: Mission integration to protect your assets C Y B E R S O L U T I O N S P O L I C Y O P E R AT I O N S P E O P L E T E C H N O L O G Y M A N A G E M E N T Ready for what s next Cyber solutions
Cybersecurity: Mission integration to protect your assets C Y B E R S O L U T I O N S P O L I C Y O P E R AT I O N S P E O P L E T E C H N O L O G Y M A N A G E M E N T Ready for what s next Cyber solutions
Benefits of Collaborative Science and Innovation - Improve Cyber Security
 Public-Private Cooperation in Cybersecurity Research Strategy Development across the Globe A View from the U.S. Department of Homeland Security (DHS) Background Envision a future... in which universities
Public-Private Cooperation in Cybersecurity Research Strategy Development across the Globe A View from the U.S. Department of Homeland Security (DHS) Background Envision a future... in which universities
The Communications Audit NEVER MORE RELEVANT, NEVER MORE VALUABLE:
 WHITE PAPER The Communications Audit NEVER MORE RELEVANT, NEVER MORE VALUABLE: VALUE PROPOSITION OBJECTIVES METHODOLOGY BY GARY DOLZALL CHIEF COMMUNICATIONS OFFICER I. INTRODUCTION: THE VALUE PROPOSITION
WHITE PAPER The Communications Audit NEVER MORE RELEVANT, NEVER MORE VALUABLE: VALUE PROPOSITION OBJECTIVES METHODOLOGY BY GARY DOLZALL CHIEF COMMUNICATIONS OFFICER I. INTRODUCTION: THE VALUE PROPOSITION
How To Write A Cybersecurity Framework
 NIST Cybersecurity Framework Overview Executive Order 13636 Improving Critical Infrastructure Cybersecurity 2nd ENISA International Conference on Cyber Crisis Cooperation and Exercises Executive Order
NIST Cybersecurity Framework Overview Executive Order 13636 Improving Critical Infrastructure Cybersecurity 2nd ENISA International Conference on Cyber Crisis Cooperation and Exercises Executive Order
Critical Infrastructure Cybersecurity Framework. Overview and Status. Executive Order 13636 Improving Critical Infrastructure Cybersecurity
 Critical Infrastructure Cybersecurity Framework Overview and Status Executive Order 13636 Improving Critical Infrastructure Cybersecurity Executive Order: Improving Critical Infrastructure Cybersecurity
Critical Infrastructure Cybersecurity Framework Overview and Status Executive Order 13636 Improving Critical Infrastructure Cybersecurity Executive Order: Improving Critical Infrastructure Cybersecurity
Cybersecurity Framework: Current Status and Next Steps
 Cybersecurity Framework: Current Status and Next Steps Federal Advisory Committee on Insurance November 6, 2014 Adam Sedgewick Senior IT Policy Advisor Adam.Sedgewick@nist.gov National Institute of Standards
Cybersecurity Framework: Current Status and Next Steps Federal Advisory Committee on Insurance November 6, 2014 Adam Sedgewick Senior IT Policy Advisor Adam.Sedgewick@nist.gov National Institute of Standards
NASCIO 2014 State IT Recognition Awards
 NASCIO 2014 State IT Recognition Awards Project: California Cybersecurity Task Force Category: Cybersecurity Initiatives Project Initiation Date: September, 2012 Project Completion Date: May 2013 Carlos
NASCIO 2014 State IT Recognition Awards Project: California Cybersecurity Task Force Category: Cybersecurity Initiatives Project Initiation Date: September, 2012 Project Completion Date: May 2013 Carlos
ISO Strategic Plan 2011-2015. Solutions to Global Challenges
 ISO Strategic Plan 2011-2015 Solutions to Global Challenges ISO the International Organization for Standardization ISO has a membership of 163* national standards bodies from countries large and small,
ISO Strategic Plan 2011-2015 Solutions to Global Challenges ISO the International Organization for Standardization ISO has a membership of 163* national standards bodies from countries large and small,
Partnership for Cyber Resilience
 Partnership for Cyber Resilience Principles for Cyber Resilience 1. Recognition of interdependence: All parties have a role in fostering a resilient shared digital space 2. Role of leadership: Encourage
Partnership for Cyber Resilience Principles for Cyber Resilience 1. Recognition of interdependence: All parties have a role in fostering a resilient shared digital space 2. Role of leadership: Encourage
EXECUTIVE ORDER 13702 - - - - - - - CREATING A NATIONAL STRATEGIC COMPUTING INITIATIVE. By the authority vested in me as President by the
 This document is scheduled to be published in the Federal Register on 08/03/2015 and available online at http://federalregister.gov/a/2015-19183, and on FDsys.gov EXECUTIVE ORDER 13702 - - - - - - - CREATING
This document is scheduled to be published in the Federal Register on 08/03/2015 and available online at http://federalregister.gov/a/2015-19183, and on FDsys.gov EXECUTIVE ORDER 13702 - - - - - - - CREATING
Programmes and Effects of the CESSDA Trust Project
 WP3 - Strengthening and widening through planning and engagement Start month: 1 End month: 24 Objectives The overall objective of WP3 is to deliver a state of play evaluation of social science data archives
WP3 - Strengthening and widening through planning and engagement Start month: 1 End month: 24 Objectives The overall objective of WP3 is to deliver a state of play evaluation of social science data archives
State of Minnesota IT Governance Framework
 State of Minnesota IT Governance Framework June 2012 Table of Contents Table of Contents... 2 Introduction... 4 IT Governance Overview... 4 Process for Developing the New Framework... 4 Management of the
State of Minnesota IT Governance Framework June 2012 Table of Contents Table of Contents... 2 Introduction... 4 IT Governance Overview... 4 Process for Developing the New Framework... 4 Management of the
REQUEST FOR PROPOSALS: CENTER FOR LONG-TERM CYBERSECURITY
