CIT 470: Advanced Network and System Administration. Topics. Change Management. Change and Configuration Management
|
|
|
- Lindsey Houston
- 10 years ago
- Views:
Transcription
1 CIT 470: Advanced Network and System Administration Change and Configuration Management CIT 470: Advanced Network and System Administration Slide #1 Topics 1. Change Management 2. Change Processes 3. Revision Control 4. Configuration Management 5. cfengine Images from Pro Git CIT 470: Advanced Network and System Administration Slide #2 Change Management Effective planning and implementation of changes to systems. Changes should be 1. Well documented. 2. Have a backout plan. 3. Reproducible. CIT 470: Advanced Network and System Administration Slide #3 1
2 Why do we need Change Management? March 26-29, 2006: BART trains halted to avoid running into each other when computer systems crashed. Crashes on Monday/Tuesday resulted from software maintenance upgrades. Crash on Wednesday resulted from installing a backup system to avoid future crashes. Thousands of passengers stranded for several hours each time. CIT 470: Advanced Network and System Administration Slide #4 Change Management 1. Plan change. 2. Test change on single system. 3. Test change on multiple systems. 4. File a change request. 5. Change committee approves request. 6. Schedule change. 7. Communication with users/admins. 8. Change systems at scheduled time. 9. Post-event analysis. CIT 470: Advanced Network and System Administration Slide #5 Testing Changes Automated checks. Sanity checks like Samba testparm. Reboot system. Test on one system first. Then test on set of systems. Dedicated test systems. System admin workstations. Virtual machines. CIT 470: Advanced Network and System Administration Slide #6 2
3 When do you need a Change Proposal? Does the change impact critical services? Critical machines/services Business critical: e-commerce server, etc. Essential services: routers, DNS, NFS, auth. Non-critical machines/services Individual desktops Internal news web server CIT 470: Advanced Network and System Administration Slide #7 Change Proposal 1. Description of the change. 2. Systems impacted by change. 3. Why the change is being made. 4. Risks presented by the change. 5. Test procedure. 6. Backout plans. 7. How long the change will require. CIT 470: Advanced Network and System Administration Slide #8 Communication Communicate change to impacted people. What change is being made (nontechnical.) Which services will be unavailable. When and how long will they be unavailable. What actions do they need to task (if any.) Communication issues If you send too many notes, they ll be ignored. Send notices only to those impacted. Push critical notices; use pull for non-critical. CIT 470: Advanced Network and System Administration Slide #9 3
4 Routine Major Scheduling Scope When Notification Type Single host or user. Many hosts or users. Sensitive None but major impact on failure. Anytime. Personal. Off-peak Push. Off-peak. Pull. CIT 470: Advanced Network and System Administration Slide #10 Change Freezes Time when only minor updates can be done. End of quarter or year. Crunch time for projects. CIT 470: Advanced Network and System Administration Slide #11 Backing Out Decide back-out conditions before downtime Avoid the just 5 more minutes problem. Be sure that someone is keeping track of time. Questions: How much time is required for back out? When is the latest time you can successfully back out? Will backing out this change prevent other changes from being committed? CIT 470: Advanced Network and System Administration Slide #12 4
5 Backing Out: How to do it? Service-level changes Use revision control system to revert config. Restart service. Machine-level changes Soft cutover: Old service is still running. Hard cutover: Power up old server or restore from backups. Issues Data migration. Compatibility. CIT 470: Advanced Network and System Administration Slide #13 Automatic Checks Check integrity of critical files before use. Some services provide checks: LDAP, SMB. Check startup files by rebooting machine. Write your own checks for other files. Most people only do this after they have a problem. CIT 470: Advanced Network and System Administration Slide #14 Revision Control Revision control systems provide Conflict management: prevents multiple people from modifying file at once and corrupting it. Change history: records who modified the file when and why the change was made. Revision control paradigms Lock-Modify-Unlock: rcs Copy-Modify-Merge: cvs, subversion, etc. Distributed: darcs, git, mercurial CIT 470: Advanced Network and System Administration Slide #15 5
6 Local Version Control CIT 470: Advanced Network and System Administration Slide #16 Centralized Version Control CIT 470: Advanced Network and System Administration Slide #17 Distributed Version Control CIT 470: Advanced Network and System Administration Slide #18 6
7 Local Git Operations CIT 470: Advanced Network and System Administration Slide #19 Git File Lifecycle CIT 470: Advanced Network and System Administration Slide #20 Gitk history visualizer CIT 470: Advanced Network and System Administration Slide #21 7
8 CIT 470: Advanced Network and System Administration Slide #22 References 1. Mark Burgess, Principles of Network and System Administration, 2 nd edition, Wiley, Aeleen Frisch, Essential System Administration, 3 rd edition, O Reilly, Thomas A. Limoncelli and Christine Hogan, The Practice of System and Network Administration, Addison-Wesley, Evi Nemeth et al, UNIX System Administration Handbook, 3 rd edition, Prentice Hall, Todd R. Weiss, IT upgrades slow BART trains in San Francisco, ,00.html, ComputerWorld, March 31, CIT 470: Advanced Network and System Administration Slide #23 8
Topics. CIT 470: Advanced Network and System Administration. Help Desk Life. Types of Help Desks. Scope of Coverage. Help Desk Size.
