Spam-Blocking Server m
|
|
|
- Myron Hines
- 8 years ago
- Views:
Transcription
1 US A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/ A1 Oliver et al. (43) Pub. Date: May 24, 2012 (54) SIGNATURE GENERATION USING MESSAGE Publication Classi?cation SUMMARIES (51) Int- Cl (76) Inventors: Jonathan J. Oliver, San Carlos, CA G06F 15/16 (200601) (US); David A. Koblas, Los Altos, CA (Us); Brian K_ Wilson, pale (52) US. Cl /206 Alto, CA (U S) (21) App1.No.: 13/360,971 (57) ABSTRACT (22) Filed Jan Systems and methods for processing a message are provided..., A message may be processed to generate a message summary Related US. Application Data by removing or replacing certain Words, phrases, sentences, punctuation, and the like. Message signatures based upon the (63) Continuation of application No. 11/903,413,?led on message summary may be generated and stored in a signature Sep. 20, 2007, now Pat. No. 8,112,486, Which is a database, Which may be used to identify and/or classify spam continuation of application No. 10/371,977,?led on messages. Subsequently received messages may be classi?ed Feb. 20, 2003, now Pat. No. 7,299,261. by signature and processed based on classi?cation. Spam-Blocking Server m Mail Device 199 Summarization & Signature Generation Engine w Mail Device 199 Summarization & Signature Generation Engine 119
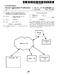
2 Patent Application Publication May 24, 2012 Sheet 1 of4 US 2012/ A1 Spam-Blocking Server M Database 1114 Mail Device 1.02 Summarization & Signature Generation Engine M Mail Device _1_O_6. Summarization & Signature Generation Engine 112 FIG. 1
3 Patent Application Publication May 24, 2012 Sheet 2 0f 4 US 2012/ A1 Receive a message / Z00 Summarize message /' Z0 7. 4/ Generate signature set / 20+ <\/S ignature in db? Mb / 7 ' 2 0 $ /// \ 1/ / i7 Process normal message. 14 I Take actien / 2W Fig. 2
4 Patent Application Publication May 24, 2012 Sheet 3 0f 4 US 2012/ A1 Receive a message Seiect message r592, Indicate junk status / 30% Summarize vmessage / 9mg vgenerate signature #3055 Submit to database 3 Update configuration wgiz Perform Action m Fig. 3
5 Patent Application Publication May 24, 2012 Sheet 4 0f 4 US 2012/ A1 Spell. check flf'oo ' L Remove extraneous words 24 0 Z i Repiace remaining words with canonical / [k0 q, version L Sort-words i Make words unique / Q / A498 D i Evaluate importance /4H 0 i Take important words / 4' 2" l. Generate signature / H Li Fig. 4
6 US 2012/ A1 May 24, 2012 SIGNATURE GENERATION USING MESSAGE SUMMARIES CROSS REFERENCE TO RELATED APPLICATIONS [0001] This application is a continuation and claims the priority bene?t of US. patent application Ser. No. 11/903,413 entitled Signature Generation Using Message Summaries and?led Sep. 20, 2007 Which is a continuation and claims the priority bene?t of US. patent application Ser. No. 10/371,977 entitled Message Classi?cation Using a Summary and?led Feb. 20, This application is related to US. patent appli cation Ser. No. 10/371,987 entitled Using Distinguishing Properties To Classify Messages and?led Feb. 20, The disclosures of the aforementioned applications are incorpo rated herein by reference. BACKGROUND OF THE INVENTION [0002] 1. Field of the Invention [0003] The present invention relates generally to message classi?cation. More speci?cally, a system and method for classifying messages to block junk messages (spam) are disclosed. [0004] 2. Description of RelatedArt [0005] People have become increasingly dependent on for their daily communication. is popular because it is fast, easy, and has little incremental cost. Unfor tunately, these advantages of are also exploited by marketers Who regularly send out large amounts of unsolic ited junk (also referred to as spam ). Spam messages are a nuisance for users. They clog people s box, Waste system resources, often promote distasteful subjects, and sometimes sponsor outright scams. [0006] There have been efforts to block spam using spam blocking software in a collaborative environment Where users contribute to a common spam knowledge base. For privacy and e?iciency reasons, the spam-blocking software generally identi?es spam messages by using a signature generated based on the content of the message. A relatively straightfor Ward scheme to generate a signature is to?rst remove leading and trailing blank lines then compute a checksum on the remaining message body. HoWever, spam senders (also referred to as spammers ) have been able to get around this scheme by embedding variations4often as random stringsi in the messages so that the messages sent are not identical and generate different signatures. [0007] Another spam-blocking mechanism is to remove Words that are not found in the dictionary as Well as leading and trailing blank lines, and then compute the checksum on the remaining message body. HoWever, spammers have been able to circumvent this scheme by adding random dictionary Words in the text. These super?uous Words are sometimes added as White text on a White background, so that they are invisible to the readers but nevertheless confusing to the spam-blocking software. [0008] The existing spam-blocking mechanisms have their limitations. Once the spammers learn how the signatures for the messages are generated, they can alter their message generation software to overcome the blocking mechanism. It Would be desirable to have a Way to identify messages that cannot be easily overcome even if the identi?cation scheme is known. It Would also be useful if any antidote to the identi? cation scheme Were expensive to implement or Would incur signi?cant runtime costs. SUMMARY [0009] Systems and methods of the present invention pro vide for processing messages. A message may be processed to generate a message summary by removing or replacing certain Words, phrases, sentences, punctuation, and the like. For example, redundant Words may be removed. Message signatures based upon the message summary may be generated and stored in a signature database, Which may be used to identify and/ or classify spam messages. Subsequently received messages may be classi?ed using signatures based on message summaries and processed based on classi?cation. [0010] Methods of the present invention may include removing non-useful Words from the message or replacing the remaining Words With canonical equivalent Words. The resulting summary may then be transferred to a signature generation engine. The signature generation engine may gen erate one or more signatures based on the resulting summary. The signatures may be used to classify subsequently received messages, Which may then be processed based on their clas si?cation. Some embodiments of the present invention fur ther include storing the signatures in a signature database. [0011] Systems of the present invention may include a sig nature database, a server, and a mail device comprising a summarization and signature generation module. The sum marization and signature generation module generates mes sage summaries from a message and generates one or more message signatures based on the resulting summary. The message signatures may be stored in the signature database and used by the server to identify and classify subsequently received messages. The server is further con?gured to process the subsequently received messaged based on the classi?ca tion. [0012] An embodiment of the present invention may include computer storage media that include instructions for processing messages to generate message summaries and message signatures based on the message summary. Further embodiments may include instructions for storing the mes sage summaries in a signature database. BRIEF DESCRIPTION OF THE DRAWINGS [0013] The present invention Will be readily understood by the following detailed description in conjunction With the accompanying drawings, Wherein like reference numerals designate like structural elements, and in Which: [0014] FIG. 1 is a block diagram illustrating a spam mes sage classi?cation network according to one embodiment of the present invention. [0015] FIG. 2 is a?owchart illustrating how a message is classi?ed, according to one embodiment of the present inven tion. [0016] FIG. 3 is a?owchart illustrating how a user classi?es a message as spam, according to one embodiment of the present invention. [0017] FIG. 4 is a?owchart illustrating the summarization process according to one embodiment of the present inven tion. DETAILED DESCRIPTION [0018] It should be appreciated that the present invention can be implemented in numerous Ways, including as a pro
7 US 2012/ A1 May 24, 2012 cess, an apparatus, a system, or a computer readable medium such as a computer readable storage medium or a computer network Wherein program Instructions are sent over optical or electronic communication links. It should be noted that the order of the steps of disclosed processes may be altered Within the scope of the invention. [0019] A detailed description of one or more preferred embodiments of the invention is provided below along With accompanying?gures that illustrate by Way of example the principles of the invention. While the invention is described in connection With such embodiments, it should be understood that the invention is not limited to any embodiment. On the contrary, the scope of the invention is limited only by the appended claims and the invention encompasses numerous alternatives, modi?cations and equivalents. For the purpose of example, numerous speci?c details are set forth in the following description in order to provide a thorough under standing of the present invention. The present invention may be practiced according to the claims Without some or all of these speci?c details. For the purpose of clarity, technical material that is known in the technical?elds related to the invention has not been described in detail so that the present invention is not unnecessarily obscured. [0020] An improved system and method for classifying mail messages are disclosed. In one embodiment, the mes sage is processed to construct a summary that transforms information in the message into a condensed canonical form. A set of signatures is generated based on the summary. In some embodiments, the distinguishing properties in the mes sage are extracted also and used in combination With the summary to produce signatures. The signatures for junk mes sages are stored in a database and used to classify these messages. [0021] FIG. 1 is a block diagram illustrating a spam mes sage classi?cation network according to one embodiment of the present invention. The system allows users in the network to collaborate and build up a knowledge base of known spam messages, and uses this knowledge to block spam messages. A spam message is?rst sent to a mail device 100. The mail device may be a mail server, a personal computer running a mail client, or any other appropriate device used to receive messages. A user reads the message and determines Whether it is spam. [0022] If the message is determined to be spam, a summa rization and signature generation engine 108 on the mail device summarizes the message and generates one or more signatures (also referred to as thumbprints) based on the summarized message. The summarization and signature gen eration engine may be a separate program or part of the mail-processing program on the mail device. The signature is sent to a spam-blocking server 102, Which stores the signature in a database 104. Different types of databases are used in various embodiments, including commercial database prod ucts such as Oracle databases,?les, or any other appropriate storage that allow data to be stored and retrieved. In some embodiments, the database also keeps track of the number of times a signature has been identi?ed as spam by other users of the system. The database may be located on the spam-block ing server device, on a network accessible by server 102, or on a network accessible by the mail devices. In some embodi ments, the database is cached on the mail devices and updated periodically. [0023] When a mail device 106 receives a message, the mail device s summarization and signature generation engine 110 summarizes the message, generates one or more signa tures for the message, and sends the signatures along With any other query information to the spam-blocking server. The spam-blocking server looks up the signatures in the database, and replies With information regarding the signatures. The information in the reply helps mail device 106 determine Whether the message is spam. [0024] Mail device 106 may be con?gured to use informa tion from the spam-blocking server to determine Whether the message is spam in different Ways. For example, the number of times the message Was classi?ed by other users as spam may be used. If the number of?ags exceeds some preset threshold, the mail device processes the message as spam. The number and types of matching signatures and the effect of one or more matches may also be con?gured. For example, the message may be considered spam if some of the signa tures in the signature set are found in the database or the message may be determined to be spam only if all the signa tures are found in the database. [0025] In some embodiments, spam-blocking server 102 acts as a gateway for messages. The server includes a sum marization and signature generation engine similar to the engine included in a mail device. Incoming messages are received by the server, Which performs summarization and signature generation on the message. The server looks up the signature in the database, and processes the message accord ing to the result of the lookup. [0026] Since spam-blocking software can easily detect identical spam messages, spammers often send out many variations on the same message to avoid detection. They may switch the location of sentences and paragraphs, insert ran dom Words, or use different Words and phrases. The key information conveyed in these variations of messages, how ever, stays about the same. The summarization and signature generation engine distills the information in the messages and produces a summary. [0027] During the summarization process, Words that are not useful are discarded. Examples of non-useful Words include commonly occurring Words such as a, an, the, to and other selected Words that are not considered helpful for the purpose of distinguishing the message (also referred to as stop Words), and sentences or passages that spammers insert on purpose. [0028] The remaining Words and phrases are replaced With their canonical equivalents. The canonical equivalent of a Word or a phrase is an identi?er used to represent all syn onyms of the Word or phrase, Which may be a Word, a phrase, a value, a letter or any other appropriate representation. Redundant information is then removed, and Words are optionally ranked and selected based on their importance. There are many different Ways of evaluating the importance of Words, such as ranking Words based on their probability of occurrence in spam messages, probability of occurrence in natural language, or combinations thereof. [0029] The resulting summary is a condensed, canonical form of a message. Thus, different messages that have the same or equivalent information have the same summary, and can be more easily identi?ed using such a summary. Using a summary to identify and classify messages makes it harder for spammers to alter their message generation scheme to evade detection. It is rather unlikely that messages other than those sent by the same spammer Would have the same sum mary. Therefore, the risk of false classi?cation is reduced.