 102 S Hall Rd Berkeley, CA 94720 510-664-7506 cltc@berkeley.edu REQUEST FOR PROPOSALS: CENTER FOR LONG-TERM CYBERSECURITY The University of California, Berkeley Center for Long-Term Cybersecurity (CLTC)
102 S Hall Rd Berkeley, CA 94720 510-664-7506 cltc@berkeley.edu REQUEST FOR PROPOSALS: CENTER FOR LONG-TERM CYBERSECURITY The University of California, Berkeley Center for Long-Term Cybersecurity (CLTC)
Docket No. DHS-2015-0017, Notice of Request for Public Comment Regarding Information Sharing and Analysis Organizations
 Submitted via ISAO@hq.dhs.gov and www.regulations.gov July 10, 2015 Mr. Michael Echols Director, JPMO-ISAO Coordinator NPPD, Department of Homeland Security 245 Murray Lane, Mail Stop 0615 Arlington VA
Submitted via ISAO@hq.dhs.gov and www.regulations.gov July 10, 2015 Mr. Michael Echols Director, JPMO-ISAO Coordinator NPPD, Department of Homeland Security 245 Murray Lane, Mail Stop 0615 Arlington VA
ITU National Cybersecurity/CIIP Self-Assessment Tool
 ITU National Cybersecurity/CIIP Self-Assessment Tool ICT Applications and Cybersecurity Division Policies and Strategies Department ITU Telecommunication Development Sector April 2009 Revised Draft For
ITU National Cybersecurity/CIIP Self-Assessment Tool ICT Applications and Cybersecurity Division Policies and Strategies Department ITU Telecommunication Development Sector April 2009 Revised Draft For
National Security & Homeland Security Councils Review of National Cyber Security Policy. Submission of the Business Software Alliance March 19, 2009
 National Security & Homeland Security Councils Review of National Cyber Security Policy Submission of the Business Software Alliance March 19, 2009 Question # 1: What is the federal government s role in
National Security & Homeland Security Councils Review of National Cyber Security Policy Submission of the Business Software Alliance March 19, 2009 Question # 1: What is the federal government s role in
Incident Management & Forensics Working Group. Charter
 Incident Management & Forensics Working Group Charter February 2013 2013 Cloud Security Alliance All Rights Reserved All rights reserved. You may download, store, display on your computer, view, print,
Incident Management & Forensics Working Group Charter February 2013 2013 Cloud Security Alliance All Rights Reserved All rights reserved. You may download, store, display on your computer, view, print,
In December 2011, the White House Office of Science. Introducing the federal cybersecurity R&D strategic plan. Leaping ahead on cybersecurity
 Introducing the federal cybersecurity R&D strategic plan Douglas Maughan, Bill Newhouse, and Tomas Vagoun In December 2011, the White House Office of Science and Technology Policy (OSTP) released the document,
Introducing the federal cybersecurity R&D strategic plan Douglas Maughan, Bill Newhouse, and Tomas Vagoun In December 2011, the White House Office of Science and Technology Policy (OSTP) released the document,
Department of Commerce. National Institute of Standards and Technology
 Department of Commerce National Institute of Standards and Technology Three- Year Programmatic Plan FY 2012 FY 2014 Table of Contents INTRODUCTION... 3 NIST: PROMOTING U.S. INNOVATION AND INDUSTRIAL COMPETITIVENESS...
Department of Commerce National Institute of Standards and Technology Three- Year Programmatic Plan FY 2012 FY 2014 Table of Contents INTRODUCTION... 3 NIST: PROMOTING U.S. INNOVATION AND INDUSTRIAL COMPETITIVENESS...
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T I D C M a r k e t S c a p e : U. S. B u s i n e s s C o n s u l t i n g S e r v i c
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T I D C M a r k e t S c a p e : U. S. B u s i n e s s C o n s u l t i n g S e r v i c
San Diego State University Strategic Plan: Economic Development Working Group Report. Introduction
 San Diego State University Strategic Plan: Economic Development Working Group Report Introduction By celebrating and expanding existing partnerships among all SDSU s service communities, and continuing
San Diego State University Strategic Plan: Economic Development Working Group Report Introduction By celebrating and expanding existing partnerships among all SDSU s service communities, and continuing
Mary Ellen Seale National Protection and Programs Directorate May 16, 2012
 Finding & Integrating CyberTech in the U.S. Government Mary Ellen Seale National Protection and Programs Directorate May 16, 2012 Obtaining Federal Funding Understanding the Landscape Contracting Small
Finding & Integrating CyberTech in the U.S. Government Mary Ellen Seale National Protection and Programs Directorate May 16, 2012 Obtaining Federal Funding Understanding the Landscape Contracting Small
NIST Cybersecurity Framework. ARC World Industry Forum 2014
 NIST Cybersecurity Framework Vicky Yan Pillitteri NIST ARC World Industry Forum 2014 February 10-13, 2014 Orlando, FL Executive Order 13636 Improving Critical Infrastructure Cybersecurity It is the policy
NIST Cybersecurity Framework Vicky Yan Pillitteri NIST ARC World Industry Forum 2014 February 10-13, 2014 Orlando, FL Executive Order 13636 Improving Critical Infrastructure Cybersecurity It is the policy
PAINTER EXECUTIVE SEARCH
 PAINTER EXECUTIVE SEARCH Position Description Painter Executive Search is supporting the in a search for an experienced to lead a broad regional coalition of Bay Area land conservation agencies and organizations
PAINTER EXECUTIVE SEARCH Position Description Painter Executive Search is supporting the in a search for an experienced to lead a broad regional coalition of Bay Area land conservation agencies and organizations
Foundation for HEP Software
