US A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2005/ A1 Liu (43) Pub. Date: Jan.
|
|
|
- Kristian Mason
- 8 years ago
- Views:
Transcription
1 US A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2005/ A1 Liu (43) Pub. Date: Jan. 20, 2005 (54) SPAM PROCESSING SYSTEM AND METHODS INCLUDING SHARED INFORMATION AMONG PLURAL SPAM FILTERS (76) Inventor: Gary G. Liu, Plano, TX (US) Correspondence Address: FISH & RICHARDSON RC DAIN RAUSCHER PLAZA MINNEAPOLIS, MN (US) (21) Appl. No.: 10/623,112 (22) Filed: Jul. 18, 2003 Publication Classi?cation (51) Int. Cl?..... G06F 15/16; H04L 9/32; H04L 9/00; G06F 12/14; G06F 11/30 (52) US. Cl /207; 709/204; 713/200 (57) ABSTRACT Methods and apparatus for?ltering spam. In one aspect, the method is for?ltering spam in a messaging system and includes con?rming that a message sender can receive, sharing information indicating that the message sender can receive among a plurality of spam?lters in the messaging system and using the information at a given one of the plurality of spam?lters to determine if a message should be allowed Without separately determining Whether the mes sage sender can receive. I Step 200: Receive an message I 19 Step 201:Check it Sender address format is correct. I Yes) Step 202: Create a Check Sender Request (401) to be sent to the Data Center (102). The Request includes Sender address and all recipients addresses. FStep 203: Sign and Encrypt Request using Crypto Engine (34). I Step 204: Send signed and encrypted Request to Data Center (102). l Step 205: Receive signed and encrypted Response from Data Center (1 02). I Step 208: --> Dispose the message. l Step 20B: Decrypt and verify Response using Crypto Engine (34). veri?ed), Step 212: Pass code required? Error Response eritications Fail Step 207: Check the Response (402) forthe Following cases: a) Sender is in the black list. b) Sender is in the white list. 0) Sender is in the unconfirmed list. In this case, the Case (0) Response will also contain the number (N) of Con?rmation s sent to the sender that has not been Answered and the time (T) the Data Center has been Step 210: Determine waiting for the answer. whether to deliver, dispose, or hold the Case (a) message based on N and Taccording to a policy. _ Step 211! HOld the 3"?! 23%;; message (store it in e We Temporary Message message' Storage (36)). contain the correct pass code 7
2 Patent Application Publication Jan. 20, 2005 Sheet 1 of 9 US 2005/ A1 i Data Center (102) Secure Environment Third Party Hosted _Complete i 5 White List (21) Black List (22) Unconfirmed sew Ema" s '"" " (106) i E Confirmation Records (20) wt (23) Other Services (12) Sender-Recipient Associations MQYFUaI List i 5 Database (24) Ed't'ng U' (25) SPAM Filter for Third Party 5 : Host Solution (103c) E 5 Check Sender Status Update Status Sender : ; Service (27) Service (28) Response SPAM Filter Logic (33) i 5... PTOCGSSOI' (29) Crypto Engine (34) i 5 List of SPAM Filter Public Keys (30) (Optional) 1: 5 - Operating CPU & Held Message Handler i ; Crypto Eng'ne (26) System (31) Memory (32) (35) 3 5 Temporary Message E : l Storage (36) E 5 Direct Access 5 Public Network (Internet) (101) Firewall (7) ISP or Mail Server (11) Firewall (7) PN SPAM Server Filter (103a) for Mail SPAM Client (103D) Filter rrir SPAM Filter Logic (33) SPAM Filter Logic (33) M a Server (9) Crypto Engine (34) Crypto Engine (34) Held Message Handler Held Message Handler (35) (35) Temporary Message Temporary Message Storage (36) Storage (36) Client (10) Mail Server (9) FIG. 1
3 Patent Application Publication Jan. 20, 2005 Sheet 2 of 9 US 2005/ A1 Step 200: Receive an message No 17 Step 201: Check if Sender address format is correct. Yes" Step 202: Create a Check Sender Request (401) to be sent to the Data Center (102). The Request includes Sender address and all recipients addresses. v Step 203: Sign and Encrypt Request using Crypto Engine (34). l Step 204: Send signed and encrypted Request to Data Center (102). Step 205: Receive signed and encrypted Response from Data Center (1 02). v Step 266: Decrypt and verify Response using Crypto Engine (34). l Error Response "verifications Fail erified Step 207: Check the Response (402) for the Following cases: a) Sender is in the black list. b) Sender is in the white list. c) Sender is in the unconfirmed list. In this case, the case (0) Response will also contain the number (N) of Confirmation s sent to the sender that has not been " Answered and the time (T) the Data Center has been Step 210: Determine waiting for the answer. whether to deliver, dispose, or hold the case (a) message based on N and T according st 212 P to a policy. ep : ass, 8 0 code required? v j v lap 81 Ste 211: Hold the > Drspose the Step 209: megsage (store it in message. Deliver the Temporary Message message' Storage (36)). Step 213: Does the message contain the correct pass code? FIG. 2
4 . - _ - Patent Application Publication Jan. 20, 2005 Sheet 3 of 9 US 2005/ A1 Step 300: Periodically starts (30 minutes, for example) Step 301: Compile a list of Senders tor the messages stored in the Temporary Message Storage (36) - Step 302: Create an Update Status Request (403) containing the list of Senders resulted from Step 301. Step 303: Sign and Encrypt Request using Crypto Engine (34). Step 304: Send signed and encrypted Request to Data Center (102). Step 305: Receive signed and encrypted Response from Data Center (1 02). ll Step 306: Decrypt and verify Response using Crypts Engine (34). erified F... I Error Response _ eritieatian Fail Repeated lor each Sande; Status listed in the Update Status Response (404) Step 307: For each sender in the Update Status Response (404) check whether: a) Sender is in the black list. b) Sender is in the white list. case (6) c) Sender is in the uncon?rmed list. In this case, the Response will also include the number (N) of Con?rmation s sent to the sender that has not been Answered and the time (T) the Data Center has been : I Waiting for the answer. " Case (a) ' "Case (b) Step 310: Determine 5 Step one: Dispose Step 309: Deliver tgfceg'gggue : 1 all the messages from that Sender. all messages from that Sender. to hold {he message based on N T according to a policy. Step 311: n Continue ' : holding the messages : i ' in Temporary Message E : Storage (36). :
5 Patent Application Publication Jan. 20, 2005 Sheet 4 of 9 US 2005/ A1 Spam Filter Sends: Data Center Returns: Check Sender Request (401) Sender Status Response (402) SPAM Filter Type Sender Address Subject Time Number of Recipients List of Recipients (Each item includes Recipient's address and recipient type, such as To, Cc, or Bcc.) Random Number Sender Address Sender Status (in white list, in black list, or in unconfirmed list) Number (N) of unanswered con?rmation.. s. (Present only when Sender is in the unconfirmed list) The maximum time (T) the data center has been waiting for the answer to the confirmation s. (Present only when Sender is in the unconfirmed list) Pass code (Present when pass code is required for the white list sender). Random Number Spam Filter Sends: Data Center Returns: Update Status Request (403) Update Status Response (404). SPAM Filter Type Number of Senders Number of Senders List of Sender Statuds. Each item - contains the same ata items in L'St of Senders Sender Status Response (402) Random Number except the Random Number. Random Number FIG. 4
6 Patent Application Publication Jan. 20, 2005 Sheet 5 of 9 US 2005/ A1 Step 500: Receive signed and encrypted Check Sender Request (401) Step 501: Decrypt and verify the Request using Crypto Engine (26) eriii?aii?n Fail Step 513: Return ' Error Response. Step 502: Check whether Sender Address is: a) In the white list (21), b) In the black list (22), c) In the uncon?rmed list (23),or it) Not in any of the lists. Cases (a), (b) n N m ( D 0: A O A O Step 505: - Check if confirmation forthe same message _ has been Sent No?g???gg'iosnend em" to Sender address. "'Yes Step 507: Update the Unconfirmed List (23). Step 508: Compose an appropriate Sender Status Response (402). Step 509: Sign and encrypt Sender Status Response (402) using Crypto Engine (26). Step 510: Send signed and encrypted Response to SPAM Filter Step 511: Update Sender - Recipient Associations Database (24) Step 512: Alert the Data Center Operator if certain predetermined SPAM signatures are detected in the Sender-Recipient Association Database. FIG. 5
7 r _ - _. _... _. _.... Patent Application Publication Jan. 20, 2005 Sheet 6 of 9 US 2005/ A1 Step 600: Receive signed and encrypted Update Status Request (403) l l! Step 601: Decrypt and verify the Request using Crypto Engine (26) eri?cation Fail Step 602: Create an Update Status Response Step 607: Return (404) with an empty List of Sender Status. Error Response Repeated for each Sender in the List of Update Status Request (403). i Step 603: Get Sender Status (whetherthe Sender is in the black list (22), in the white list (21), in the unconfirmed list (23), or not in any of the lists.) Step 604: Add the Sender Address and its Status to the List of Sender Status in the Update Status Response (404). l! Step 605: Sign and encrypt Update Status Response (404) using Crypto Engine (26) v Step 606: Send signed and encrypted Response to SPAM Filter FIG. 6
8 Patent Application Publication Jan. 20, 2005 Sheet 7 of 9 US 2005/ A1 From: antispamcenter@zixcorp.com Sent: Friday, April 25, :39 AM To: john@example.com Subject: Re: Conference call schedule Your message titled "Conference call schedule" sent at Friday, April 25, :25 AM has been held temporarily and will not be delivered to those recipients who use Zix SPAM filter. The reason is.because you are not currently in the trusted sender database. To be added to the database, click the following hyperlink and enter the authorization code below. Your original message will be delivered and you will be added to the trusted sender database. After that, you will not receive any more notices like this one and your future messages will be immediately delivered to all recipients. Authorization Code : FIG. 7
9 Patent Application Publication Jan. 20, 2005 Sheet 8 of 9 US 2005/ A1 Sender Response Processor Step 800: Receive HTTP Request resulted from Sender clicking the hyperlink in the confirmation . l Step 801: Return a web form asking the Sender to enter the Authorization Code. 1 Step 802: Receive Authorization Code entered by Senderl l 1 Step 803: Check if Authorization Code is correct. I lcorrect llncorrect 7' Step 804: Move Sender from Unconfirmed list (23) to White List (21). Step 806: Return a web page telling the Sender that the Authorization Code * is not correct and asking i Step 805: Return a web page indicating success. the Sender to try again. FIG. 8
10 Patent Application Publication Jan. 20, 2005 Sheet 9 of 9 US 2005/ A1 notice sent when the pass code requirement is turned on From: antispamcenter@zixcorp.com Sent: Friday, April 25, :39 AM To: john@example.com Subject: Pass code required According to user complaints and the data we collected, a large number of unsolicited messages appear to be sent from your address ohn@example.com. It is possible that a spammer is sending out spams preten ing to e rom your address. in orderto filter out spams while letting your messages to go through, you need to include the following pass code on the first line of every message you send out. The pass code will allow your messages to pass through the Zix SPAM filters while blocking spammer's messages pretending to be from you. Please note, a message sent without the correct pass code will be blocked by the Zix SPAM filters. 370urebn3s983sg From the following site, you may download plug-ins that will automatically insert the pass code into every message you send out. The plug-in will put the pass code in a header of the message, instead of on the first line, so that it will not be seen by the recipient. notice sent when the pass code requirement is turned off From: antispamcenter@zixcorp.com Sent: Friday, April 25, :39 All To: john@example_com Subject: Pass code not required any more We are pleased to inform you that the spammer who has been sending spams pretending to be from your s address has been tracked down and his lsp has terminated his account. He is not sending any more spams pretending to be from your address. As a result, we have turned off the pass code requirement on your address. You do not have to include the pass code in your messages any more. FIG. 9
11 US 2005/ A1 Jan. 20, 2005 SPAM PROCESSING SYSTEM AND METHODS INCLUDING SHARED INFORMATION AMONG PLURAL SPAM FILTERS TECHNICAL FIELD [0001] This invention relates to methods and apparatus for processing messages. BACKGROUND [0002] With the advent of modern computer technology, individuals increasingly use electronic means to transfer information from one location to another. For example, is a popular and ef?cient means for transferring information from one user to another. The popularity of messaging systems such as has risen dramatically among individuals, and a similar rise has occurred in the business use of messaging systems. Conventional point to point transfers from one computer to another represent the vast majority of these communications, however a myriad of handheld devices are now available that deliver messages to non-traditional computing platforms (pagers, PDA s, Black berry devices, Internet set top boxes and the like). [0003] Unfortunately the use of such messaging systems comes With measures of dif?culties. The messaging systems have become a equally convenient form of communication for marketers, promoters, advertisers and others Wishing to provide often unsolicited content (spam) to users of such messaging systems. Studies have suggested that spam accounts for nearly 1/3 of all the message traf?c coming into a corporate messaging system. Further, malicious use of spam can create system failures, such as seen When a denial of service attack is successful in overloading a target mes saging system. In addition to individual inconveniences, spam adds to network congestion (e.g., Internet congestion) by consuming large amounts of storage space and band Width. While the cost of sending out millions of spam s is very low (much cheaper than postal junk mail), the costs (direct and indirect) on the receive end is not insubstantial. [0004] Numerous conventional systems exist for identify ing and processing spam. Some conventional systems rely on identifying the source of the spam, e.g., the real address of the spam sender. HoWever, spammers (i.e., spam originators) often mask their identity or source of origin to avoid these type of detection systems. In one type of conventional system employed at an Internet Service Provider (ISP), the identi?cation of a source (i.e., real addresses of a spammer) Will cause the ISP to immediately terminate the spammer s account or limit their activity. [0005] Since most spammers do not identify themselves (e.g.; their real source addresses) this information can be used to?lter out a signi?cant amount of spam. For example, a conventional spam?lter can be used to send back a con?rmation to a source address of a suspect message to check if the sender can receive. If the con?rmation fails, this information can then be used to decide Whether a message should be treated as a spam. Such an idea has been used in several anti-spam systems, includ ing the systems and methods disclosed in US. Pat. Nos. 6,199,102 and 6,546,416, and the published patent applica tion [0006] In all these systems, a spam?lter installed either at an client or at a mail server is used to?lter out spam. When an message arrives at the spam?lter, the spam?lter Will temporarily hold the message and send a con?r mation to the original sender. The message held Will be delivered only after the original sender answers the con?rmation correctly. Optionally, the spam?lter keeps a list of con?rmed senders (a White list ). When a sender answers the con?rmation correctly, he Will be put into the White list so that the next time When a message from the same sender arrives, the message Will be