 Topics CIT 470: Advanced Network and System Administration Help Desks 1. Help Desk Management 2. Help Desk Software 3. Workflow 4. Trend Analysis CIT 470: Advanced Network and System Administration Slide
Topics CIT 470: Advanced Network and System Administration Help Desks 1. Help Desk Management 2. Help Desk Software 3. Workflow 4. Trend Analysis CIT 470: Advanced Network and System Administration Slide
CIT 470: Advanced Network and System Administration. Topics. Help Desk Life. Help Desks
 CIT 470: Advanced Network and System Administration Help Desks CIT 470: Advanced Network and System Administration Slide #1 Topics 1. Help Desk Management 2. Help Desk Software 3. Workflow 4. Trend Analysis
CIT 470: Advanced Network and System Administration Help Desks CIT 470: Advanced Network and System Administration Slide #1 Topics 1. Help Desk Management 2. Help Desk Software 3. Workflow 4. Trend Analysis
CIT 470: Advanced Network and System Administration. Topics. Help Desk Life. Help Desks
 CIT 470: Advanced Network and System Administration Help Desks CIT 470: Advanced Network and System Administration Slide #1 Topics 1. Help Desk Management 2. Help Desk Software 3. Workflow 4. Trend Analysis
CIT 470: Advanced Network and System Administration Help Desks CIT 470: Advanced Network and System Administration Slide #1 Topics 1. Help Desk Management 2. Help Desk Software 3. Workflow 4. Trend Analysis
Continuous Integration. CSC 440: Software Engineering Slide #1
 Continuous Integration CSC 440: Software Engineering Slide #1 Topics 1. Continuous integration 2. Configuration management 3. Types of version control 1. None 2. Lock-Modify-Unlock 3. Copy-Modify-Merge
Continuous Integration CSC 440: Software Engineering Slide #1 Topics 1. Continuous integration 2. Configuration management 3. Types of version control 1. None 2. Lock-Modify-Unlock 3. Copy-Modify-Merge
INSTRUCTOR: Dwight Makaroff - Thorvaldson 281.3 x8656. Available via appointment.
 Network and System Administration - CMPT 433 Syllabus University of Saskatchewan 2012-2013 Term 2 DESCRIPTION AND LEARNING OBJECTIVES ----------------------------------- CALENDAR DESCRIPTION: This course
Network and System Administration - CMPT 433 Syllabus University of Saskatchewan 2012-2013 Term 2 DESCRIPTION AND LEARNING OBJECTIVES ----------------------------------- CALENDAR DESCRIPTION: This course
Topics. CIT 470: Advanced Network and System Administration. Why Monitoring? Why Monitoring? Historical Monitoring Processes. Historical Monitoring
 Topics CIT 470: Advanced Network and System Administration System Monitoring 1. Why monitoring? 2. Historical monitoring 3. Real-time monitoring 4. Monitoring techniques 5. Monit 6. Web-based monitoring
Topics CIT 470: Advanced Network and System Administration System Monitoring 1. Why monitoring? 2. Historical monitoring 3. Real-time monitoring 4. Monitoring techniques 5. Monit 6. Web-based monitoring
5 Reasons Your Business Needs Network Monitoring
 5 Reasons Your Business Needs Network Monitoring Intivix.com (415) 543 1033 5 REASONS YOUR BUSINESS NEEDS NETWORK MONITORING Your business depends on the health of your network for office productivity.
5 Reasons Your Business Needs Network Monitoring Intivix.com (415) 543 1033 5 REASONS YOUR BUSINESS NEEDS NETWORK MONITORING Your business depends on the health of your network for office productivity.
Five Reasons Your Business Needs Network Monitoring
 Five Reasons Your Business Needs Network Monitoring cognoscape.com Five Reasons Your Business Needs Network Monitoring Your business depends on the health of your network for office productivity. Most
Five Reasons Your Business Needs Network Monitoring cognoscape.com Five Reasons Your Business Needs Network Monitoring Your business depends on the health of your network for office productivity. Most
CIT 470: Advanced Network and System Administration. Topics. Why Monitoring? System Monitoring
 CIT 470: Advanced Network and System Administration System Monitoring CIT 470: Advanced Network and System Administration Slide #1 Topics 1. Why monitoring? 2. Historical monitoring 3. Real-time monitoring
CIT 470: Advanced Network and System Administration System Monitoring CIT 470: Advanced Network and System Administration Slide #1 Topics 1. Why monitoring? 2. Historical monitoring 3. Real-time monitoring
Source Control Systems
 Source Control Systems SVN, Git, GitHub SoftUni Team Technical Trainers Software University http://softuni.bg Table of Contents 1. Software Configuration Management (SCM) 2. Version Control Systems: Philosophy
Source Control Systems SVN, Git, GitHub SoftUni Team Technical Trainers Software University http://softuni.bg Table of Contents 1. Software Configuration Management (SCM) 2. Version Control Systems: Philosophy
IT6203 Systems & Network Administration. (Optional)
 Systems & Network Administration (Optional) INTRODUCTION This is one of the Optional courses designed for Semester 6 of the Bachelor of Information Technology Degree program. This course on Systems & Network
Systems & Network Administration (Optional) INTRODUCTION This is one of the Optional courses designed for Semester 6 of the Bachelor of Information Technology Degree program. This course on Systems & Network
Upgrading Client Security and Policy Manager in 4 easy steps
 Page 1 of 13 F-Secure White Paper Upgrading Client Security and Policy Manager in 4 easy steps Purpose This white paper describes how to easily upgrade your existing environment running Client Security
Page 1 of 13 F-Secure White Paper Upgrading Client Security and Policy Manager in 4 easy steps Purpose This white paper describes how to easily upgrade your existing environment running Client Security
CIT 470: Advanced Network and System Administration. Topics. Performance Monitoring. Performance Monitoring
 CIT 470: Advanced Network and System Administration Performance Monitoring CIT 470: Advanced Network and System Administration Slide #1 Topics 1. Performance monitoring. 2. Performance tuning. 3. CPU 4.