 Foundation for HEP Software (Richard Mount, 19 May 2014) Preamble: Software is central to all aspects of modern High Energy Physics (HEP) experiments and therefore to their scientific success. Offline
Foundation for HEP Software (Richard Mount, 19 May 2014) Preamble: Software is central to all aspects of modern High Energy Physics (HEP) experiments and therefore to their scientific success. Offline
Project Concept Proposal Guide Lines
 Project Concept Proposal Guide Lines Contents 1.0 Overview 2 1.1 Background... 2 1.2 Process.. 2 2.0 Content of Proposal Main Body 3 2.1 Cover Page 3 2.2 Technical and Programmatic Background 4 2.3 Project
Project Concept Proposal Guide Lines Contents 1.0 Overview 2 1.1 Background... 2 1.2 Process.. 2 2.0 Content of Proposal Main Body 3 2.1 Cover Page 3 2.2 Technical and Programmatic Background 4 2.3 Project
PROJECT AUDIENCE REQUEST FOR PROPOSAL: Business Plan
 CONTENTS Introduction Proposal Submission deadline Background Summary of Goals Project Details o Business Plan Participants Financial Planning o Business structure/leadership model Framework Board governance/structure
CONTENTS Introduction Proposal Submission deadline Background Summary of Goals Project Details o Business Plan Participants Financial Planning o Business structure/leadership model Framework Board governance/structure
Principles of IT Governance
 Principles of IT Governance Governance of enterprise IT focuses on delivering services to support top line growth while moving operational savings to the bottom line. The management of IT services has
Principles of IT Governance Governance of enterprise IT focuses on delivering services to support top line growth while moving operational savings to the bottom line. The management of IT services has
How To Help A Project In The Germany
 University-Industry Liaison in the Argentine ICT Sector Alejandra M. Alvaredo 1, M. Florencia Rossaro 1 1 University-Industry Liaison Area, Manuel Sadosky Foundation Abstract The Argentine ICT sector has
University-Industry Liaison in the Argentine ICT Sector Alejandra M. Alvaredo 1, M. Florencia Rossaro 1 1 University-Industry Liaison Area, Manuel Sadosky Foundation Abstract The Argentine ICT sector has
State of California Department of Transportation. Transportation System Data Business Plan
 DRAFT Page i State of California Department of Transportation Transportation System Data Business Plan RFO# TSI DPA-0003 September 29, 2011 DRAFT Page ii Table of Contents Executive Summary... 4 Chapter
DRAFT Page i State of California Department of Transportation Transportation System Data Business Plan RFO# TSI DPA-0003 September 29, 2011 DRAFT Page ii Table of Contents Executive Summary... 4 Chapter
CHREATE: Phase Three Design and Plan John Boudreau, Ian Ziskin & Carolyn Rearick
 CHREATE: Phase Three Design and Plan John Boudreau, Ian Ziskin & Carolyn Rearick Overview This document provides the business plan for Phase Three of the CHREATE project. It contains the projects, deliverables
CHREATE: Phase Three Design and Plan John Boudreau, Ian Ziskin & Carolyn Rearick Overview This document provides the business plan for Phase Three of the CHREATE project. It contains the projects, deliverables
UNITED NATIONS COMMISSION ON SCIENCE AND TECHNOLOGY FOR DEVELOPMENT
 UNITED NATIONS COMMISSION ON SCIENCE AND TECHNOLOGY FOR DEVELOPMENT Chairman s draft recommendations on the basis of the consolidated version of the rolling document A. Shaping the outcomes of IGF meetings
UNITED NATIONS COMMISSION ON SCIENCE AND TECHNOLOGY FOR DEVELOPMENT Chairman s draft recommendations on the basis of the consolidated version of the rolling document A. Shaping the outcomes of IGF meetings
Tools for Managing and Measuring the Value of Big Data Projects
 Tools for Managing and Measuring the Value of Big Data Projects Abstract Big Data and analytics focused projects have undetermined scope and changing requirements at their core. There is high risk of loss
Tools for Managing and Measuring the Value of Big Data Projects Abstract Big Data and analytics focused projects have undetermined scope and changing requirements at their core. There is high risk of loss
NEW MEXICO ECONOMIC DEVELOPMENT DEPARTMENT STATE EXPENDITURES FOR BUSINESS INCUBATORS ACT REQUEST FOR INCUBATOR CERTIFICATION
 NEW MEXICO ECONOMIC DEVELOPMENT DEPARTMENT STATE EXPENDITURES FOR BUSINESS INCUBATORS ACT REQUEST FOR INCUBATOR CERTIFICATION 1. Requesting Agency: 2. Address: 3. Phone: Fax: Email: 4. Type of entity:
NEW MEXICO ECONOMIC DEVELOPMENT DEPARTMENT STATE EXPENDITURES FOR BUSINESS INCUBATORS ACT REQUEST FOR INCUBATOR CERTIFICATION 1. Requesting Agency: 2. Address: 3. Phone: Fax: Email: 4. Type of entity:
Healthcare Internal Audit: In a Time of Transition
 The 2015 State of the Internal Audit Profession Study Healthcare Internal Audit: In a Time of Transition The healthcare industry in the United States is facing many challenges with the enactment of legislation
The 2015 State of the Internal Audit Profession Study Healthcare Internal Audit: In a Time of Transition The healthcare industry in the United States is facing many challenges with the enactment of legislation
OAS CYBER SECURITY INITIATIVE. Global Forum on Cyber Expertise (GFCE)
 OAS CYBER SECURITY INITIATIVE Global Forum on Cyber Expertise (GFCE) CONTENTS 2 3 9 12 OAS Regional Cyber Security Framework What we offer to our Member States How we do our work ANNEX -A- OAS CYBER SECURITY
OAS CYBER SECURITY INITIATIVE Global Forum on Cyber Expertise (GFCE) CONTENTS 2 3 9 12 OAS Regional Cyber Security Framework What we offer to our Member States How we do our work ANNEX -A- OAS CYBER SECURITY
EVALUATION GUIDELINES
 EVALUATION GUIDELINES Introduction This document outlines the reviewing process and defines the responsibilities of the participants in the process. It details a number of important issues, such as: FCT