8 US 2012/ A1 May 24, 2012 [0030] FIG. 2 is a?owchart illustrating how a message is classi?ed, according to one embodiment of the present inven tion. First, a message is received (200). The message is pro cessed to produce a summary (202). One or more signatures are generated based on the summary (204), and then looked up in a database (206). If the signatures are not found in the database, then no user has classi?ed the message as spam and the system can proceed to process the message as a normal message, delivering the message or displaying it when appro priate (208). If, however, the signatures are found in the database, then the same message or a message similar to it has been classi?ed as spam. Some appropriate action is taken accordingly (210). In an embodiment where the process takes place on a mail client, the action includes classifying the message as spam and moving it to an appropriate junk folder. In an embodiment where the process takes place on a mail server, the action includes quarantining the message so it is recoverable by the administrator or the user. [0031] Sometimes, a spam message is delivered to the user s inbox because the signature of the message summary is not found in the database. This may happen the?rst time a particular spam message is sent, when the message is yet to be classi?ed as spam by a suf?cient number of users on the network, or when not enough variants of the message have been identi?ed. The user who receives the message can then make a contribution to the database by indicating the message as spam. In one embodiment, the mail client software includes a junk button in its user interface. The user can click on this button to indicate that a message is junk. Without further action from the user, the software automatically extracts information from the message, submits the informa tion to the server, and deletes the message from the user s inbox. In some embodiments, the mail client software also updates the user s con?gurations accordingly. For instance, the software may add the sender s address to a blacklist. The blacklist is a list of addresses used for blocking messages. Once an address is included in the blacklist, future messages from that address are automatically blocked. [0032] FIG. 3 is a?owchart illustrating how a user classi?es a message as spam according to one embodiment of the present invention. A spam message is received by the user (300). The user selects the message (3 02), and indicates that the message is junk by clicking on a junk button or some other appropriate means (304). The summarization and signature generation engine summarizes the message (306), and gen erates a set of signatures based on the summary (308). The signatures, which are used to identify the message, are sub mitted to the database (310). Thus, matching signatures can be found in the database for messages that have the same summary. In some embodiments, the con?guration of the user s mail client software is updated based on the classi?ca tion (312). For example, the sender s address is added to a blacklist for blocking future messages from the same sender. An action is performed on the message accordingly (314). A variety of actions may be performed, including deleting the message from the user s inbox, rejecting or bouncing the message, quarantining the message, etc. [0033] FIG. 4 is a?owchart illustrating the summarization process according to one embodiment of the present inven tion. A spell check is performed on the message (400). Incor rectly spelled words are corrected; the ones that are not cor rectable are discarded. In some embodiments, exceptions are made for items that may not be found in the dictionary for legitimate reasons, such as URLs and addresses. [0034] After the spell check, extraneous information such as stop words that are not useful for distinguishing the mes sage are removed from the message (402). The summariza tion and signature generation engine uses a collection of stop words to?nd words that should be removed from the mes sage. Sometimes, spammers include random sentences and passages such as Shakespearean sonnets in spam messages in attempts to evade detection. Thus, in some embodiments, the engine also includes sentences and passages that are known to be often included by spammers, and uses these well-known sentences and pas sages to remove extraneous words. Remov ing extraneous words from the message helps simplify the sentence structure and reduces the number of words to be further processed. In some embodiments, punctuations, tabs, or blank lines are also removed. Steps 400 and 402 are pre processing steps that put the message into a better form for further processing. Upon the completion of steps 400 and 402, the message has been reduced to a list of corrected words that excludes certain words not useful for distinguishing the message. [0035] The remaining words are looked up in a thesaurus or any other collection that organizes words into groups accord ing to their meanings. Each group includes similar words and phrases, and has a word or phrase that is the canonical equiva lent of all the words and phrases in the group. The term canonical equivalent means the word or phrase that is selected to represent the group of words where the word or phrase has been found. In some embodiments, the canonical equivalent is not itself a word or phrase but is simply an identi?er such as a number or letter that identi?es the list where the word or phrase from the message is found. The remaining words in the message are then replaced with their canonical equivalents (404). It should be noted that in differ ent embodiments only words may be looked up or some words may be combined into phrases for lookup. The remain der of this description refers to words only for the purpose of clarity. It should be noted that the same principles apply to phrases and that principles apply whether a canonical word is selected in (404) or an identi?er of the word group is selected. [0036] Sometimes, a word has multiple meanings. The canonical equivalent of the word is selected from multiple groups of words using a prede?ned process. In some embodi ments, the canonical equivalent that is most likely to occur in spam messages is selected. For example, the word?ies has two canonical equivalents according to a thesaurus, air travel and insect. Since there are many spam messages related to air travel and relatively fewer related to insects,?y is more likely to be what is intended by the spammer and is therefore chosen over insect. In some embodiments, all the canonical equivalents are added to the list. Using the previous example, both?y and insect are added to the list. In some embodiments, the meaning that occurs in the language most frequently is chosen. [0037] The canonical equivalent words (or identi?ers) are then sorted (406). There are sometimes multiple instances of the same word. Duplicates are removed to make the words unique (408). The importance of the words is evaluated (410), and some of the more important words are chosen (412). It should be noted that steps are optional, and some or all of them may be omitted in different embodiments. There are many different ways to evaluate the importance of words. In some embodiments, the importance of words is determined by their probability of occurrence in spam messages. Con cepts that typically appear in spam messages are ranked
9 US 2012/ A1 May 24, 2012 higher. For example, credit,?nance, sex are popular spam ideas and thus receive high ranking. In some embodi ments, Words are ranked based on their probability of occur rence in the language. In some embodiments, a combination of techniques is used. The importance ranking of the Words is kept separately in some embodiments, and used to rearrange the list of Words in some embodiments. This process produces a summary that includes the resulting Words. [0038] The summarization and signature generation engine takes the summary to generate a set of signatures (414). There are many Ways to generate the signatures using the summary. In some embodiments, a transform function (such as a secure hash function or a checksum) is applied to the bytes in the summary to produce a single signature. In some embodi ments, the transform function is applied to Words in the sum mary to produce a set of signatures including a plurality of signatures. In some embodiments, no transformation is applied to the summary and the signature is set to be the summary. [0039] Sometimes the summary must meet a certain mini mum byte requirement to generate the signatures. In some embodiments, the entire summary or the Words in the sum mary are discarded if they have fewer than a prede?ned num ber of bytes. Thus, the probability of signature collision is lowered. [0040] For the purposes of example, a spam message is examined and summarized using the process described in FIG. 4. The original message is as follows: [0041] Dear Bob, [0042] I am a Nigerian WidoeW. I have 26 million dollars in a bank in Nigeria that I need to tran:sfer to an US. bank account. Please send me your bank account num ber so I can transfer the monney, and you may keep 1 million dollars for yourself. [0043] First, the spell check corrects WidoeW to WidoW, and monney to money. [0044] After removing the non-essential Words, the Words that are left are: Bob, Nigerian, WidoW, 26, million, dollars, bank, Nigeria, need, transfer, U.S., bank, account, send, bank, account, number, transfer, money, keep, 1, million, dollars. [0045] After replacing those Words With their canonical equivalents, the new Words are: name, third-world country, WidoW, number, large number, money, bank,?rst-world country, need,?nancial transaction, third-world country, bank, account, send; bank, account, number,?nancial trans action, money, keep, number, large number, money. [0046] The Words are sorted, and the new Word list is as follows: account, account, bank, bank, bank,?nancial trans action,?nancial transaction,?rst-world country, keep, large number, large number, money, money, money, name, need, number, number, number, send, third-world country, third World country, WidoW. [0047] The Words are then made unique to form the follow ing list: account, bank,?nancial transaction,?rst-world coun try, keep, large number, money, name, need, number, send, third-world country, WidoW. [0048] The importance of the Words is then evaluated, and the more important Words receive greater values. The result ing list shows the ranking values in parentheses: account (1 5), bank (12),?nancial transaction (1 6),?rst-World country (1 0), keep (8), large number (13), money (20), name (4), need (9), number (12), send (1 l), third-world country (12), WidoW (15). The important Words are then chosen. In some embodi ments, a prede?ned number of Words With the highest ranking may be chosen. In some embodiments, a variable number of Words that meet a certain importance ranking may be chosen. In this embodiment, the ten Words that have the highest importance ranking are chosen; they are: account, bank,?nancial transaction,?rst-world country, large