CIT 470: Advanced Network and System Administration Performance Monitoring CIT 470: Advanced Network and System Administration Slide #1 Topics 1. Performance monitoring. 2. Performance tuning. 3. CPU 4.
Ingeniørh. Version Control also known as Configuration Management
 Ingeniørh rhøjskolen i Århus Version Control also known as Configuration Management Why version control? Teamwork You work in a team. You open a file and start work on it. Your colleague opens a file and
Ingeniørh rhøjskolen i Århus Version Control also known as Configuration Management Why version control? Teamwork You work in a team. You open a file and start work on it. Your colleague opens a file and
CIT 668: System Architecture. Performance Testing
 CIT 668: System Architecture Performance Testing Topics 1. What is performance testing? 2. Performance-testing activities 3. UNIX monitoring tools What is performance testing? Performance testing is a
CIT 668: System Architecture Performance Testing Topics 1. What is performance testing? 2. Performance-testing activities 3. UNIX monitoring tools What is performance testing? Performance testing is a
Backup and Redundancy
 Backup and Redundancy White Paper NEC s UC for Business Backup and Redundancy allow businesses to operate with confidence, providing security for themselves and their customers. When a server goes down
Backup and Redundancy White Paper NEC s UC for Business Backup and Redundancy allow businesses to operate with confidence, providing security for themselves and their customers. When a server goes down
VMware vsphere 5 Quick Start Guide
 VMware vsphere 5 Quick Start Guide This document is created to provide some basic information about VMware, and allow you, the customer, to determine when and how to engage us for support or other needs
VMware vsphere 5 Quick Start Guide This document is created to provide some basic information about VMware, and allow you, the customer, to determine when and how to engage us for support or other needs
Basic Router and Switch Instructions (Cisco Devices)
 Basic Router and Switch Instructions (Cisco Devices) Basic Device Connection 1. Connect to the device via the console cable (light blue cable) and the use of a terminal program (Windows Hyperterminal,
Basic Router and Switch Instructions (Cisco Devices) Basic Device Connection 1. Connect to the device via the console cable (light blue cable) and the use of a terminal program (Windows Hyperterminal,
How Routine Data Center Operations Put Your HA/DR Plans at Risk
 How Routine Data Center Operations Put Your HA/DR Plans at Risk Protect your business by closing gaps in your disaster recovery infrastructure Things alter for the worse spontaneously, if they be not altered
How Routine Data Center Operations Put Your HA/DR Plans at Risk Protect your business by closing gaps in your disaster recovery infrastructure Things alter for the worse spontaneously, if they be not altered
How To Use 1Bay 1Bay From Awn.Net On A Pc Or Mac Or Ipad (For Pc Or Ipa) With A Network Box (For Mac) With An Ipad Or Ipod (For Ipad) With The
 1-bay NAS User Guide INDEX Index... 1 Log in... 2 Basic - Quick Setup... 3 Wizard... 3 Add User... 6 Add Group... 7 Add Share... 9 Control Panel... 11 Control Panel - User and groups... 12 Group Management...
1-bay NAS User Guide INDEX Index... 1 Log in... 2 Basic - Quick Setup... 3 Wizard... 3 Add User... 6 Add Group... 7 Add Share... 9 Control Panel... 11 Control Panel - User and groups... 12 Group Management...
How To Fix A Powerline From Disaster To Powerline
 Perforce Backup Strategy & Disaster Recovery at National Instruments Steven Lysohir 1 Why This Topic? Case study on large Perforce installation Something for smaller sites to ponder as they grow Stress
Perforce Backup Strategy & Disaster Recovery at National Instruments Steven Lysohir 1 Why This Topic? Case study on large Perforce installation Something for smaller sites to ponder as they grow Stress
NetIQ Advanced Authentication Framework. Maintenance Guide. Version 5.1.0
 NetIQ Advanced Authentication Framework Maintenance Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Purposes of Maintenance 3 Difficulties of Maintenance
NetIQ Advanced Authentication Framework Maintenance Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Purposes of Maintenance 3 Difficulties of Maintenance
ICT Disaster Recovery Plan
 Dronfield Henry Fanshawe School Policy No: S33 ICT Disaster Recovery Plan Revision No: 1 Date Issued: September 2012 Committee: Author: Statutory RDD Date Adopted: September 2012 Minute No: 12/20 Review
Dronfield Henry Fanshawe School Policy No: S33 ICT Disaster Recovery Plan Revision No: 1 Date Issued: September 2012 Committee: Author: Statutory RDD Date Adopted: September 2012 Minute No: 12/20 Review
Other documents in this series are available at: servernotes.wazmac.com
 Wazza s Snow Leopard Server QuickStart 14. Win XP - Workgroup Setup About the Document This document is the fourteenth in a series of documents describing the process of installing and configuring a Mac
Wazza s Snow Leopard Server QuickStart 14. Win XP - Workgroup Setup About the Document This document is the fourteenth in a series of documents describing the process of installing and configuring a Mac
Maximum Availability Architecture. Oracle Best Practices For High Availability. Backup and Recovery Scenarios for Oracle WebLogic Server: 10.
 Backup and Recovery Scenarios for Oracle WebLogic Server: 10.3 An Oracle White Paper January, 2009 Maximum Availability Architecture Oracle Best Practices For High Availability Backup and Recovery Scenarios
Backup and Recovery Scenarios for Oracle WebLogic Server: 10.3 An Oracle White Paper January, 2009 Maximum Availability Architecture Oracle Best Practices For High Availability Backup and Recovery Scenarios
VeriCentre 3.0 Upgrade Pre-Installation and Post Installation Guidelines
 VeriCentre 3.0 Upgrade Pre-Installation and Post Installation Guidelines * For actual installation steps, please refer to the VeriCentre 3.0 Installation guide that came with the VeriCentre 3.0 software.