EVALUATION GUIDELINES Introduction This document outlines the reviewing process and defines the responsibilities of the participants in the process. It details a number of important issues, such as: FCT
Sustaining the Race to the Top Reforms
 Sustaining the Race to the Top Reforms Race to the Top (RTTT) presents states with a unique opportunity to accelerate their efforts to graduate all high school students prepared for college, careers and
Sustaining the Race to the Top Reforms Race to the Top (RTTT) presents states with a unique opportunity to accelerate their efforts to graduate all high school students prepared for college, careers and
Cyber ROI. A practical approach to quantifying the financial benefits of cybersecurity
 Cyber ROI A practical approach to quantifying the financial benefits of cybersecurity Cyber Investment Challenges In 2015, global cybersecurity spending is expected to reach an all-time high of $76.9
Cyber ROI A practical approach to quantifying the financial benefits of cybersecurity Cyber Investment Challenges In 2015, global cybersecurity spending is expected to reach an all-time high of $76.9
ILA Strategic Plan 2012 2017
 ILA Strategic Plan 2012 2017 If you practice, study, or teach leadership; If you seek a community of people who share your passion for leadership; We invite you to be a vital part of the continued growth
ILA Strategic Plan 2012 2017 If you practice, study, or teach leadership; If you seek a community of people who share your passion for leadership; We invite you to be a vital part of the continued growth
Turning Strategic Insight Into Business Impact
 Turning Strategic Insight Into Business Impact VMware Accelerate Advisory Services Identify Opportunities and Create Strategies for the Journey to IT as a Service No longer relegated to simply keeping
Turning Strategic Insight Into Business Impact VMware Accelerate Advisory Services Identify Opportunities and Create Strategies for the Journey to IT as a Service No longer relegated to simply keeping
October 7, 2011. Presented to. The PMI Washington DC Chapter. Pedro Agosto. Director of Client Services, XA Systems, LLC. pedro.agosto@xasystems.
 October 7, 2011 Presented to The PMI Washington DC Chapter By Pedro Agosto Director of Client Services, XA Systems, LLC pedro.agosto@xasystems.com Introduction Re-evaluating IT Services Today s Challenges
October 7, 2011 Presented to The PMI Washington DC Chapter By Pedro Agosto Director of Client Services, XA Systems, LLC pedro.agosto@xasystems.com Introduction Re-evaluating IT Services Today s Challenges
Experience the commitment WHITE PAPER. Information Security Continuous Monitoring. Charting the Right Course. cgi.com 2014 CGI GROUP INC.
 Experience the commitment WHITE PAPER Information Security Continuous Monitoring Charting the Right Course May 2014 cgi.com 2014 CGI GROUP INC. During the last few months of 2013, six federal agencies
Experience the commitment WHITE PAPER Information Security Continuous Monitoring Charting the Right Course May 2014 cgi.com 2014 CGI GROUP INC. During the last few months of 2013, six federal agencies
CLOSING THE DOOR TO CYBER ATTACKS HOW ENTERPRISES CAN IMPLEMENT COMPREHENSIVE INFORMATION SECURITY
 CLOSING THE DOOR TO CYBER ATTACKS HOW ENTERPRISES CAN IMPLEMENT COMPREHENSIVE INFORMATION SECURITY CLOSING THE DOOR TO CYBER ATTACKS Cybersecurity and information security have become key challenges for
CLOSING THE DOOR TO CYBER ATTACKS HOW ENTERPRISES CAN IMPLEMENT COMPREHENSIVE INFORMATION SECURITY CLOSING THE DOOR TO CYBER ATTACKS Cybersecurity and information security have become key challenges for
Governance Structure
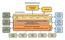 Secretariat -1 Chairs of Standing Committees - 3 Governance Structure Management Committee Secretariat Community and Municipal Consultative and Advisory Forum Board of Directors Principal Investigator
Secretariat -1 Chairs of Standing Committees - 3 Governance Structure Management Committee Secretariat Community and Municipal Consultative and Advisory Forum Board of Directors Principal Investigator
Role and Skill Descriptions. For An ITIL Implementation Project
 Role and Skill Descriptions For An ITIL Implementation Project The following skill traits were identified as fairly typical of those needed to execute many of the key activities identified: Customer Relationship
Role and Skill Descriptions For An ITIL Implementation Project The following skill traits were identified as fairly typical of those needed to execute many of the key activities identified: Customer Relationship
PART II THE ROAD AHEAD: IMPLEMENTING KNOWLEDGE MANAGEMENT
 PART II THE ROAD AHEAD: IMPLEMENTING KNOWLEDGE MANAGEMENT CHAPTER 4 THE 10-STEP KNOWLEDGE MANAGEMENT ROAD MAP IN THIS CHAPTER Understand the 10-step KM road map and how it applies to your company. Understand
PART II THE ROAD AHEAD: IMPLEMENTING KNOWLEDGE MANAGEMENT CHAPTER 4 THE 10-STEP KNOWLEDGE MANAGEMENT ROAD MAP IN THIS CHAPTER Understand the 10-step KM road map and how it applies to your company. Understand
USP Strategic Planning and Initiatives
 Prescription/Non-Prescription Stakeholder Forum Meeting #6 for 2010-2015 Tuesday, October 21, 2014 USP Strategic Planning and Initiatives Emily M. Kaine, MD Vice President, Strategy Building from our mission,
Prescription/Non-Prescription Stakeholder Forum Meeting #6 for 2010-2015 Tuesday, October 21, 2014 USP Strategic Planning and Initiatives Emily M. Kaine, MD Vice President, Strategy Building from our mission,
Developing and Enhancing Cyber Security Capabilities in the Region. Khaled Gamo Technology Advisor Ministry of communication and informatics