delivered Without delay and Without sending another con?rmation . [0007] One problem of these prior art systems, however, is that they generally require a conventional sender (i.e., non spammer) to answer many con?rmation s, causing quite an inconvenience to the sender. For a system that does not use a White list, a conventional sender generally needs to answer as many con?rmation s as the number of spam?lters installed among the recipients for each message the sender sends out. For example, if one sends an to three recipients (john@example.com, gary@anotherexample.com, and cc s dave@thirdexample.com), the sender Would be required to answer three con?rmation s, if all the recipients have an anti-spam?lter installed. In addition, the conventional sender Would have to answer three con?rmation s each time a message is sent to the three recipients. [0008] For a system that uses a White list, a conventional sender generally needs to answer as many con?rma tion s as the number of spam?lters installed among the recipients for at least a?rst message sent. Because each spam?lter keeps a separate White list, a conventional sender still needs to answer one con?rmation for each spam?lter installed among the recipients he sends s to. In the above example, the conventional sender still has to answer three con?rmation s When he sends out a?rst message, although he/she Will not receive any con?rmation s When he sends additional messages to the same three recipients. [0009] One shortcoming of these prior art systems is that each conventional spam?lter Works in isolation and does not share information With other spam?lters. More speci? cally, conventional spam?lters do not share a White list of veri?ed sender addresses. For this reason, a conventional spam?lter always has to send a con?rmation to each sender to verify his address, even though other spam?lters Within a given network may have already veri?ed his address. In addition, conventional spam?lters do not share other information that could be useful in detecting spammers, such as information to detect a spammer s sig nature. For example, because a spammer sends to a large number of unrelated addresses, events detected by a plurality of spam?lters could be correlated and trends developed to detect a signature of a spammer (e.g., this address, though valid, sends too many messages to unrelated addresses), even if that spammer is using his/her real address. Conventional spam?lters in these prior art systems Work in isolation, and do not share information that could be correlated to detect the signature of spammers. SUMMARY [0010] In one implementation, the invention provides a data center to send out con?rmation messages (e.g.,
12 US 2005/ A1 Jan. 20, s), to process sender s responses, and to keep a White list of con?rmed senders, a black list of known spam mers, and an uncon?rmed list of the senders Who have not answered a con?rmation yet. In this implementation, the spam?lters, on the other hand, do not handle con?rmation messages or keep any of the lists. A spam?lter queries the data center to obtain the status of a sender in order to determine Whether a received message from that sender should be delivered, disposed (e.g. deleted, sent to a junk mail boxes, etc.), or temporarily held While the data center is Waiting for the answer to the con?rmation message. [0011] In another implementation, the invention provides a method for detecting spam in a messaging system and includes generating a White list of con?rmed message send ers, each of said con?rmed message senders having been con?rmed as being able to receive messages. The method includes sharing the White list among a plurality of spam?lters in the messaging system and using the White list at a given one of the plurality of spam?lters to determine if a sender of a received message has been previously con?rmed. If the sender has been con?rmed, the method includes forwarding the received message to a recipient Without separately con?rming the sender. [0012] Aspects of the invention can include one or more of the following features. The messaging system can be an system. The White list can be shared With at least two spam?lters. If the sender has not been previously con?rmed, the method can include sending a con?rmation to the sender and verifying a response from the sender. If the response is veri?ed, the sender can be added to the White list at the given spam?lter and the information can be shared With other spam?lters in the messaging system. Sharing can include publishing the White list at a central location. Using the White list can include checking the White list maintained at a central location. If the sender has not been previously con?rmed, the method further includes sending a con?rma tion to the sender and verifying a response from the sender. If the response is veri?ed, the method can include adding the sender to the White list at a central location that is shared among the plurality of spam?lters. [0013] In another aspect, the invention provides a method for identifying a spam message and includes receiving a message at a spam?lter in a network that includes a plurality of spam?lters, identifying the sender of the message and determining if the sender has been previously con?rmed as a valid sender including determining if the sender is included in a list of con?rmed senders for any spam?lter in the network. If the sender has been con?rmed, then the method can include forwarding the received message to a recipient Without separately con?rming the sender. [0014] Aspects of the invention can include one or more of the following features. The method can include determining if the sender has not been previously con?rmed and if not con?rmed, sending a con?rmation to the sender and verify ing a response from the sender. If the response is acceptable, the sender can be added to the White list at the given spam?lter and the information can be shared With other spam?lters in network. Sharing can include publishing the White list at a central location. [0015] In another aspect, the invention can provide a method for detecting a spammer in a network that includes a plurality of spam?lters and includes collecting informa tion relating to a sender from a plurality of the spam?lters, determining a trend in the collected information and identify a spammer based on the trend. [0016] Aspects of the invention can include one or more of the following features. Collecting information can include collecting information relating to a number of messages sent by a sender to unrelated addresses. Determining trends can include correlating the messages received by an indi vidual spam?lter relating to a same sender. Identifying can include determining that a sender is a spammer if a number of messages sent to unrelated addresses in the corre lated data exceeds a predetermined threshold. The threshold can be time dependent. [0017] In another aspect the invention provides a method for detecting spam in a messaging system and includes generating a White list of con?rmed message senders and maintaining the White list at a data center, receiving a message at a spam?lter in a network that includes a plurality of spam?lters, verifying With the data center that the sender of the message is a con?rmed message sender, add if so, forwarding the received message to a recipient Without separately con?rming the sender. [0018] In another aspect the invention provides a method for identifying a spam message and includes receiving a message at a spam?lter in a network that includes a plurality of spam?lters, identifying the sender of the message and verifying With a data center coupled to a plurality of the spam?lters if the sender has been previously con?rmed as a valid sender including determining if the sender is included in a list of con?rmed senders for any spam?lter in the network, the list being maintained at the data center. If the sender has been previously con?rmed, the received message is forwarded to a recipient Without separately con?rming the sender. [0019] In another aspect, the invention provides a method for detecting a spammer in a network that includes a plurality of spam?lters and includes collecting, using a data center, information relating to a sender from a plurality of the spam?lters, determining a trend in the collected infor mation; and identifying a spammer based on the trend, including adding the sender to a list of con?rmed spammers maintained by the data center. [0020] Aspects of the invention may include one or more of the following features. Collecting information can include collecting information relating to a number of messages sent by a sender to unrelated addresses. Determining trends can include correlating messages received by an individual spam?lter relating to a same sender. Identifying can include determining that a sender is a spammer if a number of messages sent to unrelated addresses in the correlated data exceeds a predetermined threshold. [0021] In another aspect, the invention provides a method for?ltering spam in a messaging system and includes con?rming that a message sender can receive, sharing infor mation indicating that the message sender can receive among a plurality of spam?lters in the messaging system and using said information at a given one of the plurality of spam?lters to determine if a message should be allowed Without separately determining Whether the message sender can receive. [0022] Aspects of the invention can include one or more of the following features. A passcode can be associated With
13 US 2005/ A1 Jan. 20, 2005 one or more of the con?rmed senders in the list, and the method can include verifying a message received from a sender in the list includes the passcode if speci?ed. The method can include triggering an addition of a passcode for a sender in the list upon an occurrence of an prede?ned event. The event can include detection that an address associated With the sender has been compromised. A pass code can be included in the list for one or more con?rmed senders. The passcode can be automatically added at a time for transmission of a message from the sender in the messaging system. A plug in module can be provided for automatically adding the passcode. The plug in module can be adapted to add the passcode prior to transmission to the messaging system. The method can include correlating sender-recipient data at a spam?lter in the messaging system, determining data related to how fast a list of recipients grows for a given sender; determining a list of unacceptable senders using the sender-recipient data and the determined data and sharing the list of unacceptable senders With other spam?lters in the messaging system. The method can maintain a list of recipients for each sender of messages processed by a given spam?lter. The list can be maintained at a data center. [0023] In one aspect, the invention provides a method for processing messages at a spam?lter in a messaging system Where the messaging system includes a plurality of spam?lters. The method includes receiving a message for pro cessing, the message from an sender for delivery to an intended recipient, and determining if the sender is a con?rmed sender including querying a data center to determine if the sender is included in a list of con?rmed senders based on information received from any of the plurality of spam?lters in the messaging system. Con?rmed senders are senders having a veri?ed capability to receive messages. If the sender is a con?rmed sender, the method can enable transmission of the message to the intended recipient. [0024] In another aspect, the invention provides a method for processing messages at a spam?lter in a messaging system, the messaging system including a plurality of spam?lters. The method includes receiving a message for pro cessing, the message from a sender for delivery to an intended recipient, determining if the sender is a con?rmed sender, including querying a data center to determine if the sender is included in a list of con?rmed senders based on information received from any of the plurality of spam?lters in the messaging system. Con?rmed senders are senders having a veri?ed capability to receive messages. If the sender is a not a con?rmed sender, the sender is con?rmed including sending the sender a noti?cation. Upon receipt of a con?rmation from the sender, the sender s con?rmed status can be shared With the plurality of spam?lters in the messaging system including publishing the sender s status to the data center. [0025] In another aspect, the invention provides a method for minimizing spam in a messaging system, the messaging system including a plurality of spam?lters. The method includes receiving a request from one of the spam?lters in the messaging system to verify if a sender of a message is a con?rmed sender. A con?rmed sender is a sender having a veri?ed capability to receive messages. The method includes evaluating a list of con?rmed senders and providing a noti?cation to the one spam?lter indicating Whether the sender s status is con?rmed. [0026] In another aspect, the invention provides a method for minimizing span in a messaging system and includes receiving a request from one of the spam?lters in the messaging system to verify if a sender of a message is a con?rmed sender, a con?rmed sender being a sender having a veri?ed capability to receive messages and evaluating a list of con?rmed senders. If the sender is not included in the list of con?rmed senders, the method includes con?rming the sender including providing a noti?cation to the sender and upon receipt of a con?rmation of from the sender, sharing the sender s status With the other spam?lters in the mes saging system including adding the sender to the list and providing a noti?cation to the one spam?lter indicating Whether the sender s status is con?rmed. [0027] The invention can be implemented to realize one or more of the following advantages. A system is provide that eliminates the inconvenience of having to answer many con?rmation s, and allows for information to be col lected and shared by all the spam?lters in a given network. A system and method are provided for sharing White lists among spam?lters in a given network. In addition, a system and method is provided for collecting information from among plural span?lters and correlating information to detect the signature of a spammer, even if the spammer may be using his/her real address. Using the proposed system, a conventional sender only needs to answer one con?rmation , regardless of the number of spam?lters that are installed by the intended recipients of his messages. Using the proposed system, information can be collected by the data center from the spam?lters and analyzed to detect spammers, even if these spammers use their real address and are able to answer con?rmation s. In the proposed system, the spam?lters are much simpli?ed because they do not have to handle con?rmation s and manage the lists (White list, the black list, and the uncon?rmed list) [0028] The details of one or more embodiments of the invention are set forth in the accompanying drawings and the description below. Other features, objects, and advan tages of the invention Will be apparent from the description and drawings, and from the claims. DESCRIPTION OF DRAWINGS [0029] FIG. 1 is a simpli?ed block diagram of an anti SPAM system including a Data Center and three different SPAM Filter con?gurations. [0030] FIG. 2 is the logical How of SPAM Filter Logic. [0031] FIG. 3 is the logical How of the Held Message Handler FIG. 4 is the data format of the requests sent from the SPAM?lter and the responses from the Data Center. [0032] FIG. 5 is the logical How of Check Sender Status Service for the Data Center. [0033] FIG. 6 is the logical How of Update Status Service for the Data Center FIG. 7 is an example of con?rmation sent to the Sender. [0034] FIG. 8 is the logical How of Sender Response Processor for the Data Center. [0035] FIG. 9 contains examples of notices sent to a Sender When the pass code requirement is turned on or off.