number, money, number, send, third-world country, WidoW. Generally, messages that are variations on the same theme of a WidoW conducting?nancial transaction on bank account between?rst-world country and third-world country should have simi lar canonical form. These Words are then used to generate one or more signatures. As noted above, instead of Words, the list may comprise a set of identi?ers in, for example, numerical order, that represent the categories of Words or phrases occur ring most often in the message. Also, in some embodiments, other criteria are used to select the list including probability of occurrence in a message of a category of Words. [0049] Some embodiments of the system employ other summarization techniques, such as the topic speci?c summa rization technique described in MSc in Speech and Language Processing Dissertation: Automatic summarizing based on sentence extraction: A statistical approach by Byron Geor gantopoulos and the neural net based technique described in Sumatra: A system forautomatic Summary Generation by D. H. Lie. In some embodiments, the summarization and signa ture generation engine provides interfaces to utilize a sum marization module. The summarization module, Which may be provided by a third-party, produces summaries for text inputs. [0050] The summarization technique is sometimes com bined With the distinguishing properties identi?cation tech nique described in US. patent application Ser. No. 10/371, 987?led Feb. 20, 2003 and entitled Using Distinguishing Properties to Classify Messages, the disclosure of Which has been previously incorporated by reference. In one embodi ment, the summarization technique is applied to produce one or more signatures, and distinguishing properties such as contact information embedded in the message are identi?ed to produce additional signatures. [0051] The generated signatures are transferred and stored in the database. In one embodiment, the signatures are for matted and transferred using extensible markup In some embodiments, the signatures are correlated and the relationships among them are also recorded in the database. For example, if signatures from different messages share a certain signature combination, other messages that include the same signature combination may be classi?ed as spam automatically. In some embodiments, the number of times each signature has been sent to the database is updated. [0052] Using signatures to identify a message gives the system greater?exibility and allows it to be more expandable. For example, the mail client software may only identify one type of distinguishing property in its?rst version. In later versions, new types of distinguishing properties are added. The system can be upgraded Without requiring changes in the spam-blocking server and the database. [0053] An improved system and method for classifying a message have been disclosed. The message is processed to generate a summary that is a condensed, canonical form of the message. One or more signatures are generated based on the summary. Signatures of spam messages are stored in a data base to effectively block spam messages. [0054] Although the foregoing invention has been described in some detail for purposes of clarity of understand ing, it Will be apparent that certain changes and modi?cations
10 US 2012/ A1 May 24, 2012 may be practiced Within the scope of the appended claims. It should be noted that there are many alternative Ways of imple menting both the process and apparatus of the present inven tion. Accordingly, the present embodiments are to be consid ered as illustrative and not restrictive, and the invention is not to be limited to the details given herein, but may be modi?ed Within the scope and equivalents of the appended claims. What is claimed is: 1. A method for processing an electronic-mail message, comprising: receiving a message sent over a communication network, the message including a message body and received at an inbox of a mail device; receiving an indication from a user that the message is a junk message; and executing instructions stored in memory, Wherein execu tion of the instructions by a processor: summarizes the message body to produce a summary, Wherein summarizing the message body includes removing at least one Word that is not useful in clas sifying the message, and replacing a Word in the body of the message With an identi?er that represents all synonyms of the Word, generates a signature based on the summary, compares the generated signature to a database of sig natures corresponding to signatures of previously received messages, and processes the message based on at least the generated signature. 2. The method of claim 1, Wherein processing the message includes deleting the message from the inbox. 3. The method of claim 1, Wherein processing the message includes quarantining the message in a junk folder stored at the mail device. 4. The method of claim 1, Wherein processing the message includes rejecting the message from the inbox. 5. The method of claim 1, Wherein the execution of instruc tions by the processor further stores the generated signature in memory for use in classifying a subsequently received mes sage. 6. The method of claim 1, Wherein the signature is gener ated using a transform function. 7. The method of claim 1, Wherein the removed Word includes a Word that appears in a message previously classi?ed as a spam message. 8. The method of claim 1, Wherein summarizing the mes sage body further includes removing redundant information. 9. The method of claim 1, Wherein the signature is gener ated after the summary meets a minimum byte requirement. 10. The method of claim 1, Wherein the execution of instructions by the processor further ranks a Word in the summary of the message body after the summary is gener ated, Wherein the ranking is based on at least a probability the Word occurs in a message. 11. The method of claim 1, Wherein summarizing the mes saging body further includes correcting any incorrectly spelled Word in the mes sage body prior to removing the one or more non-useful Words. 12. A system for processing an electronic-mail message, comprising: memory for storing information regarding a message pre viously classi?ed as a junk mes sage, the message includ ing a message body; a message gateway including a summarization and signa ture generation engine stored in memory, the summari zation and signature engine executable by a processor to: summarize the message body of a message received over a communications network to produce a summary, Wherein summarizing the message body includes removing at least one Word that is not useful in clas sifying the message, and replacing a Word in the body of the message With an identi?er that represents all synonyms of the Word, generate a signature based on the summary, compare the generated signature to a database of signa tures corresponding to signatures of previously received messages, and processes the message based on at least the generated signature. 13. The system of claim 12, Wherein the received message has been classi?ed as a junk message by a user. 14. A non-transitory computer-readable storage medium having embodied thereon a program, the program being executable by a processor to perform a method for processing an electronic-mail message, the method comprising: receiving a message, the message including a message body, receiving an indication from a user that the message is a junk message; summarizes the message body to produce a summary, Wherein summarizing the message body includes removing at least one Word that is not useful in classi fying the message, and replacing a Word in the body of the message With an identi?er that represents all syn onyms of the Word; generating a signature based on the summary; comparing the generated signature to a database of signa tures corresponding to signatures of previously received messages; and processing the message based on at least the generated signature.
US 201203 03424Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303424 A1 Lundstrom (43) Pub. Date: NOV.
 US 201203 03424Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303424 A1 Lundstrom (43) Pub. Date: NOV. 29, 2012 (54) METHOD AND SOFTWARE FOR Publication Classi?cation
US 201203 03424Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303424 A1 Lundstrom (43) Pub. Date: NOV. 29, 2012 (54) METHOD AND SOFTWARE FOR Publication Classi?cation
Lookup CNAM / other database for calllng
 (19) United States US 20140003589Al (12) Patent Application Publication (10) Pub. No.: US 2014/0003589 A1 Martino et al. (43) Pub. Date: Jan. 2, 2014 (54) (71) (72) (73) (21) (22) (63) PROVIDING AUDIO
(19) United States US 20140003589Al (12) Patent Application Publication (10) Pub. No.: US 2014/0003589 A1 Martino et al. (43) Pub. Date: Jan. 2, 2014 (54) (71) (72) (73) (21) (22) (63) PROVIDING AUDIO
US 20130325834A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0325834 A1 Simburg (43) Pub. Date: Dec.
 US 20130325834A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0325834 A1 Simburg (43) Pub. Date: Dec. 5, 2013 (54) LINK ALLOCATION FOR SEARCH ENGINE (52) US. Cl. OPTIMIZATION
US 20130325834A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0325834 A1 Simburg (43) Pub. Date: Dec. 5, 2013 (54) LINK ALLOCATION FOR SEARCH ENGINE (52) US. Cl. OPTIMIZATION
US 20140046812A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046812 A1 FAN et al. (43) Pub. Date: Feb.
 US 20140046812A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046812 A1 FAN et al. (43) Pub. Date: (54) EXPENSE REPORTS FOR PAYMENTS MADE (52) US. Cl. WITH A MOBILE DEVICE
US 20140046812A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046812 A1 FAN et al. (43) Pub. Date: (54) EXPENSE REPORTS FOR PAYMENTS MADE (52) US. Cl. WITH A MOBILE DEVICE
US 20090157756Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0157756 A1 Sanvido (43) Pub. Date: Jun.
 US 20090157756Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0157756 A1 Sanvido (43) Pub. Date: Jun. 18, 2009 (54) FILE SYSTEM FOR STORING FILES IN Publication Classi?cation
US 20090157756Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0157756 A1 Sanvido (43) Pub. Date: Jun. 18, 2009 (54) FILE SYSTEM FOR STORING FILES IN Publication Classi?cation
US 20120215907A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0215907 A1 Chung (43) Pub. Date: Aug.
 US 20120215907A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0215907 A1 Chung (43) Pub. Date: (54) SYSTEMS AND METHODS FOR (52) US. Cl...... 709/224 SELF-ADJUSTING LOGGING
US 20120215907A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0215907 A1 Chung (43) Pub. Date: (54) SYSTEMS AND METHODS FOR (52) US. Cl...... 709/224 SELF-ADJUSTING LOGGING
(71) Applicant: SPEAKWRITE, LLC,Austin, TX (US)
 US 20130304465Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0304465 A1 Henry et al. (43) Pub. Date: NOV. 14, 2013 (54) METHOD AND SYSTEM FOR AUDIO-VIDEO (52) US. Cl.
US 20130304465Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0304465 A1 Henry et al. (43) Pub. Date: NOV. 14, 2013 (54) METHOD AND SYSTEM FOR AUDIO-VIDEO (52) US. Cl.