VeriCentre 3.0 Upgrade Pre-Installation and Post Installation Guidelines * For actual installation steps, please refer to the VeriCentre 3.0 Installation guide that came with the VeriCentre 3.0 software.
When Your Networkʼs Down, Call Crown
 When Your Networkʼs Down, Call Crown 521 W. Broad Avenue Albany, GA 31701 Phone: 229.317.7940 Fax: 229.317.7941 [email protected] MANAGED SERVICES & FLAT RATE I.T. SUPPORT Our Managed Services,
When Your Networkʼs Down, Call Crown 521 W. Broad Avenue Albany, GA 31701 Phone: 229.317.7940 Fax: 229.317.7941 [email protected] MANAGED SERVICES & FLAT RATE I.T. SUPPORT Our Managed Services,
INFUSION BUSINESS SOFTWARE Installation and Upgrade Guide
 INFUSION BUSINESS SOFTWARE Installation and Upgrade Guide 27/01/2016 Published by Infusion Business Software Ltd All Rights Reserved Copyright Infusion Business Software Ltd 2012 Copyright No part of this
INFUSION BUSINESS SOFTWARE Installation and Upgrade Guide 27/01/2016 Published by Infusion Business Software Ltd All Rights Reserved Copyright Infusion Business Software Ltd 2012 Copyright No part of this
Source Control Guide: Git
 MadCap Software Source Control Guide: Git Flare 11.1 Copyright 2015 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this
MadCap Software Source Control Guide: Git Flare 11.1 Copyright 2015 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this
Training Events Database (TED) Setup Guide
 This document describes the basic process for installing the Training Events Database (TED) system. It does not cover installing FileMaker Pro or FileMaker Server, the software needed to run TED, or how
This document describes the basic process for installing the Training Events Database (TED) system. It does not cover installing FileMaker Pro or FileMaker Server, the software needed to run TED, or how
3. Where can I obtain the Service Pack 5 software?
 Reasons to upgrade: 1. What are the features of BlackBerr y Enterprise Server 4.1 Service Pack 5? What issues does Service Pack 5 address? Are there any current known issues with Service Pack 5? The BlackBerry
Reasons to upgrade: 1. What are the features of BlackBerr y Enterprise Server 4.1 Service Pack 5? What issues does Service Pack 5 address? Are there any current known issues with Service Pack 5? The BlackBerry
All rights reserved. Trademarks
 All rights reserved This manual, as well as the software described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. The content of this manual
All rights reserved This manual, as well as the software described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. The content of this manual
Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide
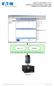 Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide Hyper-V 6.0 NetWatch Main operating system: 2008 Enterprise x64 (hosting Hyper-V) Eaton UPS Eaton NetWatch
Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide Hyper-V 6.0 NetWatch Main operating system: 2008 Enterprise x64 (hosting Hyper-V) Eaton UPS Eaton NetWatch
Upgrading a computer to Windows 10 with PetLinx
 25 August, 2015 Upgrading a computer to Windows 10 with PetLinx Microsoft have recently released Windows 10 and offered it as a free upgrade for user of Windows 7 and 8/8.1. In most cases, computers with
25 August, 2015 Upgrading a computer to Windows 10 with PetLinx Microsoft have recently released Windows 10 and offered it as a free upgrade for user of Windows 7 and 8/8.1. In most cases, computers with
Version Control with Subversion
 Version Control with Subversion Introduction Wouldn t you like to have a time machine? Software developers already have one! it is called version control Version control (aka Revision Control System or
Version Control with Subversion Introduction Wouldn t you like to have a time machine? Software developers already have one! it is called version control Version control (aka Revision Control System or
Citrix Application Streaming. Universal Application Packaging and Delivery Breaking Away from Traditional IT
 Citrix Application Streaming Universal Application Packaging and Delivery Breaking Away from Traditional IT Application Packaging Application Delivery to Endpoint Devices Application Isolation Mode Automatic
Citrix Application Streaming Universal Application Packaging and Delivery Breaking Away from Traditional IT Application Packaging Application Delivery to Endpoint Devices Application Isolation Mode Automatic
System Admin Module User Guide. Schmooze Com Inc.