14 US 2005/ A1 Jan. 20, 2005 [0036] Like reference symbols in the various drawings indicate like elements. DETAILED DESCRIPTION [0037] The present invention provides a unique method for identifying and processing unwanted message content in a messaging system. It is understood that the following disclosure provides many different implementations, or examples, for implementing different features. Techniques and requirements that are only speci?c to certain implemen tations should not be imported into other implementations. Also, speci?c examples of networks, components, and for mats are described below to simplify the present disclosure. These are, of course, merely examples and are not intended to limit the invention from that described in the claims. While an messaging system Will be described, the teachings of the present invention may have applicability to other messaging systems. [0038] In the implementation described below, a Data Center is used to send out con?rmation s to senders to con?rm that they can receive. Normal senders have no problem receiving the con?rmation and responding to it. Spammers, however, afraid of being tracked down quickly, rarely use real addresses When sending out spam, and therefore cannot receive the con?r mation and respond to it. Once a sender has success fully responded to the con?rmation , the sender Will be put into a list of con?rmed senders (a White list ) main tained in the Data Center. In one implementation, a black list of known spammers can also be kept by the Data Center. Aplurality of SPAM Filters can be installed either at mail servers or at clients throughout a given network. The SPAM Filters can query the Data Center to obtain the sender s status information to decide Whether an message from that sender should be delivered, disposed, or temporarily held. In one implementation, if the sender is in the black list, the message Will be disposed; and if the sender is in the White list, the message Will be delivered (With exceptions Which Will be discussed below). If the sender is neither in the White list nor in the black list, the Data Center Will send a con?rmation to the sender, and then return certain information such as how many con?r mation s have been sent to that sender and how long the Data Center has been Waiting for the answer. Such information can then be used by the SPAM Filter to decide Whether to deliver the message, dispose the message, or temporarily hold the message according to a local policy that is speci?c to the individual SPAM Filter. For the messages temporarily held, the SPAM Filter can check With the Data Center periodically to see if the sender s status has changed and then decide Whether the message should be delivered, disposed, or continue to be held according to the local policy. [0039] It is possible that a spammer may send out spams pretending to be from a legitimate user already in the White list. In order to block spammer s messages While allowing the legitimate user s messages to go through, a pass code may be required for certain addresses in the White list. The pass code can be maintained in the Data Center. If the pass code requirement is turned on for an address in the White list, the returned sender status from the Data Center Will indicate that the sender is in the White list, but a speci?c pass code is required. The SPAM?lter can be con?gured to block the message unless it contains the correct pass code (on the?rst line or in the header, for example). The pass code can be sent by the Data Center to the address owner in an . The spammer that does not actually own that address Will not be able to receive/know the pass code. The burden for the legitimate user to add the pass code to every message can be eliminated by an client plug-in that automatically inserts the pass code into sent messages. The pass code requirement can be enabled or disabled as required if the system of the user determines that spam is being sent from a given users account. [0040] When a large number of SPAM Filters are installed at many sites over the Internet, the Data Center Will be able to collect rich information from the queries sent by the SPAM Filters. Such information can be used to distinguish spammers from certain legitimate bulk senders, such as a subscription-based mailing list. One such example of information collected is sender-recipient correlation data. By keeping a list of recipients that a sender has ever sent a message to, the Data Center can detect spam events by Watching how fast the recipient list grows. For a spammer, the list of recipients Will grow very fast While each batch of spams is usually sent to a different set of recipients. For a mailing list sender, the list of recipients Will grow slowly and different messages Will be sent to roughly the same set of recipients periodically. These different signatures can be used to distinguish spammers from mailing lists. [0041] As shown in FIG. 1, a Data Center (102) is connected to the Internet (101). Also connected to the Internet (101) are a plurality of SPAM?lters in various con?gurations (103). SPAM Filters and their con?gurations 103 are discussed in greater detail below. [0042] The Data Center (102) is one or more generalized or specialized computers that includes CPU and Memory (32) and operating system (31). In addition, the Data Center (102) includes the following components: a White List (21), Black List (22), Uncon?rmed List (23), Con?rmation Mes sage Records (20), Sender Recipient Associations Data base (24), Manual List Editing UI (25), Check Sender Status Service (27), Update Status Service (28), Sender Response Process (29), Crypto Engine (26) and List of SPAM Filter Public Keys (30) White List (21) is a list of con?rmed message (e.g., ) senders, those Who have successfully responded to a con?rmation message (e.g., ) sent by the Data Center (102) or are otherwise con?rmed (e.g., con?rmed by other Data Centers or Spam Filters). By Way of example, the Data Center Will be described in terms of an system. Those of ordinary skill in the art Will recog nize that the principles disclosed have applicability to other systems (non- ), including hybrid systems that only use to receive or otherwise communicate With a sender or recipient but not both. [0043] White list (21) can include individual addresses as Well as domain names to indicate that all addresses in a given domain have been con?rmed. Indi vidual addresses can be entered automatically When the sender successfully responds to the con?rmation or manually by the Data Center Operator using the Manual List Editing UI (25). Domain names can be entered into the White list manually. Thereafter, s from con?rmed send ers identi?ed in the White list (21) Will generally be accepted
15 US 2005/ A1 Jan. 20, 2005 by any one of the plurality of SPAM?lters in the network and delivered to the recipients. One exception is When an address in the White list is marked as pass code required. In this case, a message Will be blocked unless it contains the correct pass code. When an address is marked as pass code required, the associated pass code can also be stored along With the address in White list (21). The Data Center Operator can enable or disable the pass code requirement manually using the Manual List Editing UI (25). The pass code requirement is enabled When the Data Center Operator discovers that a spammer is sending spams pretending to be a legitimate user in White list (21). The pass code can be disabled When the spammer has been tracked down and terminated. In one implementa tion, When the pass code requirement is enabled or disabled, an appropriate notice (e. g., ) Will be sent to the affected sender (e.g., the address that has been compromised). Thereafter, the sender can include the pass code in each transmission as appropriate. Examples of such notices are shown in FIG. 9. Descriptions of pass codes and methods for verifying pass codes using the Data Center (102) and Spam Filters are discussed in greater detail below. [0044] Black List (22) is a list of known Spammers or other type of malicious senders (e.g., senders). Mes sages (e.g., s) from these senders Will generally be disposed by a receiving SPAM?lter and Will not be deliv ered to the recipients. Black list (22) can also include domain names to indicate that all addresses in a given domain are in the Black list (22). Domain names and individual addresses can be entered by the Data Center Operator using the Manual List Editing UI (25). [0045] Uncon?rmed List (23) contains the senders Who have not responded to the con?rmation messages (e.g., s) yet. For each of the uncon?rmed senders, additional data can be kept, including the time the?rst con?rmation message (e.g., ) Was sent (Which can be used to calculate the maximum time the Data Center (102) has been Waiting for the response to the con?rmation message (time T)), and the number of con?rmation messages sent to that sender (number N). In one implementation, both the number N and time T Will be returned to a requesting SPAM Filter When the SPAM Filter queries the status of an uncon?rmed sender. [0046] Con?rmation Message Records (20) stores relevant information for the con?rmation messages (e.g., s) sent to the Sender. In one implementation, each record contains the Sender address, the Subject and Time of the original message (the original message from the Sender that caused the con?rmation to be sent), and the Authori Zation Code sent in the con?rmation . In one imple mentation, the record is identi?ed by a unique Con?rma tion ID, Which Will also be sent in the con?rmation . [0047] Sender Recipient Associations Database (24) is used to store information of sender-recipient correlations. In one implementation, Sender Recipient Associations Data base (24) keeps a list of recipients a sender has ever sent a message to, the time the recipient Was added to the list, and the number of repeated sends to a same recipient. From such information, the Data Center (102) can determine how many recipients a sender has been sending messages to, how fast his recipient list is growing, and Whether he is sending to the same set of recipients repeatedly or sending to a large number of recipients Without repeating. These characteris tics can be used to distinguish spammers from legitimate bulk mail senders such as mailing lists. For a conventional mailing list sender, the recipient list Will grow slowly While the number of repeated sends is relatively high. For a conventional spammer, the recipient list Will grow very fast and repeated sends seldom occur, or at least, not until the recipient list has become very large. [0048] Manual List Editing UI (25) is a program that has a user interface that allows a Data Center Operator to manually edit the White List (21), the Black List (22), the Uncon?rmed List (23), and the Sender Recipient Associa tion Database (24). [0049] Check Sender Status Service (27) is a server pro gram running on the Data Center (102) to process a Check Sender Request (401 in FIG. 4) from the SPAM Filter and return a Sender Status Response (402 in FIG. 4). This Request/Response pair allows a given SPAM Filter to retrieve the sender s status from the Data Center (102) (Whether the sender is in White List (21), Black List (22), or Uncon?rmed List (23)). In one implementation, the Check Sender Request contains both the sender s address and associated recipients addresses, and therefore, can also be used to update the Sender Recipient Association Database (24). FIG. 5 describes the logical How of the Check Sender Status Service (27) in greater detail. [0050] Update Status Service (28) is a server program running on the Data Center (102) to process an Update Status Request (403 in FIG. 4) from a given SPAM Filter and return an Update Status Response (404 in FIG. 4). This Request/Response pair allows the SPAM Filter to periodi cally check if the sender s status has changed in the Data Center (102) in order to decide Whether a message held in temporary storage (e.g., Temporary Storage (36)) should be delivered, disposed, or continued to be held. FIG. 6 describes the logical How of the Update Status Service (28) in greater detail. [0051] Sender Response Process (29) is a server program running on the Data Center to process the sender s response to the con?rmation message (e.g., ). If the sender has responded to the con?rmation message (e.g., ) cor rectly, his/her identifying information (e.g., address) Will be added to White List (21). FIG. 8 describes the logical How of Sender Response Process (29) in greater detail. [0052] Crypto Engine (26) is a set of cryptographic rou tines and related public/private keys To add to the security of the system, Crypto Engine (26) can be used to secure the communication between the Data Center (102) and the SPAM Filters In one implementation, the Check Sender Request (401 in FIG. 4), the Sender Status Response (402 in FIG. 4), the Update Status Request (403 in FIG. 4), and the Update Status Response (404 in FIG. 4) are all signed and encrypted messages. Crypto Engine (26) can be used by the Data Center (102) to decrypt a request from the SPAM Filter, verify the SPAM Filter s digital signature on the request, digitally sign the response, and encrypt the response. As Would be apparent to one of ordinary skill in the art, encryption and digital signature are not absolutely necessary for the proposed spam system to Work. HoWever, they can be used for the following reasons. First, spammers like to sniff on the Internet to discover addresses. A
16 US 2005/ A1 Jan. 20, 2005 Well-designed anti-spam system should not give spammers an advantage by sending addresses over the Internet in the clear. For this reason, the communications between the SPAM Filter and the Data Center (102) can be encrypted. Second, the Data Center contains rich information about a large number of addresses. Ideally not just anyone (i.e., a spammer) can send a request to the Data Center (102) to obtain such information (e.g., to harvest good addresses). For this reason, the request sent to the Data Center (102) can be signed and only the digital signatures of legitimate SPAM Filters are honored by the Data Center (102). [0053] List of SPAM Filter Public Keys (30) keeps a list of public keys of authorized SPAM Filters. As described above, only digital signatures that can be veri?ed by a public key in the list are considered legitimate in one implemen tation. [0054] FIG. 1 also shows three different con?gurations 103 in Which the SPAM Filter is used. A SPAM Filter for Mail Server con?guration provides a SPAM Filter (103a) between the FireWall (7) and the Mail Server (9) of a typical corporate network. In such a con?guration, the SPAM?ltering is carried out before s reach the Mail Server (9). In this con?guration, the SPAM Filter (103a) can be a software layer running on the same computer of the Mail Server (9), or on a dedicated computer between the FireWall (7) and the Mail Server [0055] A SPAM Filter for Client con?guration provides a SPAM?lter (103b) that is typically a software layer running on the same computer of the Client (10), for example, a plug-in of the Microsoft Outlook. In such a con?guration, SPAM?ltering is carried out before the message is put into the InboX of the client. Such a client-based con?guration can be used by individual users connected to the Internet through an ISP or by users of a corporation that Would rather conduct SPAM?ltering at the client level, instead of at the gateway. In such a system, the SPAM Filtering is conducted When the messages are retrieved from the ISP or Mail Server (11). [0056] In a third con?guration, a SPAM Filter (103c) is used as one of the services in a third party hosted secure solution (106). Third party hosted secure solu tions redirect all messages of a corporation to a third party system via a irtual Private NetWork (PN) or other type of secure connection, Where the messages can be virus scanned, SPAM-?ltered, encrypted, decrypted, digi tally signed, and veri?ed, according to con?gurable policies. As shown in FIG. 1, an Message Redirector (8), sitting between the FireWall (7) and the Mail Server (9), redirects all incoming and outgoing messages to the third party system (106) via a PN. The third party system can provide all the services to secure the messages, including the service provided by SPAM Filter (103c) and other services (12). If the third party system (106) is located in the same secure environment of the Data Center (102) (Operated by the same entity), SPAM Filter (103c) can directly access the Data Center (102) Without using the Internet (101), as shown in FIG. 1. In such a case, encryp tion and digital signature for the communication between the SPAM Filter and the Data Center Will be optional. [0057] SPAM Filters (103a-c) can be identically con?g ured and include the