Hay (43) Pub. Date: Oct. 17, 2002
 US 20020152322A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0152322 A1 Hay (43) Pub. Date: Oct. 17, 2002 (54) (76) (21) (22) (51) (52) METHOD AND APPARATUS FOR FACILITATING
US 20020152322A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0152322 A1 Hay (43) Pub. Date: Oct. 17, 2002 (54) (76) (21) (22) (51) (52) METHOD AND APPARATUS FOR FACILITATING
Back up information data by blocks, and generate backup data of each block
 US 20140046903A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046903 A1 Ylll (43) Pub. Date: (54) DATA BACKUP AND RECOVERY METHOD Publication Classi?cation FOR MOBILE
US 20140046903A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046903 A1 Ylll (43) Pub. Date: (54) DATA BACKUP AND RECOVERY METHOD Publication Classi?cation FOR MOBILE
NJ (US) (51) Int. Cl. H04L 9/00 (2006.01) Correspondence Address: (52) US. Cl... 380/278; 713/ 150 ALFRED C. ROTH (57) ABSTRACT
 . I. I. I US 20080187140A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0187140 A1 McGillian et al. (43) Pub. Date: Aug. 7, 2008 (54) METHOD AND SYSTEM OF SECURELY Related
. I. I. I US 20080187140A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0187140 A1 McGillian et al. (43) Pub. Date: Aug. 7, 2008 (54) METHOD AND SYSTEM OF SECURELY Related
software, and perform automatic dialing according to the /*~102
 US 20140105199A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0105199 A1 Tian (43) Pub. Date: (54) METHOD AND APPARATUS FOR AUTOMATIC DIALING ACCESS POINTS (71) Applicant:
US 20140105199A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0105199 A1 Tian (43) Pub. Date: (54) METHOD AND APPARATUS FOR AUTOMATIC DIALING ACCESS POINTS (71) Applicant:
(12) Patent Application Publication (10) Pub. No.: US 2003/0035525 A1 Wu et al. (43) Pub. Date: Feb. 20, 2003
 (19) United States US 20030035525A1 (12) Patent Application Publication (10) Pub. No.: US 2003/0035525 A1 Wu et al. (43) Pub. Date: (54) (76) (21) (22) SYSTEM AND METHOD FOR DISTINGUISHING TELEPHONE NUMBER
(19) United States US 20030035525A1 (12) Patent Application Publication (10) Pub. No.: US 2003/0035525 A1 Wu et al. (43) Pub. Date: (54) (76) (21) (22) SYSTEM AND METHOD FOR DISTINGUISHING TELEPHONE NUMBER
US 20130073440A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0073440 A1 Chen (57)
 US 20130073440A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0073440 A1 Chen (43) Pub. Date: Mar. 21, 2013 (54) PAYROLL SYSTEM AND METHOD Publication Classi?cation (76)
US 20130073440A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0073440 A1 Chen (43) Pub. Date: Mar. 21, 2013 (54) PAYROLL SYSTEM AND METHOD Publication Classi?cation (76)
wanagamem transformation and management
 US 20120150919Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0150919 A1 Brown et al. (43) Pub. Date: Jun. 14, 2012 (54) (76) (21) (22) (60) (51) AGENCY MANAGEMENT SYSTEM
US 20120150919Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0150919 A1 Brown et al. (43) Pub. Date: Jun. 14, 2012 (54) (76) (21) (22) (60) (51) AGENCY MANAGEMENT SYSTEM
(Us) (73) Assignee: Avaya Technology Corp. Je?' McElroy, Columbia, SC (US); (21) Appl. No.: 10/413,024. (22) Filed: Apr. 14, 2003 (57) ABSTRACT
 US 20040202300A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0202300 A1 Cooper et al. (43) Pub. Date: Oct. 14, 2004 (54) CALL HANDLING USING NON-SPEECH CUES VIA A PERSONAL
US 20040202300A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0202300 A1 Cooper et al. (43) Pub. Date: Oct. 14, 2004 (54) CALL HANDLING USING NON-SPEECH CUES VIA A PERSONAL
US 20050027827A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0027827 A1 Owhadi et al. (43) Pub. Date: Feb.
 US 20050027827A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0027827 A1 Owhadi et al. (43) Pub. Date: Feb. 3, 2005 (54) SYSTEM FOR PROVIDING SUPPORT FOR AN ELECTRONIC
US 20050027827A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0027827 A1 Owhadi et al. (43) Pub. Date: Feb. 3, 2005 (54) SYSTEM FOR PROVIDING SUPPORT FOR AN ELECTRONIC
US 20020116467A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0116467 A1 Boyer et al. (43) Pub. Date: Aug.
 US 20020116467A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0116467 A1 Boyer et al. (43) Pub. Date: Aug. 22, 2002 (54) METHOD AND APPARATUS FOR Publication Classi?cation
US 20020116467A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0116467 A1 Boyer et al. (43) Pub. Date: Aug. 22, 2002 (54) METHOD AND APPARATUS FOR Publication Classi?cation
US 20070016324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016324 A1. Operating System. 106 q f 108.
 US 20070016324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016324 A1 Oddiraj u et al. (43) Pub. Date: Jan. 18, 2007 (54) SYSTEM BOOT OPTMZER (75) nventors: Chandar
US 20070016324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016324 A1 Oddiraj u et al. (43) Pub. Date: Jan. 18, 2007 (54) SYSTEM BOOT OPTMZER (75) nventors: Chandar
Patent Application Publication Sep. 30, 2004 Sheet 1 0f 2. Hierarchical Query. Contact Ow FIG. 1
 US 20040193595A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0193595 A1 Kaminsky et al. (43) Pub. Date: Sep. 30, 2004 (54) NEAREST KNOWN PERSON DIRECTORY FUNCTION (75)
US 20040193595A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0193595 A1 Kaminsky et al. (43) Pub. Date: Sep. 30, 2004 (54) NEAREST KNOWN PERSON DIRECTORY FUNCTION (75)
Access List: my-fw-rule
 US 200701573 02Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0157302 A1 Ottamalika et al. (43) Pub. Date: Jul. 5, 2007 (54) METHODS AND SYSTEMS FOR Publication Classi?cation
US 200701573 02Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0157302 A1 Ottamalika et al. (43) Pub. Date: Jul. 5, 2007 (54) METHODS AND SYSTEMS FOR Publication Classi?cation
US 20020072350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0072350 A1 Fukuzato (43) Pub. Date: Jun.
 US 20020072350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20020072350 A1 Fukuzato (43) Pub. Date: Jun. 13, 2002 (54) BACKUP METHOD OF APPLICATIONS OF PORTABLE CELLULAR PHONE
US 20020072350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20020072350 A1 Fukuzato (43) Pub. Date: Jun. 13, 2002 (54) BACKUP METHOD OF APPLICATIONS OF PORTABLE CELLULAR PHONE
US 20130007621A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0007621 A1 Warren (43) Pub. Date: Jan.
 US 20130007621A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0007621 A1 Warren (43) Pub. Date: Jan. 3, 2013 (54) (76) (21) (22) (51) (52) SYSTEM FOR LEARNING NAMES OF
US 20130007621A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0007621 A1 Warren (43) Pub. Date: Jan. 3, 2013 (54) (76) (21) (22) (51) (52) SYSTEM FOR LEARNING NAMES OF
Telephone Dressing Systems - Advantages and Disadvantages
 I US 20030185352A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0185352 A1 Savage et al. (43) Pub. Date: (54) AUTOMATED MESSAGE BROADCAST SYSTEM WITH DUAL MESSAGE SOURCES
I US 20030185352A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0185352 A1 Savage et al. (43) Pub. Date: (54) AUTOMATED MESSAGE BROADCAST SYSTEM WITH DUAL MESSAGE SOURCES
US 20070139188A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0139188 A1 Ollis et al. HOME PROCESSOR /\ J\ NETWORK
 US 20070139188A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0139188 A1 Ollis et al. (43) Pub. Date: Jun. 21, 2007 (54) (75) (73) (21) (22) METHOD AND APPARATUS FOR COMMUNICATING
US 20070139188A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0139188 A1 Ollis et al. (43) Pub. Date: Jun. 21, 2007 (54) (75) (73) (21) (22) METHOD AND APPARATUS FOR COMMUNICATING
(30) Foreign Application Priority Data
 US 20040015727A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0015727 A1 Lahti et al. (43) Pub. Date: Jan. 22, 2004 (54) SYNCHRONIZATION METHOD (76) Inventors: Jerry Lahti,
US 20040015727A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0015727 A1 Lahti et al. (43) Pub. Date: Jan. 22, 2004 (54) SYNCHRONIZATION METHOD (76) Inventors: Jerry Lahti,
(12) United States Patent Edelen
 US008285799B2 (12) United States Patent Edelen (10) Patent N0.: (45) Date of Patent: Oct. 9, 2012 (54) QUOTA-BASED ARCHIVING (75) Inventor: James Edelen, Renton, WA (U S) (73) Assignee: Microsoft Corporation,
US008285799B2 (12) United States Patent Edelen (10) Patent N0.: (45) Date of Patent: Oct. 9, 2012 (54) QUOTA-BASED ARCHIVING (75) Inventor: James Edelen, Renton, WA (U S) (73) Assignee: Microsoft Corporation,
(12) United States Patent (16) Patent N6.= US 6,611,861 B1 Schairer et al. (45) Date of Patent: Aug. 26, 2003
 US006611861B1 (12) United States Patent (16) Patent N6.= Schairer et al. () Date of Patent: Aug. 26, 2003 (54) INTERNET HOSTING AND ACCESS SYSTEM Primary Examiner AyaZ Sheikh AND METHOD Assistant Examiner
US006611861B1 (12) United States Patent (16) Patent N6.= Schairer et al. () Date of Patent: Aug. 26, 2003 (54) INTERNET HOSTING AND ACCESS SYSTEM Primary Examiner AyaZ Sheikh AND METHOD Assistant Examiner
(43) Pub. Date: Feb. 16, 2012
 US 20120041897A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0041897 A1 Teague et al. (43) Pub. Date: (54) (75) (73) (21) (22) (63) MARKET INDICATOR PROCESS AND METHOD
US 20120041897A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0041897 A1 Teague et al. (43) Pub. Date: (54) (75) (73) (21) (22) (63) MARKET INDICATOR PROCESS AND METHOD
T0 THE USER EE JEQE, THE REWRWTEN CQNTENT includeng A REFERENCE N132
 US 20130091305A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0091305 A1 Freeman et al. (43) Pub. Date: Apr. 11, 2013 (54) IDENTIFYING USERS THROUGH A PROXY (52) US. Cl.
US 20130091305A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0091305 A1 Freeman et al. (43) Pub. Date: Apr. 11, 2013 (54) IDENTIFYING USERS THROUGH A PROXY (52) US. Cl.