 Schmooze Com Inc. Chapters Overview Using the Module DDNS DNS Email Setup FTP Server Intrusion Detection License Network Settings Notification Settings Port Management Power Options Storage Time Zone Updates
Schmooze Com Inc. Chapters Overview Using the Module DDNS DNS Email Setup FTP Server Intrusion Detection License Network Settings Notification Settings Port Management Power Options Storage Time Zone Updates
RMM/MDM. Quick Reference Guide
 RMM/MDM Quick Reference Guide Contents Getting Started...3 Probe and Agent Management...3 Installing a Windows Probe...3 Installing an Agent...5 Windows Agents...5 Updating Monitoring Software - Manually...5
RMM/MDM Quick Reference Guide Contents Getting Started...3 Probe and Agent Management...3 Installing a Windows Probe...3 Installing an Agent...5 Windows Agents...5 Updating Monitoring Software - Manually...5
Version Control. Version Control
 Version Control CS440 Introduction to Software Engineering 2013, 2015 John Bell Based on slides prepared by Jason Leigh for CS 340 University of Illinois at Chicago Version Control Incredibly important
Version Control CS440 Introduction to Software Engineering 2013, 2015 John Bell Based on slides prepared by Jason Leigh for CS 340 University of Illinois at Chicago Version Control Incredibly important
Network Computing Architects Inc. (NCA) Network Operations Center (NOC) Services
 Network Computing Architects Inc. (NCA), provides outsourced IT services by monitoring and managing clients computing assets. Included Services: For all systems covered under NOC Support, the following
Network Computing Architects Inc. (NCA), provides outsourced IT services by monitoring and managing clients computing assets. Included Services: For all systems covered under NOC Support, the following
LISTSERV in a High-Availability Environment DRAFT Revised 2010-01-11
 LISTSERV in a High-Availability Environment DRAFT Revised 2010-01-11 Introduction For many L-Soft customers, LISTSERV is a critical network application. Such customers often have policies dictating uptime
LISTSERV in a High-Availability Environment DRAFT Revised 2010-01-11 Introduction For many L-Soft customers, LISTSERV is a critical network application. Such customers often have policies dictating uptime
SyncThru Database Migration
 SyncThru Database Migration Overview Database Migration for SyncThru application is an intuitive tool that enables the data stored in the database of an older version of SyncThru, to be moved to the database
SyncThru Database Migration Overview Database Migration for SyncThru application is an intuitive tool that enables the data stored in the database of an older version of SyncThru, to be moved to the database
XMS Quick Start Guide
 812-0055-002D XMS Quick Start Guide Overview of Quick Start Steps This guide will quickly get you up and running with the Xirrus Management System (XMS). It includes instructions for setting up the XMS
812-0055-002D XMS Quick Start Guide Overview of Quick Start Steps This guide will quickly get you up and running with the Xirrus Management System (XMS). It includes instructions for setting up the XMS
WEB SERVER MONITORING SORIN POPA
 WEB SERVER MONITORING SORIN POPA Keywords: monitoring systems, web server, monitoring process Sorin POPA, Associate Professor, PhD. University of Craiova Abstract. This paper introduces web-server monitoring,
WEB SERVER MONITORING SORIN POPA Keywords: monitoring systems, web server, monitoring process Sorin POPA, Associate Professor, PhD. University of Craiova Abstract. This paper introduces web-server monitoring,
NEW YORK CITY COLLEGE OF TECHNOLOGY/CUNY
 NEW YORK CITY COLLEGE OF TECHNOLOGY/CUNY Computer Systems Technology Department Course: CST2405 System Administration - Windows (2 class hours, 2 lab hours, 3 credits) Course Description: This introductory
NEW YORK CITY COLLEGE OF TECHNOLOGY/CUNY Computer Systems Technology Department Course: CST2405 System Administration - Windows (2 class hours, 2 lab hours, 3 credits) Course Description: This introductory
NETASQ SSO Agent Installation and deployment
 NETASQ SSO Agent Installation and deployment Document version: 1.3 Reference: naentno_sso_agent Page 1 / 20 Copyright NETASQ 2013 General information 3 Principle 3 Requirements 3 Active Directory user
NETASQ SSO Agent Installation and deployment Document version: 1.3 Reference: naentno_sso_agent Page 1 / 20 Copyright NETASQ 2013 General information 3 Principle 3 Requirements 3 Active Directory user
Patch Management Policy
 Patch Management Policy L2-POL-12 Version No :1.0 Revision History REVISION DATE PREPARED BY APPROVED BY DESCRIPTION Original 1.0 2-Apr-2015 Process Owner Management Representative Initial Version No.:
Patch Management Policy L2-POL-12 Version No :1.0 Revision History REVISION DATE PREPARED BY APPROVED BY DESCRIPTION Original 1.0 2-Apr-2015 Process Owner Management Representative Initial Version No.:
Storage Sync for Hyper-V. Installation Guide for Microsoft Hyper-V
 Installation Guide for Microsoft Hyper-V Egnyte Inc. 1890 N. Shoreline Blvd. Mountain View, CA 94043, USA Phone: 877-7EGNYTE (877-734-6983) www.egnyte.com 2013 by Egnyte Inc. All rights reserved. Revised
Installation Guide for Microsoft Hyper-V Egnyte Inc. 1890 N. Shoreline Blvd. Mountain View, CA 94043, USA Phone: 877-7EGNYTE (877-734-6983) www.egnyte.com 2013 by Egnyte Inc. All rights reserved. Revised
If you have used Outlook Web Access then you will find Zarafa Webaccess very familiar.