 Developing and Enhancing Cyber Security Capabilities in the Region Khaled Gamo Technology Advisor Ministry of communication and informatics 1 Content 1 2 3 Cyber Security Strategy and Key Requirement Efforts
Developing and Enhancing Cyber Security Capabilities in the Region Khaled Gamo Technology Advisor Ministry of communication and informatics 1 Content 1 2 3 Cyber Security Strategy and Key Requirement Efforts
SMEWG Strategic Plan 2013-2016
 /SMEWG35/035 SMEWG Strategic Plan 2013-2016 Purpose: Information Submitted by: Chair 35 th Small and Medium Enterprises Working Group Meeting St. Petersburg, Russia 1-2 August Strategic Plan 2013-2016
/SMEWG35/035 SMEWG Strategic Plan 2013-2016 Purpose: Information Submitted by: Chair 35 th Small and Medium Enterprises Working Group Meeting St. Petersburg, Russia 1-2 August Strategic Plan 2013-2016
How Winners Sell Outsourcing Services: Proven Best Practices
 , LLC Application Outsourcing: Consulting and Sales Training Services How Winners Sell Outsourcing Services: Proven Best Practices David J. Smith Principal, LLC djsmith@conscientiallc.com, LLC 2007 All
, LLC Application Outsourcing: Consulting and Sales Training Services How Winners Sell Outsourcing Services: Proven Best Practices David J. Smith Principal, LLC djsmith@conscientiallc.com, LLC 2007 All
PESC MEMBERSHIP 2010-2011
 PESC MEMBERSHIP 2010-2011 Postsecondary Electronic Standards Council 1250 Connecticut Avenue, NW ~ Suite 200 Washington, D.C. 20036 +1.202.261.6516 phone +1.202.261.6517 fax Unlocking the Power of Data
PESC MEMBERSHIP 2010-2011 Postsecondary Electronic Standards Council 1250 Connecticut Avenue, NW ~ Suite 200 Washington, D.C. 20036 +1.202.261.6516 phone +1.202.261.6517 fax Unlocking the Power of Data
Fortune 500 Medical Devices Company Addresses Unique Device Identification
 Fortune 500 Medical Devices Company Addresses Unique Device Identification New FDA regulation was driver for new data governance and technology strategies that could be leveraged for enterprise-wide benefit
Fortune 500 Medical Devices Company Addresses Unique Device Identification New FDA regulation was driver for new data governance and technology strategies that could be leveraged for enterprise-wide benefit
PREPARED TESTIMONY OF THE NATIONAL CYBER SECURITY ALLIANCE MICHAEL KAISER, EXECUTIVE DIRECTOR ON THE STATE OF CYBERSECURITY AND SMALL BUSINESS
 PREPARED TESTIMONY OF THE NATIONAL CYBER SECURITY ALLIANCE MICHAEL KAISER, EXECUTIVE DIRECTOR ON THE STATE OF CYBERSECURITY AND SMALL BUSINESS BEFORE THE COMMITTEE ON HOUSE SMALL BUSINESS SUBCOMMITTEE
PREPARED TESTIMONY OF THE NATIONAL CYBER SECURITY ALLIANCE MICHAEL KAISER, EXECUTIVE DIRECTOR ON THE STATE OF CYBERSECURITY AND SMALL BUSINESS BEFORE THE COMMITTEE ON HOUSE SMALL BUSINESS SUBCOMMITTEE
Due Process for the GRI Reporting Framework
 Introduction 1. All documents in the GRI Framework must be developed in accordance with the due process principles approved by the GRI Board of Directors and outlined in this document. The Technical Advisory
Introduction 1. All documents in the GRI Framework must be developed in accordance with the due process principles approved by the GRI Board of Directors and outlined in this document. The Technical Advisory
Cybersecurity Framework. Executive Order 13636 Improving Critical Infrastructure Cybersecurity
 Cybersecurity Framework Executive Order 13636 Improving Critical Infrastructure Cybersecurity National Institute of Standards and Technology (NIST) Mission To promote U.S. innovation and industrial competitiveness
Cybersecurity Framework Executive Order 13636 Improving Critical Infrastructure Cybersecurity National Institute of Standards and Technology (NIST) Mission To promote U.S. innovation and industrial competitiveness
Implementing a Data Governance Initiative
 Implementing a Data Governance Initiative Presented by: Linda A. Montemayor, Technical Director AT&T Agenda AT&T Business Alliance Data Governance Framework Data Governance Solutions: o Metadata Management
Implementing a Data Governance Initiative Presented by: Linda A. Montemayor, Technical Director AT&T Agenda AT&T Business Alliance Data Governance Framework Data Governance Solutions: o Metadata Management
knowledge management enabling winning offerings
 Business scenario knowledge management enabling winning offerings In today s rapidly changing and dynamic IT landscape, the IT industry is constantly faced with the challenge of keeping up with the pace
Business scenario knowledge management enabling winning offerings In today s rapidly changing and dynamic IT landscape, the IT industry is constantly faced with the challenge of keeping up with the pace
Security and Privacy Trends 2014
 2014 Agenda Today s cyber threats 3 You could be under cyber attack now! Improve 6 Awareness of cyber threats propels improvements Expand 11 Leading practices to combat cyber threats Innovate 20 To survive,
2014 Agenda Today s cyber threats 3 You could be under cyber attack now! Improve 6 Awareness of cyber threats propels improvements Expand 11 Leading practices to combat cyber threats Innovate 20 To survive,
Cybersecurity in the Utilities Sector Best Practices and Implementation 2014 Canadian Utilities IT & Telecom Conference September 24, 2014
 Cybersecurity in the Utilities Sector Best Practices and Implementation 2014 Canadian Utilities IT & Telecom Conference September 24, 2014 Victoria Yan Pillitteri Advisor for Information Systems Security
Cybersecurity in the Utilities Sector Best Practices and Implementation 2014 Canadian Utilities IT & Telecom Conference September 24, 2014 Victoria Yan Pillitteri Advisor for Information Systems Security
I D C T E C H N O L O G Y S P O T L I G H T. L e ve r a g i n g N e tw o r k Virtualization for B u s i n e s s D i fferentiation