\ \ \ connection connection connection interface interface interface
 US 20140122910A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20140122910 A1 Chiu et al. (43) Pub. Date: May 1, 2014 (54) RACK SERVER SYSTEM AND OPERATION Publication Classi?cation
US 20140122910A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20140122910 A1 Chiu et al. (43) Pub. Date: May 1, 2014 (54) RACK SERVER SYSTEM AND OPERATION Publication Classi?cation
205 Controller / 205
 US 20130089195A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0089195 A1 KIMBLE (43) Pub. Date: Apr. 1 1, 2013 (54) NEXT GENERATION AUTO-DIALER (52) US. Cl. CPC..... H04M3/42
US 20130089195A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0089195 A1 KIMBLE (43) Pub. Date: Apr. 1 1, 2013 (54) NEXT GENERATION AUTO-DIALER (52) US. Cl. CPC..... H04M3/42
(12) Patent Application Publication (10) Pub. No.: US 2013/0325512 A1 Kim et al. (43) Pub. Date: Dec. 5, 2013
 (19) United States US 20130325512Al (12) Patent Application Publication (10) Pub. No.: US 2013/0325512 A1 Kim et al. (43) Pub. Date: Dec. 5, 2013 (54) ELECTRONIC MEDICAL RECORD SYSTEM Publication Classi?cation
(19) United States US 20130325512Al (12) Patent Application Publication (10) Pub. No.: US 2013/0325512 A1 Kim et al. (43) Pub. Date: Dec. 5, 2013 (54) ELECTRONIC MEDICAL RECORD SYSTEM Publication Classi?cation
US 20130138449A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0138449 A1 Pi0t (43) Pub. Date: May 30, 2013
 US 20130138449A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0138449 A1 Pi0t (43) Pub. Date: May 30, 2013 (54) SYSTEM AND METHOD FOR SCHEDULING (52) us. c1. HoME VISITS
US 20130138449A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0138449 A1 Pi0t (43) Pub. Date: May 30, 2013 (54) SYSTEM AND METHOD FOR SCHEDULING (52) us. c1. HoME VISITS
US 20090055802A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0055802 A1 CROSBY (43) Pub. Date: Feb.
 US 20090055802A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0055802 A1 CROSBY (43) Pub. Date: (54) SELECTIVE MONITORING OF SOFTWARE Publication Classi?cation APPLICATIONS
US 20090055802A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0055802 A1 CROSBY (43) Pub. Date: (54) SELECTIVE MONITORING OF SOFTWARE Publication Classi?cation APPLICATIONS
60 REDIRECTING THE PRINT PATH MANAGER 1
 US006788429B1 (12) United States Patent (10) Patent No.: US 6,788,429 B1 Clough et al. (45) Date of Patent: Sep. 7, 2004 (54) REMOTE PRINT QUEUE MANAGEMENT FOREIGN PATENT DOCUMENTS (75) Inventors: James
US006788429B1 (12) United States Patent (10) Patent No.: US 6,788,429 B1 Clough et al. (45) Date of Patent: Sep. 7, 2004 (54) REMOTE PRINT QUEUE MANAGEMENT FOREIGN PATENT DOCUMENTS (75) Inventors: James
g 0 No 17 Personalize Message 26 > Fig. 5 '2 i 22 2 Approve Message 12 > Fig. 2
 US 20050256764A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0256764 A1 Beaumont et al. (43) Pub. Date: Nov. 17, 2005 (54) METHOD AND SYSTEM FOR GENERATING (52) US. Cl......
US 20050256764A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0256764 A1 Beaumont et al. (43) Pub. Date: Nov. 17, 2005 (54) METHOD AND SYSTEM FOR GENERATING (52) US. Cl......
(54) LOTTERY METHOD Publication Classi?cation
 US 20130231987A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0231987 A1 Veverka et al. (43) Pub. Date: Sep. 5, 2013 (54) LOTTERY METHOD Publication Classi?cation (71)
US 20130231987A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0231987 A1 Veverka et al. (43) Pub. Date: Sep. 5, 2013 (54) LOTTERY METHOD Publication Classi?cation (71)
(54) RAPID NOTIFICATION SYSTEM (52) US. Cl... 709/206. (57) ABSTRACT (75) Inventors: Anand Rajasekar, San Jose, CA
 US 20120303720A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303720 A1 Rajasekar et a]. (43) Pub. Date: NOV. 29, 2012 (54) RAPID NOTIFICATION SYSTEM (52) US. Cl......
US 20120303720A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303720 A1 Rajasekar et a]. (43) Pub. Date: NOV. 29, 2012 (54) RAPID NOTIFICATION SYSTEM (52) US. Cl......
US 20020174380A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2002/0174380 A1. Mannarsamy (43) Pub. Date: NOV.
 US 20020174380A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2002/0174380 A1 Mannarsamy (43) Pub. Date: NOV. 21, 2002 (54) HELPDESK SYSTEM AND METHOD (52) US. Cl...... 714/25
US 20020174380A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2002/0174380 A1 Mannarsamy (43) Pub. Date: NOV. 21, 2002 (54) HELPDESK SYSTEM AND METHOD (52) US. Cl...... 714/25
US 20070019798Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0019798 A1 Voight et al. SUBSCRIBER DATABASE.
 US 20070019798Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0019798 A1 Voight et al. (43) Pub. Date: Jan. 25, 2007 (54) METHOD AND APPARATUS FOR PROVIDING CUSTOMIZED
US 20070019798Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0019798 A1 Voight et al. (43) Pub. Date: Jan. 25, 2007 (54) METHOD AND APPARATUS FOR PROVIDING CUSTOMIZED
222252 211222 1111;111:131... ~~~~~~~~~~~~~~~~~~~ 2221522 [73] Assigneez Rockwell Semiconductor Systems 5,754,639 5/1998 Flockhart et al...
![222252 211222 1111;111:131... ~~~~~~~~~~~~~~~~~~~ 2221522 [73] Assigneez Rockwell Semiconductor Systems 5,754,639 5/1998 Flockhart et al... 222252 211222 1111;111:131... ~~~~~~~~~~~~~~~~~~~ 2221522 [73] Assigneez Rockwell Semiconductor Systems 5,754,639 5/1998 Flockhart et al...](/thumbs/31/14952948.jpg) I I US0059012A Ulllted States Patent [19] [11] Patent Number: Dez0nn0 [] Date of Patent: * May 4, 1999 [54] APPARATUS AND METHOD FOR 5,526,416 6/1996 DeZonno et al...... 379/266 IDENTIFYING RECORDS ()1?
I I US0059012A Ulllted States Patent [19] [11] Patent Number: Dez0nn0 [] Date of Patent: * May 4, 1999 [54] APPARATUS AND METHOD FOR 5,526,416 6/1996 DeZonno et al...... 379/266 IDENTIFYING RECORDS ()1?
/ \33 40 \ / \\ \ \ M / 32. 28f 1. (19) United States (12) Patent Application Publication Lawser et al. NETWORK \ 36. SERVlCE 'NTERNET SERVICE
 (19) United States (12) Patent Application Publication Lawser et al. US 20130336314A1 (10) Pub. N0.: US 2013/0336314 A1 (43) Pub. Date: Dec. 19, 2013 (54) (71) (72) (73) (21) (22) (63) METHOD FOR COMPLETING
(19) United States (12) Patent Application Publication Lawser et al. US 20130336314A1 (10) Pub. N0.: US 2013/0336314 A1 (43) Pub. Date: Dec. 19, 2013 (54) (71) (72) (73) (21) (22) (63) METHOD FOR COMPLETING
(54) METHODS AND SYSTEMS FOR FINDING Publication Classi?cation CONNECTIONS AMONG SUBSCRIBERS TO AN EMAIL CAMPAIGN (51) Int- Cl
 US 201403 79420A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0379420 A1 Chestnut et al. (43) Pub. Date: Dec. 25, 2014 (54) METHODS AND SYSTEMS FOR FINDING Publication
US 201403 79420A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0379420 A1 Chestnut et al. (43) Pub. Date: Dec. 25, 2014 (54) METHODS AND SYSTEMS FOR FINDING Publication
US 20050015455A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2005/0015455 A1 Liu (43) Pub. Date: Jan.
 US 20050015455A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2005/0015455 A1 Liu (43) Pub. Date: Jan. 20, 2005 (54) SPAM PROCESSING SYSTEM AND METHODS INCLUDING SHARED INFORMATION
US 20050015455A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2005/0015455 A1 Liu (43) Pub. Date: Jan. 20, 2005 (54) SPAM PROCESSING SYSTEM AND METHODS INCLUDING SHARED INFORMATION
US 20020141557A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0141557 A1 STRANDBERG (43) Pub. Date: Oct.
 ---- US 20020141557A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0141557 A1 STRANDBERG (43) Pub. Date: (54) SYSTEM AND METHOD FOR PROVIDING AN AUTOMATIC TELEPHONE CALL
---- US 20020141557A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0141557 A1 STRANDBERG (43) Pub. Date: (54) SYSTEM AND METHOD FOR PROVIDING AN AUTOMATIC TELEPHONE CALL
(IP Connection) Miami (54) (76) (21) (22) (51) (52) Application
 US 20070016777Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016777 A1 Henderson et al. (43) Pub. Date: Jan. 18, 2007 (54) (76) (21) (22) (51) (52) METHOD OF AND SYSTEM
US 20070016777Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016777 A1 Henderson et al. (43) Pub. Date: Jan. 18, 2007 (54) (76) (21) (22) (51) (52) METHOD OF AND SYSTEM
Support systems messaging via email
 > _. US 20110231500A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0231500 A1 Zhu et al. (43) Pub. Date: Sep. 22, 201 1 (54) SYSTEM AND METHOD FOR INTEGRATING Publication
> _. US 20110231500A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0231500 A1 Zhu et al. (43) Pub. Date: Sep. 22, 201 1 (54) SYSTEM AND METHOD FOR INTEGRATING Publication
US 20120066004A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0066004 A1 Lee (43) Pub. Date: Mar.
 US 212664A1 (19) United States (12) Patent Application Publication (1) Pub. o.: US 212/664 A1 Lee (43) Pub. Date: Mar. 15, 212 (54) (76) (21) (22) (6) METHOD AD SYSTEM FOR PERSOAL ISURACE COMPARISO AD
US 212664A1 (19) United States (12) Patent Application Publication (1) Pub. o.: US 212/664 A1 Lee (43) Pub. Date: Mar. 15, 212 (54) (76) (21) (22) (6) METHOD AD SYSTEM FOR PERSOAL ISURACE COMPARISO AD
(12) United States Patent Munshi et al.
 US008806190B1 (12) United States Patent Munshi et al. (10) Patent N0.: () Date of Patent: Aug. 12, 14 (54) METHOD OF TRANSMISSION OF ENCRYPTED DOCUMENTS FROM AN EMAIL APPLICATION (76) Inventors: Amaani
US008806190B1 (12) United States Patent Munshi et al. (10) Patent N0.: () Date of Patent: Aug. 12, 14 (54) METHOD OF TRANSMISSION OF ENCRYPTED DOCUMENTS FROM AN EMAIL APPLICATION (76) Inventors: Amaani
remote backup central communications and storage facility
 US 20040122914A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0122914 A1 Williams (43) Pub. Date: (54) SECURE DATA BACKUP (52) US. Cl...... 709/217; 711/162 COMMUNICATIONS
US 20040122914A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0122914 A1 Williams (43) Pub. Date: (54) SECURE DATA BACKUP (52) US. Cl...... 709/217; 711/162 COMMUNICATIONS
US 201403 80094A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0380094 A1 Kota et al. (43) Pub. Date: Dec.