 Zarafa Setup Guide The Zarafa server on Igaware allows you to share e-mail, calendars, contacts and tasks via Outlook, on your PDA/Blackberry/Mobile phone or through our Webaccess. The Zarafa Webaccess
Zarafa Setup Guide The Zarafa server on Igaware allows you to share e-mail, calendars, contacts and tasks via Outlook, on your PDA/Blackberry/Mobile phone or through our Webaccess. The Zarafa Webaccess
ITIL A guide to Event Management
 ITIL A guide to Event Management An event can be defined as any detectable or discernable occurrence that has significance for the management of the IT Infrastructure of the delivery of IT service and
ITIL A guide to Event Management An event can be defined as any detectable or discernable occurrence that has significance for the management of the IT Infrastructure of the delivery of IT service and
Installation Manual Version 8.5 (w/sql Server 2005)
 C ase Manag e m e n t by C l i e n t P rofiles Installation Manual Version 8.5 (w/sql Server 2005) T E C H N O L O G Y F O R T H E B U S I N E S S O F L A W Table of Contents - 2 - Table of Contents SERVER
C ase Manag e m e n t by C l i e n t P rofiles Installation Manual Version 8.5 (w/sql Server 2005) T E C H N O L O G Y F O R T H E B U S I N E S S O F L A W Table of Contents - 2 - Table of Contents SERVER
DeployStudio Server Quick Install
 DeployStudio Server Quick Install v1.7.0 The DeployStudio Team [email protected] Requirements OS X 10.7.5 to 10.11.1 DeployStudioServer_v1.7.x.pkg and later NetBoot based deployment 100 Mb/s switched
DeployStudio Server Quick Install v1.7.0 The DeployStudio Team [email protected] Requirements OS X 10.7.5 to 10.11.1 DeployStudioServer_v1.7.x.pkg and later NetBoot based deployment 100 Mb/s switched
ICANWK401A Install and manage a server
 ICANWK401A Install and manage a server Release: 1 ICANWK401A Install and manage a server Modification History Release Release 1 Comments This Unit first released with ICA11 Information and Communications
ICANWK401A Install and manage a server Release: 1 ICANWK401A Install and manage a server Modification History Release Release 1 Comments This Unit first released with ICA11 Information and Communications
the limits of your infrastructure. How to get the most out of virtualization
 the limits of your infrastructure. How to get the most out of virtualization Business white paper Table of contents Executive summary...4 The benefits of virtualization?...4 How people and processes add
the limits of your infrastructure. How to get the most out of virtualization Business white paper Table of contents Executive summary...4 The benefits of virtualization?...4 How people and processes add
Version 2.10 Installation and Configuration Guide
 Version 2.10 Installation and Configuration Guide Document Version 1.6 QGate Software Limited D2 Fareham Heights, Standard Way, Fareham Hampshire, PO16 8XT United Kingdom Tel +44 (0)1329 222800 [email protected]
Version 2.10 Installation and Configuration Guide Document Version 1.6 QGate Software Limited D2 Fareham Heights, Standard Way, Fareham Hampshire, PO16 8XT United Kingdom Tel +44 (0)1329 222800 [email protected]
Topics. CIT 470: Advanced Network and System Administration. Logging Policies. System Logs. Throwing Away. How to choose a logging policy?
 Topics CIT 470: Advanced Network and System Administration Logging 1. System logs 2. Logging policies 3. Finding logs 4. Syslog 5. Syslog servers 6. Log monitoring CIT 470: Advanced Network and System
Topics CIT 470: Advanced Network and System Administration Logging 1. System logs 2. Logging policies 3. Finding logs 4. Syslog 5. Syslog servers 6. Log monitoring CIT 470: Advanced Network and System
Achieving Continuous Integration with Drupal
 23 Au gu Achieving Continuous Integration with Drupal st 20 12 Achieving Continuous Integration with Drupal Drupalcon Munich 2012 Barry Jaspan [email protected] The Evolution of a Drupal Developer
23 Au gu Achieving Continuous Integration with Drupal st 20 12 Achieving Continuous Integration with Drupal Drupalcon Munich 2012 Barry Jaspan [email protected] The Evolution of a Drupal Developer
CSE 265: System and Network Administration
 CSE 265: System and Network Administration Making mixed environments work Sharing Resources Common authentication Network name resolution Printers Files Making Windows look like Linux and vice versa Add
CSE 265: System and Network Administration Making mixed environments work Sharing Resources Common authentication Network name resolution Printers Files Making Windows look like Linux and vice versa Add
User Guide to the Snare Agent Management Console in Snare Server v7.0
 User Guide to the Snare Agent Management Console in Snare Server v7.0 Intersect Alliance International Pty Ltd. All rights reserved worldwide. Intersect Alliance Pty Ltd shall not be liable for errors
User Guide to the Snare Agent Management Console in Snare Server v7.0 Intersect Alliance International Pty Ltd. All rights reserved worldwide. Intersect Alliance Pty Ltd shall not be liable for errors
Version Control for Computational Economists: An Introduction
 Version Control for Computational Economists: An Introduction Jake C. Torcasso April 3, 2014 Starting Point A collection of files on your computer Changes to files and new files over time Interested in
Version Control for Computational Economists: An Introduction Jake C. Torcasso April 3, 2014 Starting Point A collection of files on your computer Changes to files and new files over time Interested in
Symantec Backup Exec 12.5 for Windows Servers. Quick Installation Guide
 Symantec Backup Exec 12.5 for Windows Servers Quick Installation Guide 13897290 Installing Backup Exec This document includes the following topics: System requirements Before you install About the Backup
Symantec Backup Exec 12.5 for Windows Servers Quick Installation Guide 13897290 Installing Backup Exec This document includes the following topics: System requirements Before you install About the Backup
Software Configuration Management. Slides derived from Dr. Sara Stoecklin s notes and various web sources.