following components: SPAM Filter Logic (33), Temporary Message Storage (36), Held Message Handler (35) and Crypto Engine (34) [0058] SPAM Filter Logic (33) is a process that conducts SPAM?ltering. When a message (e.g., message) is received at the SPAM Filter, the SPAM Filter Logic (33) Will query the Data Center (102) for the status of the sender, and then decide Whether the message should be delivered, dis posed, or temporarily held in the Temporary Message Stor age (36). The logical?ow of the process is described in more detail in FIG. 2. [0059] Temporary Message Storage (36) is used to tem porarily hold the messages from the senders in the Uncon?rmed List (23) those senders that the Data Center (102) is still Waiting for their responses to the con?rmation mes sages (e.g., con?rmation messages). [0060] Held Message Handler (35) is a process for han dling the messages temporarily held in the Temporary Mes sage Storage (36). In one implementation, Held Message Handler (35) process Will automatically start at?xed inter vals, check the sender status at the Data Center (102), and then decide Whether the messages held in the Temporary Message Storage (36) should be delivered, disposed, or continue to be held. The logical How of the Held Message Handler (35) process is described in more detail in FIG. 3. [0061] Crypto Engine (34) is a set of cryptographic rou tines and related public/private keys that can be used to secure the communications between the Data Center (102) and the SPAM Filters. Crypto Engine (34) can be used by the SPAM Filter to sign and encrypt the requests sent to the Data Center (102) and decrypt and verify the responses from the Data Center (102). In one implementation Where the SPAM Filter (103c) for third party hosted solution is located in the same secure environment of the Data Center (102), the SPAM Filer (103c) can directly access the Data Center (102) and the Crypto Engine (34) is not necessary. [0062] Referring now to FIG. 2, the detailed logical How of SPAM Filter Logic (33) is shown. The process starts at Step (200) When a message (e.g., message) is received. By Way of example, the process Will be described in terms of an system. [0063] At Step (201), SPAM Filter Logic (33) checks if the message contains properly formatted information. For example, the SPAM Filter Logic (33) can at this step check the sender address in the From:?eld. In one implementation, if the message contains a Reply-toz?eld, the format of the Reply-toz address Will also be checked. The general format of all Internet headers and the consis tency between them can also be checked. A domain name lookup can be conducted at this step to check if the domain of sender s address actually exists and the IP address is consistent With the IP address making the SMTP connec tion, if such information is available. If any of the proscribed checks fails, the process Will jump to Step (208) to dispose the message and the process ends. If all the checks succeed, the process continues to Step (202). [0064] At Step (202), SPAM Filter Logic (33) creates a Check Sender Request to be sent to the Data Center (102). In one implementation, the data items included in the Check Sender Request is shown in FIG. 4 as item (401). Check Sender Request (401) can include a SPAM Filter Type (Which indicates Whether the SPAM Filter is mail server
17 US 2005/ A1 Jan. 20, 2005 based (103a), client based (103b), or third party hosted (103c)), Sender Address, Subject, Time, a list of Recipients, and a Random Number. The Sender Address can be either the Reply-toz address, if the mes sage has one, or the From: address, if the message does not have a Reply-toz header. The subject can be the subject of the message. The Time can be the time of the message converted to a universal time that does not depend on time Zone. The list of Recipients can include the number of recipients, and then for each recipient, the recipient s address and the recipient type (such as To, Cc, or Bcc). Subject and Time can be used in the con?rmation to give the sender a reference to the original message. Subject and Time can also be used to uniquely identify the message, so that the Data Center (102) Will not send out duplicated con?rmation messages (e. g., s) When a message sent to multiple recipients reaches different SPAM Filters. The Recipient list is used to send the Sender Recipient corre lation information to the Data Center (102). Sender Re cipient Correlation information can be used to distinguish spammers from other legitimate bulk mailers, such as a subscription-based mailing list. The Random Number in the Request can be returned in the Response from the Data Center (102). The Random Number can be used to ensure that the Response received from the Data Center (102) is truly generated by the Data Center in real time, not a playback event. [0065] At Step (203), SPAM Filter Logic (33) signs and encrypts the Check Sender Request (401) using the Crypto Engine (34). As Was described above, this step is optional. In one implementation, a 1024-bit RSA algorithm is used for both the public key encryption and digital signature, a 160-bit SHA1 is used for the secure hash, and a 128-bit AES algorithm is used for symmetric key encryption. More speci?cally, the SPAM Filter uses its 1024-bit RSA private key to sign the SHA1 hash computed from the Check Sender Request (401) to create the signature. The signature is then attached to the Request to create the signed Request. Finally, the signed Request is encrypted by a randomly generated 128b-bit AES symmetric key, Which in turn, is encrypted by the 1024-bit RSA public key of the Data Center (102). [0066] At Step (204), SPAM Filter Logic (33) sends the (optionally signed and encrypted) Check Sender Request (401) to the Data Center (102). In one implementation, an HTTP POST is used to send the signed and encrypted Request to the Data Center (102). The HTTP protocol typically has little or no problems penetrating conventional corporate?rewalls. For a third party hosted SPAM Filter (103c) that accesses the Data Center (102) directly, Step (204) may send a plaintext Check Sender Request (401) Without digital signature and encryption. [0067] At Step (205), SPAM Filter Logic (33) receives the (optionally signed and encrypted) Response from the Data Center (102). If an error response is received from the Data Center (as a result of a communication error) or the Request is otherwise corrupted or tampered With (e.g., the signature can not be veri?ed), the process may continue at Step (202) to try again. [0068] At Step (206), SPAM Filter Logic (33) (decrypts as necessary and) veri?es the Response received from the Data Center (102) (again, using the Crypto Engine (34) as required). In one implementation, a 1024-bit RSA algorithm is used for both the public key encryption and digital signature, a 160-bit SHA1 is used for the secure hash, and a 128-bit AES algorithm is used for symmetric key encryp tion. More speci?cally, the SPAM Filter uses its 1024-bit RSA private key to recover a 128-bit AES key encrypted by the SPAM Filter s public key. Then, the AES key is used to decrypt the Response. The SPAM Filter then veri?es the digital signature on decrypted Response. Speci?cally, the signature is veri?ed using the public key of the Data Center (102) to recover a SHA1 hash. Then, the recovered hash is compared With the hash computed from the Response to see if they are equal. In addition, the process also compares the Sender Address and the Random Number in the Response to see if they are the same as those sent in the request (this ensures that the Response is truly generated by the Data Center in response to the Request, and is not a playback event). If any of the decryption and signature veri?cation steps fails, indicating that the Response may be corrupted or tampered With, the process returns to Step (202) to try again. If all the decryption and veri?cation succeed, the process Will continue to Step (207). Again, Step (206) may not be necessary for a third party hosted SPAM Filter (105) situated in the same secure environment of the Data Center (102). [0069] At Step (207), SPAM Filter Logic (33) interprets the Response received from the Data Center (102). The Response can be of the form of a Sender Status Response shown as item (402) of FIG. 4. In the implementation shown, the Sender Status Response (402) contains Sender Address and Sender Status indicating Whether the Sender is in the White List (21), in the Black List (22), or in the Uncon?rmed List (23). If the Sender is in the Uncon?rmed List (23), two additional data items, the Number N and the Time T, can also included in the Sender Status Response (402). Number N refers to the number of unan swered con?rmation messages (e.g., s) that have been sent to that Sender. Time T, refers to the maximum time the Data Center (102) has been Waiting for the response to the con?rmation messages (e.g., s) from the Sender. APass Code may be included in the Sender Status Response (402) When the Sender is in the White list (21). The receipt of a Pass Code indicates that the SPAM Filter should block the message, unless it contains the correct Pass Code. If the Sender is in the Black List (22) (Case a), the process continues at Step (208). If the Sender is in the White List (21) (Case b), the process continues at Step (209). If the Sender is in the Uncon?rmed List (23) (Case c), the process continues at Step (210). [0070] At Step (212), SPAM Filter Logic (33) checks if a Pass Code is in the Sender Status Response (402). If so, it indicates that the correct Pass Code is required for the message to be delivered and the process continues at Step (213) to check the Pass Code in the message. OtherWise, the process continues at Step (209) to deliver the message. [0071] At Step (213), SPAM Filter Logic (33) checks if the message contains the correct Pass Code. If so, the process continues at Step (209) to deliver the message. OtherWise, the process continues at Step (208) to dispose the message. [0072] At Step (210), SPAM Filter Logic (33) uses the Number N and Time T to determine Whether to dispose the message, deliver the message, or hold the message in the Temporary Message Storage (36) according to a local policy.
18 US 2005/ Al Jan. 20, 2005 One example policy is: If N<3 and T<24 hours, deliver the message; if N>10 or T>120 hours, dispose the message; otherwise, hold the message in the Temporary Message Storage (36). This example policy Will allow 1 or 2 messages to go through immediately before an uncon?rmed Sender has a chance to respond to the con?rmation Within 24 hours. HoWever, if the Sender has not responded to more than 10 con?rmation s or has not responded to the?rst con?rmation Within 5 days, he Will be treated as a spammer and all future messages from this sender Will be disposed using a local policy allows each SPAM Filter to set an individual criterion for determining What should be treated as a SPAM and how tight the SPAM?ltering should be (Whether to allow a few messages to be delivered before the sender s address is con?rmed). If at Step (210), SPAM Filter Logic (33) determines that the message should be disposed, the process continues at Step (208). If at Step (210), SPAM Filter Logic (33) determines that the message should be delivered, the process continues at Step (209). If at Step (210), SPAM Filter Logic (33) determines that the message should be held in the Temporary Message Storage (36), the process continues at Step (211). [0073] At Step (208), SPAM Filter Logic (33) Will dispose the message, and after that, the process ends. The disposition of the message may include sending the message to a junk mail box, putting the message into a SPAM folder, Writing the message into a log?le, or simply deleting the message. The messages reaching Step (208) are regarded as SPAM messages and should ordinarily be deleted. Sending noti? cations to the sender, recipient, or administrator Will only amplify the SPAM problem. [0074] At Step (209), SPAM Filter Logic (33) Will deliver the message to the recipient(s), and thereafter, the process ends. [0075] At Step (211), SPAM Filter Logic (33) Will store the message in the Temporary Message Storage (36), and thereafter, the process ends. In one implementation, mes sages stored in the Temporary Message Storage (36) are indexed by the senders addresses so that a list of senders can be easily obtained and all messages from a particular sender can be easily manipulated. [0076] Messages held in the Temporary Message Storage (36) are processed by the Held Message Handler (35). In one implementation, Held Message Handler (35) automatically starts at a?xed interval (e. g., 30 minutes) to check With Data Center (102) to determine if the status of the senders of the messages held in the Temporary Message Storage (36) has been changed and then decide Whether a message should be delivered, continued to be held, or disposed. The logical How of the Held Message Handler (35) is shown in FIG. 3. [0077] The process of Held Message Handler (35) starts at Step (300) at?xed intervals, for example, 30 minutes. At Step (301) Held Message Handler (35)compiles a list of senders s addresses from the messages stored in the Temporary Message Storage (36). In one implementation Where the messages stored in the Temporary Message Stor age (36) are indexed by senders addresses as described in Step (211), the list of senders can be easily obtained. [0078] At Step (302), Held Message Handler (35) creates an Update Status Request. In one implementation, the data items included in the Update Status Request is as shown in FIG. 4 including item (403). Update Status Request (403) contains a SPAM Filter Type, a List of Sender Addresses, and a Random Number. The SPAM Filter Type indicates Whether the SPAM Filter is mail server based (103a), client based (103b), or third party hosted (103c). The List of Sender Addresses can include all senders Whose messages are held in the Temporary Message Storage (36). The Random Number in the Request Will be returned in the Response from the Data Center (102). The Random Number is used to ensure that the Response received from the Data Center is truly generated by the Data Center in real time, not a playback event. [0079] At Step (303), Held Message Handler (35) signs and encrypts the Update Status Request (403) using the Crypto Engine (34). In one implementation, 1024-bit RSA algorithm, 160-bit SHA1, and 128-bit AES are used to sign and encrypt the Update Status Request (403) in the same Way as described in Step (203). As described above, the signing and encryption of the Update Status request is optional. [0080] At Step (304), Held Message Handler (35) sends the (optionally signed and encrypted) Update Status Request (403) to the Data Center (102). For a third party hosted SPAM Filter (105) that accesses the Data Center (102) directly, Held Message Handler (35) may send the Update Status Request (403) Without digital signature and encryp tion. In response to the transmission, Held Message Handler (35) may receive an error response from the Data Center (102) if there is any communication error or the Request is corrupted or tampered With. In this case, the process Will continue at Step (302) to try again. [0081] At Step (305), Held Message Handler (35) receives the (optionally signed and encrypted) Response from the Data Center (102). For a third party hosted SPAM Filter (105) situated in the same secure environment of the Data Center (102), the Response received may not be signed and encrypted. [0082] At Step (306) Held Message Handler (35) decrypts and veri?es the Response received from the Data Center (102) using the Crypto Engine (34) as required. Similar to Step (206), the veri?cations can not only include verifying the digital signature on the Response, but also include verifying that the List of Senders and the Random Number in the Response are the same as those sent in the Request. This ensures that the Response is truly generated by the Data Center in response to the Request, not a playbac event. If any of the decryption and veri?cation steps fails, indicat ing that the Response may be corrupted or tampered With, the process continues at Step (302) to try again. If all the decryption and veri?cation checks succeed, the process Will continue to Step (307). [0083] In one implementation, the Response from the Data Center (102), after decryption and signature veri?cation, is an Update Status Response as is shown as item (404) in FIG. 4. The Update Status Response (404) contains a List of Sender Status and a Random Number. The Random Number is the same Random Number sent in the Request and has been used in Step (306) to thwart the playback attack. The List of Sender Status can be a list Where each item contains the same data items of a Sender Status Response (402) except the Random Number. In other Words, each item in the