 US 201403 80094A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0380094 A1 Kota et al. (43) Pub. Date: (54) AVOIDING RESTART ON ERROR IN DATA (52) US. Cl. INTEGRATION CPC.....
US 201403 80094A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0380094 A1 Kota et al. (43) Pub. Date: (54) AVOIDING RESTART ON ERROR IN DATA (52) US. Cl. INTEGRATION CPC.....
US 20130254326Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0254326 A1 Weng et al. (43) Pub. Date: Sep.
 1 l US 20130254326Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0254326 A1 Weng et al. (43) Pub. Date: Sep. 26, 2013 (54) ELECTRONIC DEVICE, CLOUD STORAGE Publication
1 l US 20130254326Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0254326 A1 Weng et al. (43) Pub. Date: Sep. 26, 2013 (54) ELECTRONIC DEVICE, CLOUD STORAGE Publication
(12) United States Patent Buchman et a1.
 USOO8832030B1 (12) United States Patent Buchman et a1. (10) Patent N0.: (45) Date of Patent: Sep. 9, 2014 (54) (75) (73) (21) (22) (51) (52) (58) SHAREPOINT GRANULAR LEVEL RECOVERIES Inventors: Matthew
USOO8832030B1 (12) United States Patent Buchman et a1. (10) Patent N0.: (45) Date of Patent: Sep. 9, 2014 (54) (75) (73) (21) (22) (51) (52) (58) SHAREPOINT GRANULAR LEVEL RECOVERIES Inventors: Matthew
Cunneciiun to credit cards dltabase. The system analyzes all credit cards aeecums.
 US 20050137949A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0137949 A1 Rittman et al. (43) Pub. Date: Jun. 23, 2005 (54) AUTOMATIC, CHARACTERIZED AND PRIORITIZED TRANSACTIONS
US 20050137949A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0137949 A1 Rittman et al. (43) Pub. Date: Jun. 23, 2005 (54) AUTOMATIC, CHARACTERIZED AND PRIORITIZED TRANSACTIONS
Levy Processing System 1_Q
 US 20130332350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0332350 A1 Polk (43) Pub. Date: Dec. 12, 2013 (54) SYSTEMS AND METHODS FOR (52) US. Cl. PROCESSINIG LEIES
US 20130332350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0332350 A1 Polk (43) Pub. Date: Dec. 12, 2013 (54) SYSTEMS AND METHODS FOR (52) US. Cl. PROCESSINIG LEIES
Ulllted States Patent [19] [11] Patent Number: 5,943,406
![Ulllted States Patent [19] [11] Patent Number: 5,943,406 Ulllted States Patent [19] [11] Patent Number: 5,943,406](/thumbs/30/14188909.jpg) US005943406A Ulllted States Patent [19] [11] Patent Number: 5,943,406 Leta et al. [45] Date of Patent: Aug. 24, 1999 [54] TELEPHONE CALL TRACKING AND 4,813,065 3/1989 Segala..... 379/112 BILLING SYSTEM
US005943406A Ulllted States Patent [19] [11] Patent Number: 5,943,406 Leta et al. [45] Date of Patent: Aug. 24, 1999 [54] TELEPHONE CALL TRACKING AND 4,813,065 3/1989 Segala..... 379/112 BILLING SYSTEM
USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362. Hunt et al. [45] Date of Patent: Nov. 21, 1995
![USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362. Hunt et al. [45] Date of Patent: Nov. 21, 1995 USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362. Hunt et al. [45] Date of Patent: Nov. 21, 1995](/thumbs/30/14713887.jpg) llllllllllllllllllllllllllllllllllllllllll l llllllllllllllllllllllll USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362 Hunt et al. [45] Date of Patent: Nov. 21, 1995 [54] DISPATCHING
llllllllllllllllllllllllllllllllllllllllll l llllllllllllllllllllllll USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362 Hunt et al. [45] Date of Patent: Nov. 21, 1995 [54] DISPATCHING
i Load balancer relays request to selected node
 US 20040243709A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0243709 A1 Kalyanavarathan et al. (43) Pub. Date: Dec. 2, 2004 (54) SYSTEM AND METHOD FOR CLUSTER-SENSITIVE
US 20040243709A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0243709 A1 Kalyanavarathan et al. (43) Pub. Date: Dec. 2, 2004 (54) SYSTEM AND METHOD FOR CLUSTER-SENSITIVE
(12) United States Patent (10) Patent N0.: US 7,068,424 B1 Jennings et al. (45) Date of Patent: Jun. 27, 2006
 US007068424B1 (12) United States Patent (10) Patent N0.: US 7,068,424 B1 Jennings et al. (45) Date of Patent: Jun. 27, 2006 (54) MULTIPLE PULSE GENERATION 6,141,127 A * 10/2000 Boivin et a1...... 398/92
US007068424B1 (12) United States Patent (10) Patent N0.: US 7,068,424 B1 Jennings et al. (45) Date of Patent: Jun. 27, 2006 (54) MULTIPLE PULSE GENERATION 6,141,127 A * 10/2000 Boivin et a1...... 398/92
(12) Unlted States Patent (10) Patent N0.2 US 7,428,664 B2 Sirbu (45) Date of Patent: Sep. 23, 2008
 US007428664B2 (12) Unlted States Patent (10) Patent N0.2 Sirbu (45) Date of Patent: Sep. 23, 2008 (54) PROTOCOL REPLAY SYSTEM 5,287,506 A * 2/1994 Whiteside..... 714/39 6,708,292 B1 * 3/2004 Mangasarian..
US007428664B2 (12) Unlted States Patent (10) Patent N0.2 Sirbu (45) Date of Patent: Sep. 23, 2008 (54) PROTOCOL REPLAY SYSTEM 5,287,506 A * 2/1994 Whiteside..... 714/39 6,708,292 B1 * 3/2004 Mangasarian..
/12 [-16. U CIUUU Cl UUCIEI U CICIUU. (12) Patent Application Publication (10) Pub. No.: US 2002/0193094 A1 Lawless et al.
 (19) United States US 20020193094A1 (12) Patent Application Publication (10) Pub. No.: US 2002/0193094 A1 Lawless et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR DOWNLOADNG SOFTWARE PRODUCTS DRECTLY
(19) United States US 20020193094A1 (12) Patent Application Publication (10) Pub. No.: US 2002/0193094 A1 Lawless et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR DOWNLOADNG SOFTWARE PRODUCTS DRECTLY
(12) United States Patent (16) Patent N6.= US 6,198,814 B1 Gill (45) Date of Patent: Mar. 6, 2001
 US006198814B1 (12) United States Patent (16) Patent N6.= Gill (45) Date of Patent: Mar. 6, 2001 (54) SYSTEM AND METHOD FOR ENTERING 5,621,790 * 4/1997 Grossman 6161...... 379/266 CALL OUTCOME RECORDS IN
US006198814B1 (12) United States Patent (16) Patent N6.= Gill (45) Date of Patent: Mar. 6, 2001 (54) SYSTEM AND METHOD FOR ENTERING 5,621,790 * 4/1997 Grossman 6161...... 379/266 CALL OUTCOME RECORDS IN
(12> Ulllted States Patent (10) Patent N0.: US 6,591,288 B1 Edwards et al. (45) Date of Patent: Jul. 8, 2003
 ' ' US006591288B1 (12> Ulllted States Patent (10) Patent N0.: Edwards et al. (45) Date of Patent: Jul. 8, 2003 (54) DATA NETWORK ACCELERATED ACCESS EP 0837584 4/1998..... H04L/29/06 SYSTEM W0 WO 96/34340
' ' US006591288B1 (12> Ulllted States Patent (10) Patent N0.: Edwards et al. (45) Date of Patent: Jul. 8, 2003 (54) DATA NETWORK ACCELERATED ACCESS EP 0837584 4/1998..... H04L/29/06 SYSTEM W0 WO 96/34340
(12) United States Patent Halonen
 (12) United States Patent Halonen US006334053B1 () Patent N0.: (45) Date of Patent: Dec. 25, 2001 (54) PROCEDURE AND SYSTEM FOR PROVIDING AN ANSWERING SERVICE (75) Inventor: Mikko Halonen, Oulu (Fl) (73)
(12) United States Patent Halonen US006334053B1 () Patent N0.: (45) Date of Patent: Dec. 25, 2001 (54) PROCEDURE AND SYSTEM FOR PROVIDING AN ANSWERING SERVICE (75) Inventor: Mikko Halonen, Oulu (Fl) (73)
POTENTIAL. SC DA Il'JA N INTERFACE m. (21) Appl. No.: 11/037,604
 US 20050125439A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0125439 A1 Nourbakhsh et al. (43) Pub. Date: Jun. 9, 2005 (54) METHOD AND APPARATUS FOR MULTI-CONTACT SCHEDULING
US 20050125439A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0125439 A1 Nourbakhsh et al. (43) Pub. Date: Jun. 9, 2005 (54) METHOD AND APPARATUS FOR MULTI-CONTACT SCHEDULING
[11] [45] USER ANSWERS TELEPHONE CALL FOR CLIENT USING WEB-ENABLED TERMINAL 18 WEB-ENABLED TERMINAL 1B LOOKS UP CLIENT
![[11] [45] USER ANSWERS TELEPHONE CALL FOR CLIENT USING WEB-ENABLED TERMINAL 18 WEB-ENABLED TERMINAL 1B LOOKS UP CLIENT [11] [45] USER ANSWERS TELEPHONE CALL FOR CLIENT USING WEB-ENABLED TERMINAL 18 WEB-ENABLED TERMINAL 1B LOOKS UP CLIENT](/thumbs/27/10625613.jpg) United States Patent [19] Waldner et al. [11] [45] US006141413A Patent Number: Date of Patent: Oct. 31, 2000 [54] [75] [73] TELEPHONE NUMBER/WEB PAGE LOOK-UP APPARATUS AND METHOD Inventors: Wayne Waldner,
United States Patent [19] Waldner et al. [11] [45] US006141413A Patent Number: Date of Patent: Oct. 31, 2000 [54] [75] [73] TELEPHONE NUMBER/WEB PAGE LOOK-UP APPARATUS AND METHOD Inventors: Wayne Waldner,
I SEARCH DATABASE l/ VISIT WEBSITE k ( UPDATE RECORDS Y (54) (75) (73) (21) (22) (63) (60) (US); Gary Stephen Shuster, Oakland, SELECT SUB-DOMAIN NAME
 US 20060293973Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0293973 A1 Shuster et al. (43) Pub. Date: Dec. 28, 2006 (54) (75) (73) (21) (22) (63) (60) METHOD AND APPARATUS
US 20060293973Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0293973 A1 Shuster et al. (43) Pub. Date: Dec. 28, 2006 (54) (75) (73) (21) (22) (63) (60) METHOD AND APPARATUS
US 20110043191A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0043191 A1 Gutierrez (43) Pub. Date: Feb.