 Software Configuration Management Slides derived from Dr. Sara Stoecklin s notes and various web sources. What is SCM? SCM goals Manage the changes to documents, programs, files, etc. Track history Identify
Software Configuration Management Slides derived from Dr. Sara Stoecklin s notes and various web sources. What is SCM? SCM goals Manage the changes to documents, programs, files, etc. Track history Identify
How to Choose your Red Hat Enterprise Linux Filesystem
 How to Choose your Red Hat Enterprise Linux Filesystem EXECUTIVE SUMMARY Choosing the Red Hat Enterprise Linux filesystem that is appropriate for your application is often a non-trivial decision due to
How to Choose your Red Hat Enterprise Linux Filesystem EXECUTIVE SUMMARY Choosing the Red Hat Enterprise Linux filesystem that is appropriate for your application is often a non-trivial decision due to
Polycom CMA System Upgrade Guide
 Polycom CMA System Upgrade Guide 5.0 May 2010 3725-77606-001C Trademark Information Polycom, the Polycom Triangles logo, and the names and marks associated with Polycom s products are trademarks and/or
Polycom CMA System Upgrade Guide 5.0 May 2010 3725-77606-001C Trademark Information Polycom, the Polycom Triangles logo, and the names and marks associated with Polycom s products are trademarks and/or
Free Network Monitoring Software for Small Networks
 Free Network Monitoring Software for Small Networks > WHITEPAPER Introduction Networks are becoming critical components of business success - irrespective of whether you are small or BIG. When network
Free Network Monitoring Software for Small Networks > WHITEPAPER Introduction Networks are becoming critical components of business success - irrespective of whether you are small or BIG. When network
Snare Agent Management Console User Guide to the Snare Agent Management Console in Snare Server v6
 User Guide to the Snare Agent Management Console in Snare Server v6 InterSect Alliance International Pty Ltd Page 1 of 14 Intersect Alliance International Pty Ltd. All rights reserved worldwide. Intersect
User Guide to the Snare Agent Management Console in Snare Server v6 InterSect Alliance International Pty Ltd Page 1 of 14 Intersect Alliance International Pty Ltd. All rights reserved worldwide. Intersect
VERITAS Backup Exec TM 10.0 for Windows Servers
 VERITAS Backup Exec TM 10.0 for Windows Servers Quick Installation Guide N134418 July 2004 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software
VERITAS Backup Exec TM 10.0 for Windows Servers Quick Installation Guide N134418 July 2004 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software
ACTi NVR Config Converter User s Manual. Version 1.0.0.17 2012/06/07
 ACTi NVR Config Converter User s Manual Version 1.0.0.17 2012/06/07 Legal Notice Disclaimer The information contained in this document is intended for general information purposes. ACTi Corporation shall
ACTi NVR Config Converter User s Manual Version 1.0.0.17 2012/06/07 Legal Notice Disclaimer The information contained in this document is intended for general information purposes. ACTi Corporation shall
What s New with VMware Virtual Infrastructure
 What s New with VMware Virtual Infrastructure Virtualization: Industry-Standard Way of Computing Early Adoption Mainstreaming Standardization Test & Development Server Consolidation Infrastructure Management
What s New with VMware Virtual Infrastructure Virtualization: Industry-Standard Way of Computing Early Adoption Mainstreaming Standardization Test & Development Server Consolidation Infrastructure Management
Version Control Systems
 Version Control Systems ESA 2015/2016 Adam Belloum [email protected] Material Prepared by Eelco Schatborn Today IntroducGon to Version Control Systems Centralized Version Control Systems RCS CVS SVN
Version Control Systems ESA 2015/2016 Adam Belloum [email protected] Material Prepared by Eelco Schatborn Today IntroducGon to Version Control Systems Centralized Version Control Systems RCS CVS SVN
POC Installation Guide for McAfee EEFF v4.1.x using McAfee epo 4.6. New Deployments Only Windows Deployment
 POC Installation Guide for McAfee EEFF v4.1.x using McAfee epo 4.6 New Deployments Only Windows Deployment 1 Table of Contents 1 Introduction 4 1.1 System requirements 4 1.2 High level process 5 1.3 Troubleshooting
POC Installation Guide for McAfee EEFF v4.1.x using McAfee epo 4.6 New Deployments Only Windows Deployment 1 Table of Contents 1 Introduction 4 1.1 System requirements 4 1.2 High level process 5 1.3 Troubleshooting
Upgrade Guide BES12. Version 12.1
 Upgrade Guide BES12 Version 12.1 Published: 2015-02-25 SWD-20150413111718083 Contents Supported upgrade environments...4 Upgrading from BES12 version 12.0 to BES12 version 12.1...5 Preupgrade tasks...5
Upgrade Guide BES12 Version 12.1 Published: 2015-02-25 SWD-20150413111718083 Contents Supported upgrade environments...4 Upgrading from BES12 version 12.0 to BES12 version 12.1...5 Preupgrade tasks...5
BarTender Version Upgrades. Best practices for updating your BarTender installation WHITE PAPER
 BarTender Version Upgrades Best practices for updating your BarTender installation WHITE PAPER Contents Understanding Version Upgrades 3 Upgrading BarTender to a Newer Version 4 Planning a Version Upgrade
BarTender Version Upgrades Best practices for updating your BarTender installation WHITE PAPER Contents Understanding Version Upgrades 3 Upgrading BarTender to a Newer Version 4 Planning a Version Upgrade
Best practices for data migration.
 IBM Global Technology Services June 2007 Best practices for data migration. Methodologies for planning, designing, migrating and validating data migration Page 2 Contents 2 Executive summary 4 Introduction
IBM Global Technology Services June 2007 Best practices for data migration. Methodologies for planning, designing, migrating and validating data migration Page 2 Contents 2 Executive summary 4 Introduction
Version Control with Git
 Version Control with Git Ben Wasserman ([email protected]) 15-441 Computer Networks Recitation 3 1/28 What is version control? Revisit previous code versions Backup projects Work with others Find where
Version Control with Git Ben Wasserman ([email protected]) 15-441 Computer Networks Recitation 3 1/28 What is version control? Revisit previous code versions Backup projects Work with others Find where
Embarcadero Performance Center 2.7 Installation Guide
 Embarcadero Performance Center 2.7 Installation Guide Copyright 1994-2009 Embarcadero Technologies, Inc. Embarcadero Technologies, Inc. 100 California Street, 12th Floor San Francisco, CA 94111 U.S.A.