 I D C T E C H N O L O G Y S P O T L I G H T L e ve r a g i n g N e tw o r k Virtualization for B u s i n e s s D i fferentiation July 2014 Adapted from The Network Virtualization Evolution in Telecom by
I D C T E C H N O L O G Y S P O T L I G H T L e ve r a g i n g N e tw o r k Virtualization for B u s i n e s s D i fferentiation July 2014 Adapted from The Network Virtualization Evolution in Telecom by
How To Understand And Understand The Concept Of Business Architecture
 WHITE PAPER Business Architecture: Dispelling Ten Common Myths William Ulrich, TSG, Inc. Whynde Kuehn, S2E Consulting Inc. Business Architecture: An Evolving Discipline B usiness architecture is a maturing
WHITE PAPER Business Architecture: Dispelling Ten Common Myths William Ulrich, TSG, Inc. Whynde Kuehn, S2E Consulting Inc. Business Architecture: An Evolving Discipline B usiness architecture is a maturing
Project Management Institute STRATEGIC PLAN. Prepared by: PMI Board of Directors
 Project Management Institute STRATEGIC PLAN Prepared by: PMI Board of Directors Last Revised: 30 November 2012 TABLE OF CONTENTS OVERVIEW... 1 PMI S CORE IDEOLOGY... 3 Core Purpose.... 3 Our Core Values...
Project Management Institute STRATEGIC PLAN Prepared by: PMI Board of Directors Last Revised: 30 November 2012 TABLE OF CONTENTS OVERVIEW... 1 PMI S CORE IDEOLOGY... 3 Core Purpose.... 3 Our Core Values...
Texas Infrastructure Council Planning and building the future for Texas' infrastructure
 TXIC Texas Infrastructure Council Planning and building the future for Texas' infrastructure Texas Infrastructure Council Mission To support state and local governments in the formation and implementation
TXIC Texas Infrastructure Council Planning and building the future for Texas' infrastructure Texas Infrastructure Council Mission To support state and local governments in the formation and implementation
Enterprise Architecture: A Governance Framework
 Enterprise Architecture: A Governance Framework Part I: Embedding Architecture into the Organization Sohel Aziz, Thomas Obitz, Reva Modi and Santonu Sarkar The whitepapers arei related to two sessions
Enterprise Architecture: A Governance Framework Part I: Embedding Architecture into the Organization Sohel Aziz, Thomas Obitz, Reva Modi and Santonu Sarkar The whitepapers arei related to two sessions
The Emergence of Security Business Intelligence: Risk
 The Emergence of Security Business Intelligence: Risk Management through Deep Analytics & Automation Mike Curtis Vice President of Technology Strategy December, 2011 Introduction As an industry we are
The Emergence of Security Business Intelligence: Risk Management through Deep Analytics & Automation Mike Curtis Vice President of Technology Strategy December, 2011 Introduction As an industry we are
Business Continuity for Cyber Threat
 Business Continuity for Cyber Threat April 1, 2014 Workshop Session #3 3:00 5:30 PM Susan Rogers, MBCP, MBCI Cyberwise CP S2 What happens when a computer program can activate physical machinery? Between
Business Continuity for Cyber Threat April 1, 2014 Workshop Session #3 3:00 5:30 PM Susan Rogers, MBCP, MBCI Cyberwise CP S2 What happens when a computer program can activate physical machinery? Between
ASAE s Job Task Analysis Strategic Level Competencies
 ASAE s Job Task Analysis Strategic Level Competencies During 2013, ASAE funded an extensive, psychometrically valid study to document the competencies essential to the practice of association management
ASAE s Job Task Analysis Strategic Level Competencies During 2013, ASAE funded an extensive, psychometrically valid study to document the competencies essential to the practice of association management
The Future of Census Bureau Operations
 The Future of Census Bureau Operations Version 1.0 April 25, 2013 The Future of Census Bureau Operations Page ii [This page intentionally left blank] The Future of Census Bureau Operations Page iii Document
The Future of Census Bureau Operations Version 1.0 April 25, 2013 The Future of Census Bureau Operations Page ii [This page intentionally left blank] The Future of Census Bureau Operations Page iii Document
STATE OF WISCONSIN INVESTMENT BOARD STRATEGIC PLAN 2014-2017
 STATE OF WISCONSIN INVESTMENT BOARD STRATEGIC PLAN 2014-2017 Note from the Executive Director The State of Wisconsin Investment Board (SWIB) has a sacred trust to fulfill our fiduciary duties to the trusts
STATE OF WISCONSIN INVESTMENT BOARD STRATEGIC PLAN 2014-2017 Note from the Executive Director The State of Wisconsin Investment Board (SWIB) has a sacred trust to fulfill our fiduciary duties to the trusts
Agile Master Data Management A Better Approach than Trial and Error
 Agile Master Data Management A Better Approach than Trial and Error A whitepaper by First San Francisco Partners First San Francisco Partners Whitepaper Executive Summary Market leading corporations are
Agile Master Data Management A Better Approach than Trial and Error A whitepaper by First San Francisco Partners First San Francisco Partners Whitepaper Executive Summary Market leading corporations are
Commercial Performance Management. Executive Summary. Commercial Performance Management
 Commercial Performance Management Executive Summary Copyright, All Rights Reserved, e-strategia Consulting Group, Inc. Integrated processes and digital tools to drive business results 1. Commercial Performance
Commercial Performance Management Executive Summary Copyright, All Rights Reserved, e-strategia Consulting Group, Inc. Integrated processes and digital tools to drive business results 1. Commercial Performance
OPTIMUS SBR. Optimizing Results with Business Intelligence Governance CHOICE TOOLS. PRECISION AIM. BOLD ATTITUDE.