 US 20110043191A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0043191 A1 Gutierrez (43) Pub. Date: Feb. 24, 2011 (54) PHOENIX PROBE X VOLTAGE TESTER Publication Classi?cation
US 20110043191A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0043191 A1 Gutierrez (43) Pub. Date: Feb. 24, 2011 (54) PHOENIX PROBE X VOLTAGE TESTER Publication Classi?cation
US 20070203917A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0203917 A1 Du et al. (43) Pub. Date: Aug.
 ' i.. 2. Y. US 20070203917A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0203917 A1 Du et al. (43) Pub. Date: (54) COMMUNICATION SYSTEM AND METHOD FOR IMPLEMENTING ONLINE
' i.. 2. Y. US 20070203917A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0203917 A1 Du et al. (43) Pub. Date: (54) COMMUNICATION SYSTEM AND METHOD FOR IMPLEMENTING ONLINE
ADD UPLOADED DATA TO CLOUD DATA REPOSITORY
 US 20120311081A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0311081 A1 Robbin et al. (43) Pub. Date: Dec. 6, 2012 (54) MANAGEMENT OF NETWORK-BASED DIGITAL DATA REPOSITORY
US 20120311081A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0311081 A1 Robbin et al. (43) Pub. Date: Dec. 6, 2012 (54) MANAGEMENT OF NETWORK-BASED DIGITAL DATA REPOSITORY
US 20120222106Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0222106 A1 Kuehl (43) Pub. Date: Aug.
 US 20120222106Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0222106 A1 Kuehl (43) Pub. Date: (54) AUTOMATED HYBRID CONNECTIONS (52) US. Cl...... 726/11 BETWEEN MULTIPLE
US 20120222106Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0222106 A1 Kuehl (43) Pub. Date: (54) AUTOMATED HYBRID CONNECTIONS (52) US. Cl...... 726/11 BETWEEN MULTIPLE
UnitTestplans. plan. Fun ctional Specificatio. System Test plan 5. Performance (54) (75) (73) (21) (22) (86) (30) HLDILLD.
 US 20130067440Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0067440 A1 Tendulkar (43) Pub. Date: Mar. 14, 2013 (54) (75) (73) (21) (22) (86) (30) SYSTEM AND METHOD FOR
US 20130067440Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0067440 A1 Tendulkar (43) Pub. Date: Mar. 14, 2013 (54) (75) (73) (21) (22) (86) (30) SYSTEM AND METHOD FOR
GATEWAY ' 8 8 8 o o o
 US 20130102274A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0102274 A1 Lauwaert (43) Pub. Date: Apr. 25, 2013 (54) SYSTEMS AND METHODS FOR MOBILE Publication Classi?cation
US 20130102274A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0102274 A1 Lauwaert (43) Pub. Date: Apr. 25, 2013 (54) SYSTEMS AND METHODS FOR MOBILE Publication Classi?cation
i VlRTUAL SERVER 1 \ VIRTUAL SERVER 2, _ 7
 US 20110225267A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0225267 A1 OHASHI (43) Pub. Date: Sep. 15, 2011 (54) SERVER SYSTEM FOR VIEWING IN-HOUSE INFORMATION, AND METHOD
US 20110225267A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0225267 A1 OHASHI (43) Pub. Date: Sep. 15, 2011 (54) SERVER SYSTEM FOR VIEWING IN-HOUSE INFORMATION, AND METHOD
. tlllll,1! 1% 11:11 I.,W/ "-111 // out AIHI/ ) I \\ M10. 1 I! (1' 1L- 1!!! I VEHICLE} I] r20 (TRAFFIC COMPUTER 10 RECEIVING UNIT 41 I \ ")SENSOR
![. tlllll,1! 1% 11:11 I.,W/ -111 // out AIHI/ ) I \\ M10. 1 I! (1' 1L- 1!!! I VEHICLE} I] r20 (TRAFFIC COMPUTER 10 RECEIVING UNIT 41 I \ )SENSOR . tlllll,1! 1% 11:11 I.,W/ -111 // out AIHI/ ) I \\ M10. 1 I! (1' 1L- 1!!! I VEHICLE} I] r20 (TRAFFIC COMPUTER 10 RECEIVING UNIT 41 I \ )SENSOR](/thumbs/32/15591097.jpg) United States Patent [19] Albrecht et al. US005812069A [11] Patent Number: [] Date of Patent: Sep. 22, 1998 [54] METHOD AND SYSTEM FOR FORECASTING TRAFFIC FLOWS [75] Inventors: UWe Albrecht, Miinchen;
United States Patent [19] Albrecht et al. US005812069A [11] Patent Number: [] Date of Patent: Sep. 22, 1998 [54] METHOD AND SYSTEM FOR FORECASTING TRAFFIC FLOWS [75] Inventors: UWe Albrecht, Miinchen;
(73) Assignee: Realovation Holdings, LLC d/b/a/ systems methods and Software? for improving Communic?
 US 20130297442A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0297442 A1 Simons et al. (43) Pub. Date: NOV. 7, 2013 (54) SYSTEM AND METHOD FOR ROUTING AND Publication Classi?cation
US 20130297442A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0297442 A1 Simons et al. (43) Pub. Date: NOV. 7, 2013 (54) SYSTEM AND METHOD FOR ROUTING AND Publication Classi?cation
NETWORK BOUNDARY PRIVATE NETWORK PUBLIC _1 NETWORK
 US 20050177647A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0177647 A1 Anantha et al. (43) Pub. Date: (54) (75) (73) (21) (22) (51) MOBILE IP EXTENSION TO SUPPORT PRIVATE
US 20050177647A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0177647 A1 Anantha et al. (43) Pub. Date: (54) (75) (73) (21) (22) (51) MOBILE IP EXTENSION TO SUPPORT PRIVATE
US 20030110248A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2003/0110248 A1 Ritchc (43) Pub. Date: Jun.
 US 20030110248A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2003/0110248 A1 Ritchc (43) Pub. Date: (54) (76) (21) (22) (51) (52) AUTOMATED SERVICE SUPPORT OF SOFTWARE DISTRIBUTION
US 20030110248A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2003/0110248 A1 Ritchc (43) Pub. Date: (54) (76) (21) (22) (51) (52) AUTOMATED SERVICE SUPPORT OF SOFTWARE DISTRIBUTION
(54) RETARGETING RELATED TECHNIQUES (52) US. Cl... 705/1453 AND OFFERINGS. (75) Inventors: Ayrnan Farahat, San Francisco, (57) ABSTRACT
 US 20120271714Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0271714 A1 Farahat et a]. (43) Pub. Date: Oct. 25, 2012 (54) RETARGETING RELATED TECHNIQUES (52) US. Cl......
US 20120271714Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0271714 A1 Farahat et a]. (43) Pub. Date: Oct. 25, 2012 (54) RETARGETING RELATED TECHNIQUES (52) US. Cl......