19 US 2005/ A1 Jan. 20, 2005 List of Sender Status can contain the Sender Address and a Sender Status indicating Whether the Sender is in the White List (21), Black List (22), or Uncon?rmed List (23), and if the Sender is in the Uncon?rmed List (23), the number of unanswered con?rmation s (N) and the maximum time the Data Center (102) has been Waiting for the answer to con?rmation s Will also be included in the item. [0084] The remainder of the logical?ow starting from Step (307) Will be repeated for each Sender in the List of Sender Status in the Update Status Response (404). The processing for each Sender is very similar to the Steps (207)-(211) in FIG. 2. HoWever, after processing each item in the List of Sender Status, the process Will continue at Step (307) so as to process the next item in the List, until all the Senders in the List have been processed. [0085] At Step (307), Held Message Handler (35) decides What to do next according to the status of the Sender. If the Sender is in the Black List (22) (Case a), the process continues at Step (308). If the Sender is in the White List (21) (Case b), the process continues at Step (309). If the Sender is in the Uncon?rmed List (23) (Case c), the process continues at Step (310). [0086] Similar to Step (210) in FIG. 2, at Step (310) Held Message Handler (35) uses the Number N and Time T to determine Whether the Sender s messages held in the Tem porary Message Storage (36) should be delivered, continued to be held, or otherwise disposed according to a local policy. In one implementation, the same policy used in Step (210) of FIG. 2 is used in Step (310) for consistency. If at Step (310) Held Message Handler (35) determines that the mes sage should be otherwise disposed, the process continues at Step (308). If at Step (310) Held Message Handler (35) determines that the message should be delivered, the process continues at Step (309). If at Step (310) Held Message Handler (35) determines that the message should continued to be held in the Temporary Message Storage (36), the process continues at Step (311). [0087] At Step (308), Held Message Handler (35) Will dispose all messages in the Temporary Message Storage (36) that are from the particular Sender, and thereafter, the process continues at Step (307) again to process the next item in the List of Sender Status. The disposition of the messages may include sending the messages to a junk mail box, putting the messages into a SPAM folder, Writing the messages into a log?le, or simply deleting the messages. At Step (309), Held Message Handler (35) Will deliver to the recipient(s) ALL messages in the Temporary Message Stor age (36) that are from the particular Sender, and thereafter, the process continues at Step (307) again to process the next item in the List of Sender Status. [0088] At Step (311), Held Message Handler (35) Will maintain ALL the messages from the particular Sender in the Temporary Message Storage (36). The process then contin ues at Step (307) to again process the next item in the List of Sender Status. After?nishing processing ALL the items in the List of Sender Status at Step (308), (309), or (311), the process ends. [0089] Referring now to FIG. 5, the logical How of the Check Sender Status Service (27) in the Data Center (102) is shown. The function of the Check Sender Status Service (27) is to receive the (optionally signed and encrypted) Check Sender Request (401) sent from the SPAM Filter at Step (204) of FIG. 2, and then return a (optionally signed and encrypted) Sender Status Response (402) that Will be received by the SPAM Filter at Step (205) of FIG. 2. [0090] The process of Check Sender Status Service (27) starts at Step (500) When the (optionally signed and encrypted) Check Sender Request (401) sent from the SPAM?lter at Step (204) is received. At Step (501), Check Sender Status Service (27) decrypts and veri?es the signed and encrypted Request using the Crypto Engine (26) to recover the Check Sender Request (401) as necessary. The veri?ca tion can not only verify the digital signature on the Request using the public key of the SPAM Filter, but can also verify that the SPAM Filter s public key is in the List of SPAM Filer Public Keys (30) to ensure that the key is authentic. The Check Sender Request (401) may not be signed and encrypted at all, When it is sent from a third party hosted SPAM Filter (105) situated in the same secure environment of the Data Center (102). In such a case, Step (501) can be skipped. If the decryption or veri?cation fails at Step (501), the process continues at Step (513), Which returns an error response to the SPAM Filter, and the process ends. If all the decryption and veri?cations succeed, the process continues to Step (502). [0091] At Step (502), Check Sender Status Service (27) checks the status of Sender Address. There are 4 possibilities: a) the Sender is in the White List (21), b) the Sender is in the Black List (22), c) the Sender is in the Uncon?rmed List (23), and d) the Sender is not in any of the lists. For cases a) and b) the Sender is either in the White List (21) or is in the Black List (22), the process continues at Step (508). For cases c) and d) the Sender is either in the Uncon?rmed List (23) or not in any list at all, the process continues at Step (505). [0092] At Step (505), Check Sender Status Service (27) checks Whether a con?rmation message (e.g., ) for the same message (e.g., as identi?ed by subject and time) has been sent to the Sender Location (e.g., ) Address previously. This step checks if a record can be found in the Con?rmation Message Records (20) that contains the iden tifying information (e.g., Address, Subject, and Time) matching these items in the Check Sender Request (401). If so, the process continues at Step (508). OtherWise, the process continues at Step (506). Using the uniqueness of the identifying information (e.g., the Sender Address, Subject, and Time), the Data Center (102) can avoid sending multiple con?rmation messages When a message addressed to multiple recipients is processed by several SPAM Filters. In other Words, When an uncon?rmed sender sends out one message to many recipients, he/she Will only receive one con?rmation message, regardless how many recipients are in the To:, Ccz, and Bccz?elds. HoWever, the uncon?rmed sender Will continue receiving one con?rmation message for each distinct message he sends out, regardless the number of recipients in the message header, until he answers one of the con?rmation messages. Thereafter, the Sender Will be included in the White List (21) and Will not receive any further con?rmation messages. The advantage of such a design is that it gives the Sender ample chances to answer one of the con?rmation messages, even if the?rst a few con?rmation messages are lost, ignored, or accidentally deleted. Such a design also avoids the annoyance of receiv
20 US 2005/ A1 Jan. 20, 2005 ing too many con?rmation messages. While the Subject and Time, Which are also needed in the con?rmation message to refer to the original message (see Step (506) below), are used to uniquely identify the message here, alternative Ways of uniquely identifying the message are possible. For example, the Message-ID can be used to uniquely identify the message. [0093] At Step (506), Check Sender Status Service (27) sends a con?rmation message (e.g., ) to Sender (e.g., using the Sender Address). A Con?rmation Message Record Will also be created in the Con?rmation Message Records (20). The Record is identi?ed by a unique Con?r mation Identi?er (ID) and, in one implementation, includes the Sender Address, Subject, and Time obtained from the Check Sender Request (401), and a randomly generated AuthoriZation Code. A typical example of a con?rmation is shown in FIG. 7. While the text of the con?rmation message is arbitrary as long as it explains the purpose of the message and What to do With it, a few design considerations should be noted. [0094] The con?rmation message can include a hyperlink that includes the unique Con?rmation ID (id= 8afc2389cb98d401 in the example). This ID Will be sent to Data Center (102) When the hyperlink is clicked allowing the Data Center (102) to quickly?nd the corresponding record in the Con?rmation Message Records (20). [0095] The subject of the con?rmation message can be Re: plus the original subject (Subject in Check Sender Request (401)). This gives the original message sender an indication that the con?rmation message is in response to his original message. OtherWise, the con?rmation message itself can be easily mistaken as a SPAM and ignored, because it is from a location (e.g., address (antispamcenter@zixcorp.com in the example)) unknown to the original message sender. The subject and the time (Subject and Time in Check Sender Request (401)) are used to refer to the original message. In one implementation, there is no mentioning of the recipients. This avoids expos ing the recipients addresses in the con?rmation message, Which is sent in the clear (not encrypted). As mentioned before, a Well-designed system should avoid unnecessary exposure of user addresses. [0096] The AuthoriZation Code can be randomly gener ated, converted to a distorted graphic form, such as a GIF, and then attached to the con?rmation message. This makes it very dif?cult for a machine to recognize the authorization code. It requires a human to answer the con?rmation correctly. [0097] One noteworthy example situation relates to the processing of the con?rmation messages by the SPAM Filters, if for example the Sender has a SPAM Filter installed. In order to avoid unnecessary delays, the sender address of the con?rmation message (antispamcenter@zixcorp.com in the example of FIG. 7), can be included in White List (21) before Data Center (102) starts to operate. This Will cause all SPAM Filters to allow the con?rmation messages to pass through the system imme diately. The sender address of the con?rmation message (e.g. antispamcenter@zixcorp.com) can require a pass code, because the address Will become common knowledge. Accordingly to avoid spammers from spoo?ng the system, the Pass Code can be used and veri?ed by all SPAM Filters. The Pass Code can be included in a user header in the con?rmation message and the same Pass Code can be returned in the Sender Status Response (402) When the SPAM Filter queries the status of the sender address (e.g., antispamcenter@zixcorp.com). Because the Data Center (102) controls both the Pass Code in the con?rmation message and the Pass Code in the Sender Status Response (402), the Pass Code for the Sender Location (e.g., antispamcenter@zixcorp.com) can be changed frequently to avoid being discovered and used by spammers. [0098] In an alternative implementation, the domains or addresses protected by a SPAM Filter can be manually entered into the White list When a customer purchases the SPAM Filter. In this Way, the con?rmation messages Will never be sent to an address protected by a SPAM Filter (because the address protected by the SPAM Filter has already been added to the White list When the customer purchased the SPAM Filter). In such an alternative imple mentation, if the sender address of the con?rmation message (e.g., antispamcenter@zixcorp.com) is used only for sending con?rmation s and not for other purposes (e.g. contacting customers), then it can be included in Black list (22) to block messages that appear to be originating from it. In this case, the notices, such as those shown in FIG. 9 should use a sender address that is different from the sender address of the con?rmation to avoid being blocked. [0099] After sending the con?rmation message at Step (506), the process continues at Step (507) to update the Uncon?rmed List (23). In one implementation, each item in the Uncon?rmed List (23) contains the Sender data (e.g., Sender Address), the time the?rst con?rmation message Was sent (Which can be used to calculate the maximum time (T) the Data Center (102) has been Waiting for the answer to the con?rmation messages), and the number of con?rmation messages sent The procedure of updating the Uncon?rmed List (23) depends on Whether the Sender is already in the List (depends on Whether it is case c), or case d described above)). If the Sender is already in the Uncon?rmed List (23) (case c)), the process Will simply increase the number of con?rmation s sent (N) by 1. On the other hand, if the Sender is not in the Uncon?rmed List (23) (case d)), the process Will add a new item to the Uncon?rmed List (23). The item added to the Uncon?rmed List (23) can include the Sender Address, the time of the?rst con?rmation (the time of the con?rmation sent at Step (506) (Which can be used to calculate (T) later), and the number of con?rmation s sent N=1. After Step (507), the process for cases c) and d) also continues at Step (508). [0100] At Step (508) Check Sender Status Service (27) composes an appropriate Sender Status Response (402). In one implementation, the data items included in the Sender Status Response is shown in item (402) of FIG. 4. In this example, the Response includes the Sender Address and the Sender Status indicating Whether the Sender is in the White List (21), in the Black List (22), or in the Uncon?rmed List (23). If the Sender is in the White List (21) and is marked as pass code required, the associated Pass Code Will also be include in the Sender Status Response (402). If the Sender is in the Uncon?rmed List (23), the number of con?rmation s sent (N), and the maximum time the Data Center is Waiting for the answer to the con?rmation
US 20020141557A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0141557 A1 STRANDBERG (43) Pub. Date: Oct.
 ---- US 20020141557A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0141557 A1 STRANDBERG (43) Pub. Date: (54) SYSTEM AND METHOD FOR PROVIDING AN AUTOMATIC TELEPHONE CALL
---- US 20020141557A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0141557 A1 STRANDBERG (43) Pub. Date: (54) SYSTEM AND METHOD FOR PROVIDING AN AUTOMATIC TELEPHONE CALL
Telephone Dressing Systems - Advantages and Disadvantages
 I US 20030185352A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0185352 A1 Savage et al. (43) Pub. Date: (54) AUTOMATED MESSAGE BROADCAST SYSTEM WITH DUAL MESSAGE SOURCES
I US 20030185352A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0185352 A1 Savage et al. (43) Pub. Date: (54) AUTOMATED MESSAGE BROADCAST SYSTEM WITH DUAL MESSAGE SOURCES
Lookup CNAM / other database for calllng
 (19) United States US 20140003589Al (12) Patent Application Publication (10) Pub. No.: US 2014/0003589 A1 Martino et al. (43) Pub. Date: Jan. 2, 2014 (54) (71) (72) (73) (21) (22) (63) PROVIDING AUDIO
(19) United States US 20140003589Al (12) Patent Application Publication (10) Pub. No.: US 2014/0003589 A1 Martino et al. (43) Pub. Date: Jan. 2, 2014 (54) (71) (72) (73) (21) (22) (63) PROVIDING AUDIO
US 20050027827A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0027827 A1 Owhadi et al. (43) Pub. Date: Feb.
 US 20050027827A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0027827 A1 Owhadi et al. (43) Pub. Date: Feb. 3, 2005 (54) SYSTEM FOR PROVIDING SUPPORT FOR AN ELECTRONIC
US 20050027827A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0027827 A1 Owhadi et al. (43) Pub. Date: Feb. 3, 2005 (54) SYSTEM FOR PROVIDING SUPPORT FOR AN ELECTRONIC
(12) United States Patent (16) Patent N6.= US 6,611,861 B1 Schairer et al. (45) Date of Patent: Aug. 26, 2003
 US006611861B1 (12) United States Patent (16) Patent N6.= Schairer et al. () Date of Patent: Aug. 26, 2003 (54) INTERNET HOSTING AND ACCESS SYSTEM Primary Examiner AyaZ Sheikh AND METHOD Assistant Examiner
US006611861B1 (12) United States Patent (16) Patent N6.= Schairer et al. () Date of Patent: Aug. 26, 2003 (54) INTERNET HOSTING AND ACCESS SYSTEM Primary Examiner AyaZ Sheikh AND METHOD Assistant Examiner
US 20070016324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016324 A1. Operating System. 106 q f 108.
 US 20070016324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016324 A1 Oddiraj u et al. (43) Pub. Date: Jan. 18, 2007 (54) SYSTEM BOOT OPTMZER (75) nventors: Chandar
US 20070016324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016324 A1 Oddiraj u et al. (43) Pub. Date: Jan. 18, 2007 (54) SYSTEM BOOT OPTMZER (75) nventors: Chandar
Hay (43) Pub. Date: Oct. 17, 2002
 US 20020152322A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0152322 A1 Hay (43) Pub. Date: Oct. 17, 2002 (54) (76) (21) (22) (51) (52) METHOD AND APPARATUS FOR FACILITATING
US 20020152322A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0152322 A1 Hay (43) Pub. Date: Oct. 17, 2002 (54) (76) (21) (22) (51) (52) METHOD AND APPARATUS FOR FACILITATING
US 201203 03424Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303424 A1 Lundstrom (43) Pub. Date: NOV.