 OPTIMUS SBR CHOICE TOOLS. PRECISION AIM. BOLD ATTITUDE. Optimizing Results with Business Intelligence Governance This paper investigates the importance of establishing a robust Business Intelligence (BI)
OPTIMUS SBR CHOICE TOOLS. PRECISION AIM. BOLD ATTITUDE. Optimizing Results with Business Intelligence Governance This paper investigates the importance of establishing a robust Business Intelligence (BI)
TMC Pooled Fund Study Federal Highway Administration
 Transportation Management Center Business Planning and Plans Handbook Developed for TMC Pooled Fund Study Federal Highway Administration By Booz Allen Hamilton Inc. and Kimley Horn and Associates, Inc.
Transportation Management Center Business Planning and Plans Handbook Developed for TMC Pooled Fund Study Federal Highway Administration By Booz Allen Hamilton Inc. and Kimley Horn and Associates, Inc.
Digital Customer Experience
 Digital Customer Experience Digital. Two steps ahead Digital. Two steps ahead Organizations are challenged to deliver a digital promise to their customers. The move to digital is led by customers who are
Digital Customer Experience Digital. Two steps ahead Digital. Two steps ahead Organizations are challenged to deliver a digital promise to their customers. The move to digital is led by customers who are
Process Methodology. Wegmans Deli Kiosk. for. Version 1.0. Prepared by DELI-cious Developers. Rochester Institute of Technology
 Process Methodology for Wegmans Deli Kiosk Version 1.0 Prepared by DELI-cious Developers Rochester Institute of Technology September 15, 2013 1 Table of Contents 1. Process... 3 1.1 Choice... 3 1.2 Description...
Process Methodology for Wegmans Deli Kiosk Version 1.0 Prepared by DELI-cious Developers Rochester Institute of Technology September 15, 2013 1 Table of Contents 1. Process... 3 1.1 Choice... 3 1.2 Description...
IT Governance Overview
 IT Governance Overview Contents Executive Summary... 3 What is IT Governance?... 4 Strategic Vision and IT Guiding Principles... 4 Campus-Wide IT Strategic Vision... 4 IT Guiding Principles... 4 The Scope
IT Governance Overview Contents Executive Summary... 3 What is IT Governance?... 4 Strategic Vision and IT Guiding Principles... 4 Campus-Wide IT Strategic Vision... 4 IT Guiding Principles... 4 The Scope
CENTRE FOR STRATEGIC CYBERSPACE + SECURITY SCIENCE LEADERSHIP. RESEARCH. DEFENCE.