Embarcadero Performance Center 2.7 Installation Guide Copyright 1994-2009 Embarcadero Technologies, Inc. Embarcadero Technologies, Inc. 100 California Street, 12th Floor San Francisco, CA 94111 U.S.A.
Software Release Management
 Software Release Management Thomas Lampoltshammer Bernhard Zechmeister University of Salzburg Department of Computer Sciences June 11, 2011 Table of Contents 1 Concepts of Software Release Management Release
Software Release Management Thomas Lampoltshammer Bernhard Zechmeister University of Salzburg Department of Computer Sciences June 11, 2011 Table of Contents 1 Concepts of Software Release Management Release
Networking Best Practices Guide. Version 6.5
 Networking Best Practices Guide Version 6.5 Summer 2010 Copyright: 2010, CCH, a Wolters Kluwer business. All rights reserved. Material in this publication may not be reproduced or transmitted in any form
Networking Best Practices Guide Version 6.5 Summer 2010 Copyright: 2010, CCH, a Wolters Kluwer business. All rights reserved. Material in this publication may not be reproduced or transmitted in any form
Time Machine How-To Guide
 Configuration Guide Time Machine How-To Guide Overview Whether you are backing up data on a regular basis or periodically, Time Machine will save that data on a local or remote disk drive. Saving data
Configuration Guide Time Machine How-To Guide Overview Whether you are backing up data on a regular basis or periodically, Time Machine will save that data on a local or remote disk drive. Saving data
Rapid recovery from bare metal, to dissimilar hardware or to and from virtual environments.
 Product Scenarios StorageCraft Technology Corporation Backup Fast, Recover Faster 2010 StorageCraft Technology Corporation. All Rights Reserved. This brochure is for informational purposes only. STORAGECRAFT
Product Scenarios StorageCraft Technology Corporation Backup Fast, Recover Faster 2010 StorageCraft Technology Corporation. All Rights Reserved. This brochure is for informational purposes only. STORAGECRAFT
Windows Offline Files
 Windows Offline Files 1. Description: Windows Offline Files or Client Side Caching (CSC) allows files and folders stored on any Server Message Block (SMB) network share to be available offline. To further
Windows Offline Files 1. Description: Windows Offline Files or Client Side Caching (CSC) allows files and folders stored on any Server Message Block (SMB) network share to be available offline. To further
Running 4D Server as a Service on Windows
 Running 4D Server as a Service on Windows By Timothy Aaron Penner, Technical Services Team Member, 4D Inc. Technical Note 10-02 1 Table of Contents Table of Contents... 2 Abstract... 3 Introduction...
Running 4D Server as a Service on Windows By Timothy Aaron Penner, Technical Services Team Member, 4D Inc. Technical Note 10-02 1 Table of Contents Table of Contents... 2 Abstract... 3 Introduction...
Streamlining Patch Testing and Deployment
 Streamlining Patch Testing and Deployment Using VMware GSX Server with LANDesk Management Suite to improve patch deployment speed and reliability Executive Summary As corporate IT departments work to keep
Streamlining Patch Testing and Deployment Using VMware GSX Server with LANDesk Management Suite to improve patch deployment speed and reliability Executive Summary As corporate IT departments work to keep
ITIL A guide to event management
 ITIL A guide to event management Event management process information Why have event management? An event can be defined as any detectable or discernable occurrence that has significance for the management
ITIL A guide to event management Event management process information Why have event management? An event can be defined as any detectable or discernable occurrence that has significance for the management
Maintaining HMI and SCADA Systems Through Computer Virtualization
 Maintaining HMI and SCADA Systems Through Computer Virtualization Jon Reeser Systems Engineer PROFI-VISION Automation 1150 Glenlivet Drive Allentown, PA 18106 [email protected] Thomas Jankowski
Maintaining HMI and SCADA Systems Through Computer Virtualization Jon Reeser Systems Engineer PROFI-VISION Automation 1150 Glenlivet Drive Allentown, PA 18106 [email protected] Thomas Jankowski
High Availability and Disaster Recovery Solutions for Perforce
 High Availability and Disaster Recovery Solutions for Perforce This paper provides strategies for achieving high Perforce server availability and minimizing data loss in the event of a disaster. Perforce
High Availability and Disaster Recovery Solutions for Perforce This paper provides strategies for achieving high Perforce server availability and minimizing data loss in the event of a disaster. Perforce
High Availability and Clustering
 High Availability and Clustering AdvOSS-HA is a software application that enables High Availability and Clustering; a critical requirement for any carrier grade solution. It implements multiple redundancy
High Availability and Clustering AdvOSS-HA is a software application that enables High Availability and Clustering; a critical requirement for any carrier grade solution. It implements multiple redundancy
Initial Set-up of Remote Monitoring Service with the APC Network Management Card
 Configuration Guide Initial Set-up of Remote Monitoring Service with the APC Network Management Card Overview This documents explains how to set-up the Remote Monitoring Service (RMS) on an APC Network
Configuration Guide Initial Set-up of Remote Monitoring Service with the APC Network Management Card Overview This documents explains how to set-up the Remote Monitoring Service (RMS) on an APC Network
Faronics Core Migration Guide
 1 2 Last modified: November, 2009 1999-2009 Faronics Corporation. All rights reserved. Faronics, Deep Freeze, Faronics Core Console, Faronics Anti-Executable, Faronics Device Filter, Faronics Power Save,
1 2 Last modified: November, 2009 1999-2009 Faronics Corporation. All rights reserved. Faronics, Deep Freeze, Faronics Core Console, Faronics Anti-Executable, Faronics Device Filter, Faronics Power Save,