 US 201203 03424Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303424 A1 Lundstrom (43) Pub. Date: NOV. 29, 2012 (54) METHOD AND SOFTWARE FOR Publication Classi?cation
US 201203 03424Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303424 A1 Lundstrom (43) Pub. Date: NOV. 29, 2012 (54) METHOD AND SOFTWARE FOR Publication Classi?cation
(12) Patent Application Publication (10) Pub. No.: US 2003/0035525 A1 Wu et al. (43) Pub. Date: Feb. 20, 2003
 (19) United States US 20030035525A1 (12) Patent Application Publication (10) Pub. No.: US 2003/0035525 A1 Wu et al. (43) Pub. Date: (54) (76) (21) (22) SYSTEM AND METHOD FOR DISTINGUISHING TELEPHONE NUMBER
(19) United States US 20030035525A1 (12) Patent Application Publication (10) Pub. No.: US 2003/0035525 A1 Wu et al. (43) Pub. Date: (54) (76) (21) (22) SYSTEM AND METHOD FOR DISTINGUISHING TELEPHONE NUMBER
software, and perform automatic dialing according to the /*~102
 US 20140105199A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0105199 A1 Tian (43) Pub. Date: (54) METHOD AND APPARATUS FOR AUTOMATIC DIALING ACCESS POINTS (71) Applicant:
US 20140105199A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0105199 A1 Tian (43) Pub. Date: (54) METHOD AND APPARATUS FOR AUTOMATIC DIALING ACCESS POINTS (71) Applicant:
Filtering E-mail for Spam: PC
 Filtering E-mail for Spam: PC Last Revised: April 2003 Table of Contents Introduction... 1 Objectives... 1 Filtering E-mail for Spam... 2 What Is Spam?... 2 What Is UT Doing About Spam?... 2 What Can You
Filtering E-mail for Spam: PC Last Revised: April 2003 Table of Contents Introduction... 1 Objectives... 1 Filtering E-mail for Spam... 2 What Is Spam?... 2 What Is UT Doing About Spam?... 2 What Can You
I SEARCH DATABASE l/ VISIT WEBSITE k ( UPDATE RECORDS Y (54) (75) (73) (21) (22) (63) (60) (US); Gary Stephen Shuster, Oakland, SELECT SUB-DOMAIN NAME
 US 20060293973Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0293973 A1 Shuster et al. (43) Pub. Date: Dec. 28, 2006 (54) (75) (73) (21) (22) (63) (60) METHOD AND APPARATUS
US 20060293973Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0293973 A1 Shuster et al. (43) Pub. Date: Dec. 28, 2006 (54) (75) (73) (21) (22) (63) (60) METHOD AND APPARATUS
(Us) (73) Assignee: Avaya Technology Corp. Je?' McElroy, Columbia, SC (US); (21) Appl. No.: 10/413,024. (22) Filed: Apr. 14, 2003 (57) ABSTRACT
 US 20040202300A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0202300 A1 Cooper et al. (43) Pub. Date: Oct. 14, 2004 (54) CALL HANDLING USING NON-SPEECH CUES VIA A PERSONAL
US 20040202300A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0202300 A1 Cooper et al. (43) Pub. Date: Oct. 14, 2004 (54) CALL HANDLING USING NON-SPEECH CUES VIA A PERSONAL
(71) Applicant: SPEAKWRITE, LLC,Austin, TX (US)
 US 20130304465Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0304465 A1 Henry et al. (43) Pub. Date: NOV. 14, 2013 (54) METHOD AND SYSTEM FOR AUDIO-VIDEO (52) US. Cl.
US 20130304465Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0304465 A1 Henry et al. (43) Pub. Date: NOV. 14, 2013 (54) METHOD AND SYSTEM FOR AUDIO-VIDEO (52) US. Cl.
USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362. Hunt et al. [45] Date of Patent: Nov. 21, 1995
![USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362. Hunt et al. [45] Date of Patent: Nov. 21, 1995 USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362. Hunt et al. [45] Date of Patent: Nov. 21, 1995](/thumbs/30/14713887.jpg) llllllllllllllllllllllllllllllllllllllllll l llllllllllllllllllllllll USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362 Hunt et al. [45] Date of Patent: Nov. 21, 1995 [54] DISPATCHING
llllllllllllllllllllllllllllllllllllllllll l llllllllllllllllllllllll USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362 Hunt et al. [45] Date of Patent: Nov. 21, 1995 [54] DISPATCHING
US 20120222106Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0222106 A1 Kuehl (43) Pub. Date: Aug.
 US 20120222106Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0222106 A1 Kuehl (43) Pub. Date: (54) AUTOMATED HYBRID CONNECTIONS (52) US. Cl...... 726/11 BETWEEN MULTIPLE
US 20120222106Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0222106 A1 Kuehl (43) Pub. Date: (54) AUTOMATED HYBRID CONNECTIONS (52) US. Cl...... 726/11 BETWEEN MULTIPLE
Filtering E-mail for Spam: Macintosh
 Filtering E-mail for Spam: Macintosh Last Revised: April 2003 Table of Contents Introduction... 1 Objectives... 1 Filtering E-mail for Spam... 2 What Is Spam?... 2 What Is UT Doing About Spam?... 2 What
Filtering E-mail for Spam: Macintosh Last Revised: April 2003 Table of Contents Introduction... 1 Objectives... 1 Filtering E-mail for Spam... 2 What Is Spam?... 2 What Is UT Doing About Spam?... 2 What
Avira Managed Email Security AMES FAQ. www.avira.com
 Avira Managed Email Security AMES FAQ www.avira.com Can AMES be used immediately after an account for our organization has been set up in the MyAccount user portal? Using your account requires a change
Avira Managed Email Security AMES FAQ www.avira.com Can AMES be used immediately after an account for our organization has been set up in the MyAccount user portal? Using your account requires a change
/ \33 40 \ / \\ \ \ M / 32. 28f 1. (19) United States (12) Patent Application Publication Lawser et al. NETWORK \ 36. SERVlCE 'NTERNET SERVICE
 (19) United States (12) Patent Application Publication Lawser et al. US 20130336314A1 (10) Pub. N0.: US 2013/0336314 A1 (43) Pub. Date: Dec. 19, 2013 (54) (71) (72) (73) (21) (22) (63) METHOD FOR COMPLETING
(19) United States (12) Patent Application Publication Lawser et al. US 20130336314A1 (10) Pub. N0.: US 2013/0336314 A1 (43) Pub. Date: Dec. 19, 2013 (54) (71) (72) (73) (21) (22) (63) METHOD FOR COMPLETING
\ \ \ connection connection connection interface interface interface
 US 20140122910A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20140122910 A1 Chiu et al. (43) Pub. Date: May 1, 2014 (54) RACK SERVER SYSTEM AND OPERATION Publication Classi?cation
US 20140122910A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20140122910 A1 Chiu et al. (43) Pub. Date: May 1, 2014 (54) RACK SERVER SYSTEM AND OPERATION Publication Classi?cation
Back up information data by blocks, and generate backup data of each block
 US 20140046903A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046903 A1 Ylll (43) Pub. Date: (54) DATA BACKUP AND RECOVERY METHOD Publication Classi?cation FOR MOBILE
US 20140046903A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046903 A1 Ylll (43) Pub. Date: (54) DATA BACKUP AND RECOVERY METHOD Publication Classi?cation FOR MOBILE
US 20020174380A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2002/0174380 A1. Mannarsamy (43) Pub. Date: NOV.
 US 20020174380A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2002/0174380 A1 Mannarsamy (43) Pub. Date: NOV. 21, 2002 (54) HELPDESK SYSTEM AND METHOD (52) US. Cl...... 714/25
US 20020174380A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2002/0174380 A1 Mannarsamy (43) Pub. Date: NOV. 21, 2002 (54) HELPDESK SYSTEM AND METHOD (52) US. Cl...... 714/25
SPAM FILTER Service Data Sheet
 Content 1 Spam detection problem 1.1 What is spam? 1.2 How is spam detected? 2 Infomail 3 EveryCloud Spam Filter features 3.1 Cloud architecture 3.2 Incoming email traffic protection 3.2.1 Mail traffic
Content 1 Spam detection problem 1.1 What is spam? 1.2 How is spam detected? 2 Infomail 3 EveryCloud Spam Filter features 3.1 Cloud architecture 3.2 Incoming email traffic protection 3.2.1 Mail traffic
Secure Email Frequently Asked Questions
 Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Microsoft Outlook 2010 contains a Junk E-mail Filter designed to reduce unwanted e-mail messages in your
 Overview of the Junk E-mail Filter in Outlook (Much of this text is extracted from the Outlook Help files.) Microsoft Outlook 2010 contains a Junk E-mail Filter designed to reduce unwanted e-mail messages
Overview of the Junk E-mail Filter in Outlook (Much of this text is extracted from the Outlook Help files.) Microsoft Outlook 2010 contains a Junk E-mail Filter designed to reduce unwanted e-mail messages
(12) United States Patent Edelen
 US008285799B2 (12) United States Patent Edelen (10) Patent N0.: (45) Date of Patent: Oct. 9, 2012 (54) QUOTA-BASED ARCHIVING (75) Inventor: James Edelen, Renton, WA (U S) (73) Assignee: Microsoft Corporation,
US008285799B2 (12) United States Patent Edelen (10) Patent N0.: (45) Date of Patent: Oct. 9, 2012 (54) QUOTA-BASED ARCHIVING (75) Inventor: James Edelen, Renton, WA (U S) (73) Assignee: Microsoft Corporation,
(12) United States Patent
 US008914855B2 (12) United States Patent Whitmyer, Jr. (10) Patent N0.: (45) Date of Patent: US 8,914,855 B2 Dec. 16, 2014 (54) PORTABLE PASSWORD KEEPER WITH INTERNET STORAGE AND RESTORE (75) Inventor:
US008914855B2 (12) United States Patent Whitmyer, Jr. (10) Patent N0.: (45) Date of Patent: US 8,914,855 B2 Dec. 16, 2014 (54) PORTABLE PASSWORD KEEPER WITH INTERNET STORAGE AND RESTORE (75) Inventor:
Email Marketing Do s and Don ts A Sprint Mail Whitepaper
 Email Marketing Do s and Don ts A Sprint Mail Whitepaper Table of Contents: Part One Email Marketing Dos and Don ts The Right Way of Email Marketing The Wrong Way of Email Marketing Outlook s limitations
Email Marketing Do s and Don ts A Sprint Mail Whitepaper Table of Contents: Part One Email Marketing Dos and Don ts The Right Way of Email Marketing The Wrong Way of Email Marketing Outlook s limitations
No filter is perfect. But with your help, MailCleaner may aim at perfection. Case Description Solution
 A Filter inaccuracies No filter is perfect. But with your help, MailCleaner may aim at perfection. The filtering system implemented by MailCleaner relies on automated and systematic controls that cannot
A Filter inaccuracies No filter is perfect. But with your help, MailCleaner may aim at perfection. The filtering system implemented by MailCleaner relies on automated and systematic controls that cannot
Cloud Services. Email Anti-Spam. Admin Guide
 Cloud Services Email Anti-Spam Admin Guide 10/23/2014 CONTENTS Introduction to Anti- Spam... 4 About Anti- Spam... 4 Locating the Anti- Spam Pages in the Portal... 5 Anti- Spam Best Practice Settings...
Cloud Services Email Anti-Spam Admin Guide 10/23/2014 CONTENTS Introduction to Anti- Spam... 4 About Anti- Spam... 4 Locating the Anti- Spam Pages in the Portal... 5 Anti- Spam Best Practice Settings...
US 20020116467A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0116467 A1 Boyer et al. (43) Pub. Date: Aug.
 US 20020116467A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0116467 A1 Boyer et al. (43) Pub. Date: Aug. 22, 2002 (54) METHOD AND APPARATUS FOR Publication Classi?cation
US 20020116467A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0116467 A1 Boyer et al. (43) Pub. Date: Aug. 22, 2002 (54) METHOD AND APPARATUS FOR Publication Classi?cation
(54) RAPID NOTIFICATION SYSTEM (52) US. Cl... 709/206. (57) ABSTRACT (75) Inventors: Anand Rajasekar, San Jose, CA
 US 20120303720A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303720 A1 Rajasekar et a]. (43) Pub. Date: NOV. 29, 2012 (54) RAPID NOTIFICATION SYSTEM (52) US. Cl......
US 20120303720A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303720 A1 Rajasekar et a]. (43) Pub. Date: NOV. 29, 2012 (54) RAPID NOTIFICATION SYSTEM (52) US. Cl......
US 20130073440A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0073440 A1 Chen (57)
 US 20130073440A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0073440 A1 Chen (43) Pub. Date: Mar. 21, 2013 (54) PAYROLL SYSTEM AND METHOD Publication Classi?cation (76)
US 20130073440A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0073440 A1 Chen (43) Pub. Date: Mar. 21, 2013 (54) PAYROLL SYSTEM AND METHOD Publication Classi?cation (76)
Quick Start Policy Patrol Mail Security 10
 Quick Start Policy Patrol Mail Security 10 This guide will help you start using Policy Patrol Mail Security as quickly as possible. For more detailed instructions, consult the Policy Patrol manual. Step
Quick Start Policy Patrol Mail Security 10 This guide will help you start using Policy Patrol Mail Security as quickly as possible. For more detailed instructions, consult the Policy Patrol manual. Step
About this documentation
 Wilkes University, Staff, and Students have a new email spam filter to protect against unwanted email messages. Barracuda SPAM Firewall will filter email for all campus email accounts before it gets to
Wilkes University, Staff, and Students have a new email spam filter to protect against unwanted email messages. Barracuda SPAM Firewall will filter email for all campus email accounts before it gets to
US 20140046812A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046812 A1 FAN et al. (43) Pub. Date: Feb.
 US 20140046812A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046812 A1 FAN et al. (43) Pub. Date: (54) EXPENSE REPORTS FOR PAYMENTS MADE (52) US. Cl. WITH A MOBILE DEVICE
US 20140046812A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046812 A1 FAN et al. (43) Pub. Date: (54) EXPENSE REPORTS FOR PAYMENTS MADE (52) US. Cl. WITH A MOBILE DEVICE
US 20090157756Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0157756 A1 Sanvido (43) Pub. Date: Jun.
 US 20090157756Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0157756 A1 Sanvido (43) Pub. Date: Jun. 18, 2009 (54) FILE SYSTEM FOR STORING FILES IN Publication Classi?cation
US 20090157756Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0157756 A1 Sanvido (43) Pub. Date: Jun. 18, 2009 (54) FILE SYSTEM FOR STORING FILES IN Publication Classi?cation
Implementing Transparent Security for Desktop Encryption Users
 Implementing Transparent Security for Desktop Encryption Users Solutions to automate email encryption with external parties Get this White Paper Entrust Inc. All All Rights Reserved. 1 1 Contents Introduction...