 CSCSS CENTRE FOR STRATEGIC CYBERSPACE + SECURITY SCIENCE LEADERSHIP. RESEARCH. DEFENCE. CSCSS CENTRE FOR STRATEGIC CYBERSPACE + SECURITY SCIENCE The early 21st century has been defined by the Internet,
CSCSS CENTRE FOR STRATEGIC CYBERSPACE + SECURITY SCIENCE LEADERSHIP. RESEARCH. DEFENCE. CSCSS CENTRE FOR STRATEGIC CYBERSPACE + SECURITY SCIENCE The early 21st century has been defined by the Internet,
16094/14 MM/mj 1 DG E - 1C
 Council of the European Union Brussels, 26 November 2014 (OR. en) 16094/14 OUTCOME OF PROCEEDINGS From: On: 25 November 2014 To: CULT 134 AUDIO 69 MI 945 RELEX 980 STATIS 128 Education, Youth, Culture
Council of the European Union Brussels, 26 November 2014 (OR. en) 16094/14 OUTCOME OF PROCEEDINGS From: On: 25 November 2014 To: CULT 134 AUDIO 69 MI 945 RELEX 980 STATIS 128 Education, Youth, Culture
Executive Order 13636: The Healthcare Sector and the Cybersecurity Framework. September 23, 2014
 Executive Order 13636: The Healthcare Sector and the Cybersecurity Framework September 23, 2014 Executive Order: Improving Critical Infrastructure Cybersecurity It is the policy of the United States to
Executive Order 13636: The Healthcare Sector and the Cybersecurity Framework September 23, 2014 Executive Order: Improving Critical Infrastructure Cybersecurity It is the policy of the United States to
For more information about this proposal, contact: [David Greenbaum, Director IST Data Services, 2195 Hearst Avenue #250B, 510-642-7429]
![For more information about this proposal, contact: [David Greenbaum, Director IST Data Services, 2195 Hearst Avenue #250B, 510-642-7429] For more information about this proposal, contact: [David Greenbaum, Director IST Data Services, 2195 Hearst Avenue #250B, 510-642-7429]](/thumbs/27/10742258.jpg) FY 07-08 IT Budget Proposal Chief Information Officer: Data Management Governance ABBA Category One: Institutional Effectiveness ABBA Category Two: Information Technology For more information about this
FY 07-08 IT Budget Proposal Chief Information Officer: Data Management Governance ABBA Category One: Institutional Effectiveness ABBA Category Two: Information Technology For more information about this
HR Function Optimization
 HR Function Optimization People & Change Advisory Services kpmg.com/in Unlocking the value of human capital Human Resources function is now recognized as a strategic enabler, aimed at delivering sustainable
HR Function Optimization People & Change Advisory Services kpmg.com/in Unlocking the value of human capital Human Resources function is now recognized as a strategic enabler, aimed at delivering sustainable
University of Wisconsin Platteville IT Governance Model Final Report Executive Summary
 University of Wisconsin Platteville IT Governance Model Final Report Executive Summary February 2013 Project Objectives & Approach Objectives: Build on the efforts of the Technology Oversight Planning
University of Wisconsin Platteville IT Governance Model Final Report Executive Summary February 2013 Project Objectives & Approach Objectives: Build on the efforts of the Technology Oversight Planning
Re: Electronic Standards for Public Health Information Exchange
 NCVHS June 16, 2014 Honorable Sylvia Mathews Burwell Secretary, Department of Health and Human Services 200 Independence Avenue, S.W. Washington, D.C. 20201 Re: Electronic Standards for Public Health Information
NCVHS June 16, 2014 Honorable Sylvia Mathews Burwell Secretary, Department of Health and Human Services 200 Independence Avenue, S.W. Washington, D.C. 20201 Re: Electronic Standards for Public Health Information
Introduction to the Open Data Center Alliance SM
 Introduction to the Open Data Center Alliance SM Legal Notice This Open Data Center AllianceSM Usage: Security Monitoring is proprietary to the Open Data Center Alliance, Inc. NOTICE TO USERS WHO ARE NOT
Introduction to the Open Data Center Alliance SM Legal Notice This Open Data Center AllianceSM Usage: Security Monitoring is proprietary to the Open Data Center Alliance, Inc. NOTICE TO USERS WHO ARE NOT
The Role of ITIL in IT Governance
 The Role of ITIL in IT Governance Leveraging IT Governance around IT Service Management Presented By: Rick Leopoldi RL Information Consulting LLC Q2 2005 People Process Technology Why Focus on IT Governance
The Role of ITIL in IT Governance Leveraging IT Governance around IT Service Management Presented By: Rick Leopoldi RL Information Consulting LLC Q2 2005 People Process Technology Why Focus on IT Governance
ICANN Draft Five Year Strategic Plan (FY16 FY20)
 ICANN Draft Five Year Strategic Plan (FY16 FY20) For best results, download this document and view it outside of your browser with Adobe Reader version 9 or higher. Introduction The core value of ICANN
ICANN Draft Five Year Strategic Plan (FY16 FY20) For best results, download this document and view it outside of your browser with Adobe Reader version 9 or higher. Introduction The core value of ICANN
EMR ASM Alliance Executive Group: Terms of Reference
 EASTERN METROPOLITAN REGION ASM Alliance Executive Group TERMS OF REFERENCE The EMR ASM Alliance The EMR ASM Alliance has been created to support the implementation of the Active Service Model (ASM) across
EASTERN METROPOLITAN REGION ASM Alliance Executive Group TERMS OF REFERENCE The EMR ASM Alliance The EMR ASM Alliance has been created to support the implementation of the Active Service Model (ASM) across
Tech Launch Arizona. Start-up Guide For New Companies Licensing Technologies Invented at the University of Arizona
 Tech Launch Arizona Start-up Guide For New Companies Licensing Technologies Invented at the University of Arizona Contents The Idea-to-Impact Continuum... 1 The TLA Start-up Pathway... 3 1. Investigator:
Tech Launch Arizona Start-up Guide For New Companies Licensing Technologies Invented at the University of Arizona Contents The Idea-to-Impact Continuum... 1 The TLA Start-up Pathway... 3 1. Investigator:
Federal Reserve System Secure Payments Task Force
 2015 Federal Reserve System. Materials are not to be used without Federal Reserve consent. Federal Reserve System Secure Payments Task Force Teleconference June 4, 2015 Secure Payments Task Force Anti-Trust
2015 Federal Reserve System. Materials are not to be used without Federal Reserve consent. Federal Reserve System Secure Payments Task Force Teleconference June 4, 2015 Secure Payments Task Force Anti-Trust
Public Sector Interest Group (PSIG)
 BBRT Public Sector Interest Group (PSIG) What is the Beyond Budgeting idea? A set of performance management principles whose adoption leads to: More dynamic performance management processes that enable
BBRT Public Sector Interest Group (PSIG) What is the Beyond Budgeting idea? A set of performance management principles whose adoption leads to: More dynamic performance management processes that enable