check is encoded for causing it to b; oplerable with a, predetermined metering device. In t e a ternative em
 12/23/82 Unlted States XF? LHBI'I'QOES Patent [19] [11] 4,317,028 Simjian [] Feb. 23, 1982 [54] SUBSCRIBER CHECK ACCEPTING AND check adapted to operate a metering device comprises ISSUING APPARATUS means
12/23/82 Unlted States XF? LHBI'I'QOES Patent [19] [11] 4,317,028 Simjian [] Feb. 23, 1982 [54] SUBSCRIBER CHECK ACCEPTING AND check adapted to operate a metering device comprises ISSUING APPARATUS means
(12) Ulllted States Patent (10) Patent N0.: US 8,532,017 B2 Ojala et a]. (45) Date of Patent: Sep. 10, 2013
![(12) Ulllted States Patent (10) Patent N0.: US 8,532,017 B2 Ojala et a]. (45) Date of Patent: Sep. 10, 2013 (12) Ulllted States Patent (10) Patent N0.: US 8,532,017 B2 Ojala et a]. (45) Date of Patent: Sep. 10, 2013](/thumbs/40/20548245.jpg) US008532017B2 (12) Ulllted States Patent (10) Patent N0.: US 8,532,017 B2 Ojala et a]. (45) Date of Patent: Sep. 10, 2013 (54) TPC COMMAND SIGNALING IN DL (58) Field of Classi?cation Search CONTROL CHANNEL
US008532017B2 (12) Ulllted States Patent (10) Patent N0.: US 8,532,017 B2 Ojala et a]. (45) Date of Patent: Sep. 10, 2013 (54) TPC COMMAND SIGNALING IN DL (58) Field of Classi?cation Search CONTROL CHANNEL
US 20060100919A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0100919 A1 Levine (43) Pub. Date: May 11, 2006
 US 20060100919A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0100919 A1 Levine (43) Pub. Date: May 11, 2006 (54) EMPLOYEE RECRUITING SYSTEMS AND METHODS (76) Inventor:
US 20060100919A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0100919 A1 Levine (43) Pub. Date: May 11, 2006 (54) EMPLOYEE RECRUITING SYSTEMS AND METHODS (76) Inventor:
1,5 F., n M 3 My MM, 3 2. M5, ' 120 1. (21) App1.N0.: 13/789,334 M/WMWW W ~ 3> ( I INTERNET < 114. (71) ApplicantszRobert Monster, Sammamish, WA
 v US 2013023 8496A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0238496 A1 Monster et al. (43) Pub. Date: Sep. 12, 2013 (54) SYSTEM AND METHOD FOR DOMAN LEASNG, ACQUSTON
v US 2013023 8496A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0238496 A1 Monster et al. (43) Pub. Date: Sep. 12, 2013 (54) SYSTEM AND METHOD FOR DOMAN LEASNG, ACQUSTON
Ff'if ~ _ INVISIWALL. Shively (43) Pub. Date: NOV. 28, 2002 . LOCAL ONSITE. (Us) (21) Appl. No.: 09/865,377
 US 20020178378A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0178378 A1 Shively (43) Pub. Date: NOV. 28, 2002 (54) SECURE NTRUSON DETECTON SYSTEM (76) nventor: Geo?'rey
US 20020178378A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0178378 A1 Shively (43) Pub. Date: NOV. 28, 2002 (54) SECURE NTRUSON DETECTON SYSTEM (76) nventor: Geo?'rey
(12) United States Patent (10) Patent N0.: US 8,282,471 B1 Korner (45) Date of Patent: Oct. 9, 2012
 US008282471B1 (12) United States Patent (10) Patent N0.: US 8,282,471 B1 Korner (45) Date of Patent: Oct. 9, 2012 (54) COMPUTER-IMPLEMENTED SPORTS 2011/0003634 A1* 1/2011 Manteris..... 463/25 WAGERING
US008282471B1 (12) United States Patent (10) Patent N0.: US 8,282,471 B1 Korner (45) Date of Patent: Oct. 9, 2012 (54) COMPUTER-IMPLEMENTED SPORTS 2011/0003634 A1* 1/2011 Manteris..... 463/25 WAGERING
1 JOURNAL SYSTEM 16 / 10w T 12 8\ EMAIL ARCHIVE STORAGE ARCHIVE. STORAGE l 6 USER METADATA \ MA'LBOX T : DATABASE ARCHIVING (54) (75) Assignee: (73)
 US 20120259817Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0259817 A1 Baessler et al. (43) Pub. Date: (54) (75) (73) (21) (22) (63) UTLZNG METADATA TO OPTMZE EFFCENCY
US 20120259817Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0259817 A1 Baessler et al. (43) Pub. Date: (54) (75) (73) (21) (22) (63) UTLZNG METADATA TO OPTMZE EFFCENCY
Present Invention of the Internet - A Practical Approach to Marketing
 US 20070150355Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0150355 A1 Meggs (43) Pub. Date: Jun. 28, 2007 (54) WEB-BASED INCENTIVE SYSTEM AND Related U.s. Application
US 20070150355Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0150355 A1 Meggs (43) Pub. Date: Jun. 28, 2007 (54) WEB-BASED INCENTIVE SYSTEM AND Related U.s. Application
llllllllllllllillllllllllllllllllllllllllllllllllllllllllllllllllllllllllll
 llllllllllllllillllllllllllllllllllllllllllllllllllllllllllllllllllllllllll USOO5535162A United States Patent [19] [11] Patent Number: 5,535,162 Uenoyama [45] Date of Patent: Jul. 9, 1996 [54] ELECTRICALLY
llllllllllllllillllllllllllllllllllllllllllllllllllllllllllllllllllllllllll USOO5535162A United States Patent [19] [11] Patent Number: 5,535,162 Uenoyama [45] Date of Patent: Jul. 9, 1996 [54] ELECTRICALLY
United States Patent [191
 United States Patent [191 Fancy [54] REDUNDANT SIGNAL CIRCUIT [75] Inventor: Thomas A. Fancy, Westminster, Mass. [73] Assignee: General Electric Company, Schenectady, NY. [211 Appl. No.: 854,973 [22] Filed:
United States Patent [191 Fancy [54] REDUNDANT SIGNAL CIRCUIT [75] Inventor: Thomas A. Fancy, Westminster, Mass. [73] Assignee: General Electric Company, Schenectady, NY. [211 Appl. No.: 854,973 [22] Filed:
ENCODED $30 CERT'F'CATE -+ DECODE CERTIFICATE
 US 20130346742A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0346742 A1 Tada et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR DEVICE Publication Classi?cation AUTHENTICATION
US 20130346742A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0346742 A1 Tada et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR DEVICE Publication Classi?cation AUTHENTICATION
Filetto et al. [45] Date of Patent: Feb. 15, 2000
![Filetto et al. [45] Date of Patent: Feb. 15, 2000 Filetto et al. [45] Date of Patent: Feb. 15, 2000](/thumbs/39/20301551.jpg) US006025842A United. States Patent [19] [11] P a t en tn um b er: 6, 025, 842 Filetto et al. [45] Date of Patent: Feb. 15, 2000 [54] SYSTEM AND METHOD FOR WINDOW 5,046,001 9/1991 Barker et al...... 364/200
US006025842A United. States Patent [19] [11] P a t en tn um b er: 6, 025, 842 Filetto et al. [45] Date of Patent: Feb. 15, 2000 [54] SYSTEM AND METHOD FOR WINDOW 5,046,001 9/1991 Barker et al...... 364/200
(12) United States Patent
 US008914855B2 (12) United States Patent Whitmyer, Jr. (10) Patent N0.: (45) Date of Patent: US 8,914,855 B2 Dec. 16, 2014 (54) PORTABLE PASSWORD KEEPER WITH INTERNET STORAGE AND RESTORE (75) Inventor:
US008914855B2 (12) United States Patent Whitmyer, Jr. (10) Patent N0.: (45) Date of Patent: US 8,914,855 B2 Dec. 16, 2014 (54) PORTABLE PASSWORD KEEPER WITH INTERNET STORAGE AND RESTORE (75) Inventor:
United States Patent [191 [11] Patent Number: 4,732,385
![United States Patent [191 [11] Patent Number: 4,732,385 United States Patent [191 [11] Patent Number: 4,732,385](/thumbs/30/14321926.jpg) United States Patent [191 [11] Patent Number: 4,732,385 Castellanos [45] Date of Patent: Mar. 22, 1988 [54] ROULETTE F 0R GAMI N G FOREIGN PATENT DOCUMENTS [76] Invento? Rodolfo 1,3- castf?lanos, Escalmendi,
United States Patent [191 [11] Patent Number: 4,732,385 Castellanos [45] Date of Patent: Mar. 22, 1988 [54] ROULETTE F 0R GAMI N G FOREIGN PATENT DOCUMENTS [76] Invento? Rodolfo 1,3- castf?lanos, Escalmendi,
Ulllted States Patent [19] [11] Patent Number: 5,859,416
![Ulllted States Patent [19] [11] Patent Number: 5,859,416 Ulllted States Patent [19] [11] Patent Number: 5,859,416](/thumbs/30/14417385.jpg) US005859416A. Ulllted States Patent [19] [11] Patent Number: Gatto [] Date of Patent: *Jan. 12, 1999 [54] FUEL PUMP SYSTEM WITH AUTOMATED 5,144,1 9/1992 Yoshida..... 2/379 TRANSACTION PROCESSING 5,175,416
US005859416A. Ulllted States Patent [19] [11] Patent Number: Gatto [] Date of Patent: *Jan. 12, 1999 [54] FUEL PUMP SYSTEM WITH AUTOMATED 5,144,1 9/1992 Yoshida..... 2/379 TRANSACTION PROCESSING 5,175,416
United States. (12) Patent Application Publication (10) Pub. No.: US 2013/0268350 A1 Koonce et al. (43) Pub. Date: Oct. 10, 2013 (19) (54) (71) (72)
 (19) United States US 20130268350A1 (12) Patent Application Publication (10) Pub. No.: US 2013/0268350 A1 Koonce et al. (43) Pub. Date: Oct. 10, 2013 (54) (71) (72) (21) (22) (63) SYSTEM AND METHOD FOR
(19) United States US 20130268350A1 (12) Patent Application Publication (10) Pub. No.: US 2013/0268350 A1 Koonce et al. (43) Pub. Date: Oct. 10, 2013 (54) (71) (72) (21) (22) (63) SYSTEM AND METHOD FOR
5,793,972 Aug. 11, 1998
 United States Patent [19] Shane USOO5793972A [11] Patent Number: [45] Date of Patent: 5,793,972 Aug. 11, 1998 [54] SYSTEM AND METHOD PROVIDING AN INTERACTIVE RESPONSE TO DIRECT MAIL BY CREATING PERSONALIZED
United States Patent [19] Shane USOO5793972A [11] Patent Number: [45] Date of Patent: 5,793,972 Aug. 11, 1998 [54] SYSTEM AND METHOD PROVIDING AN INTERACTIVE RESPONSE TO DIRECT MAIL BY CREATING PERSONALIZED
United States Patent [191 Brugliera et al.
 United States Patent [191 Brugliera et al. [11] [45] Patent Number: 4,910,767 Date of Patent: Mar. 20, 1990 [54] [75] [73] [21] [22] [51] [52] [58] [56] ANI AUTO DIALER WITH CARRIER CURRENT INTERFACE Inventors:
United States Patent [191 Brugliera et al. [11] [45] Patent Number: 4,910,767 Date of Patent: Mar. 20, 1990 [54] [75] [73] [21] [22] [51] [52] [58] [56] ANI AUTO DIALER WITH CARRIER CURRENT INTERFACE Inventors:
(54) METHOD FOR AUTOMATED HANDLING OF Publication Classi?cation OUTBOUND CONTACTS REQUIRING ASSURED CONNECTION TO A LIVE AGENT (51) Int- Cl
 US 20140044256A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0044256 A1 Zgardovski et al. (43) Pub. Date: (54) METHOD FOR AUTOMATED HANDLING OF Publication Classi?cation
US 20140044256A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0044256 A1 Zgardovski et al. (43) Pub. Date: (54) METHOD FOR AUTOMATED HANDLING OF Publication Classi?cation
USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611. 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999
![USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611. 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999 USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611. 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999](/thumbs/31/15320422.jpg) USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999 [54] APPARATUS AND METHOD FOR 5,526,416 6/1996 Dezonno et al...... 379/266 IDENTIFYING
USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999 [54] APPARATUS AND METHOD FOR 5,526,416 6/1996 Dezonno et al...... 379/266 IDENTIFYING
Barracuda Spam Control System
 Barracuda Spam Control System 1. General Information The Barracuda anti-spam server inspects all email coming into campus from the Internet for spam and either delivers the message to your email inbox,
Barracuda Spam Control System 1. General Information The Barracuda anti-spam server inspects all email coming into campus from the Internet for spam and either delivers the message to your email inbox,