Implementing Transparent Security for Desktop Encryption Users Solutions to automate email encryption with external parties Get this White Paper Entrust Inc. All All Rights Reserved. 1 1 Contents Introduction...
Outlook 2010 basics quick reference sheet
 Outlook 2010 basics Microsoft Outlook 2010 is the world s leading personal information management and communications application. Outlook 2010 delivers complete e-mail, contact, calendar, and task functionality.
Outlook 2010 basics Microsoft Outlook 2010 is the world s leading personal information management and communications application. Outlook 2010 delivers complete e-mail, contact, calendar, and task functionality.
Provisional application No. 61/082,685,?led on Jul. 22, 2008. the non-member private key are not generated. 116 Registered Log Archive
 US 20100023757Al (19) United States (12) Patent Application Publication (10) Pub. N0.2 US 2010/0023757 A1 Nguyen-Huu et al. (43) Pub. Date: (54) (75) (73) (21) (22) (60) METHODS AND SYSTEMS FOR SENDING
US 20100023757Al (19) United States (12) Patent Application Publication (10) Pub. N0.2 US 2010/0023757 A1 Nguyen-Huu et al. (43) Pub. Date: (54) (75) (73) (21) (22) (60) METHODS AND SYSTEMS FOR SENDING
Email Security 8.0 User Guide
 Email Security 8.0 User Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential damage to
Email Security 8.0 User Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential damage to
Spam-Blocking Server m
 US 20120131118A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0131118 A1 Oliver et al. (43) Pub. Date: May 24, 2012 (54) SIGNATURE GENERATION USING MESSAGE Publication
US 20120131118A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0131118 A1 Oliver et al. (43) Pub. Date: May 24, 2012 (54) SIGNATURE GENERATION USING MESSAGE Publication
escan Anti-Spam White Paper
 escan Anti-Spam White Paper Document Version (esnas 14.0.0.1) Creation Date: 19 th Feb, 2013 Preface The purpose of this document is to discuss issues and problems associated with spam email, describe
escan Anti-Spam White Paper Document Version (esnas 14.0.0.1) Creation Date: 19 th Feb, 2013 Preface The purpose of this document is to discuss issues and problems associated with spam email, describe
Introduction. How does email filtering work? What is the Quarantine? What is an End User Digest?
 Introduction The purpose of this memo is to explain how the email that originates from outside this organization is processed, and to describe the tools that you can use to manage your personal spam quarantine.
Introduction The purpose of this memo is to explain how the email that originates from outside this organization is processed, and to describe the tools that you can use to manage your personal spam quarantine.
Policy Patrol 7 Upgrade Guide
 Policy Patrol 7 technical documentation September 4, 2012 www.policypatrol.com If you have Policy Patrol 4, 5 or 6 installed you can upgrade to version 7 and keep your existing configuration. Please follow
Policy Patrol 7 technical documentation September 4, 2012 www.policypatrol.com If you have Policy Patrol 4, 5 or 6 installed you can upgrade to version 7 and keep your existing configuration. Please follow
(30) Foreign Application Priority Data
 US 20040015727A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0015727 A1 Lahti et al. (43) Pub. Date: Jan. 22, 2004 (54) SYNCHRONIZATION METHOD (76) Inventors: Jerry Lahti,
US 20040015727A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0015727 A1 Lahti et al. (43) Pub. Date: Jan. 22, 2004 (54) SYNCHRONIZATION METHOD (76) Inventors: Jerry Lahti,
US 20030110248A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2003/0110248 A1 Ritchc (43) Pub. Date: Jun.
 US 20030110248A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2003/0110248 A1 Ritchc (43) Pub. Date: (54) (76) (21) (22) (51) (52) AUTOMATED SERVICE SUPPORT OF SOFTWARE DISTRIBUTION
US 20030110248A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2003/0110248 A1 Ritchc (43) Pub. Date: (54) (76) (21) (22) (51) (52) AUTOMATED SERVICE SUPPORT OF SOFTWARE DISTRIBUTION
US 20070203917A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0203917 A1 Du et al. (43) Pub. Date: Aug.
 ' i.. 2. Y. US 20070203917A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0203917 A1 Du et al. (43) Pub. Date: (54) COMMUNICATION SYSTEM AND METHOD FOR IMPLEMENTING ONLINE
' i.. 2. Y. US 20070203917A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0203917 A1 Du et al. (43) Pub. Date: (54) COMMUNICATION SYSTEM AND METHOD FOR IMPLEMENTING ONLINE
Trend Micro Hosted Email Security Stop Spam. Save Time.
 Trend Micro Hosted Email Security Stop Spam. Save Time. How it Works: Trend Micro Hosted Email Security A Trend Micro White Paper l March 2010 Table of Contents Introduction...3 Solution Overview...4 Industry-Leading
Trend Micro Hosted Email Security Stop Spam. Save Time. How it Works: Trend Micro Hosted Email Security A Trend Micro White Paper l March 2010 Table of Contents Introduction...3 Solution Overview...4 Industry-Leading
Emailing from The E2 Shop System EMail address Server Name Server Port, Encryption Protocol, Encryption Type, SMTP User ID SMTP Password
 Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Email Getting Started Guide Unix Platform
 Edition/Issue Email Getting Started Guide Unix Platform One of the most important features of your new Web Hosting account is access to a personalized Email solution that includes individual Email addresses
Edition/Issue Email Getting Started Guide Unix Platform One of the most important features of your new Web Hosting account is access to a personalized Email solution that includes individual Email addresses
Patent Application Publication Sep. 30, 2004 Sheet 1 0f 2. Hierarchical Query. Contact Ow FIG. 1
 US 20040193595A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0193595 A1 Kaminsky et al. (43) Pub. Date: Sep. 30, 2004 (54) NEAREST KNOWN PERSON DIRECTORY FUNCTION (75)
US 20040193595A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0193595 A1 Kaminsky et al. (43) Pub. Date: Sep. 30, 2004 (54) NEAREST KNOWN PERSON DIRECTORY FUNCTION (75)
ENCODED $30 CERT'F'CATE -+ DECODE CERTIFICATE
 US 20130346742A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0346742 A1 Tada et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR DEVICE Publication Classi?cation AUTHENTICATION
US 20130346742A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0346742 A1 Tada et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR DEVICE Publication Classi?cation AUTHENTICATION
Basic E- mail Skills. Google s Gmail. www.netliteracy.org
 Email it s convenient, free and easy. Today, it is the most rapidly growing means of communication. This is a basic introduction to email and we use a conversational non- technical style to explain how
Email it s convenient, free and easy. Today, it is the most rapidly growing means of communication. This is a basic introduction to email and we use a conversational non- technical style to explain how
The basic groups of components are described below. Fig X- 1 shows the relationship between components on a network.
 Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
English Translation of SecurityGateway for Exchange/SMTP Servers
 Testing: Alt N Technologies SecurityGateway by Sandra Lucifora Administrators spend a considerable amount of their time on the job on eliminating unwanted messages. Viruses, Phishing, and Spoofing pose
Testing: Alt N Technologies SecurityGateway by Sandra Lucifora Administrators spend a considerable amount of their time on the job on eliminating unwanted messages. Viruses, Phishing, and Spoofing pose
NJ (US) (51) Int. Cl. H04L 9/00 (2006.01) Correspondence Address: (52) US. Cl... 380/278; 713/ 150 ALFRED C. ROTH (57) ABSTRACT
 . I. I. I US 20080187140A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0187140 A1 McGillian et al. (43) Pub. Date: Aug. 7, 2008 (54) METHOD AND SYSTEM OF SECURELY Related
. I. I. I US 20080187140A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0187140 A1 McGillian et al. (43) Pub. Date: Aug. 7, 2008 (54) METHOD AND SYSTEM OF SECURELY Related
(IP Connection) Miami (54) (76) (21) (22) (51) (52) Application
 US 20070016777Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016777 A1 Henderson et al. (43) Pub. Date: Jan. 18, 2007 (54) (76) (21) (22) (51) (52) METHOD OF AND SYSTEM
US 20070016777Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016777 A1 Henderson et al. (43) Pub. Date: Jan. 18, 2007 (54) (76) (21) (22) (51) (52) METHOD OF AND SYSTEM
FTA Computer Security Workshop. Secure Email
 FTA Computer Security Workshop Secure Email March 8, 2007 Stan Wiechert, KDOR IS Security Officer Outline of Presentation The Risks associated with Email Business Constraints Secure Email Features Some
FTA Computer Security Workshop Secure Email March 8, 2007 Stan Wiechert, KDOR IS Security Officer Outline of Presentation The Risks associated with Email Business Constraints Secure Email Features Some
Handling Unsolicited Commercial Email (UCE) or spam using Microsoft Outlook at Staffordshire University
 Reference : USER 190 Issue date : January 2004 Revised : November 2007 Classification : Staff Originator : Richard Rogers Handling Unsolicited Commercial Email (UCE) or spam using Microsoft Outlook at
Reference : USER 190 Issue date : January 2004 Revised : November 2007 Classification : Staff Originator : Richard Rogers Handling Unsolicited Commercial Email (UCE) or spam using Microsoft Outlook at
Symantec Hosted Mail Security Getting Started Guide
 Symantec Hosted Mail Security Getting Started Guide Redirecting Your MX Record You have successfully activated your domain within the Symantec Hosted Mail Security Console. In order to begin the filtration
Symantec Hosted Mail Security Getting Started Guide Redirecting Your MX Record You have successfully activated your domain within the Symantec Hosted Mail Security Console. In order to begin the filtration
Libra Esva. Whitepaper. Glossary. How Email Really Works. Email Security Virtual Appliance. May, 2010. It's So Simple...or Is It?
 Libra Esva Email Security Virtual Appliance Whitepaper May, 2010 How Email Really Works Glossary 1 2 SMTP is a protocol for sending email messages between servers. DNS (Domain Name System) is an internet
Libra Esva Email Security Virtual Appliance Whitepaper May, 2010 How Email Really Works Glossary 1 2 SMTP is a protocol for sending email messages between servers. DNS (Domain Name System) is an internet
US 20020072350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0072350 A1 Fukuzato (43) Pub. Date: Jun.
 US 20020072350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20020072350 A1 Fukuzato (43) Pub. Date: Jun. 13, 2002 (54) BACKUP METHOD OF APPLICATIONS OF PORTABLE CELLULAR PHONE
US 20020072350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20020072350 A1 Fukuzato (43) Pub. Date: Jun. 13, 2002 (54) BACKUP METHOD OF APPLICATIONS OF PORTABLE CELLULAR PHONE
Network Service, Systems and Data Communications Monitoring Policy
 Network Service, Systems and Data Communications Monitoring Policy Purpose This Policy defines the environment and circumstances under which Network Service, Systems and Data Communications Monitoring
Network Service, Systems and Data Communications Monitoring Policy Purpose This Policy defines the environment and circumstances under which Network Service, Systems and Data Communications Monitoring
ModusMail Software Instructions.
 ModusMail Software Instructions. Table of Contents Basic Quarantine Report Information. 2 Starting A WebMail Session. 3 WebMail Interface. 4 WebMail Setting overview (See Settings Interface).. 5 Account
ModusMail Software Instructions. Table of Contents Basic Quarantine Report Information. 2 Starting A WebMail Session. 3 WebMail Interface. 4 WebMail Setting overview (See Settings Interface).. 5 Account
g 0 No 17 Personalize Message 26 > Fig. 5 '2 i 22 2 Approve Message 12 > Fig. 2
 US 20050256764A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0256764 A1 Beaumont et al. (43) Pub. Date: Nov. 17, 2005 (54) METHOD AND SYSTEM FOR GENERATING (52) US. Cl......
US 20050256764A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0256764 A1 Beaumont et al. (43) Pub. Date: Nov. 17, 2005 (54) METHOD AND SYSTEM FOR GENERATING (52) US. Cl......
Quick Start Policy Patrol Spam Filter 9
 Quick Start Policy Patrol Spam Filter 9 This guide will help you start using Policy Patrol Spam Filter as quickly as possible. For more detailed instructions, consult the Policy Patrol manual. Step 1.
Quick Start Policy Patrol Spam Filter 9 This guide will help you start using Policy Patrol Spam Filter as quickly as possible. For more detailed instructions, consult the Policy Patrol manual. Step 1.
US 20120215907A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0215907 A1 Chung (43) Pub. Date: Aug.
 US 20120215907A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0215907 A1 Chung (43) Pub. Date: (54) SYSTEMS AND METHODS FOR (52) US. Cl...... 709/224 SELF-ADJUSTING LOGGING
US 20120215907A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0215907 A1 Chung (43) Pub. Date: (54) SYSTEMS AND METHODS FOR (52) US. Cl...... 709/224 SELF-ADJUSTING LOGGING
Introduction. Friday, June 21, 2002
 This article is intended to give you a general understanding how ArGoSoft Mail Server Pro, and en Email, in general, works. It does not give you step-by-step instructions; it does not walk you through
This article is intended to give you a general understanding how ArGoSoft Mail Server Pro, and en Email, in general, works. It does not give you step-by-step instructions; it does not walk you through
User Guide. Version 3.0 April 2006
 User Guide Version 3.0 April 2006 2006 Obvious Solutions Inc. All rights reserved. Dabra and Dabra Network are trademarks of Obvious Solutions Inc. All other trademarks owned by their respective trademark
User Guide Version 3.0 April 2006 2006 Obvious Solutions Inc. All rights reserved. Dabra and Dabra Network are trademarks of Obvious Solutions Inc. All other trademarks owned by their respective trademark
(12> Ulllted States Patent (10) Patent N0.: US 6,591,288 B1 Edwards et al. (45) Date of Patent: Jul. 8, 2003
 ' ' US006591288B1 (12> Ulllted States Patent (10) Patent N0.: Edwards et al. (45) Date of Patent: Jul. 8, 2003 (54) DATA NETWORK ACCELERATED ACCESS EP 0837584 4/1998..... H04L/29/06 SYSTEM W0 WO 96/34340
' ' US006591288B1 (12> Ulllted States Patent (10) Patent N0.: Edwards et al. (45) Date of Patent: Jul. 8, 2003 (54) DATA NETWORK ACCELERATED ACCESS EP 0837584 4/1998..... H04L/29/06 SYSTEM W0 WO 96/34340
E-Mail Management Solutions. Spamfinder. MailDepot. MailSealer. 100% spam protection for your business. Compliant, permanent e-mail archiving
 E-Mail Management Solutions Spamfinder MailDepot MailSealer 100% spam protection for your business Compliant, permanent e-mail archiving digital signature and e-mail encryption Spamfinder Anti-spam and
E-Mail Management Solutions Spamfinder MailDepot MailSealer 100% spam protection for your business Compliant, permanent e-mail archiving digital signature and e-mail encryption Spamfinder Anti-spam and
Savita Teli 1, Santoshkumar Biradar 2
 Effective Spam Detection Method for Email Savita Teli 1, Santoshkumar Biradar 2 1 (Student, Dept of Computer Engg, Dr. D. Y. Patil College of Engg, Ambi, University of Pune, M.S, India) 2 (Asst. Proff,
Effective Spam Detection Method for Email Savita Teli 1, Santoshkumar Biradar 2 1 (Student, Dept of Computer Engg, Dr. D. Y. Patil College of Engg, Ambi, University of Pune, M.S, India) 2 (Asst. Proff,
Avoiding Malware in Your Dental Practice. 10 Best Practices to Defend Your Data
 Avoiding Malware in Your Dental Practice 10 Best Practices to Defend Your Data Avoiding Malware in Your Dental Practice Like most small business owners, you must protect your dental practice s computer
Avoiding Malware in Your Dental Practice 10 Best Practices to Defend Your Data Avoiding Malware in Your Dental Practice Like most small business owners, you must protect your dental practice s computer
An Overview of Spam Blocking Techniques
 An Overview of Spam Blocking Techniques Recent analyst estimates indicate that over 60 percent of the world s email is unsolicited email, or spam. Spam is no longer just a simple annoyance. Spam has now
An Overview of Spam Blocking Techniques Recent analyst estimates indicate that over 60 percent of the world s email is unsolicited email, or spam. Spam is no longer just a simple annoyance. Spam has now
IMF Tune Opens Exchange to Any Anti-Spam Filter
 Page 1 of 8 IMF Tune Opens Exchange to Any Anti-Spam Filter September 23, 2005 10 th July 2007 Update Include updates for configuration steps in IMF Tune v3.0. IMF Tune enables any anti-spam filter to
Page 1 of 8 IMF Tune Opens Exchange to Any Anti-Spam Filter September 23, 2005 10 th July 2007 Update Include updates for configuration steps in IMF Tune v3.0. IMF Tune enables any anti-spam filter to
Quick Start Policy Patrol Mail Security 9
 Quick Start Policy Patrol Mail Security 9 This guide will help you start using Policy Patrol Mail Security as quickly as possible. For more detailed instructions, consult the Policy Patrol manual. Step
Quick Start Policy Patrol Mail Security 9 This guide will help you start using Policy Patrol Mail Security as quickly as possible. For more detailed instructions, consult the Policy Patrol manual. Step
SonicWALL Anti-Spam Desktop User Guide
 SonicWALL Anti-Spam Desktop User Guide Version 6.2 SonicWALL, Inc. 2001 Logic Drive San Jose, CA 95124-3452 Phone: +1.408.745.9600 Fax: +1.408.745.9300 E-mail: info@sonicwall.com Part Number: 232-001812-00
SonicWALL Anti-Spam Desktop User Guide Version 6.2 SonicWALL, Inc. 2001 Logic Drive San Jose, CA 95124-3452 Phone: +1.408.745.9600 Fax: +1.408.745.9300 E-mail: info@sonicwall.com Part Number: 232-001812-00
SPAM UNDERSTANDING & AVOIDING
 SPAM UNDERSTANDING & AVOIDING Modified: September 28, 2006 SPAM UNDERSTANDING & AVOIDING...5 What is Spam?...6 How to avoid Spam...6 How to view message headers...8 Setting up a spam rule...10 Checking
SPAM UNDERSTANDING & AVOIDING Modified: September 28, 2006 SPAM UNDERSTANDING & AVOIDING...5 What is Spam?...6 How to avoid Spam...6 How to view message headers...8 Setting up a spam rule...10 Checking
Psychic Psychic Psychic Psychic Psychic
 US 20070274495Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0274495 A1 Youd et al. (43) Pub. Date: NOV. 29, 2007 (54) SYSTEMS AND METHODS FOR EXPERT Publication Classi?cation
US 20070274495Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0274495 A1 Youd et al. (43) Pub. Date: NOV. 29, 2007 (54) SYSTEMS AND METHODS FOR EXPERT Publication Classi?cation
Avoiding Malware in Your Dental Practice. 10 Best Practices to Defend Your Data
 Avoiding Malware in Your Dental Practice 10 Best Practices to Defend Your Data Avoiding Malware in Your Dental Practice Like most small business owners, you must protect your dental practice s computer
Avoiding Malware in Your Dental Practice 10 Best Practices to Defend Your Data Avoiding Malware in Your Dental Practice Like most small business owners, you must protect your dental practice s computer
Typical spam characteristics
 Typical spam characteristics How to effectively block spam and junk mail By Mike Spykerman CEO Red Earth Software This article discusses how spam messages can be distinguished from legitimate messages
Typical spam characteristics How to effectively block spam and junk mail By Mike Spykerman CEO Red Earth Software This article discusses how spam messages can be distinguished from legitimate messages
How To Configure Forefront Threat Management Gateway (Forefront) For An Email Server
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Email Migration Project Plan for Cisco Cloud Email Security
 Sales Tool Email Migration Project Plan for Cisco Cloud Email Security 2014 Cisco and/or its affiliates. All rights reserv ed. This document is Cisco Conf idential. For Channel Partner use only. Not f
Sales Tool Email Migration Project Plan for Cisco Cloud Email Security 2014 Cisco and/or its affiliates. All rights reserv ed. This document is Cisco Conf idential. For Channel Partner use only. Not f
(51) Int Cl.: H04L 12/58 (2006.01) H04L 29/06 (2006.01)
 (19) TEPZZ_986 8 B_T (11) EP 1 986 382 B1 (12) EUROPEAN PATENT SPECIFICATION (4) Date of publication and mention of the grant of the patent: 19.02.14 Bulletin 14/08 (1) Int Cl.: H04L 12/8 (06.01) H04L
(19) TEPZZ_986 8 B_T (11) EP 1 986 382 B1 (12) EUROPEAN PATENT SPECIFICATION (4) Date of publication and mention of the grant of the patent: 19.02.14 Bulletin 14/08 (1) Int Cl.: H04L 12/8 (06.01) H04L
Support systems messaging via email
 > _. US 20110231500A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0231500 A1 Zhu et al. (43) Pub. Date: Sep. 22, 201 1 (54) SYSTEM AND METHOD FOR INTEGRATING Publication
> _. US 20110231500A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0231500 A1 Zhu et al. (43) Pub. Date: Sep. 22, 201 1 (54) SYSTEM AND METHOD FOR INTEGRATING Publication
The GlobalCerts TM SecureMail Gateway TM
 Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
US 20120066004A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0066004 A1 Lee (43) Pub. Date: Mar.
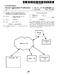 US 212664A1 (19) United States (12) Patent Application Publication (1) Pub. o.: US 212/664 A1 Lee (43) Pub. Date: Mar. 15, 212 (54) (76) (21) (22) (6) METHOD AD SYSTEM FOR PERSOAL ISURACE COMPARISO AD
US 212664A1 (19) United States (12) Patent Application Publication (1) Pub. o.: US 212/664 A1 Lee (43) Pub. Date: Mar. 15, 212 (54) (76) (21) (22) (6) METHOD AD SYSTEM FOR PERSOAL ISURACE COMPARISO AD
PROOFPOINT - EMAIL SPAM FILTER
 416 Morrill Hall of Agriculture Hall Michigan State University 517-355-3776 http://support.anr.msu.edu support@anr.msu.edu PROOFPOINT - EMAIL SPAM FILTER Contents PROOFPOINT - EMAIL SPAM FILTER... 1 INTRODUCTION...
416 Morrill Hall of Agriculture Hall Michigan State University 517-355-3776 http://support.anr.msu.edu support@anr.msu.edu PROOFPOINT - EMAIL SPAM FILTER Contents PROOFPOINT - EMAIL SPAM FILTER... 1 INTRODUCTION...
REPUTATION-BASED MAIL FLOW CONTROL
 WHITE PAPER REPUTATION-BASED MAIL FLOW CONTROL Blocking Extreme Spam and Reducing False Positives Blocking unsolicited commercial email or spam is an increasingly important but difficult task for IT staff.
WHITE PAPER REPUTATION-BASED MAIL FLOW CONTROL Blocking Extreme Spam and Reducing False Positives Blocking unsolicited commercial email or spam is an increasingly important but difficult task for IT staff.
OIS. Update on the anti spam system at CERN. Pawel Grzywaczewski, CERN IT/OIS HEPIX fall 2010
 OIS Update on the anti spam system at CERN Pawel Grzywaczewski, CERN IT/OIS HEPIX fall 2010 OIS Current mail infrastructure Mail service in numbers: ~18 000 mailboxes ~ 18 000 mailing lists (e-groups)
OIS Update on the anti spam system at CERN Pawel Grzywaczewski, CERN IT/OIS HEPIX fall 2010 OIS Current mail infrastructure Mail service in numbers: ~18 000 mailboxes ~ 18 000 mailing lists (e-groups)
Title: Spam Filter Active / Spam Filter Active : CAB Page 1 of 5
 Friday, April 18, 2008 11:24:8 AM Title: Spam Filter Active / Spam Filter Active : CAB Page 1 of 5 Name: Author: Subject: Spam Filter Active CAB Administrator Spam Filter Active Keywords: Category: The
Friday, April 18, 2008 11:24:8 AM Title: Spam Filter Active / Spam Filter Active : CAB Page 1 of 5 Name: Author: Subject: Spam Filter Active CAB Administrator Spam Filter Active Keywords: Category: The
US 20070139188A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0139188 A1 Ollis et al. HOME PROCESSOR /\ J\ NETWORK
 US 20070139188A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0139188 A1 Ollis et al. (43) Pub. Date: Jun. 21, 2007 (54) (75) (73) (21) (22) METHOD AND APPARATUS FOR COMMUNICATING
US 20070139188A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0139188 A1 Ollis et al. (43) Pub. Date: Jun. 21, 2007 (54) (75) (73) (21) (22) METHOD AND APPARATUS FOR COMMUNICATING
Using Email Security to Protect Against Phishing, Spam, and Targeted Attacks: Combining Features for Higher Education
 White Paper Using Email Security to Protect Against Phishing, Spam, and Targeted Attacks: Combining Features for Higher Education Online criminals are constantly looking for new ways to reach their targets
White Paper Using Email Security to Protect Against Phishing, Spam, and Targeted Attacks: Combining Features for Higher Education Online criminals are constantly looking for new ways to reach their targets
Configuring Your Gateman Email Server
 Configuring Your Gateman Email Server Your Gateman Lifestyle Server includes an Email Server that provides users access to email via an email client and via your web browser using your laptop and mobile
Configuring Your Gateman Email Server Your Gateman Lifestyle Server includes an Email Server that provides users access to email via an email client and via your web browser using your laptop and mobile
johnireland@eircom.net
 Email Electronic mail is the transmission of mainly text based messages across networks. This can be within a particular network - internal mail - or between networks - external mail. The most common network
Email Electronic mail is the transmission of mainly text based messages across networks. This can be within a particular network - internal mail - or between networks - external mail. The most common network
(12) United States Patent Halonen
 (12) United States Patent Halonen US006334053B1 () Patent N0.: (45) Date of Patent: Dec. 25, 2001 (54) PROCEDURE AND SYSTEM FOR PROVIDING AN ANSWERING SERVICE (75) Inventor: Mikko Halonen, Oulu (Fl) (73)
(12) United States Patent Halonen US006334053B1 () Patent N0.: (45) Date of Patent: Dec. 25, 2001 (54) PROCEDURE AND SYSTEM FOR PROVIDING AN ANSWERING SERVICE (75) Inventor: Mikko Halonen, Oulu (Fl) (73)
Manual Spamfilter Version: 1.1 Date: 20-02-2014
 Manual Spamfilter Version: 1.1 Date: 20-02-2014 Table of contents Introduction... 2 Quick guide... 3 Quarantine reports...3 What to do if a message is blocked inadvertently...4 What to do if a spam has
Manual Spamfilter Version: 1.1 Date: 20-02-2014 Table of contents Introduction... 2 Quick guide... 3 Quarantine reports...3 What to do if a message is blocked inadvertently...4 What to do if a spam has
Cunneciiun to credit cards dltabase. The system analyzes all credit cards aeecums.
 US 20050137949A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0137949 A1 Rittman et al. (43) Pub. Date: Jun. 23, 2005 (54) AUTOMATIC, CHARACTERIZED AND PRIORITIZED TRANSACTIONS
US 20050137949A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0137949 A1 Rittman et al. (43) Pub. Date: Jun. 23, 2005 (54) AUTOMATIC, CHARACTERIZED AND PRIORITIZED TRANSACTIONS
Managing Spam With Outlook Express
 Managing Spam with Outlook Express Managing Spam With Outlook Express 4Introduction 4Verizon Online Spam Detector 4Using Outlook Express Tools to Reduce Spam 1 Verizon Online 2 Managing Spam with Outlook
Managing Spam with Outlook Express Managing Spam With Outlook Express 4Introduction 4Verizon Online Spam Detector 4Using Outlook Express Tools to Reduce Spam 1 Verizon Online 2 Managing Spam with Outlook
